 Open Access
Open Access
REVIEW
Unveiling the Hidden Pixels: A Comprehensive Exploration of Digital Image Steganography Schemes
Department of Computer Science, Central University of Karnataka, Kadaganchi, 585367, India
* Corresponding Author: Nagaraj V. Dharwadkar. Email:
Journal of Information Hiding and Privacy Protection 2025, 7, 1-31. https://doi.org/10.32604/jihpp.2025.060898
Received 12 November 2024; Accepted 23 January 2025; Issue published 27 March 2025
Abstract
Steganography, the art of concealing information within innocuous mediums, has been practiced for centuries and continues to evolve with advances in digital technology. In the modern era, steganography has become an essential complementary tool to cryptography, offering an additional layer of security, stealth, and deniability in digital communications. With the rise of cyber threats such as hacking, malware, and phishing, it is crucial to adopt methods that protect the confidentiality and integrity of data. This review focuses specifically on text-in-image steganography, exploring a range of techniques, including Least Significant Bit (LSB), Pixel Value Differencing (PVD), and Transform Domain methods, to evaluate their effectiveness in real-world applications. The analysis covers key parameters such as embedding capacity, computational complexity, and the interplay with data compression and cryptographic techniques. While significant progress has been made in improving the security and quality of images in steganographic systems, challenges remain. For instance, higher payloads can lead to reduced Peak Signal-to-Noise Ratio (PSNR), compromising image quality. Despite these limitations, recent advancements show promising results in balancing security with minimal distortion. This paper provides valuable insights into the strengths and weaknesses of current techniques, highlighting future research directions that may enhance both the robustness and efficiency of steganographic methods in digital security.Keywords
Acronyms
| AWGN | Additive White Gaussian Noise |
| DCT | Discrete Cosine Transform |
| DPVD | Dynamic Pixel Value Differencing |
| EMD | Earth Mover’s Distance |
| IWT | Integer Wavelet Transform |
| MSB | Most Significant Bit |
| PVD | Pixel Value Differencing |
| SSIM | Structural Similarity Index Measure |
| BPP | Bits Per Pixel |
| DFT | Discrete Fourier Transform |
| DWT | Discrete Wavelet Transform |
| FPR | False Positive Error |
| LSB | Least Significant Bit |
| PSNR | Peak Signal-to-Noise Ratio |
| QI | Quality Index |
| WTEA | White-Tailed Eagle Algorithm |
Digital communication is the cornerstone of modern interaction. It is the process of exchanging messages, data, and information over digital channels between people, organizations, and gadgets. Digital communication modes, including email, instant messaging, video calls, and social media platforms, have revolutionized the way we communicate and collaborate. Digital communication supports real-time collaboration remote work and establishes relations across geographical boundaries. Digital communication has become essential to both personal and professional life, enabling innovation, productivity, and social interaction [1]. However, with the advantages of digital communication also come significant threats and concerns. Among these, the most important issues are those of security and privacy. The digital terrain is at risk from many possible forms of attacks, attacks that range from malicious hacking and data breaches to unauthorized surveillance and interception. As we increasingly depend on digital communication, so does the requirement of taking the necessary steps to save our information assets from such threats increase [2].
Numerous traditional techniques have been put into practice to lessen the risks related to digital communication. Some of them are shown in Fig. 1. Digital cryptography is another method of encryption of messages to ensure their confidentiality and integrity [3]. The use of cryptography in the protection of sensitive communications has been as old as the need for secure transactions of information; the mathematical algorithms and protocols ensure the unavailability of the original message (plaintext) to unauthorized parties [4]. In addition to ensuring confidentiality, cryptography guarantees the integrity and authenticity of data through symmetric and public key cryptographic techniques. A limitation of cryptography is the issue of key management. Steganography addresses this issue by concealing the presence of the message itself [5]. The information age has taken threats to information security to an extremely sophisticated and pervasive level. Cybercriminals illegally access confidential data by taking advantage of network, system, and software flaws. Malware compromises data integrity and confidentiality by infecting systems with viruses, worms, and ransomware, among others. Other major threats involve phishing attacks by hackers who tend to masquerade as authentic entities to extort sensitive information from users [6].

Figure 1: Traditional techniques to mitigate risks in digital communication
In light of the existing and emerging threats posed by cyber criminals, the necessity of higher information protection standards can be deemed inevitable. Companies and businesses operating in various industries are obliged to provide security measures and solutions to secure their intangible assets. Information security continues to remain relevant, not only as a way of protecting the content of information but also as one of the means of maintaining compliance with the requirements of legislation, as well as preserving customers’ trust and ensuring the security of the organization’s reputation [7].
Cryptography remains a core element of information security, employing encryption and decryption techniques to protect and analyse message traffic. It provides confidentiality, Integrity, and authenticity since it maps the sensitive information into an encrypted form termed cipher space which is intelligible only to the authorized parties. Nevertheless, based on the use of encryption, cryptography may actually alert the targeted party to the presence of encrypted communication and hence represents problems in other situations where secrecy and plausible denial are preferred. Furthermore, problems in the area of key management, and the analysis of cryptographic techniques also remain crucial concerns of cryptographic safety and security [3].
Steganography, derived from the Greek word for ‘covered writing,’ refers to the practice of embedding information within seemingly innocuous cover objects. Contrasted with cryptography, where messages are encrypted in order to obscure their understanding. Unlike cryptography, which focuses on obscuring the content of the message, steganography emphasizes hiding the very presence of the message. There are various categories of steganography, including image, audio, video, and text. In any of the above-mentioned categories of steganography, a cover object is chosen as the carrier for the hidden message. Then using specific methods, specific secret data is inserted inside the cover object. On the receiver end, the secret information that was hidden is recovered from the cover object, completing the communication [8]. With the rising need for secure communication, steganography has gained much impetus as an addendum to traditional encryption techniques. While encryption scrambles the contents of a message, steganography embeds a hidden message such that its very presence is not suspected. There are several uses for this skill of sending information covertly, including copyright protection, digital forensics, cybersecurity, and covert communication [9]. Fig. 2 depicts some of the most common image steganography techniques. Audio and video steganography hide information in audio files or video frames, whereas text steganography hides information in text documents or messages. In all the categories, the purpose is to make the cover object look like the original to any naked eye observer but enable safe communication between the intended parties [10].

Figure 2: Common image steganography techniques
In image steganography, embedding algorithms conceal secret data within a cover image using techniques like Least Significant Bit (LSB) substitution, where the least significant bits of the image’s pixels are altered. In the transform domain, techniques like the Discrete Cosine Transform Discrete Cosine Transform (DCT) embed information within the frequency components of the image. The extraction algorithms recover the hidden data by reading the modified bits or coefficients. The goal is to maximize the data capacity of the steganographic image while maintaining its imperceptibility. At the same time, the image must remain robust against processing operations without compromising these two aspects. In summary, these algorithms work together to securely hide and recover information from images, ensuring they remain undisturbed [11]. This flow is shown in Fig. 3 and Fig. 4.
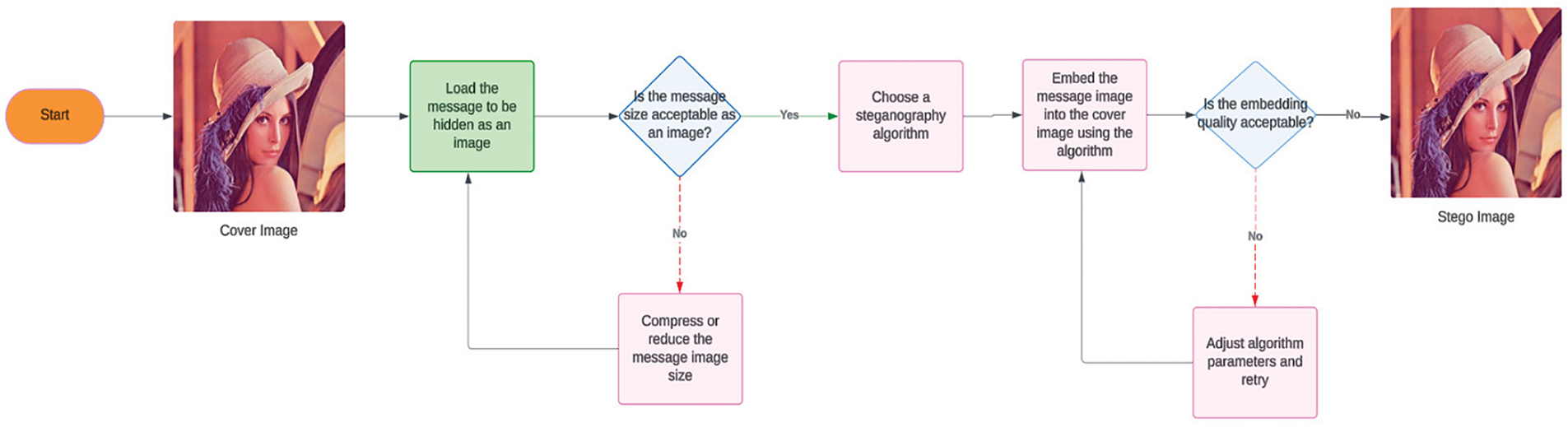
Figure 3: Flow of image steganography using embedding algorithm
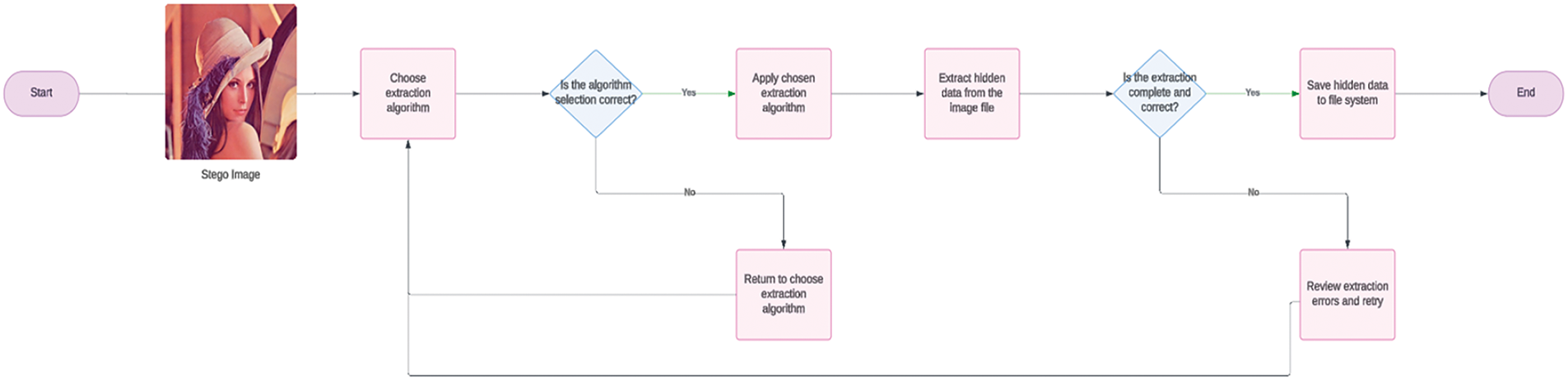
Figure 4: Flow of image steganography using extraction algorithm
The following are important terms necessary for a comprehensive understanding of steganography [12]:
1. Cover Image: The original image used for hiding the secret message.
2. Stego Image: The image with the secret message embedded in it.
3. Payload: The amount of secret message embedded within the cover image.
4. Embedding: The process of hiding data within the cover image.
5. Extraction: The process of retrieving the hidden data from the stego image.
6. Steganalysis: The detection and analysis of hidden messages within carrier media.
7. Cover Selection: The process of choosing an appropriate cover image for embedding the secret message.
8. Capacity: The maximum amount of information that can be embedded into a cover image without significantly altering its appearance.
Steganography is an effective complement to the limitations of traditional encryption in secure communication. Essentially, steganography differs from cryptography in that it hides the message rather than the contents of the message, since it inserts the message within digital data, which is often difficult to recognize. Steganography complements cryptography by concealing the message within other content, making it harder to detect.
The relationship between steganography, cryptography, and data compression is that they both work to protect information but go differently in methodology. Steganography conceals messages within other data, so the presence of such a message is hard to identify. Cryptography encodes messages for the safe transmission of data; data compression reduces data size for easy handling, as shown in Fig. 5. These techniques can be employed singularly or together to increase security. For example, a message may first be compressed to reduce its size, encrypted to ensure confidentiality, and then embedded into a cover image using steganography for covert transmission. This integration of compression and encryption with steganography may significantly enhance the effectiveness and versatility of secure communication [13–15]. With modern society advancing into a world where communication is increasingly shifting to the online environment, the combination of methods for protecting information has become even more relevant to cover new demands.
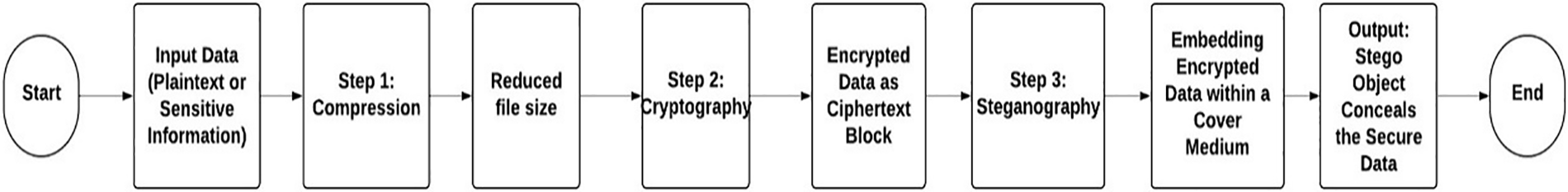
Figure 5: Flow of image steganography using extraction algorithm
Together, these techniques offer a comprehensive solution for protecting digital communication and personal information, ensuring confidentiality and trust even amidst evolving threats [16]. Due to the increasing landscape of cyber threats, a number of techniques related to information hiding have emerged as inherent modules within an information security paradigm. All these techniques aim to embed sensitive information within digital content in such a way that it remains undetected by unauthorized parties. One such technique is steganography, which embeds secret information inside cover media in ways imperceptible to unauthorized parties. Steganography embeds hidden information by altering pixels in images, samples in audio files, or frames in video streams in ways that are imperceptible to the human eye or ear [17].
This paper provides a comprehensive study of various steganography techniques, focusing on recent advancements in both spatial and transform domains. The aim of this study is to discuss different approaches and analyse their benefits and notable limitations. This will cover basic steganography methods as well as techniques that combine data compression and cryptography. The paper begins with an overview of current research in steganography. It then analyses various steganography techniques, evaluating their effectiveness and practical applications. The performance metrics section further assesses these techniques in terms of embedding capacity and computational complexity. Finally, the review concludes with the research findings and suggests directions for future research.
Spatial domain refers to the original representation of an image or signal in terms of its spatial coordinates; for example, an image is said to be represented as rows and columns of pixels, or samples in a signal. Operations that are performed directly in the spatial domain of an image. This includes basic operations like pixel value changes, filter application, or direct operations based on image or signal data in an arithmetic manner [18].
The popular and understated original technique LSB gives birth to all the modifications and other techniques in image steganography; the alteration of LSB will only cause a slight change in color and, therefore, is mostly not visible to the human eye. Authors in [19] proposed the use of both LSB and Most Significant Bit (MSB) in color image steganography. The scheme uses a 24-bit color image with RGB values ranging from 0 to 255, where each pixel is represented by 3 bytes and one byte is used for embedding the LSB. Working is done in three steps: embedding and extraction using the secret key as the scheme, embedding it after the sinusoidal function is used to find the embedding locations, and finally, conditional embedding based on the size of the cover image. The use of both LSB and MSB embedding results in an increase in embedding capacity and robustness, but this increases the complexity of the method. Finally, the secret message is extracted using the same secret key and the LSB/MSB manipulation. Authors in [20] proposed the approach through bit rotation and inversion scoring to present a fresh approach to LSB extraction and embedding in grayscale images. This new approach based on bit rotation and inversion scoring these employ the classical method of image steganography by replacing the least significant bits of grayscale pixels in the cover image. The size of the message is embedded in the LSBs of the first 16 grayscale pixels. The process of embedding involves grouping pixels of the cover image with calculated gaps and replacing their LSBs with bits of the secret message. During extraction, the size of the message is extracted first, and then the embedded message is retrieved. It takes into consideration the rotation and inversion indicators during extraction, enhancing the robustness against steganalysis. The method proposed by [21] is a bi-directional LSB steganography scheme that creates fixed-size blocks out of the cover image’s LSB plane. Depending on how similar the cover and message bits are, the bits of each block are XOR’d with the matching message bits to determine whether the message will be encoded forward or backward. The performance evaluation demonstrates how effectively the information is hidden while preserving image quality, using metrics such as mean squared error and structural similarity indices in addition to its potential to minimize detectability by lowering the quantity of bits in the cover image that must be altered. However, this method may lack robustness in high-security scenarios, as its focus is more on minimizing the impact on the cover image rather than ensuring high security. In summary, spatial domain techniques for image steganography have been explored in various forms: some offer straightforward advantages in terms of ease of implementation but come with simple challenges related to detectability, while more advanced techniques such as combinations of LSB and MSB embedding, bit rotation and inversion scoring, and bi-directional LSB steganography offer better embedding capacity, robustness, and security, albeit at the cost of increased complexity and computational resources. This evolution highlights a trade-off between preserving image quality and enhancing the security of the embedded information an area of ongoing research.
For I be the cover image represented as a matrix of pixel intensities, where Ii,j represents the intensity value of the pixel at coordinates (i, j). The Pixel Value Differencing (PVD) algorithm calculates the difference between adjacent pixel intensities in the cover image. This can be represented as:
where
Finally, the stego image is generated by updating the pixel intensities based on the modified differences:
where
In image steganography, the image is divided into multiple blocks, and pixel differences are altered to suit the need for embedding, as explained by [23]. The adaptive block-based PVD technique is proposed by [24]. In the presented PVD scheme, the image under consideration is transformed into non-overlapping blocks of size 3 × 3, and the difference matrix is computed based on the median of the pixel differences in each block. The algorithm adjusts the minimum and maximum difference range, placing the secret data in regions of the image with high-intensity fluctuations. Confidentiality is enhanced by embedding data in areas with edges and intensity gradients, avoiding smooth or flat regions.
Texture images, which exhibit higher embedding capacity compared to normal images, are also considered in this method, further improving the algorithm. The proposed algorithm performs well, particularly at low embedding rates, yielding a higher Peak Signal-to-Noise Ratio (PSNR) compared to conventional PVD methods. Such enhanced PVD for color images is employed by [25] using a technique called Dynamic Pixel Value Differencing (DPVD), which not only embeds data in optimal directions but also in each channel. It splits the cover image into pixel blocks and computes horizontal, vertical, and diagonal PZ means per frame.
According to the PVD method, data bits are buried in each block depending on the maximum embedding limit for every channel direction. Extraction requires partitioning of the stego-image as in the embedding algorithm, computing the new differences, and obtaining the binary data of each color channel depending on the maximum embedding directionality. DPVD not only enhances embedding capacity but also increases the extraction difficulty by extending the embedding process across the color channels of the image.
As for the spatial domain, image steganography techniques present a wide variety of methods, each of which has unique advantages and drawbacks. Some techniques, such as LSB, are quite simple and can be implemented with low computational complexity; however, they are easily detected. The advanced techniques include basic PVD and MSB as well as incorporating S/N chaotic maps, which improve security and capacity and sometimes, but not necessarily, lead to higher complexity and computational costs. The development of steganography techniques is still actively focused on improving embedding efficiency, robustness, and resistance to steganalysis attacks.
The use of LSB in combination with PVD leverages the simplicity of LSB and the robustness of PVD. By integrating these techniques, the goal is to improve both the embedding capacity and the likelihood of avoiding detection. For instance, while single or dual LSB (Least Significant Bit) is a basic approach suggested by [26], there is the variant called Five Directional PVD with Modified LSB Substitution that divides the image into non-overlapping blocks. Each block is then transformed using k-bit Least Significant Bit substitution. This involves calculating the difference values and using binary bits from the secret data stream based on the range tables while optimizing pixel values to avoid boundary issues. In addition to the regular embedding process, extraction involves a reverse procedure, using additional directional computations to recover the embedded data. This technique has been enhanced by merging the advantages of PVD and LSB methods, improving its embedding accuracy and capacity. Splitting the image into a set of independent n × n blocks and using k-bit LSB substitution regulates pixel values within the block and avoids boundary problems.
Pradhan et al. [27] presented a study that combines Least Significant Bit (LSB) substitution, Pixel Value Differencing (PVD), and Exploiting Modification Direction (Earth Mover’s Distance (EMD)) to optimize embedding capacity and imperceptibility. The authors utilized a hybrid approach where LSB enhanced simplicity, PVD improved payload capacity, and EMD ensured minimal distortion. The results showed a hiding capacity of up to 4 bpp and PSNR values exceeding 40 dB, indicating strong imperceptibility. However, Structural Similarity Index Measure (SSIM) and Quality Index (QI) were not discussed in detail, limiting the robustness assessment. While this methodology effectively balances capacity and imperceptibility, further exploration of its security against complex attacks is needed.
Authors in [28] introduced a new embedding technique in gray-scale images where pixel pairs are 1 × 2 blocks and compared their difference to determine how many hidden bits need to be included The quantization levels control the embedding process by categorizing pixel intensities into three ranges: low, medium, and high occurrences. In contrast, extraction is carried out by using the range table to determine the quantity of additional inactive bits and then extracting them in accordance with the LSBs. This method enables an elegant writing of the secret data and extraction without any other information; it equally provides a perfect hiding of text without causing much interference to the image quality. In this context, Authors in [29] proposed a steganography model utilizing a Duffing map to generate a random index vector (RIV) for data hiding. Chaotic sequences are employed to enhance embedding capacity without significantly affecting distortion. The RIV that excludes the true values along with the indices and they are not repeating within the image dimensions offers ultimate embedding. The process involves mapping the cover image and secret message to the image, generating chaotic random numbers, and acquiring exclusive indices before modifying the LSB of the concealed image as guided by the RIV. However, one must bear in mind that there is a collision probability associated with the indexes being generated, which means that the generated index can accidentally overwrite other data or even alter it.
Authors in [30] formulated steganography algorithm that uses PVD in combination with LSB on RGB covers to embed the secret data. As opposed to an ordered map which works through pixels in a sequential manner, hence the security is improved. There are two kinds of steps in preprocessing, namely RGB channel extraction and Integer Wavelet Transform (IWT). The process of embedding begins at the high-frequency sub bands and the process of postprocessing includes, reconstruction of image and inverse wavelet transform. Extraction remains similar to embedding, whereby it applies the same chaotic map alongside a secret key. It meets requirements for shallow hiding and does not compromise the quality of the image, but may be vulnerable to detection techniques designed for non-sequential hiding patterns. Authors in [31] combined LSB substitution with error correction coding, using Hamming codes to enhance robustness and ensure reliable data extraction in noisy conditions. The hybrid approach emphasizes maintaining visual imperceptibility, achieving a PSNR of over 35 dB and SSIM values above 0.90, demonstrating minimal perceptual degradation. While the integration of error correction strengthens resistance to noise, the method’s payload capacity is limited compared to techniques like PVD or EMD. This makes it ideal for secure communication in environments prone to noise, though further optimization is required for applications demanding higher embedding capacities, particularly in hybrid spatial steganography systems.
Tables 1–3 summarize various spatial domain techniques, highlighting their respective advantages and limitations. The techniques include the least significant bit embedding, hybrid techniques, generation of random sequences, bi-directional techniques of coding, block-based techniques, and chaotic algorithms. Advantages include high security with an increase in the efficiency of embedding and minimal distortion of images. Limitations include computational complexity, vulnerability in attacks, and possible degradations of image quality. Each technique has unique features that enhance the embedding capacity or resistance to steganalysis, but at the cost of one or the other; thus, much care should be taken according to specific application requirements.



The transform domain refers to an alternative representation of image data, obtained by applying mathematical transformations such as the Discrete Fourier Transform (DFT), DCT, Discrete Wavelet Transform (DWT), and others. Transforming the image into a different domain can reveal certain features or properties of the data that may be useful for embedding secret information or for enhancing certain aspects of the steganographic process, such as imperceptibility or robustness against attacks. It manipulates transformed coefficients instead of pixel values, offering new opportunities for data hiding and manipulation [32].
Most commonly used Technique DCT works as per follows:
Given a finite sequence of N data points x[n] for 0n < N, the DCT of order N is defined as:
where
The inverse DCT (IDCT), which transforms the signal back from the frequency domain to the spatial domain, is given by:
Various normalization factors may be applied to the DCT formulation depending on the specific variant (e.g., Type-II DCT used in JPEG compression).
According to the study by [33], proper covering selection based on local variance allows for the imperceptibility of the watermark. Following this, the DCT to the YCbCr components is used to determine relevant scales. The message bits to be conveyed secretly are embedded under curvelet coefficients. A key is used to select the blocks. The extraction process involves converting the stego RGB images to YCbCr, computing the DWT of the Cb and Cr components, and extracting the hidden bits using the key. The process of embedding the data into the curvelet coefficients preserves a high level of security, as keeping it out of the reach of unauthorized users affects the neighborhood of the transformed shape of the coefficients. The accuracy of the algorithm depends on parameter settings such as α, β, and δ, which may need to be adjusted to suit different situations.
To improve the steganographic capacity of JPEG images, authors in [34] introduced an improved method that utilizes Block Entropy Transformation (BET) to enhance JPEG steganography by spatially embedding entropy in the DCT domain. It employs spatial distortion measures to encode the embedding entropy for each DCT coefficient that is used in JPEG images. The distortion measure for quantized DCT coefficients is derived using inverse mapping of optimum parameters for minimal distortion embedding. BET is employed for initial embedding, and Gaussian filtering is applied to smooth the distortion in the way described below. Additionally, this method combines both spatial and JPEG domains to create a more secure steganography technique, which minimizes distortion, as demonstrated in the experimental results.
To minimize embedding errors and produce stego-images that closely resemble normal images, undetectable to the naked eye, authors in [35] developed a technique that integrates DT-CWT with data embedding for steganography. Initially, the RGB cover image and the secret image are pre-processed. The secret image is transformed into its gradient and blurred versions through Gaussian smoothing. Next, DT-CWT is applied to the cover image, producing coefficient sub-bands that increase the embedding capacity. These sub-bands contain secret patches, which are embedded using intensity mapping. Finally, in step 6, the coefficients are inverted back into the spatial domain for transmission. During retrieval, the stego-image undergoes the DT-CWT process, after which the patches, embedded with exclusive keys, are extracted and transformed back into the secret image.
Authors in [36] suggested an approach to reduce distortion in the resulting stego-image to provide near-perfect representation of the cover image while holding the messages. This approach utilizes the DCT, One-Time Pad (OTP), and Pseudo-Random Noise Sequence (PN-Sequence) to securely embed and extract messages within grayscale images. In the encryption and embedding process, the cover image is divided into multiple blocks, from which the DC coefficients are extracted using the DCT. The second message, a secret binary image, is encrypted with OTP and embedded into the DC matrix using PN-Sequence binary numbers, ensuring that the message remains intact and accessible only to the authors. The decryption and extraction processes closely mirror the embedding process. The DCT and PN-Sequence are used to extract the hidden message, while OTP decryption is applied to decode the resulting secret image.
For JPEG image steganography, authors in [37] proposed a two-module approach. This approach involves encrypting the secret message, embedding it into the carrier signal, and decoding the same signal to retrieve the encrypted message. The encoding module involves dividing the image into smaller 8 × 8 blocks, applying the DCT, quantization, embedding the secret message using Singular Value Decomposition (SVD), and finally performing entropy encoding. The extraction module of the steganography system is responsible for retrieving the hidden message from the stego-image by reversing the above processes. This approach is based on JPEG compression, where the message is embedded during the distortion process, which helps in the transmission and storage of secret information, thereby enhancing the overall effectiveness of the process. The mathematical formulations of the forward DWT and its inverse (IDWT)
Forward DWT: Let I(x, y) be the pixel intensity of the image at coordinates (x, y). The forward DWT decomposes the image into approximation (low-frequency) coefficients LL and detail (high-frequency) coefficients LH, HL, and HH. The approximation coefficients LL are obtained by convolving the image with a low-pass filter h and downsampling by 2 in both dimensions:
The detail coefficients LH, HL, and HH are obtained similarly by convolving the image with high-pass filters g1, g2, and g3 (or their flipped versions) and down sampling:
where h, g1, g2, and g3 are the filter coefficients.
Inverse DWT: The inverse DWT reconstructs the original image from the approximation and detail coefficients. It involves up sampling and filtering operations using synthesis filters h˜, g1˜, g˜2, and g˜3. The reconstructed image I^(x,y) is obtained by:
where LL, LH, HL, and HH are the approximation and detail coefficients, and
Authors in [38] described a method that uses double wavelet transforms in a steganographic approach, enabling the insertion of secret text into the cover image. First, the cover image is decomposed into wavelet coefficients by applying 2D DWT, and the secret text is converted to its ASCII codes and then transformed into its wavelet coefficients with 1D DWT. According to the sign of these HH coefficients, the pixels of the cover image and text pixels are combined to create stego-pixels. Finally, the stego-image is formed by performing an inverse wavelet transformation of the concatenated quarters of waves. This embedded technique improves the construction of a two-dimensional digital watermark by using a dual wavelet transform approach in both the spatial and frequency domains, offering higher security and robustness compared to single transform methods.
In recent work, authors in [39] suggested a steganography algorithm that employs Quaternion Fast Fourier Discrete Transform (QFFDT) to hide textual messages in cover images for maximum security and stability. They minimize an embedding function and maximize an extraction function. In this process, the cover image is altered using the quaternion Fourier transform and small ratios to embed the secret message. During extraction, the hidden message is retrieved from the stego-image using cropping operations and the inverse quaternion fast Fourier transform, minimizing data degradation. This method utilizes the ability of QFFDT to deal with quaternion-valued signals and offers the best approach to hiding textual messages within cover images without much distortion.
Authors in [40] introduced a steganographic method based on Singular Value Decomposition (SVD) and 2D DWT for embedding and extracting messages. SVD and 2D DWT are used to embed the process based on the message image and the cover image, respectively. The S matrix extracted through SVD is well concealed within the HH matrix of DWT, while the U and V matrices act as keys. In this process of feature extraction, the DWT of the stego-image is calculated to produce sub-bands, from where the S matrix is derived from the HH matrix and the U and V matrices are extracted to reconstruct the message image through the inverse SVD. The proposed multi-layered approach enhances resilience while maintaining a high PSNR. It also protects digital media from certain attacks, such as (Additive White Gaussian Noise (AWGN)). Authors in [41] introduced a method that employs wavelet domain transformation and adaptive weights to increase the robustness of data regarding data loss.
This process involves decomposing the original image into blocks and applying the second-generation 2D DWT to each block. An adaptive algorithm assigns weights to the wavelet coefficients, and blocks whose total 2D weights are below a preset threshold are transmitted. The coefficients are then converted into binary form, and the secret data is embedded in the Least Significant Bit (LSB) section. The extraction of secret data at the receiver end is only possible if both block partitioning and all block indices are transmitted securely. MSE, PSNR, and SSIM were used to compare the proposed method with existing methods, and visual results were also assessed. Although the adaptive algorithm and wavelet transformation offer optimal data embedding and extraction processes suitable for real-time applications, the high computational demands of these techniques can raise concerns regarding their impact on computational capacity.
This process involves decomposing the original image into blocks and applying the second-generation 2D DWT to each block using an adaptive algorithm. From them blocks with lower total weight are preferred being selected for the secret data embedding into their LSBs. Decoded blocks are returned to decimal representation; then the two-dimensional Inverse Discrete Cosine Transform is provided to get the stego image. It is evident that the block size influences performance metrics and accuracy, without compromising image quality.
Tables 4–6 show the strengths and weaknesses of techniques that use approaches in the transform domain. It provides a summary of transform domain techniques used in steganography, along with their advantages and drawbacks, as identified in various research articles. Advantages include expansion of the message capacity, improvement of message security, and ability to maintain picture quality; disadvantages include susceptibility to specific forms of attack, high computation costs for encryption and decryption procedures, and variation in the measure of security based on parameters such as the block size of the image. As will be discussed, each algorithm performs well in different scenarios, depending on factors such as flexibility to work with different image formats or resistance to certain types of attacks. However, factors like available computational power and acceptable levels of distortion are crucial in real-world applications. Specifically, transform domain techniques play a vital role in advancing the capabilities of steganography. They offer the advantages of higher message-hiding capacity, enhanced security, and better image quality preservation, while also providing the flexibility needed to improve steganographic methods. Compared to standard techniques, each transform domain method has its own strengths and weaknesses. In this context, it is essential to recognize these distinctions to avoid misunderstandings and ensure the best course of action is taken in any given situation.

4 Techniques Using Data Compression
This section discusses the techniques that use various algorithms to compress data before embedding it into cover images or text to reduce the size of the secret message while maintaining security. Data compression plays a pivotal role in steganography by reducing the size of the payload, which enhances embedding efficiency and minimizes the detectability of hidden data. It not only optimizes the use of storage space in cover media but also adds an additional layer of security by transforming the message into a compact format before embedding [13–15]. Integrating data compression into steganographic systems improves the embedding process’s efficiency and reduces the detectability of the hidden message. This synergy between data compression and steganography provides a robust solution for secure and efficient communication in scenarios requiring both data protection and resource optimization [44,45]. To begin, let’s define key terminologies necessary for understanding these techniques [46]:
• Lossy Compression: Reduces the amount of data by eliminating unnecessary information. However, it results in a loss of some data.
• Lossless Compression: Reduces the amount of data without losing any information to ensure that the hidden data remains intact during compression and extraction.
• Entropy Coding: Shorter codes are assigned to more frequent data values and longer codes to less frequent ones using entropy coding based on their probability of occurrence.
• Run-Length Encoding (RLE): A count and a single value are substituted for sequential identical data values in RLE, a basic type of lossless compression.
Authors in [47] incorporated the Deflate compression algorithm with the LSB approach. Deflate compression uses LZ77 and Huffman coding techniques. LZ77 uses a dictionary-based mechanism where character matches are recorded using parameters such as offset, length, and codeword. Huffman coding produces a tree from character frequencies and represents characters as a binary code. LSB message embedding is done after the secret message is compressed. In manipulating the color channels of the cover image, LSB embedding is used in either red, green, or blue. In this way, integrating the Deflate compression algorithm with the LSB approach gives advantages in steganography. In the technique proposed by [48], the secret data is embedded after multilayer encoding, and False Positive Error (FPE) is applied using Huffman coding. This technique combines cryptography and compression techniques to tackle the problems of imperceptibility and security. The secret message undergoes multilayer encoding using FPE, which reduces its size while enhancing security. Thereafter, Huffman Coding is applied to it for further compression. The secret message is thus compressed through the Huffman tree so constructed.
To selectively embed information in high-texture regions, authors in [49] proposed the ADEDGEMME2 method, which utilizes matrix encoding and region selection to improve data hiding. It uses the MME2 method for adaptive embedding to enable multiple embedding solutions while maintaining pixel block complexity. Region selection relies on the complexity of pixel blocks to select areas where the texture is high so that distortion is minimized. The approach estimates complexity through the use of pixel differences, whereby blocks with complexity above 1.0 are chosen for embedding. While this method improves security against various attacks, its reliance on pixel block complexity for region selection may limit its applicability to certain types of images, particularly those with uniform textures.
Authors in [50] proposed a new technique called HEWTEA-IS. This method applies Haar DWT for decomposition of the image into frequency bands. For the selection of pixels, it uses a White-Tailed Eagle Algorithm (WTEA). Huffman encoding provides lossless data compression. During extraction, DWT transforms the stego images back into spatial representation. WTEA locates the hidden information, and Huffman decoding will produce the secret message. The chaotic map-based WTEA optimizes pixel selection, thereby enhancing the security of the method. By using the WTEA and Huffman encoding, the method provides robustness against detection. Using Haar (DWT) and taking care in choosing the frequency bands, the method ensures secrecy while maintaining image quality.
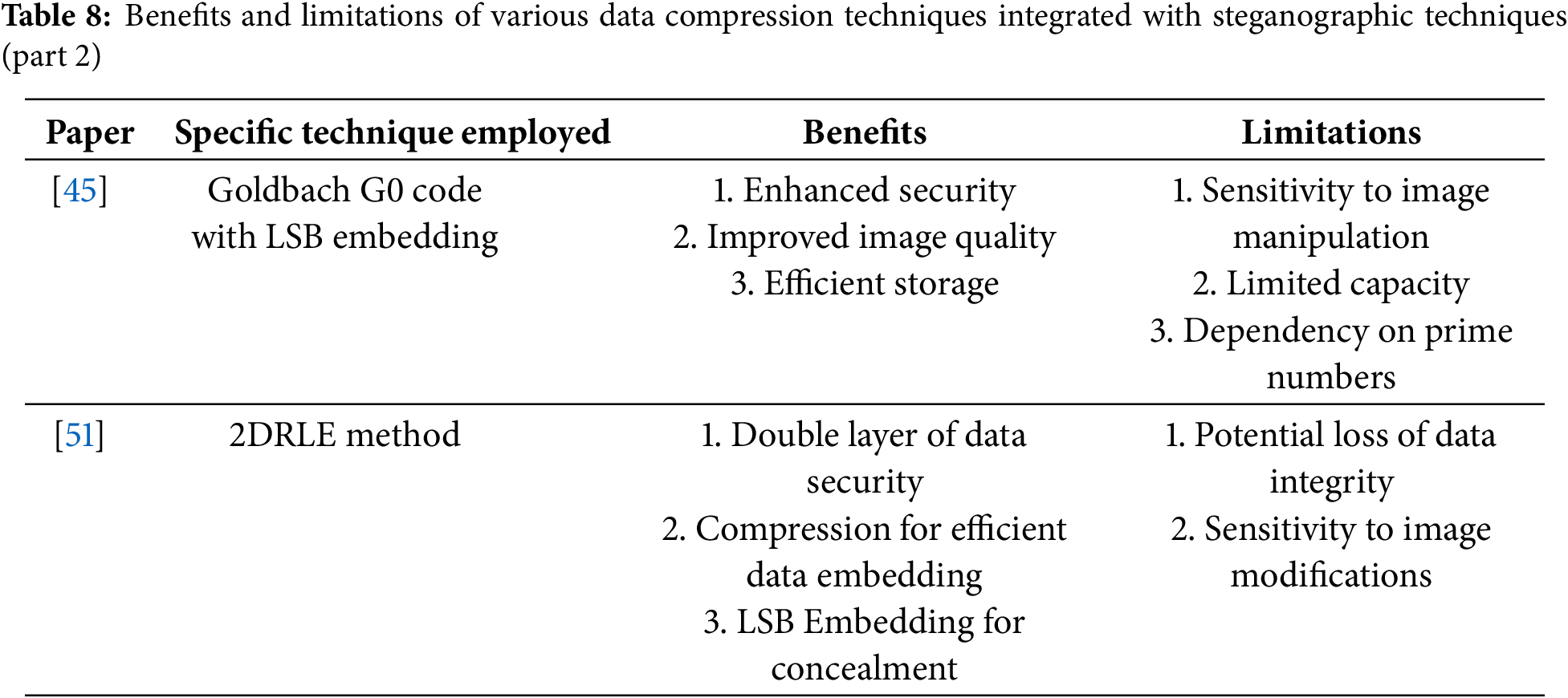
Method proposed in [45] utilizes the Goldbach G0 code for text compression. It first sorts the characters based on how frequently they appear and in what order. Then, to each character, its binary equivalent is associated with the codeword from the first two prime numbers from the computation of 2(n+3). Then, the codeword is substituted for each character of the text. After that, LSB hides the text within the cover image. This technique embeds the compressed text into the cover image using LSB, arranging characters according to their frequency of occurrence. As a result, the data is efficiently hidden with the least amount of processing overhead. The 2DRLE method, which uses lossless text image compression, was proposed by [51] to generate a compressed image with a smaller file size compared to the original. Three stages will comprise the 2DRLE method: row scanning, column scanning, and entropy coding. Row scanning involves the storage of consecutive repeated rows of the image as single rows; column scanning will then be applied to the resulting image, identifying and storing consecutive repeating columns. The resulting symbol set from both row and column scanning is encoded using Huffman coding, further reducing the image size by representing the most frequent symbols with shorter codes. This method significantly reduces the image size by compressing white space repetition.
Tables 7 and 8 outline the advantages and drawbacks of data compression techniques integrated with transform-domain steganography methods. The steganography techniques include techniques such as Huffman compression, DCT, and Deflate compression. Benefits are lossless compression, enhanced security, enhanced image quality, and increased hiding capacity. The deficiencies arising from these techniques include potential loss of data during compression, dependency on image quality, and complexity in managing the encryption key. Each of the approaches offers specific advantages, such as efficient embedding or additional security layers, but practical implementation has to take into consideration challenges like sensitivity of parameters and data integrity to realize optimized data storage, efficiency in transmission, and robust security in actual scenarios.

5 Techniques Using Cryptography with Data Compression
Techniques that use cryptography first encrypt the secret message using cryptographic algorithms to ensure data security. Then, they compress the encrypted message to reduce data size for efficient transmission and storage within cover images or texts. This dual layered approach enhances both security and efficiency: encryption ensures confidentiality, while compression reduces the data footprint, making it more difficult to detect and intercept during transmission. For instance, symmetric encryption algorithms such as AES (Advanced Encryption Standard) or DES (Data Encryption Standard) are commonly used to encrypt messages before compression. The encrypted data, being more randomized, also benefits from entropy-based compression techniques, which further reduce its size. These methods are particularly useful in scenarios where both security and efficient use of cover medium capacity are crucial, such as secure multimedia sharing or covert communications in bandwidth-constrained environments [14,44,45]. Here are some commonly used terminologies for understanding techniques in this domain.
• Encryption: The process of transforming readable data, or plaintext, into ciphertext is called encryption.
• Decryption: The process where ciphertext is converted back into plaintext.
• Symmetric Encryption: A single key is used for both encryption and decryption in symmetric encryption.
• Asymmetric Encryption: A public key is used for encryption, and a private key is used for decryption in asymmetric encryption.
Authors in [52] proposed method for text steganography, which makes use of Unicode characters and encryption techniques for concealing a secret message in a cover text. It involves the encoding of the secret message by utilizing the AES encryption algorithm and embedding it within the cover text by using Unicode characters. The embedded message is then compressed using the Huffman algorithm to reduce the stego-text size, achieving high compression efficiency. This approach guarantees both security and data compression efficiency regarding concealing information in the text documents. The algorithm proposed by [53] combines RSA encryption with various data compression techniques, such as Huffman coding, RLE, or DWT, in steganography. The secret message is first encrypted using RSA during the embedding process and then inserted into the LSB of the cover image. The stego-image is then compressed using the RLE, DWT, or Huffman coding methods. The stego-image is decompressed, the message is extracted from the LSBs, and RSA is used to decode it. RSA-based encryption provides the line of defence for the secure transmission of the message. The role of Huffman coding, RLE, or DWT is to reduce the size of the stego-image and optimize the storage and transmission. While compression reduces the file size, it may also cause some information loss, potentially affecting image quality. To share the symmetric key securely, the system proposed by [54] uses both cryptography and steganography in tandem. Through AES encryption with symmetric key sharing, messages are encrypted and hidden in cover images, thereby evading visual detection. SCrypt hashing algorithm enhances security on shared keys against dictionary attacks. Compressing the messages, AES encrypts in counter mode CBC, encoding and embedding in cover images using LSB. The message is recovered through the extraction of stego-objects and password validation via the SCrypt hashing algorithm. Integration of AES encryption and SCrypt hashing enhances the confidentiality and integrity of messages. Authors in [55] proposed a technique combining a variant of the Collatz Conjecture with Diffie-Hellman Key Exchange to establish a shared secret key and generate unique random locations for LSB-based image steganography. By modifying the Collatz Conjecture, unique random numbers are generated iteratively from a given secret key. These generated random numbers determine the pixels for hosting the secret message bits in a way that is both secure and robust. Encryption is performed by XORing the secret message with the random numbers represented in binary. The Diffie-Hellman Key Exchange provides a mechanism for generating the keys without actually sending the key over the internet; hence, the possibility of its interception is reduced to a minimum. Successful implementation would require that the shared secret key generated through the Diffie-Hellman Key Exchange be kept secure to avoid access by unauthorized users and thus ensure confidentiality. Authors in [56] proposed system that combines DWT compression, AES encryption, and LSB steganography for advanced data security. In the embedding phase, the secret image is first compressed using DWT and then encrypted using AES prior to its embedding into the cover image using LSB. In the extraction phase, the cipher text extracted from the stego-image is decrypted using AES and decompressed using DWT to retrieve the secret image. Huffman coding and achromatic components are utilized in this approach to enhance data encoding and representation. DWT compression may deteriorate the image quality, especially with increased compression ratios. Authors in [57] proposed the two-stage encryption, one-stage steganography approach for data security enhancement, wherein the integration of steganography and cryptography is done. First, the important text is divided into two parts, encrypted separately by the Caesar Cipher and Vigenère Cipher. Thereafter, the ciphertext is converted into Morse code to further encrypt the ciphertext. Finally, the ciphertext written in Morse code is embedded inside an image with the help of the LSB technique to hide the encrypted message within the cover image. Multi-layering is the best approach for the encryption of the data and transmitting it safely, and it reduces the file size through compression techniques like Morse coding and LSB embedding. The encryption methodology proposed by [58] consists of two major stages: modified Caesar Cipher encryption and Card Deck Shuffle Rearrangement. The first part consists of a modified version of the Caesar Cipher algorithm that encrypts image pixels with variable shifts determined by keys extracted from the master key for added security and to avoid easy decryption. The second part of the process is the pixel rearrangement using a transposition Cipher adapted to the riffle shuffle technique. The two-fold encryption strengthens data security and makes decryption more difficult. Modifying the Caesar Cipher with variable shifts and using a transposition cipher for pixel rearrangement significantly enhance data security, making decryption much more difficult for attackers. The effectiveness of the encryption scheme depends on the proper setting of parameters, such as key sizes and the number of sub-decks, which must be carefully tuned for optimal performance.
The proposed encryption algorithm of [59] presents a novel approach using frequency domain compression and lightweight chaos. It uses dynamic key generation with plaintext correlation, applying chaotic sequences for encryption. Dynamic key generation, time domain shifting, DCT coding, quantification, coefficient extraction, compression coding, coefficient scrambling, and diffusion encryption are the main steps included in this algorithm. The algorithm transforms the given plaintext images to the corresponding cipher text images by passing through a series of domain transformations, including frequency domain mapping and chaotic sequence-based encryption. This work uses dynamic keys and chaotic sequences, which enhance information security, making the encrypted information difficult for unauthorized users to interpret. The technique proposed by [60] provides an efficient encryption and decryption process and is fit for real-time applications with secure data transferring. It combines AES crypto-algorithm with Dynamic XOR for image steganography. AES handles the secure encryption and decryption, while Dynamic XOR conceals the message in the image. During encryption, the message is first converted to binary bits, and each pixel value is XORed with a dynamic key derived from the message.
Subsequently, the resulting image is encrypted using AES. Reversing this process yields the decrypted image, from which the hidden message can be extracted the dynamic XOR hides the message in image without any distortion of visual quality; thus, from the visual point of view, it would be hard to detect for third parties. The handling of keys, particularly for Dynamic XOR, requires meticulous care to prevent unauthorized access and ensure data integrity.
As per Tables 9 and 10, cryptographic and data compression methods combined with transform domain steganography to offer advantages in security, high hiding capacity, and data transmission efficiency but are limited by factors like computational complexity, susceptibility to different attacks, capacity constraints, and image distortion. RSA, AES, Huffman coding, and LSB encoding are some of the techniques that improve data confidentiality and robustness; however, some factors need to be taken into consideration, such as key management, algorithm dependency, and the computational overhead the solution brings with it. This integration of cryptography and data compression creates a robust framework for secure communication. By encrypting the message before compression, the system achieves layered protection, ensuring that even if the compression is reverse-engineered, the data remains secure due to the encryption. This dual technique is particularly beneficial for applications requiring high security and optimal storage or transmission efficiency, such as secure financial transactions and military communications.


6 Summarized Results of above Discussed Techniques
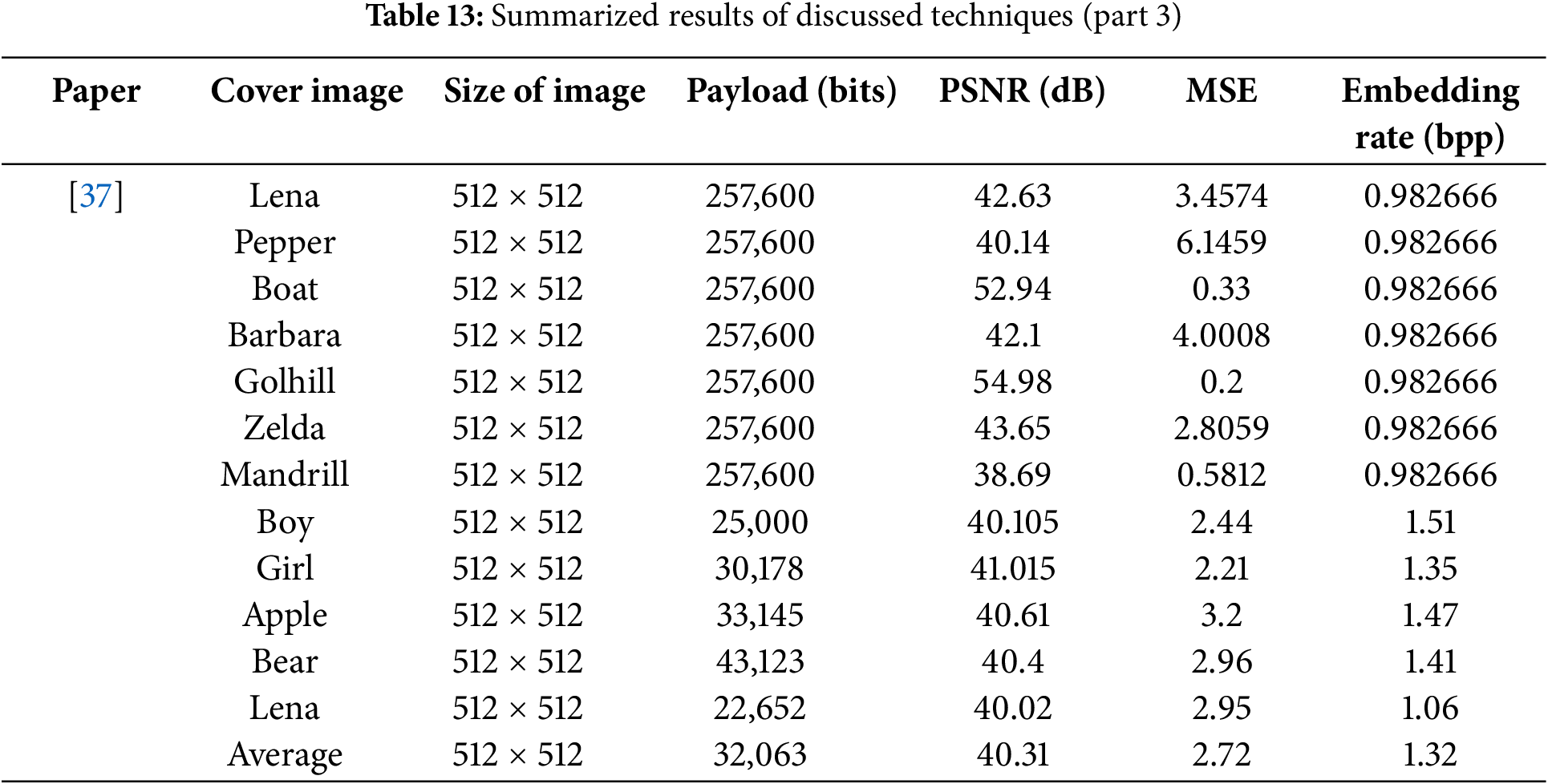
The Tables 11–13 summarize findings of various image steganography techniques. The metrics include the size of the cover image, payload (bits embedded), (PSNR), Mean Squared Error (MSE), and Embedding Rate. Authors in [19] used various image formats, including JPEG, PNG, and BMP, for images such as Mandrill, Lena, Baboon, Boy, Peppers, and Monarch. This study reports high PSNR values (around 70–73 dB), suggesting excellent image quality after embedding, with very low MSE values (0.0032–0.0057) and a low embedding rate ( 0.006–0.007). Authors in [20] focus on smaller images (32 × 32 to 121 × 121), achieving PSNR values between 55.58 and 67.24 dB and very high embedding rates (8 bits per pixel). These results suggest significant data embedding capacity, though quality diminishes as MSE with image size. Authors in [21] report extremely low PSNR values (0.48–0.5 dB) and very high MSE (up to 234714.501), indicating significant quality degradation for images such as Lena and Cat. [24] and [25] both deal with high payloads (over 1 million bits), achieving moderate PSNR (46.69–53.99 dB) and MSE values (around 1.046–5.617), with embedding rates between 4.46 and 5.25. Authors in [26] achieved high payloads (over 2 million bits) while maintaining PSNR values between 35.15 and 40.34 dB and moderate MSE, demonstrating a balance between capacity and quality. [28] and [30] show consistent performance with PSNR values around 31.94 to 54.15 dB and varied MSE values, reflecting different embedding capacities and image qualities. [37] consistently embed 257,600 bits, with PSNR values ranging from 38.69 to 54.98 dB, reflecting varying image quality across different images. [53] evaluate several images with moderate payloads, achieving PSNR values around 40 dB and MSE values near 2.54, demonstrating balanced performance. Finally, authors in [47] reported very high PSNR values (75.77–76.03 dB) and very low MSE (0.0016–0.0017), suggesting excellent quality with an exceptionally high embedding rate (55.775). This comprehensive summary offers insights into the trade-offs between embedding capacity, image quality, and payload across different steganography techniques.


This review presents a comprehensive overview of the evolving field of image steganography, exploring a range of techniques across both spatial and transform domains. Traditional methods like LSB embedding are simple but prone to detection, while advanced techniques, including hybrid and transform domain approaches, offer enhanced security and efficiency at the cost of increased computational complexity. The integration of steganography with data compression and cryptographic methods further bolsters security and transmission efficiency, albeit with trade-offs such as computational overhead and potential image distortion. Achieving the right balance between these factors is crucial for practical applications. Despite notable advancements, challenges like computational complexity, vulnerability to attacks, and image quality degradation persist, emphasizing the need for ongoing innovation in the field.
Future Scope:
The future of image steganography lies in addressing its current limitations while leveraging emerging technologies. Key directions include:
• Optimization of Hybrid Methods: Developing hybrid techniques that combine the strengths of different approaches while mitigating their weaknesses.
• Application of AI and ML: Incorporating machine learning and artificial intelligence to enhance steganographic systems’ security, adaptability, and efficiency.
• Standardization: Creating standardized protocols and tools for seamless integration across platforms to facilitate broader adoption.
• Advancements in Data Compression and Cryptography: Exploring innovative combinations of compression and cryptographic techniques to improve security and transmission efficiency.
• Real-World Application: Focusing on practical implementations in areas like digital forensics, secure communication, and copyright protection, ensuring robust solutions for increasingly digital interactions.
By addressing these opportunities, researchers and practitioners can advance the field of image steganography to meet the growing demands of secure and efficient digital communication.
Acknowledgement: The author would like to express sincere gratitude to Mr. Harsh S Deshmukh, Dr. S. U. Mane, Computer Science Engineering Department, Rajarambapu Institute of Technology, Rajaramnagar for their support in completing the literature survey.
Funding Statement: The author declares that no funding was received for the preparation or completion of this review paper.
Availability of Data and Materials: All the papers referenced in this review are publicly available through various academic databases, including IEEE Xplore, Google Scholar, ResearchGate, ScienceDirect, and Springer. The materials referenced in the review can be accessed from these platforms.
Ethics Approval: None.
Conflicts of Interest: The author declares no conflicts of interest to report regarding the present study.
References
1. Saravanan V, Ramachandran M, Soundharaj S. Exploring various digital communication and its classification. Renew Nonrenewable Energy. 2022;1:52–7. doi:10.46632/rne/1/1/9. [Google Scholar] [CrossRef]
2. Digital technology’s threats to human security. In: 2022 special report on human security; 2022. p. 65–75. doi:10.18356/9789210014007c006. [Google Scholar] [CrossRef]
3. Yadav R. Analysis of cryptography in information technology. Int J Sci Res Eng Manag. 2023;7(3). doi:10.55041/IJSREM18379. [Google Scholar] [CrossRef]
4. Chandra G, Verma SB, Yadav AK. Cryptography techniques for information security. In: Computational intelligent security in wireless communications; 2022. p. 191–200. doi:10.1201/9781003323426-11. [Google Scholar] [CrossRef]
5. Thakre N, Junghare S, Sakhre P, Khawse D. Steganography a technique to hide information within an image. J Cyber Secur, Priv Issues Chall. 2023;2:14–9. doi:10.46610/JCSPIC.2023.v02i01.003. [Google Scholar] [CrossRef]
6. Aslan M, Aktuğ SS, Ozkan-Okay M, Yılmaz AA, Akin E. A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions. Electronics. 2023;12(6):1333. doi:10.3390/electronics12061333. [Google Scholar] [CrossRef]
7. Winsley BB, Muthukannan M. Information security. In: Advances in library and information science. IGI Global. 2020. doi:10.4018/978-1-7998-1482-5.ch017. [Google Scholar] [CrossRef]
8. Kumar A, Pooja K. Steganography-a data hiding technique. Int J Comput Appl. 2010;9(7):19–23. doi:10.5120/1398-1887. [Google Scholar] [CrossRef]
9. Singla D, Verma N, Patni S. A review on spatial and transform domain-based image steganography. In: Advances in multimedia and interactive technologies. IGI Global. 2023. doi:10.4018/978-1-6684-6864-7.ch010. [Google Scholar] [CrossRef]
10. Febryan A, Purboyo T, Saputra R. Steganography methods on text, audio, image and video: a survey. Int J Appl Eng Res. 2017 Jan;12:10485–90. [Google Scholar]
11. Kaur R, Singh B. A robust and imperceptible n-Ary based image steganography in DCT domain for secure communication. Multimed Tools Appl. 2024;83:20357–86. doi:10.1007/s11042-023-16330-9. [Google Scholar] [CrossRef]
12. Yahya A. Introduction to steganography. In: Steganography techniques for digital images; 2018 Jun 13. doi:10.1007/978-3-319-78597-4_1. [Google Scholar] [CrossRef]
13. Sidar S, Chandel G, Garg D. Hybrid technique of data security by ECS (Encryption, Compression, Steganography). Int J Adv Res Ideas Innov Technol. 2020;6:753–8. [Google Scholar]
14. Sethi P, Kapoor V. A proposed novel architecture for information hiding in image steganography by using genetic algorithm and cryptography. Procedia Comput Sci. 2016;87:61–6. doi:10.1016/j.procs.2016.05.127. [Google Scholar] [CrossRef]
15. Mishra R, Mishra A, Bhanodiya P. An edge based image steganography with compression and encryption. In: 2015 International Conference on Computer, Communication and Control (IC4); 2015; Indore, India. p. 1–4. doi:10.1109/IC4.2015.7375510. [Google Scholar] [CrossRef]
16. AL-Shaaby AA, AlKharobi T. Cryptography and steganography: new approach. Trans Netw Commun. 2017;5(6). doi:10.14738/tnc.56.3914. [Google Scholar] [CrossRef]
17. Vasava D, Doshi N. Study and analysis of network steganography methods. Vol. 311, In: Choudrie J, Mahalle P, Perumal T, Joshi A, editors. ICT with intelligent applications. Smart innovation, systems and technologies. Singapore: Springer; 2023. doi:10.1007/978-981-19-3571-8_9. [Google Scholar] [CrossRef]
18. Sharma N, Batra U. A review on spatial domain technique based on image steganography. In: 2017 International Conference on Computing and Communication Technologies for Smart Nation (IC3TSN). Gurgaon, India: IEEE; 2017. p. 24–7. doi:10.1109/IC3TSN.2017.8284444. [Google Scholar] [CrossRef]
19. Mahdi AS. An improved method for combine (LSB and MSB) based on color image RGB. Eng Technol J. 2021;39:231–42. doi:10.30684/etj.v39i1B.1574. [Google Scholar] [CrossRef]
20. Subong RA, Fajardo AC, Kim YJ. Adaptive bit rotation and inversion scoring: a novel approach to LSB image steganography. In: 2018 IEEE 10th International Conference on Humanoid, Nanotechnology, Information Technology,Communication and Control, Environment and Management (HNICEM); 2018 Nov 29–Dec 2. Baguio City, Philippines: IEEE; 2018. p. 1–6. doi:10.1109/HNICEM.2018.8666228 [Google Scholar] [CrossRef]
21. Al-Momin MMSA, Abed IA, Leftah HA. A new approach for enhancing LSB steganography using bidirectional coding scheme. Int J Electr Comput Eng. 2019;9:5286–94. doi:10.11591/ijece.v9i6.pp5286-5294. [Google Scholar] [CrossRef]
22. Swain G. Advanced digital image steganography Using LSB, PVD, and EMD: emerging research and opportunities. IGI Global. 2019. doi:10.4018/978-1-5225-7516-0. [Google Scholar] [CrossRef]
23. Wu D, Tsai W. A steganographic method for images by pixel-value differencing. Pattern Recognit Lett. 2003;24:1613–26. doi:10.1016/S0167-8655(02)00402-6. [Google Scholar] [CrossRef]
24. Hosam O, Ben Halima N. Adaptive block-based pixel value differencing steganography. Secur Commun Netw. 2016;9:5036–50. doi:10.1002/sec.1676. [Google Scholar] [CrossRef]
25. Abdel Hameed M, Aly S, Hassaballah M. An efficient data hiding method based on adaptive directional pixel value differencing (ADPVD). Multimed Tools Appl. 2017;77:14705–23. doi:10.1007/s11042-017-5056-4. [Google Scholar] [CrossRef]
26. Swain G. High capacity image steganography using modified LSB substitution and PVD against pixel difference histogram analysis. Secur Commun Netw. 2018:1–14. doi:10.1155/2018/1505896. [Google Scholar] [CrossRef]
27. Pradhan KRS, Swain G. Digital image steganography using LSB substitution, PVD, and EMD. Math Probl Eng. 2018:1804953. doi:10.1155/2018/1804953. [Google Scholar] [CrossRef]
28. Hussain M, Riaz Q, Saleem S, Ghafoor A, Jung KH. Enhanced adaptive data hiding method using LSB and pixel value differencing. Multimed Tools Appl. 2021;80:20381–401. doi:10.1007/s11042-021-10652-2. [Google Scholar] [CrossRef]
29. Abd AS, Hussein EAR. Design secure multi-level communication system based on duffing chaotic map and steganography. Indones J Electr Eng Comput Sci. 2022;25:238–46. doi:10.11591/ijeecs.v25.i1.pp238-246. [Google Scholar] [CrossRef]
30. Yassin N. Data hiding technique for color images using pixel value differencing and chaotic map. Jordan J Comput Inf Technol. 2022;8(3):242–55. doi:10.5455/jjcit.71-1642508824. [Google Scholar] [CrossRef]
31. Kosuru SNVJD, Pradhan A, Basith KA, Sonar R, Swain G. Digital image steganography with error correction on extracted data. IEEE Access. 2023;11:80945–57. doi:10.1109/ACCESS.2023.3300918. [Google Scholar] [CrossRef]
32. Gnanitha G, Swetha A, Teja GS, Vasavi DS, Sirisha BL. Review on image steganography transform domain techniques. In: Intelligent manufacturing systems in Industry 4.0. Singapore: Springer; 2023. p. 501–12. doi:10.1007/978-981-99-1665-8_43. [Google Scholar] [CrossRef]
33. Gharavi H, Rajaei B. A robust steganography algorithm based on curvelet transform. In: Electrical Engineering (ICEEIranian Conference on; 2018 May 8–10; Mashhad, Iran: IEEE; 2018. p. 1624–8. doi:10.1109/icee.2018.8472443. [Google Scholar] [CrossRef]
34. Hu X, Ni J, Shi YQ. Efficient JPEG steganography using domain transformation of embedding entropy. IEEE Signal Process Lett. 2018;25:773–7. doi:10.1109/LSP.2018.2818674. [Google Scholar] [CrossRef]
35. Kadhim IJ, Premaratne P, Vial PJ. Secure image steganography using dual-tree complex wavelet transform block matching. In: 2018 Second International Conference on Electronics, Communication and Aerospace Technology (ICECA); 2018 Mar 29–31. Coimbatore, India: IEEE; 2018. p. 41–7. doi:10.1109/iceca.2018.8474616. [Google Scholar] [CrossRef]
36. Ayub N, Selwal A. An improved image steganography technique using edge based data hiding in DCT domain. J Interdiscipl Math. 2020;23:357–66. doi:10.1080/09720502.2020.1731949. [Google Scholar] [CrossRef]
37. Tchakounté F, Kamdem P, Kamgang J, Tchapgnouo H, Atemkeng M. An efficient DCT-SVD steganographic approach applied to JPEG images. EAI Endorsed Trans Ind Netw Intell Syst. 2020;7:166365. doi:10.4108/eai.28-9-2020.166365. [Google Scholar] [CrossRef]
38. Oudah KM, Abed NA, Khudhair SR, Kaleefah MS. Improvement of image steganography using discrete wavelet transform. Eng Technol J. 2020;38:83–7. doi:10.30684/etj.v38i1A.266. [Google Scholar] [CrossRef]
39. ElSharkawy MI. Using quaternion fourier transform in steganography systems. Int J Commun Netw Inform Security. 2022;10(2). doi:10.17762/ijcnis.v10i2.3266. [Google Scholar] [CrossRef]
40. Singh J, Singla M. Image steganography technique based on singular value decomposition and discrete wavelet transform. Int J Electric Electronic Res. 2022;10:122–5. doi:10.37391/IJEER. [Google Scholar] [CrossRef]
41. Alobaidi T, Mikhael W. An adaptive steganography insertion technique based on wavelet transform. J Eng Appl Sci. 2023;70(1):144. doi:10.1186/s44147-023-00300-x. [Google Scholar] [CrossRef]
42. BrahmaNaidu N, RamaKrishna K, Diyyala K, Sai Swaroop M, Sandeep K. Image steganography using modified DWT technique. Int J Food Nutr Sci. 2023;11(12). doi:10.48047/ijfans/v11/i12/212. [Google Scholar] [CrossRef]
43. Alobaidi T, Mikhael W. An adaptive steganography insertion technique based on cosine transform. Iraqi J Electric Electron Eng. 2024;20:45–58. doi:10.37917/ijeee. [Google Scholar] [CrossRef]
44. Wahab OFA, Khalaf A, Hussein A, Hamed H. Hiding data using efficient combination of RSA cryptography and compression steganography techniques. IEEE Access. 2021;9:31805–15. doi:10.1109/ACCESS.2021.3060317. [Google Scholar] [CrossRef]
45. T.Arroyo JC. LSB image steganography with data compression technique using goldbach G0 code algorithm. Int J Emerg Trends Eng Res. 2020;8:3259–64. doi:10.30534/ijeter/2020/62872020. [Google Scholar] [CrossRef]
46. Jayasankar U, Thirumal V, Dhavachelvan P. A survey on data compression techniques: from the perspective of data quality, coding schemes, data type and applications. J Saud Univ Comput Inform Sciences/Maǧalaẗ Ǧamʼaẗ Al-Malīk Saud: Ùlm Al-Ḥasib Wa Al-Maʼlumat. 2021;33:1–20. doi:10.1016/j.jksuci.2018.05.006. [Google Scholar] [CrossRef]
47. Tayyeh HK, Ahmed AL-Jumaili AS. A combination of least significant bit and deflate compression for image steganography. Int J Electr Comput Eng. 2022;12(1):358–64. doi:10.11591/ijece.v12i1.pp358-364. [Google Scholar] [CrossRef]
48. Majeed MA, Sulaiman R, Shukur Z. New text steganography technique based on multilayer encoding with format-preserving encryption and huffman coding. Int J Adv Comput Sci Appl. 2022;13. doi:10.14569/issn.2156-5570. [Google Scholar] [CrossRef]
49. Nguyen TD, Le HQ. A secure image steganography based on modified matrix encoding using the adaptive region selection technique. Multimed Tools Appl. 2022;81:25251–81. doi:10.1007/s11042-022-12677-7. [Google Scholar] [CrossRef]
50. Alkhliwi S. Huffman encoding with white tailed eagle algorithm-based image steganography technique. Eng, Technol Appl Sci Res. 2023;13:10453–9. doi:10.48084/etasr.5501. [Google Scholar] [CrossRef]
51. Nuha HH. Lossless text image compression using two dimensional run length encoding. Jurnal Online Informatika. 2020;4:75–8. doi:10.15575/join.v4i2.330. [Google Scholar] [CrossRef]
52. Ali RH, Kadhim JM. Text-based steganography using huffman compression and AES encryption algorithm. Iraqi J Sci. 2021:4110–20. doi:10.24996/ijs.2021.62.11.31. [Google Scholar] [CrossRef]
53. AbdelWahab OF, Hussein AI, Hamed HF, Kelash HM, Khalaf AA. Efficient combination of RSA cryptography, lossy, and lossless compression steganography techniques to hide data. Procedia Computer Sci. 2021;182:5–12. doi:10.1016/j.procs.2021.02.002. [Google Scholar] [CrossRef]
54. Oo BB, Aung MT. Enhancing secure digital communication media using cryptographic steganography techniques. In: 2020 International Conference on Advanced Information Technologies (ICAIT); 2020 Nov 4–5. Yangon, Myanmar: IEEE; 2020. p. 1–6. doi:10.1109/icait51105.2020.9261790. [Google Scholar] [CrossRef]
55. Molato AD, Calanda FB, Sison AM, Medina RP. LSB-based random embedding image steganography technique using modified collatz conjecture. In: 2022 7th International Conference on Signal and Image Processing (ICSIP); 2022 Jul 20–22; Suzhou, China: IEEE; 2022. p. 367–71. doi:10.1109/ICSIP55141.2022.9886754. [Google Scholar] [CrossRef]
56. Awadh WA, Alasady AS, Hamoud AK. Hybrid information security system via combination of compression, cryptography, and image steganography. Int J Electr Comput Eng. 2022;12:6574–84. doi:10.11591/ijece.v12i6.pp6574-6584. [Google Scholar] [CrossRef]
57. Majid Msallam M, Aldoghan F. Multistage encryption for text using steganography and cryptography. J Tech. 2023;5:38–43. doi:10.51173/jt.v5i1.1087. [Google Scholar] [CrossRef]
58. Veera D, Mangrulkar R, Bhadane C, Bhowmick K, Chavan P. Modified caesar cipher and card deck shuffle rearrangement algorithm for image encryption. J Inf Telecommun. 2024;8(2):280–300. doi:10.1080/24751839.2023.2285549. [Google Scholar] [CrossRef]
59. Wen H, Huang Y, Lin Y. High-quality color image compression-encryption using chaos and block permutation. J King Saud Univ-Comput Inf Sci. 2023;35(8):101660. doi:10.1016/j.jksuci.2023.101660. [Google Scholar] [CrossRef]
60. Madhu D, Vasuhi S, Samydurai A. Dynamic 8-bit XOR algorithm with AES crypto algorithm for image steganography. Signal Image Video Process. 2024;18(1):429–45. doi:10.1007/s11760-024-03165-6. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools