 Open Access
Open Access
ARTICLE
Modified Computational Ranking Model for Cloud Trust Factor Using Fuzzy Logic
Research Institute of China Telecom, Shanghai, 201315, China
* Corresponding Author: Lei Shen. Email:
Intelligent Automation & Soft Computing 2023, 37(1), 507-524. https://doi.org/10.32604/iasc.2023.037640
Received 11 November 2022; Accepted 07 February 2023; Issue published 29 April 2023
Abstract
Through the use of the internet and cloud computing, users may access their data as well as the programmes they have installed. It is now more challenging than ever before to choose which cloud service providers to take advantage of. When it comes to the dependability of the cloud infrastructure service, those who supply cloud services, as well as those who seek cloud services, have an equal responsibility to exercise utmost care. Because of this, further caution is required to ensure that the appropriate values are reached in light of the ever-increasing need for correct decision-making. The purpose of this study is to provide an updated computational ranking approach for decision-making in an environment with many criteria by using fuzzy logic in the context of a public cloud scenario. This improved computational ranking system is also sometimes referred to as the improvised VlseKriterijumska Optimizacija I Kompromisno Resenje (VIKOR) method. It gives users access to a trustworthy assortment of cloud services that fit their needs. The activity that is part of the suggested technique has been broken down into nine discrete parts for your convenience. To verify these stages, a numerical example has been evaluated for each of the six different scenarios, and the outcomes have been simulated.Keywords
Cloud computing refers to the on-demand delivery of information over the internet. These services are, in general, categorized into three different types. They are service infrastructure, service platform, and service software [1]. There are a few distinct varieties of clouds. There are a few different kinds of cloud computing infrastructures [2]. The public cloud does not have any restrictions on whom it can sell services on the internet. Only approved customers, in limited circumstances, can purchase services from a private cloud [3]. The main motto of cloud computing is to provide services to users with ease and scalable access to resources. The types of clouds and their services are shown in Fig. 1.
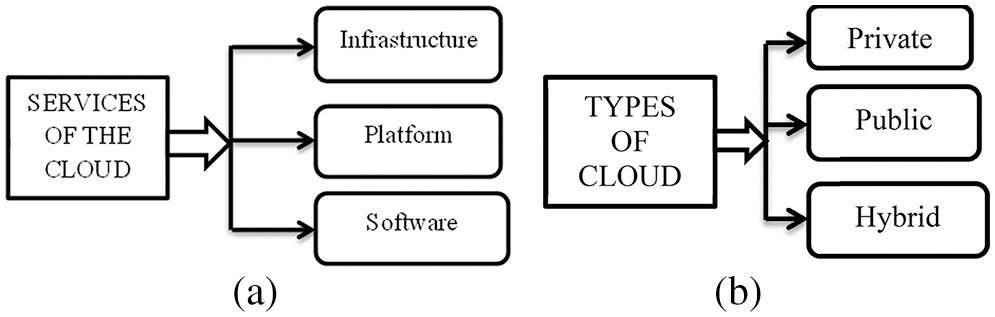
Figure 1: Types of clouds and its services
A third-party provider owns the services in the public cloud, and that particular private owner operates it. The proprietor strips the maintenance of the cloud—the cost of setting up and operating the services is comparatively less. Multiple users can share the platform of the public cloud. Thus the security associated with the public cloud is very low [4]. The control that an individual can have over the services is also limited in the case of public cloud environments. The private cloud is designed in such a way as to provide services to a particular organization. Since the resources are not shared as in the case of the public cloud, the security mechanism is more in the private cloud. The control of the cloud services is high, and the flexibility is also more [5,6]. The organization can set up restrictions in a private cloud, whereas the right lies with the third-party service provider in a public cloud. A hybrid cloud is a combination of both the public cloud and the private cloud. The deployment options are high with this cloud. The bursting of the cloud is also possible. The complexities associated with the hybrid cloud are high, and it is costly as well. Software services refer to the ability of the user to access an application or software without actually installing it or maintaining it [7]. Access can be done over the internet. Since these services do not require installation and maintenance, the usage cost is less. It can also be called web-based software or on-demand software. The advantages of the software services are that they are effective in cost, the time for the operation is less, they have ease of accessibility, updates are done automatically, and the scalability is more. In the platform service, the users can build and create software over the internet. This development can be done with the help of a web browser. The user will not have the authority over the underlying application, and they cannot permanently host its operation [8]. The user will only have the option of changing the settings associated with the configuration for the temporary hosting of the program. The infrastructure service provides the computerized infrastructure in an outsourcing method. The virtual space used by the customers is charged based on the number of users accessed [9]. The advantages are that it is cost-effective, website hosting can be done, better security, and easy maintenance. The service selection of the cloud can be made in several methods. The earlier available methods have been reviewed before carrying out the proposed work.
The authors in [10] have developed a fuzzy logic-based user trust method. Here they have put forth approaches for overcoming the drawbacks of the access control methods that are being used traditionally. Four types of evidence, namely, login, security operation, and performance, have been considered for evaluating cloud users. The conclusion of this work states that the proposed FluoroUracil Breath Test (FUBT) method provides more flexibility and scalability. A trust administration model has been developed by Vidhika et al. [11]. An analysis of the present models available for trust management has been carried out in their study. A secure multi-layer trust-based model has been proposed by Jane et al. [12]. The building up of this model requires the combination of fuzzy logic of the on-demand states and the different security mechanisms. A trust management-based fuzzy rule for the cloud computing environment has been put forth by Mona et al. [13]. Their research focuses on the problem of how to handle trust in a network of different clouds. Trust values for the providers of computational services have been calculated using a mixture of objective and subjective metrics. A solution to the dilemma of making a call when there are numerous factors to consider is the VIKOR technique. The authors have concluded that the VIKOR method is an effective tool for selecting the best value when the decision maker is unsure which preference to express [14]. The computational ranking method can be used to evaluate health information [15]. Eric Afful-Dadzie has carried out this research work. The designed framework helps to evaluate and rank the internet-based health information providers in which linguistic variables clear the uncertainties. The selection of suppliers based on the measurement of entropy for objective weighting can be made using the VIKOR method as per the work done by Ali Shemshadi and his co-authors [16]. Subjective weights were regulated based on the Shanon entropy concept in accordance with the objective weights. Alguliyev et al. has proposed a method to select personnel in a multiple-criteria environment by using the VIKOR technique [17]. The fuzzy numbers were used in a triangular fashion to determine the stability of the personnel and for the approximation of the linguistic values.
VIKOR method has been used by Min Xue and his co-authors for the decision analysis of bi-dimensional fuzzy information [18]. The resultant analysis has proved the applicability and validity of the proposed method. A study has been carried out by Bashir Hayat and his co-researchers in cloud computing scenarios in accordance with fuzzy logic. The important features of the fuzzy logic mechanism in the cloud computing environment have been discussed [19]. Fuzzy interference system can be used for the RFID access control system in case of risks. One such work has been done by Dima Suleiman and their co-authors [20]. The risk values are exposed to under and over-estimation. User behaviour time analysis has been utilized to detect uncharacteristic access behaviour. Javed Alam and Dr. Manoj Kumar Pandey has developed an RFID traffic light control system that uses fuzzy logic for its operation. The software behind the proposed concepts has been developed using MATLAB, and the corresponding results have been simulated [21]. The performance evaluation of cloud computing in fuzzy logic has been studied by Aruna et al. [22]. With the rapid improvement of the cloud and its resources, techniques must be developed to evaluate the performance. The main motive of this work was to spread the performance on the cloud infrastructure and application levels. Marija Paunovic and his co-authors have developed a method for the selection of cloud suppliers using the dual-stage fuzzy logic model. The proposed model provides advanced reliability and reduced subjectivity of the decision-maker. The proposed method tends to have provided improved accuracy by means of numerical values [23]. The ranking of the parameters in the fuzzy logic can be done in accordance with the quality of service and trust. One such work has been proposed by Faiz et al. [24]. Cloud computing finds its applications in a vast area. It is also used in the E-learning platform. The researchers have proposed a method for identifying the effectiveness of the students while attending classes in the E-learning platforms [25]. The feedback from the students through their facial emotions plays a vital role in helping the teachers to provide improvised teaching. The proposed method provides a practical fuzzy logic framework to identify emotions in cloud-based E-learning platforms. Rajganesh et al. have devised a method for determining and selecting cloud infrastructure services using a decision-making broker. This trader mediates interactions between suppliers and end users. It identifies the necessary services by employing fuzzification and defuzzification mechanisms [26]. Searching for a keyword becomes tedious when a large amount of data is in the database. The researchers have developed a keyword search mechanism using encryption associated with fuzzy logic [27]. Data encryption requires high privacy and security. The proposed method identifies the matching or the nearest matching files based on similar semantics.
2.1 Identified Limitations of Existing Systems
Based on the above studies, the following challenges have been identified in the intended domain of research.
(i) The control on the ranking system is diminishing, and has no proper control in determining the ranking system.
(ii) The ranking system is provided based on the trust degree of the Cloud Service Provider (CSR) with limited criteria.
2.2 Objectives of the Proposed Work
With reference to the above-identified challenges in the proposed work, the following objectives have been framed for the proposed work.
(i) To provide an updated computational ranking approach for decision-making in an environment with many criteria by using fuzzy logic in the context of a public cloud scenario.
(ii) To design an improved computational ranking system using improvised VlseKriterijumska Optimizacija I Kompromisno Resenje (VIKOR) method.
(iii) To ease the users to access a trustworthy assortment of cloud services that fit their needs.
The things that are not clear and are confusing in nature can be referred to by the term fuzzy. In real-time applications, there might be different scenarios where it is difficult to find whether a parameter is true or false. Utilizing fuzzy logic, it is possible to solve the uncertainties of any situation by considering the inaccuracies. In the Boolean system of solving inaccuracies [28], there are two different values representing the true and the false conditions. The true condition is represented by 1, and the false condition is represented by 0. In the fuzzy logic system, there are no such true and false values; instead, there is an intermediate value that is partially true and partially false. The representation of true and false values of Boolean logic and fuzzy logic is given in Fig. 2 when the temperature in the parameter is under consideration.
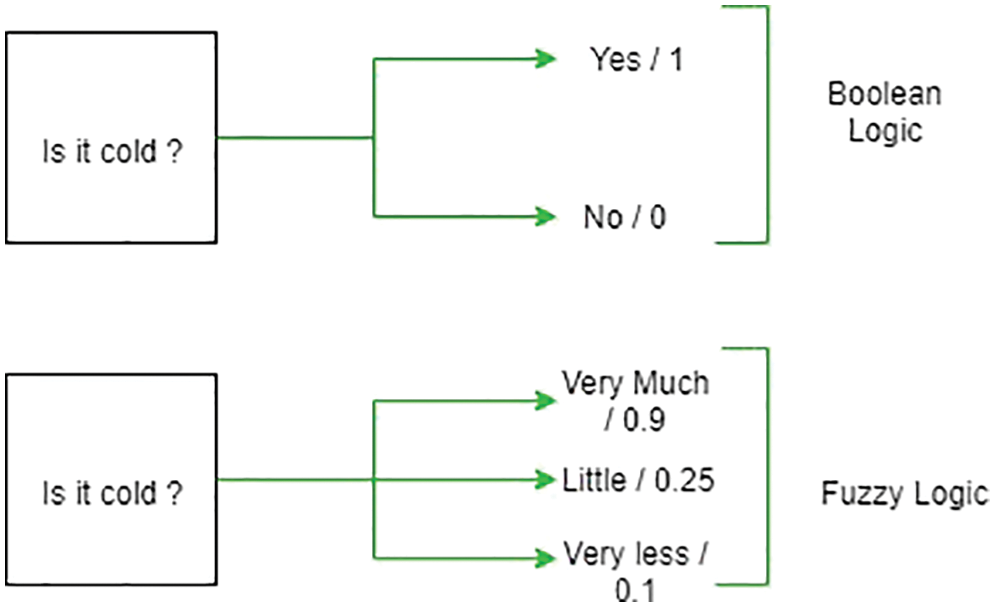
Figure 2: True and false value representation of Boolean logic and fuzzy logic
The architecture of the fuzzy logic system is shown in Fig. 3. The architecture consists of four different blocks, namely the rule base block, fuzzification block, interference engine block, and the defuzzification block.
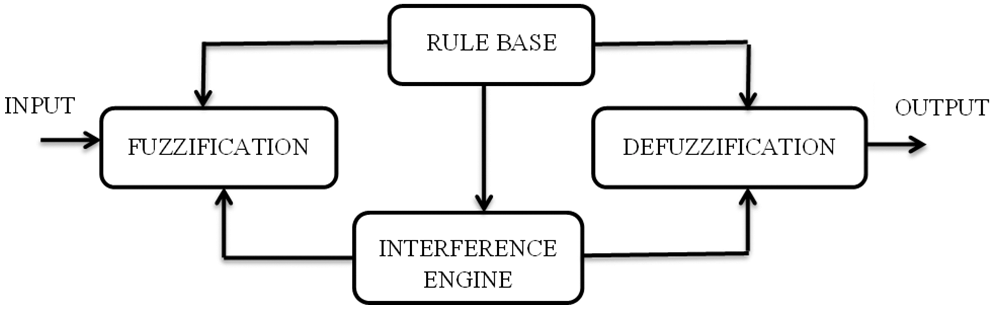
Figure 3: Architecture of fuzzy logic system
Rule base block: The rule base block holds the group of protocols and the if-then statements given by the experts to maintain the system that makes the decisions depending upon the linguistic data. Recent developments in the fuzzy logic system help to reduce the vast amount of rules followed in the fuzzy controlling systems.
Fuzzification block: It is used to convert the inputs into fuzzy sets.
Interference engine block: It identifies the degree of similarity between the present input in accordance with every rule and determines which rule has to be thrown out to the input parameter.
Defuzzification block: The fuzzy sets attained through the engine are converted into values of crispness through this block.
3.2 Basic Terms and Definitions
CIS: CIS stands for cloud infrastructure services. It is the accumulation of hardware and software features that aid in the cloud computing mechanism. It could contain the computational power, data storage mechanism, the interface between the input and the output. Cloud infrastructure services can provide low proprietorship of low cost, high flexibility and scalability. The cloud infrastructure services are available for the private, public and hybrid cloud environments.
CSP: CSP stands for cloud service provider. It represents a third-party organization that provides infrastructure services and storage services for the cloud-based platform. The services are provided on demand. For instance, data storage and computation power can be attained without the user’s direct active contact.
CSR: CSR stands for Certificate signing request. It is a message that is encrypted and sent from the digital certificate applicant’s SSL (secure socket layer) to the certificate authority.
3.3 VIKOR Method or Compromised Ranking Method
VIKOR stands for “Vlse Kriterijumska Optimizacija I Kompromisno Resenje”. It provides an optimized and compromised solution between the multiple criteria available. It can be utilized when the decision maker requires a solution almost nearer to the ideal one. It works on tracing out a compromised solution in the presence of conflicts among the available alternatives. This is done by ranking the alternatives. The compromise ranking method is one of the effective methods for selecting a particular group of values from a wide variety of alternatives available. It helps in ranking based on the close of the required values with the values of the alternatives.
The value of Kq, I in the above equation represents the distance between the alternative solution and the ideal solution. It can be expressed, in other words, by the extent to which the alternative is useless and non-useless. The number of the existing alternatives is represented by I, Ai indicates the alternative options and Gij represents the value of evaluation of the ith criteria in accordance with the alternative Aj. The distance between the alternative Aj and the ideal solution is given by Kqi.
The compromised ranking method uses two important criteria for making the decisions. They are the weight of the criteria and the weight of the utility. Vi represents the weight of the criteria, and the weight of the utility is represented by w. W. represents the maximum use of the group. The compromised ranking index Gi is given by the following equation.
As already mentioned, u represents the useful value of the largest group and (1 − u) the usefulness of the individual parameter.
The compromised modified ranking method differs from the traditional compromised ranking method in the following aspects.
✓ The traditional ranking method cannot point out the variations in the performance values that prevail between the status quo and the ideal point.
✓ Due to this, the ideal value for the positive case is R* = 0; the ideal value for the negative case is R− = 0. The ideal value for the positive case is T* = 0; the ideal value for the negative case is T− = 0 to get the appropriate index value for Z.
✓ When u is greater than 0.5, the 0 ≤ u ≤ 1, R is greater than T and when u is lesser than 0.5, it indicates that T is greater than R.
✓ When u is equal to 1, it indicates the decision-making process for the maximum group utility approach.
✓ When u is equal to 0, it indicates the decision-making process for the minimum group utility approach of the individual target.
When Gimod is simplified, we get
The final compromised solution can be improvised based on the two conditions, condition 1 and condition 2.
Condition 1: Advantage that is acceptable
where CIS(1) is the alternative and Zmod is represented by
where Z represents the total count of available alternatives.
Condition 2:Stability that is acceptable
CIS(1) is the ranked to be the best in Rj. Hence CIS(1) can be taken as the compromised solution only if both the conditions are satisfied. If any of these conditions are not satisfied, then
Condition 1 is not satisfied: set of (CIS(1), CIS(2), ……. CISI) will be taken as the solution that is best.
Condition 2 is not satisfied: CIS(1), CIS(2) will be taken as the solution that is best.
This paper’s cloud service selection method consists of nine consecutive steps. These steps aid the CSR and CSP to,
• A detailed description of the distinguishing alternatives of the CIS concerning the trust utilizing which the CSP can attain the requirements of the trust before dispatching the data into the cloud.
• Provide the necessary improvement that has to be done to the CIS by the CSRs to attain the ideal trust level.
The block diagram representation of the compromised ranking method is shown in Fig. 4.
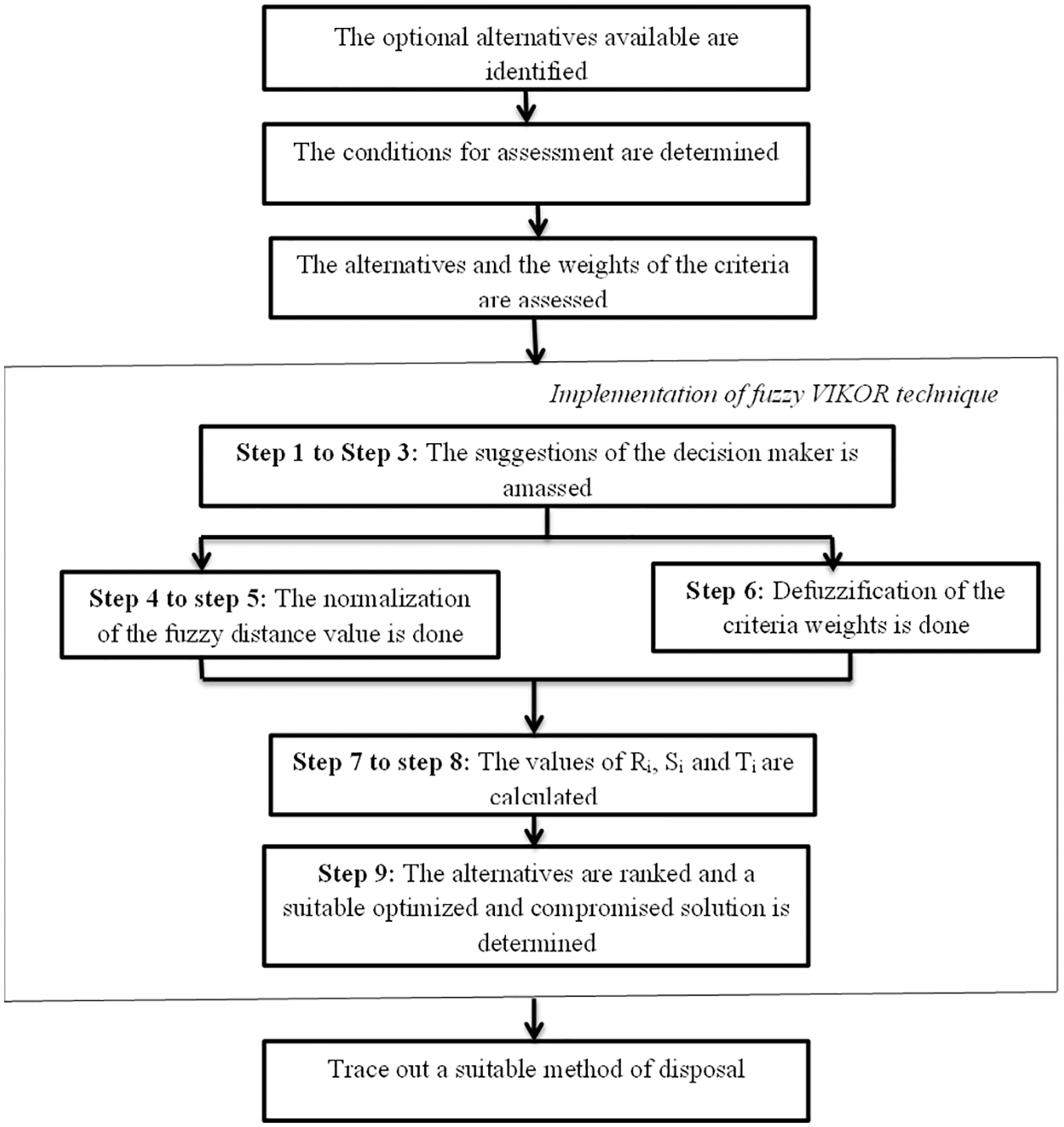
Figure 4: Steps involved in the fuzzy VIKOR (compromised ranking) method
Step 1: Identification of the alternative or optional sets.
✓ A set of A optional sets: CIS = (CIS1, CIS2, CIS3, …………. CISa)
✓ A set of B optional sets: C = (C1, C2, C3, …………………… Cb)
✓ A set of C optional sets: DM = (DM1, DM2, DM3, ………. DMc)
✓ A fuzzy rating set: CISj (1, 2, 3 …. a) and criteria Ci (i = 1, 2, 3 …. b), K {kji, I = 1, 2, 3 ….. b}
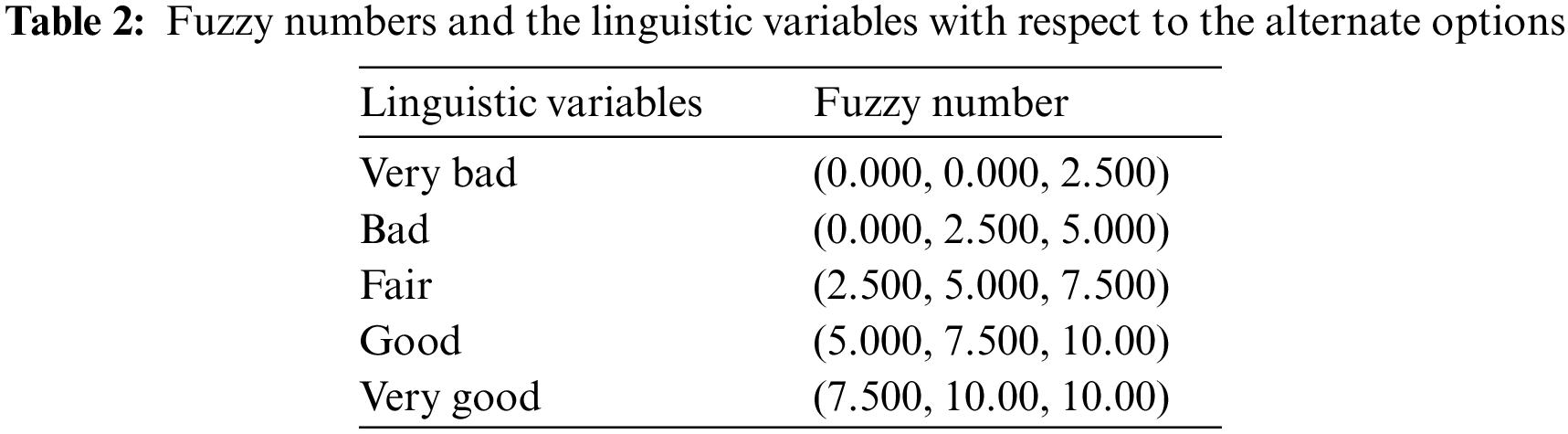
Step 2: The membership functions are defined in this step along with the linguistic variables. The fuzzy numbers and the linguistic variables are listed in Table 1.
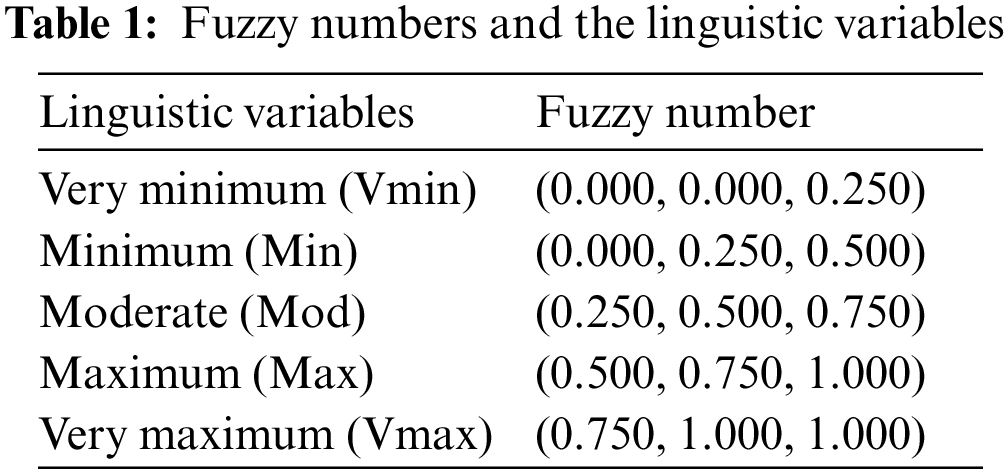
The fuzzy numbers and the linguistic variables with respect to the alternate options given in Table 2.
Step 3: Two major criteria are used for the computation of the weight of the fuzzy and the rating of the options for constructing the decision-making matrix. The jth option fuzzy rating with respect to the criteria I of the decision maker q be Hjiq = (Hji1, Hji2, Hji3) and the weight of importance of the criteria I provided by the decision maker q is represented by Vjiq = (Vji1, Vji2, Vji3). Hence the prominent weight of every criterion and the rates of fuzzy of the alternatives are given by the following equations.
The aggregation functions are used for the development of the decision based matrix. The decision matrix can be used to solve the problems related to the CIS.
Step 4: The brittle values of the fuzzy weights can be calculated with the help of the defuzzification method related to the centre-of-area approach. The centre of area defuzzification method is used to defuzzify the decision-making matrix, and it is represented by the following formula
Step 5: Identify the maximum value of Gj* and the minimum value of Gj− for all the criteria. Here j = 1, 2, 3 …. m represents the total number of available criteria.
Step 6: The ranking values of the concordance and discordance are calculated for the alternatives.
Step 7: The compromised ranking index Gimod is calculated.
Step 8: The order strategy in increasing order will be used to sort the alternatives depending upon the values of Rj, Tjmod and Gjmod. The resultant values will be segregated as a group of three ranking tables.
Step 9: The optional parameter for the compromise solution will be attained through the two conditions, condition 1 and condition 2.
The evaluation of and selection procedure of the CSP is provided using an example. Five alternatives of CSP are denoted by A and about fifteen criteria have been defined and represented by D. The various steps used in the evaluation and the selection are given below.
Step 1: The group of sets, decisions and alternatives are selected as the initial step.
Assume that CSR Z is in search to select the best option from the five options (CIS1, CIS2, CIS3, CIS4, CIS5). These alternatives will be evaluated by a group of five decision makers D ( D1, D2, D3, D4, D5) under the fifteen different criteria. The criteria that have been considered for evaluation are listed in Table 3.
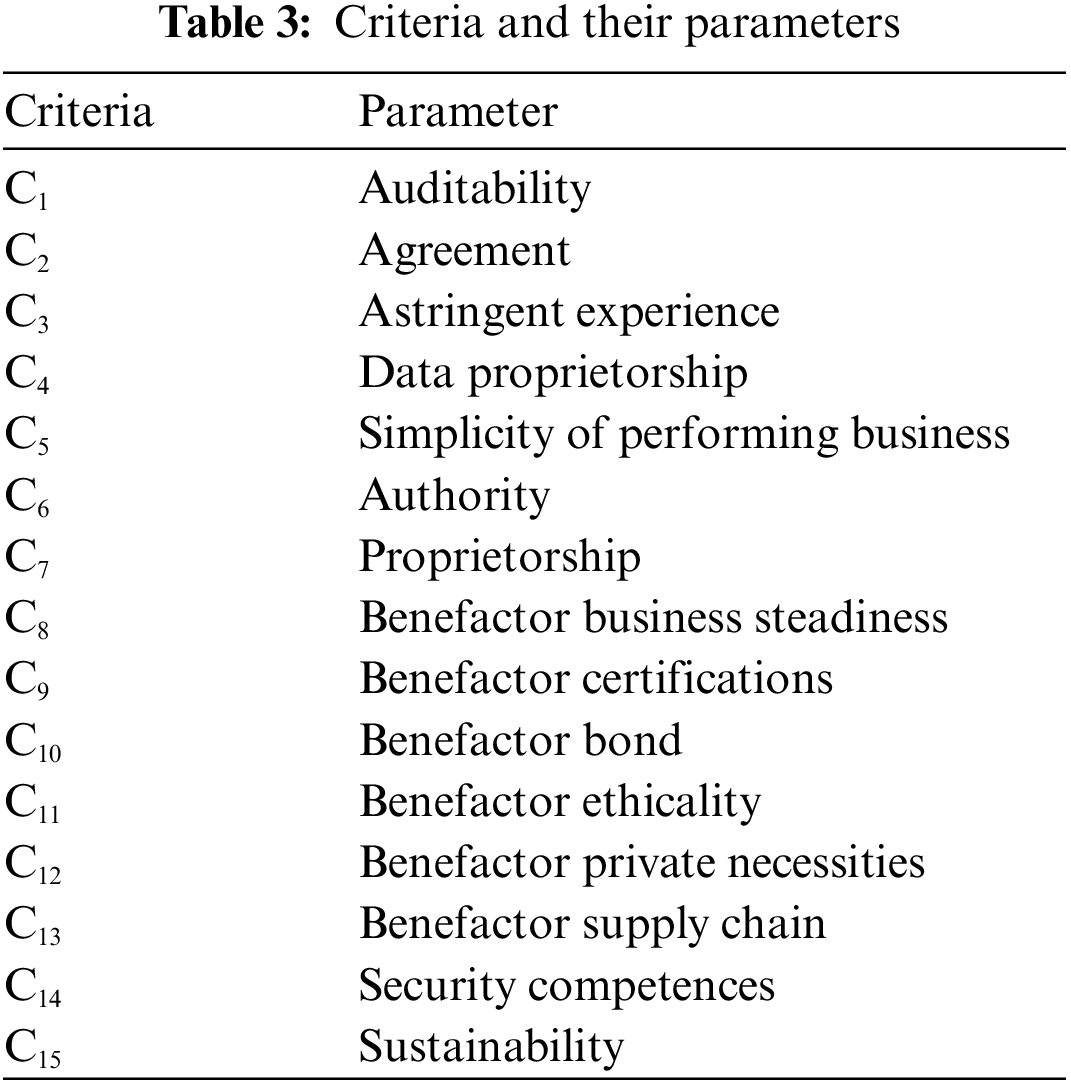
The criteria selection for the evaluation has been taken from the service management index given by CSMIC 2011. These criteria can be used to evaluate the CIS characteristics of the CSPs. This, in turn, helps in the development of trust in the CSR of any CSP. The decision-makers have to check out all the trust criteria of available alternatives and select one of the best among them. This is illustrated in Fig. 5.
Figure 5: Diagrammatic representation of the numerical example
Step 2: The five decision-makers are used for selecting the linguistic variables and the membership functions. These are used for the selection of the prominent criteria of the weight and the assessment ratings of the available optional alternatives through every criterion. The decision-makers for different criteria have been tabulated in Table 4.
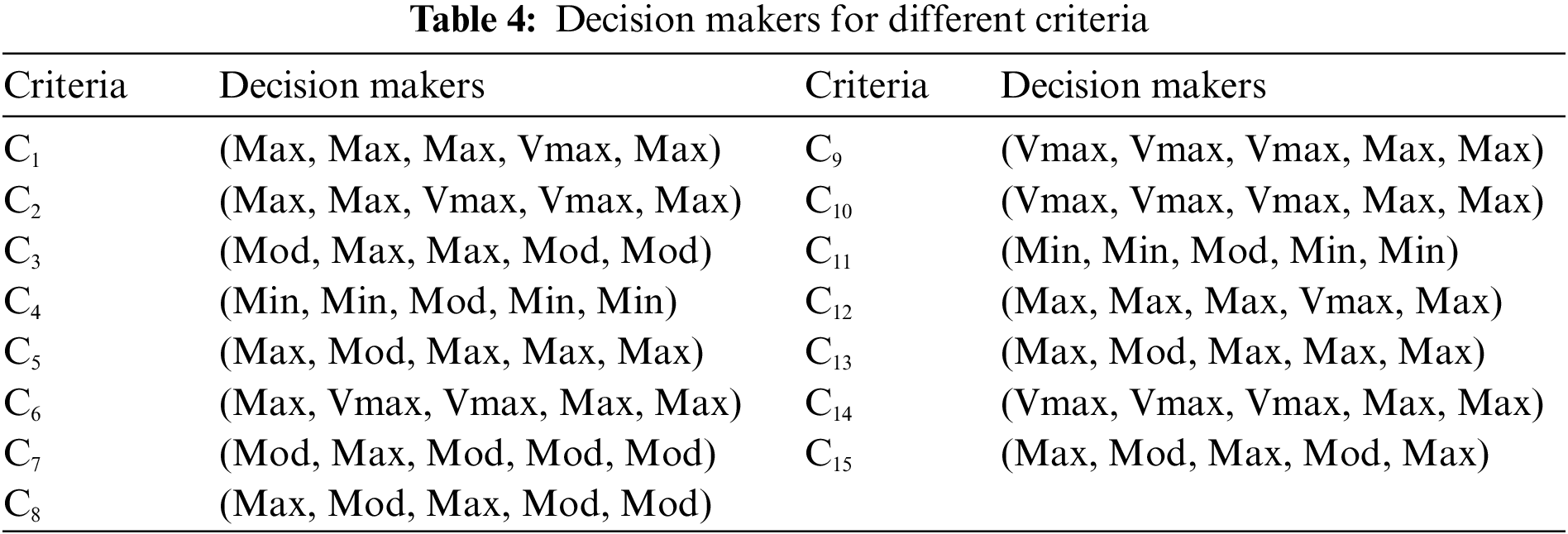
Step 3 and step 4: Change the linguistic terms into fuzzy numbers that are triangular and cumulate the fuzzy weights of the criteria and the alternatives using the equations provided. Table 6 represents the various brittle values of the weights and the ratings of the optional alternatives. The variation of PCS with weight values for different criteria is shown in Table 5, and a graphical representation of the PCS value to different weights is shown in Fig. 6.
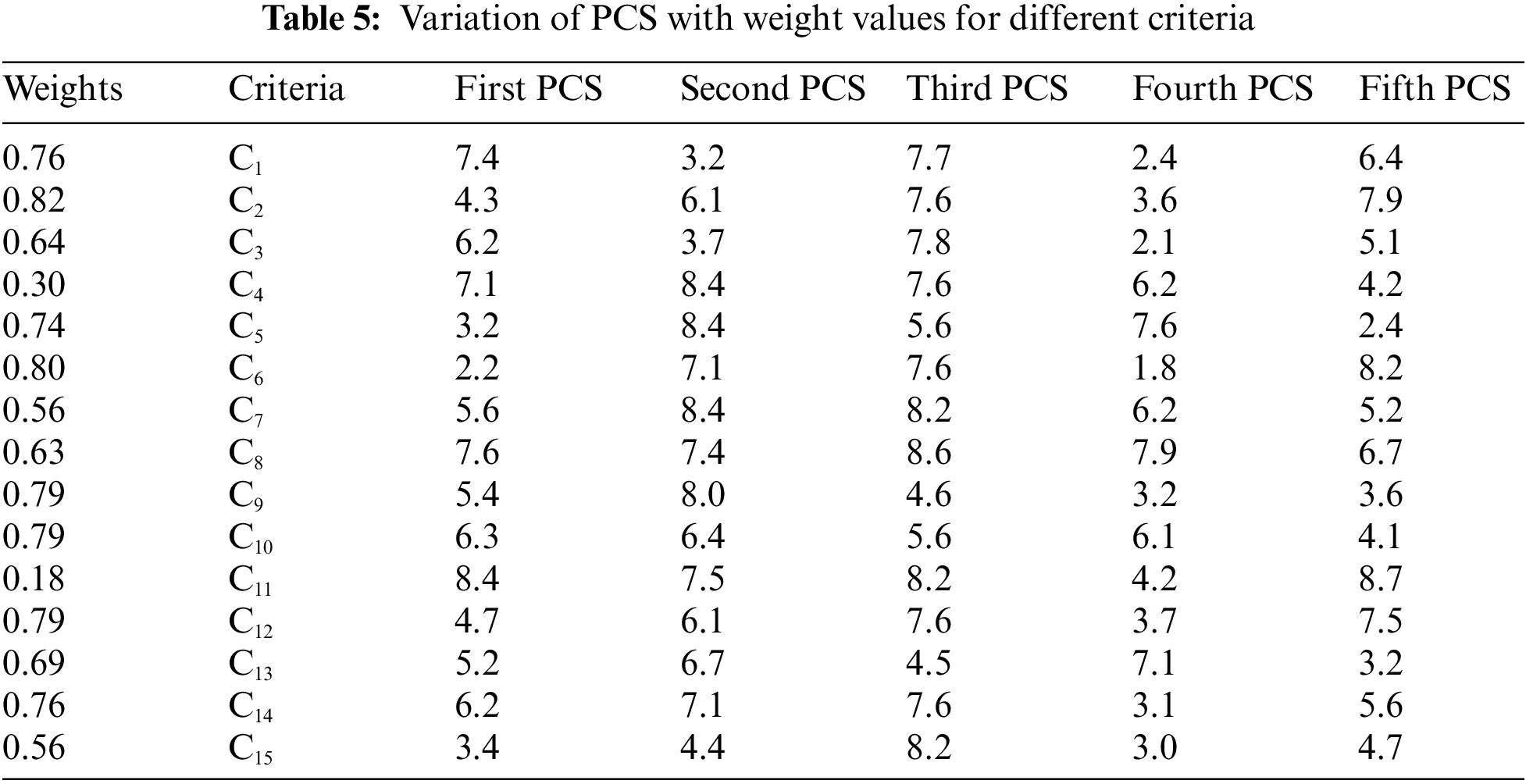
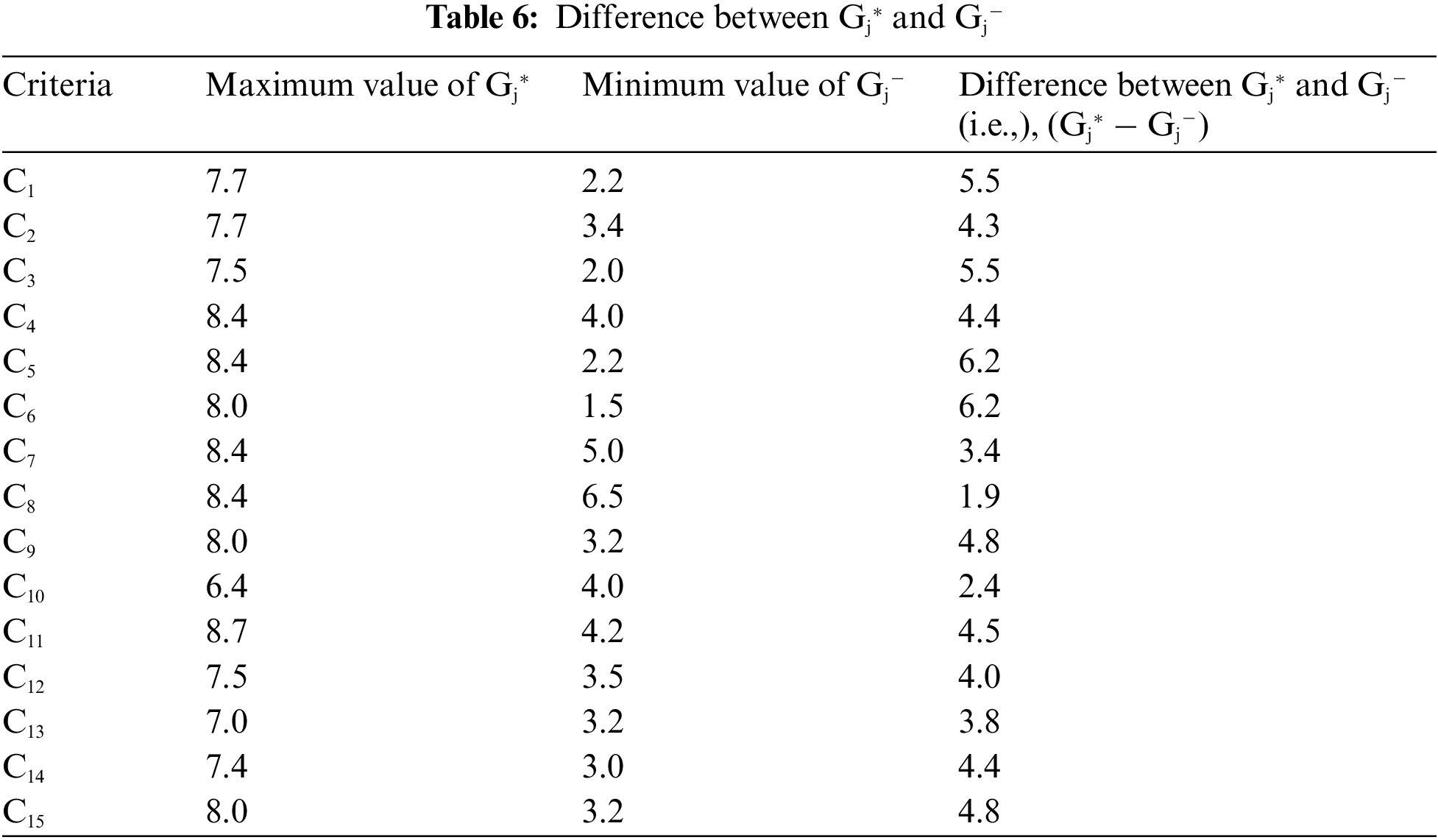
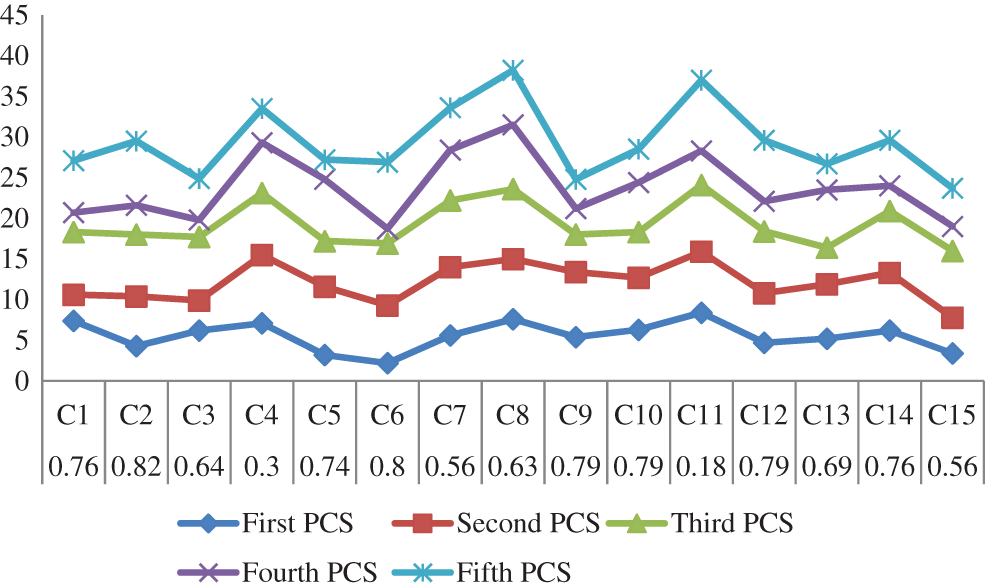
Figure 6: Graphical representation of the PCS value with respect to different weights
Step 5: The maximum value of the Gj* and the minimum value of the Gj− have been determined and are tabulated in Table 6. The graphical representation of criteria vs. the minimum and maximum value of Gj* and Gj− respectively is shown in Fig. 7. Graphical representation of criteria vs. the difference value of Gj* and Gj− is shown in Fig. 8.
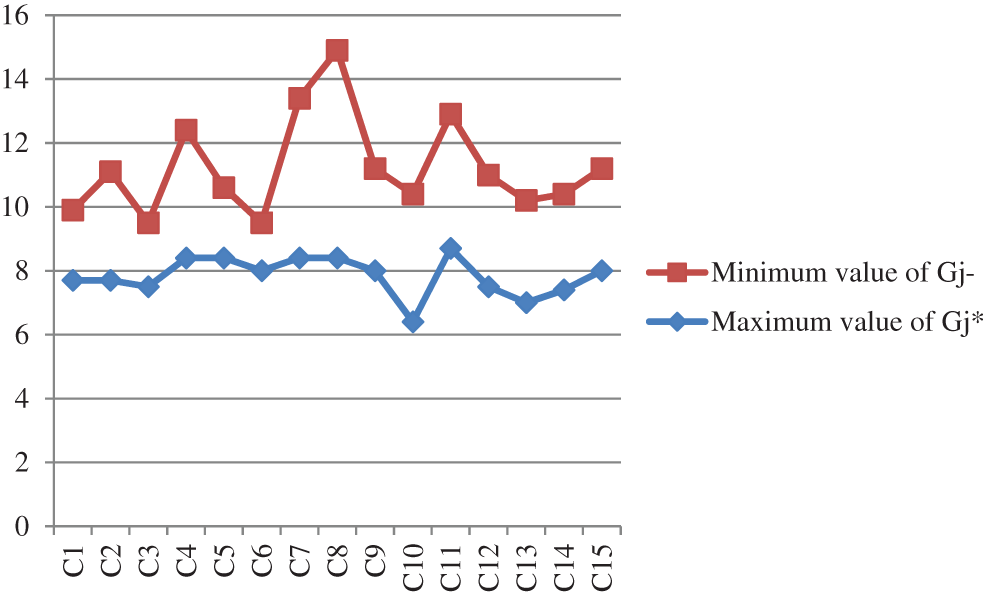
Figure 7: Graphical representation of criteria vs. minimum and maximum value of Gj* and Gj− respectively
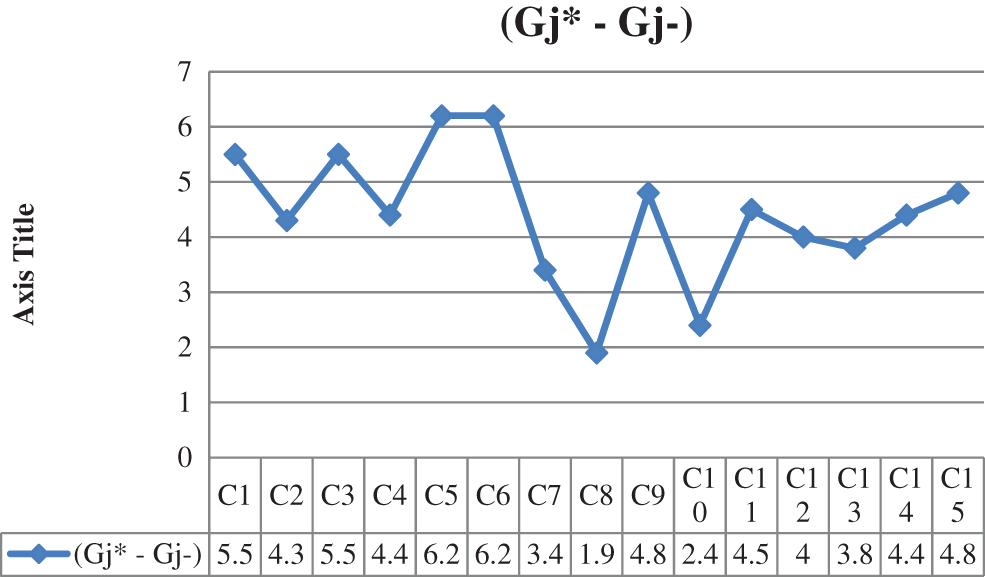
Figure 8: Graphical representation of criteria vs. difference value of Gj* and Gj−
Step 6 and step 7: The values of the concordance (Ri), discordance (Timod) and computational ranking index (Gimod) are calculated and tabulated in Table 7. Fig. 9 shows the variation of Ri, Timod and Gimod for different CIS.
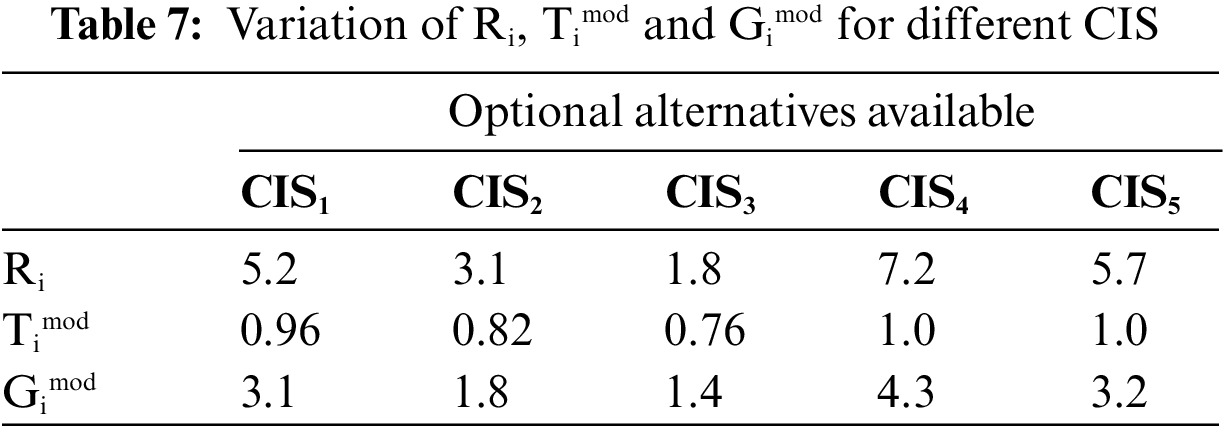
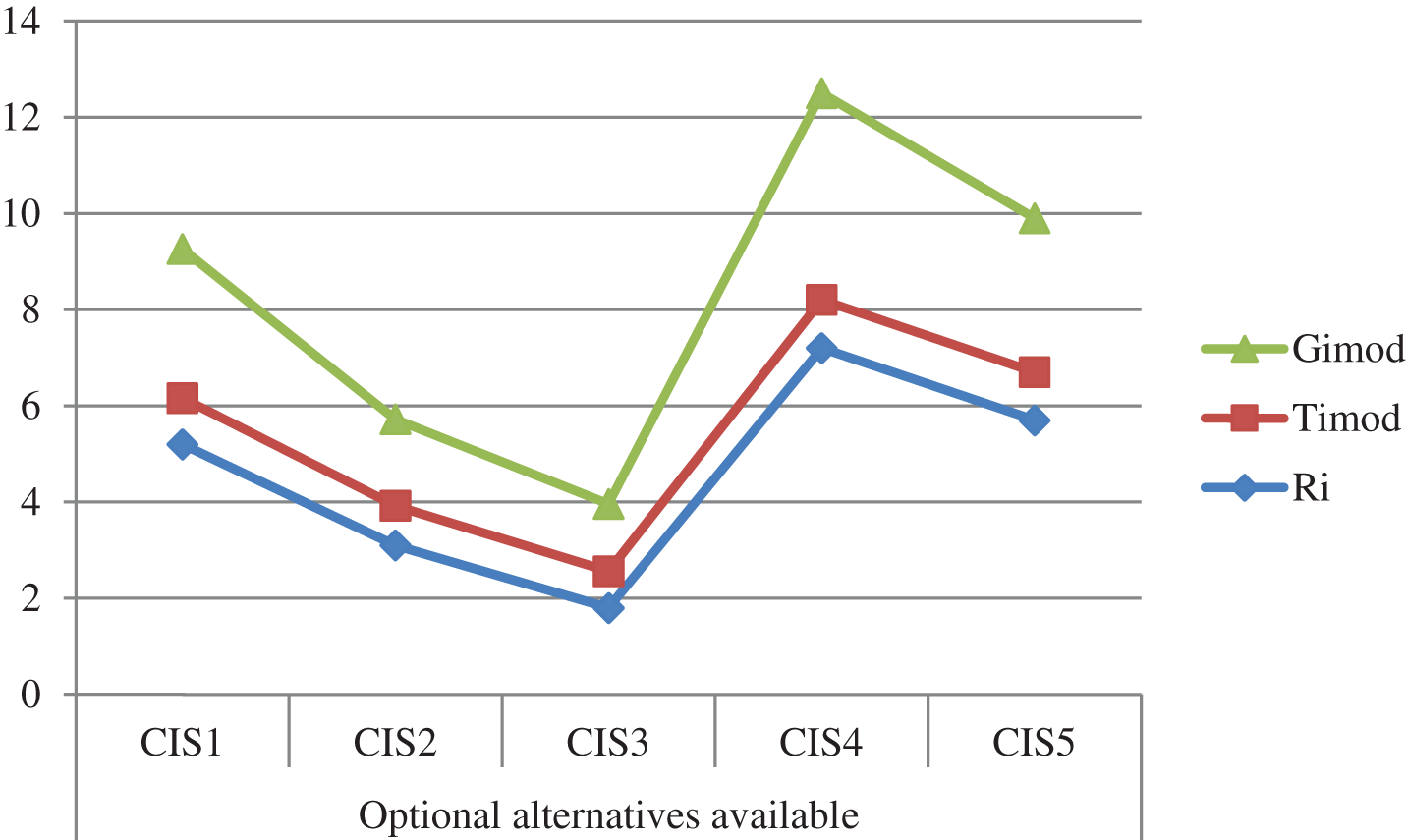
Figure 9: Variation of Ri, Timod and Gimod for different CIS
Step 8: The ranking of Ri, Timod and Gimod are sorted and ranked in the ascending order. These values are plotted in Table 8.
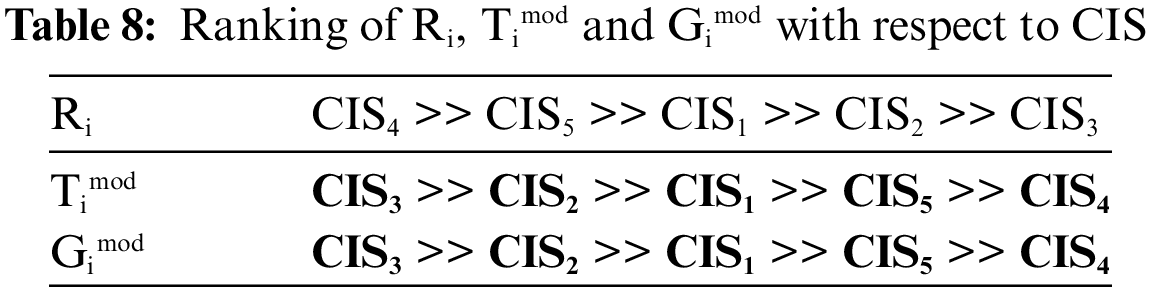
Gimod values are ranked for six different states and it is tabulated in Table 9 and the variation of PCS rates for six distinct situations is shown in Fig. 10.
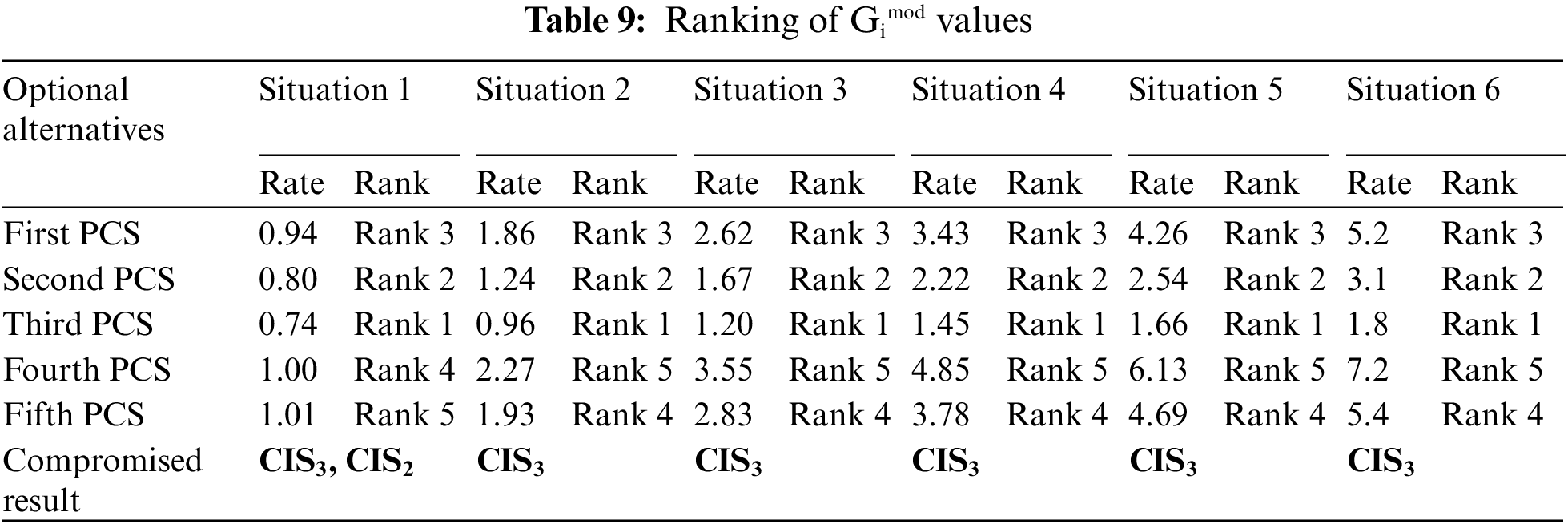
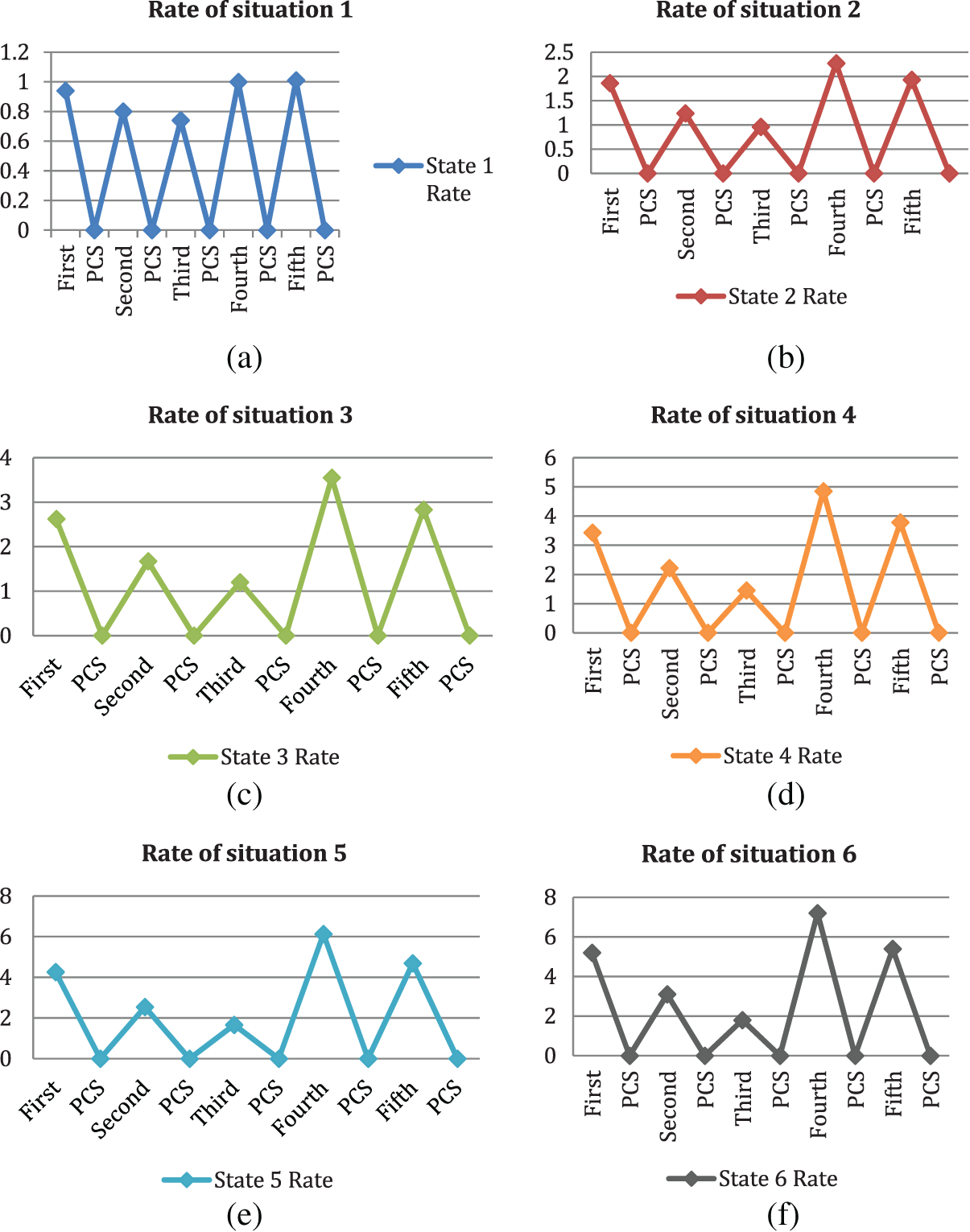
Figure 10: The variation of PCS rates for six distinct situations
Step 9: The resultant compromised solution has been calculated and it is shown in Table 10. Fig. 11 shows the graphical representation of maximum Gimod, minimum Gimod and Zmod.
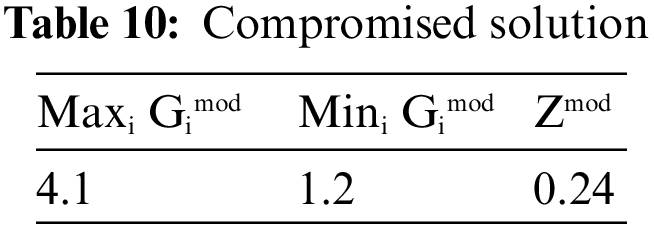
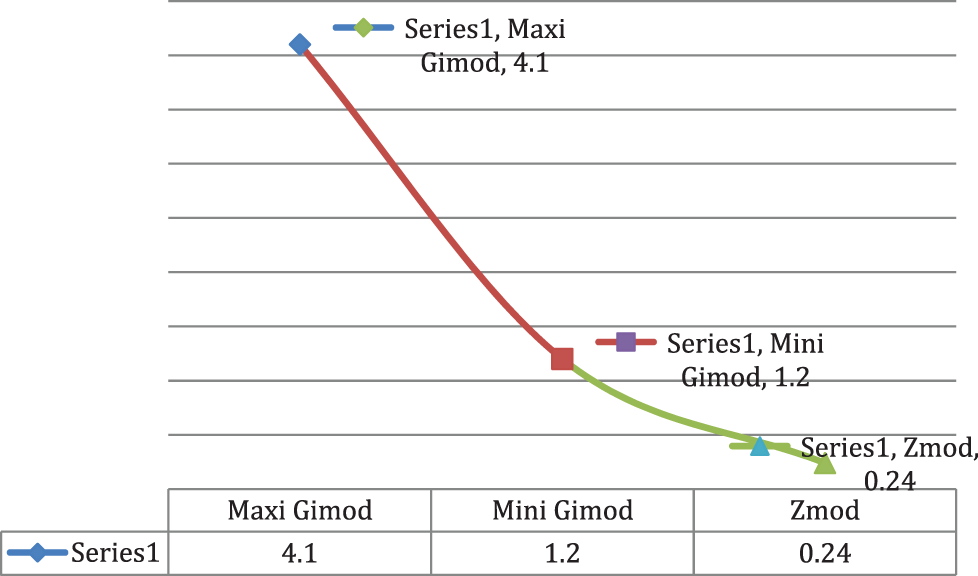
Figure 11: Graphical representation of maximum Gimod, minimum Gimod and Zmod
It is seen that CIS3 has an advantage and it is said to be the best rank in Timod. Therefore CIS3 can be the compromised solution as it satisfies both the earlier-mentioned conditions. The reason for considering three different states is to estimate the changes in the values to the changing parameters.
The trust level associated with the cloud service providers and requesters has become an important factor. The proposed work introduces a modified computational ranking method (also called improvised VIKOR) for decision-making in public cloud environments. The underlying parameter of the entire proposed work deals with the utilization of fuzzy logic. The computational ranking method has been segmented into nine different steps. These steps have been evaluated utilizing a numerical example, and the simulation results have been stained for six distinct situations. This proposed work shall be further improved by employing an optimization algorithm and fuzzy logic to achieve a better level of ranking systems.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. G. Saxena and K. Nanath, “Cloud performance evaluation using fuzzy logic,” in Proc. IEEE Int. Conf. on Electrical, Computer and Communication Technologies (ICECCT), Coimbatore, India, pp. 1–8, 2015. [Google Scholar]
2. A. Basu and S. Ghosh, “Implementing fuzzy TOPSIS in cloud type and service provider selection,” Advances in Fuzzy Systems, vol. 2018, pp. 1–12, 2018. [Google Scholar]
3. A. Malhotra, S. Dhurandher, M. Gupta and B. Kumar, “Integer multiplication ranking method for cloud services selection,” Journal of Ambient Intelligence and Humanized Computing, vol. 2021, pp. 1–12, 2021. [Google Scholar]
4. R. Baki, “Application of ROC and CODAS techniques for cloud service provider selection,” Gaziantep University Journal of Social Sciences, vol. 21, no. 1, pp. 217–230, 2022. [Google Scholar]
5. K. R. Kalantari, A. Ebrahimnejad and H. Motameni, “Presenting a new fuzzy system for web service selection aimed at dynamic software rejuvenation,” Complex & Intelligent Systems, vol. 6, pp. 697–710, 2020. [Google Scholar]
6. I. Otay and Y. Tugba, “Multi-criteria cloud computing service provider selection employing pythagorean fuzzy AHP and VIKOR,” Intelligent and Fuzzy Techniques: Smart and Innovative Solutions, vol. 2021, pp. 423–431, 2021. [Google Scholar]
7. N. N. Iyengar, A. Banerjee and G. Ganapathy, “A fuzzy logic based defense mechanism against distributed denial of services attack in cloud environment,” International Journal of Communication Networks and Information Security (IJCNIS), vol. 6, no. 3, pp. 1–16, 2022. [Google Scholar]
8. M. Jaiganesh and A. Vincent Antony Kumar, “B3: Fuzzy-based data center load optimization in cloud computing,” Mathematical Problems in Engineering, vol. 2013, no. 1, pp. 1–18, 2013. [Google Scholar]
9. S. Rizvi, J. Mitchell, A. Razaque, M. R. Rizvi and I. Williams, “A fuzzy inference system (FIS) to evaluate the security readiness of cloud service providers,” Journal of Cloud Computing, vol. 9, no. 1, pp. 1–14, 2020. [Google Scholar]
10. M. Alruwaythi and K. E. Nygard, “Fuzzy logic approach based on user behavior trust in cloud security,” in Proc. IEEE Int. Conf. on Electro Information Technology (EIT), Brookings, USA, vol. 2019, pp. 1–6, 2019. [Google Scholar]
11. V. Vidhika and C. Vipul, “A trust rating model using fuzzy logic in cloud,” in Proc. of ICICC 2018, Delhi, India, vol. 2, pp. 1–34, 2019. [Google Scholar]
12. S. M. Jane, L. Maozhen, T. Gareth and O. Clement, “Fuzzy logic approach to modelling trust in cloud computing,” IET Cyber-Physical Systems: Theory & Applications, vol. 2, pp. 1–14, 2017. [Google Scholar]
13. S. Mona, A. Navid, T. Elham, S. Safieh and K. Rasoul, “Fuzzy rule-based trust management model for the security of cloud computing,” Mathematical Problems in Engineering, vol. 2021, pp. 1–14, 2021. [Google Scholar]
14. N. Zhang and G. Wei, “Extension of VIKOR method for decision making problem based on hesitant fuzzy set,” Applied Mathematical Modelling, vol. 37, no. 7, pp. 4938–4947, 2013. [Google Scholar]
15. E. Afful-Dadzie, S. Nabareseh and Z. K. Oplatková, “Fuzzy VIKOR approach: Evaluating quality of internet health information,” in Proc. Federated Conf. on Computer Science and Information Systems, Warsaw, Poland, pp. 183–190, 2014. [Google Scholar]
16. S. Ali, S. Hossein, T. Mehran and T. Mohammad, “A fuzzy VIKOR method for supplier selection based on entropy measure for objective weighting,” Expert Systems and Applications, vol. 38, no. 10, pp. 12160–12167, 2011. [Google Scholar]
17. R. M. Alguliyev and R. S. Mahmudova, “Multicriteria personnel selection by the modified fuzzy VIKOR method,” The Scientific World Journal, vol. 2015, no. 612767, pp. 1–16, 2015. [Google Scholar]
18. M. Xue, X. Tang and N. Feng, “An extended VIKOR method for multiple attribute decision analysis with bidimensional dual hesitant fuzzy information,” Mathematical Problems in Engineering, vol. 2016, no. 4274690, pp. 1–16, 2016. [Google Scholar]
19. H. Bashir, K. Kyong and K. Ki-Il, “A study on fuzzy logic based cloud computing,” Cluster Computing, vol. 21, pp. 1–15, 2018. [Google Scholar]
20. S. Dima, Al Z. Malek and S. Adnan, “Enhanced multilevel fuzzy inference system for risk adaptive hybrid RFID access control system,” International Journal of Online and Biomedical Engineering (iJOE), vol. 18, pp. 31–51, 2022. [Google Scholar]
21. A. Javed and M. K. Pandey, “Anintegrated traffic light control system using RFID technology and fuzzy logic,” International Journal on Emerging Technologies, vol. 8, pp. 420–430, 2017. [Google Scholar]
22. L. Aruna and M. Aramudhan, “A comparative study of performance evaluation of services in cloud computing,” Advances in Intelligent Systems and Computing, vol. 1, pp. 533–540, 2015. [Google Scholar]
23. P. Marija, R. Nebojsa, G. Vladimir, M. Biljana and M. Olivera, “Two-stage fuzzy logic model for cloud service supplier selection and evaluation,” Mathematical Problems in Engineering, vol. 2018, pp. 1–11, 2018. [Google Scholar]
24. M. Faiz and A. K. Daniel, “Fuzzy cloud ranking model based on QoS and trust,” in Proc. 2020 Fourth Int. Conf. on I-SMAC (IoT in Social, Mobile, Analytics and Cloud) (I-SMAC), Tamilnadu, India, pp. 1051–1057, 2020. [Google Scholar]
25. M. Kyle, Q. Yanzhen and C. Marilyn, “An affective computing and fuzzy logic framework to recognize affect for cloud-based e-learning environment using emoticons,” Cloud Computing and Security, vol. 17, pp. 288–299, 2017. [Google Scholar]
26. N. Rajganesh and T. Ramkumar, “A fuzzy-based decision-making broker for effective identification and selection of cloud infrastructure services,” Soft Computing, vol. 23, no. 19, pp. 9669–9683, 2019. [Google Scholar]
27. M. K. Yadav, D. Gugal, S. Matkar and S. Waghmare, “Encrypted keyword search in cloud computing using fuzzy logic,” in Proc.2019 1st Int. Conf. on Innovations in Information and Communication Technology (ICIICT), Chennai, India, vol. 2019, pp. 1–4, 2019. [Google Scholar]
28. R. Shyamala and D. Prabakaran, “A survey on security issues and solutions in virtual private network,” International Journal of Pure and Applied Mathematics, vol. 119, no. 15, pp. 3115–3122, 2018. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools