 Open Access
Open Access
ARTICLE
Energy Efficient Green Routing for UAVs Ad-Hoc Network
1 Department of Computer Science and Engineering, Sree Sowdambika College of Engineering, Tamil Nadu, India
2 Department of Computer Science and Engineering-AI & ML, School of Engineering, Malla Reddy University, Hyderabad, India
3 Faculty of Electrical and Computer Engineering, University of Engineering and Technology Peshawar, 25000, Peshawar, Pakistan
4 Department of Computer Engineering, College of Computer and Information Sciences, King Saud University, P.O. Box 51178, Riyadh, 11543, Kingdom of Saudi Arabia
* Corresponding Author: Salman A. AlQahtani. Email:
Intelligent Automation & Soft Computing 2023, 37(1), 1111-1127. https://doi.org/10.32604/iasc.2023.034369
Received 15 July 2022; Accepted 10 March 2023; Issue published 29 April 2023
Abstract
The purpose of this article is to propose Stability-based Energy-Efficient Link-State Hybrid Routing (S-ELHR), a low latency routing protocol that aims to provide a stable mechanism for routing in unmanned aerial vehicles (UAV). The S-ELHR protocol selects a number of network nodes to create a Connected Dominating Set (CDS) using a parameter known as the Stability Metric (SM). The SM considers the node’s energy usage, connectivity time, and node’s degree. Only the highest SM nodes are chosen to form CDS. Each node declares a Willingness to indicate that it is prepared to serve as a relay for its neighbors, by employing its own energy state. S-ELHR is a hybrid protocol that stores only partial topological information and routing tables on CDS nodes. Instead of relying on the routing information at each intermediary node, it uses source routing, in which a route is generated on-demand, and data packets contain the addresses of the nodes the packet will transit. A route recovery technique is additionally utilized, which first locates a new route to the destination before forwarding packets along it. Through simulation for various network sizes and mobility speeds, the efficiency of S-ELHR is shown. The findings demonstrate that S-ELHR performs better than Optimized Link State Routing (OLSR) and Energy Enhanced OLSR (EE-OLSR) in terms of packet delivery ratio, end-to-end delay, and energy consumption.Keywords
Unmanned aerial vehicles (UAVs) have grown in popularity recently due to their superior transportation, affordability, and effectiveness of delivery. UAV Ad Hoc Networks (UANETs) is made up of flying objects that can travel in any direction and communicate with one another even without a ground connection. UAVs have been more well-liked recently in both industry and education due to their adaptability and flexible services. Because of their focus on establishing and designing control systems, UANets have various applications, including agricultural management, animal inspection, and medical applications for the military Several routing protocols have been proposed for the UANETs [1–6]. Routing protocols are divided into proactive and reactive categories based on the route discovery principle. Active protocols, as opposed to reactive protocols, make periodic changes to the routes for every pair of nodes. The reactive or on-demand protocols use a broadcasting strategy to only provide the route when it is required.
A network’s Virtual Backbone (VB), often referred to as a CDS, is a subset of nodes that are connected to one other. The CDS nodes are identified by implementing distributed or centralized methods. Distributed algorithms are largely used to select the CDS dynamically. The CDS can communicate between nodes [7–11]. The maintenance features built into the backbone construction algorithms let them adjust to topology changes brought on by node mobility. The stability of the virtual backbone is essential because most algorithms favor nodes with a high degree.
The three types of network-wide broadcasting techniques are based on probability, area, and neighbor knowledge [12]. These resource-intensive techniques are used by almost all routing protocols, such as Ad-hoc On-Demand Distance Vector (AODV) [13], Dynamic Source Routing (DSR) [14], and Optimized Link State Routing (OLSR) [15]. The Multipoint Relay (MPR) mechanism, based on neighbor information, is used by OLSR to reduce duplicate broadcasting. In MPR, each node selects some of its one-hop neighbors as forwarding nodes. These MPR nodes make sure that all two-hop neighbors receive the broadcast packets [16–19]. These MPRs combine to generate a CDS [20,21]. The data transfer through the backbone or CDS reduces the number of broadcast packets because only the nodes in the CDS are responsible for packet forwarding.
Most routing protocols use hop count as a selection metric, and it has been observed that the routes found are unstable. The study of utilizing CDS to support additional network functions, like multi-hop communications, has recently attracted more attention [10,11,22–24]. The performance of the network will be significantly improved by a stable backbone or CDS because node mobility frequently results in connection failures in UANET. In this article, we look at the stability of CDS. The suggested work uses three metrics: link connection time, which evaluates the time it takes for any two nodes to join, degree weight, which reduces CDS size, and energy weight, which selects nodes with more energy. The metric stability parameter combines these measurements. In a hybrid protocol, network-wide routing and broadcasting are done via stable CDS.
The partial link state information is distributed to all the nodes using multipoint relays. OLSR builds and updates routing tables by using MPR to distribute partial link status data to all network nodes. The two different types of control traffic in OLSR are HELLO and Topology Control (TC) packets. Each node gathers the 2-hop neighborhood information via HELLO packets. Although HELLO packets are periodically sent, no node ever forwards them. On an MPR selector list, every node keeps track of the nodes that have selected it as their MPR. Each node examines the addresses contained in the HELLO message, and if an ID is present in the MPR selection list, it is added to the list. A node checks to see if the sender is on the MPR selector list when it gets a packet. The packet will be sent if so. The OLSR protocol also frequently sends topology control (TC) packets. The TC packet, which is created by the MPR node, contains the link state data. There is also an MPR selection list. A node is aware that every other node in the TC packet can only be reached through the sender. The sender is the node in the next hop. Following the execution of shortest-path algorithms, the full network topology is discovered in this way, and routing tables are generated. The packet forwarding is handled by the MPR nodes [15].
In the graph G (V, E) of UAV networks, also known as UANETs, the collection of UAVs in the network is referred to as V, and the communication links between them as E. Each node in our homogeneous network has a fixed transmission range. An edge occurs between two nodes if their distance is less than their transmission range. A node is capable of locating itself via the Global Positioning System (GPS) or any other system. Table 1 contains a list of the symbols used in our work.
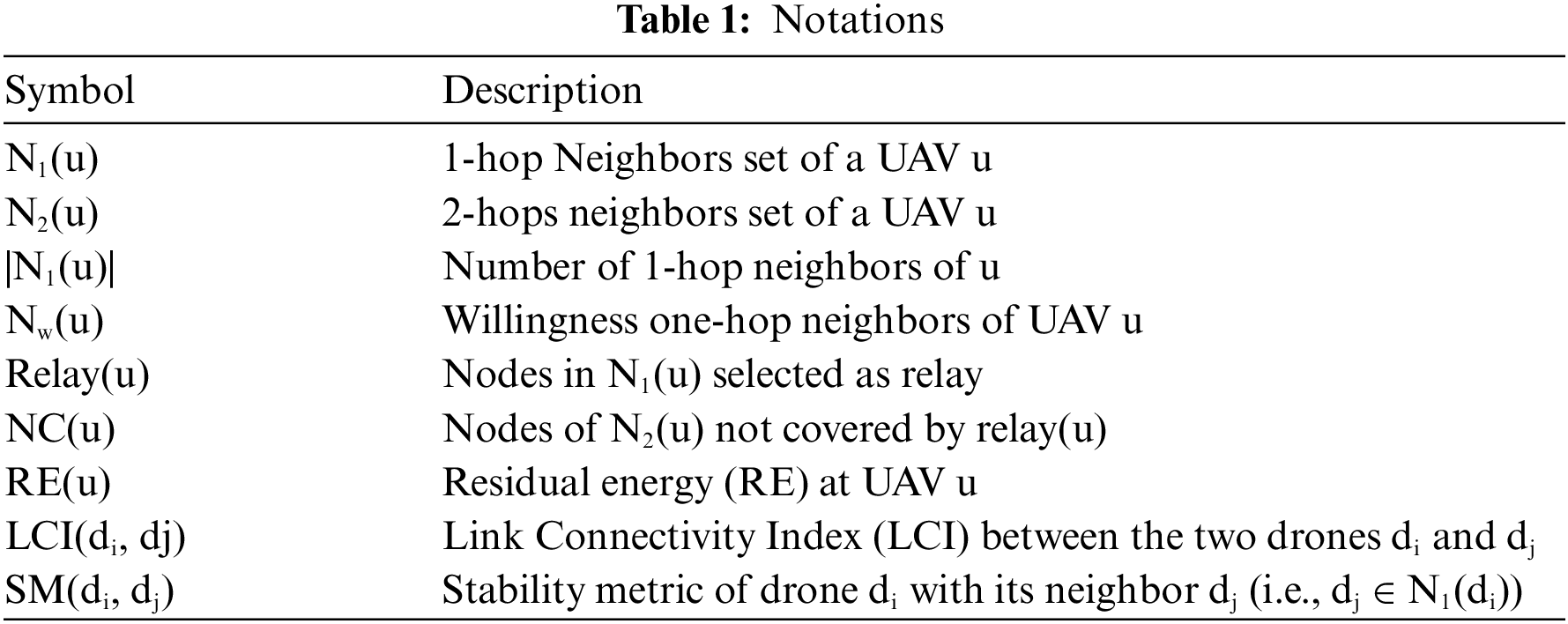
The related definitions are given below:
Definition 1: Relay(u) For a node ∀u ∈ V in a graph G = (V, E), Relay(u) = {v|v ∈ N1(u)} such that N2(u) = Sx∈ Relay(u)N1(x)
Definition 2: Connected Dominating Set (CDS) A set S ⊆ V is referred to as Dominating Set (DS) if, given a connected and undirected graph G = (V, E), ∀v ∈ V either v ∈ S or ∃x ∈ N1(v) with x ∈ S, (i.e., V = Ux∈S N1(x) ). If the graph that S produces is connected, it is referred to as CDS.
UAVNet is represented by the edge-weighed, connected, and undirected graph G = (V, E, W). The problem can be modeled using the edge weight function W : E → R+, where V = {v1, v2, ..., vn} denotes the set of nodes of UANET, E = {(vi , vj) | i ≤ n, j ≤ n} ⊆ V × V denotes the communication links between the nodes, and W = {w(i, j) | ∀(vi , vj) ∈ E} denotes the set of weights associated with the communication links.
The rest of the article is structured as follows: Section 2 presents the relevant works. Section 3 presents the contributions of the proposed research. The S-ELHR protocol is explained in Section 4. The simulation's findings are shown in section 5. Section 6 represents the work’s conclusion.
Based on the received signal intensity, anticipated link expiration period, and energy, a link’s stability is assessed. This section examines the routing protocols and CDS creation techniques based on these metrics.
2.1 CDS/Virtual Backbone Construction
The Bounded Diameter Minimum Spanning Tree (BDMST) problem is given as a learning automata-based distributed approach to creating a virtual backbone [25–27]. For quick and effective broadcasting in urban settings, a minimal-size CDS construction technique based on node velocity is proposed. This CDS’ primary function is to lessen the lag in VANET setups. The low stability metric is used to choose the nodes for CDS [22]. Nodes with a higher degree and fewer link modifications were given preference for forming CDS [28]. A stable dominating set construction based on link stability is suggested [23]. If the received beacon signal intensity is less than a threshold, a link is considered weak. To create a stable CDS, nodes with strong connections are found. In UANETs, a framework for backbone stability is established. Their model makes use of the dynamics of node movements, improving network stability for UAVs by taking connection information into account. The backbone creation algorithm favours sign control, total control of incidence, and incidence control over all other factors [29]. For both static and dynamic situations, a CDS construction technique is put forth [30]. In a dynamic setting, a brand-new heuristic called CDS-Hex is suggested [31]. Three metrics—mobility speed, degree, and energy—have been employed in an MPR-based method to build a stable CDS that is energy efficient. For MPR nodes with transmission power, battery power, degree, and mobility, a weight-based screening method has been proposed [32].
For the purpose of maintaining connectivity among the drone horde in applications for transportation during disasters, a CDS has been implemented. A node with a higher priority has been chosen for CDS [27,33,34]. For effective connectivity and maintenance in flying ad hoc networks, a topology management technique based on connection estimate is presented [24]. To provide a reliable and efficient virtual backbone, a scheduling technique based on minimum CDS is suggested. For UAVs of the Urban Internet of Vehicles, stable clustering and MPR selection are dependent on node quality of service (QoS). The QoS function was created as a node stability metric using a Bayesian belief function that took environmental indicators into account [35]. An improved OLSR protocol based on changed willingness is proposed [36], and the OLSR protocol configurations are tuned to work with UANETs. In order to choose MPRs in OLSR based on the drone’s neighbourhood, energy, stability, and key utilisation, a stable path selection employing the whale and lion optimization method is designed [37]. For FANETs, a delay- and link-stability-based routing protocol has been created. According to the highest importance of the nodes, a red-black priority tree is built in their job. Nodes are designated for selection if their stability exceeds the threshold value [38]. The packets are routed based on the link stability with regard to the positions and speeds of the nodes. The Euclidean distance was used to calculate the location stability. The velocity stability is determined each time the UAV gets a HELLO packet. The components of this protocol are adaptive HELLO packet control and route repair [39]. A connected dominating set with MPR-based broadcasting strategy was put forth [40]. Multi-objective OLSR, an energy-conscious OLSR methodology, was put out by [41–44]. By taking into account the transmission power usage and residual energy within each node, they calculated a composite energy cost and used this composite energy index as the routing metric.
2.2 MPR or Clustering Based Routing
Destination-Sequenced Distance-Vector (DSDV) Routing named Improved Sequencing Heuristic-DSDV (ISH-DSDV) is proposed for the internet of flying vehicles [45]. The bellman-ford algorithm, which consists of routing updates, information broadcasting, and a stale approach, is presented by ISH-DSDV. A clustering technique that is energy-efficient is proposed to transmit data in sensor nodes during emergency disaster monitoring. When evaluating a node's suitability to serve as a cluster head, factors such as degree, transmission power, mobility, starting energy of each sensor node, trust value node, and distance from the base station to each sensor node are all taken into consideration. Additionally, the node energy level and communication link quality are taken into account when determining the optimum path to the destination following each of these processes, aggregation algorithms employing an XOR gate operation remove duplicate information from various nodes [46].
A routing method for the Internet of Everything (IoE), in which some IoE-objects in the UAV-enabled IoE (Ue-IoE) are given the task of route computation (from neighbour objects to destination). The route computation objects (RCO) are chosen based on various factors, such as mobility and energy remaining. When an RCO has to communicate with another item, they relay the routing information to its neighbours. To evenly spread the load, the work of RCO is rotated among all IoE-objects in Ue-IoE [47]. This prevents the routing tables of all Ue-IoE objects from being impacted by the topology's frequent changes. IoT is a key component in the Smart Transport Infrastructure (STI) era. They first thoroughly examine the vehicular network and STI before illuminating the blockchain and Federated Learning through actual-world applications. Then, from the perspectives of security and privacy, FL and blockchain applications in the Vehicular Ad Hoc Network (VANET) environment are thoroughly addressed [48–55].
When a relay node in clustering or relay-based routing receives a packet, it consults the routing tables held by the relay nodes to pass the packet to the next hop. However, the nodes’ mobility may result in two issues: First, the source node may employ links that are not present while calculating routes; second, the topology may change while the packet is being forwarded. When these two issues exist, packet forwarding fails. Consequently, creating a reliable path for packet delivery is the main problem in UANETs. This inspired the development of a routing protocol that offers stable routing paths. The contributions of this work are summarized here,
1. For load balancing, a weight (ratio of actual and beginning energy) based willingness computation is implemented.
2. The connection connectivity period, energy, and degree of nodes are functions of the stability measure, which is how the CDS nodes are chosen.
3. S-ELHR, a hybrid link-state routing protocol, was developed to leverage CDS nodes to relay topology messages and maintain partial topology data.
4. S-ELHR uses source routing, which does away with the need for intermediate nodes to maintain routing tables.
5. In S-ELHR, a method for route recovery is added to allow for network topology changes.
4 Stability-Based Energy-Efficient Link-State Hybrid Routing (S-ELHR)
The suggested procedure S-ELHR is a hybrid protocol that sends data packets utilising on-demand source routing and relay-based broadcasting to determine the topology. It executes routing over CDS after creating CDS. An SM, a function on the link connection index, degree weights, and energy, is used in the CDS construction. Relay nodes are chosen based on their SM values. The CDS nodes are used to disseminate the topological information during the topology discovery or broadcasting of S-ELHR. The CDS nodes are used for routing, and each data packet carries a complete routing path that is built on demand. The stability metric calculation, CDS creation, and routing in S-ELHR are all explained in the following sections.
4.1 Stability Metric (SM) Calculation
We suggest a measure called SM that accounts for the three different cost metrics, Link Connectivity Index (as established in Section 4.1.2), Energy Weight (as defined in Section 4.1.3), and Degree Weight (as defined in Section 4.1.4), in order to determine the stability of a link. The predicted link expiration duration between the two nodes is calculated using the LCI measure. This statistic is used to identify the node that can provide a longer-lasting route and is more stable. Because nodes with higher energy must be chosen, the energy metric is employed to extend CDS lifetime. When nodes with more neighbours are chosen, CDS will be smaller in size.Therefore, our stability metric combines all three metrics to create the smallest CDS with the longest lifetime. Each node in the network computes its weights for energy and degree. It informs its one-hop neighbours of this knowledge. Following receipt of this data, each node determines the stability measure for each of its one-hop neighbours. The SM of a node u to its neighbor v can be defined as follows,
where α + β + γ = 1.
4.1.1 Computation of Willingness
Each node has a variable called Willingness, which indicates if it is ready to forward packets for other nodes. As its conditions alter, a node’s willingness may change dynamically. Each node in S-ELHR employs weight to determine its Willingness, which is a ratio between actual and starting energy. If the expected weight is less than 10% according to our protocol, a node announces a WILL LOW. Willingness is set to WILL DEFAULT if the expected ratio is between 10% and 50%. If not, a node expresses its willingness to be WILL_HIGH. The weight-based Willingness selection is shown in Table 2.

In this study, a weight-based choosing of willingness is added to the relay selection to improve the relay selection. Nodes can now declare a willingness value of WILL HIGH, which suggests a high willingness, or WILL LOW, which denotes a low willingness to act as a relay. In this protocol, a node with WILL LOW will never be included in the CDS selection. The weight value of the issuing node is stored in the HELLO message’s Willingness field.
4.1.2 Link Connectivity Index (LCI) Metric
The expected connection lifespan of two nodes, di and dj, as described by [42–44], is the basis for the LCI metric. The formula for this time is as follows. Let di and dj each have coordinates of (Xdi, Ydi) and (Xdj, Ydj), respectively. The two nodes are traveling in directions of θdi and θdj at speeds of vdi and vdj, respectively. Let R represent the nodes’ transmission range. Then, the amount of time CI(di , dj), the drones di and dj will stay connected is
where p, q, r, s can be calculated by Eqs. (3)–(6), respectively.
4.1.3 Energy Weight (EW) Metric
The EW of a node u is the ratio of remaining energy in u to the maximum energy of nodes in N1(u)
4.1.4 Degree Weight (DW) Metric
The DW of a node u is the ratio of the number of neighbors of u to the maximum degree of nodes in N1(u)
4.2 CDS Construction in S-ELHR
Our method may construct a CDS without any prior knowledge of the global network topology. Each node keeps a record of its one-hop and two-hop neighbours’ IDs. To support these updates, HELLO messages are sent on a regular basis. The following steps make up the proposed CDS selection process: Each node first chooses which group of one-hop neighbours it will use as its relay nodes in terms of stability metric. The relay set is then communicated to each node’s one-hop neighbours. Each node first sets its dominant flag to false. If x is the only node that can reach some of its neighbours, node v chooses one-hop neighbour x as its relay. If not, it selects the neighbour with the highest SM value as a one-hop neighbour. Up until all of the two-hop neighbours are covered, this process is repeated. The dominating flag is then set to true for each relay set node. A CDS is created for the network by all the dominant nodes. The selection process for CDS is shown in Algorithm 1.
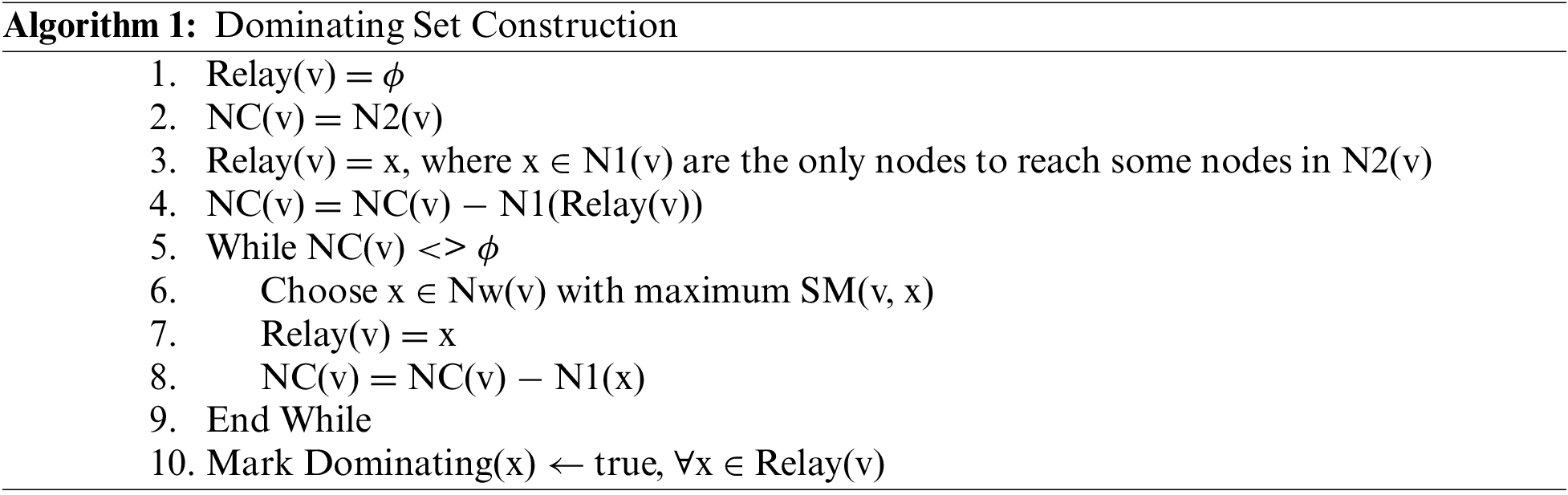
This section explains the topology discovery and source routing in S-ELHR.
Each node in the network is responsible for maintaining the local features and partial topological information. Details regarding the communication channel between nodes and their neighbours are provided via local information. Relay-update messages, which list the nodes that have been chosen as relays, are transmitted by each dominant node. The relay update messages cause the partial topology information base to be updated. The relay-update message is forwarded in the manner described below:
1) Relay-update messages are sent to all of a node’s neighbours when the node is the message’s sender.
2) When the node from which it receives the message for the first time is on the list of Relay-Selector, the relay node will pass the message to all of its neighbours. Otherwise, the message cannot be forwarded.
3) Step (2) is repeated until no more forwards are needed.
4.3.2 Route Computation and Route Recovery
When a node wants to deliver a datagram, a route computation is performed. In S-ELHR, nodes don’t keep track of routing tables. The topology information base’s shortest path algorithm is used to build the path for the given destination address. The only intermediate nodes in the established path are the dominating nodes. In addition, source routing rather than hop-by-hop routing is used in S-ELHR for data re-transmission and to enhance routing performance. A source node establishes a complete path. The packets will be re-transmitted by the dominant relay nodes. As each packet contains a complete path for transmission, maintaining routing tables at intermediate nodes is no longer necessary. Because the network is dynamic, broken links are a possibility. A route recovery strategy is also used by the S-ELHR to adjust to network topology changes. Intermediate nodes examine if the next hop in a packet’s source route is a neighbour as each S-ELHR packet conveys the routing path. If so, the packet is forwarded. If not, a new route to the destination is computed using route re-computation, and the packets are then forwarded along the new route. This method is explained by Algorithm 2.

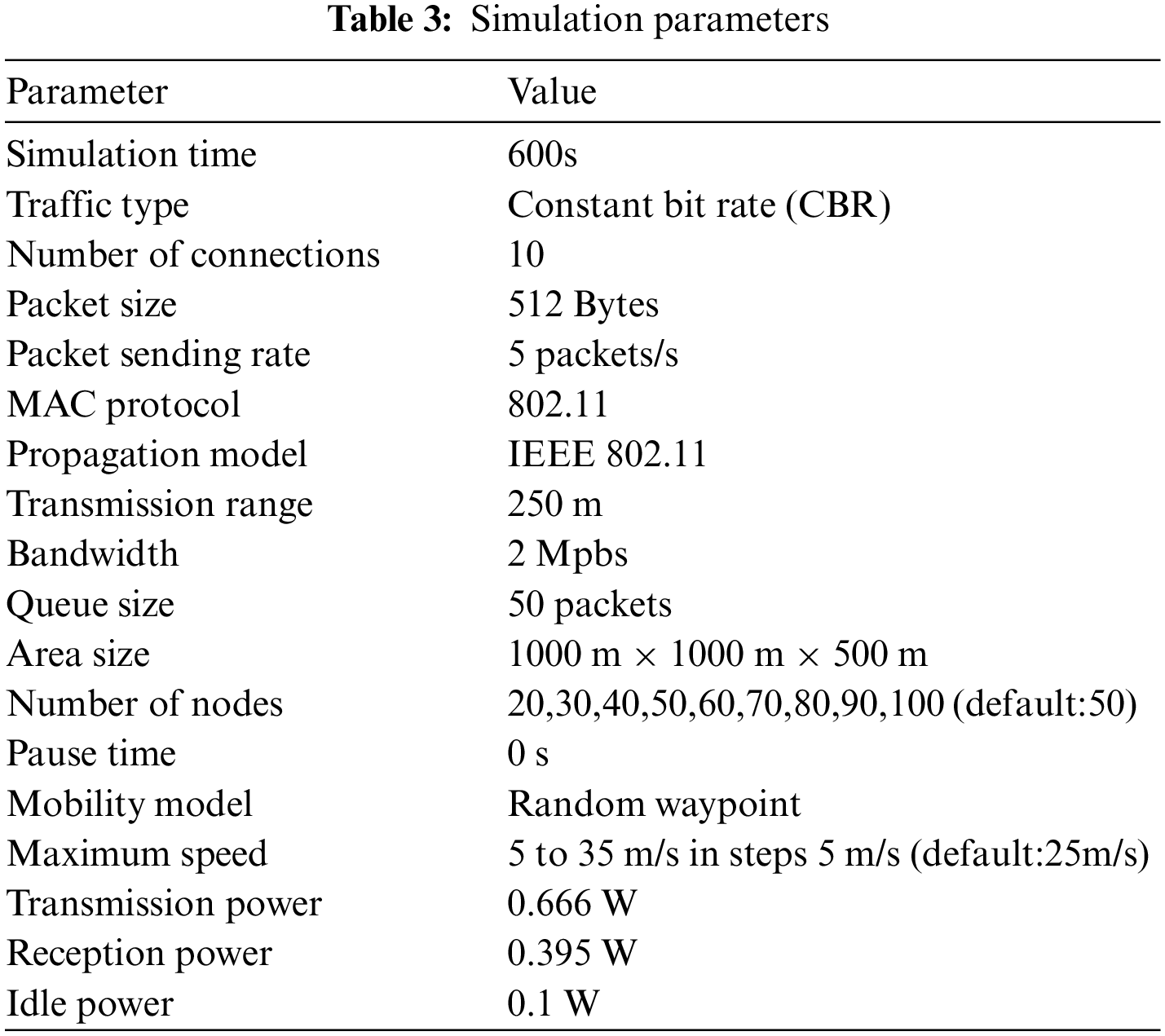
The simulations are run using NS2 to assess the suggested work. 512-byte Constant Bit Rate (CBR) packets are sent over the air. Pairs of sources and destinations are chosen at random. Table 3 provides a summary of the simulation’s parameters. Error graphs are used to display the average of the findings, which are drawn from 30 trials. The performance of S-ELHR is compared to OLSR and EE-OLSR because the proposed work uses CDS nodes for network-wide broadcasting and routing.
5.1 Impact on the Selected Relay Nodes
Fig. 1. illustrates how, as protocol nodes expand, so does the number of relay nodes. Nodes with less leftover energy are excluded by the weight-based willingness. The number of relay nodes is greatly decreased by the CDS construction with stability metric. Additionally, the suggested protocol S-ELHR chooses a reliable CDS that can offer a long-lasting routing path. The OLSR's MPR selection method does not account for difficulties with route stability. But in EE-OLSR energetic status is used MPR construction process. WILL DEFAULT and energetic status, respectively, are used in OLSR and EE-willingness-based OLSR's MPR selection. Comparing S-ELHR to EE-OLSR and OLSR, the figure demonstrates that S-ELHR has the smallest relay set size.
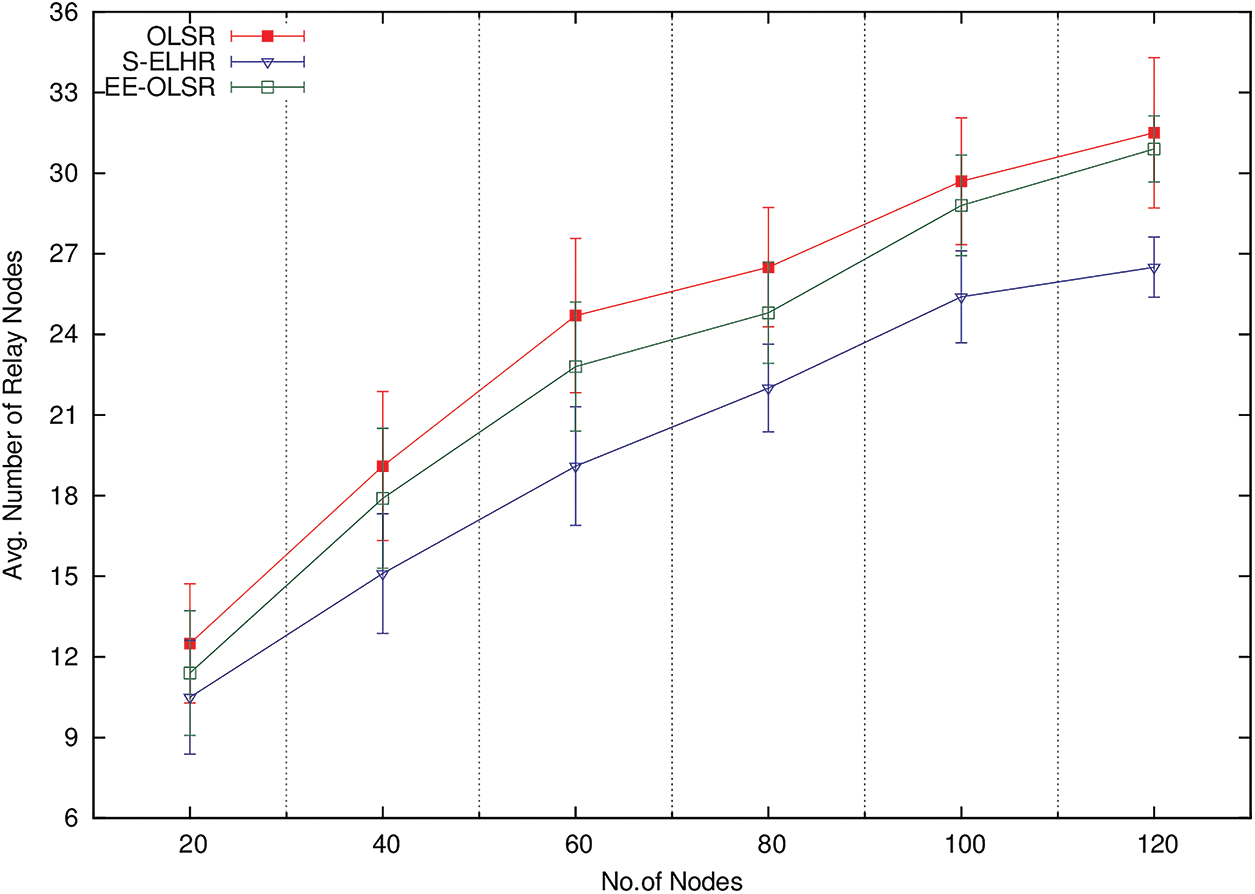
Figure 1: Average MPR size
The performance of the networks is significantly influenced by the length of the shortest path linking the various sources and destinations. Longer paths cause the traffic flow's delay, jitter, and packet loss to increase. The average path lengths for the protocols are computed in order to assess the impact on the path lengths, and they are displayed in Fig. 2. S-ELHR performs better than OLSR and EE-OLSR because it chooses fewer CDS nodes in sparse networks. When the network is denser, the likelihood of shorter pathways is higher. In denser networks, the average path length for S-ELHR, OLSR, and EE-OLSR is almost the same. However, when compared to OLSR and EE-OLSR, the S-ELHR provides the shortest average path length.
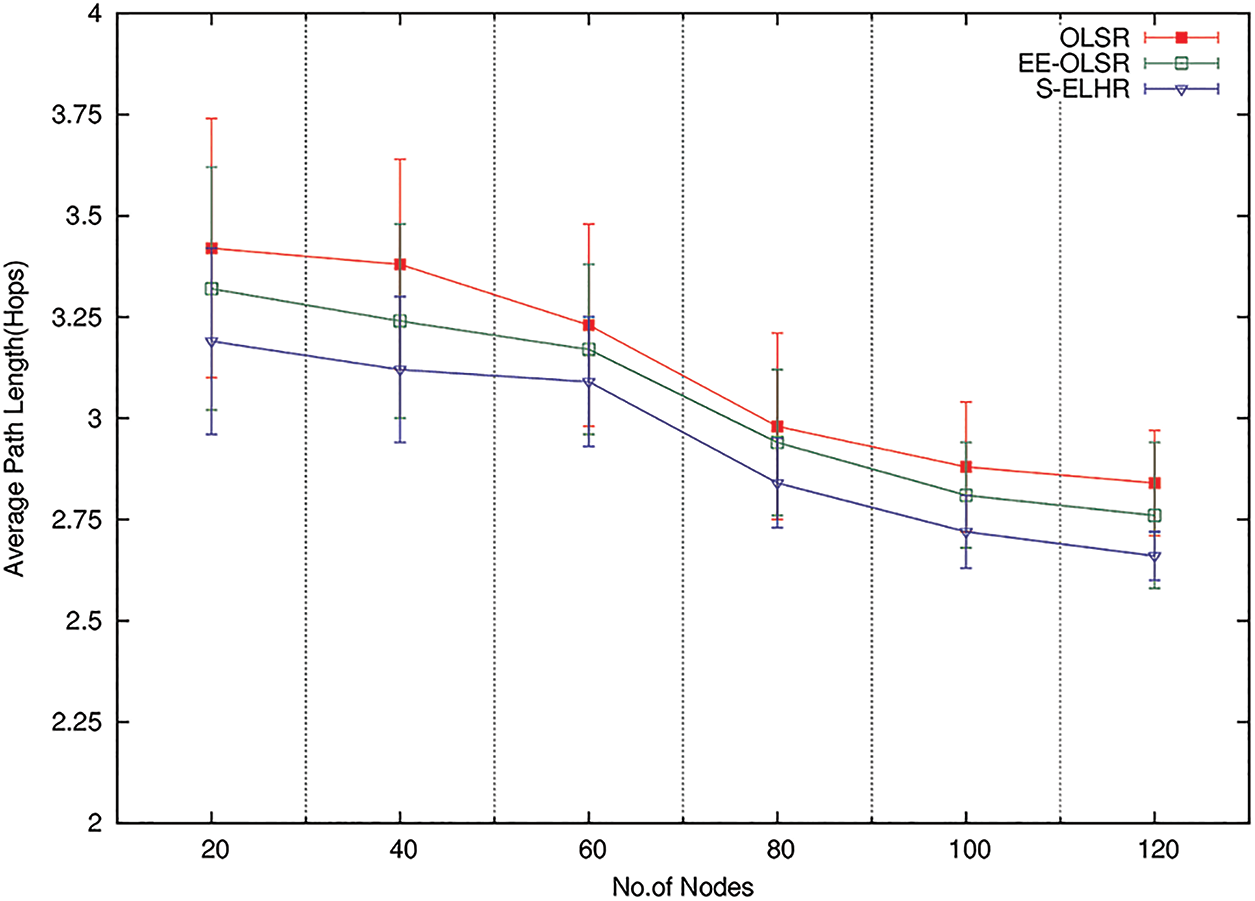
Figure 2: Average path length in hops
5.3 Impact on Number of Topology Message Forwarding
The average number of topological messages sent by each node during the simulations is shown in Fig. 3a against network density. Since there are more relay nodes as the network size grows for the protocols, there are more topological messages. The stability of the CDS is taken care of by the connection index, degree, and energy measurements employed in S-ELHR. As a result, in OLSR, the path across these nodes has fewer link breakages than the path through MPR. The EE-OLSR protocol offers a more energy-rich path than OLSR since it considers the nodes' energy consumption as an MPR selection metric. EE-OLSR has more topology overhead than S-ELHR because of the bigger MPR set size. In contrast to OLSR and EE-OLSR, S-ELHR has minimal topological message overhead. The topology overhead of the protocols is seen to grow with changing speed in Fig. 3b. The increased topology overhead for the protocols is a result of the more topology change caused by faster nodes. When the node speed is more than 25 m/s, the MPR set frequently changes for both OLSR and EE-OLSR. More topological message forwarding results from this. S-ELHR has the least topological overhead among the protocols, but, as a result of the stability metric’s tendency to prevent frequent changes in the DS set.
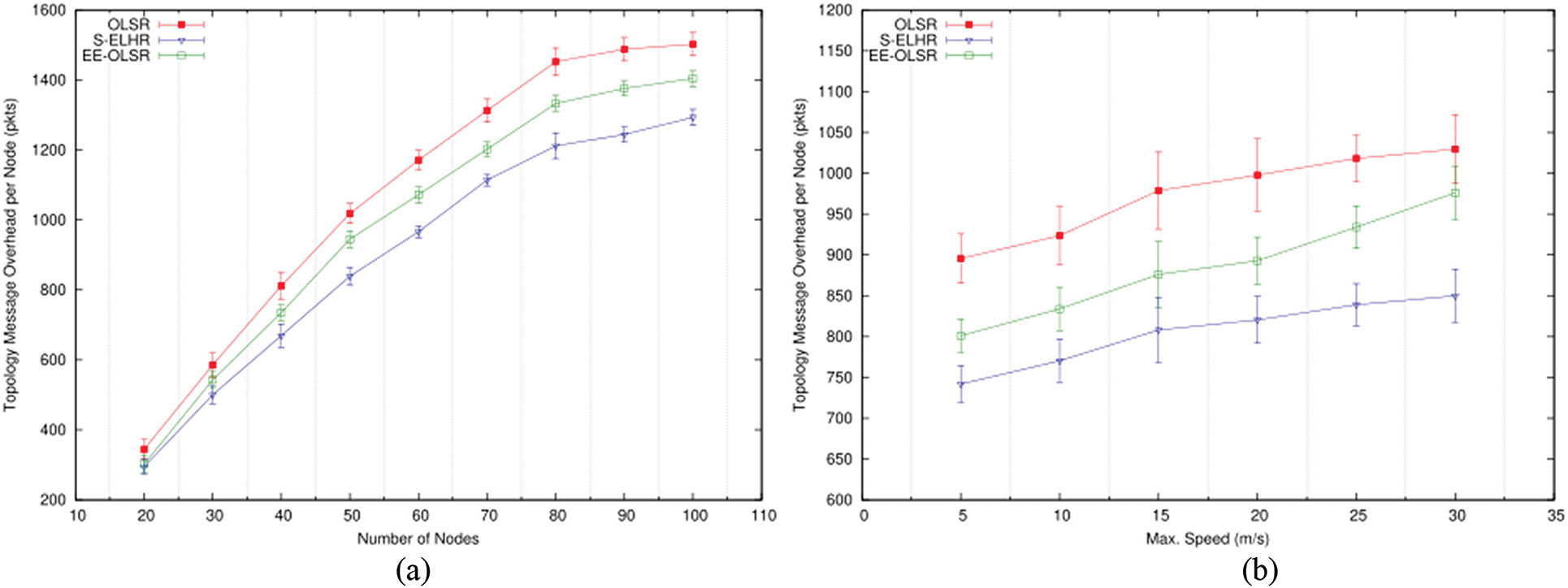
Figure 3: Topology message overhead
5.4 Impact on Energy Consumption
Fig. 4 depicts the typical energy used for the planned work with various network sizes and node speeds. (a) and (b). The S-ELHR uses the least amount of energy when compared to the EE-OLSR and OLSR since it has minimal control overhead. Fig. 4b demonstrates how the energy consumption of the protocols rises as the speed does. Due to increased route breakage at speeds greater than 20 m/s, EE-OLSR and OLSR use more energy. S-ELHR uses the least amount of energy when compared to EE-OLSR and OLSR since it forwards messages across fewer, more stable nodes with minimal topology.
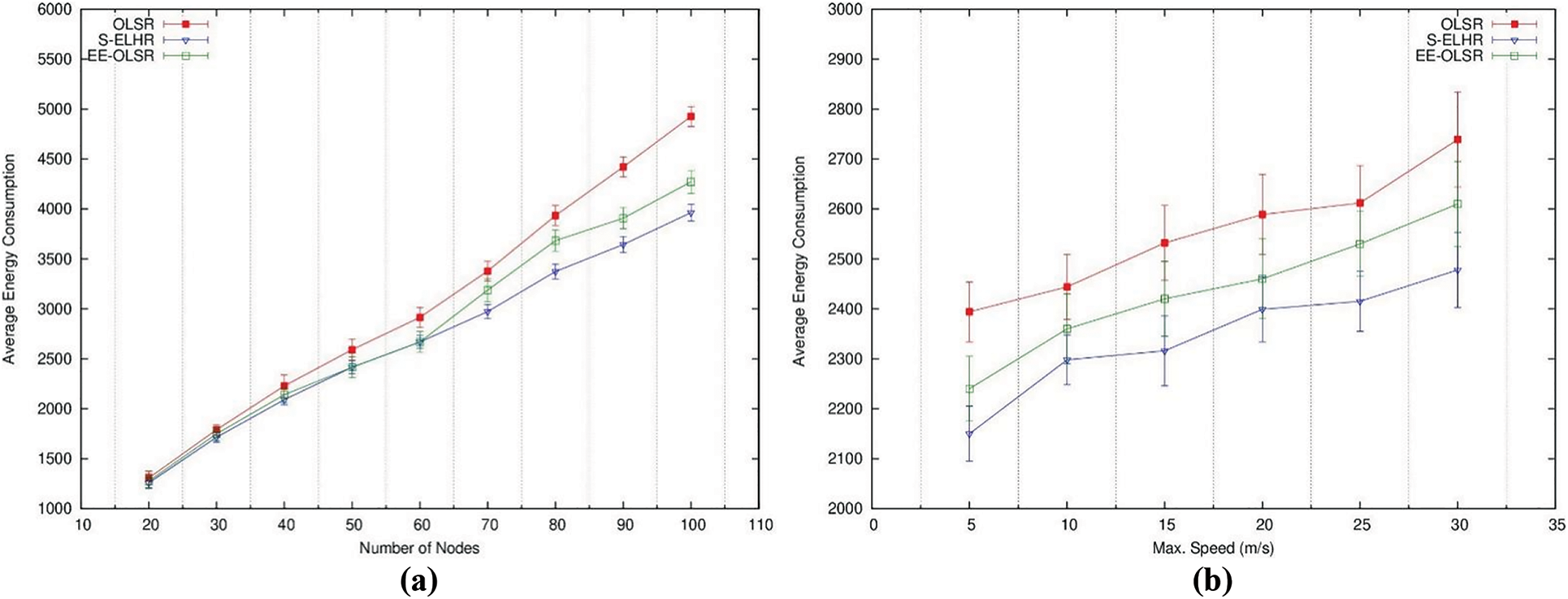
Figure 4: Average energy consumption
5.5 Impact in Routing Performances
The statistics in Figs. 5a and 5b are displayed to indicate the number of control packets transmitted for each successful data packet transmission. The routing overhead is shown as a function of network size in Fig. 5a. S-ELHR generates fewer control packets than EE-OLSR and OLSR because fewer nodes are selected to serve as relays. This graph demonstrates how node mobility has an impact on the control overhead of the protocols. Despite enhanced node mobility, S-ELHR generates much less overhead than EE-OLSR and OLSR. This is because S has fewer link breaks than other chains. A whole new path can likewise be constructed using the route recovery technique. As a result, S-ELHR has the least amount of routing overhead when compared to EE-OLSR and OLSR. This is shown in Fig. 5b.
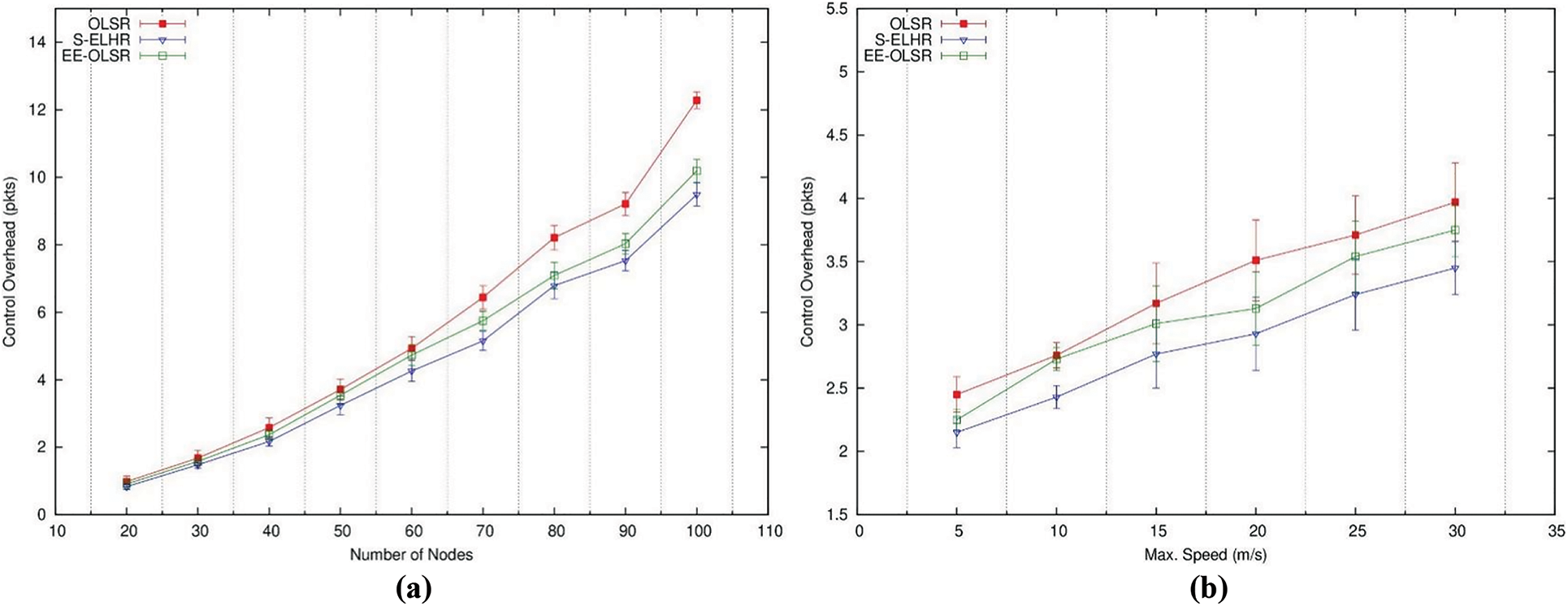
Figure 5: Control overhead per data packet
The number of control packets sent for each successful data packet transfer is shown in Figs. 5a and 5b. Fig. 5 depicts the routing overhead for various network sizes (a). S-ELHR produces fewer control packets than EE-OLSR and OLSR because fewer nodes are chosen as relays. As the node mobility increases, it is clear that the protocols’ control overhead rises. S-ELHR creates significantly less overhead than EE-OLSR and OLSR while having more node mobility since there are fewer link breakages. A new route is also rebuilt using a route recovery method. As a result, S-ELHR has the lowest routing overhead when compared to EE-OLSR and OLSR. In Fig. 5, this is depicted (b).
The effectiveness of the protocols is assessed with different network sizes. Five CBR packets are generated from 10 randomly selected source and destination nodes every second, with the maximum node speed in the simulation set to 25 m/s. As the network size grows, as shown in Fig. 6a the performance of OLSR degrades, demonstrating that OLSR does not scale with expanding network size. The results in Fig. 6a demonstrate that when the network’s node count increases, the S-ELHR maximizes the packet delivery ratio. With more reliable routes, the S-ELHR source routing technique lowers packet loss. Fig. 6b displays the performance when the nodes’ speeds increase. Nodes’ top speed has been raised from 5 to 45 m/s in increments of 5 m/s. When the node speed is low, the protocols show a similar delivery ratio, but as the node speed grows, the delivery ratio decreases. S-source ELHR’s routing and route recovery mechanisms make it possible to provide more packets than the competition. As a result, S-ELHR has the highest delivery ratio when compared to EE-OLSR and OLSR, showing better node mobility resistance.
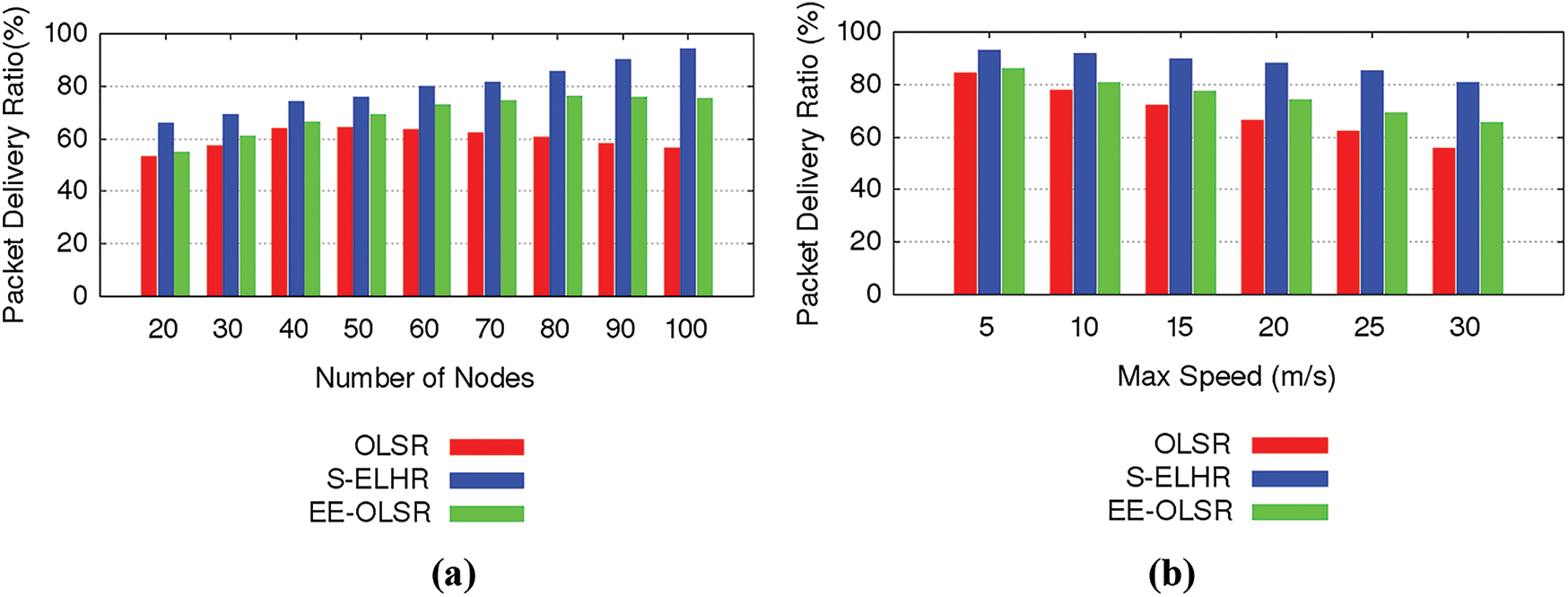
Figure 6: Packet delivery ratio
5.5.3 Average End-to-End Delay:
The average end-to-end delay with varying network sizes is shown in Fig. 7a. Compared to OLSR and EE-OLSR, S-ELHR has the smallest average end-to-end delay because the packets it routes travel a shorter distance. The production of too many control packets in OLSR and EE-OLSR uses up a lot of network resources, which increases delay. The delay vs maximum node speed for a network of 50 nodes is shown in Fig. 7b. The graph demonstrates that as node speed increases, so does the protocol delay. This is because there are more frequent path breakdowns, which are linked to higher node mobility. By enabling the nodes to begin forwarding the packet through a different route after the path break, S-ELHR reduces the latency using the route recovery mechanism.
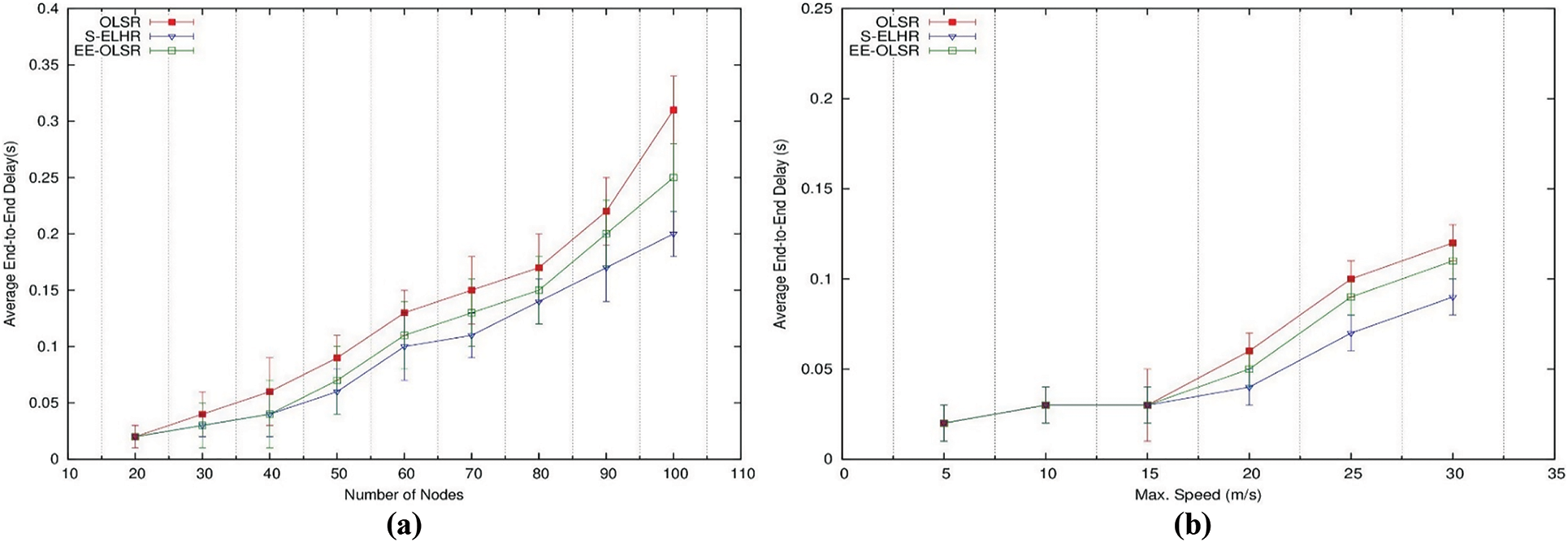
Figure 7: Average end-to-end delay
In this study, we propose the S-ELHR hybrid routing mechanism, which offers a reliable and long-lasting topology for routing. To choose stable relay nodes as dominating nodes, we employed a measure called the Stability Metric, which considers the connection connectivity duration, energy, and degree of nodes. The data transmission and topology discovery are carried out by the chosen dominating nodes. S-ELHR routes are computed on-demand, and source routing is used for data packet forwarding. An additional route recovery method is implemented to accommodate changes in network topology. The proposed work’s performance is assessed for a range of network sizes and node speeds, and its results are contrasted with those of EE-OLSR and OLSR. According to the simulation results, large networks have the highest S-ELHR packet delivery ratio. Due to the proposed protocol’s utilization of dominant nodes to relay messages, S-ELHR has the lowest control overhead, which lowers the network's energy usage. S-ELHR has strong scalability over a range of network sizes. S-ELHR also has the smallest average end-to-end delay when using the route recovery method. With high node mobility, the S-ELHR source-routing mechanism with route recovery performs well. S-ELHR protocol is hence appropriate for dynamic networks with large traffic loads.
Acknowledgement: The authors are extremely thankful to King Saud University for its financial support.
Funding Statement: This Research is funded by Research Supporting Project Number (RSPD2023R585, King Saud University, Riyadh, Saudi Arabia.
Author Contributions: Conceptualization, M.M., and R.R.; methodology, I.H.; software, I.H.; validation, I.H. and S.A.A.; formal analysis, I.H.; investigation, I.H., and S.A.A.; resources, I.H.; data curation, I.H.; writing—original draft preparation, M.M. and R.R.; writing—review and editing, M.M. and I.H.; visualization, I.H. and R.R.; supervision, R.R. and I.H.; project administration, I.H., and S.A.A.; funding acquisition, I.H. and S.A.A. All authors have read and agreed to the published version of the manuscript.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. I. Bekmezci, O. K. Sahingoz and S. Temel, “Flying ad-hoc networks (FANETsA survey,” Ad Hoc Networks, vol. 11, no. 3, pp. 1254–1270, 2013. [Google Scholar]
2. M. Y. Arafat and S. Moh, “Routing protocols for unmanned aerial vehicle networks: A survey,” IEEE Access, vol. 7, pp. 99694–99720, 2019. [Google Scholar]
3. R. A. Nazib and S. Moh, “Routing protocols for unmanned aerial vehicle-aided vehicular ad hoc networks: A survey,” IEEE Access, vol. 8, pp. 77535–77560, 2020. [Google Scholar]
4. K. Palan and P. Sharma, “FANET communication protocols: A survey,” International Journal of Computer Science and Communications, vol. 7, no. 1, pp. 219–223, 2015. [Google Scholar]
5. J. Jiang and G. Han, “Routing protocols for unmanned aerial vehicles,” IEEE Communications Magazine, vol. 56, no. 1, pp. 58–63, 2018. [Google Scholar]
6. Q. Sang, H. Wu, L. Xing and P. Xie, “Review and comparison of emerging routing protocols in flying ad hoc networks,” Symmetry, vol. 12, no. 6, pp. 971, 2020. [Google Scholar]
7. X. Qi, P. Yuan, Q. Zhang and Z. Yang, “CDS-based topology control in FANETs via power and position optimization,” IEEE Wireless Communications Letters, vol. 9, no. 12, pp. 2015–2019, 2020. [Google Scholar]
8. B. Wang, Y. Sun, T. Do-Duy, E. Garcia-Palacios and T. Q. Duong, “Adaptive d-hop connected dominating set in highly dynamic flying ad-hoc networks,” IEEE Transactions on Network Science and Engineering, vol. 8, no. 3, pp. 2651–2664, 2021. [Google Scholar]
9. R. Ramalakshmi and S. Radhakrishnan, “Connected k-coverage topology control for area monitoring in wireless sensor networks,” Wireless Personal Communications, vol. 84, no. 2, pp. 1051–1067, 2015. [Google Scholar]
10. R. Ramalakshmi and S. Radhakrishnan, “Weighted dominating set based routing for ad hoc communications in emergency and rescue scenarios,” Wireless Networks, vol. 21, no. 2, pp. 499–512, 2015. [Google Scholar]
11. R. Ramalakshmi and S. Radhakrishnan, “Energy efficient stable connected dominating set construction in mobile ad hoc networks,” in Proc. of Int. Conf. on Computer Science and Information Technology, Bangalore, India, pp. 63–72, 2012. [Google Scholar]
12. P. Montolio-Aranda, J. Garcia-Alfaro and D. Megias, “Improved flooding of broadcast messages using extended multipoint relaying,” Journal of Network and Computer Applications, vol. 34, no. 2, pp. 542–550, 2011. [Google Scholar]
13. H. Ullah, M. Khan, I. Hussain, I. Ullah, P. Uthansakul et al., “An optimal energy management system for university campus using the hybrid firefly lion algorithm (FLA),” Energies, vol. 14, no. 19, pp. 6028, 2021. [Google Scholar]
14. F. Ahmad, A. Ahmad, I. Hussain, G. Muhammad, Z. Uddin et al., “Proactive caching in D2D assisted multitier cellular network,” Sensors, vol. 22, no. 14, pp. 5078, 2022. [Google Scholar] [PubMed]
15. T. Clausen and P. Jacquet, “Optimized link state routing (OLSR) RFC 3626,” IETF Networking Group, vol. 11, 2003. [Google Scholar]
16. P. Xie, “An enhanced OLSR routing protocol based on node link expiration time and residual energy in ocean FANETS,” in Proc. of 24th Asia-Pacific Conf. on Communications (APCC), Ningbo, China, pp. 598–603, 2018. [Google Scholar]
17. Y. Jiao, W. Li and I. Joe, “OLSR improvement with link live time for FANETs,” in Advanced Multimedia and Ubiquitous Engineering. Springer, vol. 12, pp. 521–527, 2017. [Google Scholar]
18. P. Wróblewski, J. Kupiec, W. Drożdż, W. Lewicki and J. Jaworski, “The economic aspect of using different plug-in hybrid driving techniques in urban conditions,” Energies, Switzerland, vol. 14, no. 12, pp. 3543, 2021. [Google Scholar]
19. A. V. Leonov and G. A. Litvinov, “Simulation-based packet delivery performance evaluation with different parameters in flying ad-hoc network (FANET) using AODV and OLS,” Journal of Physics: Conference Series, vol. 1015, pp. 32178, 2018. [Google Scholar]
20. J. Wu, W. Lou and F. Dai, “Extended multipoint relays to determine connected dominating sets in MANETs,” IEEE Transactions on Computers, vol. 55, no. 3, pp. 334–347, 2006. [Google Scholar]
21. Y. S. Yen, H. C. Chang, R. S. Chang and H. C. Chao, “Routing with adaptive path and limited flooding for mobile ad hoc networks,” Computers & Electrical Engineering, vol. 36, no. 2, pp. 280–290, 2010. [Google Scholar]
22. M. A. Togou, A. Hafid and P. K. Sahu, “A stable minimum velocity CDS-based virtual backbone for VANET in city environment,” in Proc. of 39th Annual IEEE Conf. on Local Computer Networks, Edmonton, AB, Canad, pp. 510–513, 2014. [Google Scholar]
23. P. R. Sheu, H. Y. Tsai, Y. P. Lee and J. Y. Cheng, “On calculating stable connected dominating sets based on link stability for mobile ad hoc networks,” Journal of Applied Science and Engineering, vol. 12, no. 4, pp. 417–428, 2009. [Google Scholar]
24. X. Qi, X. Gu, Q. Zhang and Z. Yang, “A link-estimation based multi-CDSs scheduling mechanism for FANET topology maintenance,” in Proc. of Int. Conf. on Space Information Network, Wuzhen, China, Springer, pp. 66–86, 2019. [Google Scholar]
25. J. Akbari Torkestani, “A stable virtual backbone for wireless MANETS,” Telecommunication Systems, vol. 55, no. 1, pp. 137–148, 2014. [Google Scholar]
26. W. Ullah, I. Hussain, I. Shehzadi, Z. Rahman and P. Uthansakul, “Tracking a decentralized linear trajectory in an intermittent observation environment,” Sensors, vol. 20, no. 7, pp. 2127, 2020. [Google Scholar] [PubMed]
27. S. Khan, I. Hussain and M. I. Khattak, “Consensus based formation control of multiple UAVs,” Journal of Information Communication Technologies and Robotic Applications, vol. 11, no. 1, pp. 31–37, 2020. [Google Scholar]
28. P. Wróblewski, “Technology for obtaining asymmetries of stereometric shapes of the sealing rings sliding surfaces for selected anti-wear coatings,” in SAE Powertrains, Fuels & Lubricants Meeting, SAE Technical Paper, SAE International USA, pp. 2229, 2020. [Google Scholar]
29. J. Cui, L. Wang, B. Hu and S. Chen, “Incidence control units selection scheme to enhance the stability of multiple UAVs Network,” IEEE Internet of Things Journal, vol. 9, no. 15, pp. 13067–13076, 2022. [Google Scholar]
30. P. Wróblewski, W. Drożdż, W. Lewicki and P. Miązek, “Methodology for assessing the impact of aperiodic phenomena on the energy balance of propulsion engines in vehicle electromobility systems for given areas,” Energies, vol. 14, no. 8, pp. 2314, 2021. [Google Scholar]
31. M. Striki and T. McAuley, “Using novel distributed heuristics on hexagonal connected dominating sets to model routing dissemination,” Telecommunication Systems, vol. 52, no. 4, pp. 1757–1775, 2013. [Google Scholar]
32. G. Shenbagalakshmi and T. Revathi, “Enhanced route discovery using connected dominating set and 2-hop repair in wireless ad hoc networks,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 3, pp. 4193–4203, 2021. [Google Scholar]
33. A. Kurt, N. Saputro, K. Akkaya and A. S. Uluagac, “Distributed connectivity maintenance in swarm of drones during post-disaster transportation applications,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 9, pp. 6061–6073, 2021. [Google Scholar]
34. S. Zaman, L. U. Khan, I. Hussain and L. Mihet-Popa, “Fast computation of highly oscillatory ODE problems: Applications in high-frequency communication circuits,” Symmetry, vol. 14, no. 1, pp. 115, 2022. [Google Scholar]
35. P. Wróblewski, “An innovative approach to data analysis in the field of energy consumption and energy conversion efficiency in vehicle drive systems-the impact of operational and utility factors,” in Proc. of the 37th Int. Business Information Management Association (IBIMA), Cordoba, Spain, pp. 2391–2398, 2021. [Google Scholar]
36. E. A. Tuli, M. Golam, D. S. Kim and J. M. Lee, “Performance enhancement of optimized link state routing protocol by parameter configuration for UANET,” Drones, vol. 6, no. 1, pp. 22, 2022. [Google Scholar]
37. I. Hussain, I. Ullah, W. Ali, G. Muhammad and Z. Ali, “Exploiting lion optimization algorithm for sustainable energy management system in industrial applications,” Sustainable Energy Technologies and Assessments, Elsevier, vol. 22, pp. 102237, 2022. [Google Scholar]
38. A. Hussain, T. Hussain, F. Faisal, I. Ali, I. Khalil et al., “DLSA: Delay and link stability aware routing protocol for flying ad-hoc networks (FANETs),” Wireless Personal Communications, vol. 121, no. 4, pp. 2609–2634, 2021. [Google Scholar]
39. I. Ullah, I. Hussain and M. Singh, “Exploiting grasshopper and cuckoo search bio-inspired optimization algorithms for industrial energy management system: Smart industries,” Energies, vol. 9, no. 1, pp. 105, 2020. [Google Scholar]
40. T. Moulahi, S. Nasri and H. Guyennet, “Broadcasting based on dominated connecting sets with MPR in a realistic environment for WSNs & ad hoc,” Journal of Network and Computer Applications, vol. 35, no. 6, pp. 1720–1727, 2012. [Google Scholar]
41. Z. Guo, S. Malakooti, S. Sheikh, C. Al-Najjar and B. Malakooti, “Multi-objective OLSR for proactive routing in MANET with delay, energy, and link lifetime predictions,” Applied Mathematical Modelling, vol. 35, no. 3, pp. 1413–1426, 2011. [Google Scholar]
42. W. Su, S. J. Lee and M. Gerla, “Mobility prediction and routing in ad hoc wireless networks,” International Journal of Network Management, vol. 11, no. 1, pp. 3–30, 2001. [Google Scholar]
43. S. Zaman, I. Hussain and D. Singh, “Fast computation of integrals with fourier-type oscillator involving stationary point,” Mathematics, vol. 7, no. 12, pp. 1160, 2019. [Google Scholar]
44. I. Hussain, M. Ullah, I. Ullah, A. Bibi, M. Naeem et al., “Optimizing energy consumption in the home energy management system via a bio-inspired dragonfly algorithm and the genetic algorithm,” Electronics, vol. 9, no. 3, pp. 406, 2020. [Google Scholar]
45. I. U. Khan, M. A. Hassan, M. Fayaz, J. Gwak and M. A. Aziz, “Improved sequencing heuristic DSDV protocol using nomadic mobility model for FANETS,” Computer, Material and Continua, vol. 70, no. 2, pp. 3653–3666, 2022. [Google Scholar]
46. P. Wróblewski and G. Koszalka, “An experimental study on frictional losses of coated piston rings with symmetric and asymmetric geometry,” SAE International Journal of Engines, vol. 14, no. 6, pp. 853–866, 2021. [Google Scholar]
47. M. Ahmad, F. Ullah, I. Wahid, A. Khan, M. I. Uddin et al., “A bio-Inspired routing optimization in UAV-enabled internet of everything,” CMC-Computers Materials & Continua, vol. 67, no. 1, pp. 321–336, 2021. [Google Scholar]
48. P. Wróblewski and W. Lewicki, “A method of analyzing the residual values of low-emission vehicles based on a selected expert method taking into account stochastic operational parameters,” Energies, vol. 14, no. 21, pp. 6859, 2021. [Google Scholar]
49. A. R. Javed, M. A. Hassan, F. Shahzad, W. Ahmed, S. Singh et al., “Integration of blockchain technology and federated learning in vehicular (IoT) networks: A comprehensive survey,” Sensors, vol. 22, no. 12, pp. 4394, 2022. [Google Scholar] [PubMed]
50. S. Prabakaran, R. Ramar, I. Hussain, B. P. Kavin, S. S. Alshamrani et al., “Predicting attack pattern via machine learning by exploiting stateful firewall as virtual network function in an SDN network,” Sensors, vol. 22, no. 3, pp. 709, 2022. [Google Scholar] [PubMed]
51. A. R. Javed, M. Usman, S. U. Rehman, M. U. Khan and M. S. Haghighi, “Anomaly detection in automated vehicles using multistage attention-based convolutional neural network,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 7, pp. 4291–4300, 2020. [Google Scholar]
52. M. A. Hassan, A. R. Javed, T. Hassan, S. S. Band, R. Sitharthan et al., “Reinforcing communication on the internet of aerial vehicles,” IEEE Transactions on Green Communications and Networking, vol. 6, no. 3, pp. 1288–1297, 2022. [Google Scholar]
53. M. Arshad, A. Hussain, S. A. G. A. Shah, P. Wróblewski, Zunaira et al., “Thermal energy investigation of magneto-hydrodynamic nano-material liquid flow over a stretching sheet: Comparison of single and composite particles,” Alexandria Engineering Journal, Elsevier, vol. 61, no. 12, pp. 10453–10462, 2022. [Google Scholar]
54. P. Wróblewski and R. Rogólski, “Experimental analysis of the influence of the application of tin, tialn crn and dlc1 coatings on the friction losses in an aviation internal combustion engine intended for the propulsion of ultralight aircraft,” Materials, vol. 14, no. 22, pp. 6839, 2021. [Google Scholar]
55. P. Wróblewski, “Analysis of torque waveforms in two-cylinder engines for ultralight aircraft propulsion operating on 0w-8 and 0w-16 oils at high thermal loads using the diamond- like carbon composite coating,” SAE International Journal of Engines, vol. 15, no. 1, pp. 129–146, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools