 Open Access
Open Access
ARTICLE
Cooperative Channel and Optimized Route Selection in Adhoc Network
1 Department of Computer Science and Engineering, St. Joseph’s Institute of Technology, Chennai, 600119, Tamilnadu, India
2 Department of Computer Science & Engineering, SNS College of Technology, Coimbatore, 641035, Tamilnadu, India
3 Department of Computer Science & Engineering, SNS College of Engineering, Coimbatore, 641107, Tamilnadu, India
4 Department of Information Technology, Karpagam Institute of Technology, Coimbatore, 641032, Tamilnadu, India
* Corresponding Author: D. Manohari. Email:
Intelligent Automation & Soft Computing 2023, 36(2), 1547-1560. https://doi.org/10.32604/iasc.2023.030540
Received 28 March 2022; Accepted 09 May 2022; Issue published 05 January 2023
Abstract
Over the last decade, mobile Adhoc networks have expanded dramatically in popularity, and their impact on the communication sector on a variety of levels is enormous. Its uses have expanded in lockstep with its growth. Due to its instability in usage and the fact that numerous nodes communicate data concurrently, adequate channel and forwarder selection is essential. In this proposed design for a Cognitive Radio Cognitive Network (CRCN), we gain the confidence of each forwarding node by contacting one-hop and second level nodes, obtaining reports from them, and selecting the forwarder appropriately with the use of an optimization technique. At that point, we concentrate our efforts on their channel, selection, and lastly, the transmission of data packets via the designated forwarder. The simulation work is validated in this section using the MATLAB program. Additionally, steps show how the node acts as a confident forwarder and shares the channel in a compatible method to communicate, allowing for more packet bits to be transmitted by conveniently picking the channel between them. We calculate the confidence of the node at the start of the network by combining the reliability report for the first hop and the reliability report for the secondary hop. We then refer to the same node as the confident node in order to operate as a forwarder. As a result, we witness an increase in the leftover energy in the output. The percentage of data packets delivered has also increased.Keywords
For security reasons, the mobile Adhoc network uses extremely sensitive routing and employs a variety of communication channels to reach its objective. When nodes in a far away area communicate data wirelessly, there is a possibility that the reliability of the other nodes in the transmission will be compromised. Occasionally, information is forwarded to a node; however, if the receiver is unreliable or the forwarding node channel is unable to send all of the information, the network transmission is rendered useless; this condition has the potential to result in significant packet loss and network delay. In this proposed CRCN paradigm, protocol approaches are used to address transmission issues and provide the necessary solution for safely reaching the target [1]. In this proposed CRCN architecture, we offer a network lifetime extension-aware cooperative channel access network that is utilized to adapt to performing a multi-unbiased object function, with the following inputs:
We have developed a multi-unbiased adaptive design that selects a confident forwarder from a source to send packets to a destination. The protocol used in this research improves the network life of nodes, energy management, node decoding performance, and finds responsive forwarders to transmit the packets [2]. The purpose of this research is to develop a dependable mobile Adhoc network. We offer an ideal method for nodes to choose the channel that uses the least energy to connect to a neighbor, and then select the channel based on the unusable condition directly, or jointly, thereby paving the way and transmitting information with a confident neighbor. We assume that nodes have asymmetric transmission due to node usage; the available transfer power at both the source and forwarder can be any value; it is determined by the node utilization from the start to the current state. Fig. 1 illustrates how the proposed architecture offers a powerful best confident forwarder selection technique for constructing a path from source to destination.
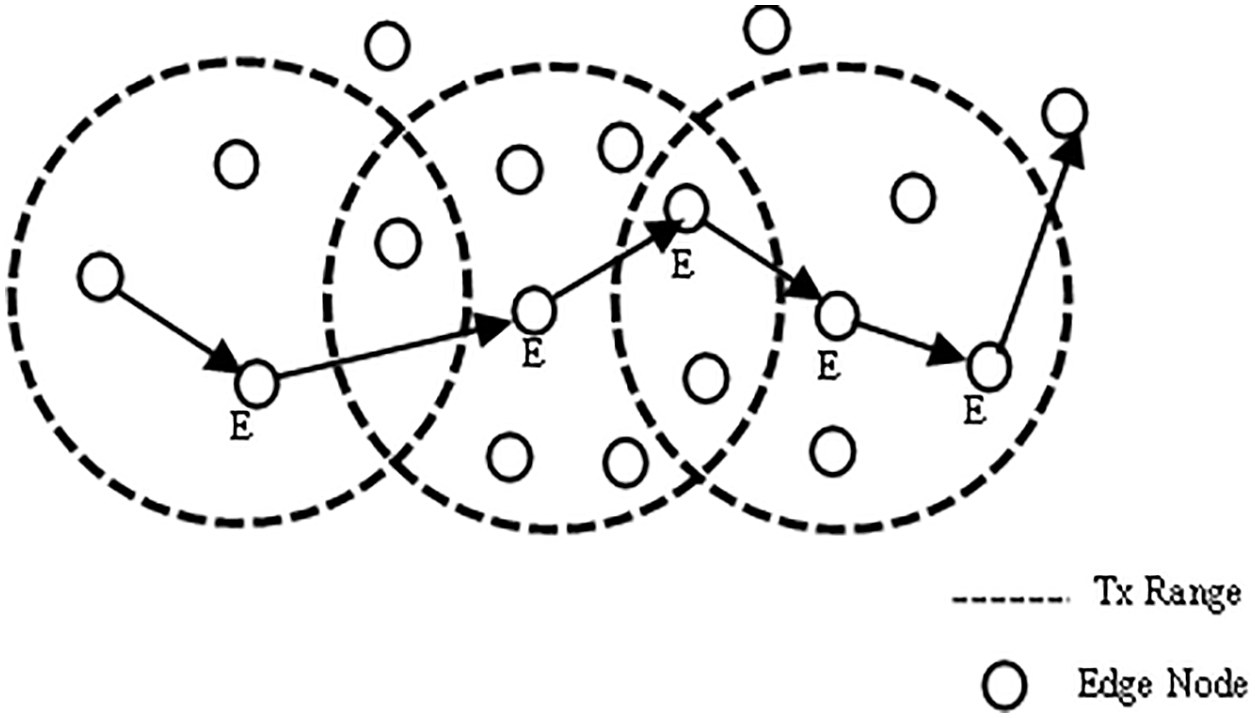
Figure 1: Transmission range nodes
Apart from the channel selection, this activity utilizes optimization calculations to provide multi-unbiased security and channel selection-based routing system. Here, we worked on the whale lioness calculations, which include lioness action into the whale to produce the ideal solution via perfect goal programming. The objectives identified in this suggested technique include numerous quality criteria derived from the media access control layer MAC, as well as distance and a confidence specification derived from the routing layer called the confidence of the node. We develop the fitness function to finalize the forwarder based on the afore said parameter adjustments [3]. The CRCN routing algorithm is composed of the following steps: (a) establishing quality measurements at two layers, (b) computing confidence levels, (c) identifying numerous disjoint paths, and (d) optimal pathfinding using the proposed multiple purpose channel selection methods. Thus, the proposed method provides an optimal transportation route with a favorable PDR, throughput, delay and energy consumption. The vital inputs of the suggested method for the confident based routing and lifetime extension aware channel access are as follows:
• Designing a multi unbiassed optimization system for reliable routing by recognizing the above quality of service metrics and a confidence parameter as multi unbiassed.
• Using many unbiassed models, i.e., energy, latency, link lifetime, distance, and confidence design, for the data transmission, so that the route is adopted and efficient, accelerating the convergence process [4], and reducing the number of discontinuous pathways.
It was necessary to extend the network’s life span to identify the best possible relay node for a given transmission power given at each source and relay node. Relay node selection in the MAC layer was also influenced by the transmission gain and residual energy.
In this work, we have taken place channel selection when the routing packets sent to find the path reach the MAC layer. The rest of this manuscript is discussed as follows. The part II represents the literature surveys in brief. In part III, the document pointed out the CRCN-cooperative channel selection and optimized route formation based on confidence in the Adhoc network is discussed. In section, IV informed the performance evaluation of the CRCN protocol and the end part carries out the CRCN conclusion, aims, and future opinions.
Due to the restricted amount of power available for computing and radio transmission in ad hoc networks, node performance is critical. Additionally, there may be considerable constraints on the available bandwidth and radio frequencies [5]. Ad hoc networks can also be beneficial for law enforcement, emergency response and rescue missions. Because the ad hoc networks can be created rapidly and inexpensively, they are well suited for the commercial applications such as wireless networks or virtual classrooms [6]. It has been an extended time since these devices reached their full capability. Thanks to wireless technologies, these massive pieces of equipment may now communicate with any new machinery and be used anywhere. Wireless medical technology such as CodeBlue and MobiHealth [7] is in use. This model’s representation of the wireless channel includes broadcast omni-directional antennas, large-scale route loss, and fading. Utilize it in lieu of OSI layer design and specialized routing protocols to provide a comprehensive perspective of the routing challenge [8]. As the number of devices in an ad-hoc network grows, management becomes increasingly difficult. Connecting ad-hoc networks to wired networks is not possible. Ad-hoc networks provide a novel method of wireless communication for mobile hosts. There is no fixed infrastructure such as base stations in mobile switching [9]. We undertake energy-efficient routing before scheduling nodes’ transmissions to identify the least-powerful paths. The created schedule is based on end-to-end traffic data and preceding routing decisions [10]. A mobile node consumes battery power in addition to sending and receiving data by listening to the wireless medium for communication requests from other nodes [11]. The topology of the universe is constantly changing. The topology of a mobile ad hoc network is constantly changing as nodes move [12]. The radio range of the other nodes in the ad hoc network is continually changing, requiring constant updating of the routing information [13]. MANET’s have a wide range of applications, from large-scale moveable and dynamic networks to small networks constrained by their power supply. Along with the legacy applications that migrate from the old infrastructure environment, a considerable number of new services can and will be developed for the ad hoc context [14]. Each node within a network’s wireless range receives packets, regardless of whether they were meant for another node. Due to these characteristics, it is simple for each node to view the packets of other nodes or to the inject fault packets into the network. Vital nodes may experience battery drain and hence become unavailable for routing, resulting in broken links and a severe impact on the routing protocol’s performance [15]. Another key objective is to conserve energy on nodes to ensure the network’s longevity. Without an established communication infrastructure, a group of wireless mobile hosts forms its network dynamically. However, due to its open network architecture and shifting network topology, it is vulnerable to both internal and external attacks. Reactive routing protocols are more efficient in dynamic topologies such as MANET. A concerted effort is being made to improve (Ad-hoc On-Demand Distance Vector) AODV, the most widely used reactive routing technique. The Internet technical task committee has designated AODV as the official routing protocol for MANET [16]. Radios can broadcast over a large region. To determine whether a packet should be sent or received locally, each node within that range must receive it. Even if the majority of these packets are discarded, they use energy under this basic energy model [13]. The capacity of the power management system to respond to variations in traffic load is reflected in the length of the soft-state timer. We give methods for determining a neighbor’s power management [17], as broadcasting to a sleeping node is not the same as broadcasting to an active node. There are a variety of power control approaches that can be used to minimize network interference. Finally, the author Abdullah Waqas et al. [18] offered a routing algorithm for edge computing-enabled 5g networks, as well as a system of recommended metrics that is a function of the created and received interference in the network. The received interference term ensures that the Signal to Interference plus Noise Ratio (SINR) along the route remains greater than the threshold value, whilst the produced interference term ensures that only those nodes are chosen to forward packets that cause minimal interference to other nodes. The results indicate that the suggested method outperforms standard routing protocols in terms of network speed and outage probability.
3 CRCN Design and Implementation
Consider a Graph
The initial confidence values for each wireless node is calculated using a differential evolutionary method. After calculating the initial confidence values, the multi-objective method is used based on the Lion whale optimization
The degree of one-hop evolution is identified from a diverse evolution-based belief evaluation model as shown in Fig. 2. After calculating the one-hop confidence values, the table of confidence is broadcasting to one of its hop neighbors by the wireless sender.
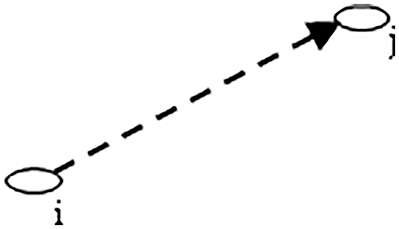
Figure 2: One hop communication
We calculate the one-hop confidence
Each node buys a one-hop report and checks the activities of its neighbors. When calculating the confidence value between two nodes, it falls between 0 and 1. Of these, 0 is taken as the confidence-less node and 1 is considered as a very reliable node. Each node start storing the information about the neighbor in an array format, they are:
• Neighbor’s trust value,
• The amount of energy present in the node
• Changes in distances
• Channel life between two nodes
• Calculate how many routes can be set by a neighbor node
3.4 Secondary Node Trust Validation
Similarly, from the confidence tables obtained, the number of secondary hop confidence
Here
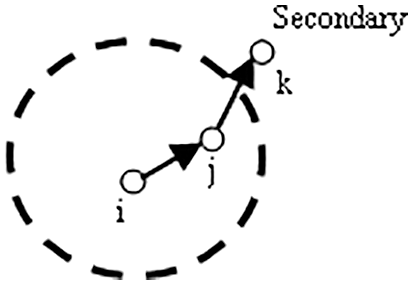
Figure 3: Secondary hop communication
With each iteration of the confidence
This variable average model uses weighted distribution based on the weighting factor. Where α and β are considered as the tunable weight value. These two together will be within the number 1.
4 Network Resource Validations
The energy parameter for each neighboring node is intended based on the number of packets transferred and the energy cost
The distance between both latitude and longitude is calculated in Eq. (5) and denoted as x and y.
The transmission range of the node is signified by the radius r. Using these values as input, the connection lifetime for each node is calculated as seen below Eq. (6).
Parameter distance is calculated by means of Euclidean distance estimation using latitude and longitude as inputs. The next parameter is to calculate how many routes are available for each node to reach the destination by its neighbor with node counts
4.1 Optimized Path Selection Initiation
Once the objective parameters for each node have been calculated, the
Here boundary value
4.2 The Following Steps are Implemented During Further Repetitions
The node status update during the optimization process is recognized by hunting behavior of
Here
Using the
Population-related solution vectors are calculated using the following Eq. (11),
where
If the developed solution has more
4.3 Multi-Purpose Optimization Evaluated in MAC Layer
Second multi-purpose optimization is used in the mac layer for optimal medium access-based transmission during data transmission. During the data transfer period, node sends request to send-
Here
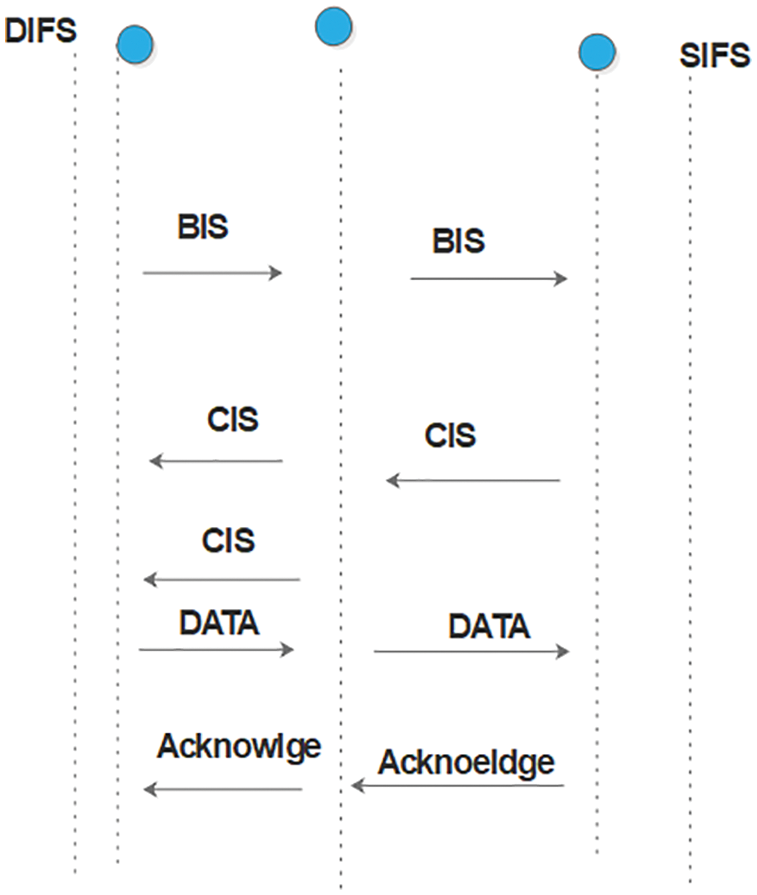
Figure 4: Channel selection
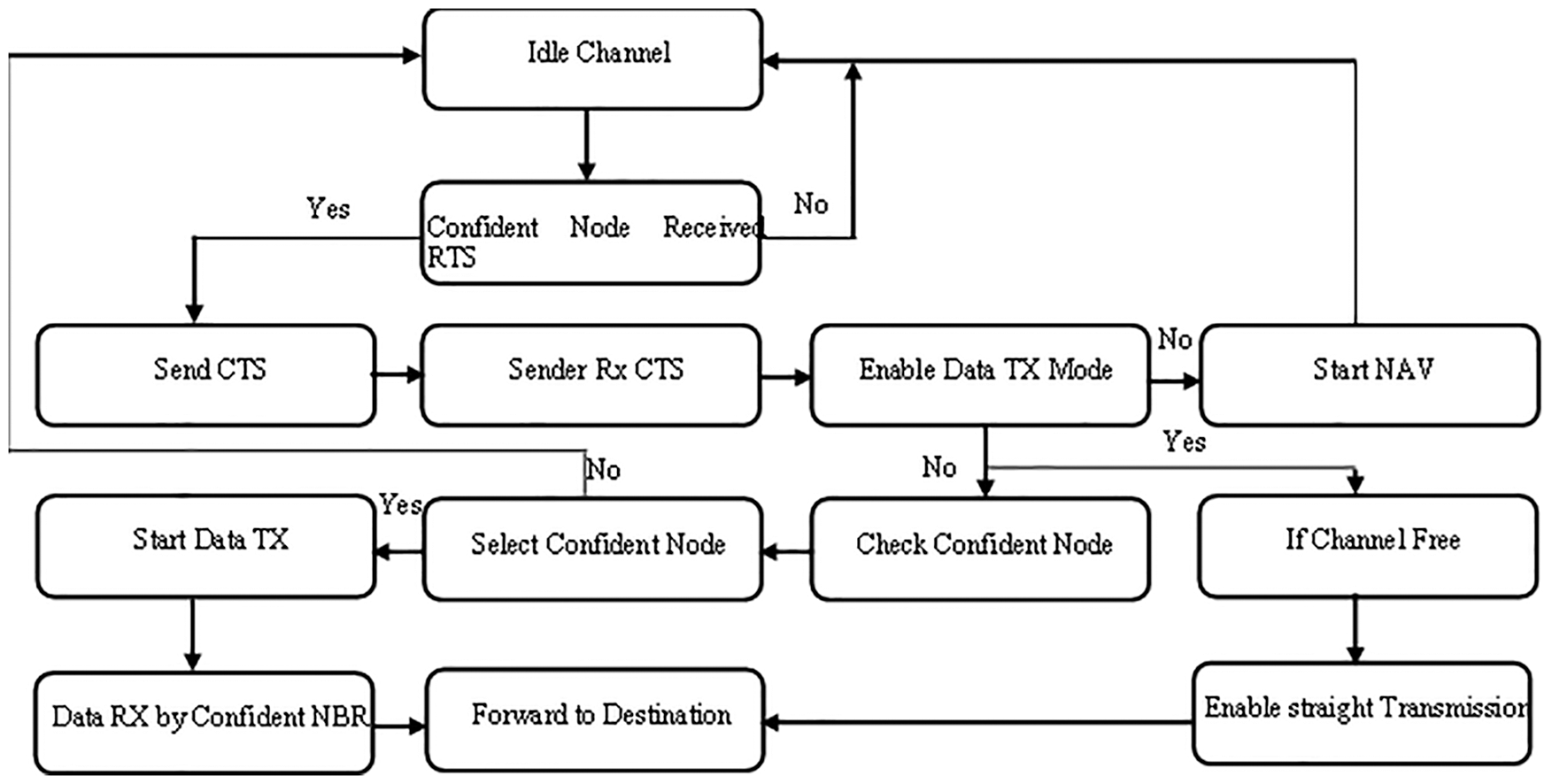
Figure 5: Communication at MAC layer
Even after the waiting period if the node is unable to get the channel confirmation, it cancels the previous request and initiates the new one as a timeout of
In cooperative transmission period, the optimal
Then the confident node
and the confident node connection
Then, the waiting period for the
Then, the time takes for the data packets to reach the
After receiving the
If another transaction occurs within that transmission region at the same time, the joint exchange is initiated by updating
If the frame transmission delay is less than the
Transmission power parameter is computed as ratio between the straight connection power
Here
beta is set to ensure timely selection of the forwarder. Based on the estimated optimal transmission power, the forwarder power strong helping node for the current transmission is calculated as
Network size is tested as 1000 × 1000 within an area in this experiment. As well as making changes to protocol routing and the mac layers and testing the performance of those changes in graphs format as given below Tab. 1. This protocol tells the best way to select a reliable forwarder and select the appropriate channel for the packets as they go through the network at regular intervals, here we see their test results.
Packet delivery ratio is the percentage of packets conventional at the destination depending on the number of packets shipped. Here, the CRCN protocol has received more packets at the destination. This Fig. 6 shows that this is achieved by the neighbor’s reliable selection module and by changing the channel selection method on the mac layer. By adding the largest number of packets to the destination, the designed CRCN protocol can see to it that the data packets are delivered to the destination in the correct manner. Here, we give the packet size as input and see the output of the resulting changes. By comparing between two techniques, the proposed method reaches the better Packet Size vs. Packet Delivery Ratio results.
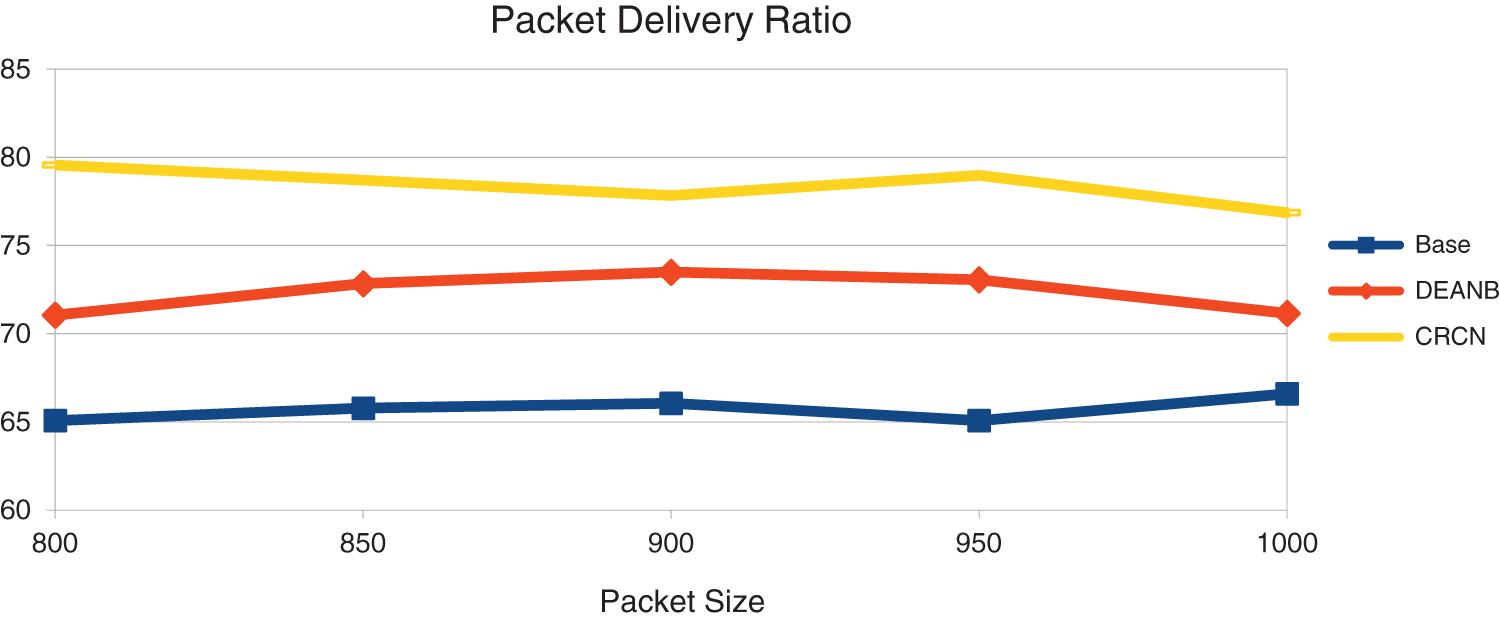
Figure 6: Packet size vs. packet delivery ratio
Throughput is the bits count of packets going to the destination. If the destination has received too many bits, we can know that the network is performing better. Here we can see that the CRCN protocol has received more packets than the compared others as shown in Fig. 7. This is an expression of the secured network and the network transmission is increased by selecting the proper node as the forwarder by the reports of the neighboring nodes and the reports of the nodes around it. And, by easily selecting the channel between them, more packet bits are delivered.
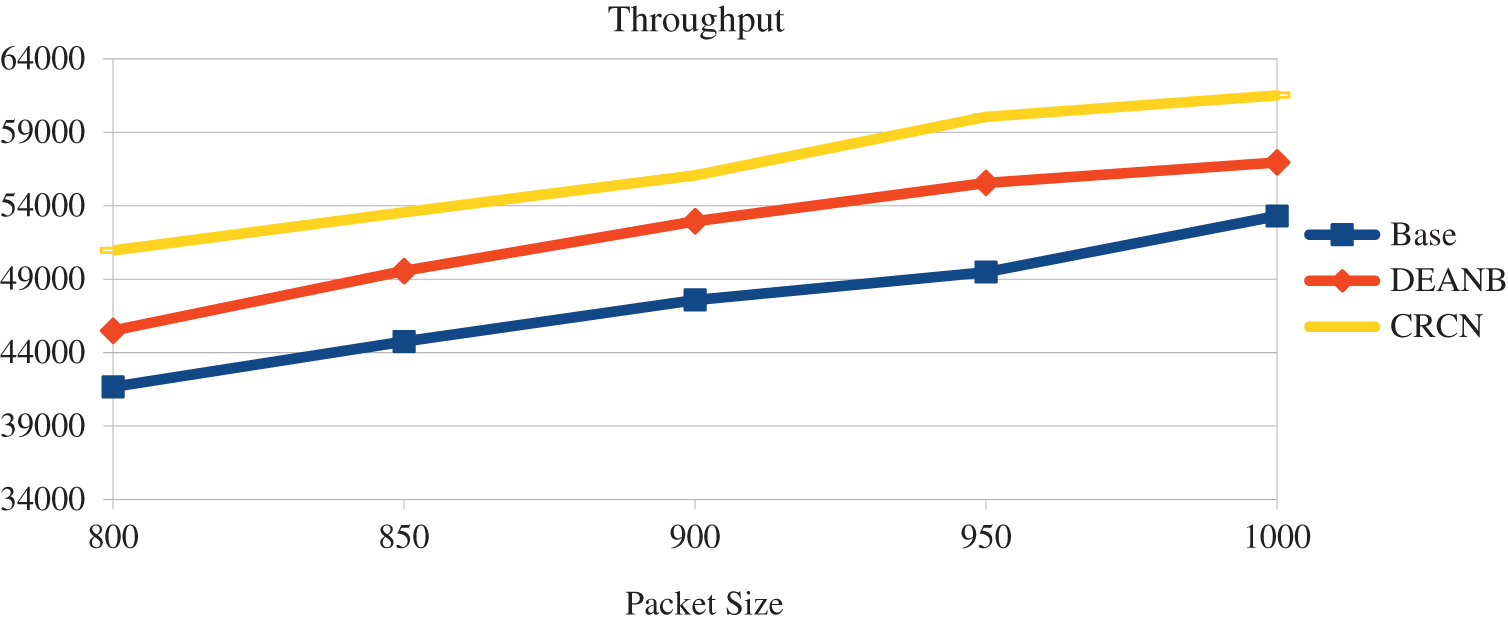
Figure 7: Packet size vs. throughput
This is an expression of the secured network, and the network transmission is increased by selecting the proper node as the forwarder by the reports of the neighbors and the reports of the second level nodes. And, by easily selecting the channel between them, more packet bits are delivered. Also, the reliability of the node is a factor, so in this proposed CRCN protocol, the reliability of the node and their channel selection act as an important parameter. By comparing between two techniques, the proposed method reaches the better packet transmission range vs. delay results. The Fig. 8 shows that its functions are very good.
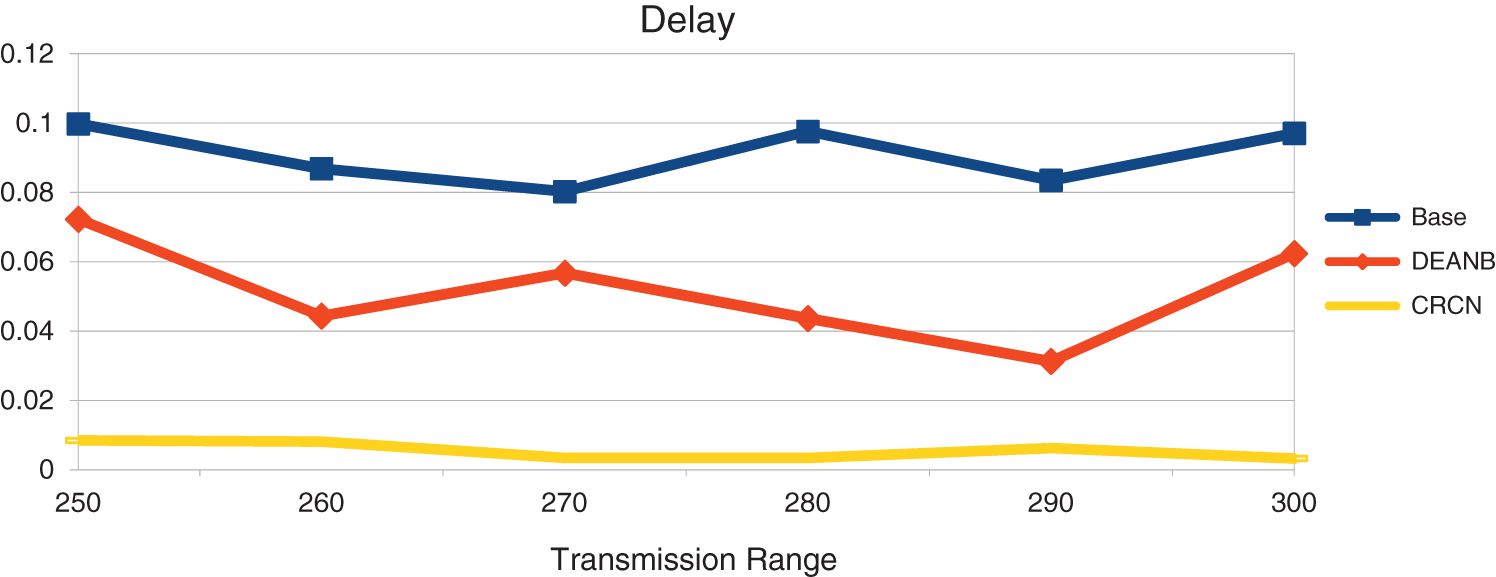
Figure 8: Transmission range vs. delay
Energy plays an important role in this. Network energy management is done with initial energy, remaining energy, packet transmission power, receiving power, so energy is also calculated as an important parameter when selecting the confident node. The Fig. 9 shows that the amount of energy stored in the network has increased due to this. Energy will be depleted very fast by unreliable nodes and that issue is solved here. Also, packets may expire if the correct channel is not set. The same issue is solved here. Due to this, the remaining energy in CRCN has increased.
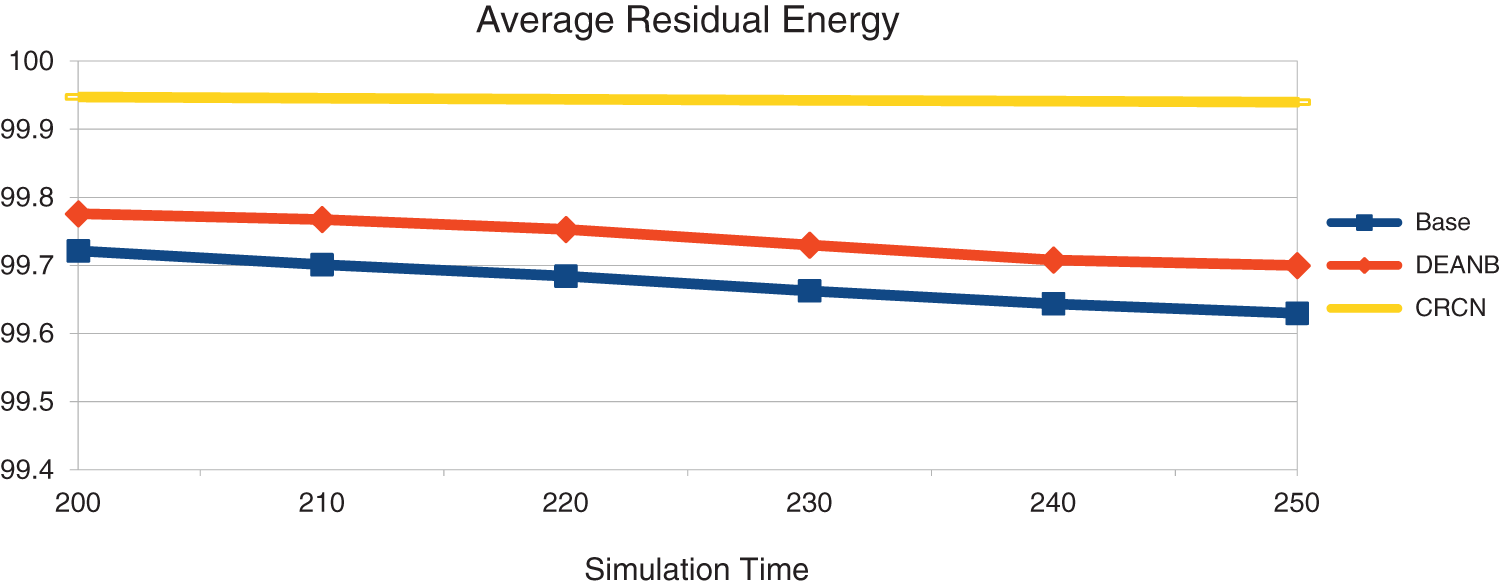
Figure 9: Simulation time vs. remaining energy
In this study, the steps show how the node acts as a confident forwarder and shares the channel in a way that is compatible with communication. We calculate the confidence of the node at the start of the network with the reliability report of the one hop and the reliability report of the secondary hop report. We figure out the combined confidence and use the same node as the most confident node as a forwarder, so we can move things along faster. When the routing packets sent to find the path reach the MAC layer, the next node in the path can be contacted directly if the channel is not used by any other nodes, and the channel is chosen. There will be no way to connect the channel unless there is a node that is sure. Then the path will be set. In this experiment, the amount of energy that is stored in the network is more than before. The nodes that aren’t reliable will use up a lot of energy very quickly, but that problem has been solved here. Even if the right channel is set, packets may not last long if they don’t reach the right person. The same thing has been solved here. Because of this, the amount of energy left in CRCN has gone up. When a node is confident, it chooses the best channel and the path is set up so that the network performance can be better than with the other protocols. To make the network work better, we can use this network security to let us use cognitive based channel selection and scheduling.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. R. H. Jhaveri Patel, N. M. Zhong and Y. Sangaiah, “Sensitivity analysis of an attack-pattern discovery based trusted routing scheme for mobile ad-hoc networks in industrial IoT,” IEEE Access, vol. 5, no. 6, pp. 20085–20103, 2018. [Google Scholar]
2. J. A. Anser, G. Han and H. Wang, “A novel reliable adaptive beacon time synchronization algorithm for large-scale vehicular ad hoc networks,IEEE,” Transactions on Vehicular Technology, vol. 8, no. 68, pp. 11565–11576, 2019. [Google Scholar]
3. C. F. Wang, Y. P. Chiou and G. H. Liaw, “Nexthop selection mechanism for nodes with heterogeneous transmission range in VANETs,” Computer Communications, vol. 1, no. 55, pp. 22–31, 2015. [Google Scholar]
4. W. Y. Lim, N. C. Luong, D. T. Hoang, Y. Jiao, Y. C. Liang et al., “Federated learning in mobile edge networks: A comprehensive survey,” IEEE Communications Surveys & Tutorials, vol. 8, no. 22, pp. 2031–2063, 2019. [Google Scholar]
5. Z. Lidong and Z. J. Haas, “Securing ad hoc networks,” IEEE Network, vol. 13, no. 6, pp. 24–30, 1999. [Google Scholar]
6. M. Haenggi, “Routing in ad hoc networks – a wireless perspective,” in First Int. Conf. on Broadband Networks, DC, USA, pp. 652–660, 2004. [Google Scholar]
7. V. Karpijoki, “Security in ad hoc networks,” in Proc. of the Helsinki University of Technology, Seminars on Network Security, Helsinki, Finland, pp. 1–14, 2000. [Google Scholar]
8. N. Krishnaraj and S. Sangeetha, “A study of data privacy in internet of things using privacy preserving techniques with its management,” International Journal of Engineering Trends and Technology, vol. 70, no. 2, pp. 43–52, 2022. [Google Scholar]
9. C. Yu, B. Lee and Y. H. Yong, “Energy efficient routing protocols for mobile ad hoc networks,” Wireless Communications and Mobile Computing, vol. 3, pp. 959–973, 2003. [Google Scholar]
10. S. Kulkarni, S. Ambaji and G. Raghavendra Rao, “A performance analysis of energy efficient routing in mobile ad hoc network,” International Journal of Simulations–Systems, Science and Technology–IJSSST, vol. 10, no. 1–A, pp. 1–9, 2010. [Google Scholar]
11. Y. Xu, H. Johnand and E. Deborah, “Geography-informed energy conservation for ad hoc routing,” in Proc. of the 7th Annual Int. Conf. on Mobile Computing and Networking, Rome, Italy, pp. 70–84, 2001. [Google Scholar]
12. A. Spyropoulos and C. S. Raghavendra, “Energy efficient communications in ad hoc networks using directional antennas,” in Proc. Twenty-First Annual Joint Conf. of the IEEE Computer and Communications Societies, BC, Canada, vol. 1, pp. 220–228, 2002. [Google Scholar]
13. M. V. S. S. Nagendranth, M. R. Khanna, N. Krishnaraj, M. Y. Sikkandar, M. A. Aboamer et al., “Type II fuzzy-based clustering with improved ant colony optimization-based routing (T2FCATR) protocol for secured data transmission in manet,” The Journal of Supercomputing, vol. First Online, pp. 1–22, 2022. [Google Scholar]
14. R. Zheng and R. Kravets, “On-demand power management for ad hoc networks,” in Proc. IEEE INFOCOM 2003. Twenty-second Annual Joint Conf. of the IEEE Computer and Communications Societies, BC, Canada, vol. 1, pp. 481–491, 2003. [Google Scholar]
15. T. Vaiyapuri, V. S. Parvathy, V. Manikandan, N. Krishnaraj, D. Gupta et al., “A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for IoT based mobile edge computing,” Wireless Personal Communications, vol. First Online, pp. 1–24, 2021. [Google Scholar]
16. G. Priyanka, V. Parmar and R. Rishi, “Manet: Vulnerabilities, challenges, attacks, application,” IJCEM International Journal of Computational Engineering & Management, vol. 11, no. 1, pp. 32–37, 2011. [Google Scholar]
17. P. Rajamohan and W. C. Kong, “Performance analysis and special security issues of secure routing protocols in ad-hoc networks,” International Journal of Scientific Engineering and Technology, vol. 3, no. 8, pp. 1094–1099, 2014. [Google Scholar]
18. A. Waqas, H. Mahmood and N. Saeed, “Interference aware cooperative routing for edge computing-enabled 5G networks,” IEEE Sensors Journal, vol. 12, no. 5, pp. 325–336, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools