 Open Access
Open Access
ARTICLE
Cluster Head Selection and Multipath Routing Based Energy Efficient Wireless Sensor Network
1 Department of Information Technology, SNS College of Technology, Coimbatore, 641035, India
2 Department of Computer Science and Engineering, Kongu Engineering College, Erode, 638060, India
* Corresponding Author: T. Shanmugapriya. Email:
Intelligent Automation & Soft Computing 2023, 36(1), 879-894. https://doi.org/10.32604/iasc.2023.032074
Received 05 May 2022; Accepted 29 June 2022; Issue published 29 September 2022
Abstract
The Wireless Sensor Network (WSN) is a network of Sensor Nodes (SN) which adopt radio signals for communication amongst themselves. There is an increase in the prominence of WSN adaptability to emerging applications like the Internet of Things (IoT) and Cyber-Physical Systems (CPS). Data security, detection of faults, management of energy, collection and distribution of data, network protocol, network coverage, mobility of nodes, and network heterogeneity are some of the issues confronted by WSNs. There is not much published information on issues related to node mobility and management of energy at the time of aggregation of data. Towards the goal of boosting the mobility-based WSNs’ network performance and energy, data aggregation protocols such as the presently-used Mobility Low-Energy Adaptive Clustering Hierarchy (LEACH-M) and Energy Efficient Heterogeneous Clustered (EEHC) scheme have been examined in this work. A novel Artificial Bee Colony (ABC) algorithm is proposed in this work for effective election of CHs and multipath routing in WSNs so as to enable effective data transfer to the Base Station (BS) with least energy utilization. There is avoidance of the local optima problem at the time of solution space search in this proposed technique. Experimentations have been conducted on a large WSN network that has issues with mobility of nodes.Keywords
As data gathering networks, Wireless Sensor Networks (WSNs) constitute dense distribution of nodes which are able to reliably monitor from long distances. Connectivity, computation, signal processing, and sensing are supported by the WSN’s Sensor Nodes (SNs). Within a specific environment, events can be observed and reacted to by an administrator with the aid of SNs. Limited resource devices like power and processing units are the SNs’ key weakness. The SNs’ singular attributes and constraints put forward numerous obstacles like time synchronization, network security, node localization, routing, and clustering. The key issues related to WSN design [1] comprise of effective transmission of data, integral security, effectivity of energy, as well as lengthier longevity of system. There is SN deployment in areas where it is impossible to either recharge or replace a battery for applications like the domains of military and surveillance. A network’s total performance and coverage properties can be badly affected by a single node’s failure. For these kinds of practical WSNs, it is essential to maintain the coverage properties for longer time periods. Either the entire or a part of the sensed information is aggregated prior to being transmitted by the WSNs to the Base Station (BS). Limited lifespan as a result of low battery backup is the WSN’s intrinsic shortcoming. Therefore, the development of energy efficient communication along with low-cost on-node processing and self-organizing connectivity is the primary issue that is the focus of research. For systems [2] with constrained energy, long operating horizons are primarily ensured with low power usage. In WSNs, for fault and intrusion tolerance to boost delivery of data, an efficient mechanism is multipath routing. Its fundamental idea is that with more paths involved in the delivery of data, there will be increase in the probability of at least one path arriving at the sink node or the BS. Majority of the prior research used to address multipath routing usage for the improvement of reliability. There were also a few researches that focussed on the toleration of insider attacks with multipath routing usage. But, these researches used to primarily ignore the trade-off between Quality of Service (QoS) gain vs. energy consumption that could severely decrease the lifespan of the system [3]. For WSNs, an energy effective methodology is the clustering of nodes. There is grouping of the nodes in this methodology for cluster formation. There is at least a single Cluster Head (CH) per cluster. The nodes utilize either single or multi-hop communication for delivery of data to their associated CH rather than direct delivery to the BS. All the data from the clusters are gathered and aggregated by the CH. Aggregation process helps in data minimization and results in energy conservation in the CHs. After this, the aggregated data is sent via either single or multi-hop communication to the BS by the CH. There is re-clustering of the nodes once a particular certain period of time (round time) has lapsed. Long distance communication of nodes to the BS can be avoided with node clustering. In fact, aids in the SNs’ energy conservation as just some like the CHs participate in long distance data delivery. For intra-cluster communication, the clustering methodology uses the TDMA scheduling method. There is allocation of slots to the nodes for data delivery. Energy conservation is accomplished by the nodes by transition to sleep state for other nodes’ slots and also by avoiding overhearing and idle listening [4]. The nodes can circumvent collisions by data delivery only in the allocated slots. Even more nodal energy conservation is achieved through avoidance of overhearing, idle listening as well as collisions.
Insertion of a percentage of heterogeneous nodes is yet another method of prologation of WSN lifespan. SNs with diverse abilities like distinct sensing range and computing power are the constituents of heterogeneous WSN. As these WSNs are more closer to real life situations, they are extremely advantageous in real deployments. Clustering methodologies are of two types: (i) Homogeneous clustering scheme–refers to the technique of clustering applied in homogeneous sensor networks; and (ii) Heterogeneous clustering scheme–refers to the technique of clustering applied in heterogeneous sensor networks. Majority of the presently-used clustering approaches like the LEACH take into account homogeneous sensor networks in which similar battery energy is considered for the design of all the SNs. Upon application to heterogeneous WSN, there is inefficient performance of the homogeneous WSNs’ energy saving schemes. Due to this, the heterogeneous WSNs’ [5] attributes must be taken into account for the design of energy efficient clustering protocols. The following properties must be fulfilled by the heterogeneous routing protocols: (i) Energy Consumption Balance. During initial network deployment, there is diversity in the network’s nodal energies. Battery changing for the nodes is very difficult and may even be near impossible in certain scenarios due to the constrained energy resource as well as huge number of deployed SNs. Afterwards, the network will be deployed with certain nodes having more energy that serves as the data aggregation’s centre. This in turn, aids in the balancing of the entire network. (ii) Communication Coordination. Node deployment with diverse communication radii is at times essential because of the unfavourability of communication environments in certain sensing areas. (iii) Effectivity in Computation and Storage. There is extreme limitation of a SN’s computational and storage ability. As certain protocols have the nodes frequently serving as the aggregation and relay nodes, in comparison to other nodes, there is a necessity for these nodes to have better computational and storage abilities so as to fulfil this need [6]. Numerous shortcomings of the presently-used clustering algorithm involve: unbalanced node lifespan [7], additional nodal overheads as well as energy coverage, poor awareness to the residual energy nodes, complexity management in large-scale WSNs, information transmission delays, nodal deaths, poor stability, lack of adaptivity to the heterogeneous network, high energy usage, and low network longevity. Various researchers have propounded research strategies which exploit certain metaheuristic techniques were utilized for the homogeneous networks’ CH election optimization. For heterogeneous WSNs, nodes utilize certain tactical amendments in the threshold-based formula for the accomplishment of the election of CHs. Minimization of energy utilization is the goal for CH election’s optimization technique. The optimized CH election towards most energy efficient routing is regarded as a Non-deterministic Polynomial-time hard (NP-hard) problem. Certain metaheuristic techniques incorporate certain primary factors for CH election in the fitness function [8] construction process for CH election optimization. During this, the application of metaheuristic techniques to the grounds of its characteristics will aid in optimal solution convergence. As of now, there has been development of a multitude of optimization routing strategies for CH election optimization in order to assure the network’s reliability at the time of transfer of data. For CH determination, researchers have exploited numerous metaheuristic algorithms like the Genetic Algorithm (GA), the Ant Colony Optimization (ACO), the Particle Swarm Optimization (PSO), and so on. Despite that, these metaheuristic algorithms still need extra enhancement on the energy stabilization and the efficiency for maximizing the network’s durability. This work has proposed an ABC algorithm variation for optimal CH election such that WSNs can achieve delay-less routing as well as energy efficiency. The following sections provide the organization of the investigation’s remaining portion. Discussion of the associated literary works is given in Section 2. Explanation for the various techniques utilized in this work is given in Section 3. Results of the experimentation are given in Section 4. Eventually, this work’s conclusion is given in Section 5.
The entire network was fragmented into clusters during the process of clustering. A CH was chosen by each cluster to serve as a head at the time of process of communication. However, there was rapid energy loss in the CHs because of their higher responsibility. Due to this, the effective election of CHs is a very critical task. Rajpoot et al. [9] had grouped the sensors into clusters via energy-efficient heterogeneous clustering. Three metrics were utilized for CH election: (a) delay as a function of the residual energy of nodes, transmission power, and so on; (b) distance between the nodes and their corresponding CH; and (c) distance between the CHs and the BS. For reduction of the energy usage, there was addition of the re-cluster phase for WSN restructuring. It is demonstrated from the results of the simulation that the proposed algorithm could surpass the performance of the base algorithm as well as the LEACH algorithm. Only a single pheromone, that is, the minimum distance between the SNs for optimum route discovery to the BS, was employed in the conventional Ant Colony Optimization (ACO) incorporated WSNs. A Multiple Pheromone-based ACO (MPACO) was suggested by Arora et al. [10] to take into consideration other metrics like the distance between sensing nodes, their residual energy as well as the number of neighbour nodes for efficient route ascertainment. SNs are enabled by the MPACO for sensing data delivery to the BS over optimal routes with effective energy consumption so as to accomplish an extended lifetime of network. In comparison to the presently-used improved ACO technique, the MPACO demonstrates 20% more network longevity based on comprehensive evaluation. Furthermore, in comparison to other current fuzzy-based strategy like the multi-objective fuzzy clustering algorithm, MPACO demonstrated 300% of substantial improvement with regards to the longevity. Mobile sinks aid in the accomplishment of uniform energy utilization as well as load-balancing in the WSNs. The mobile sink should visit certain points in the sensors field. Optimal election of these points, also known as rendezvous points, is a NP-hard problem. As hierarchical algorithms depend only on their local information for the selection of these points, there is a low probability of choosing an optimal node as a rendezvous point. A novel technique known as the Particle Swarm Optimization Based Selection (PSOBS) was suggested by Tabibi et al. [11] for the election of optimal rendezvous points so as to address the above mentioned issue. With PSO application, the proposed technique has the ability to discover near-optimal or optimal rendezvous points for the network resources’ effective management. There is also evaluation of a weight value in the proposed technique for each SN depending on the number of data packets received from other SNs. Certain metrics of performance like hop count, number of number of rendezvous points, energy consumption, and throughput were considered for the comparison of the proposed approach against the Weighted Rendezvous Planning Based Selection (WRPBS) algorithm. A Secure Cluster-Based Routing Protocol (SCBRP) was proposed by Pavani et al. [12] which employed an adaptive PSO with optimized Firefly Algorithms (FA) during transfer of data in the WSN. The work’s aim was to boost the entire network’s lifespan by minimization of an individual node’s energy utilization. Hexagonal sensor network architecture forms the basis of the proposed SCBRP. Energy-efficient clustering, secure routing, as well as security verification are the three processes which constitutes its design. Network Simulator (NS)-3 was utilized for assessment of the proposed SCBRP’s performance. Network longevity, rate of packet drop, energy utilization, decryption time, and encryption time are some of the factors utilized during the assessment. In comparison with the earlier techniques, the outcomes of the simulations demonstrated the superior performance of the proposed SCBRP. An application of Water Cycle Algorithm (WCA) on the LEACH protocol in WSNs (which is a clustering hierarchy protocol) was presented by Gambhir et al. [13]. Observation of the flow of streams and rivers to the sea influenced the proposal of the WCA. The cost of determination of the best node as the CH is gradually minimized by the WCA. The network longevity could be sustained by this novel energy-efficient clustering mechanism. Simulations were conducted to evaluate the WCA’s performance analysis and the proposed mechanism’s potency was demonstrated through the use of a range of performances measures.
To increase the network lifespan, the primary WSN resource is energy. Even though a myriad of studies have been conducted in this field, there is still a need to improve the collection of energy-efficient data. An effective approach known as the Chaotic Whale Metaheuristic Energy Optimized Data Gathering (CWMEODG) was propounded by Sridhar et al. [14] so as to modify the data collection process with the least consumption of energy. To this technique’s parameters, there is application of a mathematical model known as the Chaotic tent map so as to detect the global optimum solution as well as achieve quick rate of convergence. It is demonstrated from the outcomes that, in comparison to other advanced techniques, the CWMEODG technique enhances the data gathering and network lifespan with minimum packet loss and minimum delay. As a potential strategy for the assurance of substantial formation of clusters and its management, an Improved Bkd-Tree-Inspired Energy-eFficient Clustering-based Routing Protocol (IBkd-Tree-IEFCRP) was put forward by Janakiraman [15]. This is an efficient strategy for the assignation of CH nodes which manage the Quality of Service’s (QoS) effect at the time of the data dissemination process. The purpose of this strategy was to handle the conservation of energy saving in terms of the data traffic through inclusion of a cluster formation scheme that had the incorporation of partition data structure’s advantages along with an improved Bkd-tree algorithm. The strategy also focusses on the CH election procedure through integration of a reactive approach which boosts the throughput with minimized jitter, delay, and energy. In comparison to other standard protocols, for different number of rounds, the proposed IBkd-Tree-IEFCRP was found to increase the throughput by 6.84%, decrease the jitter by 7.18%, and also minimize the delay by 8.42%.
For enhancing the optimization of the network lifespan, Zivkovic et al. [16] proffered the application of an improved version of the Grey Wolf Algorithm. This algorithm was utilized during the processes of cluster formation as well as election of CHs. For this research, comparisons with the conventional LEACH algorithm, Basic Grey Wolf approach as well as the PSO were drawn by testing under similar conditions of experimentations to assess the proposed exploration enhanced Grey Wolf Algorithm’s performance. The outcomes of these simulations have verified the superior performance of the proposed metaheuristic.Adaptive Buffering with Fuzzy-based Multilevel Clustering (ABFMC) was employed by Shankar et al. [17] for CH selection amongst the region cluster members. An unique number of buffer nodes is adopted by this proposed algorithm to empower the communication of all nodes with the BS. Election of transmission through the CH is used for decision making that is dependent on the distance factor. It is demonstrated from the outcomes of the simulations that the proposed ABFMC algorithm has the capability to offer efficient distribution of energy amongst the nodes as well as enhanced lifespan of network.
The proposal of an Adaptive Immune-inspired Energy-Efficient Cross-Layer routing (AIEECR) protocol was made by Yarde et al. [18] to boost the network performance. The physical layer, the transport layer, and the data link layer are the three layers which are taken into account for the transmission of data. There is utilization of the K-means approach for SN clustering. For each round, CHs are chosen depending on the value of threshold so as to minimize the usage of energy. Moreover, for coverage are enhancement and reduction of issues pertaining to coverage holes, there is application of the Adaptive Sunflower Optimization (ASFO). There is utilization of an artificial immune-based routing protocol for the election of an effective routing path for data transmission to the BS from each CH. The performance results of the proposed AIEECR-ASFO were revealed as well as compared with the other presently-used techniques such as the simple hybrid routing protocol, the QoS assured multi-objective hybrid routing algorithm, and the dynamic multi-objective routing algorithm.
There is discussions about the LEACH-Mobile, the EEHC, and the ABC-EEHC approaches in this section.
The LEACH’s operation is split into rounds, in which each round starts with a set-up phase where there is organization of the clusters, then a steady-state phase where there is transmission of data to the BS. The steady-state phase has long been compared against the set-up phase for minimization of the overheads. The LEACH-Mobile’s fundamental concept is to verify that the SNs are included in a specific cluster at the steady-state phase as the CH and that there is receipt of a certain message by the non-CH node at a time slot that is allocated as per the TDMA time schedule which each sensor cluster has, and to later rearrange the cluster with the elast amount of energy utilization.
3.1.1 Steady-State Phase in LEACH
There is division of the operation of the steady-state into frames. At the time of their assigned time slot, the nodes will transmit their data to the CH at least once per frame. When the data transfer occurs in the nodes, each slot’s duration is constant. Due to this, the time to transfer a frame of data is based on the cluster’s number of nodes. The assumption here is there is time synchronization of all the nodes and the set-up phase occurs at the same time [19]. The transmission of data can start after the clusters are formed and the TDMA schedule is set. Let the assumption be that the nodes will always have data to transmit, and this data is transferred to the CH during their assigned time of transmission. As each non-CH node’s radio can be switched off till the node’s assigned time of transmission, minimization of dissipation of energy in these nodes can be achieved. For receipt of all the data from the cluster’s nodes, the CH node should keep its receiver switched on. After this, signal processing functions are done by the CH node for the data’s compression into one signal. This is termed as the LEACH protocol’s steady-state operation. Once a specific time has lapsed, that is considered as a priori, there is the start of the next round with each node trying to determine if it must be this round’s CH as well as this information’s advertisement.
The hierarchical clustering protocol of LEACH comprises of the distributed cluster formation algorithm which enjoys benefits like high energy efficiency as well as dynamic self-organization of the cluster. However, this protocol does not assure the data transfer’s success in the WSN’s standard mobility-centric environment. There is cluster organization and CH election during the LEACH’s set-up phase. In the steady-state phase, the real transmission of data to the BS takes place. Even though the LEACH can maintain the cluster configuration during the steady state phase, it is not able to accommodate the mobile SNs’ cluster alteration. These kind of issues can be resolved by the utilization of the simple and conventional technique which adds the mobile nodes’ membership declaration to the standard LEACH protocol. The assumption in the proposed scheme is that, there must be data transfer to the CH by every non-CHs of the of the sensor network during their corresponding assigned time slots in the TDMA schedule. During the steady-state phase, the LEACH protocol’s CH will wait for the receipt of sensed data as per the TDMA schedule. However, the LEACH-Mobile’s [20] CH will transmit the request message for data transmission to the non-CH node for collecting the sensed data as per the TDMA schedule at each time slot. When the transfer of data occurs, the CH will verify with a time slot list of nodes if the sensed data has been received in accordance with the assigned TDMA time slot at every time, upon end of a frame ends, nodes are marked on the non-receipt list. If there is no receipt of the sensed data again from the node which was marked earlier when the next frame ends, the node will get removed by the CH and this time slot may get allocated the newly joined node in TDMA schedule. The assumption for the CH is that the nodes which do not reply to the data-request message are shifted and placed out of its cluster region. There will be rescheduling of the TDMA schedule and will then get transmitted to all the member nodes of the cluster.
The CH uses the data-request message to declare a node’s membership within its own cluster region. However, each mobile node has to confirm which cluster it will belong to. Upon organization of the clusters and election of the CHs, data is transferred to the CH by the non-CH nodes when the data-request message is received. Within the TDMA schedule-assigned time slot, if the data request message are is not received till the ending of the frame, the protocol operation’s procedure will proceed to the subsequent frame. If there is no receipt of the data-request message by the mobile node even when the next frame ends, it will broadcast a cluster join-request message. Upon receipt of this message, the CH will transmit CH advertisement message like that node’s set-up. Upon completion of this phase, the mobile node will determine which new cluster it will belong to for this round since there is movement of the mobile node. The advertisement message’sreceived signal strength forms the basis of this decision. When the mobile node has determined its cluster membership, it should inform the CH that it will be the cluster’s member. The newly joined mobile node’s CH will update the cluster membership list as well as the TDMA schedule, and later will broadcast the updated TDMA schedule to its corresponding cluster member nodes. The next frame’s updated schedule is used for the operation a cluster’s nodes inclusive of the newly joined mobile nodes. For the LEACH-Mobile protocol, there is increase in the transmitted message overheadsfor membership declaration and dynamic organization of the cluster with mobile nodes in every TDMA time slot in comparison to the standard LEACH protocol. The rate of transfer success of the sensed data which are collected from mobile nodes can be increased. The LEACH-Mobile is more appropriate for the WSN’s mobility-centric routing protocol since it declares the cluster membership for mobile SNs and dynamically arranges the hierarchical clustering without Global Positioning System (GPS) based location information and centralized routing table.
3.2 Energy Efficient Heterogeneous Clustered (EEHC) Scheme
The LEACH’s original version does not take into account the nodes’ heterogeneity with regards to their initial energy. So, in the presence of such heterogeneity, there is no optimization of the sensor network’s energy resource usage. This is because of the dependency of the LEACH only on the sensor network’s spatial density. There is utilization of LEACH in the presence of heterogeneity together with the assumption that there is uniform distribution of the normal, advanced, and super nodes in space. The expectation will be that the first node will die on average in a round that is near the round when the first node would die in the homogeneous case in which each node has the same energy as that of a heterogeneous case’s normal node. Moreover, there is an expectation that a normal node will be the first dead node. In the subsequent rounds, the expectation is that a normal node’s probability to die is much higher than that of a super and an advanced node. Only the super and advanced nodes would be left alive in the finals rounds. Outcomes of the simulations confirm these expectations. Suppose that there is a heterogeneous sensor network in a 100 m
Figure 1: A wireless sensor networks. (a) A snapshot of the network when all the nodes are alive and (b) snapshot of the network when some nodes are dead
This work introduces the novel heterogeneous-aware EEHC protocol [21] which has the objective of maximizing the stability as well as the lifespan of the network in the heterogeneous nodes’ presence. Take into consideration a case in which a percentage of the SN population has more energy resources in comparison to that of the network’s normal SNs. Suppose m is the representation of the fraction of the total number of nodes n, and mo is the representation of the percentage of the total number of nodes m that have
As a result, a factor of
There are almost
wherein, the predetermined percentage of CHs is denoted as
Eq. (3) for the LEACH protocol:
Here, the current round is denoted as r, the set of normal nodes which have not become CHs within the epoch’s last 1/pn rounds is denoted as G′, and the threshold which is applied to a population of n * (1 − m) normal nodes is denoted as T (sn). This will assure that each normal node will turn into a CH exactly once every
3.3 Proposed Artificial Bee Colony (ABC)-EEHC Algorithm
The bee’s natural behaviour of honey collection was the inspiration behind the ABC algorithm which is a type of swarm intelligence optimization algorithm. When comparisons are drawn with other intelligent algorithms like the PSO algorithm and the Genetic Algorithm (GA), the ABC algorithm has benefits like strong optimization capability, minimum number of set parameters, string robustness, and minimal complexity. The application of this algorithm include system and engineering design, training of Artificial Neural Networks, combination optimization, as well as various other fields.
Employed bee, onlooker bee, and scout bee are the three bee types in the conventional ABC algorithm [22]. The number of employed bees and onlooker bees generally remains equivalent and also account for the total bee colony’s half. Also, there is equivalence of the number of nectar sources to the number of employed bees and onlooker bees. An optimization problem’s potential solution is represented as the nectar source’s position whilst the value of fitness function (that is, the potential solution’s quality is represented as the amount of nectar from the food source. In the beginning, all the bees will be scout bees and there is random generation in the search space of the SN food source location as per Eq. (5):
In this equation, the food source i’s location is denoted as xi, the search space’s range is denoted as
In accordance with Eq. (6), each employed bee will search close to the existing nectar source for the generation of the location of a new food source:
In this equation, the new food source’s location is denoted as
In this equation, the ith solution’s value of fitness is denoted as fiti. Roulette is the term used for this technique of selecting an employed bee to follow. With this technique, it can be ascertained onlooker bees are more likely to follow those employed bees with large values of fitness. An employed bee i is picked by the onlooker bee to follow with a probability Pi. This bee will then become an employed bee and will carry out the employed bee’s related tasks.
During the search process, the food source is considered to be exhausted if the number of stay times of the onlooker and employed bees in the nectar source’s vicinity exceeds the Limit’s maximum limit, and a better food source has not been found. Then, the food source gets abandoned by the employed bees who in turn, will take up the roles of the scout bees. There will be random generation of a new food source in accordance with the above-mentioned Eq. (5).
As the WSNs’ total performance is affected by the election of CHs, this is a vital task for cluster formation. The responsibility of the CHs involves the gathering of data which arrives from the numerous SNs as well as the aggregated data’s transfer to the BS. An appropriate node’s election as a CH continues to be a multi-modal optimization problem that is a very arduous. As a result, for a clustering protocol with improved energy efficiency, an optimal CH election algorithm that is on the basis of the proposed ABC metaheuristic [23] has been proposed in this work. Below is the proposed algorithm’s methodology:
Initialization phase. There is initialization of the Population Number (PN), the associated food sources (SN), as well as control parameters such as the Crossover Rate (CR), the Maximum Cycle Number (MCN), and the control parameter
Fitness function derivation.
There is construction of a fitness function for evaluation of the fitness of the population’s individual food source. The proposed CH election algorithm has three goals to accomplish. At first, the node which is chosen as the CH must have the maximum residual energy as per Eq. (9):
The second goal is that the maximum distance between the CH-elected node and the BS must be minimized and also have minimum transmission power for aggregated data transmission from the CH to the BS as per Eq. (10):
Then, Eqs. (11) and (12) are used for the data aggregation as below:
wherein, the proportionality constant is denoted as K. If the value of K = 1,
As a result, the value of fitness for each solution of the population will be determined by Eq. (13).
Employed Bee Phase. Each employed bee will choose a new solution vij by utilizing the proposed ABC metaheuristic’s proposed improved search equation
There is comparison of the attained value of
Onlooker Bee Phase. By performing a waggle dance at their hive, information about the food sources of the employee bees is shared with the onlooker bee. Each employed bee generates a food source uij in accordance with the distribution given in Eq. (15):
In this equation, the crossover rate is denoted as CR. There is further assessment of the fitness of generated food source f (
wherein, the value of fitness of
Scout Bee Phase. When there is no further fitness improvement subsequent to a number of trials, the associated employed bee will turn into a scout for the random production of a new food source through the reusage of Eq. (8).
In this section, the LEACH-Mobile, EEHC and ABC-EEHC methods are used. Experiments are carried out using 500 to 3000 network size [24,25]. The average end to end delay, average Packet Delivery Ratio (PDR), average number of hops to sink and average remaining energy at network half-life as shown in Tabs. 1–4 and Figs. 2–5.
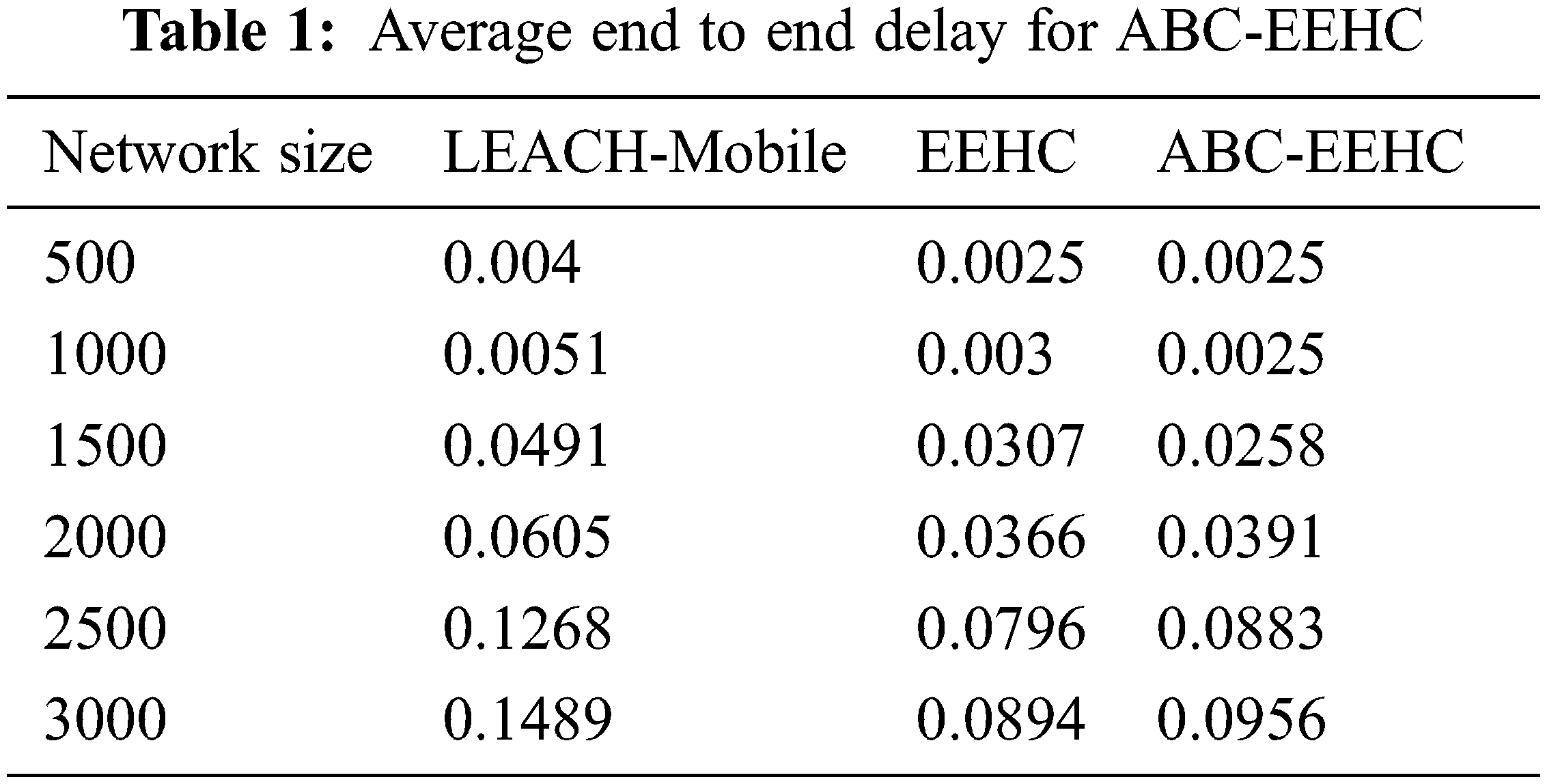
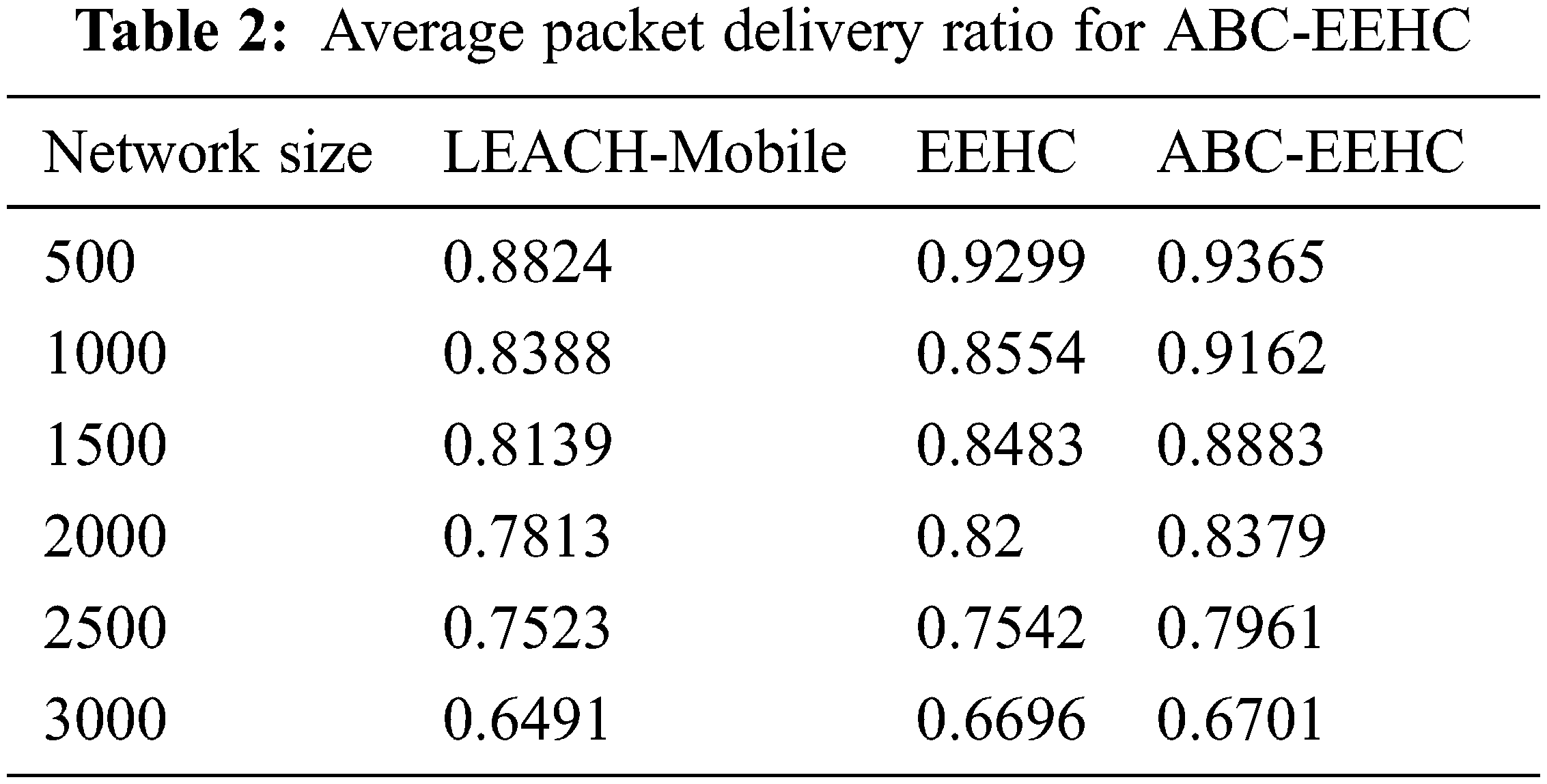
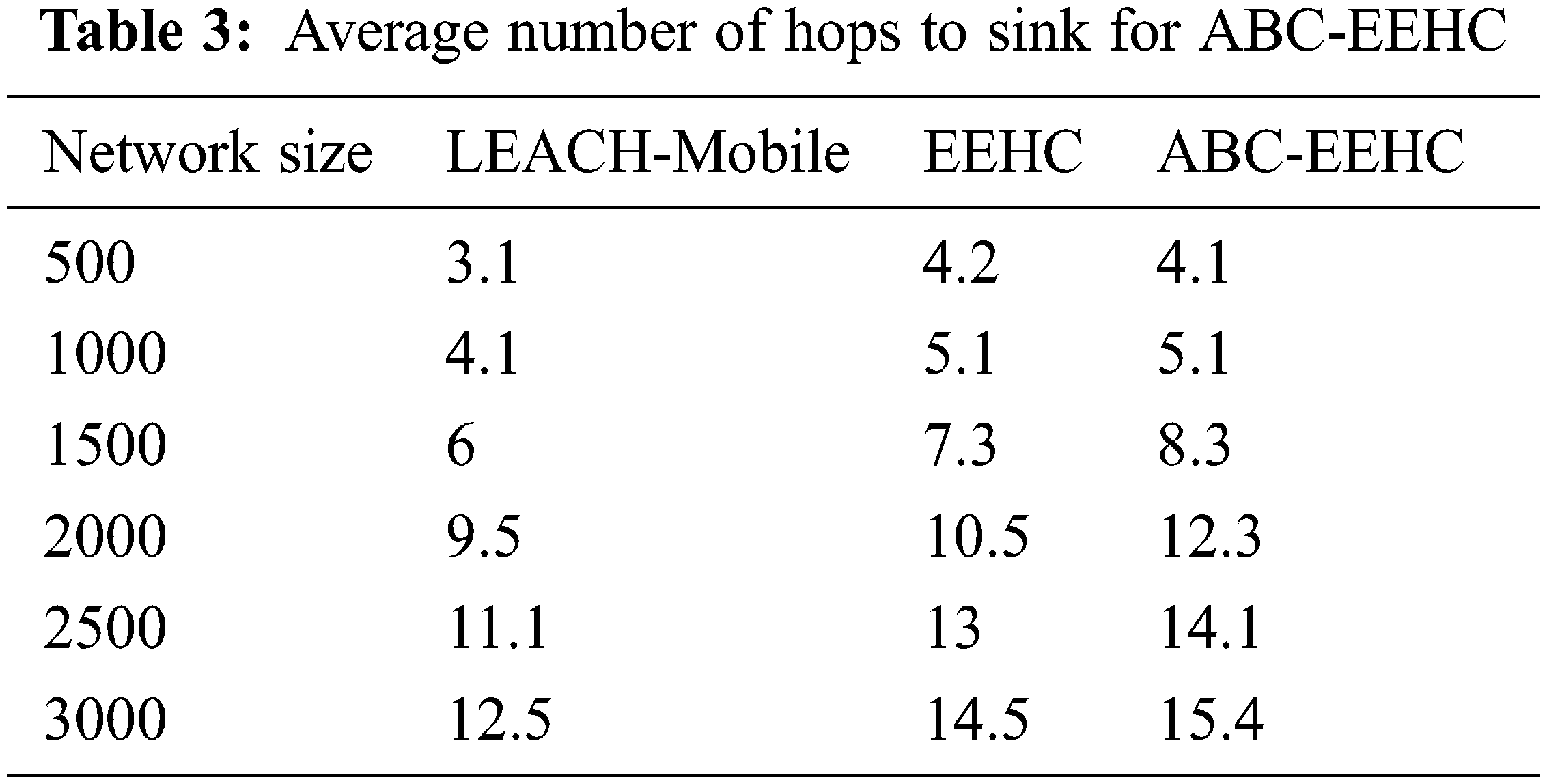
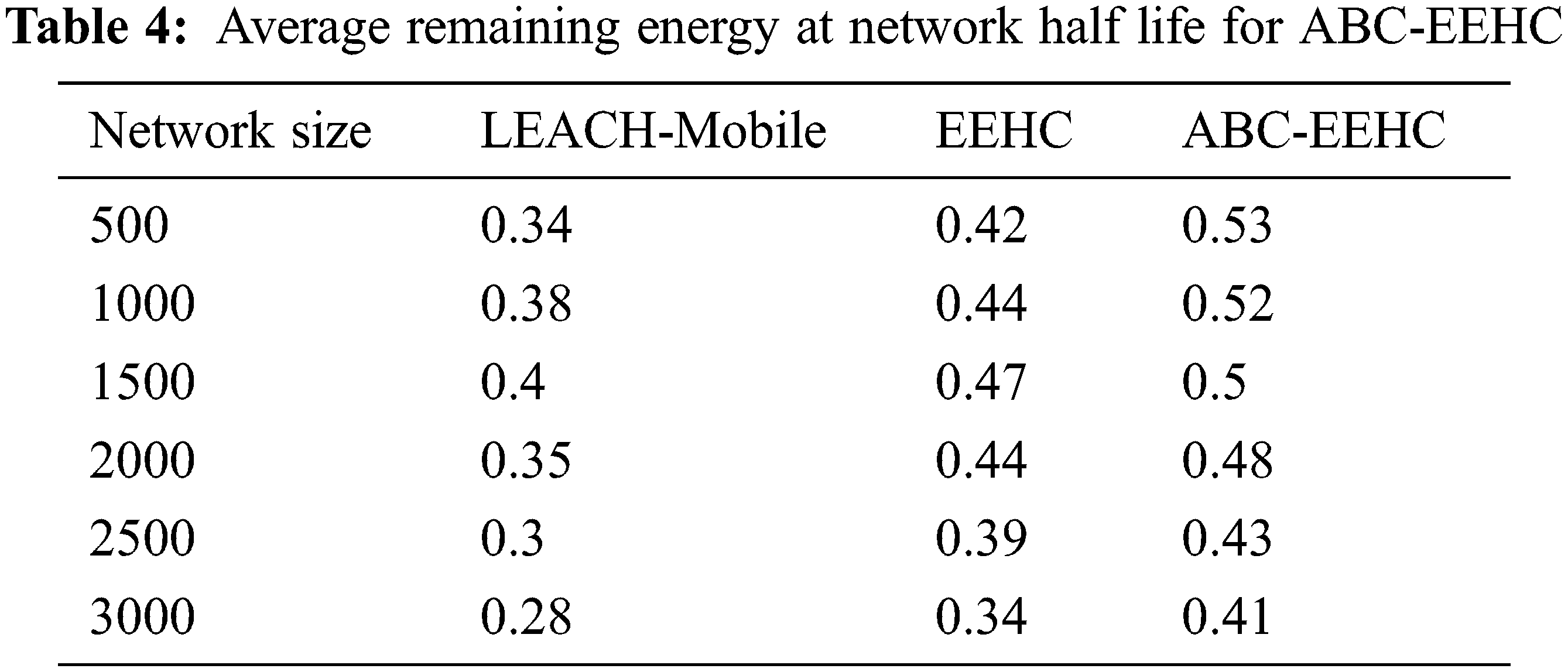
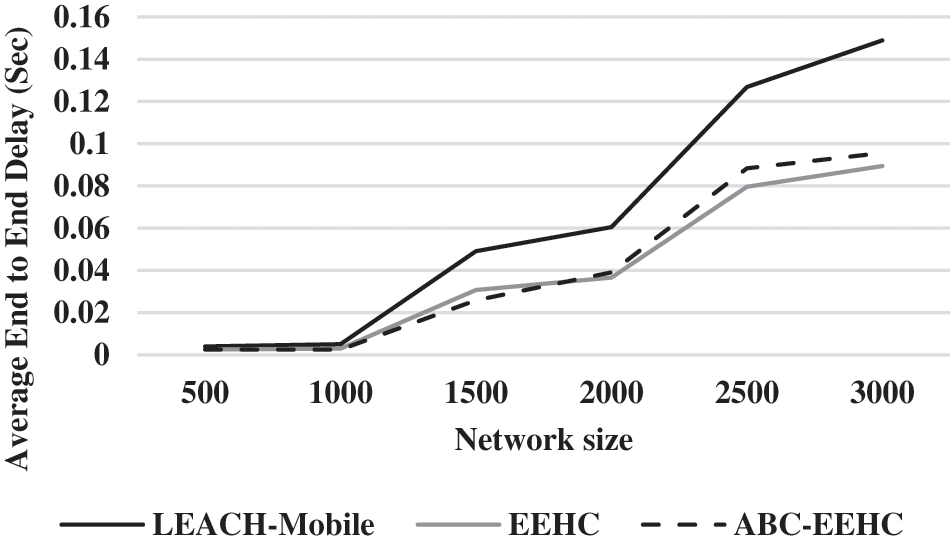
Figure 2: Average end to end delay for ABC-EEHC
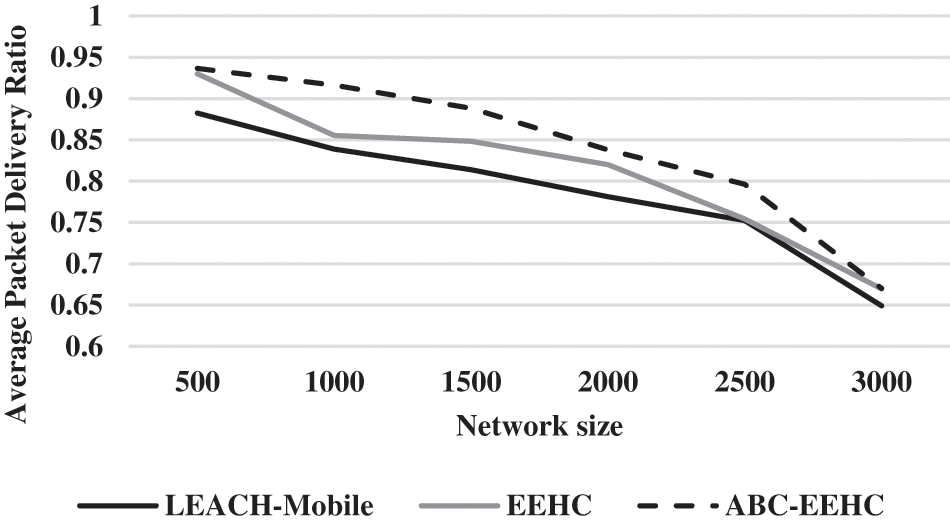
Figure 3: Average packet delivery ratio for ABC-EEHC
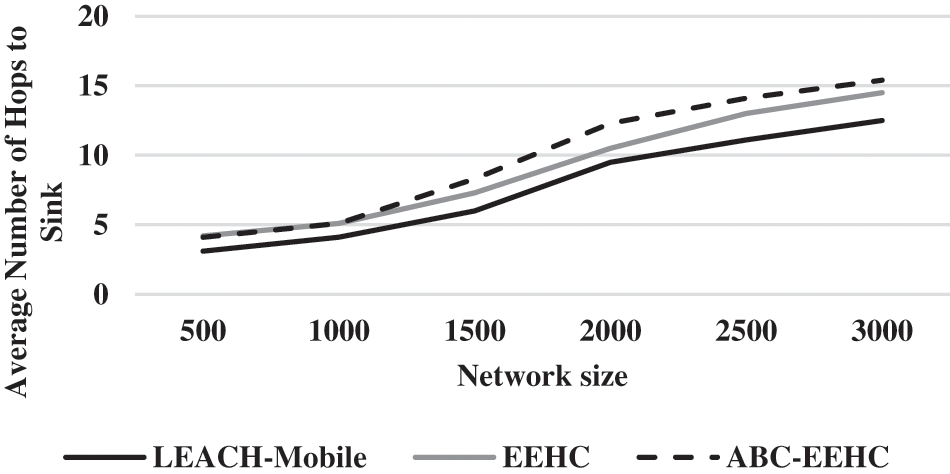
Figure 4: Average number of hops to sink for ABC-EEHC
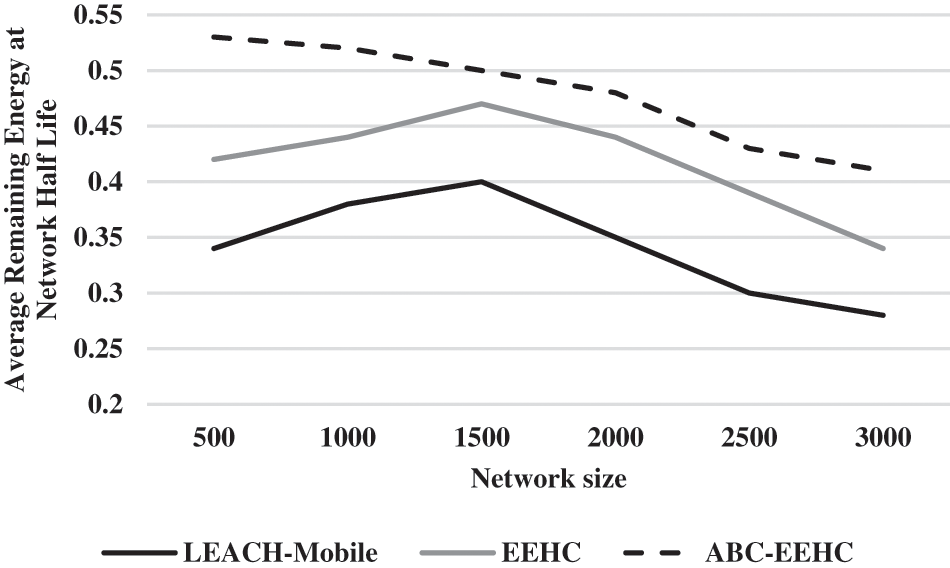
Figure 5: Average remaining energy at network half life for ABC-EEHC
From the Fig. 2, it can be observed that the ABC-EEHC has lower average end to end delay by 46.15% & no change for 500 network size, by 68.42% & 18.18% for 1000 network size, by 62.22% & 17.34% for 1500 network size, by 42.97% & 6.61% for 2000 network size, by 35.79% & 10.36% for 2500 network size and by 43.59% & 6.7% for 3000 network size when compared with LEACH-Mobile and EEHC respectively.
From the Fig. 3, it can be observed that the ABC-EEHC has higher average PDR by 5.95% & 0.71% for 500 network size, by 8.82% & 6.86% for 1000 network size, by 8.74% & 4.61% for 1500 network size, by 6.99% & 2.16% for 2000 network size, by 5.66% & 5.4% for 2500 network size and by 3.18% & 0.07% for 3000 network size when compared with LEACH-Mobile and EEHC respectively.
From the Fig. 4, it can be observed that the ABC-EEHC has higher average number of hops to sink by 27.78% & 2.41% for 500 network size, by 21.74% & no change for 1000 network size, by 32.17% & 12.82% for 1500 network size, by 25.69% & 15.79% for 2000 network size, by 23.81% & 8.12% for 2500 network size and by 20.79% & 6.02% for 3000 network size when compared with LEACH-Mobile and EEHC respectively.
From the Fig. 5, it can be observed that the ABC-EEHC has higher average remaining energy at network half-life by 43.68% & 23.16% for 500 network size, by 31.11% & 16.67% for 1000 network size, by 22.22% & 6.18% for 1500 network size, by 31.32% & 8.69% for 2000 network size, by 35.62% & 9.76% for 2500 network size and by 37.68% & 18.67% for 3000 network size when compared with LEACH-Mobile and EEHC respectively.
In Mobility, dynamic self-organization, and energy efficiency are accommodated in WSN designs in mobility-centric environments. In 'hot areas', WSN applications often have a mixture of fixed SNs along with mobile SNs. Moreover, with their movement, there must be reconstruction of the network topology through rapid reactions to the SNs’ mobility. An enhanced protocol known as the “LEACH-Mobile” was proposed in this work. In this protocol, the mobile nodes would have the ability to declare a cluster’s membership as they move as well as have the ability to verify if a mobile SN could communicate with a specific CH within an assigned time slot in the TDMA schedule. In comparison to the non-mobility centric LEACH protocol, the LEACH-Mobile protocol could accomplish a marked improvement in the rate of data transfer success with the increase of mobile nodes. An EEHC was introduced in this work for lifespan maximization through distributed election of CHs in the hierarchical WSNs. In a network, the CHs’ election probabilities are weighted by the initial energy of a node which is relative to that of other nodes. A food source will correspond to a possible solution of the optimization problem and the number of employed bees will be same as the number of food sources in the ABC metaheuristic. Moreover, this work has also proposed ABC-EEHC which is as an energy-efficient bee clustering protocol that relies on the proposed WSN metaheuristic for optimal CH election which is dependent on an efficient fitness function as well as an improved search equation. Moreover, there has been introduction of an optimal CH scheduling algorithm that aids in maintaining the nodes’ energy level balance. This in turn, boosts the lifespan of the network. Outcomes of the experimentations demonstrate the ABC-EEHC’s higher average PDR in comparison to the LEACH-Mobile by 5.95% for 500 network size, by 8.82% for 1000 network size, by 8.74% for 1500 network size, by 6.99% for 2000 network size, by 5.66% for 2500 network size, and by 3.18% for 3000 network size. Furthermore, in comparison to the EEHC, the ABC-EEHC demonstrates higher average PDRby 0.71% for 500 network size, by 6.86% for 1000 network size, by 4.61% for 1500 network size, by 2.16% for 2000 network size, by 5.4% for 2500 network size, and by 0.07% for 3000 network size.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. N. Mittal, U. Singh and B. S. Sohi, “A stable energy efficient clustering protocol for wireless sensor networks,” Wireless Networks, vol. 23, no. 6, pp. 1809–1821, 2017. [Google Scholar]
2. S. Arjunan and S. Pothula, “A survey on unequal clustering protocols in Wireless Sensor Networks,” Journal of King Saud University-Computer and Information Sciences, vol. 31, no. 3, pp. 304–317, 2019. [Google Scholar]
3. H. Al-Hamadi and R. Chen, “Redundancy management of multipath routing for intrusion tolerance in heterogeneous wireless sensor networks,” IEEE Transactions on Network and Service Management, vol. 10, no. 2, pp. 189–203, 2013. [Google Scholar]
4. V. Pal, G. Singh, R. P. Yadav and P. Pal, “Energy efficient clustering scheme for wireless sensor networks: A survey,” Journal of Wireless Networking and Communication, vol. 2, no. 6, pp. 168–174, 2012. [Google Scholar]
5. R. Sheikhpour, S. Jabbehdari and A. Khadem-Zadeh, “Comparison of energy efficient clustering protocols in heterogeneous wireless sensor networks,” International Journal of Advanced Science and Technology, vol. 36, pp. 27–40, 2011. [Google Scholar]
6. G. Han, X. Jiang, A. Qian, J. J. Rodrigues and L. Cheng, “A comparative study of routing protocols of heterogeneous wireless sensor networks,” The Scientific World Journal, vol. 2014, no. 4, pp. 1–11, 2014. [Google Scholar]
7. A. Sarkar and T. S. Murugan, “Cluster head selection for energy efficient and delay-less routing in wireless sensor network,” Wireless Networks, vol. 25, no. 1, pp. 303–320, 2019. [Google Scholar]
8. S. Verma, N. Sood and A. K. Sharma, “Genetic algorithm-based optimized cluster head selection for single and multiple data sinks in heterogeneous wireless sensor network,” Applied Soft Computing, vol. 85, pp. 105788, 2019. [Google Scholar]
9. P. Rajpoot, S. H. Singh, R. Verma, K. Dubey, S. K. Pandey et al., “Multi-factor-based energy-efficient clustering and routing algorithm for wsn,” in Proc. Soft Computing: Theories and Applications, Singapore, Springer, pp. 571–581, 2020. [Google Scholar]
10. V. K. Arora, V. Sharma and M. Sachdeva, “A multiple pheromone ant colony optimization scheme for energy-efficient wireless sensor networks,” Soft Computing, vol. 24, no. 1, pp. 543–553, 2020. [Google Scholar]
11. S. Tabibi and A. Ghaffari, “Energy-efficient routing mechanism for mobile sink in wireless sensor networks using particle swarm optimization algorithm,” Wireless Personal Communications, vol. 104, no. 1, pp. 199–216, 2019. [Google Scholar]
12. M. Pavani and P. T. Rao, “Adaptive PSO with optimised firefly algorithms for secure cluster-based routing in wireless sensor networks,” IET Wireless Sensor Systems, vol. 9, no. 5, pp. 274–283, 2019. [Google Scholar]
13. A. Gambhir, A. Payal and R. Arya, “Water cycle algorithm based optimized clustering protocol for wireless sensor network,” Journal of Interdisciplinary Mathematics, vol. 23, no. 2, pp. 367–377, 2020. [Google Scholar]
14. R. Sridhar and N. Guruprasad, “Energy efficient chaotic whale optimization technique for data gathering in wireless sensor network,” International Journal of Electrical and Computer Engineering, vol. 10, no. 4, pp. 4176, 2020. [Google Scholar]
15. S. Janakiraman, “An energy-proficient clustering-inspired routing protocol using improved bkd-tree for enhanced node stability and network lifetime in wireless sensor networks,” International Journal of Communication Systems, vol. 33, no. 16, pp. e4575, 2020. [Google Scholar]
16. M. Zivkovic, N. Bacanin, T. Zivkovic, I. Strumberger, E. Tuba et al., “Tuba etal, Enhanced grey wolf algorithm for energy efficient wireless sensor networks,” Proc. Zooming Innovation in Consumer Technologies Conference (ZINCIEEE, vol. 33, no. 16, pp. 87–92, 2020. [Google Scholar]
17. T. Shankar, A. Rajesh and R. Mageshvaran, “Adaptive buffering and fuzzy based multilevel clustering for energy efficient wireless sensor network,” Wireless Personal Communications, vol. 112, no. 1, pp. 1–18, 2020. [Google Scholar]
18. P. Yarde, S. Srivastava and K. Garg, “Adaptive immune-inspired energy-efficient and high coverage cross-layer routing protocol for wireless sensor networks,” IET Communications, vol. 14, no. 15, pp. 1–14, 2020. [Google Scholar]
19. A. Nayebi and H. Sarbazi-Azad, “Performance modeling of the LEACH protocol for mobile wireless sensor networks,” Journal of Parallel and Distributed Computing, vol. 71, no. 6, pp. 812–821, 2011. [Google Scholar]
20. D. S. Kim and Y. J. Chung, “Self-organization routing protocol supporting mobile nodes for wireless sensor network,” in Proc. First Int. Multi-Symp. on Computer and Computational Sciences (IMSCCS’06IEEE, Hangzhou, China, vol. 2, pp. 622–626, 2006. [Google Scholar]
21. D. Kumar, T. C. Aseri and R. Patel, “EEHC: Energy efficient heterogeneous clustered scheme for wireless sensor networks,” Computer Communications, vol. 32, no. 4, pp. 662–667, 2009. [Google Scholar]
22. Z. Wang, H. Ding, B. Li, L. Bao and Z. Yang, “An energy efficient routing protocol based on improved artificial bee colony algorithm for wireless sensor networks,” IEEE Access, vol. 8, pp. 133577–133596, 2020. [Google Scholar]
23. P. S. Mann and S. Singh, “Improved artificial bee colony metaheuristic for energy-efficient clustering in wireless sensor networks,” Artificial Intelligence Review, vol. 51, no. 3, pp. 329–354, 2019. [Google Scholar]
24. W. Sun, G. C. Zhang, X. R. Zhang, X. Zhang and N. N. Ge, “Fine-grained vehicle type classification using lightweight convolutional neural network with feature optimization and joint learning strategy,” Multimedia Tools and Applications, vol. 80, no. 20, pp. 30803–30816, 2021. [Google Scholar]
25. W. Sun, X. Chen, X. R. Zhang, G. Z. Dai, P. S. Chang et al., “A multi-feature learning model with enhanced local attention for vehicle re-identification,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3549–3560, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools