 Open Access
Open Access
ARTICLE
Resilient Service Authentication for Smart City Application Using IoT
Department of CSE, MRK Institute of Technology, Cuddalore, Tamilnadu, 608301, India
* Corresponding Author: Gokulakannan Elamparithi. Email:
Intelligent Automation & Soft Computing 2023, 36(1), 145-152. https://doi.org/10.32604/iasc.2023.032036
Received 04 May 2022; Accepted 07 June 2022; Issue published 29 September 2022
Abstract
Internet of Things (IoT) support for smart city systems improves service scales by ignoring various user congestion. People are looking for different security features for reliable and robust applications. Here, the Permanent Denial of Service (PDoS) problem arises from improper user identification. This article introduces the Service-Reliant Application Authentication (SRAA) to prevent PDoS attacks in a smart area of the city. In this authentication method, the security of the application is ensured through the distribution of guarded access. The supervised access distribution uses user interface features and sync with the user device. Abnormality in linking user device, application, and authentication is seen in Back Propagation (BP) readings. BP learning reduces given weights based on abnormalities trained during the access distribution process. The oddity is reflected in the sequence from previous training sessions to ensure consistent synchronization of distributed services. From PDoS, the web device displays a few unattended loads on the service, which reduces service failure. The effectiveness of the proposed verification method is verified using delays to verify metric accuracy, false standard, sync failure, and bit rate.Keywords
Internet of Things (IoT) technology empowers smart cities. In day-to-day operations in the city, intelligent city services are enabled by real-time data distribution in smart cities with specific real-time decision-making factors [1]. Focused productivity, information driven, real-time environment, customer focus, etc., are some of the features of intelligent services. IoT-enabled smart cities are being tested through the use of different applications in urban and urban services [2]. System of service is required for intelligent city services systems that allow advanced services and existing applications and applications. Disaster recovery, agriculture, transportation, health care, etc., are some of the applications areas in which intelligent city re-source systems are designed [3]. Smart city service systems powered by IoT have certain features such as modular, innovation, integrated value building, heterogeneity, productive focus, technological focus. The life cycle of intelligent city service plans includes usability, disability, performance, etc. The smart city services have three phases, namely infrastructure layer, middleware layer, and application layers [4,5].
Service management is a challenging issue for IoT. In smart city applications, devices are accessed by machines to transmit information and to perform other actions the security of sensors between sensors and actuators using authentication [6]. Access control is considered in intelligent IoT - based cities as a standard requirement. Controlling access with multi-talented features does not depend on the type of device [7]. An app-comprehensive, dedicated, flexible, and customer-independent are four aspects of controlling service access. Access control Lists (ACLs) are the area of normal access control structure [8]. Role-based access control (RBAC) is used to reduce the burden of access control lists. RBAC works better than Identity-based access control (IBAC). A few security issues that extend the validation process management, etc., are examples of access control capabilities. Sensitive data on IoT requires advanced access control and enforcement of access control policies. Flexible data access control achieves flexible policy implementation [9,10]
Huang et al. [11] has proposed a system-based access control system based on blockchain resources using blockchain. To avoid data disruption and single point failure, distributed attributes are recorded in block-chain technology. The access control system provides the requirement for lightweight calculation and high efficiency. Security analysis and performance analysis withstand different analyzes of the proposed activity indicate that it is performed on IoT systems manuscript [12].
Wazid et al. [13] consider the key control of the lightweight group divided into flexible access control. Subscriber group are administrators to limit the lock-ups with Key Distribution Center (KDC) and Small Key Distribution Centers (SKDCs). During joining events, storage counts and network connections are reduced [14]. Joint attack is prevented from providing secure group connections to Dynamic Log Generated Key Management–Access Control (DLGKM-AC). Profits in storage, calculation, and communication costs are reduced by the proposed protocol [15].
With information-centric IoT, Ding et al. [16] Suggested Hyper Allocate Calculate Effective high access control. Distribution efficiency is accelerated using a temporary storage network method and model driven by Internet Control Non-polynomial (ICN) receivers. The attribute-based command verification method improves IoT edge efficiency and resource compression [17]. Thoughtful security analysis and real-time testing are used to evaluate the proposed system. The efficiency and security of the proposed work increases while compared to the state of the art algorithm [18].
3 Proposed Smart Resilient Authentication Audit (SRAA)
In a smart city, services are still deployed in the app and ensure the security of various IoT services. Here, the user device synchronization is used by introducing the SRAA approach to the PDoS problem. This paper aims to improve reliable access assurance and reduce false positives, sync failures, and delays. To overcome these problems, the SRAA approach is being developed and provides security in the IoT environment. Fig. 1 introduces the SRAA in an intelligent IoT-based city environment.
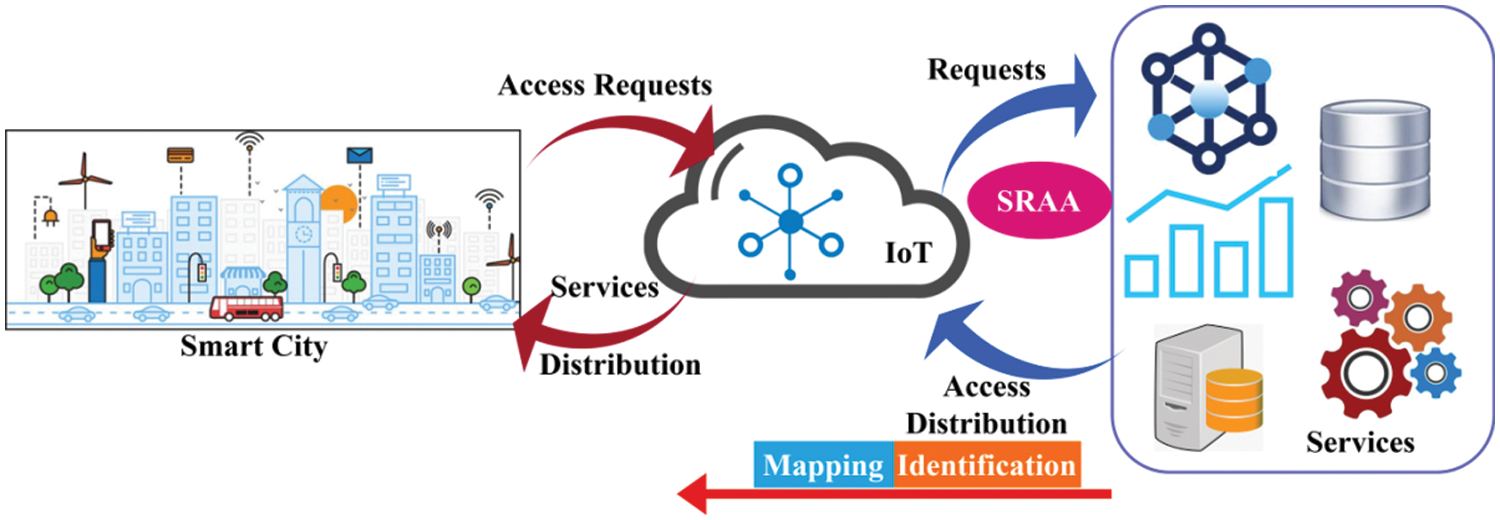
Figure 1: SRAA in IoT-based smart city
It is done by weighing on services and obtaining extraordinary services by distributing services efficiently. In this work, back propagation (BP) is used to find the sync and create the distribution of access. By posting this, communication is established between end-to-end users instantly. In this process, the first step is to identify the device’s user interface with the app and the service. If a disconnection occurs between these three components (Device, Application, and Service), it is rarely found that PDoS caused it. To address this issue, diagnostics were performed to link the three components, and evaluated in the following statistics
The identification is done by measuring the above Eq. (1) that feeds the device, application, and service communications, and is defined as τ. Occasionally the connection is verified by various services, and is represented as e′, and the numerical service is called ase_n. The identification is expressed as α, and the recognition is defined as asl_0, which is used to detect PDoS and uses rare services called b′. The device is represented as asd_i, the application is called n_a and the connection is defined as asx_c, which gives the user from the end w′. The connection is established by the device connection, and the application and analysis is done on time and provides authenticity.
The interconnection between the application and services is estimated and provides authentication for the varying services from the user in a smart city. Here, it deploys the communication and distributes the service is done for the user, and it is denoted as(x_c + w'/s_j), the distribution is represented ass_j. The time is termed ast_m, the connection is denoted asc_e, the access is termed as h′ that is distributed to the end-user request. The following Eq. (2) is used to evaluate the communication between the end-to-end users in IoT.
Communication is established between end-to-end users who use the authentication of various smart city services. This previous situation is used to analyze the communication and to evaluate the communication found in the first output. The second exit is associated with the termination of service between the end user. Here, a test is performed, and is defined as v_x and establishes a link. The previous state is called p_v which corresponds to the communication established before processing and forwarding the continuous state.
Weight is allocated to a variety of services, and communication is established between end users. Initially, weight is provided by the top services. If the increase is abnormal, the weight varies, indicating a lower width, and the validity is enhanced by performing this supply phase. In this experiment, PDoS is discussed in this section and provides access to an authorized user. The following figure is used to determine weight distribution.
In the above Eq. (3), the weights are assigned to the services for establishing communication between the end-users. Here, the weights are denoted as
Here, the interconnection is examined and maintains the commuHere, the previous service status is monitored and accessibility distribution is applied by checking the BP-related synchronization method. In this work, SRAA is used to evaluate the identification phase of PDoS attackers, and access is provided to services. Weights are assigned, and the decrease in gradient is measured by different types of processing in the IoT and determines the default service and disconnects the service. Performing these unusual services detects and disconnects services and checks sync between user devices, applications, and services. Verification is provided by examining the BP method associated with the safety method. In Figs. 2 and 3, service identification and calculation of different times are shown.
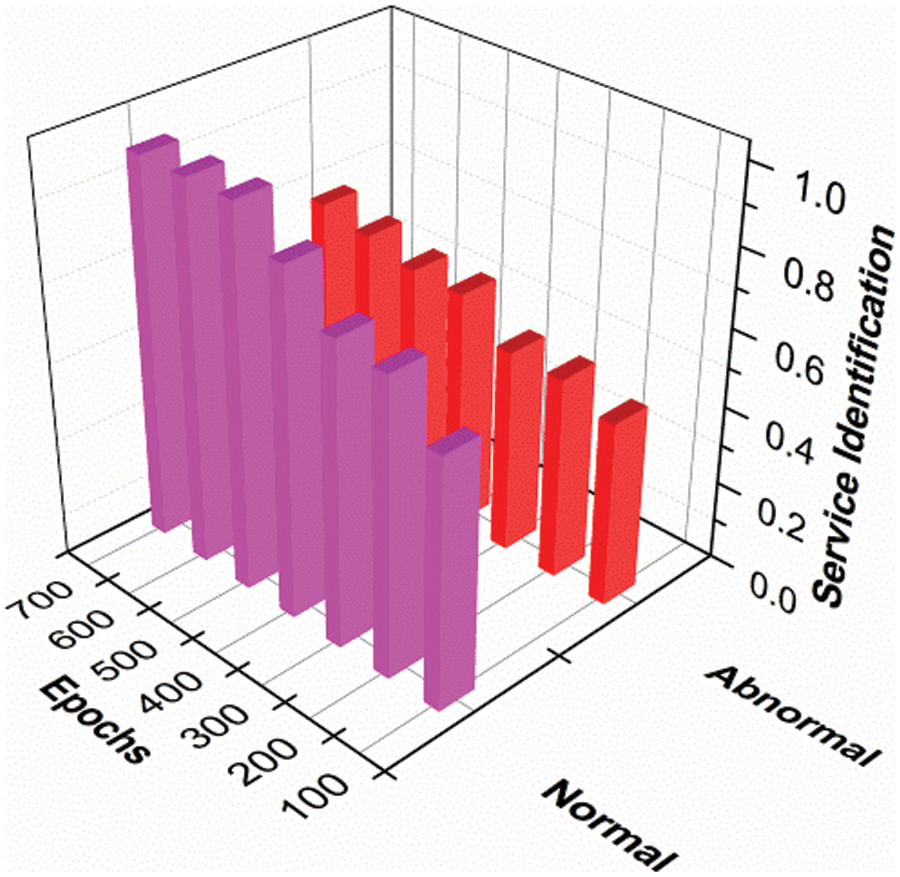
Figure 2: Service identification
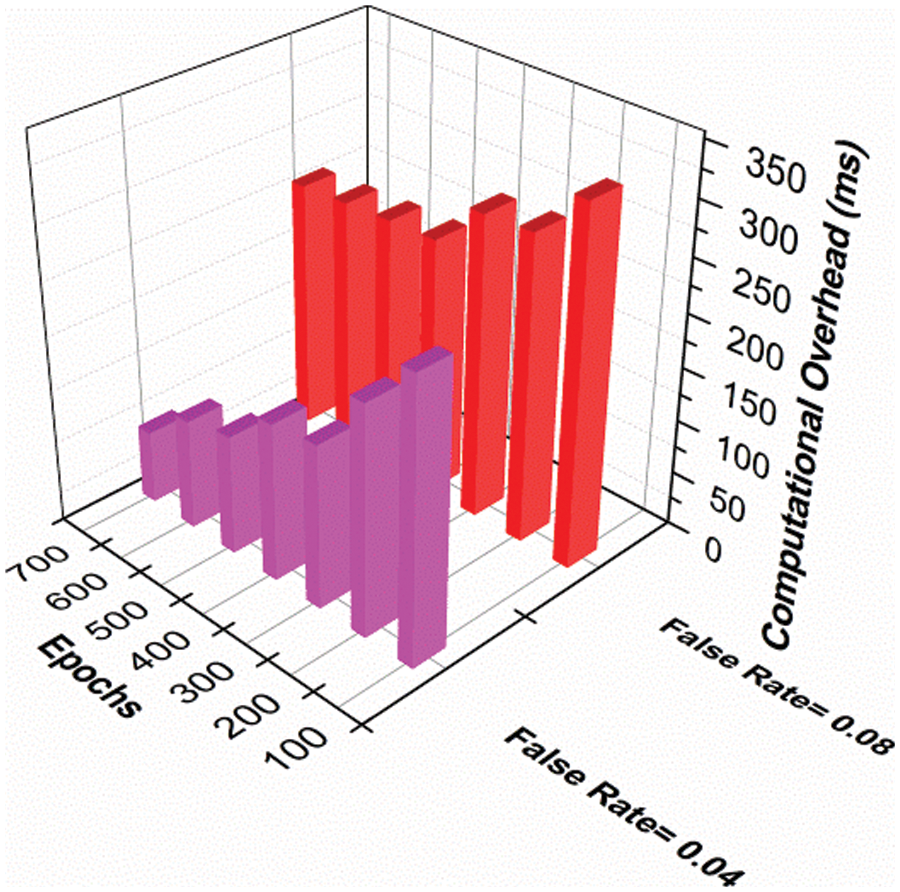
Figure 3: Computational overhead
Times vary from service to service of standard and non-standard services in the IoT environment. Displays your service for both normal and non-standard range from low to high. When epochs increase, the norm shows a higher range than non-standard services by identifying invaders shown in Fig. 3. Epoch estimates on various overheads are used immediately, and show a high to low range shown in Fig. 4. Seasons are measured by a false value in the proposed activity showing 0.0.4, 0.08. Compare that to 0.04, 0.08 indicating a high level of falsehood in this proposed activity, and the times are limited to services. The PDoS attackers are addressed in the initial stage and establish the communication between the end-users associated with the synchronization. In Tab. 1, the Service error % and mitigation % for different synchronization factors is tabulated.
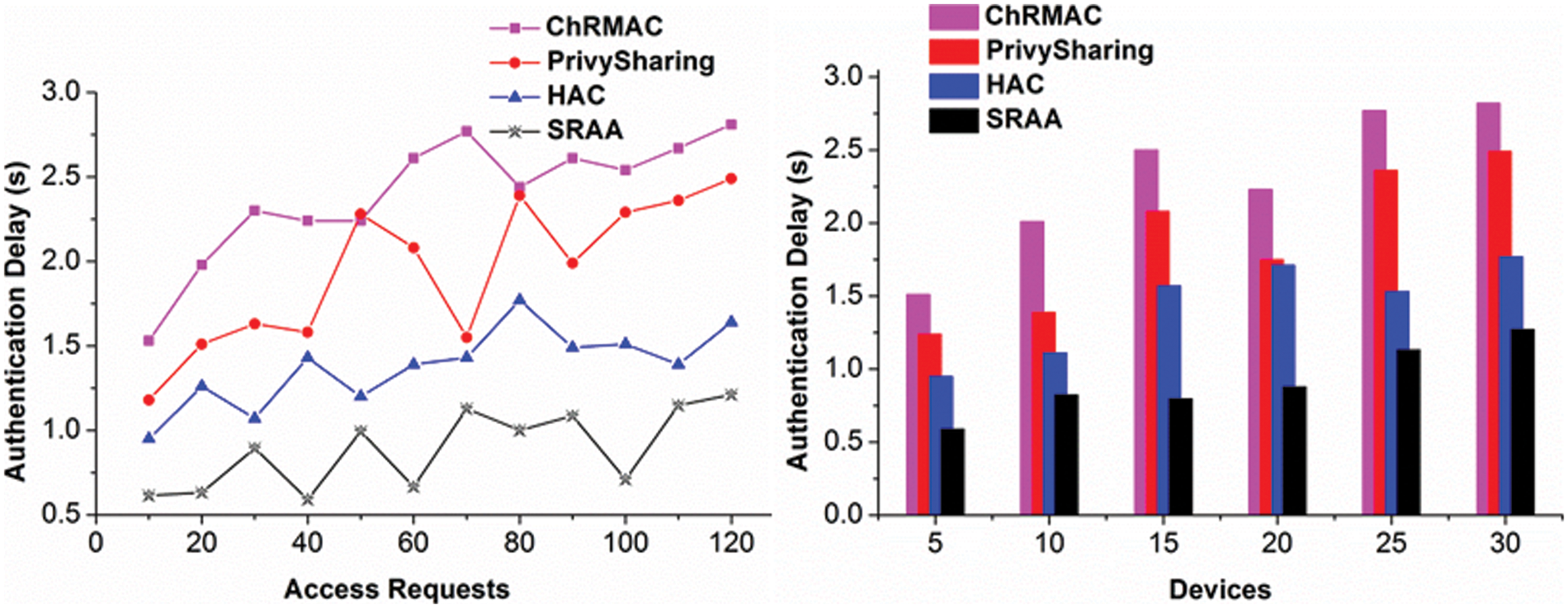
Figure 4: Authentication delay for access requests and devices

Synchronization of a percentage of different services is checked with an error and a reduction process. Here, both the error feature and the reduction indicate the low to wide range of the value and moderate error function. As the error increases, the reduction also increases, and it is the opposite process and shows better alignment shown in Tab. 1.
Periodic testing is performed to maintain synchronization for various users on IoT, and the delay factor is reduced in this processing. Common and uncommon services are identified, and the progression to BP is made and improves the verification process. When an authorized user provides a service, the level of security is significantly improved over time. Here, BP is tested along with the SRAA method and provides a reliable result by distributing access to the end user immediately.
Computation overhead for the varying access requests and interval is less and provides the authentication process on time. Here, the computation is examined periodically by equating
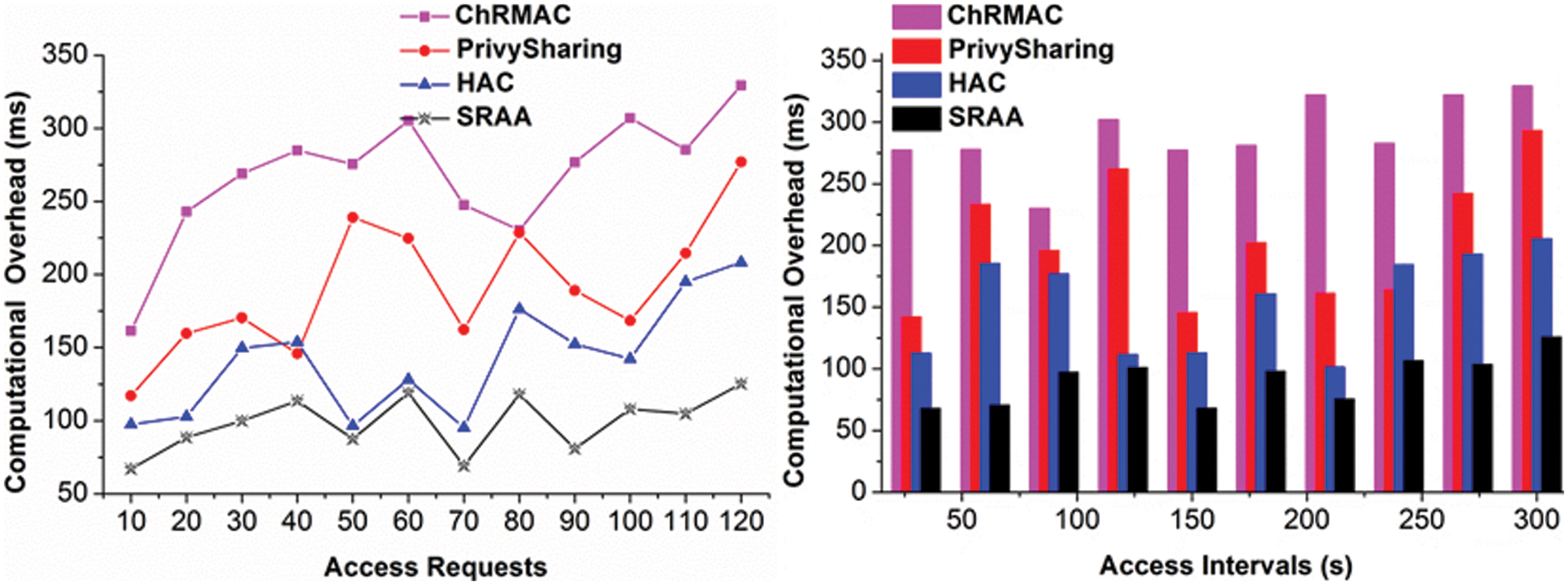
Figure 5: Computational overhead for access requests and access intervals
In Fig. 6, the access success increases for varying access requests for the devices that deploy the authentication. The synchronization is done for the three frame-works, and interconnection is examined reliably. The above comparative analysis results are tabulated in Tab. 2 for access requests, intervals, and devices.
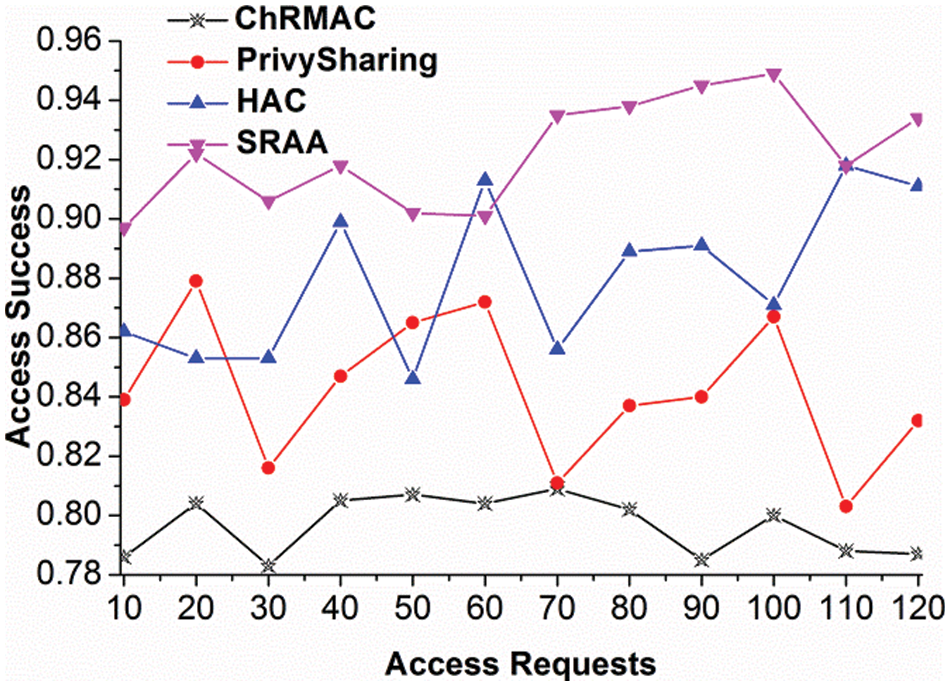
Figure 6: Access success for access requests

The proposed SRAA reduces authentication delay and computation overhead by 15.91% and 20.26% and improves access success by 9.07%. SRAA reduces authentication delay and synchronization failure by 15.38% and 8.94%.
In this article, a service-dependent app verification method was introduced to block the PDoS enemy from IoT smart city services. This approach ensures the security of the service based on access control and the sync verification process. First, synchronization between user device, application, and IoT service is verified to provide authentication. Changes/abnormalities in consensus monitoring using BP studies based on weight reduction features. The learning process is trained using troubleshooting services and service errors. Based on these factors, the distribution of the service is determined by periodic updates. Therefore, the false level of the PDoS enemy in service response is reduced. Performance tests show that the proposed method achieves minimal validation delays, sync failures, and a high number of computations which improves the success rate of distributed access. In the future, access control for multi-level application applications is scheduled to be evaluated by BP reading. This focuses on improving access control for large applications and responses to the simultaneous service.
Funding Statement: The author received no specific funding for this study.
Conflicts of Interest: The author declare that they have no conflicts of interest to report regarding the present study.
References
1. H. Yao, P. Ga, J. Wang, P. Zhang, C. Jiang et al., “Capsule network assisted IoT traffic classification mechanism for smart cities,” IEEE Internet of Things Journal, vol. 6, no. 5, pp. 7515–7525, 2019. [Google Scholar]
2. M. Tao, K. Ota and M. Dong, “Locating compromised data sources in IoT-enabled smart cities: A great-alternative-region-based approach,” IEEE Transactions on Industrial Informatics, vol. 14, no. 6, pp. 2579–2587, 2018. [Google Scholar]
3. D. Bruneo, S. Distefano, M. Giacobbe, A. L. Minnolo, F. Longo et al., “An IoT service ecosystem for smart cities: The# smartme project,” Internet of Things, vol. 5, pp. 12–33, 2019. [Google Scholar]
4. M. Saadi, M. T. Noor, A. Imran, W. T. Toor, S. Mumtaz et al., “IoT enabled quality of experience measurement for next generation networks in smart cities,” Sustainable Cities and Society, vol. 60, pp. 102–126, 2020. [Google Scholar]
5. P. F. Sheron, K. P. Sridhar, S. Baskar and P. M. Shakeel, “A decentralized scalable security framework for end-to-end authentication of future IoT communication,” Transactions on Emerging Telecommunications Technologies, vol. 5, no. 2, pp. 132–144, 2019. [Google Scholar]
6. D. Wang, B. Bai, K. Lei, W. Zhao and Y. Yang, “Enhancing information security via physical layer approaches in heterogeneous IoT with multiple access mobile edge computing in smart city,” IEEE Access, vol. 7, pp. 54508–54521, 2019. [Google Scholar]
7. P. Gomathi, S. Baskar and P. M. Shakeel, “Concurrent service access and management framework for user centric future internet of things in smart cities,” Complex & Intelligent Systems, vol. 2, no. 5, pp. 156–178, 2020. [Google Scholar]
8. N. Tapas, F. Longo, G. Merlino and A. Puliafito, “Experimenting with smart contracts for access control and delegation in IoT,” Future Generation Computer Systems, vol. 5, no. 2, pp. 213–232, 2020. [Google Scholar]
9. G. Manogaran, P. M. Shakeel, H. Fouad, Y. Nam, S. Baskar et al., “Wearable IoT smart-log patch: An edge computing-based Bayesian deep learning network system for multi access physical monitoring system,” Sensors, vol. 19, no. 13, pp. 3013–3030, 2019. [Google Scholar]
10. A. Gabillon, R. Gallier and E. Bruno, “Access controls for IoT networks,” SN Computer Science, vol. 1, no. 1, pp. 24–42, 2020. [Google Scholar]
11. J. C. Huang, M. H. Shu, B. M. Hsu and C. M. Hu, “Service architecture of IoT terminal connection based on blockchain identity authentication system,” Computer Communications, vol. 160, pp. 411–422, 2020. [Google Scholar]
12. S. Manikandan, M. Chinnadurai, D. Maria Manuel Vianny and D. Sivabalaselvamani, “Real time traffic flow prediction and intelligent traffic control from remote location for large-scale heterogeneous networking using tensorFlow,” International Journal of Future Generation Communication and Networking, vol. 13, no. 1, pp. 1006–1012, 2020. [Google Scholar]
13. M. Wazid, A. K. Das, R. G. Hussain, G. Succi and J. J. Rodrigues, “Authentication in cloud-driven IoT-based big data environment: Survey and outlook,” Journal of Systems Architecture, vol. 97, pp. 185–196. 2019. [Google Scholar]
14. P. Zhang, J. Liu, Y. Shen, H. Li and S. Jiang, “Lightweight tag-based PHY-layer authentication for IoT devices in smart cities,” IEEE Internet of Things Journal, vol. 7, no. 5, pp. 3977–3990, 2019. [Google Scholar]
15. S. Manikandan, P. Dhanalakshmi, S. Priya and A. Teena, “Intelligent and deep learning collaborative method for e-learning educational platform using tensorFlow,” Turkish Journal of Computer and Mathematics Education, vol. 12, no. 10, pp. 2669–2676, 2021. [Google Scholar]
16. S. Ding, J. Cao, C. Li, K. Fan and H. Li, “A novel attribute-based access control scheme using blockchain for IoT,” Journal of Latex Class Files, vol. 14, no. 8, pp. 1–10, 2015. [Google Scholar]
17. W. Sun, X. Chen, X. R. Zhang, G. Z. Dai and P. S. Chang, “A Multi-feature learning model with enhanced local attention for vehicle re-identification,” Computers, Materials & Continua, vol. 69, no. 3, pp. 3549–3560, 2021. [Google Scholar]
18. W. Sun, G. C. Zhang, X. R. Zhang, X. Zhang and N. N. Ge, “Fine-grained vehicle type classification using lightweight convolutional neural network with feature optimization and joint learning strategy,” Multimedia Tools and Applications, vol. 80, no. 20, pp. 30803–30816, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools