 Open Access
Open Access
ARTICLE
Efficient Clustering Using Memetic Adaptive Hill Climbing Algorithm in WSN
1 Department of Computer Science and Engineering, Adhiyamaan College of Engineering, Hosur, 635109, Tamilnadu, India
2 Department of Computer Science and Engineering, Sona College of Technology, Salem, 636005, Tamilnadu, India
* Corresponding Author: M. Manikandan. Email:
Intelligent Automation & Soft Computing 2023, 35(3), 3169-3185. https://doi.org/10.32604/iasc.2023.029232
Received 28 February 2022; Accepted 12 April 2022; Issue published 17 August 2022
Abstract
Wireless Sensor Networks are composed of autonomous sensing devices which are interconnected to form a closed network. This closed network is intended to share sensitive location-centric information from a source node to the base station through efficient routing mechanisms. The efficiency of the sensor node is energy bounded, acts as a concentrated area for most researchers to offer a solution for the early draining power of sensors. Network management plays a significant role in wireless sensor networks, which was obsessed with the factors like the reliability of the network, resource management, energy-efficient routing, and scalability of services. The topology of the wireless sensor networks acts driven factor for network efficiency which can be effectively maintained by performing the clustering process effectively. More solutions and clustering algorithms have been offered by various researchers, but the concern of reduced efficiency in the routing process and network management still exists. This research paper offers a hybrid algorithm composed of a memetic algorithm which is an enhanced version of a genetic algorithm integrated with the adaptive hill-climbing algorithm for performing energy-efficient clustering process in the wireless sensor networks. The memetic algorithm employs a local searching methodology to mitigate the premature convergence, while the adaptive hill-climbing algorithm is a local search algorithm that persistently migrates towards the increased elevation to determine the peak of the mountain (i.e.,) best cluster head in the wireless sensor networks. The proposed hybrid algorithm is compared with the state of art clustering algorithm to prove that the proposed algorithm outperforms in terms of a network life-time, energy consumption, throughput, etc.Keywords
Wireless Sensor Networks [1] is an evolved version of wireless networks, which becomes more familiar over a decade due to their military and conventional applications. The Wireless Sensor Networks (WSN) are composed of autonomous sensing devices which are deployed to monitor a certain targeted parameter in the corresponding locations. The sensors are connected to each other to form a closed network with a specific node designated as the cluster head to monitor the traffic flow in the network from one place to another. Fig. 1 depicts the structure of Wireless Sensor Networks performing the clustering process [2].
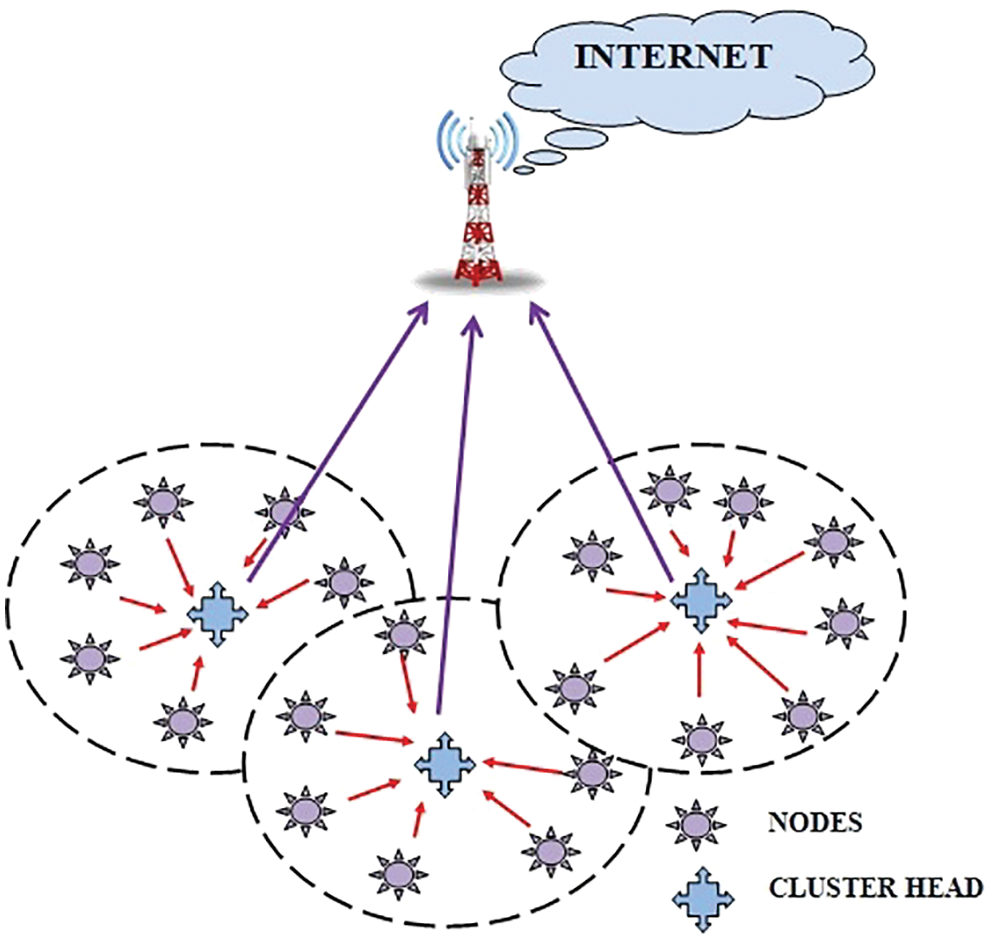
Figure 1: Wireless sensor networks with clustering process
The WSN is intended to monitor the parameters [3], not restricted to the temperature, humidity, pollutants, movement of objects and transfers the information to the base station for further processing of data and to take necessary back actions. The autonomous sensor nodes [4] are deployed in the concentrated area with pre-charged energy of specific joules. The sensor nodes [5] on transferring data from one node to another tend to lose energy during the routing process. The draining of energy in the sensor nodes leads to an increase in dead sensor nodes. Thus the dead nodes remain idle and get detached from the network population. Hence energy consumption is considered to be the more stringent operation in the Wireless Sensor Networks (WSN) [6]. Recent applications of Wireless Sensor Networks [7] follow the principle of a highly reliable oriented event of interest information delivery to the destination nodes [8]. The clustering policy [9] follows such a principle to deliver the data from the source node to the destination node. The clustering policy means to collecting the data from the sensor node and is communicated the data to the cluster head. The cluster head, in turn, transmits the data to the Base Station following the hierarchy of the cluster head. The process of clustering possesses various advantages as follows.
• The clustering process possesses mitigation of energy consumption during the data transmission.
• Mitigates the unbound delay created during the forwarding of data from one node to another.
• Ease of following data implementation techniques during data transfer from the source node to base station.
This research work proposes a novel hybrid algorithm to perform the clustering process in wireless sensor networks. The research work is composed of dual efficient algorithms namely the Memetic algorithm to perform the energy-efficient clustering process [10] while the adaptive hill-climbing algorithm is to identify the critical shortest path among the nodes in the Wireless Sensor Networks. The proposed clustering mechanism is proved to be energy efficient as it transfers the data to the neighbor node which is located at the shortest distance. The energy consumed by the nodes to transfer the data from the source node to the base station is more during the direct transfer, whereas the energy consumption can be mitigated to a great extent.
This research manuscript is preceded by a literature review in Section 2 defining the pitfalls of the existing method and framing the objective of the proposed research work. Section 3 illustrates the proposed hybrid algorithm followed by the result and analysis is performed in Section 4. The research manuscript is concluded in Section 5 mentioning the advantages of the work.
Numerous active researches were performed in this domain to design energy-efficient algorithms in the process of performing clustering in Wireless Sensor Networks. Some of the results of the notable research have been listed in this section which acts as the basis to form the objective for this research work. Dargie et al. had employed a simple clustering strategy [11] in the wireless sensor network employing the neighbor nodes to form a network. This approach enabled the assignment of the cluster head to perform multiple rounds of communication to reduce the cost incurred during the cluster head selection. Singh et al. had proposed a node overhaul scheme [12] to achieve an effective load balancing and energy efficient clustering process in the wireless sensor networks. The proposed method forms a set of initial clusters and later the clusters were formed based on the best solution obtained. This methodology enhanced the network lifetime more than the existing methods. Li et al. had designed a combined clustering model [13] integrating the game theory to resist the selective forwarding technique in wireless sensor networks. The authors employed the nash equilibrium of the game among the sensor nodes and malicious nodes to determine the attacks in wireless sensor networks. Padmanaban et al. had designed a grid-based data clustering algorithm known as the energy-efficient clustering algorithm (EESCA-WR) [14]. The proposed algorithm employs multiple grid relays (GR) and possesses a unique grid leader (LR). The performance analysis of the proposed algorithm mitigates the power consumption in the nodes during the data transfer from one node to another.
Zhu et al. had proposed a clustering algorithm based on a fast search and find of density peaks (CFSFDPs) [15] and Kernel Density Estimation (KDE) for the improvement of the selection of clustering process by employing a soft K-means clustering algorithm. The proposed algorithm improves the lifetime of the nodes when compared to the existing methodologies. Ali et al. had developed a novel ARCH-FATI [16] based cluster head selection algorithm combined with a heuristic algorithm called Rank-based clustering algorithm. The proposed algorithm enhanced the lifetime (LT) of the network by 25% when compared to the state of art algorithms. Tao et al. had proposed an unequal clustering algorithm that relies on type-2 TSK fuzzy logic algorithm (UCT2TSK) [17]. The outputs of the proposed algorithm are acquired by optimizing the cluster head and by determining the cluster dimensions. The proposed algorithm reduces the energy consumption by the nodes and improves the throughput of the network. Lata et al. had proposed the fuzzy-based LEACH clustering algorithm (LEACH-FC) [18] to improve the lifetime of the network. The proposed algorithm is analyzed and is compared with the existing algorithm and is proved to possess improved life-time and reduced power consumption. Aydin et al. had discussed and designed the algorithm to improve the energy efficiency of the wireless sensor networks. The route selection and the cluster head are formed by applying the Artificial Neural Networks [19]. The simulation results prove that the proposed method enhances the cluster head formation process. Han et al. had suggested a clustering algorithm based on meta-heuristic algorithm (CPMA). The predominant function of CPMA is the clustering process and is composed of two major operations namely selection of cluster head and coordination among the network components. The performance analysis proves that the proposed CPMA outperforms and enhanced the network lifetime.
2.1 Drawbacks of the Existing Methodologies
The existing algorithms [11–19] perform the clustering process based on the distance between the nodes and the following drawbacks have been identified from the state of art clustering methodologies.
• The cluster head was designated permanently, which leads to the reduction of network lifetime.
• The clustering was performed based on the branch-based optimization technique.
• The existing clustering algorithm employs a non-flow spitted routing mechanism to transfer the data from one node to another.
• The entire network fails, whenever the relay node is considered to be a dead node due to the drain of energy.
2.2 Objectives of the Proposed Research Work
Based on the drawbacks identified from the existing methodologies [11–19], the following are the objective framed for the proposed research work.
• To perform energy-efficient clustering process using the Memetic algorithm
• To employ an adaptive hill search algorithm for the determination of the shortest path among the nodes in the network.
The proposed work is of two folded with the memetic algorithm to perform the energy-efficient clustering process in the wireless sensor network and is followed by the adaptive hill-climbing algorithm for effective routing process by determining the critical shortest path among the cluster heads/nodes in the wireless sensor networks.
3.1 Clustering Process by Memetic Algorithm
The memetic algorithm is the enhanced version of genetic algorithm, which when designated with a task of the clustering process, determines the size of the cluster and identifies a proper node to be designated as the cluster head. The memetic algorithm is the improvised version of a genetic algorithm which is a population-based heuristic algorithm. The Memetic Algorithm (MA) [20] possesses higher order magnitude and is more rapid than the genetic algorithm. This MA algorithm can be made a hybrid by integrating a local search algorithm during the process of iteration. This proposed research work employs an adaptive hill-climbing algorithm as a local search algorithm which is intended to determine the shortest path among the nodes of the WSN. The local search is targeted to improve the convergence rate. The local search algorithm is intended to determine the shortest path by performing a jump process to a new region to trace the shortest path effectively. In the memetic Algorithm (MA), [21] the number of individual nodes is created and counted to determine the best cluster head and the size of the cluster head node. In practice, 5% of nodes are randomly chosen as the cluster head and in turn, those temporary cluster head performs a local search to determine the actual cluster head. Some of the basic terms of the proposed memetic algorithm are described below:
• Chromosome: It is a representation in terms of string for the available candidate solutions. In the proposed Memetic Algorithm (MA), the chromosome is the structure of clustering parameters of the wireless sensor nodes. The chromosome determines whether a node is a cluster head node or a member node. The chromosome representation is made in Fig. 2a.
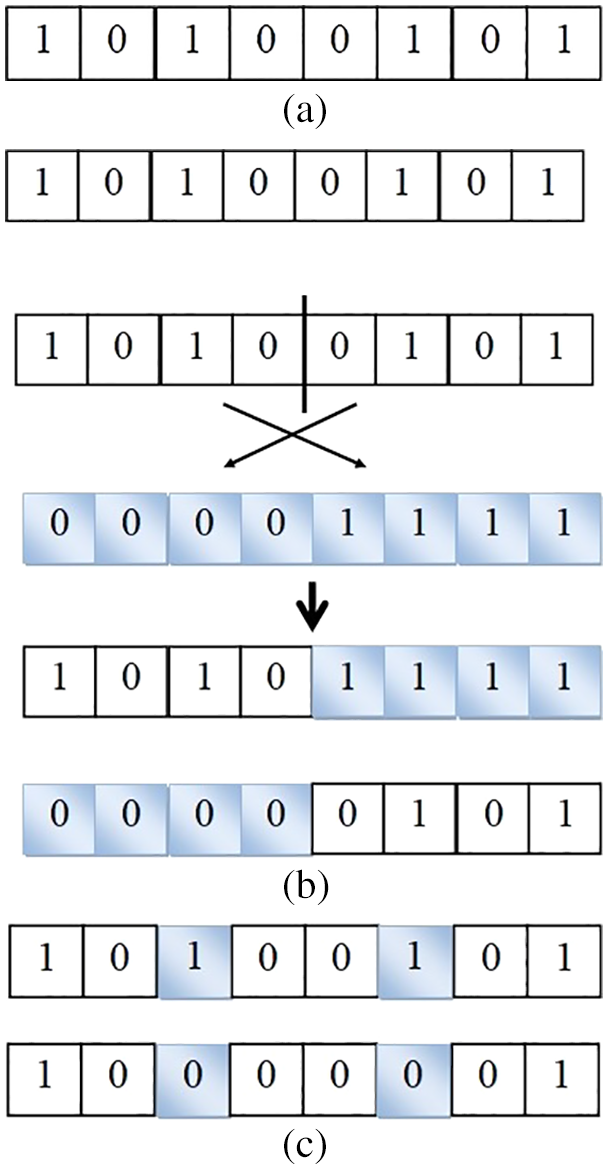
Figure 2: (a) Nodes in chromosome representation. (b) Fitness values of nodes in Crossover operation. (c) Chromosome mutation
• Selection: The entire sets of nodes are sorted according to their fitness value, from which the node with minimum fitness value has opted as cluster head. As a sign of randomness, the successive nodes are identified in a random manner, in such a way that the opted nodes possess minimal fitness values. The option of nodes with minimal fitness value exhibits maximum likelihood in the cluster.
• Crossover: This is the genetic operator which acts as a core operation in the proposed Memetic algorithm for the clustering process. The pictorial representation of the crossover is depicted in Fig. 2b.
The proposed Memetic Algorithm (MA) works on the principle of differential evolution (DE) which is a novel computational principle whose population of nodes can be mathematically represented as in Eq. (1).
where, PN is the population of the node and D1,N is the D-dimensional vector of the data routing path.
The vector index of each node is arranged in random manner to preserve the diversity of the node neighborhood.
• Mutation: The mutation operation determines the new possible solutions in forming the cluster by implementing minor disturbances to the chromosomes of the nodes. For example, the “0”s in the third and the sixth position are flipped to “1” while other positions are undisturbed. In case of clustering process, two locations chosen at random and the cluster head chosen is to be swapped as shown in Fig. 2c.
Each node in the cluster DP, N is a donor vector which employs the best fitness function. The best fitness function can be determined as represented in Eq. (2).
where, r1…4 is the fitness function scaling factor.
• Fitness Function: Fitness function is a parameter to determine the quality of the nodes in the wireless sensor networks. The evaluation of the fitness function is performed by assigning a fitness value to all nodes in the network. The parameters of the fitness function are remaining energy which is the accumulation of resultant energy at each sensor node. The direct distance is the sum of the separative distance from all nodes to the base station. The cluster distance is the sum of distances from members to the cluster head. The flowchart of the proposed memetic algorithm in energy-efficient clustering process is depicted in Fig. 3.

Figure 3: Flowchart of proposed memetic algorithm for clustering process
The Eqs. (3)–(5) represents the method of determining the residual energy as a part of determining the fitness function. The data transmission from the source node to the destination node is performed by implementing the Time Division Multiple Access (TDMA) scheduling process among the nodes. Each node is allocated with a separate time slot to communicate. Our proposed memetic algorithm assists the TDMA scheduling process and can be easily implemented with variable time slots for multiple nodes.
The algorithm for the proposed Memetic algorithm to perform energy efficient clustering process is illustrated in Tab. 1.

At the end of the memetic algorithm, based on the best solution which relies on the minimal fitness solution and with maximum residual power, the node is designated as the cluster head and is designated to coordinate the data transfer to neighborhood nodes of the Wireless Sensor Networks. The next critical concern to be addressed is to determine the shortest path among the various neighborhood cluster head so that to transfer the data with minimal power consumption. For this purpose, this proposed work employs an Adaptive Hill climbing algorithm to determine the critical shortest path.
3.2 Adaptive Hill Climbing Algorithm-Shortest Path Detection
The implementation of the memetic Algorithm (MA) for performing energy-efficient clustering in WSN is followed by the action performed by Local Search (LS) operators with local filtering process, and to assure the availability of sufficient exploitation during the evolution of node population in WSN. The Hill climbing algorithm is the common search strategy and is classified into Crossover based Hill climbing strategy and Mutation based Hill-climbing strategy. The basic principle of Hill Climbing (HC) algorithm [22] is to employ a stochastic iterative hill-climbing algorithm, to migrate the acceptance criteria of the search for the shortest path from the source cluster head to the destination node. The proposed Adaptive Hill-Climbing algorithm is an enhanced version of the conventional Hill-Climbing algorithm and is broadly classified into Steepest Mutation based Hill Climbing (SMHC) and Greedy Crossover based Hill Climbing (GCHC) methodology.
3.2.1 Greedy Crossover Based Hill Climbing
In GCHC, the individual node which is at the critical point of event occurrence is considered as one parent node while the other node is identified from the current group of nodes using the Roulette Model. The crossover is performed between two nodes namely the source node to the other nodes. The step-by-step procedure of GCHC is illustrated in Tab. 2.

3.2.2 Steepest Mutation Based Hill Climbing
The steepest mutation-based Hill Climbing (HC) algorithm modifies the chromosome in a random manner during the execution. The elite node with sufficient energy was picked out from the present situation with a better level of fitness. In SMHC, the Local Search (LS) operation is performed in a smaller area. The classification of various parameters setting methods was determined with various constant values. The steepest mutation indicates that when a single mutation operation is performed on a chromosome, it only alters a few bits at random. SMHC selects an elite individual from the present population and modifies some random bits. If the newly altered human is more fit, it will take the position of the elite individual. The algorithm for the steepest mutation-based hill-climbing process is illustrated in Tab. 3.

Various Local Search (LS) operators had reported the implementation of an adaptive hill climbing network. Each LS operator does a biased search, resulting in an approach that is efficient for some classes of problems but inefficient for others. That is, LS is problem-specific. As a result, how to improve LS operators while avoiding the use of ineffective LS approaches becomes a critical topic. Many researchers have employed numerous LS algorithms in their MAs to overcome this issue. When compared to regular MAs that use a single LS operator throughout the run, MAs with several LS methods typically outperform them. Multiple LS operators should be conducted concurrently on those persons chosen for local improvements, and a specific learning mechanism should be used to offer the efficient LS techniques a better probability of being chosen later on. The GCHC and SMHC operators in AHC are both allowed to work in the whole LS loop and are randomly selected to execute one-step LS operations at each generation while the MA is running. Let pgchc and psmhc signify the odds of applying GCHC and SMHC to the individual utilised for a local search.
The normalized hamming distance between any two nodes “i” and “j” can be represented as in Eq. (7).
and β is determined by using the mathemetical equation represented in (9).
where, Pops is the size of the pop made by the data to reach the source node to destination node. The x* mentions the best individual path achieved in the particular network. At the start of this strategy, pgchc and psmhc are both set to 0.5, implying that each LS operator has a reasonable chance of competing. Given that each LS operator always performs a biased search, the LS operator that delivers the most improvements should be given a higher selection probability. In this case, an adaptive learning strategy is employed to update the pgchc and psmhc values for each LS operator. Let’s denote the improvement degree of the chosen individual when one LS operator is employed to refine it, which can be determined using Eq. (10).
where, fini is the initial fitness function while ffin is the final fitness function of the nodes in the wireless sensor networks. The flow diagram for the proposed adaptive hill climbing algorithm is depicted in Fig. 4.

Figure 4: Flow diagram of adaptive hill climbing algorithm
The degree of improvement of each LS operator is determined at each generation when a predefined number (ls size) of iterations is reached, and then pgchc and psmhcare re-calculated to continue with the local improvement in the following generation. Assume gchc(t) and smhc(t) represent the entire improvement of GCHC and SMHC at generation t, respectively. The following Eqs. (11)-(14), can be used to compute the LS selection probabilities pgchc(t + 1) and psmhc(t + 1) at generation (t +1).
where

The two separate HC techniques, GCHC and SMHC, may not only collaborate to increase individual quality but also compete with each other to attain a higher selection probability in the AHC running process. To encourage competition, the selection probability of LS operators can be recalculated using an adaptive learning method, where the LS operator with the highest fitness [23] increase is rewarded with a better likelihood of being picked for future individual refinement. The Local Search operation performed through the Adaptive Hill Search algorithm provides a better shortest path with satisfactory fitness functions. Hence the data transferred through this shortest path consumes reduced energy and possesses maximum lifetime.
The proposed method of integrating the memetic Algorithm with the Adaptive Hill-Climbing algorithm to perform the energy-efficient clustering process [24] is implemented and tested using Network Simulator-2 (NS-2) simulating tool and the following parameters are analyzed. (i) Packet Delivery Ratio (ii) End to End Delay (iii) Throughput (iv) Energy Consumption and (v) Route Discovery Time. The Fig. 5 specifies the node position analysis of WSN in NS-2 and Fig. 6 clustering process using memetic algorithm in WSN using NS-2.

Figure 5: Node position analysis for WSN in NS-2

Figure 6: Clustering process using memetic algorithm in NS-2
The performance of the proposed method is compared with the existing methods of MLBAR-PSO, Genetic Algorithm, Memetic Algorithm, Memetic Algorithm-Hill Climbing algorithm, Modified Gravitational Search Algorithm. The simulation parameters of the proposed method is tabulated in Tab. 5.
The Packet Delivery Ratio (PDR) is a measure of data transmission dependability in Wireless Sensor Networks (WSN). The PDR is defined as the ratio of successfully transferred data packets from the originating node to the network sink to the total number of packets transmitted by the source node. Other performance parameters such as the prevalence of jitter in point-to-point data transmission, network life duration, and throughput influence the Packet Delivery Ratio. Fig. 7 depicts a visual depiction of the suggested methodology's metrics in relation to the Packet Delivery Ratio.

Figure 7: Comparison of packet delivery ratio
End-to-end or point-to-point Transmission Delay is a measurement of how long it takes a data packet to travel across a wireless sensor network (WSN). The transmission delay is made up of numerous types of latencies, including transmission latency, propagation jitter, processing latency, and queuing latency. Fig. 8 displays a point-to-point transmission delay performance comparison for the proposed MA-AHC system vs. benchmarking approaches.

Figure 8: Comparison of end to end transmission delay
Throughput is a measure of data transmission efficiency that may be used in any form of network. The number of data packets delivered effectively to the recipient is described as throughput (sink node). Fig. 9 shows a graphical comparison of throughput for the suggested technique and benchmarking methodologies.

Figure 9: Throughput-comparison
The energy consumed by electronic sensors in Wireless Sensor Networks (WSN) is defined by the energy required for detecting, identifying the shortest path, and transmitting data from one location to another. Eq. (15) represents the overall energy consumption of the electronic sensor numerically.
where, Ec : total energy consumed by nodes, Ei : initial energy possessed by nodes, Ee : Energy consumed during shortest path estimation and Et : Energy consumed during data transmission
Fig. 10 illustrates the residual energy of each node in the network after certain rounds of communication. The residual energy is measured after every 1000 rounds with an initial energy of 100 Joules to the nodes. The performance of the suggested MA-AHC algorithm demonstrates a high degree of residual energy, which directly contributes to the maximum network life time.

Figure 10: Energy consumption-comparison
The Route Discovery time for a routing mechanism in a Wireless Sensor Network is an important metric since it can reduce network lifetime if it takes too long to discover the best route. The Route Discovery Time is affected by the number of nodes/cluster heads between the originating node and the network sink.
From the comparative analysis depicted in Fig. 11, it is proved that the proposed Memetic Algorithm integrated with a Adaptive Hill-Climbing algorithm outperforms well in terms of elevation in packet delivery ratio, throughput and a massive reduction in end to end delay, energy consumption and route discovery time.

Figure 11: Comparison of route discovery time
The increase in the need for wireless surveillance and monitoring applications improves the necessity for advancements in Wireless Sensor Networks. The clustering process is performed using the memetic algorithm which is the modified version of the Genetic algorithm and the shortest path routing mechanism is performed using the Adaptive Hill Climbing algorithm. The analysis exhibits a better performance in Packet Delivery Ratio with 92%, minimal End End Delay of 16 ms, elevated throughput of 160 Mbps, possessing residual energy of 70 milli joules, and the time consumed to determine the path is just 10 ms. This method can be applicable to all Wireless Sensor Node applications. This work can further be enhanced with a reduction of packet size for the data transmission, such that the energy consumption can further be reduced.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. F. F. J. Lasso, K. Clarke, A. N. Cadavid and A. Nirmalathas, “Energy-aware routing for software-defined multihop wireless sensor networks,” IEEE Sensors Journal, vol. 21, no. 8, pp. 10174–10182, 2021. [Google Scholar]
2. J. Singh, S. S. Yadav, V. Kanungo and V. Pal, “A node overhaul scheme for energy efficient clustering in wireless sensor networks,” IEEE Sensors Letters, vol. 5, no. 4, pp. 1–4, 2021. [Google Scholar]
3. K. P. Rajput, Y. Verma, N. K. D. Venkategowda, A. K. Jagannatham and K. P. Varshney, “Robust linear transceiver designs for vector parameter estimation in MIMO wireless sensor networks under csi uncertainty,” IEEE Transactions on Vehicular Technology, vol. 70, no. 8, pp. 7347–7362, 2021. [Google Scholar]
4. H. Kim and S. W. Han, “An efficient sensor deployment scheme for large-scale wireless sensor networks,” IEEE Communications Letters, vol. 19, no. 1, pp. 98–101, 2015. [Google Scholar]
5. W. Liang, C. Ma, M. Zheng and L. Luo, “Relay node placement in wireless sensor networks: from theory to practice,” IEEE Transactions on Mobile Computing, vol. 20, no. 4, pp. 1602–1613, 2021. [Google Scholar]
6. S. K. Bidhendi, J. Guo and H. Jafarkhani, “Energy-efficient node deployment in heterogeneous two-tier wireless sensor networks with limited communication range,” IEEE Transactions on Wireless Communications, vol. 20, no. 1, pp. 40–55, 2021. [Google Scholar]
7. X. Fu, W. Li, Y. Yang and O. Postolache, “Cascading failures analysis of wireless sensor networks with varying routing schemes,” IEEE Sensors Journal, vol. 21, no. 8, pp. 10193–10203, 2021. [Google Scholar]
8. N. Gharaei, Y. D. Al-Otaibi, S. A. Butt, S. J. Malebary, S. Rahim et al., “Energy-efficient tour optimization of wireless mobile chargers for rechargeable sensor networks,” IEEE Systems Journal, vol. 15, no. 1, pp. 27–36, 2021. [Google Scholar]
9. A. Forster, Introduction to wireless sensor networks, 1st ed., England: Wiley Publication, pp. 99–112, 2016. [Google Scholar]
10. H. Al-Tous and I. Barhumi, “Reinforcement learning framework for delay sensitive energy harvesting wireless sensor networks,” IEEE Sensors Journal, vol. 21, no. 5, pp. 7103–7113, 2021. [Google Scholar]
11. W. Dargie and J. Wen, “A simple clustering strategy for wireless sensor networks,” IEEE Sensors Letters, vol. 4, no. 6, pp. 1–4, 2020. [Google Scholar]
12. J. Singh, S. S. Yadav, V. Kanungo, Yogita and V. Pal, “A node overhaul scheme for energy efficient clustering in wireless sensor networks,” IEEE Sensors Letters, vol. 5, no. 4, pp. 1–4, 2021. [Google Scholar]
13. Y. Li and Y. Wu, “Combine clustering with game to resist selective forwarding in wireless sensor networks,” IEEE Access, vol. 8, pp. 138382–138395, 2020. [Google Scholar]
14. Y. Padmanaban and M. Muthukumarasamy, “Scalable grid-based data gathering algorithm for environmental monitoring wireless sensor networks,” IEEE Access, vol. 8, pp. 79357–79367, 2020. [Google Scholar]
15. B. Zhu, E. Bedeer, H. H. Nguyen, R. Barton and J. Henry, “Improved soft-k-means clustering algorithm for balancing energy consumption in wireless sensor networks,” IEEE Internet of Things Journal, vol. 8, no. 6, pp. 4868–4881, 2021. [Google Scholar]
16. H. Ali, U. U. Tariq, M. Hussain, L. Lu, J. Panneerselvam et al., “ARSH-FATI: A novel metaheuristic for cluster head selection in wireless sensor networks,” IEEE Systems Journal, vol. 15, no. 2, pp. 2386–2397, 2021. [Google Scholar]
17. Y. Tao, J. Zhang and L. Yang, “An unequal clustering algorithm for wireless sensor networks based on interval type-2 TSK fuzzy logic theory,” IEEE Access, vol. 8, pp. 197173–197183, 2020. [Google Scholar]
18. S. Lata, S. Mehfuz, S. Urooj and F. Alrowais, “Fuzzy clustering algorithm for enhancing reliability and network lifetime of wireless sensor networks,” IEEE Access, vol. 8, pp. 66013–66024, 2020. [Google Scholar]
19. M. A. Aydin, B. Karabekir and A. H. Zaim, “Energy efficient clustering-based mobile routing algorithm on WSNs,” IEEE Access, vol. 9, pp. 89593–89601, 2021. [Google Scholar]
20. Y. Han, G. Li, R. Xu, J. Su, J. Li et al., “Clustering the wireless sensor networks: A meta-heuristic approach,” IEEE Access, vol. 8, pp. 214551–214564, 2020. [Google Scholar]
21. W. Lan, Z. Ye, P. Ruan, J. Liu, P. Yang and X. Yao, “Region-focused memetic algorithms with smart initialisation for real-world large-scale waste collection problems,” in IEEE Transactions on Evolutionary Computation, vol. 1, no. 1, pp. 1–11, 2021. http://dx.doi.org/10.1109/TEVC.2021.3123960. [Google Scholar]
22. Y. Sazaki, A. Primanita, H. Satria and R. Apriliansyah, “A comparison application of the genetic and steepest ascent hill climbing algorithm in the preparation of the crossword puzzle board,” in Proc. 12th Int. Conf. on Telecommunication Systems, Services, and Applications (TSSA), Yogyakarta, Indonesia, pp. 1–5, 2018. [Google Scholar]
23. D. Prabakaran and S. Ramachandran, “Multi-factor authentication for secured financial transactions in cloud environment,” Computers, Materials & Continua, vol. 70, no. 1, pp. 1781–1798, 2022. [Google Scholar]
24. G. S. Walia, P. Singh, M. Singh, M. Abouhawwash and H. J. Park, “Three dimensional optimum node localization in dynamic wireless sensor networks,” Computers, Materials & Continua, vol. 70, no. 1, pp. 305–321, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools