 Open Access
Open Access
ARTICLE
Routing with Cooperative Nodes Using Improved Learning Approaches
1 Department of CSIT, CVR College of Engineering, Telangana, India
2 Department of Computer Science and Engineering, St. Martin’s Engineering College, Secunderabad, Telangana, India
3 Department of Computer Science and Engineering, Dhanalakshmi Srinivasan University, Trichy, Tamilnadu, India
4 CSIT Department, CVR College of Engineering, Hyderabad, India
* Corresponding Author: R. Raja. Email:
Intelligent Automation & Soft Computing 2023, 35(3), 2857-2874. https://doi.org/10.32604/iasc.2023.026153
Received 16 December 2021; Accepted 29 March 2022; Issue published 17 August 2022
Abstract
In IoT, routing among the cooperative nodes plays an incredible role in fulfilling the network requirements and enhancing system performance. The evaluation of optimal routing and related routing parameters over the deployed network environment is challenging. This research concentrates on modelling a memory-based routing model with Stacked Long Short Term Memory (s − LSTM) and Bi-directional Long Short Term Memory (b − LSTM). It is used to hold the routing information and random routing to attain superior performance. The proposed model is trained based on the searching and detection mechanisms to compute the packet delivery ratio (PDR), end-to-end (E2E) delay, throughput, etc. The anticipated s − LSTM and b − LSTM model intends to ensure Quality of Service (QoS) even in changing network topology. The performance of the proposed b − LSTM and s − LSTM is measured by comparing the significance of the model with various prevailing approaches. Sometimes, the performance is measured with Mean Absolute Error (MAE) and Root Mean Square Error (RMSE) for measuring the error rate of the model. The prediction of error rate is made with Learning-based Stochastic Gradient Descent (L − SGD). This gradual gradient descent intends to predict the maximal or minimal error through successive iterations. The simulation is performed in a MATLAB 2020a environment, and the model performance is evaluated with diverse approaches. The anticipated model intends to give superior performance in contrast to prevailing approaches.Keywords
Recently, the Internet of Things (IoT) promotes cooperative communication among the dense network environment, which has captured the attention of researchers [1]. It possesses various advantages like high spectral efficiency, mitigates fading and enhanced transmission capacity in IoT network by spatial diversity [2]. IoT environment’s multi-hop routing with cooperative nodes is the newer area of research where one or more nodes cooperate during data transmission to the next successive hop among the suitable nodes to achieve higher throughput and network lifetime.
Some prevailing cooperative routing algorithm concentrates on transmission power adjustment of nodes to preserve the nodes’ energy. It enhances the energy efficiency to extend network lifetime with adaptive outage routing, minimal energy non-cooperative routing, and shortest path [3]. The shortest path algorithm adopts cooperative transmission cost to attain minimal energy among the cooperative paths. With the shortest path algorithm, the minimal cooperative routing model models the cooperative routing with reduced power consumption by adjusting the hop-by-hop transmission power from the source to destination [4]. In an energy-efficient cooperative routing algorithm, the nodes coordinate packets towards the successive hop with minimal energy non-cooperative path. It is specifically used to combine signal at the receiver to measure the signal-to-noise ratio threshold and reduce the E2E energy consumption [5]. Consider multi-flow cooperative routing algorithm deals with the route selection process and contention avoidance issue over medium access control layer. It promotes routing decision into a transmission-optimization issue among the contention association of multiple links multi-flows [6]. The energy-efficient cooperative routing algorithm must attain reduced total power consumption along with the fulfilment of Quality of Service (QoS) requirements and the probability of destination hop [7]. The minimal selection based forward and decode routing algorithm realizes minimal transmission for all cooperative links over the route as BER is restrictive towards the target. It intends to include relays among the cooperative nodes until the entire link BER performs route construction than the target BER. With the minimal-energy non-cooperative route, the routing model attains a considerable energy saving process compared to non-cooperative multi-hop transmission with probability requirements at the destination side needs to be fulfilled [8]. With the assistance of centralized or distributed power allocation, it predicts the minimal total transmission as the nodes’ probability turn lesser than the target value or destination probability becomes more inferior than the E2E probability.
It is highly complex to adjust the transmission power dynamically over the cooperative nodes in distributed wireless networks [9]. Thus, this research intends to analyze the throughput in direct transmission models with SNR at the receiver level and transmission power. It is observed that it can enhance the signal reception probability successfully and improve throughput [10]. Various existing approaches (in Section 2) identified that the records of the cooperative nodes are not appropriately maintained. As enormous transmission leads to massive data analysis and needs massive space for storage. Sometimes, these sorts of information are lost and lead to computational complexity. The growth of the learning model paves the way to achieve these issues efficiently. The memory management is efficiently performed with the Long-short Term Memory (LSTM), and the model provides suggestion for predicting the active cooperative nodes over the dense IoT environment. Thus, this research concentrates on modelling a routing approach among the cooperative nodes (memory-based and directional) with LSTM with theoretical experimentation. Here, two diverse forms of LSTM is adopted, they are stacked and bi-directional LSTM. It is used to analyze the routing in a random manner using the cooperative nodes. This LSTM model is used for searching and detecting the route to evaluate the PDR, E2E delay, throughput, and lifetime and so on. Thereby, the proposed model fulfils QoS even in the case of changing network topology. Our proposed model considers the Ad-Hoc On Demand Vector (AODV) routing protocol. The model performance is measured with MAE and RMSE for measuring the error rate of the model. The target objective of this research is discussed below: 1) To analyze routing among the cooperative nodes in an IoT environment using AODV routing protocol; 2) To measure the essential routing information among the cooperative nodes in a better manner. Thus, a memory-based Long Short Term Memory of learning approaches; 3) To efficiently fulfil Quality of Service (QoS) with the adoption of bi-directional LSTM even in the rare case of changing network topology; and 4) Evaluate various metrics like Packet Delivery Ratio (PDR), End-to-End (E2E), throughput, network lifetime and error rate using MATLAB simulation environment. The work is structured as: In Section 2, an extensive analysis is done with the various existing routing models in the IoT environment and the issues related to them. In Section 3, the anticipated methodology is discussed using the proposed LSTM model for memory-based and routing-based models. The extensive functionality of the proposed idea is elaborated and ensures the fulfilment of the proposed model. In Section 4, the evaluation metrics and the numerical outcomes are analyzed extensively. In Section 5, the results of the metrics are summarized, and the ideas for future research extensive are given for young researchers.
The proposed model adopts LSTM for handling the issues over cooperative nodes during the preservation of packet information and routing. The cooperative nodes pattern information is attained using the learning models. Several approaches are used in the literature to identify the mobility of the joint nodes. Mahajan et al. [11] discuss the prediction of immediate neighbourhood future typically in the next few seconds over the context of nodes mobility. The evaluation of the neighbourhood node analysis is performed over a massive dataset with Global Positioning System (GPS) data with 703 subjects. The anticipated model is competent in identifying the position with better accuracy. Zhao et al. [12] identify the point-of-interest of the connected nodes using the Markov chain concept. The author also proposes another approach for determining the trajectories of the moving objects. The author adopts the Hidden Markov Model to predict the constant movement of the cooperative nodes indeed of the trajectory pattern slices. Therefore, based on the above discussion, it is known that the apriori contact pattern information is used for data forwarding context, and it is more feasible. Jiang et al. [13] use mobility patterns among the connected nodes, which plays a crucial role in developing productive data forwarding strategies. The learning automata for transmission are discussed by Chai et al. [14]. The learning automata model significantly chooses the target for data transfer based on the data forwarding strategy and opportunistic aggregation. It identifies the vehicles mobility pattern and chooses forwarding path. During tolerance, the routing strategy is anticipated with extensive knowledge of the nodes’ mobility pattern. The dataset with mobile nodes and fixed access points are also considered. The cooperated nodes are connected with an assumption connected to the same access points that outcomes in invalid routing. An extensive analysis of the accessibility of mobile patterns is also presented by [15] in Mobile Ad-Hoc Networks (MANET). Here, mobility metrics are considered to construct a data pattern prediction model via supervised learning. He et al. [16] identifies the variations over the network topology with the NN concept. Some analysis over future research is discussed with crowd sense-data types, data pre-processing, human mobility objects and analysis approaches. Rodrigues et al. [17] discuss diverse relay node selection processes where data forwarding protocols are considered to establish link stability during data forwarding. Kolodner et al. [18] examine nodes stability by participating during routing process. The nodes with least strength than the threshold value are not facilitated to the data forwarding process. Lucas-Simarro et al. [19] discusses the on-demand routing protocol with link stability and considers bandwidth as selection parameters in the relay nodes. It predicts some available slots for linking purpose. An extensive survey on diverse routing protocols determines link stability as a primary factor. Cheng et al. [20] state that the networking region is autonomous and competent in predicting the appropriate communication model. Wu et al. [21] anticipate eliminating connectivity issues with node competency over communication with opportunistic and multi-channel connectivity. The model shows increased network size and not cost-efficient as there is a necessity to include active and passive elements over the multiple communication channels. Baadachen et al. [22] model a community network where the service providers offer service over a certain region. The model needs a specific setup with a prominent infrastructure. Some interoperable wireless networks like JupiterMesh are considered. Wang et al. [23] anticipate a cooperative model with connectivity, which acts as a gateway. Boukerche et al. [24] consider mobile phones as the gateway and Bluetooth profiles as a proxy while communicating with the Bluetooth devices. These routing methods are more feasible and best suited for processing and power constraints [25–31].
An elaborate discussion is made tdo project the significance of the anticipat idea over the IoT environment. The functionality of the cooperative nodes over the IoT environment is discussed, and the primary contribution provided by bi-directional LSTM and stacked LSTM. Both these model plays a substantial role in the IoT environment, and the analysis is done with MATLAB simulation environment. The outcomes of the approach are compared with various existing methods like Linear Regression (LR), Support Vector Machine (SVM), Decision Tree (DT), k-Nearest Neighbour (k-NN), and Artificial Neural Networks (ANN), respectively [32–35].
Let the nodes over the network possess fixed transmission power, and the entire link establishes communication in a bi-directional manner, i.e., i → j; and j → i. The channel among the sender ‘i’ and receiver ‘j’ is provided with a delay ‘θ’ and attenuation is given as ∝ i,j which is expressed as
In cooperative node-based transmission, ‘x’ is a sender, ‘y’ is cooperative node, and ‘z’ is the receiver. The node ‘z’ s receives both the signals from the ‘x’ s and cooperative node ‘y’ where the packets are generated from ‘x’. In a simplified manner, the nodes consider both ‘x’ and ‘y’ for transmitting packets with a transmission power of PT. The receiver signal is modelled as in Eq. (2):
3.2 Cooperative Route Selection Strategy
Generally, AODV is a reactive routing protocol that initiates route in a dynamic manner. Here, a productive solution with the trust value of the nodes and the energy of cooperative nodes are evaluated. In general, cooperative routing is performed in two major phases: 1) Route discovery-based on best route prediction; and 2) Route maintenance process
3.2.1 Route Discovery-based on Best Route Prediction
The source needs to generate Route Request and forwards based on the information from the routing table. The destination computes the average trust establishment value, and the response is forwarded to the packet generator (source). It is expressed as in Eq. (3):
Here, ‘N’ is several hops in the routing table, and
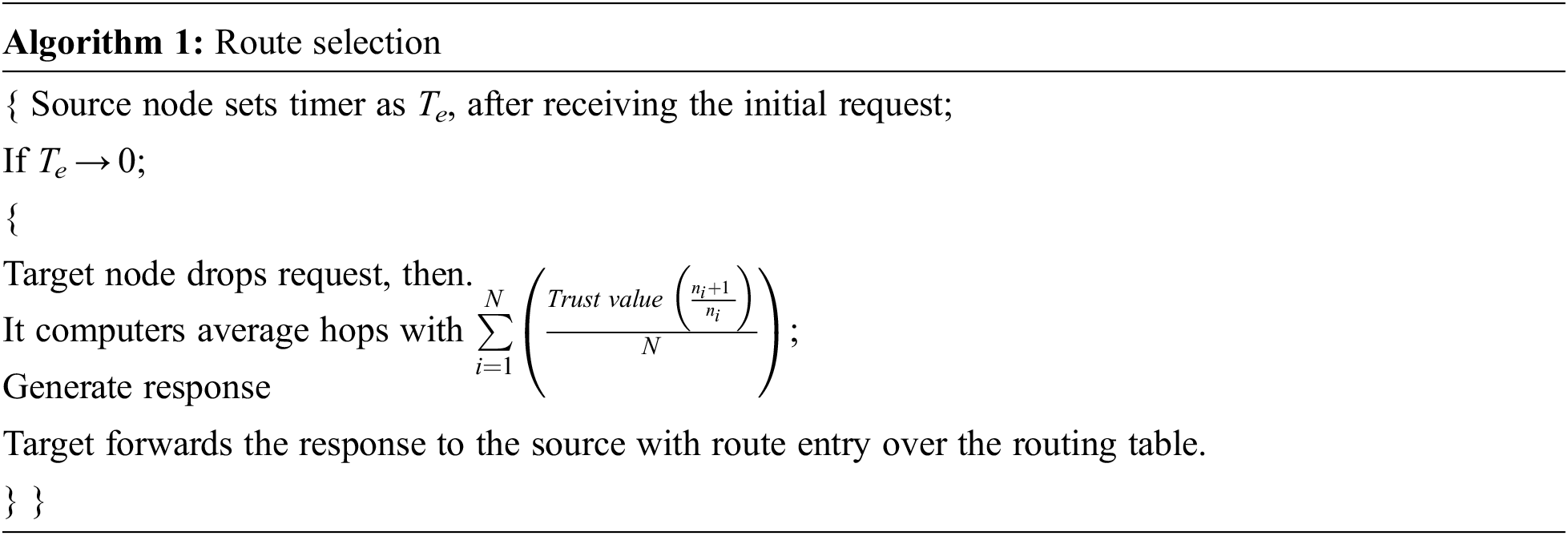
3.2.2 Route Maintenance Process
The route maintenance process is used explicitly for two diverse purposes, i.e., when the links are broken among the cooperative nodes due to mobility factor and the node’s behaviour’s trust value. In another situation, when the connection among the cooperative node is wrecked or the route lifetime gets expires, then an error notification is transferred to the source. The cooperative nodes’ trust value is reduced to less than 0.5, and the information is transferred to the source. Based on this, the source needs to discover a newer route to the target using the cooperative nodes (See Fig. 1).
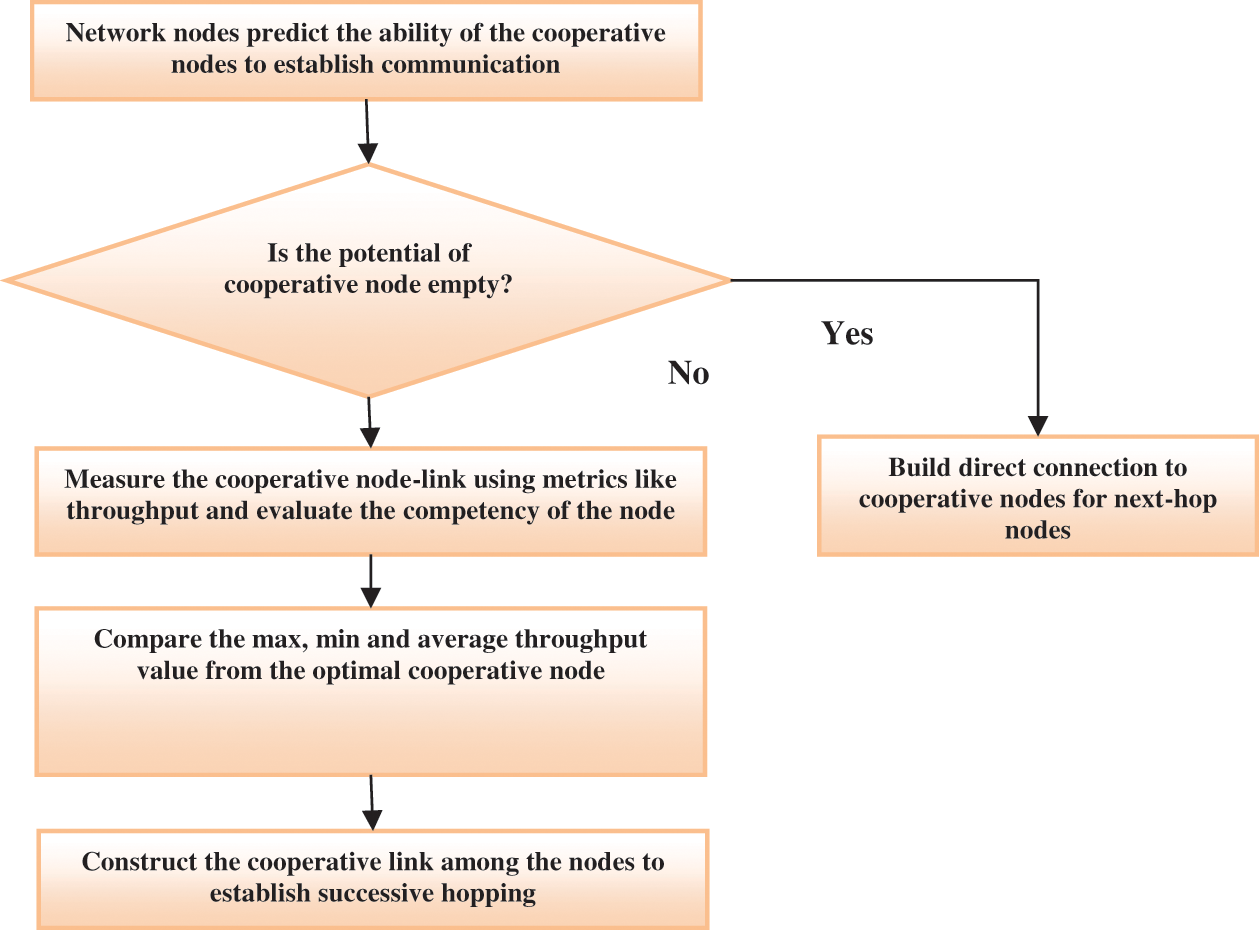
Figure 1: Cooperative node selection process
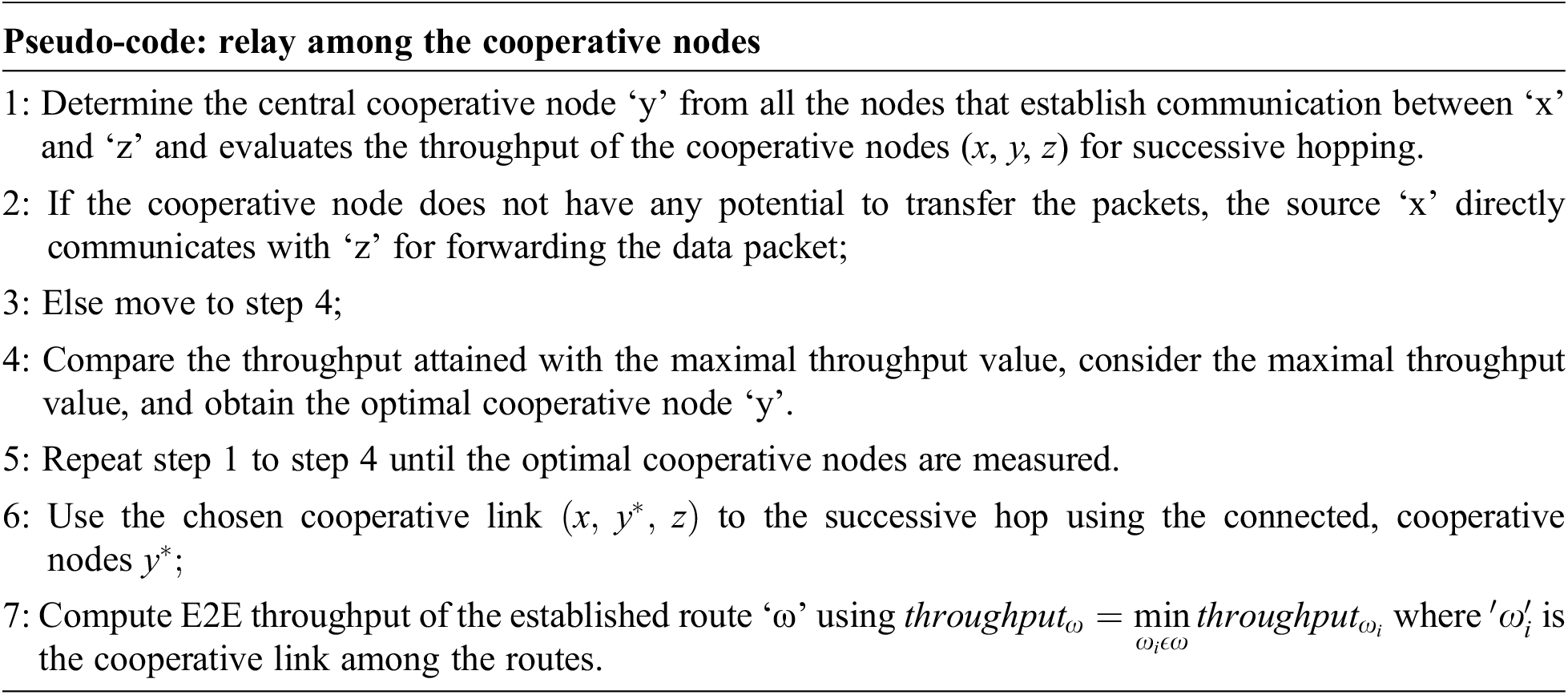
3.3 Relaying among the Cooperative Nodes
When a route selection is performed with the available cluster model, AODV starts transferring the packets among the cooperative nodes. The relay among the cooperative nodes in the IoT environment executes a cooperative relay selection process to establish the link for successive hops to reach the destination. The pseudo-code for this process is explained below:
3.4 Bi-directional Long Short Term Memory (b − LSTM)
In the learning model, some sequential neural network models like Recurrent Neural Networks (RNN), Long Short Term Memory (LSTM), and Gated Recurrent Unit (GRU) are used for analyzing and capturing the long-distance dependencies among the sequential information. Here, LSTM is considered for analyzing the routing information among the cooperative nodes to reduce the complexity and preserves essential packet information for subsequent processing over the dense IoT network model. In the conventional LSTM, the network model encounters some biasing issues and therefore, to overcome them, the proposed model considers stacked LSTM to provide promising outcomes.
The bi-directional LSTM architecture is composed of certain units known as memory blocks. These blocks comprise memory cells with self-connection (store/remember), the temporal network state, and multiplicative units termed as gates to monitor the flow of routing information over the network model, as in Fig. 2. The memory block comprises input gate, output gate and forgets gate to handle the flow of activations (input) over the memory cells, cell activations’ output flow, and scales the internal cell state via the bidirectional connection. This model is used for learning the precise timing information of the packet transmission information-based outputs. The activation and the stochastic gradient computation are performed to extract the error gradients used to train the network model. The data forwarding pass is evaluated with a packet length ‘T’ over an input sequence ‘x’ and recursively incrementally applies the updated equation. Similarly, the backwards pass (response to a request) is evaluated with t = T and computes the unit derivatives in a decremented manner. The weighted derivation based on packet transmission time step is modelled as in Eq. (4):
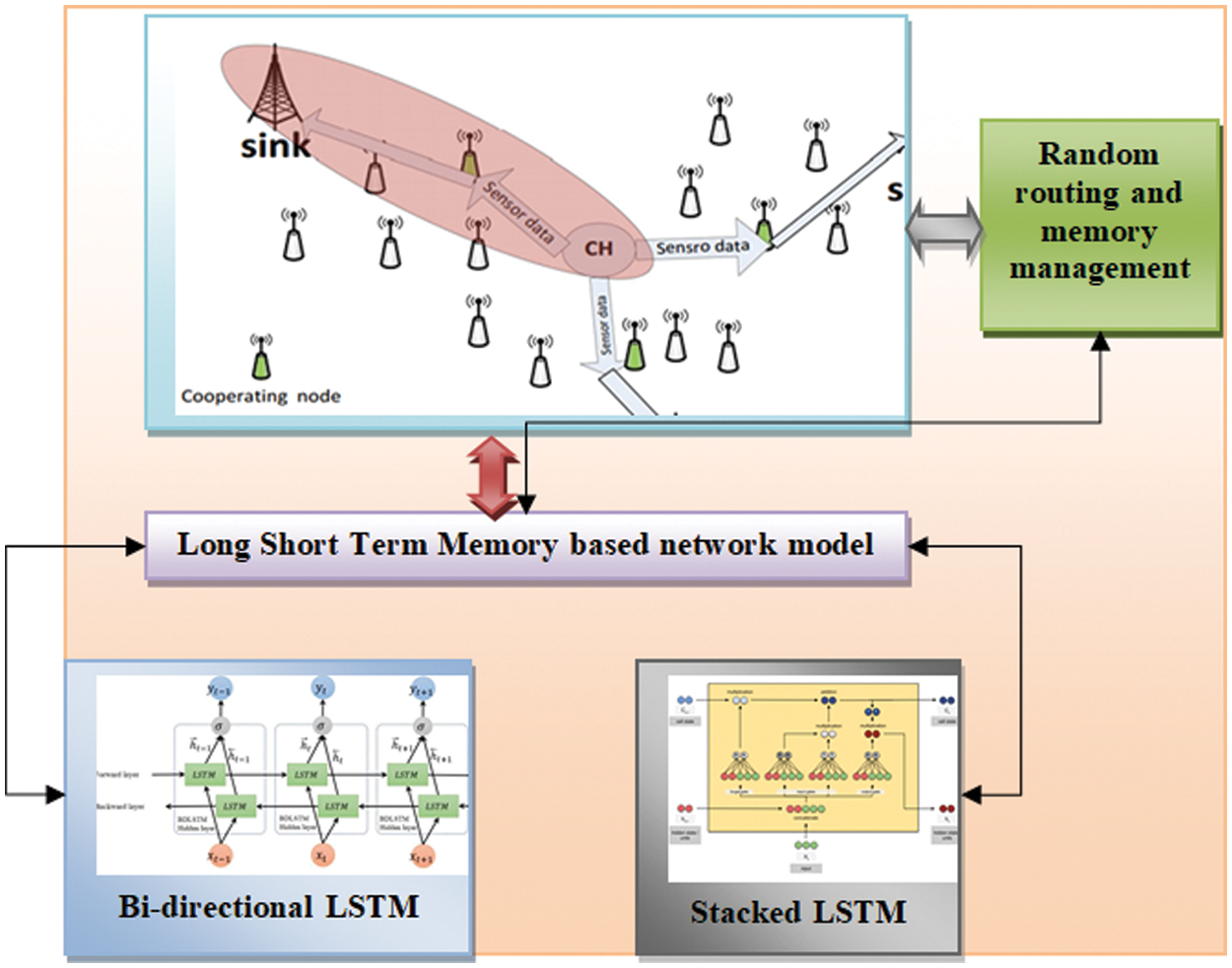
Figure 2: Generic view of the proposed model
Here, ‘O’ is objective function adopted for training purpose. The forward passes of the input, output, and forget gates are expressed in Eqs. (5)–(7):
The cell output (forward pass) of the bi-directional LSTM is expressed as in Eq. (8):
In backward pass, the input, output and the forget gates are expressed as in Eqs. (9)–(11):
The cell output (backward pass) of the bi-directional LSTM is expressed as in Eq. (12):
Here, wij is the weight of the connected nodes from
3.5 Stacked Long Short Term Memory for Cooperative Nodes Information Management
The stacked LSTM is efficiently used for resolving the gradient explosion with the set of memory units as in Fig. 2. It facilitates the network to learn the trust value of cooperative neighbourhood nodes and when to forget the prior network information of the memory unit (it holds the cooperative node details) and provides the fact regarding when to update the memory unit with further new information. The memory unit preserves the details of all the historical network information (pattern analysis, traffic flow, source and destination nodes, related information, cooperative node details, previous network connection and details of further connection establishment). All three gates manage it. This model is well suited for incoming data analysis and previously available network dataset, which holds activity logs, network records, and sensor data). The relationship and the dependencies among the incoming data are analyzed with time-steps. To perform this function, any network dataset can be considered. The dataset is partitioned into training and validation set with (Dregular data (Abnormal and Dvalid) and holds some abnormal data (Dabnormal). In the real-time IoT environment, anomalous samples are relatively lesser in number. The stacked LSTM model predominantly uses regular data for the training of hyper-parameter determined by the validation set. The prediction outcomes of the normal and abnormal data are attained concurrently. The difference between the real and predicted data is made, and the errors are identified. Consider error at every point in the test samples as the attributes of those error dataset. Here, the error dataset is partitioned into a training and testing set. The labels specify ‘0’ as normal network flow without any error or interruption, and ‘1’ specify the abnormal functionality over the network to identify the route and fail to provide the prior routing details. The fault or error over the incoming data flow is subjected to the Gaussian distribution. However, the storage assumptions are extremely efficient and provide robust outcomes. Here, Gaussian probability distribution is used to identify the attributes in the presence of a certain class label. It is expressed as p(x|y = 1) where ‘x’ and ‘y’ specifies the samples and corresponding labels. The LSTM generated sequence vector and used as an input to the successive layers of LSTM. The previous time step feedback is used to capture the routing details (from the memory)/network patterns. The dropout layer of the network excludes 5% of neurons to avoid the under-fitting and over-fitting issues. The proposed stacked LSTM model ingests various network variables like routing information, source_ID, destination_ID, packet information, file formats, routing protocol information, network pattern analysis, traffic analysis, neighbourhood connectivity, cooperative nodes movement, trust value and so on.
The model extracts the hidden patterns from the available variables and efficiently identifies the routing establishment factors. The proposed stacked model has the competency of dealing with long and short term dependency based on the network lifetime (validate the active and passive nodes over the network). The convergence rate is based on the input it, output ot, and forget ft gate. It is expressed as in Eqs. (13)–(17):
Here, it is input vector; g is activation function; W is a weighted vector, and Ct is a memory cell. The generic view of the anticipated model is shown in Fig. 2.
The proposed model is implemented, and the outcomes of the proposed idea for efficient routing over IoT are discussed in this section. The simulation is done in a MATLAB environment to measure the changing topologies and analyze the routing data. The network functionality is calculated using various standard routing algorithms like Ad-Hoc On Demand Vector (AODV), Dynamic Source Routing (DSR), Destination Sequenced Distance Vector Routing (DSDV), and Optimized Link State Routing (OLSR) to evaluate the delay, PDR, and throughput. Some other parameters like node expiry time, buffer time, buffer size, threshold measure, packet dropping and packet drop rates are evaluated. The estimation with these protocols helps predict the PDR, throughput, and delay, which is best suited to bi-directional and stacked LSTM. The parameter setup shows propagation loss model, Constant Bit Rate (CBR) traffic type, UDP protocol, random model mobility, 64 bytes packet size, Carrier-Snense Multiple Access with Collision Avoidance (CSMA/CA) media access, 1000 s execution time, pause time is 0, setting time is 50 s, and 7.5 dB.
The network size relies on the total nodes over the network, commonly known as network density. It shows a direct effect on PDR, throughput, and E2E delay over the denser IoT network environment, which leads to re-transmission, signal interference, and congestion. Here, the nodes density and the related information are provided as the input to the stacked-LSTM and need to observe the network response and preserves all the essential data related to PDR, throughput, and E2E delay. Density ranges from 5 to 100 nodes from source to cooperative nodes to destination.
The transmission speeds among the cooperative nodes are based on the upper-velocity limit to the nodes movement. It shows some consequences over the QoS. When the speed varies (low (not below 1 MPs) and high (not higher than 100 MPs)), then it tends to show some negative effect over the delay, PDR, and throughput.
The physical coverage region of the IoT network is considered in both ‘x’ and ‘y’ coordinates and represents in meter square. It shows a tremendous impact on QoS metrics as the nodes scatter far away from one another. Sometimes it leads to node congestion, delay, PDR, and throughput.
4.4 Performance Evaluation Metrics
Some evaluation metrics like E2E delay, throughput, and PDR are evaluated. The results are reviewed with changing network topologies and compared with various existing approaches.
The time consumed by the packets to reach the destination using cooperative nodes is measured as E2E delay. It is depicted as the sum of delays like propagation and transfers delay, queuing delays, re-transmission delay, request processing delay and buffering delay while predicting the route discovery. It is the average sum of the difference between the packet received and the time of packet is sent. It measures the protocol’s ability to communicate among the nodes indeed of media access mode and noise profile. Here, the delay is measured in seconds and calculated in Eq. (18):
It is the average data rate of the packet received at destination nodes. It is measured as the channel bandwidth (kbps). Here, the bytes are converted to bit. It is expressed as in Eq. (19):
It is the measure of resourceful data delivery at the destination. It is also adopted to measure network efficiency. When PDR is lower, it leads congestion environment due to incomplete/re-transmission data transmission. It is expressed as in Eq. (20):
This work automates various parameters for higher performance in an IoT network environment. This work intends to perform parameter automation and QoS metric enhancement using learning approaches. For this purpose, some parameters like upper bounds, drop rates, and the threshold is chosen and automated. The parameter ranges are manually selected from the prediction results and trained with DL algorithms. Automation is a complete task and needs further explanation.
The network nodes have queuing buffer that maintains packets while processing for routing purpose. When the network modes transfer the higher rate packets and the processing, and it consume a long time before the buffer overflow occurs owing to congestion. It leads to packet loss before queuing. The maximal node limit is specified using routing protocol, i.e., maximum buffer limit. It is mathematically expressed as in Eq. (21):
Here, Buffersize is the buffer capacity, Bufferlength is the maximum buffer limit during the routing process, Bufferpackets is the number of packets occupied already.
When the packet reaches the intermediate node, it is queued over the node buffer. It needs to wait for the processing of outstanding time. The packets are enabled to wait for maximum buffer time; later, the packets are dropped for re-transmission. It is also known as queue buffering or waiting time, as it is accountable for queuing delays. When the packets wait over the buffer for a longer time due to congestion, it leads to the further worst situation (DoS or packet drop). It is expressed as in Eq. (22):
Here, TAwaiting is residual time; Tmax is total allowed arrival time; Tarrival is the arrival time of packets, and TCurrent is the time during the residual time computed.
4.4.6 Cooperative Nodes-based Route Discovery
The sender pretends to transfer the packet via the cooperative nodes towards the destination or the number of times the target performs single or multiple attempts to reach the destination. When the cooperative nodes do not provide any route reply with the specified time, the source needs to replay waiting for a specific time and re-transmits it. It facilitates re-transmission and leads to congestion due to high network density. In an IoT environment, the number of re-transmission is enabled for a fixed set of time. It tries to re-transmit the copy of transmitted packets, and it is expressed in Eq. (23):
4.4.7 Number of Hops Between the Cooperative Nodes
The number of hops (cooperative nodes), i.e., the packets are dispatched from the sender. The hopping among the cooperative nodes is maintained by the header incrementally from one node to another. When the packet consumes more time during data transmission, it leads to higher bandwidth consumption and outcomes in congestion. It is mathematically expressed as in Eq. (24):
When the packets start moving over the network among the cooperative nodes to reach the destination and remain over there for a certain time, it is termed packet expiry time. It needs to maintain by the routing protocol, i.e., the packet leaves and the time keeps on decrementing until it reaches the destination. It is mathematically expressed as in Eq. (25):
Here, Texpiry is packet expiry time; Tstart is when packets commence; TTTL is the total time of network packet; TCurrent is the current time of the packet. The performance of the anticipated model is quantitatively assessed with Mean Square Error (MSE). It is used for evaluating the prediction accuracy with scale-dependent metrics. It shows the difference among the predicted and the actual values using the average sum of squared errors:
Here, yi is the observed value,
Tab. 1 depicts E2E delay computation among the cooperative nodes, and evaluation is done with various other routing protocols like AODV, OLSR, DSDV, DSR, and AERBA-AODV. Parameters like node density and speed analyzed with three different stages like Dmin, Dmax and Dave. Here, the delay analyzed with the execution of the AODV routing protocol is 2.40, 5.6, and 3.40, respectively. The speed measured with AODV is 2.40, 7.3, and 4.35 (See Figs. 3a and 3b). Tab. 1 depicts the PDR computation among the cooperative nodes based on threshold measure (Thresholdmin, Thresholdmax, and Thresholdavg). The threshold value based on speed parameter for AODV is 15.08, 22.90, and 19.5 and node density is 5.5, 48.05, and 25.45, respectively (See Figs. 4a and 4b). Tab. 1 depicts the PDR computation among the cooperative nodes based on threshold measure (Pmin, Pmax and Paving). The threshold value based on speed parameter for AODV is 68.35, 95.95, and 83.66 and node density is 80.7, 85.23, and 82.93, respectively (See Figs. 5a and 5b). Tab. 2 depicts RMSE and MAE computation among the cooperative nodes. Here, RMSE (see Fig. 6) for the delay, PDR and throughput are 0.28, 0.20 and 0.12 and MAE (See Fig. 7) of delay, PDR, and throughput of 0.22 0.13, and 0.10 respectively.
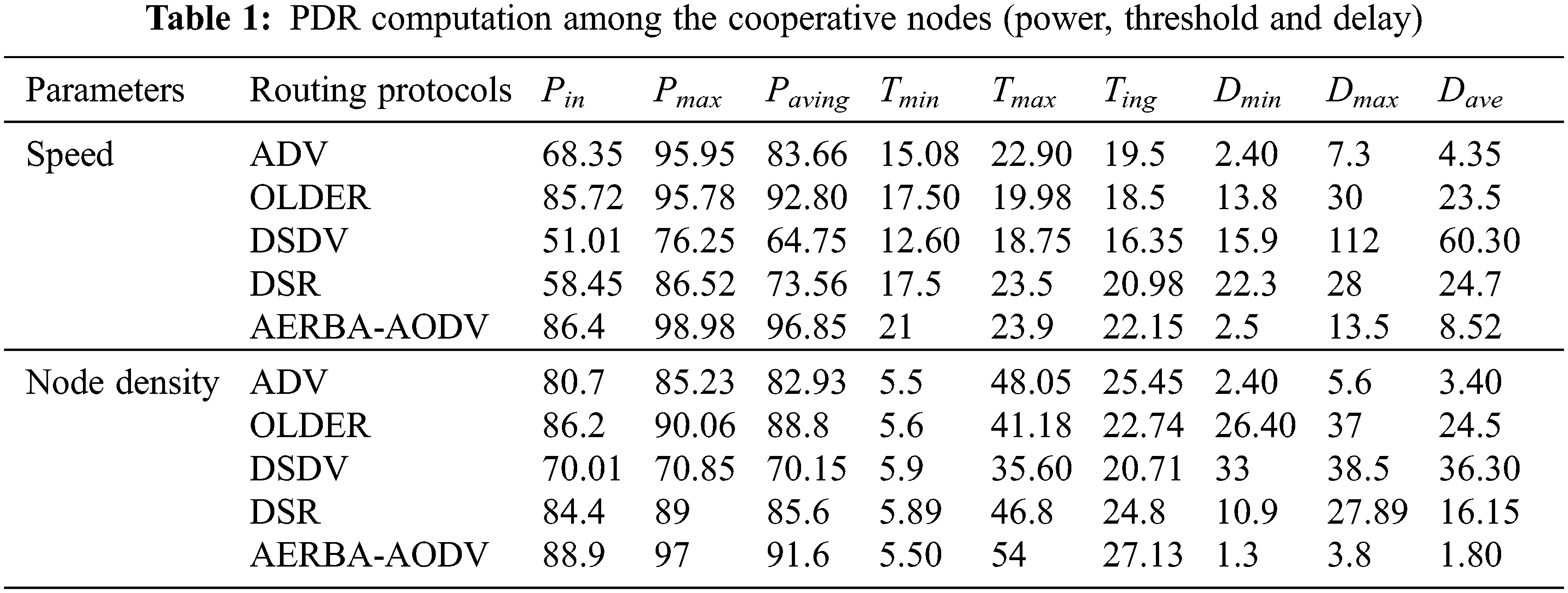
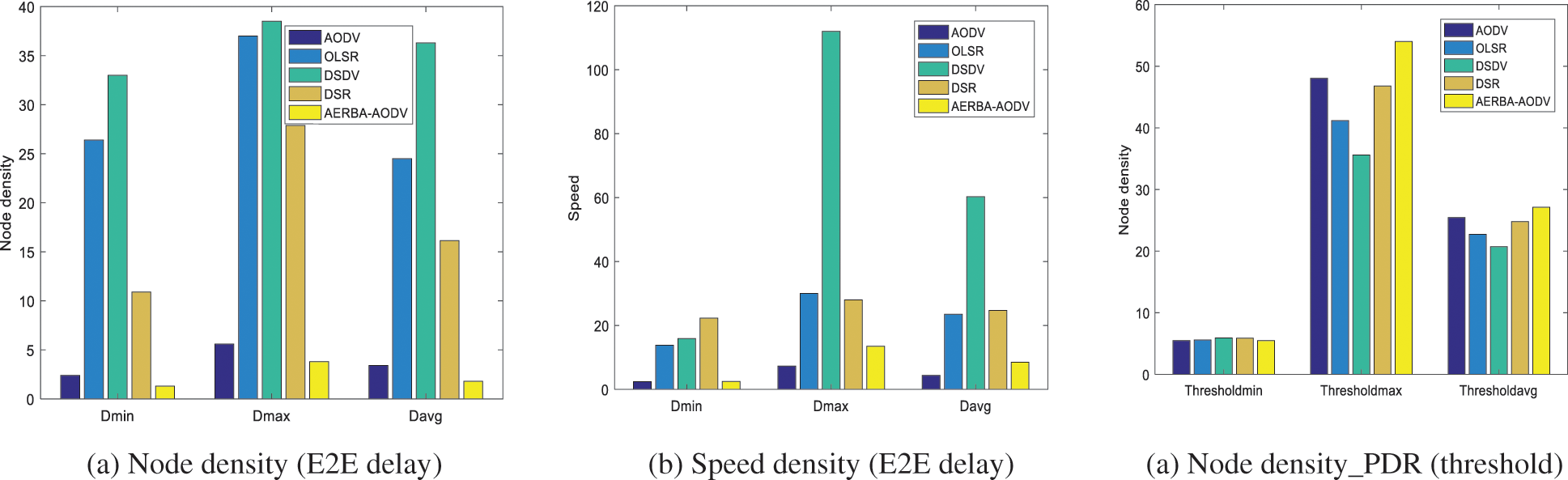
Figure 3: (a) Node density (E2E delay) (b) Speed density (E2E delay) (a) Node density_PDR (threshold)
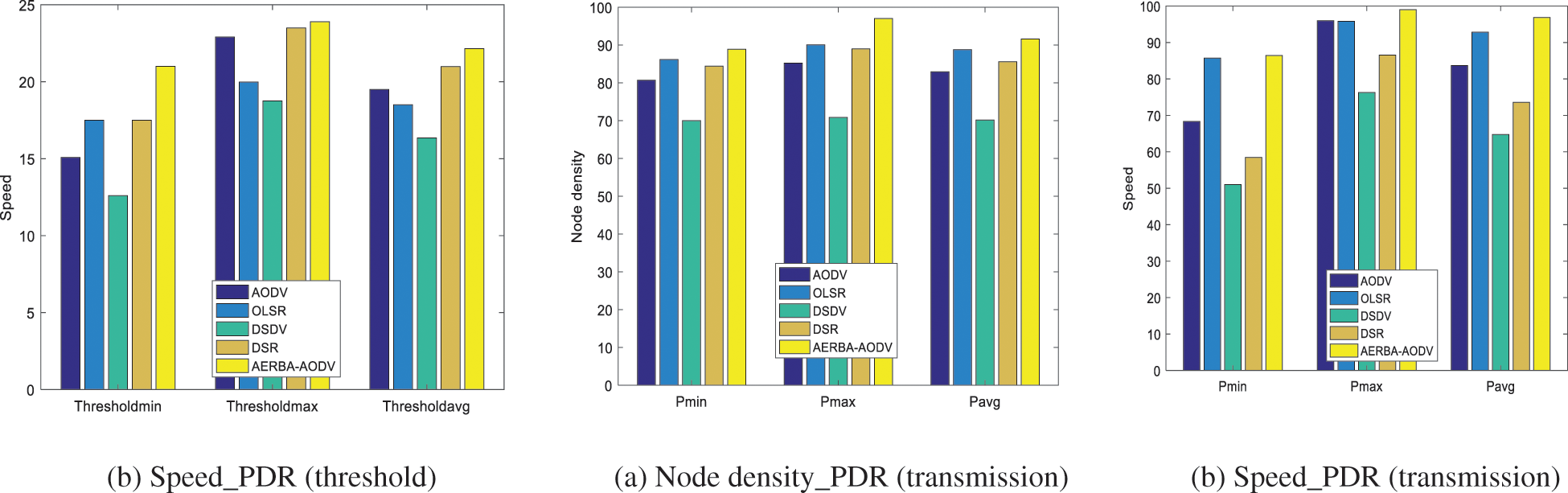
Figure 4: (a) Node density_PDR (transmission) (b) Speed_PDR (threshold) (b) Speed_PDR (transmission)
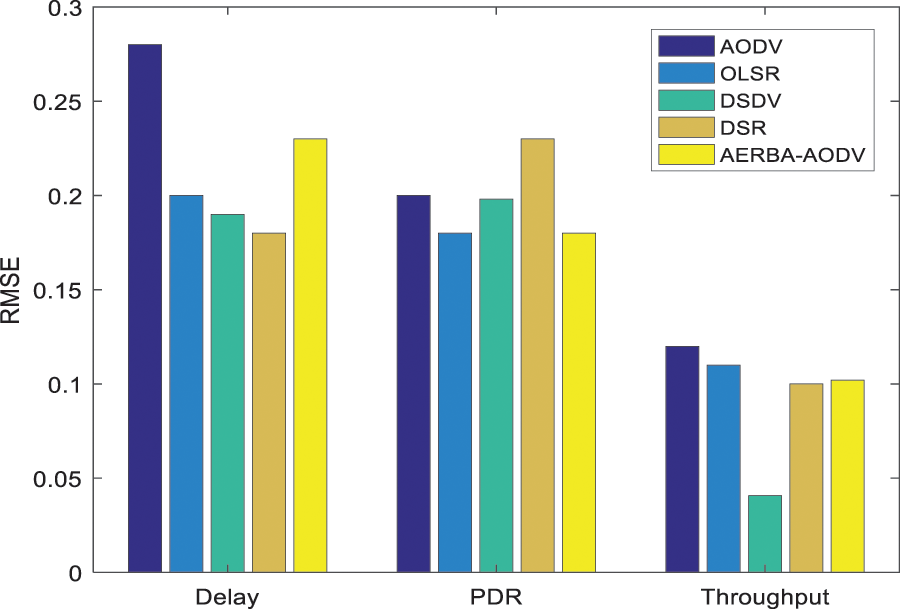
Figure 5: RMSE computation
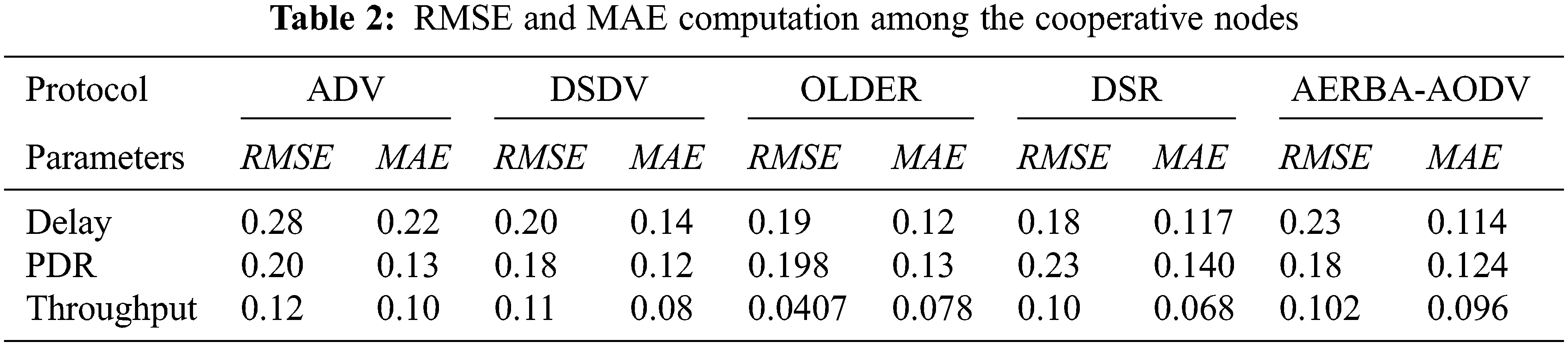
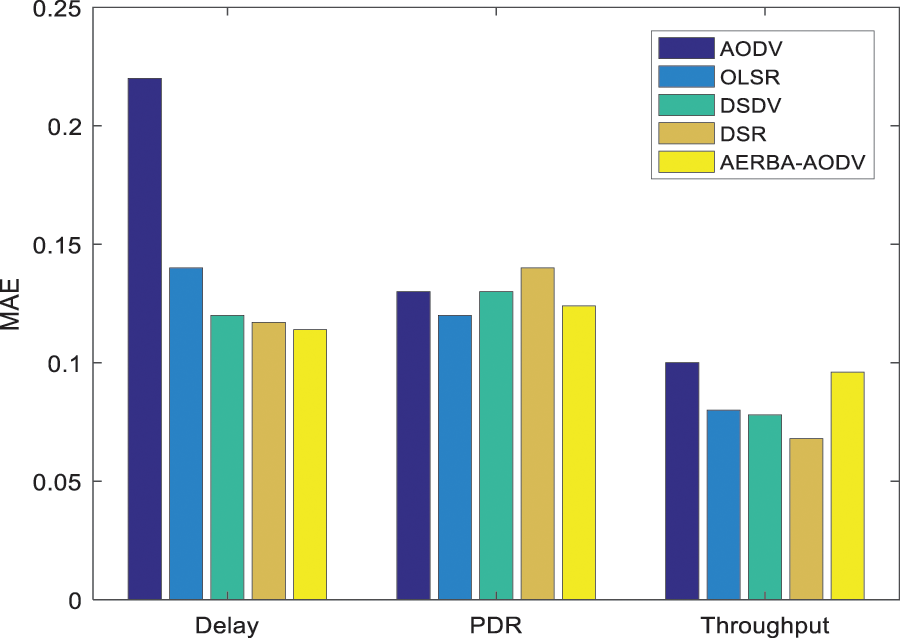
Figure 6: MAE computation

Figure 7: Throughput comparison of proposed vs. existing approaches
Tab. 3 shows the comparison of throughput of proposed vs. Existing approaches. The proposed LSTM shows 0.2015 for AODV, which is comparatively higher than other approaches. The evaluation is done among LR, SVM, ANN, k-NN, DT and LSTM. The throughput value of these approaches w.r.t. AODV is 0.1280, 0.1303, 0.1326, 0.1506, and 0.1375 respectively (See Fig. 7). Tab. 4 depicts the comparison of PDR over other approaches. The delay of LSTM is lesser than LR, SVM, ANN, k-NN, and DT, respectively. The delay analyzed with LSTM is 0.1568 and other models are 0.3099, 0.3278, 0.2786, 0.2786, and 0.2770 respectively (See Fig. 8). Tab. 4 depicts the PDR comparison of the proposed vs. Existing approaches. The delivery ratio of LSTM is 0.3567 and other models are 0.1986, 0.1985, 0.2615, 0.2280, and 0.2567 respectively (See Fig. 9). From the observation, it is known that the model works efficiently than the prevailing approaches with the adoption of the AODV routing protocol.
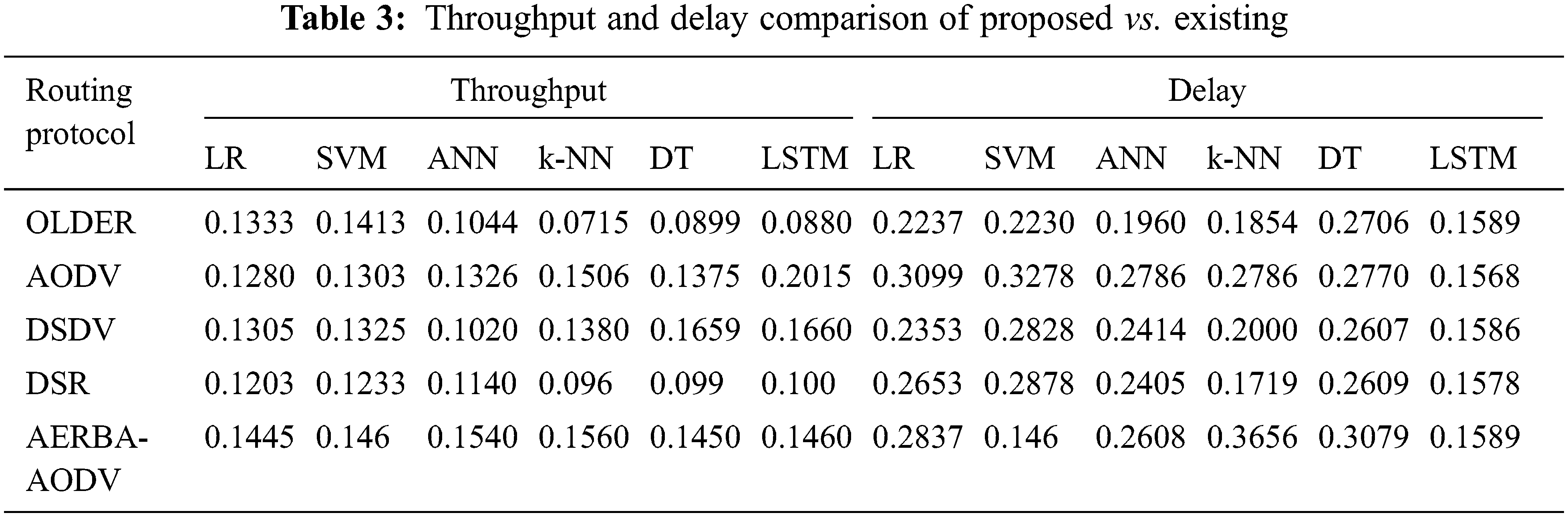
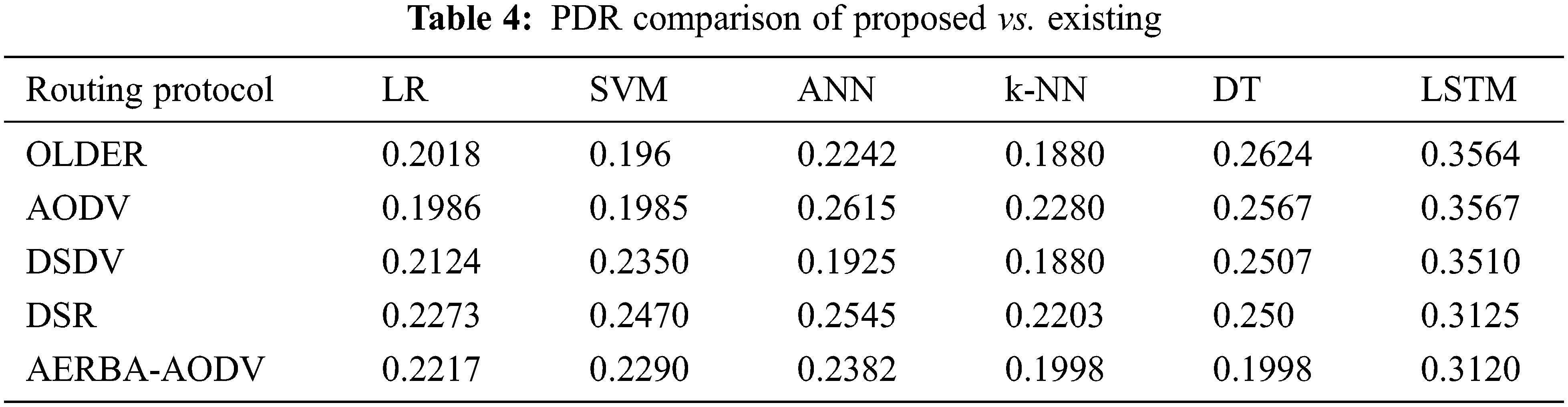
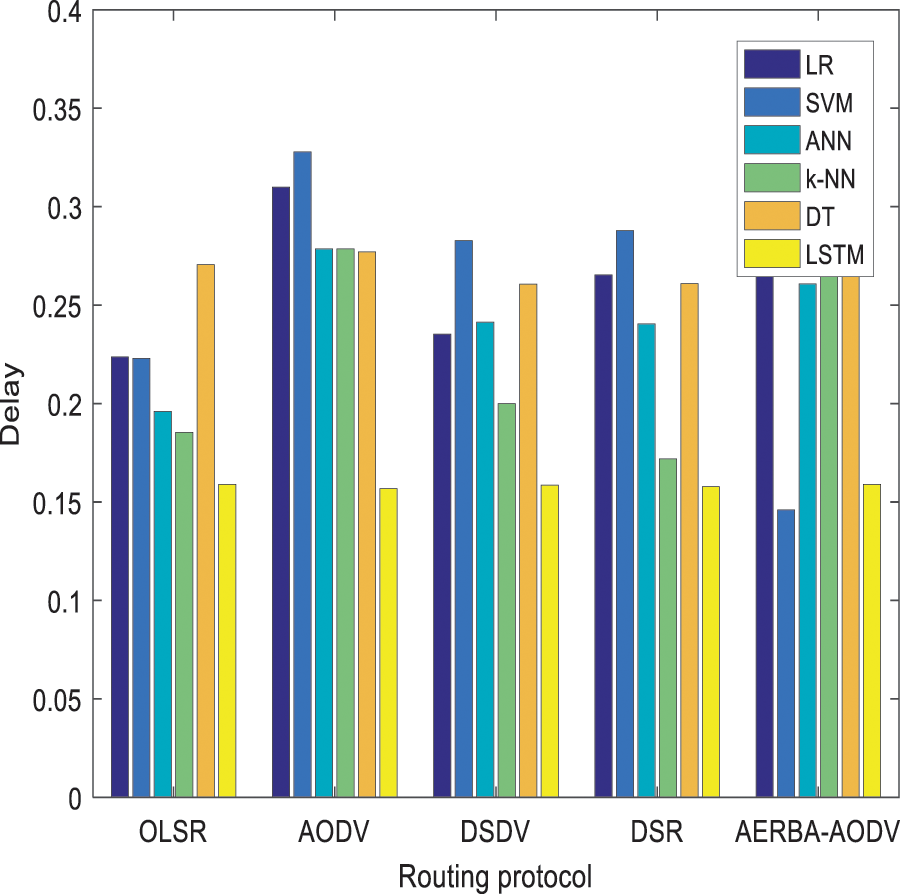
Figure 8: E2E delay comparison of proposed vs. existing
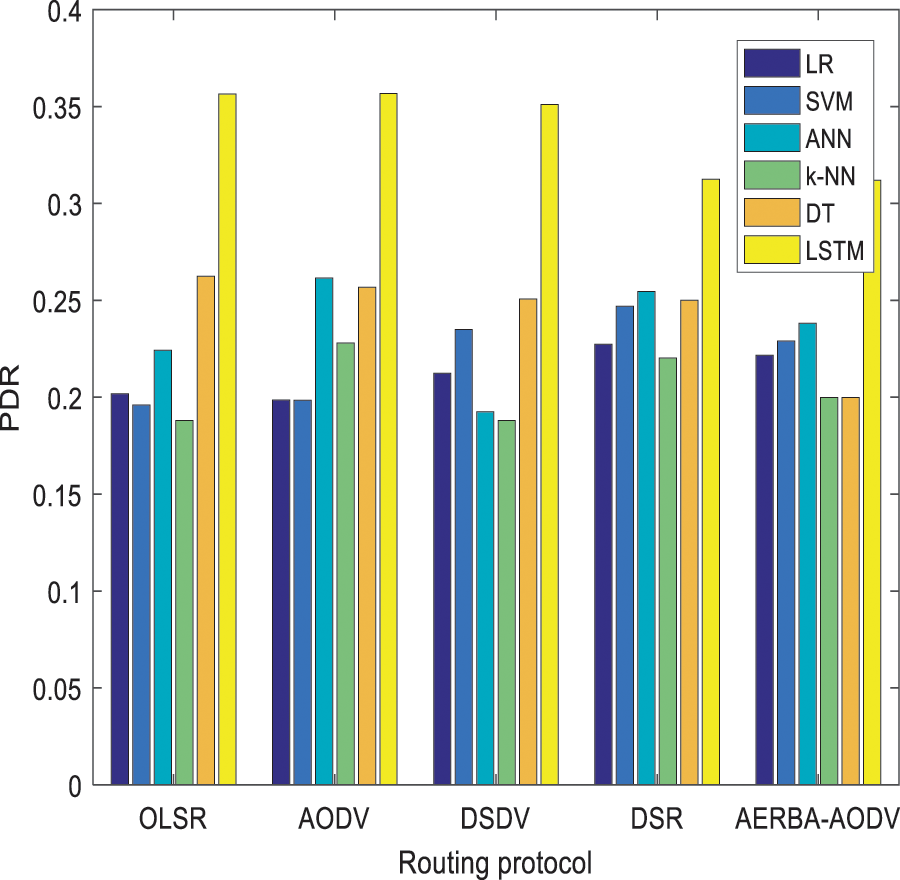
Figure 9: PDR comparison of proposed vs. existing approaches
This work provides an extensive analysis on routing information of the cooperative node over the IoT environment. With the advent of learning approaches over multiple fields, this work uses a learning model to handle real-time issues. Here, a novel s − LSTM is proposed to handle the routing information. Bi-direction (b − LSTM) is used to perform random routing and these method works efficiently to fulfil the research objectives. The functionality of the proposed stacked LSTM and bi-directional LSTM is analyzed using metrics like PDR, delay, throughput, RMSE and MAE. The error rate of the model is reduced with better convergence. The model intends to avoid over-fitting issues and reduces computational complexity. The theoretical evaluation of the model is slightly tougher; however, the model efficiently achieves the target outcome. Here, the AODV routing protocol is adopted to validate the network performance. The throughput attained with the proposed model is 0.2015, PDR is 0.3567, and delay is 0.1568. The model gives better outcomes in preserving the routing information and the decision to perform random routing with the analysis of active and passive nodes over the network. In future, the LSTM model is cooperated with various other network models to makes the training process more straightforward. Also, different optimization approaches are available to derive the global solution of the network model.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. C. Ma, W. Liang and M. Zheng, “Set-covering-based algorithm for delay constrained relay node placement in wireless sensor networks,” in Proc. IEEE Int. Conf. on Computing’16, Kuala Lumpur, Malaysia, pp. 1–6, 2016. [Google Scholar]
2. M. E. Haque and M. A. Hannan, “Toward optimum topology protocol in health monitoring,” in Performability in Internet of Things, Cham: Springer, pp. 81–109, 2018. [Google Scholar]
3. C. Ma, W. Liang, M. Zheng and H. Sharif, “A connectivity-aware approximation algorithm for relay node placement in wireless sensor networks,” IEEE Sensors Journal, vol. 16, no. 2, pp. 515–528, 2016. [Google Scholar]
4. B. Yuan, H. Chen and X. Yao, “Optimal relay placement for lifetime maximization in wireless underground sensor networks,” Information Sciences, vol. 418–419, pp. 463–479, 2017. [Google Scholar]
5. A. Nigam and Y. K. Agarwal, “Optimal relay node placement in delay constrained wireless sensor network design,” European Journal of Operational Research, vol. 233, no. 1, pp. 220–233, 2014. [Google Scholar]
6. C. Ma, W. Liang, M. Zheng and B. Yang, “Relay node placement in wireless sensor networks concerning delay and reliability requirements,” IEEE Systems Journal, vol. 13, no. 3, pp. 2570–2581, 2018. [Google Scholar]
7. C. Li, Z. Chen, Y. Wang, Y. Yao and B. Xia, “Outage analysis of the full-duplex decode-and-forward two-way relay system,” IEEE Transactions on Vehicular Technology, vol. 66, no. 5, pp. 4073–4086, 2017. [Google Scholar]
8. C. Zhu, J. J. P. C. Rodrigues, V. C. M. Leung, L. Shu and L. T. Yang, “Trust-based communication for the industrial internet of things,” IEEE Communications Magazine, vol. 56, no. 2, pp. 16–22, 2018. [Google Scholar]
9. J. S. Kumar and D. R. Patel, “A survey on internet of things: Security and privacy issues,” International Journal of Computer Applications, vol. 90, no. 11, pp. 20–26, 2014. [Google Scholar]
10. J. Ren, H. Guo, C. Xu and Y. Zhang, “Serving at the edge: A scalable IoT architecture based on transparent computing,” IEEE Network, vol. 31, no. 5, pp. 96–105, 2017. [Google Scholar]
11. P. Mahajan and A. Sachdeva, “A study of encryption algorithms AES, DES and RSA for security,” Global Journal of Computer Science and Technology, vol. 13, no. 15, pp. 15–22, 2013. [Google Scholar]
12. Z. Zhao, D. Gong, B. Lu, F. Liu and C. Zhang, “SDN-based double hopping communication against sniffer attack,” Mathematical Problems in Engineering, vol. 2016, pp. 1–13, 2016. [Google Scholar]
13. F. Jiang, C. Song, H. Xun and Z. Xu, “Combat-sniff: A comprehensive countermeasure to resist data plane eavesdropping in software-defined networks,” American Journal of Networks and Communications, vol. 5, no. 2, pp. 27–34, 2016. [Google Scholar]
14. R. Chai, H. Li, F. Meng and Q. Chen, “Energy consumption optimization-based joint route selection and flow allocation algorithm for software-defined networking,” Science China Information Sciences, vol. 60, no. 4, vol. 040306, pp. 1–14, 2017. [Google Scholar]
15. A. Whitmore, A. Agarwal and L. Da Xu, “The Internet of Things–a survey of topics and trends,” Information Systems Frontiers, vol. 17, no. 2, pp. 261–274, 2015. [Google Scholar]
16. D. He, C. Chen, S. Chan, J. Bu and L. T. Yang, “Security analysis and improvement of a secure and distributed reprogramming protocol for wireless sensor networks,” IEEE Transactions on Industrial Electronics, vol. 60, no. 11, pp. 5348–5354, 2013. [Google Scholar]
17. T. G. Rodrigues, K. Suto, H. Nishiyama and N. Kato, “Hybrid method for minimizing service delay in edge cloud computing through VM migration and transmission power control, ” IEEE Transactions on Computers, vol. 66, no. 5, pp. 810–819, 2017. [Google Scholar]
18. E. K. Kolodner, A. Shulman-Peleg, D. Naor, P. Brand, P. Dao et al., “Data-intensive storage services on clouds: Limitations, challenges and enablers,” In: D. Petcu and J. L. Vazquez-Poletti (Eds.) European Research Activities in Cloud Computing, Cambridge Scholars Publishing, United Kingdom, vol. 17, no. 13, pp. 68–96, 2012. [Google Scholar]
19. J. L. Lucas-Simarro, R. Moreno-Vozmediano, R. S. Montero and I. M. Llorente, “Scheduling strategies for optimal service deployment across multiple clouds,” Future Generation Computer Systems, vol. 29, no. 6, pp. 1431–1441, 2013. [Google Scholar]
20. X. Cheng and S. Deng, Research on Service Deployment for Edge Oriented Computing, (in ChineseHangzhou, China: Zhejiang University, Work Rep. 201801, 2018. [Google Scholar]
21. Z. Wu, Z. Lu, P. C. K. Hung, S. C. Huang, Y. Tong et al., “Qamec: A QoS-driven IoVs application optimizing deployment scheme in multimedia edge clouds,” Future Generation Computer Systems, vol. 92, pp. 17–28, 2019. [Google Scholar]
22. A. Baadachen and A. AliBelmehdi, “Fighting against packet dropping misbehaviour in multi-hop wireless ad hoc networks,” Journal of Network and Computer Applications, vol. 35, no. 3, pp. 1130–1139, 2012. [Google Scholar]
23. J. Wang, Y. Liu and Y. Jiao, “Building a trusted route in mobile ad-hoc networks considering communication reliability and path length,” Journal of Network and Computer Applications, vol. 34, no. 4, pp. 1138–1149, 2011. [Google Scholar]
24. A. Boukerche, B. Turgut, N. Aydin, M. Z. Ahmad, L. Bölöni et al., “Routing protocols in ad hoc networks: A survey,” Computer Networks, vol. 55, no. 13, pp. 3032–3080, 2011. [Google Scholar]
25. E. Huang, W. Hu, J. Crowcroft and I. Wassell, “Towards commercial mobile ad hoc network applications: A radio dispatch system,” in Proc. of MobiHoc’05, Illinois, USA, pp. 355–365, 2015. [Google Scholar]
26. I. U. Khan, I. M. Qureshi, M. A. Aziz, T. A. Cheema and S. B. H. Shah, “Smart IoT control-based nature inspired energy efficient routing protocol for flying Ad Hoc network (FANET),” IEEE Access, pp. 56371–56378, 2020. [Google Scholar]
27. I. U. Khan, M. A. Hassan, M. Fayaz, J. Gwak and M. A. Aziz, “Improved sequencing heuristic DSDV protocol using nomadic mobidility model for FANETS,” Computer, Materials & Continua, vol. 70, no. 2, pp. 3653–66, 2022. [Google Scholar]
28. I. U. Khan, M. A. Hassan, M. D. Alshehri, M. A. Ikram, H. J. Alyamani et al., “Monitoring system based flying IoT in public health and sports using and-enabled energy-aware routing,” Journal of Healthcare Engineering, vol. 21, no. 2, pp. 235–56, 2021. [Google Scholar]
29. I. U. Khan, S. B. Hussain, L. Wang, M. A. Aziz, T. Stephan et al., “Routing protocols and unmanned aerial vehicles autonomus localization in flying networks,” International Journal of Communication Systems, vol. 10, no. 2,. pp. 1–13, 2021. [Google Scholar]
30. I. U. Khan, S. Z. N. Zukhraf, A. Abdollahi, S. A. Imran, I. M. Qureshi et al., “Reinforce based optimization in wireless communication technologies and routing techniques using internet of flying vehicles,” in The 4th International Conference on Future Networks and Distributed Systems (ICFNDS), St.Petersburg, Russia, vol. 27, no. 1, pp. 1–6, 2020. [Google Scholar]
31. I. U. Khan, R. Alturki, H. J. Alyamani, M. A. Ikram, M. A. Aziz et al., “RSSI-controlled long range communication in secured enabled unmanned aerial vehicles,” Edge Intelligence in Internet of Things Using Machine Learning, vol. 21, no. 2, pp. 1–10, 2021. [Google Scholar]
32. R. Khilar, K. Mariyappan, M. S. Christo, J. Amutharaj, T. Anitha et al., “Artificial Intelligence-Based Security Protocols to Resist Attacks in Internet of Things,’ Wireless Communications and Mobile Computing, vol. 2022, no. 1440538, pp. 1–10, 2022. [Google Scholar]
33. M. Alqdah, “Intrusion Detection Attacks Classification using Machine Learning Techniques,” Journal of Computational Science and Intelligent Technologies, vol. 2, no.2, pp. 1–6, 2021. [Google Scholar]
34. R. Mugesh, “A Survey on Security Risks in Internet of Things (IoT) Environment,” Journal of Computational Science and Intelligent Technologies, vol. 1, no.2, pp. 1–8, 2020. [Google Scholar]
35. T. Rajendran, K. P. Sridhar, S. Manimurugan, S. Deepa, “Recent Innovations in Soft Computing Applications,” Current Signal Transduction Therapy, vol. 14, no.2, pp. 129–130, 2019. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools