DOI:10.32604/iasc.2022.024134

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.024134 |  |
| Article |
Decentralized Link Failure Prevention Routing (DLFPR) Algorithm for Efficient Internet of Things
1School of Computer Science and Artificial Intelligence, SR University, Warangal, Telangana, 506371, India
2Department of Networking and Communications, SRM Institute of Science and Technology, Kattankulathur, Chennai, Tamil Nadu, 603203, India
3School of Computer Science and Engineering, Center for Cyber Physical Systems, Vellore Institute of Technology (VIT), Chennai, Tamil Nadu, 600127, India
4Department of Computer Science and Engineering, M. Kumarasamy College of Engineering, Karur, Tamil Nadu, 639113, India
5Department of Computer Science and Engineering, Vignan’s Foundation for Science, Technology & Research, Guntur, Andhra Pradesh, 522213, India
6School of Computer Science and Engineering, Vellore Institute of Technology (VIT), Chennai, Tamil Nadu, 600127, India
7Department of Computer Science and Engineering, Gulzar Group of Institutions, Khanna, Punjab, 141401, India
8Department of Information Technology, Sikkim Manipal Institute of Technology, Sikkim Manipal University, Sikkim, 737136, India
9Department of Computer science and Engineering, Vels Institute of Science Technology and Advanced Studies (VISTAS), Chennai, Tamil Nadu, 600117, India
*Corresponding Author: D. Kothandaraman. Email: kothanda_raman_d@srecwarangal.ac.in
Received: 06 October 2021; Accepted: 11 January 2022
Abstract: This work implements a Decentralized Links Failure Prevention (DLFP) routing algorithm to promote enhanced and efficient Internet of Things (IoT). The work increases the mobility as well as an opportunity for loss of IoT node meeting links due to both mobility and blockers/interferers. The proposed algorithm overcomes loss issues as well as works in dynamically allocating alternate route from other IoT nodes available in near and selecting for efficient route in the network. When the link fails, bandwidth is reduced and coverage area problems for packets sending from source to destination is managed. The proposed algorithm works with light-weight wireless mesh based route handling techniques. In such case, reduced link failure, removal of route discovery latency, communication cost and control overheads, energy consumptions and network life time are to be handled with care. To address these issues, the proposed algorithm enhances the Packet Delivery Ratio (PDR) as well as transmission packet efficiently received through destination node. The ability of Dynamic Alternate Routing (DAR) to relay node handling capabilities and to improve the communication link availability of IoT nodes has ultimately increased the PDR. Simulation work was done using Network Simulator 3 (NS3) and the results show that the performance is better when compared with existing Dynamic Source Routing (DSR) and Energy Efficient Delay Tolerant Routing (EEDTR) algorithm.
Keywords: IoT; communication links; decentralized; mobility; routing performance
This work focuses mainly on Dynamically Alternate Route (DAR) handling techniques. This is a local search mechanism used for reconfiguration, discovery and addition of new nodes along with efficient handling of loss and recurrent routes, real time gathering of local link status [1,2] effective packets forwarding through dynamically mesh handling in the network operate by providing for route related such as source node route establishment towards the destination node in case change of established routes due to mobility [3]. At the same time route discovery latency should also be minimal. It should possess dynamic route handling techniques in IoT such as, mobility pattern transmission range [4,5], and interferences. Instead, an IoT mobility model is proposed where these features are captured by a single parameter λ.
Let, 0 ≤
In IoT networks, communication takes place between node i to node j in meeting-time
The proposed algorithm used in the model is a dynamic mesh topology that is built by dynamic routing. The stochastic technique considers a network with G = (N, L), n IoT nodes (n=|N|) and m links (m=L). There is a packet to be sent when an IoT node meets a sender node. They are then synced via intermediate nodes. The parameters (M/M/C) of constant-service queue as follows:
IoT nodes-arrival route-queue follows Poisson distribution with parameter λ.
The packets send a hypothetical network load which is exponential with parameter μ, and this theoretical work-load is due to IoT-MT of nodes as defined [19] by follows (1).
where, v is the constant velocity of the links, trans-mission radius is R of the links; A is coverage area of IoT nodes in the network. and
When
When
The steady state probability of IoT nodes are shown in (3).
The coverage area of nodes follows (3). The out of coverage nodes that do not follow (3) are considered as unstable. The IoT nodes contact-pattern follows the route depicted in (1). Then, the sender node (i) is modelled by M/M/C multi-server queuing parameters.
2.1 Random Direction 2D Mobility Model (RD2DMM)
The IoT nodes-meeting time starts sending packets to the random node. Else, the two IoT nodes are considered to be meeting each other. The IoT nodes gathering time is distinct from the time those authorizations of two successive meetings for each node. The nodes maintain the same communication range r. The RD2DMM in the node meeting and the IoT nodes gathering times are exponential distributions. The static communication radius is lesser when compared with distance (M).
2.2 Exponential Arrival Time λ of IoT Meeting Nodes
Modelling of IoT nodes i and j with Probability success rate (P) follows exponential distribution. The velocity and positions of the IoT nodes originate this P by using (xi, yi), (xj, yj) with P(xi, yi), P(xj, yj). Within the next time ∆t of the IoT nodes, future meeting of other nodes happen. The P(xi, yi) is dependent on the Coverage Area (CA) at ∆t time [20–28]. The coverage area and the number of nodes are highly inter related and determine the network performance. As showed in Fig. 1, the Coverage Area (CA) is given by 2rVi∆t.

Figure 1: CA covered by IoT nodes i and j1 during a time ∆t
The IoT node j2 in time ∆t adheres to a stationary distribution. Also, the velocity of IoT node j2 is considered for interpretation. The j2 IoT node is in its immobile position. The probability P for j2 IoT node which is positioned in Coverage area CA is given by (4) and (5).
where, r the points π(xi, yi) in CA as estimated by π(xi, yi) and π(xj, yj). This is to give by (6).
Conditioning IoT-node in position of the pointers the p within the next-time of ∆t of i and j, IoT-nodes has to meet each other as showed in (7)
Initially ∆t → 0. This gives an exponential with parameter as showed in (8)
In this scenario, the node j2 is in mobility with velocity Vj = vj. The node j2 has to meet other node in the next time interval ∆t. As shown in Fig. 2, CA depends on V∗ and the relay IoT node between the nodes and j.
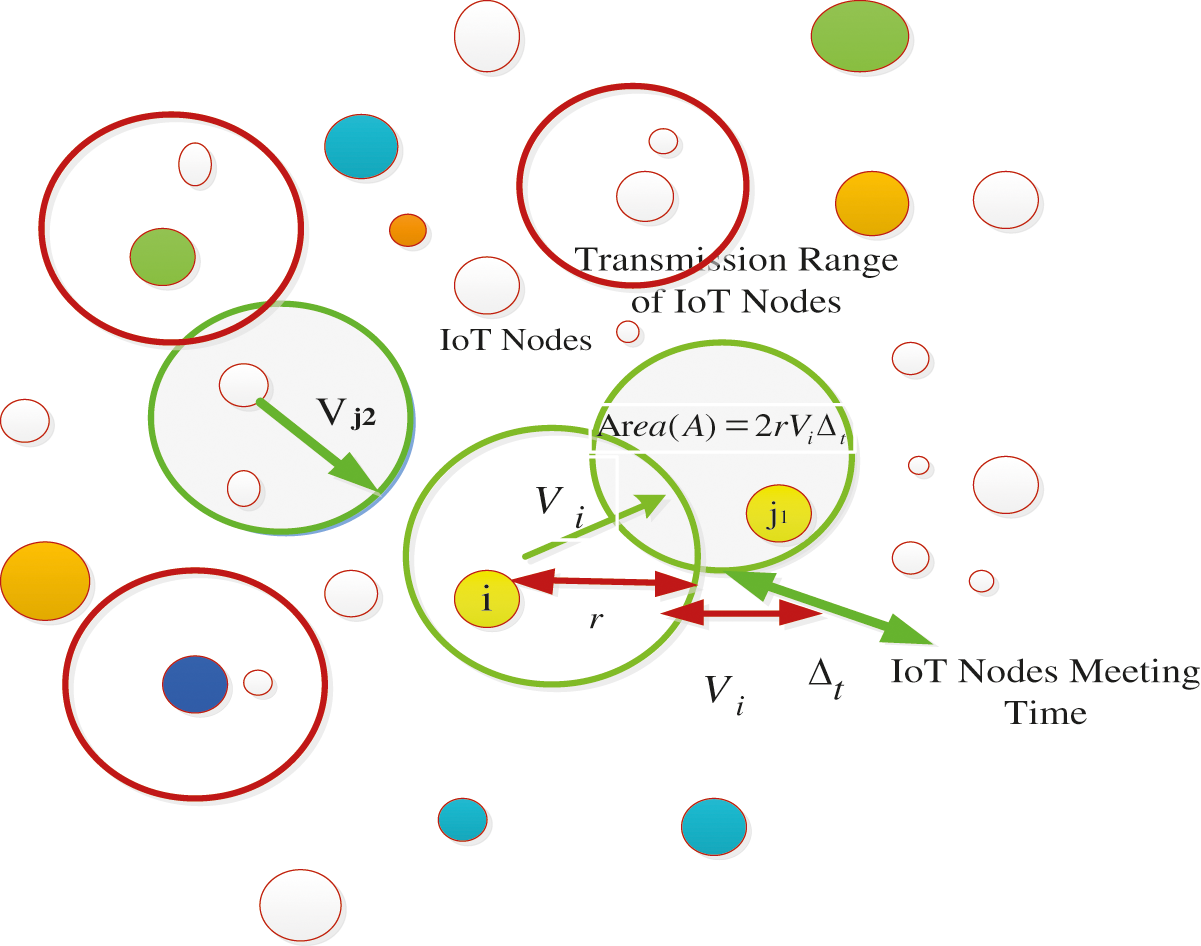
Figure 2: Position as changing the node j2 has to be meeting in nodes i
If i is the node in (xi, yi), then the probability of a “success” is given by (9)
Then, the area of CA is 2r ·V∗· ∆t. Applying the same logic over all starting positions of IoT node, i is given by (10).
where, ∆t → 0 indicates the exponential growth as shown in (11)
The IoT nodes gathering time is distinct from the time the authorizations of two successive meetings for each node within the same communication range r. The RD2DMM and the IoT nodes gathering times are exponentially distributions and extended as the static communication radius is lesser when compared with the distance (M).
2.3 IoT Nodes Meeting Time Distribution
Let i and j IoT nodes move free between each other in M × M with velocity Vi and Vj. Let IE[V∗] be the average transmit velocity of two IoT nodes, π(xi, yj) positions in the steady-state. If the communication range r << M, position of the node time t is independent of it position at time t + ∆t, and then IoT node-meeting time (F) of the nodes is exponential of λ is given in (12)
The average time till the two IoT nodes has met is showed in (13)
The meeting time distribution has to be applied to RD2DMM measures. The IoT node spatial distribution and the average relay node velocity IE[V∗] are to be computed. Let π(x, y) probability distribution function of the spatial IoT node mobility in M × M as showed in (14).
where, IoT nodes transmit for according to the RD2DMM.
2.4 Relay Nodes Velocity Distribution
The IoT nodes travel in a direction as that of a straight-line and the combined transmission is uniformly distributed. If the IoT nodes are travelling with velocity Vi = vi and Vj = vj, then the Cumulative Distribution Functions (CDF) of the relative velocity is shown in (15).
The Conditional probability Density Function (CDF) follows the derivative in (16).
If the change of direction and velocity is selected uniformly from (vmin, vmax), then the PDF of the average relay velocity under the RD2DMM is the expected value as depicted by (17).
2.5 Relay Nodes Travelling At Constant Velocity
For two IoT nodes travelling at the same velocity, the CDF of the relay velocity for the random direction is given by (18).
The distribution function is,
The average relay velocity is shown in (19).
When Vi = v = Vj as in (20),
The average relay velocity which is given in (18) is greater than v, the velocity of every node. The average relay velocity is equal to v.
2.6 IoT Node Meeting Times And Random Direction
The IoT node meeting time for the RD2DMM for r << M and is approximately exponentially (λRD) distributed, where λRD is
The expected time until nodes i and j meet is given by (23).
The average relay velocity has been calculated using (14) and (15). If the velocities of i and j IoT nodes are same and constant, i.e., V1 = v = V2, then as shown in (24),
IoT relay velocity is shows in (25).
The relationship to derive the CDF is shown in (26).
The velocity of an IoT node at a random-model in time to unconditional position is shown in (15). If the velocity of a node that is designated is uniform [vmin, vmax], then the velocity of a node under the RD2DMM is uniformly distributed and so fVi(vi) = 1/(vmax – vmin).
3 Dynamic Alternate Route Handling Techniques
The present algorithm has been implemented using dynamic alternate routing handling techniques. It follows different models such as direction, positions changes, IoT nodes within range and out of transmission range. The evaluation of the IoT node meeting time between nodes i and j1 has transmitting packets while other nodes are out of the range. These out of range nodes may in future come within the range as showed in Fig. 3.
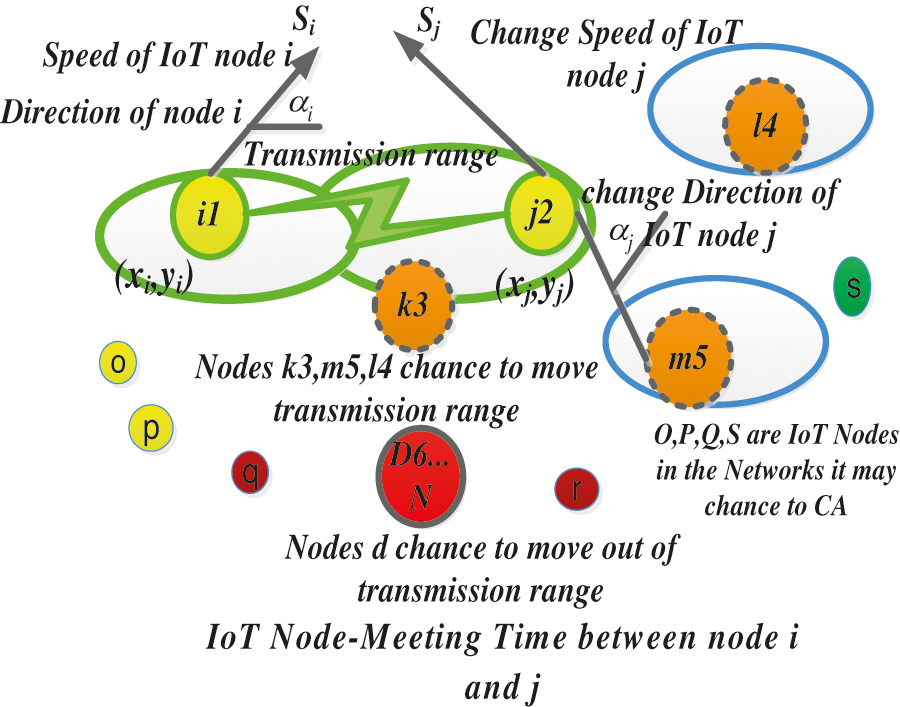
Figure 3: IoT node meeting time between i and j1
In Fig. 2, IoT nodes j2 have various direction at t = 0. The position of IoT nodes; i = 1, 2….N, j = 1, 2….N at that moment be given by (xi, yi),(xj, yj). The direction is denoted by αi, αj and the speed is denoted by si, sj,. The IoT node i and j at t ≥ 0 is shown in (8).
The IoT node is considered to have met or discrete since each other at t time and is of the distance R. Substituting in eqs. (27)–(30).
Resolving this 2 degree polynomial in t gives Eqs. (31) and (32)
where;
Here t1and t2, give the mobility’s of in time nodes when the IoT Nodes sends data into the range with one another and when it is range with each other. If;
1.
The two IoT nodes never meet in the range;
2.
IoT node meeting and separate in the past;
3.
The IoT node in range at t = 0 and discrete future at tj
4.
IoT nodes meet in future at t1 and discrete at tj. The IoT nodes t1and t2 as compared to the time until the next-change of direction or suitable event can be scheduled in the IoT networks.
4 Experimental Results and Discussion
The present work results have been evaluated using NS3. Based on these results, measures for regulating IoT battery power consumption, bandwidth consumption, increasing the PDR, residual energy of IoT nodes and reducing the control overhead is carried out. The parameter has considered in simulation as shown in Tab. 1.

Fig. 4 shows the IoT node meeting time vs. PDR for Decentralized Links Failure Prevention Routing (DLFPR) and other existing algorithm. When the IoT meeting nodes increase from 10 to 100, the PDR was obtained as 99.5% for DLFPR in IoT network. For Energy Efficient Delay Tolerant Routing (EEDTR), the PDR was obtained as 80.12% and for DSR it was 70.2%. Hence proposed algorithm shows 29.3% improved over DSR. The DSR is relatively less efficient when PDR is considered. Also, the IoT nodes are scalable without any performance issues.
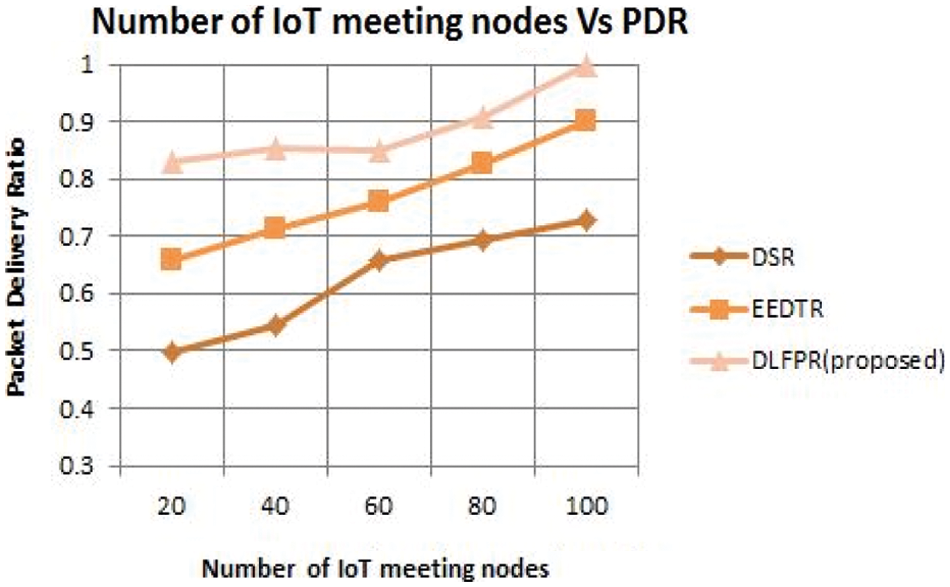
Figure 4: No. of IoT-nodes meeting vs. PDR
Fig. 5 shows the IoT meeting nodes vs. Control overhead for DLFPR and other existing algorithm. Control overhead is significant to gauging the performance and latency. When the IoT meeting nodes increase from 10 to 100, the control overhead was obtained by 498 for DLFPR in IoT. For EEDTR it was obtained as 1010 and for DSR is 1200. Hence, the proposed algorithm shows 51.2% improved over EEDTR and 20.5%.over DSR. Also, as the number of IoT nodes increases we can observe that there is no performance degradation in PDR.
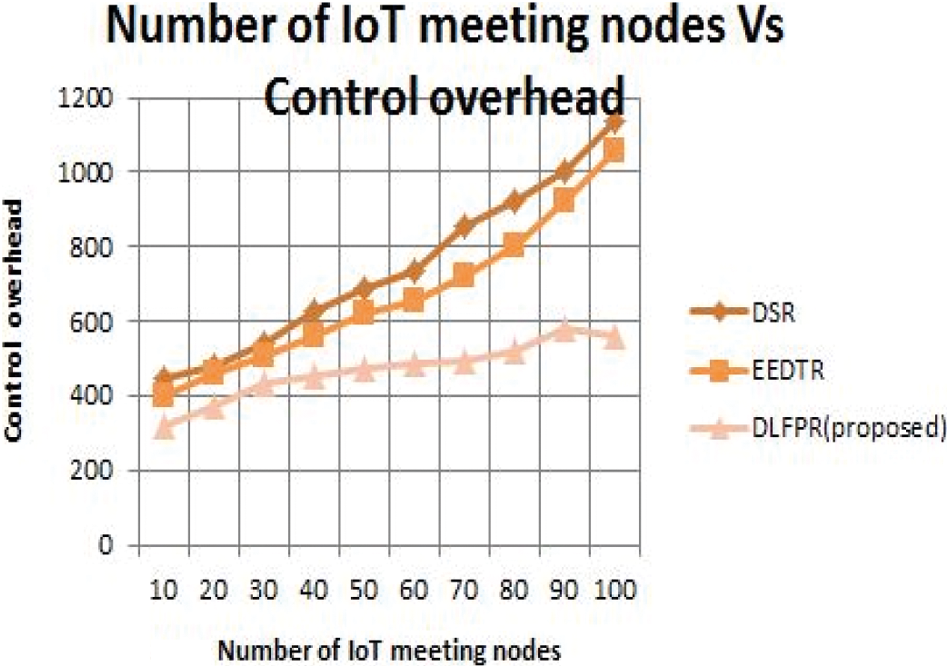
Figure 5: Number of IoT-nodes meeting time vs. control overhead
Fig. 6 shows the IoT nodes meeting time in speed(m/s) vs. average residual energy for DLFPR and other existing algorithm. When the speed increases from 2 to 10 m/s, the average residual energy was observed as 3750 mwhr for DLFPR for IoT, while the same was obtained by 3250 mwhr for EEDFT and for DSR was obtained by 2550 mwhr. Hence the proposed DLFPR shows the 37.6% improved over DSR and 14.5 over DSR.
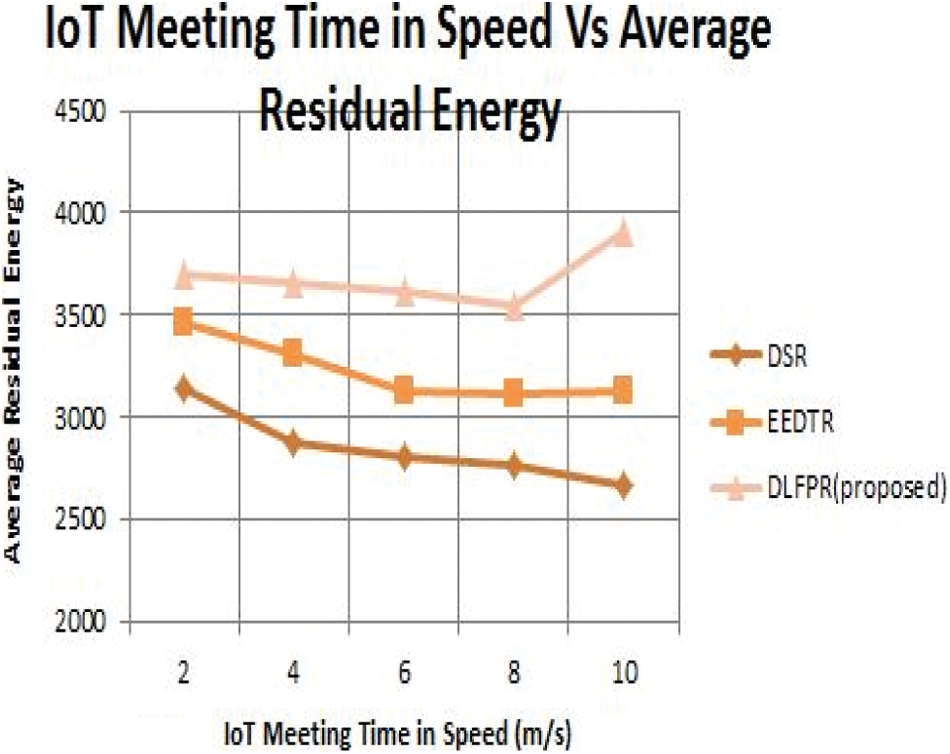
Figure 6: IoT-nodes meeting time in speed(m/s) vs. residual energy
This work proposes a statistical analysis of stochastic properties of RD2DMM. It has investigated the length and duration of IoT nodes mobility between two way-points. Also, the spatial IoT-node and its dependence on the pause- time was analyzed. The selection of direction angle at the start of a IoT nodes mobility transition, and the number of position changes for an random-way-point model used in a IoT network were discussed. Results indicated PDR as 99.5%, Control Overhead was 51.2% and speed vs. average residual energy of IoT meeting nodes was obtained as 37.6%. These were good numbers when compared with existing algorithm. Also, this work is highly scalable to accommodate more nodes without any performance degradation. All the results analysis and simulation has been carried out using IoT wireless networks. Future work will be focused towards experimenting with more nodes and evaluating the performance with more Quality of Service (QoS) parameters.
Acknowledgement: The authors wish to express their thanks to one and all who supported them during this work.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. V. Mahendran and C. Sivarammurthy, “Buffer dimensioning of DNT replication-based routing nodes,” IEEE Communications Letters, vol. 17, no. 1, pp. 11–25, 2013. [Google Scholar]
2. R. Aggarwal, S. Manickam and C. Sivarammurthy, “Cross-Layer user pairing for CSM in IEEE 802.16 networks,” IEEE Communications Letters, vol. 15, no. 5, pp. 37–52, 2011. [Google Scholar]
3. M. Lee, R. Zhang, C. Zhu, T. T. Park, C. Shin et al., “Meshing wireless personal area networks: Introducing IEEE 802.15.5,” IEEE Communications Magazine, vol. 11, no. 5, pp. 73–91, 2010. [Google Scholar]
4. R. Groenevelt, Stochastic models for mobile Ad Hoc networks. University of Nice Sophia Antipolis, Nice, France, 2005. [Google Scholar]
5. M. J. Lee, R. Zhang, J. Zheng, G. S. Ahn, C. Zhu et al., “IEEE 802.15.5 WPAN mesh standard-low rate part: Meshing the wireless sensor networks,” IEEE Journal on Selected Areas in Communications, vol. 28, no. 7, pp. 34–49, 2010. [Google Scholar]
6. D. Kothandaraman and C. Chellappan, “Direction detecting system of indoor smartphone users using BLE in IoT,” Circuits and Systems, vol. 7, no. 8, pp. 1492–1503, 2016. [Google Scholar]
7. D. Kothandaraman and C. Chellappan, “Human movement tracking system with smartphone sensing and bluetooth low energy in internet of things,” Asian Journal of Information Technology, vol. 15, no. 4, pp. 661–669, 2016. [Google Scholar]
8. D. Kothandaraman and C. Chellappan, “Human activity detection system using internet of things,” International Journal on Computer Science and Engineering, vol. 9, no. 11, pp. 657–665, 2017. [Google Scholar]
9. D. Kothandaraman and C. Chellappan, “Node rank based energy efficient routing algorithm for mobile Ad-Hoc network,” International Journal of Computer Networks & Communications, vol. 11, no. 1, pp. 45–61, 2019. [Google Scholar]
10. A. Balasundaram, S. Ashokkumar, D. Kothandaraman, E. Sudarshan and A. Harshaverdhan, “Computer vision based fatigue detection using facial parameters,” IOP Conference Series: Materials Science and Engineering, vol. 981, no. 2, pp. 21–37, 2020. [Google Scholar]
11. A. Balasundaram, D. Kothandaraman, P. J. Sathish Kumar and S. Ashokkumar, “An approach to secure capacity optimization in cloud computing using cryptographic hash function and data de-duplication,” in 2020 3rd Int. Conf. on Intelligent Sustainable Systems (ICISS), Chennai, India, pp. 1256–1262, 2020. [Google Scholar]
12. A. Harshavardhan, D. Ramesh, S. N. Pasha, S. Shwetha, S. Mohmmad et al., “IOP conference series: Materials science and engineering,” Lifting Wheelchair for Limbless People, vol. 981, no. 2, pp. 43–61, 2020. [Google Scholar]
13. M. Pushpalatha, R. Venkataraman and T. Ramarao, “Trust based energy aware reliable reactive protocol in mobile ad hoc networks,” World Academy of Science, Engineering and Technology, vol. 56, no. 68, pp. 356–359, 2020. [Google Scholar]
14. T. Senthilmurugan and K. Eswariah, “Link stability with energy aware ad hoc on demand multipath routing protocol in mobile ad hoc networks,” American Journal of Applied Sciences, vol. 10, no. 8, pp. 844–848, 2013. [Google Scholar]
15. K. Vishant, J. S. Chauhan and K. Ankit, “A comparative study of broadcast based routing protocols in mobile ad hoc networks,” International Journal of Application or Innovation in Engineering & Management (IJAIEM), vol. 2, no. 12, pp. 277–282, 2013. [Google Scholar]
16. A. Alhemyari, I. Mahamod, R. Hassan and S. Saeed, “Improving link stability of multicasting routing protocol in MANETs,” Journal of Theoretical and Applied Information Technology, vol. 55, no. 1, pp. 109–116, 2013. [Google Scholar]
17. A. Whitmore, A. Agarwal and L. Da Xu, “The internet of things – A survey of topics and trends,” Information Systems Frontiers, vol. 17, no. 2, pp. 261–274, 2015. [Google Scholar]
18. F. Liu, Y. Wang, M. Liu, K. Liu and D. Wu, “A distributed routing algorithm for data collection in low-duty-cycle wireless sensor network,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1420–1433, 2017. [Google Scholar]
19. A. Shashank, R. Vincent, A. K. Sivaraman, A. Balasundaram, M. Rajesh et al., “Power analysis of household appliances using IoT,” in 2021 Int. Conf. on System, Computation, Automation and Networking (ICSCAN), Puducherry, India, pp. 1–5, 2021. [Google Scholar]
20. H. Kharrufa, H. A. Al-Kashoash and A. H. Kemp, “RPL-based routing protocols in IoT applications: A review,” IEEE Sensors Journal, vol. 19, no. 15, pp. 5952–5967, 2019. [Google Scholar]
21. E. Ahmed, I. Yaqoob and A. Gani, “Internet-of-Things based smart environments: State of the art, taxonomy, and open research challenges,” IEEE Wireless Communications, vol. 23, no. 5, pp. 10–16, 2016. [Google Scholar]
22. A. Surjeet, A. Parkash and R. Tripathi, “QoS bandwidth estimation scheme for delay sensitive applications in MANETs,” Communications and Network, vol. 5, no. 1, pp. 1–8, 2013. [Google Scholar]
23. M. Pushpavalli, A. M. Natarajan and N. Annitha, “A quality of service based AODV with QoS-aware routing algorithms for MANETs,” International Journal of Application or Innovation in Engineering & Management (IJAIEM), vol. 2, no. 2, pp. 199–204, 2013. [Google Scholar]
24. D. Kothandaraman, A. Balasundaram, R. Dhanalakshmi, A. K. Sivaraman, S. Ashokkumar et al., “Energy and bandwidth based link stability routing algorithm for IoT,” Computers, Materials & Continua (CMC), vol. 70, no. 2, pp. 3875–3890, 2021. [Google Scholar]
25. S. S. Dhenakaran and A. Parvathavarthini, “An overview of routing protocols in mobile ad hoc network,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 3, no. 2, pp. 251–259, 2013. [Google Scholar]
26. P. Pramod Kumar, C. H. Sandeep and S. Nareshkumar, “An overview of the factors affecting handovers and effective highlights of handover techniques for next generation wireless networks,” Indian Journal of Public Health Research & Development, vol. 9, no. 11, pp. 12–25, 2018. [Google Scholar]
27. Bura Vijay Kumar, S. N. Korra, N. Swathi, D. Kothandaraman, N. Yamsani et al., “Traffic control system for vehicles on indian roads using raspberry PI,” IOP Conference Series: Materials Science and Engineering, vol. 981, no. 3, pp. 67–81, 2020. [Google Scholar]
28. V. Thirupathi and K. Sagar, “Web of Things an intelligent approach to solve interoperability issues of Internet of Things communication protocols,” IOP Conf. Series: Materials Science and Engineering, vol. 981, no. 5, pp. 23–31, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |