DOI:10.32604/iasc.2022.023207

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.023207 |  |
| Article |
Context-Aware Service Model of a Mobile Library Based on Internet of Things
1School of Computer Engineering, Jiangsu University of Technology, Changzhou, 213001, China
2School of Economics and Management, Nanjing University of Science and Technology, Nanjing, 210094, China
3Gyeongsang National University, Jinju, 52828, Korea
*Corresponding Author: Haixu Xi. Email: gaoweixihaixun@163.com
Received: 31 August 2021; Accepted: 16 December 2021
Abstract: Appropriate technology needs to be applied in libraries to provide users with more humanized, intelligent, and convenient services to improve service quality. Using theories from library science, management, and modeling, this paper examines library personalized service in the intelligent Internet of Things (IoT) environment using a literature review, comparative analysis, and UML modeling to analyze the influencing factors of mobile library users’ acceptance of personalized recommendation services. Based on the situational awareness framework, the experimental results of the effect of these personalized service recommendations show that the load factor is greater than 0.6, which indicates that the dimensions of a scalar can explain situational awareness. The P-value > 0.01 shows that the mobile library is linear and related to the user, mobile, resource, and service scenarios. Overall, based on this investigation and analysis, countermeasures, and suggestions, a personalized service system framework may be suitable for mobile libraries in the IoT environment.
Keywords: Internet of things; mobile library; situational awareness; personalized service
The 21st century is an era of information explosion. The upgrading of information technology has promoted significant changes in mobile library service models where the implementation of domestic computer networks has also made rapid progress. Networking capabilities have linked information resource sharing between libraries with the technology. Extension and expansion of Internet technology includes the Internet of Things (IoT), which is a computing concept that can identify, locate, track, monitor, and manage physical objects [1–3]. The combination of science and technology, and the wide application of IoT in our physical world can affect and change people’s lifestyles. In the case of the library, IoT is especially relevant in the promotion and operation of mobile libraries; mainly in how users’ information-seeking behavior has changed. With the wide application of intelligent devices, users are eager to apply intelligence in their information demand while enjoying library services. Knowledge services in mobile libraries are ubiquitous, which has been the state of library services for a long time. As an information service provision organization, the library should combine technology and resources organically to create an opportunity for the creation of a new mobile library service model. In its current state, the traditional library has been unable to meet the needs of users despite being supplemented by the digital library. Digital technology shows that access to information is not limited to the reading of paper documents, and users’ information needs gradually tend to be diversified and knowledgeable. However, because of their information illiteracy, the massive amount of information now available makes it difficult to meet these information needs. Accordingly, the library is challenged to provide effective information services for users. While traditional user-based search behavior and interest recommendations are widely used in a digital library, these recommendations still have limitations. Therefore, research on resource recommendations based on situational awareness continues to be treated as a hot topic in the information field [4–6].
The importance of making computers context-aware has attracted many research teams to the field of context-aware service models with good results [4,5]. In recent years, radio frequency identification device (RFID) technology has been used pervasively in the computing environment. Today, we see innumerable examples of RFID technology in different types of industries viz., logistics, public service, manufacturing, etc. Durga proposed building a context-aware RFID service model that combined ontology language OWL with CC/PP and FOAF specifications. Context ontology is a common vocabulary used to share context information within a computing domain and RFID tags. When context reasoning mechanisms and interpretation are introduced based on ontology and guidelines, the dynamic management of context in the RFID system is captured through rewritable RFID tag memory. The feasibility of the model is perhaps best illustrated by an example [6]. Based on the OSGi framework, some researchers proposed a context-aware service model in a ubiquitous agricultural environment. The proposed service model supports various context-aware applications based on RFID/USN, using available sensors and devices in the agricultural environment. Therefore, the proposed new mobile library service model can quickly be reorganized and easily use existing service resource needs without major changes to the established system architecture of the library environment. In particular, the proposed service model will be helpful for the development of context sensitive library services in various farming environments equipped with different sensors [7–9]. Although the current research results are relatively rich, there are still deficiencies, which are mainly reflected through insufficient research on context aware service models.
In research on service models, the IoT is a good method as it is key in problem resolution and is widely used. The IoT envisages a future in which digital and physical things or objects (e.g., smartphones, TVs, and cars) can be connected through appropriate information and communication technologies. A large number of applications and services are achievable including the huge scale of the IoT. The characteristics of the IoT, the heterogeneity of devices and networks, and the spontaneous occurrence of daily events will make the development of diverse applications and services a difficult task. Generally, middleware can simplify the development process by integrating heterogeneous computing and communication devices and supporting interoperability in various applications and services. Recently, proposals about IoT middleware aimed mainly at the wireless sensor network (WSN), a key component of the IoT. However, it did not consider the other three core RFID, i.e., machine to machine (M2M) communication, and supervisory control and data acquisition (SCADA). Razzaque outlined a set of requirements for IoT middleware, and comprehensively reviewed the existing middleware solutions. In addition, Razzaque also highlighted open research issues, challenges, and future research directions [10–12]. Because of the effectiveness of the IoT, research can be conducted on the mobile library service model to solve any concerns about growth or progression.
The roadmap of this paper is organized as follows. The first section compares library personalized services to ascertain innovation in library services based on the IoT. Section 2 analyzes the information demand and acceptance behavior of mobile library users from the perspective of situational awareness to determine the situational dimension. Section 3 explains the usability, usefulness, and adaptability function of situational awareness in mobile libraries. A personalized recommendation is constructed based on situational awareness of the mobile library service model. Section 4 provides the experiments and discussion, and finally, Section 5 presents the conclusion.
Internet technology is the foundation of the IoT and consists of networks that extend and expand on the Internet [13,14]. The IoT encompasses a variety of different technologies that are applied to different modules, which provide the underlying technical support for its core operation [15,16]. The IoT consists of four key supporting technological applications: RFID, sensor, M2M, and artificial intelligence technology [17,18].
RFID technology is the core technology in IoT. It can automatically identify objects and obtain related data through radio frequency signals [19–21]. RFID systems consist of three basic components: a tag, a receiver, and a transmitter. A tag is attached to the item or target so it is identifiable, while a transmitter emits a radio frequency signal to activate the tag so it can be read and the data written to it in either mobile or stationary format [22–24].
RFID technology can be automatically identified without direct visibility. It can quickly and easily identify and read data, has a large data capacity, a long service life, and strong security. RFID is increasingly being used by libraries and magazine publishers [25–27]. In recent years, the application of RFID technology in large global libraries has grown at a rate of 30% per year. The technology has been used to improve service level and quality along with the introduction of RFID equipment. These include 24-hour self-service book return machines, automatic book sorting equipment, security doors, as well as virtual library membership cards, such as second-generation ID cards.
Sensor technology is currently one of the most widely used technologies in IoT. It has been applied to modern living and includes smart devices such as automatic doors, sound-activated lights, touch screens, electronic thermometers, and precision electronic scales [28,29]. Sensors are integral to IoT services and applications and responsible for the perception and collection of data [30,31]. Specifically, a sensor is a device or component that senses and detects specific information or signal that can automatically be converted into a corresponding quantified specific signal according to certain technical specifications. Usually, it is composed of two parts, i.e., sensitive components and components responsible for conversion [32,33]. Currently, there are more than 30,000 sensors with the more common ones being pressure, heat, humidity, speed, vibration, energy consumption, and other sensitive transmitters [34].
The sensor is an indispensable device for the advancement and progression of the library. Data can be captured automatically, detected and controlled, and accurately and reliably measure various parameters to realize library automation and intelligence.
M2M is interpreted as machine-to-machine communication technology with deeper meaning based on intelligent machine terminals positioned as the core, through networked interactive services and application technology [35]. This kind of interaction and intelligence is a unique model that is different from other applications. Machines with this unique feature are provided with unique “thoughts” and “wisdom”.
M2M applications can be divided into automation, control, positioning, monitoring, maintenance, and tracking according to the functions they perform. Samples of M2M applications in diverse industries are shown in Tab. 1. M2M technology can better serve libraries through automatic loans of books and magazines, catalog queries, database management, and library security management.

2.4 Artificial Intelligence Technology
The IoT shows that objects are not independent but connected through a network to form a massive system. Fortunately, with the help of intelligent technology, the huge amount of information stored in these systems can be effectively managed.
Artificial intelligence is an interdisciplinary subject boosted by computer science, cybernetics, information theory, neurophysiology, psychology, linguistics, etc. Artificial intelligence technology can help the IoT realize the purpose of intelligent perception in the world. Currently, the research and application of AI technology focus mainly on certain aspects, as shown in Tab. 2.

In the mobile library, intelligent technology is particularly important to rely on. This technology may involve equipment such as a personalized retrieval system, intelligent robot, camera monitoring, FAQ of common problems knowledge base, office software, etc. In the era of IoT, the application of intelligent technology is more indispensable.
3.1 Theory of Acceptance Behavior of Situational Awareness Technology
Based on the rational behavior theory, this paper developed the technology acceptance model and highlighted factors that lead people to accept or reject information technology. Perceived usefulness is defined as “the degree to which a person believes in the use of a particular system,” and theorized to improve performance. Therefore, the definition of perceived usefulness is derived from the expectation value model based on the reasoning behavior theory. Perceived usefulness and reasoning behavior are two factors that affect user behavior. In the field of information systems, the technology acceptance model has been widely used and is now one of the most influential theories in the field of information systems. Some researchers have introduced other factors into the model, such as subjective norms, perceived behavior control, and self-efficacy. Correspondingly, other researchers have introduced factors related to innovative literature dissemination, such as testability, visibility, or the possibility of result demonstration. In addition, researchers also used personality and demographic characteristics as external variables to evaluate the effect of perceived usefulness and ease of use. The technology acceptance model is shown in Fig. 1.
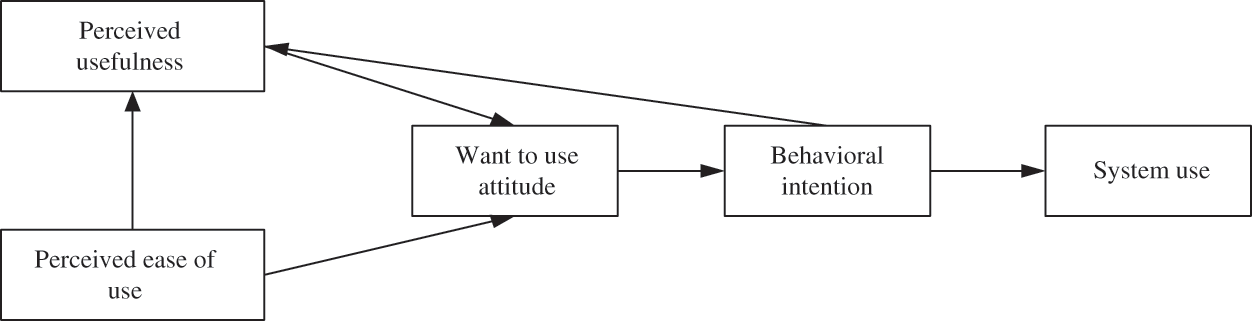
Figure 1: Technology acceptance model
3.2 Personalized Recommendation Service Model of Mobile Library Based on Situational Awareness
(1) Situational awareness in the mobile library
Users change their information needs in different situations. In the mobile library setting, users’ information activities are usually fragmented, temporary, and practical, and corresponding information needs are often related to time (a factor or a situation). In the spatial dimension, users’ space information activity has characteristics of locality and purpose, while the corresponding information demand is related to the location information situation. Within the user dimension, each person has a different identity, biological information, and other personal characteristics, as well as different interests, behavior characteristics, borrowing history, and other information preferences. A user’s corresponding information needs are related to their situational information. In the social dimension, users’ comments, interactive communication, and community sharing are related to the social situation. Therefore, the mobile library needs to perceive the situational information of users, analyze and judge their current situation, and calculate their rapid response in real-time to provide users with convenient, and fast situational information and services.
(2) Semantic similarity calculation of concept
The concept is the connotation of the word, which is the external format. Sim (W1, W2) is used to represent concept similarity. If the distance between concepts W1 and W2 on the hierarchical concept tree is dis (W1, W2), then similarity has been obtained.
(3) Similarity calculation of text resources
The concept-based text representation model is a kind of vector space model, which can better measure the lack of semantic knowledge and solve the problem of synonym and polysemy recognition. Text similarity refers to the similarity degree of subjects or contents between texts, which is similar to the joint concept of Quillian. Text similarity is calculated by the similarity degree of text feature words or concepts. When calculating the semantic similarity of a text, first calculate the semantic distance of the text, as shown in Formula 2.
Among them, dx and dy are two different texts, xi and yj are characteristic words or concepts contained in text dx and dy respectively; fi is the number of times that concept xi appears in text dx; fj is the number of times that concept yj appears in text dy; n and m are the number of concepts contained in two texts respectively. To avoid too large a calculation result of semantic distance, d is used for normalization.
d represents the number of semantic distances between concepts or characteristic words in two texts. Meanwhile, normalization of semantic distance can avoid too many characteristic words or concepts in texts, resulting in too large a semantic distance.
It can be seen that the larger the semantic distance, the smaller the similarity of the text.
(4) Similarity calculation of mobile location scenarios
It is a common method to calculate similarity based on information entropy, which is often used to measure the semantic information contained in information. In the structure of ontology construction, the concept of the root node is more abstract, and the child nodes often contain more descriptive information and are more specific. In the definition of a concept, the information content can be expressed by the formula:
Here, freq(Ci) represents the number of location concepts contained in scenario ontology construction, and M represents the number of all concepts in the ontology. When calculating the similarity of location scenarios, the product of correlation degree can be used. As shown in the formula:
where Ni and Nj represent the number of types of positions.
(5) Similarity calculation of User scenario
The ultimate service users of mobile libraries are college students, teachers, and so on. To better represent and calculate the characteristics of service objects, this paper describes the user information as gender, age, education level, professional information and location. Finally, we can use Hemingway’s formula to calculate the similarity between users, as shown in the formula.
where d (a, b) is the distance between two users. The shorter the distance between users, the greater the similarity. dmax is the maximum difference between all users. Because the agents are independent of each other, we can use the formula to calculate the similarity between users.
In the mobile library scenario ontology model, the description of time dimension is numerical, so there is no need to take the textual description, which makes the data more convenient to calculate. The similarity calculation method on time dimension would need to be redefined.
3.3 Context-Aware Service Architecture
Situational awareness within the library service system needs to obtain the user’s situational data such as time, place, personality preference, intelligent terminal characteristics, and other related data. Relying on situational data provides appropriate information for the technology to provide a real-time and accurate personalized service experience for mobile users through a personalized recommendation engine. Based on this theory, this paper proposes a hierarchical framework of context-aware service systems, as shown in Fig. 2.
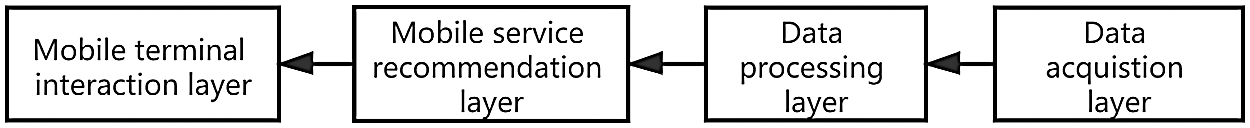
Figure 2: Framework of mobile situational awareness service system
In addition, it is worth noting that situational data collection and processing are based on basic related discipline research. The mobile terminal interaction layer is divided into two categories: interactivity and applicability. The mobile service recommendation layer involves intelligent space, tourism navigation, information system, communication system, mobile commerce, and web services. The data processing layer can be roughly divided into agent-based, metadata-based, and array space-based middleware processing technology. The network layer consists of protocol, detection, network requirements, network implementation, and other research contents.
4.1 Experimental Planning and Design
The dynamic combination of planning and design-construct of the scheduled service component unit was connected through the channel. The channel is used to connect the input and output ports of the task execution unit. These ports are all designed to facilitate seamless data transmission in the channel, which is done in real-time, safe and lossless, as shown in Fig. 3 below.
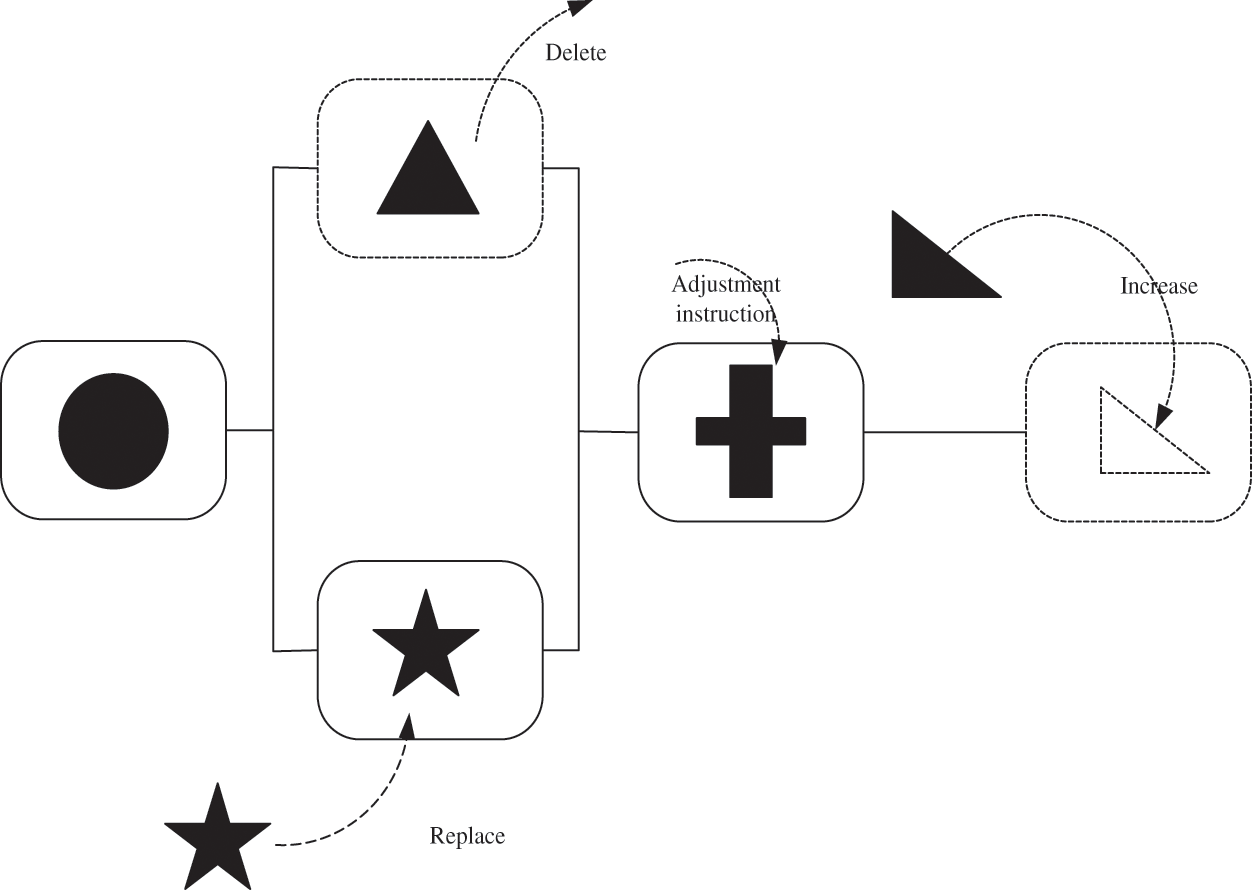
Figure 3: Planning and design diagram
It can be seen from the planning of the schematic diagram that the add-on and deletion of service components are relatively simple, which is conducive to the adaptive construction of the system. At the same time, since the operation data are stored in the database, the data let is only responsible for the data processing to realize the visual alarm function and communicate with the outside through the interface. For other task execution units, a data let is like a “black box”. Part of the data processing before and after is connected to the port near the database. Therefore, the deletion and modification of the calculation unit (data let) will not affect the inconsistency of the data. Since the data stored in the database will not create errors with the adaptive adjustment, it can greatly improve the robustness of the system.
4.2 Experiment Knowledge Base Ontology Design
The knowledge base module is responsible for acquiring and representing the required knowledge. A good knowledge model is a basis for the automatic matching mechanism. Decision-making needs relevant knowledge, so the middle layer must acquire and understand a lot of knowledge. The decision-making of context-aware service focuses on how to select the right components in the current context. Therefore, the following information is needed for making an adaptive decision:
(1) Target service needs - functional and non-functional requirements such as functional description, performance description, structural data, security, practicality, and other information.
(2) Description of available component attributes - functional and non-functional descriptions such as the function, service performance, and communication interface information with other components that can be provided by the available component.
(3) Obtain the environment information – this is needed for the operation of available components such as physical environment information, computing resources, etc.
(4) Current real-time situation data - such as obtaining current real-time and accurate environment and computing resource information for overall consideration in decision-making.
4.3 Empirical Analysis of the Proposed Model
The evaluation experts in this experiment consisted of five professors and five librarians who all had rich experience in the application of mobile libraries. First, experts were invited to use the mobile library and record their experiences. Experts’ scores were recorded by the Likert scale and weighted by the index system. Personalized service evaluation scores were obtained and shown in Tab. 3.

In Tab. 3, it shows the evaluation results of the mobile library service platform. Subsequent discussions and analyses were conducted of the user, mobile, resource, and service scenarios, and comprehensive evaluation results were produced for each service platform.
4.4 Analysis of Evaluation Results
(1) Assessment results of user scenario
As shown in Tab. 3, the evaluation results of the mobile library’s situational awareness function showed higher scores. Mobile libraries paid attention to the mobility of their service platforms, while the HowNet service platform paid more attention to user awareness. While the main purpose of the Mobile library service platform suggests a focus on service provision for more mobile users, the HowNet service platform paid more attention to improving the perceived service quality. This is shown in Fig. 4.
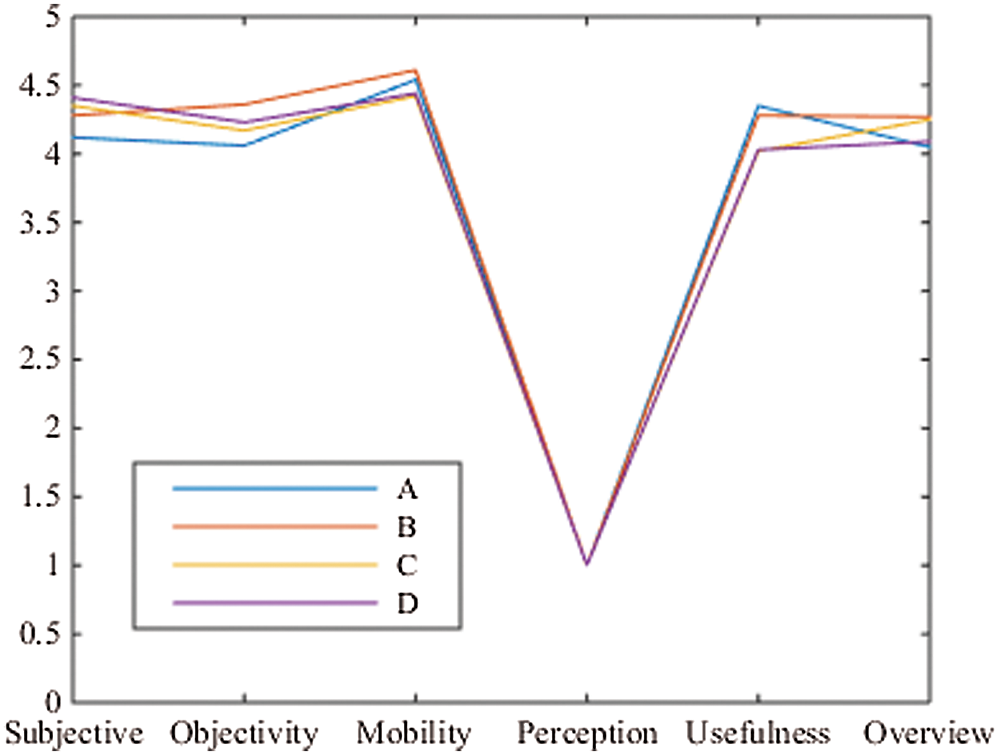
Figure 4: Graph of personal library service evaluation scores
Each service platform provided users services viz., collection, likes, footprints, downloads, retrieval, etc. These functions enable an understanding of users’ preferences and user needs. In particular, the Super Star mobile library can select interesting content according to personal customization, thus specifically targeting the recommended resources. During the registration process of the mobile platform mentioned earlier, the user’s knowledge and educational background, age, region, and other information were not collected, which lowered the rating of this option. The ranking also indicated that the service platform needed to continue to improve the development of the perception function and make recommended resources more in line with users’ needs, to improve their perception experience.
(2) Assessment results of mobile scenario
The situational awareness score of each mobile library function was not high, which suggests that the mobile library did not pay enough attention to services. Comparatively, the HowNet service platform paid more attention to the user’s perception function and the quality of perception service. Each mobile library had a high mobility score, which suggests that the mobile library attaches great importance to mobile performance, especially Yunzhou knowledge service space. This library provided users with relatively high-quality courses and resources. Superstar mobile library also provided users with reading activities that proved to be interesting according to the different regions in Fig. 5.
Figure 5: User interest in reading activity diagram
As shown in Fig. 5, a mobile library as a service platform tool can meet the needs of users to a certain extent. However, it should be noted that the development of the user perception functions in the afore-mentioned mobile libraries was not perfect, so the score was low. This also leads to user demand mining of libraries which is not good and suggests the value of resources needs to be further explored.
(3) Assessment results of resource scenario
The resource scenario built into each service platform was moderate. The National Library had the highest level of content usefulness and refinement reorganization, followed by the HowNet service platform. Additionally, Yunzhou had the worst knowledge space. Note that the National Library had a relatively high level of reorganization and development of resources, as shown in Fig. 6.

Figure 6: National library resource map
This may be because a large number of resources in the National Library were concentrated on resource collection, so the utilization and aggregation level of the resource collection, as well as the quality of service, was relatively high. HowNet service platform pushed content of news that was mainly related to lectures, albeit the content form was relatively novel. However, the content resources were relatively low to the degree of aggregation. Yunzhou’s knowledge construction of space brought users into the process, which improved the relevance of the content, although the reliability declined relatively. From the perspective of content diversification, the Superstar mobile library provided users with a great number of video and audio resources. Their update speed was also fast, which effectively improved the efficiency of users’ information acceptance.
(4) Service scenario assessment results
The service scenario was more important in the function of a mobile library. Each library emphasized the development of standardization and personalization in service scenarios. The mobile library attached great importance to the feedback speed of each service platform to ensure smooth communication between users and librarians and ensured the development of the real-time function of timely feedback and consultation. In the context of a mobile library, users can effectively maintain their privacy. Functions were developed to make usage as convenient as possible, in line with user habits, and the interface was beautiful and simple. Therefore, the user experience was greatly improved, as shown in Fig. 7.
Figure 7: User experience effect map
Unfortunately, there was no effective data to share and communicate scores between various platforms. The interface counts could not be fully invoked, which may affect the user experience. Therefore, mobile libraries need to pay attention to the sharing of data and resources, and try to build different applications and interfaces, and make mutual calls between different systems.
There were still some deficiencies in the personalized service mobile libraries offered, which leads to a decrease in user experience, the inability of users to achieve effective response speed, and the inability to meet information demands on time. This showed that the development of mobile libraries might be subject to some restrictions, which resulted in mobile library resources not being fully utilized. Currently, the mobile library needs to strengthen its application of situational awareness and integrate social applications such as WeChat and microblog. A third-party application programming interface (API) can be used to obtain users’ behavior data, and capture personalized recommendations based on users’ hobbies and needs. This information can then be used to accurately push resources to users and provide them with extended and expanded knowledge services. This can help mobile libraries to strengthen the construction of situational awareness and improve user experience and satisfaction.
This paper first analyzed the characteristics of the mobile library and examined its development and changes in different periods. Second, the application of situational awareness technology in the environment of big data and the IoT were analyzed and combined with the intelligent trends of a mobile library. A situational awareness analysis of personalized recommendation services by the mobile library was based on influencing factors such as user reception. In the mobile library, this can be an obstacle to the current application of situational awareness technology, that is, the compatibility of devices and the slow update of other hardware.
Funding Statement: This work is funded by the National Office of Philosophy and Social Sciences from the National Social Science Fund of China (Grant No. 19BTQ045). Haixu Xi received the grant and the URLs to sponsors’ websites is http://www.nopss.gov.cn/.
Conflicts of Interest: These are no potential competing interests in our paper. And all authors have seen the manuscript and approved to submit to your journal. We confirm that the content of the manuscript has not been published or submitted for publication elsewhere.
1. G. Xu, X. Li, L. Jiao, W. Wang, A. Liu et al., “BAGKD: A batch authentication and group key distribution protocol for VANETs,” IEEE Communications Magazine, vol. 58, no. 7, pp. 35–41, 2020. [Google Scholar]
2. Y. J. Ren, J. Qi, Y. Cheng, J. Wang and A. Osama, “Digital continuity guarantee approach of electronic record based on data quality theory,” Computers, Materials & Continua, vol. 63, no. 3, pp. 1471–1483, 2020. [Google Scholar]
3. L. Fang, Y. Li, X. Yun, Z. Wen, S. Ji et al., “THP: A novel authentication scheme to prevent multiple attacks in SDN-based IoT network,” IEEE Internet of Things Journal, vol. 7, no. 7, pp. 5745–5759, 2020. [Google Scholar]
4. S. Durga, S. Mohan, J. D. Peter and S. Surya, “Context-aware adaptive resource provisioning for mobile clients in intra-cloud environment,” Cluster Computing, vol. 22, no. 4, pp. 9915–9928, 2019. [Google Scholar]
5. C. Ge, W. Susilo, Z. Liu, J. Xia, P. Szalachowski et al., “Secure keyword search and data sharing mechanism for cloud computing,” IEEE Transactions on Dependable and Secure Computing, vol. 20, no. 8, pp. 1–12, 2020. [Google Scholar]
6. J. Huang, W. Lee and T. Lin, “Developing context-aware dialoguing services for a cloud-based robotic system,” IEEE Access, vol. 7, pp. 44293–44306, 2019. [Google Scholar]
7. X. Fan, Y. Hu, Z. Zheng, Y. Wang, P. Brézillon et al., “CASR-TSE: Context-aware web services recommendation for modeling weighted temporal-spatial effectiveness,” IEEE Transactions on Services Computing, vol. 14, no. 1, pp. 58–70, 2021. [Google Scholar]
8. K. Wu, W. Liu and S. Wu, “Dynamic deployment and cost-sensitive provisioning for elastic mobile cloud services,” IEEE Transactions on Mobile Computing, vol. 17, no. 6, pp. 1326–1338, 2018. [Google Scholar]
9. Y. Ren, Y. Leng, J. Qi, K. S. Pradip, J. Wang et al., “Multiple cloud storage mechanism based on blockchain in smart homes,” Future Generation Computer Systems, vol. 115, no. 3, pp. 304–313, 2021. [Google Scholar]
10. M. A. Razzaque, M. Milojevic-Jevric, A. Palade and S. Clarke, “Middleware for Internet of Things: A survey,” IEEE Internet of Things Journal, vol. 3, no. 1, pp. 70–95, 2016. [Google Scholar]
11. C. P. Ge, W. Susilo, J. Baek, Z. Liu, J. Xia et al., “Revocable attribute-based encryption with data integrity in clouds,” IEEE Transactions on Dependable and Secure Computing, vol. 21, no. 3, pp. 1–12, 2021. [Google Scholar]
12. J. Hu, L. Zhang, J. Li and Q. Wang, “A new mixed clustering-based method to analyze the gait of children with cerebral palsy,” Computers, Materials & Continua, vol. 66, no. 2, pp. 1551–1562, 2021. [Google Scholar]
13. L. Atzori, A. Iera and G. Morabito, “The Internet of Things: A survey,” Computer Networks, vol. 54, no. 15, pp. 2787–2805, 2010. [Google Scholar]
14. J. Xiong, R. Bi, M. Zhao, J. Guo and Q. Yang, “Edge-assisted privacy-preserving raw data sharing framework for connected autonomous vehicles,” IEEE Wireless Communications, vol. 27, no. 3, pp. 24–30, 2020. [Google Scholar]
15. S. Li, T. Tryfonas and H. Li, “The Internet of Things: A security point of view,” Internet Research, vol. 26, no. 2, pp. 337–359, 2016. [Google Scholar]
16. Y. J. Ren, F. Zhu, J. Wang, P. Sharma and U. Ghosh, “Novel vote scheme for decision-making feedback based on blockchain in internet of vehicles,” IEEE Transactions on Intelligent Transportation Systems, vol. 21, no. 8, pp. 1–10, 2021. [Google Scholar]
17. Y. Yang, L. Wu, G. Yin, L. Li and H. Zhao, “A survey on security and privacy issues in Internet-of-Things,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1250–1258, 2017. [Google Scholar]
18. J. Hu, G. Hu, J. Cai, L. Xu and Q. Wang, “Hospital bed allocation strategy based on queuing theory during the COVID-19 epidemic,” Computers, Materials & Continua, vol. 66, no. 1, pp. 793–803, 2021. [Google Scholar]
19. S. Laghari and M. A. Niazi, “Modeling the Internet of Things, self-organizing and other complex adaptive communication networks: A cognitive agent-based computing approach,” PLOS ONE, vol. 11, no. 1, pp. e0146760, 2016. [Google Scholar]
20. T. Li, Y. Ren and J. Xia, “Blockchain queuing model with non-preemptive limited-priority,” Intelligent Automation & Soft Computing, vol. 26, no. 5, pp. 1111–1122, 2020. [Google Scholar]
21. C. P. Ge, W. Susilo, J. Baek, Z. Liu, J. Y. Xia et al., “A verifiable and fair attribute-based proxy re-encryption scheme for data sharing in clouds,” IEEE Transactions on Dependable and Secure Computing, vol. 21, no. 7, pp. 1–12, 2021. [Google Scholar]
22. B. Han, X. Yang, Z. Sun, J. Huang, J. Su et al., “OverWatch: A cross-plane DDoS attack defense framework with collaborative intelligence in SDN,” Security and Communication Networks, vol. 2018, no. 6, pp. 226–232, 2018. [Google Scholar]
23. J. Xing, X. Chen, Q. Yang, L. Chen, Z. Yao et al., “A task-oriented user selection incentive mechanism in edge-aided mobile crowdsensing,” IEEE Transactions on Network Science and Engineering, vol. 7, no. 4, pp. 2347–2360, 2020. [Google Scholar]
24. J. Y. Ren, F. Zhu, K. S. Pradip, T. Wang, J. Wang et al., “Data query mechanism based on hash computing power of blockchain in internet of things,” Sensors, vol. 20, no. 1, pp. 1–22, 2020. [Google Scholar]
25. P. Kamalinejad, C. Mahapatra, Z. Sheng, S. Mirabbasi and Y. Guan, “Wireless energy harvesting for the Internet of Things,” IEEE Communications Magazine, vol. 53, no. 6, pp. 102–108, 2015. [Google Scholar]
26. G. A. Akpakwu, B. J. Silva, G. P. Hancke and A. M. AbuMahfouz, “A survey on 5G networks for the Internet of Things: Communication technologies and challenges,” IEEE Access, vol. 6, pp. 3619–3647, 2018. [Google Scholar]
27. Z. Chen, Y. Tian and C. Peng, “An incentive-compatible rational secret sharing scheme using blockchain and smart contract,” Science China-Information Sciences, vol. 64, no. 10, pp. 2858–2870, 2021. [Google Scholar]
28. K. Sood, S. Yu and Y. Xiang, “Software-defined wireless networking opportunities and challenges for Internet-of-Things: A review,” IEEE Internet of Things Journal, vol. 3, no. 4, pp. 453–463, 2016. [Google Scholar]
29. Y. J. Ren, Y. Leng, Y. Cheng and J. Wang, “Secure data storage based on blockchain and coding in edge computing,” Mathematical Biosciences and Engineering, vol. 16, no. 4, pp. 1874–1892, 2019. [Google Scholar]
30. N. Bizanis and F. A. Kuipers, “SDN and virtualization solutions for the Internet of Things: A survey,” IEEE Access, vol. 4, pp. 5591–5606, 2016. [Google Scholar]
31. C. Ge, Z. Liu, J. Xia and L. Fang, “Revocable identity-based broadcast proxy re-encryption for data sharing in clouds,” IEEE Transactions on Dependable and Secure Computing, vol. 18, no. 3, pp. 1214–1226, 2021. [Google Scholar]
32. B. Akinci and B. Akinci, “Situational awareness in construction and facility management,” Frontiers of Engineer Management, vol. 1, no. 3, pp. 283–289, 2015. [Google Scholar]
33. Y. Ren, J. Qi, Y. Liu, J. Wang and G. Kim, “Integrity verification mechanism of sensor data based on bilinear map accumulator,” ACM Transactions on Internet Technology, vol. 21, no. 1, pp. 1–19, 2021. [Google Scholar]
34. L. Russell, R. Goubran, F. Kwamena and F. Knoefel, “Agile IoT for critical infrastructure resilience: Cross-modal sensing as part of a situational awareness approach,” IEEE Internet of Things Journal, vol. 5, no. 6, pp. 4454–4465, 2018. [Google Scholar]
35. A. Kissinger-Knox, P. Aragon and M. Mizrahi, “Does non-moral ignorance exculpate? situational awareness and attributions of blame and forgiveness,” Acta Analytica, vol. 33, no. 2, pp. 161–179, 2018. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |