DOI:10.32604/iasc.2022.023372

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.023372 |  |
| Article |
A Cloud-Based Secure Emergency Message Dissemination Scheme in Vehicular Adhoc Networks
1Department of Information and Communication Engineering, Anna University, Chennai, India
2Department of Electronics and Communication Engineering, Dr. N.G.P. Institute of Technology, Coimbatore, India
*Corresponding Author: R. Rajasekar. Email: rajasekar.sept@gmail.com
Received: 06 September 2021; Accepted: 29 October 2021
Abstract: The Internet of vehicles and vehicular ad-hoc networks (VANET) offers numerous opportunities for managing the transportation problems effectively. The high mobility and wireless communication in VANET lead to adequate network topology modifications, resulting in network instability and insecure data communication. With an unsteady flow of traffic, vehicles are unevenly distributed in the geographical areas in practice. A new type 2 fuzzy logic-based secure clustering (T2FLSC) with cloud-based data dissemination scheme called the T2FLSC-CDD model for the VANET has been introduced for resolving this issue. The vehicles are dynamically clustered by the use of the T2FLSC technique, which elects the CHs (Cluster Head) by the use of different parameters, namely, travelling speed (TS), link quality (LQ), trust factor (TF), inter-vehicle distance (IVD) and neighboring node count (NCC). The inclusion of the trust factor helps to select the proper CHs for the secure data dissemination process. Once the CHs are selected, a cloud connection can broadcast the Emergency messages to every vehicle. To save the location details of the vehicles in the cloud securely, the Blowfish technique has also been implemented in this work. For validating the effectiveness of the T2FLSC-CDD model, an extensive results analysis has been performed with respect to various measures. The attained simulation outcomes have pointed out that the proposed model has achieved maximum packet delivery ratio (PDR) and throughput with minimum key computation time (KCT), routing control overhead (RCO), time delay (TD), and key recovery time (KRT).
Keywords: VANET; data dissemination; cloud; clustering; CH
The developing application of the Internet of things (IoT) has been converted to several domains, and one of the existing models is the Vehicular Ad Hoc Networks (VANETs), which has been transformed as a novel method of vehicles and has been named as the Internet of Vehicles (IoV) [1]. IoV plays significant roles in developing a dynamic system of vehicles for enhancing the Intelligent Transport System (ITS) with an aim of achieving effective data interchange from the other vehicles. It is capable of withstanding novel applications like road safety, entertainment, and traffic control that are difficult to analyze in their early stages. Under the application of IoV, the modifications in VANETs could be identified easily that shares data with one another and Road Side Units (RSUs). IoV has the structure of extending and improvising the reliability of VANETs for improving the travelling services and driver awareness by monitoring the traffic status, especially to guide and prevent road accidents, identify lower congested routes, and minimize the fuel application as well as air pollution [2,3]. The depiction of the maximum-level IoV communication method has been illustrated in Fig. 1. This technique helps in increasing the reliability of the vehicular networks for providing the appropriate routes for the drivers.
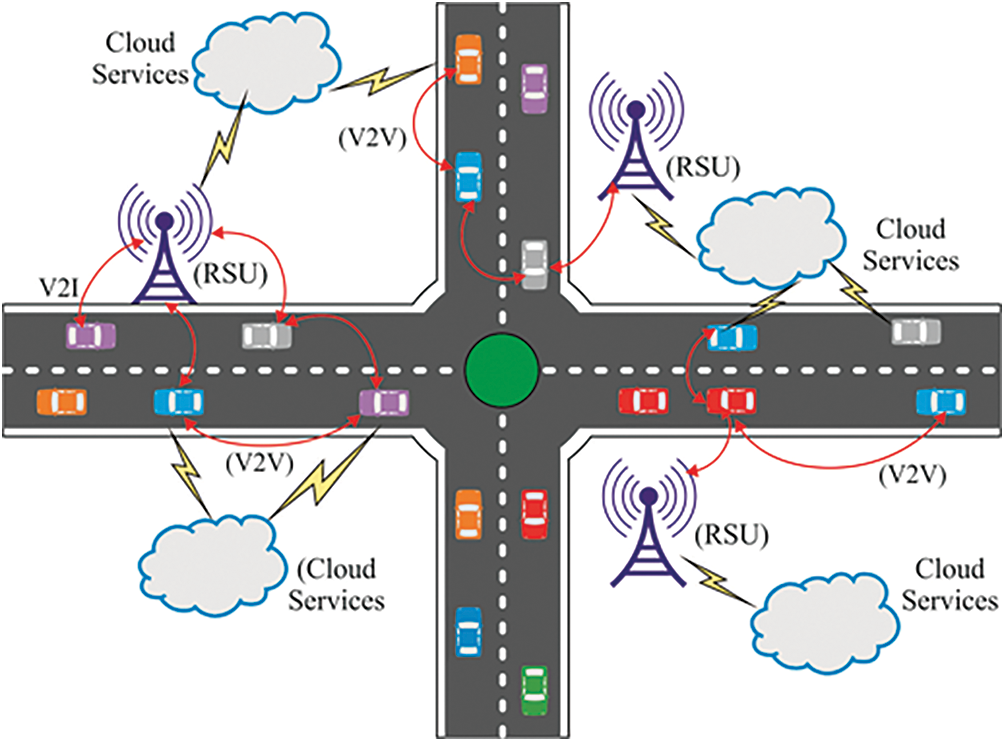
Figure 1: Internet of vehicles-communication paradigm
Vehicles rely on a multi-hop technique for forwarding the messages among each other due to the reduced wireless transmission radius [4,5]. Followed by which the radio signals would be applied for accomplishing the communication procedures that tend to integrate in the form of vehicle density at times of increased road accidents. At this point, an easy technique such as the broadcasting technique through flooding has been observed to be more expensive and thus leads to redundant communications, contentions, and collisions in the current system. It is called as a broadcast storm issue and as a spectrum scarcity. From the public side, the effective dissemination of data from vehicles can be acquired when the drivers are found to be interested in achieving relevant traffic details.
An ineffective central management system would trigger the dynamic location of the vehicles to cause network instabilities and broadcasting problems, these factors would degrade the functioning of the entire network. A feasible solution is to deploy the RSUs that may be applicable in scheduling and controlling the dynamic systems. But, the access points have been found to include additional embedding and maintenance expenses. The alternate solution is to develop clusters dynamically according to the general metrics for fixing the vehicles on the road. Followed by which the same would be applied for improving the lifespan of a connection by gathering parameters like speed, external position, and travel directions. These clusters can be used on the vehicles for forwarding the messages to the Cluster Head (CH) that would again broadcast the same to the cluster members (CM). Here, there are few limitations, namely, stability, which has to be reported for improving the lifetime of a network and its corresponding channel fading effects.
In the last decades, Cloud Computing (CC) was used for managing the complex processing procedures that were deployed locally. The integration of VANET and CC has improved the ability of a system [6,7]. In general, the mobiles can upload the time utilization, and power application work in clouds. On the other hand, the cloud-based VANET obtains the spontaneous traffic flows that comprises of the macro-controls of the local positions of the individual vehicles that develops the précised decisions of the congestion and traffic flows that computes the expected regions and reliable applicants respectively. Hence, it is applicable for forwarding the protective messages with the location of the accident case, seriousness of the accident, computation of the accident time, and diverse routes for vehicles shared in various cases. To resolve this issue, a new type 2 fuzzy logic-based secure clustering (T2FLSC) with the cloud-based data dissemination scheme called the T2FLSC-CDD model for VANET has been proposed. For validating the effectiveness of the T2FLSC-CDD model, an extensive result analysis has been performed with respect to the following measures such as, packet delivery ratio (PDR), throughput, delay, routing overhead and execution time.
The rest of the paper has been organized as follows. Section 2 offers a brief review of the existing works, and Section 3 discusses the proposed model. In addition, Section 4 provides the experimental validation, and Section 5 concludes the paper.
Several kinds of traditional message disseminating principles have been developed. The protective messages can be transferred to the Internet under the Internet under gateways and can be dispatched to the vehicles present in their respective areas. Along with a comprehensive deployment of the 3G/4G base stations (BS), developers focus on a gateway selection model for linking the VANET to the Internet. In [8], a gateway selection approach has been presented by assuming the traffic preferences for ensuring the Quality of Service (QoS). Regardless, it is pointed that many types of classical works mainly aims at the uplink criteria that assists the model in choosing the appropriate gateway by an initial vehicle for appropriately loading a message, whereas the downlink messages have also been assumed here. In [9], the researchers have applied the Connection Stability Aware Partner-based Hierarchical Mobile IPv6 (CSA-PHMIPv6) where the mobile nodes would choose the pairs with communication, these pairs have been found to withhold enough time durations with the help of the Link Expiration Time (LET) parameter.
The modeling of the CC method emerges in VANET and this effectively produces the model of the vehicular CC [10]., implied the method that focuses on the migration of the individual IP services among a data centre(DC) and an optimized DC without any interruption. In [11], the author has defined the complexities in the current mobile network equipments, and has depicted the feasibility of expanding the CC more than the DC to a mobile user that offers an end-to-end mobile connection with a cloud service (CS). In [12], the author has presented the suggestion of the vehicular clouds by consuming the conventional VANET of the clouds. This has been inspired by many sensor nodes installed on the vehicles, streets and parking regions, it offers massive communication and processing resources and offers numerous advantages to the resource providers. In [13], the technique has been signified with the taxonomy of the upcoming VANET clouds. In addition, it has defined the complexities of trust in the VANET clouds. A set of 3 kinds of vehicular computing has been listed as follows [14]:
• Networks as a Service (NaaS)
• Storage as a Service (STaaS)
• Data as a Service (DaaS)
The major application of the NaaS model is that the cloud can collect the data of vehicles that wants to provide the Internet access; it also gives an appropriate link to the vehicle when there is a requirement. In [15], the technique has been developed with a model for guiding the search of the vehicles for the dynamic cloud servers that tend to migrate to the nearby positions. This method tends to minimize the RSUs in the cloud dimensions for saving the registration of the mobile cloud servers. The RSU involves in the distribution of the registration details for activating the vehicles for both identifying and applying for the facilities of the dynamic cloud servers within the provided region. Some other techniques related to the solutions in VANET are also present in the literature [16–22].
3 The Proposed T2FLSC-DSS Model
The overall working principle of the proposed T2FLSC-DSS model has been illustrated in Fig. 2. Initially, a network would be constructed with a set of vehicles and the neighborhood discovery would take place using the Wireless Access in Vehicular Environment (WAVE) protocol. Later, the sensor linked to the vehicles would gather the details such as speed, distance, etc. Then, the vehicles would be dynamically clustered by the use of the T2FLSC technique that would elect the CHs using the various parameters such as travelling speed (TS), link quality (LQ), trust factor (TF), inter-vehicle distance (IVD) and neighboring node count (NCC). The inclusion of the trust factor would assist in the selection of proper CHs for accomplishing secure data disseminations. With the selection of the CHs, a cloud connection can broadcast the emergency messages to the individual vehicles. To save the location details of the vehicles in the cloud securely, the Blowfish technique has also been implemented in this work. The main objective of this process is to improve the security level and reduce the latency period. A vehicle to cellular structure interaction has been activated for broadcasting a message. The entire process can be listed as follows:
• Neighbour identification
• Sensor values
• CH election
• Cloud data storage
• Trust
• Broadcasting
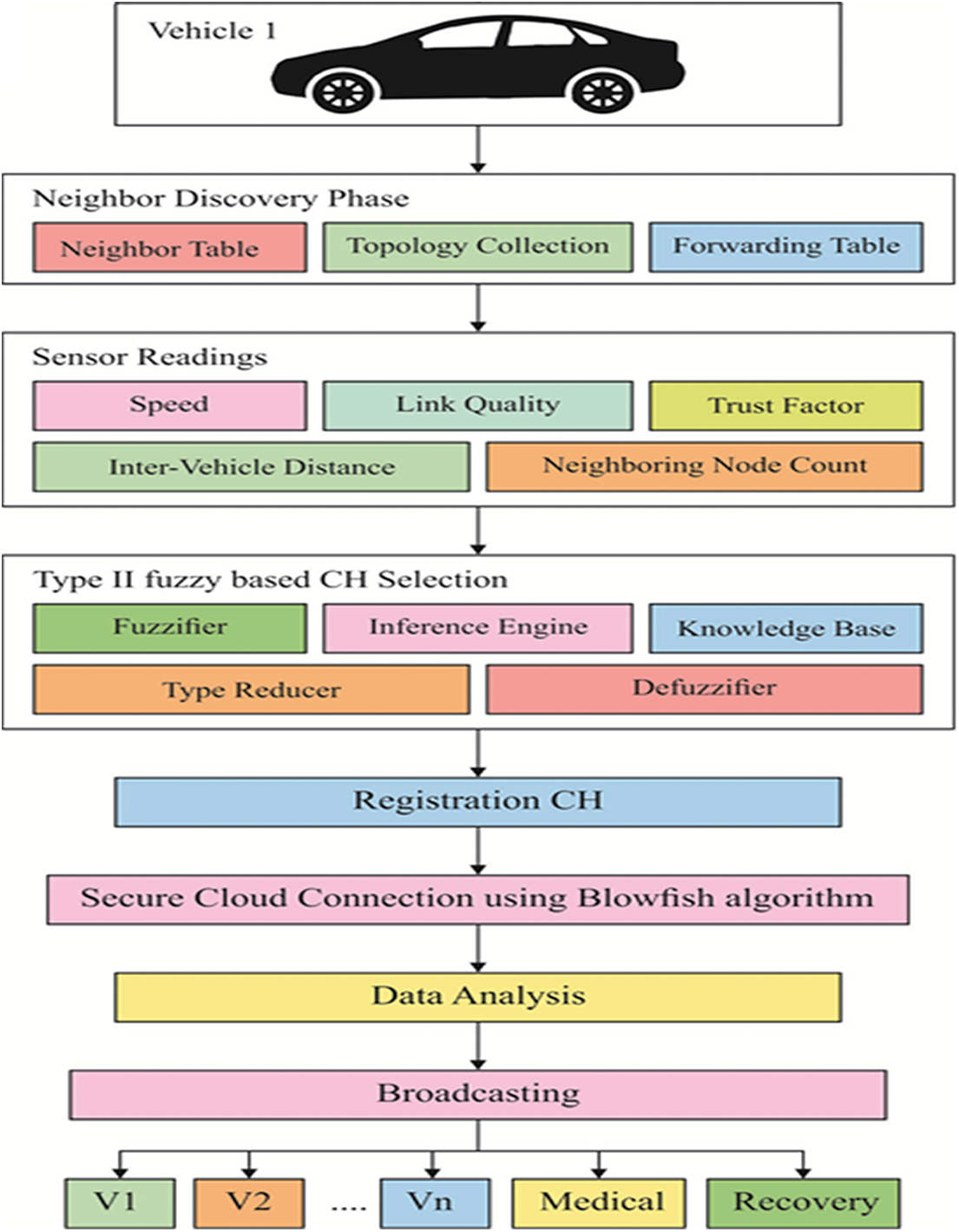
Figure 2: Overall process of the proposed method
The network topology has been deployed with n number of vehicles. Later, the sensor connected to the vehicle can be employed for acquiring the position and traffic details. WAVE assisted IEEE 802.11p method has been applied. It helps in minimizing the network delay. A particular CH can be elected for constructing the routes among the source and destination nodes during the message transmission process. Once the CH registration has been completed, a cloud link would be activated for enhancing the trust levels, this can essentially eliminate the unauthenticated data monitoring. The data transfer can be improved with the application of the blowfish concept. As a result, data analysis has been carried out for transmitting a predominant message to the alternate vehicles.
A table has been developed with n number of vehicles i.e., According to the concerned data, the network topology has been developed for accomplishing data transmission procedures. The WAVE protocol has been applied for performing this action that entirely depends upon the IEEE 802.11p standard. The stability has been boosted as well as the delay aspect has been limited in the network using this mechanism. A significant cause of applying WAVE is that it functions according to the multi-channel technique for transferring the mere infotainment data. It assures the delivery of a message with a stable and limited time period. Thus, it appears to be more applicable for the VANET based communication. Fig. 3 depicts the channels applied in the IEEE 802.11p standard that encompasses service, control channel, accident removal, secure life, maximum energy, and longer range channels.

Figure 3: Channels in the IEEE 802.11p standard
Here, the vehicles have been deployed with various sensors for providing the data on temperature, speed, and location. This data can be majorly applied for controlling traffic, road surface detection, and vehicle tracking. The main aim of vehicle monitoring is to minimize the transmission overhead and ensure table interaction. In general, the OBU is considered as a wave device that can be applied by the vehicles for interchanging the series. These units have been constrained with the processing ce for obtaining the required data, and an interface for interacting with the alternate networks relied on the IEEE 802.11p standard. The purpose of employing the OBU is that it is a wireless radio, blocking management, and a wireless radio, blocking management, and secured message. Additionally, it improves the transmission radius by transmitting data to the corresponding OBU. Hence, the message dissemination has been activated under the application of sensors for identifying the distance between the source and the destination nodes.

3.3 Type II Fuzzy Logic Based Secure Clustering (T2FLSC) Protocol
In VANET, a CH might be assumed as a constant deployment in a roadside according to the transmission radius. Every vehicle would address the present location to the CH. Here, the CH election is activated based on an auto-configuration as it is treated as a location server and records the position details of the individual vehicles. Regarding the details, the route has been built her for the data transfer procedures. Once the CH is elected, the vehicles would be registered in the CH along with a secure and exclusive ID together with a password. Initially, a vehicle would produce an arbitrary secret value that would assist in the computation of the ID and the password. Subsequently, it would forward the registration request to the High Way Authority (HWA) through a protective station. After receiving the request, an arbitrary value would be produced for estimating the ID of the desired vehicle. When a vehicle is linked with a cellular network, the pre-registration process would be carried out, and a random bit identity would be originated for the data transmission purpose.
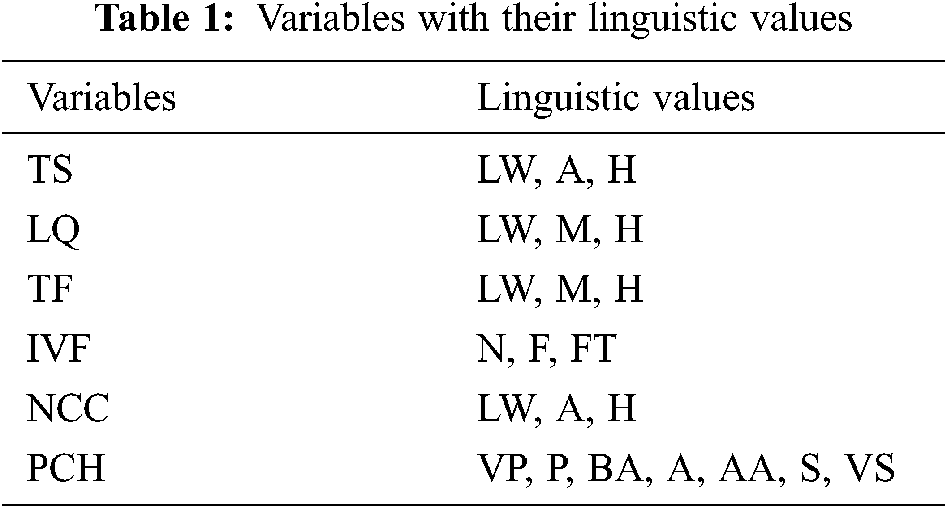
For selecting the CH, a new model has been employed termed as the Fuzzy Logic (FL). This FL has five input variables such as TS, LQ, TF, IVD and NCC. Followed by which the output features would be comprised with a probability of becoming the CH (PCH). Initially, T would represent the mobile speed of a vehicle, LQ would represent the superiority of the connected vehicles, TF would represent the intensity of its stability, IVD would signify the distance from the vehicles, and NCC would refer to the number of vehicles placed in the nearby location.
T2FL contains 4 levels as depicted in Fig. 4 that is represented as follows:

Figure 4: T2FL model
It is used for converting the actual inputs as fuzzified values. Few input features in-terms of the linguistic attributes have been used for selecting the CH and the cluster size listed in Tab. 1. Here, there are some linguistic parameters for the RE which is low, medium and high. Similarly, the linguistic features of the DBS appears to be near, far, farthest, while for the ND it is minimum, moderate, maximum, correspondingly.
Fuzzy rules/Inference engine
The structure of the T1FL and the T2FL appears to be identical. Here, a collection of 27 rules have been applied. Later, the groups of fuzzy rules for the CHs and the deciding cluster sizes have been portrayed in Tab. 2. Hence, the rule is provided by Eq. (1).
where i represents the ith rule from a fuzzy rule, A1, A2, and A3 represent their corresponding fuzzy sets of x1, x2 and x3. The rule based inference engine has been constrained with 27 rules and generated according to the Mamdani Inference model. Collections of the fuzzy rules have been portrayed in Tab. 2. In case of the type-2 FLS, the inference engine merges the rules and the map input type-2 fuzzy sets and the resultant type-2 fuzzy sets. Hence, the estimation of the unions together with their intersections appears to be essential.

T2FL is represented by the supervised membership function (MF) and the inferior MF. These expressions have been shown under the application of the T1FL MF. Next, the space from the two functions signifies a Footprint of Uncertainty (FOU) that describes the T2FL set. Suppose FOU is provided as f. If f є [0, 1], and f → 0, hence MF is termed as T1FL. When f → 0 to 1the T2FL should comprise of different ranges for the FOU that can lie between 0 to 1. However, the development of rules in the T2FL has been found to be similar to that of the T1FL that has been expressed in Eq. (2):
where, L-Less, A-Average, H-high, N-Near, F-Far, FT-Farthest, LW-Low, M-Medium, VP-Very poor, P-Poor, BA-Below Average, AA-Above Average, S-Strong, VS-Very Strong.
Once the PCH has been received, it would broadcast the message to the target vehicles. This message would be enclosed with the vehicle ID and the PCH measures. A vehicle possessing a higher probability would be elected as the CH and would transmit the CH_WON to the corresponding vehicles. Only some vehicles would receive numerous CH_WON from the neighboring vehicles. At this point, it would transmit a CH_JOIN message and would combine it with a closer CH. With the reception of the CH_JOIN message, the nearby CH would verify the given cluster size before including the new members. As the complete CM does not exceed the determined cluster size, it would approve a new CM by means of forwarding the CM_ACCEPT message; otherwise, it would transmit the CH_REJECT message.
When a vehicle receives a CM_REJECT message, it would re-transmit a CM_JOIN message to the future CH with no assumptions of the removed CH, which would be repeated until a new CH is explored. Also, the vehicle cannot be combined with another CH that exists inside a coverage region ‘R’, and then it would select the corresponding CH. Consequently, every vehicle would belong to a cluster in which the separated vehicles would appear in the VANET. By processing the various rounds efficiently the premature death of the CHs can be eliminated, and the rotation function can be carried out by a CH. When the Remaining Energy (RE) of a CH appears to be higher than the threshold value the CH rotation would exist. While the RE of a CH exceeds a threshold value, a new CH would be selected using the PCH. Such functions have been observed to eliminate the primary death of the CH and thereby enhance the lifetime of the network.
3.3.2 Type Reducer/Defuzzifier
Defuzzifier is the process of producing a quantifiable result in the Crisp logic, fuzzy sets and corresponding membership degrees. It is the process that maps a fuzzy set to a crisp set. It is typically needed in the fuzzy control systems. This model produces a T1FL result which has been reformed to the mathematical result after the implementation of a defuzzifier has been completed.
In this study, a blowfish method has been applied for eliminating the third-party users’ data monitoring. The primary cause for enabling the cloud-assisted communication in this process has been given below:
• It removes the broadcast storm issue by controlling the individual nodes from a network effectively.
• It is sufficient to solve this with a massive number of nodes.
• Network connectivity is based on the centralized or the decentralized function of a system.
In VANET, the data broadcast has been processed for distributing the emergency data, climatic conditions, and traffic information of the vehicles. Broadcast storm arises due to the sheer amount of simultaneous communications and network terminal issues. It is the constantly varying location and transmitter’s position that influences the multi-dimensional type of broadcasting. Hence, it is has become mandatory for electing the desired vehicle at the combination of message broadcast. Here, the CH selection is carried out and the CC has been activated prior to the telecast of the emergency details to that of the alternate vehicles. It improves the speed of the data transfer process in an effective way. The significant benefits of this study have been listed below:
• Limited delay
• Enhanced trust
• Maximum communication efficiency.
This section briefly explains the experimental results offered by the proposed model over the compared methods under several aspects. The proposed model has been simulated using the NS3 tool. The proposed model has been validated with respect to the following aspects such as, PDR, throughput, key computation time (KCT), routing control overhead (RCO), time delay (TD), and key recovery time (KRT).
Fig. 5 investigates the PDR analysis of the proposed model over the existing methods under varying vehicle speeds. The figure shows that the BPAB model has achieved minimum PDR and the 3P3B model reaches slightly higher PDR values. It is also demonstrated that the UMBP has offered competitive results by achieving higher PDR values over the compared methods except for the T2FLSC-CDD model. But, it has been shown that the T2FLSC-CDD model has offered the maximum PDR For a given instance under the minimum vehicle speed of 50Km/h, it can be observed that the T2FLSC-CDD model provides a maximum PDR of 96% whereas the BPAB, 3P3B and UMBP models have offered lower PDR values of 52%, 85% and 90% respectively.
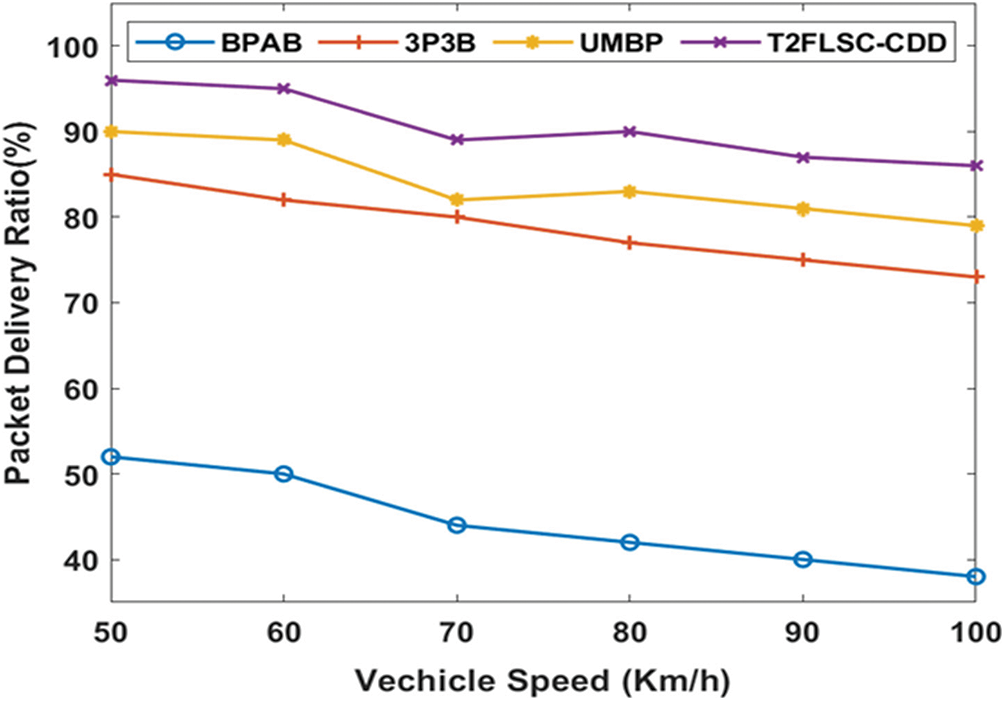
Figure 5: PDR analysis under varying vehicle speed
Similarly, under the maximum vehicle speed of100 Km/h, it has been ensured that the T2FLSC-CDD model has resulted to a maximum PDR value of 86%. In contrast, the BPAB, 3P3B, and UMBP models have lower PDR values of 38%, 73% and 79%, respectively. These values have ensured that the T2FLSC-CDD model had offered maximum PDR under varying vehicle speeds over the compared methods.
Fig. 6 examines the throughput analysis of the presented system compared with that of the traditional models with diverse vehicle speeds. The figure clearly shows that the 3P3B technique has reached the least throughput and slightly better throughput measures have been attained by the UMBP approach. Also, it has been depicted that the BPAB provides equivalent results by accomplishing maximum throughput rates than the related modules without the T2FLSC-CDD model. However, it has been observed that the higher throughput value has been obtained by the T2FLSC-CDD method. For the sample, by using a lower vehicle speed of 50Km/h, it is monitored that the T2FLSC-CDD technology gives greater throughput of 91000 kbps while the BPAB, 3P3B, and the UMBP techniques offer reduced throughput rates of 85200, 85500 and 86200 kbps correspondingly.
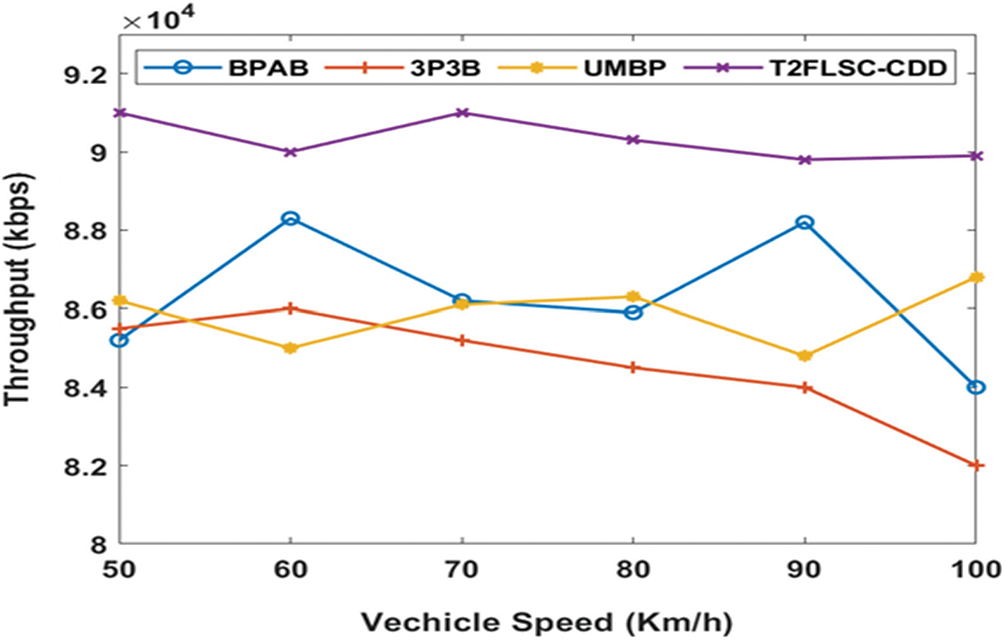
Figure 6: Throughput analysis under varying vehicle speed
Likewise, under the application of a high vehicle speed of 100 km/hr, it has been assured that the T2FLSC-CDD model tends to produce a maximum throughput value of 89900 kbps and the BPAB, 3P3B, and the UMBP modules has provided minimum throughput values of 84000, 82000 and 86800 kbps respectively. Such values have ensured that the T2FLSC-CDD model has given optimal throughput values under different vehicle speed than that of the other techniques.
4.3 Key Computation Time (KCT) Analysis
Fig. 7 analyzes the KCT analysis of the projected model over the conventional approaches using the diverse key sizes. The figure shows that the NTRU technique has accomplished higher KCT, and slightly lesser KCT measures were achieved by the VGKM method. Additionally, it has been depicted that the EGKM framework has given competing outcomes by reaching very less KCT values when compared with the alternate techniques except that of the T2FLSC-CDD model. Therefore, it has been stated that the minimum KCT has been provided by the T2FLSC-CDD method. For example, with the application of a lower key size of 64 bits, the T2FLSC-CDD module gives a lower KCT of 3600 ms while the NTRU, the VGKM and the EGKM approaches have offered greater KCT values of 3050, 2800 and 2000 ms correspondingly. Likewise, by applying a good key size of 512bits ensures that the T2FLSC-CDD model has the least KCT value of 2800 ms and the NTRU, the VGKM and the EGKM have given maximum KCT values of 5050, 4200 and 3950 ms respectively. These values thus show that the T2FLSC-CDD approach has given lesser KCT with diverse key sizes than that of the compared models.
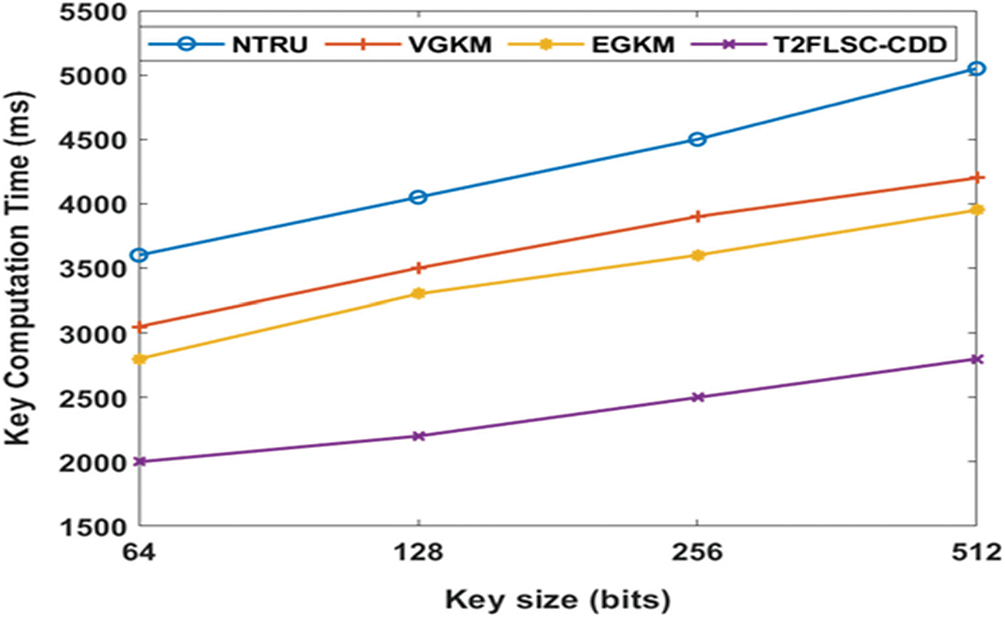
Figure 7: KCT analysis under varying key sizes
4.4 Routing Control Overhead (RCO) Analysis
Fig. 8 determines the RCO analysis of the deployed technique over the other methods under varying vehicle speeds. The figure shows that the BPAB system has attained higher RCO, and slightly decreased RCO measures have been reached by the 3P3B methods. It has been illustrated that the UMBP technique has produced a comparative outcome by accomplishing even the least RCO values when compared with the other approaches except for the T2FLSC-CDD model. Hence, it is depicted that the T2FLSC-CDD model has given the minimum RCO. For the sample, with the application of a lower vehicle speed of 50Km/hr, it has been shown that the T2FLSC-CDD model offers a lower RCO of 15% while the BPAB, the 3P3B and the UMBP frameworks have provided greater RCO values of 36%, 28% and 23% correspondingly. In the same way, using a higher vehicle speed of 100Km/hr guarantees that the T2FLSC-CDD model has reached a minimum RCO value of 32% and the BPAB, the 3P3B and the UMBP has offered higher RCO values of 51%, 46% and 41% respectively. These values have ensured that the T2FLSC-CDD model had given the least RCO under differing vehicle speeds than that of the compared approaches.
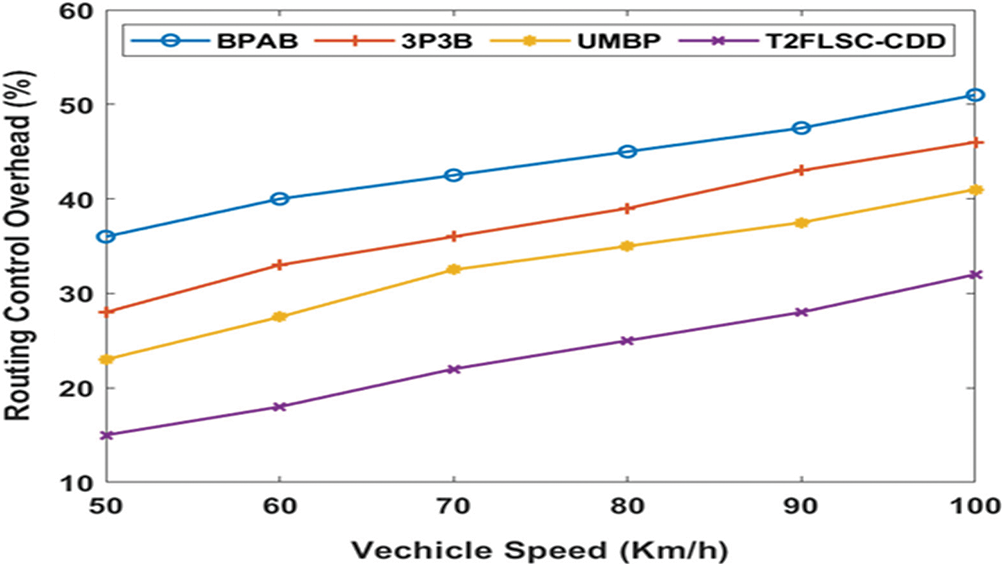
Figure 8: RCO analysis under varying vehicle speed
Fig. 9 defines the TD analysis of the developed system over the classical models with diverse vehicle speeds. The figure shows that the BPAB model has attained higher TD and slightly better TD values have been reached by the 3P3B approach. Additionally, it indicates that the UMBP module has given competing results by reaching even the minimum TD values compared with the other mechanisms except for the T2FLSC-CDD model. Therefore, it is clear that the T2FLSC-CDD model has provided the lower TD. For instance, with a reduced vehicle speed of 50 Km/hr, it can be observed that the T2FLSC-CDD model gives a least TD of 200 ms and the BPAB, the 3P3B, and the UMBP models have reached maximum TD values of 590, 400 and 280 ms correspondingly. Likewise, with the application of the modified vehicle speed of 100Km/hr, it shows that the T2FLSC-CDD framework has concluded in a lesser TD value of 320 ms and the BPAB, the 3P3B and the UMBP models have provided the maximum TD values of 910, 650 and 420 ms respectively. These values thus demonstrate that the T2FLSC-CDD technology has reached the least TD under varying vehicle speeds over the compared models.
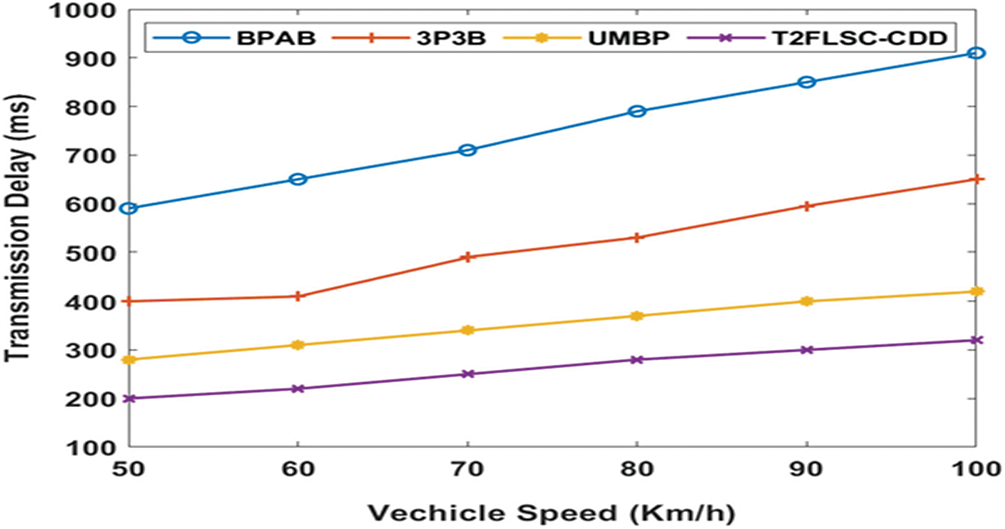
Figure 9: TD analysis under varying vehicle speed
4.6 Key Recovery Time (RCO) Analysis
Fig. 10 describes the KRT analysis of the presented system with the existing methods under varying key sizes. The figure shows that the NTRU technique has obtained higher KRT and the VGKM model accomplishes slightly lower KRT values. It is also shown that the EGKM model has provided equivalent results by reaching still lesser KRT values than the applied techniques except for the T2FLSC-CDD model. However, it is stated that the minimum KRT has been given by a T2FLSC-CDD method. For example, with the lower key size of 64 bits, it is monitored that the T2FLSC-CDD model offers a least KRT of 0.8 ms and the NTRU, the VGKM and the EGKM models have given higher KRT values of 1.42, 1.2 and 1.1 ms respectively. Similarly, under the maximum key size of 512 bits, it is ensured that the T2FLSC-CDD model tends to produce minimum KRT value of 1.2 ms while the NTRU, the VGKM and the EGKM models have offered greater KRT values of 2, 1.69 and 1.53 ms correspondingly. These values have ensured that the T2FLSC-CDD model has given minimum KRT by applying diverse key sizes when related with that of the alternate techniques.

Figure 10: KRT analysis under varying key sizes
This paper has presented a T2FLSC-CDD model for the cloud-based emergence message dissemination in VANET. The proposed model involves a set of different processes namely the neighborhood discovery phase, sensor reading, T2FLSC based CH selection, CH registration, secure cloud connection, data analysis and finally broadcasting. For validating the effectiveness of the T2FLSC-CDD model, an extensive result analyses have been carried out with respect to various measures. The obtained experimental analysis have clearly depicted that the T2FLSC-CDD model outperforms the earlier models in terms of PDR, throughput, KRT, RCO, TD and KCT. The simulation outcome thus shows that the proposed model has achieved the maximum PDR and throughput with minimum KRT, RCO, TD and KCT. In future, the performance of the proposed model can be enhanced by the inclusion of metaheuristic algorithms.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. J. Chen and G. Mao, “Capacity of cooperative vehicular networks with infrastructure support: Multi-user case,” IEEE Transactions on Vehicular Technology, vol. 67, no. 2, pp. 1546–1560, 2018. [Google Scholar]
2. T. Zhang, “Novel self-adaptive routing service algorithm for application of VANET,” Applied Intelligence, vol. 49, no. 5, pp. 1866–1879, 2019. [Google Scholar]
3. G. Hui, “New multi-hop clustering algorithm for vehicular ad hoc networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 20, no. 4, pp. 1517–1530, 2019. [Google Scholar]
4. T. Zhang, “A new method of data missing estimation with fnn-based tensor heterogeneous ensemble learning for internet of vehicle,” Neuro Computing, vol. 420, no. 1, pp. 98–110, 2021. [Google Scholar]
5. X. H. Liu, “Anew algorithm of the best path selection based on machine learning,” IEEE Access, vol. 7, no. 1, pp. 126913–126928, 2019. [Google Scholar]
6. L. Chen and J. Zhang, “A multi-path routing protocol based on link lifetime and energy consumption prediction for mobile edge computing,” IEEE Access, vol. 8, no. 1, pp. 69058–69071, 2020. [Google Scholar]
7. M. Piao and T. Zhang, “New algorithm of multi-strategy channel allocation for edge computing,” AEUE-International Journal of Electronics and Communications, vol. 126, no. 11, pp. 1–15, 2020. [Google Scholar]
8. G. Zhioua, N. Tabbane, H. Labiod and S. Tabbane, “A fuzzy multi-metric qos-balancing gateway selection algorithm in a clustered vanet to lte advanced hybrid cellular network,” IEEE Transactions on Vehicular Technology, vol. 64, no. 2, pp. 804–817, 2014. [Google Scholar]
9. T. Taleb and K. B. Letaief, “A cooperative diversity based handoff management scheme,” IEEE Transaction on Wireless Communications, vol. 9, no. 4, pp. 1462–1471, 2010. [Google Scholar]
10. T. Taleb and A. K. Sentini, “Follow me cloud: Interworking federated clouds & distributed mobile networks,” IEEE Network Magazine, vol. 27, no. 5, pp. 12–19, 2013. [Google Scholar]
11. T. Taleb, “Towards carrier cloud: Potential, challenges, & solutions,” IEEE Wireless Communications Magazine, vol. 21, no. 3, pp. 80–91, 2014. [Google Scholar]
12. S. Olariu, T. Hristov and G. Yan, “The next paradigm shift: From vehicular networks to vehicular clouds,” in Mobile Ad Hoc Networking: The Cutting Edge Directions, 2nd ed., New York, USA: IEEE Press, pp. 645–700, 2012. [Google Scholar]
13. M. Eltoweissy, S. Olariu and M. Younis, “Towards autonomous vehicular clouds,” in Ad Hoc Networks, Berlin, Heidelberg: Springer, pp. 1–16, 2010. [Google Scholar]
14. K. Mershad and H. Artail, “A framework for implementing mobile cloud services in vanets,” in IEEE 6th International Conference on Cloud Computing, Cloud Computing, Washington, D.C., USA, pp. 83–90, 2013. [Google Scholar]
15. M. Khaleel and H. Artail, “Finding a star in a vehicular cloud,” Intelligent Transportation Systems Magazine, IEEE, vol. 5, no. 2, pp. 55–68, 2013. [Google Scholar]
16. N. Kumar, J. J. P. C. Rodrigues and N. Chilamkurti, “Bayesian coalition game as-a-service for content distribution in internet of vehicles,” IEEE Internet of Things Journal, vol. 1, no. 6, pp. 544–555, 2014. [Google Scholar]
17. N. Kumar, S. Misra, J. J. Rodrigues and M. S. Obaidat, “Coalition games for spatio-temporal big data in internet of vehicles environment: A comparative analysis,” IEEE Internet of Things Journal, vol. 2, no. 4, pp. 310–320, 2015. [Google Scholar]
18. N. Kumar, N. Chilamkurti and J. H. Park, “ALCA: Agent learning–based clustering algorithm in vehicular ad hoc networks,” Personal and Ubiquitous Computing, vol. 17, no. 8, pp. 1683–1692, 2013. [Google Scholar]
19. S. Garg, A. Singh, K. Kaur, G. S. Aujla, S. Batra et al., “Edge computing-based security framework for big data analytics in VANETs,” IEEE Network, vol. 33, no. 2, pp. 72–81, 2019. [Google Scholar]
20. A. Ghaffari, “Hybrid opportunistic and position-based routing protocol in vehicular ad hoc networks,” Journal of Ambient Intelligence and Humanized Computing, vol. 11, no. 4, pp. 1593–1603, 2020. [Google Scholar]
21. H. Bagherlou and A. Ghaffari, “A routing protocol for vehicular ad hoc networks using simulated annealing algorithm and neural networks,” The Journal of Supercomputing, vol. 74, no. 6, pp. 2528–2552, 2018. [Google Scholar]
22. M. M. Nezhad and A. Ghaffari, “Hybrid routing scheme using imperialist competitive algorithm and RBF neural networks for VANETs,” Wireless Networks, vol. 25, no. 5, pp. 2831–2849, 2019. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |