DOI:10.32604/iasc.2022.020137

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2022.020137 |  |
| Article |
Developing Secure Healthcare Video Consultations for Corona Virus (COVID-19) Pandemic
1Department of Information Technology, College of Computers and Information Technology, Taif University, P.O. 11099, Taif 21944, Saudi Arabia
2Department of Computer Science and Engineering, Faculty of Electronic Engineering, Menoufia University, Menouf 32952, Egypt
3Department of Computer Science, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia
4Department of Electrical Engineering, Faculty of Engineering, Menoufia University, Shebin El-Kom 32511, Egypt
*Corresponding Author: Mohammed A. AlZain. Email: m.alzain@tu.edu.sa
Received: 11 May 2021; Accepted: 19 July 2021
Abstract: Many health networks became increasingly interactive in implementing a consulting approach to telemedicine before the COVID-19 pandemic. To mitigate patient trafficking and reduce the virus exposure in health centers, several GPs, physicians and people in the video were consulted during the pandemic at the start. Video and smartphone consultations will allow well-insulated and high-risk medical practitioners to maintain their patient care security. Video appointments include diabetes, obesity, hypertension, stroke, mental health, chemotherapy and chronic pain. Many urgent diseases, including an emergency triage for the eye, may also be used for online consultations and triages. The COVID-19 pandemic shows that healthcare option for healthy healthcare and the potential to increase to a minimum, such as video consultations, have grown quickly. The dissemination of COVID-19 viruses now aims at extending the use of Video-Health Consultations by exchanging insights and simulations of health consultations and saving costs and healthcare practices as a consequence of the COVID-19 pandemic. Our paper focuses on video consulting privacy. This essay further presents the advantages and inconveniences of video consultation and its implementation. This paper suggests the most recent video encryption method known as high efficiency video coding selective encryption (HEVC SE). Our video consultation schema has been improved to secure video streaming on a low calculation overhead, with the same bit rate and to ensure compatibility with the video format. The contribution is made with RC5, a low complexity computer, to encrypt subsets of bin-strings binarized in the HEVC sense using the context-adaptive binary arithmetic coding (CABAC) method through the bypass binary arithmetic coding. This sequence of binstrings consists of a non-zero differential transforming cosine (DCT) coefficient bit, MVD sign bits, remainder absolute DCT suffixes and absolute MVD suffixes. This paper also examines the efficiency assessment of the use of the RC5 with its modes of operations in the HEVC CABAC SE proposed. This study chooses the best operating mode for RC5 to be used for the healthcare video consultation application. Security analysis, such as histogram analysis, correlation coefficient testing and key sensitivity testing, is presented to protect against brute force and statistical attacks for the proposed schema.
Keywords: COVID-19; pandemic; healthcare video consultation; telemedicine; video compression; HEVC; video encryption; selective encryption
National digital health strategies are being used worldwide to improve patient care and potential health outcomes through a health infrastructure that can be safely accessed, easily manipulated, and shared responsibly. Digital medical consultations are one of the most important national digital health strategies, which have gained great interest with a special focus on video consultations (VCs) [1–5]. However, the general practitioners were relatively slow to support the VCs implementation because of small studies on limited patient groups. As a result, new video conference programs have appeared available free for all devices types like Skype and Zoom for personal and professional communication that concerns data protection and privacy regulations [6,7].
In the spring of 2020, the corona virus Disease (COVID-19) pandemic has spread suddenly and strongly, followed by a global societal lockdown in response to the World Health Organization (WHO) recommendations [8]. The increase in the lockdown period strongly impacted individuals’ services, organizations and governmental communities. As a consequence, healthcare facilities were exposed to the highest degree of emergency as the direct contact between clinician and patient has become a source of COVID-19 contagion. Therefore, medical physicians have been tried to consider alternative methods to avoid face-to-face visits and apply remote consultation, particularly for chronic conditions patients. As a result, there has been a global interest in VCs; the American medical association has recommended remote consultation during the COVID-19 pandemic, and telemedicine has been conducted in different specialties [9,10]. Through a video link, the clinical consultations trials have shown high satisfaction, no difference in treatment or service use and lower costs than traditional clinic-based care [11,12]. However, it is known that VCs are not suitable for all clinical situations; the recent clinicians’ guidance recommended the appropriate situations for VCs such as self-isolating clinicians, COVID-19 patients, heightened anxiety persons and people with symptoms similar to COVID-19 for reducing the contact.
Teleconferencing has received the attention of technical experts to raise efficiency, quality, and bit-stream size without extra cost and decrease quality loss in the current exceptional circumstances. The need for medical video compression to improve storage requirements and overcome video traditional lossless to avoid diagnostic errors can be achieved using HEVC. The HEVC technique effectively exploits the temporal and spatial redundancy observed in video sequences to deliver video resolutions beyond HD [13]. VCs may leak sensitive information because of the public channels insecurity and the service provider unreliability, which calls for a protection and cryptography method. Several means are designed in researches for image and video sensitive data encryption [14–20]. Naive Encryption Algorithm (NEA) is one of the first methods for video encryption as a binary sequence. However, NEA results suffer from high complexity in mobile devices and real-time transmission [21]. Selective encryption (SE) schemes protect the video content considering the video coding characteristics [22,23]. In the past decade, the H.265/HEVC codec raised the SE algorithms examination depending on the video compression domain to decrease computation cost. Nowadays, video coding standards adapted to multiple uses with compressing video techniques such as broadcasting and data storage. The high compression ratios have been achieved using CABAC coding with a reduced number of contexts coded and/or bypass coded bins [24].
This work examined a new teleconference system that employed an improved HEVC technology as a sufficient approach to enhance the video quality and the compression efficiency in the real-time VCs technology system. Many methods use common algorithms for selective video encryption, such as AES and DES. The main aim is to provide a selective encryption scheme for effective video health consultations. In this paper, the HEVC format for video coding, which can be used for video consultations in real-time, was introduced to provide a powerful selective encryption technique. The suggested strategy uses the RC5 block cipher algorithm to encrypt sign bits and suffix bits of the vector differences and discrete transformation of the motion. The proposed HEVC video consultation encoding technology requires the video bits to be encoded with low delays and HEVC bit rate and specification conformity regulation. This strategy will mean that it is confidential to easily share wellness video meetings on the Internet. In order to aid home patients in the security of access to medical care with distributed COVID-19, video consultations are required. The COVID-19 reduction would avoid the dissemination of COVID-19.
The rest of the work is organized as follows. Section 2 explores the previous related work. Section 3 introduces the HEVC preliminaries. Section 4 proposes the designed system. Section 5 explores and discusses the simulation analysis. Finally, the paper is concluded in Section 6.
COVID-19 has made telemedicine or VCs more accessible and applicable than before. Many researches are carried out to validate telemedicine processes, platforms, encryption and data storage. A data hiding scheme with improved commutative encryption to preserve HEVC the bit rate is proposed in [25]. The results proved that the bit rate in the framework unchanged with increasing the capacity of embedding. In [26], end-to-end HEVC encryption of Region of Interest (ROI) through Kvazaar HEVC encoder and open HEVC decoder. The work applied selective encryption to encrypt only the extracted ROI from the video background.
The visual information of video is protected using a lightweight encryption method to achieve a certain security level in HEVC compression efficiency as developed in [27]. Selective encryption is utilized for sensitive syntax elements to accomplish HEVC standard requirements. The obtained results proved the encryption reliability, flexibility and computational complexity of the developed method, which is also strong against plaintext and brute force attacks. An extended (SE) method for H.264/AVC (CABAC) and HEVC streams is suggested in [28]. The work relies on widely encryption by more modes of CABAC like regular mode to encrypt a major code word and the prediction modes for Intra blocks/units. Their encryption based on probability models, results in statistics disturbance which cause a bitrate overhead enhanced by the content security level of the SE. A comparative study between the scrambling efficiency and the undesirable effects is discussed with security analysis. Although the H.265/HEVC codec with selective encryption (SE) schemes has gained more attention, the video edge region is not sufficiently protected. It encrypts the syntax elements in bypass mode while keeping the data bit rate. Therefore, a tunable SE algorithm based on intra prediction mode (IPM) and scrambling of coefficients for H.265/HEVC is designed in [29]. A pseudo-random sequence is employed to encrypt residual and prediction information, which then reconstructed in H.265/HEVC encoding process. In bypass mode, the syntax elements of CABAC are encrypted. However, in regular mode, syntax elements, like chroma IPM, are ciphered. The scrambling of coefficients is adopted to protect the edge information resulting in the better subjective evaluation and visual distortion compared to existing SE algorithms. A joint encryption scheme for authenticating HEVC compressed video is presented in [30]. To achieve authentication and encryption within the HEVC standard, two separable sets of syntax elements are utilized. A two-level authentication scheme facilitates the verification process of legitimacy. The encryption modules are verified experimentally to be viable in detecting and localizing the tampered regionally. During the wake of the COVID-19 pandemic, a serious attack has mistakenly routed through China's servers by Zoom cloud. To protect the zoom user, a new video conferencing scheme using Zoom cloud, which allows Zoom users to implement their own security, is designed in [31]. The video architecture used two homomorphic encryption schemes before sending files via 256 bit TLS to secure the generated video and audio files through zoom conferencing.
The COVID-19 has created a huge gap in the treatment of lung transplant recipients and other chronic respiratory diseases. A new video consultation that includes a structured questionnaire and vital signs documentation for lung transplant recipients is implemented in [32]. A comparison of on-site visits (OSV) consultation was performed six weeks in a lung transplant center in Germany. This study performed 75 video consultations in a study of 53 patients, and 75 OSV by 51 patients. It is concluded that 77% of physician-patient contacts occurred via video consultations which reduced by 47% compared to 2019. Therefore, the technology can be recommended to supply care for wider range of chronic illness. In [33], current benefits and considerations of Telemedicine during COVID-19 are discussed and introduced how to decipher the next route of action for validating the future implementation.
The HEVC was originally conducted to decrease the needed bit rate of the ultra-high density (UHD) video for either storing or transmitting. The HEVC makes a tradeoff between video compression efficiency, coding complexity, and the coding time delay. The HEVC has a unified, flexible syntax structure that can be utilized in many applications. The HEVC can apply multiple profiles to manage different ranges of applications that have different capabilities. The HEVC profiles, like the main profile utilized for various applications and represent the sampling of a video using 8-bit, one luma and two chromas. The second profile represents the main profile utilized in the video sequences for capturing snapshots. The third profile is utilized to sample videos by 10-bit, which named as the main 10 profile. The architecture of the HEVC structure employs a hybrid video coding structure that has been utilized for the video coding standards since H.261 video coding standard. The coding structure is introduced as a hybrid because it combines the inter prediction between video frames and the prediction error transformation technique. This framework is the best way for encoding and converting the video signal to a bit-stream with a small size. Fig. 1 illustrates the HEVC encoder block diagram [34].
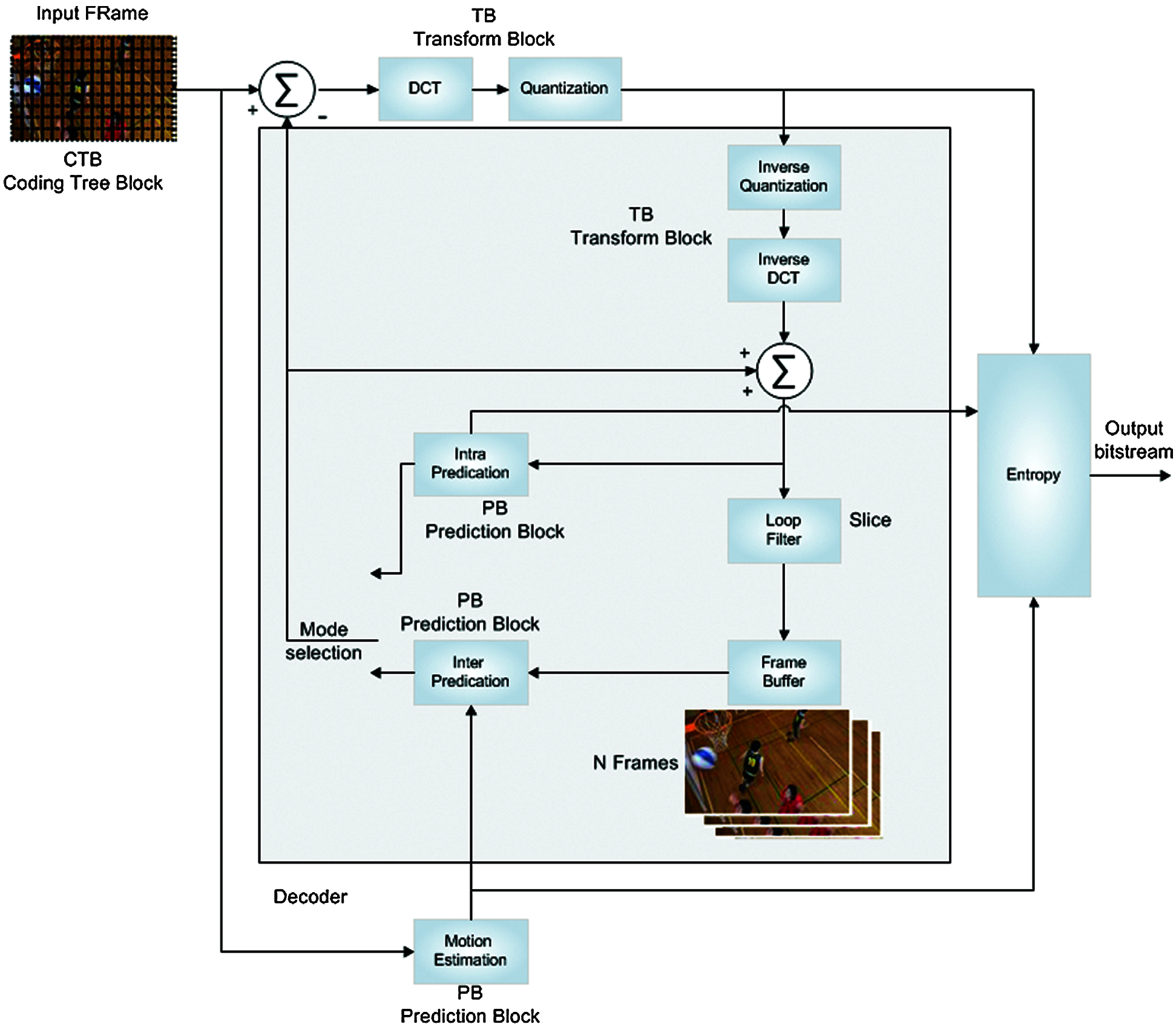
Figure 1: The HEVC encoder
From Fig. 1, HEVC is developed using the block-based hybrid video coding. The following subsections will describe the HEVC hybrid video coding structure block for more details.
4 The Proposed Encryption Method
The proposed HEVC selective encryption scheme, as shown in Fig. 2, is based on encrypting multiple HEVC syntax elements and offers an output that can be employed for real-time medical systems video consultation. The proposed selective encryption scheme encrypts some CABAC binstring syntax elements to provide sufficient encryption, low latency and compliance with the video formats.
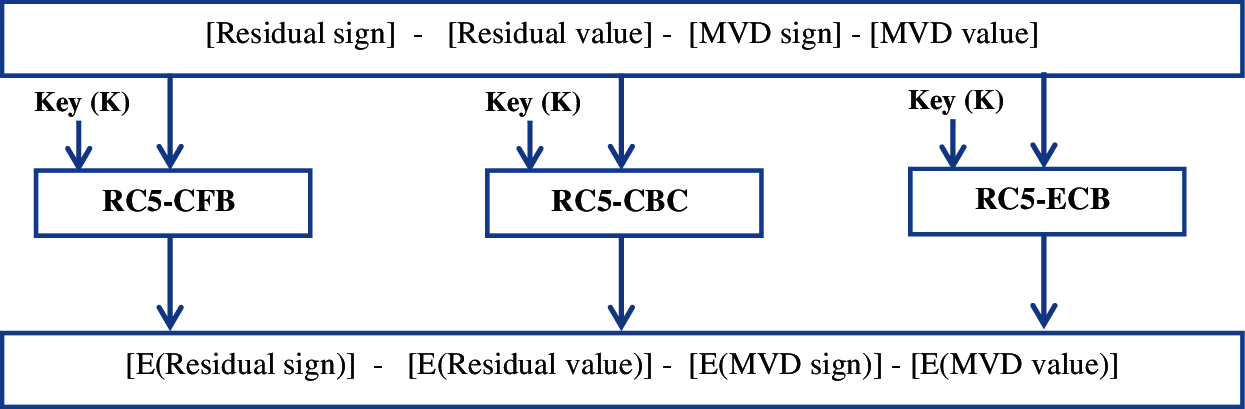
Figure 2: The proposed HEVC SE schema
The proposed system employs an algorithm of RC5 block encryption, which is one of the most popular algorithms for the block cipher. In addition, due to its following features, the proposed system employs the RC5:
• Low latency to satisfy the needs of HEVC applications in real-time.
• Compact code and no extra working memory, making it ideal for real-time HEVC hardware and software execution.
• Can use benefits such as parallelism and 32-bit integer propagation for modern processors.
The Proposed HEVC SE that used for the healthcare video consultation system is described as follows:
1- Formulate the plain bitstrings by concatenating the binstrings of Non-Zero DCT coefficients suffix and its sign values with the MVD suffixes and its signs values.
2- Encrypt the plaintext with RC5 block cipher algorithm in different operation modes (CFB, CBC and ECB) and create the encrypted binstring.
3- Encode the encrypted binstring and generate the encrypted video.
Because video protection is spreading across the Internet more and more, the anonymity and privacy of digital content are problematic against hackers. The article suggests a targeted encryption solution using video consulting based on the most modern HEVC standards for video coding. The suggested technical features could keep the camera and video format bit rate consistent.
For health video consultation, the selected encryption solution proposed is built with the selective encryption algorithm HM16.0 Reference software used as a test framework for the HEVC application.
Since Video Protection has increasingly spread across the Internet, the secrecy and privacy of digital material against hackers are a problem. The article proposes a selective encryption approach based on the most modern HEVC standard for healthcare video consultation. The technical features proposed should maintain the constant bit rate of video and video format compliance. The selective encryption approach proposed for health video consultation is developed using the HM16.0 Reference programme selective encryption algorithm used as a testing platform for applying the HEVC specifications.
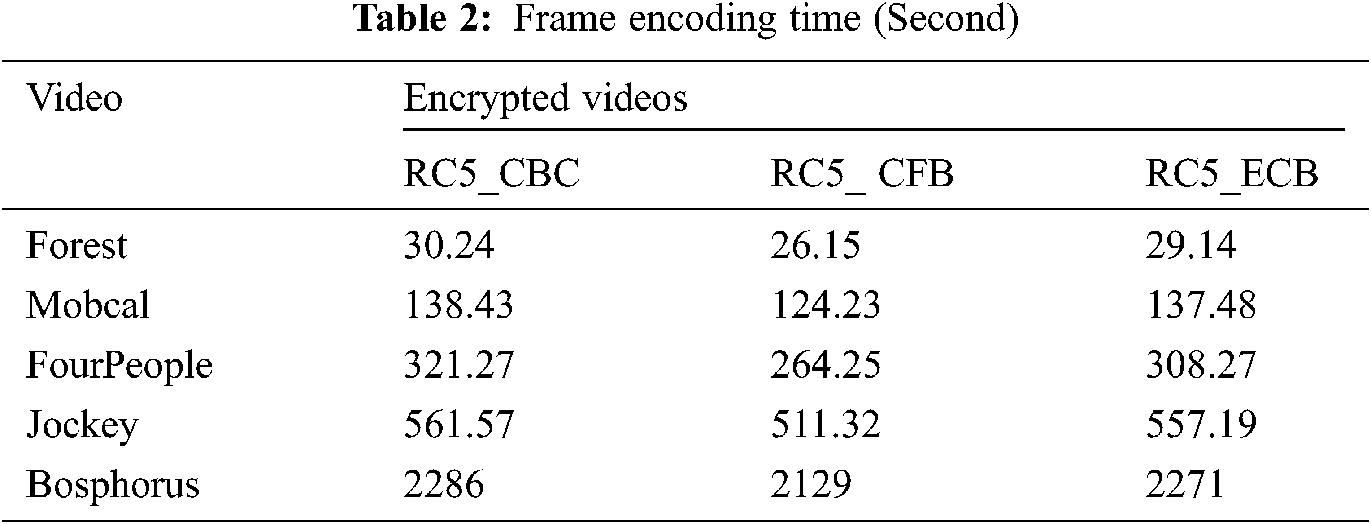
The following table gives time to encode the whole video dataset in Tab. 1 for one frame and compare our proposed RC5 video consultation SE schemes in varying modes.
The HEVC SE is smaller in Tab. 2 in CFB mode than the other operational modes (CBC and ECB). In Tab. 2, it is shown that the CFB mode for HEVC SE decreases average encoding time from 3 s in one frame (with RC5-ECB encryption algorithm) to 4 s in video with low resolution (with RC5-CBC encryption algorithm). The CFB mode reduces the encoding time for one per frame (RC5-ECB encryption algorithm) from 142 s to 157 s for video with high-resolution encryption using the RC5-CBC encryption algorithm.
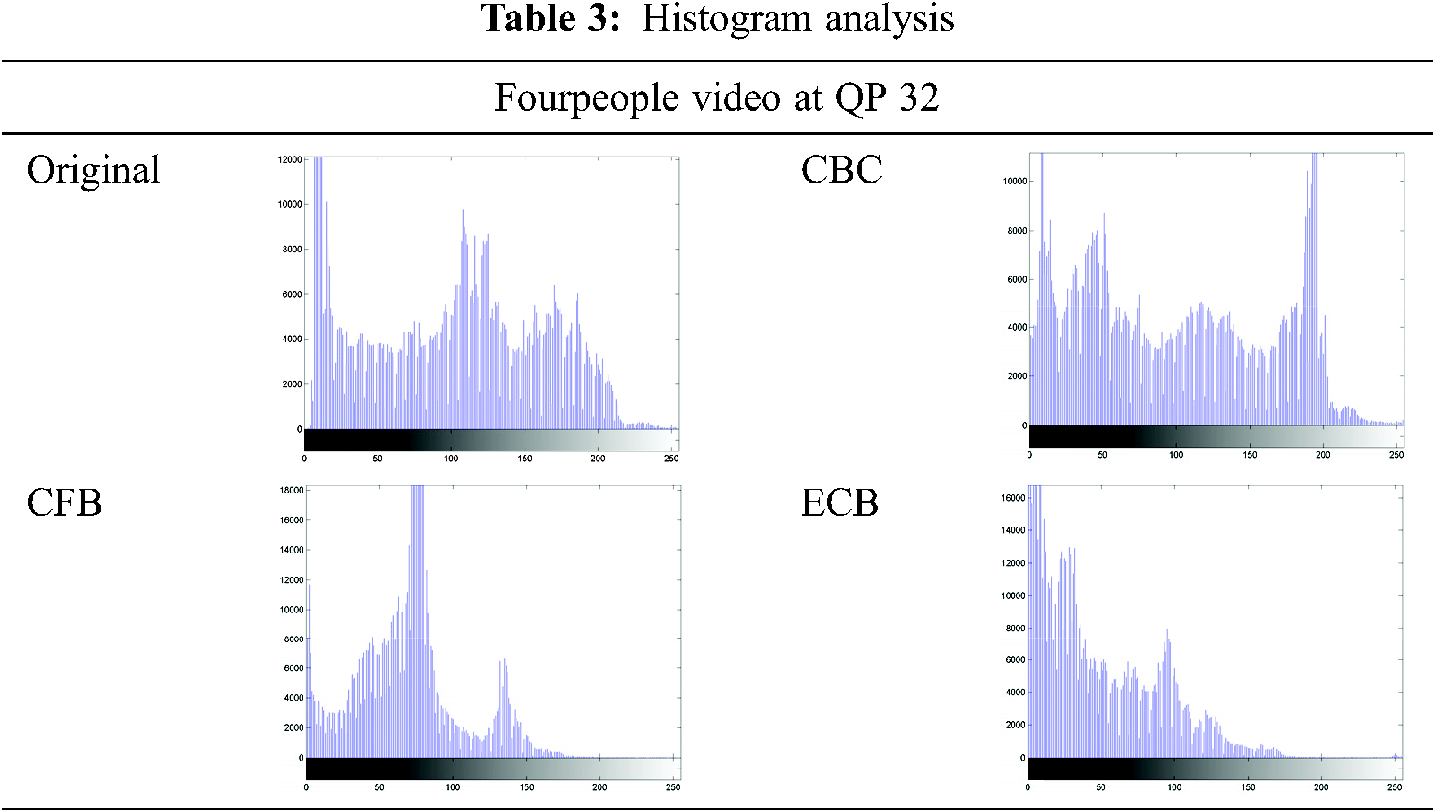
Tab. 3 presents the histogram of frame No. 50 for the compressed video and the cipher video using the proposed scheme for the FourPeople at different values of QP.
5.3 Correlation Coefficient Analysis
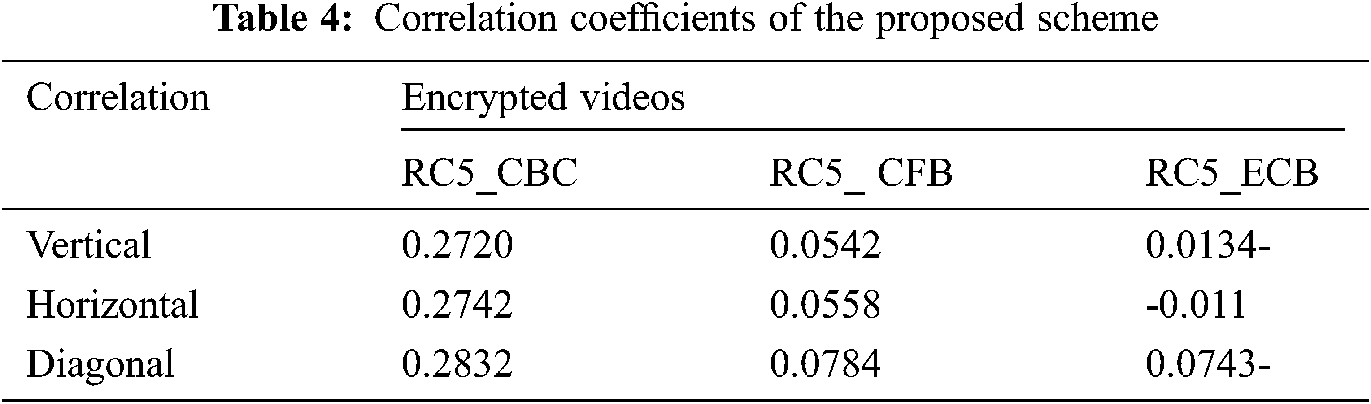
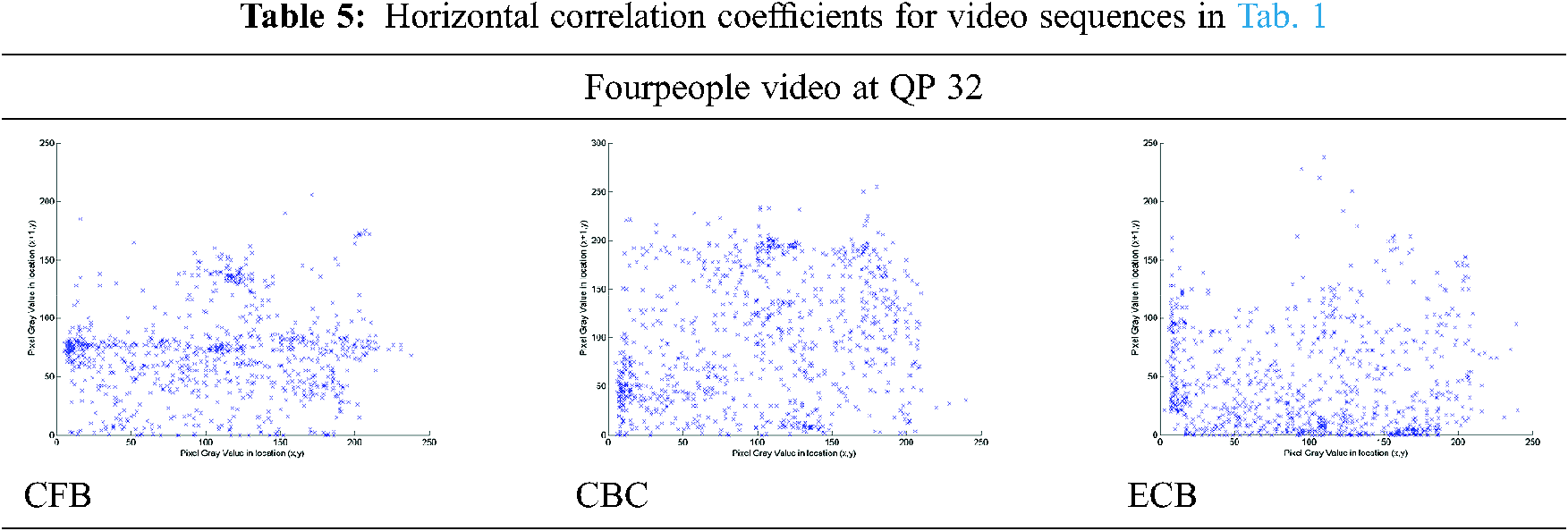
The correlation coefficient is used to measure the linear dependency of two nearby pixels at an equal position in a single frame and two corresponding pixels in separate frames [36]. For the original/cipher video for frame 50 of FourPeople, Tab. 5 provides the horizontal similarity distribution. Tab. 4 contains the correlation coefficients for the FourPeople series in different directions between the original/Cipher video.
5.4 Encryption Quality Analysis
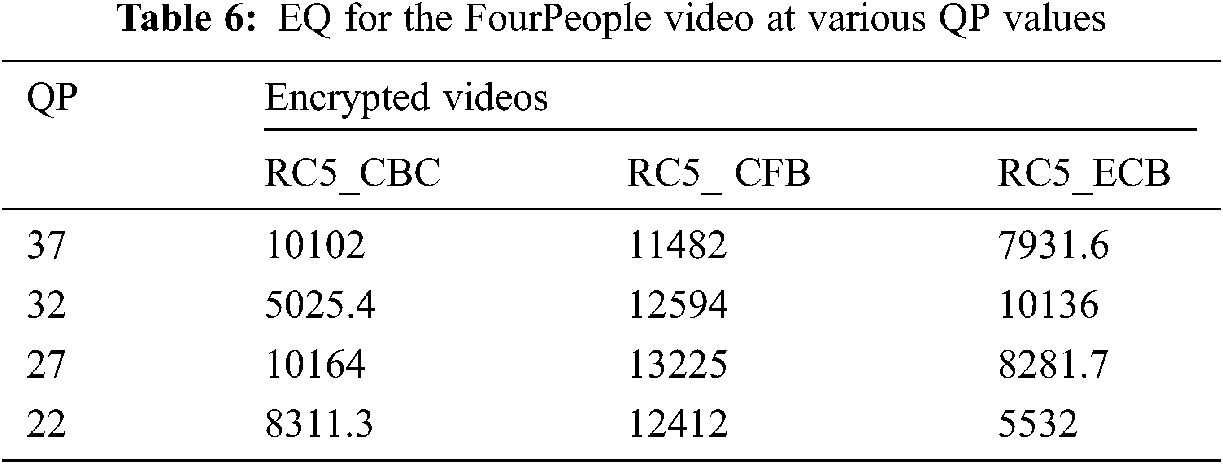
In the cipher/original frames of the video, the encrypting amount (EQ) steps mean a modification in the presence of any pixel of gray [37]. Tab. 6 displays the higher EQ range for the first 50 frames of the FourPeople cipher video frame set.
We can resist a minor modification in the cipher key of the cryptography algorithm for our video coding scheme. To retain the key sensitivity, the subsequent measures are taken:
Frame No. 50 is encrypted utilizing our video consultation encoding system as set out under Tab. 7 with the secret key"18446744407370951610”
Frame No. 50 is encrypted with the hidden key “084467440737095551610” by using the video consultation encryption scheme as shown in Tab. 7.
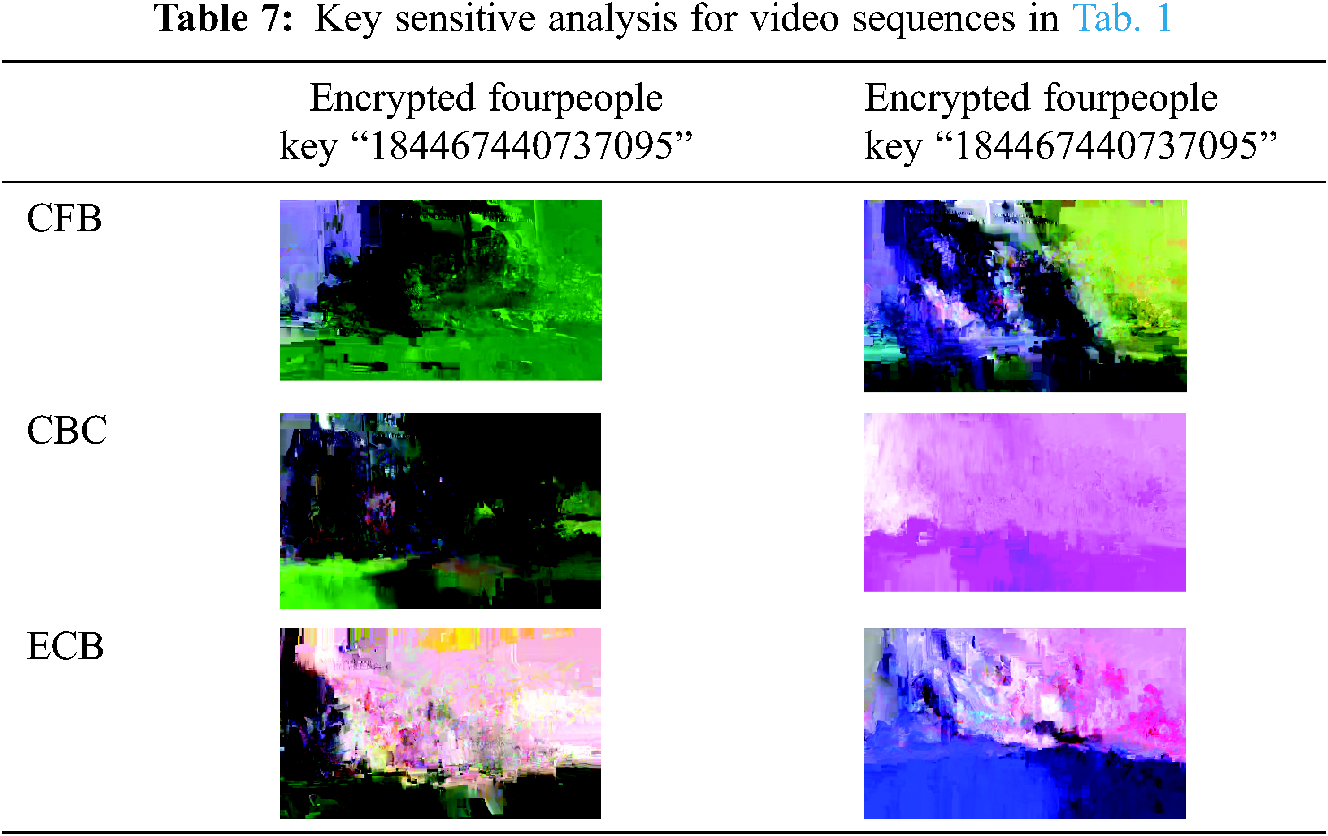
Tab. 7 shows the different ciphervideo frames with a slight correlation between the two ciphered video frames.
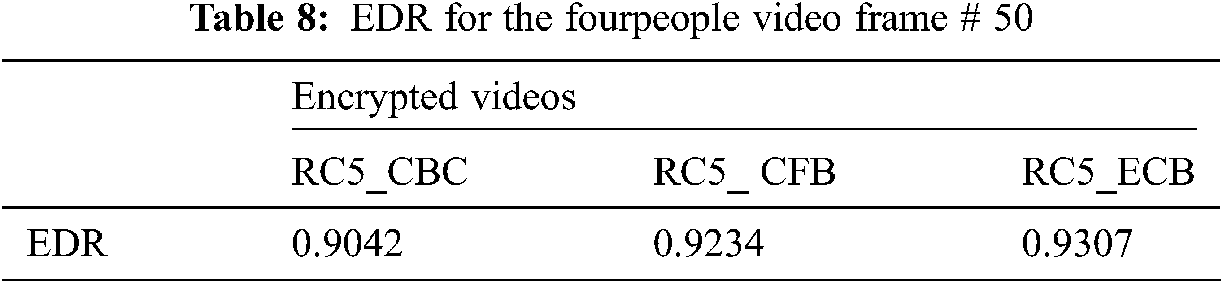
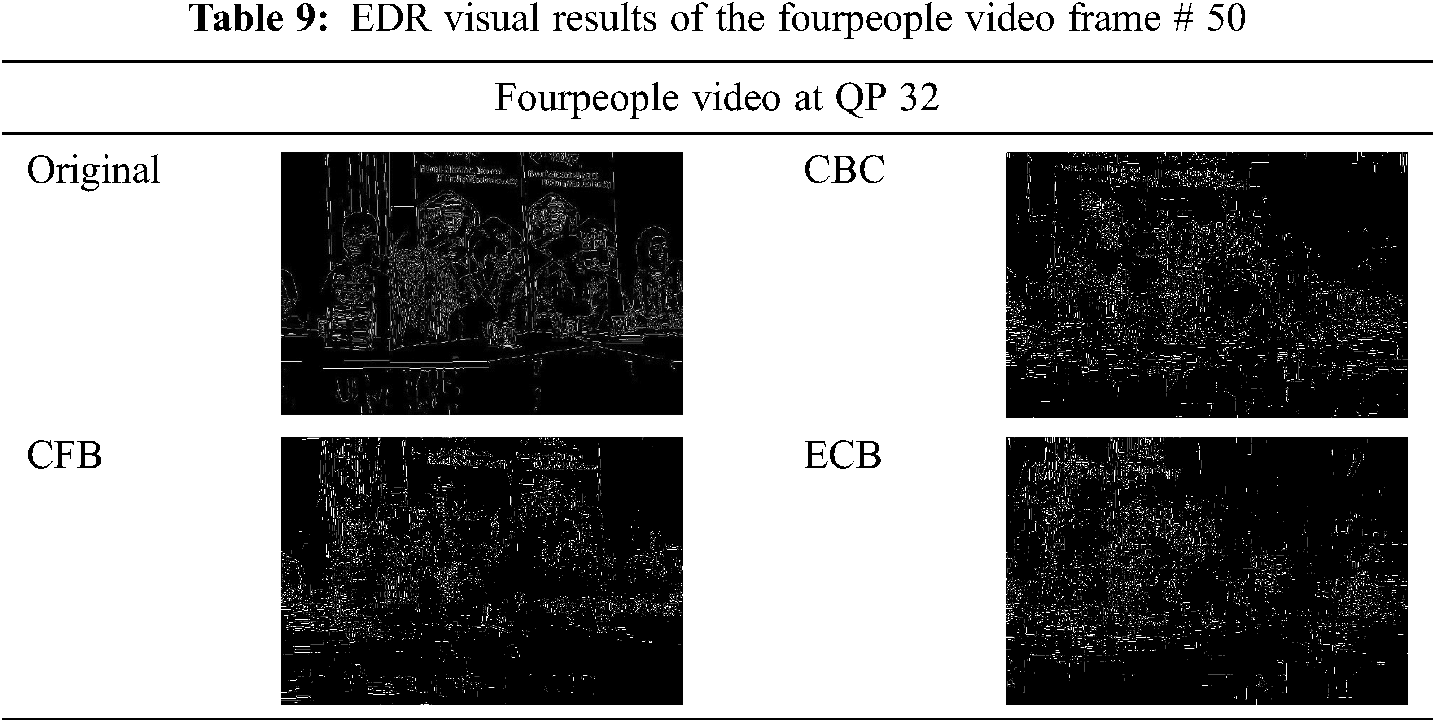
5.6 Edges Detection Protection
The edge detection is described as the distortion of frame edges of the video generated by the HEVC CABAC SE algorithm [38]. The original cipher/EDR for the four-person sequence is close to 1, which ensures that the cipher video provided by the proposed algorithm differs from the original. Tabs. 8 and 9 show the EDR for the cipher/original video frames.
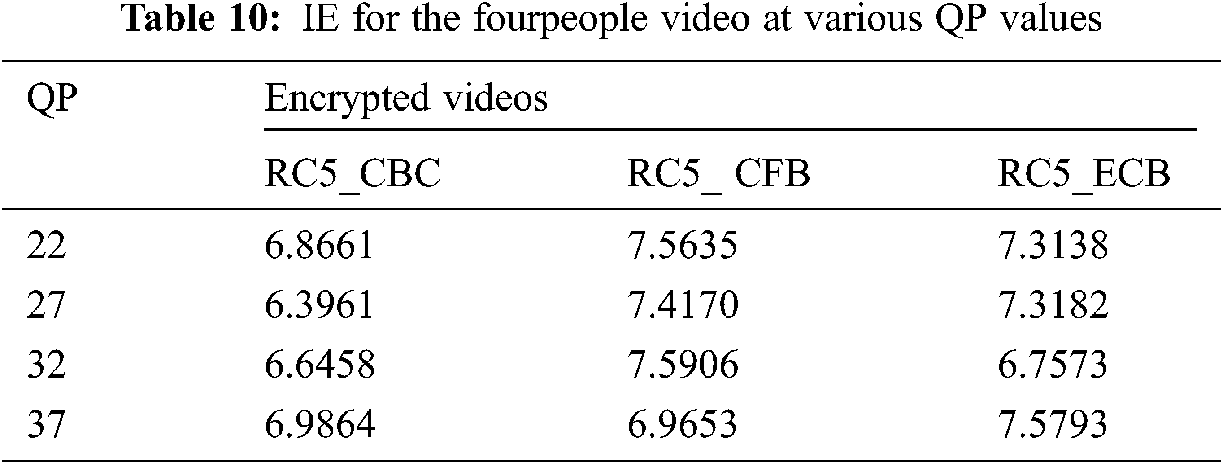
The probability that a video frame symbol exists is referred to as an entropy measure (IE) of information [39–42]. Tab. 10 shows that IE for the HEVC CABAC SE algorithm is equivalent to the same value of cipher frame number 50 from Four People. The HEVC CABAC SE algorithm is therefore protected from entropy attacks.
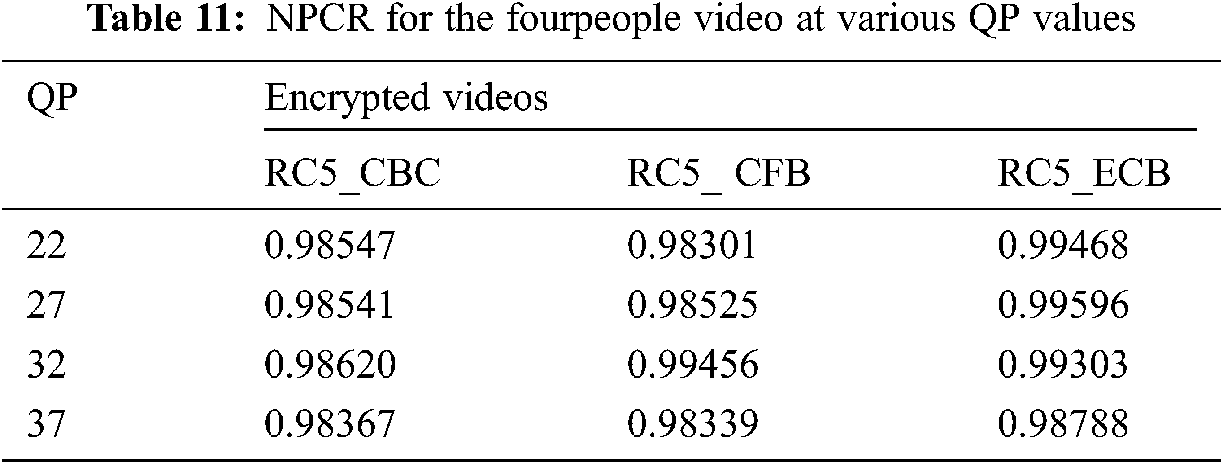
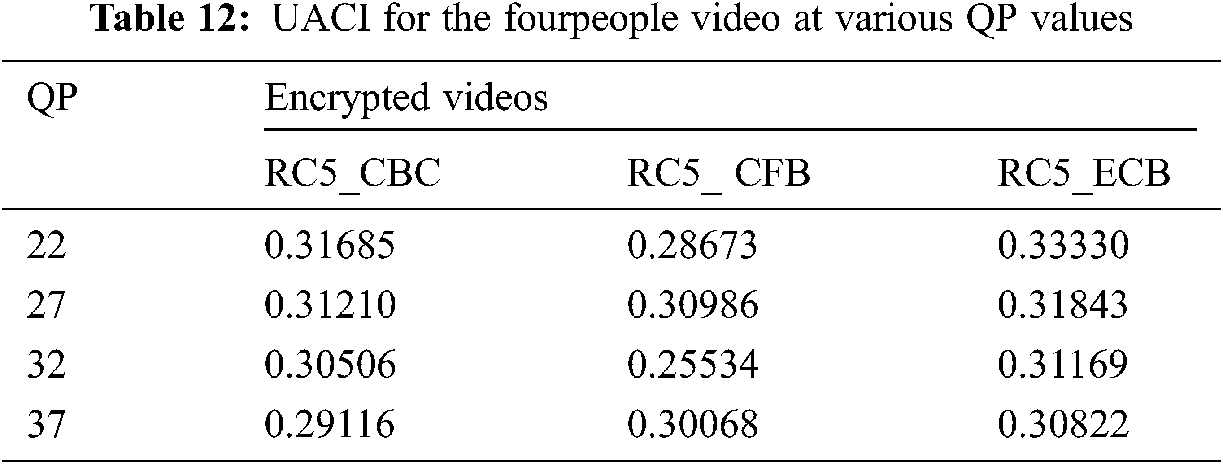
The ciphered video needs to be different from the original in the proposed video consultation schema. The unified average intensity transition (UACI) and the pixel rate (NPCR) can be evaluated to guarantee this condition [43–45]. The video consultation schema shows that the variation in colour pixels in various operating methods has been highly demonstrated in Tabs. 11 and 12.
The appearance of COVID-19 increases the use of video appointments at home for people in need of daily therapy, thus opening up beneficiaries with minor symptoms. As well as minimizing relationships with other patients and doctors, COVID-19 propagation will delay by reducing the increase in population. The spread of the corona virus led to a unique need for healthcare. The spread of the corona virus led to a unique need for healthcare. The rapid spread of the virus has returned telemedicine to health care without increasing the chance that patients and doctors will have contact. This investigation represents the confidentiality of the latest digital video code (HEVC) in the latest health video consultation process. This research aims to create selective HEVC security policies that ensure compliance with file formats, an equal bit rate and low-complexity safety of the devices used in real-time video consulting applications. In the entropy mechanism of HEVC video encoding, the RC5 also offers an important way to encrypt DCT and MVD sign bits and the absolute value. RC5 is used to encrypt video fragments vulnerable and provide a short-term delay, preserve the HEVC bit rate and enforcement format and support HEVC selective encryption. A comparative analysis is provided in various operations of HEVC SE using RC5. The experimental data shows the average time for the encoding of a frame from 3 s (using an encryption algorithm for RC5-ECB) to 4 s (using an encryption algorithm for RC5-CBC) decreased by RC5 in CFB operations. The use of CFB cipher mode also reduces the average time for encoding videos in high resolution from 142 s (using RC5-ECB encoding algorithm) to 157 s (using RC5-CBC encoding algorithm). In addition, the HEVC SE Algorithm security testing, such as encryption efficiency, keyspace and sensitivity testing, is presented in this article. The test results show that HEVC SE is robust against brutal and predictive assaults. The research finding shows that the best alternative for HEVC SE in HEVC real-time applications is to use the CFB operating mode with the RC5 block-cipher algorithm.
Acknowledgement: The authors would like to thank the Deanship of Scientific Research, Taif University, Saudi Arabia, for funding the research project number 1-441-31.
Funding Statement: This research was supported by the Deanship of Scientific Research, Taif University, Saudi Arabia, under research project number 1-441-31.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. F. Fatehi, N. Armfeld and M. Dimitrijevic, “Clinical applications of videoconferencing: A scoping review of the literature for the period 2002–2012,” Journal of Telemedicine Telecare, vol. 20, no. 7, pp. 377–383, 2014. [Google Scholar]
2. H. Fouad and H. Farouk, “Design and implementation of wireless sensors network and cloud based telemedicine system for rural clinics and health centers,” International Journal of Scientific & Engineering Research, vol. 6, no. 2, pp. 478–484, 2014. [Google Scholar]
3. D. Kobayashi, T. Otsubo and Y. Imanaka “The effect of centralization of health care services on travel time and its equality,” Health Policy, vol. 119, no. 3, pp. 298–306, 2015. [Google Scholar]
4. Y. Basta, K. Tytgat, H. Greuter, J. Klinkenbijl, P. Fockens et al., “Organizing and implementing a multidisciplinary fast track oncology clinic,” International Journal of Quality Health Care, vol. 29, no. 7, pp. 966–971, 2017. [Google Scholar]
5. S. Cain, R. Moore, L. Sturm, T. Mason, C. Fuhrman et al., “Clinical assessment and management of general surgery patients via synchronous telehealth,” Journal of Telemedicine Telecare, vol. 23, no. 2, pp. 371–375, 2017. [Google Scholar]
6. M. Bradford and N. Bradford, “The clinical use of skype-for which patients, with which problems and in which settings? A snapshot review of the literature,” International Journal of Medical Informatics, vol. 84, no. 10, pp. 737–742, 2015. [Google Scholar]
7. M. Langarizadeh, F. Moghbeli and A. Aliabadi, “Application of ethics for providing telemedicine services and information technology,” Medical Archives, vol. 71, no. 5, pp. 351–355, 2017. [Google Scholar]
8. D. Cucinotta and M. Vanelli, “WHO declares covid-19 a pandemic,” Acta Biomedical, vol. 91, no. 1, pp. 157–160, 2020. [Google Scholar]
9. A. Doshi, Y. Platt, J. Dressen and B. “Mathews “Keep calm and log on: Telemedicine for COVID-19 pandemic response,” Journal of Hospital Medicine, vol. 15, no. 5, pp. 302–304, 2020. [Google Scholar]
10. M. Compton, M. Soper and B. Reilly, “A feasibility study of urgent implementation of cystic fibrosis multidisciplinary telemedicine clinic in the face of COVID-19 pandemic: Single-center experience,” Telemedicine and E-Health, vol. 26, no. 8, pp. 978–984, 2020. [Google Scholar]
11. Z. Wong and H. Cross, “Telehealth in cancer care during the covid-19 pandemic,” The Medical Journal of Ausralia, vol. 213, pp. 237–238, 2020. [Google Scholar]
12. N. Bitar, J. Kattan, H. Kourie, D. Mukherji and N. Saghir “The Lebanese society of medical oncology (LSMO) statement on the care of patients with cancer during the covid-19 pandemic,” Future Oncology, vol. 16, no. 11, pp. 615–617, 2020. [Google Scholar]
13. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “Performance study of HEVC and H.264 video coding standards,” Menoufia J. of Electronic Engineering Research (MJEER), vol. 27, no. 1, pp. 237–259, 2018. [Google Scholar]
14. J. Yang and S. B. Li, “An efficient information hiding method based on motion vector space encoding for HEVC,” Multimedia Tools and Applications, vol. 77, no. 10, pp. 11979–12001, 2018. [Google Scholar]
15. O. S. Faragallah, M. A. AlZain, H. S. El-Sayed, J. F. Al-Amri, W. El-Shafai et al., “Secure color image cryptosystem based on chaotic logistic in the FrFT domain,” Multimedia Tools and Applications, vol. 77, pp. 1–25, 2020. [Google Scholar]
16. D. W. Xu, R. D. Wang and Y. Q. Shi, “An improved scheme for data hiding in encrypted H.264/AVC videos,” Journal of Visual Communication and Image Representation, vol. 36, pp. 229–242, 2016. [Google Scholar]
17. D. W. Xu, R. D. Wang and Y. N. Zhu, “Tunable data hiding in partially encrypted H.264/AVC videos,” Journal of Visual Communication and Image Representation, vol. 45, pp. 34–45, 2017. [Google Scholar]
18. Y. Z. Yao, W. M. Zhang and N. H. Yu, “Inter-frame distortion drift analysis for reversible data hiding in encrypted H.264AVC video bitstreams,” Signal Processing, vol. 128, pp. 531–545, 2016. [Google Scholar]
19. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “Efficient HEVC selective stream encryption using chaotic logistic map,” Journal of Multimedia Systems, vol. 24, no. 4, pp. 419–437, 2017. [Google Scholar]
20. M. Long, F. Peng and H. Y. Li, “Separable reversible data hiding and encryption for HEVC video,” Journal of Real-Time Image Processing, vol. 14, no. 1, pp. 171–182, 2018. [Google Scholar]
21. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “Comparative study of video compression techniques,” Menoufia J. of Electronic Engineering Research (MJEER), vol. 27, no. 1, pp. 1–32, 2018. [Google Scholar]
22. F. Peng, X. Gong, M. Long and X. Sun, “A selective encryption scheme for protecting H. 264/AVC video in multimedia social network,” Multimedia Tools Applications, vol. 76, no. 3, pp. 3235–3253, 2017. [Google Scholar]
23. O. S. Faragallah, W. El-Shafai, A. Afifi, I. Elashry, M. A. AlZain et al., “Efficient three-dimensional video cybersecurity framework based on double random phase encoding,” Intelligent Automation & Soft Computing, vol. 28, no.2, pp. 353–367, 2021. [Google Scholar]
24. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “CABAC-Based selective encryption for HEVC using RC6 in different operation modes,” Multimedia Tools and Applications, vol. 77, no. 21, pp. 28395–28416, 2018. [Google Scholar]
25. B. Guan and D. Xu, “An efficient commutative encryption and data hiding scheme for HEVC video,” IEEE Access, vol. 8, pp. 60232–60245, 2020. [Google Scholar]
26. M. A. Taha, N. Sidaty, W. Hamidouche, O. Dforges, J. Vanne et al., “End-to-end real-time ROI-based encryption in HEVC videos,” in 26th IEEE European Signal Processing Conf. (EUSIPCOpp. 171–175, Italy, 2018. [Google Scholar]
27. M. A. Saleh, N. M. Tahir and H. Hashim, “Fast selective encryption for video stream of high efficiency video coding standard,” Journal of Theoretical and Applied Information Technology, vol. 96, no. 20, pp. 6807–6816, 2018. [Google Scholar]
28. B. Boyadjis, C. Bergeron, B. Pesquet and F. Dufaux, “Extended selective encryption of H.264/AVC (CABAC) and HEVC encoded video streams,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 27, no. 4, pp. 892–906, 2017. [Google Scholar]
29. F. Peng, X. Zhang, Z. Lin and M. Lon, “A tunable selective encryption scheme for H.265/HEVC based on chroma IPM and coefficient scrambling,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 30, no. 8, pp. 2765–2780, 2020. [Google Scholar]
30. Y. Tew, K. Wong, R. Phan and K. Ngan, “Separable authentication in encrypted HEVC video,” Multimedia Tools and Applications, vol. 77, pp. 24165–24184, 2018. [Google Scholar]
31. A. Abukari, E. Bankas and M. Iddrisu, “A secured video conferencing system architecture using a hybrid of two homomorphic encryption schemes: A case of zoom,” International Journal of Engineering Research & Technology (IJERT), vol. 9, no. 8, pp. 237–240, 2020. [Google Scholar]
32. M. Kayser, C. Valtin, M. Greer, B. Karow, J. Fuge et al., “Video consultation in lung transplant recipients during the covid-19 pandemic,” Telemedicine and E-Health, pp. 1–22, 2020. [Google Scholar]
33. C. Wells, T. Sankar and S. Vadodaria, “Covid-19 reducing the risks: Telemedicine is the new norm for surgical consultations and communications,” Aesthetic Plastic Surgery, vol. 45, no. 1, pp. 343–348, 2021. [Google Scholar]
34. M. Zhou, W. Gao, M. Jiang and H. Yu, “HEVC lossless coding and improvements,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 22, no. 12, pp. 1839–1843, 2012. [Google Scholar]
35. A. Sallam, E. EL-Rabaie and O. S. Faragallah, “HEVC selective encryption using RC6 block cipher technique,” IEEE Transactions on Multimedia, vol. 20, no. 7, pp. 1636–1644, 2018. [Google Scholar]
36. O. S. Faragallah and H. S. El-Sayed, “Secure opto-audio cryptosystem using XORing mask and hartley transform,” IEEE Access, vol. 9, pp. 25437–25449, 2021. [Google Scholar]
37. O. S. Faragallah, H. S. El-Sayed, A. Afifi and S. F. El-Zoghdy, “Small details gray scale image encryption using RC6 block cipher,” Wireless Personal Communications, vol. 118, no. 2, pp. 1559–1589, 2021. [Google Scholar]
38. O. S. Faragallah, W. El-Shafai, A. I. Sallam, I. Elashry, E. M. EL-Rabaie et al., “Cybersecurity framework of hybrid watermarking and selective encryption for secure HEVC communication,” Journal of Ambient Intelligence and Humanized Computing, pp. 1–25, 2021. [Google Scholar]
39. M. Alajmi, I. Elashry, H. S. El-Sayed and O. S. Faragallah, “A password-based authentication system based on the CAPTCHA AI problem,” IEEE Access, vol. 8, pp. 153914–153928, 2020. [Google Scholar]
40. A. M. Hemdan, O. S. Faragallah, O. Elshakankiry and A. Elmhalaway, “A fast hybrid image cryptosystem based on random generator and modified logistic map,” Multimedia Tools and Applications, vol. 78, no. 12, pp. 16177–16193, 2019. [Google Scholar]
41. O. S. Faragallah, A. I. Sallam and H. S. El-Sayed, “Utilization of HEVC chacha20-based selective encryption for secure telehealth video conferencing,” Computers, Materials & Continua, pp. 1–15, 2021. [Google Scholar]
42. O. S. Faragallah, E. A. Naeem, H. S. El-Sayed and F. E. A. El-Samie, “Compression of grayscale images in DRPE-based encrypted domain,” Intelligent Automation & Soft Computing, pp. 1–14, 2021. [Google Scholar]
43. O. S. Faragallah, A. Afifi, I. F. Elashry, E. A. Naeem H. M. El-Hoseny et al., “Efficient optical double image cryptosystem using chaotic mapping-based fresnel transform,” Optical and Quantum Electronics, vol. 53, no. 305, pp. 1–26, 2021. [Google Scholar]
44. O. S. Faragallah, A. Afifi, W. El-Shafai, H. S. El-sayed, E. A. Naeem et al., “Investigation of chaotic image encryption in spatial and FrFT domains for cybersecurity applications,” IEEE Access, vol. 8, pp. 42491–42503, 2020. [Google Scholar]
45. O. S. Faragallah, A. Afifi, W. El-Shafai, H. S. El-sayed, M. A. AlZain et al., “Efficiently encrypting color images with few details based on RC6 and different operation modes for cybersecurity applications,” IEEE Access, vol. 8, pp. 103200–103218, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |