DOI:10.32604/iasc.2021.018207

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.018207 |  |
| Article |
Investigating the Role of Trust Dimension as a Mediator on CC-SaaS Adoption
Institute for Advanced and Smart Digital Opportunities Research Laboratory, School of Computing, Universiti Utara Malaysia, Kedah, 06010, Malaysia
*Corresponding Author: Hiba Jasim Hadi. Email: hebaj81@gmail.com
Received: 01 March 2021; Accepted: 02 April 2021
Abstract: The public sector of Iraq has been struggling from poor management of resources and numerous difficulties that affect its governmental organization’s development, such as financial issues resulting from corruption, insecurity, and the lack of IT resources and infrastructure. Thus, cloud computing Software as a Service (CC-SaaS) can be a useful solution to help governmental organizations increase their service efficiency through the adoption of low-cost technology and provision of better services. The adoption of CC-SaaS remains limited in Iraqi public organizations due to numerous challenges, including privacy and protection, legal policy, and trust. Trust was found to be an effective facilitator in the adoption of innovation in cloud computing (CC) using the Technology Organization and Environment (TOE) model. However, from the original TOE, various relationships are not confirmed for the CC-SaaS extended model. Therefore, this study investigated the effect of the trust dimension as a mediator represented by (ability, integrity, and benevolence) on an organization that intends to adopt CC-SaaS using TOE. The study also aimed to investigate the effect of perceived intensity of civil conflict factors on adopting CC-SaaS, especially in the violence and conflict environment. To fill the existing knowledge gap, this study adopted the Diffusion of Innovation and TOE model to investigate the determinants of CC-SaaS among government organizations in Iraq. Thus, ten variables are categorized within four dimensions in the study model. Furthermore, trust is seen as a critical facilitator for successful adoption, which is particularly true as a user receives customized services provided by a third party. Hence, the study further modeled and empirically validated the mediating role of trust dimension. The data are collected empirically from a sample of 367 IT professionals. Obtained results disclosed that the effects of technology, organization, and environment variables were statistically significant and reveal that external support and compliance with regulation have no significant effect. Nonetheless, trust dimension was proven a substantial facilitator in CC-SaaS adoption.
Keywords: Cloud computing; software as a service; technology organization and environment model; diffusion of innovation; trust
Cloud computing (CC) has been seen as an important next-generation computing model [1], which has recently attracted much attention from researchers in both the academic and economic fields. Software as a Service (SaaS) has emerged as a trend in information technology (IT). Software as a services (SaaS) is defined as on-demand software delivery model that possesses the highest level of cloud abstraction [2]. Additionally, it provides configuration and hosting that is highly centralized and enables automatic updates [3]; it relieves users from the installation and maintenance of Software and allows them simple access via the Internet [4]. CC-SaaS offers several benefits to organizations, including the soft initial cost of investment, service scalability, and more importantly, on-demand resources [3]; it enables users to save more from operational cost [2]; facilitates non-complex utilization of cloud-based solutions [1]; and enables the efficient provision of services, budget management, and effective service delivery [5]. Although these benefits may actually be especially interesting for developing countries, the literature reveals some difficulties and obstacles that organizations experience in adopting CC-SaaS. However, although the global SaaS adoption rate is steadily growing, the adoption rates among organizations are inadequate [6], and the adoption of CC-SaaS remains limited [2,4] due to many issues and obstacles. Trust is considered one of the major obstacles that would prevent organizations from adopting the CC [7]. Undeniably, trust is an essential factor that affects any technology adoption [8]. According to Sheng et al. [9], the trust of cloud vendors and the determination of potential risks, including privacy and security concerns, are paramount in successfully adopting a suitable cloud model. Furthermore, trust and security remain one of the main obstacles and barriers to CC adoption [10]. In addition, CC-SaaS actually represents an emerging computing model; hence, high uncertainty exists about security at varying levels of its deployment from data level to application and host level to network [11]. This reality has caused uncertainty among information executives, establishing distrust in the security of CC. Consequently, trust and integrity are seen as the key security issues in relation to CC [10] and are affecting the acceptance of new technology [12]. Subsequently, in CC-SaaS, subscribers and providers should trust each other [10]. In comparison with numerous providers of CC services on the market providing virtually the same offerings, choosing the reliable one has become a daunting challenge. Furthermore, many studies found trust as a critical aspect that caused effects for the adoption of any technology [7]. Sheng et al. [9] emphasized the benefits of CC-SaaS apart from opportunities and convenience, but the security related to trust issues remains. Thus, in CC, a need arises to establish trust between the subscriber and provider because the subscriber’s lack of trust in cloud deployment models can result in numerous problems [10]. Nevertheless, numerous empirical studies have been conducted to test the CC adoption in organization’s use of various approaches in different domains. In the CC context, Paliszkiewicz [13] stated that trust is very important, but a complex and multidimensional concept of its influence must be measured and understood. Hence, based on the literature, the impact of trust dimension as mediator on the adoption of CC-SaaS was not addressed yet. Therefore, this study aims to extend Technology Organization and Environment (TOE) by considering the indirect impact of trust dimension as a mediator on the intention to adopt CC-SaaS.
This study aimed to identify the critical factors that influence CC-SaaS adoption; the factor has been classified and prioritized on the bases of its relative importance as a critical factor for CC adoption. A mixed-method approach has initially examined the factors from the literature review and later involving experts from the information system of academicians, particularly in CC. This study’s outcome could be considered while adopting CC-SaaS in public organizations in unstable countries such as Iraq. This research has been conducted to explore the following three research questions: (i) What are the critical factors that influence the adoption of CC-SaaS in the Iraqi public organization? (ii) What are the significant dimensions which represent different identified factors? (iii) Does trust as a multi-dimension construct have a mediating effect? (iv) Which factors are more important relative to other identified factors for adopting CC-SaaS?. The core contributions of this paper can be summarized as follows:
• Identifying the important factors affecting the adoption of CC-SaaS. The current study presented a variety of repercussions for public organization’s decision to adopt CC-SaaS. Practically, it shows the indirect influence of the trust dimension on the public organization’s decision to adopt CC-SaaS.
• Developing a model for investigating the factors that influence the intention to adopt CC-SaaS. It also provides the stakeholder with insights into the effective factors for adopting CC-SaaS to build an effective strategic strategy. In addition, the model developed can be adopted by public agencies in unsuitable countries to increase their service efficiency.
• Examining the mediating effect of trust dimension. Trust as a multi-dimensional construct, mediates the relationship between (compatibility, complexity, security, privacy, and top management support) and the intention to adopt CC-SaaS.
The rest of the paper is organized in sections and sub-sections where necessary as follows: after the introductory section, Section 2 describes the related work. Section 3 presents the study model and hypothesis development. Section 4 describes the methods used in this study. Section 5 presents the results and the analysis. Section 6 details the result discussion. Section 7 establishes the conclusion and future research.
In the context of public organization studies, trust is defined as “the willingness of a party to be vulnerable to the actions of another party based on the expectation that the other will perform a particular action important to the trustor, irrespective of the ability to monitor or control that other party” [14]. Hence, many studies from the literature reveal that trust was a critical predictor affecting the process of adoption for any new technology [12]. In addition, the decision to adopt CC-SaaS is influenced by trust as a subjective predictor, which can impede the adoption of CC-SaaS [15]. The organizational challenges for CC adoption are trust, integrity, availability, authorization, confidentiality, and authentication [10]. Zissis et al. [16] stated that trust could be ensured via robust security policies and constraints on data access by people. The survey from Fujitsu Research Institute narrated that establishing trust is the main challenge to adopting CC, and it found that 88% of prospective cloud users are concerned that their data could be accessed by a third party and what is happening at the physical backend server. The lack of trust in any cloud applications or services occurs from the user side due to resource sharing and the lack of resource control [17]. Thus, CC, subscribers, and providers should trust one another, as the lack of subscribers’ trust in cloud deployment models can cause several problems [10]. Trust in cloud providers and assessment of potential risks related to privacy and security issues are therefore essential to ensure progress in the adoption of an acceptable cloud [18].
Moreover, a number of studies were conducted in an attempt to recognize the major factors that may affect trust in CC services [17]. In terms of business and technology perspectives, [19] addressed various issues relating to trust in CC. Data ownership was identified as one of the issues of concern in trusting CC. Another study by Buyya et al. [20] noted that Amazon is one of the current cloud providers that does not provide full capabilities and transparency that could enable users to track and audit data provenance and the file access history. Furthermore, a new study by Pearson [21] emphasized that a high number of Chief Information Officers in big enterprises opined that the major reason discouraging them from embracing cloud service is security; this issue is followed by data protection and privacy concern. Specifically, the lack of user control and training, uncertainty, and unauthorized secondary usage are the major privacy concerns affecting trust in CC [17]. Thus, based on [15], trust as a mediator is used to study the CC ecosystem for trust transitive and trust propagation. The scholars pointed out that due to security and privacy concerns, trust is seen as a key facilitator of efficacious business relationships in the CC ecosystems; their findings discovered the importance of trust and confirmed that trust is considered a key factor for the adoption of CC. Moreover, another study by Garrison et al. [22] identified the factors that afford a deeper understanding of individuals’ motivation toward the use of CC services despite privacy and security concerns. The authors incorporate the TPB to explain individuals’ intentions to use CC services by using trust as a moderator among attitude, subjected norm, behavioral control, and behavioral intention to use CC [22]. Another study used trust in CC to test its mediation impact on the intention to use CC application; it then examined the key determinant increasing user trust and intention to adopt CC-based applications [23]. However, these studies focus on individual behavior regarding trust between users and CC service providers. The technological, organizational, and environmental factors are not covered, and their proposed models cannot be generalized.
Therefore, trust regarding the technological factors must be examined, especially relating to security, privacy, complexity, and compatibility in CC-SaaS. In addition, the organizational factors such as top management support, which is correlated to trust from the side of organizations’ decision-makers, must be determined to know why the association is more effective. The mechanism behind the relationship among the technological and organizational factors mentioned and CC-SaaS intention to adopt through the integration of trust as mediation factor also require investigation.
3 Study Model and Hypothesis Development
Many studies have examined CC-SaaS adoption and its positive impacts. Nonetheless, this study is the first of its kind in Iraqi government institutions. A preliminary investigation was carried out to identify the relevance of the selected factors from the perspective of CC experts to generate consistent outcomes, which can improve the findings’ validity and credibility. Furthermore, this research aims to identify and model the contributing factors that influence the public organization decision in insecure countries such as Iraq and investigate the effect of perceived intensity of civil conflict (PICC) and the role of trust dimension as a mediator.
In developing this study model, a multi-perspective theoretical framework was applied through the deployment of TOE and DOI, and ten independents were used to define the dependent variable. The review of the literature revealed that these theories could be used to explain the association between technology, organization, environment, and human factors for adopting CC-SaaS in Iraqi public organizations. The TOE was introduced by Tornatzky et al. [24] as a multi-perspective framework. It illustrates a segment of the innovation process regarding how innovation adoption and implementation are influenced in the organizational context [25]. The framework identifies three building blocks that influence the adoption of an innovation, which include technological, organizational, and environmental contexts [26]. Meanwhile, [27] developed the theory of Diffusion of Innovation (DOI), which originates from sociology and helps explain the adoption from an organizational perspective [28]. Researchers consider DOI as one of the most broadly accepted models in the adoption of new technology [27]. Fig. 1 presents the study model proposed in this study.
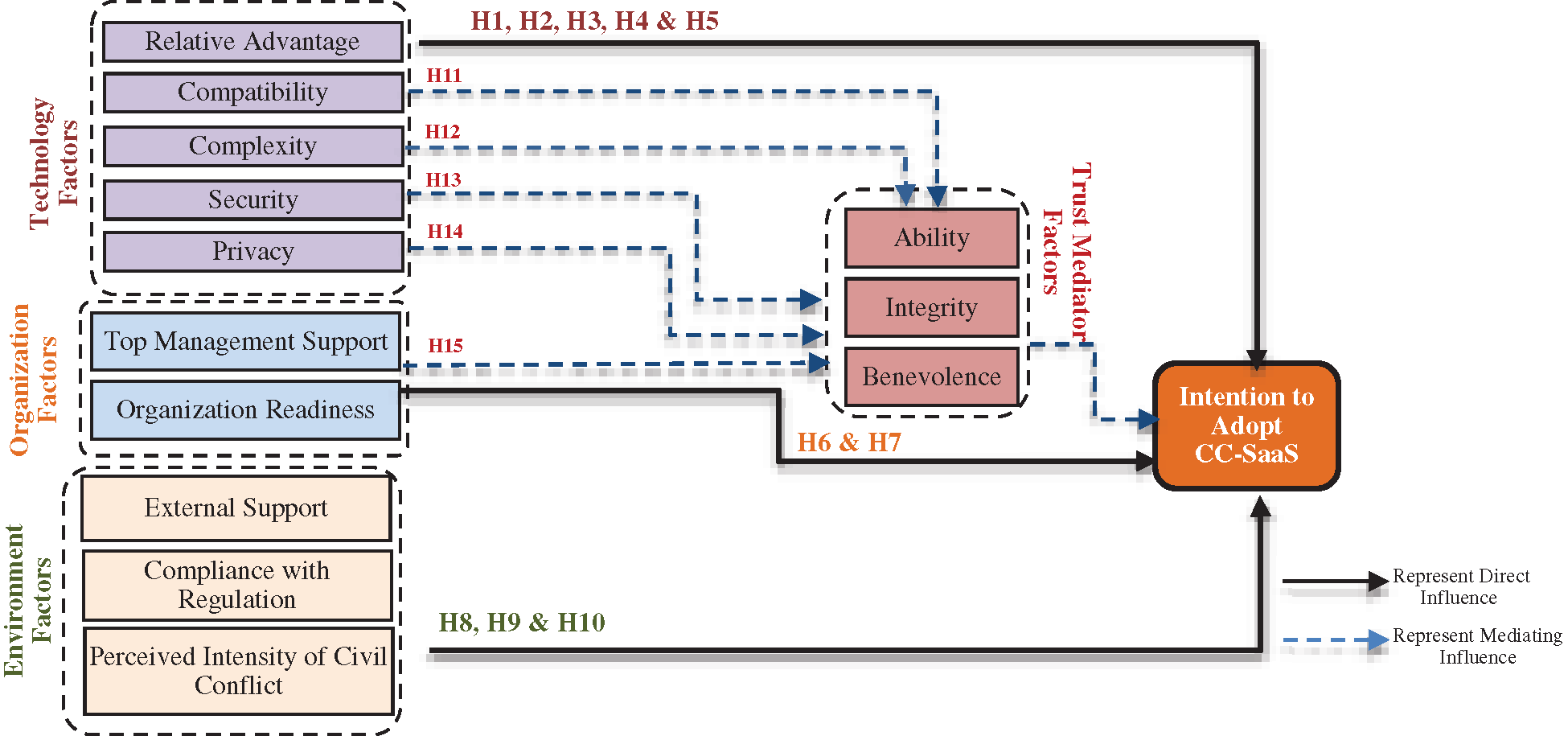
Figure 1: The study model of CC-SaaS intention to adopt
As depicted in Fig. 1, the study model is conceptualized in three dimensions, that is, technology, organization, and environment. The study supposes that these dimensions will affect Iraqi public organization’s decisions toward the adoption of CC-SaaS. The subsequent subsections explain the study model’s conceptualization as a foundation for the adoption of CC-SaaS in the Iraqi public organization.
The study built an understanding of the study variables’ associations based on the explained theoretical model. The subsequent sections define these factors and their relationship in the context of this study and the hypothesis for each relationship.
Technological Dimensions (TD) have been considered in this study as technological factors that influence the organization’s intonation toward the adoption of CC-SaaS technology [29]. Five technological factors have been identified in this study, namely, relative advantage (RA), compatibility (CM), complexity (CMx), security (Sec), and privacy (PRi).
Relative advantage: RA has been described as the degree to which users perceived CC-SaaS technology to be more efficient than other competing computing paradigms [30]. This perception is mostly built following the belief that CC-SaaS possesses some advantages in terms of economy and technology than traditional IT environments. The importance of RA placed it among the key variables of DOI [27]. Thus, organizations mostly imbibe these perceived benefits of technology and its value as among the key considerations in the adoption of new technology [31]. Therefore, the following hypothesis is proposed.
Compatibility: CM has been considered as the degree to which users perceived CC-SaaS technology to be consistent with their current infrastructures, operational skills, and organizational needs of technology [30]. CM is viewed from the perspective of technology, as the degree to which CC-SaaS solutions are matched with organizations’ existing systems. Additionally, its addressed crucial factor for consideration while an organization moves to cloud computing is the degree of CM between the CC-SaaS services and the statutory regulations that govern the organization; hence the hypothesis is proposed as:
Complexity: CMx has been considered as the degree to which users perceived the relative difficulty while learning or in the actual usage of CC-SaaS [30]. Within the IT adoption literature, CMx has been seen from the perspective of time constraint requirement in task performance, simplicity in system integration, efficiency in data transfer, and system functionality while performing the task. These features imply that the easier an organization perceived the integration of technology within its operations, the more likely its decision to adopt such technology [32]. Therefore, the CMx hypothesis is stated as:
Security: Sec has been considered the extent to which Sec measures have been installed to protect information stored in the system from unauthorized access, modification, or transit in CC-SaaS [33]. Sec is a paramount issue in CC-SaaS adoption because it affects so many perspectives within IT, including how data is stored, transmitted, and lost; it also covers confidentiality, breach of privacy, and its suitability in the organizational operations [34]. Thus, the following hypothesis is proposed:
Privacy: PRi has been defined as data and information confidentiality offered by the CC-SaaS in which only the authorized person can have access to such data and information [35]. Actually, PRi is at stake whenever a possibility exists for a third party to gain access to the data stored and information managed because user organizations could develop a tendency to lose full control over the stored data or any information processed. Consequently, the issue of PRi has remained a major concern for many businesses considering using the cloud to store data and run applications, which results in the following hypothesis:
3.2.2 Organizational Dimensions
The second dimension proposed in the model is Organizational Dimensions (ODs), which can be described in terms of resource management provisions, specification of goal, and decision-makers’ commitments that eventually affect the SaaS-based CC adoption. ODs have been classified into two (2) categories to estimate its influence on the intention to adopt CC-SaaS, namely, Top Management Support (TMS) for CC-SaaS adoption and Organizational Readiness (OR) for CC-SaaS adoption.
Top Management Support: TMS refers to the management’s commitment to provide the desired supports, including resource management, specification of goals, and decision-makers’ commitment in the CC-SaaS adoption direction [33]. The existing literature acknowledged the important role of TMS in initiating, implementing, and adopting many forms of information technologies in the context of IT adoption [36]. Hence, the proposal of this hypothesis:
Organizational Readiness: OR refers to determining an organization’s readiness in terms of technology and financial resources, which are considered vital in the CC-SaaS adoption process [21,23]. Karim [37] has also viewed it as the degree to which managers perceive and evaluate their readiness toward the possession of the desired awareness, governance structure, resources, and commitment that will ensure the successful adoption of new technology. Therefore, the following hypothesis is deducted as:
3.2.3 Environmental Dimensions
The third dimension is Environment Dimension (ED), which is recognized as an external factor influencing the decision to adopt CC-SaaS technology [29]. This study recognizes three (3) important factors composed of the environmental dimensions, which are used in investigating its influence on the intention to adopt CC-SaaS, namely, external support (ES), compliance with regulation (CR), and perceived intensity of civil conflict (PICC).
External Support: ES refers to providing all the necessary supports by various parties, including CC-SaaS providers, relative associations, or training partners, which could influence the organization’s intention toward the adoption of CC-SaaS [29]. This study considers ES from a cloud provider’s perspective, which will enable user organizations to meet their cloud service requirements. Thus, the research presented this hypothesis as:
Compliance with Regulation: CR is considered the absence of clear government regulations or rules that can provide the necessary support to an organization in the adoption of CC-SaaS, especially during a data breach [38]. The lack of a CR can potentially hinder an organization from adopting cloud technology. Thus, the following hypotheses are proposed:
Perceived Intensity of Civil Conflict: PICC is considered here as the organization’s consciousness with regard to the massive violent forces that surround and fuel civil conflict resulting from political and sectarianism differences with respect to the national values employed for the conflict’s perpetuation [39]. It is a critical factor with respect to the countries experiencing civil conflict. Thus, the adoption of technology such as CC-SaaS could potentially solve massive violence that surrounds those countries as a result of sectarianism and political instability, which can adversely affect the government’s service delivery to the citizens. A review of the existing studies detected a dearth of studies on the impact of PICC on the adoption of CC in a conflict environment, especially in a country such as Iraq. The hypothesis of PICC is presented as follows:
Trust has been identified as a mediating variable proposed to mediate the relationship between the two characteristics (technological and ODs) and the intention to adopt CC-SaaS. To establish these mediating relationships, the study considers the three dimensions of trust; ability, integrity, and benevolence. In this study, trust is appraised as the users’ level of confidence about the reliability of CC-SaaS providers and SaaS-based system functionality [40]. Trust is part of CC’s Sec issues alongside other Sec concerns such as authentication and authorization, availability, integrity, and confidentiality [10]. Trust covers a wide spectrum of issues and is far beyond merely the trust in cloud providers; it encompasses the trust of the technology itself as well as capabilities in the provision of quality service and the absence of any interruption or damage to the service provided during its delivery. Thus, considering the scope of trust in covering a wide spectrum of critical issues to organizational decision-makers, they are expected to require a certain level of assurance [41]. Therefore, this study’s trust will be operationalized using its three important dimensions covering ability, integrity, and benevolence [42]. Therefore, the following hypotheses are proposed:
The study focuses on modelling the associations amid the critical factors influencing the intention of the Iraqi public organization to adopt CC-SaaS. The importance of choosing the best research approach and design to answer the main research question was highlighted by [43]. As a direct consequence, the quantitative research strategy was employed, which helps the researchers conduct the examinations of certain hypotheses to assess the significance of the selected factors and enable the researchers to generalize their research findings to the entire population [44].
This study aims to identify factors that influence the CC-SaaS adoption in Iraqi public organizations using TOE and DOI integration. Accordingly, a self-administered questionnaire was developed in which data were collected from public organizations under the Iraqi ministries. To achieve this goal, all of the variables were measured using items adapted from previous studies, and the item was framed on a five-point Likert-Scale ranging from 1 to 5 (“strongly disagree”). In addition, instrument validity was assessed by using two rounds of pre-testing. The survey was first evaluated by academic researchers with experience in questionnaire design and then piloted with a group of IT professionals.
4.2 Data Collection and Analysis
The empirical data for this study were collected using a questionnaire survey and was distributed using two methods: mail and walk-in. The questionnaire responses were gathered from IT professionals in the selected organizations involved in the IT project development process. Furthermore, the study used two control measures by screening the survey’s questions. The first control measure was to determine the position of those who participated in the survey by excluding those uninterested in IT decisions in the participating organizations. The second control measure was CC experience, which excludes all the participants without CC experience. The majority of the responses were obtained through personal visits to the respondents. In total, 450 survey questionnaires were distributed to the targeted organizations among six Iraqi ministries. From a total of 450 distributed questionnaires, 367 were returned; this figure accounted for about 81.5% response rate. The returned questionnaires’ percentage is considered very high compared with other studies conducted within the same context and domain, which gained approximately 40% as a response rate [45]. From the 367 responses, 301 were found valid. Consequently, several data analysis techniques were used for the data cleaning process. Finally, the analysis and validation of the structural model were performed using the Smart-PLS statistical software package version 3.0.
5.1 Demographic Characteristics
The respondents of this study were composed of females and males. The gender analysis was assessed from the 367 respondents, 175 are females (47.70%), and 192 are males (52.30%) with a 40-year-old average age. This proportion is acceptable given that in most Iraqi public organizations, male staff generally outnumber their female counterpart, notably in the IT field. Furthermore, the participants’ age was checked according to five categories: approximately 7.63% of the respondents were between the ages of 18 and 27, 29.70% aged between 28 to 37, 36.24% aged between 38 to 47, 22.34% aged between 48 to 57, and 4.09% were above 57 years old. The results show that the prominent age lies in the middle generation (38–47) and that the last category is the older generation. In terms of educational level, only a few IT professionals hold a diploma at 1.09%. In comparison, others with Bachelor’s degrees account for 53.41%, Higher Diploma roughly 14.99%; Master’s degree around 18.53%; and Ph.D. about 11.99%. In essence, these findings indicate that staff in the Iraqi ministries, notably in the IT field, are highly educated and competent. The results reflect the nature of the population of the organization as the majority of the staff are bachelor’s degree holders, and the least is in the diploma category. Finally, most of the IT professionals have more than ten years of experience in their jobs, representing about 52.32%. By contrast, those with six to ten years of experience account for 38.42%; those with two to five years of experience represent 6.81% of the respondents.
To verify the model, the PLS-SEM has been applied for the data analysis phase; while choosing the PLS-SEM, the SEM significantly has two models (i.e., measurement and structural). Therefore, the present study adopts the two-step process suggested by Hair et al. [46] in conducting the analysis. The evaluation of the measurement model comes first, followed by the evaluation of the structural model.
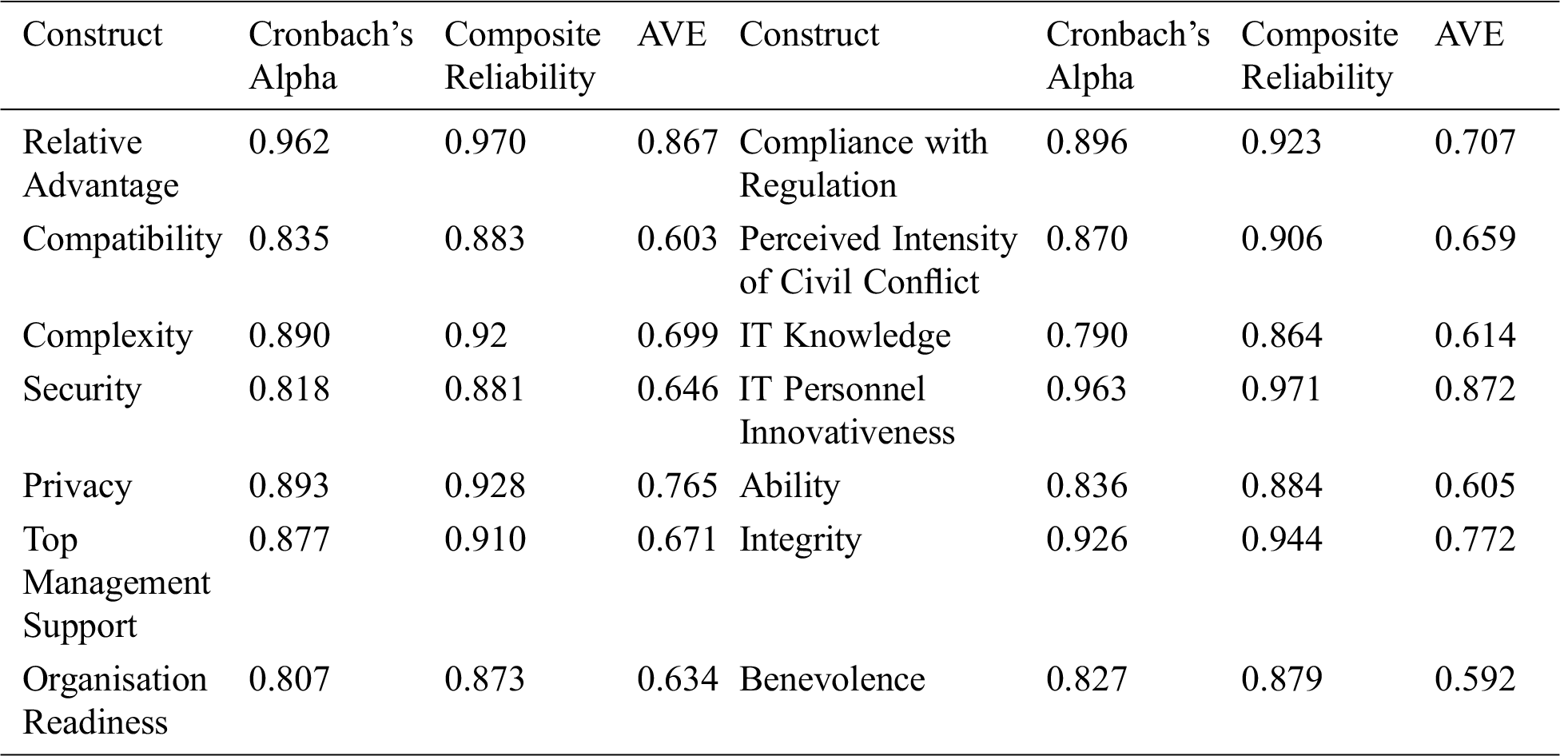
The validity and reliability of the data were established using the measurement model. This method was used to ensure that the results were high quality and eligible as Hair recommended [47]. The evaluation of construct reliability is normally undertaken through the assessment of internal consistency by using values of Alpha (α) and or composite reliability (CR) based on the common threshold of 0.70 [46]. As shown in Tab. 1, in the current study, the CR values for the model’s constructs& ranged from (0.828) to (0.971). Thus, it is considered a satisfactory criterion for constructs [47].
Convergent validity is attained when the AVE of a given construct is equal to or greater than 0.50 as suggested by Henseler and Sarstedt [48] and Hair et al. [49]; this condition implied that the latent variable’s explanatory power is, on average, more than half of its indicators’ variance. In this study, all AVE values in Tab. 1 confirmed that the constructs had achieved an acceptable level of convergent validity, as the AVE values ranged from 0.592 to 0.872, exceeding the recommended threshold of 0.50. The study’s optimized measurement model revealed sufficient convergent validity according to the results.
Table 1: Analysis of internal consistency
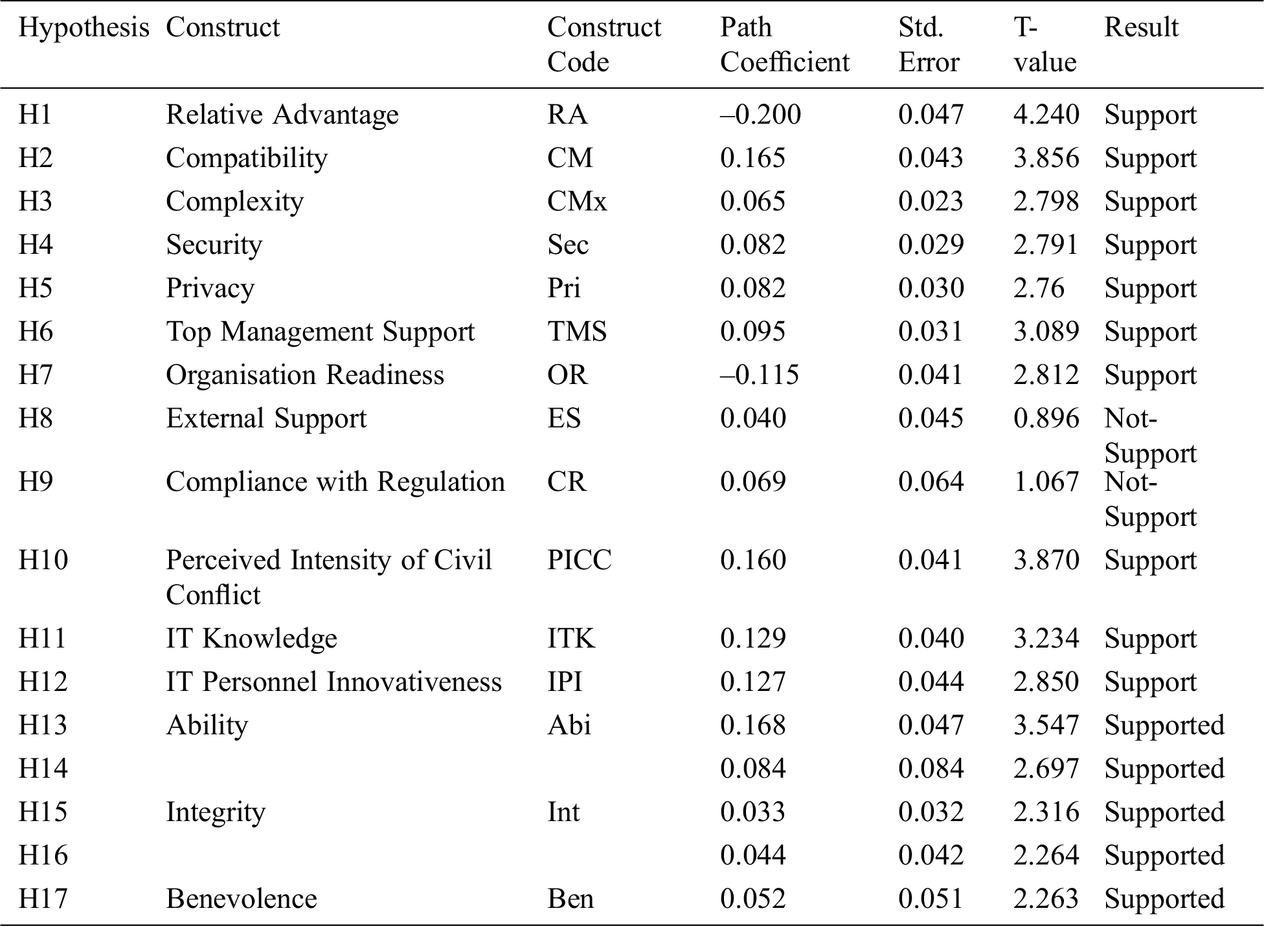
The structural model will be evaluated after the measurement model’s reliability and validity have been established, allowing the testing of the hypothesized relationship [50]. The significance of the path coefficients, which indicate the strength of the relationships between dependent and independent variables, was used to evaluate the structural model and the assessment of R2 value, which reflects the percentage of the variance of the endogenous construct (dependent variable) accounted by one or more exogenous constructs (independent variables). In assessing the R2 values in this study, we referred to the suggestion of Chin [51]. Based on the results of R2 in explaining the intention to adopt CC-SaaS, it was found to be high as the R2 value was 0.795. In addition, the significance of each path was estimated using a PLS bootstrapping method with 5,000 resamples to obtain t-values. Tab. 2 shows the hypothesis testing results.
The theoretical design employed in this study offers a unique opportunity to test whether trust as a multi-dimensional construct mediates the relationship between (CM, CMx, Sec, PRi, and TMS) and the intention toward the adoption of CC-SaaS. The assessment of the mediation effect was evaluated through path coefficient or the standardized β for the direct and indirect effects.
The TOE and DOI models were used to examine the factors that influence Iraqi government organizations’ decisions to adopt CC-SaaS. As per the result of the tested model, in making a decision to adopt CC-SaaS, the characteristics of the technology must suit the tasks to be adopted, followed by a number of external and internal factors such as organization and environment. In this study, three dimensions were examined in the analysis of the hypotheses for all supported results except H8 and H9. As indicated by the analysis, H1 postulated that RA significantly influences INT of CC-SaaS among IT professionals. The result revealed that this relationship is statistically significant and in line with a study conducted by Senarathna et al. [52]. Similarly, the result also revealed a significant effect of CM on INT, thereby supporting hypothesis H2. Similarly, H3 significantly influenced the INT, and the finding is consistent with prior studies [53]. The result of H4 also revealed a significant positive relationship between these constructs and agreed with the findings of prior studies [53]. Additionally, as postulated, the result of H5 revealed a significant influence on the INA. In essence, all the technology constructs have significant effects on the intention to adopt CC-SaaS. Moreover, H6 and H7 were found to have significant effects on INA and corroborate with studies conducted by Kandil et al. [53] and [29]. Conversely, the three drivers of the ED (i.e., ES, CR, and PICC) show different results. ES does not affect INA, and CR does not affect INA, which implied that the H8 and H9 are not supported. Therefore, H8 and H9 were rejected because they did not support the claim of this hypothesis and are consistent with [54] and [55]. Conversely, PICC was found to significantly affect INA.
Furthermore, the findings in Tab. 2 show that the trust dimension has a significant mediating effect on the intention to adopt CC-SaaS. The results show that ability has a significant effect on the relationship among CM, CMx, and intention to adopt CC-SaaS; accordingly, H11 and H12 are empirically supported. Therefore, the result on the effect of ability-based trust as a mediator is consistent with the findings of prior studies such as in Le et al. [56]. In addition, the mediation effect of integrity on the relationship among Sec, PRi, and intention to adopt CC-SaaS was investigated and indicates a significant effect, consequently supporting H13 and H14. Accordingly, the result of the effect of integrity-based trust as a mediator is consistent with the finding of prior studies in IT innovation such as the one conducted by Ong et al. [57] in north Taiwan. Furthermore, the result demonstrated that benevolence has a significant mediating influence on the relationship between TMS and intention to adopt CC-SaaS, hence, H15 is statistically supported. Therefore, the result of the effect of benevolence-based trust as a mediator is consistent with the findings of prior studies such as that of Le et al. [56], who found benevolence as a significant mediator for customer loyalty in E-banks in Indonesia. Finally, the current study concludes that trust as a multi-dimensional construct is a complementary partial mediator, which mediates the relationship among (CM, CMx, Sec, PRi, and TMS) and the intention to adopt CC-SaaS given that both of the direct and indirect effects are significant and with the same direction.
The current study’s findings had a wide range of implications for public sector organizations considering CC-SaaS adoption. Practically, it shows the indirect influence of the trust dimension on the public organization’s decision to adopt CC-SaaS. The study provides an analysis of factors affecting organizations’ adoption of CC-SaaS, which can be included in an effective strategic plan. In addition, the model developed can be adopted by public agencies in unsatiable countries to increase their service efficiency.
The study sought to determine the role of trust dimension as a mediator and the impact of PICC on the adoption of CC-SaaS. Owing to its influence in several studies within unstable countries, TOE was adopted and expanded upon by the addition of the trust dimension as a mediator and the PICC as an independent variable. According to the study findings, the dimension of trust is an important facilitator in the adoption of CC-SaaS. Trust, as a multi-dimensional construct, was discovered to be a complementary partial mediator that mediates the relationship among (CM, CMx, Sec, PRi, and TMS) and the intention to adopt CC-SaaS given that both of the direct and indirect effects are significant and with the same direction. Conversely, the results demonstrated that the PICC significantly influenced the behavioral intention toward the adoption of CC-SaaS. Furthermore, after testing the ten hypotheses, the empirical result proved that without ES, the Iraqi organizations could successfully adopt CC-SaaS. Moreover, the factor CR can potentially prevent the public organization from adopting cloud technology. However, in the Iraqi context, this analysis revealed that the CR would have no effect on the adoption of CC-SaaS due to the absence of any available regulations governing the IT or IS adoption in the country. Although the study has highlighted the critical factors that determine the adoption of CC- SaaS, the study has several limitations that can lead to direct future research. First, the study investigated the intention to adopt CC-SaaS from the perspective of IT professionals represented by the middle-level employees in their organization, whereas the end-user level was not considered. Future research should consider the individual dimension by considering the individual-level analysis for CC-SaaS adoption to remedy this limitation. Second, the sample selection process was influenced by the willingness of respondents to participate voluntarily, which incurred a sample selection bias and thus decreased the sample representativeness of the population.
Acknowledgement: Throughout the study the authors gratefully appreciate all those who contributed academically, technically, administratively, and financially to this study.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. P. R. Palos-Sanchez, F. J. Arenas-Marquez and M. Aguayo-Camacho, “Cloud computing (saas) adoption as a strategic technology: Results of an empirical study,” Mobile Information Systems, vol. 2017, no. 1, pp. 1–20, 2017. [Google Scholar]
2. G. Gallardo, J. Hernantes and N. Serrano, “Designing saas for enterprise adoption based on task, company, and value-chain context,” IEEE Internet Computing, vol. 22, no. 4, pp. 37–45, 2018. [Google Scholar]
3. I. Nanos, V. Manthou and E. Androutsou, “Cloud computing adoption decision in e-government,” in Operational Research in the Digital Era-ICT Challenges, Cham: Springer, pp. 125–145, 2019. [Google Scholar]
4. A. L. M. Ayoobkhan and D. Asirvatham, “A study on the adoption of software as a service (saas) in online business SMEs in sri lanka,” Asian Journal of Research in Computer Science, vol. 2, no. 2, pp. 1–13, 2019. [Google Scholar]
5. B. S. Shukur, M. K. Abed Ghani and M. A. Burhanuddin, “An analysis of cloud computing adoption framework for iraqi e-government,” Culture, vol. 19, pp. 34, 2018. [Google Scholar]
6. Y. C. Lee, “Adoption intention of cloud computing at the firm level,” Journal of Computer Information Systems, vol. 59, no. 1, pp. 61–72, 2016. [Google Scholar]
7. M. El-Masri and A. Tarhini, Factors affecting the adoption of e-learning systems in qatar and usa: Extending the unified theory of acceptance and use of technology 2 (utaut2). Educational Technology Research and Development, pp. 1–21, 2017. [Google Scholar]
8. H. F. Naqvi, F. H. Chandio, A. F. Soomro and M. S. Abbasi, “Software as a service acceptance model: A user-centric perspective in cloud computing context,” in 5th Int. Conf. on Engineering Technologies and Applied Sciences (ICETASBangkok, Thailand: IEEE, 2018. [Google Scholar]
9. H. K. Sheng, G. N. Samy, N. Kamaruddin, N. Maarop, N. H. Hassan et al., “Factors affecting trust of software as a service usage in public network: A correlation analysis,” in 7th Int. Conf. on Information and Communication Technology (ICoICTKuala Lumpur, Malaysia, pp. 1–6, 2019. [Google Scholar]
10. H. Karajeh, M. Maqableh and R. Masa’deh, “Privacy and security issues of cloud computing environment,” in Proceedings of the 23rd IBIMA Conference Vision, Valencia, Spain, pp. 1–15, 2020. [Google Scholar]
11. S. Seth, R. Johari, S. Mahajan and R. Bhatia, “Design and development of optimized scheduling algorithm for software as a service based applications in secure cloud environment,” in 6th Int. Conf. on Signal Processing and Integrated Networks (SPINNoida, India, pp. 329–334, 2019. [Google Scholar]
12. A. Tarhini, R. Masa’deh, A. Al-Badi, M. Almajali and S. H. Alrabayaah, “Factors influencing employees’ intention to use cloud computing,” Journal of Management and Strategy, vol. 8, no. 2, pp. 47–62, 2017. [Google Scholar]
13. J. Paliszkiewicz, “Trust: A multifaceted notion,” Managing Public Trust, Switzerland, Palgrave Macmillan, Cham, Springer, pp. 9–23,2018. [Google Scholar]
14. R. C. Mayer, J. H. Davis and F. D. Schoorman, “An integrative model of organizational trust,” Academy of Management Review, vol. 20, no. 3, pp. 709–734, 1995. [Google Scholar]
15. M. Adelmeyer, M. Walterbusch, P. Biermanski and F. Teuteberg, “Trust transitivity and trust propagation in cloud computing ecosystems,” in Twenty-Sixth European Conf. on Information Systems, Portsmouth, UK, pp. 29, 2018. [Google Scholar]
16. D. Zissis and D. Lekkas, “Addressing cloud computing security issues,” Future Generation computer systems, vol. 28, no. 3, pp. 583–592, 2012. [Google Scholar]
17. S. T. Alharbi, “Trust and acceptance of cloud computing: A revised utaut model,” in Int. Conf. on Computational Science and Computational Intelligence, Las Vegas, USA, pp. 131–134, 2014. [Google Scholar]
18. M. B. Alotaibi, “Exploring users’ attitudes and intentions toward the adoption of cloud computing in Saudi Arabia: An empirical investigation,” Journal of Computer Science, vol. 10, no. 11, pp. 2315–2329, 2014. [Google Scholar]
19. K. M. Khan and Q. Malluhi, “Establishing trust in cloud computing,” IT Professional, vol. 12, no. 5, pp. 20–27, 2010. [Google Scholar]
20. R. Buyya, S. Pandey and C. Vecchiola, “Cloudbus toolkit for market-oriented cloud computing,” in Int. Conf. on Cloud Computing, Beijing, China: IEEE, pp. 24–44, 2009. [Google Scholar]
21. S. Pearson, Privacy, security and trust in cloud computing, in Privacy and Security for Cloud Computing. London, UK: Springer, pp. 3–42, 2013. [Google Scholar]
22. G. Garrison, C. M. Rebman, S. H. Kim, C. M. Rebman Jr and S. H. Kim, “An identification of factors motivating individuals’ use of cloud-based services,” Journal of Computer Information Systems, vol. 58, no. 1, pp. 19–29, 2016. [Google Scholar]
23. C. C. Chen and M. Nakayama, “Key factors increasing the trust and intention to adopt standard cloud-based applications,” International Journal of Information Systems and Change Management, vol. 8, no. 2, pp. 144, 2016. [Google Scholar]
24. L. G. Tornatzky, M. Fleischer and A. K. Chakrabarti, “Processes of technological innovation,” Journal of Technology Transfer, vol. 16, no. 1, pp. 45–46, 1991. [Google Scholar]
25. A. Isma’ili, M. Li, Q. He and J. Shen, “Cloud computing services adoption in australian smes: A firm-level investigation,” in Pacific Asia Conference on Information Systems, Chiayi, Taiwan, pp. 1–13, 2016. [Google Scholar]
26. J. Baker, “Technology-organisation-environment framework (toein Information Systems Theory,” Springer, vol. 28, pp. 231–245, 2012. [Google Scholar]
27. E. M. Rogers, “Diffusion of innovations,” 5th ed., vol. 1. NY, USA: Simon and Schuster, pp. 1–576, 2003. [Google Scholar]
28. E. M. Rogers, “Diffusion of innovations,” 4th ed., vol. 1. NY, USA: Simon and Schuster, pp. 1–526, 1995. [Google Scholar]
29. A. Alhammadi, C. Stanier and A. Eardley, “The determinants of cloud computing adoption in saudi arabia,” in Second Int. Conf. on Computer Science & Engineering, Sydney, Australia, pp. 55–67, 2015. [Google Scholar]
30. M. Stieninger, D. Nedbal, W. Wetzlinger, G. Wagner and M. Erskine, “Factors influencing the organizational adoption of cloud computing: A survey among cloud workers,” International Journal of Information Systems and Project Management, vol. 6, no. 1, pp. 5–23, 2018. [Google Scholar]
31. N. Alkhater, R. Walters and G. Wills, “An empirical study of factors influencing cloud adoption among private sector organisations,” Telematics and Informatics, vol. 35, no. 1, pp. 38–54, 2018. [Google Scholar]
32. T. Oliveira, M. Thomas and M. Espadanal, “Assessing the determinants of cloud computing adoption: An analysis of the manufacturing and services sectors,” Information & Management, vol. 51, no. 5, pp. 497–510, 2014. [Google Scholar]
33. T. Lynn, X. Liang, A. Gourinovitch, J. P. Morrison, G. Fox et al., “Understanding the determinants of cloud computing adoption for high performance computing,” in 51st Hawaii Int. Conf. on System Sciences, Hilton Waikoloa Village, Hawaii, USA, pp. 3894–3903, 2018. [Google Scholar]
34. H. Gangwar, H. Date and R. Ramaswamy, “Understanding determinants of cloud computing adoption using an integrated,” Journal of Enterprise Information Management, vol. 28, no. 1, pp. 107–130, 2015. [Google Scholar]
35. M. A. Wahsh and J. S. Dhillon, “An investigation of factors affecting the adoption of cloud computing for e-government implementation,” in IEEE Student Conf. on Research and Development (SCOReDMalaysia: IEEE, Kuala Lumpur, pp. 323–328, 2015. [Google Scholar]
36. R. K. Singh, “Analyzing the factors for VMI implementation: A framework,” Global Business Review, vol. 14, no. 1, pp. 169–186, 2013. [Google Scholar]
37. F. Karim and G. Rampersad, “Factors affecting the adoption of cloud computing in saudi arabian universities,” International Journal of Cloud Computing and Services Science, vol. 10, no. 2, pp. 109, 2017. [Google Scholar]
38. N. Alkhater, G. Wills and R. Walters, “Factors influencing an organisation’s intention to adopt cloud computing in saudi arabia,” in 6th Int. Conf. on Cloud Computing Technology and Science, Singapore: IEEE, pp. 1040–1044, 2014. [Google Scholar]
39. M. K. Faaeq, “Factors affecting continued usage intention of electronic government among public servants in Iraq,” Ph.D. dissertation, Universiti Utara Malaysia, Malaysia, 2014. [Google Scholar]
40. H. Svare, A. H. Gausdal and G. Möllering, “The function of ability, benevolence, and integrity-based trust in innovation networks,” Industry and Innovation, vol. 27, no. 6, pp. 585–604, 2020. [Google Scholar]
41. J. K. Adjei, “The role of social media in national discourse and mobilization of citizens,” in Int. Conf. on Collaboration Technologies and Systems (CTSOrlando, Florida, USA, pp. 559–563, 2016. [Google Scholar]
42. D. Chatterjee and K. Bolar, “Determinants of mobile wallet intentions to use: The mental cost perspective,” International Journal of Human-Computer Interaction, vol. 35, no. 10, pp. 859–869, 2018. [Google Scholar]
43. U. Sekaran and R. Bougie, “Research methods for business: A skill building approach,” 7thed. London: John Wiley & Sons, pp. 1–423, 2016. [Google Scholar]
44. W. G. Zikmund, B. J. Babin, J. C. Carr and M. Griffin, “Business Research Methods,” 9th. ed. South-Western, USA: Erin Joyner, pp. 1–744, 2013. [Google Scholar]
45. H. A. Albaroodi, M. Abomaali and S. Manickam, “Iraqi’s organizations awareness to prompt open source cloud computing (oscc) in their service: A study,” in Int. Conf. on Advances in Cyber Security, Singapore, pp. 305–319, 2019. [Google Scholar]
46. J. F. Hair Jr, G. T. M. Hult, C. Ringle and M. Sarstedt, “A primer on partial least squares structural equation modeling (pls-sem),” 2nded., USA: Sage publications, pp. 1–363, 2016. [Google Scholar]
47. J. F. Hair Jr, M. Sarstedt, C. M. Ringle and S. P. Gudergan, “Advanced issues in partial least squares structural equation modeling,” USA: Sage Publications, pp. 1–253, 2017. [Google Scholar]
48. J. Henseler, “Partial least squares path modeling,” in Advanced methods for modeling markets, Switzerland: Springer, pp. 361–381,2017. [Google Scholar]
49. R. E. Anderson, B. J. Babin, W. C. Black and J. Hair, “Multivariate data analysis,” 8thed., London: Erin JOYNER, pp. 1–800, 2010. [Google Scholar]
50. J. Henseler, G. Hubona and P. A. Ray, “Using pls path modeling in new technology research: Updated guidelines,” Industrial Management & Data Systems, vol. 116, no. 1, pp. 2–20, 2016. [Google Scholar]
51. W. W. Chin, “How to write up and report PLS analyses,” in Handbook of partial least squares, 1st ed., New York: Springer, pp. 655–690, 2010. [Google Scholar]
52. I. Senarathna, C. Wilkin, M. Warren, W. Yeoh and S. Salzman, “Factors that influence adoption of cloud computing: An empirical study of australian smes,” Australasian Journal of Information Systems, vol. 22, pp. 1–31, 2018. [Google Scholar]
53. A. M. N. A. Kandil, M. A. Ragheb, A. A. Ragab and M. Farouk, “Examining the effect of toe model on cloud computing adoption in egypt,” 8th Int. Conf. on Restructuring of the Global Economy, University of Oxford, UK, vol. 9, no. 4, pp. 113–123, 2018. [Google Scholar]
54. C. F. Ming, C. K. On, A. Rayner, T. T. Guan and A. Patricia, “The determinant factors affecting cloud computing adoption by small and medium enterprises (smes) in sabah,” Malaysia Journal of Telecommunication, Electronic and Computer Engineering (JTEC), vol. 10, no. 3–2, pp. 83–88, 2018. [Google Scholar]
55. A. N. Tashkandi and I. M. Al-Jabri, “Cloud computing adoption by higher education institutions in saudi arabia: an exploratory study,” Cluster Computing, vol. 18, no. 4, pp. 1527–1537, 2015. [Google Scholar]
56. T. M. Le, N. A. D. Hediasri and S. Y. Liaw, “A Cross-cultural comparison of e-banks based on multiple mediations of trust,” Contemporary Management Research, vol. 13, no. 4, pp. 219–238, 2017. [Google Scholar]
57. C. S. Ong and Y. L. Lin, “Security, risk, and trust in individuals’ internet banking adoption: an integrated model,” International Journal of Electronic Commerce Studies, vol. 6, no. 2, pp. 343–356, 2015. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |