DOI:10.32604/iasc.2021.016382

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.016382 |  |
| Article |
Secure Image Authentication Using Watermarking and Blockchain
1Department of Computer Engineering, College of Computer and Information Sciences King Saud University 11543 Riyadh, Kingdom of Saudi Arabia
2Information Technology Department, College of Computer and Information Sciences
King Saud University, 11451 Riyadh, Kingdom of Saudi Arabia
*Corresponding Author: Wadood Abdul. Email: aabdulwaheed@ksu.edu.sa
Received: 31 December 2020; Accepted: 13 February 2021
Abstract: Image authentication is an important field that employs many different approaches and has several significant applications. In the proposed approach, we used a combination of two techniques to achieve authentication. Image watermarking is one of the techniques that has been used in many studies but the authentication field still needs to be studied. Blockchain technology is a relatively new technology that has significant research potential related to image authentication. The watermark is embedded into the third-level discrete wavelet transform (DWT) in the middle frequency regions to achieve security and imperceptibility goals. Peak signal-to-noise ratio PSNR, structural similarity matrix (SSIM), normalized correlation coefficient (NCC), and bit error rate (BER) are used to measure the performance of image watermarking. We used blockchain technology to avoid involving a trusted third party for authentication. Secure Hash Algorithm 256 (SHA-256) is applied on the watermark to save it into the blockchain. The watermark is encrypted using Advanced Encryption Standard (AES) and embedded into the image. The proposed method is tested on the USP SICI database and the MedPix medical image database. Ethereum blockchain is used to provide security, anonymity, and integrity of data with no third-party intervention. The proposed solution demonstrates enhanced security for image authentication compared with the state-of-the-art.
Keywords: Authentication; watermarking; DWT; encryption; security; hash; blockchain
The importance of image authentication has emerged in lots of areas: martial images, images for proof in court, medical images, and several other research areas [1–3]. When dealing with these images and other types of images, there is a need for a security and authentication layer to avoid incorrect judgments. Digital image processing tools are widely available and easy to use, allowing easy access, manipulation, and reuse. These days, unauthorized copies of images could be easily made to manipulate images for financial or human life losses [4]. Authenticating an image is the operation of making sure that the person who provided the image is the same person with appropriate rights to the image. Image authentication has become a more important issue since the revolution of social media and the Internet. Given the important requirement for securing sensitive information that could threaten security, we need to identify and distinguish between real and fake images. In this work, we used two techniques to authenticate images; watermarking and blockchain. Watermarking is the process of inserting secret information into the digital image. The main elements of watermarking are watermark embedding and watermark extraction. The embedding process is used to add the watermark into the cover image; on the other hand, watermark extraction extracts the watermark from the image. The key is used during the watermarking process for securing the watermark embedding and extraction procedures. Blockchain is a distributed ledger technology that saves information to make sure that it will remain the same and not be changed by anyone. It also executes and shares all the digital events with the involved users [5]. The use of the blockchain is to accomplish authentication without the involvement of a trusted third party for the secrecy of the watermark so is not be exposed to anyone expect the involved parties. Our work has many benefits in the image authentication field. Many advantages have been achieved compared to previous works and the proposed work contributes the following to the state of the art. The proposed work was implemented with high imperceptibility and security. The encrypted watermark is embedded in the third level wavelet coefficients. The watermark is hashed and added to the blockchain to improve security.
The rest of the paper is organized as follows. Section 2 presents the related works followed by Section 3 that presents the secure watermarking approach. Experimental results are presented in Section 4 followed by the comparison with state-of-the-art methods in Section 5. The work is concluded in Section 6.
In recent times, blockchain technology has gained lots of attention since it has been introduced in 2008 by Nakamoto. In Crosby et al. [6], descriptive literature on the blockchain has been introduced for the first time. The discussion is about the Bitcoin system and there is no real focus on blockchain technology. Blockchain is used in many industries, finance, medical, agriculture, smart city, internet of things, genetic engineering, energy industry, automobile insurance industry, cloud computing, cloud storage, and others. Hou [7] has introduced an E-government application of blockchain in China. Lim et al. [8] set up MyData for personal data management which was authorized by the Finnish government. A blockchain- cross-domain authentication model named BlockCAM, the cross-domain authentication protocol, has also been proposed in [9]. Liu et al. [10] introduced a combination of strong Physical Unclonable Functions (PUFs)-based authentication protocol and blockchain with Peer to Peer (P2P) distributed storage script.
A method for medical records is controlled and secured using blockchain based on a genetic algorithm and DWT is proposed in [11]. Blockchain technology has been used to provide a privacy consciousness authentication framework for a multi-server environment which was introduced by Xiong et al. [12]. Puthal et al. [13] presented a new consensus algorithm called proof of authentication for scalable blockchain. A personal data management approach that concentrates on privacy using blockchain has been produced by Zyskind et al. [14]. To accomplish fast authentication for vehicles and cooperative participation between vehicular networks, a distributed trust access authentication system is introduced relying on a blockchain network and edge computing [15]. A semi-fragile watermarking framework to increase the invisibility and manipulation recovery performance under JPEG compression is done by Chen et al. [16].
A new blind color image watermarking technique in the spatial domain was proposed by Su et al. [17]. The technique was used to get the highest eigenvalue of Schur decomposition. This eigenvalue is used when embedding and extracting the watermark. The semi-fragile watermarking method that relies on a rotation vector for content authentication purposes was introduced by Fu et al. [18]. Robust image watermarking in the Lifting Wavelet Transform (LWT) domain using more than one sub-band was proposed by Islam et al. [19]. This scheme embeds a binary watermark in the LWT sub-bands. During the extraction phase, Support Vector Machine (SVM) was used to increase the robustness. Image authentication is a field that has several methods and implementations. Combining watermarking and blockchain for image authentication is a relatively new field that still needs more research to achieve the objectives of security and imperceptibility.
3 Secure Watermarking using Hashing and Blockchain
The proposed method will introduce image authentication using watermarking and the Ethereum blockchain for gray-scale images in the frequency domains. The watermark embedding phase is shown and described in Fig. 1. First of all, the Discrete Wavelet Transform (DWT) in the third level is applied to the image that needs to be authenticated. The watermark is the image owner’s ID hash number. Advanced Encryption Standard (AES) encryption with a secret key is used to encrypt the watermark which is then embedded into the middle frequency wavelet coefficients. The same watermark that is embedded into the image is hashed with SHA-256 and saved by the user depending on the user key into the blockchain. AES and SHA-256 are used together as an extra layer of security when embedding the watermark into the image and when saving the watermark into the blockchain. AES is used for encrypting the watermark before embedding into the image. SHA-256 is used to encrypt the watermark before saving it into the blockchain. SHA-256 is used as it is a one-way function and we do not want anyone to gain access to the watermark as a consequence of getting the AES key.
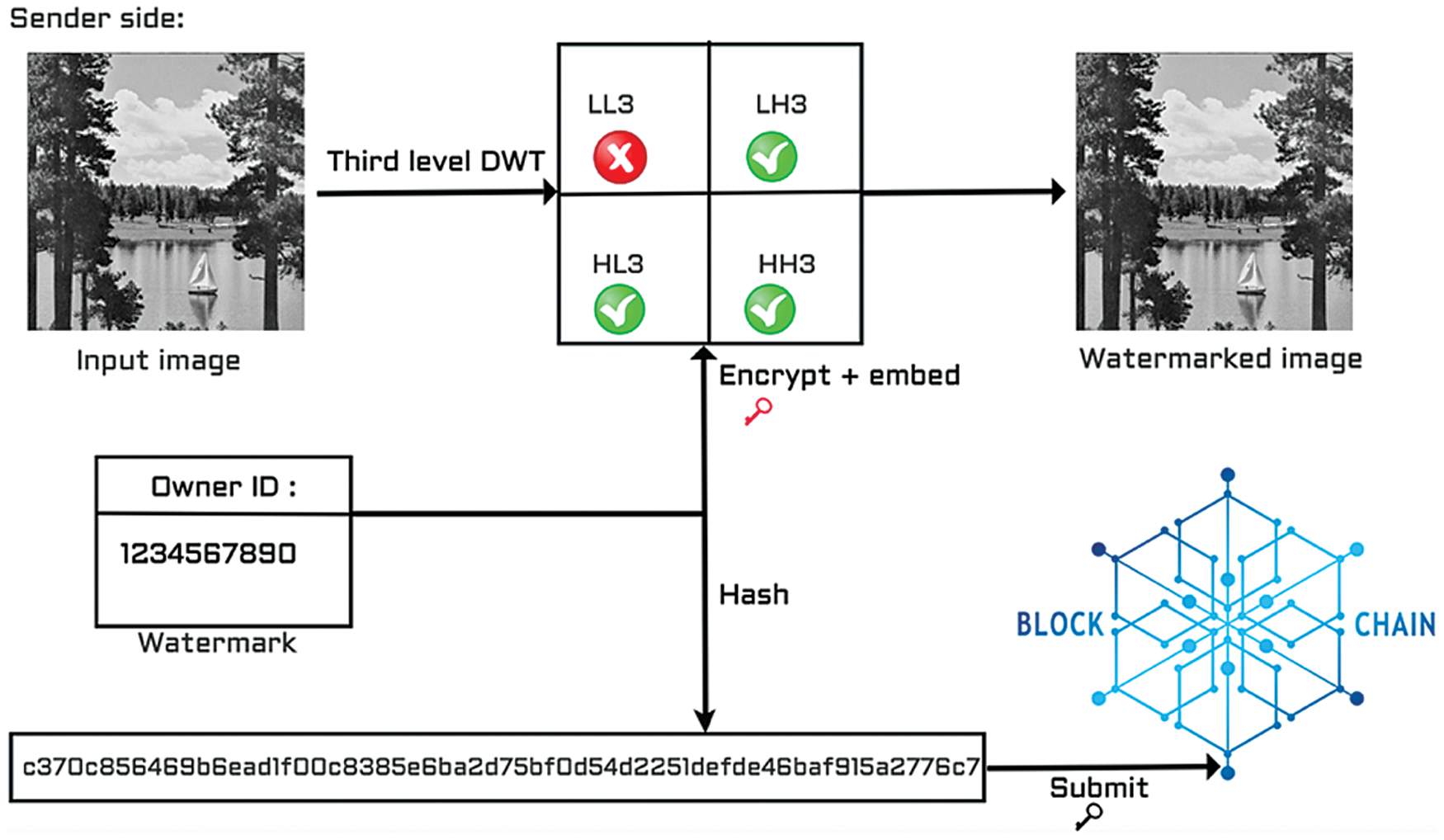
Figure 1: Proposed secure watermark embedding
The watermark extraction process is shown in Fig. 2. The extraction process is used when there is a need to check the authenticity of a received image. To authenticate a received image, the watermarked image and the encryption key are required for the watermark extraction from the image. We extract the encrypted watermark from the three middle frequency sub-bands of the image. Then the watermark is decrypted as shown in Fig. 2. Secure Hash Algorithm 256 (SHA-256) is applied onto the decrypted watermark. From the blockchain, we obtain the block number of the recorded watermark ID hash or the exact owner’s watermark ID hash that has been extracted and hashed from the received image. We use one of these two pieces of information to fetch the saved watermark from the blockchain. The final step is to compare the watermark ID hash that is extracted from the image and the watermark ID hash that is recorded into the blockchain; if they match, then the image is authentic.
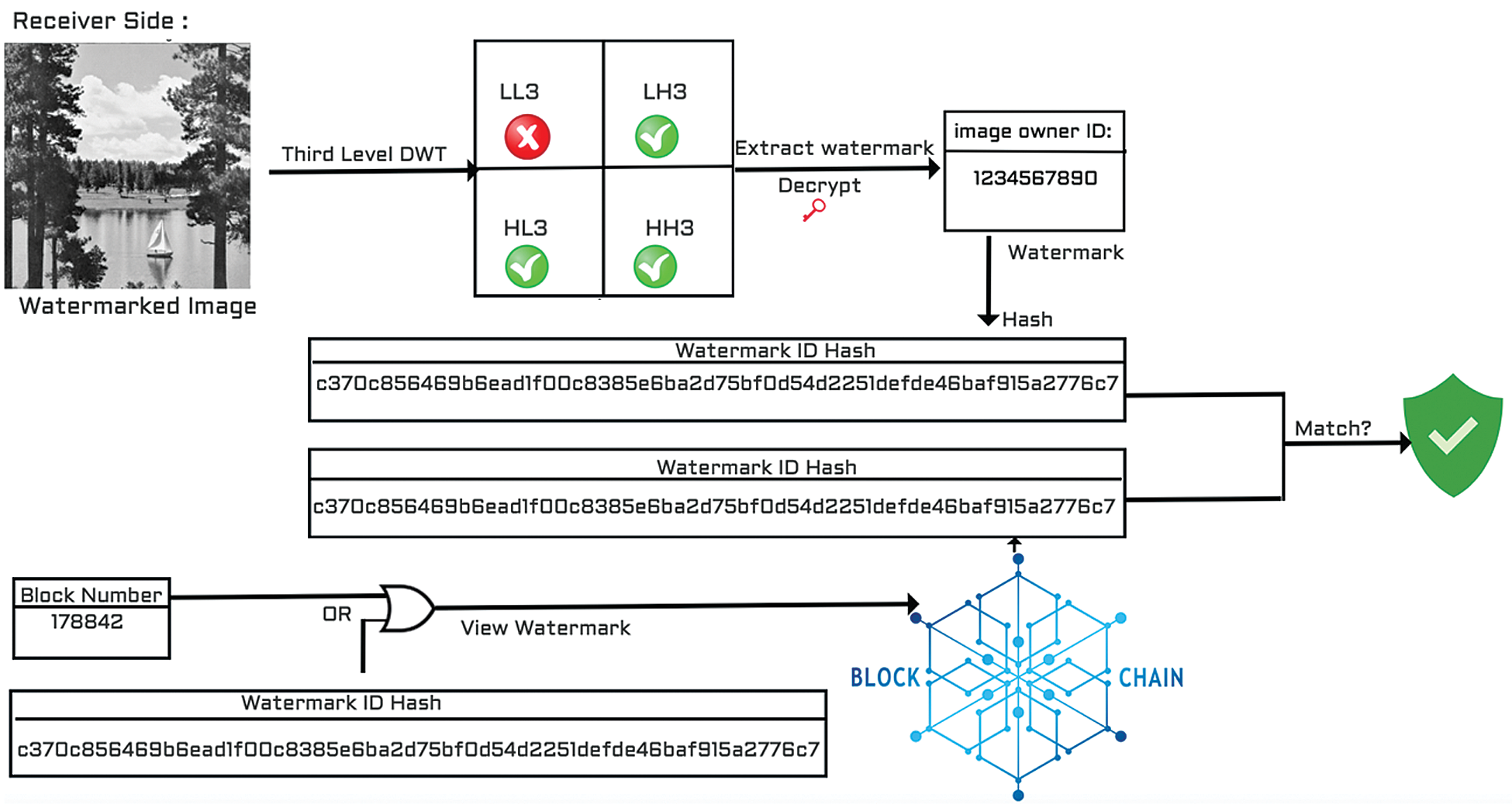
Figure 2: Secure watermark extraction
Blockchain is used to validate the authenticity of the watermark such that no third party is involved in the authentication process. In the proposed approach, AES-128 encryption is used to encrypt the watermark before embedding the watermark into the input image, as shown in Fig. 1.
3.1 Watermark Embedding Process
The watermark embedding consists of applying third-level DWT on the original image Ii. Ii is divided into 4 × 4 non-overlapping blocks. Then the watermark is encrypted using AES encryption with a secret key. The embedding strength E is initialized to 5. The difference D is calculated using the following equation:
The difference D is calculated for all the watermark Wb and the watermark is embedded into Ii. The embedding algorithm is specified in Alg. 1, where Bi is ith block of wavelet coefficients and Bini is ith embedding bit.

SHA-256 is applied to the watermark before saving it into the blockchain in the embedding phase as shown in Fig. 1, and in the extraction phase as shown in Fig. 2. After extracting the encrypted watermark from the input image and decrypting the watermark, we apply SHA-256 to the watermark. SHA-256 hashing is one of the most secure ways to secure digital information. It is a mathematical process that generates 256-bit random letters and numbers from any input.
3.2 Watermark Extraction Process
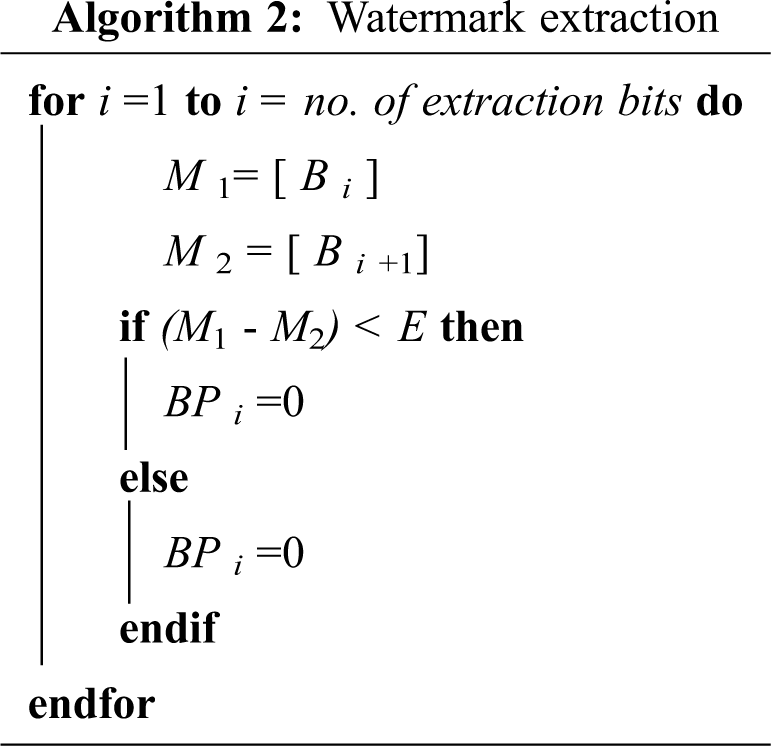
The watermarked image is decomposed into 4 × 4 blocks. The difference between the pixels Bi and Bi+1 of the neighboring blocks is calculated using Eq. 1. The extraction algorithm is specified in Alg. 2, where Bi is ith block of wavelet and BPi is ith extracted bit.
The experiments were conducted using gray-scale images of size 512 × 512 pixels and 256 × 256 pixels from USC SIPI image database [20]. In the experiments, 242 images are used. The watermark is a 10-digit ID number that is repeated thrice in the image. The reason for repeating the watermark is to increase the security and robustness of the watermark. PSNR, NCC, SSIM, and BER are used to evaluate the watermarking approach.
Peak Signal-to-Noise Ratio (PSNR) is given by Eq. 2.
where
Normalized correlation coefficient (NCC) is given by Eq. 3.
M is the number of rows of the image, N is the number of columns,
The Structural Similarity Matrix is given by Eq. 4.
where
Bit Error Rate (BER) is given in Eq. 5.
4.1 Perceptual Quality Analysis—USC SIPI Database
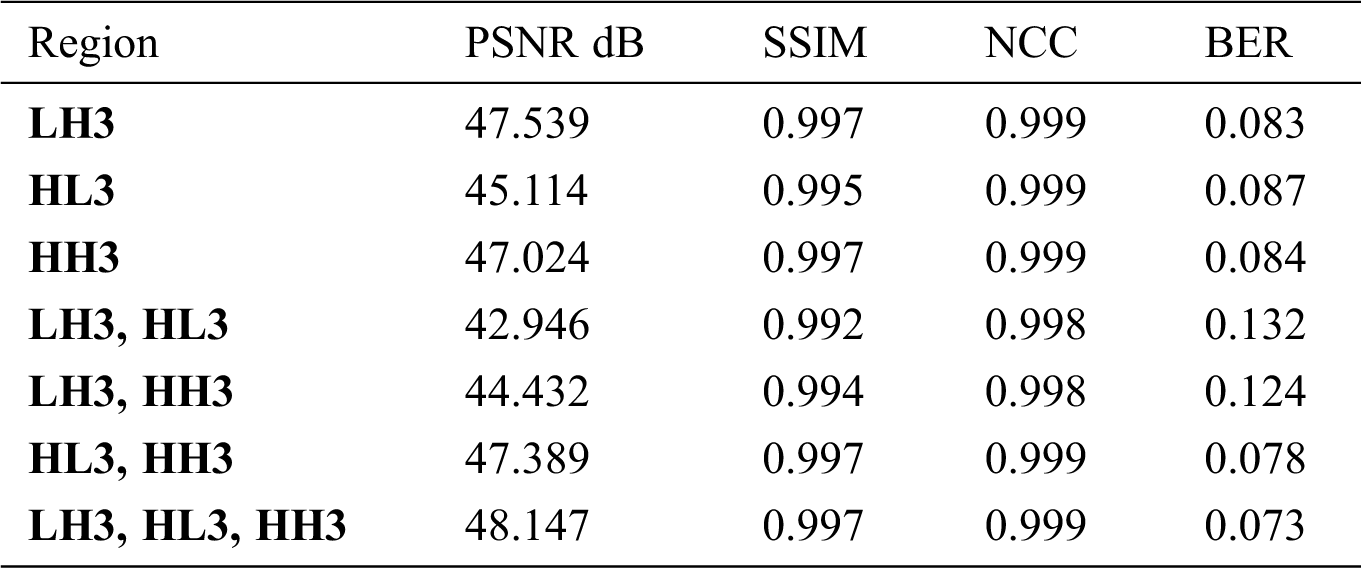
Tab. 1 shows the comparison between results when embedding into different wavelet sub-bands. The comparison is carried out to determine the effect of embedding the watermark into each region on the perceptibility metrics. Embedding into all the three third-level high frequency regions has comparable results to embedding in other sub-bands with the embedding strength 1. The results of embedding into all the three third-level high frequency sub-bands give PSNR 48.147, SSIM 0.997, NCC 0.999, and BER 0.073.
Table 1: PSNR, SSIM, NCC, BER of the USC SIPI images database using the secure method on third-level sub-bands
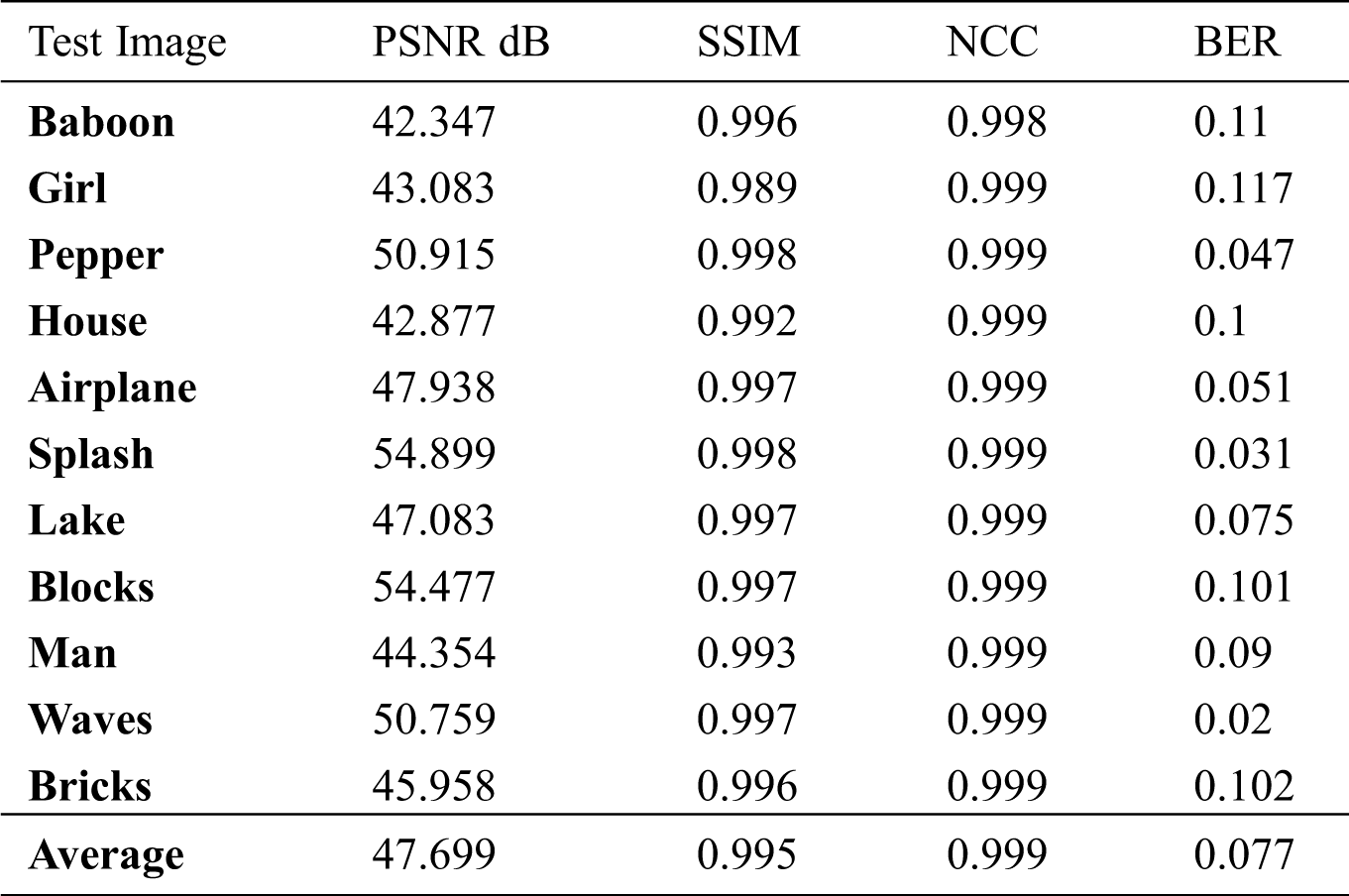
Tab. 2 shows a comparison between the results of different sample images from USC SIPI image database using the proposed method. We see that the PSNR values range from 42.347 dB to 54.899 dB. The SSIM value is between 0.989 and 0.998. NCC value is between 0.998 and 0.999. BER has values from 0.020 to 0.117.
Table 2: PSNR, SSIM, NCC, BER of sample images from USC SIPI database using the proposed method
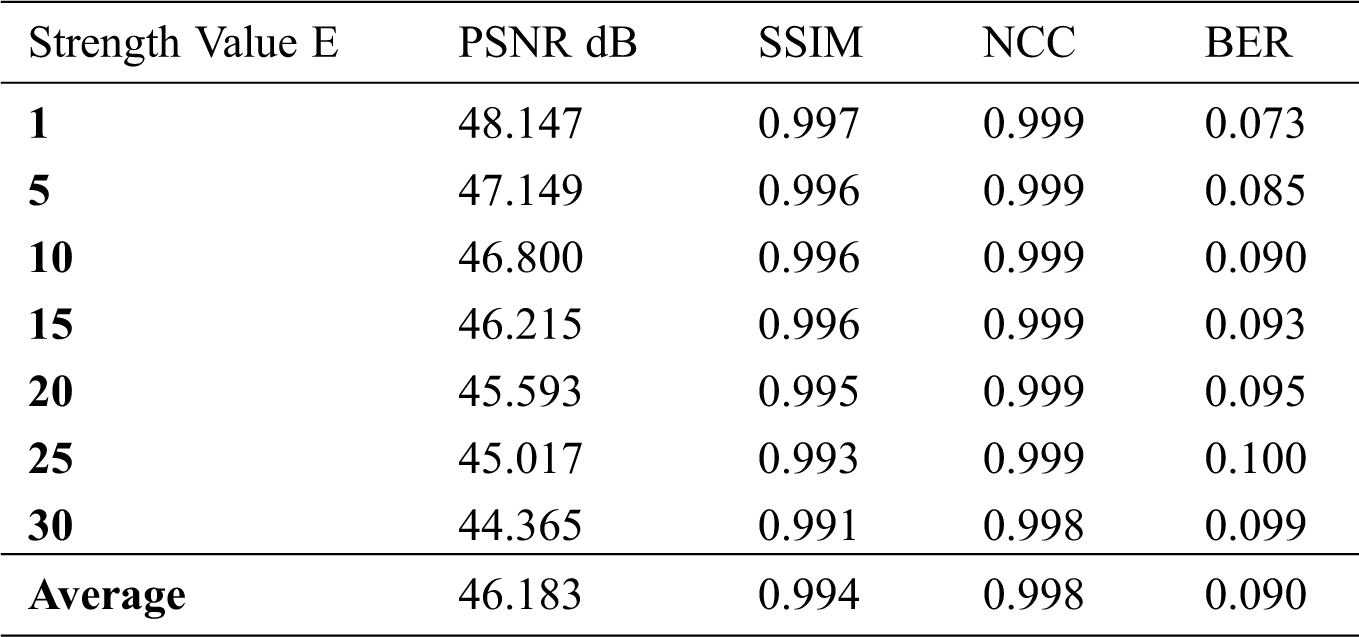
E factor is the strength of watermark embedding. Tab. 3, shows the results when applying different strength values. It also shows that whenever the value gets higher, the performance metrics get lower. The best performance metrics in terms of invisibility are achieved for E value of 1. The PSNR value, in this case, is 48.147 dB, SSIM is 0.997, NCC is 0.999, and BER is 0.073.
Table 3: PSNR, SSIM, NCC, and BER of the USC SIPI images database using different values of E
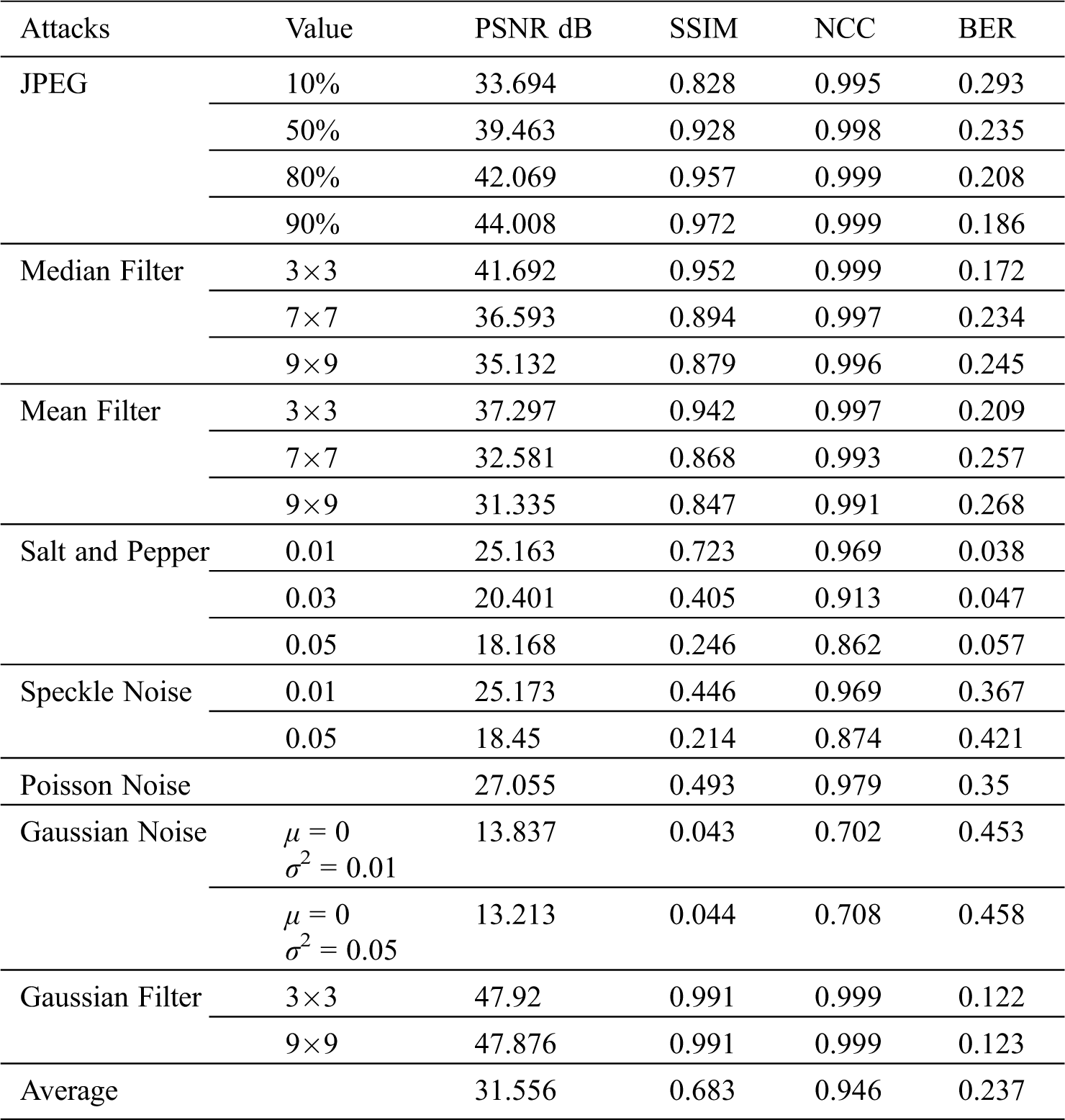
The test and analysis of the proposed watermarking approach show acceptable results on the performance metrics related to imperceptibility. The testing of the proposed watermarking method is also examined using changes and attacks such as addition of noise, compression, and filtering on the watermarked images. Tab. 4 shows the tests and results of the proposed watermarking method using different attacks such as additive white Gaussian, salt and pepper, speckle, and Poisson noise. JPEG compression, median filtering, mean filtering, and Gaussian filtering attacks were also applied to the watermarked images. From the results we get from applying these different attacks, we can see that JPEG compression with 90% has PSNR 38.469, SSIM 0.968, NCC 0.994, and BER 0.245. The calculated metrics drop as more compression is applied to the watermarked images. On the other hand, when Gaussian noise is added to the image, the lowest results of PSNR 13.144, SSIM 0.176, NCC 0.541, and BER 0.464 are obtained. This signifies the sensitivity of the watermarking algorithm to Gaussian noise.
Table 4: PSNR, SSIM, NCC, BER of the USC SIPI images database under different attacks
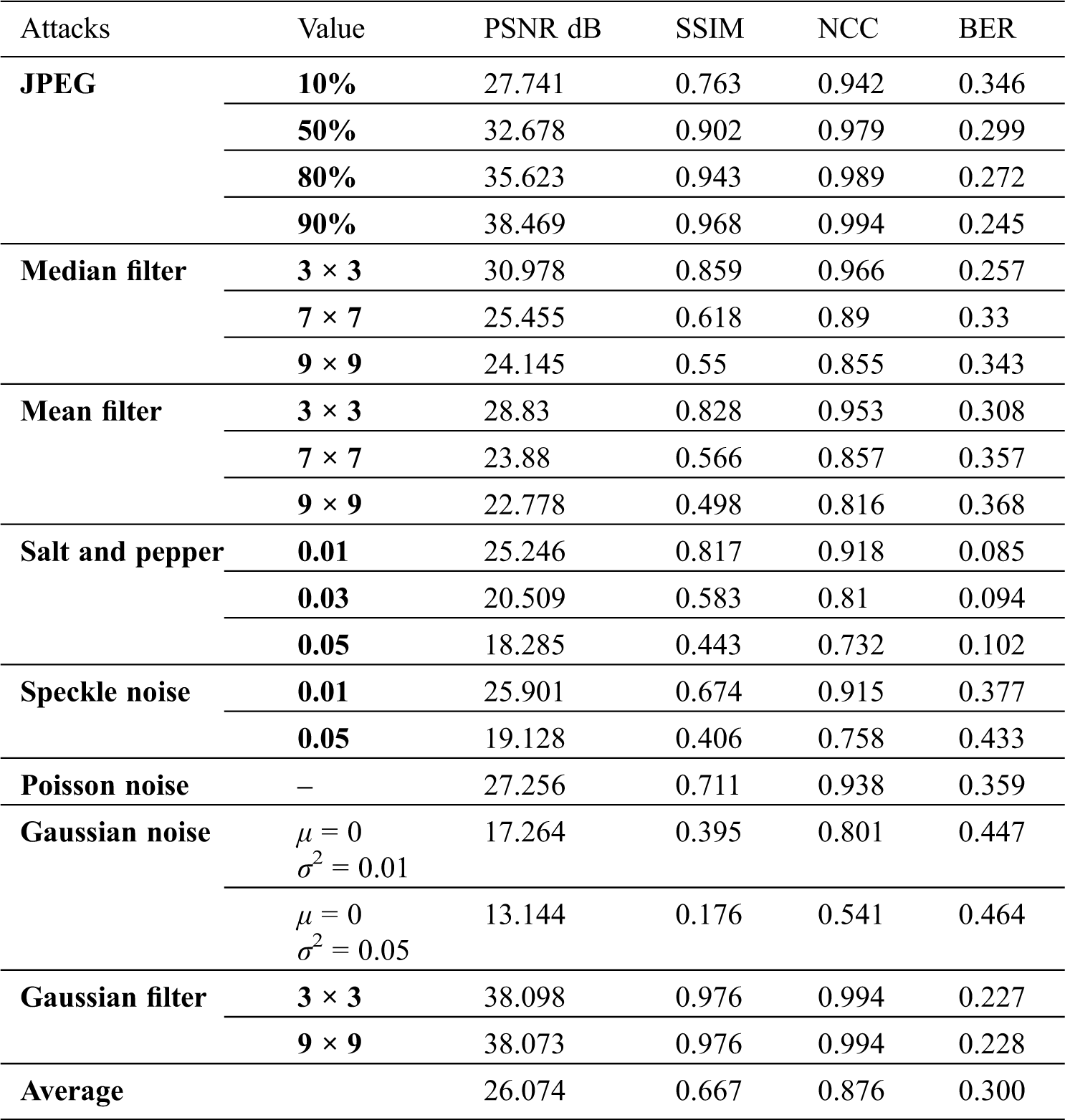
From Tabs. 1–4, we can conclude that the watermarking algorithm is not very robust against attacks. However, it has better performance in terms of imperceptibility which is a desired trait of image authentication approaches.
4.2 Perceptual Quality Analysis—MedPix Database
To demonstrate the effectiveness of the proposed watermarking approach on medical images, we used the MedPix database [21]. It is a freely available online database of medical images. Gray-scale chest X-ray images of size 256 × 256 are considered as the host images. In the experiments, we used 200 medical images. The watermark is a 10-digit ID number that is repeated three times in the image. A sample image from the database after watermarking is shown in Fig. 3b. The original image is shown in Fig. 3a.

Figure 3: Medical image—chest X-Ray a. Original chest X-ray image b. Watermarked chest X-ray image
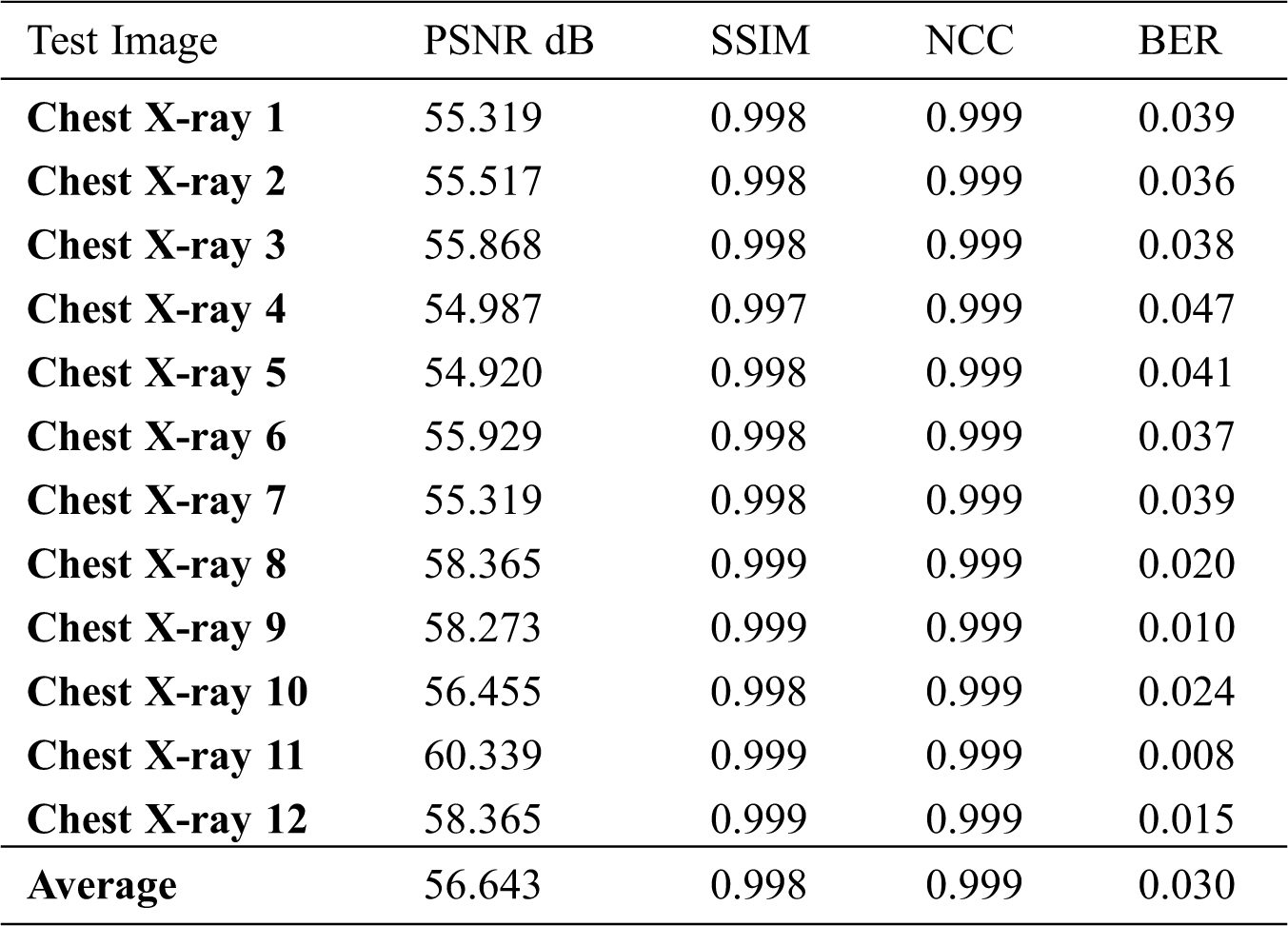
Test results of sample test images that are used for the experiments are given in Tab. 5. The highest PSNR and SSIM values for the images are 60.339 and 0.999, respectively. The NCC value is the same for all images, 0.999 and BER has the lowest value, 0.008. The lowest PSNR value is 54.920 and the lowest SSIM value is 0.997.
Table 5: PSNR, SSIM, NCC, and BER of the sample images from the MedPix database
PSNR and SSIM values decrease when using high embedding strength, as shown in Tab. 6. On the other hand, the NCC value remains the same. The BER has the highest value when E is 1.
Tab. 7 shows the PSNR, SSIM, NCC, and BER values for images from the MedPix database under different attacks. JPEG compression, median filter, mean filter, salt and pepper noise, speckle noise, additive white Gaussian noise, and Gaussian filter attacks are applied to the watermarked images. The medical images were impacted the most by Gaussian noise and least by Gaussian filter attack.
Table 6: PSNR, SSIM, NCC, and BER of the MedPix database for different values of E
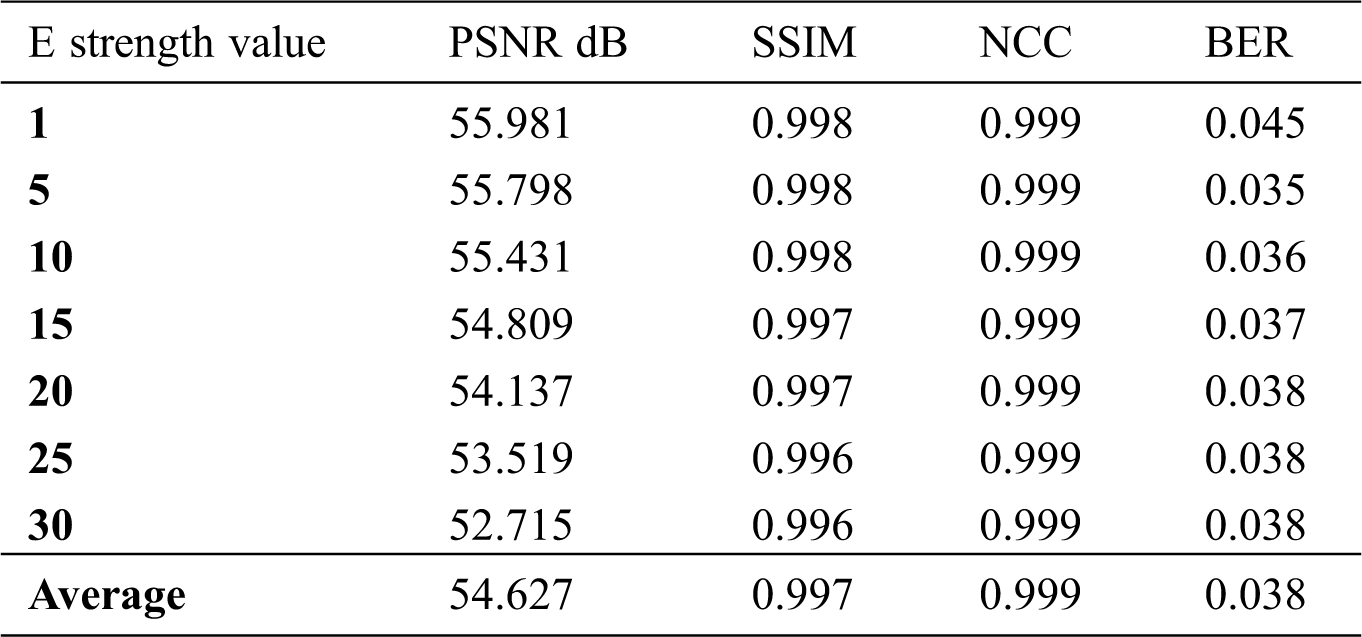
Table 7: PSNR, SSIM, NCC, and BER of the MedPix database under different attacks
4.3 Blockchain Experimental Results
To measure the performance of the blockchain, we use the CPU time for every node. We use Grafana to measure CPU time. After successfully recording the watermark into the blockchain, we used the Ethereum lite explorer and Grafana for analyzing the data recorded in the blockchain.
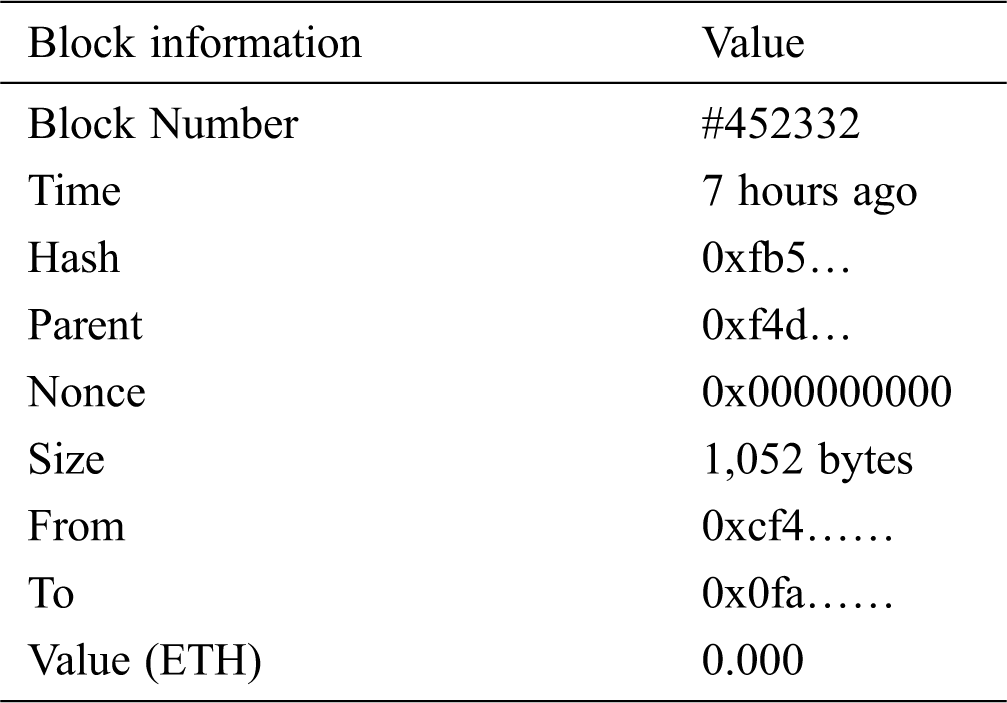
Ethereum lite explorer is an application used to connect to Ethereum javascript object notation remote procedure call compatible node which is a private Ethereum explorer that does not need any servers or any third party to show blockchain data. To display blockchain data, we could search the Ethereum lite explorer by entering the block number, transaction hash, and address. Ethereum lite explorer shows detailed information related to the block. A list of information as shown for a certain block is given in Tab. 8.
Table 8: Information shown in Ethereum lite explorer
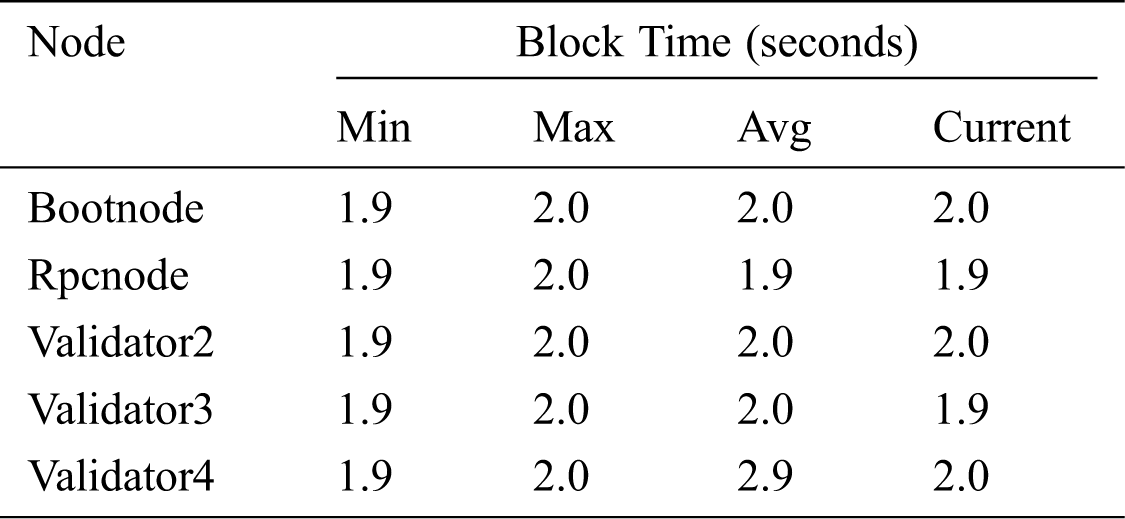
Grafana [22] is used to visualize and analyze data. It allows to query, visualize, alert on, and explore metrics. It is used as a tool to chart Time-Series DataBase (TSDB) data into clear graphs. It represents the block time graph that shows the date of the time in seconds when the block has been registered, the maximum and minimum time taken by the node to carry out a job, the average time calculated, and the current time. Tab. 9, represents values of the block time used for certain nodes. This table only shows the details of bootnode, Rpcnode, and validators nodes indicating acceptable time taken to perform tasks related to the proposed watermarking approach.
5 Comparisons With State-of-the-art Methods
Tab. 10 shows a comparison between the most relevant papers representing image authentication using watermarking or blockchain. As we can see from Tab. 10, the proposed method introduced a new method that combines watermarking and blockchain to serve the main purpose of image authentication, security, and imperceptibility all together while presenting a reasonable high PSNR. The results shown in Tab. 10 are carried out on the USC SIPI database. Tab. 11 shows a comparison between the most relevant papers representing image authentication using watermarking or blockchain for medical images using the MedPix image database.
This comparison is based on six categories: the database that has been used during the testing, the methodology, PSNR, blind, which refers to the watermarking mechanism if it requires the original image during the extraction phase, authentication method, security method, and limitation of the work. We compared the proposed method with other methods in terms of watermarking methods and their security.
The proposed work is compared with Bhowmik and Feng [23], Meng [24], and with other methods presented in [17–19] that have been tested using the same database. The average values of PSNR indicate the efficiency of the proposed approach to preserve the invisibility between the original and watermarked images. The proposed approach demonstrates better performance than state-of-the-art in several categories. The use of the blockchain to accomplish authentication without the involvement of a trusted third party with acceptable levels of PSNR is a special advantage of the proposed approach.
Tab. 11 shows the comparison with other medical image databases using the previously mentioned categories. The proposed method has reached an average PSNR of 55.981, which is the highest value compared with other methods. All the compared works have one or more limitations: lower PSNR value compared to the proposed method, absence of authentication mechanism, and absence of security mechanism. According to our review of the state-of-the-art, the proposed medical image watermarking approach is the first method that demonstrates an effective solution to the medical image authentication problem using the blockchain, thus removing the need for trusted third parties.
Table 10: Comparisons of the proposed approach using the USC SIPI database with state-of-the-art methods
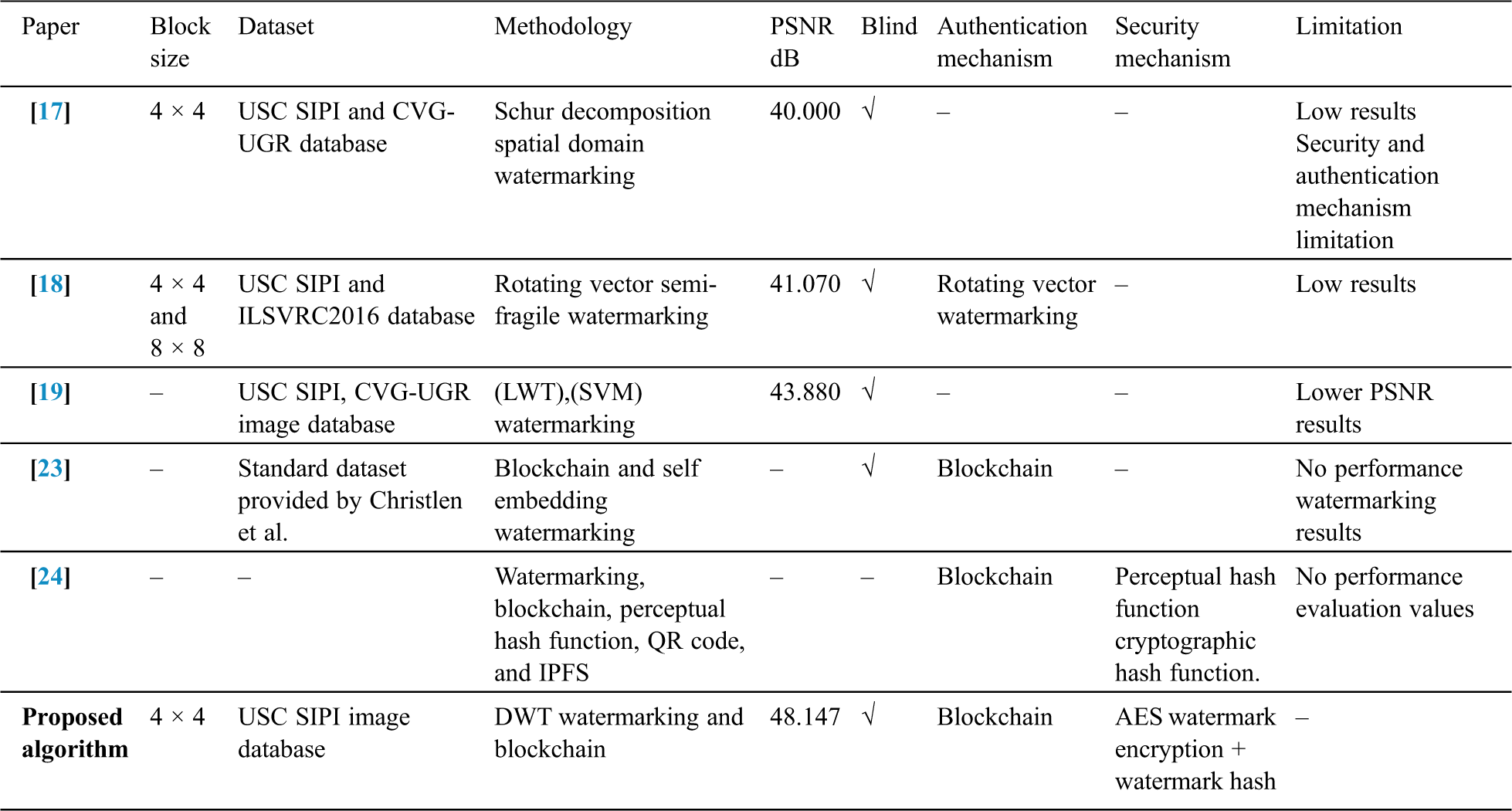
Table 11: Comparison of the MedPix medical image database with state-of-the-art methods
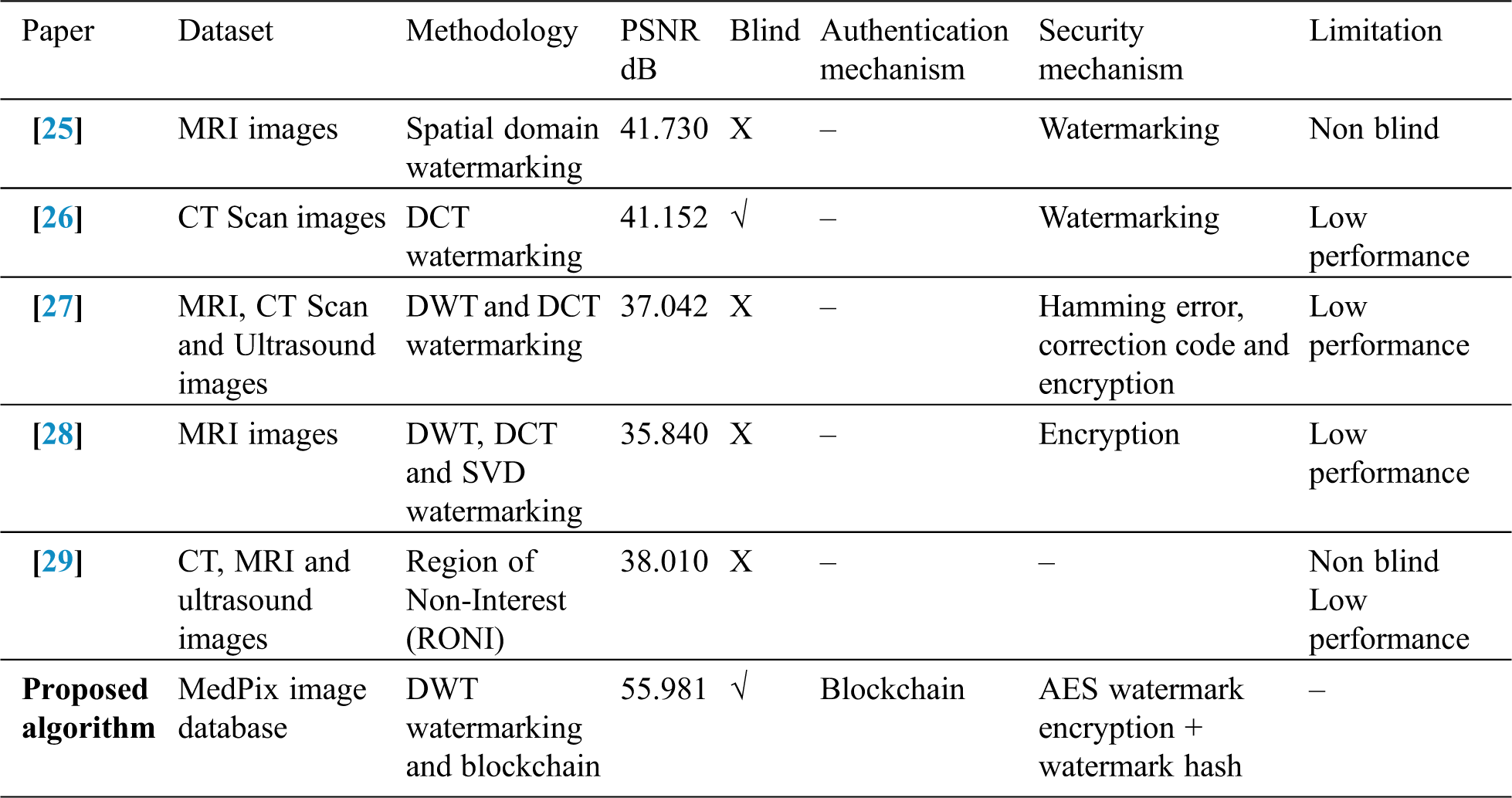
Image authentication is an important field that is carried out using different techniques. In this paper, we used watermarking and blockchain combined together to achieve image authentication. Image authentication scheme has been introduced using the technologies of watermarking in the third-level DWT, AES encryption, SHA-256 hashing, and blockchain. Our consideration is to authenticate and secure the digital images from manipulation. Our approach has five different steps to follow. Encrypting the watermark using AES encryption with a secret key. Embedding the encrypted watermark into the three middle frequency regions of the third-level DWT. Taking the same watermark and hashing to save into the blockchain. At the extraction stage, the watermark is extracted from the host image, the encrypted watermark is decrypted using the same secret key. The decrypted watermark is hashed using SHA-256 for comparing it with the hashed watermark that is saved in the blockchain. From the blockchain, we acquire the hash of the watermark or the block number of the transaction that contains the saved watermark. After getting the hash of the watermark we compare it with the watermark that is extracted from the image. If the comparison matches then it is an authentic image, if it does not match then the image has potentially been attacked and is not authentic. For the experimental tests, we used USC SIPI database and MedPix medical database with different image sizes. Our results have shown that the proposed watermarking approach gives the best performance compared to the state-of-the-art works. In the future, the proposed technique could be tested with other images such as MRI, CT, ultrasound, and other kinds of medical images. Also, the proposed algorithm can be applied on color images as future work.
Acknowledgement: This Project was funded by the National Plan for Science, Technology and Innovation (MAARIFAH), King Abdulaziz City for Science and Technology, Kingdom of Saudi Arabia, Award Number (13-INF2114-02).
Funding Statement: This Project was funded by the National Plan for Science, Technology and Innovation (MAARIFAH), King Abdulaziz City for Science and Technology, Kingdom of Saudi Arabia, Award Number (13-INF2114-02).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. O. Nafea, S. Ghouzali, W. Abdul and E. Qazi. (2016). “Hybrid multi-biometric template protection using watermarking,” Computer Journal, vol. 59, no. 9, pp. 1392–1407. [Google Scholar]
2. S. Ghouzali and W. Abdul. (2013). “Private chaotic biometric template protection algorithm,” in IEEE Second Int. Conf. on Image Information Processing (ICIIP-2013). Shimla, India, 655–659. [Google Scholar]
3. W. Abdul, O. Nafea and S. Ghouzali. (2020). “Combining watermarking and hyper-chaotic map to enhance the security of stored biometric templates,” Computer Journal, vol. 63, no. 3, pp. 479–493. [Google Scholar]
4. A. Haouzia and R. Noumeir. (2008). “Methods for image authentication: A survey,” Multimedia Tools and Applications, vol. 39, no. 1, pp. 1–46. [Google Scholar]
5. S. Bennett. (2017). Blockchain: A guide to Understanding Blockchain. Newyork, USA: The Cryptomasher Series. [Google Scholar]
6. M. Crosby, P. Pattanayak, S. Verma and V. Kalyanaraman. (2016). “Blockchain technology: Beyond bitcoin,” Applied Innovation, vol. 2, pp. 6–9. [Google Scholar]
7. H. Hou. (2017). “The application of blockchain technology in E-government in China,” in IEEE, 26th Int. Conf. on Computer Communication and Networks. Vancouver, BC, Canada, 1–4. [Google Scholar]
8. S. Y. Lim, P. T. Fotsing, A. Almasri, O. Musa, M. L. M. Kiah et al. (2018). , “Blockchain technology the identity management and authentication service disruptor: a survey,” Int. Journal on Advanced Science, Engineering and Information Technology, vol. 8, no. 4–2, pp. 1735–1745. [Google Scholar]
9. W. Wang, N. Hu and X. Liu. (2018). “BlockCAM: A blockchain-based cross-domain authentication model,” in IEEE Third Int. Conf. on Data Science in Cyberspace (DSC). Guangzhou, China, 896–901. [Google Scholar]
10. B. Liu, Z. Chen, Y. Zhang, L. Xiong, X. Yang et al. (2019). , “A new group-to-group authentication scheme based on PUGs and blockchain,” in IEEE 4th Int. Conf. on Signal and Image Processing. Wuxi, China, 279–283. [Google Scholar]
11. M. Thakur. (2017). “Authentication, authorization and accounting with Ethereum blockchain,” 61, University of Helsinki, Finland. [Google Scholar]
12. L. Xiong, F. Li S. Zeng, T. Peng and Z. Liu. (2019). “A blockchain-based privacy-awareness authentication scheme with efficient revocation for multi-server architectures,” IEEE Access, vol. 7, pp. 125840–125853. [Google Scholar]
13. D. Puthal, S. P. Mohanty, P. Nanda, E. Kougianos and G. Das. (2019). “Proof-of-authentication for scalable blockchain in resource-constrained distributed systems,” in IEEE Int. Conf. on Consumer Electronics (ICCE). Las Vegas, NV, USA, 1–5. [Google Scholar]
14. G. Zyskind and O. Nathan. (2015). “Decentralizing privacy: Using blockchain to protect personal data,” in IEEE Security and Privacy Workshops, pp. 180–184. [Google Scholar]
15. D. Drescher. (2017). “using the blockchain, Blockchain basics: A non-technical introduction in 25 steps, Frankfurt am main, Germany, , [online]. Available: http://www.softouch.on.ca/kb/data/Blockchain%20Basics.pdf [Google Scholar]
16. F. Chen, H. He and Y. Huo. (2017). “Self-embedding watermarking scheme against JPEG compression with superior imperceptibility,” Multimedia Tools and Applications, vol. 76, no. 7, pp. 9681–9712. [Google Scholar]
17. Q. Su, Z. Yuan and D. Liu. (2019). “An approximate schur decomposition-based spatial domain color image watermarking method,” IEEE Access, vol. 7, pp. 4358–4370. [Google Scholar]
18. J. Fu, J. Mao, D. Xue and D. Chen. (2020). “A watermarking scheme based on rotating vector for image content authentication,” Soft Computing, vol. 24, no. 8, pp. 5755–5772. [Google Scholar]
19. M. Islam, A. Roy and R. H. Laskar. (2020). “SVM-based robust image watermarking technique in LWT domain using different sub-bands,” Neural Computing and Applications, vol. 32, no. 5, pp. 1379–1403. [Google Scholar]
20. USC university of Southern California. (2019). “The USC-SIPI Image Database,” . [Online]. Available at: http://sipi.usc.edu/database. [Google Scholar]
21. National library of medicine. (2020). “MedPix image database,” . [Online]. Available at: https://medpix.nlm.nih.gov/. [Google Scholar]
22. Grafana Labs. (2020). “Grafana,” [online]. Available at: https://grafana.com/. [Google Scholar]
23. D. Bhowmik and T. Feng. (2017). “The multimedia blockchain: a distributed and tamper-proof media transaction framework,” in IEEE 22nd Int. Conf. on Digital Signal Processing. London, UK, 1–5. [Google Scholar]
24. Z. Meng, T. Morizumi, S. Milyata and H. Kinoshita. (2018). “Design scheme of copyright management system based on digital watermarking and blockchain,” in IEEE 42nd Int. Conf. on Computer Software and Applications. Tokyo, Japan, 359–364. [Google Scholar]
25. S. M. Mousavi, A. Naghsh, A. A. Manaf and S. A. R. Abu-Bakar. (2017). “A robust medical image watermarking against salt and pepper noise for brain MRI images,” Multimedia Tools and Applications, vol. 76, no. 7, pp. 10313–10342. [Google Scholar]
26. S. A. Parah, J. A. Sheikh, F. Ahad, N. A. Loan and G. M. Bhat. (2017). “Information hiding in medical images: A robust medical image watermarking system for E-healthcare,” Multimedia Tools and Applications, vol. 76, no. 8, pp. 10599–10633. [Google Scholar]
27. A. Sharma, A. K. Singh and S. P. Ghrera. (2017). “Robust and secure multiple watermarking for medical images,” Wireless Personal Communications, vol. 92, no. 4, pp. 1611–1624. [Google Scholar]
28. A. Anand and A. K. Singh. (2020). “An improved DWT-SVD domain watermarking for medical information security,” Computer Communications, vol. 152, no. 3, pp. 72–80. [Google Scholar]
29. N. E. H. Goléa and K. E. Melkemi. (2019). “ROI-based fragile watermarking for medical image tamper detection,” Int. Journal of High-Performance Computing and Networking, vol. 13, no. 2, pp. 199–210. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |