DOI:10.32604/iasc.2021.015129

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.015129 |  |
| Article |
ECG Encryption Enhancement Technique with Multiple Layers of AES and DNA Computing
1BIOCORE Research Group, Faculty of Information & Communication Technology, Universiti Teknikal Malaysia Melaka, Melaka, 76100, Malaysia
2Computer Science Department, College of Computer Science and Information Technology, University of Wasit, Wasit, Iraq
*Corresponding Author: Jamal Kh-Madhloom. Email: jamalkh@uowasit.edu.iq
Received: 07 November 2020; Accepted: 23 January 2021
Abstract: Over the decades, protecting the privacy of a health cloud using the design of a fog computing network is a very important field and will be more important in the near future. Current Internet of Things (IoT) research includes security and privacy due to their extreme importance in any growing technology that involves the implementation of cryptographic Internet communications (ICs) for protected IC applications such as fog computing and cloud computing devices. In addition, the implementation of public-key cryptography for IoT-based DNA sequence testing devices requires considerable expertise. Any key can be broken by using a brute-force attack with ample computing power. Therefore, establishing a model of DNA cryptography is extremely necessary to improve the interaction between current and new technologies. In addition, the implementation of public-key cryptography for IoT-based DNA sequence testing devices requires considerable expertise. The proposed algorithm can create a stable hybrid encryption algorithm based on DNA layers and advanced encryption standard (AES) to shorten encryption time and increase protection capacity to suit the IoT health cloud systems. The proposed model can protect the DNA sequence over the fog computing cloud against plain text attacks by generating (I) main key, which is the key to the EAES encryption algorithm; (II) Rule 1 key, which represents the DNA base number of possible key probabilities; and (III) Rule 2 key, which represents the number of binding probabilities of the DNA helical structure. This key is built to achieve higher levels of protection. An ECG encryption enhancement technique with multilayer AES and DNA computing (MLAESDNA) is proposed in this study. Results show that MLAESDNA can secure IoT signals via cloud computing.
Keywords: ECG encryption; IoT; AES; DNA computing; MLAESDNA
Cryptography is the science of securing the content of messages and communications. Cryptanalysis, the other subdiscipline, seeks to compromise or defeat the security achieved by cryptography. Mathematics is the foundation of cryptography and cryptanalysis. Cryptography is commonly associated with encryption, the transformation of data and information into a form that is unusable by a person who is not authorized to access that information. Historically, cryptography was used to protect the confidentiality of sensitive messages for military and diplomatic communications. Based on this traditional definition, cryptography can be seen as the science of encryption and decryption of messages, whose primary concern is to protect a message if it is disclosed to someone other than the intended recipient. With the expansion of information economy where transmission of sensitive information across untrusted media has become prevalent, the use of cryptography has become common practice not only with organizations but also with individuals; the scope of data transmission has exceeded the range of information sharing and entertainment to the core of industrial, scientific, and medical domains [1].
Recent implementations of cryptography considered cryptography as much more than the acts of encryption and decryption. While encryption and decryption techniques are used to secure sensitive information where confidentiality is important, other aspects of information security are implemented through encryption. These aspects include authentication of the message, sender, and recipient; the integrity of the message; and the nonrepudiation of the message transfer [2]. The term cryptography as used today refers collectively to techniques and applications used in protecting stored and transmitted information.
The Internet of Things (IoT) has enhanced the collection and sharing of data, and has made it more accessible to software applications and their users based on cloud computing and fog computing [3]. An IoT ecosystem consists of interconnected physical devices that support collection and exchange of data [4]. The concept of IoT has improved the connection between computer systems and the physical world. IoT provides numerous opportunities in different fields [5] including health care and telemedicine systems, which is one of the many industries that benefit from various IoT-based computer applications. It offers better health care to patients with improved treatment of various diseases [6]. Researchers in the field have been attempting to build better, secure IoT healthcare applications to expand healthcare services and provide remote care facilities for patients with chronic illnesses [5]. These applications use various sensory devices to collect patient data as ECG signals and administer treatment. The components of a typical IoT system are sensor devices, cloud-based interfaces, machine algorithms, and wireless sensor network (WSN). Sensor devices are used to collect data for the human body such as ECG signals, whereas WSN provides communication facilities [7]. Collected data are processed by the algorithms to perform the necessary analysis [8]. Moreover, cloud services offer storage facilities for collected data and allow access to users [9], whether patients or healthcare professionals. Secured [10] and protected IoT healthcare applications are required to improve the well-being of patients considering the security and privacy threats they pose to patients’ lives and other implications such as privacy violations and financial risks. This study discusses the privacy and security issues in IoT healthcare applications by analyzing the components of application architecture.
Fog computing was developed to bridge the gap between IoT devices and data centers. The main purpose of fog computing is to speed up computing processing [3]. Cloud computing is not feasible for many IoT applications; therefore, fog computing is a perfect alternative. Fog computing is suitable for many IoT services because it has many extensive benefits such as reduced latency, decreased bandwidth, and enhanced security [5]. However, the characteristics of fog raise new security and privacy issues [6]. The existing security and privacy measures of cloud computing cannot be directly applied to fog [8]. Security implications of using fog computing for IoT systems are many features (the most important ones are confidentiality, integrity, and availability [CIA]) that we considered in the case of a. However, the characteristics of fog raise new security and privacy issues [3]. The existing security and privacy measures of cloud computing cannot be directly applied to fog computing [5,6,7]. Security implications of using fog computing for IoT systems are many features (the most important ones are CIA) that we considered in the case of a failure in defending the fog computing gateway [8,9,10].
The study aims to build a multilayer reliable system of DNA sequence incorporating DNA computing and the AES algorithm that can be implemented and integrated into the biological environment on DNA computers. This technique can secure the DNA sequence over cloud-based fog computing platforms against plain-text attacks via generation of main key and rule keys. The study introduces several contributions as (i) a multilayer encryption algorithm that incorporates DNA and the AES algorithm, (ii) a reliable encryption technique for IoT-based medical healthcare systems, (iii) an encryption technique with decrement of ECG message length and hence, decrement of complex mathematical operations, and (iv) an encryption technique that improves encryption power and provides higher security and more complexity to multilayer AES and DNA (MLAESDNA).
The remainder of this study is structured as follows. Section 2 displays the current related work. Section 3 offers the indepth process of the suggested model. Section 4 provides the experiment results and their discussion. Section 5 presents the conclusions.
The rapidly growing applications of telemedicine and healthcare recently imposed the need for securing the transmission of medical data and records over the Internet or any other medium. This need motivated researchers to focus on the enhancements and modifications of existing encryption algorithms as well as develop new algorithms, as illustrated in Section 2.5. DNA inspired security encryption algorithm development due to the advanced, reliable method of encryption it is based on. Thus, several attempts have been made to enhance the standard security and encryption algorithms inspired by the DNA method of encryption.
Table 1: AES enhancements attempts
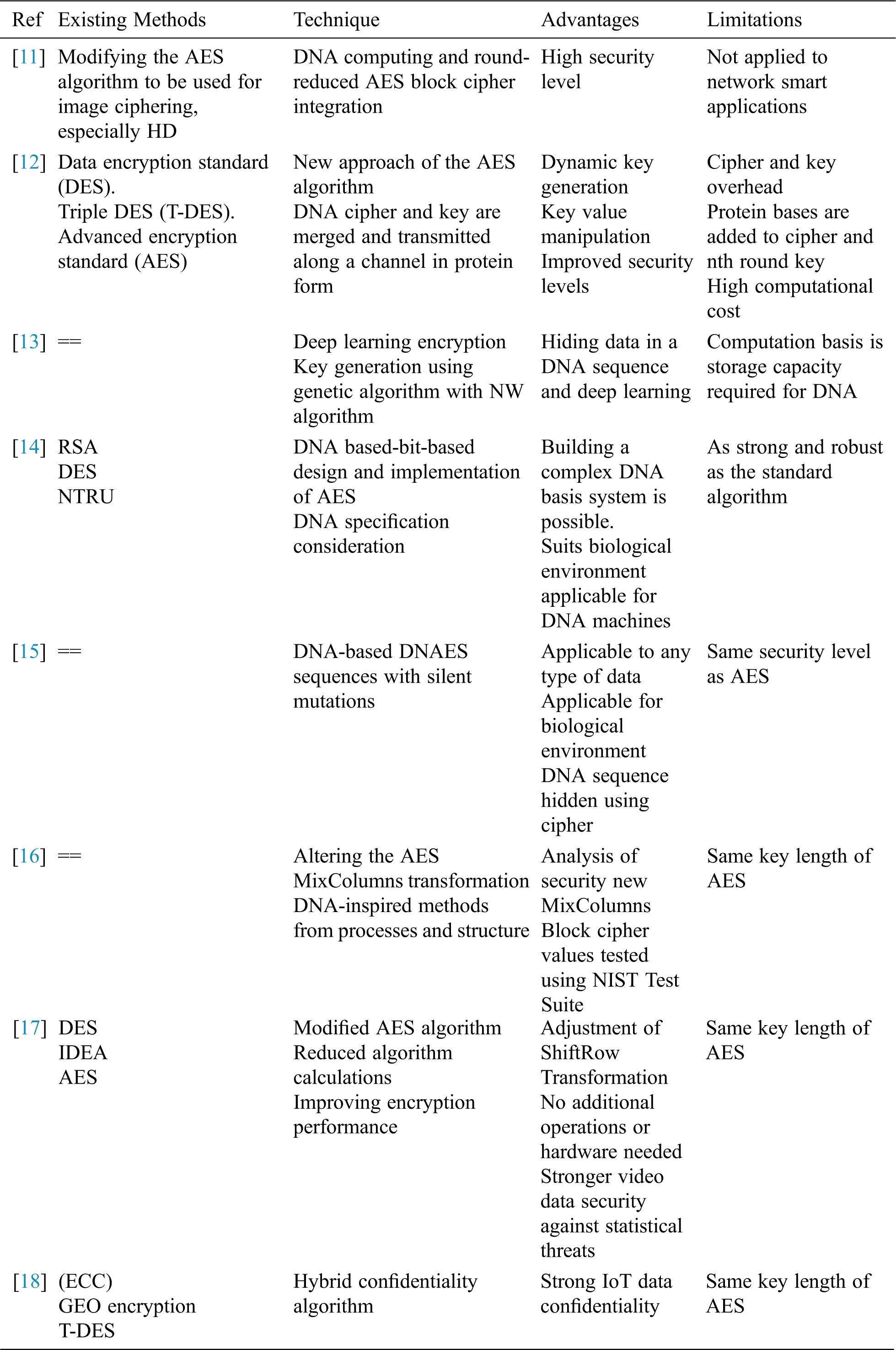
The current study focuses on comparing and analyzing the encryption enhancement trials in the steganography sector as reported in the literature published during the previous years. A general trend is to strengthen a new encryption algorithm and counter the great power of computing, especially the new generation of quantum computing device. Traditional cryptographic systems are built on strong mathematical and theoretical bases. Therefore, several researchers are interested in developing a new DNA-based AES encryption algorithm, as mentioned in Tab. 1. This algorithm will be helpful in all technologies that typically deal with an extensive number of connected devices and sensitive data stores, and exchange data between those devices. Thus, security and privacy are important factors in such applications and related applications. Moreover, the platforms must be able to achieve the data security requirements in every approach. During the study, we explore various AES enhancement studies using several approaches. Further, we examine 11 peer-reviewed articles and analyze the proportion of the enhancement of encryption algorithms for data transmission in different applications. Recently, many research articles related to AES have focused on using DNA to increase the power of encryption and have proposed algorithms to overcome the problems as high capacity, unpredictable, high-deterioration steganography techniques, where the data will not be visible to hackers even though the system is hacked. We focus on the AES algorithm and DNA addressed in recent studies. We explore different types of methods and find that the new trend is using DNA in enhancing the AES algorithm. We also study and analyze the traditional methods and their issues in encryption. We demonstrate substantial research areas including AES and DNA hybrid system usage.
The AES encryption algorithm is a common encryption algorithm developed by NIST to replace DES [19]. To encrypt and decrypt data packets, the procedure of AES algorithm first encrypts 10 iterations for 128-bit encryption keys at the first step, 12 encoding iterations for 192-bit encryption keys at the second step, and 14 encoding iterations to 256-bit encryption keys to produce the final encrypted message. Fig. 1 illustrates the flowchart of the AES [20]. These steps can be defined as follows:
a) SubBytes transformation: AES consists of a 128-bit block of data, which means every entity in the database consists of 16 bytes. Additional byte transformation requires that every entity of a data record is converted into another form of data using an eight-bit Rijndael S-box [21].
b) ShiftRows transformation: In this easy transposition, data in the remaining three lines of the state that are dependent on the row position are transformed in one cycle to another location. In the following line, a one-byte circular shift to the left is done. In rows 3 and 4, two- and three-byte circular transformations to the left are executed sequentially [22].
c) Mix Columns transformation: This transposition is similar to multiplying the states represented by columns with a matrix [23]. The values of the column vector are multiplied by a matrix with constant values as a polynomial rather than numbers.
d) AddRound Key transformation: The current state and the encryption key are XORed in this transformation. Hence, this transformation is the inverse of its own. The transformation is composed of several steps. The initial step, AddRound Key operation, is performed followed by the processing of data block that consists of SubBytes, ShiftRows via round function, Mix Columns, and AddRound Key transformation [14]. This procedure is performed iteratively based on the length of the key. The same sequence is followed for the decryption operation. The key schedules are made identical for encryption and decryption transformations by performing Inv-SubBytes, Inv-ShiftRows, Inv-Mix Columns, and AddRound Key [24].
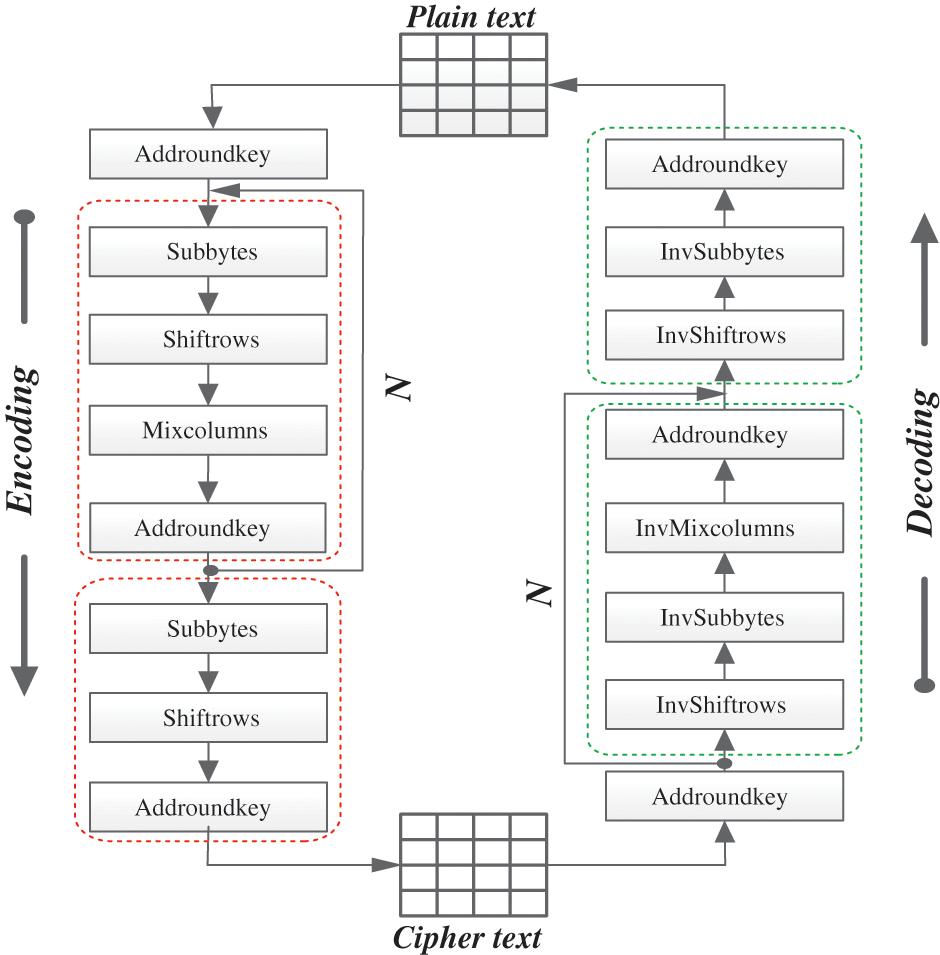
Figure 1: Flowchart of the AES algorithm [25]
In Singh [19], DNA computing and round-reduced AES block cipher are combined; in the existing method, images of dimensions use n × m = 256 × 256 pixels. However, it has not been applied to any smart network application. Moving picture experts’ group-based encryption algorithm for video AES is proposed with modification in ShiftRows transformation. Operation or hardware is not required in addition to the original AES [19]. High-definition image encryption algorithm based on AES algorithms was proposed in Albahar et al. [25]. The well-known AES with a more secure block cipher algorithm was introduced; the limitation of this technique is longer processing time, and the number of rounds is reduced by attacks on the encryption algorithm [26]. With the same objective, a hybrid RSA- and AES-based encryption algorithm for securing user’s data was introduced in the cloud [27]. The power of using RSA and AES encryption algorithm provides three encryption keys, namely, (i) public key for encryption, (ii) private key, and (iii) secret key for decryption.
In the existing research, an AES algorithm for data security is designed to provide more security using a Polybius square matrix, thus increasing the number of rounds. Another work generated the key using chaotic maps where encryption is accomplished using AES [26]. To improve encryption speed, authors synchronized the unit of key expansion where a RoundKey is generated in each clock cycle, and keys are stored and retrieved from the key RAM in the same clock cycle. Moreover, in Zhang et al. [27], authors introduced an encryption technique for digital images based on the AES encryption algorithm and concluded that their proposed technique can cope with the effect of encryption and decryption.
DNA computing refers to the concept of using biological neurons and molecules, rather than digital computers, to perform complex computations. This area of science was recently explored by an American scientist named Leonard Adelman. His contributions showed how biological molecules can be implemented and studied to solve complex mathematical computations. Initially, no relationship was observed between molecules and cryptography, but excessive research in this area established a new field of science that related the biological molecules and the science of encryption to enhance the features and capabilities of biological molecules for the science of cryptography [28,29]. DNA computer is a group of DNA strands that are collected together to solve a computational problem. Technology enables selecting proper strands and manipulating the solution, showing how huge, complex computational problems can be solved faster than the traditional computer that requires distinct processing and memory capabilities. DNA is utilized to solve such problems for the following reasons: [30].
a) It supports much denser information than traditional computers that require 1,000,000,000,000 cubic nanometers to store storage media, such as videotapes.
b) The DNA processes operations in parallel using trillions of strands because each operation on a test tube of DNA is carried out on all strands in the tube in parallel.
The linear operation of traditional computers implies that data can be manipulated in one block after another. For example, chemical reactions in biological environments occur in a parallel fashion, and every step composing these reactions influences numerous strands within the DNA sequence. Using the DNA computer for these calculations is much beneficial because it requires less energy and memory space than conventional computers [31,32]. The field of DNA computing involves not only biology scientists but also scientists from different disciplines such as computer sciences, physics, chemistry, and mathematics.
Current cryptographic algorithms have a mathematical basis. DNA-inspired algorithms are combinations of current and new cryptographic technology. This section describes in detail MLAESDNA based on data encryption that integrates AES and DNA computing. MLAESDNA aims to enhance security by increasing the key length size using the DNA layers around the AES algorithm, which leads to preventing the piracy of the illegal users.
MLAESDNA, as shown in Fig. 2, uses DNA computing techniques to increase encryption layer with the AES algorithm. The different transformations of the encryption are sequentially applied to the state. The transformation layers are ECG binarization, DNA conversion, AddRoundKey, SubBytes, ShiftRows, Mix Columns, and DNA swapping [22]. It represents a block diagram for the encryption/decryption using the multiple layers of DNA and AES algorithms of the proposed model. MLAESDNA aims to strengthen the AES algorithm and reach the highest level of security that depends on the key length in DNA and AES algorithms. In the AES algorithm, the same operations are performed many times on a fixed number of rounds. The number of rounds depends on the key size. The proposed algorithm uses a block cipher size of 128 bits and N of rounds.
DNA encryption is used to increase the key length, which adds more complexity to the AES such that it becomes immune in a manner that adapts the technological development. The key length of the proposed algorithm is (24 × 2128 × 3 × 10) bits and is calculated as follows:
• First Key:
The DNA key size is 24. This key introduces the DNA sequence where the probability of the key could be
• Second Key:
The standard AES main key size is 2128.
• Third Key:
The key size is 3 according to three different DNA bases which can be represented as one of the following:
• Fourth Key:
The standard AES round number 10.
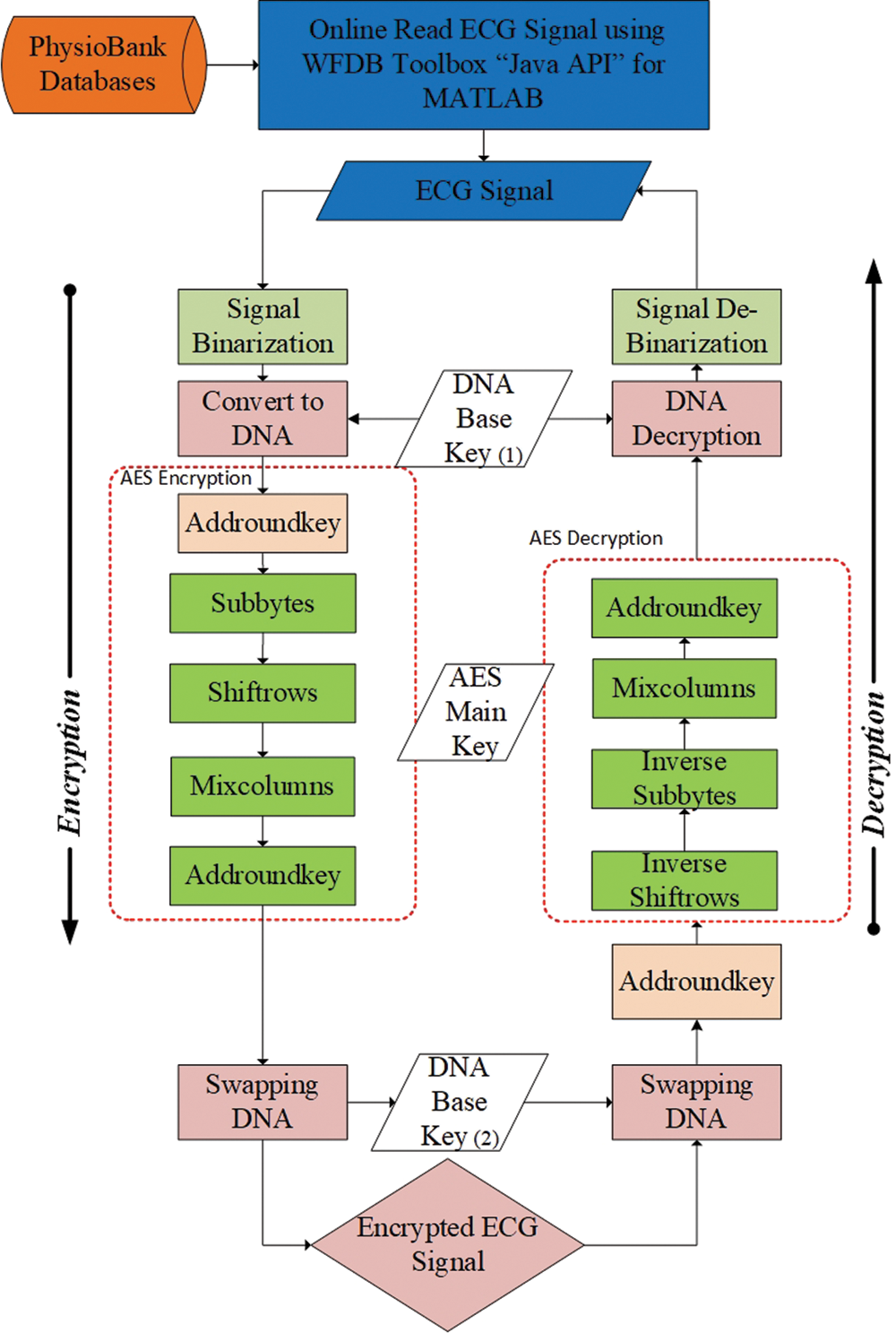
Figure 2: Flowchart of the MLAESDNA
The steps of the proposed method are explained in the following sections. The steps executed during the operation of the algorithm are outlined, and each following step is essential for the procedure of the algorithm and designed according to the algorithm design considerations to produce better algorithm performance metrics.
3.1 ECG Binarization “Preprocessing”
This step intends to convert ECG signals into binary bits using MATLAB functions to suit DNA conversion, as illustrated in Fig. 3.
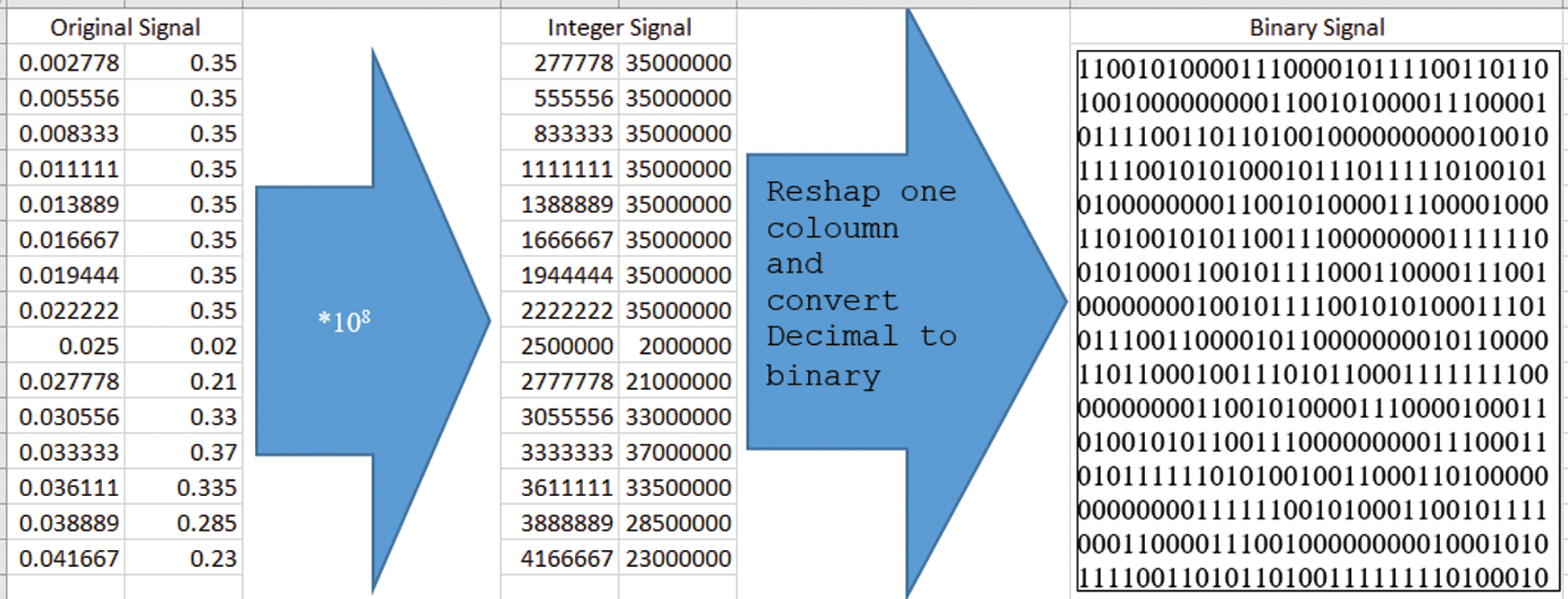
Figure 3: Flowchart of ECG preprocessing
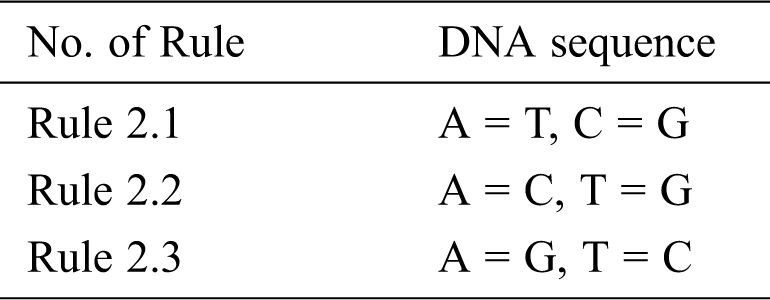
DNA encryption starts with transforming the binary message obtained from the previous step through the variable DNA bases into a DNA helix. Tab. 2 illustrates DNA Rule (1) “key size is 24.” Fig. 4 illustrates a sample of DNA helix conversion.
Table 2: DNA rule (1) with key size = 24
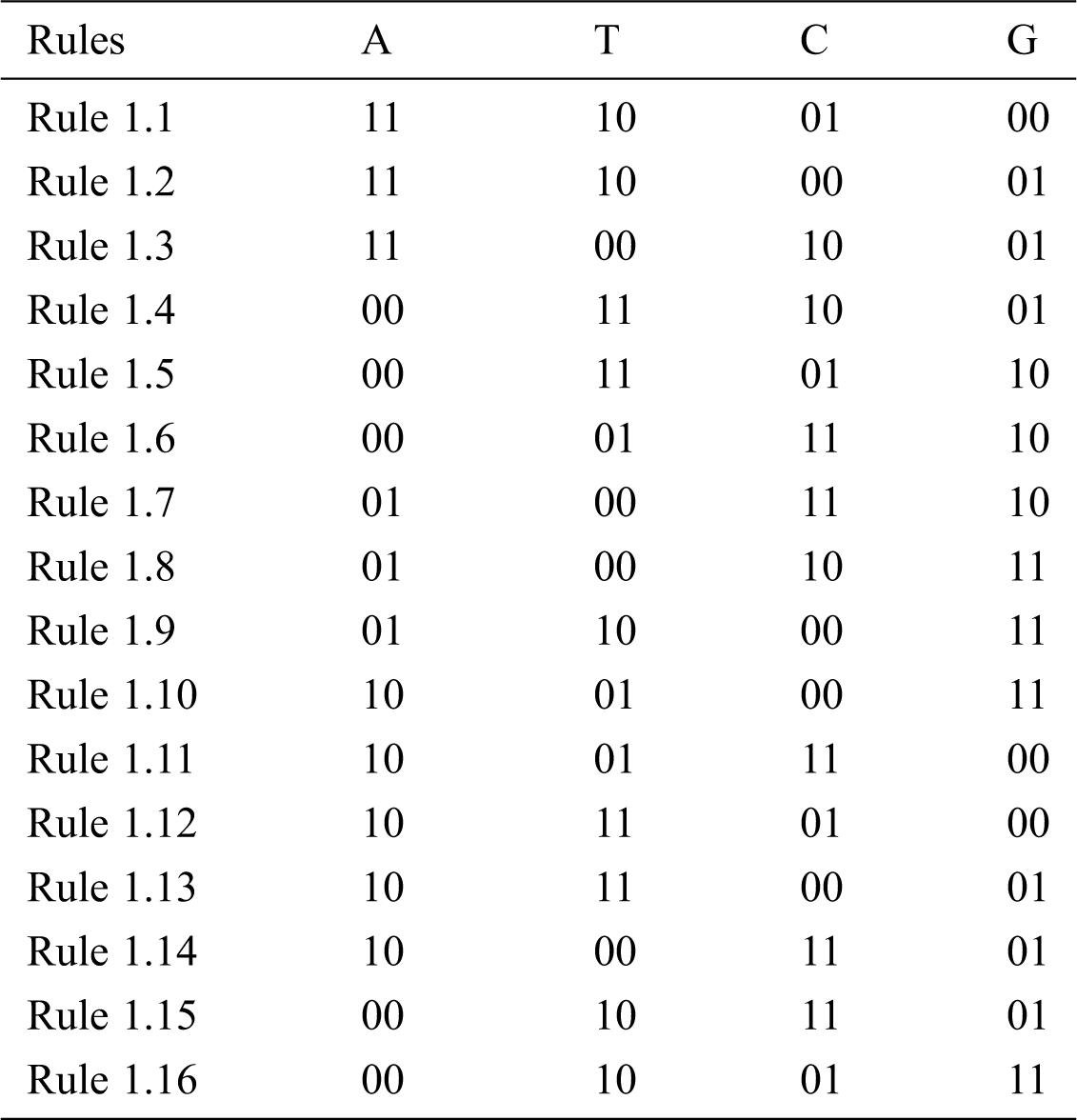
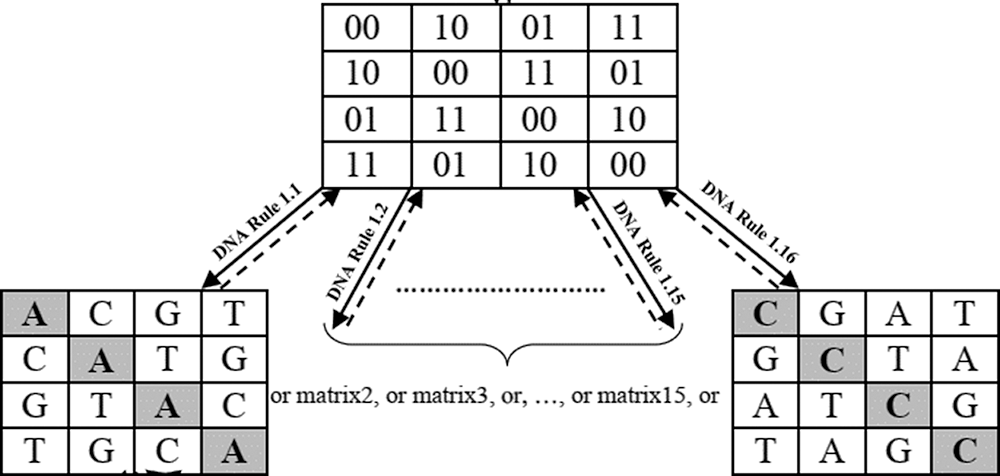
Figure 4: Sample of DNA Helix conversion
The SubBytes operation is a nonlinear byte substitution that operates on each byte of the state independently, as shown in Fig. 5. The substitution table (S-Box) is invertible and independent of any input, and precalculated forms are used. Each byte of the state is then substituted by the value in the S-Box whose index corresponds to the value in the state:
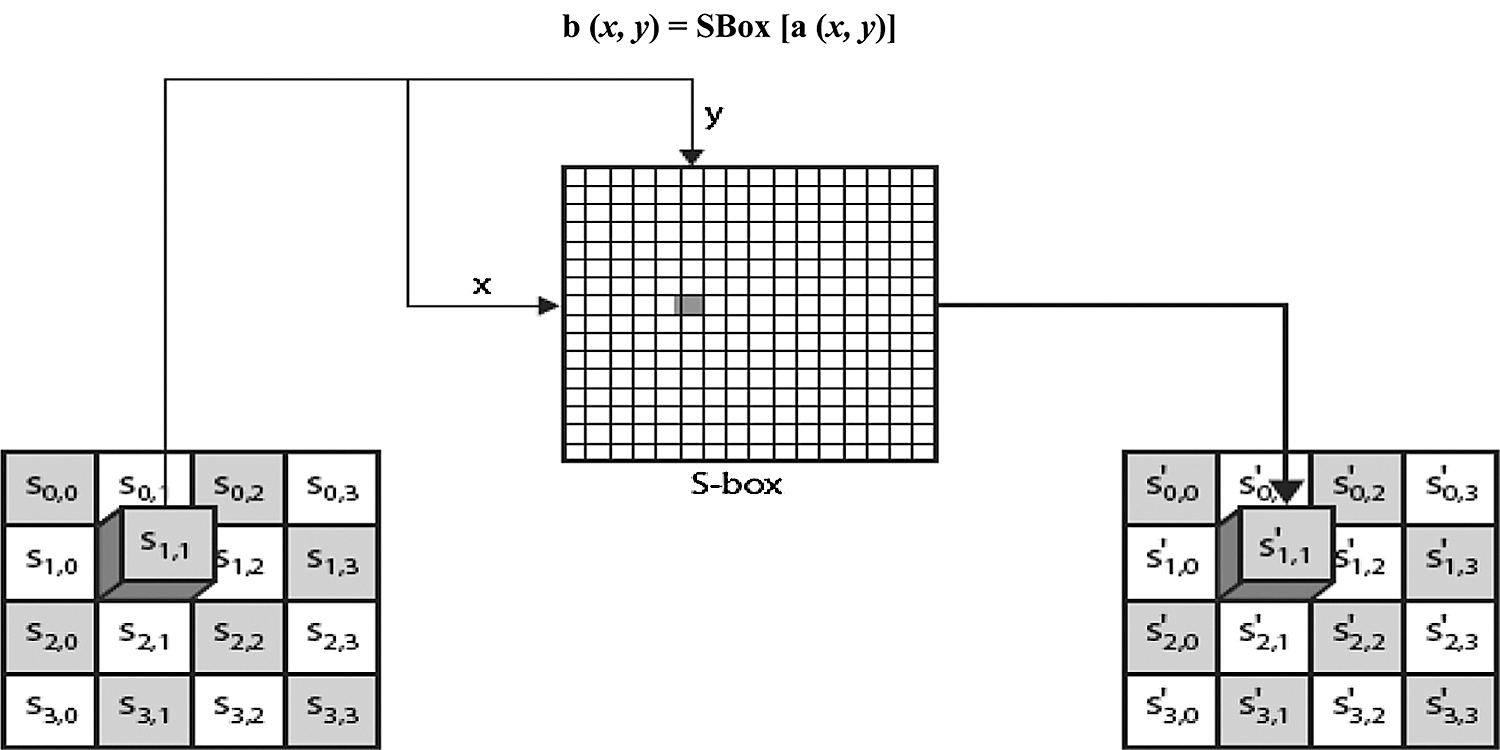
Figure 5: SubBytes operation representation
The inverse of SubBytes is the same operation using the inversed S-Box, which is also precalculated, and is a SubBytes step, as shown in Fig. 6.
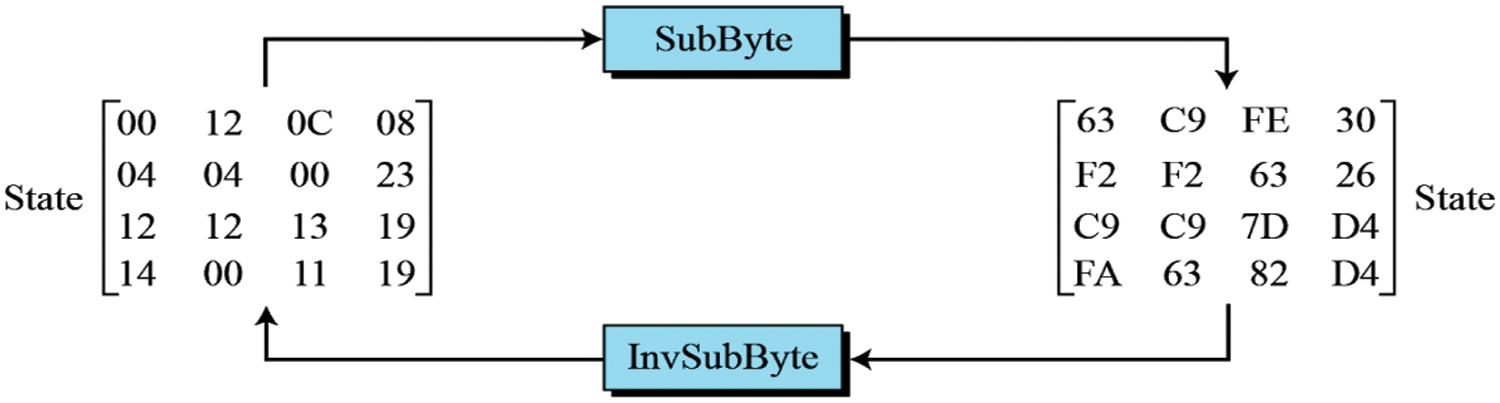
Figure 6: SubBytes and inverse of subbytes transformations
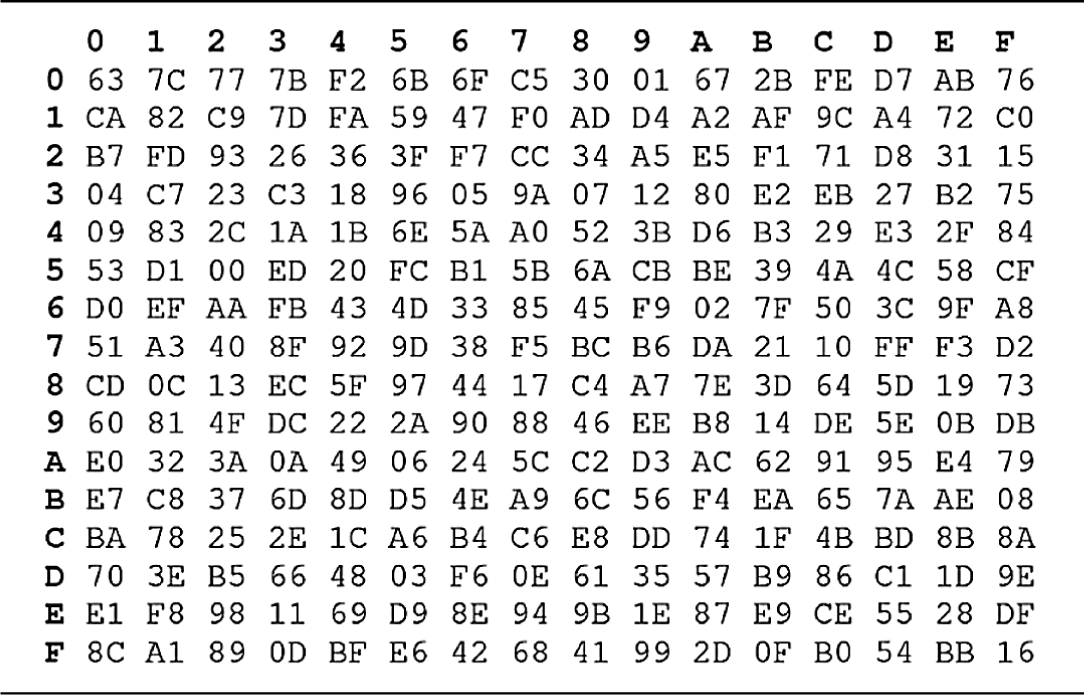
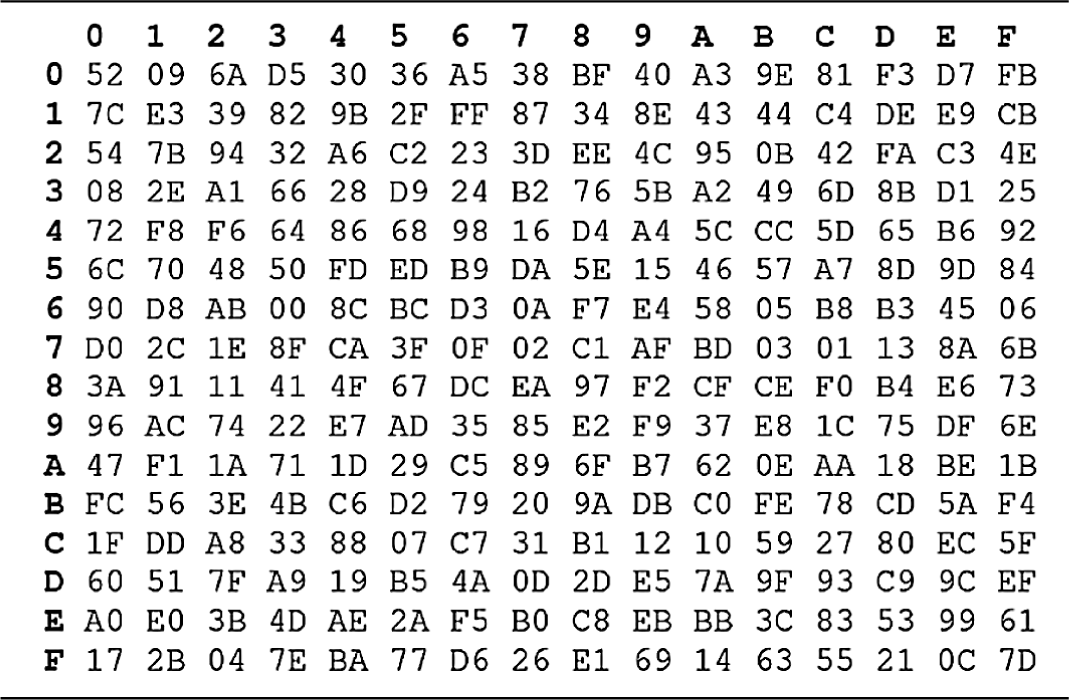
In the SubBytes step, each byte in the state is replaced with its entry in a fixed eight-bit lookup table, S; b (i, j) = S (i, j). Tabs. 3 and 4 illustrate S-Box and Inverse S-Box table, respectively. The SubBytes transformation and InvSubBytes transformation is the inverse of each other.
In this operation, each row of the state is cyclically shifted to the left, depending on the row index.
a) The 1st row is shifted 0 positions to the left.
b) The 2nd row is shifted 1 position to the left.
c) The 3rd row is shifted 2 positions to the left.
d) The 4th row is shifted 3 positions to the left.
The inverse of ShiftRows is the same cyclically shift but to the right. It is needed later for decoding. In the ShiftRows step, bytes in each row of the state are shifted cyclically to the left. The number of places each byte is shifted differs for each row. Figs. 7 and 8 show ShiftRows schema and example of ShiftRows and InvShiftRows, respectively.
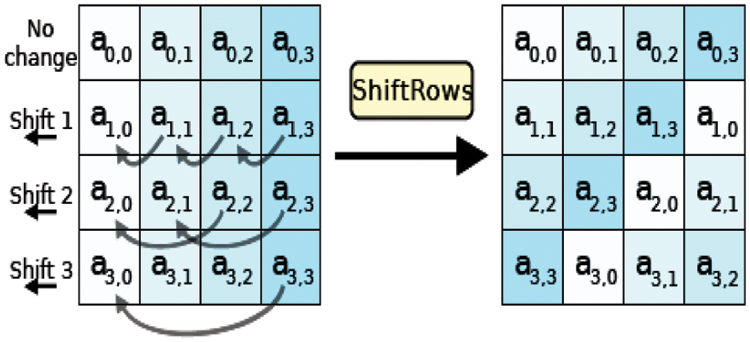
Figure 7: ShiftRows Schema
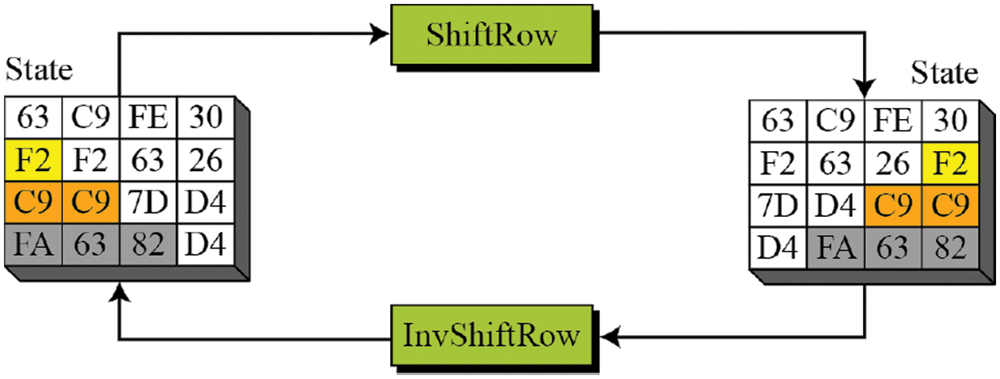
Figure 8: Inverse ShiftRows Schema
In the Mix Columns step, the four bytes of each column of the state are combined using an invertible linear transformation. The Mix Columns function takes four bytes as input and outputs four bytes, where each input byte affects all four output bytes. Together with ShiftRows, Mix Columns provides diffusion in the cipher. During this operation, each column is multiplied by the known matrix that for the 128-bit key is
The multiplication operation is defined as follows: Multiplication by 1 means no change, multiplication by 2 means shifting to the left, and multiplication by 3 means shifting to the left and then performing XOR with the initial unshifted value. After shifting, a conditional XOR with 0x1B should be performed if the shifted value is larger than 0xFF, as illustrated in Fig. 9. The Mix Columns step can also be viewed as a multiplication by a particular MDS matrix in a finite field. This process is described further in the article Rijndael mix columns.
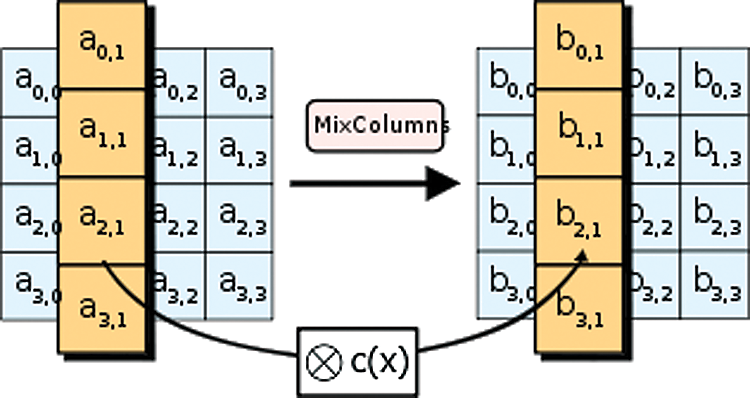
Figure 9: Mix Columns Operations
In this operation, a Round Key is applied to the state by a simple bitwise XOR. The Round Key is derived from the Cipher Key by the means of the key schedule. The Round Key length is equal to the block key length 128 bits. Fig. 10 illustrates the AddRoundKey operation, where the subkey is combined with the state. For each round, a subkey is derived from the main key using Rijndael’s key schedule, and each subkey is the same size as the state. The subkey is added by combining each byte of the state with the corresponding byte of the subkey using bitwise XOR. In the AddRoundKey step, each byte of the state is combined with a byte of the round subkey using the XOR operation.
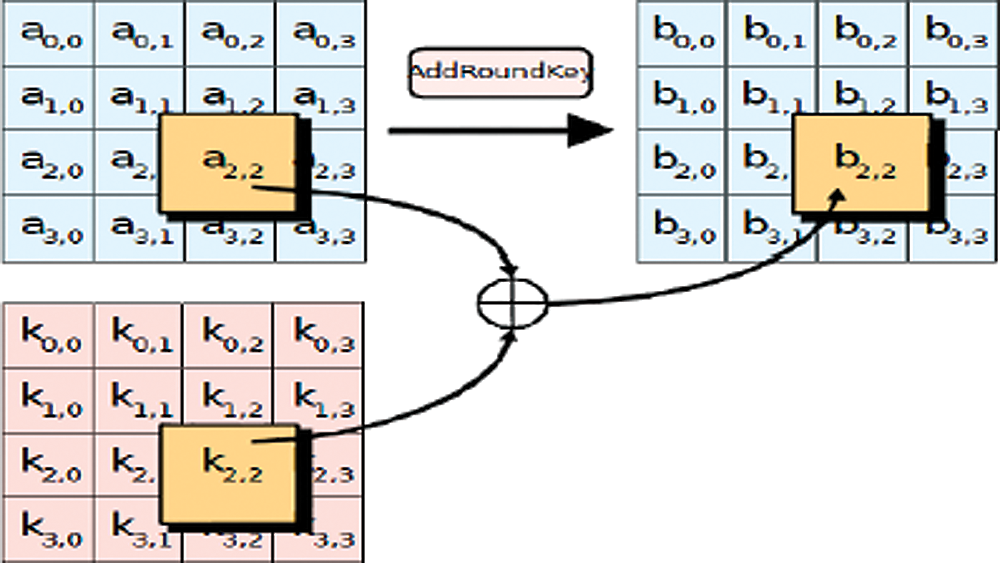
Figure 10: AddRoundKey operation
DNA swapping starts with turning the hexadecimal message obtained from the AddRoundKey step into a binary message. This message is transformed through the variable DNA bases into a DNA helix. Then, it is ciphered through the DNA bases to present a wholly different outcome that is returned into binary text. Once again, the message is transformed into a decimal message. Tab. 5 illustrates the sequence of DNA swapping operation for key size = 3.
4 Experimental Results and Security Analysis
The experimental analysis includes different security tests and results such as keyspace analysis, statistical analysis, numerical analysis, differential analysis, and encryption quality. These tests are the most considerable tests to demonstrate the satisfactory security of the proposed algorithm. The PhysioBank dataset, a large, growing archive of well-characterized digital recordings of physiologic signals and related data for use by the biomedical research community, is used in this study.
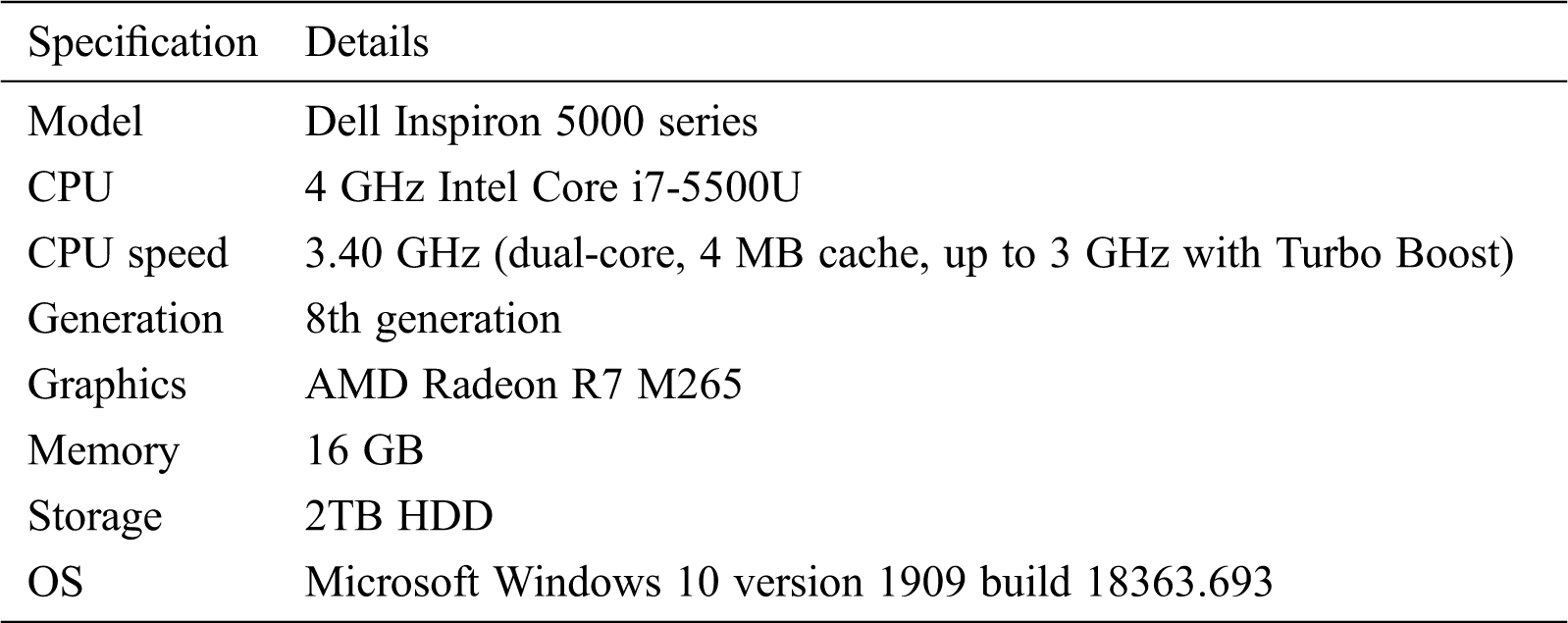
The proposed technique was simulated using a reliable simulation tool, namely, “MATLAB version (2017b).” Tab. 6 shows the specifications of simulation. The experiments were performed using Microsoft Windows platform deployed on a machine with the following specifications:
Table 6: Simulation machine specifications
4.2 Encryption and Decryption Time Analysis
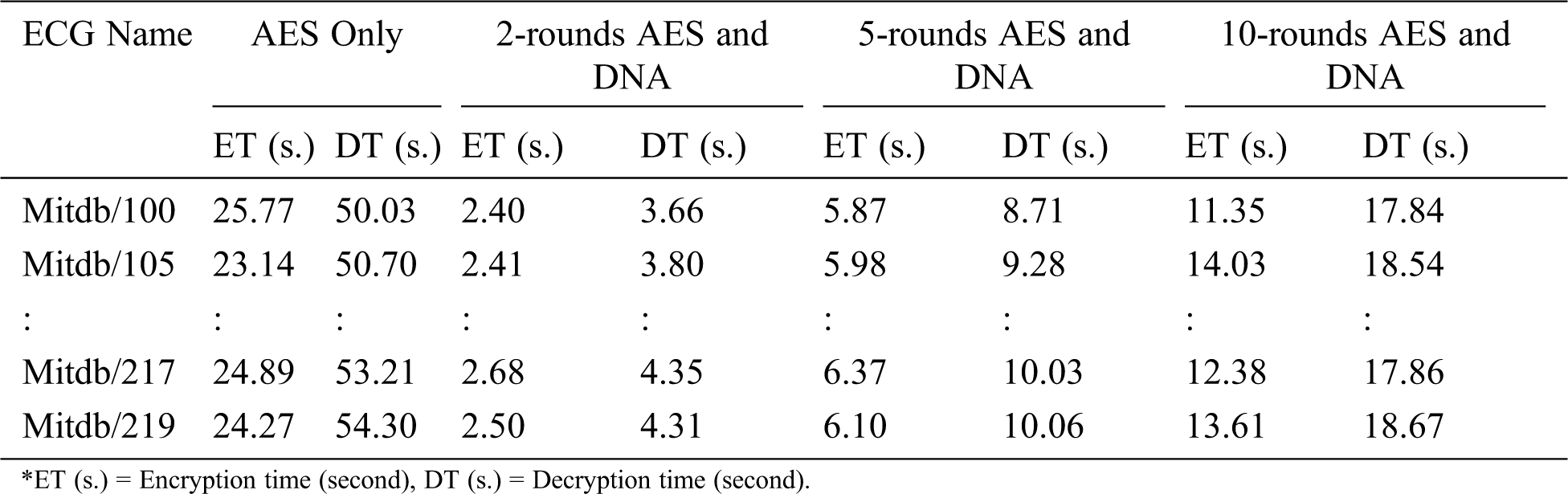
Encryption and decryption time can be used to calculate the encryption and decryption throughput of the algorithms. The performance parameters include the time taken by the algorithm for the encryption and decryption of input ECG signals. To avoid biased results, the experiment was run 10 times, and the average of the results was considered the average of the experiment. Tab. 7 shows the Encryption and decryption execution time.
Table 7: Encryption and decryption execution time with different rounds “signal length = 1000”
A complete investigation was conducted on the security of the proposed encryption technique. Several security analysis methods are used to test a cipher’s resistance to different types of attacks. Keyspace analysis is used to measure the resistance to brute-force attack. Histogram, correlation analysis of the adjacent values, and correlation analysis of the original and encrypted ECG signal are used to measure the resistance to statistical attack. Numerical analysis, for instance entropy, is a measurement of randomness. Mean square error (MSE) is used to evaluate the performance of implemented focus measures to the ECG signal quality.
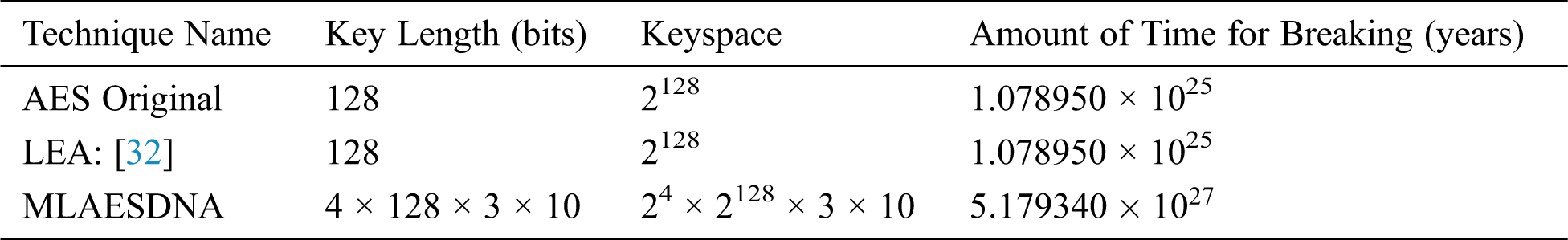
The proposed algorithm was compared with other works, and the results suggest that the proposed algorithm needs (5.179340 × 1027) years to be broken or hacked. Tab. 8 shows that the proposed algorithm is a better security against brute-force attacks and needs a long time for breaking compared with other works.
Table 8: Results of decryption breaking time
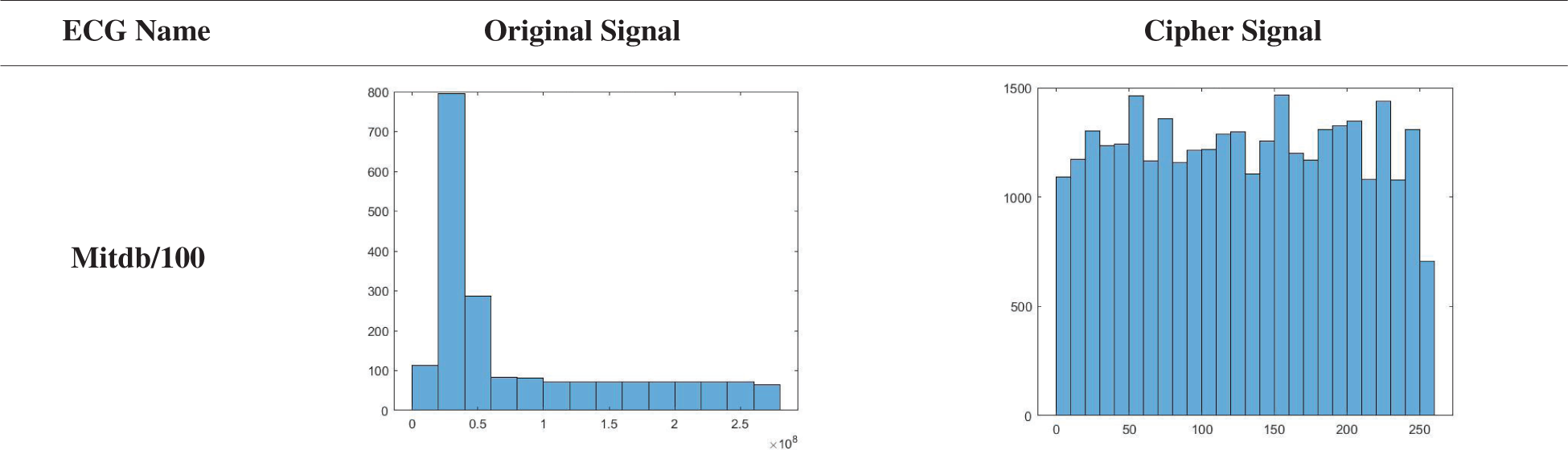
The proposed algorithm was applied to various ECG signals. Tab. 9 shows that the histograms of the cipher-ECG signal are very uniform and remarkably different from those of the plain ECG signal, which makes statistical analysis attacks on the encrypted ECG signal very difficult.
Table 9: Histograms of original and encrypted ECG signals used in simulations
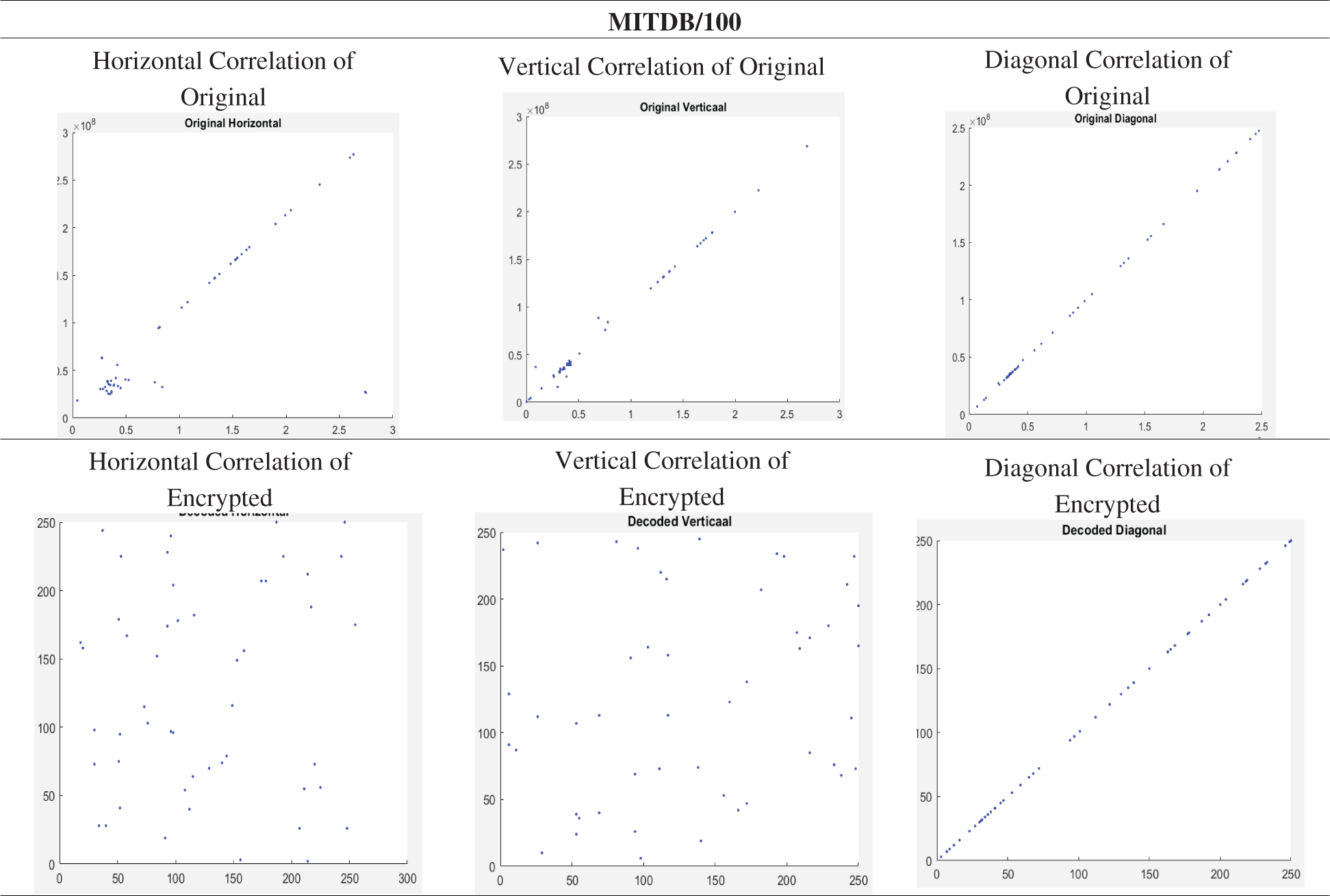
To test the effectiveness of the cryptosystem, the correlation between two contiguous values was examined in the plain ECG signal and the cipher ECG signal using the following procedure: First, 50 pairs (horizontal, vertical, and diagonal) of adjacent values from the original ECG signal and the encrypted ECG signal were randomly selected. Then, the correlation coefficient of each pair was calculated [33]. Tab. 10 shows the distribution of adjacent pixel pairs of the plain ECG signal and its cipher ECG signal in the horizontal, vertical, and diagonal directions. The pixel pairs of plain ECG signals are mostly located nearby the diagonal line in the graph.
Table 10: Horizontal, vertical, and diagonal correlations of original and encrypted ECG signals
4.7 Information Entropy Analysis
Entropy is one of the most important features that define the level of randomness and uncertainty in an ECG signal and is widely used to measure the uniform distribution of pixel gray-level in the ECG signal. The entropy is close to 8; therefore, the diffusion is good and produces a high disorder at output [34–36]. The entropy information of the encrypted ECG signals is shown in Tab. 11. The results demonstrate that the information entropies of the cipher ECG signals are close to the ideal value, which can verify that the cipher ECG signal of the proposed algorithm has good randomness.
Table 11: Results of information entropy of original and encrypted ECG signals “signal length = 1000”
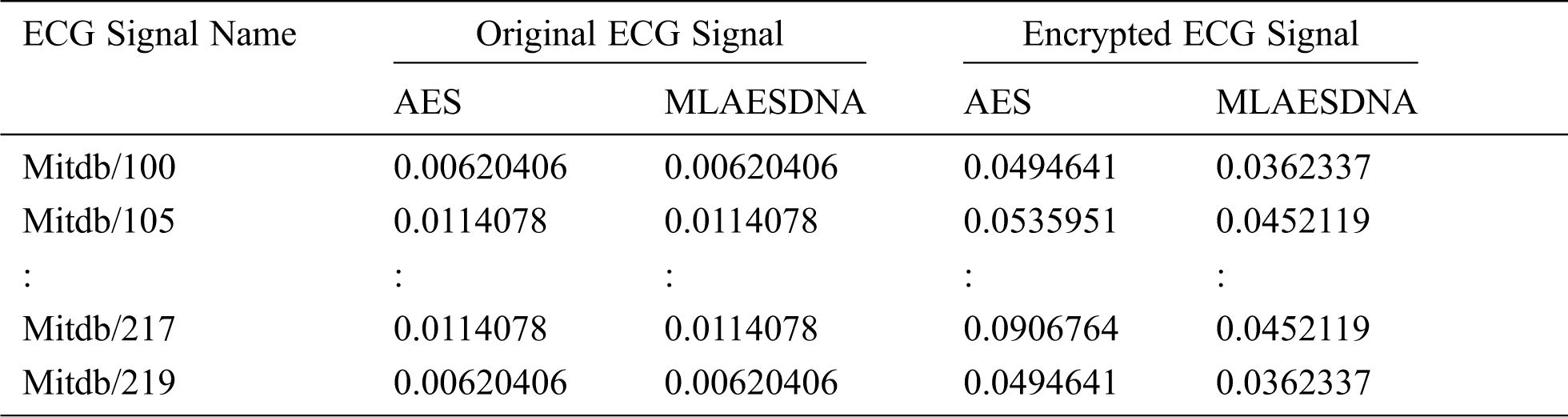
To measure the encryption strength of the proposed algorithm, several quantitative metrics such as MSE are utilized to estimate the variance between the encrypted ECG signal and the original ECG signal. Tab. 12 illustrates the MSE statistical metric result, which is used to evaluate the proposed algorithm. MSE is a very simple, very common distortion measure. The value of MSE represents the difference between the original ECG signal and the decrypted ECG signal. The smaller the MSE is, the better the result.
Table 12: MSE of “Signal Length = 1000”
Security is the major issue of any encryption technique. A good encryption algorithm should encounter most kinds of recognized attacks. Keyspace analysis is used to measure the resistance to brute-force attack. In the proposed algorithm, the keyspace is equal to (24 × 2128 × 3 × 10). This value exceeds the effective key size necessary to ensure computational security against future brute-force attacks. The histograms of the ciphered ECG signals are clearly steady and considerably different from those of the original ECG signals, which means performing statistical cryptanalysis on the ciphered ECG signal is very difficult. The correlation coefficient values indicate that the value distribution of the cipher ECG signals show a wide distortion of the correlation among values. Thus, the value information cannot be obtained from the adjacent values. Moreover, the information entropies of the cipher ECG signals are close to the ideal value, which can verify that the cipher ECG signal of the proposed algorithm has a good randomness. Therefore, the proposed algorithm is strongly resistant to differential attacks. These results are achieved due to the strong process of confusion and diffusion of the proposed algorithm. MSE is used to evaluate the performance of implemented focus measures. Remarkably better results are achieved with the proposed algorithm. The conducted experiments and results of various statistical measures demonstrate the resistance of the proposed algorithm to classical types of attack.
The results of histogram analysis, the correlation among adjacent values, the entropy results, and the MSE results demonstrate that MLAESDNA is resistant to statistical attacks. These results are related to the high sensitivity of the three different keys and the high randomization of DNA computing. Furthermore, this study could make a breakthrough into the era of cryptographic algorithm design and implementation in medical fog-computing-based healthcare applications. The implementation of the proposed technique in other domains may be altered by variable platform architectures. The study is also limited to securing medical messages other than ECG signals whose transmission requirements and metrics may vary. The proposed technique also encountered the generation and processing of four keys offered by DNA rules. These combinations may result in encryption and processing time that may be a critical issue in public health safety and emergency IoT-based applications.
This study presents MLAESDNA, a multilayer encryption algorithm incorporating DNA computing and AES algorithm. Increasing the key length has many advantages in IoT, especially in medical health systems, because it decreases the ECG message length and the complex mathematical operations that use more resources and take a longer time to process. MLAESDNA uses four keys offered by DNA rules, which improves encryption power and provides higher security and more complexity. The required decryption breaking time is remarkably increased more than 48 times of the breaking time using the original algorithm. Combining the concept of AES and DNA computing successfully enhances the encryption/decryption processes. The results show that MLAESDNA is better than the original AES algorithm and other algorithms. The results of the experiments conclude that MLAESDNA provides a high level of security, integrity, efficiency, and robustness. MLAESDNA fulfils the requirements needed to transfer the ECG signals over insecure healthcare system channels. In general, the area of joint encryption is a rich area for research. In the future work, the speed of the encryption and decryption execution time will be enhanced by integrating the quantum computing concept with MLAESDNA, applying parallel processing for MLAESDNA, and applying MLAESDNA on all medical signals in industry.
Acknowledgement: The authors thank the BIOCORE Research Group, Faculty of Information and Communication Technology, Universiti Teknikal Malaysia Melaka.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Nagaraj, G. S. V. P. Raju and V. Srinadth. (2015). “Data encryption and authetication using public key approach,” Procedia Computer Science, vol. 48, no. 2, pp. 126–132. [Google Scholar]
2. M. R. Ogiela and L. Ogiela. (2018). “Cognitive cryptography techniques for intelligent information management,” International Journal of Information Management (IJIM), vol. 40, no. 2, pp. 21–27. [Google Scholar]
3. A. A. Mutlag, M. K. Abd Ghani, N. Arunkumar, M. A. Mohammed and O. Mohd. (2019). “Enabling technologies for fog computing in healthcare IoT systems,” Future Generation Computer Systems, vol. 90, no. 3, pp. 62–78. [Google Scholar]
4. S. A. Mostafa, S. S. Gunasekaran, A. Mustapha, M. A. Mohammed and W. M. Abduallah. (2020). “Modelling an adjustable autonomous multi-agent internet of things system for elderly smart home,” Advances in Intelligent Systems and Computing, vol. 953, pp. 301–311. [Google Scholar]
5. A. M. Rahmani, T. N. Gia, B. Negash, A. Anzanpour, I. Azimi et al. (2018). , “Exploiting smart e-health gateways at the edge of healthcare internet-of-things: A fog computing approach,” Future Generation Computer Systems, vol. 78, no. 7, pp. 641–658. [Google Scholar]
6. A. A. Mutlag, M. K. Abd Ghani, M. A. Mohammed, M. S. Maashi and O. Mohd. (2020). “MAFC: Multi-agent fog computing model for healthcare critical tasks management,” Sensors, vol. 20, no. 7, pp. 1853. [Google Scholar]
7. I. Medvediev, O. Illiashenko, D. Uzun and A. Strielkina. (2018). “IoT solutions for health monitoring: Analysis and case study,” in IEEE 9th Int. Conf. on Dependable Systems, Services and Technologies (DESSERT). IEEE, pp. 163–168. [Google Scholar]
8. K. H. Abdulkareem, M. A. Mohammed, S. S. Gunasekaran, M. N. Al-Mhiqani, A. A. Mutlag et al. (2019). , “A review of fog computing and machine learning: Concepts, applications, challenges, and open issues,” IEEE Access, vol. 7, pp. 153123–153140. [Google Scholar]
9. A. Chacko and T. Hayajneh. (2018). “Security and privacy issues with IoT in healthcare,” EAI Endorsed Transactions on Pervasive Health and Technology, vol. 4, no. 14, pp. 155079. [Google Scholar]
10. M. K. A. Ghani, M. A. Mohammed, M. S. Ibrahim, S. A. Mostafa and D. A. Ibrahim. (2017). “Implementing an efficient expert system for services center management by fuzzy logic controller,” Journal of Theoretical and Applied Information Technology, vol. 95, no. 13, pp. 3127–3135. [Google Scholar]
11. E. Shehab, A. K. Farag and A. Keshk. (2014). “An image encryption technique based on DNA encoding and round-reduced AES block cipher,” International Journal of Computer Applications, vol. 107, no. 20, pp. 1–7. [Google Scholar]
12. B. M. Krishna, H. Khan, G. L. Madhumati, B. Lohitha, E. Bhavitha et al. (2017). , “FPGA implementation of DNA based AES algorithm for cryptography applications,” International Journal of Pure and Applied Mathematics, vol. 115, no. 7, pp. 525–530. [Google Scholar]
13. S. Kalsi, H. Kaur and V. Chang. (2018). “DNA cryptography and deep learning using genetic algorithm with NW algorithm for key generation,” Journal of Medical Systems, vol. 42, no. 1, pp. 1021. [Google Scholar]
14. M. Sabry, M. Hashem, T. Nazmy and M. E. Khalifa. (2015). “Design of DNA-based advanced encryption standard (AES),” in IEEE Seventh Int. Conf. on Intelligent Computing and Information Systems (ICICISIEEE, pp. 390–397. [Google Scholar]
15. H. M. Bahig and D. I. Nassr. (2019). “DNA-based AES with silent mutations,” Arabian Journal for Science and Engineering, vol. 44, no. 4, pp. 3389–3403. [Google Scholar]
16. A. H. Al-Wattar, R. Mahmod, Z. A. Zukarnain and N. Udzir. (2015). “A new DNA based approach of generating key dependent mix columns transformation,” International Journal of Computer Networks & Communications, vol. 7, no. 2, pp. 93–102. [Google Scholar]
17. P. Deshmukh and V. Kolhe. (2014). “Modified AES based algorithm for MPEG video encryption,” in International Conf. on Information Communication and Embedded Systems (ICICES2014). S.A. Engineering College, Chennai, pp. 1–5. [Google Scholar]
18. P. M. Chanal and M. S. Kakkasageri. (2019). “Hybrid algorithm for data confidentiality in internet of things,” in 10th Int. Conf. on Computing, Communication and Networking Technologies (ICCCNT). IEEE, pp. 1–5. [Google Scholar]
19. G. Singh. (2013). “A paper of encryption algorithms (RSA, DES, 3DES and AES) for information security,” International Journal of Computer Applications, vol. 67, no. 19. [Google Scholar]
20. N. Drucker, S. Gueron and V. Krasnov. (2019). “Making AES great again: The forthcoming vectorized AES instruction,” in 16th Int. Conf. on Information Technology–New Generations (ITNG 2019Cham: Springer, pp. 37–41. [Google Scholar]
21. M. M. Wong, M. L. D. Wong, C. Zhang and I. Hijazin. (2018). Circuit and system design for optimal lightweight AES encryption on FPGA. Singapore: Nanyang Technological University. [Google Scholar]
22. P. Dixit, A. K. Gupta, M. C. Trivedi and V. K. Yadav. (2018). “Traditional and hybrid encryption techniques: A survey,” in Networking Communication and Data Knowledge Engineering, pp. 239–248. [Google Scholar]
23. A. Ibrahim and G. Dalkiliç. (2017). “An advanced encryption standard powered mutual authentication protocol based on elliptic curve cryptography for RFID, proven on WISP,” Journal of Sensors, vol. 2017, pp. 1–10. [Google Scholar]
24. S. Panghal, S. Kumar and N. Kumar. (2016). “Enhanced security of data using image steganography and AES encryption technique,” International Journal of Computer Applications, vol. 42. [Google Scholar]
25. M. A. Albahar, O. Olawumi, K. Haataja and P. Toivanen. (2012). “Novel hybrid encryption algorithm based on AES, RSA, and twofish for bluetooth encryption,” Journal of Information Security, vol. 09, no. 02, pp. 168–176. [Google Scholar]
26. P. Kumar and S. B. Rana. (2016). “Development of modified AES algorithm for data security,” Optik (Stuttg), vol. 127, no. 4, pp. 2341–2345. [Google Scholar]
27. Q. Zhang and A. Qunding. (2016). “Digital image encryption based on advanced encryption standard (AES) algorithm,” in Proc.—5th Int. Conf. on Instrumentation and Measurement, Computer, Communication, and Control, IMCCC 2015, pp. 1218–1221. [Google Scholar]
28. M. A. Khan and K. Salah. (2018). “IoT security: review, blockchain solutions, and open challenges,” Future Generation Computer Systems, vol. 82, no. 15, pp. 395–411. [Google Scholar]
29. L. Cardelli. (2010). “Two-domain DNA strand displacement,” Electronic Proceedings in Theoretical Computer Science, vol. 26, pp. 47–61. [Google Scholar]
30. S. Namasudra and G. C. Deka. (2018). “Advances of DNA computing in cryptography,” in Advances of DNA computing in cryptography. [Google Scholar]
31. M. Elhoseny, G. Ramírez-González, O. M. Abu-Elnasr, S. A. Shawkat, N. Arunkumar et al. (2018). , “Secure medical data transmission model for IoT-based healthcare systems,” IEEE Access, vol. 6, pp. 20596–20608. [Google Scholar]
32. H. M.El Hennawy, A. E. Omar and S. M. Kholaif. (2014). “Design of LEA: Link encryption algorithm new proposed stream cipher algorithm,” in 31st National Radio Science Conference (NRSCIEEE, pp. 82–91. [Google Scholar]
33. J. Wu, X. Liao and B. Yang. (2018). “Image encryption using 2D Hénon-Sine map and DNA approach,” Signal Processing, vol. 153, no. 7, pp. 11–23. [Google Scholar]
34. X. J. Tong, M. Zhang, Z. Wang and J. Ma. (2016). “A joint color image encryption and compression scheme based on hyper-chaotic system,” Nonlinear Dynamics, vol. 84, no. 4, pp. 2333–2356. [Google Scholar]
35. T. Xiang, K. W. Wong and X. Liao. (2007). “Selective image encryption using a spatiotemporal chaotic system,” Chaos An Interdisciplinary Journal of Nonlinear Science, vol. 17, no. 2, pp. 023115. [Google Scholar]
36. R. Enayatifar, A. H. Abdullah, I. F. Isnin, A. Altameem and M. Lee. (2017). “Image encryption using a synchronous permutation-diffusion technique,” Optics and Lasers in Engineering, vol. 90, pp. 146–154. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |