DOI:10.32604/iasc.2021.014639

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.014639 |  |
| Article |
CMMI Compliant Workflow Models to Establish Configuration Management Integrity in Software SMEs
1Department of Computer Science, COMSATS University Islamabad, Wah Campus, Wah Cantt,Pakistan
2Department of Computer Science & IT, The Islamia University of Bahawalpur, Bahawalpur, Pakistan
3College of Computer Science and Information Technology, Al Baha University, Al Bahah, Saudi Arabia
4Department of Information and Communication Engineering, Yeungnam University, Gyeongsan, 38541, Korea
*Corresponding author: Muhammad Shafiq. Email: shafiq@ynu.ac.kr
Received: 05 October 2020; Accepted: 30 November 2020
Abstract: Capability Maturity Model Integration (CMMI) is a world-renowned framework for software process improvement, which specifies “What-To-Do” in terms of requirements. However, it leaves the “How-To-Do” part regarding implementation to implementers. The software industry especially software SMEs (SSMEs) faces difficulties in implementing the Specific Practices (SPs) of Various Process Areas (PAs). Configuration Management Process Area (CM-PA) is usually ignored despite its acknowledged importance in the software development process. Establishing integrity is one of the three Specific Goals (SGs) that CMMI ver. 1.3 requires for successful implementation of CM-PA. This goal is achieved through the implementation of two SPs (i.e., 3.1 and 3.2). In order to enable aforesaid SSMEs, pertinent research work regarding the implementation of PAs at CMMI Level-II was studied and Workflow Models (WFMs) were devised after sifting through all the relevant material. The models were assessed through Expert Panel Review (EPR) and further confirmed by conducting case studies. This work also contributes to the implementation of CM-PA. The results from EPR and case studies are promising since they not only testifies the clarity, learnability, usability, usefulness of the models but also proves its applicability to SSMEs. The proposed WFMs have a strong theoretical basis and practically proven. More industrial case studies are suggested to evaluate models for the upcoming versions of CMMI frameworks.
Keywords: Software configuration management; capability maturity model integration; software process improvement; software SMEs
The success or failure of an organization largely hinges on quality of products or services it provides. Everyone desires to have software product(s) that operate reliably without errors or being crashed. One way to enhance software quality is to improve software development processes. That’s why many SSMEs take interest in SPI. Improving the software process continually and appraising it regularly for effectiveness helps in meeting the customer’s expectations and is bound to pave a way towards a high-quality software.
There is no doubt that CMMI enables software development industry to take quality of software process to a next higher level. However, no significant number of SSMEs are opting for adoption. Like many other researcher, Gang Xu et al. [1] pointed out that CMMI offers software companies only guidelines, not the clear workflow models resulting in increased budget.
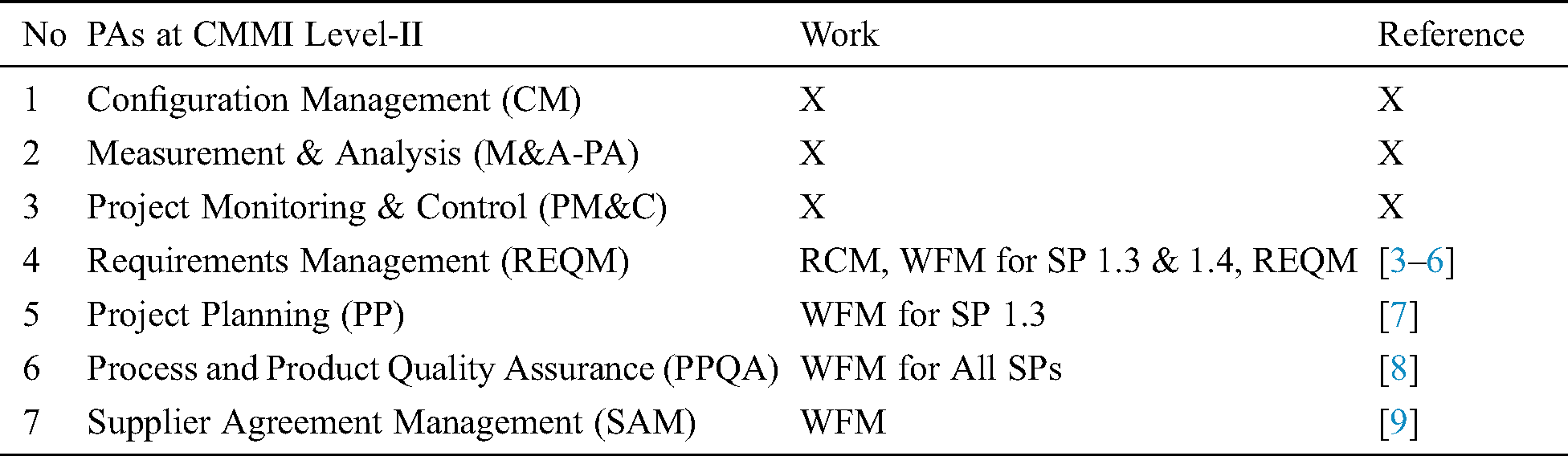
CMMI Level-II [2] consists of seven PAs including CM-PA. As elaborated in the next section, variety of research work has been carried out for implementation of PAs at CMMI Level-II, However, presently, no workflow model was found for SPs wise implementation of CM-PA particularly to help SSMEs as shown in Tab. 1. Therefore there is an intense need to devise the tailorable workflow models for SPs of CM-PA.
Table 1: Summary of workflow models devised earlier for various SPs of PAs at CMMI Level-II
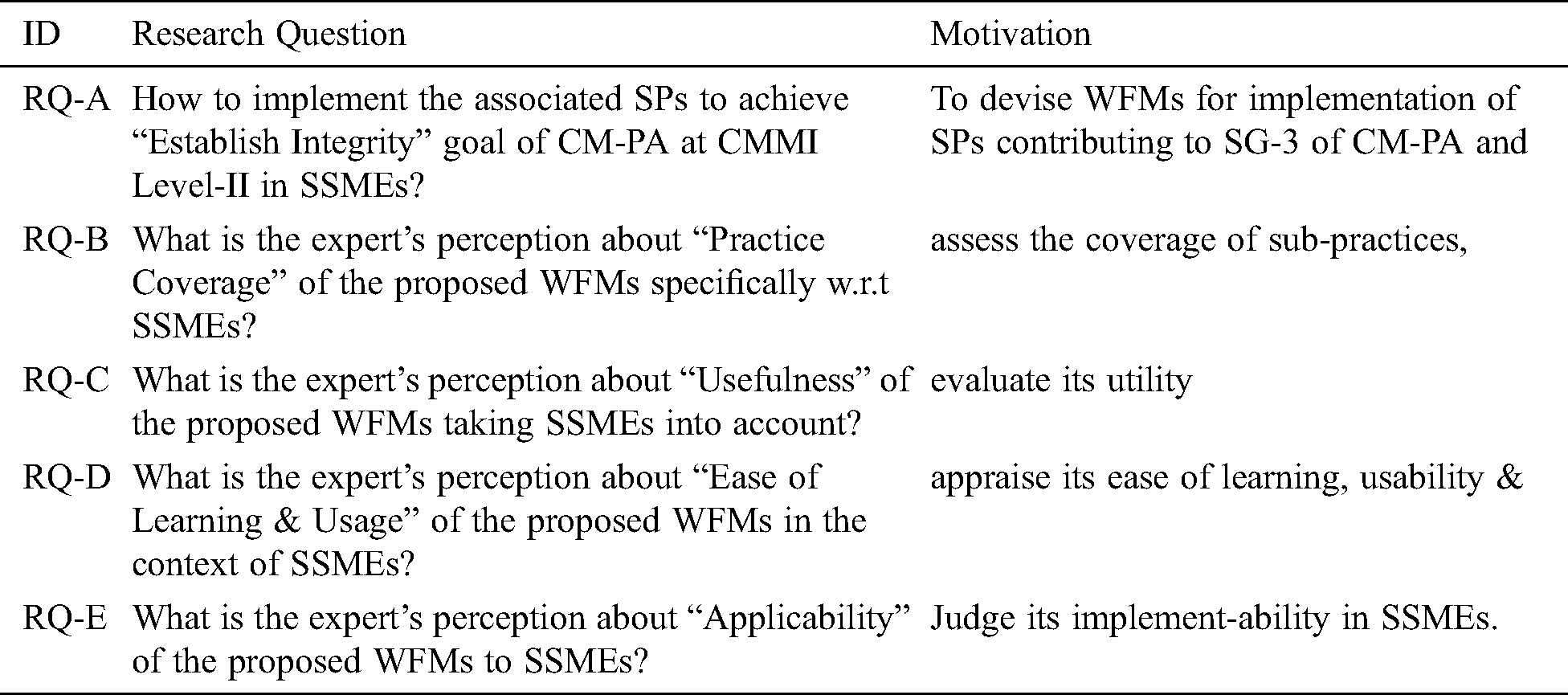
As per CMMI for Dev Ver. 1.3, CM-PA has three SGs and are achieved through implementation of seven SPs collectively. The focus of this study is to achieve the third goal (SG-3) of CM-PA by devising WFMs for implementation of two associated SPs (i.e., 3.1 and 3.2). As a vehicle to achieve the research objective, research questions are formulated as given in Tab. 2.
Organization of the paper is as follows. Sec 2 traverses through the earlier work and its limitations. Sec 3 throw light on methodology adopted and criteria for validation of the workflow model. Proposed models are elaborated in sec 4. Validation of models, threats to validity and their mitigation is given in sec 5, Sec 6 concludes the study and finally sec 7 highlights potential future work.
In order to help software development firms in implementing the best practices of REQM-PA, Niazi et al. [3] devised the CMMI compliant Requirements Change Management (RCM) Model. The model has five stages “Request”, “Validate”, “Implement”, “Verify” & “Update” and was evaluated through EPR process. Keshta [4] devised WFMs for SPs 1.3 & 1.4 of the REQM-PA having six stages “Initiate”, “Validate”, “Implement”, “Verify”, “Update” and “Release”. EPR was used to validate the models against the specified criteria. Applicability of models to small & medium sized software development organizations (SMSDOs) was evaluated in Saudi Arabian software industry. Tariq [5] has suggested to include an additional SP in REQM-PA for Software as a Services (SAAS) and carried out validation through a case study “Allwebid”. Batti [6] proposed a six-phased methodology to deal with changing requirements i.e., “Initiate”, ”Receipt”, ”Approve/Disapprove”, ”Evaluate”, ”Implement” and ”Configure” with CCB to act as central player and as a process owner. Keshta [7] also devised a WFM for implementation of SP 1.3 of PP-PA and defined phases for a project life cycle keeping in view the SMSDOs. The model comprises of four stages “Plan”, “Design”, “Review” and ”Update/Rework”. Keshta [8] further developed a WFMs for all SPs of PPQA-PA in perspective of SMSDOs. Both SP-1.1 & SP-1.2 of PPQA comprise of four stages i.e., “Plan”, “Prepare”, “Audit” & “Report”. The models were validated making use of EPR. Vivatanavorasin et al. [9] presented a three layered WFM for SAM-PA having “Contextual layer”, “Elaboration layer”, and “Definition layer”. As a proof of concept prototype, Supplier Agreement Management Tool was developed. In order to adopt CM process in DevOps environment, Erik Hochbergs and Laroy Nilsson Sjödahl [10] prepared guidelines after exploring literature and interviewing key professionals of software companies. Syahrul Fahmy et al. [11] highlighted the evolution of SCM since its beginning and appreciated that SCM techniques are also being applied to other areas.
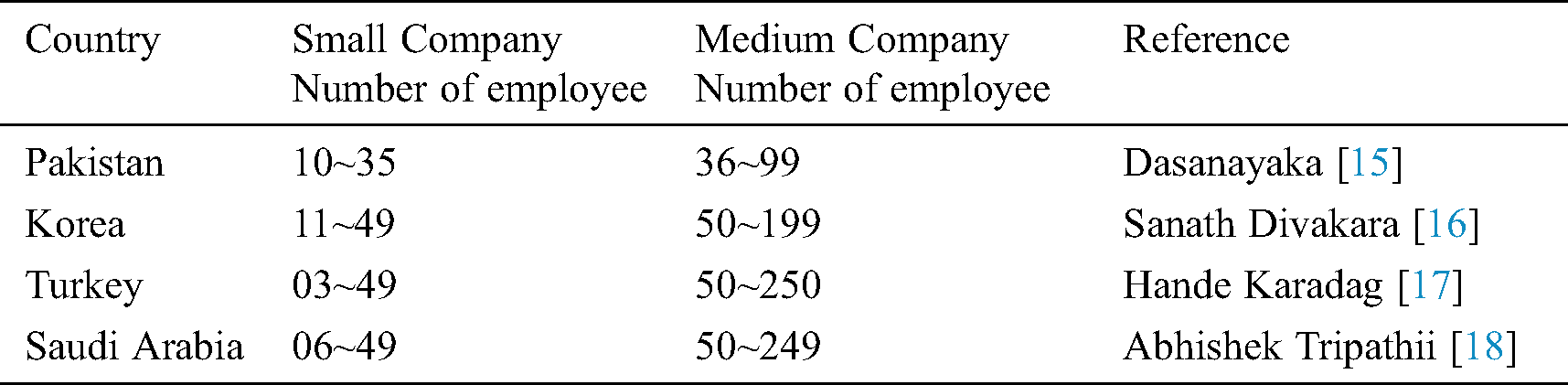
Resources are meagre in small software companies (SSCs) as compared to medium and large companies. Tuape and Ayalew [12] underscored that SPI frameworks are usually framed keeping big companies in view and thus software quality is usually compromised in SSCs. The authors identified three factors that tend to affect development process in SSC’s generally and African SSCs particularly. Victor José et al. [13] worked on how to implement the measurement process in line with the CMMI in companies whose primary business is maintenance instead of development. Tadele [14] devised a simple and easy to use framework amalgamating the CMMI ver 2.0 and DevOps to assist small companies. This framework is claimed to be comparatively cheaper & easily implementable and was validated through case study in few companies where substantial improvement was seen after implementation. Definition of SMEs varies w.r.t countries and time span. Few, collected from various studies, are given in Tab. 3.
Table 3: Categorization of SMEs
3 Methodology Adopted and Criteria for Validation of Workflow Model
Research methodology need to be devised very carefully as it has profound impact on the validity and reliability of study results. The research methodology used for this research has six major stages and is illustrated in Fig. 1.

Figure 1: Methodology adopted
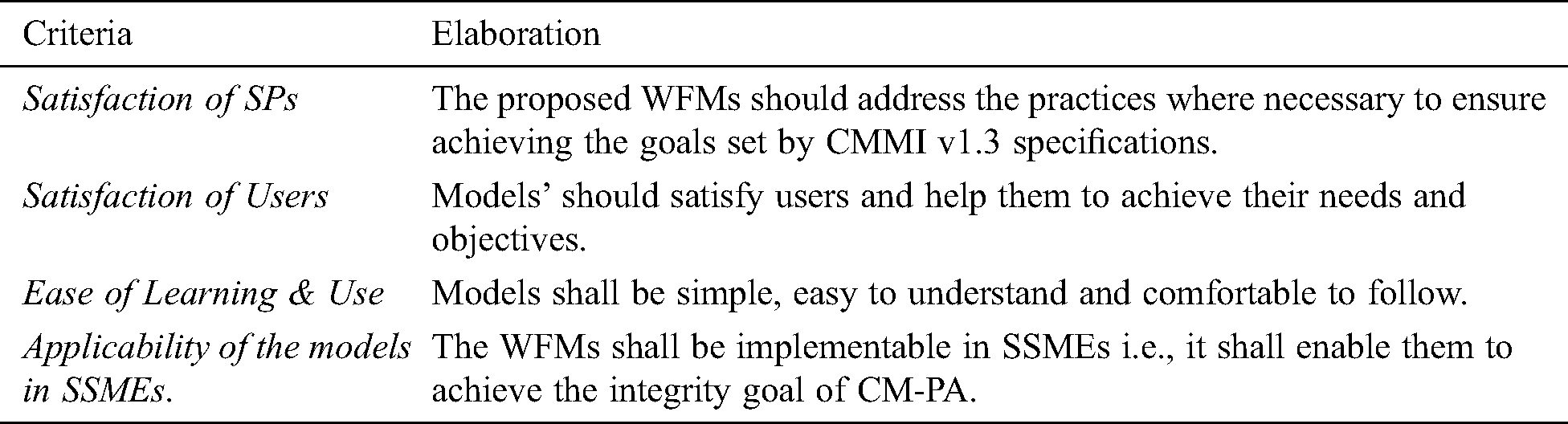
Success of a study largely depends on formulating of a sound evaluation criteria. Criteria for validation of the models in this study, because of the similar nature, has been derived from work of Niaz [3], Keshta [4,7,8] and Vivatanavorasin [9] respectively and is elaborated in Tab. 4.
4 Proposed Workflow Models for Establishing Integrity
As per CMMI Framework 1.3, the SG-1 “Establish Baselines” of CM-PA serve to establish baselines, the SG-2 “Track and Control Changes” assist in maintaining the baselines whereas the SG-3 “Establish Integrity” basically establish records and appraise the integrity of the baselines. The later goal is achieved through implementation of two SPs. The proposed WFMs for the aforesaid SPs, in this work, are composed of core stages. In fact, the activities involved in a particular SP have been logically grouped with logical sequence into stages. The proposed WFMs are constructed using well known Entry-Task-Verification-eXit (ETVX) model. Each activity is accompanied with the actor having generic title who has to perform it and the potential artifacts to be created. These actors are taken from a sample SSMEs. The implementers may tailor it as per their working environment. Further, inputs and outputs of the workflow along with the associated processes/stages are also indicated.
4.1 WFM for SP 3.1 – “Establish Configuration Management Records”
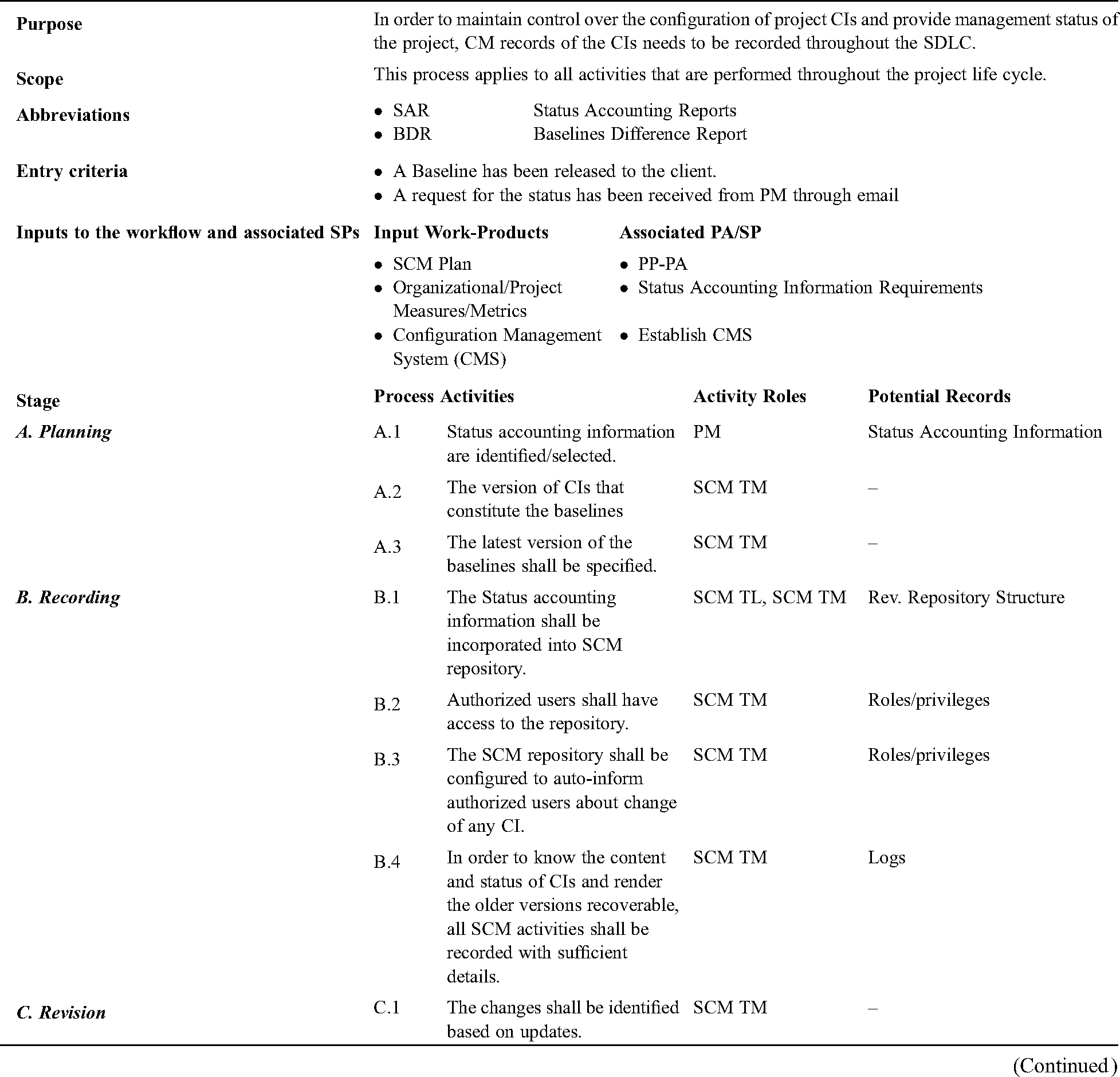
First SP of the said goal is to “Establish and maintain records describing the CIs”. In order to keep brevity, only three among many of the findings from literature are given in Tab. 5 supporting each stage i.e., “Planning”, “Recording”, “Revision”, and “Sharing Reports” of the proposed WFM for SP 3.1 of CM-PA and is depicted in Fig. 2 followed by the associated process guide in Tab. 6. Rationale for provision of process guide in tabular format is to achieve brevity and to provide structured information to implementers.
Table 5: Evidences from literature supporting each stage of WFM for SP 3.1


Figure 2: Workflow model for SP-3.1
Table 6: Process guide for SP 3.1
4.2 WFM for SP-3.2 of CM-PA “Perform Configuration Audits”
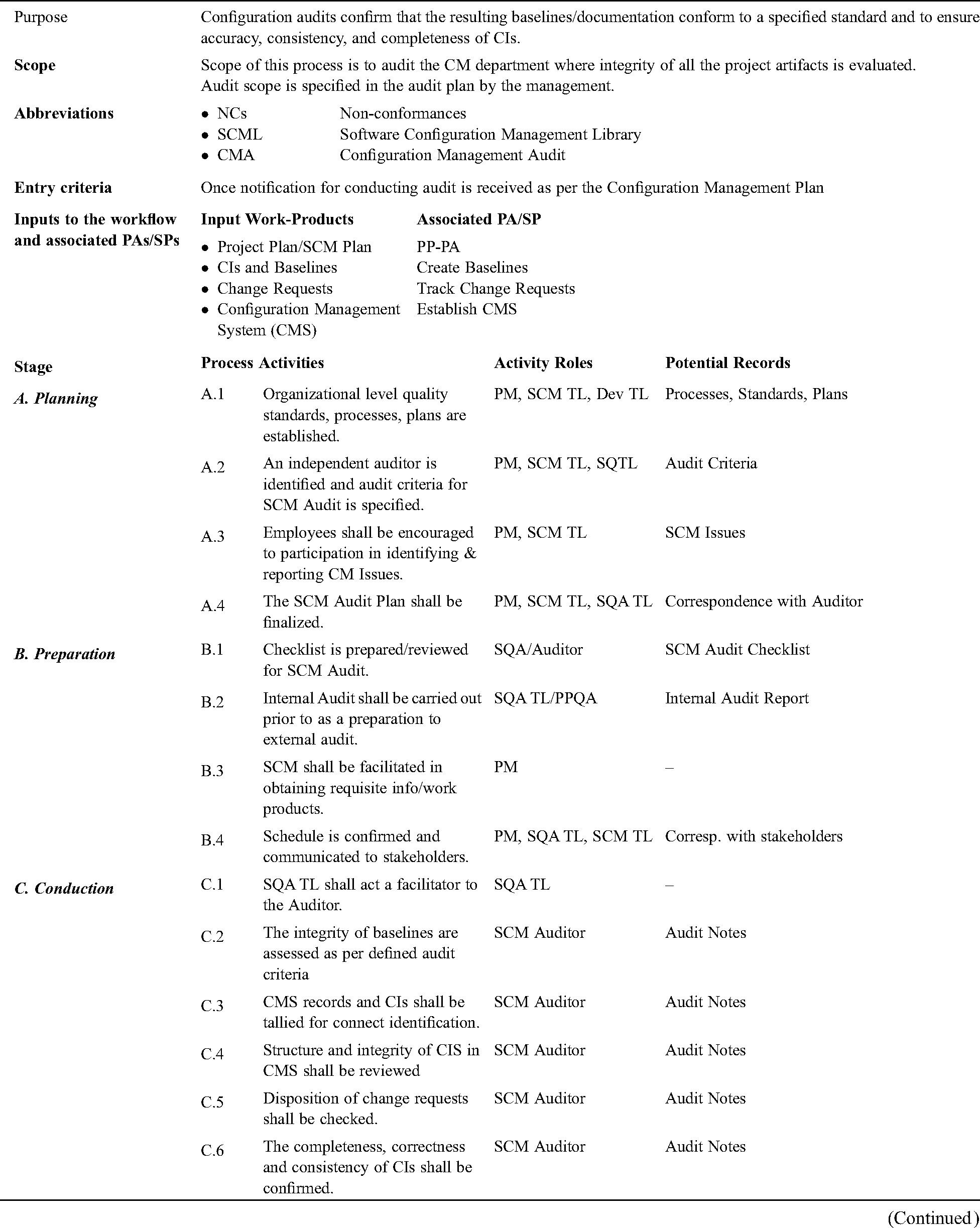
The purpose of SP-3.2 is to appraise the integrity of the baselines. As per CMMI, CM Audit is defined as “Audit is to verify that a CIs or a collection of CIs that make up a baseline conforms to a specified standard or requirement”. Only three among the findings from literature are given in Tab. 7 supporting each stage of the aforementioned WFM i.e., “Planning”, “Preparation”, “Conduction” and “Closure” and is depicted in Fig. 3 followed by the Process Guide in Tab. 8.
Table 7: Evidences from literature supporting each stage of WFM for SP 3.2


Figure 3: Workflow model for SP-3.2
Table 8: Process guide for SP 3.2
5 Validation of Proposed Models, Threats to Validity and Their Mitigation
In order to perform initial evaluation of the proposed models, an expert panel review was carried out where opinions on the models, based on the specified criteria, were taken from 10 experts. The experts having expertise in various domains (SPI, Project Management, Configuration Management and Software Development) were selected required for the study from Pakistani software industry and are enlisted along with the experience in Tab. 9.
Table 9: Profiles of the panel members
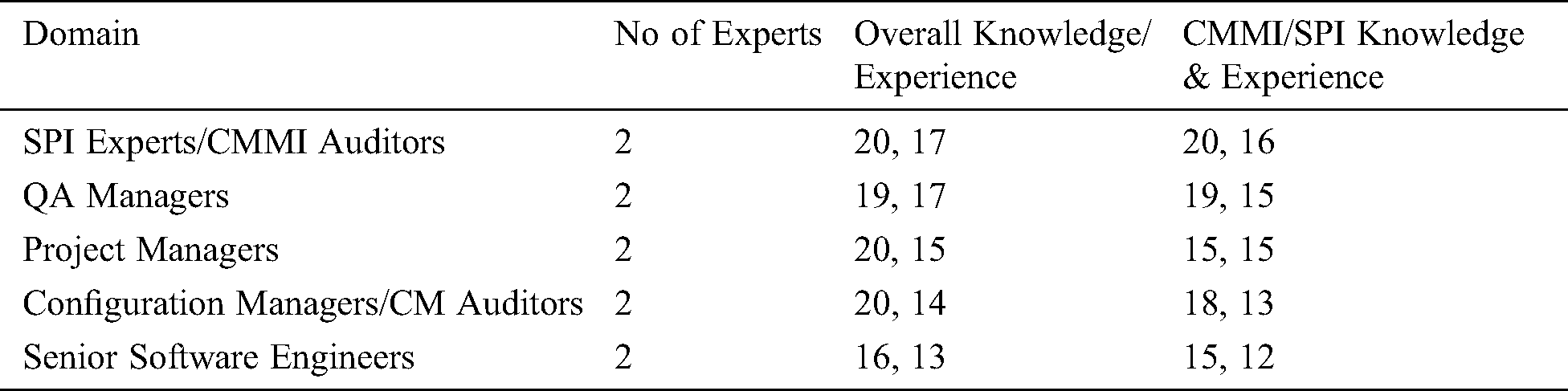
As in [26–30] the researchers are free to frame their own criteria. In this study, the experts were classified into 3 groups based on their experience and knowledge. Experts having experience less than 15 years were classified as Junior, the experts having experience greater than 17 years as Senior and the remaining were classified as In-between. As per this criteria, the panel comprised of 10 experts with 4 seniors, 2 juniors and 4 In-between.
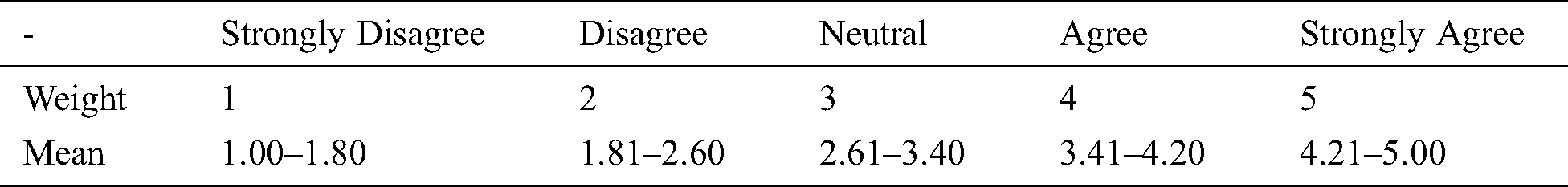
The questionnaire was formulated specifically to obtain the panel opinion on the proposed WFMs after studying the questionnaire designed for a similar work by Niazi [3] and Keshta [4,8]. The questionnaire comprised of three parts including a cover letter elucidating the purpose; demographics; and expert’s opinion. The later part addresses the validation criteria specified in Tab. 4. The questionnaire was reviewed by an academician to make it more legible and refined. The questionnaire comprised seven questions, as shown in Tabs. 11 and 12. Question 8 not shown in questionnaire was used to collect feedback to improve the models. Five point Likert measure with relative weight is given in Tab. 10.
Table 10: Relative weight of five-point liker measure
Summary of responses to questions about SP-3.1 and SP-3.2 of CM-PA are shown in Tabs. 11 and 12.
Table 11: Summary of the responses to the proposed model for Sp-3.1
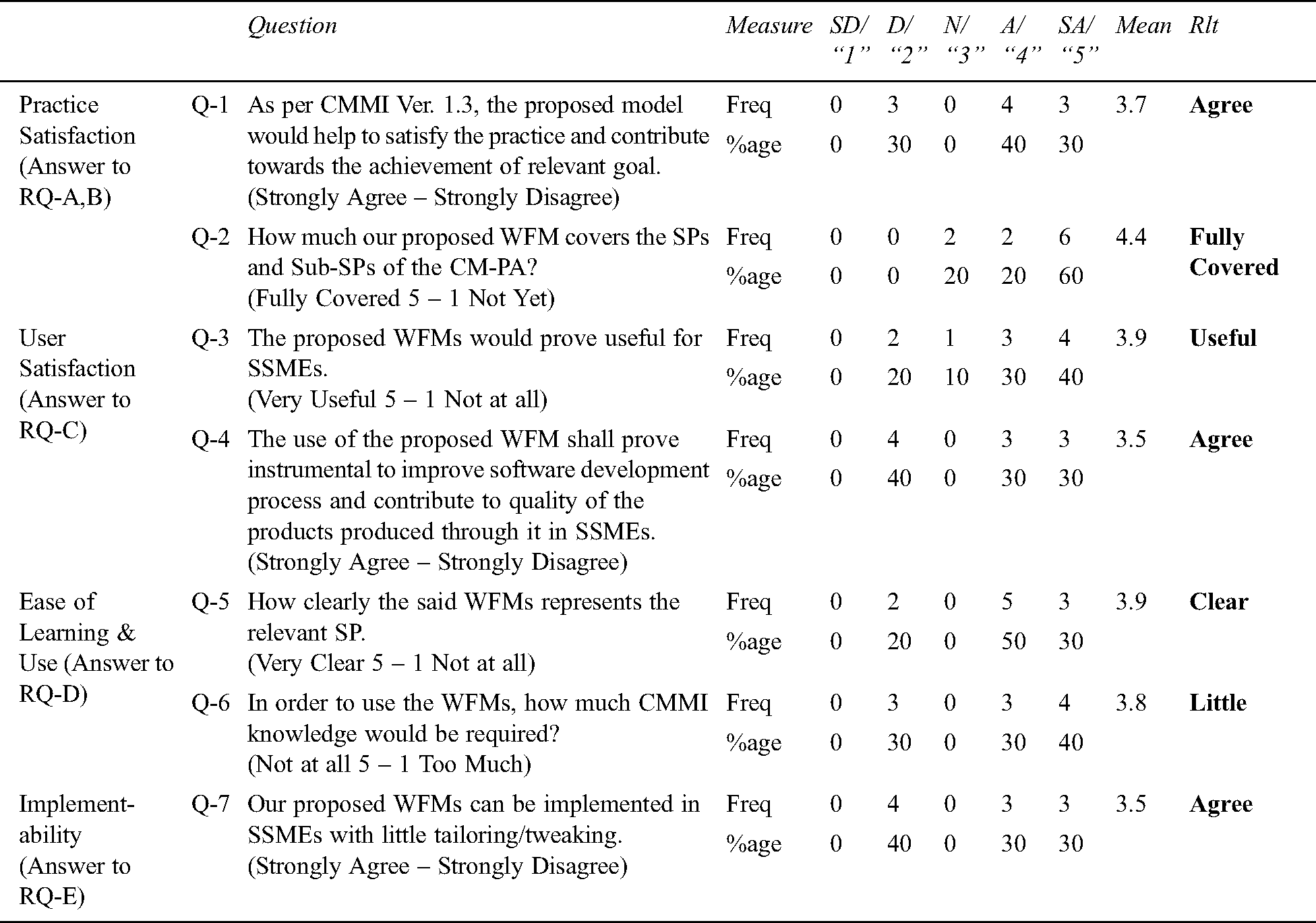
Table 12: Summary of the responses to the proposed model for SP- 3.2
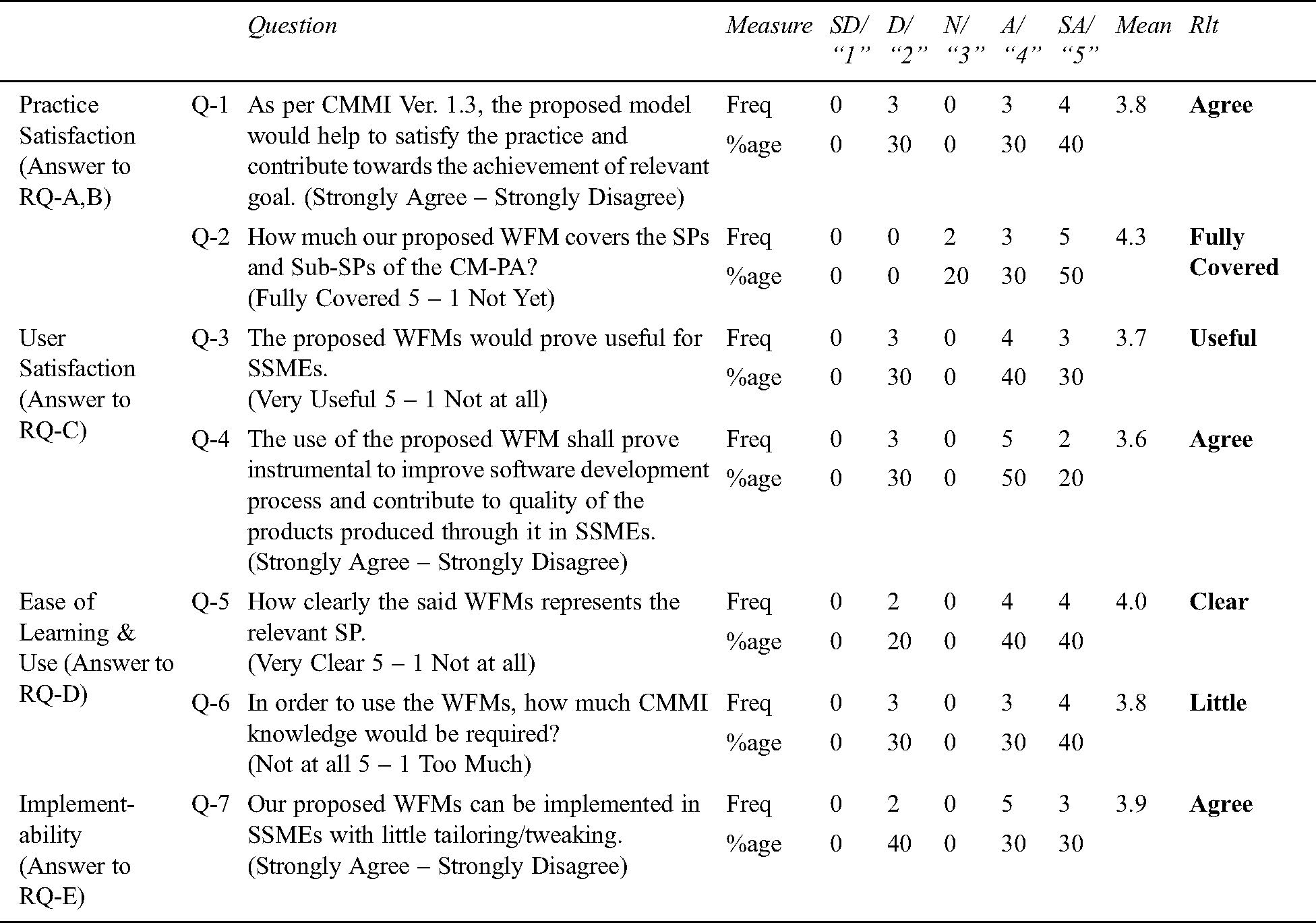
As obvious from the results of EPR, the expert are strongly agree or agree that the models are instrumental in facilitating the implementation of the SPs, supportive in achieving SG-3, provide coverage to the sub-practices, are easy to learn, believed to be very useful to the software industry, perceived to improve process and contribute to the quality of the software produced. Further, it shall particularly support SSMEs in implementing the said SPs. However, it transpired from the EPR that a little knowledge about CM-PA of CMMI and CM domain is required. Results also suggest that there is a room for improvement in the WFMs.
5.2 Validation Through Case Studies
As a confidence measure, two Pakistani software SMEs were selected for carrying out case studies. The SSMEs were willing to publish the outcome of the study, however asked for non-disclosure of the SMEs names and project’s info. As a confidentiality measure, the companies in this study are referred as Small Software Enterprise (SSE) and Medium Software Enterprise (MSE). Brief introduction of the companies are tabulated as under in Tab. 13.
Table 13: Software setups participated in study

After necessary coordination at management level, an opening sessions were arranged in both the SSMEs for participating employees including project manager, quality manager, configuration manager and relevant desirous system analysts, developers and testing professionals. The two companies’ collaborated and about 30 professionals participated. A brief presentation was given over the objectives of the study in these sessions. Soft copies of the models, templates, forms, guides were provided as well as an envelope full of hard copies was handed over for implementation in their environment within one month duration. After implementation in both the SSMEs, SCAMPI Type-“C” & Type-“B” appraisals were conducted against the said SPs to evaluate its effectiveness by the lead auditor with appraisal team members (ATM). Finally, a closing session was conducted to get feedback from participating professionals. The appraisal results were encouraging and appreciated by the lead auditor. Confidence of the lead auditor reflected from his statement that both the SSMEs fulfill the requirements of the said SPs and will certainly result in “Fully-Implemented” if SCAMPI type “A” is conducted. In closing session, feedback was collected through the questionnaire that was originally designed for EPR.
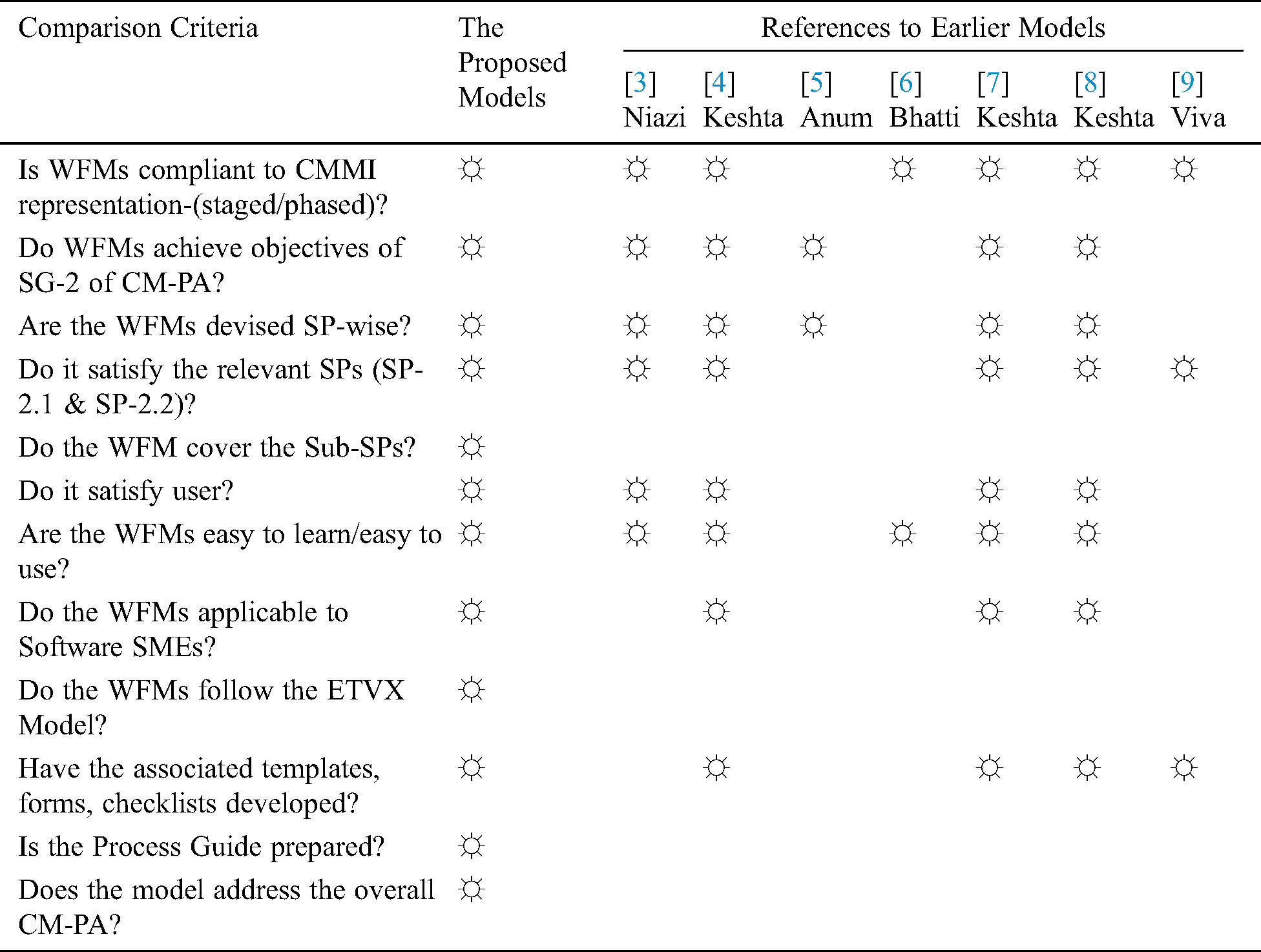
5.3 The Proposed WFMs in Comparison with Earlier Models Developed for Various PAs of CMMI
A detailed comparison of the proposed models with the existing models are inscribed in Tab. 14. The comparison criteria was taken from the work of Niazi [3], Keshta [4,7,8] and further refined.
Table 14: The proposed model in comparison with the earlier models found in literature
5.4 Limitation of the Study/Threats to Validity and Their Mitigation Strategies
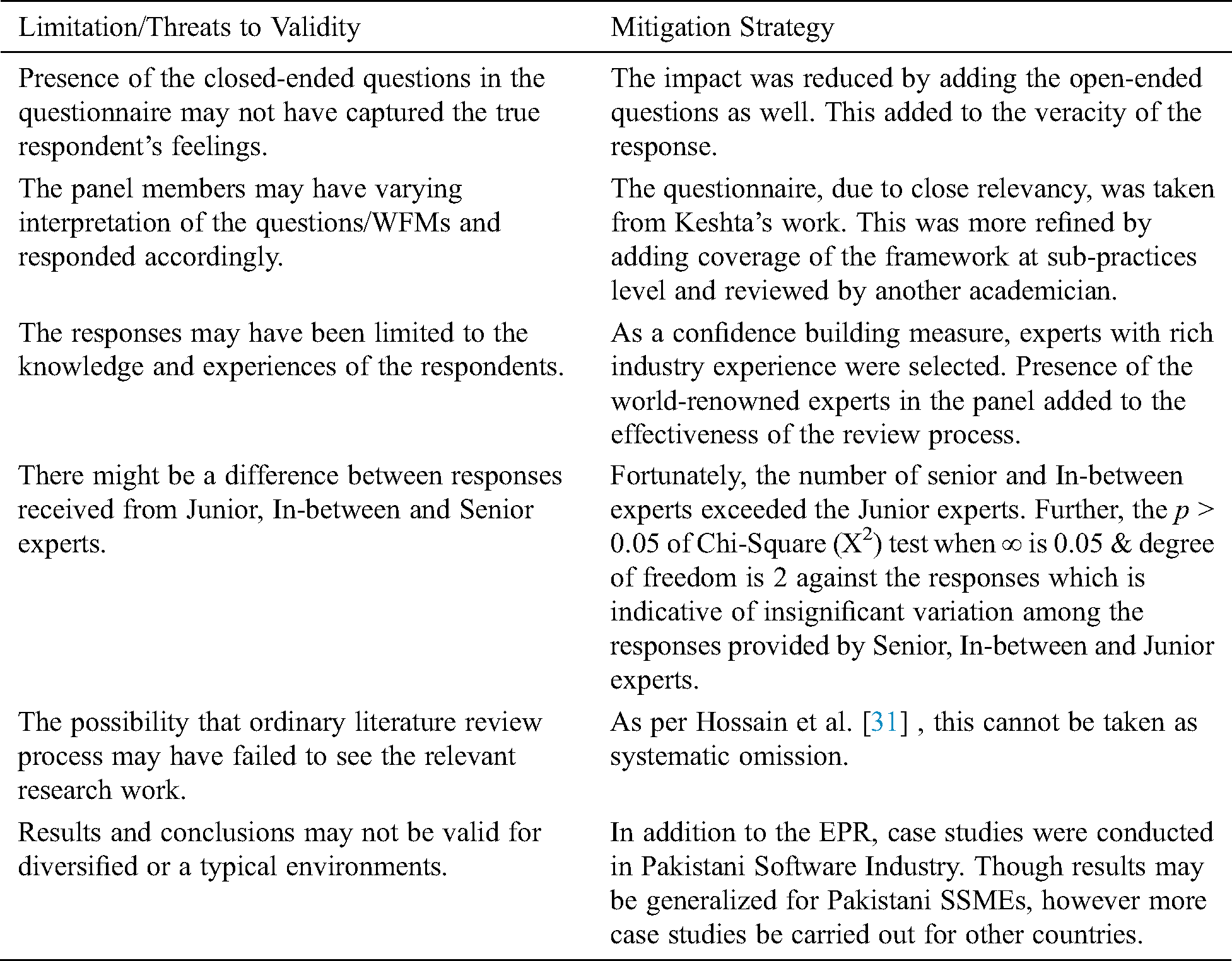
The limitations of the study, threats to its validity are explained in Tab. 15 along with mitigation strategies.
Table 15: Limitations of the study/threats to validity and mitigation strategies.
Designing a workflow model to achieve SG-3 “Establish Integrity” of CM-PA at CMMI maturity level-II and its validation was the main objective of this study. Five research questions (RQ-A~RQ-E) were formulated for the purpose. Further WFMs were devised for two SPs contributing to the aforesaid goal. It is clearly indicated in the Tabs. 11 and 12 that which question of questionnaire addresses which research question making use of which validation criteria. Responses from the experts satisfied the said criteria. The results were further affirmed through conducting case studies. It is worth-mentioning that case studies demonstrated the ability of Pakistani SSMEs to adopt the proposed models with little tailoring to adjust their contexts. Satisfactory comments from participating organizations and experts speaks well of the WFMs and add to the confidence in the evaluation results. In face-to-face discussion with the participating professionals, it transpired that they had no problem in understanding/usage of the models with associated templates, forms, checklists and process guides as helping tools. The WFMs were refined after several rounds of improvements by incorporating suggestions from academicians, professionals and finally feedback from case studies. This work shall be continued to develop WFMs for other SPs of this PA, other PAs of Level-II as well as higher levels for which the workflow models are not developed yet. The models also need to be revised/validated for future versions of the CMMI.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. G. Xu, H. Hu, P. Yu, J. Lv, P. Qu et al. (2013). , “Supporting flexibility of the CMMI process framework with a multi-layered process model,” in Web Information System and Application Conference (WISA 2013Yangzhou, China, pp. 409–414. [Google Scholar]
2. CMMI Product Team. (2010). “CMMI for Development, Version 1.3,”. [Google Scholar]
3. M. Niazi, C. Hickman, R. Ahmad and M. Ali Babar. (2008). “A model for requirements change management: Implementation of CMMI level 2 specific practice,” in 9th International Conference on Product-Focused Software Process Improvement (PROFES 2008), Springer Berlin Heidelberg, Monte Porzio Catone, Italy, vol. 5089, pp. 143–157. [Google Scholar]
4. I. Keshta, M. Niazi and M. Alshayeb. (2017). “Towards implementation of requirements management specific practices (SP1.3 and SP1.4) for Saudi Arabian small and medium sized software development organizations,” IEEE Access, vol. 5, pp. 24162–24183. [Google Scholar]
5. A. Tariq, S. A. Khan and S. Iftikhar. (2014). “Remapping of CMMI level-2 KPA’s for development process improvement of software-as-a-service (SaaS) cloud environment,” in Int. Conf. on Open Source Systems and Technologies (ICOSSTLahore, Pakistan, pp. 43–51. [Google Scholar]
6. M. W. Bhatti, F. Hayat, N. Ehsan, A. Ishaque, S. Ahmed et al. (2010). , “A methodology to manage the changing requirements of a software project,” in Int. Conf. on Computer Information Systems and Industrial Management Applications (CISIMKrackow, Poland, pp. 319–322. [Google Scholar]
7. I. Keshta. (2019). “A model for defining project lifecycle phases: Implementation of CMMI level 2 specific practice,” Journal of King Saud University - Computer and Information Sciences, pp. 1–10. [Google Scholar]
8. I. Keshta, M. Niazi and M. Alshayeb. (2018). “Towards implementation of process and product quality assurance process area for Saudi Arabian small and medium sized software development organizations,” IEEE Access, vol. 6, pp. 41643–41675. [Google Scholar]
9. C. Vivatanavorasin, N. Prompoon and A. Surarerks. (2006). “A process model design and tool development for supplier agreement management of CMMI: Capability level 2,” in XIII ASIA PACIFIC Software Engineering Conf. (APSEC’06Kanpur, India, pp. 385–392. [Google Scholar]
10. E. Hochbergs. (2020). MS Thesis by Erik Hochbergs and Laroy Nilsson Sjödahl from Department of Computer Science LTH, Lund University, Lund Sweden. [Google Scholar]
11. S. Fahmy, A. Deraman, J. Yahaya, A. Nasir and N. Shamsudin. (2020). “The evolution of software configuration management,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 1.3, pp. 50–63. [Google Scholar]
12. M. Tuape. (2019). “Factors affecting development process in small software companies,” in IEEE/ACM Symposium on Software Engineering in Africa (SEiAMontréal, Québec, Canada, pp. 16–23. [Google Scholar]
13. V. José, G. Camila, R. Balancieri and A. C. Rouiller. (2020). “The measurement process in micro and small software maintenance companies: Empirical study,” Independent Journal of Management & Production (IJM&P), vol. 11, pp. 519–538. [Google Scholar]
14. T. M. Eshete. (2020). Thesis of MS in Software Engineering by Tadele Mengiste Eshete A, School of Research and Postgraduate Studies Faculty F Computing, Bahir Dar University Bahir Dar Institute of Technology, DSpace Institution, DSpace Repository, . http://dspace.org. [Google Scholar]
15. S. Dasanayaka. (2008). “SMEs in globalized world: A brief note on basic profiles of Pakistan’s small and medium scale enterprises and possible research directions,” Research Journal of the Institute of Business Administration Karachi – Pakistan, vol. 3, no. 1, pp. 69–90. [Google Scholar]
16. S. Divakara and H. N. S. K. Surangi. (2018). “A literature review on small & medium size enterprises,” Journal of Business and Technology, vol. 2, no. 3, pp. 23. [Google Scholar]
17. H. Karadag. (2015). “The role and challenges of small and medium-sized enterprises (SMEs) in emerging economies: An analysis from Turkey,” Business and Management Studies, vol. 1, no. 2, pp. 179–188. [Google Scholar]
18. A. Tripathi. (2019). “SMEs in Saudi Arabia - an innovative tool for country’s economic growth,” Science International (Lahore), vol. 31, no. 2, pp. 261–267. [Google Scholar]
19. C. Mary Beth, M. Konrad and S. Shrum. (2017). CMMI for Development. Third Edition, Addison Wesley, Pearson Education, Boston, USA. [Google Scholar]
20. G. O’Regan. (2011). Introduction to Software Process Improvement. London Dordrecht Heidelberg New York: Springer. [Google Scholar]
21. A. Abran, J. W. Moore, R. Dupuis, R. Dupuis and L. L. Tripp. (2014). “Guide to the Software Engineering Body of Knowledge (SWEBOK), A Project of the IEEE Computer Society, Version 3.0. [Google Scholar]
22. G. O’Regan. (2014). Introduction To Software Quality Assurance. Ireland, Cham Heidelberg New York Dordrecht London: Springer. [Google Scholar]
23. J. C. Blockwood,. (2020). “Editor, Professional skepticism: A model for public sector auditing,” International Journal of Governemnt Auditing, vol. 47, no. 3, pp. 45, , [Online]. Available: www.intosaijournal.org. [Google Scholar]
24. I. Guidelines. (2010). “ISSAI Guidelines on Performance Audit,”. [Google Scholar]
25. T. Gilchrist. (2010). “Software Process Reviews/Audits Process Overview - SASQAG,”. [Google Scholar]
26. S. U. Khan, M. Niazi and R. Ahmad. (2012). “Empirical investigation of success factors for offshore software development outsourcing vendors,” Institute of Engineering and Technology Software, vol. 6, no. 1, pp. 1–15. [Google Scholar]
27. M. I. U. Lali, R. U. Mustafa, K. Saleem, M. S. Nawaz, T. Zia et al. (2017). , “Finding healthcare issues with search engine queries and social network data,” International Journal on Semantic Web and Information Systems, vol. 13, no. 1, pp. 48–62. [Google Scholar]
28. B. Shahzad, Y. Al-Ohali and A. Abdullah. (2011). “Trivial model for mitigation of risks in software development life cycle,” International Journal of the Physical Sciences, vol. 6, no. 8, pp. 2072–2082. [Google Scholar]
29. B. Shahzad and S. Afzal Safvi. (2008). “Effective risk mitigation: A user prospective,” International Journal of Mathematics and Computers in Simulation, vol. 2, no. 1, pp. 70–80. [Google Scholar]
30. M. Shafiq, M. Ahmad and J. G. Choi. (2017). “Public system usability analysis for the valuation of cognitive burden and interface standardization: A case study of cross-ATM design,” Journal of Organizational Computing and Electronic Commerce, vol. 27, no. 2, pp. 162–196. [Google Scholar]
31. E. Hossain, M. Ali Babar and H. Y. Paik. (2009). “Using scrum in global software development: A systematic literature review,” in Fourth IEEE Int. Conf. on Global Software Engineering (ICGSE 2009Limerick, Ireland, pp. 175–184. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |