DOI:10.32604/iasc.2021.012462

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.012462 |  |
| Article |
Maximizing Throughput in Wireless Multimedia Sensor Network using Soft Computing Techniques
1Department of IT, PSNA College of Engineering and Technology, Dindigul, 624622, Tamil Nadu, India
2Department of ECE, University College of Engineering, BIT Campus, Anna University, Tiruchirappalli, 620024, Tamil Nadu, India
3School of Computing, SRM Institute of Science and Technology, Kattankulathur, 603203, Tamil Nadu, India
4Department of Medical Equipment Technology, College of Applied Medical Sciences, Majmaah University, Al Majmaah, 11952, Saudi Arabia
5Department of EEE, National Engineering College, Kovilpatti, 628503, Tamil Nadu, India
6Department of EEE, SRM Institute of Science and Technology, Chennai, 603203, India
*Corresponding Author: Krishnan Muthumayil. Email: drmuthupsna@gmail.com
Received: 30 August 2020; Accepted: 19 October 2020
Abstract: Wireless Multimedia Sensor Networks (WMSN) provides valuable information for scalar data, images, audio, and video processing in monitoring and surveillance applications. Multimedia streaming, however, is highly challenging for networks as energy restriction sensor nodes limit the potential data transmission bandwidth and lead to reduced throughput. WMSN’s two key design challenges, which can be achieved by the clustering process, are energy efficiency and throughput maximization. The use of the clustering technique helps to organise the sensor nodes into clusters, and between each cluster a cluster head (CH) will be chosen. This paper introduces a new Artificial Fish Swarm Optimization Algorithm (AFSA) with a Clustering Technique for Throughput Maximization in WMSN, called AFSA-HC, based on Hill Climbing (HC). The proposed AFSA-HC algorithm includes four key processes to optimise network throughput, namely node initialization, node clustering based on AFSA-HC, data aggregation based on the deflate algorithm, and transmission of hybrid data. To check the adequate performance of the presented AFSA-HC technique, a thorough experimental review will be carried out. The results of the simulation showed that the AFSA-HC approach achieved optimum results for various steps, namely energy consumption, throughput, network life, network stability and packet loss.
Keywords: Clustering; data aggregation; energy efficiency; throughput; WMSN
Currently, WMSN is used in various circumstances to observe and control a broad range of applications such as visual monitoring, healthcare assistance, traffic operations, public safety, and industrial automation, etc. Due to the cost reduction of wireless and sensor applications, WMSN is planned to operate in a diverse backbone of the network, integrating Internet services with application-oriented networks [1]. The Internet of Things (IoT) provides the realm of simultaneous communications in which the traditional concepts of the Internet could be incorporated into the scenario of a wireless sensor network.
WMSN has the ability to frame countless source nodes that stream information continuously or at a specific time. WMSN’s basic architecture is shown in Fig. 1. In this case, there may be a lot of data in the direction of the sink that would stream over the network. The huge amount of packets cannot be sent because of less bandwidth for ad-hoc networks consisting of wireless personal area mesh topologies [2]. Similarly, multiple packets can be distributed at the same time through ad hoc paths, consuming energy in the nodes. MAC protocols for full bandwidth need to be controlled as to where the IEEE 802.11 network becomes a low-cost and acceptable situation in the case of large-scale WMSN with more lively multimedia sensor nodes. Higher bandwidth will be needed for the WMSN when the sink task is performed by Wi-Fi Access Points (APs).

Figure 1: Block diagram of WMSN
It is important to stress that there are quite a few consequences of wireless communications involving energy use, which is similarly related to Wi-Fi and WMSN. Nowadays, by launching wireless communication systems with less power consumption, there are several laborious works guiding their target of solving problems. In addition, in day-to-day operations, the normal use of energy network devices globally has been reported to be twenty-five Gigawatts, where WLAN might feature more than 5000 Wi-Fi APS as a single population. However, these ranges have arisen in recent years, as seen in Lannoo [3]. At the same time, it may be useful to note that certain important components are missing, as in the new network design technique. The traffic criteria and user density are mainly neglected. For a network where the compactness of the user and traffic load is high, the actual coverage-based optimization technique might look inadequate. Very quickly, with an increase in application use data value, WLAN and WMSN history would have high user attention; but the energy capacity will still be a significant design issue. Multimedia may have particular prototypes of transmission that modify the overtime period. Camera-enabled sensing systems are intended to send pictures or video streams with different broadband specifications. To recover the limited volume of data, scalar sensing gadgets could be stacked. In addition, the source node may pass data packets to an instance, requiring minimum latency and jitter [4]. This research paper proposes a new energy management technique to supply an energy-efficient solution between multiple sensor nodes connected with one-hop Wi-Fi connexion ends.
WMSN has limited resources and demonstrates a strong demand for broadband. In order to increase the lifetime of such networks, computational as well as communication power consumption related to data transmission must be reduced. Although CS is normally used to fix all signals from a comparatively small linear measurement, it is known to capture and display versatile signs at a value below the Nyquist value. At base intricacy, it senses and can obtain the value in a parallel manner. It is stated that CS is used in WMSN to reduce power savings. A modern sampling theory was discovered by Candes and Wakin [5] that merges sampling and compression processes at the time of data collection. Compared to traditional techniques in current WMSN, the use of the CS hypothesis could retrieve less signs and images from distant, smaller samples or measurements [6]. To approximately determine numerical data and useless measurements of CS, the sparse vector could be used. In addition, it might decrease the power utilisation of the task of image communication. Multimedia packets can be sent through various wireless methodologies, but limitations on quality of service (QoS) such as delays and jitters must be checked all the time when applications are mandatory. Generally, a creation to be tried at high achievement has been suggested by many tasks. Streaming multimedia creates many difficulties in wireless sensing meshes, which are considered to be addressed in different activities. Efforts in Boukerche et al. [7] were made by the Reliable Synchronous Transport Protocol (RSTP) to synchronise image motion from a wide range of sensing device sources. At the same time, for image processing [8], progressive coding is used. While images were gathered, when streaming along with low bandwidth nodes and incorrect medium, bad standards could be posted entirely. The journalist designed a computerised outcome in Lee and Jung [9] to minimise blocks by reducing the rate of data transmission using the Discrete Wavelet Transform (DWT) coding technique, where the quality of images was not significantly reduced. The work in Chen et al. [10] describes the cross-layer optimization of video transmission in WMSN in different ways. Research used multipath routing, where less latency paths must be regularly used to transfer data packets, including encoded video and power consumption, as it could be possible to increase the network capacity by freeing up multi-media real-time passage.
A cross-layer technique for streaming videos was designed in WMSN in Pudlewski et al. [11], using the concept of Compressive Sensor, aimed at altering data transmission speeds. The broadband needs for sensing nodes can be spectacular for all if many network source streams premium video. IEEE 802.11 MAC protocols have been developed to allow good multimedia streaming in wireless sensing nodes. Wi-Fi-based WMSN problems are addressed in a few studies. In Zhang and Ding [12], based on the importance of encoded data for MPEG-4 video streaming, the reporter established a difference in the handling of multi-media data packets in the MAC layer. It uses the extension IEEE 802.11s [13], which offers transmission groups based on QoS. In another way, the IEEE 802.11e extension is discussed in Touil et al. [14] for wireless multi-media sensing networks and some MAC access control machines of this protocol have survived [15].
The synchronisation problem in clusters was addressed by Zhou et al. [16] to enhance multi-link and time delays in multiplex networks by using an adaptive pinning strategy. Tang et al. [17] addressed clustering of medical data using the MapReduce method, achieving successful results through the algorithm of k-means. Yin et al. [18] have been working on reducing load balancing energy consumption through metaheuristic algorithms in clustered wireless sensor networks. Wang et al. [19] tested IoT components in wireless sensor networks for information exchange between devices, introduced a self-adaptive approach based on affinity propagation, and achieved better communication between devices. Liao et al. [20] checked with WSN’s coverage of interest and communication problems, it was solved by the deployment of mobile sensors with less motion through the TV-Greedy algorithm. An improved routing protocol design using machine learning algorithms was proposed by Wang et al. [21] to increase the lifetime of sensors in wireless sensor networks. Kuang et al. [22] Addressed the method of intrusion detection using SVM, PCA, and improved PSO, improved computational time and wireless sensor network accuracy.
Usually, however, power consumption is unchanged. In order to encourage innovative research in this area, heavy wireless multi-media sensor networks and power preservation must be studied attentively. This paper presents a new Clustering Technique for Throughput Maximization in WMSN, called AFSA-HC, based on the Artificial Fish Swarm Optimization Algorithm (AFSA) with Hill Climbing (HC). Since the traditional AFSA suffers from the problem of local search, the HC approach is integrated into it to improve the process of local search. The proposed AFSA-HC algorithm includes four major network throughput maximisation processes, namely node initialization, node clustering based on AFSA-HC, data aggregation based on the deflate algorithm, and hybrid data transmission. The integration of these processes allows optimum energy efficiency and throughput to be achieved. To check the successful performance of the presented AFSA-HC technique, a detailed experimental review will be carried out.
2 The Proposed AFSA-HC Technique
The proposed AFSA-HC algorithm includes four major network throughput maximisation processes, namely node initialization, node clustering based on AFSA-HC, data aggregation based on the deflate algorithm, and hybrid data transmission. Fig. 2 illustrates the working theory of the AFSA-HC algorithm proposed. The AFSA-HC algorithm is performed and builds the clusters once the nodes are deployed and initialised. The algorithm AFSA-HC effectively selects the CHs and builds the clusters. Then, the deflate algorithm is performed by the CHs to combine data obtained from the CMs. Finally, where data is transmitted in a constructive and reactive way, a hybrid data transmission approach is implemented.
2.1 AFSA-HC Based Clustering Phase
To reduce or optimise the outcome of a function by modifying its components, optimization methods are used. All acceptable value to this problem is known as feasible outcomes and the best outcome is a better one. Each technique of swarm intelligence (SI) depends on the population; their iterative process is about improving the place of separation in the population and their progress to the optimal positions. AFSA is the most desirable SI techniques with advantages such as global ability to explore, robustness, parameter setting tolerant pace, and can also check that they are not responsive to starting values [23].
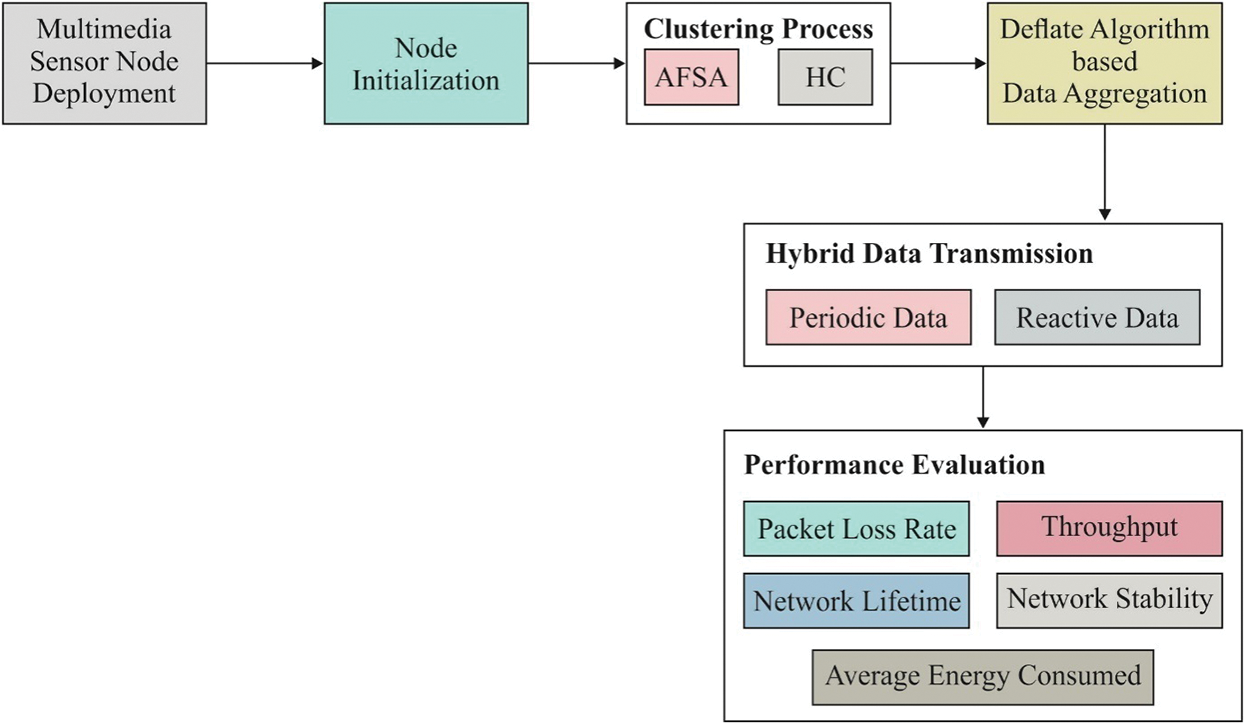
Figure 2: Block diagram of AFSA-HC technique
The ASFA imitates the fish swarm prey output and it is built to reach very quickly. A visual idea of AFSA is demonstrated in Fig. 3. An exploration starts with random results that are mapped to all fish. Fitness is calculated and the following process is started by the fish and the desired result is followed by another fish. A swarming approach is initiated when the outcome is sub-optimal. The prey procedure is initiated when the desired outcome does not come in. During this procedure, once the appropriate threshold or termination requirements are met, they will be continued.

Figure 3: Vision concept of the AFA
The AFSA has four functions that model the existence of fish in a swarm of fish. A free-move behaviour is an initial function: as in the world, fish fly generously in the swarm if it does not hurt. The 2nd feature is prey behaviour since it utilises the human body’s vision sensing, smelling, and several other usable sensing devices. In AFSA, via a visual-sized radius, the area where an artificial fish senses the prey is modelled as communities. Subsequent behaviour as a fish decides food is the 3rd function; other swarm members and obey it to obtain the food. The final purpose is the behaviour of the swarm that imitates fish as fish eternally seek to be in the swarm and does not protect leaves from hunters. The degree of food stability in the water area is an objective feature of the AFSA.
Assume that the condition vector of AFS is (x-1,x-2, … x-n) where x-1,x-2, … x-n is the fish’s place. In this area of fish, the food focus is expressed as y = f(x), where y is the objective value of the function. The gap between artificial fish is d-ij = X-i-X-j, I and j is an arbitrary fish. The step implies that the artificial fish has the highest step scale. A is the amount of the congestion factor.
Assume 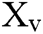 is the visual place at several moment.
is the visual place at several moment.  is the novel place. After that, the progress procedure is expressed as Eq. (1):
is the novel place. After that, the progress procedure is expressed as Eq. (1):


In the prey mode, the performances of fish are provided with Eq. (2):

Now rand is a randomized function through a series of  , 1
, 1 During this swarm stage, the performance of the swarm is provided with Eq. (3):
During this swarm stage, the performance of the swarm is provided with Eq. (3):

Following phase, the performance is provided with Eq. (4):

The 3 steps mentioned make sure both global as well as local explore and the explore direction subsequent the optimal food source is obtained. The flowchart of the AFSA is shown in Fig. 4. During this work, AFSA is altered as discussed below.
An HC technique was utilized for “local exploration” to achieve the local optimum. As HC techniques are simpler for implementation and provide more flexibility in the action of particles, the AFSA is integrated with HC. The HC techniques utilize arbitrary local search for defining the direction as well as the size of every novel phase [24]. The process involved in the HC technique is listed as follows.
• Initialization: particular the neighborhood function  and choose an initial solution
and choose an initial solution  ;
;
• Put the loop counter z = 1;
• While iteration z < Z;
Create  based on
based on  ;
;
• Compute the alter in the objective function value  ;
;
• Accept solution  if
if  ;
;
• z = z + 1;
• End
• End Procedure
• During this technique,  were intended to create a novel candidate solution as in explaining as following.
were intended to create a novel candidate solution as in explaining as following.

where  signifies the altering series of original particles.
signifies the altering series of original particles.  is random values among 0 and 1.
is random values among 0 and 1.
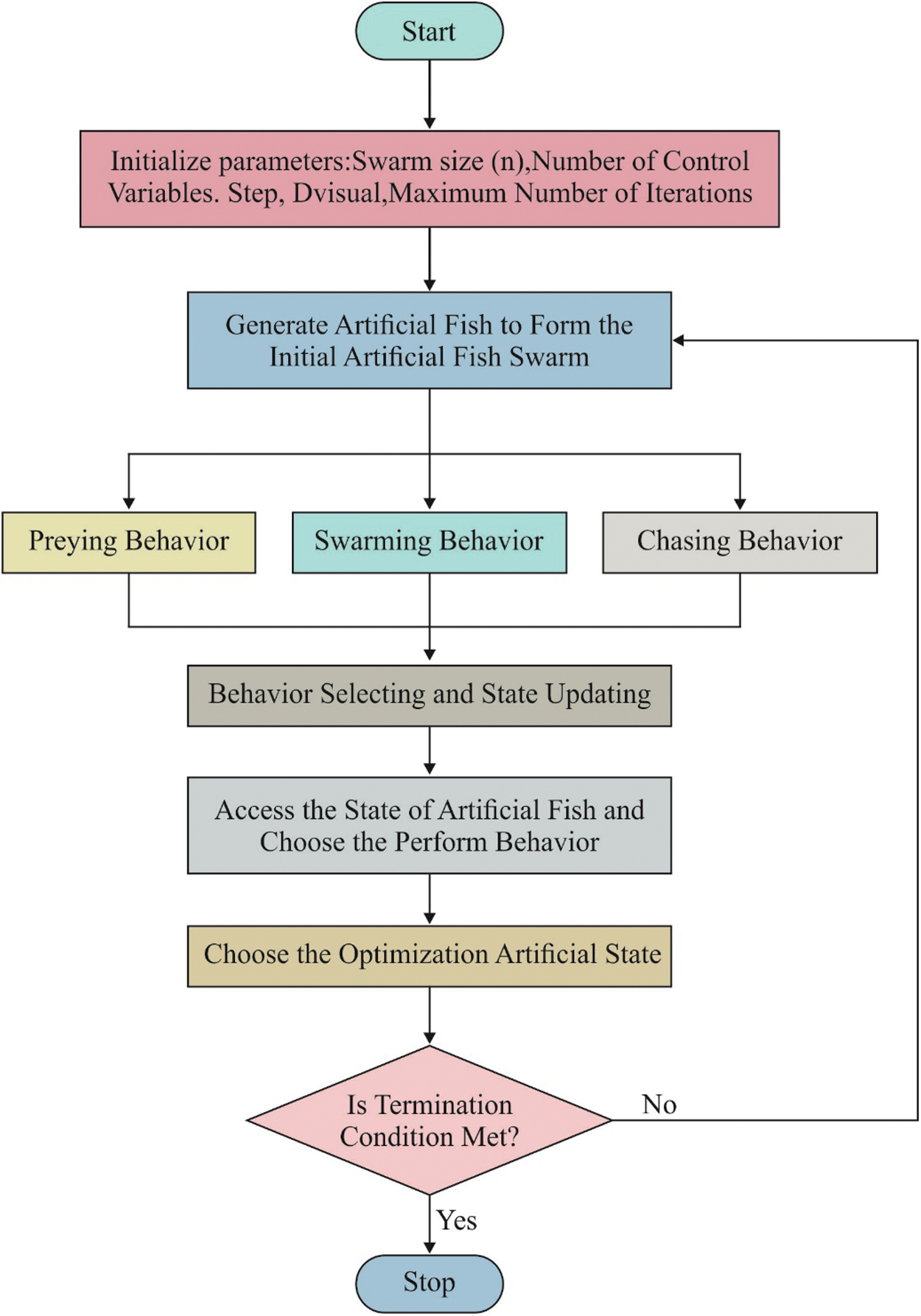
Figure 4: Flowchart of AFSA
The results are arbitrarily separate and action either swarming or subsequent performance. Utilizing competition chosen, the optimal fishes are chosen and the prey methods are started. Fishes that are enormously completely in prey are chosen and permitted to mate between themselves. A novel result created with optimal fishes is obtained to the next iteration. During this paper, the results are signified utilizing binary values and distance among the fishes calculated utilizing Hamming distance. It is calculated among 2 strings  is the number of positions as
is the number of positions as  and
and  changes. The optimal fish is chosen utilize the roulette wheel selection where the possibility of a fish individual chosen is directly proportional to fitness. The possibility of a fish
changes. The optimal fish is chosen utilize the roulette wheel selection where the possibility of a fish individual chosen is directly proportional to fitness. The possibility of a fish  through fitness
through fitness  chosen from
chosen from  number of fishes is calculated as Eq. (5):
number of fishes is calculated as Eq. (5):

For enhancing the QoS, a multi-objective function depends on an end to end delay and energy is present in Eq. (6):

where  is the end to end delay,
is the end to end delay,  is the entire delay to reach BS,
is the entire delay to reach BS,  is the maximum delay in the network to achieve BS,
is the maximum delay in the network to achieve BS,  is the residual energy in the CH,
is the residual energy in the CH,  is the primary energy. Some of the assumptions are listed below.
is the primary energy. Some of the assumptions are listed below.
• Every node is situated arbitrarily in the network.
• All nodes have similar primary energy.
• Every fish is unisex.
• Because fishes are unisexual, mating is feasible among some 2 fishes.
As the result spaces are signified in a binary format, a transfer function is needed to flip the bit if the fish modifies status. During this paper, a novel transfer function is presented for flipping the bits provided with Eq. (7):

For achieving flipping, an arbitrary number is created among  and one; the bits are flipped when the arbitrary number is below the transfer function provided with Eq. (8):
and one; the bits are flipped when the arbitrary number is below the transfer function provided with Eq. (8):

2.2 Deflate based Data Aggregation Phase
The deflate algorithm is performed by every CH to aggregate the data obtained from its CMs. Deflate is an approach to lossless encoding, which uses coding from LZSS and Huffman [25]. A Deflate stream consists of a set of blocks in which a three-bit header comes with each block.
(i) First bit: Last-block-in-stream marker: (1: This is the last stream block. 0: There are many blocks to be processed after this one).
(ii) Second and third bits: For this block, the encoding model is used. The saved block choice adds lower overhead and is used to format data that is incompressible.
The highly compressible data ends up with the dynamic Huffman encoding encoding, which independently produces an optimal Huffman tree tailored for each data block. The guidelines for generating the critical Huffman tree immediately monitor the header of the block. For a short message, the static Huffman choice is used, where the fixed saving obtained by discarding the tree outweighs the loss of compression loss due to the use of a non-optimal code. Generally, the compression is performed by the two measures that follow.
• The matching and substitution of pointer replica strings.
• Replacement of symbols using the frequency of use with novel, weighted symbols.
2.3 Hybrid Data Transmission Phase
The hybrid data transmission process begins once the CHs aggregate the data. The CHs will initially broadcast the following variables:
Attribute (A): The data is obtained from a user-interested parameter.
Threshold values: The Hard Threshold (HT) and the Soft Threshold (ST) are included. HT is a certain parameter value and the value that exceeds HT is transmitted. A minor difference in the value of the attribute is indicated by the ST, which activates the data transmission node again.
Schedule: TDMA is used for scheduling purposes, where each node is assigned a slot.
Timer: The maximum time between the two consecutive reports transmitted by the node is specified. It is a multiple of the length of the TDMA schedule and is used for constructive or periodic transformation of data.
The unwanted and redundant transfer of data can be avoided by the use of hybrid data transmission. This results in optimum energy production and it is possible to increase throughput.
To check the successful performance of the presented AFSA-HC technique, a detailed experimental review will be carried out. The results of the simulation showed that the AFSA-HC technique achieved optimum results in terms of various metrics, namely energy consumption, throughput, network lifetime, network stability and loss of packets. The parameter settings for the AFSA-HC technique are given in Tab. 1.

Tab. 2 offers an overview of the AFSA-HC model’s findings in terms of the various measurements under different node numbers. Fig. 5 indicates the study of the network stability of the AFSA-HC model with current ones, which refers to the round number at which all the nodes in the network are operational. For an efficient clustering technique, the network stability should be high. Fig. 5 showed that under a varying number of nodes, the AFSA-HC model showed greater network stability over all the other approaches. For instance, the LEACH protocol has obtained the least network stability of 220 rounds under the node count of 250. At the same time, the GA obtained a marginally better network stability of 420 rounds, while the BFSA technique gave an even greater network stability of 495 rounds. In addition, by reaching a maximum of 520 rounds, the BFSA-TF has tried to demonstrate successful network stability. However, maximum network stability of 550 rounds has been suggested by the presented AFSA-HC technique. The successful performance of the AFSA-HC technique in terms of network stability was assured by those values.
Table 2: Results analysis of proposed AFSA-HC with sate of art methods

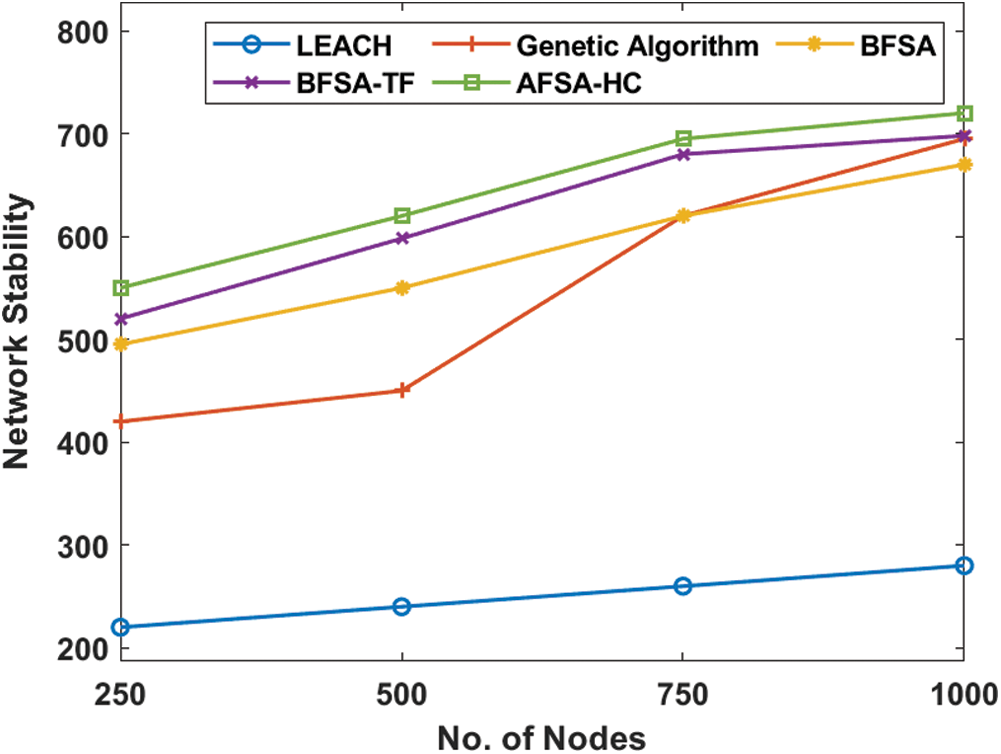
Figure 5: Network stability analysis of AFSA-HC with existing models
Fig. 6 shows the AFSA-HC method analysis with current network lifetime models that refers to the round number at which any node in the network becomes dead. The network lifetime for an efficient method of clustering can be long. The figure indicated that under a varying number of nodes, the AFSA-HC model showed a cumulative network lifetime over all the other approaches. In this case, the LEACH protocol achieved a short network life of 725 rounds under a node count of 250. At the same time, the GA obtained a much better network life of 810 rounds, while the BFSA technique also got a maximum network life of 830 rounds. In addition, by obtaining a greater of 835 rounds, the BFSA-TF has attempted to demonstrate efficient network lifetime. However, a cumulative network life of 860 rounds was described by the presented AFSA-HC technique. These values ensure that the AFSA-HC technique is successful in terms of network lifetime efficiency.
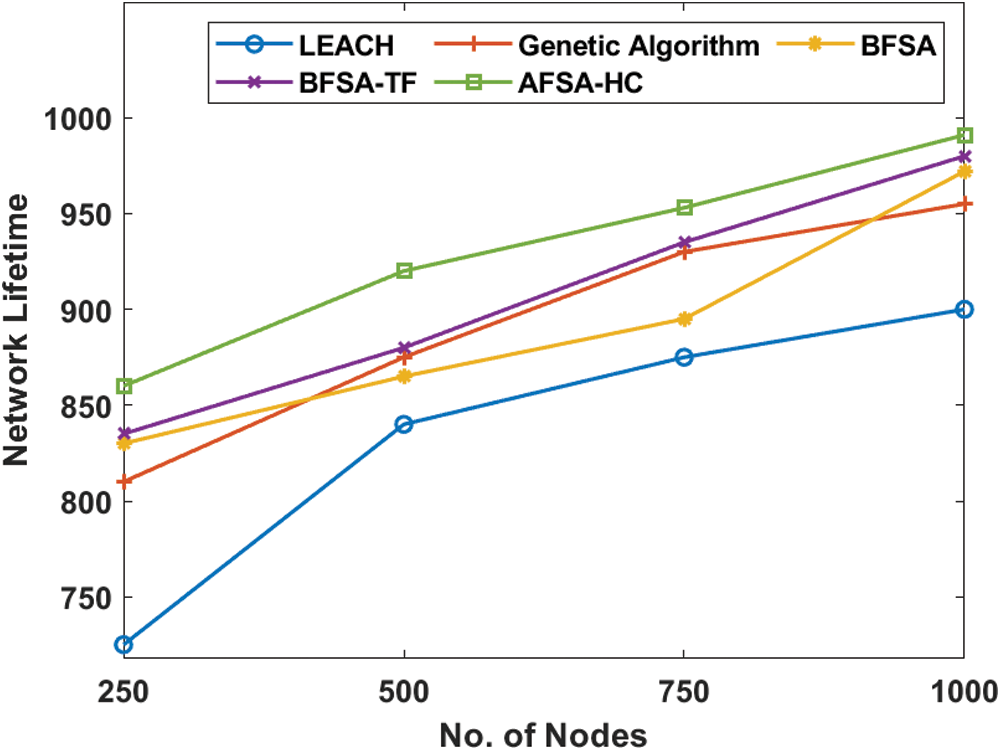
Figure 6: Network lifetime analysis of AFSA-HC with existing models
Fig. 7 shows the study of the AFSA-HC model with the predefined models in terms of average energy consumption, and the efficient clustering model needs to be reduced. The figure showed that less average energy consumption was shown by the AFSA-HC model over all the other techniques under the different number of nodes. For example, the LEACH protocol has achieved the highest average energy consumption of 0.118J under the node count of 250.
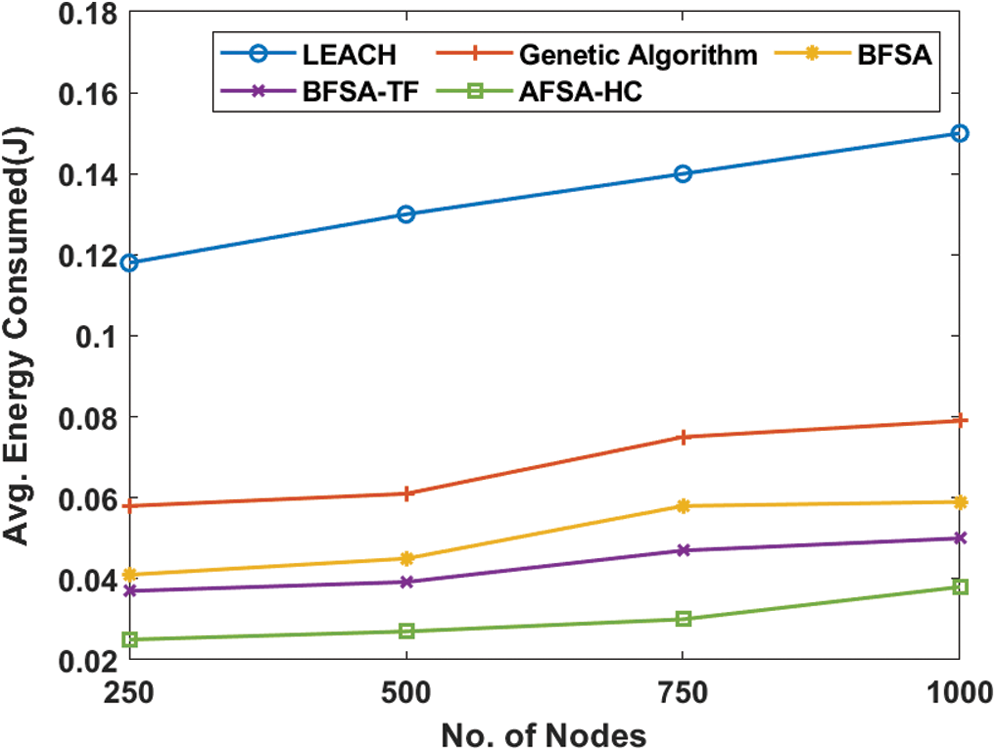
Figure 7: Average Energy Consumed analysis of AFSA-HC with existing models
At the same time, the GA obtained a marginally lower average energy consumption of 0.058J, while the BFSA method also produced a minimum average energy consumption of 0.041J. In addition, by obtaining 0.037J, the BFSA-TF has attempted to demonstrate the efficient average energy consumption. The proposed AFSA-HC system, on the other hand, has recorded a significant minimum energy consumption of 0.025 rounds. These principles have ensured the successful performance of the AFSA-HC technique with respect to average energy consumption.
Fig. 8 shows the AFSA-HC model study with current throughput models relating to the entire number of packets entirely attained by the destination. For an efficient clustering technique, the throughput must be high. The figure showed that under a varying number of nodes, the AFSA-HC model demonstrated optimum throughput over all the other techniques. For instance, the LEACH protocol has achieved a minimum throughput of 12487 under the node count of 250. Similarly, the GA obtained a slightly better throughput of 15876, while the BFSA approach provided an even higher throughput of 21658. Also, by achieving the highest of 23856, the BFSA-TF has attempted to demonstrate productive throughput. However, the highest throughput of 27563 was expressed by the projected AFSA-HC system. These values ensure that the AFSA-HC technique works efficiently in terms of throughput.
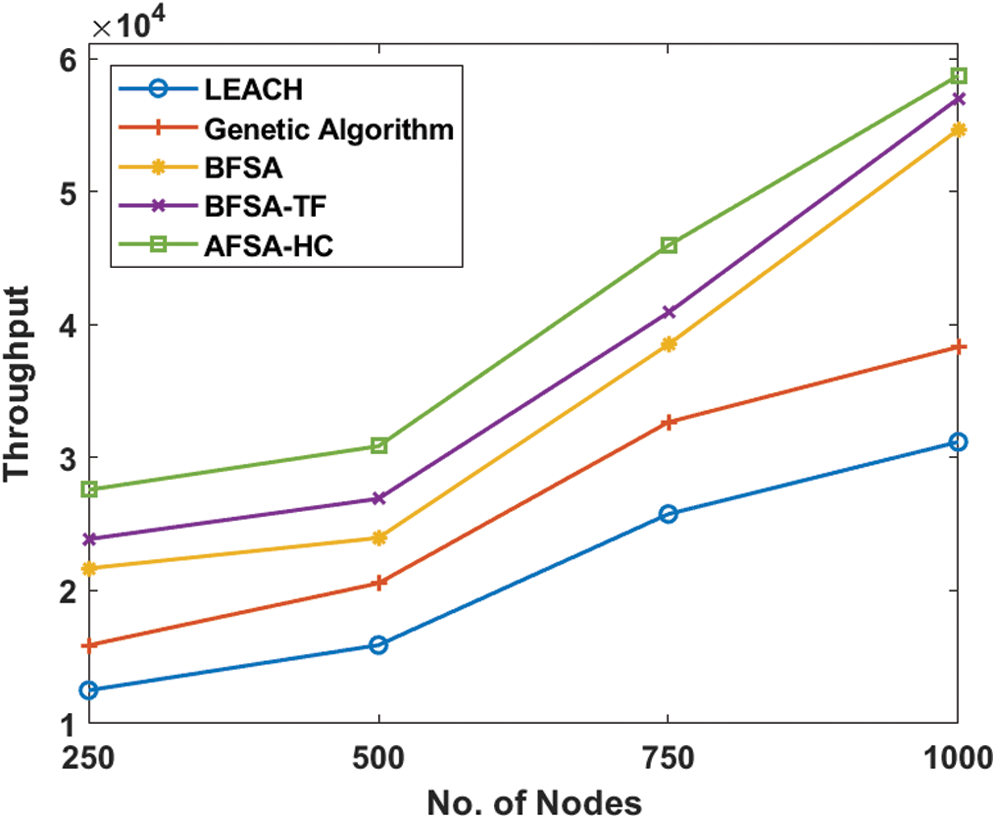
Figure 8: Throughput analysis of AFSA-HC with existing models
Fig. 9 shows the study of the AFSA-HC model with existing packet loss models, and the efficient clustering technique must be tiny. The figure indicated that under the different number of nodes, the AFSA-HC model showed less packet loss over all the other techniques. The BFSA protocol has, for example, achieved the maximum packet loss of 0.96 under the node count of 250. At the same time, the BFSA-TF obtained a small minimum packet loss of 0.955, while the GA system provided an even smaller packet loss of 0.923. The LEACH has also attempted to demonstrate productive packet loss by obtaining 0.9. However, a minimum energy consumption of 0.885 has been extensively demonstrated by the proposed AFSA-HC system. The successful performance of the AFSA-HC technique with regard to packet loss was assured by those values.
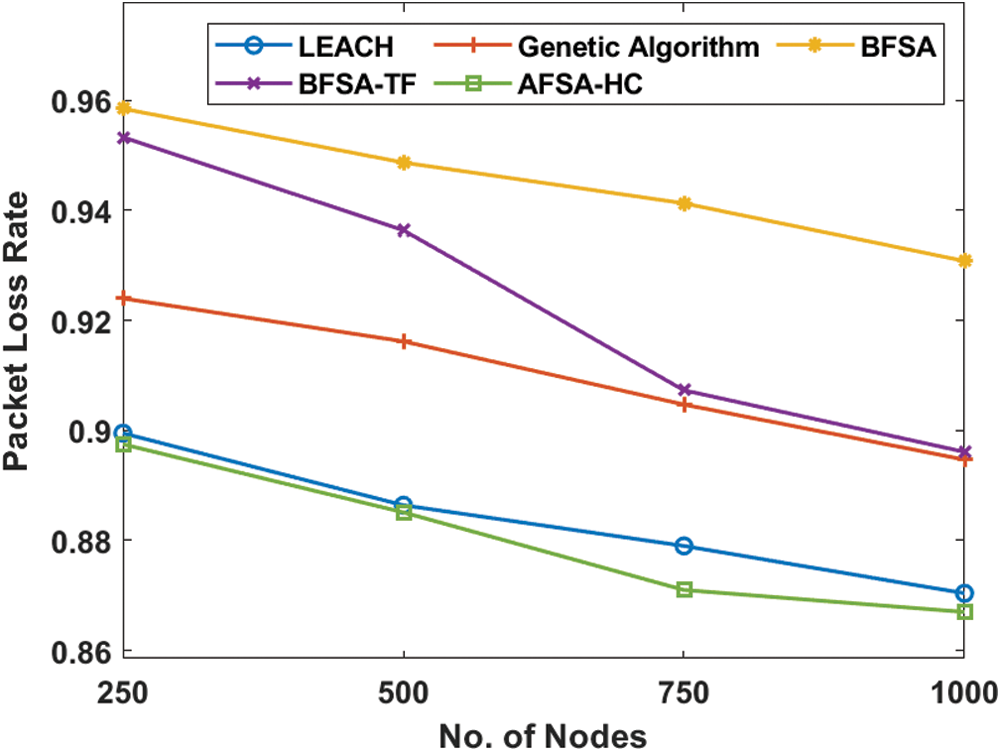
Figure 9: Packet loss analysis of AFSA-HC with existing models
From the above-mentioned tables and figures, it is ensured that the AFSA-HC model has attained maximum throughput, energy efficiency, network lifetime, and network stability with minimum packet loss rate.
An efficient AFSA-HC dependent clustering technique for WMSN performance maximisation has been presented in this paper. Four key processes are involved in the proposed AFSA-HC algorithm in order to optimise network throughput. The AFSA-HC algorithm is performed and builds the clusters once the nodes are deployed and initialised. Then, the deflate algorithm is performed by the CHs to combine data obtained from the CMs. Finally, to reduce the unnecessary amount of data transmission, a hybrid data transmission approach is applied, resulting in optimum throughput and energy consumption. A thorough collection of experiments is carried out and the comparative review shows that the AFSA-HC approach has provided efficient efficiency in terms of energy consumption, throughput, network lifespan, network reliability, and packet loss. In the future, using unequal clustering and routing techniques can improve the performance of the AFSA-HC technique.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. L. Cheng, Y. Zhang, T. Lin and Q. Ye. (2004). “Integration of wireless sensor networks, wireless local area networks and the internet,” in IEEE International Conference on Networking, Sensing and Control, Taiwan, pp. 462–467. [Google Scholar]
2. A. Monsalve, H. L. Vu and Q. B. Vo. (2013). “Optimal designs for IEEE 802.15.4 wireless sensor networks,” Wireless Communications and Mobile Computing, vol. 13, no. 18, pp. 1681–1692. [Google Scholar]
3. B. Lannoo. (2013). “Overview of ICT energy consumption.” Technical Report, Network of Excellence in Internet Science. [Google Scholar]
4. I. Almalkawi, M. Zapata, J. Al-Karaki and J. Morillo-Pozo. (2010). “Wireless multimedia sensor networks: Current trends and future directions,” Sensors, vol. 10, no. 7, pp. 6662–6717. [Google Scholar]
5. E. J. Candes and M. B. Wakin. (2008). “An introduction to compressive sampling,” IEEE Signal Processing Magazine, vol. 25, no. 2, pp. 21–30. [Google Scholar]
6. M. F. Duarte, M. A. Davenport, D. Takhar, J. N. Laska, T. Sun et al. (2008). , “Single-pixel imaging via compressive sampling,” IEEE Signal Processing Magazine, vol. 25, no. 2, pp. 83–91. [Google Scholar]
7. A. Boukerche, Y. Du, J. Feng and R. Pazzi. (2008). “A reliable synchronous transport protocol for wireless image sensor networks,” in Proc. IEEE Symposium on Computers and Communications, Marrakech, pp. 1083–1089. [Google Scholar]
8. D. G. Costa and L. A. Guedes. (2011). “A survey on multimedia-based cross-layer optimization in visual sensor networks,” Sensors, vol. 11, no. 5, pp. 5439–5468. [Google Scholar]
9. J. H. Lee and I. B. Jung. (2010). “Adaptive-compression based congestion control technique for wireless sensor networks,” Sensors, vol. 10, no. 4, pp. 2919–2945. [Google Scholar]
10. M. Chen, V. Leung, S. Mao and M. Li. (2008). “Cross-layer and path priority scheduling based real-time video communications over wireless sensor networks,” in Proc. IEEE Vehicular Technology Conf., VTC Spring 2008, Singapore, pp. 2873–2877. [Google Scholar]
11. S. Pudlewski, T. Melodia and A. Prasanna. (2012). “Compressed-sensing-enabled video streaming for wireless multimedia sensor networks,” IEEE Transactions on Mobile Computing, vol. 11, no. 6, pp. 1060–1072. [Google Scholar]
12. J. Zhang and J. Ding. (2010). “Cross-layer optimization for video streaming over wireless multimedia sensor networks,” in International Conference on Computer Application and System Modeling, Taiyuan, China, pp. 295–298. [Google Scholar]
13. C. M. D. Viegas, F. Vasques, P. Portugal and R. Moraes. (2014). “Real-time communication in IEEE 802.11s mesh networks: Simulation assessment considering the interference of non-real-time traffic sources,” EURASIP Journal of Wireless Communication and Networking, vol. 2014, Article ID. 219, pp. 1–15. [Google Scholar]
14. H. Touil, Y. Fakhri and M. Benattou. (2012). “Energy-efficient MAC protocol based on IEEE 802.11e for wireless multimedia sensor networks,” in International Conference on Multimedia Computing and Systems, Tangier, Morocco, pp. 53–58. [Google Scholar]
15. N. Chilamkurti, S. Zeadally, R. Soni and G. Giambene. (2010). “Wireless multimedia delivery over 802.11e with cross-layer optimization techniques,” Multimedia Tools and Applications, vol. 47, no. 1, pp. 89–205. [Google Scholar]
16. L. Zhou, F. Tan, F. Yu and W. Liu. (2019). “Cluster synchronization of two-layer nonlinearly coupled multiplex networks with multi-links and time-delays,” Neurocomputing, vol. 359, pp. 264–275. [Google Scholar]
17. Z. Tang, K. K. Liu, J. B. Xiao, L. Yang and Z. Xiao. (2017). “A parallel k-means clustering algorithm based on redundance elimination and extreme points optimization employing MapReduce,” Concurrency and Computation: Practice and Experience, vol. 29, no. 20, pp. 1–17. [Google Scholar]
18. X. Yin, K. Q. Zhang, B. Li, A. K. Sangaiah and J. Wang. (2018). “A task allocation strategy for complex applications in heterogeneous cluster-based wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 14, no. 8, pp. 155014771879535. [Google Scholar]
19. J. Wang, Y. Gao, K. Wang, A. K. Sangaiah and S. J. Lim. (2019). “An affinity propagation-based self-adaptive clustering method for wireless sensor networks,” Sensors, vol. 19, no. 11, pp. 2579. [Google Scholar]
20. Z. F. Liao, J. X. Wang, S. G. Zhang, J. N. Cao and G. Min. (2014). “Minimizing movement for target coverage and network connectivity in mobile sensor networks,” IEEE Transactions on Parallel and Distributed Systems, vol. 26, no. 7, pp. 1971–1983. [Google Scholar]
21. J. Wang, Y. Gao, W. Liu, A. K. Sangaiah and H. J. Kim. (2019). “An intelligent data gathering schema with data fusion supported for mobile sink in wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 15, no. 3, pp. 1550147719839581. [Google Scholar]
22. F. J. Kuang, S. Y. Zhang, Z. Jin and W. H. Xu. (2015). “A novel SVM by combining kernel principal component analysis and improved chaotic particle swarm optimization for intrusion detection,” Soft Computing, vol. 19, no. 5, pp. 1187–1199. [Google Scholar]
23. Z. Peng, K. Dong, H. Yin and Y. Bai. (2018). “Modification of fish swarm algorithm based on levy flight and firefly behavior,” Computational Intelligence and Neuroscience, vol. 2018, pp. 1–13, Article ID 9827372. [Google Scholar]
24. J. Chen, Z. Qin, Y. Liu and J. Lu. (2005). “Particle swarm optimization with local search,” in IEEE International Conference on Neural Networks and Brain, Beijing, China, vol. 1, pp. 481–484. [Google Scholar]
25. P. Deutsch. (1996). “Request for comments: 1951.” DEFLATE Compressed Data Format Specification version 1.3, . Available: ftp://ftp.uu.net/graphics/png/documents/zlib/zdoc-index.Html. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |