DOI:10.32604/iasc.2021.013310

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.013310 |  |
| Article |
Hybridized Model with Activity Load Adjusting and QOS for Wi-Fi Network System
1Department of Computer Science and Engineering, E.G.S Pillay Engineering College, Nagapattinam, 611002, Tamil Nadu, India
2Department of Computer Science, Central University Tamilnadu, Thiruvarur 610005, Tamilnadu, India
3Department of Computer Science and Engineering, E.G.S Pillay Engineering College, Nagapattinam, 611002, Tamil Nadu, India
*Corresponding Author: S. Praveen Kumar. Email: praveenkumarkegs@gmail.com
Received: 30 August 2020; Accepted: 06 November 2020
Abstract: The establishment of multi-channel routing systems in WSNs has shown the reliability of the transmission across several channels. Meeting the service quality needs of all the applications is still a challenging task. Various surveys carried out, have suggested for the development of user-oriented Wireless Sensor Network (WSN) architectures. Throughout WSNs, the Optimized Link State Routing (OLSR) and the Adhoc On Demand Vector (AODV) are the multi-way routing systems that exhibit the reliability of the multipath delivery to fulfill the customer service quality requirements. The topology is modified only on requests, by selecting the best route based on the route weights from the source to the destination nodes each time, a loss happens in the topology network. Hence, this study concentrates on the investigation of a heuristic state steering assisted separation vector of the OLSR and the AODV (OLSR-AODV) withload adjusting and quality of service aspects, for the WI-FI network system. Further, the estimated set of OLSR-AODV has been hybridized to address the problem of traffic control. The nature of the load adjusting algorithm over the multiple path of the routing protocol together with its mathematical computations have been concentrated on in this research work. Compared with the Mobile Adhoc Networks (MANET) and the CLAB algorithm, the OLSR-AODV is the routing protocol that reduces the traffic disturbances between the various nodes.
Keywords: Wireless Sensor Network (WSN); optimized link state routing protocol; ad hoc on-demand distance vector; congestion control; load management
WSNs can revolutionize the way in which knowledge can be obtained and communicated with the physical world for a number of applications. Energy power-aware routing is proposed [1] in the OLSR protocols where several current WSNs have been configured for special purposes. The absence of regular operations and sensor data representations can be used by the software or the utilities for the high-level. Energy efficient variations of the OLSR protocols consist of multiple sensor nodes that are capable of detecting the ambient data [2]. AODV, OLSR, Temporally Ordered Routing Algorithm (TORA), Dynamic Source Routing (DSR) and Destination Sequenced Distance Vector (DSDV) routing protocols [3] are compared in the mobile ad-hoc networks. In this study the collected data will be sent to the baseline which actually passes it on to the WSN observatory. Here, it is considered as a dynamically programmed wireless network with a network clear of maintenance that indicates a common Wireless Sensor Network. Jain et al. [4] has discussed the energy level accuracy and the life time enhancements in the mobile ad-hoc networks using the OLSR. Stephan et al. [5] proposed a typical wireless sensor network that consists of a sensor, a controller and a communication system. Each WSN has a sensor node which is denoted as a Node (N1, N2……… N3), and a sensing region as shown in Fig. 1. All sensing regions comprise a single Base Station (BS) for the communication of the data contents.
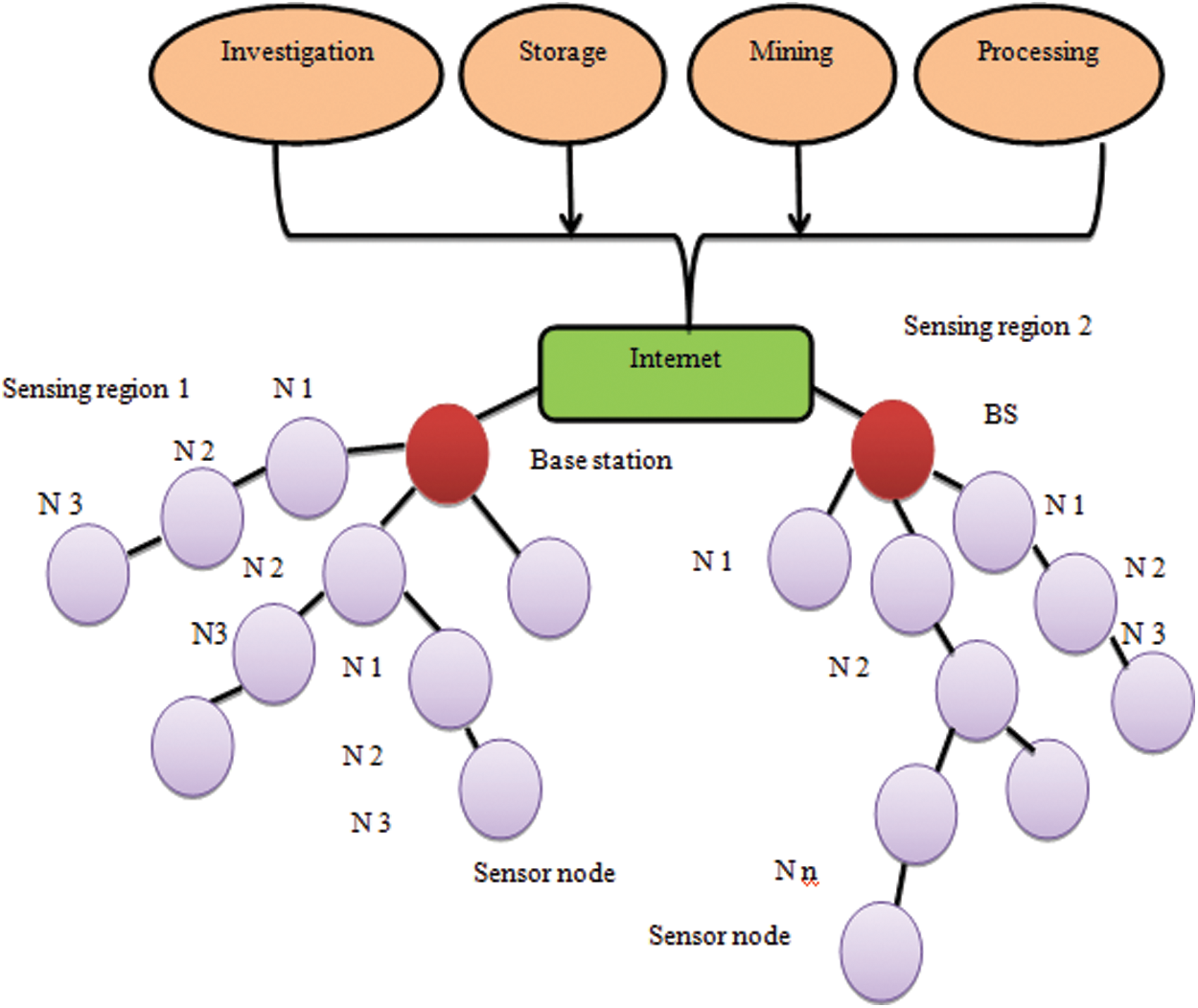
Figure 1: A typical WSN with a sensor, a controller and a communication system
Service-oriented implementations [6] have been proposed here, networks with varied performance metrics, such as latency, delay, weight balancing and efficiency have been analysed together with the analysis of the service structures and the Quality of Service (QoS) parameters correlated with these services have been accomplished. Chettibi et al. [7] proposed a service-oriented WSN and it differentiates the current network levels. Huang et al. [8] proposed a robust multi-way routing system which significantly reduces the downstream traffic and meets the QoS criteria, it further ensures secure routes between the source node and the destination node. Behzad et al. [9] discussed the route assessment strategies of the individual nodes, it further discusses the ability of its neighbours in functioning in compliance with the efficiency of the road. The architecture of the wireless sensor node [10] has been proposed here, it consists of four main modules; the sensor, processor, network and power supply modules as shown in Fig. 2. Aggarwal [11] discusses the performance analysis of the AODV, the DSDV and the DSR in MANETs with various conditions including the node or the path malfunctions, node instability, addition of new nodes or bandwidth modifications.
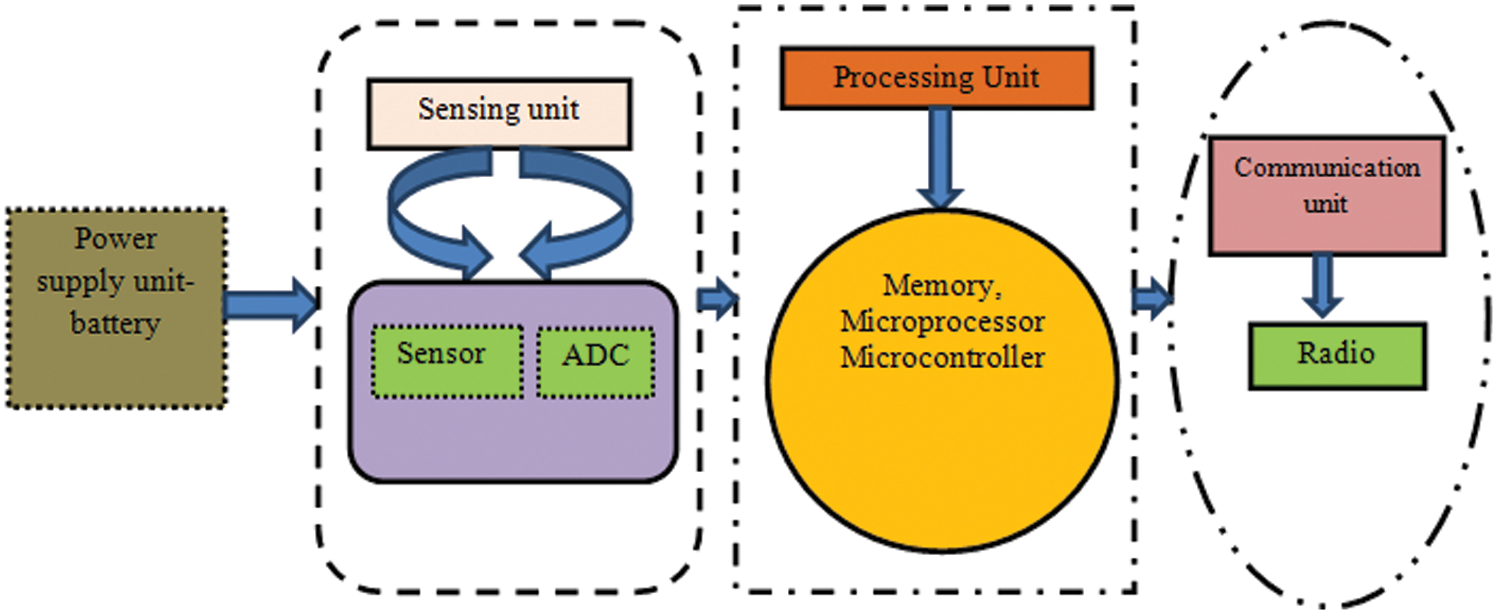
Figure 2: Architecture of Wireless Sensor Node
Booranawong et al. [12] discussed Energy consumption and the control response evaluations of the AODV routing in WSNs for building-temperature controls and further indicated that the rapid loss of the links or nodes will interrupt the network operation; reconstruction of the overall network link is therefore extremely important and must be achieved on a minimum amount of time and overhead in real-time.
The service-oriented design over the WSNs is typically not used by most of the current Multipath Routing Protocols. Aashkaar et al. [13] proposed an Enhanced energy efficient AODV routing protocol for the MANET and suggested that the Link-disjoint Multi-Path Routing is a good idea to use more robust protocol architecture and resource management to handle any client as a service function. A modified AODV protocol [14] based on the node mobility serviced WSNs will prohibit the routing messages from being sent to the arbitrary nodes. It is because of the geographical condition near the Base Station (BS) or the other device factors that some nodes of each of the sensor might be overrun by a broad congestion load. Ting et al. [15] insists that the sharing of significant volume of traffic over the WSNs is a core problem in the architecture of service-oriented WSNs as a consequence of improving the performance of WSNs. Further, to overcome the entire load and traffic problems, the OLSR-AODV (OADV) has been hybridized over the multiple path of the routing protocol and it has been mathematically derived in this research. The result of this hybridized model has been found to extend the life of the network and the number of live nodes. The rest of the paper is organised as follows: Section 2 reviews the related work, Section 3 insights the proposed OLSR-AODV hybridised model, Section 4 elaborates the mathematical model for green energy consumption and workload management with activity load adjustments and QoS for Wi-Fi network systems, Section 5 portrays the findings of the study related to the OLSR-AODV hybridised model. Finally, the paper concludes the research work and discusses the future scope.
Many research works have been carried out in the concerned field; Li et al. [16] suggested that the WSNs demonstrate the reliability of traffic delivery on the multipath so as to meet the user’s quality of service criteria through the current multi charging schemes. To analyze and identify a set of connection disjoint routes from all the accessible roads, a metric evaluation has been suggested. Considering the efficiency, congestion management and multi-path protection parameters, an effective and failure resistant routing scheme must be built to provide a secure and service-driven routing scheme. A load management and congestion reduction algorithm has been introduced in a way that it can be tailored according to the demands of the multipath. The packets are divided into different segments by using a threshold sharing algorithm that can be sent to the destination via several ways based on the route vacancies. Simulations demonstrate the efficiency of the flexible and secure routing framework for the various load balances. Schweitzer et al. [17] discussed about the MANET (mobile ad hoc network routing protocols) which appears to be susceptible to various attacks. Different solutions for multiple types of attacks have been suggested, but these strategies sometimes lack routing performance or network congestion. An essential assault of the Denial of Service (DoS) against the Optimized Link State Routing protocol (OLSR), defined as the Node Isolation Assault, happens when the topological information of the network is abused by an intruder capable of isolating the target from the rest of the network. This article proposes a new approach for protecting the OLSR protocol from node the isolation assaults by using the same attack tactics. Yuang et al. [18] reported the control of involvement in communications between all nodes in the network with the help of hierarchical and structured topology processing algorithm (CLB-AODV). The aim is to guarantee that the weighted paths between the source and the destination nodes are the best possible way in case of network failure; the topology here is modified only on requests. This algorithm is based on the AODV dynamic routing strategy for controlling the routing burden between the nodes, instead of a new protocol for dynamically controlling the topology. Simulated tests show that the number of live nodes and the average routing loads are greater than some of the more efficient recent algorithms. AlShahwan et al. [19] proposed an Optical packet switching (OPS) approach specifically planned for the data-centered IP over the wavelength multiplexing (WDM) network and the internet that acts as a leading potential optical network technology. However, such OPS technology possesses significant challenges for the transport and the quality-of-service (QoS). A new Optical Coarse Packet Switching (OCPS) paradigm is proposed to circumvent the OPS limitations that use in-band per-bomb switching in order to achieve high per formative performance and differentiated services by advocating the traffic control enforcements. The in-band header/payload modulation technique describes the Optical coarse Packet Switched IP over WDM NETwork (OPSINET) architecture and provides details of the operations of the border routers, OLSRS, and Generalized Multi-Protocol Label Switching (GMPLS) controls.
3 OLSR-AODV Hybridized Model with Activity Load Adjusting and QOS for WI-FI Network System
Consider the N-node WSN, as a relation between the N-nodes, and the graph H (A, S), where A =  is a node array as shown in Fig. 3 and the set S of edges of the graph is given in Eq. (1)
is a node array as shown in Fig. 3 and the set S of edges of the graph is given in Eq. (1)

The 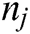 node spectrum of the transmitting and the carrier sensing attribute is represented as
node spectrum of the transmitting and the carrier sensing attribute is represented as 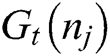 and
and 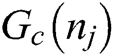 . For
. For 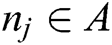 ,
,  if
if 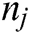 is within the range of transmission of
is within the range of transmission of  as well as the edge
as well as the edge 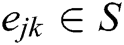 . The Node seven is represented as N1…….. N7. The path of transmission between each of the nodes is given as E1….. E6. The Routing protocol is represented as R = {P1, P2}, which refers to the total communication between each of the protocols. The representation of P1 and P2 is given as P1 = {E3, E4}, P2 = {E5, E6} as shown in Fig. 3.
. The Node seven is represented as N1…….. N7. The path of transmission between each of the nodes is given as E1….. E6. The Routing protocol is represented as R = {P1, P2}, which refers to the total communication between each of the protocols. The representation of P1 and P2 is given as P1 = {E3, E4}, P2 = {E5, E6} as shown in Fig. 3.
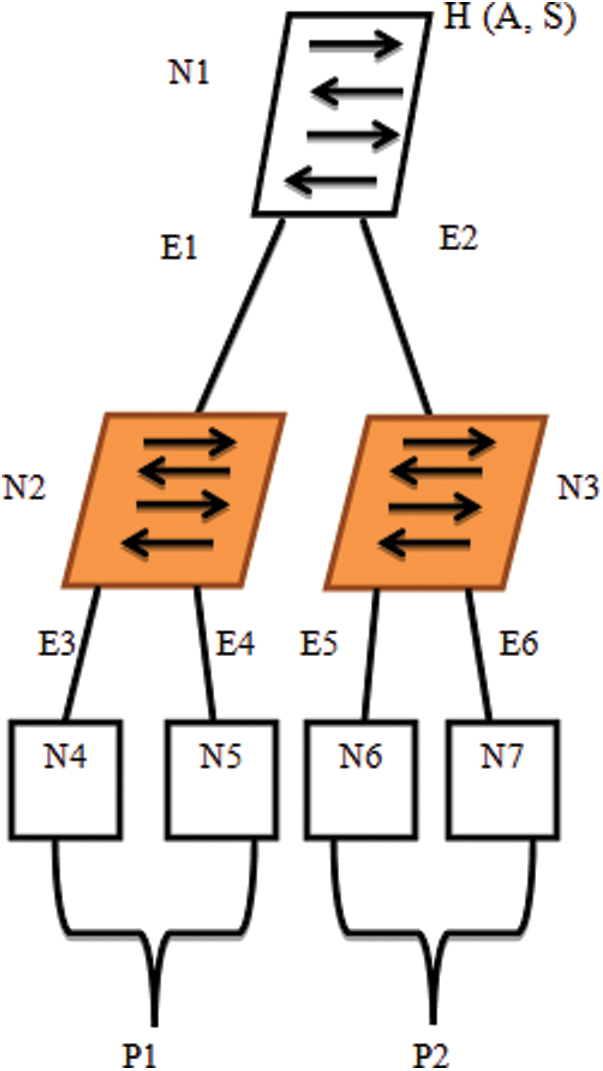
Figure 3: Network Topology and the data transmission between each node
The following necessary steps should be followed to start with the new model.
Step 1: Path  denotes the number of edges from
denotes the number of edges from  (source) to
(source) to 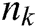 (destination).
(destination).  includes all the links from
includes all the links from  to
to  . The intermediate nodes are known here except for the source and the destination nodes. If there are M paths from node
. The intermediate nodes are known here except for the source and the destination nodes. If there are M paths from node 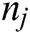 to
to  then the multipath can be represented as shown in Eq. (2)
then the multipath can be represented as shown in Eq. (2)

Step 2: Path Distance (PD)  represents the number of edges in the path.
represents the number of edges in the path.  . The shortest distance between
. The shortest distance between  and
and  on a path is shown in Eq. (3).
on a path is shown in Eq. (3).

Step 3: In order to describe the quantitative significance parameter for a connecting node, the Significance Degree ID (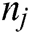 ) is provided. For example, if a mid-node appears in only one multipath path, then ID (
) is provided. For example, if a mid-node appears in only one multipath path, then ID ( ) = 1. This represents the total number of times it has been used in the multi paths. If two multi-path paths exist, then ID (
) = 1. This represents the total number of times it has been used in the multi paths. If two multi-path paths exist, then ID ( ) = 2. Then ID (
) = 2. Then ID ( ) can be defined as shown in Eq. (4).
) can be defined as shown in Eq. (4).

It is used by the function ( ,
, 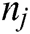 ) to determine whether or not the node
) to determine whether or not the node  exists in
exists in  multi track. The outcome is one if this exists, and the consequence becomes zero.
multi track. The outcome is one if this exists, and the consequence becomes zero.
Step 4: C (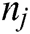 ) describes how close the node is to its neighbours. Here we use a C (
) describes how close the node is to its neighbours. Here we use a C ( ) coverage chance to represent the degree of connectivity. The degree of connectivity is represented in Eq. (5).
) coverage chance to represent the degree of connectivity. The degree of connectivity is represented in Eq. (5).

 Represent the number of edges from the node
Represent the number of edges from the node 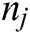 to
to 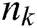 in the path
in the path  . The distance is not linked to the connection delay, just as the measurement hop count. The cost of each path, SD (t) at time (t) is calculated as an average of the nodes weight along the path, for any possible path between the transmitting and the target nodes, is derived in this algorithm.
. The distance is not linked to the connection delay, just as the measurement hop count. The cost of each path, SD (t) at time (t) is calculated as an average of the nodes weight along the path, for any possible path between the transmitting and the target nodes, is derived in this algorithm.

SD (t) is the possible path cost between the source and the destination nodes. N is the overall number of route nodes.  is the sum of the nodes along the path and it is calculated as the sum of weights.
is the sum of the nodes along the path and it is calculated as the sum of weights.
3.1 Traffic Control Detection Method
Detection of traffic is a technique to detect the buffer and the wireless channel load congestions. The multi-way congestion control system includes three major steps: 1) Identification of congestion; 2) Congestion regulation and notification; and 3) Cancelation or load correction of congestion. In this sense, an effective method of congestion management has been suggested that plans for the load deliveries in several paths for reducing the congestion on the multipath. In this way it reduces the packet losses and enhances the traffic’s efficiency, safety and reliability. The congestion warning scheme thus introduced may provide a notice of the demand ratio and congestion during its occurrence.
Traffic control detection method:
Input: 
Output: Adjust rate according to TRAFFIC
TRAFFIC Detection ();
For  ← 1 to M do
← 1 to M do
Special treatment of the first element of lines i;
If 0.85 ≤  then
then
Set traffic Level (TRAFFIC_LEVEL,0);
Else if 0.75 ≤ 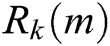 ≤ 0.85 then
≤ 0.85 then
Set traffic level (TRAFFIC_LEVEL,1);
Else if 0.4 ≤ 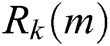 ≤ 0.75 then
≤ 0.75 then
Set traffic level (TRAFFIC_LEVEL,2);
Else
Set traffic Level (TRAFFIC_LEVEL,3);
Packet traffic 2 Hello(); Send Hello Message();
End
Each packets transmitted from one node that is from the source to the destination node, its size, simulation time, simulation area, transmission range, number of sensor nodes used in the data transmission has been clearly explained in Tab. 1.
Table 1: Simulation parameters including packet rate and size

3.2 Mathematical Model for Load Adjustment Using OLSR- OADV Method
The total energy and the load adjustment control for the Wi-Fi network has been clearly explained in this method. 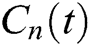 is the percentage of the amount of the total energy used to send and receive packets to their original capacity, and this is shown in Eq. (7).
is the percentage of the amount of the total energy used to send and receive packets to their original capacity, and this is shown in Eq. (7).

 is the total energy consumed by the packets transmitted in the time t,
is the total energy consumed by the packets transmitted in the time t,  is the total energy consumed by the packets received in time t.
is the total energy consumed by the packets received in time t.  is derived in Eq. (8).
is derived in Eq. (8).

 Represent the energy used by a node (n) to send any packet at time (t) and the calculation time is shown in Eq. (9).
Represent the energy used by a node (n) to send any packet at time (t) and the calculation time is shown in Eq. (9).

 is the energy used by an amplifier to send a bit.
is the energy used by an amplifier to send a bit.  is the distance between the transmitter node and the receiver node,
is the distance between the transmitter node and the receiver node,  is the transmission of packets in bits. While
is the transmission of packets in bits. While  receives data from the network life to node n at all times (t) that denotes the total energy consumed and it is shown in Eq. (10).
receives data from the network life to node n at all times (t) that denotes the total energy consumed and it is shown in Eq. (10).

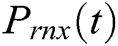 Power consumed by the receiver node at time (t) is given in Eq. (11).
Power consumed by the receiver node at time (t) is given in Eq. (11).

 represents the electronic energy per bit for the receiving packets.
represents the electronic energy per bit for the receiving packets. 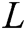 is the length of the receiving packets in bits. At the beginning of the algorithm, each node transmits their identity and their weight to the other nodes, just once, throughout the network’s entire lifetime. Each node receiving the Hello message is treated as a neighbour, constructs its routing and neighbouring table and sends and receives the packets immediately through a link that exists between the source and the destination nodes. If there is no path from the source to the target node, or if the topology shifts due to the lack of connections between the source and the target nodes, it would demand for the need of topology maintenance. A source node transmits a Routing Request (RREQ) that is updated and inserted to include the Path Cost (PC) at any point (t) before transmitting it into the other nodes, the source node adds its own load in the PC field in the RREQ. The transmission of a packet is achieved by the AODV model as shown in Fig. 4. A source node transmits the packet of data which involves both the destination address as well as the hop count with the path cost for each packet of the data as shown in Fig. 5. It includes the PC before transmitting it into the other nodes, the source node adds its own load t in the PC field in the RREQ.
is the length of the receiving packets in bits. At the beginning of the algorithm, each node transmits their identity and their weight to the other nodes, just once, throughout the network’s entire lifetime. Each node receiving the Hello message is treated as a neighbour, constructs its routing and neighbouring table and sends and receives the packets immediately through a link that exists between the source and the destination nodes. If there is no path from the source to the target node, or if the topology shifts due to the lack of connections between the source and the target nodes, it would demand for the need of topology maintenance. A source node transmits a Routing Request (RREQ) that is updated and inserted to include the Path Cost (PC) at any point (t) before transmitting it into the other nodes, the source node adds its own load in the PC field in the RREQ. The transmission of a packet is achieved by the AODV model as shown in Fig. 4. A source node transmits the packet of data which involves both the destination address as well as the hop count with the path cost for each packet of the data as shown in Fig. 5. It includes the PC before transmitting it into the other nodes, the source node adds its own load t in the PC field in the RREQ.
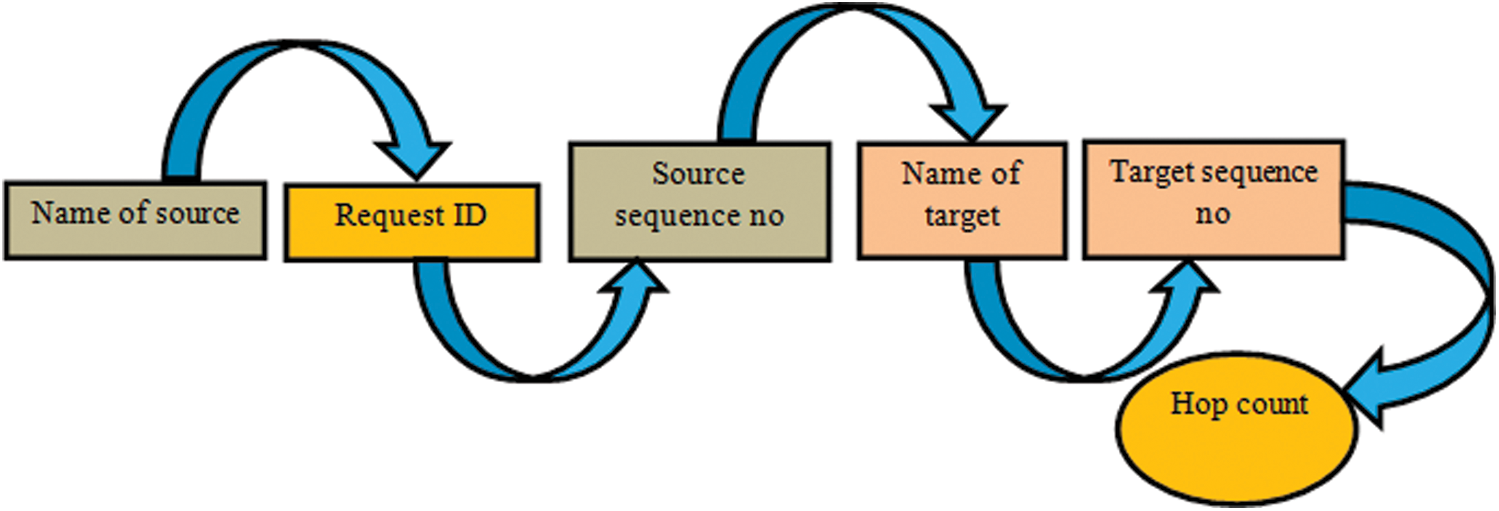
Figure 4: A source node transmits RREQ by AODV model
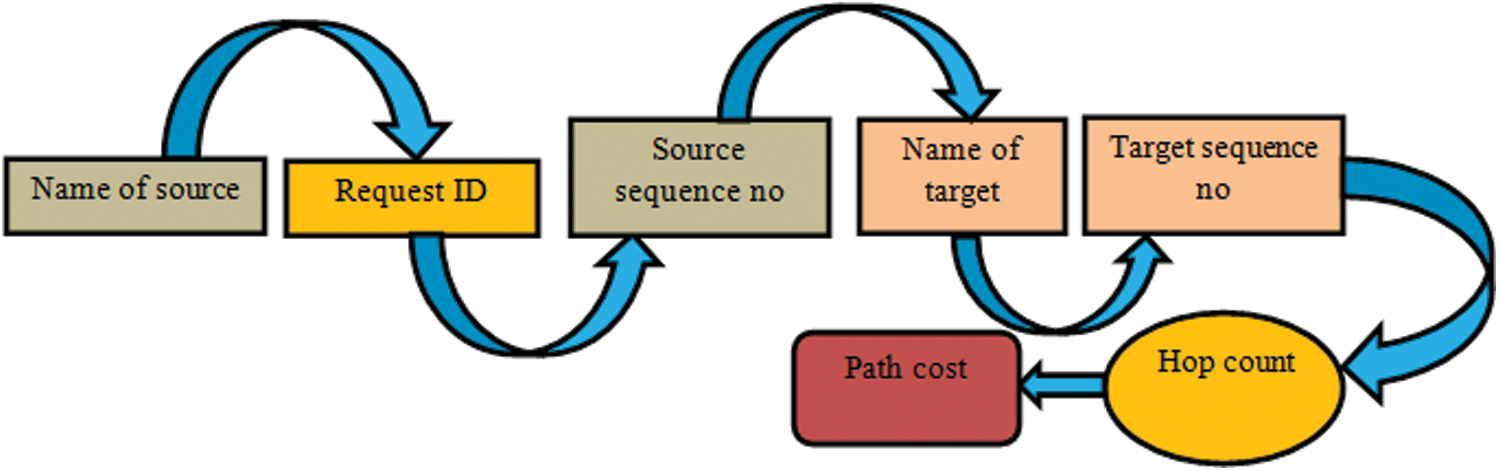
Figure 5: A source node transmits RREQ by OLSR- AODV model
3.3 Pseudocode OLSR-AODV Model
Input: Starting energy  , Total Transmitting Energy
, Total Transmitting Energy 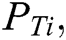 Total receiving energy
Total receiving energy 
Output: 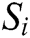 represent the each nodes topology
represent the each nodes topology 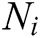
1. The information is collected
2. 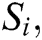 neighbour table is build
neighbour table is build
3. If  then
then
a. Get route ()
b. 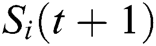 , neighbour table is build
, neighbour table is build
End if
4. Function news is collected
a. Broadcast node ID i and 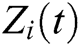 at
at 
b. Build neighbour list 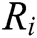
End function
5. Function get route
a. Broadcast 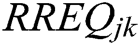 with
with 
b. If  receive
receive  then
then
a. Receive 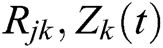 from
from 
ii. 
c. else + 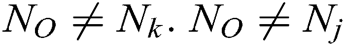 DO
DO
(i) If then
then
Reply  =
= 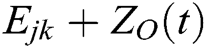
(ii) Else broadcast 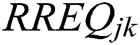 with
with 
d. End for End function
6. Choosing of route for function
FOR  ·
· DO
DO
(i) If OR (
OR ( =
= 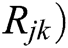
AND ( then
then 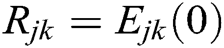
(ii) End if
End for
End function
In relation to, the total network residual energy at the end of the simulation process, the sum of the living nodes and the accumulated network simulation duration, the effectiveness of the proposed OLSR-AODV is compared with AODV and Performance Enhanced (PE)-AODV algorithms.
Pseudo code used in this proposed OLSR-OADV method and its related terms have been explained in Tab. 2. The number of nodes used in this method has been represented as  to
to 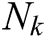 and the path cost of each of the nodes have also been provided. The total energy consumed and the maximum transmitting and receiving power for each of the nodes have also been calculated.
and the path cost of each of the nodes have also been provided. The total energy consumed and the maximum transmitting and receiving power for each of the nodes have also been calculated.
Table 2: Expansion of all terms used in OLSR- OADV model

Suppose that 60 sensor nodes are randomly used in a 2000 m by 2000 m square area. The radio transmission range for each of the node and the sensing range of the carrier are found to be 140 m. The simple parameters of the virtual network are shown in Tab. 1. The data rate is 1 Mb/s and the lifetime of each trail is 100 s. The data delivery ratio, the summing time and the speed based performance metrics are measured and each of the setting has been simulated in 50 tests. This number remains as almost 0 number of nodes until the time of 210 s has been reached, when the energy of the AODV path and the AODV begins to lose, the time observed would be 170 s, while the former nodes would be lost in the former. An OLSR-AODV algorithm exhibits a number of dead nodes during the period of simulation. Comparison of the speed and packet of the data delivery fraction between the load balancing multipath, OLSR, Communication Load Balanced (CLB)-OADV, and OLSR-OADV has been shown in Tab. 3. Each packet of the data transmitted and received with a particular speed has been measured in m/s.
Table 3: Comparison of speed of Load balancing multipath, OLSR, CLB-OADV, OLSR-OADV

The typical, OLSR, CLB-OADV, and OLSR-OADV methods observe a contrast in the packet latency based attribute. It is obvious from Tab. 4 that the OLSR-OADV shows a delay of up to 5 percent lower than that of the OLSR, CLB-OADV. CLB-OADV schedules the weight on the routes with an increase in the path vacant rate, which leads to a decrease in the traffic control for the data transmissions, the delays in these simulation processes are lowest when compared with the OLSR, CLB-OADV.
Table 4: Speed vs. end to end delay of OLSR, CLB-OADV, OLSR-OADV

Fig. 6. Shows the comparison of the load balancing multipath, the OLSR, the CLB-OADV, and the OLSR-OADV methods with the packet of data transmission and receiving speed calculations, and it has been found that the OLSR-OADV performs better than the other methods.
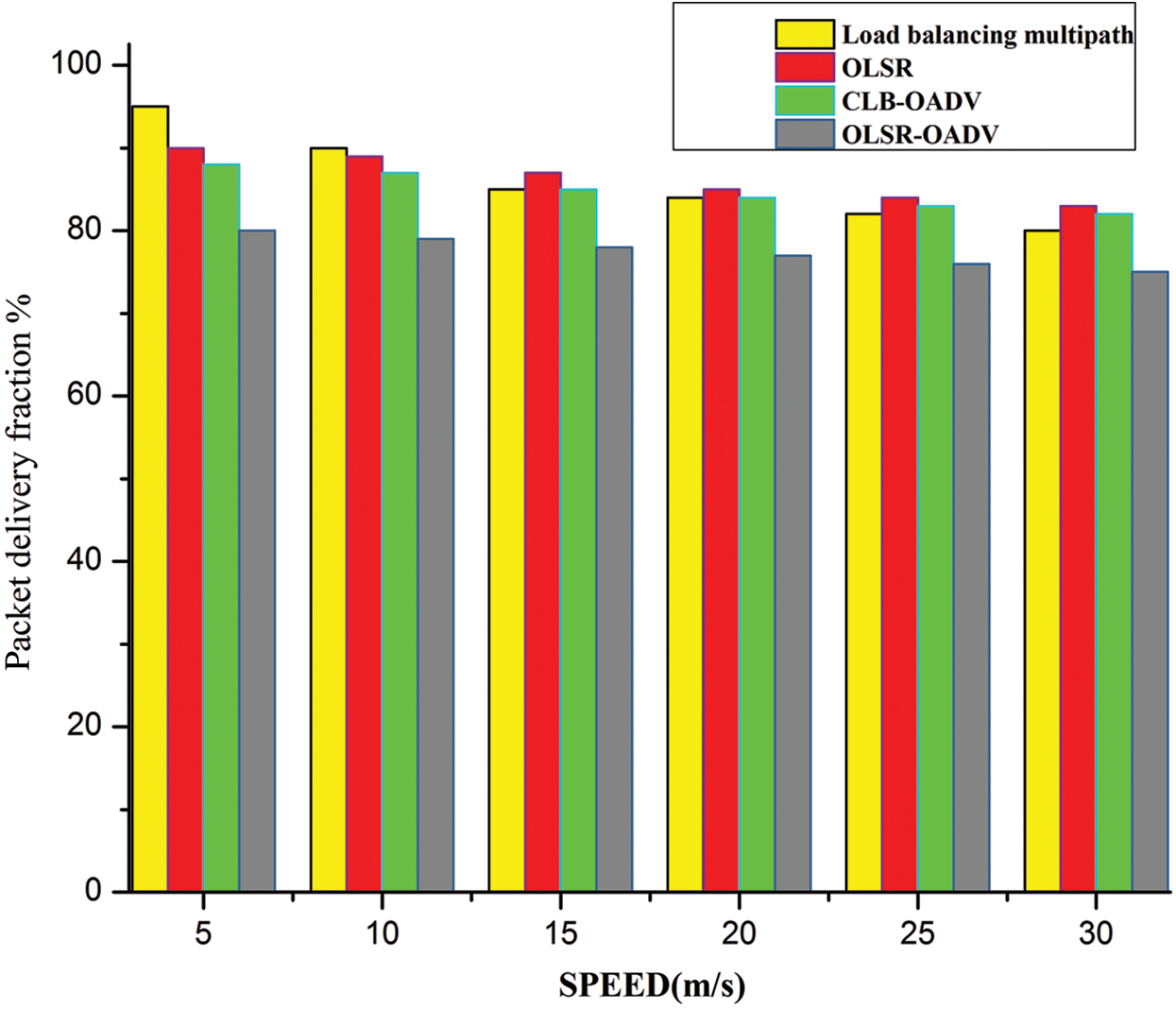
Figure 6: Shows the comparison of the load balancing multipath of OLSR, CLB-OADV, and OLSR-OADV methods
OLSR-OADV shows a delay of up to 5 percent lower than the OLSR and the CLB-OADV, as shown in Fig. 7. CLB-OADV periods the weight on routing with a larger path vacant rate, which leads to a decrease in the traffic control for the data transmission, the delays in these simulation processes are lowest compared to OLSR and CLB-OADV. The total throughput of these three methods have been compared and portrayed in Tab. 5.
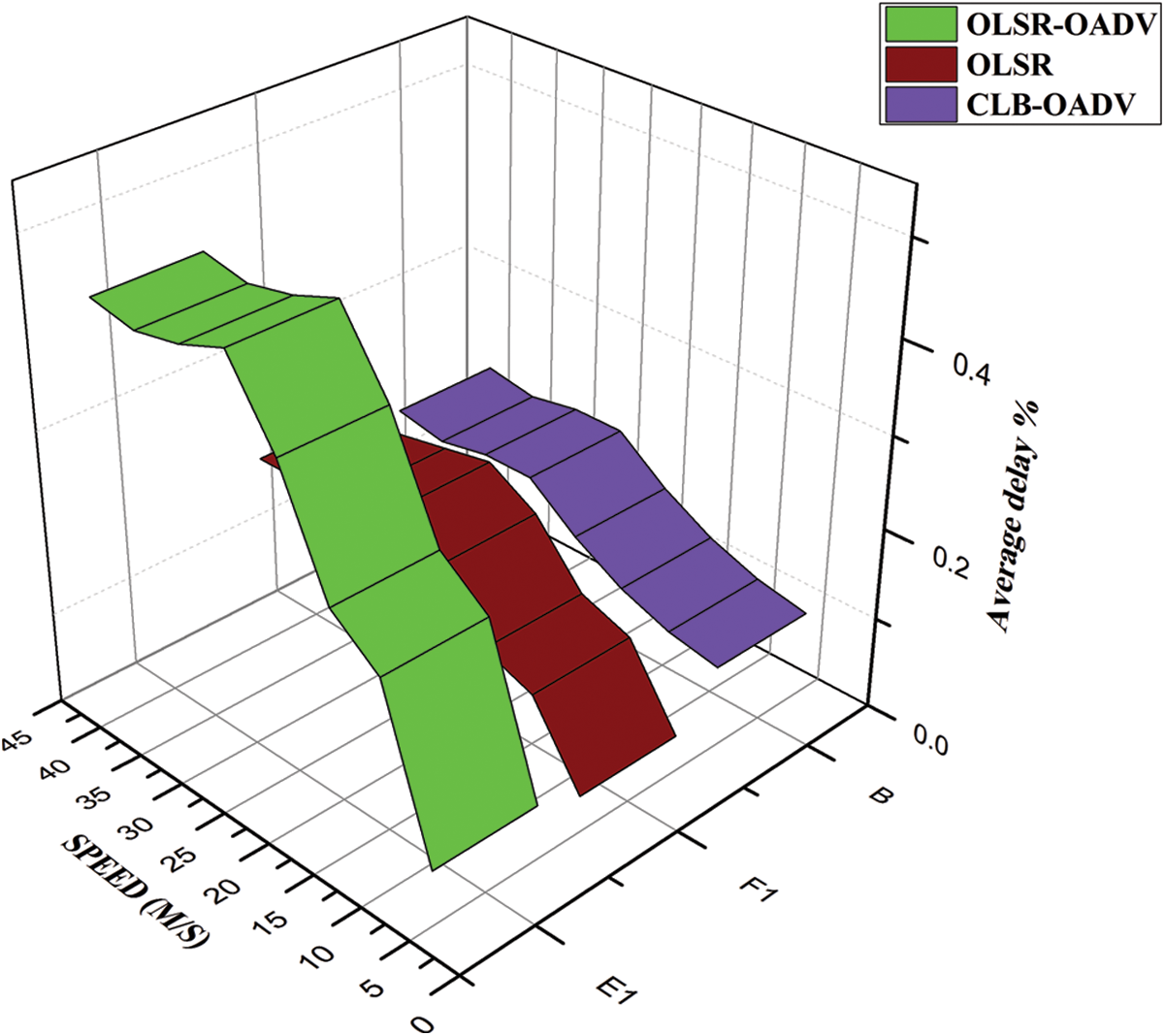
Figure 7: Comparison of speed and end to end delay of OLSR, CLB-OADV, OLSR-OADV
Table 5: Comparison of Throughput and average delay of OLSR, CLB-OADV, and OLSR-OADV

Fig. 8 shows the throughput of the three routing protocols. CLB-AODV has a higher performance of up to 40 percent over the other two protocols. The load balancing model has been achieved and a significant improvement in the efficiency has been accomplished. Comparison of the average delay of the three methods namely OLSR, CLB-OADV and OLSR-OADV has been shown in Fig. 8.
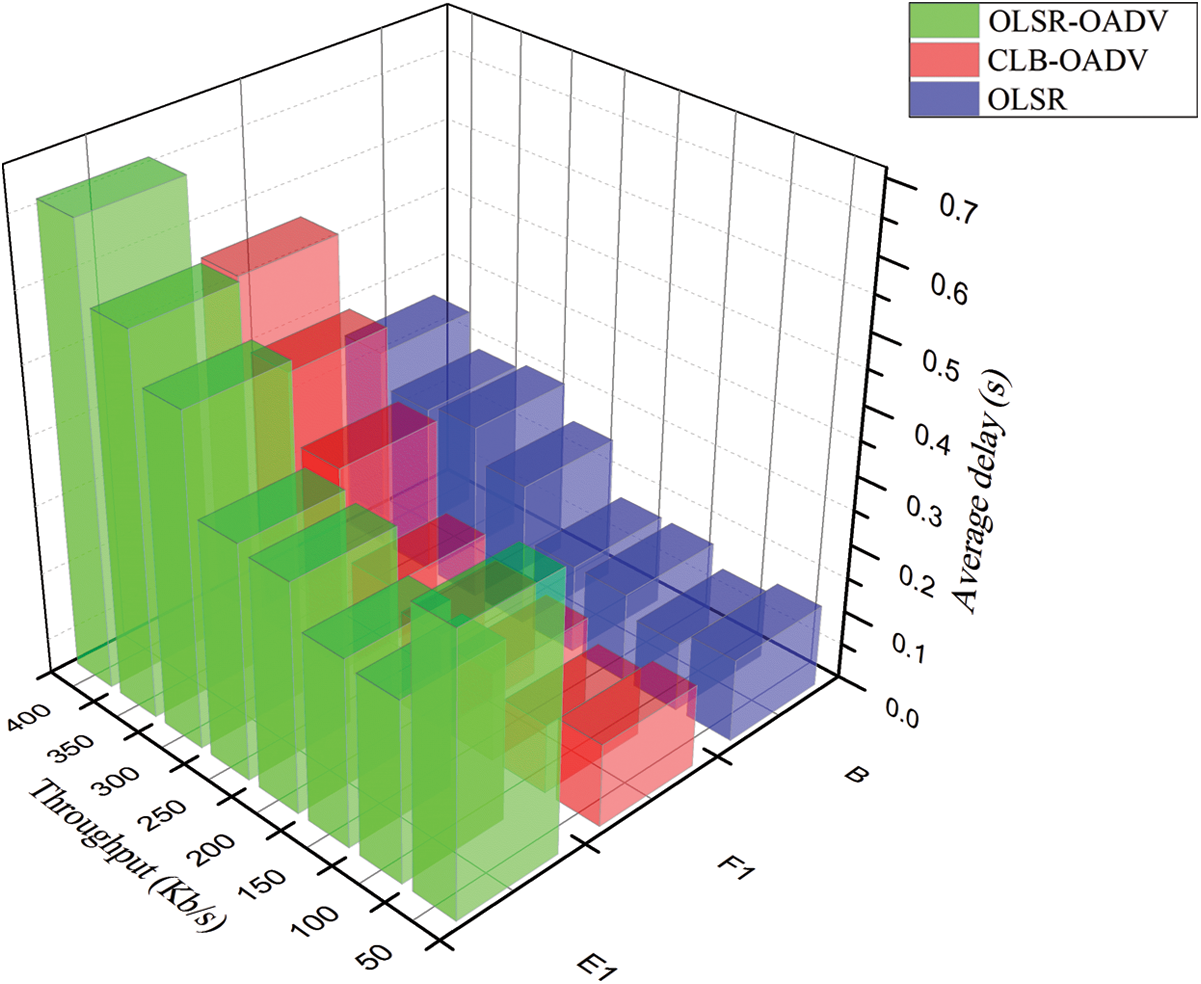
Figure 8: Comparison of throughput & average delay of OLSR, CLB-OADV, and OLSR-OADV
The CONGEST LEVEL has been adapted to the Path Vacant ratio in the data transmission process. The Routing Scheme CLB-AODV can send additional packets to those empty routes. The total number of nodes in the given time for the three protocols has been portrayed in Tab. 6.
Table 6: The total number of nodes of the three protocols OLSR, CLB-OADV, and OLSR-OADV

In Fig. 9, the simulation results of the OLSR-AODV algorithm have been found to be better for two reasons: first, only one Hello message and, on request, RREQ is transmitted on each of the nodes with a maximum transmission.
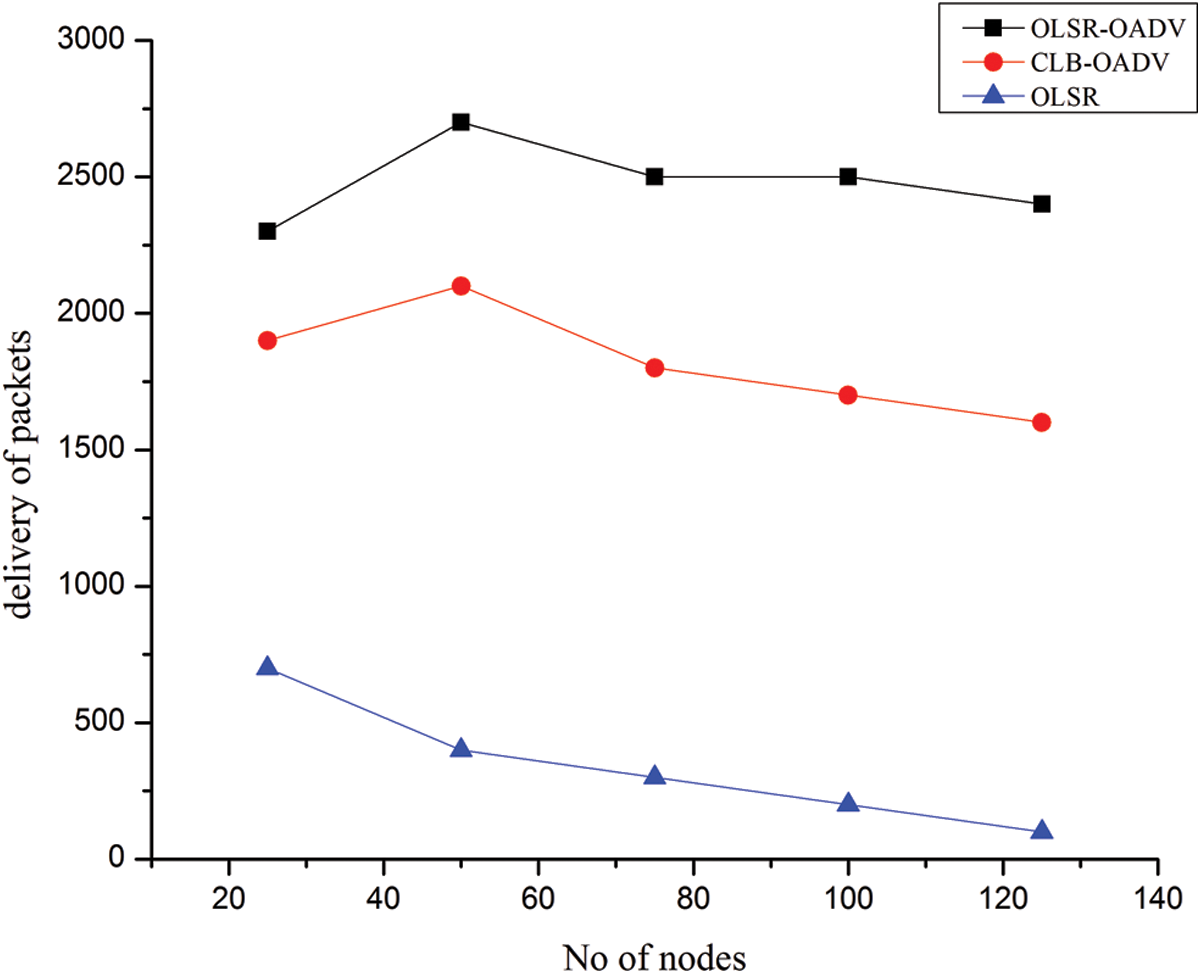
Figure 9: The total number of nodes with time of three protocols
The second is that, the weights of the nodes are dependent on the level of contact, this assures the longevity of the nodes and ensures appropriate regulations in the topology at specified intervals.
This study provides information regarding the OLSR-OADV modelling. The OLSR-OADV uses a different routing control to reduce the traffic collision between the nodes, that is, it implements appropriate traffic controls and load adjustment mechanisms. The OLSR-OADV is a flexible load-balancing multipath routing protocol that has been developed for addressing the limitations of the current multi-path routings. WSNs utilize the load balancing and the congestion control systems for the safe delivery of the data packets. The packets are supplied over the multipath in the OLSR-OADV using a proper and a flexible system that fixtures the node’s applicable capabilities and provides the optimization alternatives that are not yet available in the existing schemes. Through the way of the secret source distribution system, the OLSR-OADV significantly improves the flexibility in handling the downstream traffic. The OLSR-OADV adopts a congestion management adaptive system, which is effective even if node or link failure occurs frequently. Future study would concentrate on the mechanisms of minimizing the time taken to measure the PC, further, methodologies for evaluating the accessible routes between the source and the destination nodes would be identified.
Funding Statement: The author(s) received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. Benslimane, R. El Khoury, R. El Azouzi and S. Pierre. (2006). “Energy power-aware routing in OLSR protocol,” in Proc. of IEEE Int. Conf. on First Mobile Computing and Wireless Communication, New York, USA, pp. 14–19. [Google Scholar]
2. T. Kunz. (2008). “Energy efficient variations of OLSR,” in 2008 Int. Wireless Communications and Mobile Computing Conf., Crete Island, Greece, pp. 517–522. [Google Scholar]
3. D. Kaur and N. Kumar. (2013). “Comparative analysis of AODV, OLSR, TORA, DSR and DSDV routing protocols in mobile ad-hoc networks,” International Journal of Computer Network and Information Security, vol. 5, no. 3, pp. 39–46. [Google Scholar]
4. Y. K. Jain and R. K. Verma. (2012). “Energy level accuracy and life time increased in mobile adhoc networks using OLSR,” International Journal of Advanced Research in Computer Science and Software Engineering, vol. 2, no. 7, pp. 1–7. [Google Scholar]
5. T. Stephan and K. S. Joseph. (2016). “Cognitive radio assisted OLSR routing for vehicular sensor networks,” Procedia Computer Science, vol. 89, pp. 271–282. [Google Scholar]
6. A. Sahnoun, A. Habbani and J. ElAbbadi. (2017). “EEPR-OLSR: An energy efficient and path reliability protocol for proactive mobile adhoc network routing,” International Journal of Communication Networks and Information Security, vol. 9, no. 1, pp. 22–29. [Google Scholar]
7. S. Chettibi and S. Chikhi. (2013). “FEA-OLSR: An adaptive energy aware routing protocol for MANETs using zero-order sugeno fuzzy system,” International Journal of Computer Science Issues, vol. 10, no. 2, pp. 136–141. [Google Scholar]
8. M. Huang, Q. Liang and J. Xi. (2012). “A parallel disjointed multi-path routing algorithm based on OLSR and energy in ad-hoc networks,” Journal of Networks, vol. 7, no. 4, pp. 613–620. [Google Scholar]
9. S. Behzad, R. Fotohi and S. Jamali. (2013). “Improvement over the OLSR routing protocol in mobile ad-hoc networks by eliminating the unnecessary loops,” International Journal of Information Technology and Computer Science, vol. 5, no. 6, pp. 16–22. [Google Scholar]
10. S. Banik, B. Roy, P. Dey, N. Chaki and S. Sanyal. (2011). “QoS routing using OLSR with optimization for flooding,” International Journal of Information and Communication Technology Research, vol. 1, no. 4, pp. 165–168. [Google Scholar]
11. A. Aggarwal, S. Gandhi and N. Chaubey. (2011). “Performance analysis of AODV, DSDV and DSR in MANETS,” International Journal of Distributed and Parallel Systems, vol. 2, no. 6, pp. 167–177. [Google Scholar]
12. A. Booranawong, W. Teerapabkajorndet and C. Limsakul. (2013). “Energy consumption and control response evaluations of AODV routing in WSANs for building-temperature control,” Sensors, vol. 13, no. 7, pp. 8303–8330. [Google Scholar]
13. M. Aashkaar and P. Sharma. (2016). “Enhanced energy efficient AODV routing protocol for MANET,” in IEEE Int. Conf. on Research Advances in Integrated Navigation Systems (RAINSBangalore, India, pp. 1–5. [Google Scholar]
14. D. R. Chen. (2016). “An energy-efficient QoS routing for wireless sensor networks using self-stabilizing algorithm,” Ad Hoc Networks, vol. 37, pp. 240–255. [Google Scholar]
15. L. I. Ting, R. B. Tang and J. I. Hong. (2008). “Status adaptive routing with delayed rebroadcast scheme in AODV-based MANETs,” Journal of China Universities of Posts and Telecommunications, vol. 15, no. 3, pp. 82–86. [Google Scholar]
16. S. Li, S. Zhao, X. Wang, K. Zhang and L. Li. (2014). “Adaptive and secure load-balancing routing protocol for service-oriented wireless sensor networks,” IEEE Systems Journal, vol. 8, no. 3, pp. 858–867. [Google Scholar]
17. N. Schweitzer, A. Stulman, A. Shabtai and R. D. Margalit. (2016). “Mitigating denial of service attacks in OLSR protocol using fictitious nodes,” IEEE Transactions on Mobile Computing, vol. 15, no. 1, pp. 163–172. [Google Scholar]
18. M. C. Yuang, S. S. Lee, P. L. Tien, Y. M. Lin, J. Shih et al. (2005). , “Optical coarse packet-switched IP-over-WDM network (OPSINETTechnologies and experiments,” in Proc. of the SPIE, Optical Transmission, Switching, and Subsystems II, vol. 5625, pp. 682–691. [Google Scholar]
19. F. AlShahwan, M. Alshamrani and A. A. Amer. (2018). “Dynamic novel cross-layer performance enhancement approach for sip over OLSR,” IEEE Access, vol. 6, pp. 71947–71964. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |