DOI:10.32604/iasc.2021.014694

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2021.014694 |  |
| Article |
Hybrid Multimodal Biometric Template Protection
1LRIT—CNRST URAC No. 29, IT Center, Faculty of Sciences, Mohammed V University, Rabat, 10000, Morocco
2Department of Information Technology, College of Computer and Information Sciences, King Saud University, Riyadh, 11451, Saudi Arabia
3Meridian Team, LYRICA Laboratory, School of Information Sciences, Rabat, 10000, Morocco
4Department of Computer Engineering, College of Computer and Information Sciences, King Saud University, Riyadh, 11451, Saudi Arabia
*Corresponding Author: Sanaa Ghouzali. Email: sghouzali@ksu.edu.sa
Received: 09 October 2020; Accepted: 01 November 2020
Abstract: Biometric template disclosure starts gaining an important concern in deploying practical biometric authentication systems, where an assailant compromises the database for illegitimate access. To protect biometric templates from disclosure attacks, biometric authentication systems should meet these four requirements: security, diversity, revocability, and performance. Different methods have been suggested in the literature such as feature transformation techniques and biometric cryptosystems. However, no single method could satisfy the four requirements, giving rise to the deployment of hybrid mechanisms. In this context, the current paper proposes a hybrid system for multimodal biometric template protection to provide robustness against template database attacks. Herein, a secure sketch method is first applied to secure the fingerprint modality. Subsequently, a Dual-Tree Complex Wavelet Transform Discrete Cosine Transform (DTCWT-DCT) based watermarking is employed to entrench the fingerprint sketch into the face image. However, a 3D chaotic-map-based encryption method is employed to protect the watermarked facial image in order to offer an added security level. The experimentation performed using the ORL face database and three Fingerprint Verification Competition (FVC) fingerprint databases showed the approach’s efficiency in withstanding standard digital image watermarking attacks, brute force attacks, and information leakage. Moreover, the results revealed that the approach achieves high performance, and satisfies diversity and revocability requirements.
Keywords: Biometric template protection; secure sketch; watermarking; image; encryption; 3D chaotic map; hybrid
Regarding to the rapid spread of digital technology that renders a large amount of digital information created and delivered many times in a second, a higher level of security is required. Hence, biometric technology is presented as an alternative solution to replace the conventional token-based (e.g., passport, ID card) or knowledge-based (e.g., password, PIN code) personal identification techniques. Contrary to the traditional systems that cannot satisfy the increased security requirements, biometrics-based-authentication systems easily distinguish between fraudulent and authorized users, based on behavioral (e.g., speech, gait, signature dynamics) or physiological characteristics (e.g., face, iris, fingerprint) of the person. Generally, biometric authentication mechanisms include enrolment and authentication phases. While the enrolment phase acquires the biometric data from the genuine user, processes it, and stores it in the database as a reference, the authentication phase extracts the characteristics vector from the biometric inquiry data to be compared with reference features vector to grant or deny access.
Although biometric authentication systems provide a high level of performance, they are still vulnerable toward various sorts of attacks [1]: (1) Attacks on the user sensor (e.g., spoofing and mimicry attacks); (2) Attacks on the interface between modules; (3) Attacks on software modules; and (4) Attacks on the system’s database. The devastating attack is the one on the templates database because the attacker gains illegitimate access to the database and can subsequently replace/usurp the biometric templates. To secure the biometric data, many methods are proposed in the literature. Primarily, the methods of protecting biometric template are classified into two classes: (1) Feature transformation [2]; and (2) Biometric cryptosystems [3]. Feature transformation approach transforms biometric features with a specific password/key producing a reference biometric model to be deposited in the system’s database. Feature transformation methods are either invertible (salting) or non-invertible. Biometric cryptosystem technique links the biometric data with a secret key to generate a biometric data known as “helper data,” kept as a reference in the database. Considering the secret key’s generation mode, there exist two sorts of biometric cryptosystems: (1) Key binding (e.g., fuzzy commitment [4] and fuzzy vault [5,6]); and (2) Key generation (e.g., fuzzy extractors [7] and secure sketches [8–11]). A comprehensive survey of feature transformation and biometric cryptosystem approaches is introduced in [12].
Meanwhile, biometric watermarking has been considered as complementary techniques to secure biometric data in authentication systems [13]. Biometric watermarking methods offer a high-security level to the authentication system, where the embedded data would not be recovered using only a secret key. Moreover, the embedded data are kept linked to the cover image and thus no additional transfer resources or storage mechanisms are needed. However, watermarking directly affects the original image’s perceptual transparency by making certain distortions on the image pixels during the watermark embedding process. Furthermore, cryptographic techniques also provide a higher level of security as it is computationally difficult to retrieve the original template from the generated one without knowing the encryption key. Therefore, conventional cryptography is not suitable for biometric templates, giving rise to numerous techniques for image encryption to cope with the speed and variability constraints [14].
Biometric template protection approaches should satisfy four criteria including security, revocability, diversity, and performance. However, no single technique fulfils the four constraints of biometric template protection at a time. Hence, several hybrid approaches that combine different methods, are proposed in the literature to achieve more requirements (e.g., [10,15–22]). An extensive review that analyzes different existing biometric template protection methods is presented in [23]. In this context, the current work proposes a multimodal biometric authentication-based hybrid approach to improve the effective security and efficiency of authentication systems against template database attacks. The underlying concept of this approach is to combine: (1) Dual-Tree Complex Wavelet Transform Discrete Cosine Transform-based watermarking; (2) secure sketch; and (3) 3D chaotic map image encryption. Fusing two biometric modalities (face and fingerprint) increases the authentication performance and security. Fingerprints are chosen because they provide a high verification rate, while face modality is typically used in our daily recognition tasks.
The process of the approach adheres to the following steps: first, the secure sketch is used to provide the security of the original fingerprint features. Next, because of secure sketch non-revocability and incapability to model intra-user variations, the blind DTCWT-DCT-based watermarking method is employed to entrench the fingerprint sketch (used as watermark) into the facial image (used as a cover image). The underlying concept in this technique is to fuse the fingerprint features and face images to relate each to other. The DTCWT domain frequency decomposition is used due to the high-frequency sub-bands that provide additional security level during the watermark integration. Further, the DCT scheme is used given its withstanding of various watermarking attacks such as noising, compressing, sharpening, and filtering. Finally, the 3D chaotic map image encryption method is employed to secure the facial watermarked image. This encryption method is chosen because of its sensitivity to initial status, control parameters, non-convergence, non-periodicity and robustness against brute force attacks.
The rest of the paper is organized as follows. Section 2 describes the proposed hybrid approach in detail. The experimental results are discussed in Section 3, providing an analysis of the four biometric requirements of the proposed hybrid approach. The conclusion is presented in Section 4.
The current section provides a description of the overall framework and a detailed overview of the suggested approach components.
2.1 Overall Framework Description
Fig. 1 illustrates a chart of the suggested template protection algorithm. As shown in this diagram, the algorithm comprises two phases: Enrolment and Authentication.
Enrolment phase: In this stage, we applied the secure sketch encoder to the extracted and preprocessed fingerprint features to ensure their security, thus, sketch P is generated. Next, we used the watermarking algorithm to embed the sketch P considered as a watermark into the facial image used as a cover image. Further, the watermarked facial image (WI) is then encrypted using a chaos-based simple encryption technique via a user key K to enhance the security level. Furthermore, the encrypted watermarked facial image (EI) is warehoused in the database as a public reference.
Authentication phase: Herein, the genuine user provides a key K’ supposed to be the same as the enrolment key K. If the keys are not identical, it is asserted as an assailant. Otherwise, the user is requested to present her/his face, and fingerprint (query images). Subsequently, the reference image EI is restored from the system’s database and decrypted using the key K’ to recover the WI. Then, two parallel matching processes are carried out. The facial characteristics are taken out from both the query and reference facial images via the Orthogonal Locality Preserving Projections (OLPP) scheme introduced in [24], hence, two features sets F’ and F are respectively obtained, binarized, and compared based on the Hamming distance metric, which generates the facial modality score 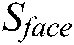 . Meanwhile, the watermark sketch P is extracted from the decrypted watermarked face image. Subsequently, the secure sketch decoder function is applied to generate a features vector FV to be matched with the features vector of the fingerprint query image using the Hamming distance metric that generates the fingerprint modality score
. Meanwhile, the watermark sketch P is extracted from the decrypted watermarked face image. Subsequently, the secure sketch decoder function is applied to generate a features vector FV to be matched with the features vector of the fingerprint query image using the Hamming distance metric that generates the fingerprint modality score 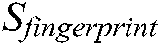 . To determine whether the authentication is successful, the score-level fusion method of the face and the fingerprint individual matching scores is employed. The Performance-Anchored Normalization method is used in this work to compute the scores of both modalities [25]. Next, the scores are merged via the weighted sum rule with an appropriate distribution of weights selected by the Equal Error Rate (EER) during the training stage. The weight,
. To determine whether the authentication is successful, the score-level fusion method of the face and the fingerprint individual matching scores is employed. The Performance-Anchored Normalization method is used in this work to compute the scores of both modalities [25]. Next, the scores are merged via the weighted sum rule with an appropriate distribution of weights selected by the Equal Error Rate (EER) during the training stage. The weight,  , is allocated to the score of the face modality
, is allocated to the score of the face modality 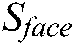 , while the weight,
, while the weight,  , is allocated to the score of the fingerprint modality
, is allocated to the score of the fingerprint modality 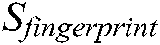 . Finally, the matching score of the multimodal biometric authentication system is computed as:
. Finally, the matching score of the multimodal biometric authentication system is computed as:

The biometric authentication system accepts or rejects an individual by comparing the matching score 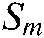 to a threshold
to a threshold 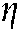 .
.
2.2 Framework Components Description
In this section, the main components of the suggested approach are described, including secure sketch, watermarking, and image encryption algorithms.
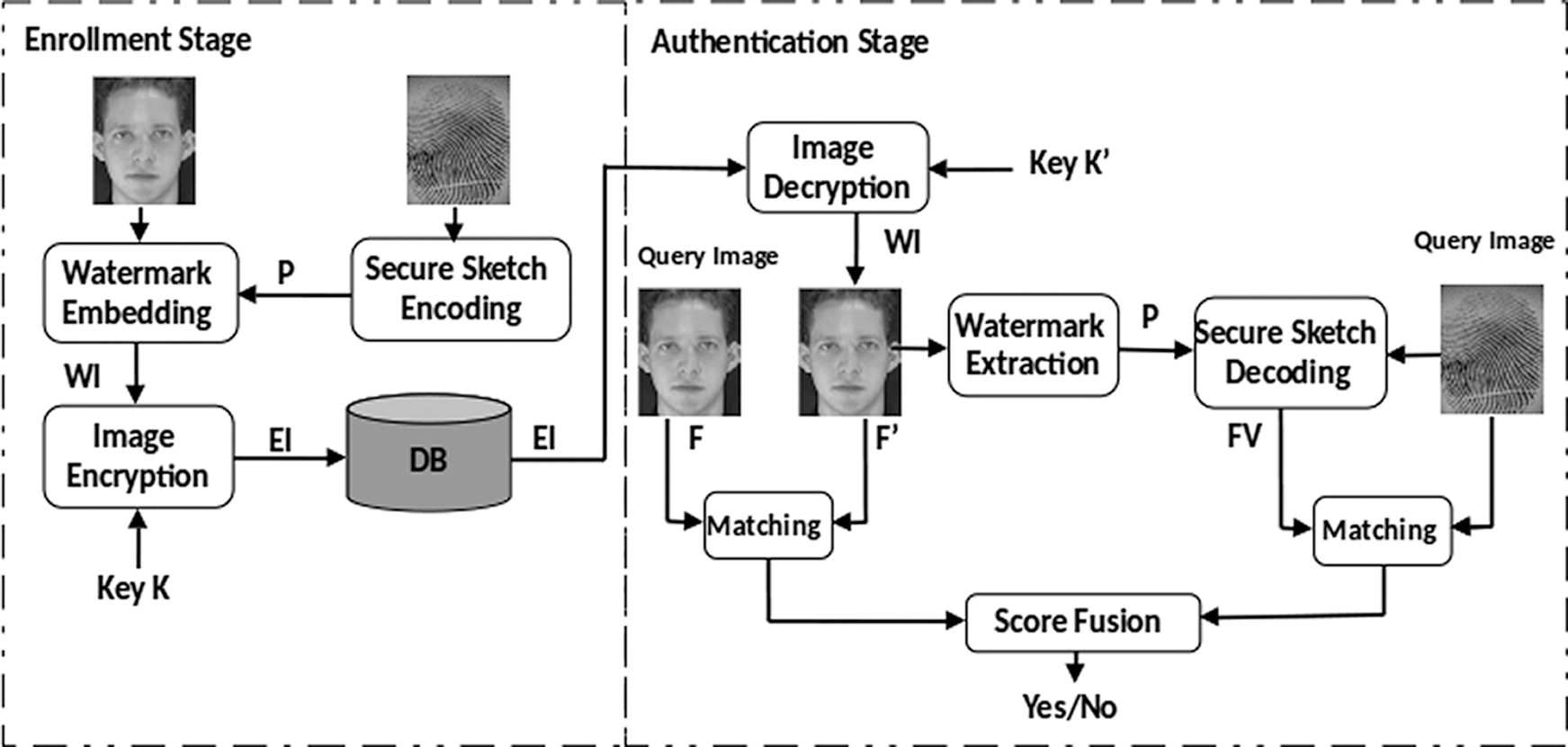
Figure 1: Proposed hybrid biometric template protection approach
The secure sketch is a key generation biometric cryptosystem method that has been recently suggested to expand the conventional cryptographic metrics in biometric data (e.g., [8–11]). This scheme includes two blocks: encoder and decoder. While the encoder gets the authentic biometric data 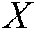 as input and generates a sketch, the decoder combines the sketch with another biometric data
as input and generates a sketch, the decoder combines the sketch with another biometric data 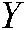 to output a template
to output a template 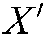 . If
. If 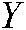 and
and 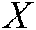 are adequately identical, the equation
are adequately identical, the equation 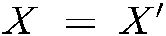 will be satisfied. The direct minutiae matching process is avoided in the proposed secure sketch algorithm due to two primary reasons. First, the proposed authentication system uses an extensive database, implying that, the minutiae-based matching strategy would not satisfy the fast-performance speed requirement. Second, fingerprint minutiae representation cannot be applied directly to a template-based secure sketch, since the minutiae extraction does not provide the same number of minutiae for different fingerprint images, whereas a fixed-length feature vector is needed as an input in a secure sketch algorithm. To solve these problems, the spectral minutiae representation is utilized rather than the minutiae sets. Hence, the minutiae points are depicted as a spectral characteristics’ vector of fixed length after being elicited from the fingerprint image through the minutiae extraction system presented in [26]. More precisely, suppose that
will be satisfied. The direct minutiae matching process is avoided in the proposed secure sketch algorithm due to two primary reasons. First, the proposed authentication system uses an extensive database, implying that, the minutiae-based matching strategy would not satisfy the fast-performance speed requirement. Second, fingerprint minutiae representation cannot be applied directly to a template-based secure sketch, since the minutiae extraction does not provide the same number of minutiae for different fingerprint images, whereas a fixed-length feature vector is needed as an input in a secure sketch algorithm. To solve these problems, the spectral minutiae representation is utilized rather than the minutiae sets. Hence, the minutiae points are depicted as a spectral characteristics’ vector of fixed length after being elicited from the fingerprint image through the minutiae extraction system presented in [26]. More precisely, suppose that 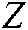 minutiae points are taken out from the fingerprint image, with
minutiae points are taken out from the fingerprint image, with 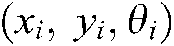 the location and orientation of the
the location and orientation of the 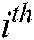 minutia and
minutia and 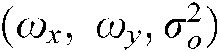 the frequencies and the parameters of the Gaussian kernel function, respectively.
the frequencies and the parameters of the Gaussian kernel function, respectively. 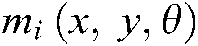 the derivative of
the derivative of 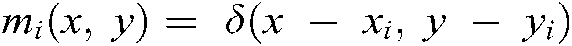 in the direction
in the direction 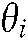 , and
, and 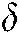 the Dirac Pulse metric. The minutiae exemplification is carried out using Eq (2) [27]:
the Dirac Pulse metric. The minutiae exemplification is carried out using Eq (2) [27]:

where 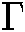 is the Fourier transform defined as:
is the Fourier transform defined as:
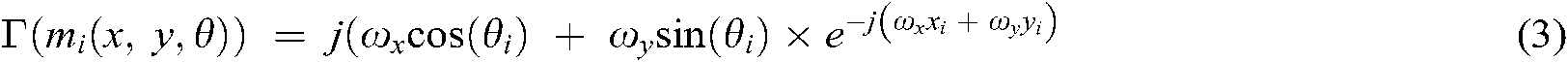
As the obtained minutia representation is sizable dimensionality, the Column Principal Component Analysis (CPCA) features reduction approach addressed in [28] is utilized to reduce the spectral features vector size. This metric is used to obviate the large dimensionality problems such as template storage and computational burden requirements. Next, the minimized features vector is quantized based on the quantization technique presented in [27]. The engendered vector is joined with the Reed-Solomon codeword SR using the exclusive OR (XOR) to generate the sketch P.
In the secure sketch decoding phase, the same process is carried out on the query fingerprint image to construct the features vector. This vector is subsequently XORed with the sketch P retrieved from the system’s database. The result is further decoded using the Reed-Solomon decoder function to retrieve the codeword SR′ that is supposed to be near to the codeword SR with correct authentication. Finally, the features vector is restored by XORing P and SR′. To determine whether the authentication is successful, the obtained features’ vector is compared to the query fingerprint image features vector according to the Hamming distance. Secure sketch encoding and decoding processes are illustrated in Fig. 2.
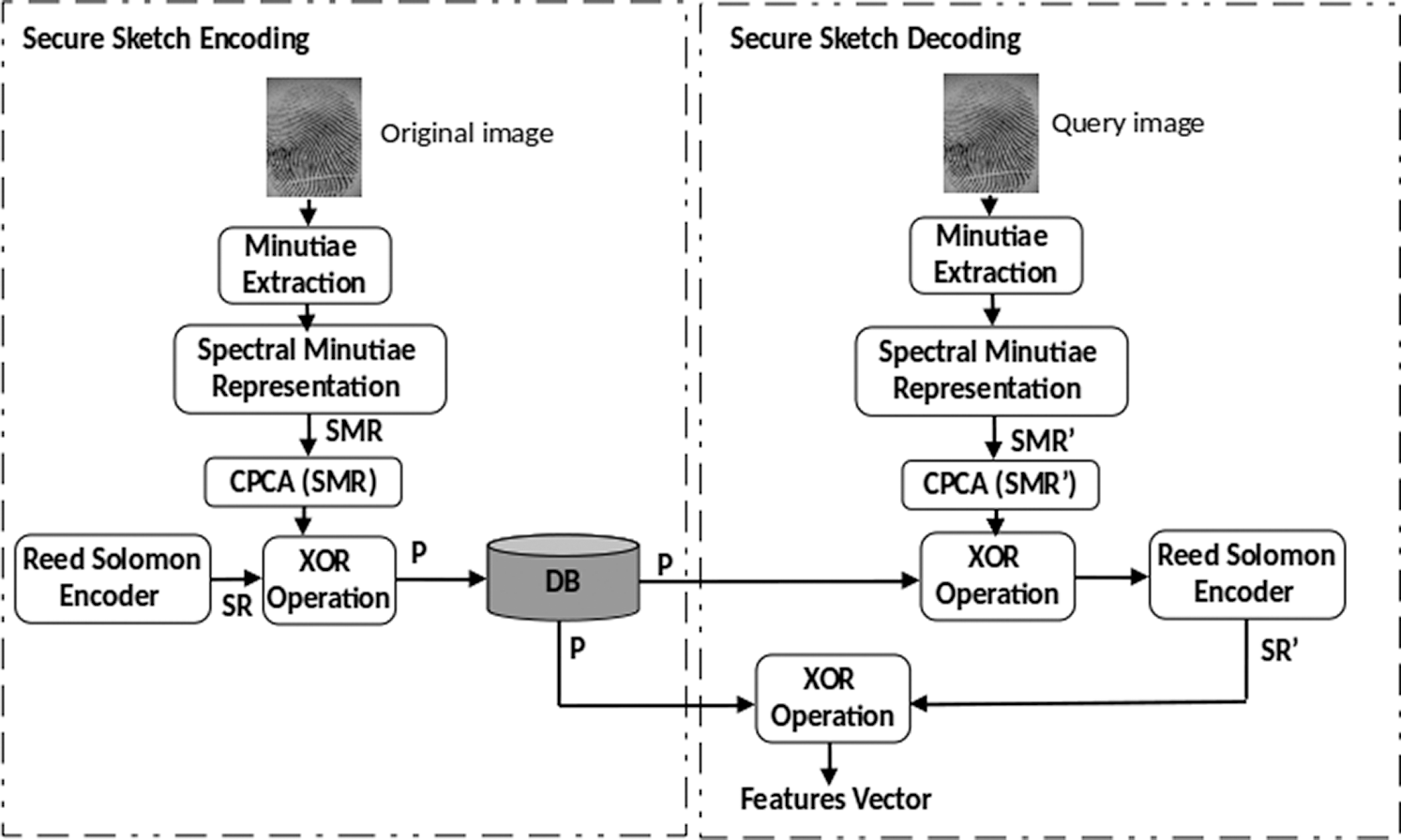
Figure 2: Block diagram of the secure sketch scheme for the fingerprint template
The security of secure sketch relies on the difficulty to estimate the original data, given that a small quantity of data is seeped out when the sketch is revealed. Therefore, an efficient solution is to restrain assailants from determining the biometric template using a compromised sketch. In [7,29], the authors suggested the use of entropy loss to measure the sketch’s information leakage, which gives an adversary the advantage to estimate the original information from a given sketch. In our study, the informal definition of entropy loss— also known as mutual information— is used. It measures the quantity of information communicated on average between the sketch P and the original fingerprint features vector F as follows:
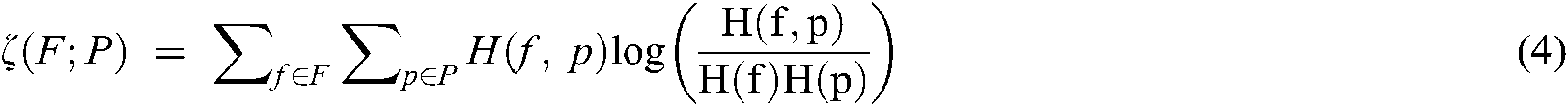
where H(F) and H(P) are the marginal distributions of F and P.
Digital watermarking is one of the leading protection expedients that has been effectively employed to protect the biometric templates (e.g., [30–38]). The watermarking algorithm used in this study relies on the DTCWT and DCT as two domain transform mechanisms. The concept used in this algorithm is to entrench the watermark with less disfigurement in the facial image while allowing blind watermark extraction via the correlation method. The DTCWT algorithm is designed to exhibit directional selectivity, which is reliable with the Human Visual System (HVS).
The watermark embedding stage starts by dismantling the facial image using one level DTCWT decomposition. Next, three high-frequency sub-bands are arbitrarily chosen and divided into  blocks. Then, the DCT transform is applied on each
blocks. Then, the DCT transform is applied on each  block. After that, the watermark bits are integrated with a gain factor μ into the DCT transformed
block. After that, the watermark bits are integrated with a gain factor μ into the DCT transformed  blocks using two produced pseudorandom series
blocks using two produced pseudorandom series  and
and  to integrate the 0 and 1 watermark bits, respectively. Finally, we execute the inverse DCT and inverse DTCWT to construct the watermarked facial image.
to integrate the 0 and 1 watermark bits, respectively. Finally, we execute the inverse DCT and inverse DTCWT to construct the watermarked facial image.
In the watermark extraction stage, the same procedure as in the watermark embedding stage is carried out on the watermarked facial image to obtain the DCT transformed blocks. Then, for each DCT transformed block, the mid-band coefficients are retrieved, and two correlations  and
and 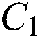 are computed with
are computed with  and
and  , respectively. In case
, respectively. In case  , the readout watermark bit is deemed 1; otherwise, it is deemed 0. The detailed information about the DTCWT-DCT-based watermarking algorithm used in this framework are found in [37].
, the readout watermark bit is deemed 1; otherwise, it is deemed 0. The detailed information about the DTCWT-DCT-based watermarking algorithm used in this framework are found in [37].
Unlike the DTCWT-based watermarking algorithm indicated in [39] that inserts the watermark into coefficients of the sub-band with an angle of 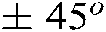 , our approach’s watermarking scheme enhances the security by randomly selecting three high-frequency sub-bands of the DTCWT decomposition. In [39], while the watermark is integrated directly into the DTCWT coefficients, the embedding is carried out in our approach by manipulating only the coefficients of the middle-frequency DCT sub-bands to affect less the lucidity of the watermarked cover image, and to prevent against compression attacks. This choice is due to two reasons: first, the high-frequency elements of the image are removed through noise attacks and compression. Second, most of the signal energy is located at low-frequency DCT sub-bands that contain the pertinent visual parts of the image.
, our approach’s watermarking scheme enhances the security by randomly selecting three high-frequency sub-bands of the DTCWT decomposition. In [39], while the watermark is integrated directly into the DTCWT coefficients, the embedding is carried out in our approach by manipulating only the coefficients of the middle-frequency DCT sub-bands to affect less the lucidity of the watermarked cover image, and to prevent against compression attacks. This choice is due to two reasons: first, the high-frequency elements of the image are removed through noise attacks and compression. Second, most of the signal energy is located at low-frequency DCT sub-bands that contain the pertinent visual parts of the image.
2.2.3 Image Encryption Algorithm
Chaos-based image encryption is one of the most widely used image security for biometric template protection (e.g., [40–46]). The chaos map employed in the proposed approach is the logistic map. It is chosen due to its simplicity and reduced complexity. Eq. (5) illustrates the 1D logistic map and the 3D formula is given in Eq. (6), where 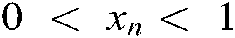 and
and 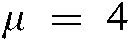 are the conditions to render the equation chaotic;
are the conditions to render the equation chaotic;  , and
, and  are the growth rates, and the initial values of
are the growth rates, and the initial values of 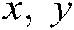 and
and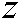 , respectively, in between 0 and 1.
, respectively, in between 0 and 1.


In this study, the 3D chaotic map encryption metric consists of a coupling of pixel value transformation, pixel position switching, and a nonlinear 3D chaos-based simple encryption scheme. Suppose  are the image dimensions.
are the image dimensions. 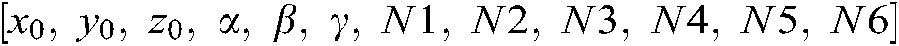 is the encryption/decryption key, where
is the encryption/decryption key, where  ,
, 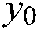 , and
, and 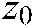 are the initial values of the 3D logistic map population
are the initial values of the 3D logistic map population 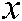 ,
,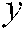 , and
, and 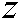 , respectively.
, respectively. 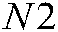 ,
,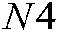 ,
,  are large random numbers used to equalize the histogram of the generated logistic map (see Eq. (7)), while
are large random numbers used to equalize the histogram of the generated logistic map (see Eq. (7)), while 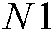 ,
,  ,
, , are used as the first index to select the chaos
, are used as the first index to select the chaos 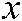 ,
, 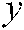 , and
, and 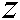 , respectively. As illustrated in Fig. 3, the proposed encryption strategy comprises the following stages [47]:
, respectively. As illustrated in Fig. 3, the proposed encryption strategy comprises the following stages [47]:
Generate a 3D logistic map based on Eq. (6) to obtain the logistic map  ,
, 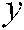 , and
, and 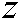 .
.
Equalize the histogram of the logistic map using Eq. (7) to improve the security level. The histogram equalization is performed owing to the non-uniform distribution of the logistic map histogram.

Permute the image pixels via a row rotation approach. This starts by arbitrary generating a considerable number N1; subsequently, choose M number of chaos x starting from index N1. Next, rotate the pixels based on chaos value x. If the x value is even, rotate to the left; if it is odd, rotate to the right.
Permute the image pixels via a column rotation approach. This starts by generating a sizable random number  ; subsequently, select
; subsequently, select 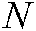 numbers of chaos y from index
numbers of chaos y from index  . Perform rotation according to the
. Perform rotation according to the 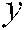 value. If the
value. If the 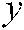 value is even, rotate up; if it is odd, rotate down.
value is even, rotate up; if it is odd, rotate down.
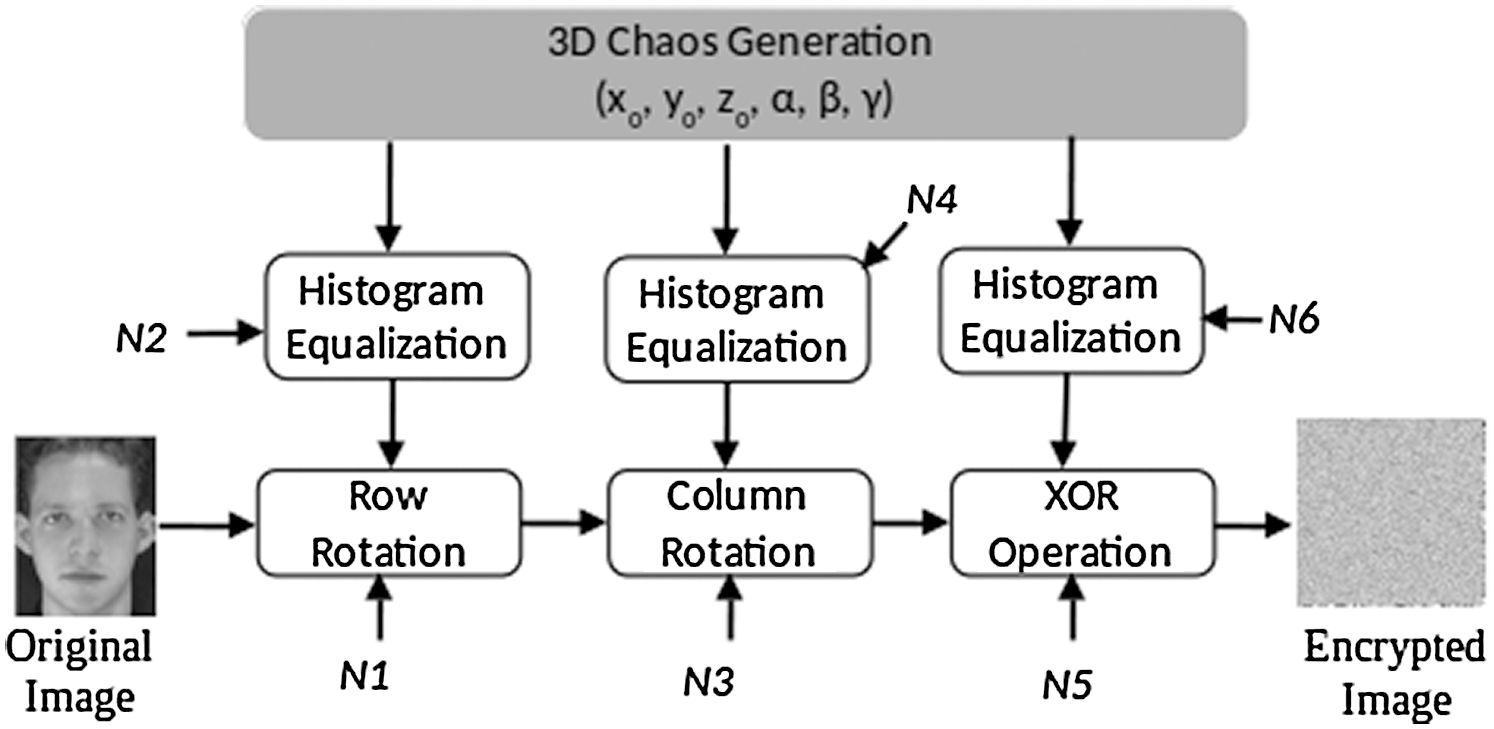
Figure 3: Encryption technique using 3D chaos
Applying row and column rotation generates an encrypted image with an unaltered histogram, that may fail toward histogram attacks. To overcome this issue, the XOR operation is applied as an added step. The underlying concept of this step is to change the image pixel value to a new value and prevent the retrieval of the original value without the chaos key. Therefore, a large random number  is generated; subsequently, the
is generated; subsequently, the  image is reshaped into a
image is reshaped into a 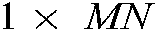 vector. Finally, the XOR operation is applied between the
vector. Finally, the XOR operation is applied between the 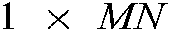 vector and the
vector and the 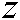 chaos from the index
chaos from the index  to obtain the encrypted image.
to obtain the encrypted image.
In the decryption stage, the encrypted image is first reshaped into a 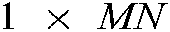 vector. Then, it is XORed with the
vector. Then, it is XORed with the 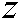 chaos using
chaos using  . Next, the inverse column rotation and inverse row rotation are applied. In the inverse column rotation, the
. Next, the inverse column rotation and inverse row rotation are applied. In the inverse column rotation, the 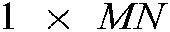 vector is reshaped into an
vector is reshaped into an  image; subsequently, based on
image; subsequently, based on  and the
and the 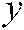 value, the rotation process is applied. If the
value, the rotation process is applied. If the 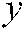 value is even, we rotate down; if it is odd, we rotate up. To get the original image, the inverse row rotation is applied using
value is even, we rotate down; if it is odd, we rotate up. To get the original image, the inverse row rotation is applied using 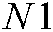 and the
and the 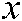 value. If the
value. If the 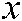 value is even, we rotate to the right; if it is odd, we rotate to the left.
value is even, we rotate to the right; if it is odd, we rotate to the left.
Extensive tests have been carried out to assess the efficiency of the suggested hybrid approach using the ORL face database and three FVC databases: FVC2002 DB1, DB2, and FVC2000 DB1.  pixels facial images and fingerprint images of size
pixels facial images and fingerprint images of size  ,
, , and
, and  pixels are obtained from FVC2002 DB1, DB2, and FVC2000 DB1, respectively. These images were divided into three datasets: Dataset1 (ORL with FVC2002 DB1), Dataset2 (ORL with FVC2002 DB2), Dataset3 (ORL with FVC2000 DB1).
pixels are obtained from FVC2002 DB1, DB2, and FVC2000 DB1, respectively. These images were divided into three datasets: Dataset1 (ORL with FVC2002 DB1), Dataset2 (ORL with FVC2002 DB2), Dataset3 (ORL with FVC2000 DB1).
Stratifying the spectral minutiae representation on the extracted minutiae points, feature matrices of 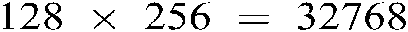 are obtained. After applying the CPCA features reduction metric, where only the pertinent features are selected, and the feature quantization method, a 10240-bits binary stream is generated (sketch P).
are obtained. After applying the CPCA features reduction metric, where only the pertinent features are selected, and the feature quantization method, a 10240-bits binary stream is generated (sketch P).
In the watermarking process, only three  high-frequency sub-bands are arbitrarily chosen from the six high-frequency sub-bands generated via the one level DTCWT decomposition. The decomposition of each selected high-frequency sub-band produces
high-frequency sub-bands are arbitrarily chosen from the six high-frequency sub-bands generated via the one level DTCWT decomposition. The decomposition of each selected high-frequency sub-band produces  blocks of dimension
blocks of dimension  each. Moreover, to get an optimal watermarking imperceptibility and good robustness against image watermarking attacks, the watermarking algorithm has been examined for various values of the gain factor
each. Moreover, to get an optimal watermarking imperceptibility and good robustness against image watermarking attacks, the watermarking algorithm has been examined for various values of the gain factor 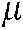 among a range of 0 to 60. The conducted experiments demonstrated that the convenient values are
among a range of 0 to 60. The conducted experiments demonstrated that the convenient values are 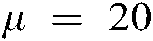 ,
,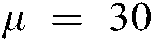 , and
, and 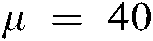 for the first, second, and third high-frequency sub-bands. Besides, various values among a range of 0 to 1 are assigned to weights values
for the first, second, and third high-frequency sub-bands. Besides, various values among a range of 0 to 1 are assigned to weights values 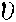 allocated to the score of the facial system and
allocated to the score of the facial system and  allocated to the fingerprint system’s score. The values of
allocated to the fingerprint system’s score. The values of  and
and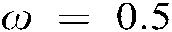 , which provide the maximum authentication performance, are chosen. Moreover, as the midb and frequencies of a DCT block have seven coefficients, pseudorandom sequences
, which provide the maximum authentication performance, are chosen. Moreover, as the midb and frequencies of a DCT block have seven coefficients, pseudorandom sequences  and
and  of length seven are generated. To implement the encryption approach,
of length seven are generated. To implement the encryption approach, 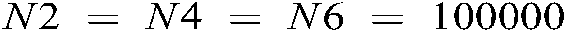 ,
, 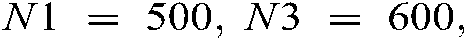 and
and 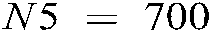 are considered.
are considered.
In this section, we put forward and discuss the evaluation results of the carried out tests to demonstrate the efficiency of the suggested approach in meeting the four requirements of biometric authentication systems.
Three scenarios are considered below to assess the security of the suggested approach.
Compromised encrypted image scenario
Suppose that the database is attacked and the encrypted facial image is stolen. It is typically computationally difficult for the attacker to estimate the key and decrypt the image due to the encryption key’s large keyspace. The keyspace refers to the set of all possible permutations of a key; in other words, it is given as the span of distinct potential values of a key. It should be sufficiently large to minimize the likelihood of an effective brute force attack. For instance, a password with 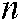 characters, where each of these characters assumes
characters, where each of these characters assumes  different values, has a keyspace size of
different values, has a keyspace size of  [48].
[48].
In the suggested 3D chaotic map encryption method, six initial conditions  ,
, 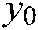 ,
, 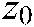 ,
,  ,
, 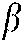 , and
, and 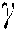 with precision
with precision 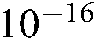 are used. Consequently, the keyspace size is
are used. Consequently, the keyspace size is 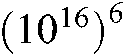 . Additionally,
. Additionally, 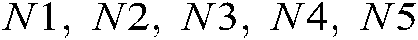 and
and  are used as random keys of precision
are used as random keys of precision 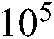 , implying that the keyspace size is
, implying that the keyspace size is 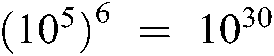 . Consequently, the keyspace size is larger than
. Consequently, the keyspace size is larger than 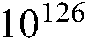 , which is sufficiently immense to withstand exhaustive attacks. Moreover, the suggested image encryption method is sufficiently secure to be sensitive to slight changes in the decryption key.
, which is sufficiently immense to withstand exhaustive attacks. Moreover, the suggested image encryption method is sufficiently secure to be sensitive to slight changes in the decryption key.
Compromised watermarked image scenario
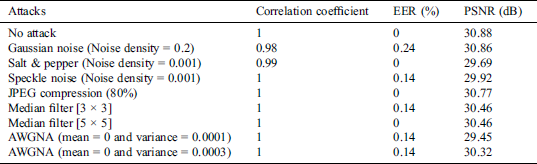
Suppose that the encrypted image is compromised and decrypted to get the watermarked facial image. The experimental results demonstrated the strength of the suggested watermarking algorithm against conventional digital image watermarking attacks, namely JPEG compression, Gaussian noise, speckle noise, salt and pepper noise, median filter, and additive white Gaussian noise. The evaluation is then reported using the correlation coefficient, Peak Signal-to-Noise Ratio (PSNR), and EER. The correlation coefficient and the PSNR are utilized to measure the quality of the extracted watermark and the integration deformation, respectively, whereas, the EER is employed to assess the authentication system’s reliability after applying the attacks. Tab. 1 presents the average of the EER, PSNR, and correlation coefficient values under the aforementioned attacks. From this table, it can be observed that the authentication performance of the watermarking algorithm was not affected by the attacks, where the EER value has been slightly minimized for some attacks. Besides, the PSNR and correlation coefficient values are slightly changed after applying attacks, which demonstrate the watermarking algorithm’s ability to withstand these attacks. However, the DTCWT-DCT-based watermarking algorithm does not preserve higher perceptual quality between the original and watermarked face images. This is due to the trade-off between the quality of the extracted watermark after embedding and the quality of the watermarked facial image. More precisely, improving the quality of the watermarked image decreases the quality of the extracted watermark and vice versa.
Table 1: Correlation coefficient, EER, and PSNR values before and after attacks
Compromised sketch scenario
Assuming that the encrypted image is compromised and decrypted, and the embedded sketch is extracted. In this case, the attacker attempts to estimate the original fingerprint features vector, given that the sketch is revealed. Since sketch P is generated using the fingerprint images, the entropy loss is calculated only over the FVC databases. In our experiments, the mutual information is calculated for each couple (F, P) of each image. Then the average of the mutual information is calculated for all images of each dataset. The average of the mutual information obtained for each dataset is 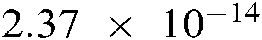 . The gained value shows that a tiny amount of mutual information is shared between the sketch and the original data, indicating that even when the sketch is extracted, the features vector information could not be leaked to the attacker.
. The gained value shows that a tiny amount of mutual information is shared between the sketch and the original data, indicating that even when the sketch is extracted, the features vector information could not be leaked to the attacker.
Different curves are plotted for the three datasets to assess the performance of the proposed system, including the genuine and impostor matching score distribution curves, the False Acceptance Rate (FAR) against the False Reject rate (FRR) curves, and the Receiver Operating Characteristic (ROC) curves. The genuine and impostor scores are generated via the FVC standard protocol [49]. Fig. 4 presents the genuine and impostor distributions related to the suggested hybrid system for the three datasets. It is noteworthy from the sub-figures that the scores are not overlapped, demonstrating the presented approach’s efficiency in discriminating between genuine and impostor users. The curves are well separated for Dataset1 and Dataset2 at the threshold’s value 0.4517 and 0.4514, respectively, and slightly overlapped for Dataset3 at the threshold range [0.8879,1.0521].
Besides, the approach’s authentication performance is attested by computing the EER and the FAR as opposed to the FRR values. The smallest of the value of the EER is the preferable, proving that the system is less likely to falsely admit impostors as genuine or falsely reject genuine as impostors. Fig. 5 shows the FAR as opposed to the FRR curves of the proposed system for the three different datasets. As can be observed from this figure, the proposed method reached lower EER values of 0%, 0%, and 0.12% on Dataset1, Dataset2, and Dataset3, respectively. Also, FRR/FAR values of 0.0083/0.2140% for the threshold 0.4512, 0.0080/0.2141% for the threshold 0.4510, and 0.0095/0.2074% for the threshold 0.9184 are obtained over the three databases, respectively. These results demonstrated the high performance and reliability of the authentication approach.
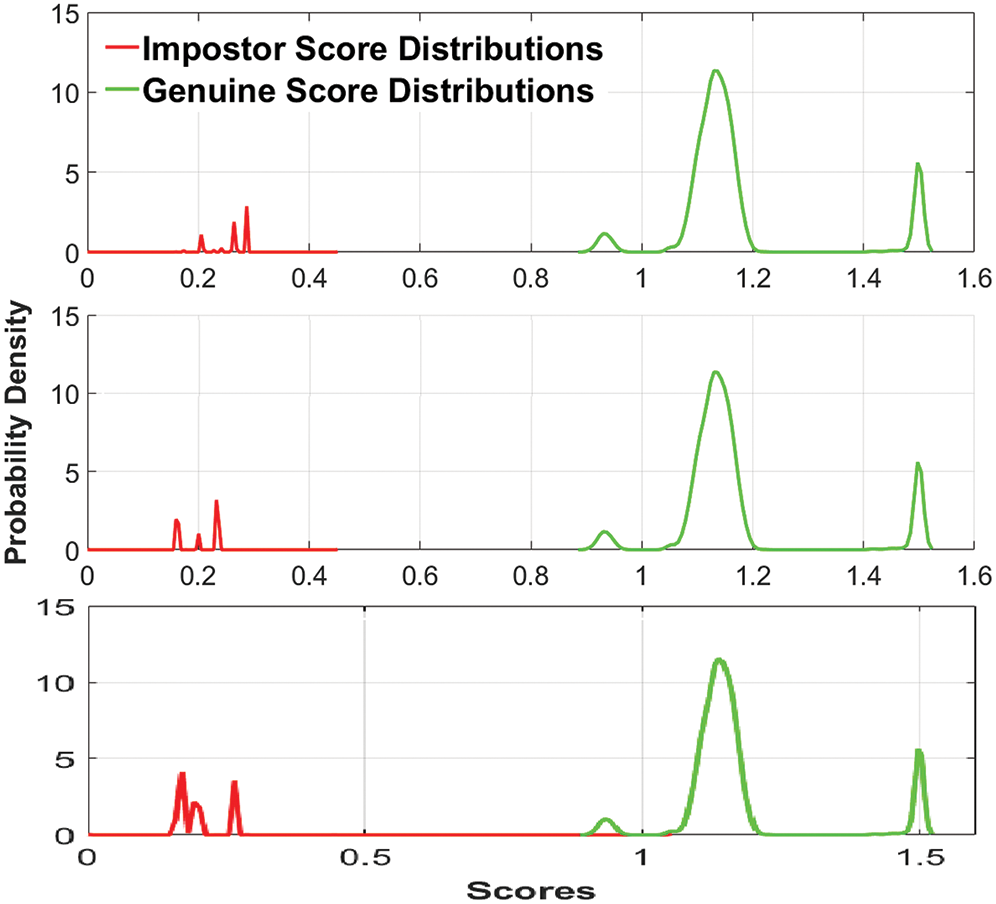
Figure 4: Genuine and impostor matching score distribution curves of the proposed hybrid system for the three datasets: Dataset1, Dataset2, and Dataset3 from top to down
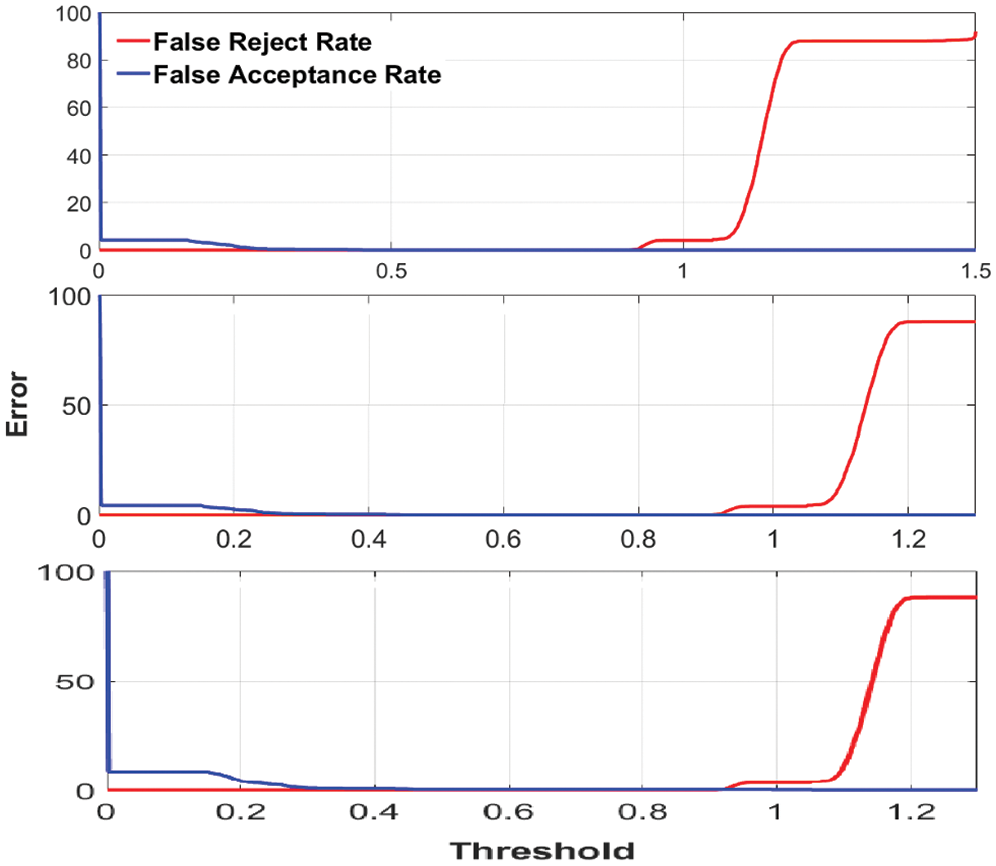
Figure 5: FAR vs. FRR curves of the proposed hybrid system, for the three datasets: Dataset1, Dataset2, and Dataset3 from top to down
In Fig. 6, the ROC curves illustrated the authentication performance of the different approaches: face-based, fingerprint-based, and the proposed fingerprint-face-based multimodal. The three sub-figures in Fig. 6 show that the fingerprint-based authentication approach performs weaker than the face-based authentication approach since the minutiae extraction process does not provide the same number of minutiae for different fingerprint images of the same user. Additionally, significant performance improvement is shown for the fingerprint-face-based multimodal authentication system, as the accuracy of 100% is achieved, similar to the face-based authentication system. The obtained results indicated that the watermarking algorithm did not degrade the system’s performance while improving the system’s security due to the combination of two different modalities and the score fusion method’s effectiveness.
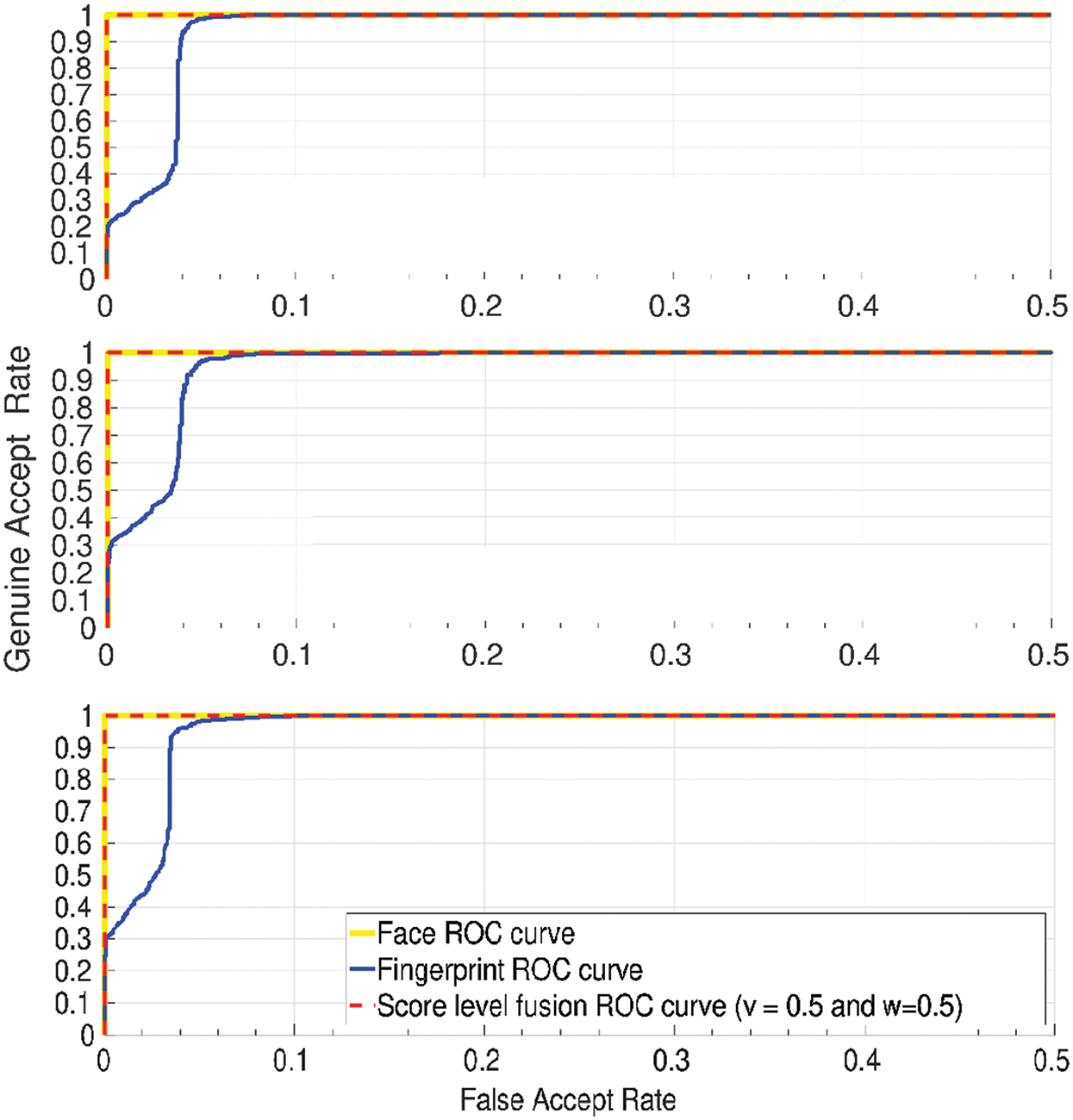
Figure 6: ROC curves of the face-based unimodal authentication system, the fingerprint-based unimodal authentication system, and the fingerprint-face-based multimodal authentication system for the three datasets Dataset1, Dataset2, and Dataset3 from top to down
3.2.3 Diversity and Revocability Analysis
A template protection approach meets the diversity criteria if it generates multiple uncorrelated templates from the same original features vectors, allowing users to register in distinct applications based on the same features without the risk of cross-matching between the corresponding databases. In comparison, the revocability requirement indicates the capability to revoke a template that has been breached and generate a novel one. The typical means to verify that a template protection method meets both properties is by producing multiple protected templates from the same original templates and different keys, and subsequently attempting to match the resulting sets of protected templates. Regarding the diversity criterion, the matching is derived using the True Rejection Rate (TRR) that measures the percentage of time the system (correctly) rejects a user with a distinct key. In our experiments, the obtained TRR values are 99.50%, 99.35%, and 98.94% for Dataset1, Dataset2, and Dataset3, respectively, which proves the suggested approach to be embedded into various applications without databases cross-matching. Regarding the revocability property, the matching is accomplished using the EER metric, where an EER value of 0% is obtained for each of the three datasets, indicating that the intra-class variation is preserved. Therefore, canceling a template that has been breached and generating a novel one will not change or affect the authentication system.
3.2.4 Computational Complexity
To examine the computational complexity of the suggested hybrid approach, the run time has been recorded during the authentication stage, which is the most crucial phase required to be carried out in real time. As illustrated in Fig. 1, this phase includes the image decryption, watermark extraction, and secure sketch decoding. All the algorithms were implemented in MATLAB and run on an Intel Core(TM) 2 Duo CPU P7450 at 2.13 GHz with 4 GB of memory. The run time is recorded during the experiments carried out over all the databases of 320 images. The average time obtained is 2.11 s for the image decryption, 1.36 s for the watermark extraction, and 3.28 s for the sketch decoding process. By adding the average time needed to perform the matching process of 0.31 s, a total average of 7.06 s is attained for the overall authentication phase.
3.2.5 Comparison with Previous Studies
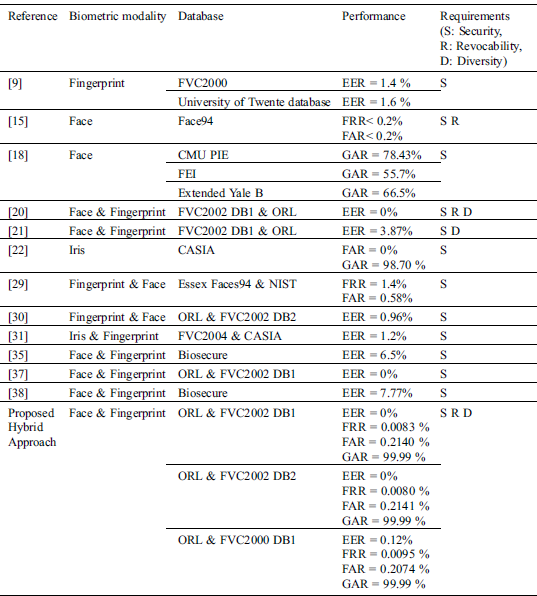
In the current section, a comparison of the suggested approach and the existing studies is presented. However, related studies used various databases and biometric modalities to endorse the efficiency of their suggested methods. Consequently, a useful comparison with our hybrid approach cannot be carried out. Tab. 2 outlines the biometric template protection methods suggested in the literature (based on watermarking, secure sketch, and image encryption methods), and their biometric modalities, criteria satisfaction, and performance results. It can be seen from this table that the suggested hybrid approach has evident advantages over the existing studies in terms of satisfying all the four requirements of biometric authentication systems.
The algorithms presented in [22,30,37] satisfied only the security and performance requirements. In [22], the authors combined cryptography and steganography to secure the storage of iris templates. The work discussed in [37] employed the same DTCWT-DCT-based watermarking algorithm used in the current work to improve the performance and security of the authentication system. Moreover, the methods presented in [9,18,29,31,35,38] achieved lower performance than the presented work, while ensuring the security criteria. These approaches used a single protection technique based on watermarking [31,35,38] or secure sketch [9,29].
The methods described in [13,20,21] satisfied more requirements, which demonstrated the advantage of using the hybrid approach. In [20], a DWT-SVD-based watermarking approach is employed to fuse the face and fingerprint features. Subsequently, a shuffling algorithm is carried out on the watermarked image, which is then XORed with a chaotic map and a Hadamard code to achieve the randomization and orthogonality of protected biometric features. This approach satisfied all the four requirements. However, its main drawback is that it is applicable only for biometric modality represented as an ordered set (e.g., face). This issue of using an ordered set of biometric modalities is improved in our proposed work as we used a fingerprint image as a cover image and manipulated its features using a face image. The results in [20] and our current work indicated a high recognition rate for all conditional cases, except when the noise levels are too high. In [21], the authors demonstrated how to integrate the fingerprint traits into various directional DWT sub-bands of the face image. Subsequently, each user is associated with a unique key and a hyper-chaotic map is employed to generate a keystream to encipher the watermarked image. This approach satisfied the security and diversity requirements. However, a lower level of performance (EER = 3.87%) is reached compared to our method.
Table 2: Summary of different biometric template protection approaches
A hybrid multimodal biometric template protection approach to provide robustness against template database attacks in biometric authentication systems is proposed in this work. Herein, the approach combines three techniques to satisfy jointly four requirements of biometric authentication systems, including security, diversity, revocability, and performance. The concept underlying the suggested approach starts by securing the fingerprint features using the secure sketch method. Subsequently, the obtained sketch is embedded in the face image based on a DTCWT-DCT watermarking approach. Finally, the watermarked face image is secured via a 3D chaotic map-based image encryption method.
Extensive experiments were carried out on the ORL face dataset and three FVC databases, including FVC2002 DB1, DB2, and FVC2000 DB1, to evaluate the suggested system. The experimental results showed a high level of security. An excellent matching performance is also achieved with EER values of 0%, 0%, and 0.12% for the three datasets, respectively. Moreover, the diversity and revocability constraints are achieved, indicating the approach’s ability to be embedded into various applications without databases cross-matching. Hence, our work makes a significant improvement compared with the existing related studies in meeting the four requirements at a time, due to its use of four potential points: multimodality, secure sketch, biometric watermarking, and chaotic map-based image encryption.
Nevertheless, as biometric authentication systems become familiar to the general public, they become frail to spoofing attacks where an assailant can readily get the biometric data from social networks to generate sophisticated models to deceive the authentication system. This attack raises the challenge of dealing with systems database attacks as well as imposters. In this regard, we intend in the future work to investigate in developing an anti-spoofing approach to distinguish between genuine and fake users.
Acknowledgement: Researchers Supporting Project No. (RSP-2020/206), King Saud University, Riyadh, Saudi Arabia.
Funding Statement: Researchers Supporting Project No. (RSP-2020/206), King Saud University, Riyadh, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. A. K. Jain, K. Nandakumar and A. Nagar. (2008). “Biometric template security,” EURASIP Journal on Advances in Signal Processing, vol. 2008, no. 1, 579416. [Google Scholar]
2. A. Nagar, K. Nandakumar and A. K. Jain. (2010). “Biometric template transformation: A security analysis,” in Media Forensics and Security II, Part of the IS&T-SPIE Electronic Imaging Symposium, San Jose, California, USA. [Google Scholar]
3. U. Uludag, S. Pankanti, S. Prabhakar and A. K. Jain. (2004). “Biometric cryptosystems: Issues and challenges,” Proceedings of the IEEE, vol. 92, no. 6, pp. 948–960. [Google Scholar]
4. A. Juels and M. Wattenberg. (1999). “A fuzzy commitment scheme,” in 6th ACM Conf. on Computer and Communications Security, pp. 28–36. [Google Scholar]
5. A. Juels and M. Sudan. (2006). “A fuzzy vault scheme,” Designs, Codes and Cryptography, vol. 38, no. 2, pp. 237–257. [Google Scholar]
6. H. M. Patel, C. N. Panuwala and A. Vora. (2016). “Hybrid feature level approach for multi-biometric cryptosystem,” in Int. Conf. on Wireless Communications, Signal Processing and Networking, Chennai, India, pp. 1087–1092. [Google Scholar]
7. Y. Dodis, L. Reyzin and A. Smith. (2004). “Fuzzy extractors: How to generate strong keys from biometrics and other noisy data,” in Int. Conf. on the Theory and Applications of Cryptographic Techniques. Proceedings: Lecture Notes in Computer Science, Interlaken, Switzerland, pp. 523–540. [Google Scholar]
8. Q. Li, Y. Sutcu and N. Memon. (2006). “Secure sketch for biometric templates,” in int. conf. on the Theory and Application of Cryptology and Information Security. Proceedings: Lecture Notes in Computer Science, Shanghai, China, pp. 99–113. [Google Scholar]
9. C. Fang, Q. Li and E. C. Chang. (2010). “Secure sketch for multiple secrets,” in Int. Conf. on Applied Cryptography and Network Security. Proc.: Lecture Notes in Computer Science, Beijing, China, pp. 367–383. [Google Scholar]
10. J. Bringer, H. Chabanne and B. Kindarji. (2008). “The best of both worlds: Applying secure sketches to cancelable biometrics,” Science of Computer Programming, vol. 74, no. 1–2, pp. 43–51. [Google Scholar]
11. Y. Sutcu, Q. Li and N. Memon. (2007). “Protecting biometric templates with sketch: theory and practice,” IEEE Transactions on Information Forensics and Security, vol. 2, no. 3, pp. 503–512. [Google Scholar]
12. C. Rathgeb and A. Uhl. (2011). “A survey on biometric cryptosystems and cancelable biometrics,” EURASIP Journal on Information Security, vol. 2011, no. 1, pp. 4. [Google Scholar]
13. J. Hämmerle-Uhl, K. Raab and A. Uhl. (2011). “Watermarking as a means to enhance biometric systems: A critical survey,” in Int. Workshop on Information Hiding. Proc.: Lecture Notes in Computer Science, Prague, Czech Republic, pp. 238–254. [Google Scholar]
14. M. Kumari, S. Gupta and P. Sardana. (2017). “A survey of image encryption algorithms,” 3D Research, vol. 8, no. 4, pp. 567. [Google Scholar]
15. T. K. Dang, Q. C. Truong, T. T. B. Le and H. Truong. (2016). “Cancellable fuzzy vault with periodic transformation for biometric template protection,” IET Biometrics, vol. 5, no. 3, pp. 229–235. [Google Scholar]
16. Y. J. Chin, T. S. Ong, A. B. J. Teoh and K. O. M. Goh. (2014). “Integrated biometrics template protection technique based on fingerprint and palmprint feature-level fusion,” Information Fusion, vol. 18, pp. 161–174. [Google Scholar]
17. H. Kaur and P. Khanna. (2016). “Biometric template protection using cancelable biometrics and visual cryptography techniques,” Multimedia Tools and Applications, vol. 75, no. 23, pp. 16333–16361. [Google Scholar]
18. S. Nazari, M. S. Moin and H. R. Kanan. (2018). “Securing templates in a face recognition system using error-correcting output code and chaos theory,” Computers & Electrical Engineering, vol. 72, pp. 644–659. [Google Scholar]
19. A. Sardar, S. Umer, C. Pero and P. Nappi. (2020). “A novel cancelable FaceHashing technique based on non-invertible transformation with encryption and decryption template,” IEEE Access, vol. 8, pp. 105263–105277. [Google Scholar]
20. O. Nafea, S. Ghouzali, W. Abdul and E. H. Qazi. (2016). “Hybrid multi-biometric template protection using watermarking,” Computer Journal, vol. 59, no. 9, pp. 1392–1407. [Google Scholar]
21. W. Abdul, O. Nafea and S. Ghouzali. (2020). “Combining watermarking and hyper-chaotic map to enhance the security of stored biometric templates,” Computer Journal, vol. 63, no. 3, pp. 479–493. [Google Scholar]
22. O. C. Abikoye, U. A. Ojo, J. B. Awotunde and R. O. Ogundokun. (2020). “A safe and secured iris template using steganography and cryptography,” Multimedia Tools and Applications, vol. 79, no. 31–32, pp. 23483–23506. [Google Scholar]
23. A. Sarkar and B. Singh. (2020). “A review on performance, security and various biometric template protection schemes for biometric authentication systems,” Multimedia Tools and Applications, vol. 79, no. 37–38, pp. 27721–27776. [Google Scholar]
24. D. Cai, X. He, J. Han and H. J. Zhang. (2006). “Orthogonal laplacianfaces for face recognition,” IEEE Transactions on Image Processing, vol. 15, no. 11, pp. 3608–3614. [Google Scholar]
25. N. Damer, A. Opel and A. Nouak. (2013). “Performance anchored score normalization for multi-biometric fusion,” in Int. Sym. on Visual Computing. Proc.: Lecture Notes in Computer Science, Rethymnon, Crete, Greece, pp. 68–75. [Google Scholar]
26. A. El-Sisi. (2011). “Design and implementation biometric access control system using fingerprint for restricted area based on Gabor filter,” International Arab Journal of Information Technology, vol. 8, no. 4, pp. 355–363. [Google Scholar]
27. Haiyun Xu, R. N. J. Veldhuis, A. M. Bazen, T. A. M. Kevenaar, T. A. H. M. Akkermans et al. (2009). , “Fingerprint verification using spectral minutiae representations,” IEEE Transactions on Information Forensics and Security, vol. 4, no. 3, pp. 397–409. [Google Scholar]
28. Haiyun Xu, Veldhuis R. N. J., Kevenaar T. A. M. and Akkermans T. A. H. M. (2009). “A fast minutiae-based fingerprint recognition system,” IEEE Systems Journal, vol. 3, no. 4, pp. 418–427. [Google Scholar]
29. Y. Sutcu, Q. Li and N. Memon. (2007). “Secure biometric templates from fingerprint-face features,” in IEEE Conf. on Computer Vision and Pattern Recognition, Minneapolis, MN, USA, pp. 1–7. [Google Scholar]
30. N. Bousnina, S. Ghouzali, M. Lafkih, O. Nafea and M. M. et al.. (2016). , “Watermarking for protected fingerprint authentication,” in 12th Int. Conf. on Innovations in Information Technology, Al-Ain, United Arab Emirates, pp. 1–5. [Google Scholar]
31. B. Ma, C. Li, Y. Wang, Z. Zhang and Y. Wang. (2010). “Block pyramid based adaptive quantization watermarking for multimodal biometric authentication,” in 20th Int. Conf. on Pattern Recognition, Istanbul, Turkey, pp. 1277–1280. [Google Scholar]
32. M. Paunwala and S. Patnaik. (2014). “Biometric template protection with DCT-based watermarking,” Machine Vision and Applications, vol. 25, no. 1, pp. 263–275. [Google Scholar]
33. S. Ghouzali. (2015). “Watermarking based multi-biometric fusion approach,” in Int. Conf. on Codes, Cryptology, and Information Security. Proc.: Lecture Notes in Computer Science, Rabat, Morocco, pp. 342–351. [Google Scholar]
34. M. A. M. Abdullah, S. S. Dlay, W. L. Woo and J. A. Chambers. (2016). “A framework for iris biometrics protection: A marriage between watermarking and visual cryptography,” IEEE Access, vol. 4, pp. 10180–10193. [Google Scholar]
35. L. R. Haddada, B. Dorizzi and N. E. Ben-Amaraa. (2017). “A combined watermarking approach for securing biometric data,” Signal Processing: Image Communication, vol. 55, pp. 23–31. [Google Scholar]
36. M. R. M. Isa, S. Aljareh and Z. Yusoff. (2017). “A watermarking technique to improve the security level in face recognition systems,” Multimedia Tools and Applications, vol. 76, no. 22, pp. 23805–23833. [Google Scholar]
37. N. Bousnina, S. Ghouzali, M. Mikram and W. Abdul. (2019). “DTCWT-DCT watermarking method for multimodal biometric authentication,” in 2nd Int. Conf. on Networking, Information Systems & Security, Rabat, Morocco, pp. 1–7. [Google Scholar]
38. L. R. Haddada and N. E. Ben-Amara. (2019). “Double watermarking-based biometric access control for radio frequency identification card,” International Journal of RF and Microwave Computer-Aided Engineering, vol. 29, no. 5, pp. 1–11. [Google Scholar]
39. K. Zebbiche, F. Khelifi and K. Loukhaoukha. (2018). “Robust additive watermarking in the dtcwt domain based on perceptual masking,” Multimedia Tools and Applications, vol. 77, no. 16, pp. 21281–21304. [Google Scholar]
40. H. I. Hsiao and J. Lee. (2015). “Fingerprint image cryptography based on multiple chaotic systems,” Signal Processing, vol. 113, pp. 169–181. [Google Scholar]
41. S. Ghouzali and W. Abdul. (2013). “Private chaotic biometric template protection algorithm,” in IEEE Second Int. Conf. on Image Information Processing, Shimla, India, pp. 655–659. [Google Scholar]
42. S. Rajendran and M. Doraipandian. (2018). “Biometric template security triggered by two dimensional logistic sine map,” Procedia Computer Science, vol. 143, pp. 794–803. [Google Scholar]
43. M. A. Murillo-Escobar, C. Cruz-Hernández, F. Abundiz-Pérez and R. M. López-Gutiérrez. (2015). “A robust embedded biometric authentication system based on fingerprint and chaotic encryption,” Expert Systems with Applications, vol. 42, no. 21, pp. 8198–8211. [Google Scholar]
44. C. Moujahdi, S. Ghouzali, M. Mikram, M. Rziza and G. Bebis. (2012). “Spiral Cube for biometric template protection,” in Int. Conf. on Image and Signal Processing. Proc.: Lecture Notes in Computer Science, Agadir, Morocco, pp. 235–244. [Google Scholar]
45. C. Moujahdi, G. Bebis, S. Ghouzali, M. Mikram and M. Rziza. (2016). “Biometric template protection using spiral Cube: performance and security analysis,” International Journal on Artificial Intelligence Tools, vol. 25, no. 01, pp. 1550027. [Google Scholar]
46. N. A. Hikal and M. M. Eid. (2020). “A new approach for palmprint image encryption based on hybrid chaotic maps,” Journal of King Saud University-Computer and Information Sciences, vol. 32, no. 7, pp. 870–882. [Google Scholar]
47. M. B. Hossain, M. T. Rahman, A. B. M. S. Rahman and S. Islam. (2014). “A new approach of image encryption using 3D chaotic map to enhance security of multimedia component,” in Int. Conf. on Informatics, Dhaka, Bangladesh: Electronics & Vision, pp. 1–6. [Google Scholar]
48. L. O’Gorman. (2003). “Comparing passwords, tokens, and biometrics for user authentication,” in Proc. of the IEEE, vol. 91, no. 12, pp. 2021–2040. [Google Scholar]
49. D. Maio, D. Maltoni, R. Cappelli, J. L. Wayman and A. K. Jain. (2002). “FVC2000: Fingerprint verification competition,” IEEE Transactions on Pattern Analysis and Machine Intelligence, vol. 24, no. 3, pp. 402–412. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |