DOI:10.32604/iasc.2020.013145

| Intelligent Automation & Soft Computing DOI:10.32604/iasc.2020.013145 |  |
| Article |
Uplink SCMA Codebook Reuse Transmission and Reception Scheme
1Qinghai Nationalities University, Xining, 810007, China
2Science and Technology on Micro-system Laboratory, Shanghai Institute of Micro-System and Information Technology, Chinese Academy of Sciences, Shanghai, 201800, China
3University of Chinese Academy of Sciences, Beijing, 100049, China
*Corresponding Author: Guoqing Jia. Email: guoqing.jia@qhmu.edu.cn
Received: 27 July 2020; Accepted: 20 September 2020
Abstract: Sparse code multiple access (SCMA) is a new non-orthogonal multiple access scheme suitable for 5G communication, which can effectively improve spectrum efficiency and support massive connections. Multiple users in the SCMA system realize the sharing of the same time-frequency resources by mapping data into codewords of a special code book (Code Book, CB). A typical SCMA system increases the spectrum utilization to 150%. In order to further improve the system spectrum utilization and increase the number of user connections, this paper proposes an uplink SCMA codebook reuse transmission and reception scheme (CB-Reuse-SCMA), which reuse a codebook to multiple users. The base station allocates β users to each codebook at the same time, so that β users use the same codebook to transmit uplink information. On the receiver of the base station, an improved Logarithmic Message Passing Algorithm (Log-MPA) is designed for multi-user detection, so that the base station can correctly detect the data of β users who reuse the same codebook. Simulation results show that at the time β = 2, the proposed scheme increased the spectrum utilization to 300%; at the time β = 3, the proposed scheme increased the spectrum utilization to 450%. Compared with the traditional SCMA scheme where the user has an exclusive codebook, the proposed scheme improves the spectrum utilization to β × 150% through codebook reuse at the expense of a small amount of SNR gain, which improves the throughput and user connection by β times number.
Keywords: 5G; code book reuse; log-MPA; spectrum utilization
Three major scenarios have been defined for 5G beyond 2020 [1]: enhanced mobile broadband (eMBB), massive machine type communication (mMTC), and ultra-reliable low-latency communications (URLLC). It has higher requirements than 4G in terms of spectrum utilization and number of connections, especially in the mMTC scenario [2–9]. Existing technologies such as orthogonal frequency division multiple access (OFDMA) are not sufficient to meet future communications requirements. In order to meet the exponential growth in the number of users in the future, 5G introduced a variety of non-orthogonal multiple access (Non-Orthogonal Multiple Access, NOMA) technology [10–14]. Among them, SCMA has attracted much attention because it can maintain good performance and complexity under high load rate [15].
SCMA is an upgraded version of low-density spread spectrum CDMA (LDS-CDMA) [16]. Unlike LDS-CDMA, SCMA directly maps different bitstreams to different sparse codewords. The multidimensional constellation is designed as a codebook, so it has a “shaping gain” that LDS cannot achieve. The codebook composed of subcarriers is SCMA The basic resource unit of the system [17,18].
Although a typical SCM system improves the spectrum efficiency to 150%, it is still insufficient to cope with the needs of large connection scenarios such as mMTC. Therefore, in order to continue to improve the spectrum efficiency of the system, the researchers also proposed many other solutions.
Kim et al. [19] combined NOMA and SCMA to add 4 regular users to a typical 6-user SCMA system, while Balasubramanya et al. [20] added a low rate to each orthogonal resource in the upstream SCMA system. LDR users, use continuous interference cancellation (SIC) and MPA to decode at the decoding end, that is, first decode the user with high power, then reconstruct the decoded user information and use SIC to eliminate its interference, and finally decode the remaining user. Both make the system spectrum utilization rate increase to 250%, but the increased system capacity is limited. At the same time, as the SNR increases, the system performance tends to saturate because the power difference between reuse users gradually decreases. Moltafet et al. [21] in a downlink multi-user system, by allocating power and resources for users, reused codebooks among multiple cells to analyze the system throughput [22]. In this scheme, for each additional user of codebook reuse, the total rate of the system increased by 25%. However, the design of the power and resource allocation scheme of this scheme is complicated. At the same time, because the decoding algorithm is based on SIC and MPA, the strong interference between users caused by the high reuse rate of the codebook will cause the user’s BER performance to decrease sharply. In order to improve the sum rate of the system, Sharma et al. [16] proposed a joint power and code domain scheme. At the sending end, the base station divides the near and far users into two clusters using different channel conditions of the users, namely: strong user clusters and weak user clusters. The transmitter uses SCMA technology to encode the users of the two clusters, and allocates different powers to the users of different clusters, so that the near and far users in the same cell can reuse the codebook. But the decoding algorithm of this scheme needs to design a complex power allocation scheme, and the two users reuse the codebook need to come from different clusters. Moreover, this scheme uses SIC in the decoding algorithm, and there is error propagation in the decoding process, and due to the maximum power limit at the transmitter, the performance of users with small power allocation is poor, resulting in poor system average BER performance. In addition, higher transmission power will also increase the user’s energy consumption, which does not meet the requirements of 5G low energy consumption. At the same time, the simulation results of the program show that the system capacity has not reached 200% of SCMA under the condition of SNR of 20 dB.
According to known literature, the spectrum efficiency improved by the existing work is still limited, and the existing technology still cannot cope with the future large connection scenario. Therefore, how to design a better SCMA large connection scheme still needs to be studied. To this end, this paper proposes an uplink SCMA transmission and reception scheme based on codebook reuse, which improves system throughput and improves the problem of poor performance of low-power users based on power allocation. This scheme is based on a scheduling mechanism. The base station allocates β users to each codebook, so that the BB users reuse the same codebook to send uplink information to the base station. At the receiving end of the base station, an improved logarithmic messaging algorithm is designed for multi-user detection, so that the base station can correctly detect the data of β users reuse the same codebook. The simulation results show that: at the expense of a small amount of BER performance, the proposed scheme improves the system spectrum efficiency and the number of user connections to β times.
3 Transmission Scheme of Uplink CB-Reuse-SCMA System
Assume that in a scheduling-based uplink multi-user SCMA communication system, a base station serves J users with the same priority, and the system has LK-dimensional codebooks of size M, where M is the user data modulation order and K is the resource number. In Fig. 1a schematic diagram of the uplink CB-Reuse-SCMA system model is shown, in which the base station allocates β users according to each codebook and each user only allocates one codebook, so that β users use the same The codebook transmits uplink information. At the user’s sending end, the SCMA encoder maps the user’s 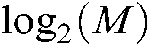 bit data to the codebook and outputs a K-dimensional codeword. Among them, the K-dimensional codeword is a sparse vector with
bit data to the codebook and outputs a K-dimensional codeword. Among them, the K-dimensional codeword is a sparse vector with  non-zero units, and the choice of N depends on the resource mapping matrix. The data streams of J users share K orthogonal time-frequency resources and transmit to the same base station after codebook mapping. The overload factor is defined as
non-zero units, and the choice of N depends on the resource mapping matrix. The data streams of J users share K orthogonal time-frequency resources and transmit to the same base station after codebook mapping. The overload factor is defined as 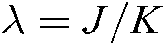 , among which
, among which 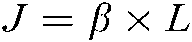 .
.
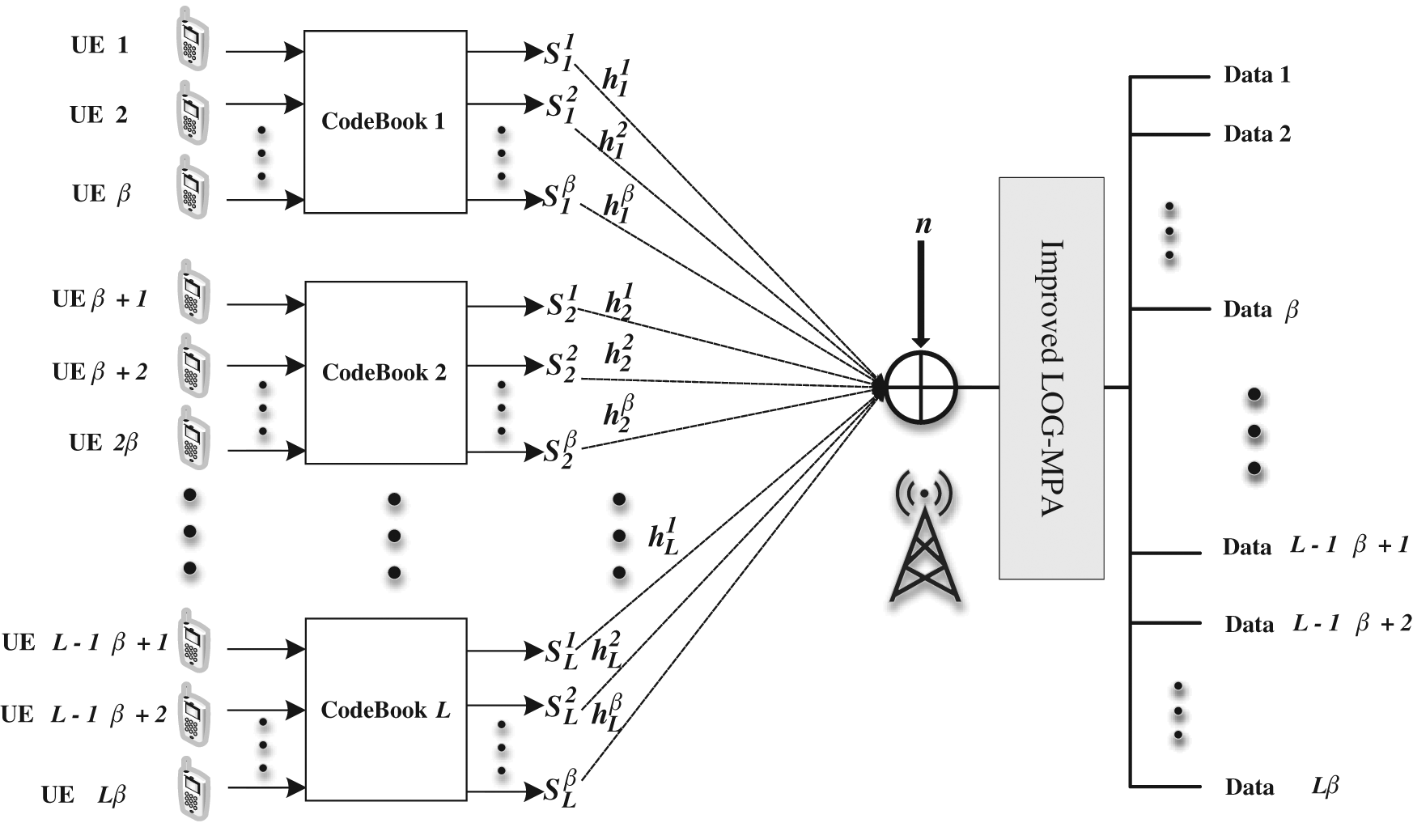
Figure 1: Uplink CB-Reuse-SCMA system model
In uplink transmission, it is assumed that all users are synchronized in time. Let 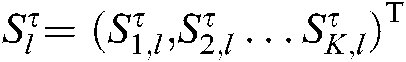 and
and 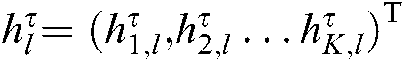 denote the codewords of the l-th user using the
denote the codewords of the l-th user using the 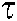 -th codebook and spread to the codewords of K subcarriers after the codebook mapping and the channel coefficients of K subcarriers, among them
-th codebook and spread to the codewords of K subcarriers after the codebook mapping and the channel coefficients of K subcarriers, among them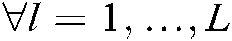 and
and 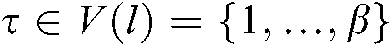 . In this system, the codebook is designed using conventional methods [23], that is, the number of subcarriers
. In this system, the codebook is designed using conventional methods [23], that is, the number of subcarriers 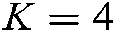 , the modulation order
, the modulation order 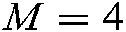 , the codebook effectively carries
, the codebook effectively carries 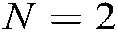 , and the subcarriers effectively carry
, and the subcarriers effectively carry 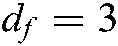 . In the system of Fig. 1, β users reuse the same codebook l, and the data stream outputs codeword
. In the system of Fig. 1, β users reuse the same codebook l, and the data stream outputs codeword  after codebook mapping. At this time, the data of β users is sparsely spread to the same orthogonal according to the resource mapping matrix On the subcarriers, the factor graph representing the resource mapping relationship is shown in Fig. 2.
after codebook mapping. At this time, the data of β users is sparsely spread to the same orthogonal according to the resource mapping matrix On the subcarriers, the factor graph representing the resource mapping relationship is shown in Fig. 2.
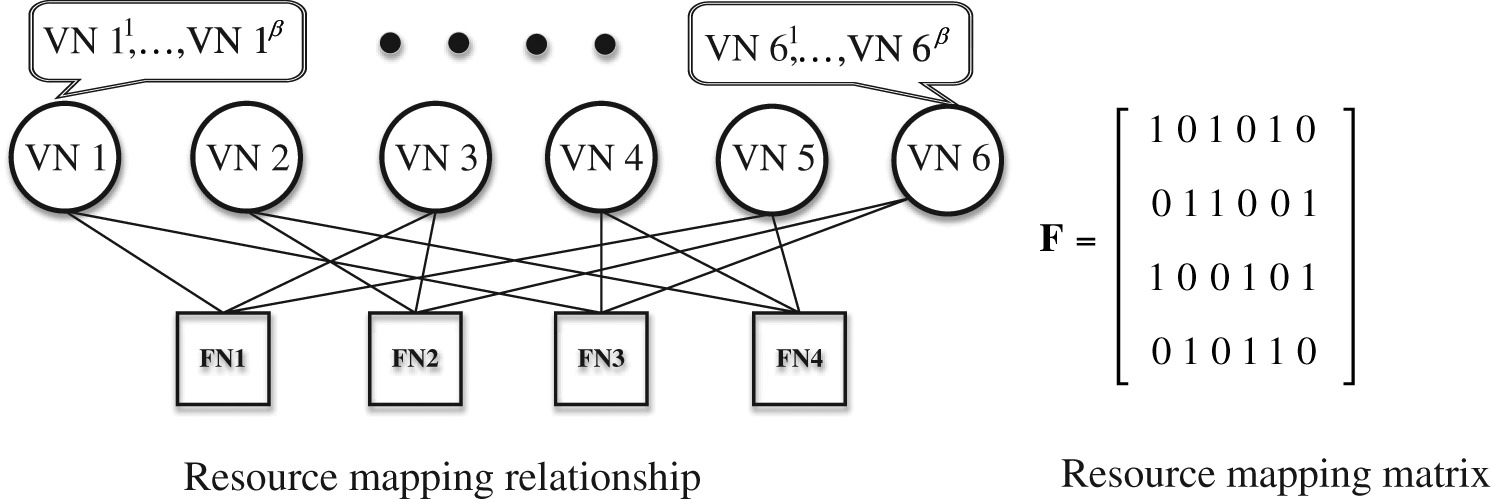
Figure 2: System factor diagram of 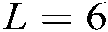 ,
, 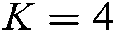
The resource mapping relationship in Fig. 2 includes two different types of nodes: K functional nodes FN (representing K subcarriers); L variable nodes VN (representing L codebooks), where each VN node contains β user nodes; the connection indicates the bearing relationship between user data and resources. Each column of the resource mapping matrix represents the resource mapping relationship of the corresponding codebook. The resource mapping relationship of β users reuse the same codebook is the same, that is, β users reuse the same column of the resource mapping matrix.
Therefore, the received signal of the base station receiver is

In the formula, 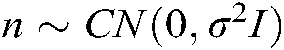 is the Gaussian white noise. The data of β users reuse the codebook l is superimposed on the same resource.
is the Gaussian white noise. The data of β users reuse the codebook l is superimposed on the same resource.
Then the received signal on the k-th carrier is:

In the formula, 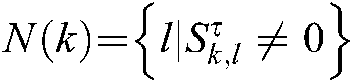 is the codebook effective bearer set, and
is the codebook effective bearer set, and 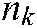 represents the noise on the k-th subcarrier.
represents the noise on the k-th subcarrier.
4 Multi-user Detection Algorithm
Log-MPA is a multi-user detection algorithm commonly used in SCMA systems [23]. It is a near-optimal iterative detection algorithm that models receivers based on factor graphs to detect multi-users. Log-MPA first iteratively detects the user codeword probability and judges the user codeword by the log-likelihood ratio (LLR). The Log-MPA decoding process is shown in Fig. 3. The Log-MPA decoder first calculates the conditional probability based on the received signal and the estimated channel correlation coefficient and noise power value; then the conditional probability and the code prior probability are used as external information Input iterative message transmission inside the FN node, by iteratively transmitting the codeword probability information between the FN node and the VN node, after reaching the maximum number of iterations, the posterior probability information of the codeword is output as soft information; finally the LLR hard decision Get user codeword information.
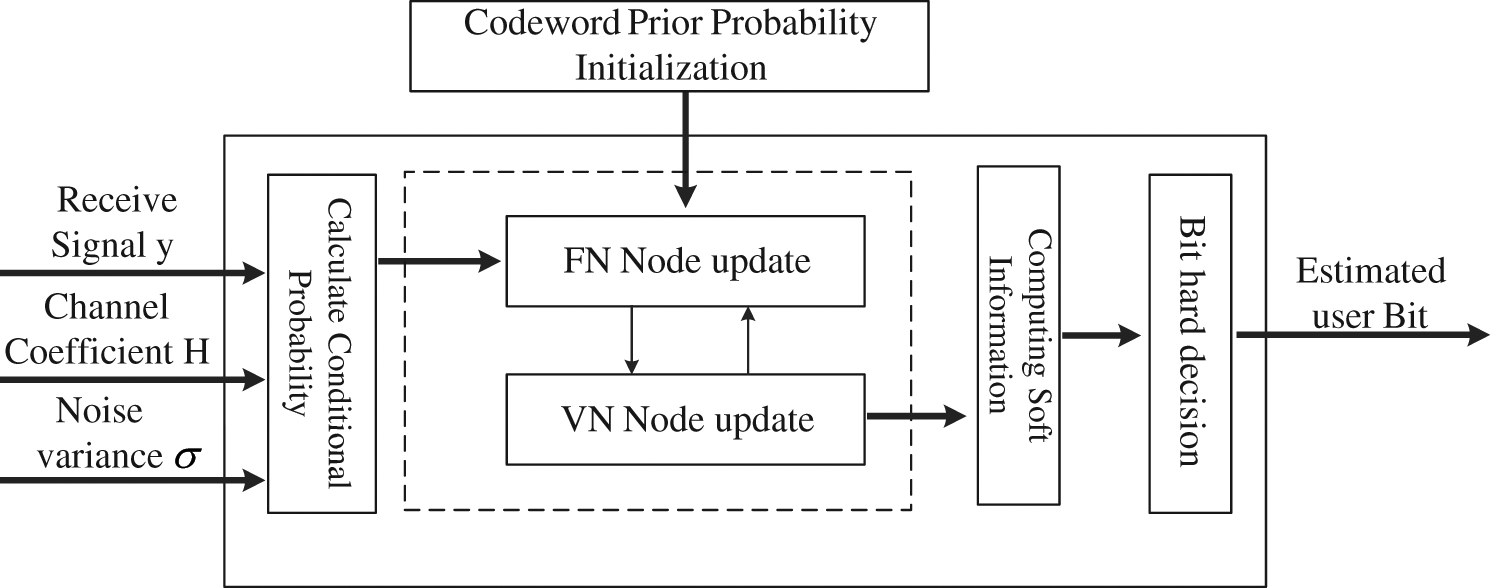
Figure 3: Log-MPA decoding flow diagram
However, the Log-MPA algorithm is designed for the SCMA system where the user monopolizes the codebook, and cannot detect the multi-user data of the codebook reuse in this system. In order to detect the multi-user data of this system, the Log-MPA algorithm is improved, and the corresponding detection algorithm is designed. The main difference between the improved algorithm and the original Log-MPA is that when the log-MPA algorithm iteratively updates the codeword probability of a VN node, only the codeword probability of a single user on that node is updated, because the original SCMA system user monopolizes the codebook; improved The detection algorithm simultaneously updates the codeword probability of AAA users reuse the node when iteratively updating the codeword probability of the VN node. The improved Log-MPA decoding process is shown in Fig. 4.
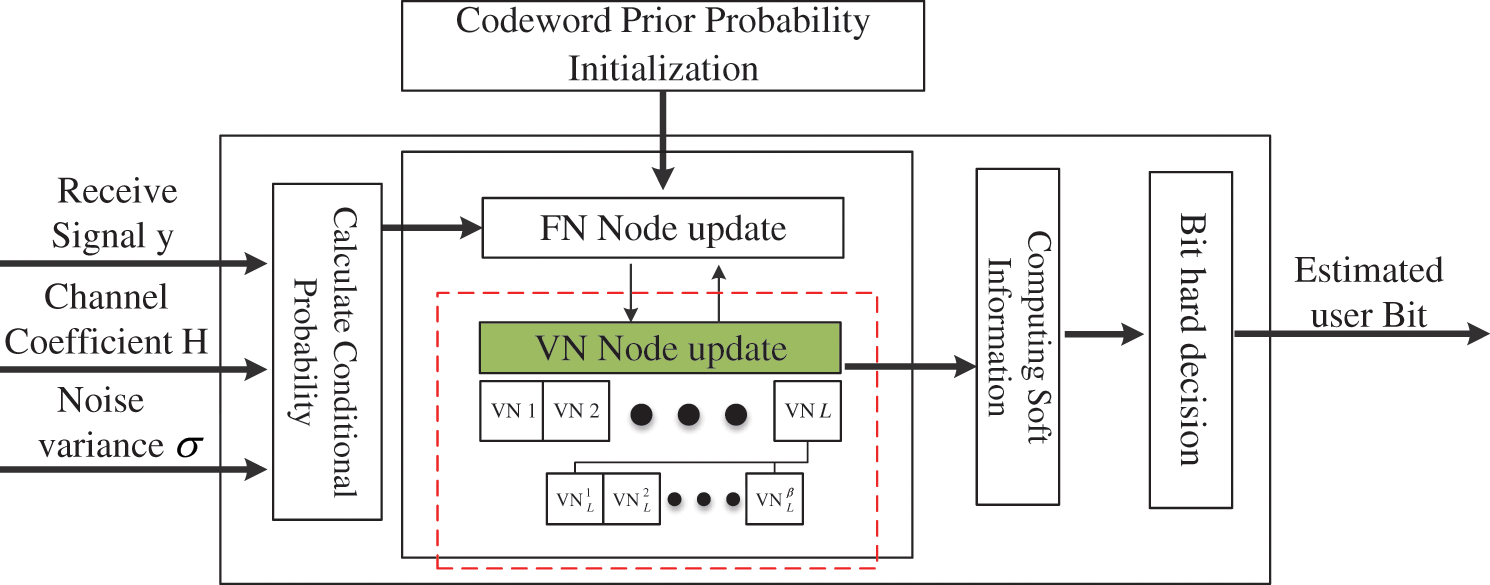
Figure 4: Improved Log-MPA decoding flow diagram
It is assumed that the base station has perfect channel coefficients and noise information. Let  represent the codeword
represent the codeword 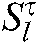 of the
of the 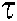 th user using the l-th codebook at the t-th iteration from FN node k to VN node
th user using the l-th codebook at the t-th iteration from FN node k to VN node  , and
, and  represents the external information from VN node l to FN node
represents the external information from VN node l to FN node 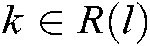 . Among them,
. Among them, 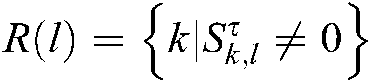 represents the effective carrier set of subcarriers, and
represents the effective carrier set of subcarriers, and 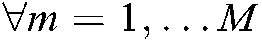 represents the M possibilities of arbitrary codewords.
represents the M possibilities of arbitrary codewords.
Step 1: Initialize the code word prior probability of each user and calculate the conditional probability of each FN node:
(a) Since the probability of M possibilities of any codeword 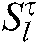 sent by the user is the same, the a priori probability is:
sent by the user is the same, the a priori probability is:
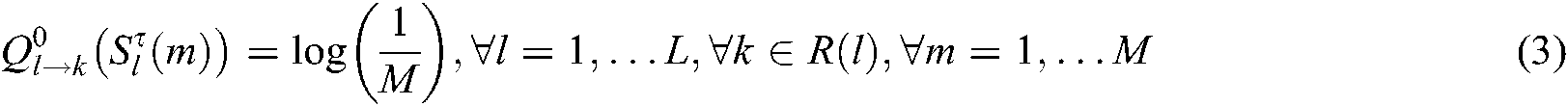
(b) The formula for calculating the conditional probability of the codeword on FN node k is:
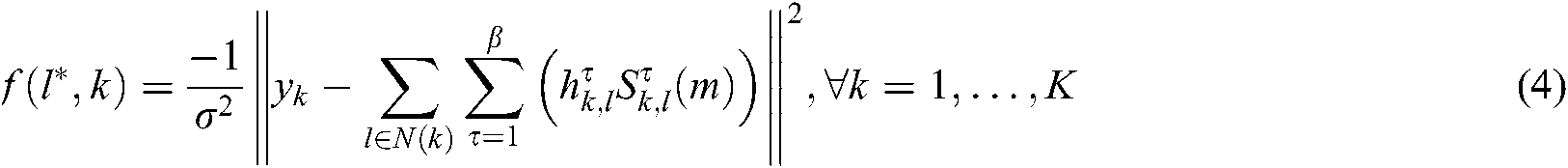
Among them, 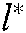 represents
represents 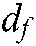 codebook units super-imposed on the functional node FN, and each unit has β users. The meaning of conditional probability is to estimate the probability of M kinds of possibilities of each codeword by calculating the Euclidean distance between the codeword and the received signal. The probability is the largest when the codeword estimates are all correct. In this system, β users reuse the codebook, so when calculating the codeword probability of users in codebook l, the codeword information of β users is superimposed.
codebook units super-imposed on the functional node FN, and each unit has β users. The meaning of conditional probability is to estimate the probability of M kinds of possibilities of each codeword by calculating the Euclidean distance between the codeword and the received signal. The probability is the largest when the codeword estimates are all correct. In this system, β users reuse the codebook, so when calculating the codeword probability of users in codebook l, the codeword information of β users is superimposed.
Step 2: Iteratively update the information of the FN node and VN node:
(a) Update the codeword probability of VN node l, the initial iteration uses the initialized  as the codeword probability, and then updates the information using Eq. (8). The VN node l contains data of β users, so when the codeword probability of VN node l is updated, the codeword information of β users is updated at the same time. At the t-th iteration, the codeword update formula of the
as the codeword probability, and then updates the information using Eq. (8). The VN node l contains data of β users, so when the codeword probability of VN node l is updated, the codeword information of β users is updated at the same time. At the t-th iteration, the codeword update formula of the 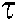 -th user is:
-th user is:

where,
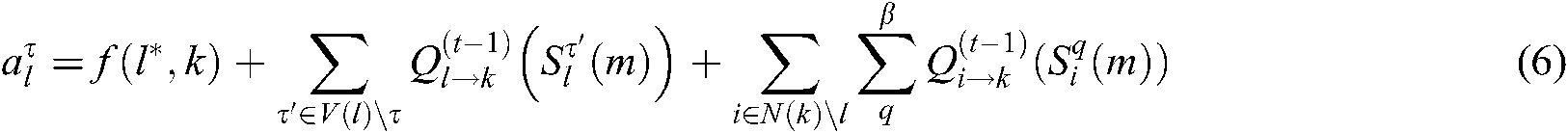
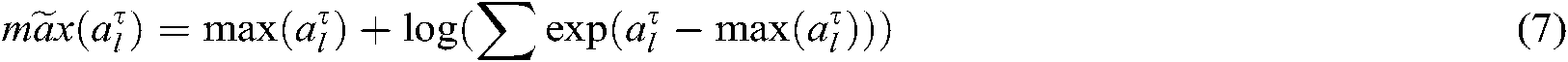
The meaning of Eq. (5) is to combine the codeword information of other users on subcarrier k to calculate the maximum probability of M codewords 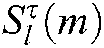 and update the VN node information. In formula (6),
and update the VN node information. In formula (6), 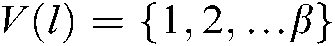 .
.
(b) Update the codeword probability of FN node k:
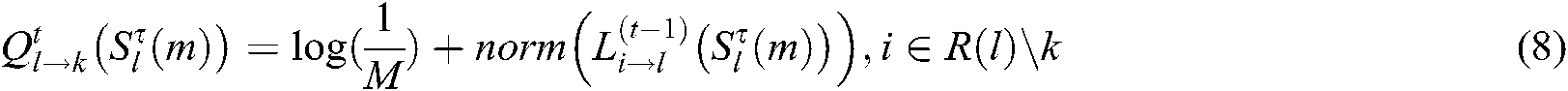
The VN node l transmits the updated code word information to the N FN nodes connected to it, and then the FN node k combines the code word prior information to update the code word information. Among them, 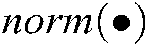 means normalization.
means normalization.
(c) Output the posterior probability of codeword 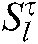 :
:
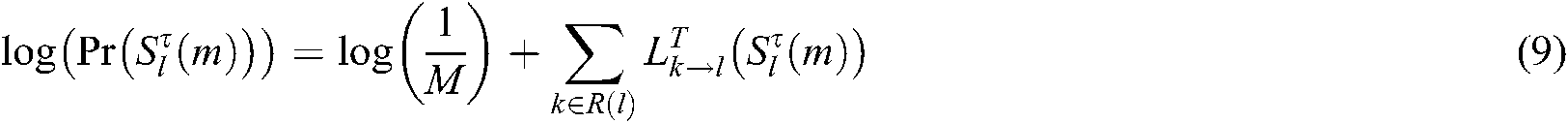
The VN node combines the codeword prior information and the updated codeword probability as the node’s posterior information. When updating the posterior information of the VN node l, the posterior probability of the codewords of β users is updated at the same time.
Step 3: Calculate LLR and estimate 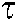 user’s bit data
user’s bit data 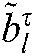 :
:
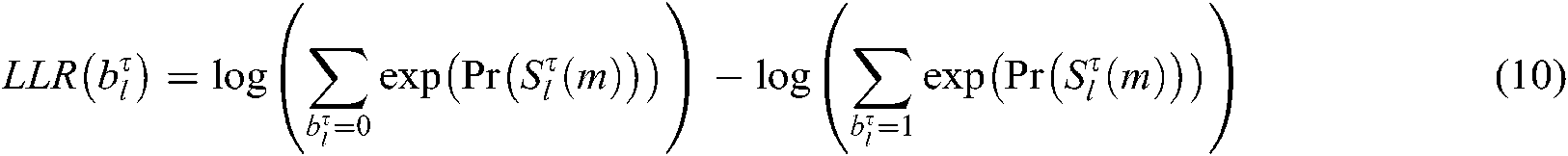

The improved Log-MPA detection algorithm is summarized as Algorithm 1:
Algorithm 1: The improved Log-MPA detection algorithm

5 Numerical Results and Analysis
To verify the performance of the proposed scheme, this section compares the bit error rate and throughput performance of SCMA and CB-Reuse-SCMA systems in the AWGN channel uplink scenario by simulation. The simulation parameters are set as follows: number of symbols N = 500000, L = 6, Nit = 7, 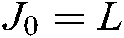 , K = 4; codebook reuse times in CB-Reuse-SCMA system are β,
, K = 4; codebook reuse times in CB-Reuse-SCMA system are β, 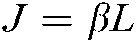 , K = 4.
, K = 4.
In Fig. 5, it shows a comparison of the BER performance of SCMA and CB-Reuse-SCMA, which verifies the BER performance of the two schemes with the same parameters changing with SNR. It can be seen from the Fig. 5 that the BER performance of SCMA and CB-Reuse-SCMA both increase as the SNR increases. Because CB-Reuse-SCMA reuses the same codebook results in interference between users of the reuse codebook, the BER performance of CB-Reuse-SCMA is lower than SCMA. But with the increase of SNR, the BER performance of CB-Reuse-SCMA is gradually approaching SCMA. The BER performance of CB-Reuse-SCMA when the SNR is 20 dB is the same as the BER performance of the SCMA when the SNR is 18 dB, namely: CB-Reuse-SCMA reduces the SNR gain by about 2 dB.
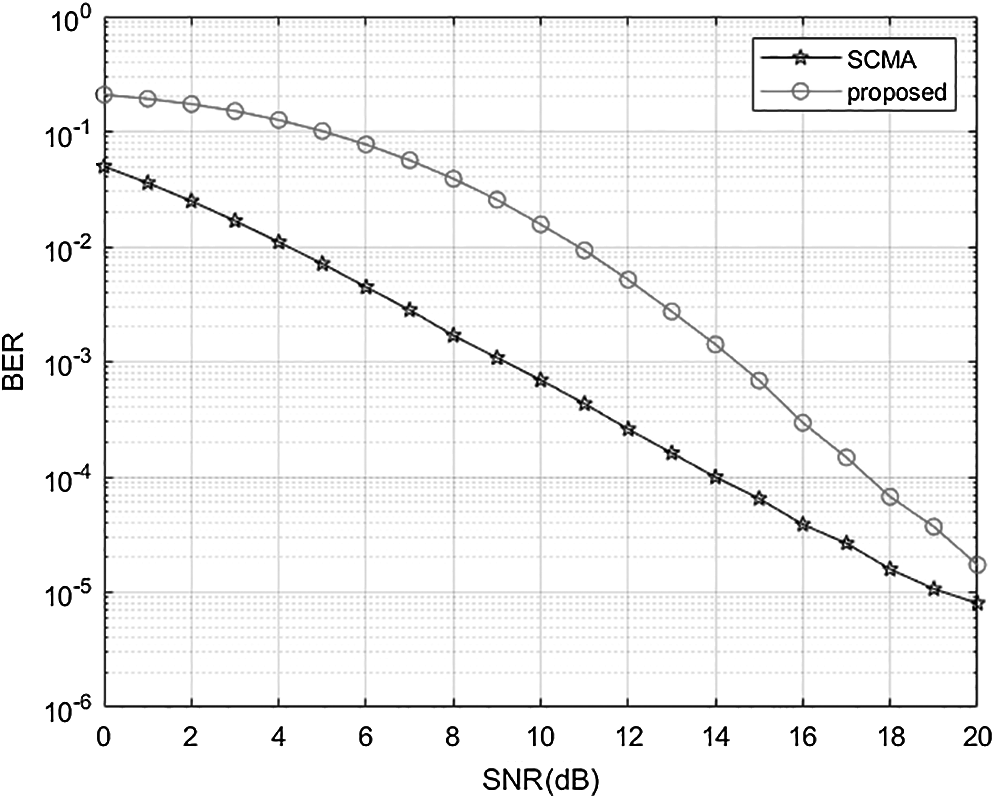
Figure 5: BER performance comparisons of SCMA and CB-Reuse-SCMA
In Fig. 6a throughput simulation diagram of the CB-Reuse-SCMA system is shown, and compares the SCMA and SCMA+LDR schemes [24]. In the case of 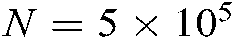 , the three schemes all use the same codebook. The SCMA user modulation mode is QPSK, that is, M = 4, so the bit data of a single SCMA user is 1 × 106. Among them, low-rate (LDR) users use BPSK modulation, the bit data of a single LDR user is 0.5 × 106. It can be seen from the Fig. 6 that as the SNR increases, the throughput of the three schemes gradually converges. This is because as the SNR increases, the BER performance of the system gradually increases. SCMA converges after 10 dB and the throughput is 6 Mbit. The SCMA+LDR scheme gradually converges after the SNR is 18 dB. This is because the average BER performance of the system is poor under low signal-to-noise ratio, and the throughput after convergence is about 8 Mbit. The proposed scheme fully converges at 12 dB, that is, the BER performance of CB-Reuse-SCMA is better than SCMA+LDR. At the same time, the throughput of CB-Reuse-SCMA is 12 Mbit, which is 2 times of SCMA and 1.5 times of SCMA+LDR.
, the three schemes all use the same codebook. The SCMA user modulation mode is QPSK, that is, M = 4, so the bit data of a single SCMA user is 1 × 106. Among them, low-rate (LDR) users use BPSK modulation, the bit data of a single LDR user is 0.5 × 106. It can be seen from the Fig. 6 that as the SNR increases, the throughput of the three schemes gradually converges. This is because as the SNR increases, the BER performance of the system gradually increases. SCMA converges after 10 dB and the throughput is 6 Mbit. The SCMA+LDR scheme gradually converges after the SNR is 18 dB. This is because the average BER performance of the system is poor under low signal-to-noise ratio, and the throughput after convergence is about 8 Mbit. The proposed scheme fully converges at 12 dB, that is, the BER performance of CB-Reuse-SCMA is better than SCMA+LDR. At the same time, the throughput of CB-Reuse-SCMA is 12 Mbit, which is 2 times of SCMA and 1.5 times of SCMA+LDR.
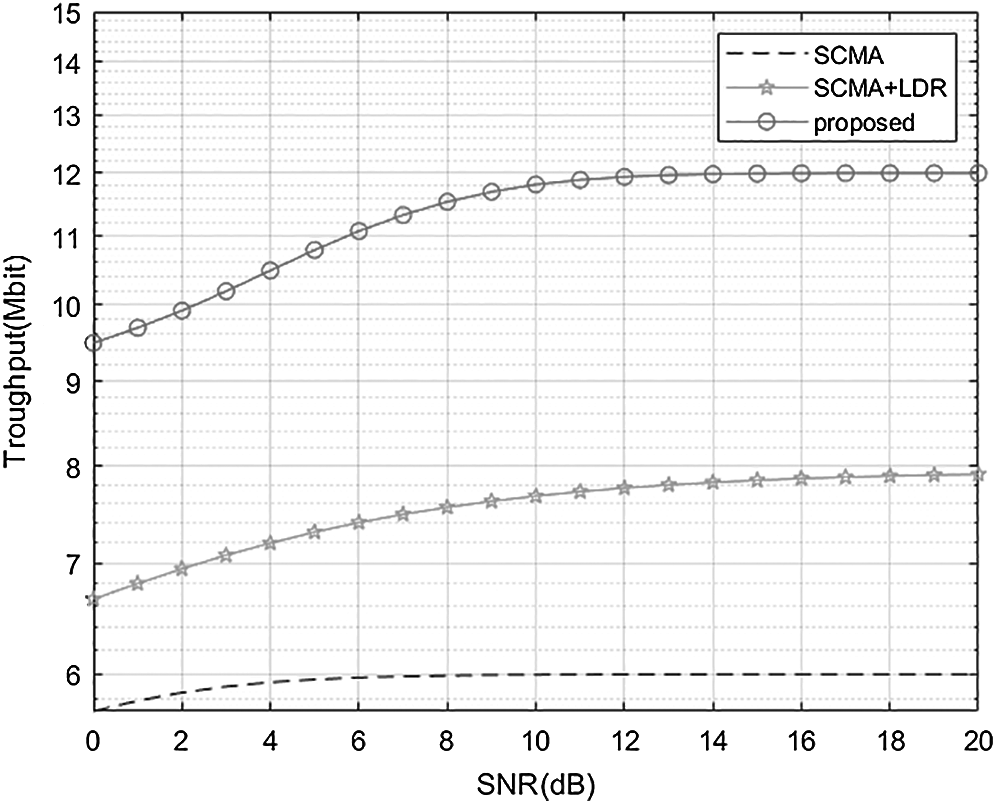
Figure 6: Throughput comparisons of SCMA and CB-Reuse-SCMA
In addition, in order to verify the throughput of the proposed scheme with SNR conversion under different β, In Fig. 7, the system throughput with β of 1, 2, 3 and SNR of 12, 16, 20, and 24 dB is simulated. Among them, β = 1 is the original SCMA scheme, that is: the number of users J = 6. It can be seen from the Fig. 7 that with the increase of β, the system throughput increases, but the SNR required for system convergence also increases. Among them, β = 1 and β = 2 have converged when SNR = 12 dB, and β = 3 has completely converged when SNR = 24 dB. Therefore, the system throughput of the proposed scheme is proportional to β.
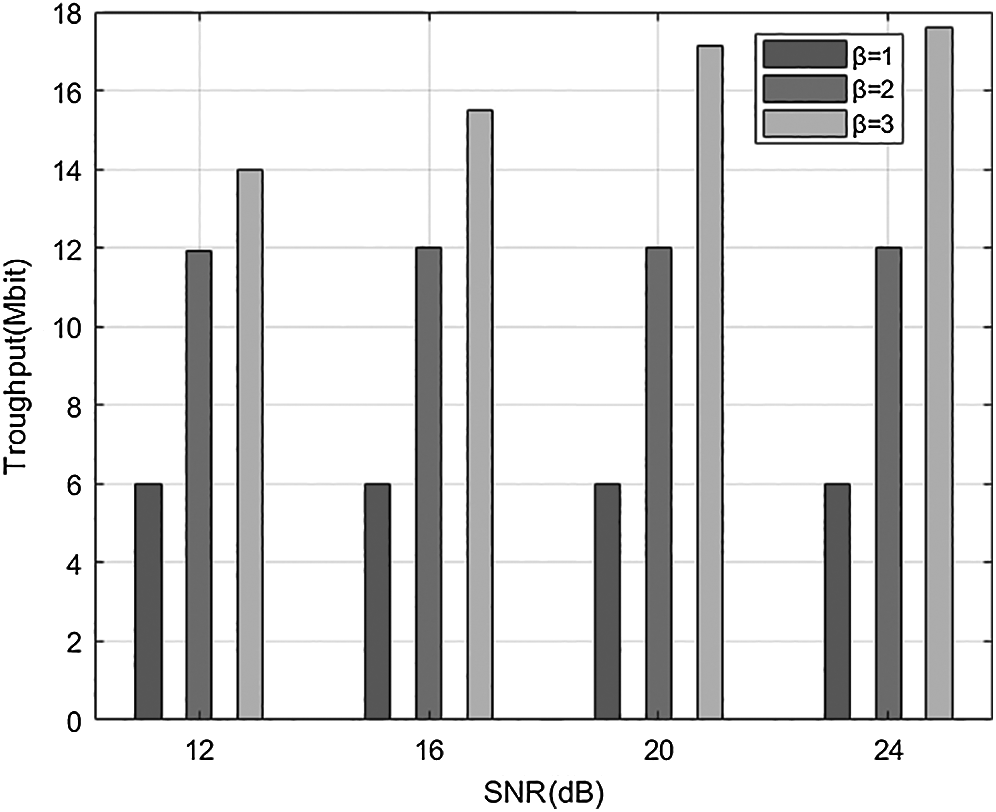
Figure 7: CB-Reuse-SCMA throughput comparisons under different 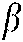 and SNR
and SNR
In order to cope with the rapid increase in 5G spectrum efficiency and the number of user connections, and to address the shortcomings of existing technologies, an uplink SCMA transmission and reception scheme based on codebook multiplexing is proposed. This scheme assigns β users with the same priority to the same codebook. At the user transmitting end, β users map superimposed data according to the assigned codebook. At the receiving end of the base station, multi-user detection is performed according to the improved Log-MPA algorithm. Simulation results prove that the proposed scheme effectively improves the throughput of the system and achieves an increase in the number of access users, while the number of access users is proportional to β.
Funding Statement: This work is supported by the National Natural Science Foundation of Qinghai Province, China (No. 2020-ZJ-724).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. Agiwal, A. Roy and N. Saxena. (2016). “Next generation 5G wireless networks: a comprehensive survey,” IEEE Communications Surveys & Tutorials, vol. 18, no. 3, pp. 1617–1655. [Google Scholar]
2. W. Fang, W. Zhang, Q. Zhao, X. Ji, W. Chen. (2019). et al., “Comprehensive analysis of secure data aggregation scheme for industrial wireless sensor network,” Computers Materials & Continua, vol. 61, no. 2, pp. 583–599. [Google Scholar]
3. F. Bi, X. Fu, W. Chen, W. Fang, X. Miao. (2020). et al., “Fire detection method based on improved fruit fly optimization-based SVM,” Computers Materials & Continua, vol. 62, no. 1, pp. 199–216. [Google Scholar]
4. W. Fang, N. Cui, W. Chen, W. Zhang and Y. Chen, “A trust-based security system for data collecting in smart city,” IEEE Transactions on Industrial Informatics. [Google Scholar]
5. C. Bockelmann, N. Pratas, H. Nikopour, K. Au, T. Svensson. (2016). et al., “Massive machine-type communications in 5G: physical and MAC-layer solutions,” IEEE Communications Magazine, vol. 54, no. 9, pp. 59–65. [Google Scholar]
6. X. F. Li, Y. B. Zhuang and S. X. Yang. (2017). “Cloud computing for big data processing,” Intelligent Automation & Soft Computing, vol. 23, no. 4, pp. 545–546. [Google Scholar]
7. J. Peng, M. Tang, M. Li and Z. Zha. (2017). “A load balancing method for massive data processing under cloud computing environment,” Intelligent Automation & Soft Computing, vol. 23, no. 4, pp. 547–553. [Google Scholar]
8. W. Wu, Y. Chen and D. Seng. (2017). “Implementation of Web mining algorithm based on cloud computing,” Intelligent Automation & Soft Computing, vol. 23, no. 4, pp. 599–604. [Google Scholar]
9. W. Zhang, W. Fang, Q. Zhao, X. Ji and G. Jia. (2020). “Energy efficiency in internet of things: An overview,” Computers Materials & Continua, vol. 63, no. 2, pp. 787–811. [Google Scholar]
10. Y. Liu, Z. Qin, M. Elkashlan, Z. Ding, A. Nallanathan. (2017). et al., “Nonorthogonal multiple access for 5G and beyond,” Proc. of the IEEE, vol. 105, no. 12, pp. 2347–2381. [Google Scholar]
11. L. Tian, C. Yan, W. Li, Z. Yuan, W. Cao. (2017). et al., “On uplink non-orthogonal multiple access for 5G: Opportunities and challenges,” China Communications, vol. 14, no. 12, pp. 142–152. [Google Scholar]
12. Z. Wu, K. Lu, C. Jiang and X. Shao. (2018). “Comprehensive study and comparison on 5G NOMA schemes,” IEEE Access, vol. 6, pp. 18511–18519. [Google Scholar]
13. S. M. R. Islam, N. Avazov, O. A. Dobre and K. Kwak. (2017). “Power-domain non-orthogonal multiple access (NOMA) in 5G systems: potentials and challenges,” IEEE Communications Surveys & Tutorials, vol. 19, no. 2, pp. 721–742. [Google Scholar]
14. Z. Ding, X. Lei, G. K. Karagiannidis, R. Schober, J. Yuan. (2017). et al., “A survey on non-orthogonal multiple access for 5G networks: Research challenges and future trends,” IEEE Journal on Selected Areas in Communications, vol. 35, no. 10, pp. 2181–2195. [Google Scholar]
15. R. Hoshyar, F. P. Wathan and R. Tafazolli. (2008). “Novel low-density signature for synchronous CDMA systems over AWGN channel,” IEEE Transactions on Signal Processing, vol. 56, no. 4, pp. 1616–1626. [Google Scholar]
16. H. Nikopour and H. Baligh. (2013). “Sparse code multiple access,” in Proc. PIMRC, New York, USA, pp. 332–336. [Google Scholar]
17. J. V. D. Beek and B. M. Popovic. (2009). “Multiple access with low-density signatures,” in Proc. GLOBELCOM, Honolulu, HI, USA, pp. 1–6. [Google Scholar]
18. N. Kim and D. Cho. (2017). “Hybrid multiple access system based on non orthogonality and sparse code,” in Proc. WCNC, New York, USA, pp. 1–6. [Google Scholar]
19. N. M. Balasubramanya, A. Gupta and M. Sellathurai. (2018). “Combining code-domain and power-domain NOMA for supporting higher number of users,” in Proc. GLOBALCOM Conf., Abu Dhabi, United Arab Emirates, pp. 1–6. [Google Scholar]
20. M. Moltafet, N. Mokari, M. R. Javan, H. Saeedi and H. Pishro-Nik. (2018). “A new multiple access technique for 5G: Power domain sparse code multiple access (PSMA),” IEEE Access, vol. 6, pp. 747–759, . DOI 10.1109/ACCESS.2017.2775338. [Google Scholar]
21. M. Moltafet, N. Mokari, M. R. Javan, H. Saeedi and H. Pishro-Nik. (2017). “PSMA for 5G: Network throughput analysis,” in Proc. PIMRC, Montreal, QC, pp. 1–6. [Google Scholar]
22. S. Sharma, K. Deka, V. Bhatia and A. Gupta. (2019). “Joint power-domain and SCMA-based NOMA system for downlink in 5G and beyond,” IEEE Communications Letters, vol. 23, no. 6, pp. 971–974. [Google Scholar]
23. P. Robertson, E. Villebrun and P. Hoeher. (1995). “A comparison of optimal and sub-optimal MAP decoding algorithms operating in the log domain,” in Proc. ICC ’95, Seattle, WA, USA, 2, pp. 1009–1013. [Google Scholar]
24. S. Zhang, K. Xiao, B. Xiao, Z. Chen, B. Xia et al. (2016). , “A capacity-based codebook design method for sparse code multiple access systems,” in Proc. WCSP, Yangzhou, China, pp. 1–5. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |