 Open Access
Open Access
ARTICLE
Blockchain-Based Message Authentication Scheme for Internet of Vehicles in an Edge Computing Environment
1 College of Artificial Intelligence and Manufacturing, Hechi University, Yizhou, 546300, China
2 College of Big Data and Computer, Hechi University, Yizhou, 546300, China
* Corresponding Author: Zhong Ruan. Email:
Computer Systems Science and Engineering 2024, 48(5), 1301-1328. https://doi.org/10.32604/csse.2024.051796
Received 15 March 2024; Accepted 11 July 2024; Issue published 13 September 2024
Abstract
As an important application of intelligent transportation system, Internet of Vehicles (IoV) provides great convenience for users. Users can obtain real-time traffic conditions through the IoV’s services, plan users' travel routes, and improve travel efficiency. However, in the IoV system, there are always malicious vehicle nodes publishing false information. Therefore, it is essential to ensure the legitimacy of the source. In addition, during the peak period of vehicle travel, the vehicle releases a large number of messages, and IoV authentication efficiency is prone to performance bottlenecks. Most existing authentication schemes have the problem of low authentication efficiency in the scenario. To address the above problems, this paper designs a novel reliable anonymous authentication scheme in IoV for Rush-hour Traffic. Here, our scheme uses blockchain and elliptic curve cryptography (ECC) to design authentication algorithms for message authentication between vehicles and roadside units (RSU). Additionally, we introduce the idea of edge computing into the scheme, RSU will select the most suitable vehicle as the edge computing node for message authentication. In addition, we used the ProVerif tool for Internet security protocols and applications to test its security, ensuring that it is secure under different network attacks. In the simulation experiment, we compare our scheme with other existing works. Our scheme has a significant improvement in computational overhead, authentication efficiency and packet loss rate, and is suitable for traffic scenarios with large message volume.Keywords
1.1 Background and Research Motivation
With the continuous maturity of intelligent vehicle technology, IoV technology has become one of the most popular topics today [1]. The main goal of IoV is to provide road services to achieve traffic management and road safety [2]. In the traditional IoV system, it mainly includes three types of communication entities: Trusted Authority (TA), RSU and vehicle [3]. Vehicles can collect daily driving data and road traffic information through sensing technology and periodically send them to RSUs or other vehicles according to the DSRC [4] standard. RSU is an indispensable role [5], which is responsible for collecting and authenticating traffic messages sent by vehicles [6]. As a trusted center in the IoV, TA serves as a registration task for RSUs and vehicles [7,8]. The traditional model is shown in Fig. 1.

Figure 1: Traditional model of IoV
As an open network, IoV uses wireless electromagnetic wave communication technology to realize V2X communication [9]. In this communication environment, messages sent by vehicles can be easily intercepted and tampered by attackers, and their authenticity, integrity and legitimacy are uncertain [10,11]. In order to filter false information and improve the IoV’s reliability, RSU needs to verify the legitimacy of traffic information generated by vehicles [12]. In addition, when the vehicle sends traffic-related information, it does not want others to know some sensitive information (such as real identity, location information, etc.) [13]. Therefore, vehicles can use pseudonyms to achieve privacy protection during communication. In IoV, the combination of privacy protection and traceability is called conditional privacy protection [14]. In today’s IoV authentication mechanism, the higher the degree of privacy protection, the greater the computational and communication overhead. Especially in the traditional certificate authentication mechanism, the defect of excessive consumption of computing and storage resources is particularly obvious [15]. Nowadays, cloud computing technology has been widely used in IoV. But cloud computing also has limitations, that is, there is a higher transmission delay. During the peak period of vehicle travel, the vehicle releases a large number of messages, IoV authentication efficiency is prone to performance bottlenecks.
With the further development of technology, edge computing technology is introduced in IoV. As a new computing model that processes data away from the network center [16], edge computing can use flexible mechanisms and strategies to process sensitive information on edge terminal nodes. In addition, we no longer use the traditional certificate authentication mechanism, but use the encryption algorithm with lower computational complexity to reduce the consumption.
This paper focuses on the research of IoV related applications, we combine blockchain and edge computing technology to design an efficient message authentication algorithm. The main research results of this paper are as follows:
(1) In the face of peak traffic scenarios, the message authentication work of the Internet of Vehicles is prone to bottlenecks. This paper is inspired by the idea of edge computing and applies it to the authentication scheme. RSU will select the most suitable vehicle as the edge computing node for message authentication according to the real-time location distance and computing load. In addition, we also use blockchain and elliptic cryptographic curve to design the authentication algorithm, which reduce authentication latency, decrease packet loss ratio and alleviate network congestion indirectly.
(2) To verify security, we conducted ProVerif simulation experiments and theoretical analysis, which prove its security and correctness. In terms of performance, simulation experiments show that our scheme can also achieve fast authentication of messages during peak hours of traffic flow, and has lower computation and transmission over-head. With the addition of edge computing nodes, the packet loss rate (PLR) of IoV system was improved.
The article is divided into seven chapters. The first chapter mainly introduces the IoV and main contributions of the article. In the following chapters, we focus on the current research status of the IoV authentication scheme. The third chapter describes the background of the entire IoV system and some related theories of cryptography. The fourth chapter describes the specific authentication scheme designed by the article. In Chapter 5, we theoretically prove that the scheme is secure. In Chapter 6, the simulation results show that the scheme is efficient. Finally, the seventh chapter summarizes this paper and looks forward to the future development.
2.1 PKI-Based Authentication Scheme
At present, Public Key Infrastructure (PKI) authentication schemes are very popular in IoV systems, this type of authentication scheme is recognized by the IEEE 1609.2 standard. Raya et al. [17] proposed an authentication scheme that can protect user identity privacy. TA will generate many key pairs and certificates for these vehicles in advance, so that these vehicles can sign the message. In reference [18], Scholars have optimized and improved the traditional PKI scheme and applied it to the IoV, which further improves the user's privacy while ensuring message integrity. Lu et al. [19] designed a new authentication mechanism using bilinear pairing cryptography algorithm. In this scenario, the certificate issuer is no longer TA, but RSU. RSU issues temporary certificates to passing vehicles for communication purposes. To sum up, these authentication mechanisms have great defects, and their overhead is very large, which is not suitable for IoV scenario. Especially when the traffic flow is particularly large, the system will face increasing pressure.
2.2 Identity-Based Authentication Scheme
Because PKI-based authentication schemes consume a lot, researchers have proposed a new scheme [20]. In these schemes, TA and RSU do not need to generate certificates for users, it greatly reduces the resource consumption. Kyung et al. [21] proposed to use pseudonym signature to protect user privacy in V2I communication. However, in this scheme, malicious nodes can modify information and cannot guarantee security. Vasudev et al. [22] implemented anonymous authentication between communicating entities through physical unclonable functions, but it cannot prevent man-in-the-middle attacks. Harsha et al. [23] designed a scheme with very low computational complexity. After mutual authentication, vehicle and RSU communicate through key negotiation. Although the performance of scheme is optimized, its security is weakened. Once a malicious event occurs, RSU cannot locate and track and know the identity of the malicious node. Zhang et al. [24] proposed the idea of batch authentication. Compared with other scheme in which RSU can only authenticate one message, this scheme can authenticate multiple messages in batches, which greatly improves the efficiency. However, due to the limited computing resources of the RSU itself, it is still unable to quickly complete the message authentication and packet loss problem is serious during the peak travel time. Liu et al. [25] provided another new batch authentication scheme for IoV. The scheme uses bilinear algorithm to sign and encrypt messages. However, the scheme does not achieve a balance between security and efficiency. Wang et al. [26] used bilinear algorithm to realize segmented authentication of vehicles. The subsequent authentication process of vehicle is related to the previous authentication, which optimizes the authentication process and reduces the computational consumption, However, this scheme relies heavily on the stability of IoV system. If there is a line fault, RSU will not know the data related to vehicle authentication for the next calculation. If multiple vehicles simultaneously initiate identity authentication, it will also affect the efficiency of RSU. The scheme proposed by Islam et al. [27] is different from the conventional scheme. These vehicles in this scheme communicate by generating a group key and can freely choose groups, regardless of joining or leaving, the vehicle's behavior will continue to promote password updates. However, this scheme cannot support message batch authentication, which is very limited in the scenario of IoV. Xu et al. [28] applied blockchain technology to IoV authentication, which not only reduces the authentication overhead, but also avoids the single point problem in the network by designing the system model of multiple TAs. However, it needs to access the cloud center resources every time, and it will increase the delay time. Song et al. [29] proposed to use vehicles with rich computing resources as fog nodes to authenticate vehicles traveling around, which greatly reduces the burden of RSU authentication. Because vehicle has fast mobility, this will make the network topology of IoV change greatly, and the stability of the scheme needs to be further proved. Vijayakumar et al. [30] proposed a scheme for 6G scenarios, However, the computational complexity of the bilinear pairings is high, which leads to a large resource overhead. He et al. [31] combined fog computing with multi-TA model to give full play to their respective advantages. The fog computing is used to reduce the time delay of authentication, and the multi-TA structure is designed to prevent single-point problems in scheme.
In today's IoV authentication research, how to maintain low-cost consumption while ensuring system security is an urgent problem to be overcome. Therefore, a qualified authentication scheme must fit the actual application scenario of IoV and meet the real-time performance while meeting the security requirements.
3 Background and System Structure
IoV system involves four types of communication entities, which are trusted agency (TA), roadside unit (RSU), vehicles and edge computing node (ECN). Fig. 2 is the system model of IoV.

Figure 2: System model of IOV
(1) TA: it has rich computing and storage resources, generally established by the government, and has full credibility [32]. It is responsible for maintaining the daily work of system operation and data storage. If malicious nodes appear in the IoV, TA can trace malicious nodes and make penalties at the same time. In the traditional IoV, it is often set up a TA, if the TA encounters a performance bottleneck, it will reduce the efficiency of authentication of system. And the setting of a single TA is also easy to cause the centralization problem. Therefore, this scheme places a TA in each region. These TA act as blockchain nodes to form an alliance chain and regularly publish relevant information on vehicle registration.
(2) RSU: it is also a completely trusted third party and it can communicate directly with TA and vehicles [33]. In this scheme, it is responsible for publishing the anonymous identity of vehicles and verifying the legitimacy of messages collected by edge computing nodes. RSU can join the alliance chain after being registered and authenticated by TA. As a blockchain light node, it is used for maintaining the network information.
(3) Edge computing node (ECN): it is also essentially a legitimate vehicle and has a certain amount of computing resources. It is a node selected by RSU and is responsible for assisting the RSU in message authentication.
(4) Vehicle: it is the main user of IoV and can enjoy the service application of the system. Each vehicle has a communication device and tamper-proof device (TPD).
3.2 Related Cryptography Theory
In 1987, Miller and Koblitz proposed elliptic curve cryptography [34], which is based on the knowledge of groups and fields in mathematics. Because it has the characteristics of high safety strength and fast calculation speed, it is suitable for the environment with limited resources. ECC is more difficult to factorize the large composite number than RSA. It is generally defined as formula
The addition principle of elliptic curve: take two points
The multiplication principle of elliptic curve: it is different from our usual multiplication. It is calculated in the form of accumulation. For example, when 3Q needs to be calculated, it is generally reduced to

Figure 3: Elliptic curve algorithm example R = P + Q
Most encryption applications based on elliptic curves mainly use the following two generally accepted thorny issues:
The elliptic curve discrete logarithm problem: For example,
The elliptic curve computational Diffie-Hellman problem [35] (ECCDH). It is difficult to calculate abP for any known
Blockchain itself is a distributed system, It is characterized by chain connection, decentralization, group decision-making, and programmable customization. Each data block on the chain is stored in a chain structure and connected in chronological order.
In proposed scheme, all TA and RSU form a multi-server network based on a consortium chain. TA is a miner (full node) in the blockchain network with accounting rights, and RSU (light node) does not participate in the accounting. A new TA must be authorized before joining the network. Light nodes want to access information on the blockchain, must be authorized by the full node. Considering that the resources of IoV node are limited, we use the PBFT algorithm with higher efficiency and less computing resource consumption to make group decision between nodes. Our scheme also uses smart contract technology to automatically execute and manage data information in the authentication process according to predetermined rules, supporting users to achieve flexible and diverse automated operations, which helps to simplify the process and improve the authentication efficiency.
The IoV system needs to have the following security features:
(1) Privacy protection: In the Internet era, users pay great attention to their privacy. In the process of communication, users do not want to expose their personal information and identity.
(2) Unforgeability: Any illegal vehicle cannot forge a legitimate signature.
(3) Traceability: If malicious behavior occurs in the system, TA can track and recover the identity of malicious nodes.
(4) Unlinkability: When a node receives multiple messages from the same vehicle, it is impossible to determine whether these messages are from the same message source.
(5) Resist man-in-the-middle attack: Attackers cannot implement this type of attack.
In this chapter, we will explain each step of the authentication scheme in detail. The scheme has six steps: system set-up, registration, pseudonym generation, edge computing node selection, vehicle message signature, and vehicle message authentication. The complete authentication process will be shown in Fig. 4.

Figure 4: The process of messages authentication
When the system starts, TA performs the system set-up phase. If a vehicle wants to join IoV, it must obtain identity and key in system from the TA. These pre-operations are carried out in a secure network environment.
In our scheme, once vehicle gets
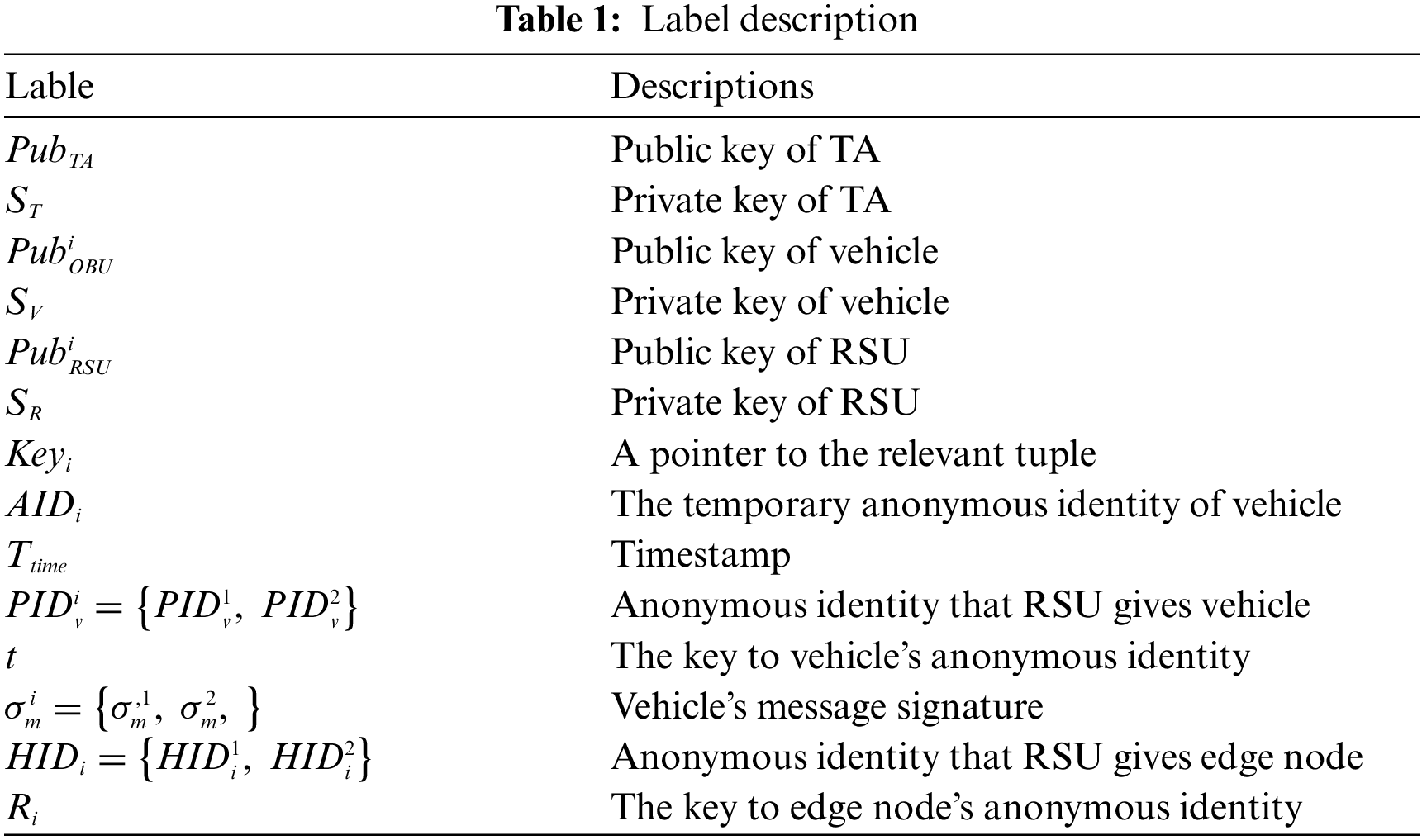
The symbols and parssssameter definitions that appear in the scheme will be explained and explained in detail in Table 1.
At this stage, TA, as a fully trusted node, will complete the initialization of the system and broadcast the generated system parameters. It has a total of four steps:
Step (1): TA selects
Step (2): TA selects a random number
Step (3): TA chooses three one-way hash functions:
Step (4): TA publishes {
4.2.1 Registration of Vehicles
When a vehicle needs to be registered, its driver should submit the relevant information to TA. After TA checks that the received information is correct, it first randomly selects a number
After calculating public and private keys of the vehicle, TA calculates
Finally, TA will send message
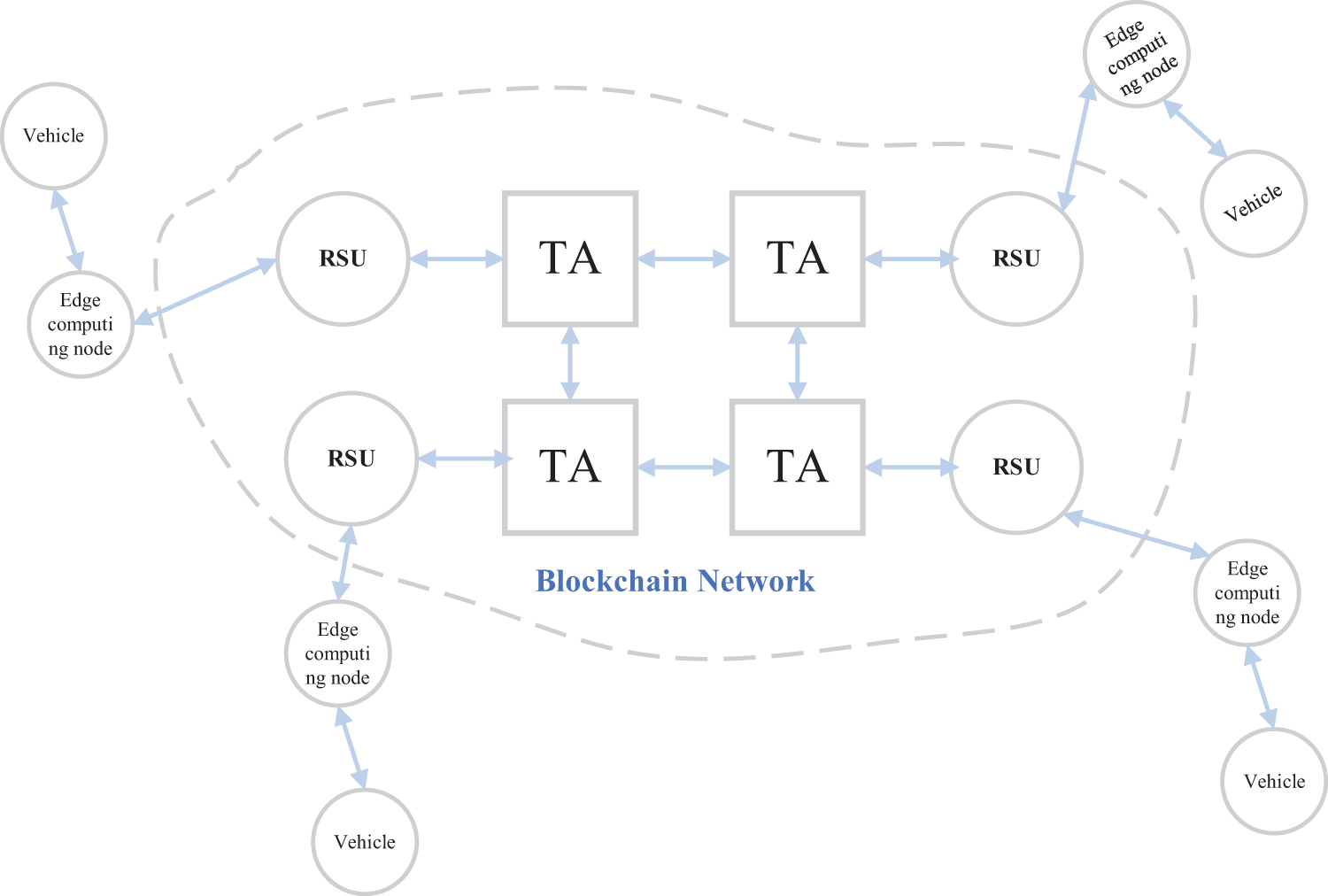
Figure 5: Blockchain structure of system
When roadside unit equipment
Finally, TA sends message

Figure 6: The registration process of vehicle and RSU
4.3 Anonymous Identity Generation of Vehicles
4.3.1 The Vehicle Applies for Anonymity
First, vehicle will request an anonymous identity from RSU, but it will first use a temporary anonymity to complete the application. The vehicle randomly selects a
where
The specific implementation algorithm is as follows:

4.3.2 RSU Issues Anonymous Identity to Vehicles
When
After
If the equation holds, then the message is indeed sent by vehicle, and
where anonymous identity is

4.3.3 Vehicle Receives Anonymous Identity
When vehicle
If not equal, then the
The specific implementation algorithm is as follows:

The application process of anonymous identity is shown in the Fig. 7.

Figure 7: Application of anonymous identity
4.4 Selection of Edge Computing Nodes
All vehicles can apply to become ECN, but must meet two requirements, one is parked within the communication range of
(1) First, vehicle should be a legal vehicle registered through IoV system. Vehicle can use private key t of temporary identity to sign the message
The vehicle sends
If the equation is passed, then the legitimacy of the application vehicle is verified, and the vehicle can be listed as one of candidate ECN.
(2) Considering the success rate of message authentication, ECN should have sufficient computing resources and maintain a short communication distance with
In terms of computing resources, we are more inclined to select vehicles with more available computing resources. When a vehicle is applying as a bus, considering that it has more computing resources and is a fully trusted node, we will give priority to the bus.
The formula for selecting ECN is as follows:

When vehicle becomes ECN,
4.5 Messages Publish and Authentication
After vehicle is on the road, it first randomly selects a number
The vehicle will select the nearest ECN

When ECN receives instruction of
ECN merge authenticated successful and time-sensitive messages into
Finally, the ECN sends message

When
If the equation holds, then
In terms of security, we have theoretically verified the scheme, and it can resist the network attack behavior in Chapter 3.4.
Theorem 1: The scheme can resist adaptive chosen message attack.
The whole proof process is carried out under the principle of ECDLP. The following is the proof process:
Adversary A forged a signature
Initialization: Challenger C first selects a random number
Signature query: After C receives a message request from A, C randomly selects
Output: A final output message tuple
C uses Eq. (23) to check message tuples. If the equation does not hold, C ends the game.
In this paper, the above process is repeated with different values
Through Eqs. (23) and (24), we can get
Therefore, this paper can get
5.2 Informal Security Analysis
5.2.1 The Correctness of Signature
When the ECN starts the first step of authentication, it will use Eq. (26) to judge:
5.2.2 Vehicle Identity’s Privacy Protection
In the process of IoV communication, in order to protect identity privacy and security, all communication entities use anonymous identity to communicate. Taking an ordinary vehicle as an example, we use
If malicious node wants to understand vehicle’s privacy data, then it must know
In addition, the anonymous identity of the vehicle can be changed at any time. When other vehicles receive multiple messages from the same vehicle, it cannot know vehicle’s identity that sends these messages. That is to say, the scheme of this paper satisfies unlinkability.
In this scheme, in order to protect their privacy, everyone uses anonymous identity to communicate. In order to prevent malicious behavior of legitimate users, RSU and TA can trace its real identity through anonymous identity. The formulas used by RSU and TA for identity traceability are as follows:
Because other nodes do not know the secret key of
The messages
5.2.5 Resist Man-in-the-Middle Attackss
We can avoid adversaries impersonating others to participate in communication, in our scheme, anonymous identity applications and message sending require multi-stakeholder participation and mutual authentication. During the entire authentication session, the message sent by each node needs to be signed using the corresponding secret key. The pseudonym and the generated signature message are based on the ECDL problem, so it can effectively resist the man-in-the-middle attack.
In this part, the team also used simulation tools to carry out security simulation experiments and performance analysis experiments.
6.1 Safety Simulation Experiment
We chose the widely accepted software tool ProVerif for experimental operation and the complete scheme described in Section 4 is implemented and verified in ProVerif. For a detailed description of the scheme, please see the Fig. A1.
In the experimental simulation, malicious node’s goal is to launch an attack to obtain the privacy of the vehicle. Simulation results (as shown in Fig. 8) show that although malicious nodes launch network attacks, they still fail to achieve their goals. Malicious nodes can’t get vehicle’s private data, such as

Figure 8: The scheme’s simulation results
6.2 Performance Simulation Experiment
In terms of performance, we mainly analyze several factors and compare the performance with CAEC [36], DCBA [37] and ABAH [38] schemes.
We use a popular cryptography library called Crypto + + library to measure all the cryptographic operations involved in the above scheme. The performance evaluation is carried out in a machine environment configured with Intel i7-9750 3 GHZ and Visual Studio 2019. In addition, we also use the Veins simulation platform to build simulation scenarios for experiments.
We set up a security level of 80 bits scheme, Elliptic curve cryptography is set as follows:
In a single RUS domain, we take the scenario where the vehicle only transmits one message as an example for analysis. In the whole process, the computational consumption generated by the vehicle ‘s signature is


Figure 9: The authentication and signature computation overhead of a message
Next, we consider the peak scenario of vehicle travel. In a short period of time, many vehicles send messages to ECN, ECN will batch authenticate the corresponding messages. In most cases, batch authentication of ECN is passed at one time.
We assume that within the communication domain of

Figure 10: Comparison of computational consumption
We also consider the influence of the number of ECN. Fig. 11 reveals the correlation between time consumption and ECNs. With the addition of more ECN, the time consumption of message authentication becomes less, because ECN greatly alleviates the authentication pressure of RSU and accelerates the whole process.

Figure 11: The correlation between the number of ECNs and computational consumption
In the part, we consider another factor, namely the communication overhead. We have done experiments on the communication consumption between DCBA, CAEC, ABAH and this scheme. Taking the communication domain of an RSU as an example. At a certain time, the sum of the transmission consumption of all vehicles and the transmission consumption of ENC is the total communication overhead in the domain.
In Chapter 6.1, we know that the
We clearly know the communication consumption of each scheme from Table 3. In this scheme, the data sent from vehilce to ECN is


Figure 12: Comparison of communication consumption of message authentication

Figure 13: Impact of the number of ECN on communication consumption
In high-density traffic scenarios, it is easy to cause packet loss events during transmission. To reflect advantages of this scheme in this aspect, in the part, we use the Veins simulation architecture to conduct experiments. The calculation formula of packet loss rate is

Fig. 14 is the PLR results of the experiment under different vehicle traffic scenarios. From the experimental results, it can be known that the throughput of IoV is easily affected by the size of traffic flow. The larger the traffic flow, the higher the packet loss rate. In our scheme (only one ECN is set), the traffic flow is in the range of 2~16 vehicles per metre, the PLR is 2.91%~3.06%, and we increased ECN to 2 vehicles, the PLR is 2.89%~2.93%. All in all, our scheme still has certain advantages and is suitable for authentication in peak traffic scenarios.

Figure 14: Comparison of PLR
This paper is devoted to the application research of IoV, we combine blockchain and edge computing technology to design a novel scheme for message authentication. Unlike in traditional authentication scheme, ECN in the scheme will assume part of the responsibility of RSU for the first round of message authentication, which can make full use of the idle computing resources and accelerate the overall authentication process of messages. In addition, TA and RSU in the scheme are used as blockchain nodes to maintain vehicle information. By accessing the information on the blockchain, RSU can authenticate vehicles from different domains and enable vehicles to achieve cross-domain authentication. The scheme we designed also has limitations. Considering that ECN are temporarily parked vehicles, there is uncertainty in identity authentication work. At the same time, frequent replacement of ECN will also increase the resource consumption of the system.
At present, most of authentication mechanisms are mainly aimed at the security characteristics required by IoV. The higher the security of the scheme, the greater the corresponding computational communication consumption. How to achieve a perfect balance between the two and design a high security and performance authentication scheme is still our goal in the future. Nowadays, blockchain, artificial intelligence and other technologies can be used in authentication schemes, and it is also feasible to design authentication schemes by combining multiple technologies.
Acknowledgement: Throughout the submission process, we are very grateful for the patient guidance of editors and reviewers. We thank our colleagues and experts for their guidance and support.
Funding Statement: This research was funded by Guangxi Natural Science Foundation General Project—Research on Visual Positioning and Navigation Robot Based on Deep Learning, Project Number: 2023GXNSFAA026025.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Qiping Zou, Zhong Ruan; data collection: Zhong Ruan; analysis and interpretation of results: Zhong Ruan; draft manuscript preparation: Huaning Song. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Data sharing is not applicable to this article as no datasets were generated or analyzed during the current study.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Hammoud, “AI, blockchain, and vehicular edge computing for smart and secure IoV: Challenges and directions,” IEEE Internet Things Mag., vol. 3, no. 2, pp. 68–73, 2020. doi: 10.1109/IOTM.0001.1900109. [Google Scholar] [CrossRef]
2. P. M. Rao, S. Jangirala, S. Pedada, A. K. Das, and Y. H. Park, “Blockchain integration for IoT-Enabled V2X communications: A comprehensive survey, security issues and challenges,” IEEE Access, vol. 3281844, no. 11, pp. 54476–54494, 2023. [Google Scholar]
3. M. T. Abbas and M. Afaq, “SD-IoV: SDN enabled routing for internet of vehicles in road-aware approach,” J. Ambient Intell. Hum. Comput., vol. 11, no. 3, pp. 1265–1280, 2020. doi: 10.1007/s12652-019-01319-w. [Google Scholar] [CrossRef]
4. M. El, S. Samira, and E. G. Abdelaziz, “Internet of vehicles: Concept, process, security aspects and solutions,” Multimed. Tools Appl., vol. 81, no. 12, pp. 16563–16587, 2020. [Google Scholar]
5. J. Cui, L. Wei, J. Zhang, Y. Xu, and H. Zhong, “An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks,” IEEE Trans. Intell. Transp. Syst., vol. 20, no. 5, pp. 1621–1632, 2018. doi: 10.1109/TITS.2018.2827460. [Google Scholar] [CrossRef]
6. S. O. Ogundoyin, “An autonomous lightweight conditional privacy-preserving authentication scheme with provable security for vehicular ad-hoc networks,” Int. J. Comput. Appl., vol. 42, no. 2, pp. 196–211, 2020. doi: 10.1080/1206212X.2018.1477320. [Google Scholar] [CrossRef]
7. S. Jiang, X. Zhu, and L. Wang, “An efficient anonymous batch authentication scheme based on HMAC for VANETs,” IEEE Trans. Intell. Transp. Syst., vol. 17, no. 8, pp. 2193–2204, 2016. doi: 10.1109/TITS.2016.2517603. [Google Scholar] [CrossRef]
8. C. Yang, J. Peng, Y. Xu, Q. Wei, L. Zhou and Y. Tang, “Edge computing-based VANETs’ anonymous message authentication,” Symmetry, vol. 14, no. 12, pp. 2662, 2022. doi: 10.3390/sym14122662. [Google Scholar] [CrossRef]
9. B. Palaniswamy, S. Camtepe, E. Foo, and J. Pieprzyk, “An efficient authentication scheme for intra-vehicular controller area network,” IEEE Trans. Inf. Forensics Secur., vol. 15, pp. 3107–3122, 2020. doi: 10.1109/TIFS.2020.2983285. [Google Scholar] [CrossRef]
10. Z. Shen, F. Ren, and H. Wang, “Combining blockchain and crowd-sensing for location privacy protection in Internet of vehicles,” Veh. Commun., vol. 45, pp. 100724–100732, 2024. doi: 10.1016/j.vehcom.2023.100724. [Google Scholar] [CrossRef]
11. M. Azees, P. Vijayakumar, and L. J. Deboarh, “EAAP: Efficient anonymous authentication with conditional privacy-preserving scheme for vehicular Ad Hoc networks,” IEEE Trans. Intell. Transp. Syst., vol. 18, no. 9, pp. 2467–2476, 2017. doi: 10.1109/TITS.2016.2634623. [Google Scholar] [CrossRef]
12. J. Cui, D. Wu, J. Zhang, Y. Xu, and H. Zhong, “An efficient authentication scheme based on semi-trusted authority in VANETs,” IEEE Trans. Vehicular Technol., vol. 68, no. 3, pp. 2972–2986, 2019. doi: 10.1109/TVT.2019.2896018. [Google Scholar] [CrossRef]
13. J. Cui, J. Wen, S. Han, and H. Zhong, “Efficient privacy-preserving scheme for real-time location data in vehicular ad-hoc network,” IEEE Internet Things J., vol. 5, no. 5, pp. 3491–3498, 2018. doi: 10.1109/JIOT.2018.2797206. [Google Scholar] [CrossRef]
14. L. Zhang, “OTIBAAGKA: A new security tool for cryptographic mix-zone establishment in vehicular ad hoc networks,” IEEE Trans. Inf. Forensics Secur., vol. 12, no. 6, pp. 2998–3010, 2017. doi: 10.1109/TIFS.2017.2730479. [Google Scholar] [CrossRef]
15. W. Xiong, R. Wang, Y. Wang, F. Zhou, and X. Luo, “CPPA-D: Efficient conditional privacy-preserving authentication scheme with double-insurance in VANETs,” IEEE Trans. Vehicular Technol., vol. 70, no. 4, pp. 3456–3468, 2021. doi: 10.1109/TVT.2021.3064337. [Google Scholar] [CrossRef]
16. W. Shi, X. Zhang, Y. Wang, and Q. Zhang, “Edge computing: State-of-the-art and future directions,” J. Comput. Res. Dev., vol. 56, no. 1, pp. 69–89, 2019. [Google Scholar]
17. M. Raya and J. -P. Hubaux, “Securing vehicular ad hoc networks,” J. Comput. Secur., vol. 15, no. 1, pp. 39–68, 2007. doi: 10.3233/JCS-2007-15103. [Google Scholar] [CrossRef]
18. Y. Sun, R. Lu, X. Lin, X. Shen, and J. Su, “An efficient pseudonymous authentication scheme with strong privacy preservation for vehicular communications,” IEEE Trans. Vehicular Technol., vol. 59, no. 1, pp. 3589–3603, 2010. doi: 10.1109/TVT.2010.2051468. [Google Scholar] [CrossRef]
19. R. Lu, X. Lin, H. Zhu, P. -H. Ho, and X. Shen, “ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications,” in Proc. IEEE INFOCOM, Phoenix, AZ, USA, 2008, pp. 1229–1237. [Google Scholar]
20. Y. Qing, Z. Xiao, Z. Jing, and X. L. Wang, “A novel authentication and key agreement scheme for Internet of Vehicles,” Future Gener. Comput. Syst., vol. 145, no. 1, pp. 415–428, 2023. doi: 10.1016/j.future.2023.03.037. [Google Scholar] [CrossRef]
21. K. -A. Shim, “CPAS: An efficient conditional privacy-preserving authentication scheme for vehicular sensor networks,” IEEE Trans. Vehicular Technol., vol. 61, no. 4, pp. 1874–1883, 2012. doi: 10.1109/TVT.2012.2186992. [Google Scholar] [CrossRef]
22. H. Vasudev, D. Das, and A. V. Vasilakos, “Secure message propagation protocols for IoVs communication components,” Comput. Electr. Eng., vol. 82, no. 1, pp. 106555, 2020. doi: 10.1016/j.compeleceng.2020.106555. [Google Scholar] [CrossRef]
23. H. Vasudev, V. Deshpande, D. Das, and S. K. Das, “A lightweight mutual authentication protocol for V2V communication in internet of vehicles,” IEEE Trans. Vehicular Technol., vol. 69, no. 6, pp. 6709–6717, 2020. doi: 10.1109/TVT.2020.2986585. [Google Scholar] [CrossRef]
24. C. Zhang, X. Lin, R. Lu, P. -H. Ho, and X. Shen, “An efficient message authentication scheme for vehicular communications,” IEEE Trans. Vehicular Technol., vol. 57, no. 6, pp. 3357–3368, 2008. doi: 10.1109/TVT.2008.928581. [Google Scholar] [CrossRef]
25. B. Liu and L. Zhang, “An improved identity-based batch verification scheme for VANETs,” in Proc. 2013 5th Int. Conf. Intell. Netw. Coll. Syst., Xi’an, China, 2013, pp. 809–814. [Google Scholar]
26. C. Wang, R. Huang, J. Shen, J. Liu, P. Vijayakumar and N. Kumar, “A novel lightweight authentication protocol for emergency vehicle avoidance in VANETs,” IEEE Internet Things J., vol. 8, no. 18, pp. 14248–14257, 2021. doi: 10.1109/JIOT.2021.3068268. [Google Scholar] [CrossRef]
27. S. H. Islam, M. S. Obaidat, P. Vijayakumar, E. Abdulhay, F. Li and M. K. C. Reddy, “A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs,” Future Gener. Comput. Syst., vol. 84, no. 1, pp. 216–227, 2018. doi: 10.1016/j.future.2017.07.002. [Google Scholar] [CrossRef]
28. Z. Xu, W. Liang, K. -C. Li, J. Xu, and H. Jin, “A blockchain-based roadside unit-assisted authentication and key agreement protocol for internet of vehicles,” J. Parallel Distr. Comput., vol. 149, no. 1, pp. 29–39, 2021. doi: 10.1016/j.jpdc.2020.11.003. [Google Scholar] [CrossRef]
29. L. Song, G. Sun, H. Yu, X. Du, and M. Guizani, “FBIA: A fog-based identity authentication scheme for privacy preservation in internet of vehicles,” IEEE Trans. Vehicular Technol., vol. 69, no. 5, pp. 5403–5415, 2020. doi: 10.1109/TVT.2020.2977829. [Google Scholar] [CrossRef]
30. P. Vijayakumar, M. Azees, S. A. Kozlov, and J. J. Rodrigues, “An anonymous batch authentication and key exchange protocols for 6G enabled VANETs,” IEEE Trans. Intell. Transp. Syst., vol. 23, no. 2, pp. 1630–1638, 2021. doi: 10.1109/TITS.2021.3099488. [Google Scholar] [CrossRef]
31. Y. He, G. Li, and J. Liu, “Conditional privacy protection authentication scheme based on fog computing and multi-TA in Internet of vehicles,” Appl. Res. Comput., vol. 1, pp. 6–23, 2022. [Google Scholar]
32. S. -F. Tzeng, S. -J. Horng, T. Li, X. Wang, P. -H. Huang and M. K. Khan, “Enhancing security and privacy for identity-based batch verification scheme in VANETs,” IEEE Trans. Vehicular Technol., vol. 66, no. 4, pp. 3235–3248, 2015. [Google Scholar]
33. X. Zhu, S. Jiang, L. Wang, and H. Li, “Efficient privacy-preserving authentication for vehicular ad hoc networks,” IEEE Trans. Vehicular Technol., vol. 63, no. 2, pp. 907–919, 2013. doi: 10.1109/TVT.2013.2294032. [Google Scholar] [CrossRef]
34. N. Andola, Raghav, and V. K. Yadav, “A lightweight blockchain for authentication and anonymous authorization in IoD,” Wirel. Pers. Commun., vol. 119, no. 1, pp. 343–362, 2021. doi: 10.1007/s11277-021-08214-8. [Google Scholar] [CrossRef]
35. G. Xu, H. Bai, and J. Xing, “SG-PBFT: A secure and highly efficient distributed blockchain PBFT consensus algorithm for intelligent Internet of vehicles,” J. Parallel Distr. Comput., vol. 164, no. 1, pp. 1–11, 2022. doi: 10.1016/j.jpdc.2022.01.029. [Google Scholar] [CrossRef]
36. W. Peng, N. Han, and C. Song, “CAEC: Certificateless IOV identity authentication scheme in edge computing environment,” (in ChineseJ. Beijing Univ. Posts Telecommun., vol. 45, no. 2, pp. 46–51, 2022. [Google Scholar]
37. A. K. Sutrala, P. Bagga, A. K. Das, N. Kumar, J. J. Rodrigues and P. Lorenz, “On the design of conditional privacy preserving batch verification-based authentication scheme for Internet of vehicles deployment,” IEEE Trans. Vehicular Technol., vol. 69, no. 5, pp. 5535–5548, 2020. doi: 10.1109/TVT.2020.2981934. [Google Scholar] [CrossRef]
38. I. Ali, Y. Chen, N. Ullah, R. Kumar, and W. He, “An efficient and provably secure ECC-based conditional privacy-preserving authentication for vehicle-to-vehicle communication in VANETs,” IEEE Trans. Vehicular Technol., vol. 70, no. 2, pp. 1278–1291, 2021. doi: 10.1109/TVT.2021.3050399. [Google Scholar] [CrossRef]
Appendix A

Figure A1: Coding of the scheme
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools