 Open Access
Open Access
ARTICLE
Priority Based Energy Efficient MAC Protocol by Varying Data Rate for Wireless Body Area Network
School of Information Technology and Engineering, Vellore Institute of Technology, Vellore, Tamil Nadu, 632014, India
* Corresponding Author: Usha Devi Gandhi. Email:
Computer Systems Science and Engineering 2024, 48(2), 395-411. https://doi.org/10.32604/csse.2023.041217
Received 14 April 2023; Accepted 07 July 2023; Issue published 19 March 2024
A correction of this article was approved in:
Correction: Priority Based Energy Efficient MAC Protocol by Varying Data Rate for Wireless Body Area Network
Read correction
Abstract
Wireless Body Area Network (WBAN) is a cutting-edge technology that is being used in healthcare applications to monitor critical events in the human body. WBAN is a collection of in-body and on-body sensors that monitor human physical parameters such as temperature, blood pressure, pulse rate, oxygen level, body motion, and so on. They sense the data and communicate it to the Body Area Network (BAN) Coordinator. The main challenge for the WBAN is energy consumption. These issues can be addressed by implementing an effective Medium Access Control (MAC) protocol that reduces energy consumption and increases network lifetime. The purpose of the study is to minimize the energy consumption and minimize the delay using IEEE 802.15.4 standard. In our proposed work, if any critical events have occurred the proposed work is to classify and prioritize the data. We gave priority to the highly critical data to get the Guarantee Tine Slots (GTS) in IEEE 802.15.4 standard superframe to achieve greater energy efficiency. The proposed MAC provides higher data rates for critical data based on the history and current condition and also provides the best reliable service to high critical data and critical data by predicting node similarity. As an outcome, we proposed a MAC protocol for Variable Data Rates (MVDR). When compared to existing MAC protocols, the MVDR performed very well with low energy intake, less interruption, and an enhanced packet-sharing ratio.Keywords
The Wireless Body Area Network interfaces individual sensor nodes or actuator nodes that have been implanted in the body of the patient skin. Multi-hop or star topology architecture is used for the placement of the sensor nodes in the patient’s body during the particular system model implementation.
The WBAN is used in various applications like sports monitoring, home monitoring, and remote healthcare monitoring, Let us consider the functioning in the field of medical advances, various body sensors that are contained in a wireless body area network are deployed on a patient body whose primary role is to record or measure the various body parameter values such as breathing, ECG, heart rate, body fluid pressure, body disorder and so on. The patient who is monitored from a remote location in the hospital is offered advantages such as free movement to any preferred location and is not restrained to staying inside closed boundaries. This tends to minimize the medical expenditure the patient would have paid if he or she was forced to stay inside hospital premises. Additionally, this also encourages a faster and more accurate diagnosis of the patient using the information or data values that are collected for a given period in the environment the patient resides.
Based on the medium access technique, the MAC protocol can be categorized into two type’s contention-based access schemes and contention-free access schemes. The Contention-Based Protocol (CBP) is a communications protocol that allows users to share data in a common radio channel without pre-coordination. Moreover, in the case of the contention-free access scheme MAC protocol, the channel is utilized by the nodes based on pre-assigned time slots. This research article is focused on minimizing energy consumption to extend the lifetime of the network by classifying and assigning priority to the data generated in WBAN, prescheduling the high-priority data to win the contention-free in IEEE 802.15.4 standard to minimize the delay and maximize the throughput by varying data rate. Resnick’s formula is used to predict the critical event which is useful for prescheduling to access the channel without any delay. The remaining section is organized as follows. Section 2 challenges in WBAN, Section 3 is literature review where the some of the research work related to MAC protocol for priority and scheduling in WBAN, Section 4 is proposed work, Section 5 is implementation and results, followed by Section 6 conclusion.
The challenges encountered while implementing WBAN to monitor patient critical events from a remote location are that the MAC protocol consumes more energy which minimizes the lifetime of the network, and it fails to handle the burst traffic which increases the delay because the network attains less throughput. The research should focus on designing and developing a new MAC protocol that should minimize energy consumption to increase the lifetime of the network, minimize the delay and increase the throughput.
This section explains the existing MAC protocol which reduced the energy consumption and increased the lifetime of the Network.
In this paper, the critical health data can be prioritized as type 1, type 2, and type 3. Where the fixed length of MAC-super frame headers will be used for type 1 traffic devices while variable length MAC-super frame headers will be used by the rest of the types of devices. To optimize the transmission power Particle Swarm Optimization is used [1]. This paper used Resnick’s formula to predict the accuracy with the help of recommendation and collaborative filtering [2].
The research is focused on how to solve the energy efficiency problems that arise while operating with wireless body area networks, and the concept of MAC protocol technology comes into the picture. The processes or functions that MAC protocol performs are handling energy requirements, managing the errors that arise, framing the data existing, transmission tasks arrangement, and control of the channel being accessed. If we had to describe a MAC protocol that is both reliable and effective, it can be said as follows—the protocol should increase the data throughput and increases the network’s energy efficiency thereby achieving the most use of the WBAN channel and increasing the lifetime of the battery being used [3].
The master and slave architecture is used in this paper. The master node assigns the time slots for slave nodes to avoid the collision, at the same time Clear Channel Assessment (CCA) algorithm based on standard listen-before-transmit (LBT) is used to increase the performance [4].
In this paper, the author discusses the energy-efficient execution of a real-time medical WBSN. These sensor nodes are wide-ranging nodes. Moreover, the sensor nodes must be ultra-low-power, low-rate treatment-function nodes. It should also “work-on demand” to verify events in the slave nodes. The slave node performs the activities such as incentives and drug delivery. The channel that is observed will consume too much power for longstanding use. Hence these requests cannot be satisfied at the same time in commonly-used single-channel executions. To solve this problem a secondary channel is introduced additionally in which the channel is used only for listening. Developing the secondary channel, the node can reach real-time “work-on demand” and zero idle power, utilizing the energy from the “demand token” [5].
The body sensors can be able to request a “collision-free” time slot, each, and every time they consider it required. Consistently, they can reject to transmit, if there is a bad channel link. These results illustrate an enhancement in the system’s overall performance. The expected MAC model is evaluated by computer simulations in terms of quality of service and energy intake under particular healthcare circumstances [6].
At the beginning of each slot, the packet is classified as Critical data and non-critical data, and the critical data is communicated to the coordinator for further processing. With that, the retransmission of packets is reduced [7].
In this paper, the author discussed IEEE 802.15.4; a superframe structure to satisfy the QoS of three type’s services such as differentiated alarm control requiring immediate data transmission or command. The transmission requires a low data rate and the routine traffic requires a major bandwidth which consumes more energy. So it is given the least priority. Resource allotment provided for these services is decided by the coordinator [8].
In this article, the author tells about the key features of WBANs for several applications. Current WBAN structures convey the results to on-demand, emergency, and ordinary traffic. In addition, the in-body antenna design and low-power MAC protocol for WBAN are discussed. In our discussion, this article also discussed the need for new power-efficiency keys for in-body and on-body sensor networks [9].
The author discusses the topographies of sensor networks and applications that impact a MAC investigation, for computing the energy Conservation and throughput capacities as vital goals, the nodes are put in regular intervals of time at nap state, to reduce energy intake when listening to an idle channel. Simulations tool such as Castalia OMNeT++ is used for specific parameter description. From the result, it was discussed that the T-MAC protocol can reduce energy consumption [10].
In this article, the rotational listening strategy (RLS) is applied to enhance the rate of effective communication for WBAN the author. The channel admission process is logically divided into several minor slots that are independently allocated to each node. It provides an analytical and numerical cohabitation result for the state of affairs. The nodes without RLS are associated with an RLS-enabled WSN. Simulations are calculated on the performance of RLS. At last, the results show that RLS certainly progresses transmission efficiency and energy consumption [11].
This proposed protocol separates the data channel and control channels, for collision-free communication, which improves the performance of throughput energy efficiency, and minimum delay compared to 802.15.4 [12].
Body QoS has a unique solution compared to other protocols; it adopts the Asymmetric architecture all the processing is done at sensing sensors and aggregates and formed the virtual MAC protocol which supports other MAC protocols to implement the data communication, at last protocol implements adaptive resource scheduling [13].
In this paper, the author discusses the novel Time Division Multiple Access (TDMA)-based MAC protocol for communications between mobile nodes in BSNs using uplink/downlink at irregular network strategy. A planning set of rules of TDMA and random frame formats are also recommended. The Base Station inspects the routing list and transmission power for each sensor. The simulation results recommend the TDMA protocol. The TDMA protocol is used to reduce the data slot duration to enhance performance [14].
This paper, discussed the survey of energy efficiency MAC protocols for WBASNs. The work defines complete data about different energy-efficient MAC protocols with their energy optimization procedures; LPL, Scheduled Contention, and Time Division Multiple Access TDMA are described. It is systematically compared with three path loss prototype models. By using MATLAB simulating tools for communications in WBASNs [15].
This paper the discussed structure of wireless channels, the range of the traffic access latency, and the need for minimization of energy consumption. The combination of two different superframe structures is used to convert a hybrid MAC protocol and this Hybrid model is named Priority MAC (PMAC). The statistics channels are separated and precedence is given to emergency traffic. The wearable sensors use the sleep mode to consume energy [16].
The author talks about a new standard to develop a minimized energy intake Low-power and Low data rate requests protocol which is the ZigBee standard, which has GTS the Superframe structures to transfer Life-threatening transmission data. The protocol is distributed into several significant levels, if a node miss to get the slot for transmission, the Coordinator is the centralized node who is in charge to increase the significant level of the node in the next cycle [17].
In this paper, the author discussed mainly the main structure behind schedule in this technology is the Internet which involves many IoT devices and data. But the devices coupled with IoT nodes are mixed in nature. Clever IoT devices are well-ordered remotely and can communicate directly without anthropological involvement. They not only screen their surroundings but they can also execute mutual tasks in coordination with each other [18].
In this research article, the author explains an eMC-MAC, the calculation is created on traffic place in order. In the projected eMC-MAC protocol, mini slots during CFP, the critical packets are organized by the controller node in an energy-well-organized technique. Therefore, the recommended eMC-MAC protocol transmits crisis data packets to the coordinator with a low-priced delay. NS-3 simulating tool is used for simulation [19].
In this work, the author conversed about how to reduce energy wastage, awaken radio-based techniques to control rest, and dynamic modes of body sensors. A Markov model is used to determine the node states. Logical terminologies are resultant of the model to investigate the performance of typical energy intake, throughput, packet drop probability, and average delay during normal and crisis data. The simulation results from demonstrations that the typical energy consumption and delay are relatively higher during crisis data communication with reply mode [20].
In this paper, the Precedence-built packet balanced backlog MAC protocol is proposed as a solution for various challenges like energy consumption and communication of crisis data in a strict real-time consistent manner which are faced by Wireless Body Area Networks. The main aim is to send the most critical packets over on-request and non-critical packets. In this protocol, The Scheduling is done based on priority. The packets with lower and higher threshold values are considered Critical packets. So these protocols have 2 different queues for both lower and higher threshold critical values. High and low Threshold values are kept in the queue based on timing. The packet with less remaining time is scheduled first from the packets. So on this; an evaluation is done by comparing parameters with other models. The Packet delivery ratio, the proposed model shows the highest value compared to its counterparts due to the usage of 2 queues. The average delay is the least for the proposed protocol compared to other counterparts. Energy Consumption is the least for the proposed model compared to others. The Throughput is the highest for the proposed model when compared to others. So in this way, the proposed model has shown good values and work can be further extended by applying several bio-inspired algorithms, etc. the protocol used is MAC; the Channel Access Method is WBAN, Wireless Technology used is IEEE 802.15.6, the Priority obtained is High, the Energy Consumption is Low and the throughput is High [21].
In this paper, the author presents limited concepts in polling-based channel access mechanisms to make an energy-well-organized and QoS-aware MAC protocol. In PMAC, they have discussed the various categories of traffic flow in WBAN and built them on their features. Then, there have provided different polling mechanisms and discourse on how the recommended mechanisms can come across the performance requirements of several traffic types in WBAN. The OMNeT++ emulator to evaluate the demonstration of the proposed PMAC protocol [22].
In this paper, a new Energy Well-organized and Load Balanced Priority Queue Algorithm (ELBPQA) using WBAN to transmit risky data through the lowest delay are introduced. The priority is carried out in three different stages including high priority, moderate priority, and low-slung priority. Predictable as its priority, the data is scheduled and communicated with the help of the hardware scheduler. The outcomes are compared with the current devices in terms of throughput, packet delivery ratio, delay, and power consumption [23].
This paper introduces us to a new way/structure which uses IoT for the well-being of critical patients. They proposed a MAC protocol that is very efficient in terms of energy. The in-body sensors communicate through WBAN (wireless body area network). These sensors’ entire network originated at a single hub. The structure has been divided into 2 divisions. The first division mainly focuses on the handling of emergency events whereas the second division takes care of the communication between the in-body sensors. As there are multiple sensors placed in the patient’s body and there will be continuous periodic data from them, they used a scheduling mechanism for minimal collisions. The sensors periodically give data about emergency events so that they can avoid the sudden occurrence of an emergency event. The main pros of the algorithm are its low latency and low power consumption. The Protocol used is MAC Protocol. Channel Access Method is BAN (wireless body area network), the Wireless Technology used is IEEE 802.15.6, it is given High Priority, the Quality of service is great, the Energy consumption is very low and the Stimulator tool used is MATLAB [24].
In this paper, the limitations caused by the IEEE 802.15.6 standard, which allows communication between various devices in the Wireless Body Area Networks, are overcome by proposing an alternate solution that can be used as an extension of the standard protocol. The synchronization scheme used here is based on heartbeat sensing at its core. The paper mainly deals with Capacitive Body-Coupled Communication (C-BCC) and it presents a new HB-MAC protocol compatible with it. It is a low-level protocol. According to the report, the HB-MAC to accommodates event-driven and unpredictable traffic. The protocol used is MAC Protocol; the Channel Access Method is WBAN, The Wireless Technology used is 802.15.6, there is High Priority, the Throughput is also high, and the Simulation tool used for result analysis is OMNeT++. The QoS is very good [25].
Since WBAN’s evolution is limited by the sensor nodes’ energy restrictions, the author has suggested a protocol named Energy-efficient Directional Approach Medium Access Control (EDA-MAC). It aims to cut down on energy usage and extend the network’s life, by the use of directional antennas in planned allocation as the majority of existing scheduled MAC protocols are structured into using omnidirectional antennas, which are inefficient in terms of power usage. EDA-MAC protocol is formulated on the scheduled access procedure of IEEE 802.15.6. The EDA-MAC protocol differentiates between different types of traffic and orders transmission sequences based on user preferences. EDA-MAC uses multi-beam and single-beam directional modes respectively, but data transmission is mostly done in single-beam mode. The duration of burst data transmissions is also taken into account. Simulation and analytical tests were carried out in both saturated as well as unsaturated network traffic states. The final observations of the simulations are that the energy consumption of EDA-MAC is comparatively lesser whilst its throughput surpasses that of IEEE 802.15.6 under identical conditions, thereby making E-healthcare health monitoring convenient. The protocol used is the MAC protocol. The channel access on WBAN is IEEE 802.15.6. is given high priority and low energy consumption with high throughput. The QoS is guaranteed [26].
In this article, the author suggested a graph-built priority-aware MAC protocol for WBANs and its major drawback that occurs during the probability of Collison and the cost of transmission that rise. The author also discussed the Superframe Duration (SD) and contention-free time slots (CFTS) models which are used to decrease the possibility of data transmission Collison. The MAC Protocol is used here. High Priority is given to Cluster-tree topology. The MATLAB Simulator is used for the result. The result shows that Energy Consumption is low and the throughput is high in graph-based priority-aware MAC protocol [27].
It is a well-known fact that the process of data collection from multiple sensors nodes each with a different delay deadline in a WBAN (Wireless Body Area Network) is a difficult task. While data collecting in an inter-WBAN has been handled in many kinds of literature, the same has not been done for intra-WBAN. The authors have proposed two unique priority mechanisms for intra-WBAN communication in this paper. The first is an event-based priority, whereas the second is an energy-focused priority. These proposed mechanisms can minimize average packet delivery latency while also increasing energy efficiency across all nodes. In the proposed MAC the priority is assigned to the traffic which is labeled as emergency or relevant according to the delayed deadline. The presence of any critical or relevant event at a node results in the high priority of that node. For performance valuation, the authors passed out several numerical evaluations using the C++ language. From the simulation results, it was clear that the modified superstructures in the proposed MAC mechanism have achieved great performance improvements [28].
This paper is about proposing a trust-based secure routing protocol. Because of the huge scale of generation and interchange of data between IoT devices, as well as the limited IoT security available to secure data transmission; attackers can easily breach data pathways. In IoT applications, RPL provides minimal protection against certain RPL-specific and WSN-inherited threats. Furthermore, existing Internet and routing security solutions are restricted in memory, processing, and power, making it difficult for IoT devices to function correctly. New techniques have all been presented as modification schemes for the safekeeping of IoT networks and routing. This paper offers SMTrust, a theoretical architecture for routing protocol for security in the IoT. In comparison to existing confidence modes like DCTM-RPL and SecTrust-RPL, SMTrust will deliver superior network performance. Our method is exclusive in analyzing both sensor and sink node mobility measures. The previous models have not been addressed. The energy consumption is very low. The protocol used is MAC. The technology used is IEEE 802.15.6. It given high priority [29].
In this paper, a multi-group hybrid MAC protocol is suggested so that the energy intake is reduced of the various nodes utilized in the healthcare area. The energy consumption problem is tackled using a probability stochastic model. To build this protocol various assumptions were made some of them were: Not all nodes send data all the time in the network, the power consumption of different sensors is not homogenous, sense and send approach is used. The various nodes send their data to transmit to the access point, it acts as a coordinator. Each node is given a priority and not all nodes have the same priority, it is calculated based on fitness data type, the arrival rate of traffic, and the size of the packet. Based on the priority they are divided into various stochastic groups and then for each transmission event, the mean value of time is calculated. This process is carried out for each node. The time complexity for this protocol was found to be O(n). The CSMA scheme is also applied in this methodology, to avoid the problem of collision only 1 node will send a request message to the access point. The access point will respond by replying with an acknowledgment message broadcast. To make sure that only 1 node is sending the message TDMA is utilized for allotting time slots.
It is observed that the convergence speed of the proposed methodology is better than that of the conventional protocols available, e.g., being 12% faster than the HyMAC protocol and thus has faster convergence. It is also observed that the energy consumption is also less with 204 mJ of energy being utilized in the proposed methodology and 220 mJ in HyMAC. This was made possible due to TDMA. Upon using a high number of nodes attached to the network also it was observed that the proposed protocol performed better than the conventional protocols available [30].
This paper presents a guaranteed time (GTS) allocation according to a dissimilar standard for different data path sounds about various sensor areas to guarantee energy effectiveness, small delay, great saturation, etc. Because of the sudden criticism of Patient status, the sensor node with a sudden rise in data rate is given the most important and assigned additional power than the GTS. By using simulating tools like Castalia 3.3 and OMNeT++. The patient’s data can be calculated according to the situation. It also helps to manage critical situations for any person in any age group. So this job improves health quality and reduces the burden on healthy people. Each node contains various important sensor signals that signal direct data at all times intervals to the coordinator node that provides GTS power according to various data traffic. It also guarantees critical data transmission in proper time to the caretaker for immediate support to the patient in an emergency. There are various features compiled separately and are considered real-time provision support for any dynamic health conditions for handling all powerful situations and help with effective remote monitoring. The Implementation of the sequential model in the MAC protocol for WBAN-based.
Data gaining assistance is done to calculate the efficiency of the recommended system is considered physical activity and this proves the effectiveness of our work in real-time status are few advantages in the proposed system. It is also permitted for an unexpected change in multiple sensors or signals at a time. Power used for all GTS off configurations conditions is great for both of these variants because the sensors constantly struggle to access channels in the long run time, and there is no allocation of space adjustments in GTS. GTS variability, provisional variance output is very close to GTS off. Temporary variations include the effect full body movements capture the causing delay due to environmental changes and the movement of nodes [31]. Priority-based traffic scheduling is proposed to minimize the packet drop to increase throughput. To increase throughput both the priority and location of the data received are considered [32]. In this paper, they proposed Traffic Prioritized Load Balanced Scheduling (TPLBS) to minimize the packet drop in the priority queue [33].
This paper addressed the solution to the two basic problems such as physical-layer security and centralized. To achieve the combined blockchain technology and physically unclonable functions (PUFs). The proposed work achieved less communication and computation cost [34].
In this paper, to preserve privacy and to solve the over-centralized server problem they proposed a blockchain-based secure, interactive, and fair (BSIF) method that attains a low computation cost [35].
To minimize the unnecessary data transmission (i-Health) in Fog architecture, Fog Ranking Service (FRS) and Fog Probing Service (FPS) are introduced [36].
In this paper, the proposed identity-based seamless privacy preservation (IB-SPP) method requires less time to authenticate in critical situations with minimum data [37].
This paper, the proposed Age of Information (AoI) based optimization, which helped to maintain data freshness in the application field [38].
The proposed work was carried out with the help of Castilla and OMNeT++ simulator, the proposed method is the modifications of IEEE 802.15.4 standard, there are six sensors placed on the hip, wrist, chest, foot, and arms of the human body, which are arranged in star topology as shown in Fig. 1a if any event is generated, the data will be sent to the coordinator. If any critical event was generated the proposed method classifies the three types of data. The first one is High critical data example low respiratory, low oxygen, and low Blood pressure, the second one is critical data, such as High Blood Pressure, High and the third one is normal data such as Body temperature. Sometimes, oxygen sensors also send critical data. Next, classified data types are taken for priority calculation [25,31], Based on the priority value the data are sent to the coordinator at varying data rates to minimize the delay as per the criticality. If High critical data and the bandwidth are guaranteed to send in CFP (Contention Free Period), the normal data will be transmitted in the contention period. At last Resnick’s standard prediction [2] was used to predict the highly critical data and allocate the GTS (Guaranteed time slot) before the event to minimize the delay. If the data rate is high, with the critical data, the GTS (Guaranteed time slot) slots will increase as per the requirements, the complete process is given the proposed algorithm, the same is shown in the flow diagram in Fig. 1b, dynamic allocation of GTS IEEE 802.15.4 superframe structure is shown in Fig. 2.
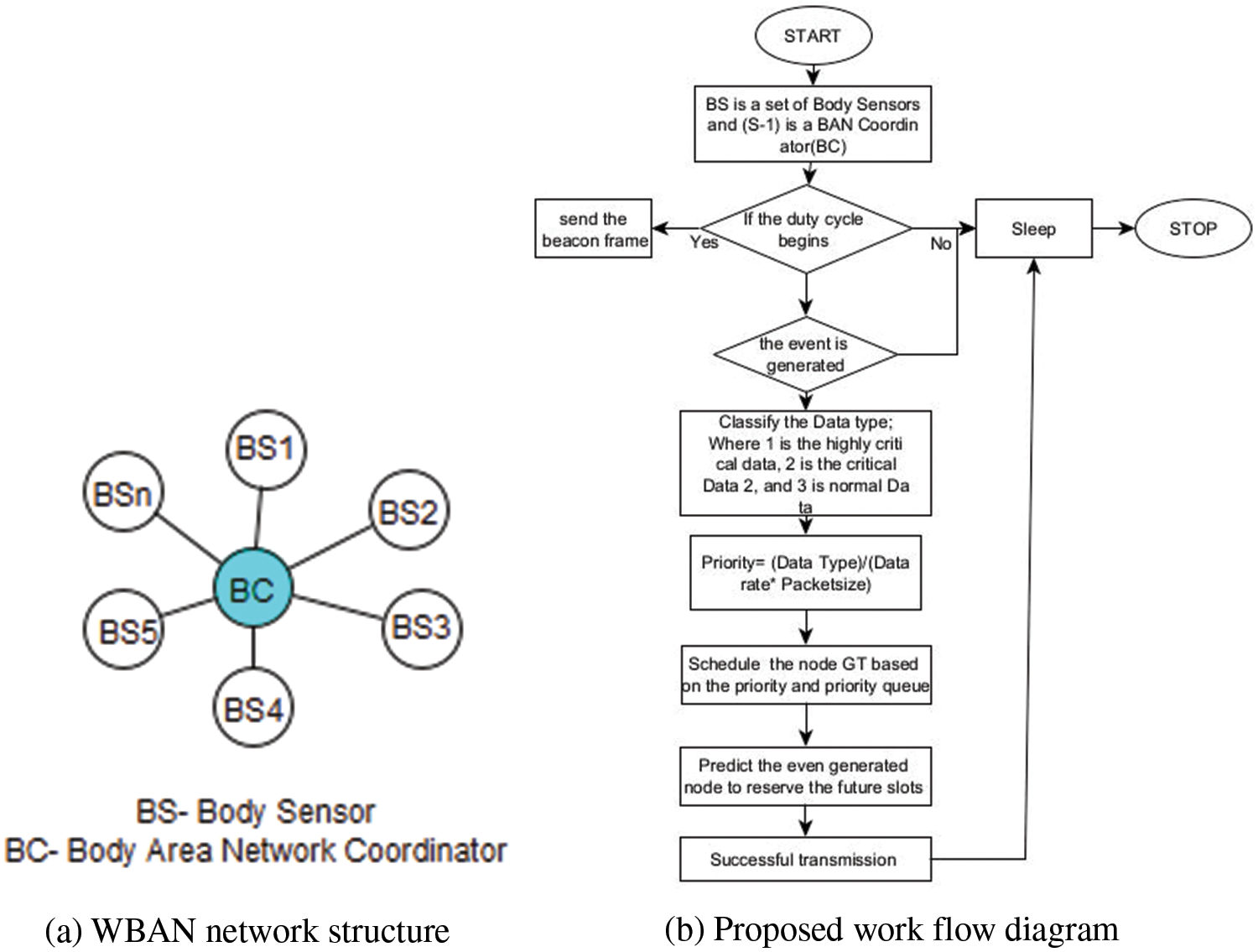
Figure 1: (a) WBAN network structure (b) Proposed work flow diagram
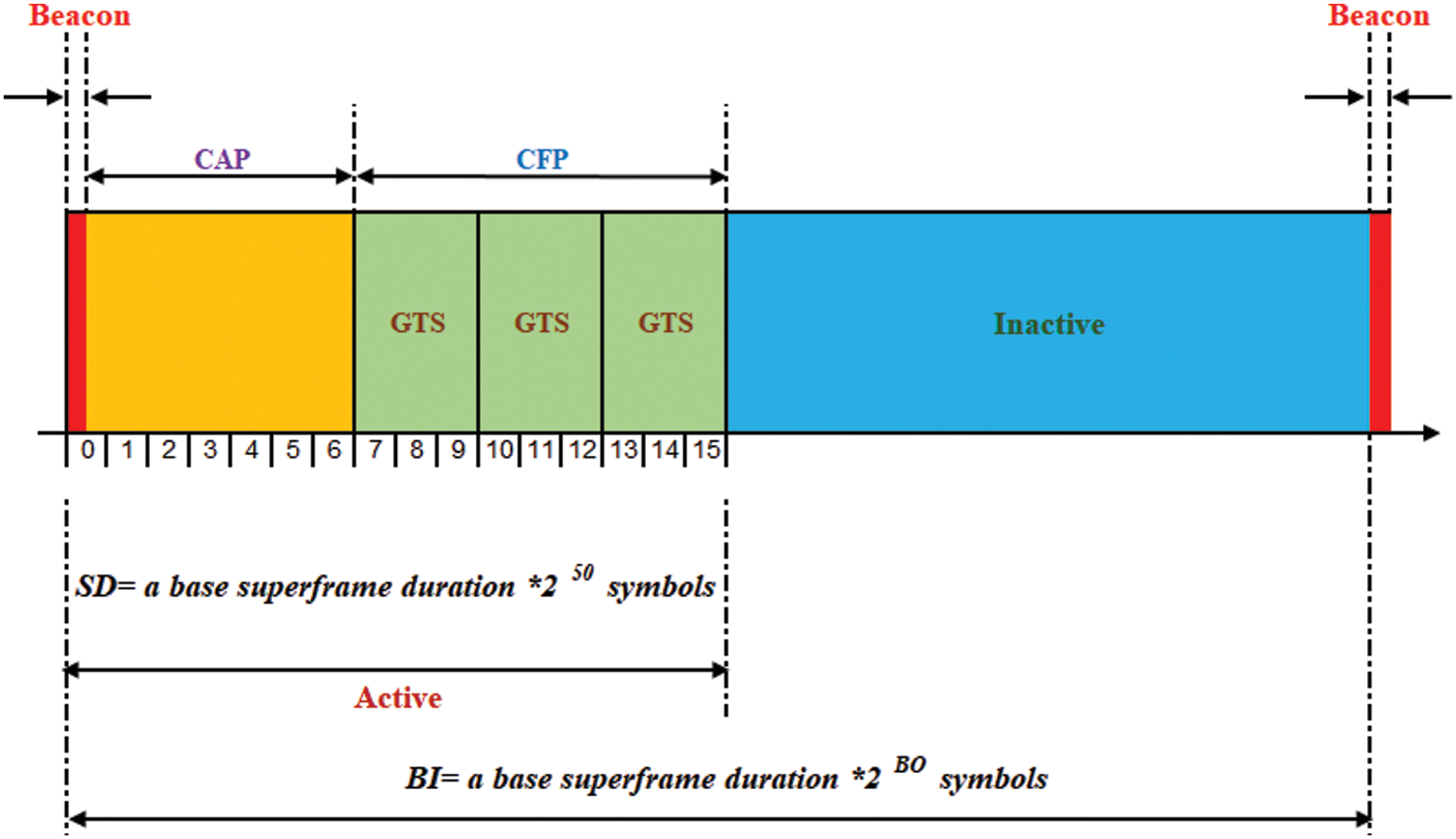
Figure 2: Proposed superframe structure in various GTS slots

Energy Consumption Calculation
The following equations are used to calculate the energy consumption:
The Total Energy Consumption is
where
The energy consumed during an active state
where energy is consumed during sensing,
Energy Consumption during data transmission is calculated as
The Total Energy Consumption is
The Residual Energy will be calculated as
where
The Residual Energy at any point in time (t)
Energy Consumption Calculation.
5 Implementation and Result Analysis
The demonstration of the MVDR protocol is associated with the T-MAC and ZigBee MAC by using the Castalia Simulator. The Simulation used the requirement of IEEE 802.15.4, the WBAN star topology with N-1 devices, and one Coordinator. Classifying the data types, which is used to calculate the Priority to transfer the data with minimum delay and minimum energy consumption to improve the better performance of the MVDR protocol. We used the default BO and vary the slots according to the data rates for both CAP and GTS, the simulations are executed in various time intervals, here we presented the results which are executed in 100 sec, which gave the common output.
The following are the performance metrics that have been considered to compare the protocols.
5.1 Transmitted Packets with Various Protocols
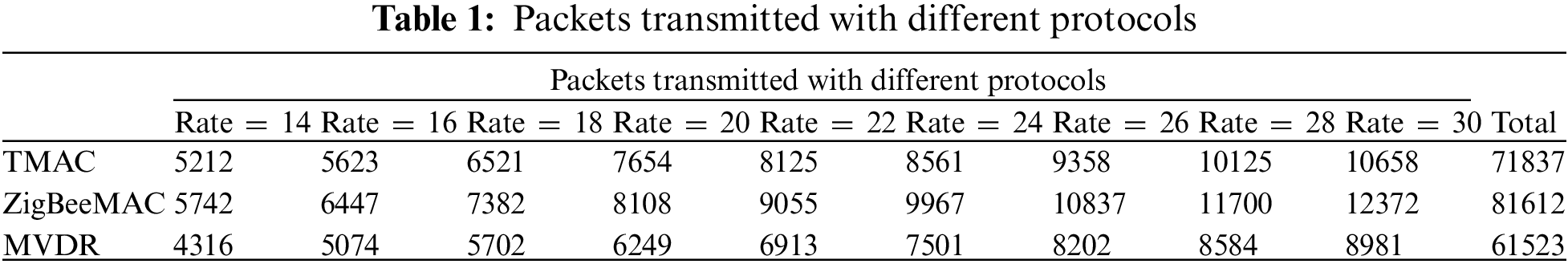
Fig. 3, displays the total number of packets transmitted by three different protocols: TMAC = 71837, ZigBeeMAC = 81612, and MVDR = 61523. The ZigBee MAC has the highest transmission packets than the TMAC protocol. TMAC protocol has higher transmission packets than MVDR protocol. The comparative data are shown in Table 1. Though the transmitted packets are slightly less by MVDR, there are differences in the number of packets received which is going to discuss later.
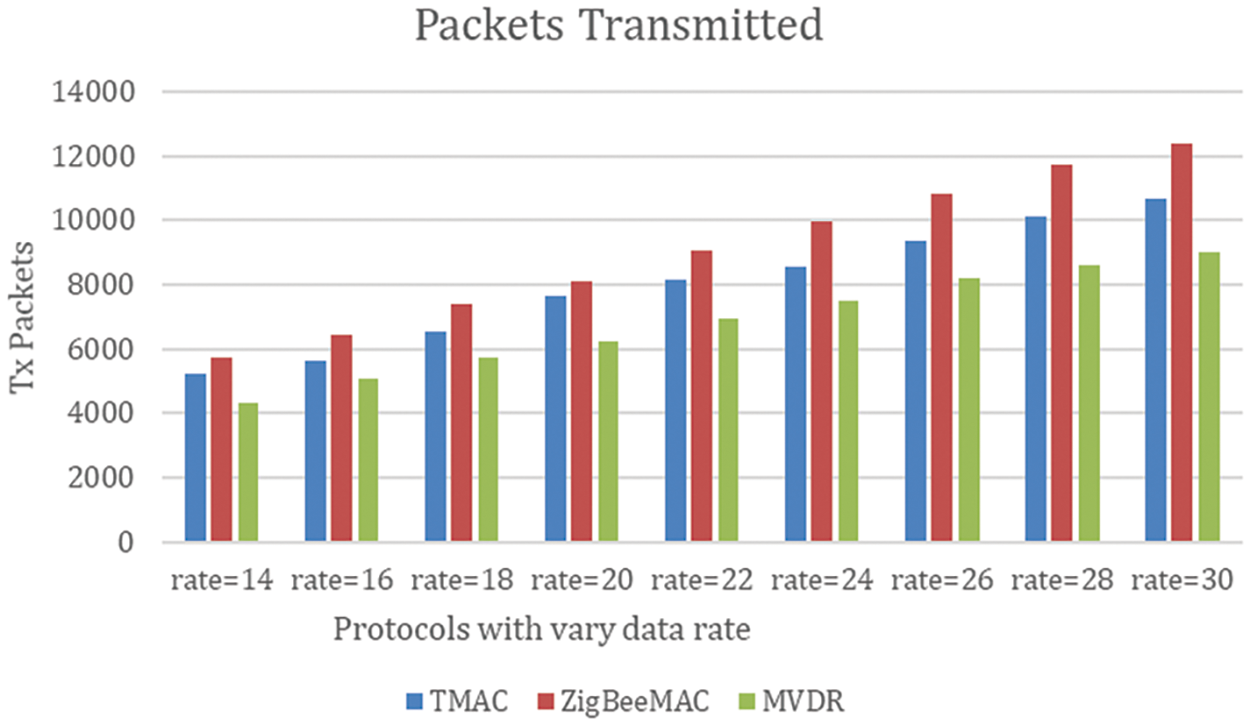
Figure 3: Packets are transmitted with various data rates for different protocols
5.2 Packets Received per Node with Vary Data Rate
In Fig. 4, the simulation results show the packets received per node. The total number of packets received by individual nodes. We compare the sum of packets received by individual protocols by varying data rates given in Fig. 5. As per the simulation results the TMAC protocol received 34987 packets, the ZigBee protocol received 50548 packets, and MVDR received 54098 packets. When comparing the MVDR protocol with the other two, MVDR performs well because the transmitted packets are fewer, and received packets are more compared to other protocols. The reason is MVDR transmits the packets with the minimum delay because of maximum GTS also this protocol prioritizes the packets and predicts the packets before the event generation.
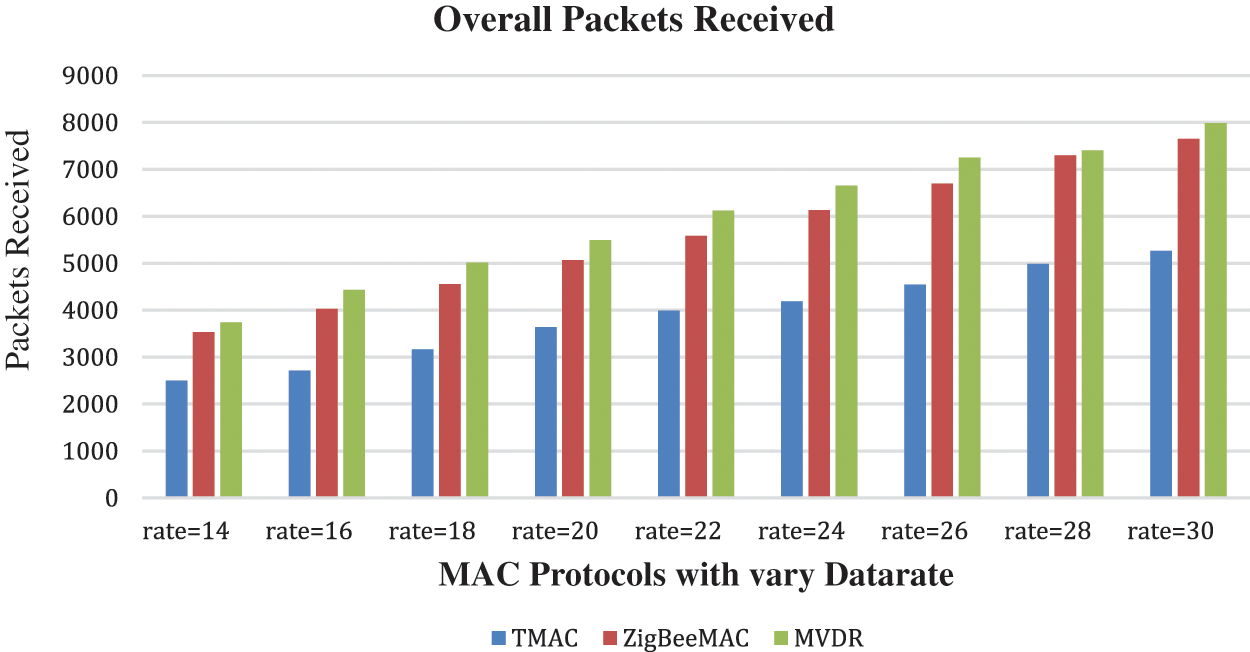
Figure 4: MAC protocols with overall packets received with vary data rates
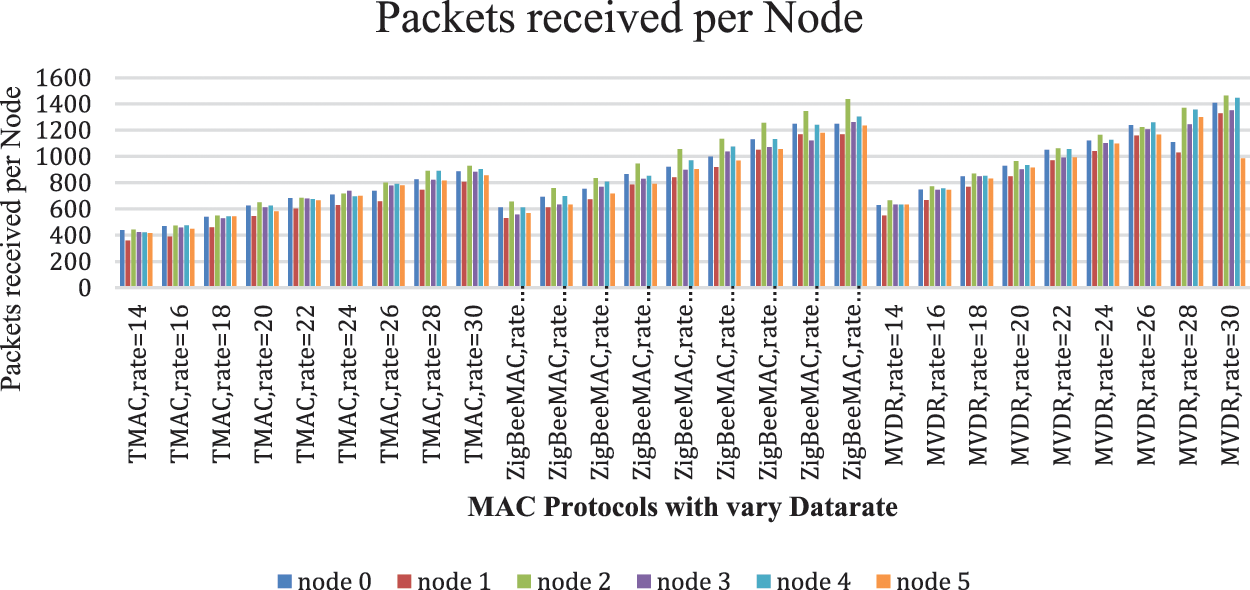
Figure 5: Packets received per node with vary data rate
5.3 Energy Consumption per Node
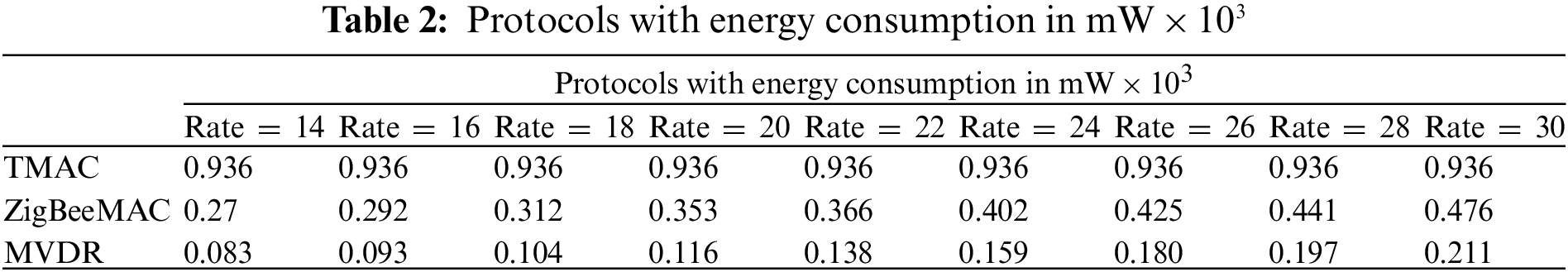
In Fig. 6, the simulation result shows the consumed energy for individual nodes. It displays that the MVDR protocol performs better when compared to the other protocols by varying data rates. The overall energy consumed by varying data rates for the individual protocol is given in Fig. 7. The results show TMAC consumes 8428 mW, ZigBee MAC consumes 3337 mW and MVDR consumes 1281 mW which is less compared to other protocols. The reason is MVDR transmits fewer data packets and receives so some transmitted energy will be saved, the packets are delivered with minimum delay, and some energy is saved because less number of packets are processed in Queue, reducing the active period. The comparative data are shown in Table 2.
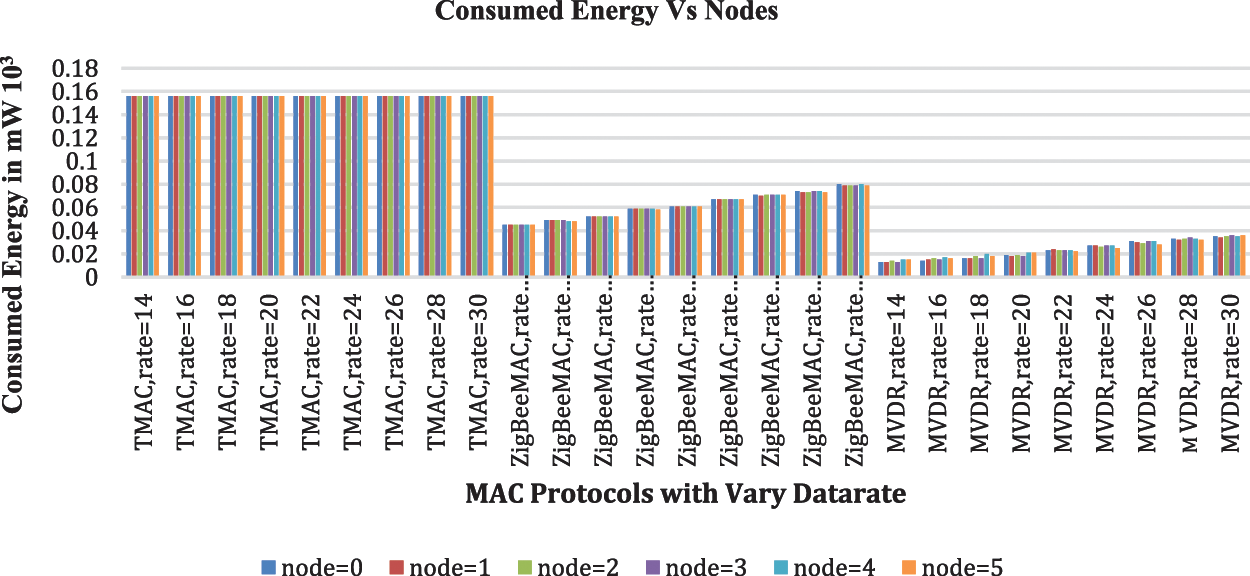
Figure 6: Energy consumption per node
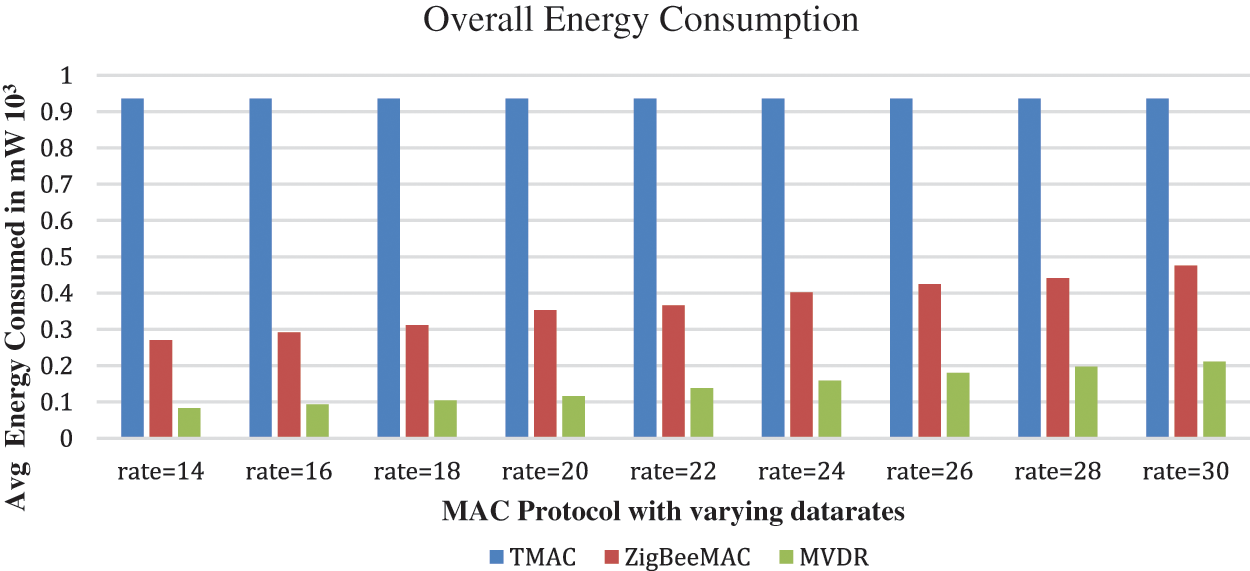
Figure 7: Overall energy consumption
In Fig. 8, the simulation results show the MVDR protocol shows better performance when it is related to other MAC protocols. The packets are distributed with the minimum delay due to the priority and prediction given to the nodes by the controller. The average delay is calculated for all three protocols. The TMAC protocol is 47%, ZigBee is 61%, and MVDR is 87%.
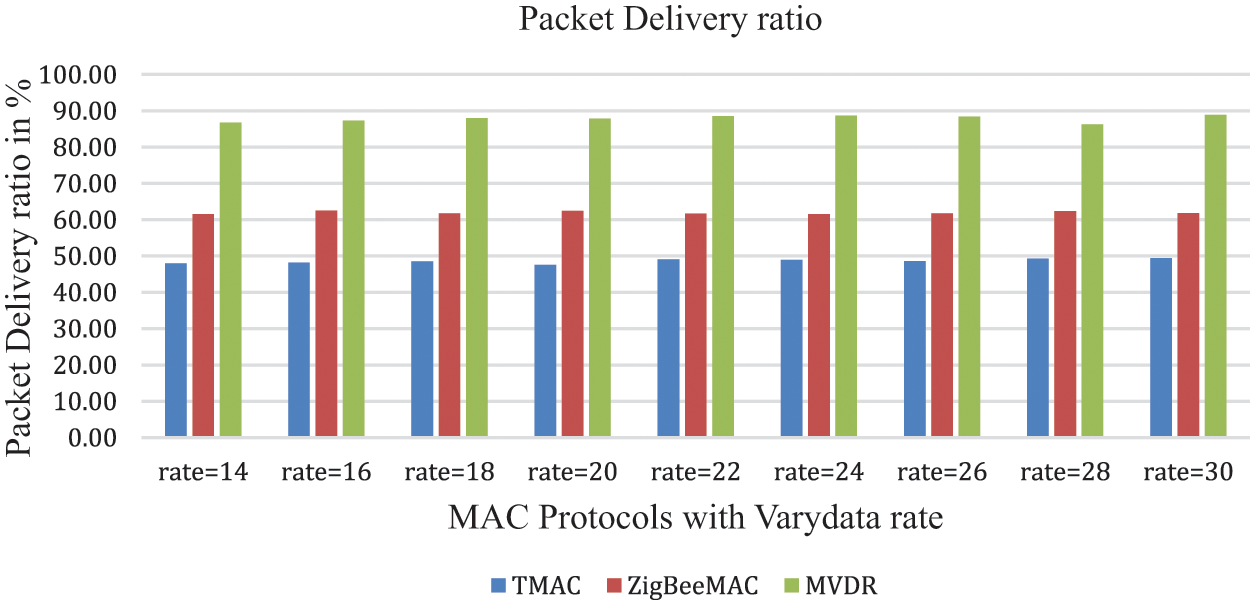
Figure 8: Packet delivery ratio
5.5 Packets in Queue vs. Delay
In Fig. 9, the results show the TMAC protocol has 47043 undelivered packets in Queue, ZigBee has 41043 undelivered packets in Queue, and MVDR is 29932 undelivered packets in Queue. If the average value is compared for Packet delivery ratio MVDR is 107 average packets in queue better in performance than ZigBee and 157.3 average packets in queue and 168.2 average packets in queue for TMAC.
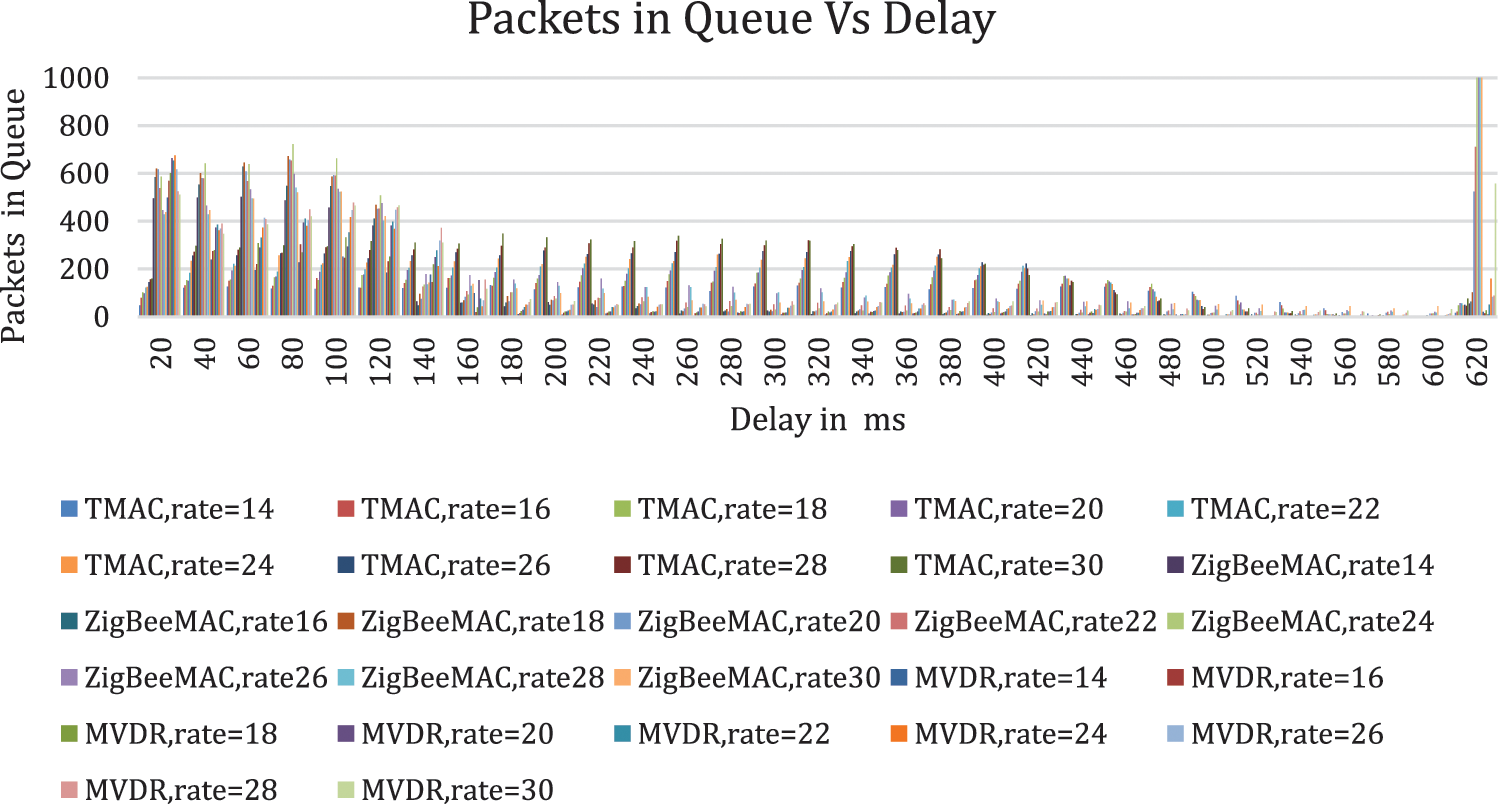
Figure 9: Packets in Queue vs. Delay
The lifetime of the network is calculated based on the given equation
As per the consumed energy with an initial energy of is 18720 J, The lifetime of TMAC is 37.0370 min, ZigBee MAC is 93.4 min, and MVDR 243.5 min. Approximately MVDR extends 155 min more than the ZigBee protocol.
The proposed MVDR protocol demonstrates better in low-power WBAN in terms of energy intake, packet transmission, and delay. When related to contemporary protocols like TMAC and ZigBee protocol. By varying the concepts of the IEEE 802.15.4 standard, the data types are prioritized and predicted in the MVDR protocol. The data rates vary depending on the priority and predictions. The MVDR reduces its transmitted packets, minimizes packet delay, which reduces energy consumption, and increases network lifetime with the help of priority and predictions. In the future, the research must be expanded to protect devices from internal attacks in IoT, cloud-based smart health systems, and multimedia-based smart healthcare applications. The simulation was executed with the static network in the future the proposed work tested with the dynamic network in real-time mode. In the future, the proposed work may be tested with a larger network.
Acknowledgement: The researchers would like to thank Vellore Institute of Technology.
Funding Statement: The authors received no specific funding for this study.
Author Contributions: The authors confirm contribution to the paper as follows: both the authors have the equal contributions in study conception and design, analysis and interpretation of results. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable (This article does not involve data availability and this section is not applicable).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Adhikary, S. Chattopadhyay and S. Choudhury, “A novel bio-inspired algorithm for increasing throughput in wireless body area network (WBAN) by mitigating inter-WBAN interference,” Advanced Computing and Systems for Security, vol. 6, pp. 21–37, 2018. [Google Scholar]
2. J. O’Donovan and B. Smyth, “Trust in recommender systems,” in Proc. of the 10th Int. Conf. on Intelligent User Interfaces, California, USA, pp. 167–174, 2005. [Google Scholar]
3. Y. K. Huang, A. C. Pang and H. N. Hung, “An adaptive GTS allocation scheme for IEEE 802.15.4,” IEEE Transactions on Parallel and Distributed Systems, vol. 19, no. 5, pp. 641–651, 2008. [Google Scholar]
4. O. Omeni, A. C. W. Wong, A. J. Burdett and C. Toumazou, “Energy efficient medium access protocol for wireless medical body area sensor networks,” IEEE Transactions on Biomedical Circuits and Systems, vol. 2, no. 4, pp. 251–259, 2008. [Google Scholar] [PubMed]
5. X. Zhang, H. Jiang, X. Chen, L. Zhang and Z. Wang, “An energy-efficient implementation of on-demand MAC protocol in medical wireless body sensor networks,” in 2009 IEEE Int. Symp. on Circuits and Systems, Taipei, Taiwan, pp. 3094–3097, 2009. [Google Scholar]
6. B. Otal, L. Alonso and C. Verikoukis, “Highly reliable energy-saving MAC for wireless body sensor networks in healthcare systems,” IEEE Journal on Selected Areas in Communications, vol. 27, no. 4, pp. 553–565, 2009. [Google Scholar]
7. K. A. Ali, J. H. Sarker and H. T. Mouftah, “A MAC protocol for cognitive wireless sensor body area networking,” Wireless Communications and Mobile Computing, vol. 10, no. 12, pp. 1656–1671, 2010. [Google Scholar]
8. H. Cao, S. González-Valenzuela and V. C. M. Leung, “Employing IEEE 802.15.4 for quality of service provisioning in wireless body area sensor networks,” in 2010 24th IEEE Int. Conf. on Advanced Information Networking and Applications, Perth, Australia, pp. 902–909, 2010. [Google Scholar]
9. S. Ullah, P. Khan, N. Ullah, S. Saleem, H. Higgins et al., “A review of wireless body area networks for medical applications,” arXiv preprint arXiv:1001.0831, 2010. [Google Scholar]
10. G. Mihai, D. A. Alina and B. Ion, “Performance analysis on T-MAC protocol over a body area network,” in 2010 3rd Int. Symp. on Electrical and Electronics Engineering (ISEEE), Brasov, Romania, pp. 224–227, 2010. [Google Scholar]
11. H. W. Tseng, S. T. Sheu and Y. Y. Shih, “Rotational listening strategy for IEEE 802.15.4 wireless body networks,” IEEE Sensor Journal, vol. 11, no. 9, pp. 1841–1855, 2010. [Google Scholar]
12. Y. Zhang and G. Dolmans, “Priority-guaranteed MAC protocol for emerging wireless body area networks,” Annals of Telecommunications-Annales des Télécommunications, vol. 66, no. 3, pp. 229–241, 2011. [Google Scholar]
13. G. Zhou, Q. Li, J. Li, Y. Wu, S. Lin et al., “Adaptive and radio-agnostic QoS for body sensor networks,” ACM Transactions on Embedded Computing Systems (TECS), vol. 10, no. 4, pp. 1–34, 2011. [Google Scholar]
14. L. Lin, K. J. Wong, A. Kumar, S. L. Tan and S. J. Phee, “An energy-efficient MAC protocol for mobile in-vivo body sensor networks,” in 2011 Third Int. Conf. on Ubiquitous and Future Networks (ICUFN), Dalian, China, pp. 95–100, 2011. [Google Scholar]
15. N. Javaid, S. Hayat, M. Shakir, M. A. Khan, S. H. Bouk et al., “Energy efficient mac protocols in wireless body area sensor networks–A survey,” arXiv preprint arXiv:1303.2072, 2013. [Google Scholar]
16. N. Bradai, L. C. Fourati, S. Boudjit and L. Kamoun, “New priority MAC protocol for wireless body area networks,” in Proc. of the 3rd ACM MobiHoc Workshop on Pervasive Wireless Healthcare, Bangalore, India, pp. 1–6, 2013. [Google Scholar]
17. Y. Huang, S. Member, A. Pang and H. Hung, “An adaptive GTS allocation scheme,” IEEE Transactions on Parallel and Distributed Systems, vol. 19, no. 5, pp. 641–651, 2008. [Google Scholar]
18. R. H. Kim and P. S. Kim, “An effect of delay reduced MAC protocol for WBAN based medical signal monitoring,” in 2015 IEEE Pacific Rim Conf. on Communications, Computers and Signal Processing (PACRIM), Victoria, Canada, pp. 434–437, 2015. [Google Scholar]
19. S. Pandit, K. Sarker, M. Razzaque and A. M. Jehad Sarkar, “An energy-efficient multiconstrained QoS aware MAC protocol for body sensor networks,” Multimedia. Tools and Application, vol. 74, no. 14, pp. 5353–5374, 2015. [Google Scholar]
20. M. B. Rasheed, N. Javaid, M. Imran, Z. A. Khan, U. Qasim et al., “Delay and energy consumption analysis of priority guaranteed MAC protocol for wireless body area networks,” Wireless Networks, vol. 23, no. 4, pp. 1249–1266, 2017. [Google Scholar]
21. D. Liu, J. Wang, C. Jiang, F. Ren and Y. Ren, “A contention-oriented node sleeping MAC protocol for WBAN,” in 2018 IEEE Wireless Communications and Networking Conf. (WCNC), Spain, pp. 2–7, 2018. [Google Scholar]
22. A. Bhatia and R. K. Patro, “A delay and energy efficient poll-based mac protocol for wireless body area networks,” Wireless Personal Communications, vol. 99, no. 2, pp. 915–939, 2018. [Google Scholar]
23. M. Ambigavathi and D. Sridharan, “Energy efficient and load balanced priority queue algorithm for wireless body area network,” Future Generation Computer Systems, vol. 88, pp. 586–593, 2018. [Google Scholar]
24. L. Aissaoui Ferhi, K. Sethom and F. Choubani, “Energy efficiency optimization for wireless body area networks under 802.15.6 standard,” Wireless Personal Communications, vol. 109, no. 3, pp. 1769–1779, 2019. [Google Scholar]
25. N. Sultana, F. Huq, M. A. Razzaque and M. M. Rahman, “Prioritized IEEE 802.15.6 mac protocol for wireless body area network,” in 2019 Int. Conf. on Sustainable Technologies for Industry 4.0 (STI), Dhaka, Bangladesh, pp. 1–5, 2019. [Google Scholar]
26. A. K. Pandey and N. Gupta, “An energy-efficient distributed queuing random access (EE-DQRA) MAC protocol for wireless body sensor networks,” Wireless Networks, vol. 26, no. 4, pp. 2875–2889, 2020. [Google Scholar]
27. F. Ullah, A. H. Abdullah, O. Kaiwartya, J. Lloret and M. M. Arshad, “EETP-MAC: Energy efficient traffic prioritization for medium access control in wireless body area networks,” Telecommunication System, vol. 75, no. 2, pp. 181–203, 2020. [Google Scholar]
28. S. Misra, P. K. Bishoyi and S. Sarkar, “I-MAC: In-body sensor MAC in wireless body area networks for healthcare IoT,” IEEE Systems Journal, vol. 15, no. 3, pp. 4413–4420, 2020. [Google Scholar]
29. S. M. Muzammal, R. K. Murugesan, N. Z. Jhanjhi and L. T. Jung, “SMTrust: Proposing trust-based secure routing protocol for RPL attacks for IoT applications,” in 2020 Int. Conf. on Computational Intelligence (ICCI), Malaysia, pp. 305–310, 2020. [Google Scholar]
30. R. Gupta and S. Biswas, “Priority-based IEEE 802.15.4 MAC by varying GTS to satisfy heterogeneous traffic in healthcare application,” Wireless Networks, vol. 26, no. 3, pp. 2287–2304, 2020. [Google Scholar]
31. H. Sharmila and N. Jaisankar, “E-MHMS: Enhanced MAC-based secure delay-aware healthcare monitoring system in WBAN,” Cluster Computing, vol. 23, no. 3, pp. 1725–1740, 2020. [Google Scholar]
32. A. K. Subramanian, U. Ghosh, S. Ramaswamy, W. S. Alnumay and P. K. Sharma, “PrEEMAC: Priority based energy efficient MAC protocol for wireless body sensor networks,” Sustainable Computing: Informatics and Systems, vol. 30, pp. 100510, 2021. [Google Scholar]
33. T. Samal and M. R. Kabat, “A prioritized traffic scheduling with load balancing in wireless body area networks,” Journal of King Saud University-Computer and Information Sciences, vol. 34, no. 8, pp. 5448–5455, 2022. [Google Scholar]
34. W. Wang, Q. Chen, Z. Yin, G. Srivastava, T. Reddy et al., “Blockchain and PUF-based lightweight authentication protocol for wireless medical sensor networks,” IEEE Internet of Things Journal, vol. 9, no. 11, pp. 8883–8891, 2021. [Google Scholar]
35. W. Wang, Y. Yang, Z. Yin, K. Dev, X. Zhou et al., “BSIF: Blockchain-based secure, interactive, and fair mobile crowd sensing,” IEEE Journal on Selected Areas in Communications, vol. 40, no. 12, pp. 3452–3469, 2022. [Google Scholar]
36. J. L. Sarkar, V. Ramasamy, A. Majumder, B. Pati, C. R. Panigrahi et al., “I-Health: SDN-based Fog architecture for IIoT applications in healthcare,” IEEE/ACM Transactions on Computational Biology and Bioinformatics, pp. 1–8, 2022. [Google Scholar]
37. B. D. Deebak, F. H. Memon, S. A. Khowaja, K. Dev, W. Wang et al., “In the digital age of 5G networks: Seamless privacy-preserving authentication for cognitive-inspired internet of medical things,” IEEE Transactions on Industrial Informatics, vol. 18, no. 12, pp. 8916–8923, 2022. [Google Scholar]
38. Y. Yang, W. Wang, Z. Yin, R. Xu, X. Zhou et al., “Mixed game-based AoI optimization for combating COVID-19 with AI bots,” IEEE Journal on Selected Areas in Communications, vol. 40, no. 11, pp. 3122–3138, 2022. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools