 Open Access
Open Access
ARTICLE
Archimedes Optimization with Deep Learning Based Aerial Image Classification for Cybersecurity Enabled UAV Networks
Information Technology Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah, 21589, Saudi Arabia
* Corresponding Author: Mahmoud Ragab. Email:
Computer Systems Science and Engineering 2023, 47(2), 2171-2185. https://doi.org/10.32604/csse.2023.039931
Received 24 February 2023; Accepted 22 May 2023; Issue published 28 July 2023
Abstract
The recent adoption of satellite technologies, unmanned aerial vehicles (UAVs) and 5G has encouraged telecom networking to evolve into more stable service to remote areas and render higher quality. But, security concerns with drones were increasing as drone nodes have been striking targets for cyberattacks because of immensely weak inbuilt and growing poor security volumes. This study presents an Archimedes Optimization with Deep Learning based Aerial Image Classification and Intrusion Detection (AODL-AICID) technique in secure UAV networks. The presented AODL-AICID technique concentrates on two major processes: image classification and intrusion detection. For aerial image classification, the AODL-AICID technique encompasses MobileNetv2 feature extraction, Archimedes Optimization Algorithm (AOA) based hyperparameter optimizer, and backpropagation neural network (BPNN) based classifier. In addition, the AODL-AICID technique employs a stacked bi-directional long short-term memory (SBLSTM) model to accomplish intrusion detection for cybersecurity in UAV networks. At the final stage, the Nadam optimizer is utilized for parameter tuning of the SBLSTM approach. The experimental validation of the AODL-AICID technique is tested and the obtained values reported the improved performance of the AODL-AICID technique over other models.Keywords
Nowadays, drones or Unmanned Aerial Vehicles (UAVs) [1] can be referred to as flying objects that can fly autonomously or with the help of human pilots. Drones were utilized for rescue operations, package delivery, environmental management, aerial mapping, aerial photography, irrigation, monitoring, and other critical applications [2]. Intrusion detection methods and Security schemes will be utilized for guaranteeing critical security features [3]. The aerial image classifier methods present different indispensable classes that can be achieved by operating the changes in spatial organization along with that systematic process for devising the desired method. Dissimilar to pixel categorizing methods, scene classifier delivers localized data even at the occurrence of wider aerial imageries which have unambiguous semantic data of surfaces [4,5].
In this study, aerial scenes are distinguished into lower-level structures which often use spectral, texture, structural features, and many more [6]. Then, low-level feature vectors that are visual parameters are filtered globally or locally and implemented for defining the aerial scene images. Recently, deep learning (DL) based techniques were implemented in high-level feature extraction [7]. The orthodox DL methods deliver a potential result while processing existing problems such as speech or object analysis, processing and predicting the natural language. So, the above-discussed structure gained a reputed task and attained an existing ranking which had a focus on educational fields along with that commercial groups. Also, DL techniques relevant to hierarchical features defined several phases of extraction. Also, deep Convolutional neural networks (DCNN) were crucial components implemented in scene classification, inspecting in addition to detecting processes [8]. DL methods, particularly CNN, have attained great achievement in segmentation, image classification, and detection on numerous benchmarks [9]. CNN refers to a hierarchical network invariant to image translations. The key to success is the capability to study the progressively complicated transformations of input and for capturing invariances from large, labelled data sets [10]. But it is problematic to directly implement the CNNs to remote sensing scene classification for millions of variables to train the CNNs, which trained samples are inadequate for training.
This study presents an Archimedes Optimization with Deep Learning based Aerial Image Classification and Intrusion Detection (AODL-AICID) technique in secure UAV networks. The presented AODL-AICID technique concentrates on two major processes: image classification and intrusion detection. For aerial image classification, the AODL-AICID technique encompasses MobileNetv2 feature extraction, Archimedes Optimization Algorithm (AOA) based hyperparameter optimizer, and backpropagation neural network (BPNN) based classifier. In addition, the AODL-AICID technique employs a stacked bidirectional long short-term memory (SBLSTM) model to accomplish intrusion detection for cybersecurity in UAV networks. At the final stage, the Nadam optimizer is used for optimal hyperparameter tuning of the SBLSTM model. The experimental validation of the AODL-AICID technique is tested under different performance measures.
He et al. [11] examine a conditional GAN (CGAN)-related collaborative ID technique with blockchain (BC) allowed distributed federated learning for solving these issues. This research establishes LSTM into CGAN trained for improving the outcome of generative networks. According to the extracting feature capability of LSTM networks, the created data with CGAN can be utilized as augmented data and executed in the classification and recognition of intrusion data. Alissa et al. [12] concentrated on the proposal of a Crystal Structure Optimizer with DAE-based ID (CSODAE-ID) for securing the IoD platform. The purpose of the projected CSODAE-ID technique is to detect the intrusion presence from the IoD platform. During the presented CSODAE-ID technique, a novel Modified Deer Hunting Optimized-based FS (MDHO-FS) system was executed for choosing the feature subsets. Simultaneously, the Auto-encoder (AE) technique was utilized for the intrusion classifier from the IoD platform. The CSO technique is simulated by the development of crystal frameworks dependent upon the lattice points utilized finally the hyperparameter-tuning procedure.
Tan et al. [13] introduce an ID approach dependent upon a DBN optimizer by PSO technique. At primary, the classifier method dependent upon the DBN has been created, and the PSO system was utilized for optimizing the hidden layer node count of DBN for obtaining a better DBN infrastructure. Sedjelmaci et al. [14] concentrate on a particular case which is UAV Edge Computing (UEC) network. Addressing the security problem in the UEC network has compulsory owing to the significance of UEC services like network traffic monitor, or searching and rescuing functions. Zhang et al. [15] present a hybrid approach dependent upon either spectral traffic investigation or robust controller or observer to anomaly estimate inside a UAV network. This technique was dependent upon either Lyapunov Krasovskii functional or dynamic performance.
Whelan et al. [16] examine a novelty-based method to ID from UAVs by utilizing a one-class classifier. PCA was implemented to sensor logs for reducing dimensional, and one-class classifier techniques can be created per sensor. The count of one-class classifiers can be chosen: One-Class SVM, AE-NN, and Local Outlier Factor. In [17], a railway clearance ID technique in aerial video dependent upon CNN was presented. Initially, the rail track area has declared in aerial single frame image with linear segment recognition technique, line segment merge as well as screen. At last, the single frame detection outcome was optimised by the inter-frame connection of videos for obtaining the last outcome of railway clearance ID from aerial video.
In this study, we have developed a new AODL-AICID technique for aerial image classification and intrusion detection in UAV networks. The presented AODL-AICID technique concentrates on two major processes: image classification and intrusion detection. For aerial image classification, the AODL-AICID technique encompasses MobileNetv2 feature extraction, an AOA-based hyperparameter optimizer, and a BPNN-based classifier. In addition, the AODL-AICID technique employed the Nadam optimizer with the SBLSTM model for intrusion detection in the UAV networks. Fig. 1 depicts the overall procedure of the AODL-AICID approach.
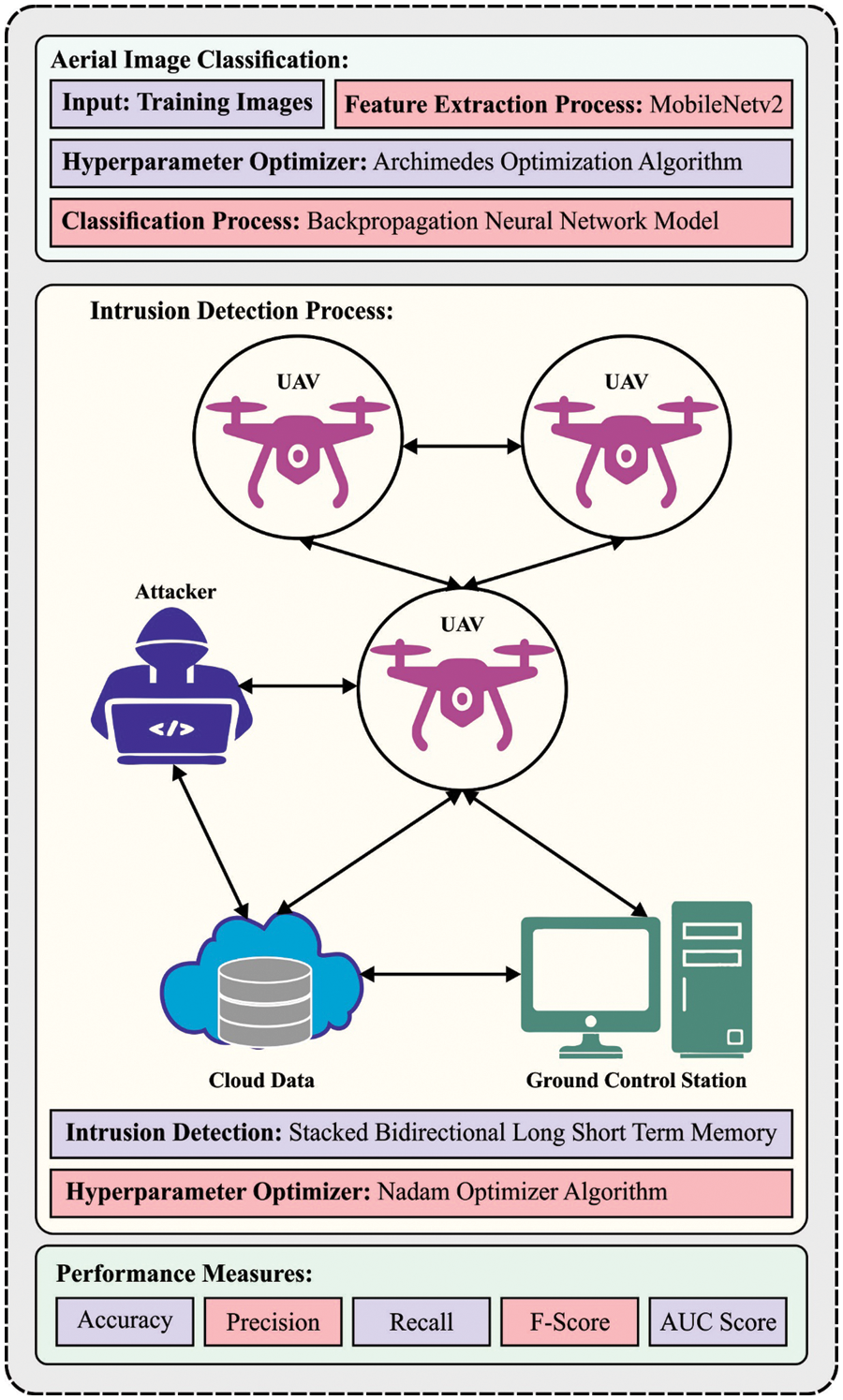
Figure 1: Overall procedure of the AODL-AICID system
3.1 Module I: Aerial Image Classification
In this study, the AODL-AICID technique encompasses MobileNetv2 feature extraction, an AOA-based hyperparameter optimizer, and a BPNN-based classifier applied for aerial imageclassification.
Here, the AODL-AICID technique involves the MobileNetv2 model to generate a collection of future vectors. MobileNet architecture alternatively referred to as MobileNetV1 applies to embedded devices and smartphones [18]. Depthwise separable convolution was designed that comprised depthwise and pointwise convolutional layers for decreasing the size of the parameter and reducing the dimension of several layers. Following, rectified linear unit (ReLU) and batch normalization (BN) layers are added afterwards depth-wise separable convolution.
While applying MobileNet for testing on the ImageNet data, MobileNetV1 had 4.2 M parameters, whereas widespread architecture GoogLeNet and VGG16 architecture had 6.8 and 138 M, correspondingly. The experiment of the GoogLeNet attained 69.8% of accuracy whereas the MobileNetV1 on the ImageNet dataset attained 70.6% of accuracy. The authors developed a MobileNetV2 by increasing invert residual, a short connection. The inverted residual was introduced to deal with the memory problem by decreasing the quantity of tensor stored in memory while processing. The linear bottleneck which is a rise in the number of feature maps namely ResNet increase the feature maps from 64 to 128, 256, and 512, correspondingly. MobileNetV2 structure could reduce the number of parameters and be faster in computational time than MobileNetV1. The experiment with MobileNetV2 attained an accuracy of 72.0%, that is was greater than NASNet, MobileNetV1, and ShuffleNet.
To adjust the hyperparameter values of the MobielNetv2 model, the AOA algorithm is applied in this work. The AOA approach [19] was applied to resolve the optimization problem in conjunction with NR mathematical approach. The AOA technique is a metaheuristic approach used to resolve different mathematical optimized problems and is verified the ability for fetching a global solution from a limited duration. The AOA's necessary condition hinges on Archimedes’ rule of buoyancy. The AOA enables various phases defining the nearby global solution, and this phase is illustrated by the following expression:
Phase 1: The initial population contains the immersed object (solution) and is regarded by acceleration, volume, and density. Every solution was initialized by the arbitrary place from the fluid as given below, following the fitness value to every solution is evaluated.
Now
Phase 2: The density and volume of every solution were upgraded through the succeeding equation:
Now
Phase 3: During the transfer operator and density factor, the collision among solutions remains in an equilibrium state and it can be mathematically expressed in the following:
In Eq. (7),
Phase 4: During exploration, the collision between solutions takes place. Thus, if
Now
Phase 5: During exploitation, no collision among solutions takes place. If
In Eq. (10),
Phase 6: The Normalize acceleration is used to assess the percentage of alteration:
In Eq. (11), g, and z show the normalized range.
Phase 6: during Evaluation, the fitness value of each solution is assessed, and the best solution was registered, for example, upgrading the optimal solution
For classifying aerial images, the BPNN model is used. BPNN uses a monitored learning technique and the feed-forward structure of ANN [20]. The conventional BPNN involves a single hidden layer, 1 input layer, and one output layer. It contains n output neurons, one input neuron, and
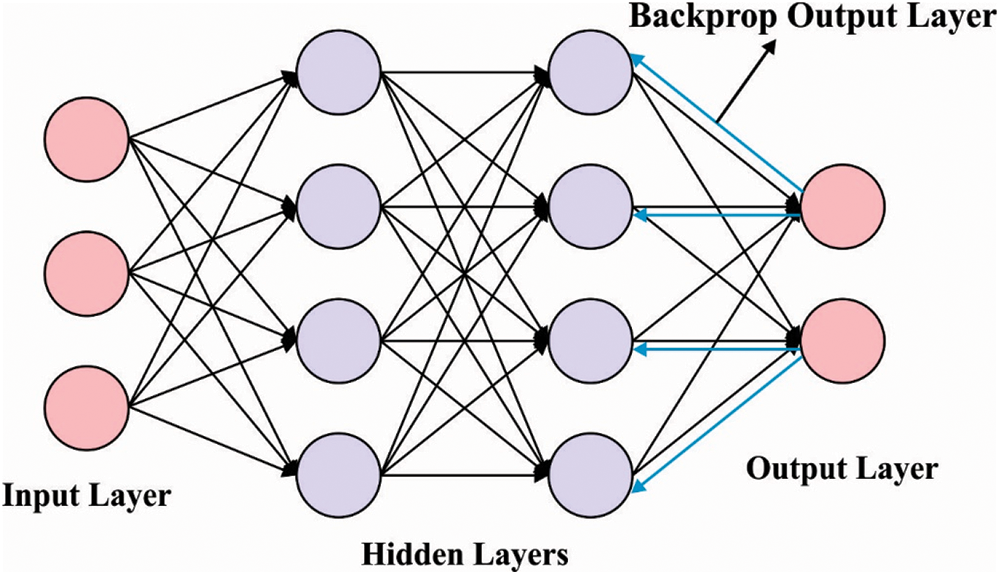
Figure 2: Architecture of BPNN
Place
Output from the neuron in the input layer is
Output from the neuron in the hidden layer is
Output from the neuron in the output layer is
where
3.2 Module II: Intrusion Detection
To recognize the intrusions accurately, the SBLSTM model is exploited here. The conventional architecture of LSTM successfully resolves the gradient disappearing problem and transports valuable data within the LSTM model [21]. Now, the Recurrent Neural Network (RNN) failed to capture long-term dependency among feature vectors. The LSTM cell encompasses of forget gate
• Forget gate: this gate determines how much information from the previous layer
In Eq. (15),
• Input gate: this gate determines the amount of network input
Now,
• Output gate: this gate determines the number of data transported to the LSTM from the cell state
whereas
The final output of the LSTM cell is output cell state
The intermediate input cell is represented by
Now
The LSTM is exploited by fruit fly optimization for NN information for the analysis of time series. At the same time, LSTM was employed in fully diverse fields to predict the lifetime of equipment in the mechanical transmission system. A BiLSTM includes two different LSTMs that integrate data from two directions. Next, the data is accomplished as word annotation from the user information. The forward LSTM process the input left to right and evaluates the hidden layer
Furthermore, the deep hierarchical technique enhances classification performance. On the other hand, the stacked BLSTM is effective in the shallow learning mechanism, thereby the proposed technique determines the stacking BLSTM to apply the local context and latent symmetry complex dataset. The output of the lower layer becomes the input of the upper layer in the Stacked BLSTM.
Finally, the Nadam optimizer is used for the hyperparameter tuning process. Nadam is called a variant of the weight update rule [22]. It can be calculated by expression of
Thus, the Nadam update rule was presented by substituting the bias-corrected prediction of the previous momentum vector
The experimental validation of the AODL-AICID method is tested through the UCM Land use data [23]. It is a 21-class land-use image data set meant for research purposes. There exist 100 images for all classes. Every image measures 256 × 256 pixels. The images are manually extracted from large imagery with the help of the USGS National Map Urban Area Imagery collection for various urban areas around the country. The pixel resolution of this public domain imager is 1 foot. Fig. 3 depicts the sample images from the UCM dataset.

Figure 3: Sample images from UCM dataset
Table 1 reports detailed classification outcomes of the AODL-AICID technique with other DL models. Fig. 4 investigates the classification results of the AODL-AICID model with existing models in terms of
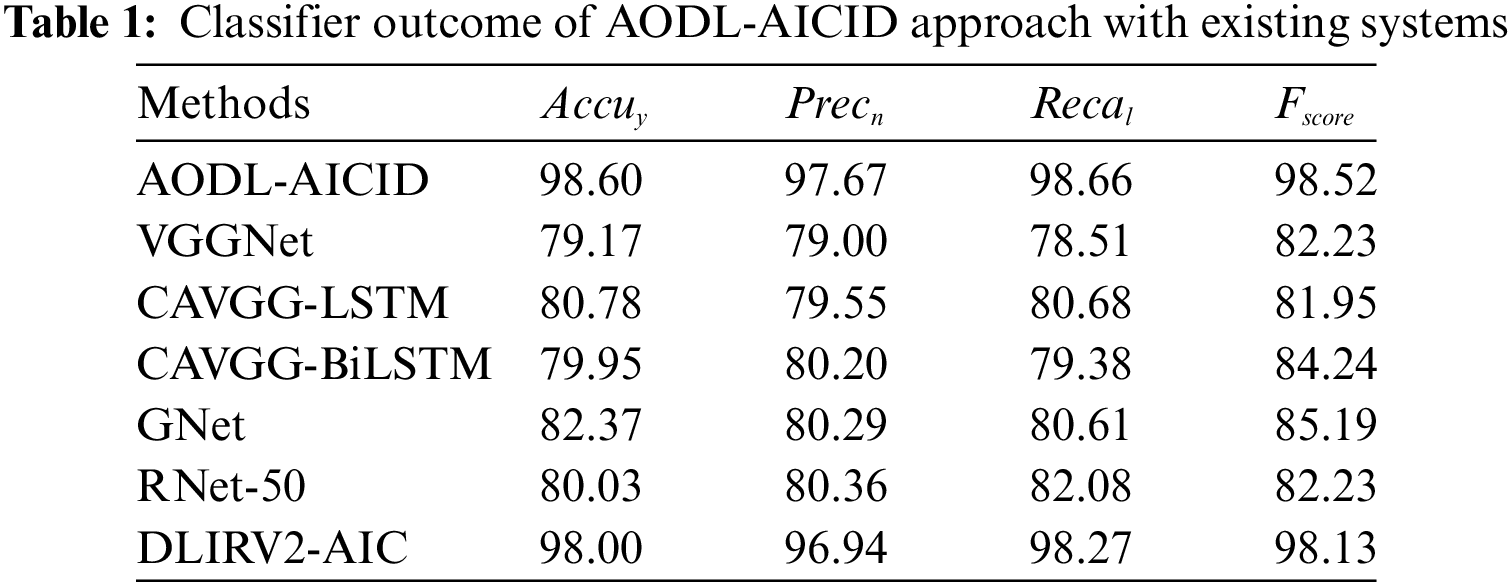
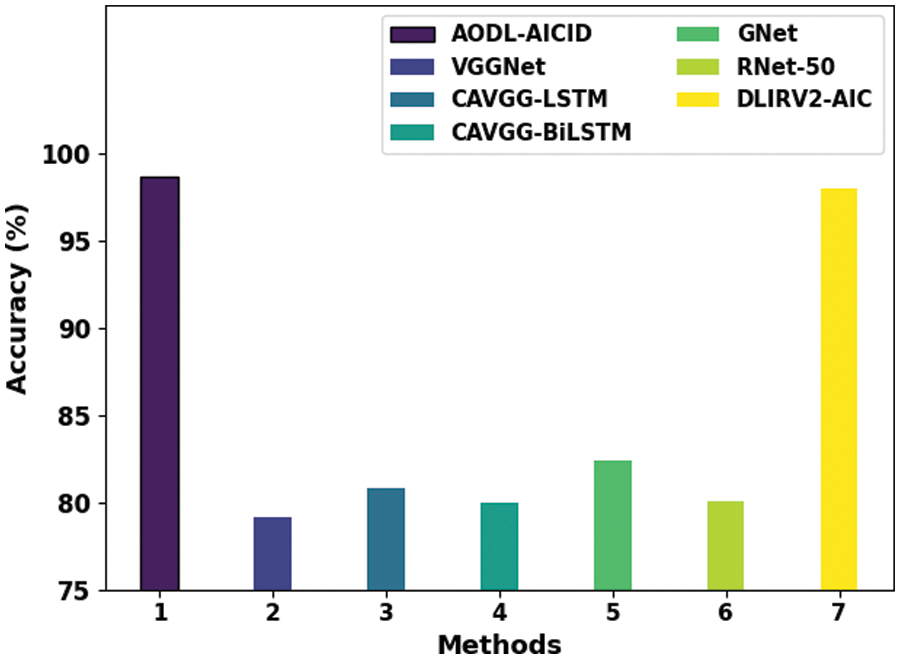
Figure 4:
Fig. 5 investigates the classification results of the AODL-AICID method with existing techniques in terms of
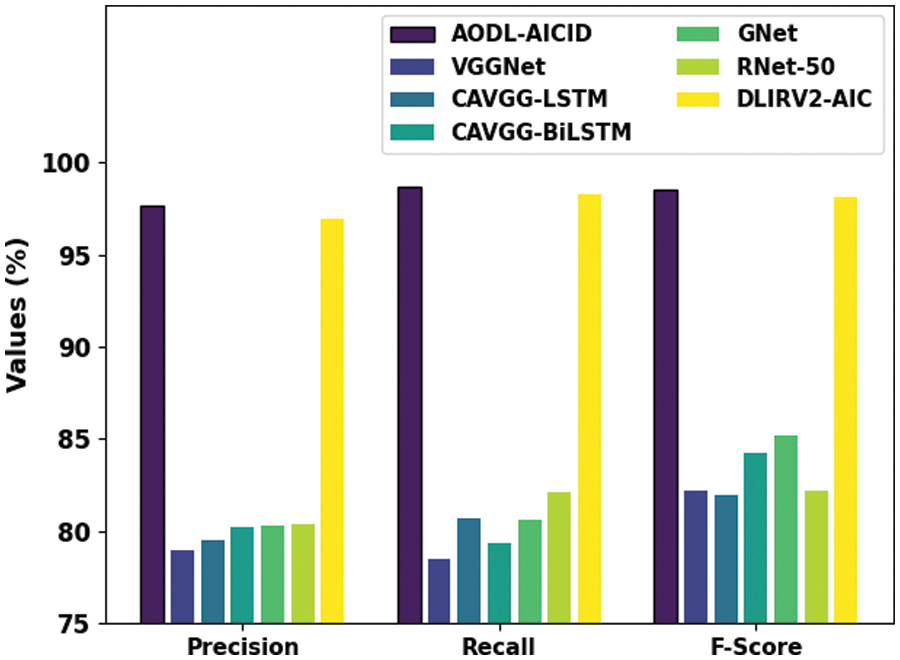
Figure 5:
To assure the enhanced performance of the AODL-AICID method, a detailed result analysis takes place on the CSE-CIC-IDS-2018 dataset [24]. In this case, only four types of attacks were considered.
Table 2 and Fig. 6 investigate the attack detection results of the AODL-AICID model under botnet and DDoS attacks [5,25]. The outcomes show that the AODL-AICID technique has recognized both botnet and DDoS attacks proficiently. For instance, the AODL-AICID model has accomplished a higher
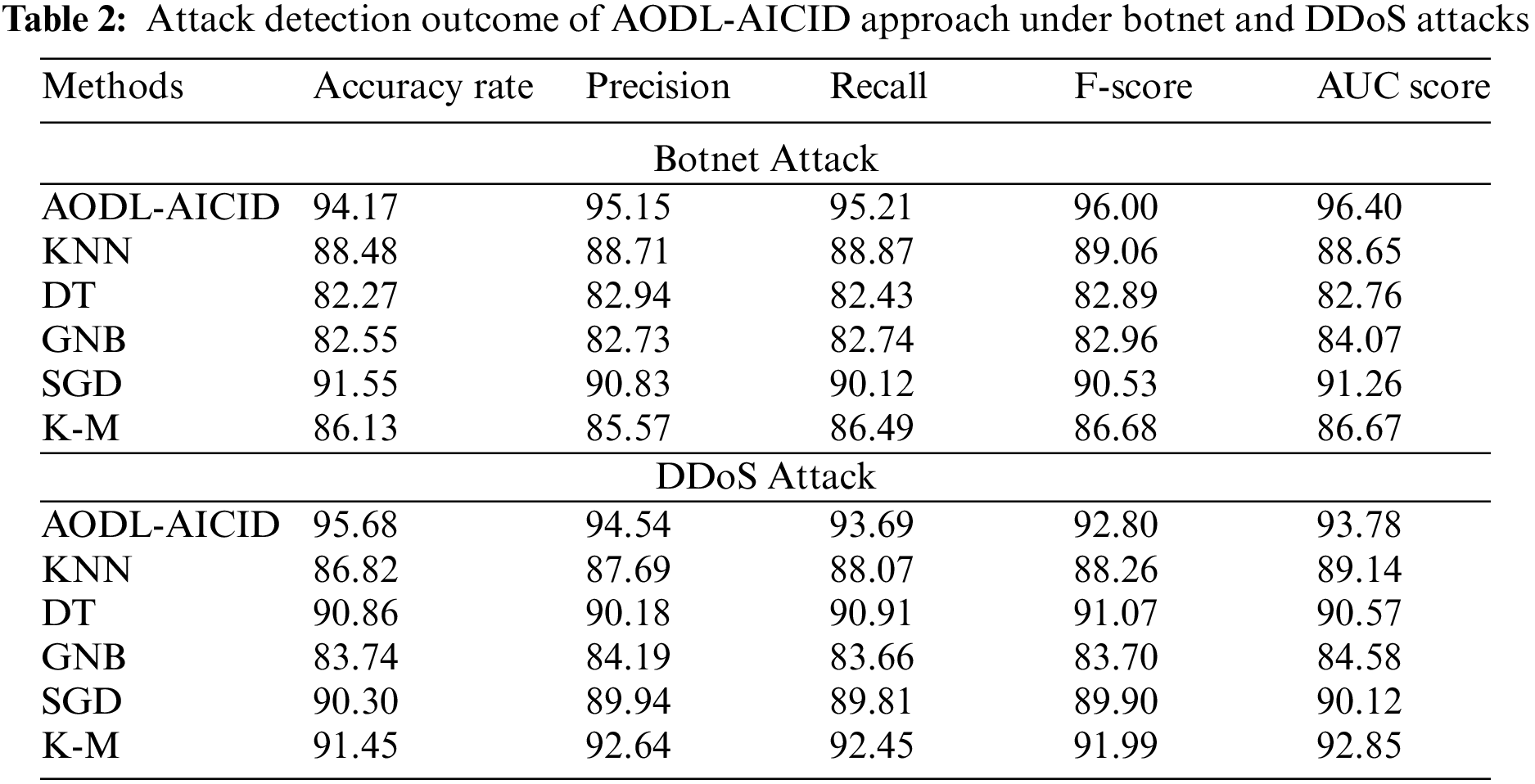
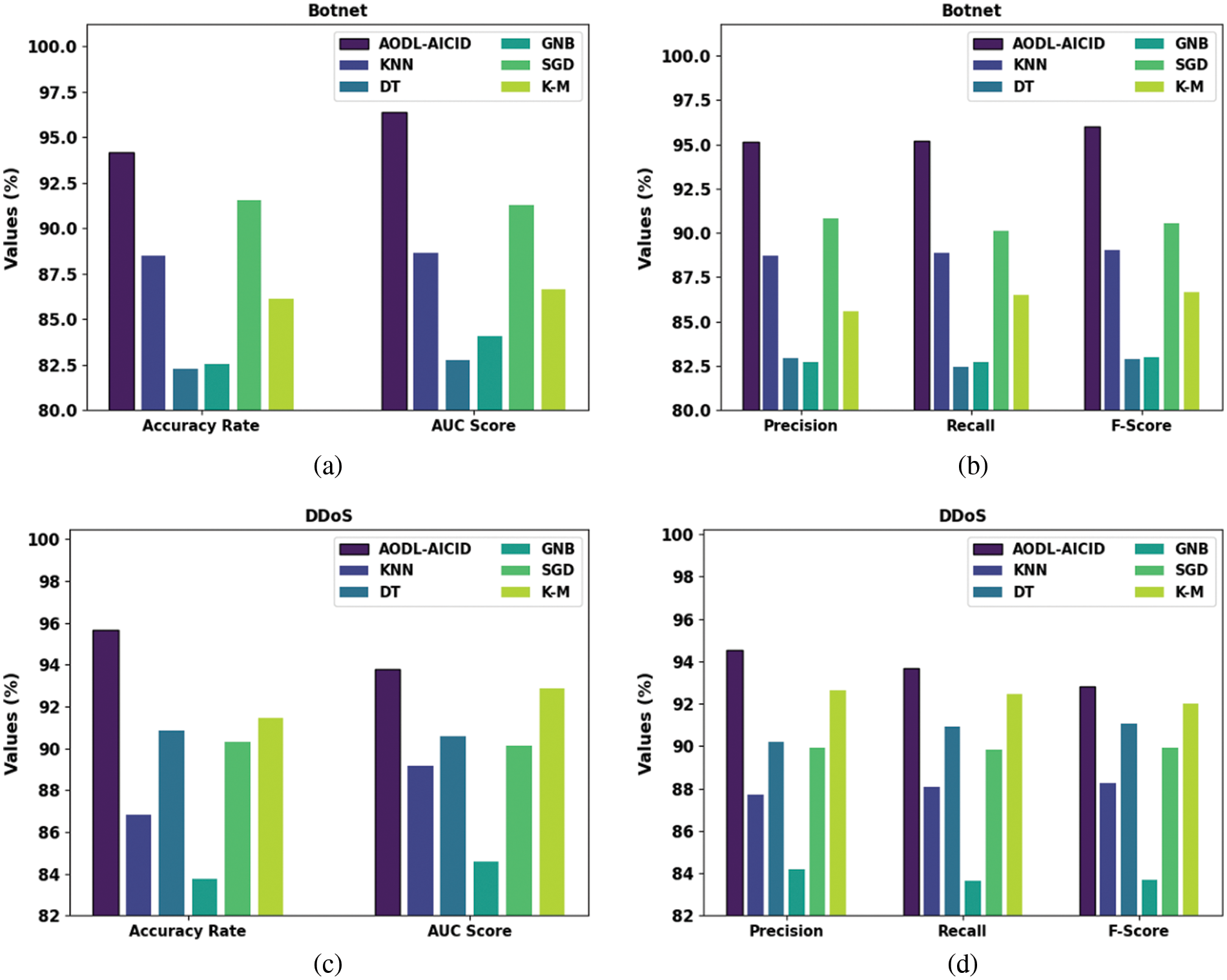
Figure 6: Attack detection of AODL-AICID approach (a,b) Botnet attacks (c,d) DDoS attack
Table 3 and Fig. 7 investigate the attack detection results of the AODL-AICID approach under web and Infiltration attacks. The results specified that the AODL-AICID method has recognized both botnet and DDoS attacks proficiently. For example, the AODL-AICID model has accomplished a higher
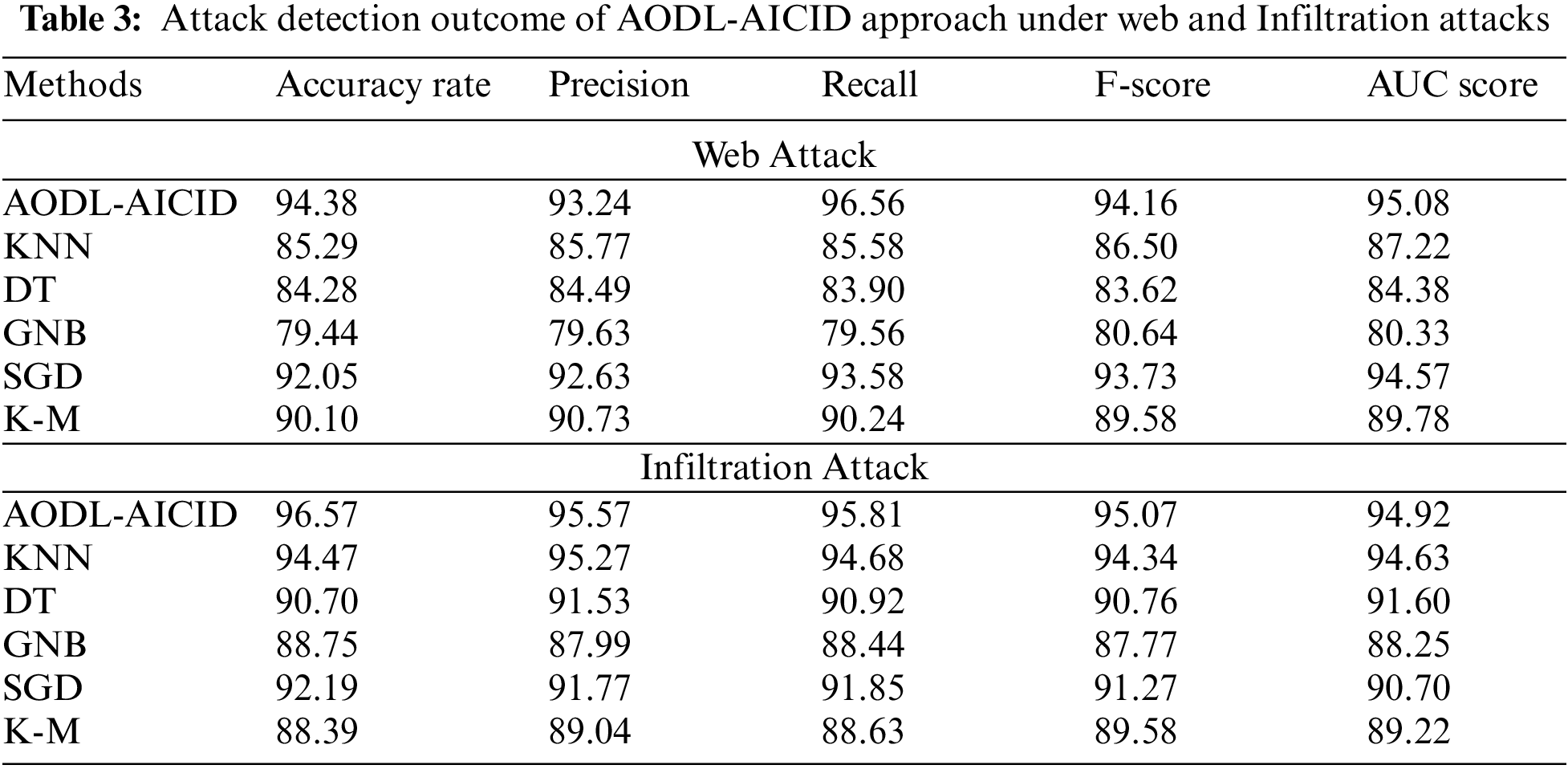
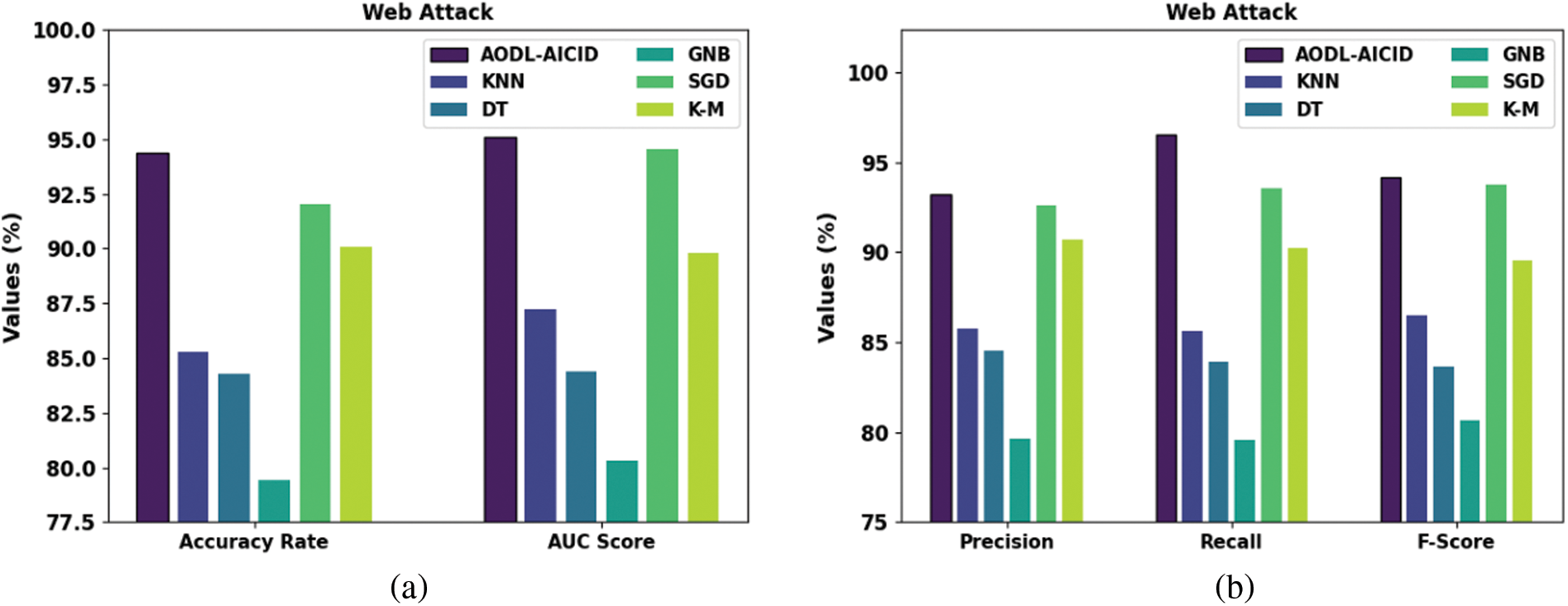
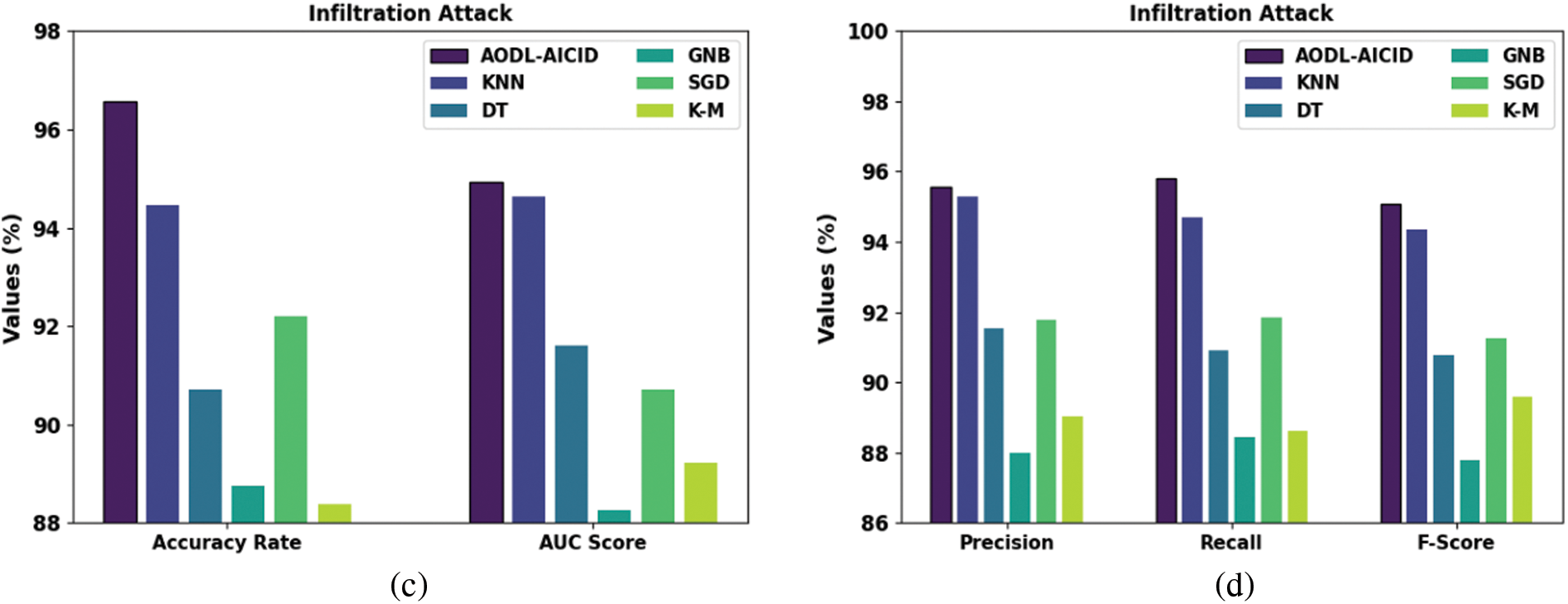
Figure 7: Attack detection of AODL-AICID approach (a,b) web attacks (c,d) infiltration attack
These results ensured the effectual performance of the AODL-AICID model on the UAV networks.
A new AODL-AICID technique has been introduced for aerial image classification and intrusion detection in UAV networks. The presented AODL-AICID technique concentrates on two major processes: image classification and intrusion detection. For aerial image classification, the AODL-AICID technique encompasses MobileNetv2 feature extraction, an AOA-based hyperparameter optimizer, and a BPNN-based classifier. In addition, the AODL-AICID technique employed the Nadam optimizer with the SBLSTM method for intrusion detection in the UAV networks. The result analysis of the AODL-AICID technique is tested under different performance measures. In future, deep learning-based ensemble fusion models can boost the performance of the AODL-AICID approach.
Funding Statement: This research work was funded by Institutional Fund Projects under Grant No. (IFPIP: 511-611-1443). Therefore, the authors gratefully acknowledge technical and financial support provided by the Ministry of Education and Deanship of Scientific Research (DSR), King Abdulaziz University (KAU), Jeddah, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. S. Ouiazzane, M. Addou and F. Barramou, “A multiagent and machine learning based denial of service intrusion detection system for drone networks,” in Geospatial Intelligence, Advances in Science, Technology & Innovation Book Series. Cham: Springer, pp. 51–65, 2022. [Google Scholar]
2. Y. Miao, Y. Tang, B. A. Alzahrani, A. Barnawi, T. Alafif et al., “Airborne LiDAR assisted obstacle recognition and intrusion detection towards unmanned aerial vehicle: Architecture, modeling and evaluation,” IEEE Transactions on Intelligent Transportation Systems, vol. 22, no. 7, pp. 4531–4540, 2020. [Google Scholar]
3. E. H. Abualsauod, “A hybrid blockchain method in internet of things for privacy and security in unmanned aerial vehicles network,” Computers and Electrical Engineering, vol. 99, pp. 107847, 2022. [Google Scholar]
4. J. Whelan, A. Almehmadi and K. El-Khatib, “Artificial intelligence for intrusion detection systems in unmanned aerial vehicles,” Computers and Electrical Engineering, vol. 99, pp. 107784, 2022. [Google Scholar]
5. M. Ragab and A. Addas, “Low complexity encoder with multilabel classification and image captioning model,” CMC-Computers Materials & Continua, vol. 72, no. 3, pp. 4323–4337, 2022. [Google Scholar]
6. Q. Abu Al-Haija and A. Al Badawi, “High-performance intrusion detection system for networked UAVs via deep learning,” Neural Computing and Applications, vol. 34, no. 3, pp. 1–16, 2022. [Google Scholar]
7. G. Choudhary, V. Sharma, I. You, K. Yim, R. Chen et al., “Intrusion detection systems for networked unmanned aerial vehicles: A survey,” in 14th Int. Wireless Communications & Mobile Computing Conf. (IWCMC), Limassol, Cyprus, pp. 560–565, 2018. [Google Scholar]
8. S. Ouiazzane, F. BarramoU and M. Addou, “Towards a multi-agent based network intrusion detection system for a fleet of drones,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 10, pp. 351–362, 2020. [Google Scholar]
9. M. Ragab and M. F. S. Sabir, “Outlier detection with optimal hybrid deep learning enabled intrusion detection system for ubiquitous and smart environment,” Sustainable Energy Technologies and Assessments, vol. 52, pp. 02311, 2022. [Google Scholar]
10. M. Ragab, E. Ashary, W. Aljedaibi, I. Alzahrani, A. Kumar et al., “A novel metaheuristics with adaptive neuro-fuzzy inference system for decision making on autonomous unmanned aerial vehicle systems,” ISA Transactions, vol. 132, pp. 16–23, 2023. [Google Scholar] [PubMed]
11. X. He, Q. Chen, L. Tang, W. Wang and T. Liu, “CGAN-based collaborative intrusion detection for uav networks: A blockchain empowered distributed federated learning approach,” IEEE Internet of Things Journal, vol. 10, no. 1, pp. 120–132, 2023. [Google Scholar]
12. K. A. Alissa, S. S. Alotaibi, F. S. Alrayes, M. Aljebreen, S. Alazwari et al., “Crystal structure optimization with deep-autoencoder-based intrusion detection for secure internet of drones environment,” Drones,vol. 6, no. 10, pp. 297, 2022. [Google Scholar]
13. X. Tan, S. Su, Z. Zuo, X. Guo and X. Sun, “Intrusion detection of UAVs based on the deep belief network optimized by PSO,” Sensors, vol. 19, no. 24, pp. 5529, 2019. [Google Scholar] [PubMed]
14. H. Sedjelmaci, A. Boudguiga, I. B. Jemaa and S. M. Senouci, “An efficient cyber defense framework for UAV-edge computing network,” Ad Hoc Networks, vol. 94, pp. 101970, 2019. [Google Scholar]
15. R. Zhang, J. P. Condomines, N. Larrieu and R. Chemali, “Design of a novel network intrusion detection system for drone communications,” in IEEE/AIAA 37th Digital Avionics Systems Conf. (DASC), London, UK, pp. 1–10, 2018. [Google Scholar]
16. J. Whelan, T. Sangarapillai, O. Minawi, A. Almehmadi and K. El-Khatib, “Novelty-based intrusion detection of sensor attacks on unmanned aerial vehicles,” in Proc. of the 16th ACM Symp. on QoS and Security for Wireless and Mobile Networks, Alicante, Spain, pp. 23–28, 2020. [Google Scholar]
17. H. Huang, L. Liang, G. Zhao, Y. Yang and K. Ou, “Railway clearance intrusion detection in aerial video based on convolutional neural network,” in Chinese Control and Decision Conf. (CCDC), Nanchang, China, pp. 1644–1648, 2019. [Google Scholar]
18. B. Lin, H. Su, D. Li, A. Feng, H. Li et al., “PlaneNet: An efficient local feature extraction network,” PeerJ Computer Science, vol. 7, pp. e783, 2021. [Google Scholar] [PubMed]
19. F. A. Hashim, K. Hussain, E. H. Houssein, M. S. Mabrouk and W. Al-Atabany, “Archimedes optimization algorithm: A new metaheuristic algorithm for solving optimization problems,” Applied Intelligence, vol. 51, no. 3, pp. 1531–1551, 2021. [Google Scholar]
20. N. T. Long and L. H. Chuong, “A back propagation neural network model with the synthetic minority over-sampling technique for construction company bankruptcy prediction,” International Journal of Sustainable Construction Engineering and Technology, vol. 13, no. 3, pp. 68–79, 2022. [Google Scholar]
21. X. Liu, S. Liu, X. Li, B. Zhang, C. Yue et al., “Intelligent tool wear monitoring based on parallel residual and stacked bidirectional long short-term memory network,” Journal of Manufacturing Systems, vol. 60, pp. 608–619, 2021. [Google Scholar]
22. S. Bera and V. K. Shrivastava, “Analysis of various optimizers on deep convolutional neural network model in the application of hyperspectral remote sensing image classification,” International Journal of Remote Sensing, vol. 41, no. 7, pp. 2664–2683, 2020. [Google Scholar]
23. http://weegee.vision.ucmerced.edu/datasets/landuse.html [Google Scholar]
24. I. Sharafaldin, A. H. Lashkari and A. A. Ghorbani, “Toward generating a new intrusion detection dataset and intrusion traffic characterization,” in Proc. of the 4th Int. Conf. on Information Systems Security and Privacy, Funchal, Madeira, Portugal, pp. 108–116, 2018. [Google Scholar]
25. M. S. Minu and R. A. Canessane, “Deep learning-based aerial image classification model using inception with residual network and multilayer perceptron,” Microprocessors and Microsystems, vol. 95, pp. 104652, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools