 Open Access
Open Access
ARTICLE
Optimal Deep Learning Based Ransomware Detection and Classification in the Internet of Things Environment
1 Department of Information Systems, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
2 Department of Computer Science, College of Science & Art at Mahayil, King Khalid University, Saudi Arabia
3 Department of Computer Science, College of Sciences and Humanities- Aflaj, Prince Sattam bin Abdulaziz University, Saudi Arabia
4 Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
* Corresponding Author: Anwer Mustafa Hilal. Email:
Computer Systems Science and Engineering 2023, 46(3), 3087-3102. https://doi.org/10.32604/csse.2023.036802
Received 12 October 2022; Accepted 06 January 2023; Issue published 03 April 2023
Abstract
With the advent of the Internet of Things (IoT), several devices like sensors nowadays can interact and easily share information. But the IoT model is prone to security concerns as several attackers try to hit the network and make it vulnerable. In such scenarios, security concern is the most prominent. Different models were intended to address these security problems; still, several emergent variants of botnet attacks like Bashlite, Mirai, and Persirai use security breaches. The malware classification and detection in the IoT model is still a problem, as the adversary reliably generates a new variant of IoT malware and actively searches for compromise on the victim devices. This article develops a Sine Cosine Algorithm with Deep Learning based Ransomware Detection and Classification (SCADL-RWDC) method in an IoT environment. In the presented SCADL-RWDC technique, the major intention exists in recognizing and classifying ransomware attacks in the IoT platform. The SCADL-RWDC technique uses the SCA feature selection (SCA-FS) model to improve the detection rate. Besides, the SCADL-RWDC technique exploits the hybrid grey wolf optimizer (HGWO) with a gated recurrent unit (GRU) model for ransomware classification. A widespread experimental analysis is performed to exhibit the enhanced ransomware detection outcomes of the SCADL-RWDC technique. The comparison study reported the enhancement of the SCADL-RWDC technique over other models.Keywords
The Internet of Things (IoT) is a copious amount of physical devices interconnected with the internet. Embedded with software and sensor nodes that can share and collect information online, IoT gadget is invaluable for improving productivity and enhancing a large number of processes all over the industry [1–3]. There is a considerable expansion in the severity and amount of cyber-based attacks. Generally, distinct variants of malware are the major reason for cyberattacks. Malware is software proposed to use network and computer systems’ vulnerabilities to gain financial benefits and execute malicious activities [4]. Trojans, viruses, backdoors, worms, ransomware, and rootkits are popular examples of malware. Ransomware attack causes a problem for the distributed IoT platform and halts smooth work among heterogeneous data centre [5]. This mechanism contains the complex structure of method and corpora. The data centre environment has a large amount of information and pays money to avoid damage to the exploitation and reputation of information [6].
Even though various methodologies are developed for detecting malware [7], it is still a prominent topic amongst research workers because of the increasing number of new malware and its difficulty [8]. The conventional method for malware detection is signature-based. This method requires saving each known and existing malware signature to identify malware samples. The general problem with this method is that they needed help identifying unknown and new malware samples [9]. As well, database updating with new signatures takes considerable time, and at that time, malware is capable of performing malicious actions [1–3, 10].
Furthermore, storing each present malware’s signature could be more efficient and costly [5–7, 11]. The heuristic machine learning (ML) method is commonly applied to overcome this limitation. First, this technique extracts feature from malware sample that describes the behaviour and content of the malware. Then, this feature is used for training a model to identify malware samples [8]. But this method requires the detection of significant features beforehand, which is sometimes impossible, costly, and time-consuming due to limited available malware samples, which is a major constraint in IIoT and IoT platforms [9,10].
This article develops a Sine Cosine Algorithm with Deep Learning based Ransomware Detection and Classification (SCADL-RWDC) technique in an IoT environment. In the presented SCADL-RWDC technique, the major intention exists in recognizing and classifying ransomware attacks in the IoT platform. The SCADL-RWDC technique uses the SCA feature selection (SCA-FS) model to improve the detection rate. Besides, the SCADL-RWDC technique exploits a hybrid grey wolf optimizer (HGWO) with a gated recurrent unit (GRU) model for the ransomware classification process. A widespread experimental analysis is performed to exhibit the enhanced ransomware detection outcomes of the SCADL-RWDC technique.
The authors in [12] employed DL approaches to extract the latent representation of higher dimensional data to identify malicious performance accurately. Especially this method present was dependent upon a hybrid feature engineering system of traditional and VAEs. This system was utilized to reduce the data’s dimensionality and extract an optimum representation of gathered model actions. Next, a novel feature vector has passed to a constructed classification dependent upon DNN and batch-normalized methods. Naeem [13] examined a further accurate and fast method to detect malware from IoT environments. The authors establish a Malware Threat Hunting System (MTHS) in the presented method. In MTHS, primary converts malware binary to colour image and conducts the ML or DL studies for effectual malware detection. The authors lastly make a baseline for comparing the efficiency of MTHS with classic recent malware detection techniques.
Naeem et al. [14] proposed a structure for detecting malware attacks on the Industrial Internet of Things (MD-IIOT). This technique was presented for a comprehensive investigation of malware, depending upon the colour image visualized and deep CNN. The outcomes of the presented system are related to former techniques for malware detection. Moti et al. [15] presented MalGan, a structure to detect and generate novel malware instances dependent upon the raw byte code at the edge layer of IoT networks. CNN is employed to extract higher-level features, and a boundary-seeking Generative Adversarial Network (GAN) system generates novel malware instances. Therefore, even with some malware instances, an essential count of earlier unseen malware instances was detectable with maximum accuracy. For capturing the short- and long-term dependency of features, the authors utilized an attention-based method, an integration of CNN and LSTM. The attention system enhances the model’s efficiency by increasing or decreasing attention for particular features. Kumar [16] introduces a new malware classifier with fine-tuning CNNs (MCFTCNN) method. This method utilizes deep transfer learning (DTL) to classify the malware image into its corresponding family. The presented method improves the ResNet50 technique by changing the final layer with a fully connected (FC) dense layer.
In [17], an automated ML-based ransomware classification model is derived. Using the malware life cycle on the Windows platform, real-time examination of ransomware samples is performed to identify various traits of harmful code patterns. The grid search hyperparameter optimizer is used to determine the optimal fit approaches, and the results are examined over the test dataset. The authors in [18] presented the major suggestion and schemes to mitigate ransomware. An automated indexing approach is developed to offer searching functions, similarity verification, classification, and clustering. The proposed model mainly aims at the original ransomware binary and the indexing engine based on the hybridized data from the static analyzer system. The proposed model tracks and classifies ransomware depending on the static features to determine the resemblance among various ransomware samples.
In this article, we have introduced automated ransomware detection using the SCADL-RWDC technique. The goal of the SCADL-RWDC technique lies in the recognition and classification of ransomware attacks in the IoT environment. It follows three processing stages: SCA-FS-based feature subset selection, GRU classification, and HGWO parameter tuning. Fig. 1 represents the block diagram of the SCADL-RWDC system.
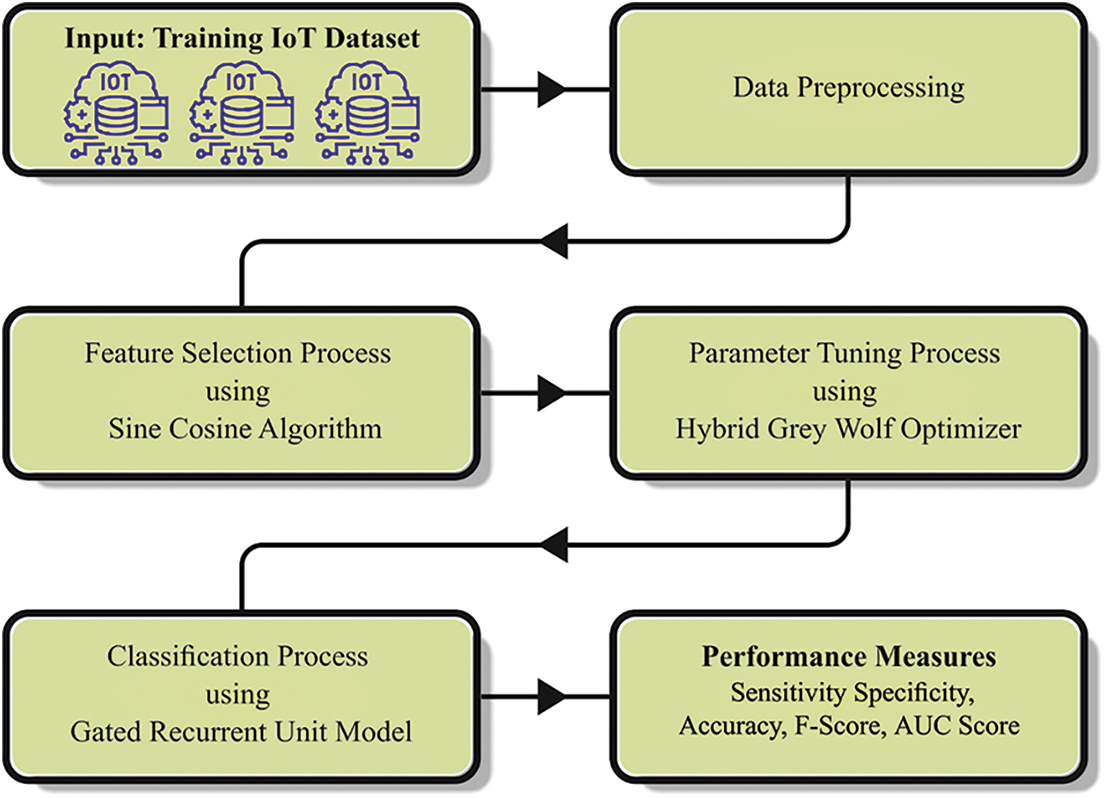
Figure 1: Block diagram of SCADL-RWDC system
In the primary stage, the min-max normalizes system was executed to transform the input database into a suitable format. Min-max normalized system is utilized for scaling the feature in zero and one with the subsequent expression.
In Eq. (1),
3.2 Algorithmic Design of SCA-FS Technique
The SCADL-RWDC technique applied the SCA-FS model to choose features optimally in this work. SCA is a metaheuristic approach developed with shallow efficiency [19] and a population-based method that begins with searching for random solutions. Thus, each random optimization highlights the exploitation and exploration of the problem. In SCA, two distinct mathematical formulas are utilized for updating the solution for the balance of exploitation and exploration:
Four variables should be presented. It reduced linearly from a to
The comprehensive equation for variable
In Eq. (3),
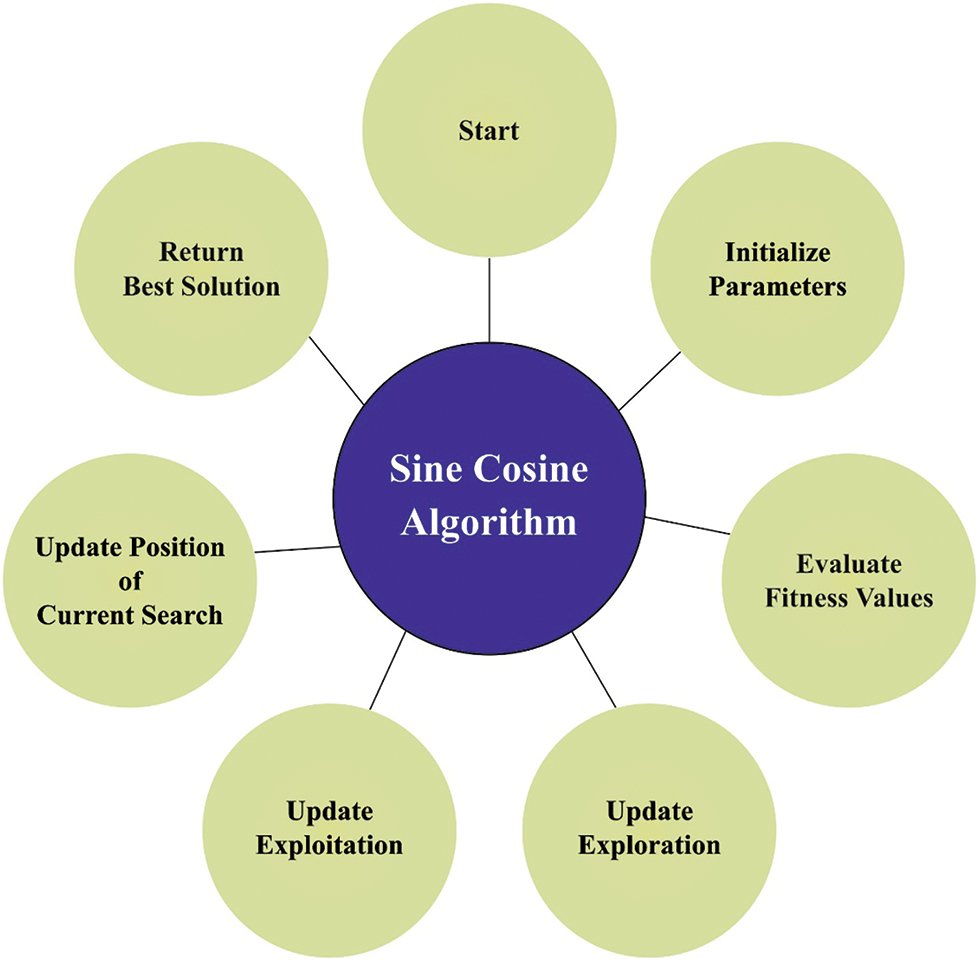
Figure 2: Flowchart of SCA
It demonstrates the present trend of the solution towards the target solution. The equation of SCA is presented to two arithmetical functions involving sine and cosine operations. The effects on those functions depend on how to attain the following solution and determine the location amongst the sensible and the existing solutions to the problem.
The effect of cosine and sine functions in a random integer on the following solution. Two trends are analyzed: the inner direction of the present and outside space.
The common step of SCA starts with the optimization procedure of a set of primary random solutions. With increasing assessments, the better solution is the target solution presently retained.
Consequently, the fitness function is utilized for evaluating individual solutions as follows:
Whereas ErrorRate denotes the classification error rate.
3.3 Ransomware Attack Detection Using GRU Model
The SCADL-RWDC technique exploited the HGWO with the GRU model for ransomware classification. GRU network is a variant of the LSTM network in RNN that mostly replaces the two gating units of LSTM (input and forgetting gates) with one gating unit (update gate) [20]. It is well-designed and employed in the area of time series prediction.
Similarly, The GRU-NN works with the LSTM, where it has two gates, such as reset and update gates. These gates receive the
Short-time series dependency is attained through the reset gate:
Estimate update gate in the following:
The candidate vector can be attained afterwards by updating the following:
Update memory to obtain hidden layer output outcomes:
In Eq. (7),
Finally, the HGWO algorithm is used for the hyperparameter tuning process. In the HGWO algorithm, for the position update, the target encircling nature of the grey wolf can be arithmetically modelled [21]. The distance between the target and grey wolf for different wolf groups is formulated as follows.
The location updating of a grey wolf for the following iteration is shown as follows:
Whereas
Whereas ‘a’ corresponds to the linear conversion from the exploration to the exploitation stage in the following,
In Eq. (12),
Location updating for the next iteration is attained by:
Eqs. (11), (12) are utilized for evaluating distinct factors in (14)–(19). Now,
The proposed model is simulated using Python 3.6.5 tool on PC i5-8600k, GeForce 1050Ti 4 GB, 16 GB RAM, 250 GB SSD, and 1 TB HDD. The parameter settings are learning rate: 0.01, dropout: 0.5, batch size: 5, epoch count: 50, and activation: ReLU. The ransomware classification results of the SCADL-RWDC model are assessed on a dataset with 840 samples, as depicted in Table 1. The dataset holds 420 goodware samples and 420 ransomware samples.

The confusion matrix gained by the SCADL-RWDC technique is portrayed in Fig. 3. On 80% of the TR database, the SCADL-RWDC model has categorized 318 samples into goodware and 336 samples into ransomware. Meanwhile, on 20% of the TS database, the SCADL-RWDC approach has classified 83 samples into goodware and 82 samples into ransomware. Finally, on 70% of the TR database, the SCADL-RWDC method has classified 293 samples into goodware and 292 samples into ransomware.
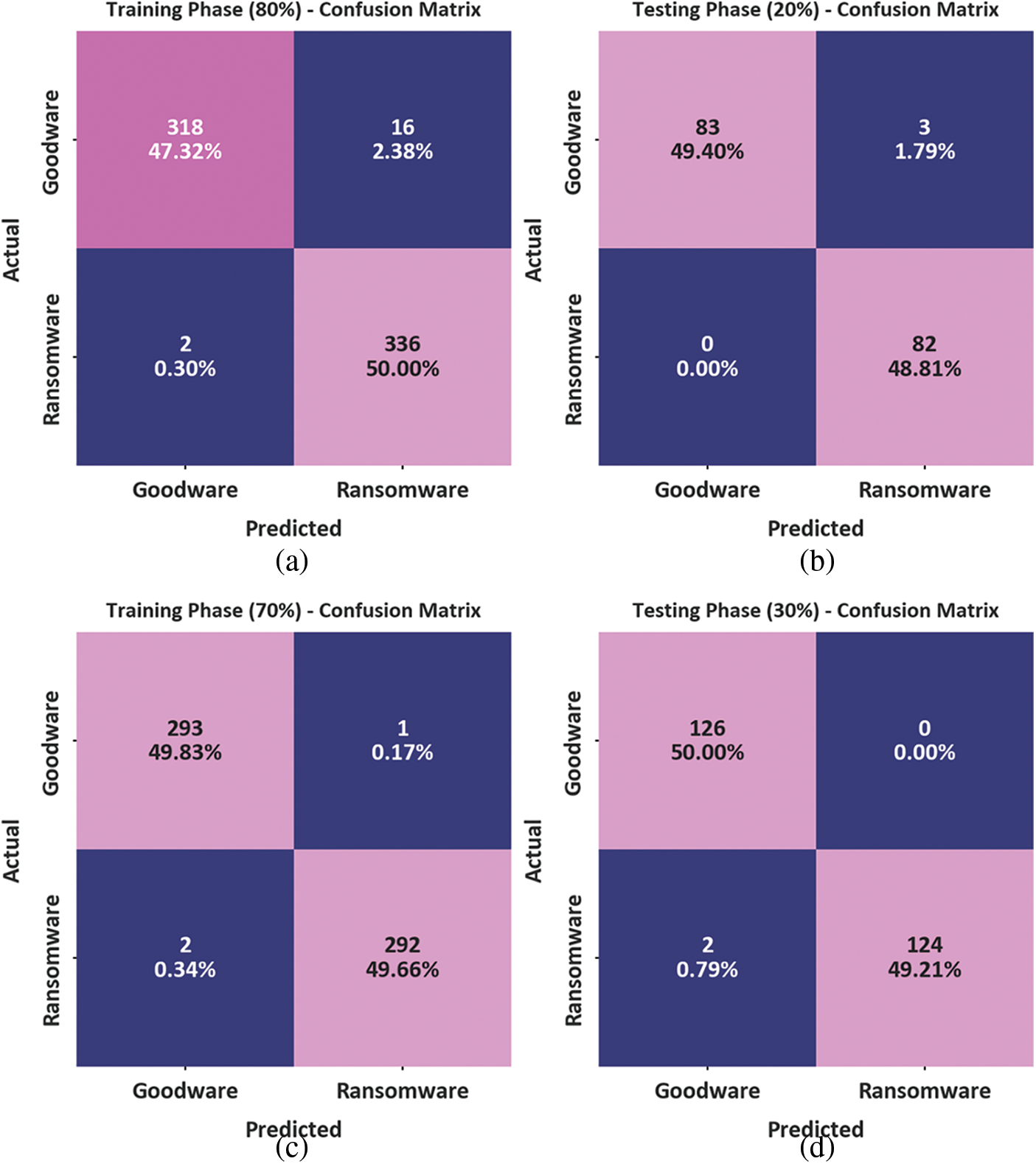
Figure 3: Confusion matrices of SCADL-RWDC system (a–b) TR and TS database of 80:20 and (c–d) TR and TS database of 70:30
Table 2 offers detailed results of the SCADL-RWDC model on 80% of TR and 20% of TS databases.

Fig. 4 reports an overall ransomware classification outcome of the SCADL-RWDC model on 80% of the TR database. In the goodware class, the SCADL-RWDC model has obtained
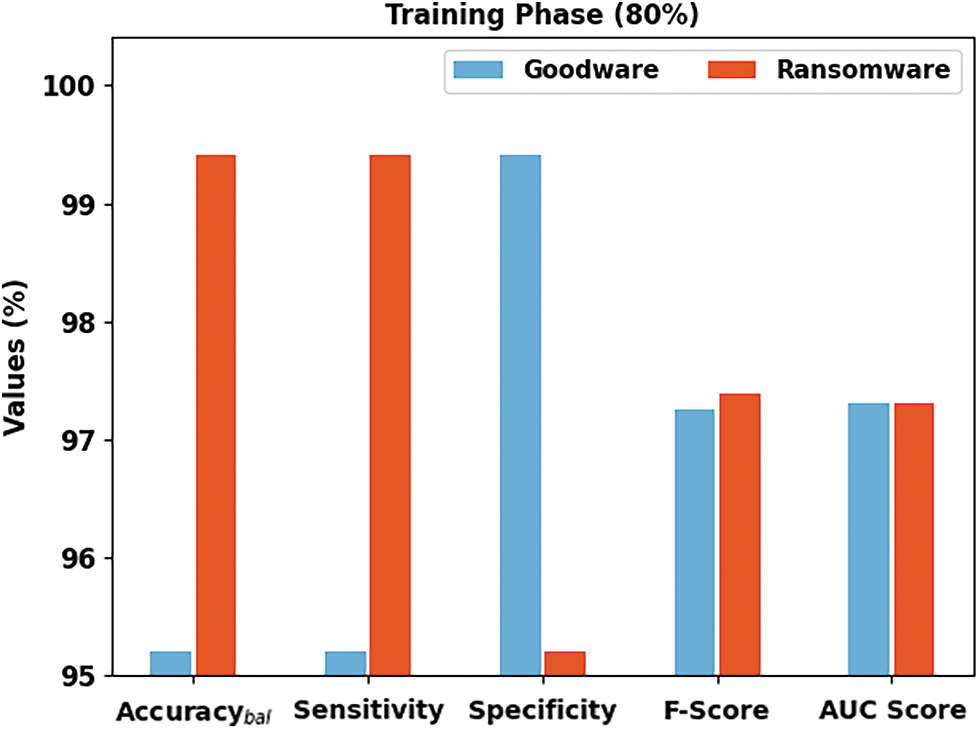
Figure 4: Result analysis of the SCADL-RWDC system in 80% of the TR database
Fig. 5 reports the overall ransomware classification outcomes of the SCADL-RWDC model on 20% of the TS database. In goodware class, the SCADL-RWDC algorithm has gained
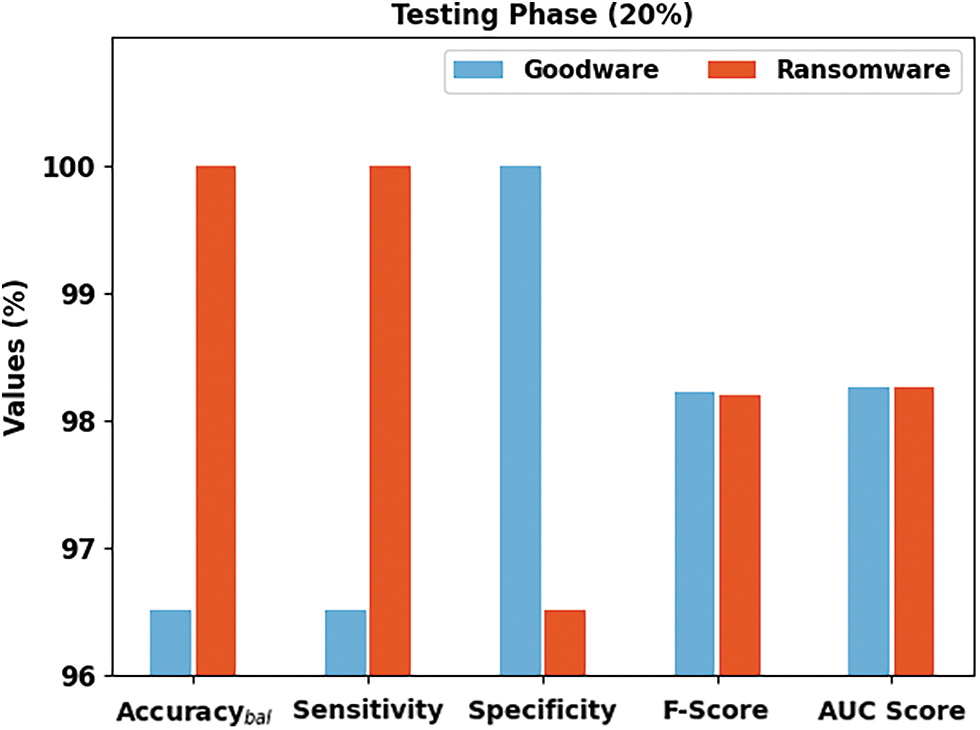
Figure 5: Result analysis of SCADL-RWDC system in 20% of the TS database
Table 3 provides a detailed outcome of the SCADL-RWDC approach on 70% of TR databases and 30% of TS databases.

Fig. 6 demonstrates an overall ransomware classification result of the SCADL-RWDC algorithm on 70% of TR data. In goodware class, the SCADL-RWDC approach has acquired
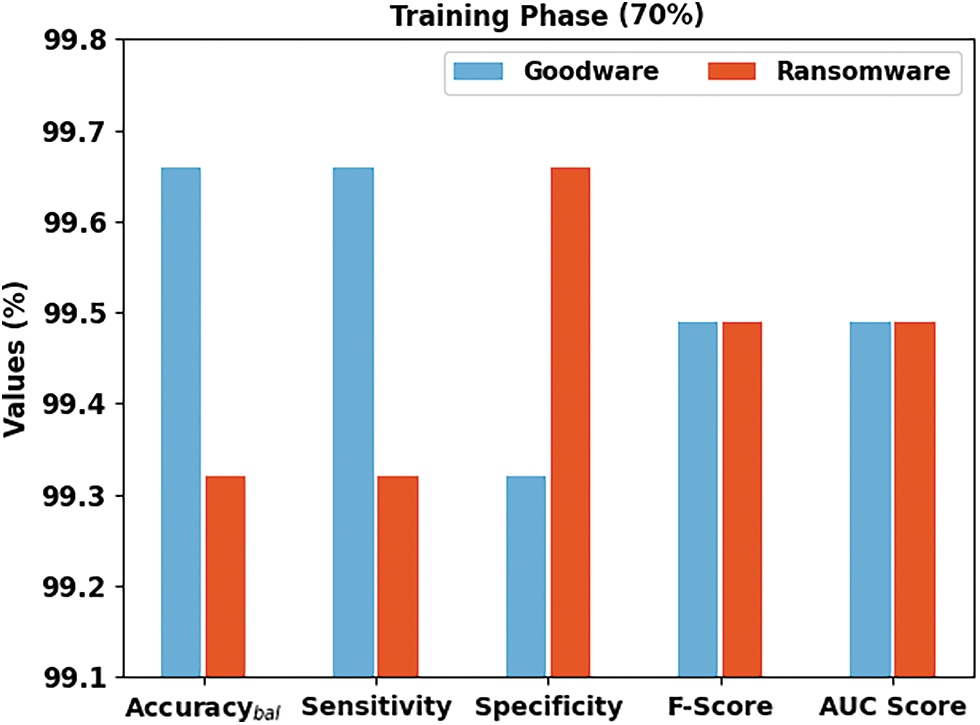
Figure 6: Result analysis of the SCADL-RWDC system in 70% of the TR database
Fig. 7 depicts an overall ransomware classification result of the SCADL-RWDC methodology on 30% of TS data. In goodware class, the SCADL-RWDC system has achieved
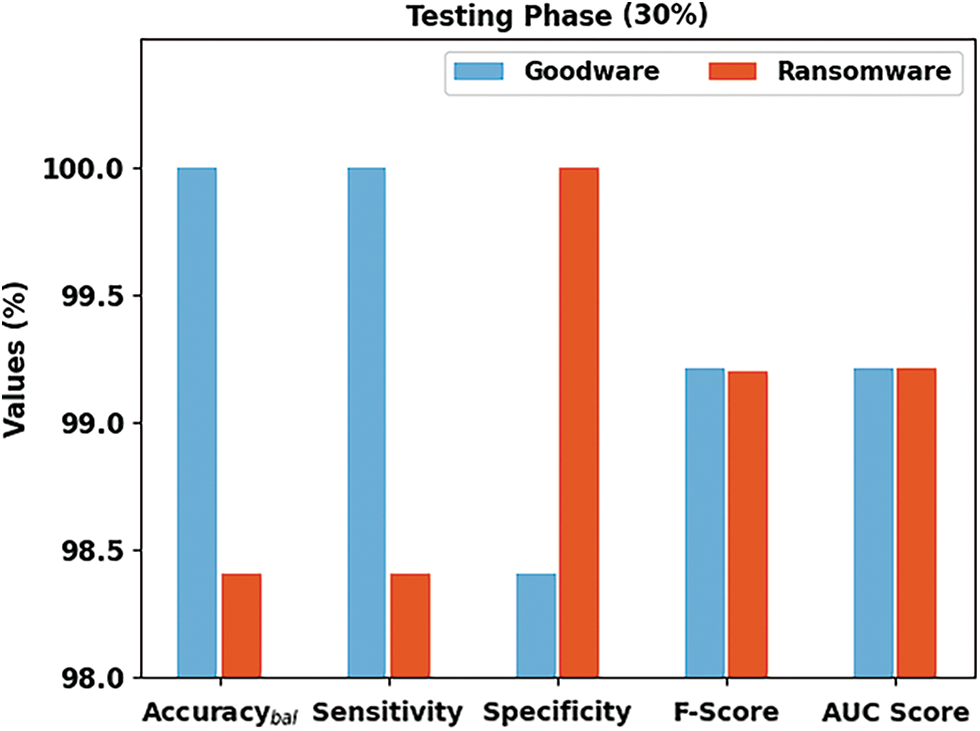
Figure 7: Result analysis of SCADL-RWDC system in 30% of the TS database
The training accuracy (
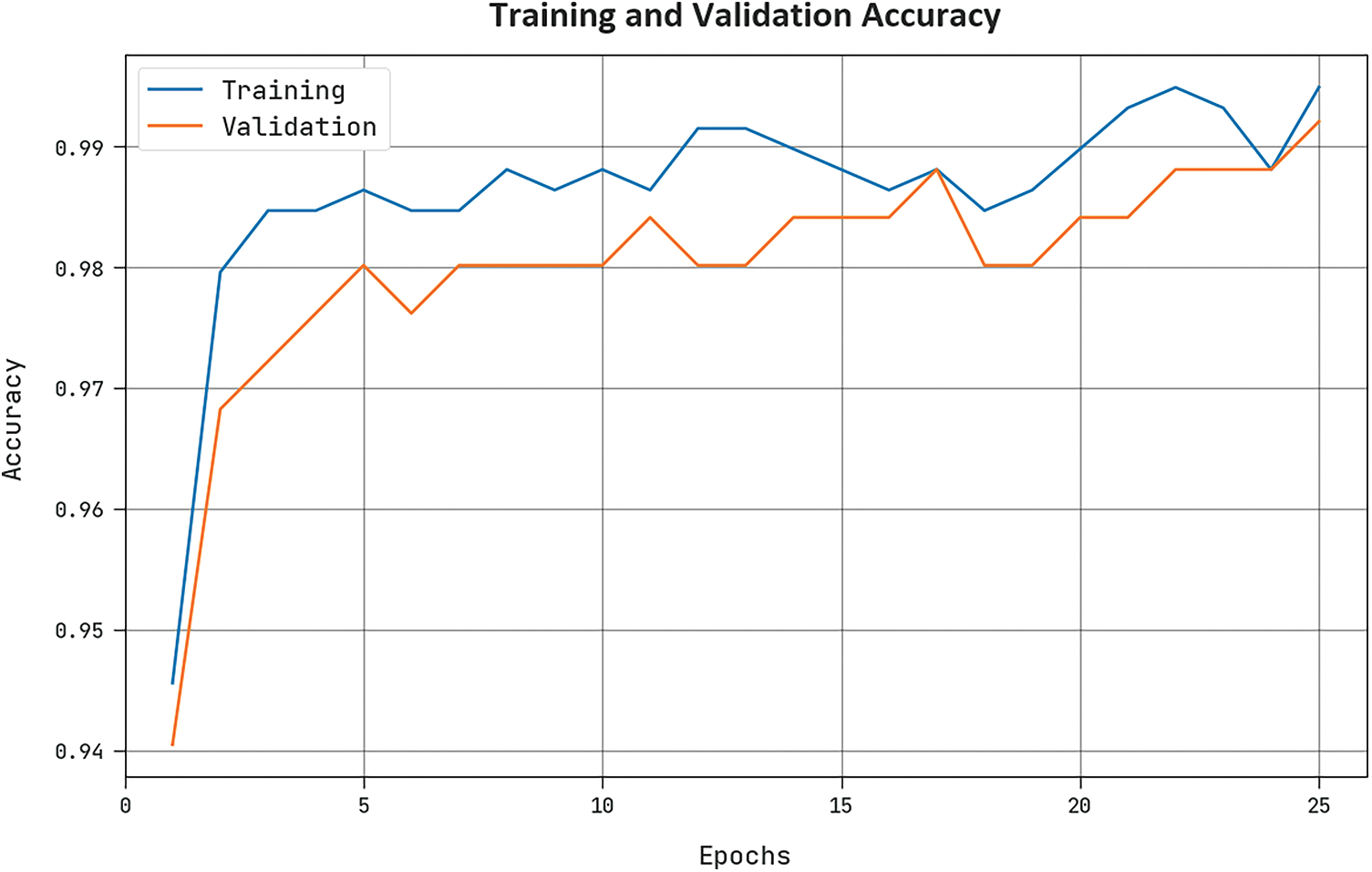
Figure 8:
The training loss (
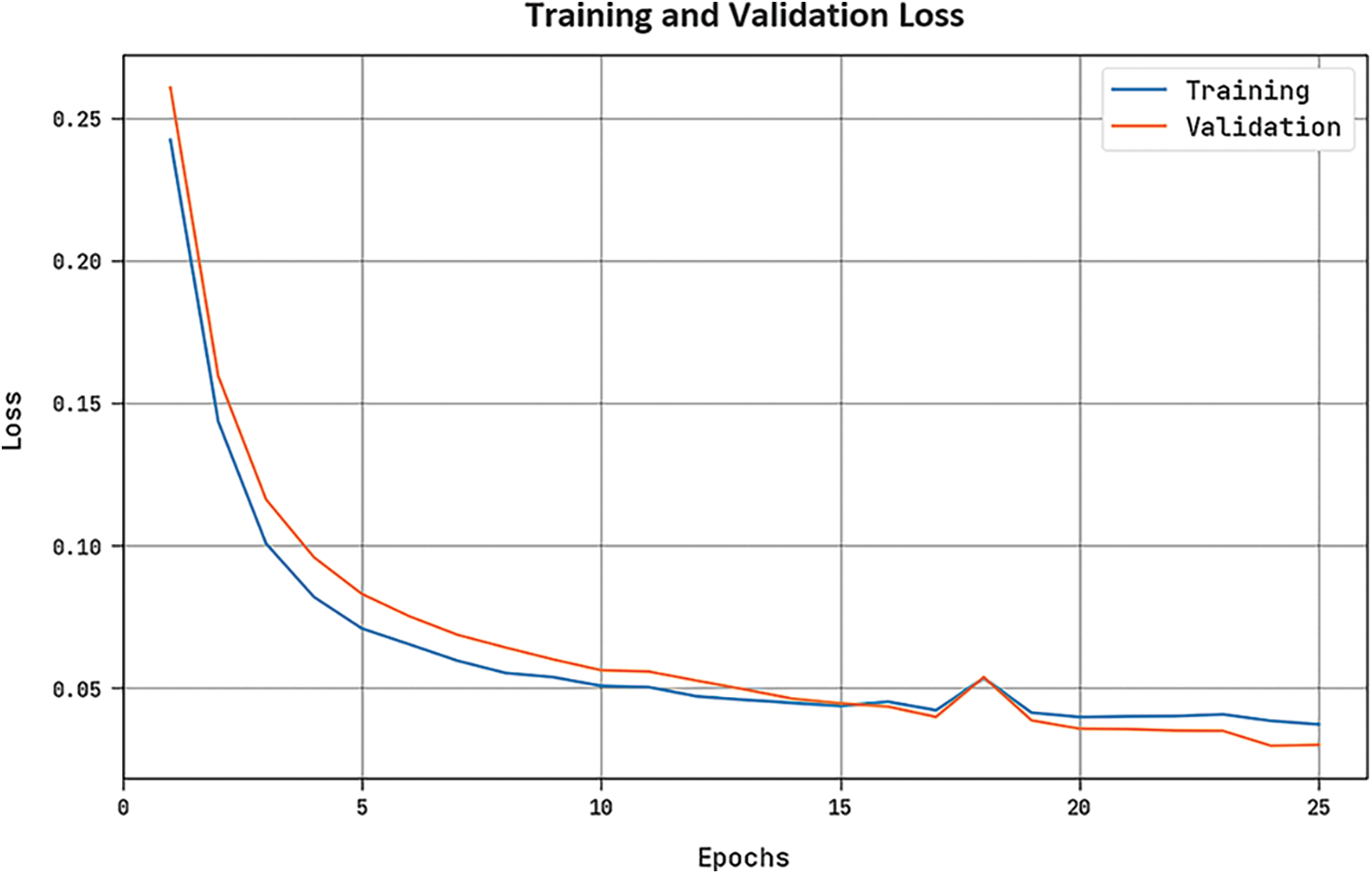
Figure 9:
A comparative examination of the SCADL-RWDC with other ML approaches occurs in Table 4 [22].

Fig. 10 illustrates a comparison study of the SCADL-RWDC model with current ML approaches in terms of
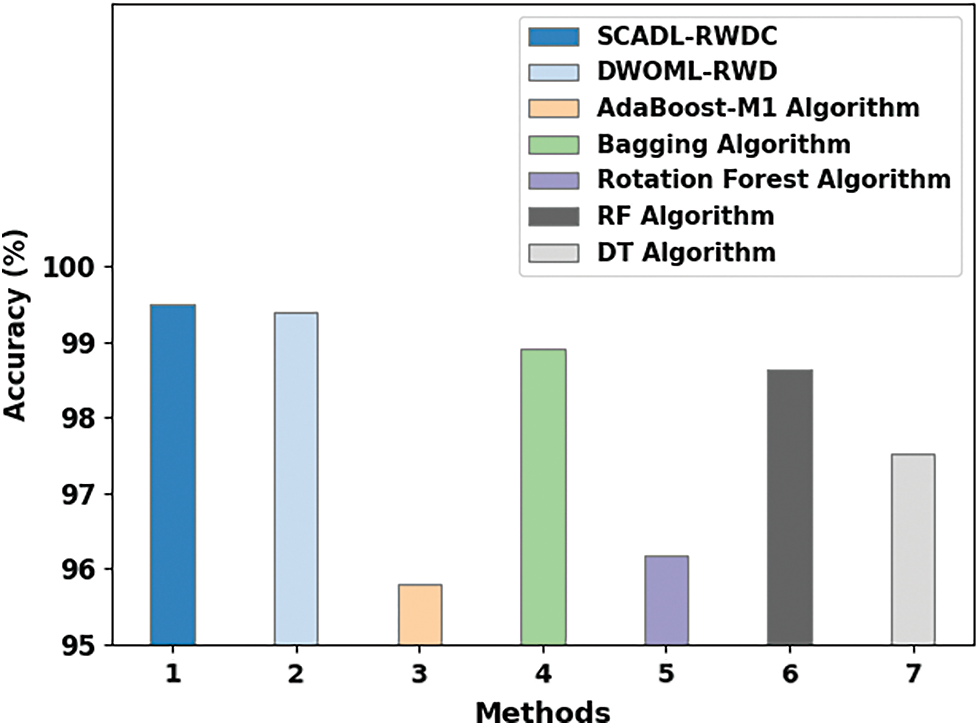
Figure 10:
Fig. 11 illustrates a comparison study of the SCADL-RWDC with current ML approaches in
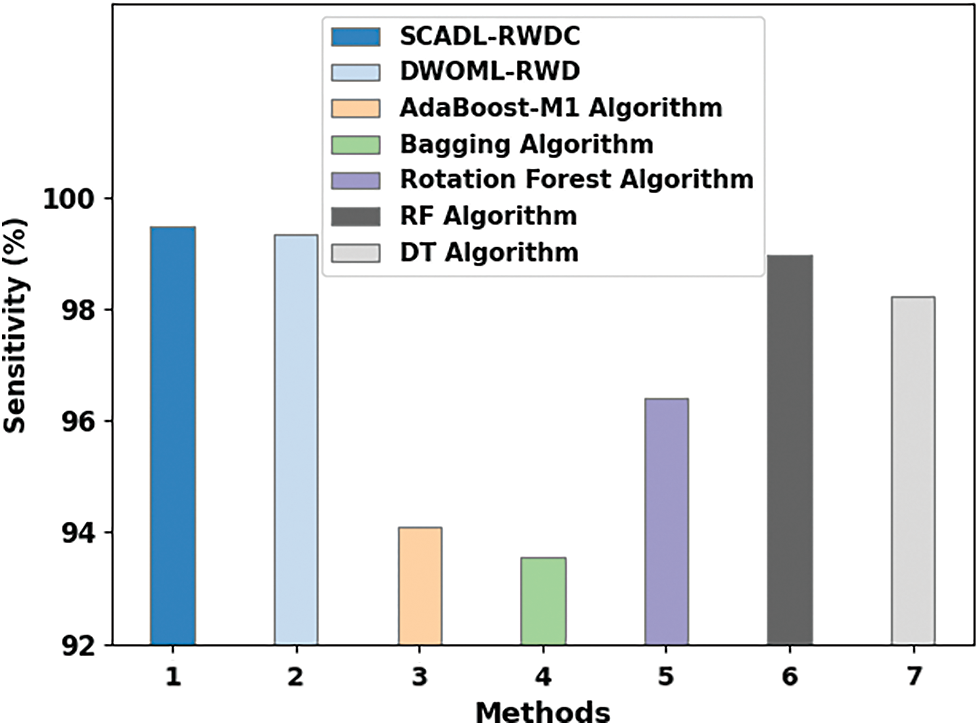
Figure 11:
Fig. 12 shows a comparison study of the SCADL-RWDC with current ML methods in
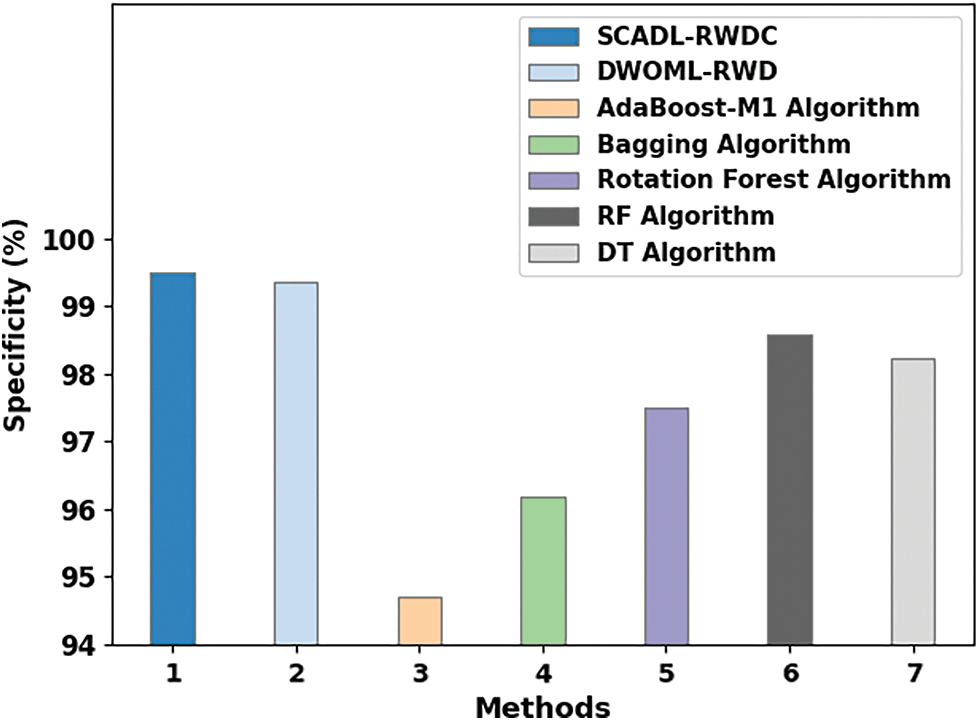
Figure 12:
Fig. 13 depicts a comparison study of the SCADL-RWDC with current ML techniques in terms of
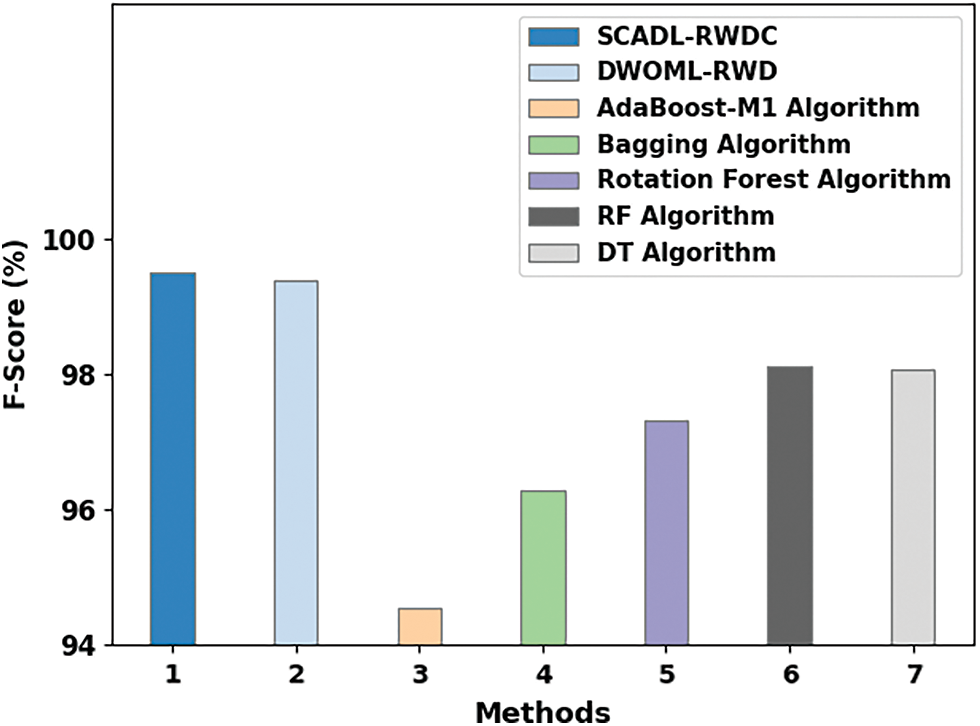
Figure 13:
In this article, we have introduced automated ransomware detection using the SCADL-RWDC technique. The goal of the SCADL-RWDC technique lies in the recognition and classification of ransomware attacks in the IoT environment. The SCADL-RWDC technique was applied to the SCA-FS model to improve the detection rate. Besides, the SCADL-RWDC technique exploited the HGWO with the GRU model for the ransomware classification process. A widespread experimental analysis is performed to exhibit the enhanced ransomware detection outcomes of the SCADL-RWDC technique. The comparison study reported the enhancement of the SCADL-RWDC technique over other models with maximum accuracy of 99.49%. Thus, the presented SCADL-RWDC technique can be employed for the automated recognition of security attacks in the IoT platform. In the future, the performance of the SCADL-RWDC technique can be improvised using hybrid deep learning (DL) models.
Funding Statement: This work was funded by the Deanship of Scientific Research at Princess Nourah bint Abdulrahman University, through the Research Groups Program Grant No. (RGP-1443-0051).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. I. Bello, H. Chiroma, U. A. Abdullahi, A. Y. U. Gital, F. Jauro et al., “Detecting ransomware attacks using intelligent algorithms: Recent development next direction from deep learning and big data perspectives,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, pp. 8699–8717, 2021. [Google Scholar]
2. U. Urooj, B. A. S. Al-rimy, A. Zainal, F. A. Ghaleb, M. A. Rassam et al., “Ransomware detection using the dynamic analysis and machine learning: A survey and research directions,” Applied Sciences, vol. 12, no. 1, pp. 172, 2021. [Google Scholar]
3. M. Humayun, N. Z. Jhanjhi, A. Alsayat and V. Ponnusamy, “Internet of things and ransomware: Evolution, mitigation and prevention,” Egyptian Informatics Journal, vol. 22, no. 1, pp. 105–117, 2021. [Google Scholar]
4. D. Sanvito, G. Siracusano, R. Gonzalez, and R. Bifulco, “Poster: MUSTARD–Adaptive behavioral analysis for ransomware detection,” in Proc. of the 2022 ACM SIGSAC Conf. on Computer and Communications Security, Los Angeles CA USA, Nov, pp. 3455–3457, 2022. [Google Scholar]
5. M. Hirano, R. Hodota and Kobayashi, “RanSAP: An open dataset of ransomware storage access patterns for training machine learning models,” Forensic Science International: Digital Investigation, vol. 40, pp. 301314, 2022. [Google Scholar]
6. S. Aurangzeb, H. Anwar, M. A. Naeem and M. Aleem, “BigRC-EML: Big-data based ransomware classification using ensemble machine learning,” Cluster Computing, vol. 25, pp. 3405–3422, 2022. [Google Scholar]
7. Y. A. Ahmed, S. Huda, B. A. S. Al-rimy, N. Alharbi, F. Saeed et al., “A weighted minimum redundancy maximum relevance technique for ransomware early detection in industrial iot,” Sustainability, vol. 14, no. 3, pp. 1231, 2022. [Google Scholar]
8. B. M. Khammas, “Ransomware detection using random forest technique,” ICT Express, vol. 6, no. 4, pp. 325–331, 2020. [Google Scholar]
9. J. Du, S. H. Raza, M. Ahmad, I. Alam, S. H. Dar et al., “Digital forensics as advanced ransomware pre-attack detection algorithm for endpoint data protection,” Security and Communication Networks, vol. 2022, pp. 1–16, 2022. [Google Scholar]
10. S. Usharani, P. M. Bala and M. M. J. Mary, “Dynamic analysis on crypto-ransomware by using machine learning: Gandcrab ransomware,” In Journal of Physics: Conference Series, vol. 1717, no. 1, pp. 012024, 2021. [Google Scholar]
11. D. W. Fernando, N. Komninos and T. Chen, “A study on the evolution of ransomware detection using machine learning deep learning techniques,” IoT, vol. 1, no. 2, pp. 551–604, 2020. [Google Scholar]
12. Al-Hawawreh and E. Sitnikova, “Leveraging deep learning models for ransomware detection in the industrial internet of things environment,” in Military Communications and Information Systems Conf. (MilCIS), Canberra, ACT, Australia, pp. 1–6, 2019. [Google Scholar]
13. H. Naeem, “Detection of malicious activities in internet of things environment based on binary visualization and machine intelligence,” Wireless Personal Communications, vol. 108, no. 4, pp. 2609–2629, 2019. [Google Scholar]
14. H. Naeem, F. Ullah, M. R. Naeem, S. Khalid, D. Vasan et al., “Malware detection in industrial internet of things based on hybrid image visualization and deep learning model,” Ad Hoc Networks, vol. 105, pp. 102154, 2020. [Google Scholar]
15. Z. Moti, S. Hashemi, H. Karimipour, A. Dehghantanha, A. N. Jahromi et al., “Generative adversarial network to detect unseen internet of things malware,” Ad Hoc Networks, vol. 122, pp. 102591, 2021. [Google Scholar]
16. S. Kumar, “MCFT-CNN: Malware classification with fine-tune convolution neural networks using traditional transfer learning in internet of things,” Future Generation Computer Systems, vol. 125, pp. 334–351, 2021. [Google Scholar]
17. S. Gokul Srinath, “Ransomware detection using machine learning and AI based re-enforcement learning method,” Journal of Optoelectronics Laser, vol. 41, no. 11, pp. 128–133, 2022. [Google Scholar]
18. B. Yamany, M. S. Elsayed, A. D. Jurcut, N. Abdelbaki, and M. A. Azer, “A new scheme for ransomware classification and clustering using static features,” Electronics, vol. 11, no. 20, pp. 3307, 2022. [Google Scholar]
19. W. Zhou, P. Wang, A. A. Heidari, X. Zhao and H. Chen, “Spiral Gaussian mutation sine cosine algorithm: Framework and comprehensive performance optimization,” Expert Systems with Applications, vol. 209, pp. 118372, 2022. [Google Scholar]
20. W. Lv, Y. Lv, J. Guo and J. Ma, “A lane-changing decision-making model of bus entering considering bus priority based on gru neural network,” Computational Intelligence and Neuroscience, vol. 2022, pp. 1–10, 2022. [Google Scholar]
21. R. Devarapalli, B. V. Rao and A. Al-Durra, “Optimal parameter assessment of Solar Photovoltaic module equivalent circuit using a novel enhanced hybrid GWO-SCA algorithm,” Energy Reports, vol. 8, pp. 12282–12301, 2022. [Google Scholar]
22. K. A. Alissa, D. H. Elkamchouchi, K. Tarmissi, A. Yafoz, R. Alsina et al., “Dwarf mongoose optimization with machine-learning-driven ransomware detection in internet of things environment,” Applied Sciences, vol. 12, no. 19, pp. 9513, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools