 Open Access
Open Access
ARTICLE
Artificial Algae Optimization with Deep Belief Network Enabled Ransomware Detection in IoT Environment
1 Department of Computer Science, College of Sciences and Humanities-Aflaj, Prince Sattam bin Abdulaziz University, Riyadh, Saudi Arabia
2 Department of Electrical Engineering, College of Engineering, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
3 Department of Computer Sciences, College of Computer and Information Sciences, Princess Nourah bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
4 Department of Computer Science, College of Science and Art at Muhaeyl, King Khalid University, Abha, Saudi Arabia
5 Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
* Corresponding Author: Mesfer Al Duhayyim. Email:
Computer Systems Science and Engineering 2023, 46(2), 1293-1310. https://doi.org/10.32604/csse.2023.035589
Received 26 August 2022; Accepted 04 November 2022; Issue published 09 February 2023
Abstract
The Internet of Things (IoT) has gained more popularity in research because of its large-scale challenges and implementation. But security was the main concern when witnessing the fast development in its applications and size. It was a dreary task to independently set security systems in every IoT gadget and upgrade them according to the newer threats. Additionally, machine learning (ML) techniques optimally use a colossal volume of data generated by IoT devices. Deep Learning (DL) related systems were modelled for attack detection in IoT. But the current security systems address restricted attacks and can be utilized outdated datasets for evaluations. This study develops an Artificial Algae Optimization Algorithm with Optimal Deep Belief Network (AAA-ODBN) Enabled Ransomware Detection in an IoT environment. The presented AAA-ODBN technique mainly intends to recognize and categorize ransomware in the IoT environment. The presented AAA-ODBN technique follows a three-stage process: feature selection, classification, and parameter tuning. In the first stage, the AAA-ODBN technique uses AAA based feature selection (AAA-FS) technique to elect feature subsets. Secondly, the AAA-ODBN technique employs the DBN model for ransomware detection. At last, the dragonfly algorithm (DFA) is utilized for the hyperparameter tuning of the DBN technique. A sequence of simulations is implemented to demonstrate the improved performance of the AAA-ODBN algorithm. The experimental values indicate the significant outcome of the AAA-ODBN model over other models.Keywords
The Internet of Things (IoT) is a gathering of small devices or gadgets equipped with several sensors to assist an individual in executing several daily routines [1]. IoT gadgets are entrenched gadgets linked to home appliances, vehicles, and many more that allow such objects to exchange and connect data. Millions of IoT gadgets were in use, continuing to multiply [2]. This might allure a challenger to mount a malevolent assault by pointing to IoT gadgets. An adversary could alter the default identifications of these gadgets and, after utilizing such gadgets, could raise assaults on other mechanisms [3]. A honeypot was a deception program devised to detect an attacker’s behaviour or activity to compromise the production mechanism. A honeypot could help as a surveillance tool and even seizure attack signs [4]. The behavioural analysis of seized signs offers valuable insights into effective system loopholes. Though honeypots do not secure IoT systems straightly, it is employed for strengthening IDS (Intrusion Detection System) and firewall located at the network periphery [5].
Several wide security systems were addressing IoT safety, chiefly by conventional cryptographic concepts [6]. But, the prevailing cryptographic solutions on separate IoT gadgets were inadequate for satisfying the complete spectrum of IoT security due to the dynamic nature of IoT networks and assaults [7]. There are numerous features of gadgets in an IoT system like device-to-device proximity transmission, Low-power and low-cost communications, huge deployment, Self-organization Inter-connectivity, self-healing features, Heterogeneity, Low Latency Communication, and Requirement of Ultra-Reliable, and Dynamic variations in the network that forms the security provision very difficult chore in IoT [8]. It raised the landscape of threats for the invaders. The investigation community in IoT was inspecting the scope of the immense volume of realistic data produced by IoT gadgets [9]. Then, they modelled several Deep Learning (DL) and Machine Learning (ML) systems for IoT security by binding information from the data. Besides, DL-related security systems could learn heterogeneous characteristics in formless data by themselves, and therefore these were heterogeneity tolerant [10]. It is utilized for detecting the new mutated assaults from their previous forms; thus, security systems do not require a patch on IoT gadgets.
The authors in [11] construct a two-phase mixed RF model, ransomware detection technique, and Markov model. Firstly the author focuses on the Windows API call series pattern and constructs a Markov model for capturing the features of ransomware. Then, the author constructs an RF-ML model for the residual data for controlling false negative (FNR) and false positive (FPR) error rates. Baek et al. [12] developed a two-phase hybrid malware recognition (2-MaD) technique for securing IoT devices from obscured malware in smart city settings. The 2-MaD includes two phases of IoT malware detection. Firstly, the opcode is extracted afterwards, acting out static analysis, and the learned data used through the Bi-LSTM model, benign files are discovered. Next, dynamic analysis can be done on files categorized as benign in nested virtual environments. Afterwards, extracting data on behaviour and process memory from the behaviour log, malware is identified through a trained EfficientNet-B3 mechanism depending on the system changes.
Basnet et al. [13] developed the novel DL-based ransomware detection architecture in the Supervisory control and data acquisition (SCADA) controlled electric vehicle charging station (EVCS) with the performance assessment of 3 DL systems, namely DNN, 1D-CNN, and LSTM-RNN. Nisa et al. [14] developed a feature fusion system for integrating the feature extracting in pre-trained Inception-v3 and AlexNet DNN with features accomplished through segmentation-based fractal texture analysis (SFTA) of image expressive the malware code. In the study, the author uses a distinct pre-trained model (Inception-V3 and AlexNet) for extracting features. The objective is to enhance the accuracy of the malware classification since these two models have qualities and characteristics for extracting various features.
The authors in [15] designed the DL method utilized in malware recognition for detecting ransomware in an emulation sequence. The author presents a specified RNN model to capture local event patterns from the ransomware series utilizing the conception of the attention mechanism. Azmoodeh et al. [16] established a DL-based algorithm for detecting Internet of Battlefield Things (IoBT) malware through the device’s Operational Code (OpCode) sequences. The author transmutes OpCodes as vector space and employs a deep Eigenspace learning model for classifying benign and malicious applications. Also, the author demonstrates the sustainability of the presented model in detecting malware and its robustness against junk code insertion attacks.
This study develops an Artificial Algae Optimization Algorithm with Optimal Deep Belief Network (AAA-ODBN) Enabled Ransomware Detection in an IoT environment. The presented AAA-ODBN technique mainly intends to recognize and categorize ransomware in the IoT environment. The presented AAA-ODBN technique follows a three-stage process: feature selection, classification, and parameter tuning. In the first stage, the AAA-ODBN technique uses AAA based feature selection (AAA-FS) technique to elect feature subsets. Secondly, the AAA-ODBN technique employs the DBN model for ransomware detection. At last, the dragonfly algorithm (DFA) is utilized for the hyperparameter tuning of the DBN approach. A sequence of simulations is executed to demonstrate the improved performance of the AAA-ODBN approach. In short, the paper’s contribution is summarized as follows.
• Develop a new AAA-ODBN model for Ransomware Detection in an IoT environment.
• Employ the AAA-FS technique to select the optimal set of features.
• Employ DFA with the DBN model for the classification process.
The rest of the paper is organized as follows. Section 2 offers the proposed model, and Section 3 provides the performance validation. Lastly, Section 4 concludes the study.
This study developed a novel AAA-ODBN model for ransomware detection in the IoT environment. The presented AAA-ODBN technique mainly intends to recognize and categorize ransomware in the IoT environment. Fig. 1 demonstrates the overall process of the AAA-ODBN approach. As shown in the figure, the presented AAA-ODBN technique follows a three-stage process: feature selection, classification, and parameter tuning. Initially, input data is preprocessed, and then an optimal set of features is chosen by AAA. Moreover, the DFA-DBN model is applied to the detection process.

Figure 1: Overall process of AAA-ODBN approach
2.1 Feature Selection Using AAA-FS Model
In the first stage, the AAA-ODBN exploited the AAA-FS technique to elect feature subsets. AAA mimics real algae to survive by determining and moving towards a suitable platform and recreating the upcoming generation [17]. In these subsections, they would concisely examine AAA as follows:
Set
The AAA contains evolutionary, adaptation, and helical movements. The AC tries to move toward that optimum place by developing, adapting, and moving. Note that a critical concept in AAA is the size of AC of
From the expression,
Algae make natural movement towards the water region with adequate light and other nutrients. In AAA, all the ACs move towards an optimum AC with the maximum size or optimum main function. However, this motion is based on selecting 3 dissimilar algal cells and modifying their positions, expressed as follows.
Now,
Now,
Generally, AC with good nutrient sources develops quickly, and unusual nutrient sources might weaken to pass away. Similarly, in AAA, AC
Now, the smallest and biggest signify AC,
AC suffered from starvation in unsatisfactory light and nutrients during this developing procedure. It is the process whereby the starved AC tries to move toward the biggest colony and adapt to the situation. Once the main function accomplishes the best value, the corresponding AC residues the starvation level not changed. Otherwise, the starvation value increases by 1. The later motion of AC terminates, the AC has maximal starvation value (Eq. (13)) adapted to the biggest AC with probability
Now,
During the presented method, the fitness function (FF) utilized for balancing betwixt the classifier accuracy (maximal) and the count of particular features from all the solutions (minimal) attained with the particular feature, Eq. (10) symbolizes the FF for calculating the solution.
At this time,
2.2 Ransomware Detection Using DBN
The AAA-ODBN technique employs the DBN model for ransomware detection at this stage. DBN is the base model because it shows improved efficiency in lower speed regulation conditions in pretraining [18].
(1) RBM: DBN is a multi-layer NN comprising a sequence of stacked RBMs. The architecture of RMB is a bipartite graph, viz., nodes in the layer aren’t interconnected, whereby the initial layer is the input node
Every node could take distinct states. Also, the state of these models is defined once the state of every node is defined and represents the degree to which the method takes the state; furthermore, the model was estimated using the energy function. Fig. 2 illustrates the framework of the DBN technique.

Figure 2: Structure of DBN
The energy function is determined by Eq. (16) once the state space of
(2) K-step Contrastive Divergence Methodology (k-CDM): the default Gibbs sampling RBM training model is more ineffective since the
Next, based on
The calculation of
Next,
In CD-1 (Gaussian to Gaussian), the energy function was re-determined by:
When the K-step is set to one-step, afterwards
While Eq. (19) changed to:
(3) Building
2.3 Parameter Tuning Using DFA
Finally, the DFA is utilized for the hyperparameter tuning of the DBN model. Dragonfly has unique swarming behaviours that encompass migration (dynamic swarm) and hunting (static swarm) [19]. Static swarming has major features such as local movement and fast evolution in the flying direction. In static swarming, the dragonfly hunts for food while flying back and forth in a smaller group, whereas in dynamic swarming, the dragonfly moves in one direction over a longer distance. Such behaviours are comparable to the 2 stages of optimization using metaheuristics, such as exploration and exploitation, correspondingly.
In DFA, five major aspects exist to update the location of dragonflies in a swarm: distraction, separation, alignment, cohesion, and attraction.
The separation
In Eq. (24), X indicates the existing location,
The alignment
In Eq. (25),
The cohesion
The attraction
In Eq. (27),
The distraction
In Eq. (28),
The swarm behaviour of dragonflies is a grouping of those factors. For upgrading the location of the dragonfly, 2 vectors, step
In Eq. (29),
Afterwards, the computation of the step vector, the location vector is evaluated by Eq. (30),
For exploration, searching space can be performed by a random walk (Levy Ilight) and is evaluated using Eq. (31).
Now,
where
The location of the dragonfly is upgraded as follows.
Now, d indicates the dimension of the location vector.
This section assesses the experimental validation of the AAA-ODBN approach utilizing a dataset [20], as depicted in Table 1. IoT-23 is a new network traffic dataset from the Internet of Things (IoT) devices. It has 20 malware captures executed in IoT devices and 3 captures for benign IoT device traffic.

The confusion matrices provided by the AAA-ODBN model under distinct TR and TS dataset is given in Fig. 3. With 80% of TR data, the AAA-ODBN approach has categorized 360 samples into M-1, 341 samples into M-2, 343 samples into M-3, 351 samples into M-4, 366 samples into M-5, 360 samples into M-6, 342 samples into M-7, 369 samples into M-8, and 372 samples into B. Simultaneously, with 20% of TS data, the AAA-ODBN system has categorized 91 samples into M-1, 99 samples into M-2, 99 samples into M-3, 93 samples into M-4, 82 samples into M-5, 94 samples into M-6, 67 samples into M-7, 75 samples into M-8, and 88 samples into B. Concurrently, with 70% of TR data, the AAA-ODBN technique has categorized 278 samples into M-1, 287 samples into M-2, 292 samples into M-3, 308 samples into M-4, 280 samples into M-5, 298 samples into M-6, 283 samples into M-7, 308 samples into M-8, and 318 samples into B. Finally, with 30% of TS data, the AAA-ODBN methodology has categorized 116 samples into M-1, 1230 samples into M-2, 123 samples into M-3, 122 samples into M-4, 124 samples into M-5, 128 samples into M-6, 140 samples into M-7, 132 samples into M-8, and 144 samples into B.
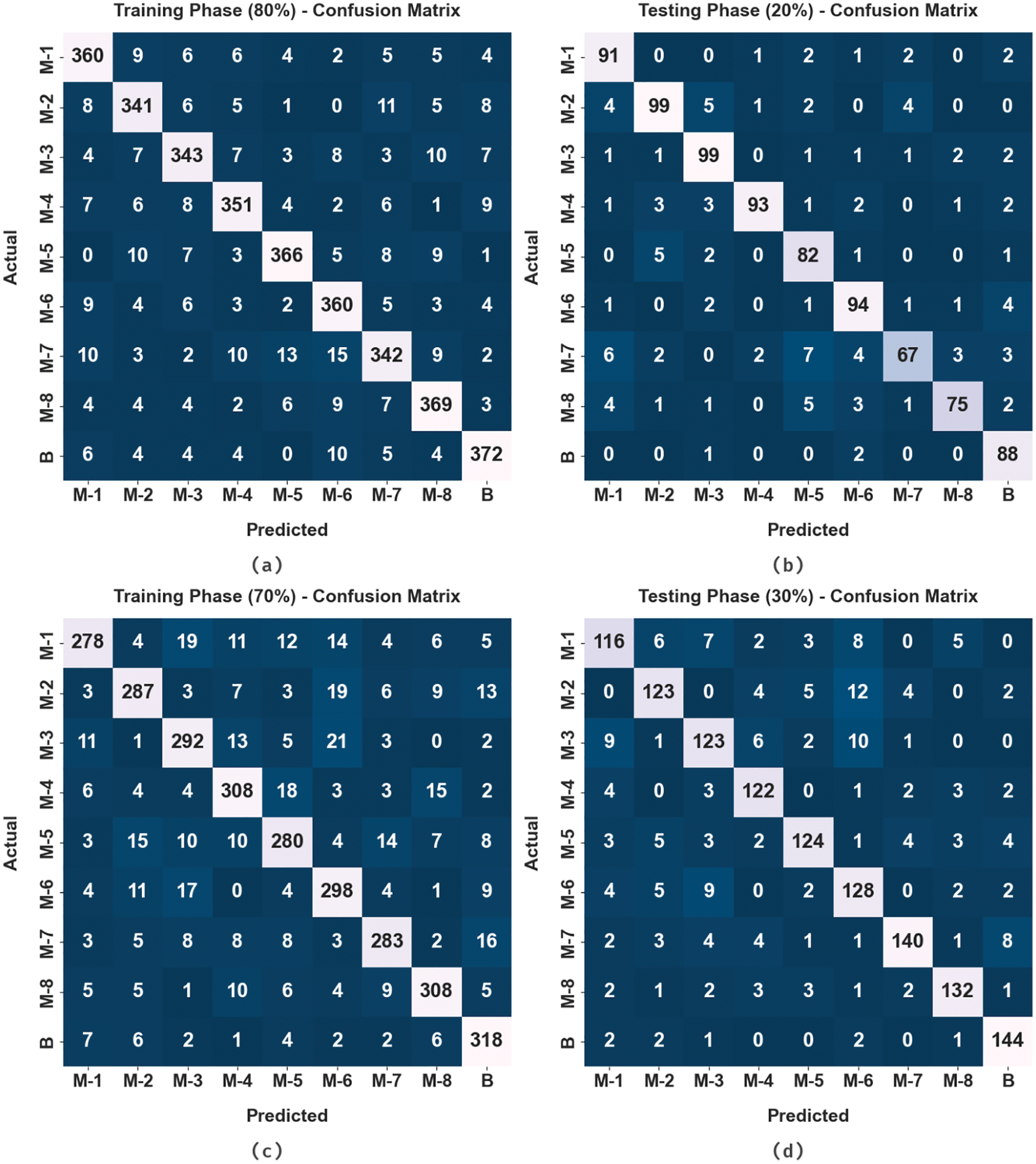
Figure 3: Confusion matrices of AAA-ODBN approach (a) 80% of TR dataset, (b) 20% of TS dataset, (c) 70% of TR dataset, and (d) 30% of TS dataset
Table 2 provides an overall result analysis of the AAA-ODBN model on 80% of TR data and 20% of TS data.

Fig. 4 illustrates a brief ransomware detection outcome of the AAA-ODBN approach on 80% of TR data. These results ensured that the AAA-ODBN model has improved under all classes. For the sample, in the M-1 class, the AAA-ODBN technique has an accessible

Figure 4: Average analysis of AAA-ODBN algorithm under 80% of TR data
Fig. 5 depicts a brief ransomware detection result of the AAA-ODBN technique on 20% of TS data. These outcomes ensured that the AAA-ODBN technique had demonstrated enhanced results under all classes. For sample, in the M-1 class, the AAA-ODBN methodology has an accessible

Figure 5: Average analysis of AAA-ODBN algorithm under 20% of TS data
Table 3 provides an overall result investigation of the AAA-ODBN technique on 70% of TR data and 30% of TS data. Fig. 6 showcases a detailed ransomware detection outcome of the AAA-ODBN technique on 70% of TR data. These outcomes indicated that the AAA-ODBN approach had enhanced outcomes in all classes. For sample, in the M-1 class, the AAA-ODBN system has an existing


Figure 6: Average analysis of AAA-ODBN algorithm under 70% of TR data
Fig. 7 defines a brief ransomware detection outcome of the AAA-ODBN methodology on 30% of TS data. These outcomes ensured that the AAA-ODBN technique had outperformed improved outcomes under all classes. For sample, in the M-1 class, the AAA-ODBN model has obtainable

Figure 7: Average analysis of AAA-ODBN algorithm under 30% of TS data
The training accuracy (TRA) and validation accuracy (VLA) acquired by the AAA-ODBN approach under the test dataset is displayed in Fig. 8. The experimental result outperformed that the AAA-ODBN method has reached enhanced values of TRA and VLA. In specific, the VLA looked that superior to TRA.

Figure 8: TRA and VLA analysis of AAA-ODBN algorithm
The training loss (TRL) and validation loss (VLL) realized by the AAA-ODBN methodology under the test dataset are shown in Fig. 9. The experimental result stated that the AAA-ODBN approach had decreased values of TRL and VLL. In certain, the VLL is lesser than TRL.

Figure 9: TRL and VLL analysis of AAA-ODBN algorithm
An obvious precision-recall investigation of the AAA-ODBN methodology under the test dataset is depicted in Fig. 10. The figure states that the AAA-ODBN technique has improved precision-recall values under distinct class value labels.

Figure 10: Precision-recall analysis of AAA-ODBN algorithm
A detailed ROC analysis of the AAA-ODBN system under the test dataset is displayed in Fig. 11. The outcome exhibited by the AAA-ODBN technique demonstrated its ability to classify various class labels.

Figure 11: ROC curve analysis of AAA-ODBN algorithm
At last, a comparison analysis of the AAA-ODBN approach with existing methodologies in terms of


Figure 12: Comparative analysis of AAA-ODBN approach with existing methodologies
In this study, a novel AAA-ODBN technique has been developed for ransomware detection in the IoT environment. The presented AAA-ODBN technique mainly intends to recognize and categorize ransomware in the IoT environment. The presented AAA-ODBN technique follows a three-stage process: feature selection, classification, and parameter tuning. In the first stage, the AAA-ODBN exploited the AAA-FS technique to elect feature subsets. Secondly, the AAA-ODBN technique employs the DBN model for ransomware detection. At last, the DFA is utilized for the hyperparameter tuning of the DBN approach. A sequence of simulations is executed to demonstrate the improved performance of the AAA-ODBN system. The experimental values indicate the significant outcomes of the AAA-ODBN model over other models. As a part of the future scope, feature reduction approaches can improve the outcome of the AAA-ODBN model.
Funding Statement: This work was funded by the Deanship of Scientific Research at Princess Nourah bint Abdulrahman University, through the Research Groups Program Grant no. (RGP-1443-0048).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. D. W. Fernando, N. Komninos and T. Chen, “A study on the evolution of ransomware detection using machine learning and deep learning techniques,” IoT, vol. 1, no. 2, pp. 551–604, 2020. [Google Scholar]
2. U. Urooj, B. A. S. Al-rimy, A. Zainal, F. A. Ghaleb and M. A. Rassam, “Ransomware detection using the dynamic analysis and machine learning: A survey and research directions,” Applied Sciences, vol. 12, no. 1, pp. 172, 2021. [Google Scholar]
3. R. Damaševičius, A. Venčkauskas, J. Toldinas and Š. Grigaliūnas, “Ensemble-based classification using neural networks and machine learning models for windows PE malware detection,” Electronics, vol. 10, no. 4, pp. 485, 2021. [Google Scholar]
4. C. W. Tien, S. W. Chen, T. Ban and S. Y. Kuo, “Machine learning framework to analyze IoT malware using elf and opcode features,” Digital Threats: Research and Practice, vol. 1, no. 1, pp. 1–19, 2020. [Google Scholar]
5. S. I. Bae, G. B. Lee and E. G. Im, “Ransomware detection using machine learning algorithms,” Concurrency and Computation: Practice and Experience, vol. 32, no. 18, pp. e5422, 2020. [Google Scholar]
6. S. Sharma, C. R. Krishna and R. Kumar, “Android ransomware detection using machine learning techniques: A comparative analysis on GPU and CPU,” in 21st Int. Arab Conf. on Information Technology (ACIT), Giza, Egypt, pp. 1–6, 2020. [Google Scholar]
7. Y. Dion and S. N. Brohi, “An experimental study to evaluate the performance of machine learning algorithms in ransomware detection,” Journal of Engineering Science and Technology, vol. 15, no. 2, pp. 967–981, 2020. [Google Scholar]
8. F. Noorbehbahani, F. Rasouli and M. Saberi, “Analysis of machine learning techniques for ransomware detection,” in 16th Int. ISC (Iranian Society of Cryptology) Conf. on Information Security and Cryptology (ISCISC), Mashhad, Iran, pp. 128–133, 2019. [Google Scholar]
9. M. Asam, S. J. Hussain, M. Mohatram, S. H. Khan, T. Jamal et al., “Detection of exceptional malware variants using deep boosted feature spaces and machine learning,” Applied Sciences, vol. 11, no. 21, pp. 10464, 2021. [Google Scholar]
10. M. Dib, S. Torabi, E. Bou-Harb and C. Assi, “A multi-dimensional deep learning framework for iot malware classification and family attribution,” IEEE Transactions on Network and Service Management, vol. 18, no. 2, pp. 1165–1177, 2021. [Google Scholar]
11. J. Hwang, J. Kim, S. Lee and K. Kim, “Two-stage ransomware detection using dynamic analysis and machine learning techniques,” Wireless Personal Communications, vol. 112, no. 4, pp. 2597–2609, 2020. [Google Scholar]
12. S. Baek, J. Jeon, B. Jeong and Y. S. Jeong, “Two-stage hybrid malware detection using deep learning,” Human-Centric Computing and Information Sciences, vol. 11, no. 27, pp. 10–22967, 2021. [Google Scholar]
13. M. Basnet, S. Poudyal, M. H. Ali and D. Dasgupta, “Ransomware detection using deep learning in the SCADA system of electric vehicle charging station,” in IEEE PES Innovative Smart Grid Technologies Conf.-Latin America (ISGT Latin America), Lima, Peru, pp. 1–5, 2021. [Google Scholar]
14. M. Nisa, J. H. Shah, S. Kanwal, M. Raza, M. A. Khan et al., “Hybrid malware classification method using segmentation-based fractal texture analysis and deep convolution neural network features,” Applied Sciences, vol. 10, no. 14, pp. 4966, 2020. [Google Scholar]
15. R. Agrawal, J. W. Stokes, K. Selvaraj and M. Marinescu, “Attention in recurrent neural networks for ransomware detection,” in IEEE Int. Conf. on Acoustics, Speech and Signal Processing (ICASSP), Brighton, UK, pp. 3222–3226, 2019. [Google Scholar]
16. A. Azmoodeh, A. Dehghantanha and K. K. R. Choo, “Robust malware detection for internet of (battlefield) things devices using deep eigenspace learning,” IEEE Transactions on Sustainable Computing, vol. 4, no. 1, pp. 88–95, 2018. [Google Scholar]
17. A. Abugabah, A. A. AlZubi, M. Al-Maitah and A. Alarifi, “Brain epilepsy seizure detection using bio-inspired krill herd and artificial alga optimized neural network approaches,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 3, pp. 3317–3328, 2021. [Google Scholar]
18. W. Deng, H. Liu, J. Xu, H. Zhao and Y. Song, “An improved quantum-inspired differential evolution algorithm for deep belief network,” IEEE Transactions on Instrumentation and Measurement, vol. 69, no. 10, pp. 7319–7327, 2020. [Google Scholar]
19. E. Yousefpoor, H. Barati and A. Barati, “A hierarchical secure data aggregation method using the dragonfly algorithm in wireless sensor networks,” Peer-to-Peer Networking and Applications, vol. 14, no. 4, pp. 1917–1942, 2021. [Google Scholar]
20. A. Parmisano, S. Garcia and M. J. Erquiaga, “A labeled dataset with malicious and benign IoT network traffic, https://www.stratosphereips.org/datasets-iot23. [Google Scholar]
21. A. Sahu, S. Sharma, M. Tanveer and R. Raja, “Internet of Things attack detection using hybrid deep learning model,” Computer Communications, vol. 176, no. 3, pp. 146–154, 2021. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools