 Open Access
Open Access
ARTICLE
Aquila Optimization with Machine Learning-Based Anomaly Detection Technique in Cyber-Physical Systems
1 Department of Computer Science and Engineering, University College of Engineering, Panruti, 607106, India
2 Department of Electronics and Communication Engineering, University College of Engineering, Panruti, 607106, India
3 College of Technical Engineering, The Islamic University, Najaf, Iraq
4 Medical Instrumentation Techniques Engineering Department, Al-Mustaqbal University College, Babylon, Iraq
* Corresponding Author: A. Ramachandran. Email:
Computer Systems Science and Engineering 2023, 46(2), 2177-2194. https://doi.org/10.32604/csse.2023.034438
Received 17 July 2022; Accepted 25 November 2022; Issue published 09 February 2023
Abstract
Cyber-physical system (CPS) is a concept that integrates every computer-driven system interacting closely with its physical environment. Internet-of-things (IoT) is a union of devices and technologies that provide universal interconnection mechanisms between the physical and digital worlds. Since the complexity level of the CPS increases, an adversary attack becomes possible in several ways. Assuring security is a vital aspect of the CPS environment. Due to the massive surge in the data size, the design of anomaly detection techniques becomes a challenging issue, and domain-specific knowledge can be applied to resolve it. This article develops an Aquila Optimizer with Parameter Tuned Machine Learning Based Anomaly Detection (AOPTML-AD) technique in the CPS environment. The presented AOPTML-AD model intends to recognize and detect abnormal behaviour in the CPS environment. The presented AOPTML-AD framework initially pre-processes the network data by converting them into a compatible format. Besides, the improved Aquila optimization algorithm-based feature selection (IAOA-FS) algorithm is designed to choose an optimal feature subset. Along with that, the chimp optimization algorithm (ChOA) with an adaptive neuro-fuzzy inference system (ANFIS) model can be employed to recognise anomalies in the CPS environment. The ChOA is applied for optimal adjusting of the membership function (MF) indulged in the ANFIS method. The performance validation of the AOPTML-AD algorithm is carried out using the benchmark dataset. The extensive comparative study reported the better performance of the AOPTML-AD technique compared to recent models, with an accuracy of 99.37%.Keywords
Cyber physical system (CPS) involves incorporating the physical system into the real-time and control software in the cyber world, whereby the network interconnects the two worlds and is accountable for the data exchange amongst themselves [1]. Wide-ranging development in communication technology might assist real-time communication with lower latency making them possible to remotely control various physical systems and provide smart facilities to CPS users [2]. Furthermore, adapting wired and wireless networks in a CPS allows the state of a large number of industrial equipment to be observed. Consequently, it is the potential to flexibly organize and handle a complicated industrial system [3]. Therefore, the CPS is the fundamental technology for different industrial sectors involving smart grid systems, smart transportation systems, and medical systems. Fig. 1 displays the overview of CPS.
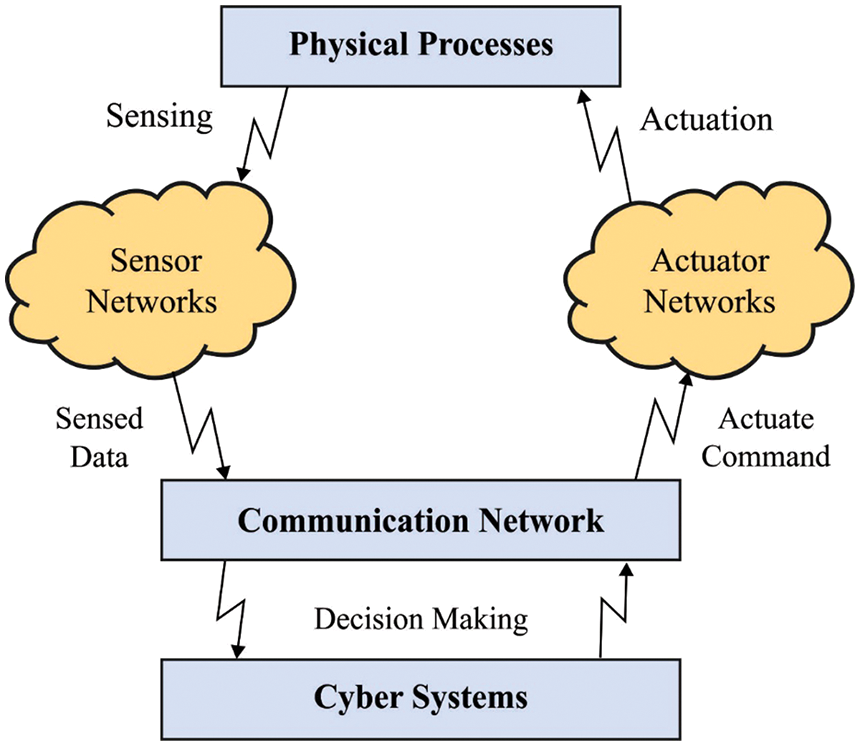
Figure 1: Overview of CPS
As the connectivity of CPS rises and becomes increasingly sophisticated, the path through which attackers infiltrate the CPS is growing [4]. The network that connects the CPS and the control software is particularly susceptible to an external attacker that aims to invade the physical system and cause a malfunction in the CPS [5]. Once the attacker access the network, the control authority of CPS operation on the network can be seized, the implementation of control critical software is disturbed in the cyber world, and the attacker's power of the CPS or control the physical system with a deceitful attack detection technique [6]. The CPS attack harms industrial processes and equipment, which causes human casualties and economic losses. To identify unexpected errors and attacks in CPS, an anomaly detection system is introduced to mitigate the threat [7]. For instance, statistical models (for example, Gaussian model, histogram-based model) based method, rule, and state estimation (for example, Kalman filter) are exploited to learn the typical status of CPS. But the method usually needs expert knowledge (for example, the operator manually extracts some rules) or should be aware of the fundamental distribution of standard datasets [8].
Machine learning (ML) approaches don’t depend on domain-specific knowledge. However, they typically need a massive amount of labelled datasets (for example, classification-based method). They also could not capture the unique attribute of CPS (for example, spatiotemporal relationship). An intrusion detection system (IDS) ensures network transmission security [9]. Physical property is captured to represent the immutable nature of CPS. Program implementation semantics are considered to protect the control system. But, as CPS becomes more complex and the attack is more stealthy, this method is more difficult to ensure the status of CPS (for example, protecting multi-variate physical measurement). It requires further domain knowledge (for example, correlation and more components) [10]. An anomaly detection system needs to adapt to capture novel features of CPS.
This article develops an Aquila Optimizer with Parameter Tuned Machine Learning Based Anomaly Detection (AOPTML-AD) technique in the CPS environment. The presented AOPTML-AD model pre-processes the network data by converting it into a compatible format. In addition, the improved Aquila optimization algorithm-based feature selection (IAOA-FS) technique is designed to choose an optimal feature subset. Furthermore, the chimp optimization algorithm (ChOA) with an adaptive neuro-fuzzy inference system (ANFIS) model can be employed to recognise anomalies in the CPS environment. The ChOA is applied for optimal adjustment of the membership function (MF) indulged in the ANFIS model. The performance validation of the AOPTML-AD algorithm is carried out using the benchmark datasets.
Thiruloga et al. [11] introduce a new unsupervised technique for detecting cyber-attacks in (CPS). The authors define an unsupervised learning method by using a Recurrent Neural network (RNN) that can be a time sequence predictor in this method. They employ the Cumulative Sum technique for identifying anomalies in a replication of a water treatment plant. The presented technique not just identifies anomalies in the CPS but also detects a sensor that has been attacked. In [12], the researchers review the existing deep learning (DL)-related anomaly detection (DLAD) techniques in CPSs. They suggest a taxonomy relating to the anomaly’s types, implementation, evaluation metrics, and strategies for understanding the necessary properties of existing techniques. Additionally, they use this taxonomy for identifying and highlighting novel features and models in every CPS field. Luo et al. [13] suggest an anomaly detection method by integrating the intellectual DL method called convolutional neural network (CNN) with Kalman Filter (KF) related Gaussian-Mixture Model (GMM). The suggested method can be utilized to detect abnormal conduct in CPSs. This recommended structure has 2 significant procedures. The primary step was pre-processing the data by filtering and transforming the original data into an innovative format and attained privacy data preservation. And then, the research scholars suggested the GMM-KF integrated deep CNN method for anomaly detection (AD) and precisely assessed the posterior probability of legitimate and anomalous events in CPSs.
Nagarajan et al. [14] suggested the Data-Correlation-Aware Unsupervised DL method for AD in CPS that utilizes an undigraph framework for storing samples and implied relation amongst samples. The authors devise a dual-AE for training both original features and implied correlation features amongst data. They build an estimation network by use of GMM for evaluating the probability sample distribution for the completion of an anomaly analysis. Xi et al. [15] recommend a new time sequence anomaly detection technique termed Neural System Identification and Bayesian Filtering (NSIBF), where a specially crafted NN framework was posed for system identification. Singh and Feng et al. [16] offer a structure and method to develop a cyber-physical AD system (CPADS) that uses synchrophasor dimensions and network packet properties to detect data integrity and transmission failure assaults on measurement and control signals in CRAS. The suggested ML-related method adopts a rules-related technique for selecting relevant input features, uses DT and variational mode decomposition (VMD) methods for developing multiple classification methods, and executes final event identification utilizing a rules-related decision logic. In [17], an intelligent anomaly identification (IAI) method for these mechanisms was provided using data-driven tools which leverage a multi-class support vector machine (MSVM) for anomaly localization and classification. The impacts of cyber-anomalies like false data injection and denial of service (DoS) assaults that target the transmission network were taken in this study.
In this study, a new AOPTML-AD model intends to recognize and detect anomalous behaviour in the CPS environment. The presented AOPTML-AD framework initially pre-processed the network data by converting them into a compatible format. The IAOA-FS method is designed to elect an optimal subset of features. This study utilises the ChOA with the ANFIS model for anomaly detection and classification. Fig. 2 depicts the overall process of the AOPTML-AD approach.
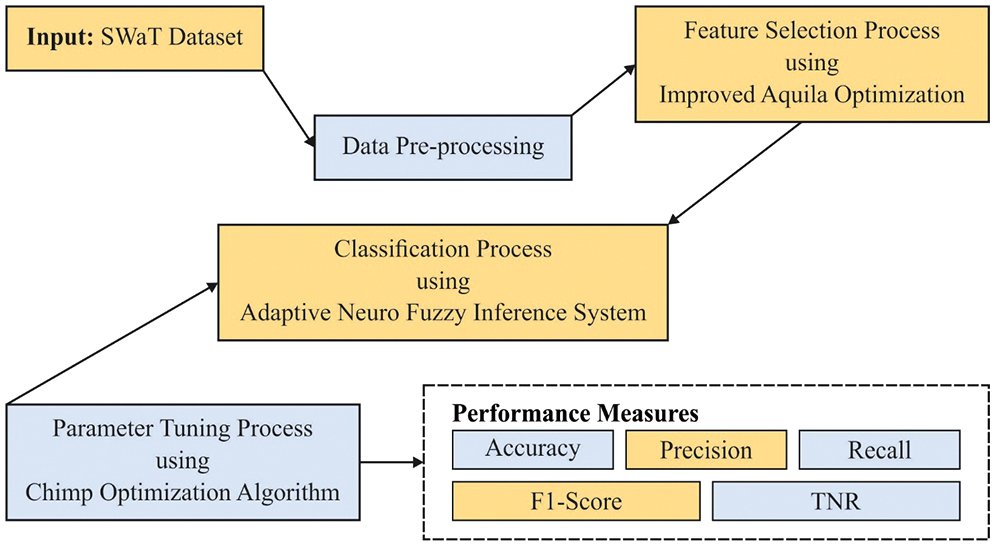
Figure 2: Overall process of AOPTML-AD approach
The presented AOPTML-AD framework initially pre-processed the network data by converting them into a compatible format. The data accumulated in real applications is noisy and consist of certain missing values or errors. Moreover, the scale of data from various kinds of sensors could differ. Thus, data cleaning becomes essential and significant for further processing. The
Here,
Once the input data is pre-processed, the IAOA-FS algorithm is designed to choose an optimal subset feature. AOA was recently introduced. It was claimed and proven with better performance and faster convergence speed than other techniques [18]. Also, the individual in a swarm of the AOA has four ways to upgrade its location, but they could only select two during the first 2/3 full process in exploration and two during the exploitation process. In the presented technique, there exist four approaches for individuals as follows:
Strategy 1: Expanded exploration.
In Eq. (2),
In Eq. (3),
Strategy 2: Narrowed exploration.
In Eq. (4),
where
where
From the expression,
Strategy 3: Expanded exploitation.
In Eq. (12),
Strategy 4: Narrowed exploitation.
In Eq. (13),
The IAOA is derived by including the quasi-oppositional based learning (QOBL) concept. In the AOA, the population tries to reach the optimal solutions located in an identified place. Thus, the water strider attempts to go to the same places, so the diversity of individuals is lost. A familiar process amongst the meta-heuristics is utilizing the Quasi Opposition-Based Learning (QOBL) approach to resolve this problem. It is executed as follows:
Whereas
The fitness function (FF) of the IAOA-FS technique is developed to have a balance between the classification accuracy (maximum) and the number of selected features in every solution (minimum) attained by utilizing this selected feature, Eq. (20) denotes the FF to estimate solution.
From the expression,
At this stage, the chosen features are passed into the ANFIS model and are utilized for the recognition of anomalies in the CPS environment. Generally, ANFIS produces a mapping among outputs and inputs by applying “IF-THEN rules” (otherwise called as “Takagi-Sugeno inference model”) [19]. As shown, the input of Layer 1 is characterized as
From the expression,
Eq. (24) describes the output of Layer 3:
In Eq. (24),
The output of Layer 4 is characterized as follows:
In Eq. (25),
At last, the output of Layer 5 is characterized as follows:
3.4 Parameter Tuning Using ChOA
At the final stage, the ChOA is applied for optimal adjustment of the membership function (MF) involved in the ANFIS method. The ChoA is inspired by chimps’ social status relationship and hunting behaviour. The four individual groups searched the problem space locally and globally, utilizing its unique pattern [20]. The drive and chase are provided as the subsequent formulas.
The present iteration number was determined with the symbol
The nonlinear reduction of
During the exploitation stage, the chimp’s performance was modelled by formulas as follows.
In the above formulas,
The original ChOA technique integrates 6 distinct chaos maps and 2 distinct sets of formulas for upgrading dynamic approaches. The dynamic model was utilized to define the coefficients
For the simplicity of this work, only one group of dynamic models and one chaos map are utilized. The chaos map was recognized as Gauss or Mouse. It can be determined as:
During the final phase, chimps relinquish their hunting responsibility and then obtain meet and succeeding social drive (sex and grooming). It can strive to gather meat chaotically during the outcome. For great dimensional problems, ChOA is developed to address two problems of slow convergence speed and traps from local optima. This chaotic performance in the final step supports chimps in overcoming the two problems of entrapment in local optimum and sluggish convergence rate from higher dimension problems resolving.
The ChoA method extracts the fitness function (FF) to obtain improvised classifier outcomes. It fixes a positive integer to denote the superior performance of the candidate solutions. In this work, the reduction of the classifier error rate can be regarded as the FF, as presented below in Eq. (43). The optimum solution comprises a minimum error rate, and the poor solution receives a higher error rate.
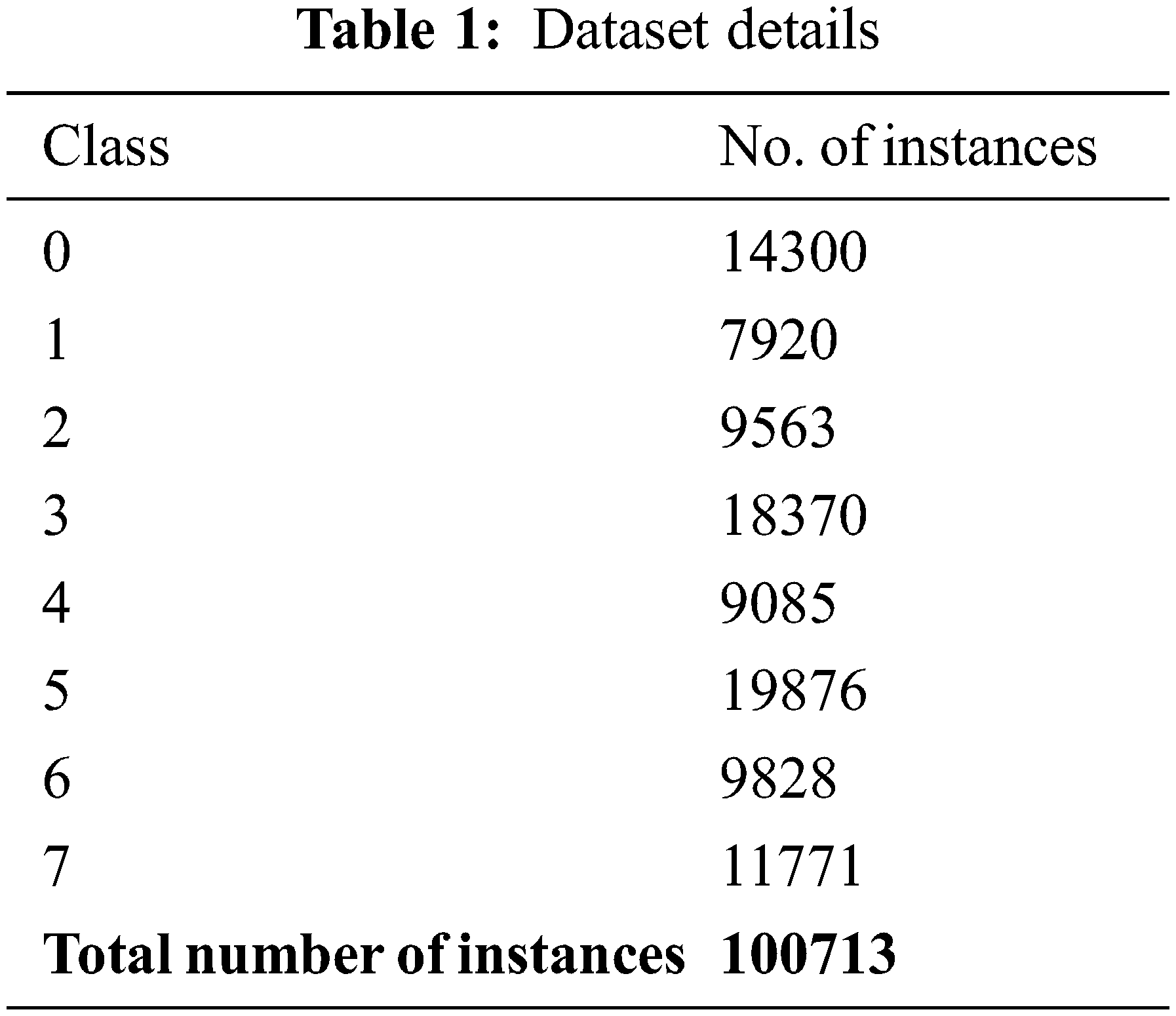
The experimental validation of the presented model is tested using the SWaT dataset [21]. It offers real data from a simpler form of the real-world water treatment plant. The datasets enable authors to devise and evaluate defence mechanisms for CPSs and comprise both network traffic as well as data concerning the physical property of a system. The dataset holds 100713 samples with seven class labels, as depicted in Table 1.
The confusion matrices generated by the AOPTML-AD model on distinct training (TR) and testing (TS) datasets are shown in Fig. 3. On 70% of TR data, the AOPTML-AD model has identified 9695 samples into class0, 5354 samples into class1, 6476 samples into class2, 12598 samples into class3, 6158 samples into class4, 13512 samples into class5, 6628 samples into class6, and 7974 samples into class 7. Also, on 30% of TS data, the AOPTML-AD method has identified 4241 samples into class 0, 2266 samples into class1, 2807 samples into class2, 5475 samples into class3, 2582 samples into class4, 5748 samples into class5, 2880 samples into class6, and 3363 samples into class7. In addition, on 80% of TR data, the AOPTML-AD technique has identified 11122 samples into class 0, 6164 samples into class 1, 7405 samples into class2, 14449 samples into class3, 7142 samples into class4, 15561 samples into class5, 7462 samples into class6, and 9164 samples into class7.
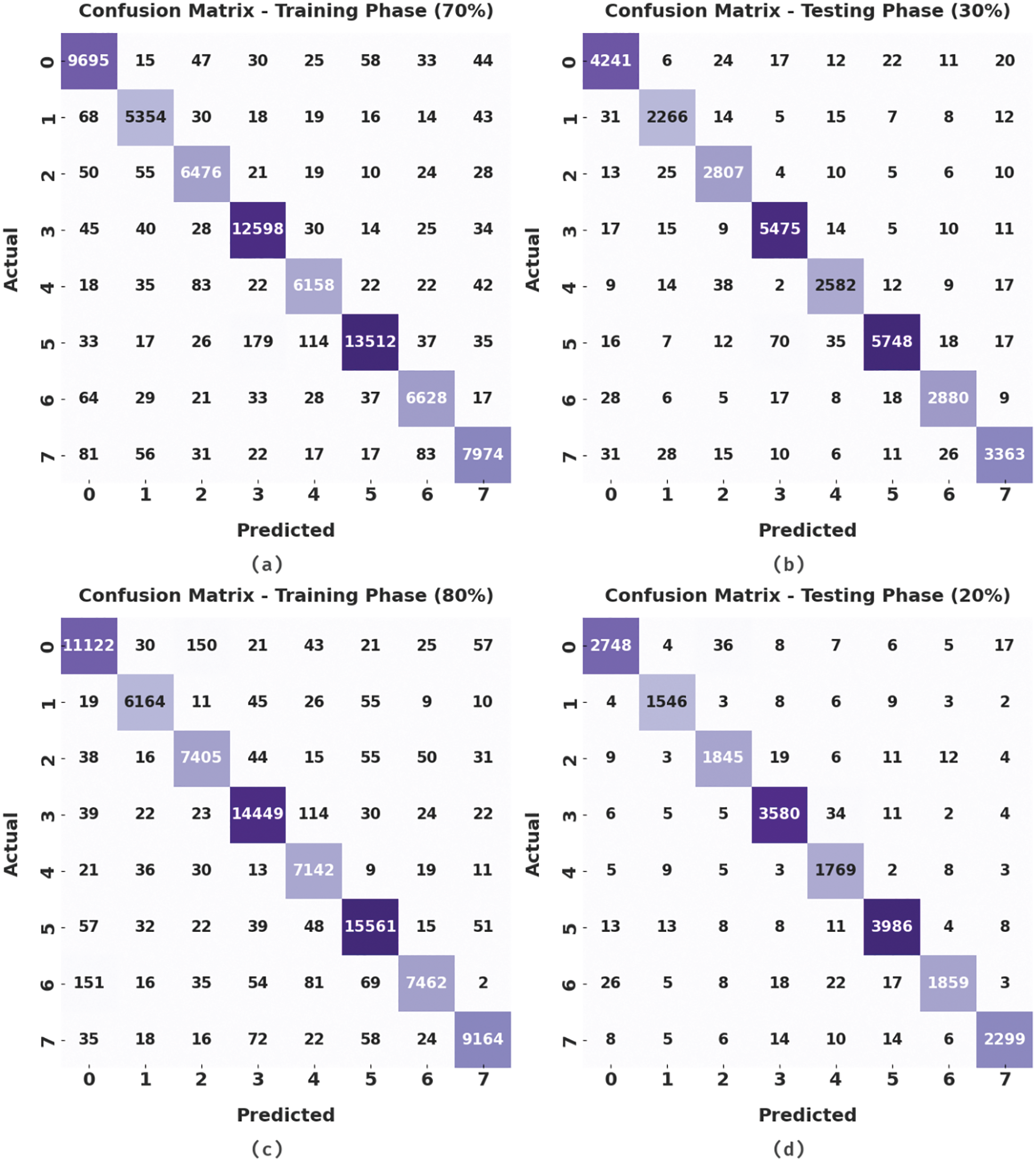
Figure 3: Confusion matrices of AOPTML-AD approach (a) 70% of TR data, (b) 30% of TS data, (c) 80% of TR data, and (d) 20% of TS data
Table 2 and Fig. 4 provide the overall classification outcomes of the AOPTML-AD model on 70% of TR data and 30% of TS data. The experimental values implied that the AOPTML-AD model had gained effectual outcomes under all classes. For instance, on 70% of TR data, the AOPTML-AD model has attained an average
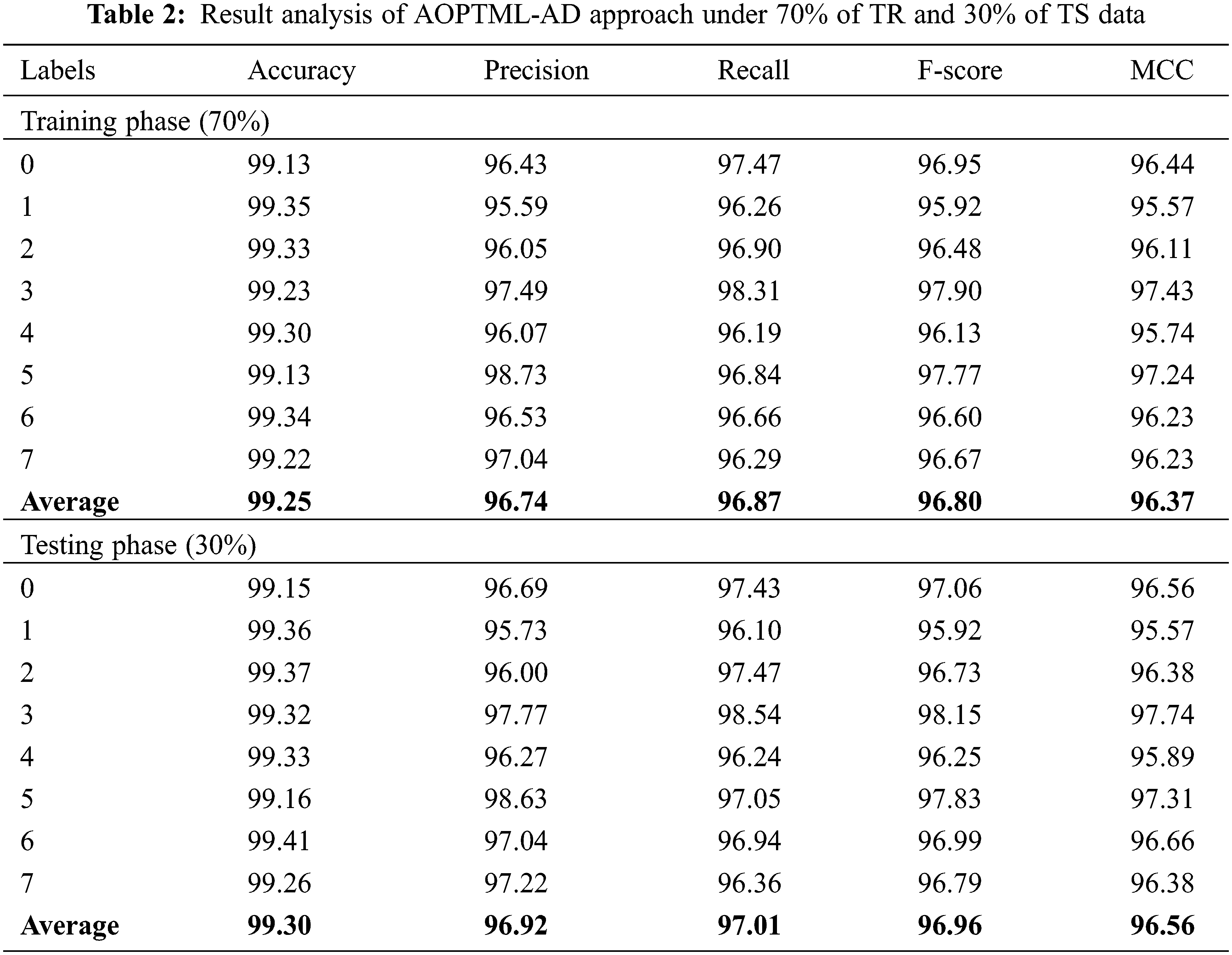
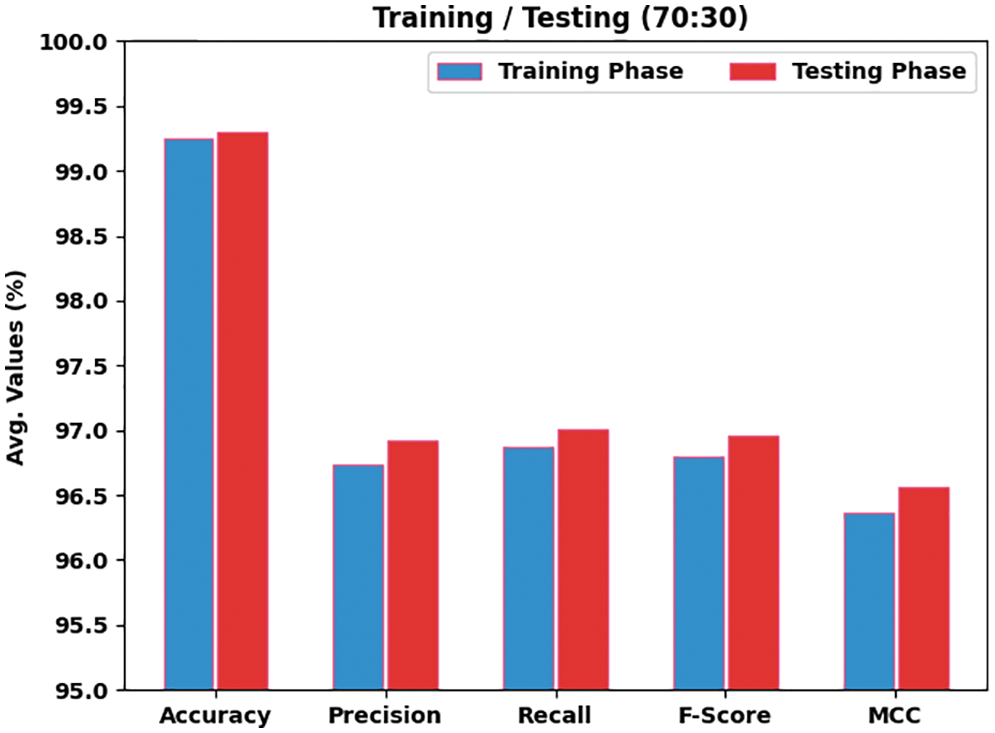
Figure 4: Average analysis of AOPTML-AD approach under 70% of TR and 30% of TS data
Next to that, on 30% of TS data, the AOPTML-AD approach has acquired an average
Table 3 and Fig. 5 offer the overall classification outcomes of the AOPTML-AD technique on 80% of TR data and 20% of TS data. The experimental values implied that the AOPTML-AD approach had obtained effectual outcomes under all classes. For example, on 80% of TR data, the AOPTML-AD algorithm has reached an average
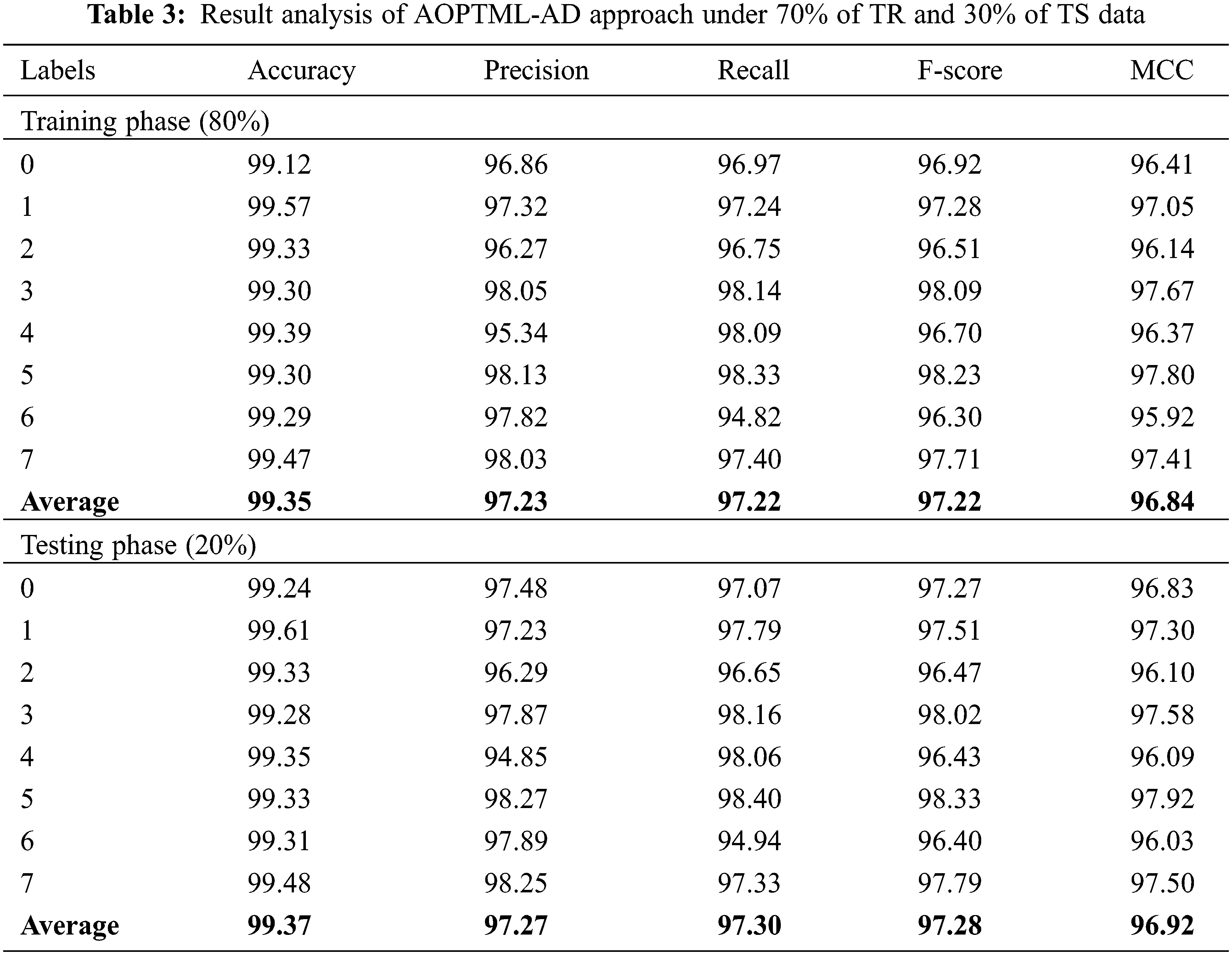
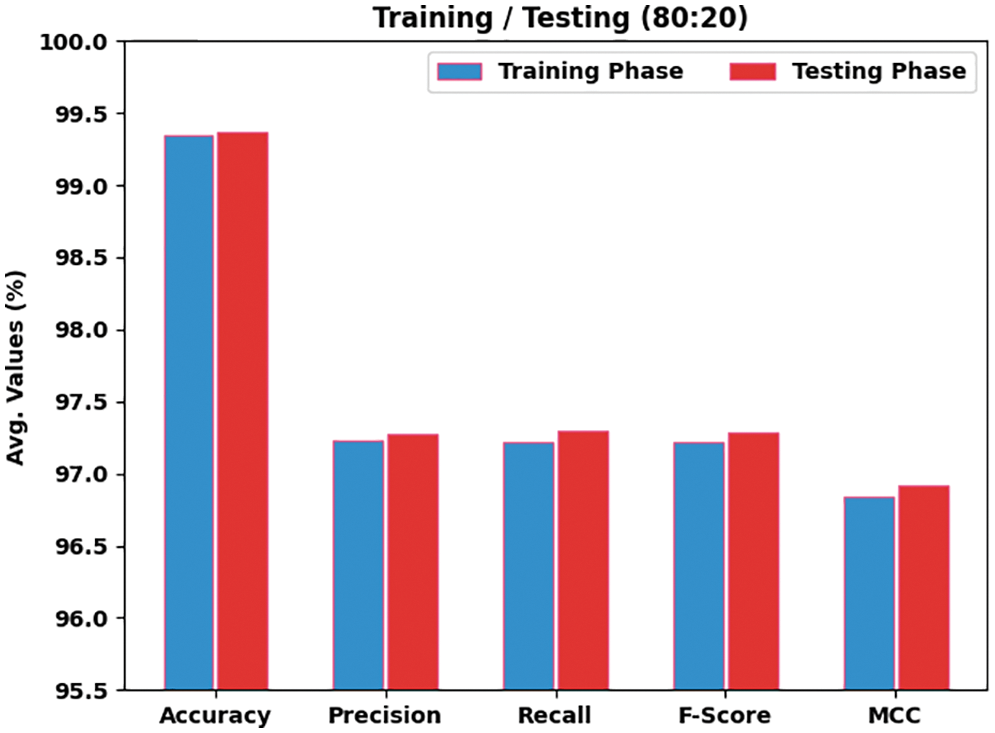
Figure 5: Average analysis of AOPTML-AD approach under 80% of TR and 20% of TS data
The training accuracy (TA) and validation accuracy (VA) acquired by the AOPTML-AD algorithm on the test dataset is demonstrated in Fig. 6. The experimental outcome denoted that the AOPTML-AD approach has achieved maximum values of TA and VA. In Particular, the VA is greater than TA.
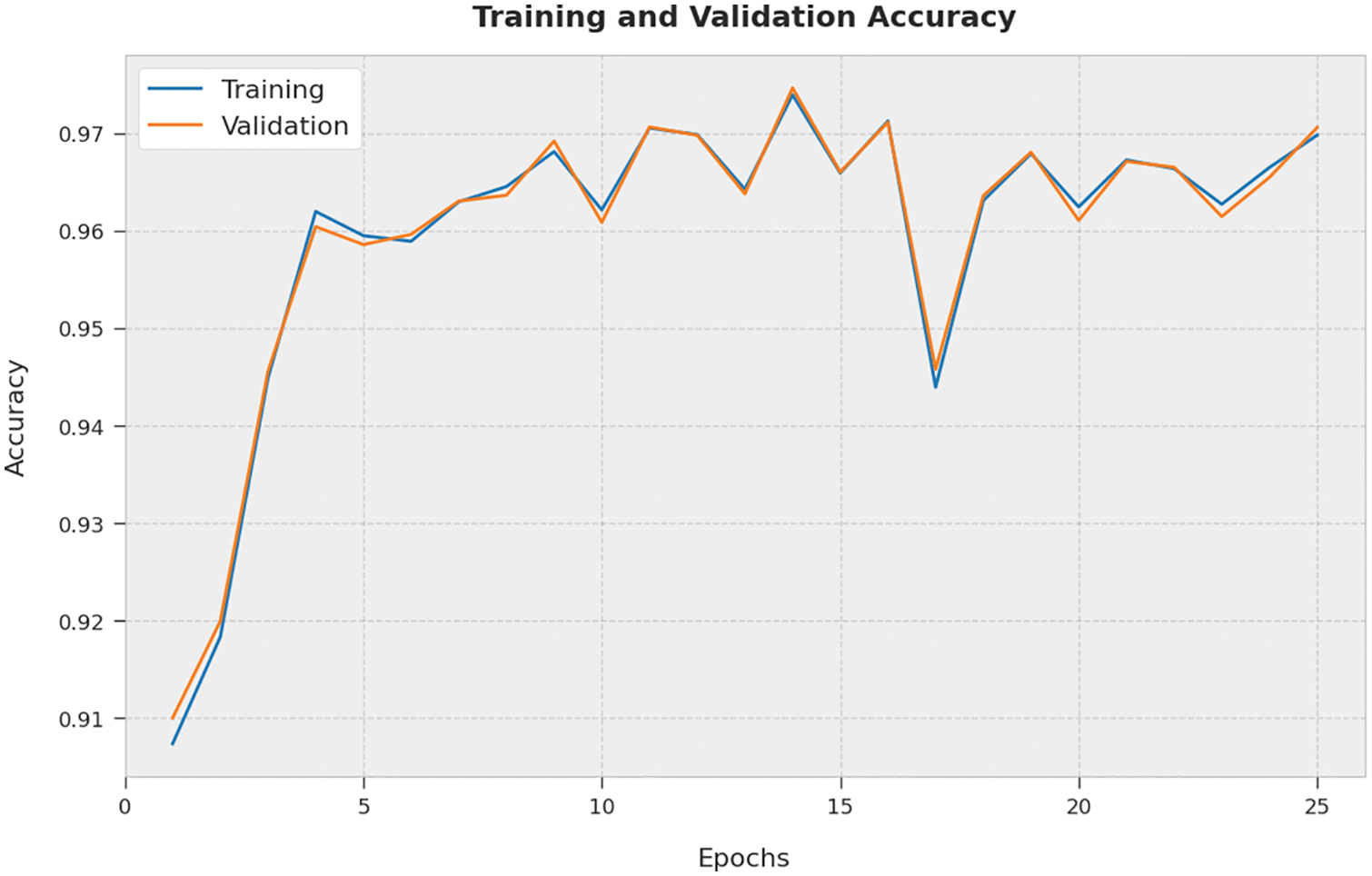
Figure 6: TA and VA analysis of the AOPTML-AD approach
The training loss (TL) and validation loss (VL) gained by the AOPTML-AD approach on the test dataset are established in Fig. 7. The experimental outcome represented that the AOPTML-AD methodology has accomplished the least values of TL and VL. Specifically, the VL is lesser than TL.
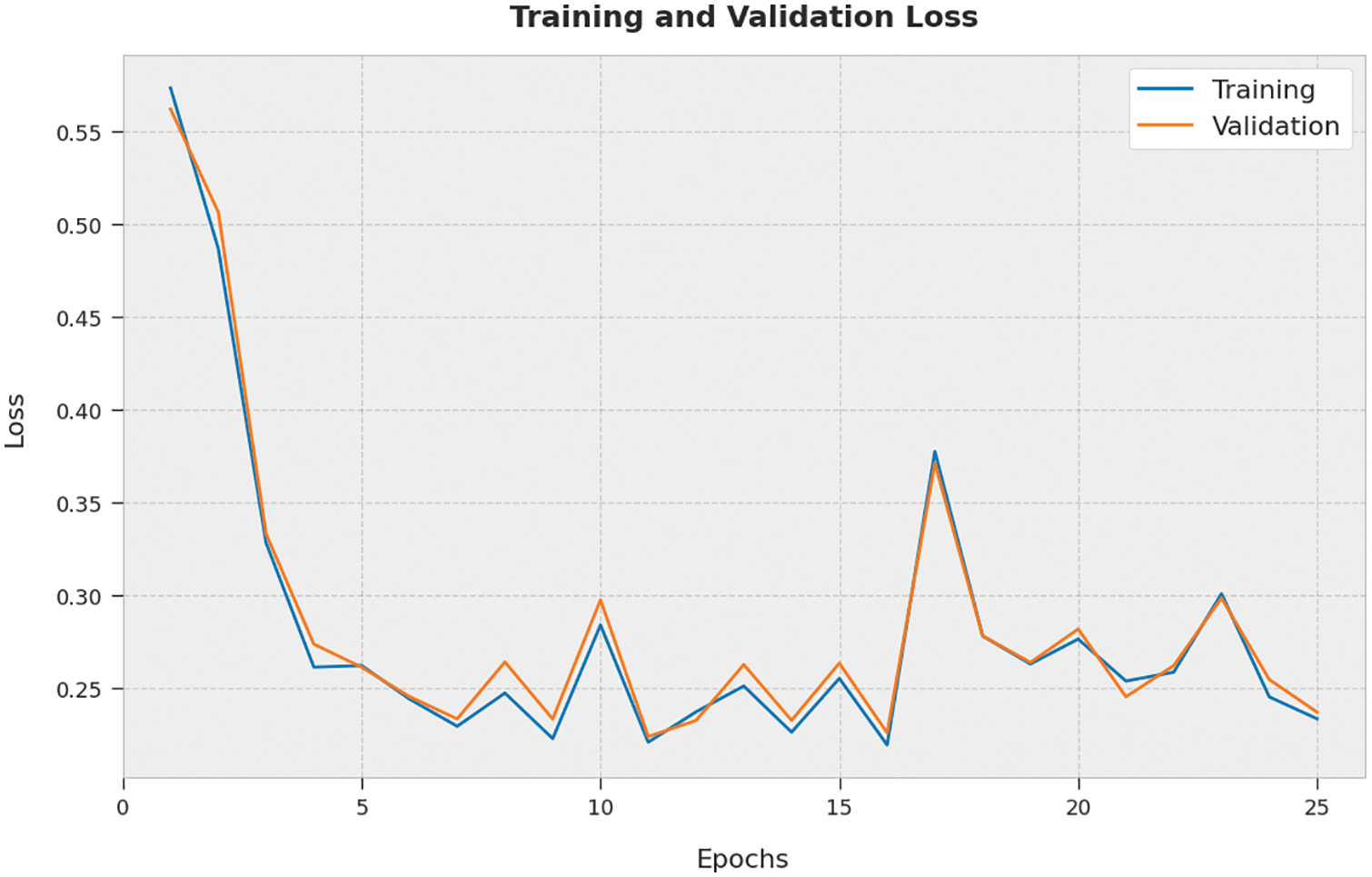
Figure 7: TL and VL analysis of the AOPTML-AD approach
A clear precision-recall analysis of the AOPTML-AD technique on the test dataset is depicted in Fig. 8. The figure denoted the AOPTML-AD approach has resulted in enhanced values of precision-recall values under all classes.
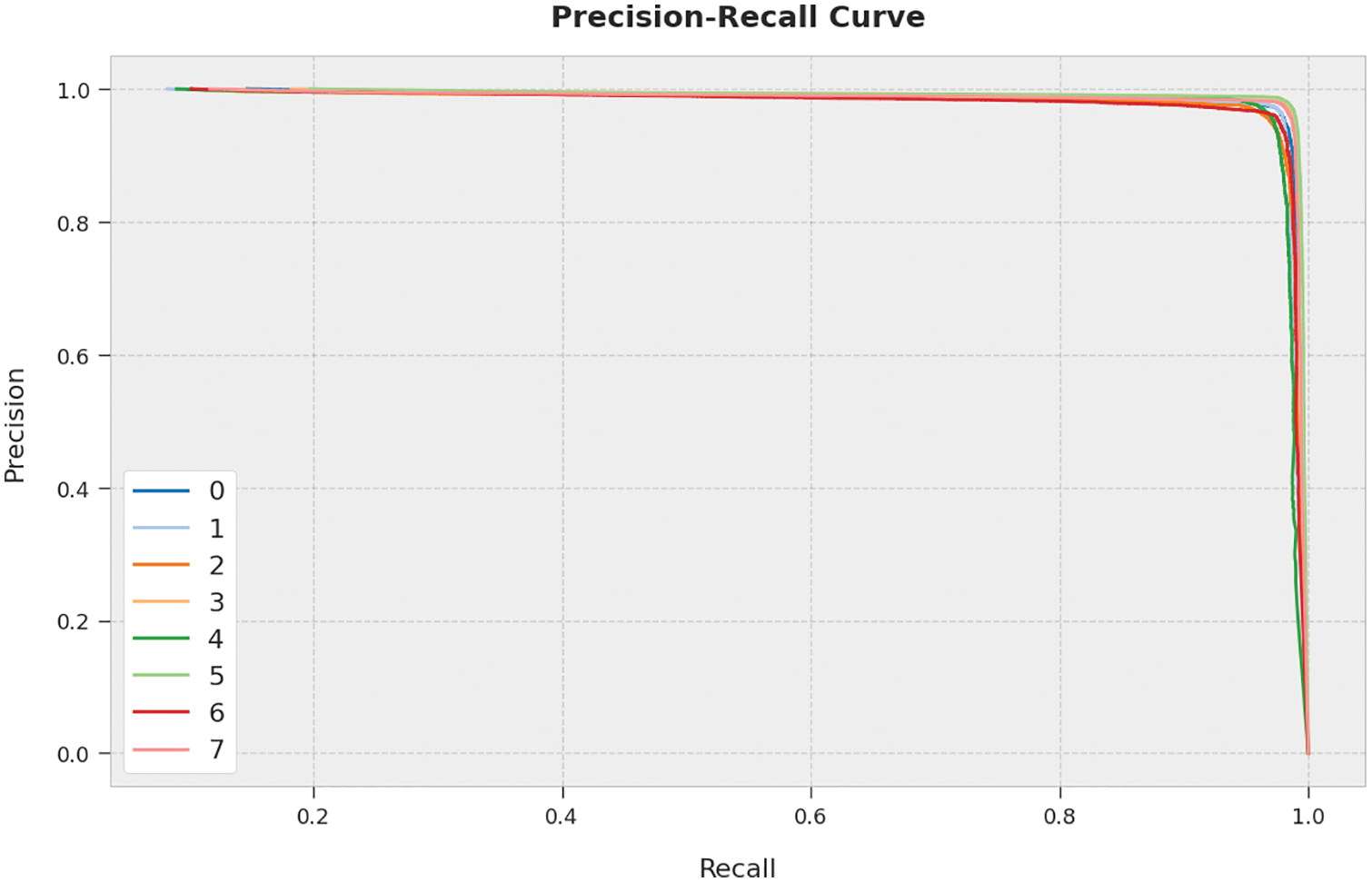
Figure 8: Precision-recall curve analysis of the AOPTML-AD approach
A brief ROC investigation of the AOPTML-AD approach to the test dataset is portrayed in Fig. 9. The results exhibited the AOPTML-AD approach has shown its ability to categorize distinct classes on the test dataset.
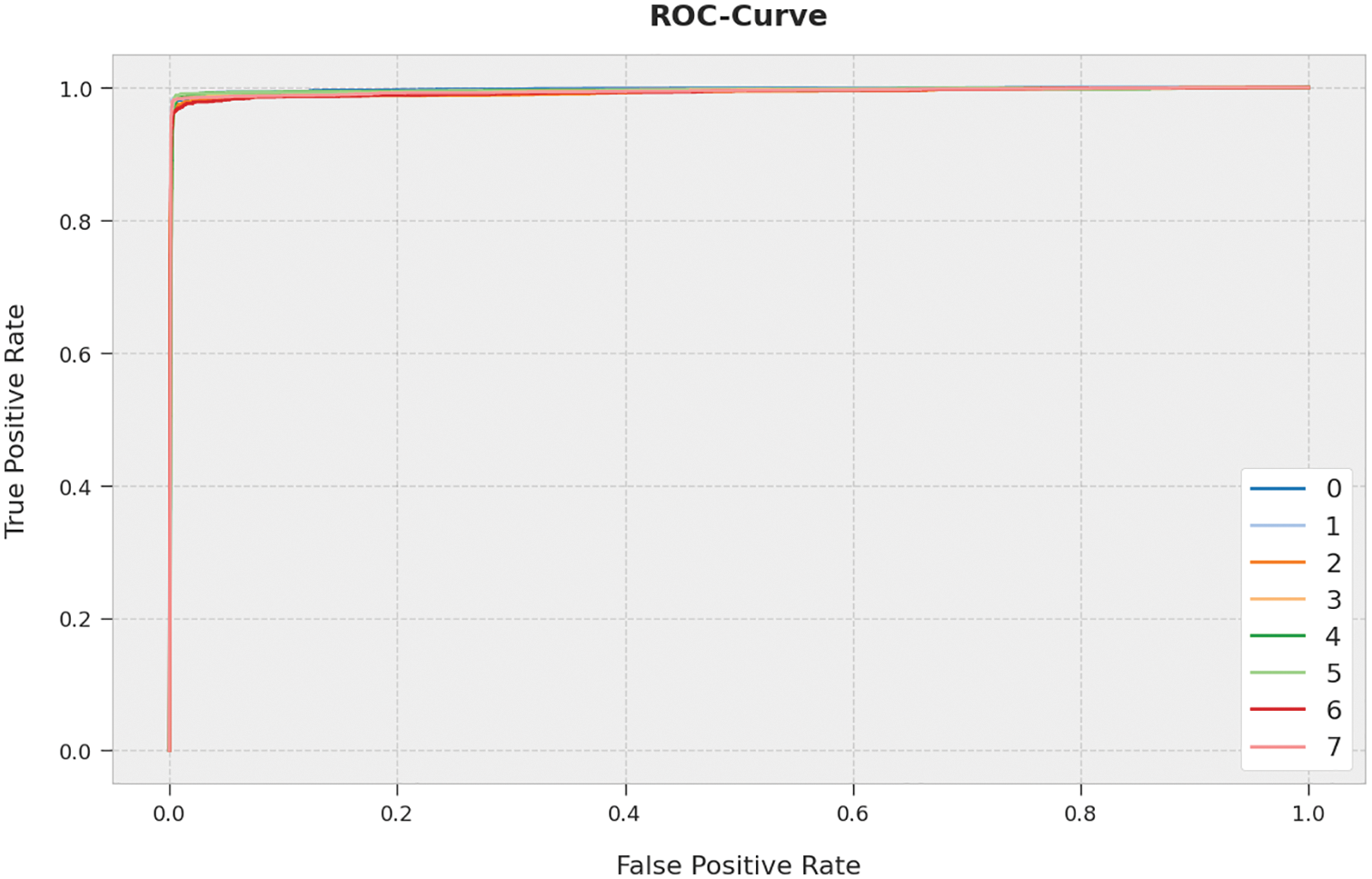
Figure 9: ROC curve analysis of the AOPTML-AD approach
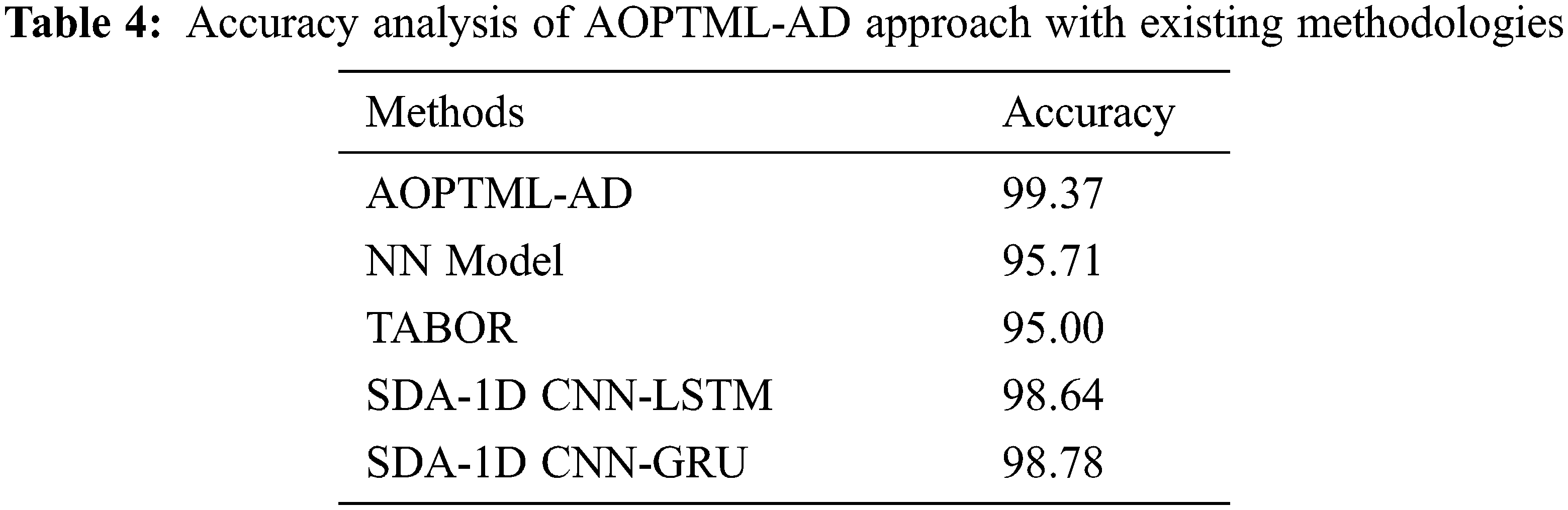
Table 4 offers a comparative
Finally, a comparative analysis of the AOPTML-AD model with the recent state-of-the-art models is portrayed in Table 5. The obtained values highlighted that the AOPTML-AD model had reported better results than other models. Fig. 10 renders a brief
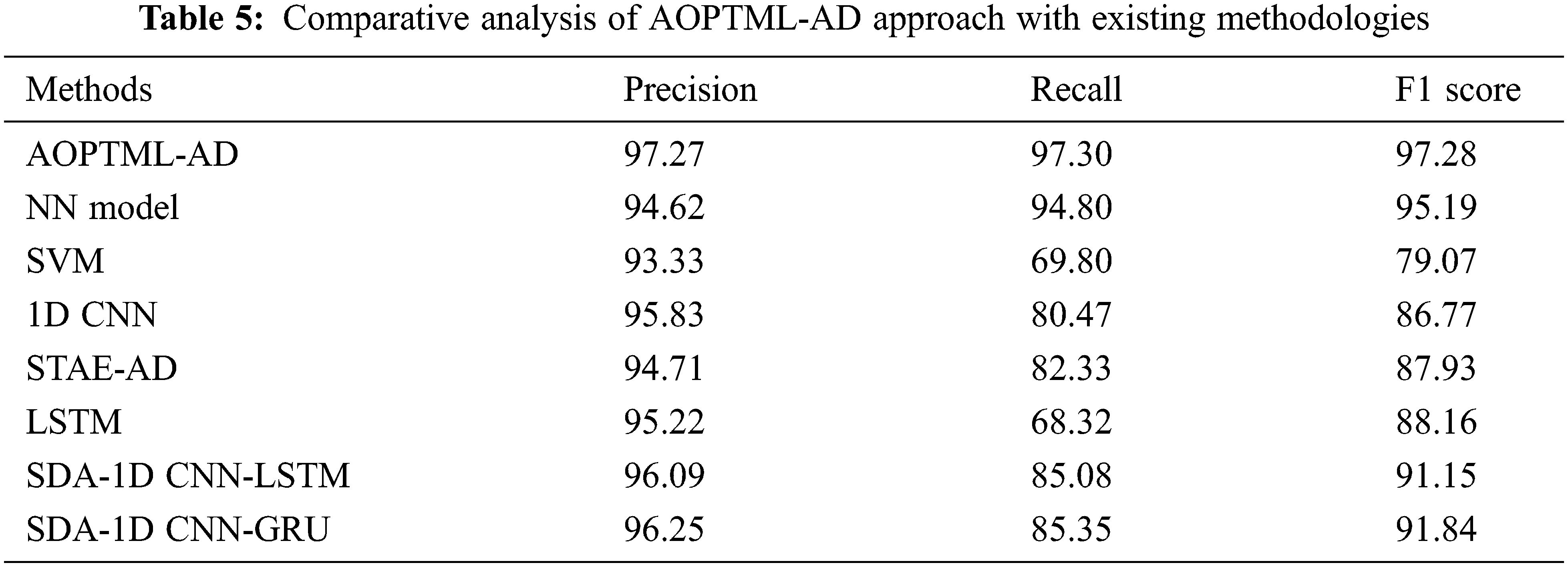
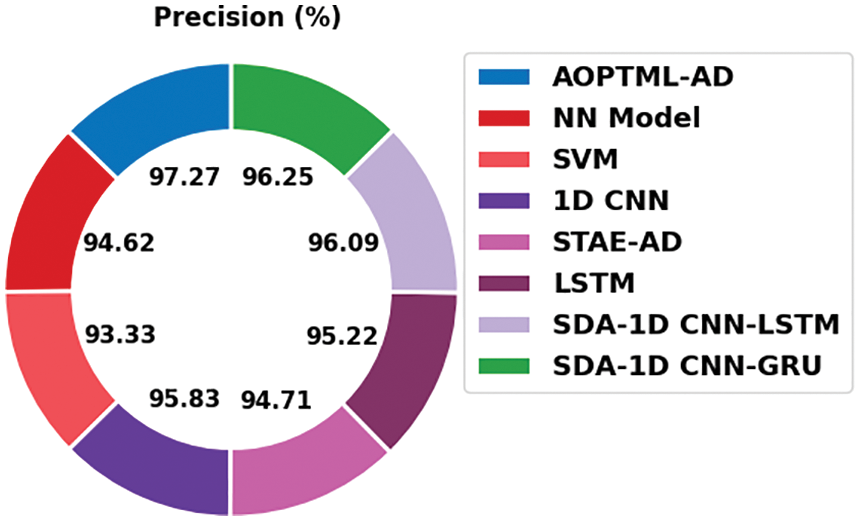
Figure 10:
Fig. 11 provides recent models’ comparative
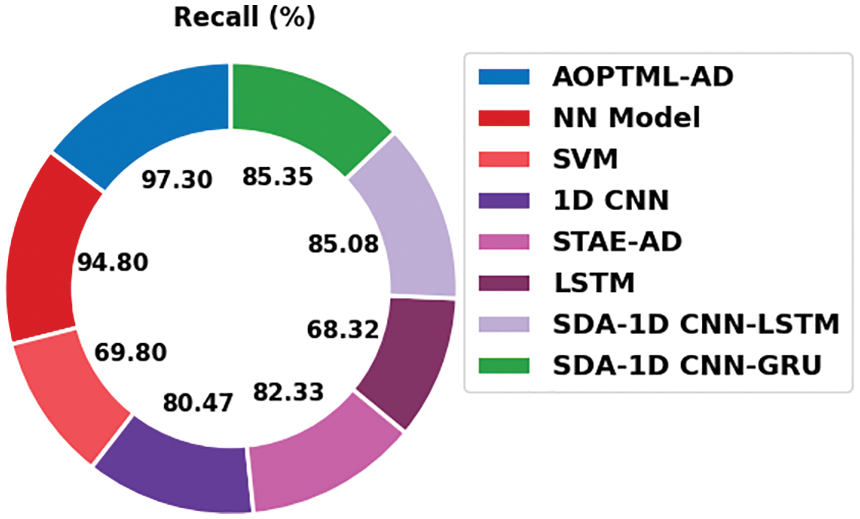
Figure 11:
Fig. 12 grants a detailed
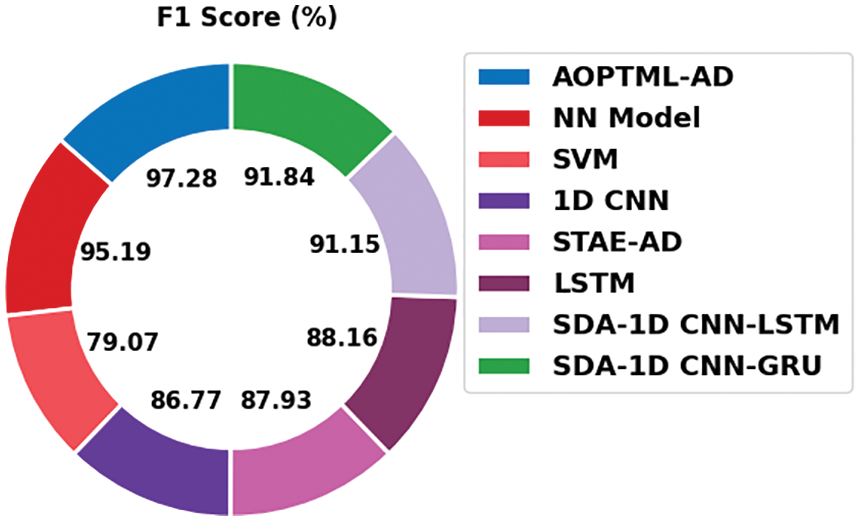
Figure 12:
The detailed results and discussion assume that the AOPTML-AD model has accomplished maximum performance over other models.
In this study, a new AOPTML-AD model intends to recognize and detect anomalous behaviour in the CPS environment. The presented AOPTML-AD framework initially pre-processed the network data by converting them into a compatible format. Followed by the IAOA-FS approach is designed to choose an optimal subset of features. Then, the ChOA with ANFIS model is utilized for the recognition of anomalies in the CPS environment. The ChOA can be applied for optimal adjustment of the MF involved in the ANFIS model. The performance validation of the AOPTML-AD methodology is executed by making use of the benchmark dataset. A detailed result analysis assured the supremacy of the AOPTML-AD approach compared to recent models with an accuracy of 99.37%. In the future, hybrid DL classification models can improve the performance of the proposed model.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. H. M. Rouzbahani, H. Karimipour, A. Rahimnejad, A. Dehghantanha and G. Srivastava, “Anomaly detection in cyber-physical systems using machine learning,” in Handbook of Big Data Privacy, Cham: Springer, pp. 219–235, 2020. [Google Scholar]
2. I. Priyadarshini, A. Alkhayyat, A. Gehlot and R. Kumar, “Time series analysis and anomaly detection for trustworthy smart homes,” Computers and Electrical Engineering, vol. 102, no. 20, pp. 108193, 2022. [Google Scholar]
3. F. S. Mozaffari, H. Karimipour and R. M. Parizi, “Learning based anomaly detection in critical cyber-physical systems,” in Security of Cyber-Physical Systems, Cham: Springer, pp. 107–130, 2020. [Google Scholar]
4. X. Jiang, W. He and T. Han, “Performance analysis and optimization of novel hybrid communication mode for vehicular network,” in 2020 IEEE Int. Conf. on Communication, Networks and Satellite (Comnetsat), Batam, Indonesia, pp. 81–86, 2020. [Google Scholar]
5. T. S. Mohamed, S. Aydin, A. Alkhayyat and R. Q. Malik, “Kalman and Cauchy clustering for anomaly detection based authentication of IoMTs using extreme learning machine,” IET Communications, vol. 2, no. 4, pp. cmu2.12467, 2022. https://doi.org/10.1049/cmu2.12467. [Google Scholar]
6. A. Jones, Z. Kong and C. Belta, “Anomaly detection in cyber-physical systems: A formal methods approach,” in 53rd IEEE Conf. on Decision and Control, Los Angeles, CA, USA, pp. 848–853, 2014. [Google Scholar]
7. M. Keshk, E. Sitnikova, N. Moustafa, J. Hu and I. Khalil, “An integrated framework for privacy-preserving based anomaly detection for cyber-physical systems,” IEEE Transactions on Sustainable Computing, vol. 6, no. 1, pp. 66–79, 2021. [Google Scholar]
8. M. Saez, F. Maturana, K. Barton and D. Tilbury, “Anomaly detection and productivity analysis for cyber-physical systems in manufacturing,” in 2017 13th IEEE Conf. on Automation Science and Engineering (CASE), Xi’an, pp. 23–29, 2017. [Google Scholar]
9. B. Eiteneuer and O. Niggemann, “LSTM for model-based anomaly detection in cyber-physical systems,” arXiv preprint arXiv:2010.15680, 2020. [Google Scholar]
10. P. Wang and M. Govindarasu, “Cyber-physical anomaly detection for power grid with machine learning,” in Industrial Control Systems Security and Resiliency, Cham: Springer, pp. 31–49, 2019. [Google Scholar]
11. S. V. Thiruloga, V. K. Kukkala and S. Pasricha, “TENET: Temporal CNN with attention for anomaly detection in automotive cyber-physical systems,” in 2022 27th Asia and South Pacific Design Automation Conf. (ASP-DAC), Taipei, Taiwan, pp. 326–331, 2022. [Google Scholar]
12. J. Goh, S. Adepu, M. Tan and Z. S. Lee, “Anomaly detection in cyber physical systems using recurrent neural networks,” in 2017 IEEE 18th Int. Symp. on High Assurance Systems Engineering (HASEI), Singapore, pp. 140–145, 2017. [Google Scholar]
13. Y. Luo, Y. Xiao, L. Cheng, G. Peng and D. (Daphne) Yao, “Deep learning-based anomaly detection in cyber-physical systems: Progress and opportunities,” ACM Computing Surveys (CSUR), vol. 54, no. 5, pp. 1–36, 2022. [Google Scholar]
14. S. M. Nagarajan, G. G. Deverajan, A. K. Bashir, R. P. Mahapatra and M. S. Al-Numay, “IADF-CPS: Intelligent anomaly detection framework towards cyber physical systems,” Computer Communications, vol. 188, no. 2, pp. 81–89, 2022. [Google Scholar]
15. L. Xi, R. Wang and Z. J. Haas, “Data-correlation-aware unsupervised deep-learning model for anomaly detection in cyber-physical systems,” IEEE Internet of Things Journal, vol. 9, no. 22, pp. 1, 2022. https://doi.org/10.1109/JIOT.2022.3150048. [Google Scholar]
16. C. Feng and P. Tian, “Time series anomaly detection for cyber-physical systems via neural system identification and bayesian filtering,” in Proc. of the 27th ACM SIGKDD Conf. on Knowledge Discovery & Data Mining, Virtual Event, Singapore, pp. 2858–2867, 2021. [Google Scholar]
17. V. K. Singh and M. Govindarasu, “A cyber-physical anomaly detection for wide-area protection using machine learning,” IEEE Transactions on Smart Grid, vol. 12, no. 4, pp. 3514–3526, 2021. [Google Scholar]
18. A. A. Khan, O. A. Beg, M. Alamaniotis and S. Ahmed, “Intelligent anomaly identification in cyber-physical inverter-based systems,” Electric Power Systems Research, vol. 193, no. 4, pp. 107024, 2021. [Google Scholar]
19. Y. J. Zhang, Y. X. Yan, J. Zhao and Z. -M. Gao, “AOAAO: The hybrid algorithm of arithmetic optimization algorithm with aquila optimizer,” IEEE Access, vol. 10, pp. 10907–10933, 2022. [Google Scholar]
20. M. S. Jalaee, A. G. Nejad, S. A. Jalaee, N. A. Zarin and R. Derakhshani, “A novel hybrid artificial intelligence approach to the future of global coal consumption using whale optimization algorithm and adaptive neuro-fuzzy inference system,” Energies, vol. 15, no. 7, pp. 2578, 2022. [Google Scholar]
21. Z. K. Eisham, M. M. Haque, M. S. Rahman, M. M. Nishat, F. Faisal et al., “Chimp optimization algorithm in multilevel image thresholding and image clustering,” Evolving Systems, vol. 77, no. 8, pp. 195, 2022. https://doi.org/10.1007/s12530-022-09443-3. [Google Scholar]
22. R. Taormina, S. Galelli, N. O. Tippenhauer, E. Salomons, A. Ostfeld et al., “Battle of the attack detection algorithms: Disclosing cyber attacks on water distribution networks,” Journal of Water Resources Planning and Management, vol. 144, no. 8, pp. 04018048, 2018. [Google Scholar]
23. C. M. Paredes, D. M. Castro, V. I. Junquera and A. G. Potes, “Detection and isolation of dos and integrity cyber attacks in cyber-physical systems with a neural network-based architecture,” Electronics, vol. 10, no. 18, pp. 1–28, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools