 Open Access
Open Access
ARTICLE
Enhanced Metaheuristics with Trust Aware Route Selection for Wireless Sensor Networks
1 Department of IT, The University of Technology and Applied Sciences-Ibri, PO Box: 466, Ibri, Postal Code: 516, Sultanate of Oman
2 Chaitanya Bharathi Institute of Technology, Hyderabad, Telangana, India
3 Department of Electrical Engineering, College of Engineering, Jouf University, Saudi Arabia
4 Department of Computer Science and Engineering, Vignan’s Institute of Information Technology, Visakhapatnam, 530049, India
5 School of Electrical and Electronic Engineering, Engineering Campus, Universiti Sains Malaysia, Nibong Tebal, 14300, Penang, Malaysia
* Corresponding Author: Mohamad Khairi Ishak. Email:
Computer Systems Science and Engineering 2023, 46(2), 1431-1445. https://doi.org/10.32604/csse.2023.034421
Received 16 July 2022; Accepted 22 November 2022; Issue published 09 February 2023
Abstract
Recently, a trust system was introduced to enhance security and cooperation between nodes in wireless sensor networks (WSN). In routing, the trust system includes or avoids nodes related to the estimated trust values in the routing function. This article introduces Enhanced Metaheuristics with Trust Aware Secure Route Selection Protocol (EMTA-SRSP) for WSN. The presented EMTA-SRSP technique majorly involves the optimal selection of routes in WSN. To accomplish this, the EMTA-SRSP technique involves the design of an oppositional Aquila optimization algorithm to choose safe routes for data communication. For the clustering process, the nodes with maximum residual energy will be considered cluster heads (CHs). In addition, the OAOA technique gets executed to choose optimal routes based on objective functions with multiple parameters such as energy, distance, and trust degree. The experimental validation of the EMTA-SRSP technique is tested, and the results exhibited a better performance of the EMTA-SRSP technique over other approaches.Keywords
Wireless Sensor Network (WSN) has evolved into one of the promising technologies utilized in the current ecosphere [1]. WSN observes the environments in which it may be placed for collecting data and can identify variations in observing regions of humidity, temperature, sound, vibration pressure, motion, and intensity [2]. WSN application programs are broadly utilized in smart home monitoring systems, environmental observing systems, bridges or building operational monitoring systems, bio-medical applications, military solicitations, inventory management systems, habitat monitoring systems, industrial robotics systems, and health monitoring mechanisms natural disaster monitoring mechanisms, and traffic monitoring system [3].
A wireless network is considered an adaptable gadget meant for data communication. It uses radio frequency algorithms such as wireless channels for sending data via air, eradicating the wired requirements [4]. A common technique for some final transmission phases between the gadgets of wired networks and smartphones is enhancing the cellular network as an alternative one of wired connections [5]. In return, the availability of mass media for broadcasting causes the wireless network to be highly vulnerable to safety menaces. The safety assault is an action that interrupts the machine’s safety in contrast to the unit via an intelligent threat. There may be various types of menaces [6]. The defence menaces are classified as passive and active assaults. Despite various services of safety authentication, counting access management, data completeness, and non-repudiation, encoding of data the assault lasts [7]. Moreover, WSNs are more sensitive as the nodes are recurrently positioned in an uncomfortable range. Even though, several applications routes at the atmospheres which are unreliable that further desire a sheltered routing and transmission [8]. Fig. 1 depicts the overview of WSN.
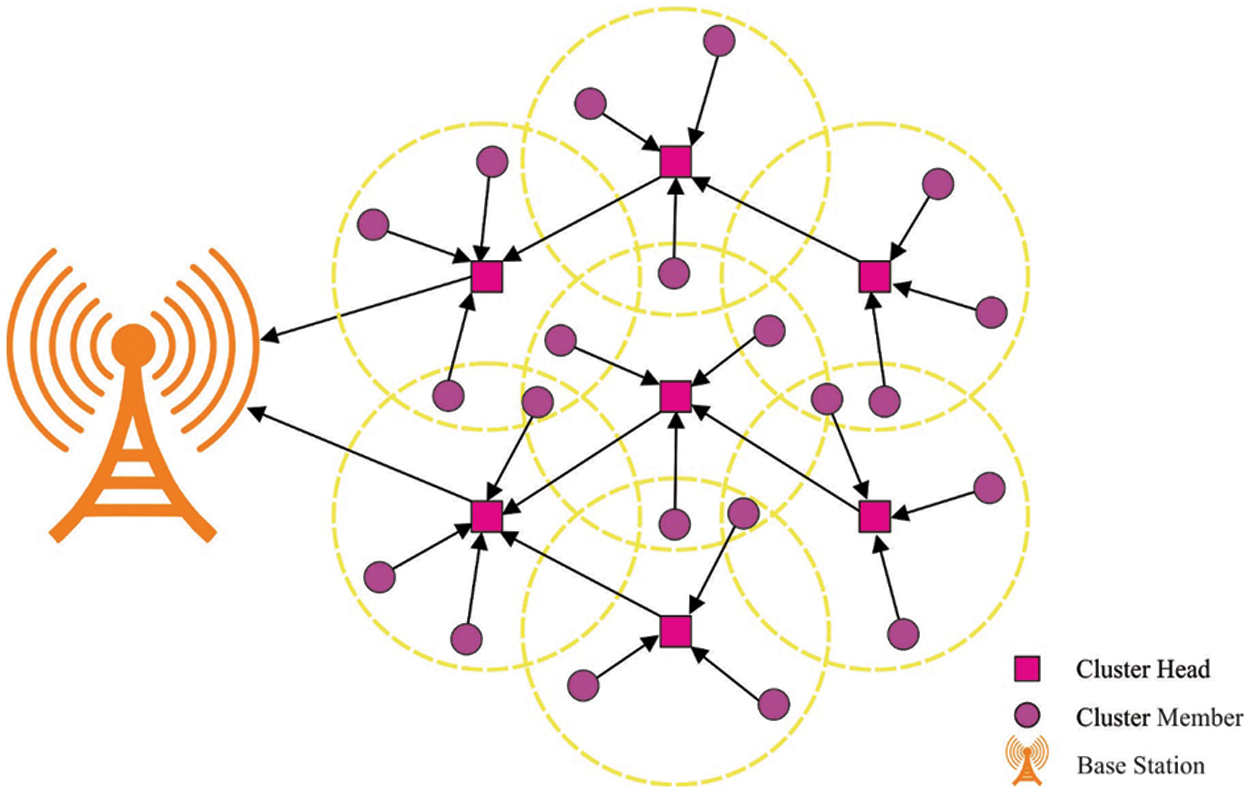
Figure 1: Overview of WSN
Otherwise, the sensor nodes (SN) route the accumulation of data to its transitional nodes that are linked with wireless gadgets for transmitting data against a receiver node. Yet, an appropriate or ideal protocol for routing in an optimum way is suitable for data communication via a few nodes which contain a routing path of multi-hop along with its extent inside them than the receiver [9]. Power utilization should be minimal by considering the delicate decision-making methodologies that rest on the regulations such as nodes clustering and routing to execute a perfect routing function [10]. However, the creation of cluster nodes and selecting the cluster head takes place for every cluster path and routing path, completely over CHs, therefore, diminishing the amount of the contributing node; so far, these grounds decrease in energy utilization. Though several models are available in the literature, it is still needed to design a secure routing protocol in WSN along with the clustering process. In addition, the usage of multiple input parameters for optimal clustering and routing becomes essential in WSN.
This article introduces Enhanced Metaheuristics with Trust Aware Secure Route Selection Protocol (EMTA-SRSP) for WSN. The presented EMTA-SRSP technique involves the design of an oppositional Aquila optimization algorithm to choose secure routes for data communication. For the clustering process, the nodes with maximum residual energy will be considered cluster heads (CHs). In addition, the OAOA technique gets executed to choose optimal routes based on objective functions with multiple parameters such as energy, distance, and trust degree. Since the EMTA-SRSP technique considers the trust level of the nodes, the routes with maximum security will be considered. The experimental validation of the EMTA-SRSP algorithm has been tested in several prospects.
Awan et al. [11] devise an effective routing method by compiling IoT with Blockchain (BC) for distributed nodes that operate in a distributed way for using the transmission links professionally. The presented protocol employs smart contracts in heterogeneous IoT environments for finding a route to BS. Every node could ensure routes from IoT nodes to sink then BS, allowing IoT gadgets to collaborate at the transmission time. The presented routing protocol eliminates redundant data and IoT network assaults, results in lesser energy utilization, and enhances network life. Sanchez et al. [12] introduce a decentralized mechanism that ensures the security and autonomy of an IoT network. The devised technique helps protect data availability and integrity related to the security benefits BC offers and the use of cryptographic tools. The presented approach’s accuracy has been measured on a temperature and humidity-sensed IoT-related WSN. The attained outcomes prove the proposal satisfies the major needs of an IoT network. It is autonomous, secure for sharing and sending information among users and gadgets, has privacy, is dependable, and the data can be accessible in the infrastructure.
A new trust-aware localized routing and class-related dynamic encryption method were offered in [13]. The technique initially finds the route to attaining the destiny and sends the data packets. By identification of the values of such variables, the value of trusted data forwarding support (TDFS) can be measured. Amjad et al. [14] modelled distance, degrees, and remaining energy-related low-energy adaptive clustering hierarchy (DDR-LEACH) protocols. DDR-LEACH can be employed for replacing CHs with the ordinary node depending on maximal RE, degree, and minimal distance from BS. In addition, saving a vast amount of data in BC can be expensive. An external data storage, called an interplanetary file system (IPFS), can be used to deal with this problem. Moreover, to ensure data security in IPFS, AES 128-bit was employed, which executes superior to the prevailing encryption methods.
An effectual real-time service-centric feature-sensitivity-analysis (RSFSA) method can be presented in [15]. The RSFSA algorithm examines the sensitivity of distinct features accessed through any service at many levels. At every stage, the technique verifies the feature set is accessed and the number of features the users have granted accessibility for computing the FLAG value for the user respective to the profile given. Depending on the value of FLAG, the users may be provided or denied access to the service. In contrast, the technique manages various encryption methods and keys for every feature level. Elhoseny et al. [16] aim to devise an IoT solution for AI-assisted privacy preservation with big data transmitting utilizing BC. Initially, the presented method employs a graph-modeling to advance a reliable and scalable system to collect and transmit data. Then, symmetric-related digital certificates were used to offer authentic and confidential communication with communication sources utilizing BC.
This article introduced a novel EMTA-SRSP algorithm for security in WSN. The presented EMTA-SRSP technique involves the optimal selection of safe routes in WSN. To accomplish this, the EMTA-SRSP technique involves the design of an oppositional Aquila optimization algorithm to choose secure routes for data communication. For the clustering process, the nodes with maximum residual energy will be considered CHs. In addition, the OAOA technique is executed to choose optimal routes based on objective functions with multiple parameters such as energy, distance, and trust degree.
All the sensors in the network have preliminary energy as
Consequently, energy dissipation through nodes when transmitting Ubytes of a dataset is characterized by,
From the expression,
In Eq. (4),
But the dissipated energy through the receiver afterwards receiving Ubytes of a dataset through CH is characterized by,
Afterwards, receiving or transmitting Ubytes of the dataset, the energy values of every node
The data transmission technique continues; each node is assumed to be a dead node. The node is assumed to be a dead node as long as the node has an energy which is lesser than 0.
In this work, the OAOA technique is designed using oppositional-based learning (OBL) with AOA. The AOA methodology is a novel swarm intelligence (SI) technique [18]. There exist 4 hunting approaches of Aquila; for a variety of prey, Aquila could adaptably shift the hunting approaches for dissimilar prey and then utilize faster speed integrated into claws and sturdy feet to attack the target. The overview of the arithmetic formula is illustrated below.
Step 1: Extended exploration (
The Aquila flies above the ground level and broadly examines the searching region, following a vertical dive taken while describing the prey region. These behaviours are arithmetically formulated by the following formula:
Now,
Step 2: Narrowed exploration (
It is a popular hunting methodology for Aquila. It employs shorter gliding for attacking the target afterwards, a descendant with the selected region, and flying nearby the prey, and it is represented as follows:
Here,
Let s and
Now,
Step 3: Expanded exploitation
Once the prey area is identified normally, the Aquila begins implementing an initial attack. AOA employs the designated location for approaching and attacking the target. These behaviours are arithmetically expressed as follows:
Now,
Step 4: Narrowed exploitation
Now, the Aquila hunts the target regarding attacking the prey and escape trajectory and it is arithmetically formulated in the following:
Now,
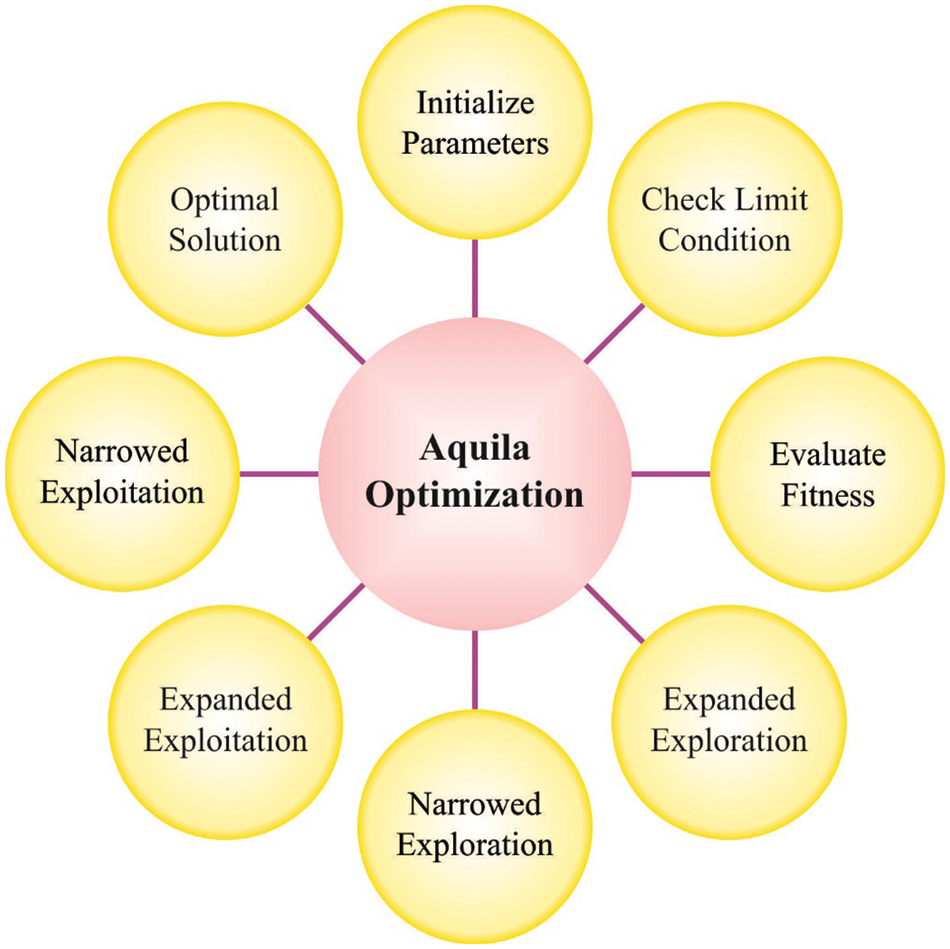
Figure 2: Processes involved in the AO technique
The OAOA is derived by using the oppositional-based learning (OBL) concept. OBL is a novel intelligent optimization technique [19]. The idea of reverse learning is to deliberate reverse and forward solutions, choose the optimum solution as the initialized population and initiate the population through reverse learning that could extend the searching interval of the population. Also, it improves the efficiency and speed of the model to search for the optimum solution. Presently, afterwards opposition based learning was developed,
The inverse solution is formulated using Eq. (17):
where
In Eq. (18), k is a uniformly distributed arbitrary value among zero, and one viz., a common inverse factor,
3.3 Trust-Aware Route Selection Process
In this study, the OAOA technique gets executed to choose optimal routes based on objective function with multiple parameters such as energy, distance, and trust degree. The OAOA aimed to extend the network lifespan and diminish the energy utilization of every sensor. Assume
Consider
Subjected to,
The constraints (21) state that the next hop node of CHi lies in the interval of CHi, and the next hop node is
The proposed model is simulated using the MATLAB tool. In this section, the performance of the EMTA-SRSP model is investigated under varying aspects. Table 1 and Fig. 3 provide packet delay (PDEL) examination of the EMTA-SRSP model with other models [4]. The results reported that the EMTA-SRSP model had enhanced results under all nodes. For example, with 500 nodes, the EMTA-SRSP model has presented a lower PDEL of 230 s, whereas the PSO and TDRS-WSN-DL models have obtained higher PDEL of 425 and 352 s correspondingly. Meanwhile, with 1000 nodes, the EMTA-SRSP method has offered a lower PDEL of 221 s, whereas the PSO and TDRS-WSN-DL algorithms have attained higher PDEL of 377 and 307 s correspondingly.
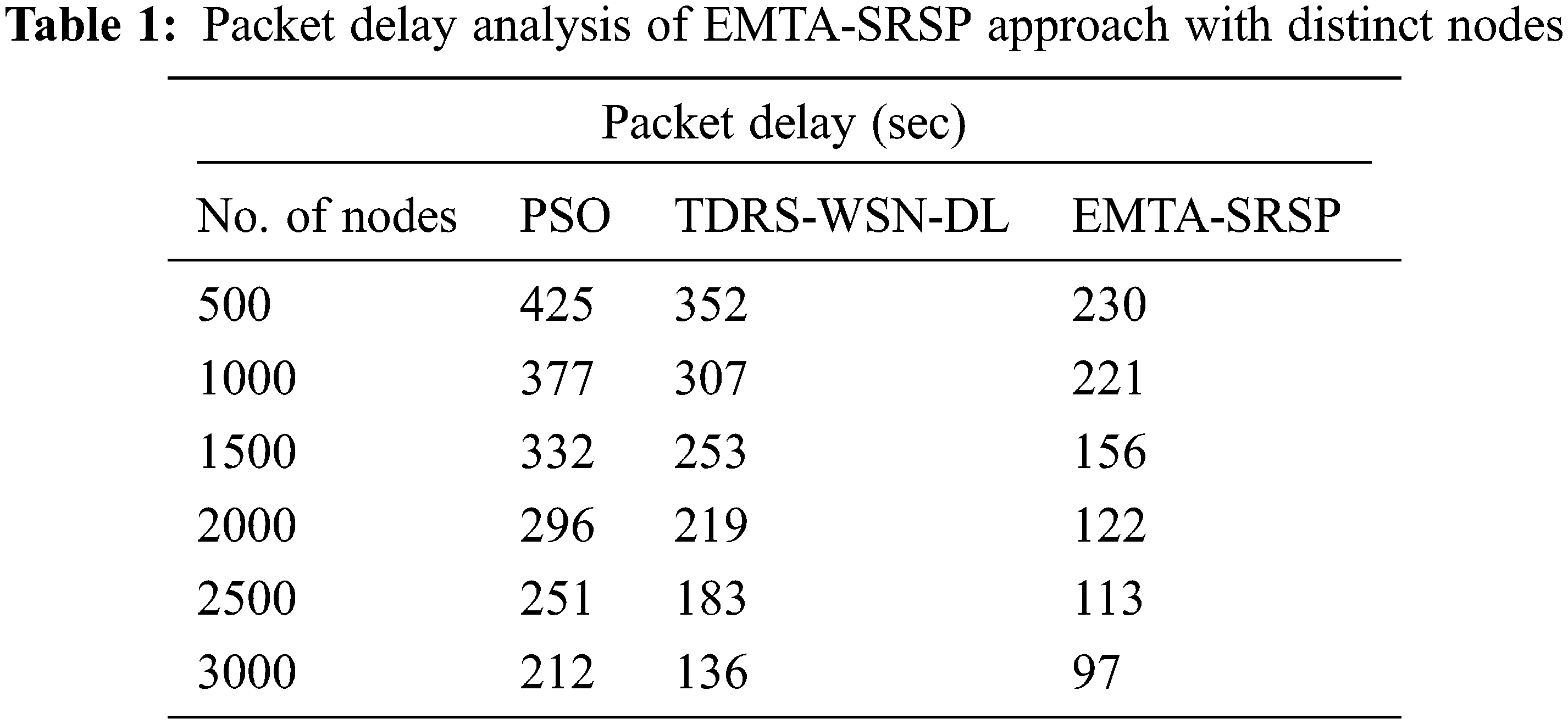
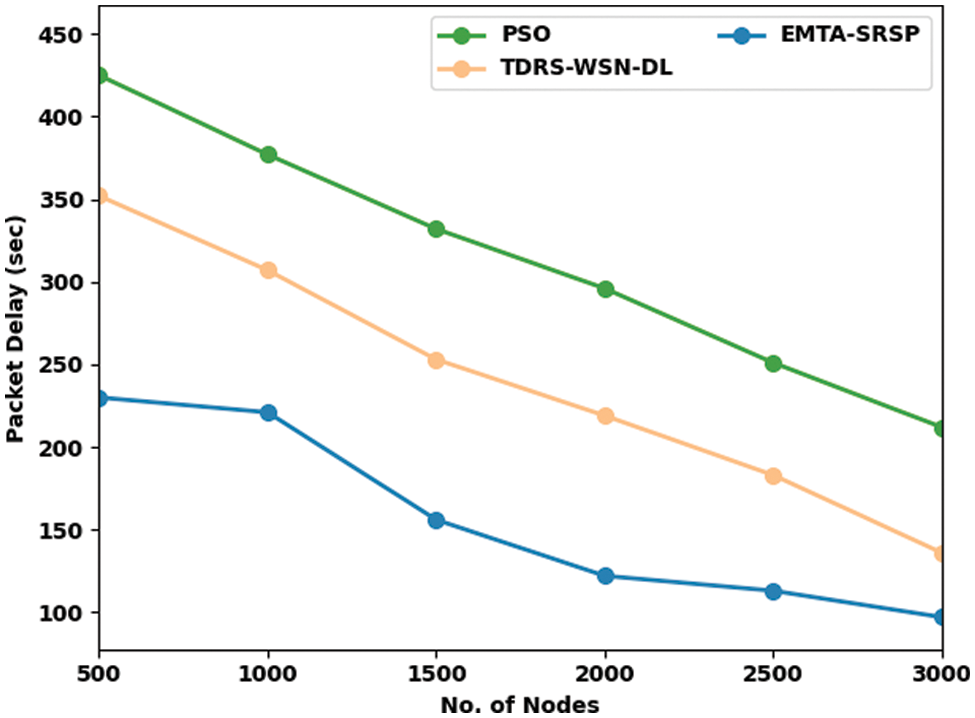
Figure 3: Packet delay analysis of EMTA-SRSP approach with distinct nodes
In addition, with 1500 nodes, the EMTA-SRSP approach has rendered a lower PDEL of 156 s, whereas the PSO and TDRS-WSN-DL models have acquired higher PDEL of 332 and 253 s correspondingly. Then, with 2000 nodes, the EMTA-SRSP model presented a lower PDEL of 122 s, whereas the PSO and TDRS-WSN-DL methodologies have attained higher PDEL of 296 and 219 s correspondingly.
In Table 2 and Fig. 4, a comprehensive packet delivery ratio (PDR) investigation of the EMTA-SRSP model with recent models occurs. The results ensured that the EMTA-SRSP model had shown higher PDR values under each node. For example, with 500 nodes, the EMTA-SRSP method has gained a maximum PDR of 0.966 bps, while the PSO and TDRS-WSN-DL models have attained a minimal PDR of 0.693 and 0.892 bps, correspondingly. Similarly, with 1000 nodes, the EMTA-SRSP method has attained a maximum PDR of 0.942 bps, whereas the PSO and TDRS-WSN-DL approaches have attained a minimal PDR of 0.668 and 0.863 bps correspondingly. Also, with 1500 nodes, the EMTA-SRSP algorithm has obtained a maximum PDR of 0.884 bps while the PSO and TDRS-WSN-DL approaches have attained minimal PDR of 0.585 and 0.767 bps correspondingly. At last, with 2000 nodes, the EMTA-SRSP method has attained a maximum PDR of 0.788 bps whereas the PSO and TDRS-WSN-DL models have attained minimal PDR of 0.531 and 0.668 bps correspondingly.
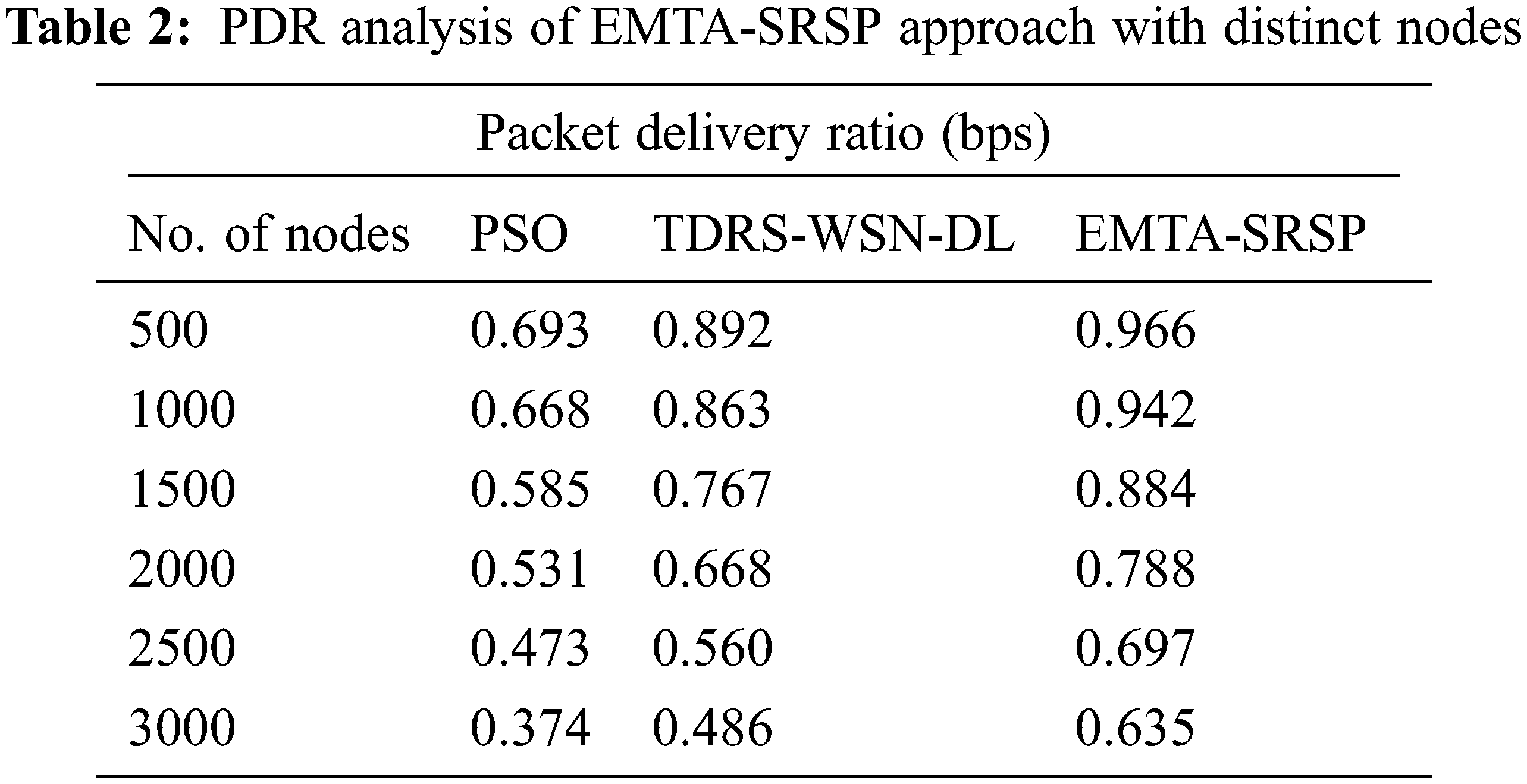
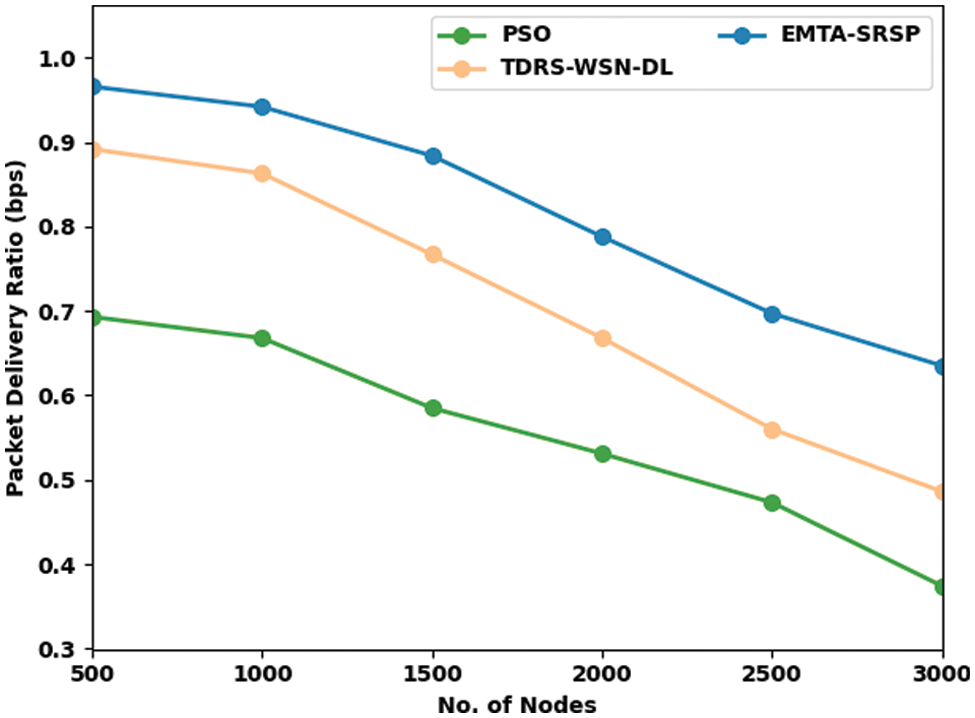
Figure 4: PDR analysis of EMTA-SRSP approach with distinct nodes
In Table 3 and Fig. 5, a comprehensive Packet drop (PDROP) study of the EMTA-SRSP algorithm with recent models occurs. The results ensured that the EMTA-SRSP approach displayed higher PDROP values under each node. For example, with 500 nodes, the EMTA-SRSP approach has attained a maximum PDROP of 40 p/s whereas the PSO and TDRS-WSN-DL approaches have attained minimal PDROP of 86 and 56 p/s correspondingly. Similarly, with 1000 nodes, the EMTA-SRSP method has obtained a maximum PDROP of 42 p/s whereas the PSO and TDRS-WSN-DL approaches have attained minimal PDROP of 92 and 63 p/s correspondingly. Also, with 1500 nodes, the EMTA-SRSP approach has achieved a maximal PDROP of 47 p/s whereas the PSO and TDRS-WSN-DL approaches have attained minimal PDROP of 103 and 71 p/s correspondingly. At last, with 2000 nodes, the EMTA-SRSP model has obtained a maximum PDROP of 54 p/s whereas the PSO and TDRS-WSN-DL models have gained minimal PDROP of 109 and 78 p/s correspondingly.
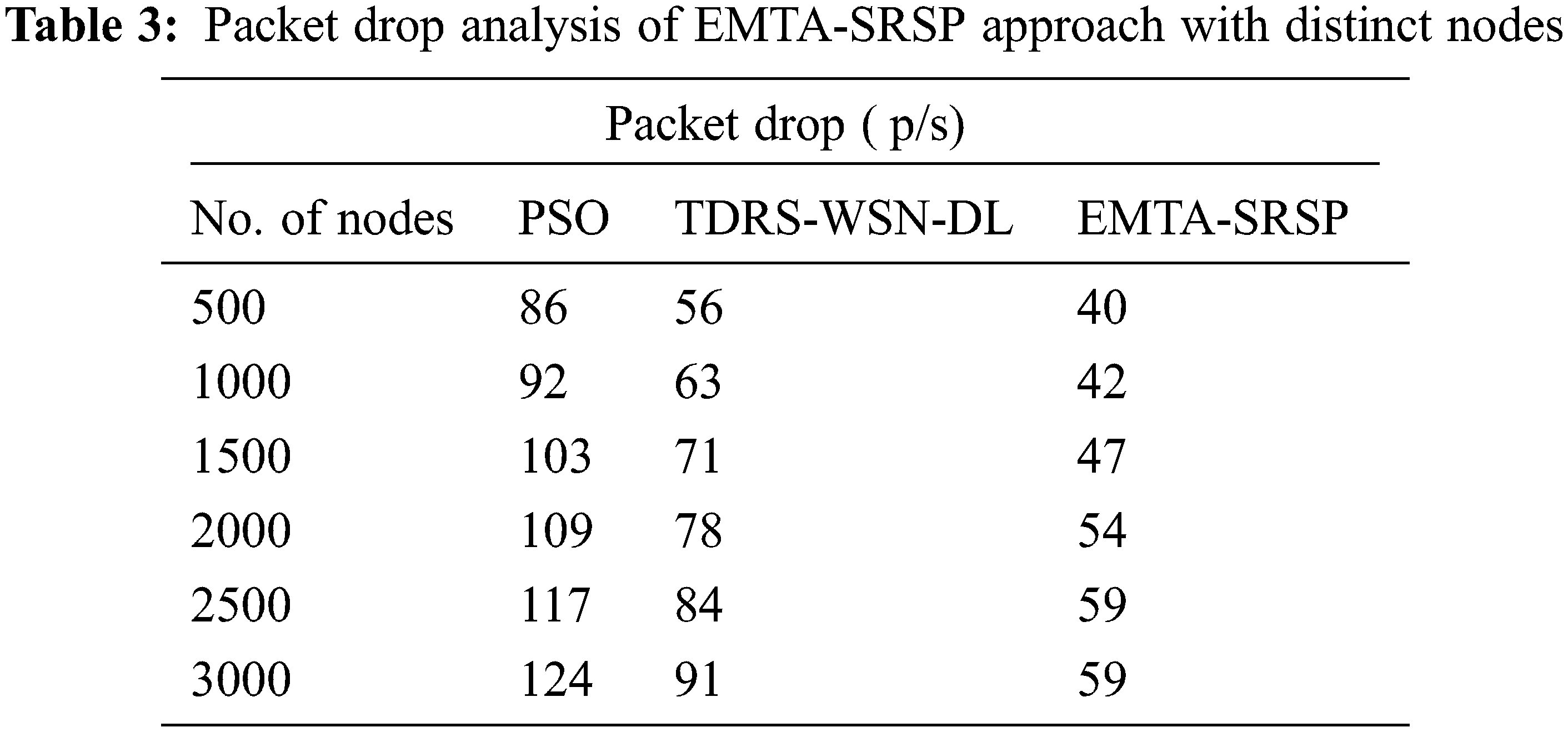
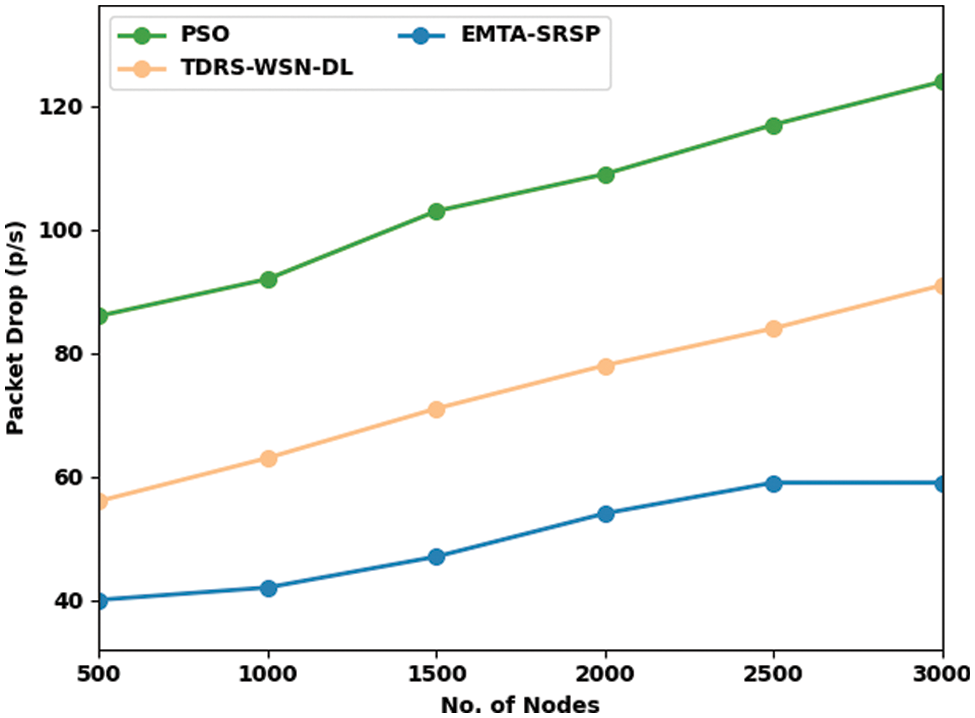
Figure 5: Packet drop analysis of EMTA-SRSP approach with distinct nodes
In Table 4 and Fig. 6, a comprehensive Energy Consumption (ECOM) examination of the EMTA-SRSP method with recent models takes place. The results ensured that the EMTA-SRSP model had shown higher ECOM values under each node. For example, with 500 nodes, the EMTA-SRSP model has achieved a maximal ECOM of 0.28j while the PSO and TDRS-WSN-DL techniques have attained minimal ECOM of 1.59 and 0.65j respectively. Similarly, with 1000 nodes, the EMTA-SRSP model has gained a maximal ECOM of 0.73j whereas the PSO and TDRS-WSN-DL models have attained minimal ECOM of 3.26 and 1.79j correspondingly. Also, with 1500 nodes, the EMTA-SRSP methodology has gained a maximum ECOM of 1.30j whereas the PSO and TDRS-WSN-DL algorithms have attained minimal ECOM of 5.47 and 2.65j correspondingly. Finally, with 2000 nodes, the EMTA-SRSP model has gained a maximum ECOM of 2.04j whereas the PSO and TDRS-WSN-DL models have attained minimal ECOM of 7.84 and 3.75j correspondingly.
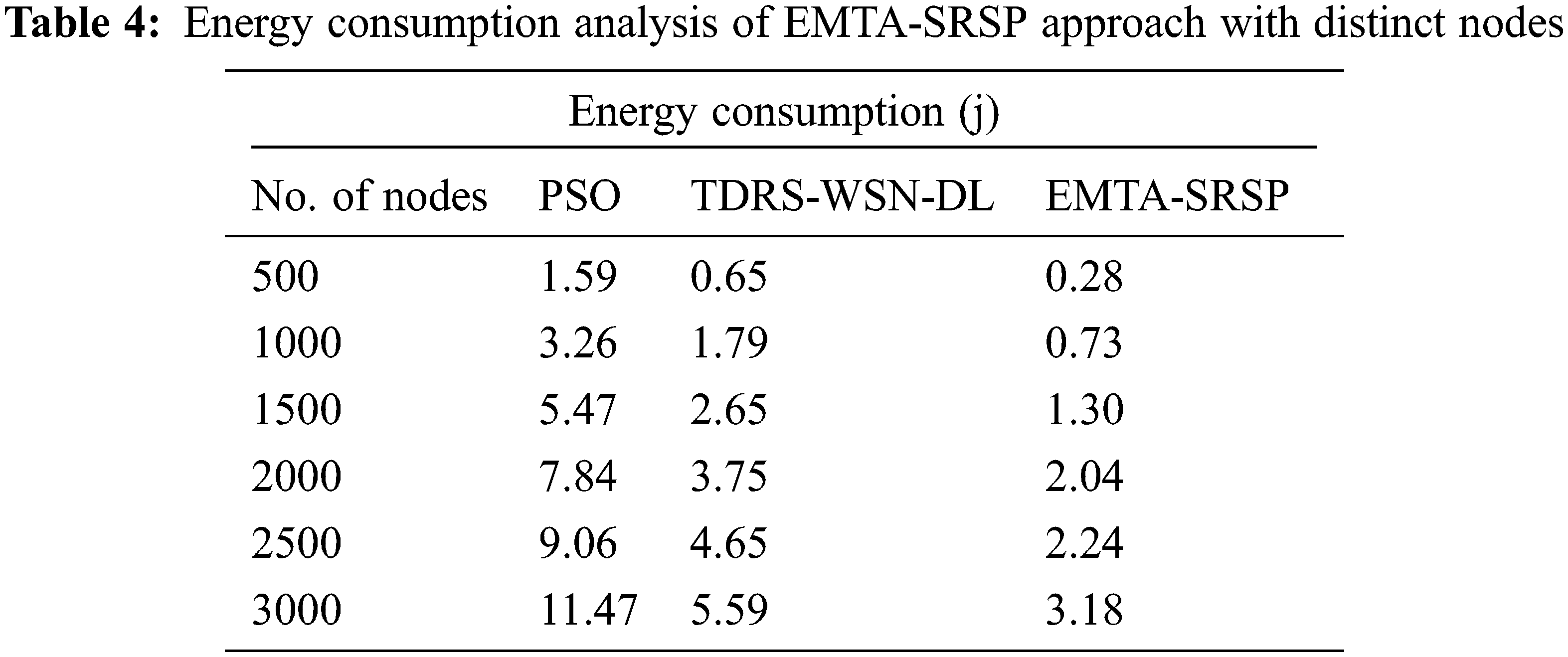
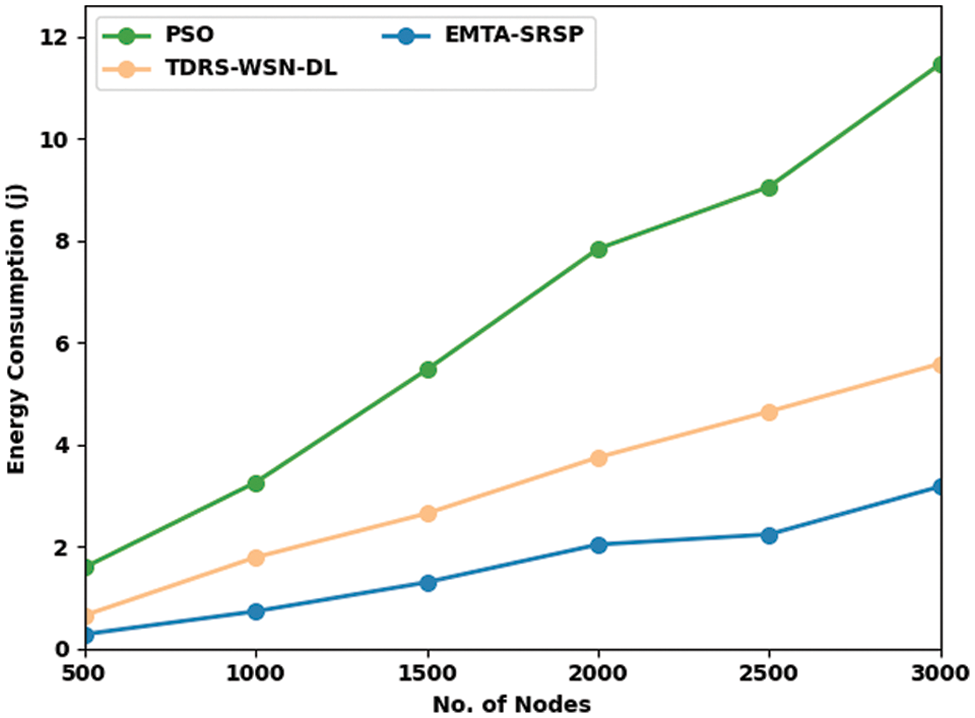
Figure 6: ECOM analysis of EMTA-SRSP approach with distinct nodes
In Table 5 and Fig. 7, a wide-ranging Latency (LAT) analysis of the EMTA-SRSP algorithm with recent models occurs. The results assured the EMTA-SRSP model had shown higher LAT values under all nodes. For example, with 500 nodes, the EMTA-SRSP model has gained maximum LAT of 0.216 bps whereas the PSO and TDRS-WSN-DL models have attained minimal LAT of 0.599 and 0.288 bps correspondingly. Likewise, with 1000 nodes, the EMTA-SRSP model has gained maximum LAT of 0.243 bps, whereas the PSO and TDRS-WSN-DL models have attained minimal LAT of 0.609 and 0.366 bps, respectively. Besides, with 1500 nodes, the EMTA-SRSP approach has acquired maximal LAT of 0.274 bps whereas the PSO and TDRS-WSN-DL models have gained minimal LAT of 0.644 and 0.418 bps correspondingly. Finally, with 2000 nodes, the EMTA-SRSP model has achieved a maximum LAT of 0.315 bps whereas the PSO and TDRS-WSN-DL models have obtained minimal LAT of 0.661 and 0.496 bps, correspondingly.
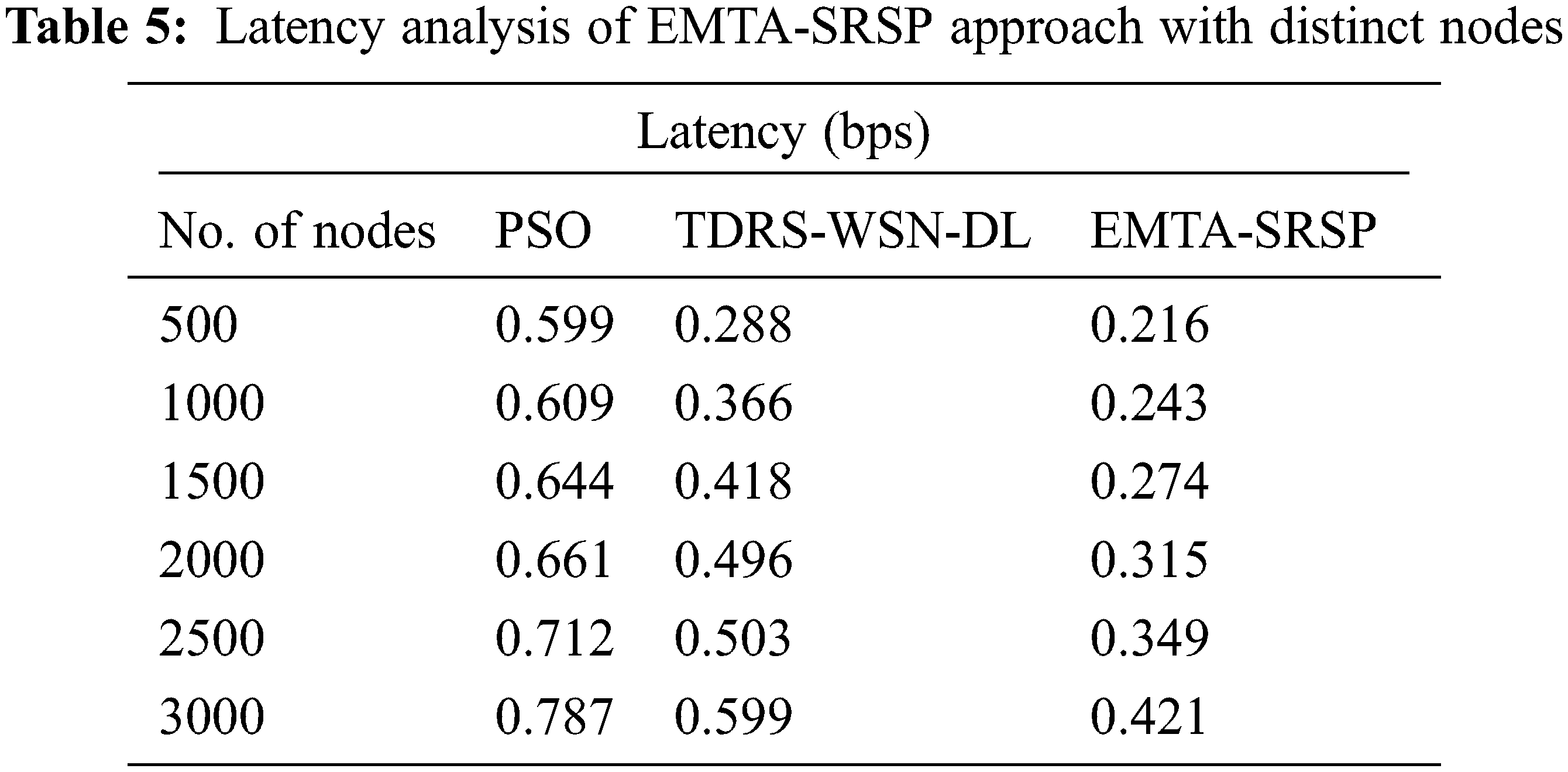
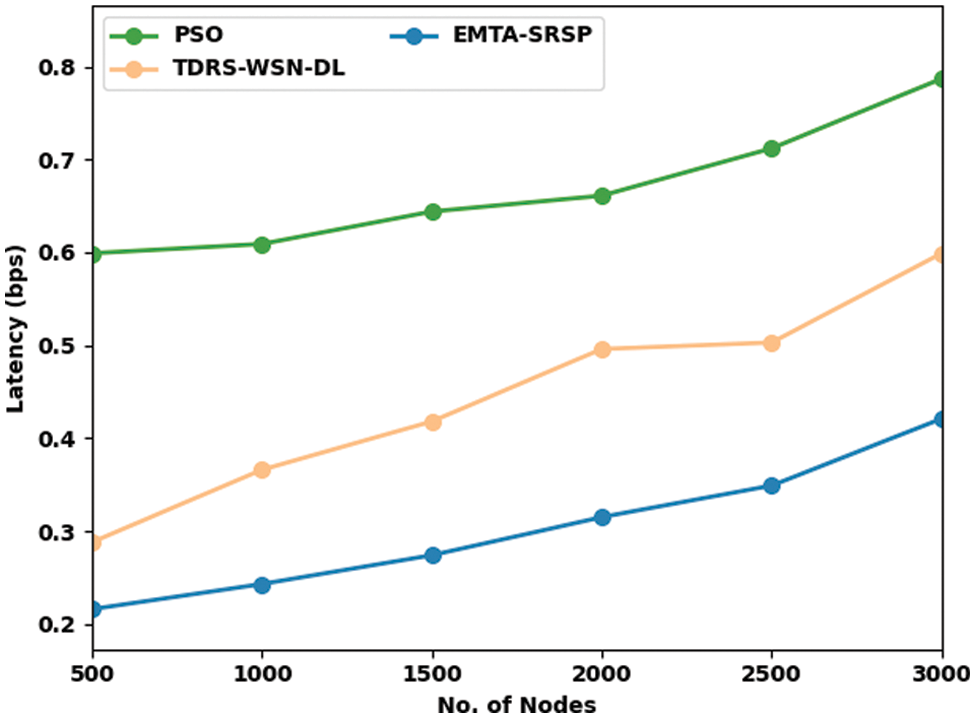
Figure 7: Latency analysis of EMTA-SRSP approach with distinct nodes
In Table 6 and Fig. 8, a widespread Throughput (THROU) investigation of the EMTA-SRSP model with recent models occurs. The results implicit in the EMTA-SRSP algorithm have shown higher THROU values under each node. For example, with 500 nodes, the EMTA-SRSP model has achieved a maximal THROU of 1514 bps whereas the PSO and TDRS-WSN-DL models have gained minimal THROU of 954 and 1265 bps correspondingly. Likewise, with 1000 nodes, the EMTA-SRSP approach has acquired a maximum THROU of 1711 bps whereas the PSO and TDRS-WSN-DL algorithms have reached a minimal PDR of 1141 and 1141 bps correspondingly. Moreover, with 1500 nodes, the EMTA-SRSP technique has achieved maximal THROU of 1898 bps while the PSO and TDRS-WSN-DL models have attained minimal THROU of 1317 and 1638 bps correspondingly. At last, with 2000 nodes, the EMTA-SRSP approach has reached a maximum THROU of 2053 bps whereas the PSO and TDRS-WSN-DL techniques have attained minimal THROU of 1493 and 1804 bps correspondingly.
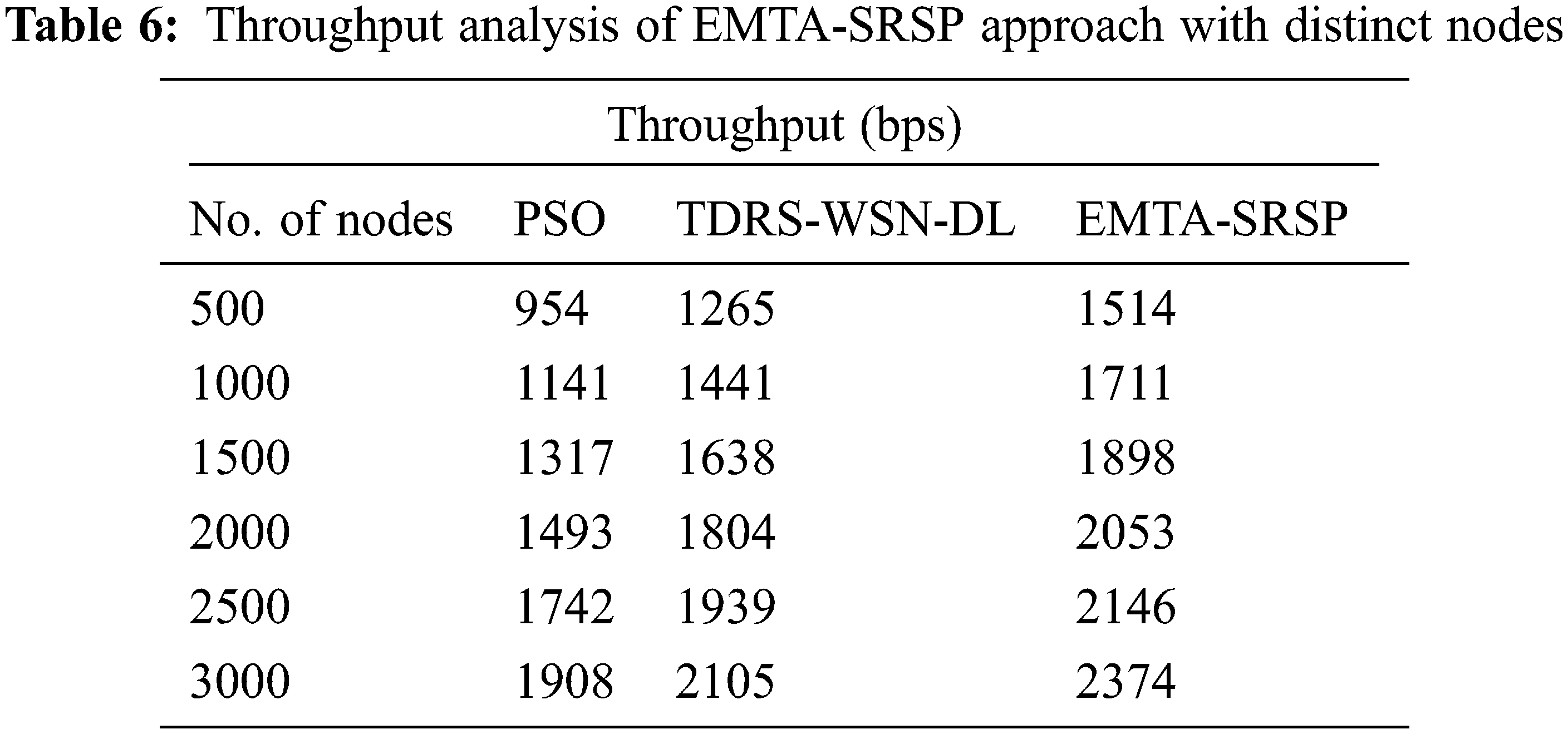
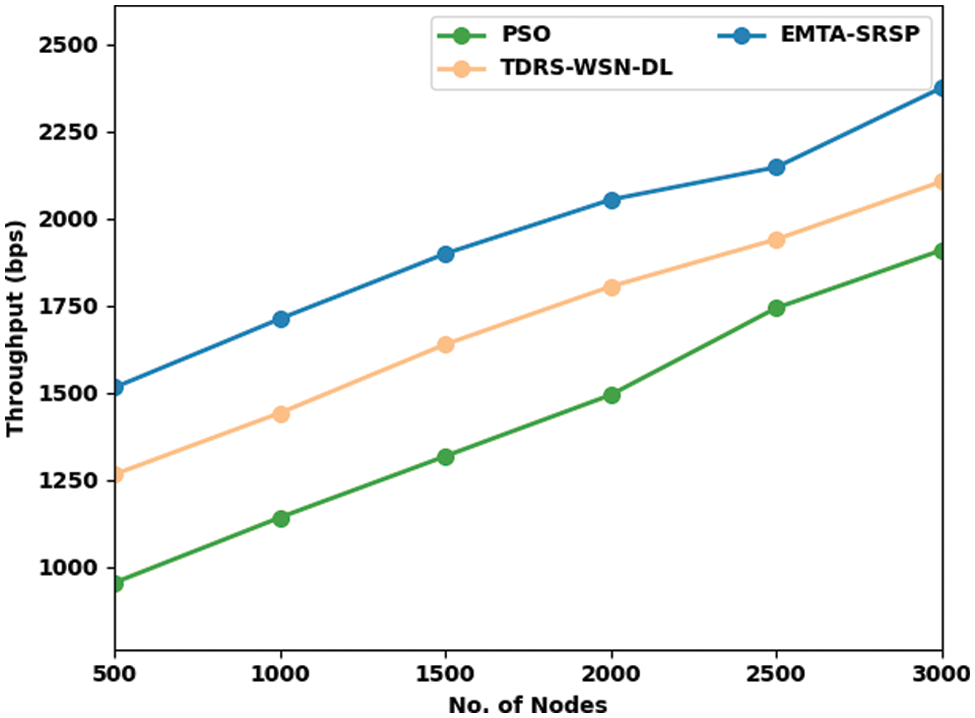
Figure 8: Throughput analysis of EMTA-SRSP approach with distinct nodes
In Table 7 and Fig. 9, a comprehensive Cluster Overhead (COH) inquiry of the EMTA-SRSP model with recent models take place. The results denoted the EMTA-SRSP methodology has shown higher COH values under each node. For example, with 500 nodes, the EMTA-SRSP method has reached a maximum COH of 790 p/s whereas the PSO and TDRS-WSN-DL models have attained minimal COH of 1170 and 980 p/s correspondingly.
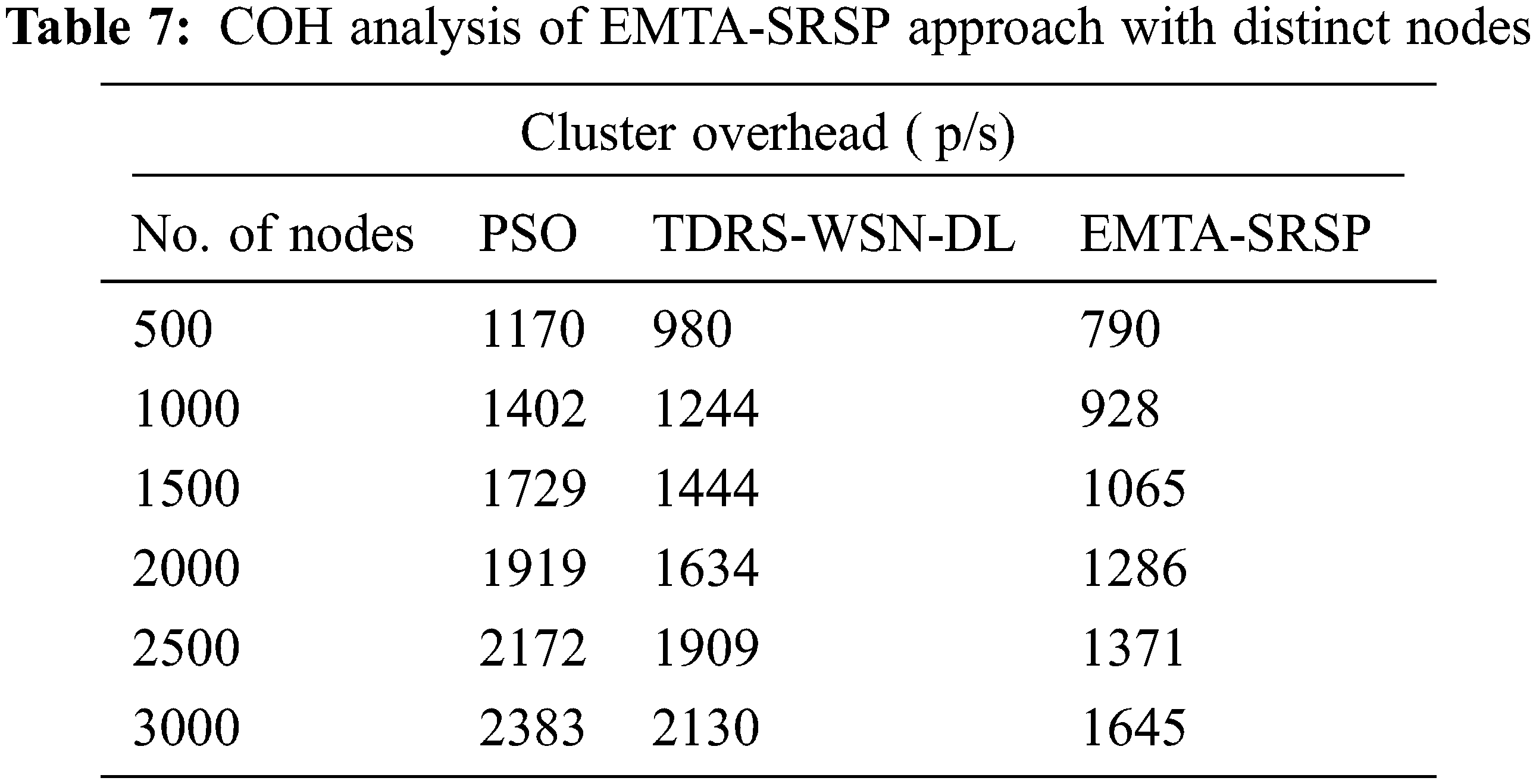
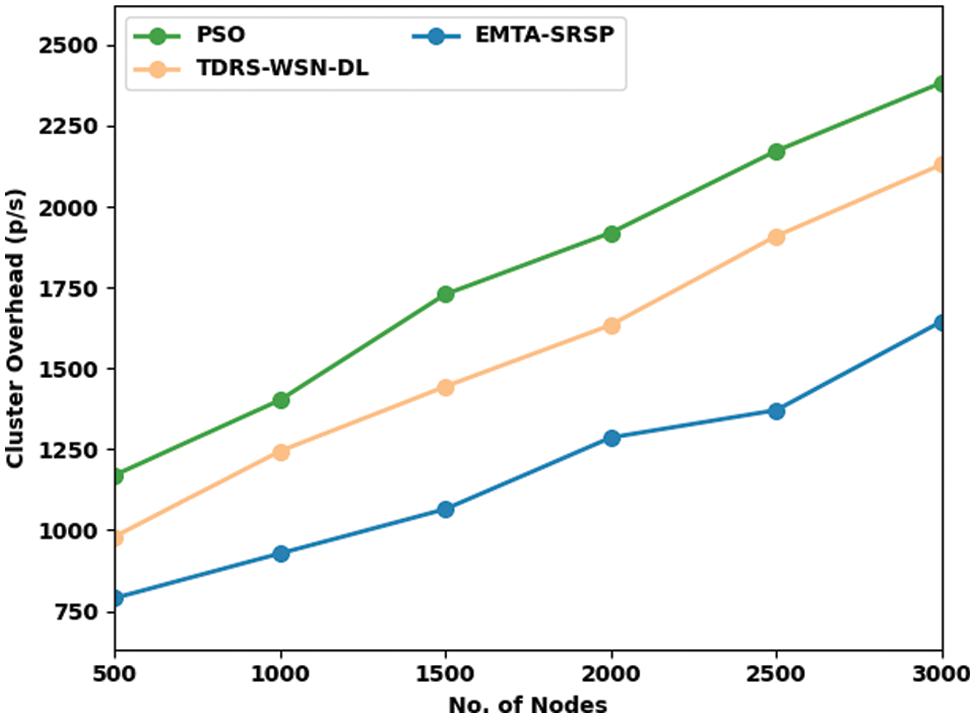
Figure 9: COH analysis of EMTA-SRSP approach with distinct nodes
Similarly, with 1000 nodes, the EMTA-SRSP approach has obtained a maximum COH of 928 p/s whereas the PSO and TDRS-WSN-DL models have attained minimal COH of 1402 and 1244 p/s correspondingly. Also, with 1500 nodes, the EMTA-SRSP algorithm has obtained maximal COH of 1065 p/s whereas the PSO and TDRS-WSN-DL approaches have attained minimal COH of 1729 and 1444 p/s correspondingly. At last, with 2000 nodes, the EMTA-SRSP model has gained a maximum COH of 1286 p/s whereas the PSO and TDRS-WSN-DL models have attained minimal COH of 1919 and 1634 p/s correspondingly.
In this article, a novel EMTA-SRSP technique has been introduced for security in WSN. The presented EMTA-SRSP technique majorly involves the optimal selection of secure routes in WSN. To accomplish this, the EMTA-SRSP technique involves the design of an oppositional Aquila optimization algorithm to choose secure routes for data communication. For the clustering process, the nodes with maximum residual energy will be considered as CHs. In addition, the OAOA technique gets executed to choose optimal routes, based on objective functions with multiple parameters such as energy, distance, and trust degree. Since the EMTA-SRSP technique considered the trust level of the nodes, the routes with maximum security will be chosen into account. The proposed model can be employed in real-time applications such as environmental monitoring, smart cities, fault diagnosis, etc. The experimental validation of the EMTA-SRSP technique is tested and the results exhibited a better performance of the EMTA-SRSP technique over other approaches. In future, the performances of the EMTA-SRSP method can be enhanced using data aggregation techniques.
Acknowledgement: The authors would like to thank Universiti Sains Malaysia (USM) and the Ministry of Higher Education Malaysia for providing the research grant, Fundamental Research GrantScheme (FRGS-Grant No: FRGS/1/2020/TK0/USM/02/1) that helped to carry out this research.
Funding Statement: This research was supported by the Universiti Sains Malaysia (USM) and the Ministry of Higher Education Malaysia through Fundamental Research GrantScheme (FRGS-Grant No: FRGS/1/2020/TK0/USM/02/1).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. H. Lazrag, A. Chehri, R. Saadane and M. D. Rahmani, “Efficient and secure routing protocol based on blockchain approach for wireless sensor networks,” Concurrency and Computation: Practice and Experience, vol. 33, no. 22, pp. e6144, 2021. [Google Scholar]
2. J. Yang, S. He, Y. Xu, L. Chen and J. Ren, “A trusted routing scheme using blockchain and reinforcement learning for wireless sensor networks,” Sensors, vol. 19, no. 4, pp. 970, 2019. [Google Scholar]
3. S. Awan, N. Javaid, S. Ullah, A. Khan, A. Qamar et al., “Blockchain based secure routing and trust management in wireless sensor networks,” Sensors, vol. 22, no. 2, pp. 411, 2022. [Google Scholar]
4. M. Revanesh and V. Sridhar, “A trusted distributed routing scheme for wireless sensor networks using blockchain and meta-heuristics-based deep learning technique,” Transactions on Emerging Telecommunications Technologies, vol. 32, no. 9, pp. 1–19, 2021. [Google Scholar]
5. O. I. Khalaf and G. M. Abdulsahib, “Optimized dynamic storage of data (ODSD) in IoT based on blockchain for wireless sensor networks,” Peer-to-Peer Networking and Applications, vol. 14, no. 5, pp. 2858–2873, 2021. [Google Scholar]
6. H. Trabelsi, A. Guermazi and W. Jerbi, “A novel secure routing protocol of generation and management cryptographic keys for wireless sensor networks deployed in internet of things,” International Journal of High Performance, vol. 16, no. 2/3, pp. 87, 2020. [Google Scholar]
7. A. M. Srivastava, P. A. Rotte, A. Jain, and S. Prakash, “Handling data scarcity through data augmentation in training of deep neural networks for 3D data processing,” International Journal on Semantic Web and Information Systems, vol. 18, no. 1, pp. 1–16, 2022. [Google Scholar]
8. J. Chu, X. Zhao, D. Song, W. Li, S. Zhang et al., “Improved semantic representation learning by multiple clustering for image-based 3D model retrieval,” International Journal on Semantic Web and Information Systems, vol. 18, no. 1, pp. 1–20, 2022. [Google Scholar]
9. N. Tariq, M. Asim, F. Al-Obeidat, M. Z. Farooqi, T. Baker et al., “The security of big data in fog-enabled IoT applications including blockchain: A survey,” Sensors, vol. 19, no. 8, pp. 1788, 2019. [Google Scholar]
10. R. Bharanidharan, “A novel blockchain approach for improve the performance of network security using polynomial ephemeral blockchain-based secure routing in wireless sensor network,” Journal of Computational and Theoretical Nanoscience, vol. 17, no. 12, pp. 5598–5604, 2020. [Google Scholar]
11. S. H. Awan, S. Ahmed, A. Nawaz, S. Sulaiman, K. Zaman et al., “BlockChain with IoT, an emergent routing scheme for smart agriculture,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 4, pp. 420–429, 2020. [Google Scholar]
12. A. E. G. Sanchez, E. A. R. Araiza, J. L. G. Cordoba, M. T. Ayala and A. Takacs, “Blockchain mechanism and symmetric encryption in a wireless sensor network,” Sensors, vol. 20, no. 10, pp. 2798, 2020. [Google Scholar]
13. M. H. Kumar, V. Mohanraj, Y. Suresh, J. Senthilkumar and G. Nagalalli, “Trust aware localized routing and class-based dynamic blockchain encryption scheme for improved security in WSN,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 5, pp. 5287–5295, 2021. [Google Scholar]
14. S. Amjad, S. Abbas, Z. Abubaker, M. Alsharif, A. Jahid et al., “Blockchain-based authentication and cluster head selection using ddr-leach in internet of sensor things,” Sensors, vol. 22, no. 5, pp. 1972, 2022. [Google Scholar]
15. A. S. Kumar, S. G. Winster and R. Ramesh, “Efficient sensitivity orient blockchain encryption for improved data security in cloud,” Concurrent Engineering, vol. 29, no. 3, pp. 249–257, 2021. [Google Scholar]
16. M. Elhoseny, K. Haseeb, A. A. Shah, I. Ahmad, Z. Jan et al., “IoT solution for ai-enabled privacy-preserving with big data transferring: An application for healthcare using blockchain,” Energies, vol. 14, no. 17, pp. 5364, 2021. [Google Scholar]
17. N. Mittal and U. Singh, “Distance-based residual energy-efficient stable election protocol for WSNs,” Arabian Journal for Science and Engineering, vol. 40, no. 6, pp. 1637–1646, 2015. [Google Scholar]
18. S. Wang, H. Jia, L. Abualigah, Q. Liu and R. Zheng, “An improved hybrid aquila optimizer and harris hawks algorithm for solving industrial engineering optimization problems,” Processes, vol. 9, no. 9, pp. 1551, 2021. [Google Scholar]
19. M. F. Ahmad, N. A. M. Isa, W. H. Lim and K. M. Ang, “Differential evolution with modified initialization scheme using chaotic oppositional based learning strategy,” Alexandria Engineering Journal, vol. 61, no. 12, pp. 11835–11858, 2022. [Google Scholar]
20. J. Duan, D. Yang, H. Zhu, S. Zhang and J. Zhao, “TSRF: A trust-aware secure routing framework in wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 10, no. 1, pp. 209436, 2014. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools