 Open Access
Open Access
ARTICLE
Improved Multi-Path Routing for QoS on MANET
1 Department of Computer Science and Engineering, PSN College of Engineering and Technology, Tirunelveli, 627152, Tamil Nadu, India
2 Department of Information Systems, College of Computer Sciences and Information Technology, King Faisal University, Al Hasa, Saudi Arabia
3 Department of Information Systems, College of Computer and Information Science, Princess Nourah bint Abdulrahman University, P.O. BOX 84428, Riyadh, 11671, Saudi Arabia
4 Department of Computer Science & Engineering, Swami Keshvanand Institute of Technology, Management & Gramothan (SKIT), Jaipur, 302017, Rajasthan, India
* Corresponding Author: M. Vargheese. Email:
Computer Systems Science and Engineering 2023, 45(3), 2521-2536. https://doi.org/10.32604/csse.2023.031476
Received 18 April 2022; Accepted 17 June 2022; Issue published 21 December 2022
Abstract
A Mobile Ad hoc NETwork (MANET) is a self-configuring network that is not reliant on infrastructure. This paper introduces a new multipath routing method based on the Multi-Hop Routing (MHR) technique. MHR is the consecutive selection of suitable relay nodes to send information across nodes that are not within direct range of each other. Failing to ensure good MHR leads to several negative consequences, ultimately causing unsuccessful data transmission in a MANET. This research work consists of three portions. The first to attempt to propose an efficient MHR protocol is the design of Priority Based Dynamic Routing (PBDR) to adapt to the dynamic MANET environment by reducing Node Link Failures (NLF) in the network. This is achieved by dynamically considering a node’s mobility parameters like relative velocity and link duration, which enable the next-hop selection. This method works more efficiently than the traditional protocols. Then the second stage is the Improved Multi-Path Dynamic Routing (IMPDR). The enhancement is mainly focused on further improving the Quality of Service (QoS) in MANETs by introducing a QoS timer at every node to help in the QoS routing of MANETs. Since QoS is the most vital metric that assesses a protocol, its dynamic estimation has improved network performance considerably. This method uses distance, linkability, trust, and QoS as the four parameters for the next-hop selection. IMPDR is compared against traditional routing protocols. The Network Simulator-2 (NS2) is used to conduct a simulation analysis of the protocols under consideration. The proposed tests are assessed for the Packet Delivery Ratio (PDR), Packet Loss Rate (PLR), End-to-End Delay (EED), and Network Throughput (NT).Keywords
Mobile Ad hoc NETwork (MANET) is very beneficial in different scenarios. In order to support routed communication between multiple Mobile Nodes (MN), a routing protocol helps to determine node communication links and routes packets accordingly. Hence, a MANET becomes highly adaptable and can be deployed in almost all environments. These MANETs advance the operational efficiency of specific civilian applications. MANET can be divided into two types: infrastructure and infrastructure-less networks. To connect MN to the fixed infrastructure, fixed equipment such as Base Stations (BS) and Access Points (AP) are used. When a source MN wishes to communicate with another MN, the source MN does not need to be aware of the routes between them in order to trigger communication with the BS. MANET has no fixed architecture. However, the communication paradigm follows the Open System Interconnection (OSI) network model [1–5].
Some of the challenges and issues faced in MANETs cause difficulties in the communication process. Unless these challenges are known and predicted, it is impossible to design systems that help communication among MANETs. Generally, routing is one of the primary tasks of every node connected to a MANET. Since mobility is one of the criteria distinguishing MANETs from other wireless technologies, reconfiguring the network into routes is a mandate for communication. This can be achieved only by the routing strategies, which are classified mainly into Multi-hop routing. Quality of Service (QoS) defines the efficiency of a network, showing the PDR of the communication. Both types of routing provide different QoS due to their respective routing strategies. Multipath routing is transmitting data from a single Source Node to a single Destination Node through multiple paths (Fig. 1). MANET communication is only possible between nodes in direct range of each other, which means data needs to be relayed by some other intermediate node. A data packet is sent through Multi-Hop Routing (MHR) available at the instant of data transmission to the intended Destination Node. One of the main reasons for doing this is to increase the reliability of the transmitting data, and the other is to balance the routing load. Load Balancing (LB) is part of this routing that aims to share the available bandwidth among the nodes, reducing bandwidth limitations.
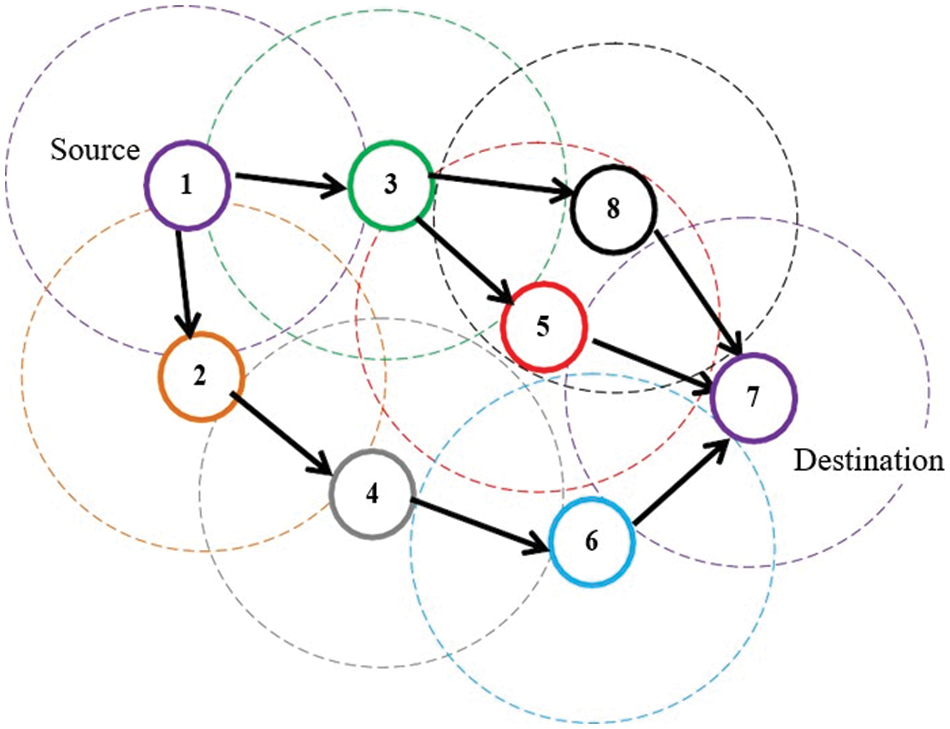
Figure 1: Model of multipath routing
The challenging part of communication among MN is to select the most appropriate next node dynamically among a given set of Neighborhood Nodes (NN) in MANET. In MANETs, auto-reconfiguration of ad hoc links takes place as and when required by just finding the reachable and nearest MN to route data from Source Node (SN) to Destination Node (DN) [5–10]. This, however, does not result in the best performance due to the changing dynamics in the MANET. An inefficient NN selection may result in link breakages, lost routes and hence failure of the entire route, leading to slow network failure. Hence, there is a need to consider other link and MN metrics to enhance the routing performance [4]. For MANET, there is a wide range of routing protocols to choose from. Before transmitting data to the DN, all traditional routing protocols build the route. As a result, an Node Link Failures (NLF) in MANET is possible. The data never reaches the DN due to NLF in the network. The Source Node reconfigures the data transmission route after that. In MANET, this tends to result in End to End Delay (EED) and routing overhead. This research proposes Priority Based Dynamic Routing (PBDR), which is a new routing method to address this. The PBDR also uses the Locate the Link Residual Life (LRL) to build the route [10–15].
MNs in a MANET should use this protocol. It provides rapid adaptation to dynamic link conditions, low processing and memory overhead, and low network allocations and helps determine unicast routes to Destination Node within MNs. It ensures loop freedom by using DN sequence numbers, preventing the issues that come with traditional distance vector protocols. Each MN acts as a highly specialised router, and routes are obtained on-demand rather than at regular intervals. This routing algorithm is suitable for a dynamic, self-starting network, like the one MANET users can set up [16–20].
The author has proposed that QoS is a measure of successful communication in PDR with minimal latency [21–25]. The Pakcdet Delivery Ration (PDR), Packet Loss Ratio (PLR), and EED occurring in the network are the three parameters generally assessed to estimate the QoS. Apart from these, NT is another primary parameter for judging network performance under various conditions. These techniques increase the network performance. The author has proposed that a survey of all the QoS-based routing protocols has shown the significance of QoS. However, this parameter alone does not serve as a stand-alone strategy for routing.
Core-Extraction Distributed Ad Hoc Routing (CEDAR) is a routing protocol that proactively sets up a core set for route configuration, QoS management, routing information, and packet forwarding. On behalf of these nodes, only core hosts maintain local topology information, actively engage in the exchange of topology and available bandwidth information, and carry out the necessary route discovery, route maintenance, and call admission. A greedy algorithm is used to create an estimated total minimal level dominating set in advance, in which all hosts in the network are either members of the core/one-hop Neighbour Nodes or not [26–30].
The author proposed in this study a novel routing algorithm based on SGC to minimize network overhead and achieve better MANET robustness and reliability. Based on ant foraging and work division, the design concept was born. By implementing a selective global correction to pheromone intensity, a more efficient route selection mechanism is created. The results show that, when compared to the AODV routing protocol and algorithm with selective global correction introduced in this paper, the function of each MN in MANET can reduce EED, improve stability, and increase the effectiveness of communication [31–35]. In order to obtain the routes to the Destination Node, generally, the route request messages are flooded across the network. Not all the request (REQ) messages are responded to with a route reply, which indicates the number of unwanted route REQ messages. A reliability check and flood algorithm for a wireless multi-hop network improve the network’s reliability by controlling flooding and single hop authentication checks. This method also uses link quality estimation in the network [36–40].
The Ant Routing Algorithm (ARA) suggested a new routing method for MANETs that refers to the biological behaviour of large communities of insects like ants and bees. MANETs, which are primarily made up of nodes with limited capacities and moving randomly in an unpredictable environment, can be used to replicate the success of complex solutions with only a small amount of intelligence and the capacities of each individual. To improve the ARA routing algorithm, new performance measures for determining how good a route is between two nodes were found [41–45].
3.1 Link Aware Improved Dynamic Routing
MNs transmit data without the use of external devices like APs in MANETs. MANET nodes are self-contained and capable of acting as relays. The node-to-node link is also dynamically changing. In a highly dynamic environment, it is difficult to transmit data to the node. The MANET’s highly dynamic environment is proposed to be used by PBDR. Before forwarding data through a node, the LRL reduces the NLF. When choosing the Next Forwarder Node (NFN), the velocity of the moving mode is taken into account. This allows the PBDR to lower the network’s EED. The proposed routing scheme lowers routing overhead while also lowering the EED. In addition, the NLF is reduced by this scheme.
The link between the nodes is constantly changing as the network’s topology changes. If the DN is within the SN’s transmission range, the node sends the information directly to the indented DN. The SN transmits through intermediate relay nodes if the Destination Node is present outside of the communication range. The MN functions as a relay node in and of itself. MANET supports a wide range of routing protocols. All traditional routing protocols build the route before transmitting data to the DN.
As a result, there is a chance that an NLF will occur in MANET. The data never reaches DN because of NLF in the network. The Source Node reconstructs the data transmission route after that. In MANET, this results in EED and routing overhead. To address this, this paper proposes PBDR, a new routing scheme. The LRL is also used by the PBDR to construct the route. Based on the LRL and the node’s speed, the PBDR selects the NFN. The SN in PBDR locates the list of NN. The NFN is then chosen based on the LRL and distance to the DN. The SN is unaware of the entire route to the DN. The intermediate relay node is also responsible for reconstructing the route failure in the proposed method.
NFN is an option provided by the proposed routing method. Furthermore, because the LRL is factored into the equation when attempting to build the route, the proposed method has a lower risk of NLF. The routing approach is used to minimize the EED by considering the distance between the currently active node and the targeted DN. The network’s reliability is ensured by lowering the NLF.
The concept of proposed routing, which is the intermediate process between the SN and DN to transmit data, is explained in Fig. 2. The SN intends to send the data to the DN. To form the NN list, the SN first determines which nodes are within their communication range. First, see if DN is in the NN list. If it exists, the data is sent directly to the DN. If not, it uses the following procedure to find the best forwarder node in the NN list.
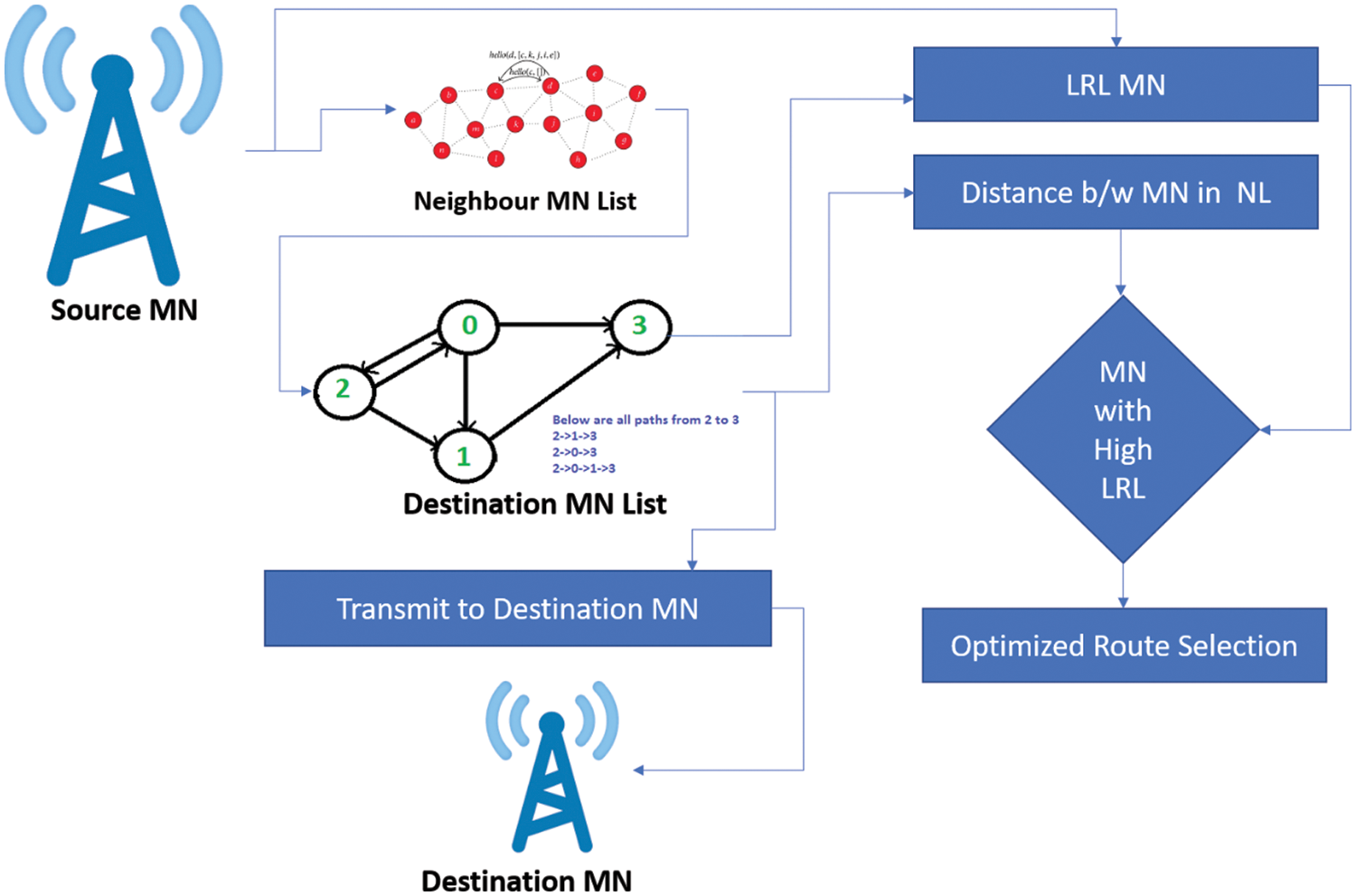
Figure 2: Architecture diagram of proposed improved multi-path dynamic routing
Algorithm for Link Residual Life
Step 1. LRL link between SN and NN.
Step 2. Decide the distance between the nodes in the NN and DN graphs.
Step 3. As an NFN, select the node with the highest LRL and the shortest path.
Step 4. Send the information to the best forwarder node available.
Step 5. Step 1 is iterated until the data packet receives DN.
The LRL is the period of a link between two MNs. The LRL is computed using Eq. (1)
Distance implies the NN must move to prevent the SN. The relative velocity calculates the moving node’s direction, Eq. (2)
To become an NFN, the distance between the node and the DN should decrease. The proposed routing scheme is expected to reduce the PLR during routing due to reducing NLFs in the network. The network route EED will also be reduced.
3.2 An Improved Priority Dynamic Routing
The use of MANETs is increasing rapidly, primarily due to mobility. Applications requiring high PDR are usually critical during network communications, like military operations and disaster management. The challenges involved in routing in a highly mobile environment are many. The unavailability of relaying nodes often hinders the successful data transmission of nodes in a MANET. However, the condition where the availability of nodes is high yet routing operations are entirely productive and successful gives rise to the need for dynamic routing strategies. PBDR was designed to minimize NLFs and improve the quality of routing in MANETs. In this chapter, an improvement on a proposed method to further improve QoS in MANETs is introducing a QoS timer at every node to help in the QoS routing of MANETs. The addition of a counter at each node fixes a time interval (Kij) for checking QoS.
The QoS is measured using the QoS by Eq. (3).
where ‘i’ is the previous instant of time, and ‘j’ is the current instant of time. Every node in the network has its own QoS ratio, which is measured individually. The standard PBDR algorithm considers LRL and the distance between nodes to find a suitable forwarder node. Fig. 3 depicts the process flow of the proposed method, which has been integrated with the PBDR algorithm. It demonstrates that a counter C is reset after every K Sec., where K is the difference between the current time and the previous instant Timei. In order to maintain consistency, K is assumed to be constant when calculating the QoS ratio for a node in order to maintain consistency and allow each node’s QoS performance to be compared to that of the others. When the counter is reset, the QoS estimated at each node is flushed. This ensures that routing functions have access to only the latest QoS ratios. The LRL and distance-based node selection techniques can generate completely different results than the QoS-based selection method. Furthermore, QoS-based node selection with low LRL does not improve NT. As an outcome, the algorithm below is used to implement the QoS-based selection.
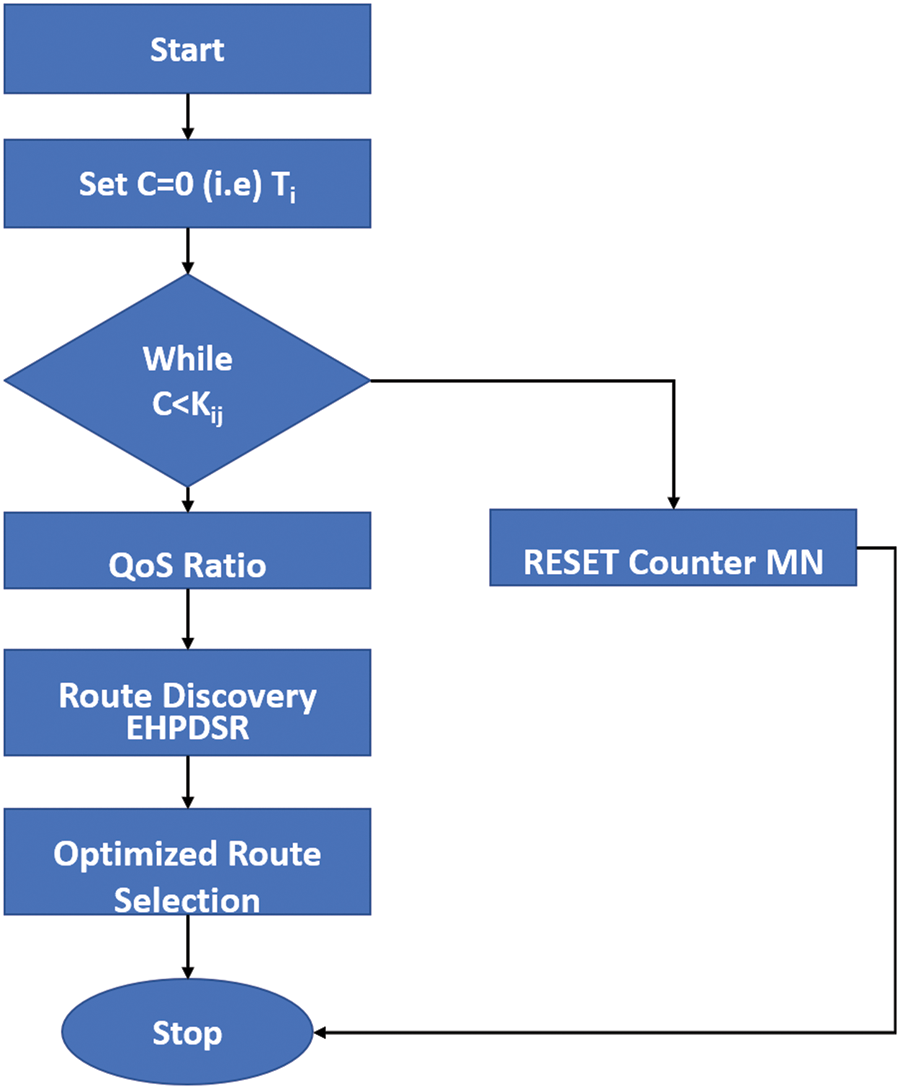
Figure 3: Flow chart of the proposed model
Algorithm for Quality of Service
Step 1. If
Step 2. {
Step 3. LRL = MAX && Distance = MIN
Step 4. }
Step 5. {
Check the QoS
If
{
QoS > QoS_TH
}
{
Select as the best forwarder
}
End If
Step 6. }
Step 7. End If
Step 8. Else
Step 9. {
Select the node with the highest QoS check LRL
If
{
LRL > LRLThreashold_Value
}
{
Select as the best forwarder
}
End If
Step 10. }
The EPBDR assumes values as fixed constants to perform simulations, Kij and W.
STEP 1: The time interval for buffer flushing that aggregates the QoS ratio is symbolised by the Kij value. Kij denotes the amount of time needed for counter C to reset. Fig. 4 illustrates how this works considering the data transmission between the Nodei and Nodej. The QoS ratio estimation takes the number of data packets transmitted between 0 and T. By subdividing the entire T value into fixed time intervals, output data such as values for Kij—can be obtained. The value of Kij can be in the range of a few ‘ms’ for good function.
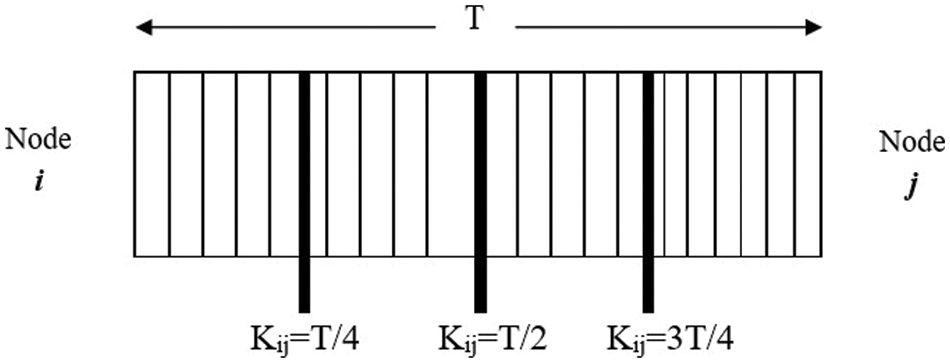
Figure 4: Computation process of active nodes
STEP-II: The threshold value of the LRL is dynamically estimated to ensure that the valid node is selected from a node’s NN list as the next node. This is achieved by considering a percentage of the maximum LRL (LRLMAX) as a dynamic threshold estimated by Eq. (4)
Because the QoS ratio is only used to enhance HPDR results, the range of W is bound to 0.5–1. A novel MHR is highly selective in choosing the route to the DN when a communication process is initiated. Our Improved Multi-Path Dynamic Routing (IMPDR) takes into account the distances between the nodes, their link statistics, trust, and QoS to figure out the best way to get to DN. There are multiple problems with most of the MHR protocols. Reaching QoS is a challenge, whereas reachability is another challenge in MANETs. In order to be as efficient as possible, an IMPDR algorithm takes into account more than a few factors for routing performance.
The IMPDR algorithm can be explained in Fig. 5. The Src_N (S) can send data to its immediate Nr_N (nodes 1, 2, and 3). For clarity, these nodes can be called level 1 Nr_N. The next level of Nr_Ns (for N1: N2, N4 and N5; for N2: N3, N5, N6 and N8; for N3: N2, N6, N7) are assessed here before the selection of the level 1-hop using Hop Selection Factor (HSF). At MANET, the data is not sent to the level 1 Nr_N until the following link is ready and reliable to reach the Dst_N.
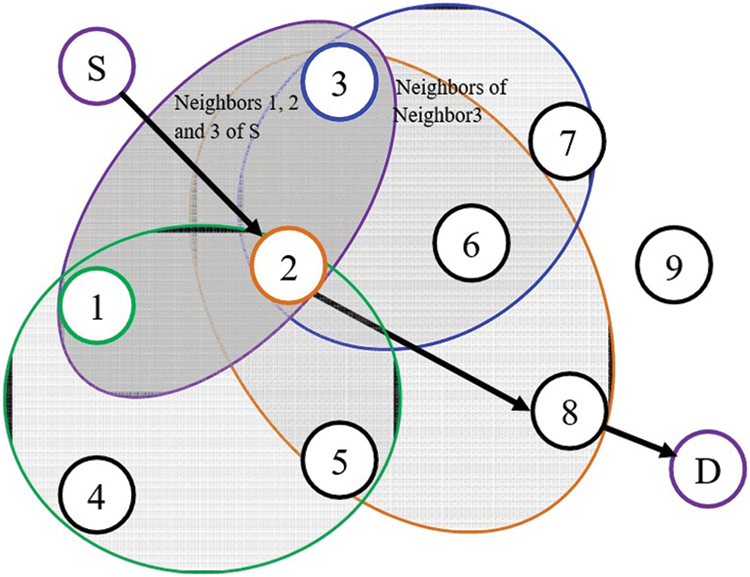
Figure 5: Routing function
To understand the workings of the IMPDR algorithm, It shows 11 nodes that are mobile and form a MANET. Each next hop is selected based on the best node, chosen from the best HSF expressed in Eq. (5). The hop selection factor is predicted by the matrix ‘M’ determinant. Distance, Linkability, Trust, and QoS are the four methods used for the Nx_H selection.
where Li,j is the linkability, Di,j is the distance, Trj is the trust value, and Qj is the QoS of the Nx_H ‘j’ from the current node ‘i’, respectively.
Each node that wants to send information to another node becomes the Src_N ‘i’ here that consecutively finds its NN ‘j’ using this algorithm. During such an NN selection process, each node dynamically determines the following parameters.
Distance: Distance is the first and most important factor influencing how effective data transfer can be. Distance is based on the strength of the RREP signal that the replying nodes send back. Hence, distance is given an essential role in determining the NN. Dj is the distance between Nodej and Nodei. The Level 1 NN distance is denoted by Di, j/Dj, k denotes level 2.
Link Dynamics: A new parameter called linkability that assesses the link statistics at Lj is defined. The link statistics are dynamically obtained from the Medium Access Control (MAC) layer for every node. The linkability of a node is the product of the link state and the distance between the nodes. The value of Li,j denotes the linkability between i and j and the value of Lj,k, similar to that of distance, is known while computing HSF at level 1. The advantage of estimating Lj,k for a node is that we estimate the link between the Nodei and Nodej and consider the link conditions of the Nodej with other NNs and provide stability of the network while routing, preventing link errors.
Trust: The trust factor is a measure of the legitimacy of a node. Knowing how trustworthy a node can be before any information is routed to one is vital. However, other security schemes are not restricted in this context. The trust is built by an NN tagging system here. An acknowledgement is sent to SN at the end of successful data transmission, and an acknowledgement is sent to SN. The other nodes overhear this acknowledgement broadcast by the receiver, and the trust value of the node that has successfully sent data to the receiver is incremented. The node trust is estimated similarly to the linkability and is represented by ‘Tj’ Eq. (6).
The nodes in the immediate NN aggregate the node trust values from the corresponding NN. However, the node trust value is considered in the complimented format HSF.
Quality of Service: QoS indicates the performance of a node in terms of how well it can process the information that propagates through the network. The PDR and PLR are the three most essential factors in accessing performance. The three parameters are added together to calculate the individual QoS values. These values usually lie within the limits of 0 < 1. These individual QoS are taken into the matrix as shown in Eq. (7).
PDRj is PDR of ‘j’, PLRj is PLR of ‘j’, and PLRj is EED of ‘j’ by Eq. (8). Here ‘i’ is SN whose data ‘j’.
The value of Qj is dynamically estimated and used in HSF for level 1-hop selection. So, the 2-hop k’s QoS is also determined as Qk, which is determined even before the computation of Qj. Fig. 6 shows the flow of the HPMDSR method.
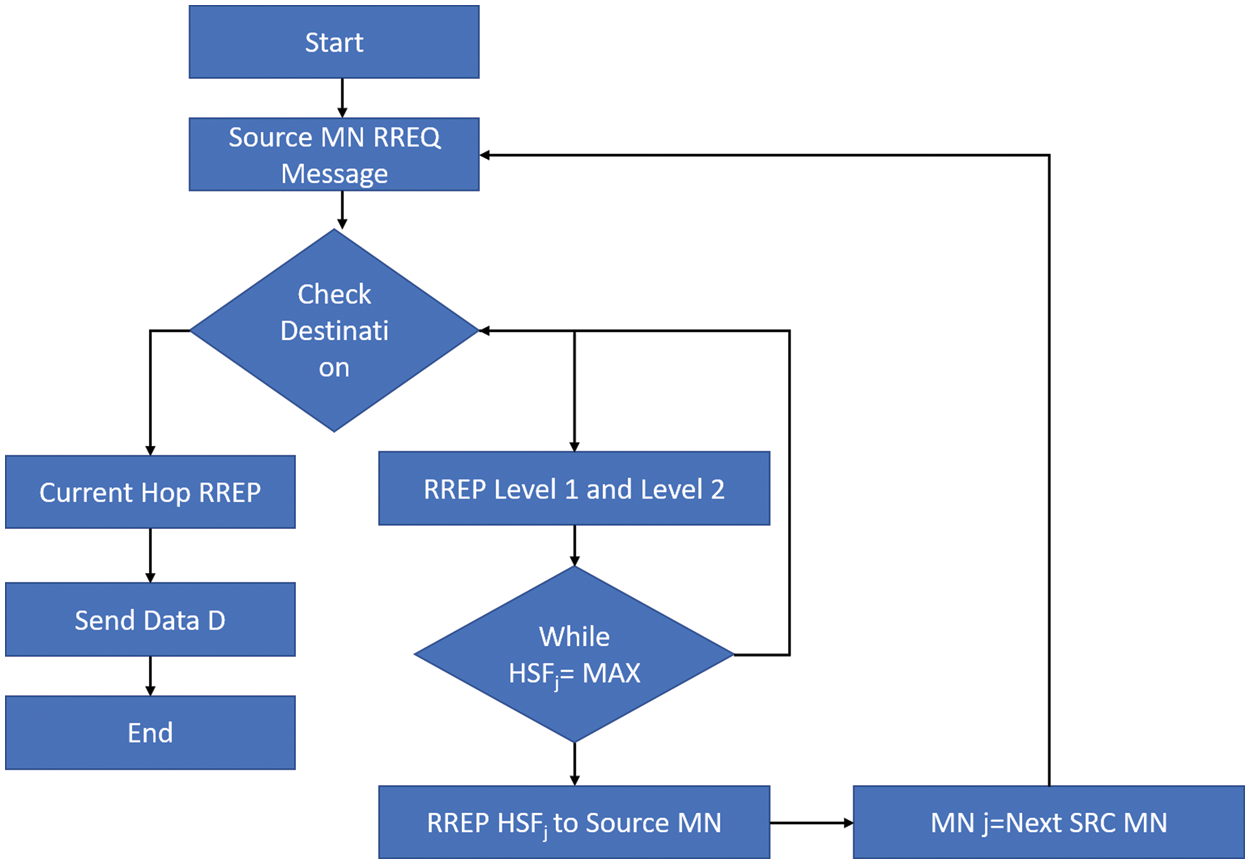
Figure 6: Data flow diagram of proposed IMPDR
Step 1. Initially, the SN “S” sends the Route Request (RREQ) message to the direct NN.
Step 2. It checks the route availability to reach the DN “D.”
Step 3. If the current hop returns the available route via RREP, it sends data to DN “D” through the available route.
Step 4. If the current hop does not return the available route, Then
Step 5. RREP is received, and Hop Selection Factor’s (HSF) value is estimated for levels 1 and 2.
Step 6. Check the value of HSF with its maximum value.
Step 7. If it has reached the maximum, Then send RREP with HSFj of the particular node to the current SN.
Step 8. Current SN “S” transmits the data to Nodej
Step 9. Nodej is assigned as the next SN
Step 10. The exact process repeats until the data properly reaches the DN “D”.
Every RREP packet carries Li,j, Tr,j, Qj and HSFk, where ‘i’ is the current hop, ‘j’ is the level 1 node, and ‘k’ is the level 2 node. The levels usually indicate the next set of NN. Before the node sends the data to NN, it checks if a route exists in the cache. The strategy looks more like a hierarchical one, but it is only estimated at the current hop using the information from the NH and possible next-to-next hops. It indicates that the hop-by-hop estimation is performed dynamically and consecutively until the information reaches the DN. There is not much propagation of routing information, and hence the hesitation about overhead in the network can be avoided.
Network Simulation 2 (NS2) is open-source software for simulation that implements C++ and Tool Command Language (TCL). C++ is a fast-running language that is used for packet processing. TCL is used to classify simulations and manipulate existing C++ objects. The simulation analysis is performed separately to compare and contrast the traditional routing protocols using Random Way Point (RWP) and City Section Mobility (CSM) models. The simulation parameters used for this analysis are presented in Tab. 1.
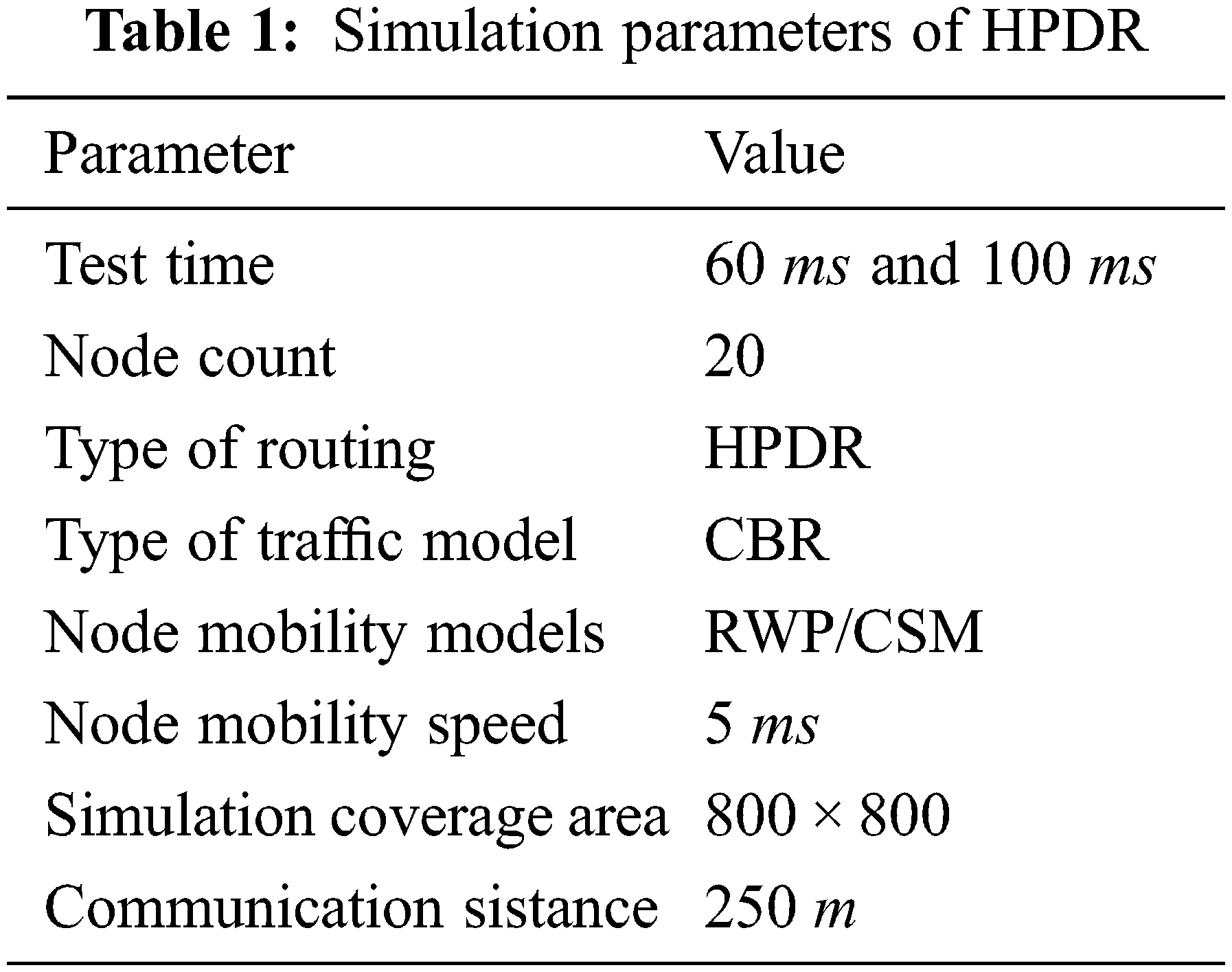
It implies that 20 nodes are transmitted across an 800 m × 800 m simulation area. The MNs move around the simulation area at a speed of 5 ms using the RWP mobility model. Within a 250 m radius, each node directly links to the MNs. To control traffic flow in MANET, the Constant Bit Rate (CBR) traffic model is used. The parameters NT, Link duration, and EED evaluate the proposed method’s performance. Changing the mobility models, such as RWP and CSM, is used to evaluate performance.
The PDR, PLR, Average EED, and NT are measured for all the RWP and CSM model protocols below.
PDR is the rate at which the various receivers receive information from the source over a simulation period. It is one of the most important parameters used to assess the QoS of routes in the network. The PDR is measured using Eq. (9) for the ‘n’ number of receivers in the network. The PDR decides the rate of success of the data transmissions in a network.
The statistics illustrated in Fig. 7 indicate that the PDR of IMPDR is much greater than the other protocols in RWP and CSM. This is due to the apt number of parameters estimated during the dynamic mobility of nodes communicating as a MANET. IMPDR provides the least PDR when compared to the other protocols.
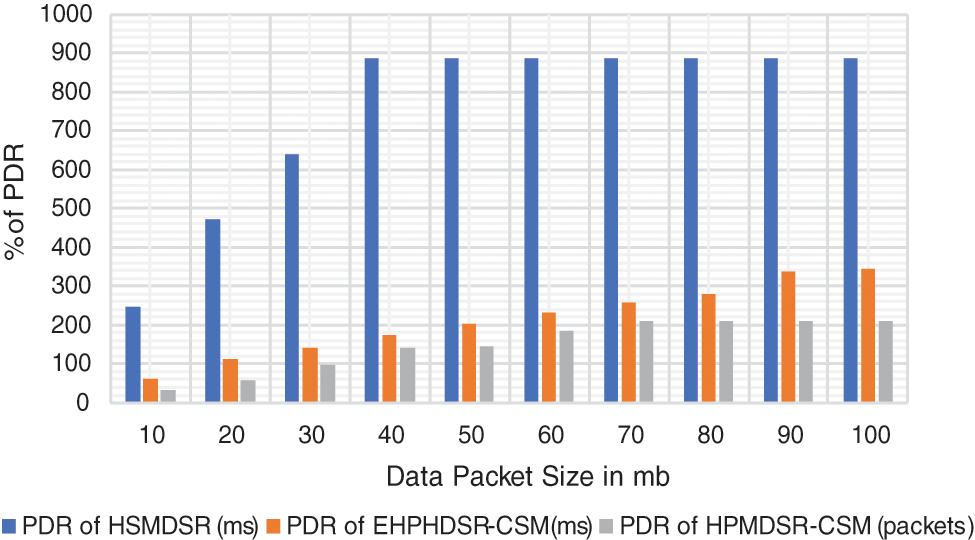
Figure 7: Packet delivery ration
During data transfer, the PLR determines the number of PLRs in a network. The values were obtained using the PLR formula in Eq. (10). In some cases, PLR is preferred over PDR when determining the routing protocol used in a MANET.
Although the HPMDSR provides greater PDR, it also provides greater PLR. As shown in Fig. 8, the PLR is higher in the same method, especially in the RWP model. Hence, IMPDR can be suggested for city scenarios rather than RWP mobility models. This means that DSR has a more significant loss than IMPDR because the QoS includes the loss as a parameter, and dynamic estimation is done, so the loss is taken into account.
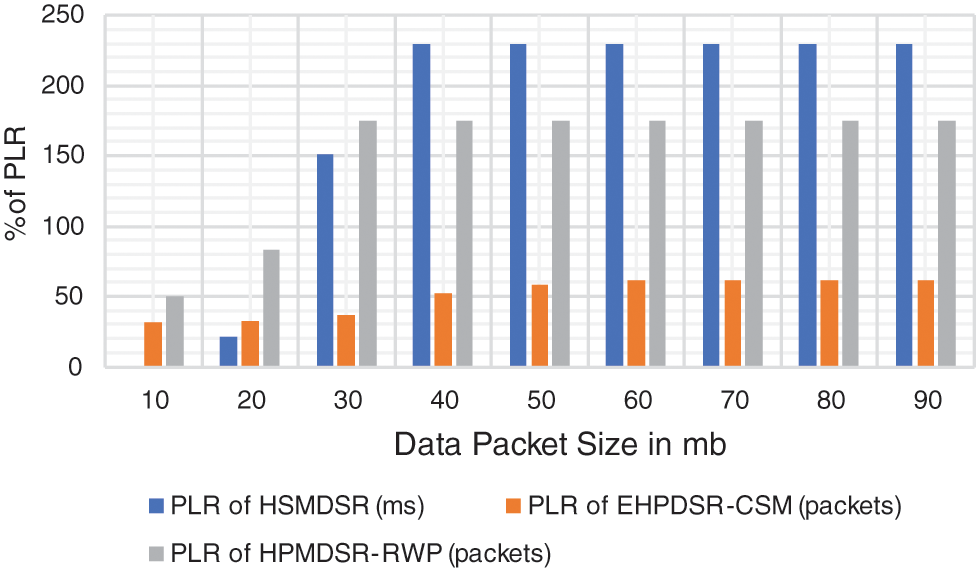
Figure 8: Packet loss ratio
EED refers to the lag caused in the data transmission process while communicating over the network. Most protocols may have high PDR but greater EED, making them preferable for communications. Fig. 9 shows the average EED for each node in IMPDR. The values were obtained using the EED formula in Eq. (11).
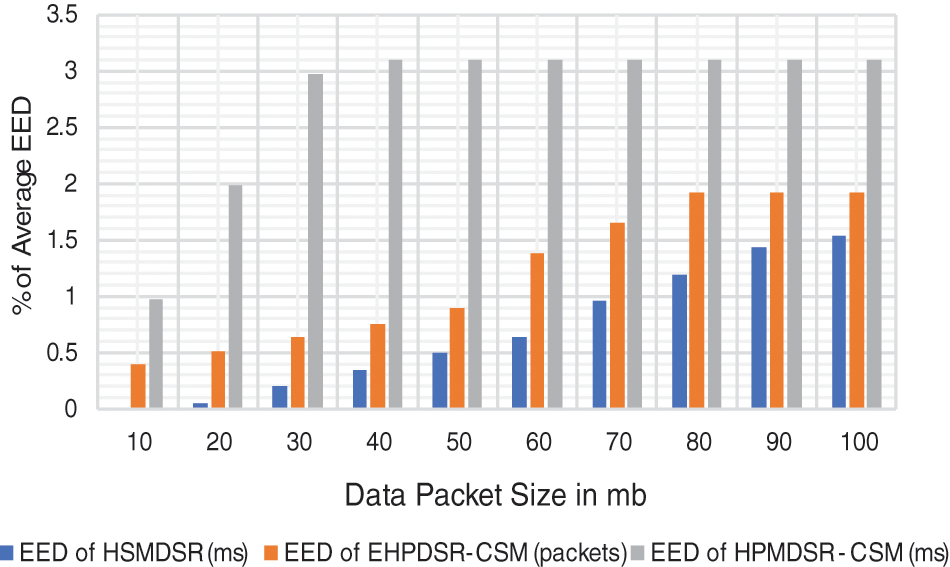
Figure 9: End-to-end delay
It can be observed from Fig. 9 that IMPDR has a greater EED. All three protocols have lower EED for the nodes in the CSM when compared to the RWP model. The apparent reason is the randomness of the node mobility in the RWP model.
NT is the overall number of PDR to all the DN in the network and is obtained for IMPDR protocols in the CSM and RWP mobility models. NT is measured using Eq. (12) to measure the total PDR rate in the network. As observed in, the NT is excellent for the HPMDSR in mobility models (Fig. 10).
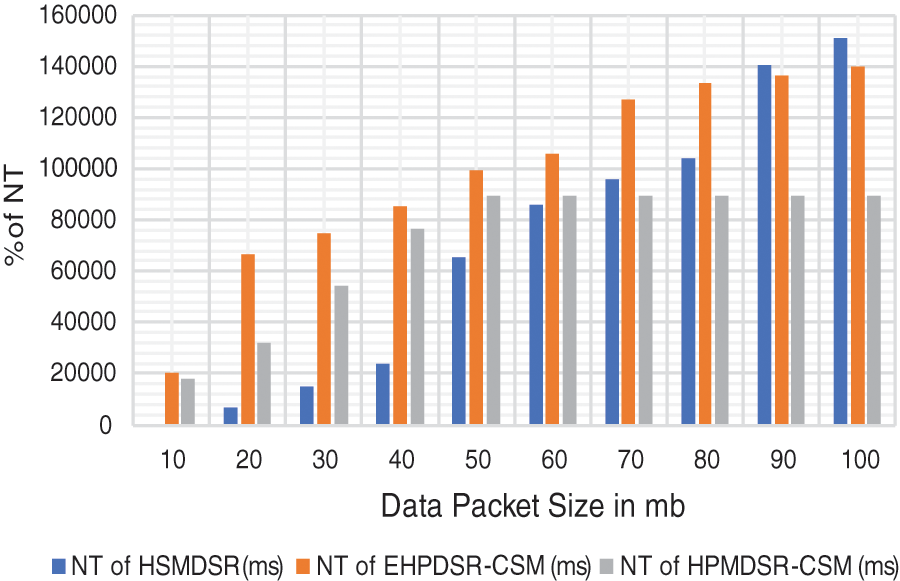
Figure 10: Network throughput
The PDR, PLR, EED, and Network Throughput (NT) explain why a single protocol is better than the other protocols. In that context, IMPDR has the highest PDR, highest PLR, lowest EED, and highest NT when simulated with both the mobility models. It performs better among all the protocols proposed in this research work. The simulation analysis of the proposed IMPDR has been presented. The LRL was predicted to reduce the NLF before packet forwarding through a node enhanced the PDR and significantly reduced the PLR efficiently and successfully. Because the velocity of the mobility model is taken into account when selecting the NFN, NLFs have been reduced, resulting in a significant increase in the NT of IMPDR over traditional protocol. Both RWP and CSM have been used to compare and contrast the performance of IMPDR protocols. This analysis has concluded that the IMPDR performs better in the CSM Scenarios. An improvement to the IMPDR in terms of QoS routing was proposed in this section. The simulation results indicate that the IMPDR performs better than the IMPDR in QoS. T is significantly increased in the IMPDR, PLR is decreased, and the EED is maintained at a lower level than the IMPDR. This is because the QoS is a result of the link-state being well. Hence, in cases where the LRL measurement is not stable, and the LRL changes rapidly due to interference and environmental obstacles, the QoS ratio helps minimise NLFs while routing. From the analysis, it can be concluded that the CSM performs better in all the measured metrics and that IMPDR is more suitable to be applied in a city scenario where the movement of nodes is a bit more uniform, unlike in the RWP model. The IMPDR is used for efficient NN selection that eventually improves the route to a great extent. A strategy to perform routing using the parameters distance, linkability, trust, and QoS by estimating the HSF dynamically is proposed. From the simulation results, it can be concluded that the efficiency of the proposed IMPDR outperforms traditional protocols in terms of NT and PLR.
MANETs are currently being implemented to use possible real-time applications, and hence the need for their advancement is always present. The PDR, PLR, EED, and NT contribute to why a single protocol is better than the other protocols. This makes IMPDR preferable for MANETs for crucial and tactical applications like military and defense operations and emergency and recovery operations. It’s vital to think about how cognitive radio ad hoc networks work before figuring out how to do efficient routing. Future research could ensure efficient CRAHN communication. This future work proposes physical layer modelling.
Funding Statement: This research is supported by Princess Nourah bint Abdulrahman University Researchers Supporting Project number (PNURSP2022R195), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Mahamune and M. M. Chandane, “Evaluating routing protocols for mobile ad hoc networks under varying network scenarios,” in 3rd Int. Conf. on Intelligent Communication Technologies and Virtual Mobile Networks, Tirunelveli, India, pp. 220–225, 2021. [Google Scholar]
2. B. Donepudi, T. Jayasankar, V. P. Sriram, S. Sudhakar and K. B. Prakash, “Speech emotion recognition using state-of-art learning algorithms,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1340–1345, 2020. [Google Scholar]
3. C. Chen, L. Liu, T. Qiu, K. Yang, F. Gong et al., “ASGR: An artificial spider-web-based geographic routing in heterogeneous vehicular networks,” IEEE Transactions on Intelligent Transportation Systems, vol. 20, no. 5, pp. 1604–1620, 2019. [Google Scholar]
4. C. Sathiya Kumar, V. Priya, V. P. Sriram, K. Sankar Ganesh, G. Murugan et al., “An efficient algorithm for quantum key distribution with secure communication,” Journal of Engineering Science and Technology, vol. 15, no. 1, pp. 77–93, 2020. [Google Scholar]
5. C. Y. Liu, H. J. Huang and H. W. Du, “Optimal RSUs deployment with delay bound along highways in VANET,” Journal of Combinatorial Optimization, vol. 33, no. 4, pp. 1168–1182, 2017. [Google Scholar]
6. D. G. Zhang, J. X. Gao, X. H. Liu, T. Zhang and D. Zhao, “Novel approach of distributed & adaptive trust metrics for MANET,” Wireless Networks, vol. 25, pp. 3587–3603, 2019. [Google Scholar]
7. D. M. Khan, T. Aslam, N. Akhtar, S. Qadri and N. A. Khan, “Blackhole attack prevention in mobile ad-hoc network (MANET) using ant colony optimization technique,” Information Technology and Control, vol. 49, no. 3, pp. 308–319, 2020. [Google Scholar]
8. G. Jagadeesh, J. Vellingiri, J. Gitanjali, K. Arivuselvan and S. Sudhakar, “An improved trusted on-demand multicast routing with qos for wireless networks,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 1, pp. 261–265, 2020. [Google Scholar]
9. G. Murugan, A. Syed Musthafa, D. Abdul Jaleel, C. Sathiya Kumar and S. Sudhakar, “Tourist spot proposal system using text mining,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1358–1364, 2020. [Google Scholar]
10. G. Murugan, N. Keerthana, K. Sujatha, S. Sudhakar, K. Amarendra et al., “Towards taxonomy for cloud computing as business models and deployment: A technical review,” International Journal of Advanced Science and Technology, vol. 29, no. 3, pp. 9096–9106. 2020. [Google Scholar]
11. H. Liu, T. Qiu, X. Zhou and C. Chen, “Parking-area-assisted spider-web routing protocol for emergency data in urban VANET,” IEEE Transactions on Vehicular Technology, vol. 69, no. 1, pp. 971–982, 2020. [Google Scholar]
12. J. Gao, S. V. Buldyrev, H. E. Stanley and S. Havlin, “Networks formed from interdependent networks,” Nature Physics, vol. 8, no. 1, pp. 40–48, 2012. [Google Scholar]
13. J. Wilson and K. Subramaniam, “Improved multi-objective data transmission using conventional route selection algorithm in mobile ad hoc network,” Peer-to-Peer Networking and Applications, vol. 13, pp. 1091–1101, 2020. [Google Scholar]
14. K. Muthumayil, R. Karuppathal, T. Jayasankar, B. Aruna Devi, N. B. Prakash et al., “A big data analytical approach for prediction of cancer using modified k-nearest neighbour algorithm,” Journal of Medical Imaging and Health Informatics, vol. 11, no. 8, pp. 2120–2125, 2021. [Google Scholar]
15. K. Devipriya, D. Prabha, V. Pirya and S. Sudhakar, “Deep learning sentiment analysis for recommendations in social applications,” International Journal of Scientific & Technology Research, vol. 9, no. 1, pp. 3812–3815, 2020. [Google Scholar]
16. K. Rajakumari, M. Vinoth Kumar, V. Garima, S. Balu, D. K. Sharma et al., “Fuzzy based ant colony optimization scheduling in cloud computing,” Computer Systems Science and Engineering, vol. 40, no. 2, pp. 581–592, 2022. [Google Scholar]
17. K. Sasi Kala Rani, D. Ramya, J. Manikandan and S. Sudhakar, “Monitoring emotions in the classroom using machine learning,” International Journal of Scientific & Technology Research, vol. 9, no. 1, pp. 3723–3726, 2020. [Google Scholar]
18. M. Avuthu Sai, S. Sudhakar, G. Arumugam, P. Srinivasan and K. B. Prakash, “Age and gender prediction using convolution, ResNet50, and inception ResNetV2,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1328–1334, 2020. [Google Scholar]
19. M. Ichaba, F. Musau and S. N. Mwendia, “Performance effects of algorithmic elements in selected MANETs routing protocols,” Advances in Science Technology and Engineering Systems Journal, vol. 5, no. 3, pp. 62–71, 2020. [Google Scholar]
20. M. K. Riaz, F. Yangyu and I. Akhtar, “A multidimensional trust inference model for the mobile ad-hoc networks,” in 28th Wireless and Optical Communications Conf., Beijing, China, pp. 1–5, 2019. [Google Scholar]
21. M. N. Siraj, Z. Ahmed, M. K. Hanif, M. H. Chaudary and K. Jayakrishna, “A hybrid routing protocol for wireless distributed networks,” IEEE Access, vol. 6, pp. 67244–67260, 2018. [Google Scholar]
22. N. Satheesh, D. Sudha, D. Suganthi, S. Sudhakar, S. Dhanaraj et al., “Certain improvements to location aided packet marking and DDoS attacks in internet,” Journal of Engineering Science and Technology, vol. 15, no. 1, pp. 94–107, 2020. [Google Scholar]
23. P. Deivendran, K. Anbazhagan, P. Sailaja, E. Sujatha, M. Rajesh Babu et al., “Scalability service in data center persistent storage allocation using virtual machines,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 2135–2139, 2020. [Google Scholar]
24. P. Kanmani, V. Priya, N. Yuvaraj, S. Sudhakar and V. P. Sriram, “Inaccuracy correction method for moving shapes and shadows in video coding object,” International Journal of Scientific & Technology Research, vol. 9, no. 3, pp. 4561–456, 2020. [Google Scholar]
25. P. S. Ngangbam, S. Shruti, R. P. Thandaiah, S. Tripti, R. Selvakumar et al., “Investigation on characteristics of monte carlo model of single-electron transistor using orthodox theory,” Sustainable Energy Technologies and Assessments, vol. 48, no. 101601, pp. 1–15, 2021. [Google Scholar]
26. P. Thirumoorthy, A. Daniyal, B. Surbhi, A. M. Areej, P. Dadheech et al., “Improved energy based multi-sensor object detection in wireless sensor networks,” Intelligent Automation & Soft Computing, vol. 33, no. 1, pp. 227–244, 2022. [Google Scholar]
27. R. Gowthamani, K. Sasi Kala Rani, E. Mohanraj and S. Sudhakar, “Enhancing security through blockchain technology–a quick review,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 5126–5129, 2020. [Google Scholar]
28. R. Nithya, K. Amudha, A. Syed Musthafa, D. K. Sharma, E. H. R. Asis et al., “An optimized fuzzy-based ant colony algorithm for 5G-MANET,” Computers, Materials & Continua, vol. 70, no. 1, pp. 1069–1087, 2022. [Google Scholar]
29. R. Vasanthi, O. I. Khalaf, C. A. T. Romero, S. Sudhakar and D. K. Sharma, “Interactive middleware services for heterogeneous systems,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1241–1253, 2022. [Google Scholar]
30. R. Zarzoor, “Enhancing dynamic source routing (DSR) protocol performance based on link quality metrics,” in Int. Seminar on Application for Technology of Information and Communication, Semarangin, Indonesia, pp. 17–21, 2021. [Google Scholar]
31. S. Biruntha, S. Balaji, S. Dhyakesh, B. R. Karthik Srini, J. Boopala et al., “Digital approach for siddha pulse diagnosis,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 2140–2143, 2020. [Google Scholar]
32. S. Mehbodniya, A. Bhatia, A. Mashat, E. Mohanraj and S. Sudhakar “Proportional fairness based energy-efficient routing in wireless sensor network,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1071–1082, 2022. [Google Scholar]
33. S. Nanthini, S. N. Kalyani and S. Sudhakar, “Energy-efficient clustering protocol to enhance network lifetime in wireless sensor networks,” Computers, Materials & Continua, vol. 68, no. 3, pp. 3595–3614, 2021. [Google Scholar]
34. S. S. Y. Bharadwaj, P. Rajaram, V. P. Sriram, S. Sudhakar and K. B. Prakash, “Effective handwritten digit recognition using deep convolution neural network,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1335–1339, 2020. [Google Scholar]
35. S. Stalin David, M. Anam, K. Chandraprabha, S. Arun Mozhi Selvi, D. K. Sharma et al., “Cloud security service for identifying unauthorized user behaviour,” Computers, Materials & Continua, vol. 70, no. 2, pp. 2581–2600, 2022. [Google Scholar]
36. S. Stalin David, S. Arun Mozhi Selvi, S. Sivaprakash, P. Vishnu Raja, D. K. Sharma et al., “Enhanced detection of glaucoma on ensemble convolutional neural network for clinical informatics,” Computers Materials & Continua, vol. 70, no. 2, pp. 2563–2579, 2022. [Google Scholar]
37. S. Sudhakar and S. Chenthur Pandian “Secure packet encryption and key exchange system in mobile ad hoc network,” Journal of Computer Science, vol. 8, no. 6, pp. 908–912, 2012. [Google Scholar]
38. S. Sudhakar and S. Chenthur Pandian, “A trust and co-operative nodes with affects of malicious attacks and measure the performance degradation on geographic aided routing in mobile ad hoc network,” Life Science Journal, vol. 10, no. 4s, pp. 158–163, 2013. [Google Scholar]
39. S. Sudhakar and S. Chenthur Pandian, “An efficient agent-based intrusion detection system for detecting malicious nodes in MANET routing,” International Review on Computers and Software (I.RE.CO.S,), vol. 7, no. 6, pp. 3037–304, 2012. [Google Scholar]
40. S. Sudhakar, N. Satheesh, S. Balu, R. S. Amireddy and G. Murugan, “Optimizing joins in a map-reduce for data storage and retrieval performance analysis of query processing in HDFS for big data,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 8, no. 5, pp. 2062–2067, 2019. [Google Scholar]
41. T. Qiu, B. Li, W. Qu, E. Ahmed and X. Wang, “TOSG: A topology optimization scheme with global small world for industrial heterogeneous internet of things,” IEEE Transactions on Industrial Informatics, vol. 15, no. 6, pp. 3174–3184, 2019. [Google Scholar]
42. U. Zeb, W. U. Khan, S. Irfanullah and A. Salam, “The impact of transmission range on performance of mobile ad-hoc network routing protocols,” in 3rd Int. Conf. on Computing, Mathematics and Engineering Technologies, Sukkur, Pakistan, pp. 1–4, 2020. [Google Scholar]
43. V. Bibhu, A. Kumar, B. P. Lohani and P. K. Kushwaha, “Blackhole attack in mobile ad hoc network and its avoidance,” in Int. Conf. on Innovative Practices in Technology and Management, pp. 103–107, Noida, India, 2021. [Google Scholar]
44. Y. Yao, Q. Cao and A. V. Vasilakos, “EDAL: An energy-efficient, delay-aware, and lifetime-balancing data collection protocol for heterogeneous wireless sensor networks,” IEEE Transactions on Networking, vol. 23, no. 3, pp. 810–823, 2015. [Google Scholar]
45. Z. Gao, D. Chen, S. Cai and H. C. Wu, “Optdynlim: An optimal algorithm for the one-dimensional RSU deployment problem with nonuniform profit density,” IEEE Transactions on Industrial Informatics, vol. 15, no. 2, pp. 1052–1061, 2019. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools