 Open Access
Open Access
ARTICLE
Energy-Efficient Routing Using Novel Optimization with Tabu Techniques for Wireless Sensor Network
1 Department of Electrical and Computer Engineering, International Islamic University Malaysia, Kuala Lumpur, 53100, Malaysia
2 Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
3 Department of Information Technology, College of Computer and Information Sciences, Princess Nourah Bint Abdulrahman University, P.O. Box 84428, Riyadh, 11671, Saudi Arabia
4 Department of Information Systems, College of Science & Art at Mahayil, King Khalid University, Saudi Arabia
5 Department of Industrial Engineering, College of Engineering at Alqunfudah, Umm Al-Qura University, Saudi Arabia
6 Department of Digital Media, Faculty of Computers and Information Technology, Future University in Egypt, New Cairo, 11835, Egypt
7 College of Science and Humanities Studies in Alquwayiyah, Shaqra University, Saudi Arabia
* Corresponding Author: Manar Ahmed Hamza. Email:
Computer Systems Science and Engineering 2023, 45(2), 1711-1726. https://doi.org/10.32604/csse.2023.031467
Received 18 April 2022; Accepted 16 June 2022; Issue published 03 November 2022
Abstract
Wireless Sensor Network (WSN) consists of a group of limited energy source sensors that are installed in a particular region to collect data from the environment. Designing the energy-efficient data collection methods in large-scale wireless sensor networks is considered to be a difficult area in the research. Sensor node clustering is a popular approach for WSN. Moreover, the sensor nodes are grouped to form clusters in a cluster-based WSN environment. The battery performance of the sensor nodes is likewise constrained. As a result, the energy efficiency of WSNs is critical. In specific, the energy usage is influenced by the loads on the sensor node as well as it ranges from the Base Station (BS). Therefore, energy efficiency and load balancing are very essential in WSN. In the proposed method, a novel Grey Wolf Improved Particle Swarm Optimization with Tabu Search Techniques (GW-IPSO-TS) was used. The selection of Cluster Heads (CHs) and routing path of every CH from the base station is enhanced by the proposed method. It provides the best routing path and increases the lifetime and energy efficiency of the network. End-to-end delay and packet loss rate have also been improved. The proposed GW-IPSO-TS method enhances the evaluation of alive nodes, dead nodes, network survival index, convergence rate, and standard deviation of sensor nodes. Compared to the existing algorithms, the proposed method outperforms better and improves the lifetime of the network.Keywords
WSN is a collection of economical, operative, and adaptable Sensor Nodes (SNs) that work together to examine the Age of Information (AoI). The sensors collect information from the area of interest and send it to a Base Station (BS) for processing. WSN has assisted in monitoring the remote settings. Moreover, it is incredibly beneficial in gathering the data in a variety of distant locations, including rescue teams, forests, military conflict areas, undersea research, changes in the climate, and so on. WSNs have a large number of sensor nodes that are connected to a base station. In fact, it is difficult to load and reinstall the sensor nodes in remote places [1].
On the other side, the data communication method among the network elements is highly susceptible to intervention as well as the impact of the external environment due to the complicated blockage and other attributes of the software atmosphere of the network. The connection characterization is the probability-based interconnection state of the period relationship and time disconnection. Many academics have studied energy usage management in wireless sensor networks in recent years. Cluster head multi-hop mixed routing depending on a clustered architecture is a prominent topic in the research community right now [2].
In order to solve the issue of Cluster Head Selection (CHS), various strategies were used. Normal CHS techniques and optimum CHS techniques are two types of CHS systems. The best CHS techniques are still classified as meta-heuristic and heuristic procedures [3]. These methods are designed to provide answers for the optimization of algorithms using concise and simple concepts, which are frequently explorative. To deal with the heterogeneity, several heuristic techniques have been suggested in the literature. The mathematical inefficiencies of the search phase are the flaws in heuristic techniques; which focus on high and huge issues. On the contrary, meta-heuristic optimization approaches have attracted and increased attention in recent years.
The lifespan of the system is extended by observing the areas that are divided into groups. Each cluster contains a large number of sensor nodes. Just one sensor serves as Cluster Head (CH), with the others serving as member nodes. The data is gathered from individual sensors in the given area. During the process of CH selection in each area, the nodes with the highest power residues pertinent to certain other nodes are selected as CH [4].
Cluster routing is used when a network has many clusters; each cluster has a tree structure that is made up of various CH and cluster membership. The data collected by cluster members is sent to CH, who compiles it by multi-hop CHs or sends the data to the BS. The clustering routing method advantages load demand by trying to balance the access point in every round of CH selection; the information obtained by the cluster members is transferred by CH after a merger to reduce the power consumption. It is carried out by the network to send information and eliminate each cluster node that sends the forwarding data individually [5–7].
The problem of selecting power balance CH is nothing but Nondeterministic Polynomial Time (NP)-hard. There have been numerous extensive studies on these topics in the research [8,9]. Several meta-heuristic algorithms clustering systems have been suggested in the research, but they all have a power consumption unbalance [10]. There is no equal distribution of CHs in this problem, and strongly laden CHs die quicker than under-loaded CHs. It is due to the assumption that the fitness value uses the average difference between CH and BS to choose all CHs that are closest to BS.
The main contributions of the proposed GW-IPSO-TS work are given below:
• It effectively selects the energy-balanced Cluster Head (CH) and enhances the energy efficiency.
• Improved particle swarm optimization enhances the link quality, and residual energy and solves the problem in the path selection.
• Tabu search protocol enables the solution space, therefore it reduces the sensor deployment problem.
• By using the Grey wolf method, the unidentified nodes are found with the help of the anchor node (CH), therefore the computation time is reduced.
The remaining sections of this paper are structured as follows; Section 2 discusses the related research works, Section 3 describes the Wireless Sensor Networks and Optimization methods for the reduction of energy efficiency, Section 4 discusses the results and the comparison of the experiment and Section 6 concludes the proposed optimization method with future work.
Whenever there is an unbalance in the data transmission of the network, a power gap is generated, leading the Strong Node (SN) to die prematurely, reducing the lifespan of the network [11–13], In [14,15], the author offered a strategy for which the communication range was changed dependent on the distances between CHs and their users, dealing with the problem. The implementation of the firefly optimization technique has also extended the longevity of the network. This method was applied against the standardized algorithms in a variety of scenarios. According to the findings of their research, this algorithm produced better outcomes in terms of network life. The researcher, on the other hand, makes no mention of the SNs’ overall energy maximization while preserving the optimal CH distance.
The author [16] proposed an improved Cuckoo Search (CS)-based power balancing node clustered technique based on the new objective function using a uniform distribution of CHs. In [17], the researcher employed an upgraded Harmony Search (HS) based routing to transport data packets between CHs and the sink in another paper. The performance of the provided combined clustering and routing protocols was assessed using energy efficiency, the amount of live and dead nodes, and network longevity. In comparison to the existing methods, the novel Cuckoo-Harmony Search-based combined route and clustering protocol has revealed more results.
Clustering routing techniques benefit in terms of basic structure, effective topology systems, and the absence of complicated routing paths. Low Energy Adaptive Clustering Hierarchy (LEACH) [18], a classic clustering routing protocol, employs the normal nodes as cluster-heads in a probabilistic method, balancing the extra power usage of cluster heads to some degree and extending the lifetime of the system.
The node value is utilized as the foundation for CH selection, and it is determined based on the residual energy of nodes and their distances from BS. The Cluster Head Cycle Switching Schemes (CHCS) method selects the member nodes with the maximum residual power and the cluster head node with the most votes in the area that is chosen [19]. In [20], a process for assessing the cluster head rating that depends on the comparison of cluster head to BS length to total power consumption was provided.
The researcher [21] developed a CHS methodology based on the Artificial Bee Colony (ABC) technique, which is an optimization tool. In specific, three factors are used to evaluate the fitness function of ABC; intra-cluster length, sink station distance, and residual energy. The author [22] established an efficient and reliable clustering technique for WSNs based on the ABC algorithm for node density, balanced network power usage, and network longevity. The research usage of mobile WSN is data gathering and network clustering. The ABC algorithm has the drawback of converging at a sluggish velocity during the searching phase.
In order to improve the performance of a network, the author [23] proposed an improved firefly algorithm and synchronous firefly optimization. Actually, the benefit of the Firefly algorithm is that it avoids many local optima. When compared to the Leach protocol, it fared better. While transferring the data to BS, the CH gathers it. This increased work requires a lot of energy, causing network depletion to be unequal. The author [24] presented a grouping method that used Grey Wolf Optimization (GWO) to choose CHs. The findings were generated by the expected power usage and the remaining energy of all nodes while picking CHs. The proposed approach employs the same clustering method for multiple consecutive stages to improve energy consumption.
For expediting the threshold responsive energy-efficient clustering method in WSNs, the author [25] presented an enhanced flower pollination method. It was done to keep the system stable for a longer length of time. Because the reason is that the last node dies longer in the proposed scheme, the first node kills faster than in previous designs. The squirrel search method [26], which was motivated by the hunting behavior of flying squirrels is used in the fields including such Micro-Electrical Mechanical components (MEMS) [27], storage systems are used [28–31] yet another continuously evolving planning procedure. In the energy-aware confidence, the Gravitational Search Algorithm (ETGSA) was introduced in WSN addressing energy-saving issues, boosting network reliability, and lowering computing complexity.
The proposed method has enhanced the lifetime of the network by optimal Cluster Head (CH) selection. Also, it improves the routing path by Improved Particle Swarm Optimization and Tabu Search (TS). The architecture of the proposed method is shown in Fig. 1.
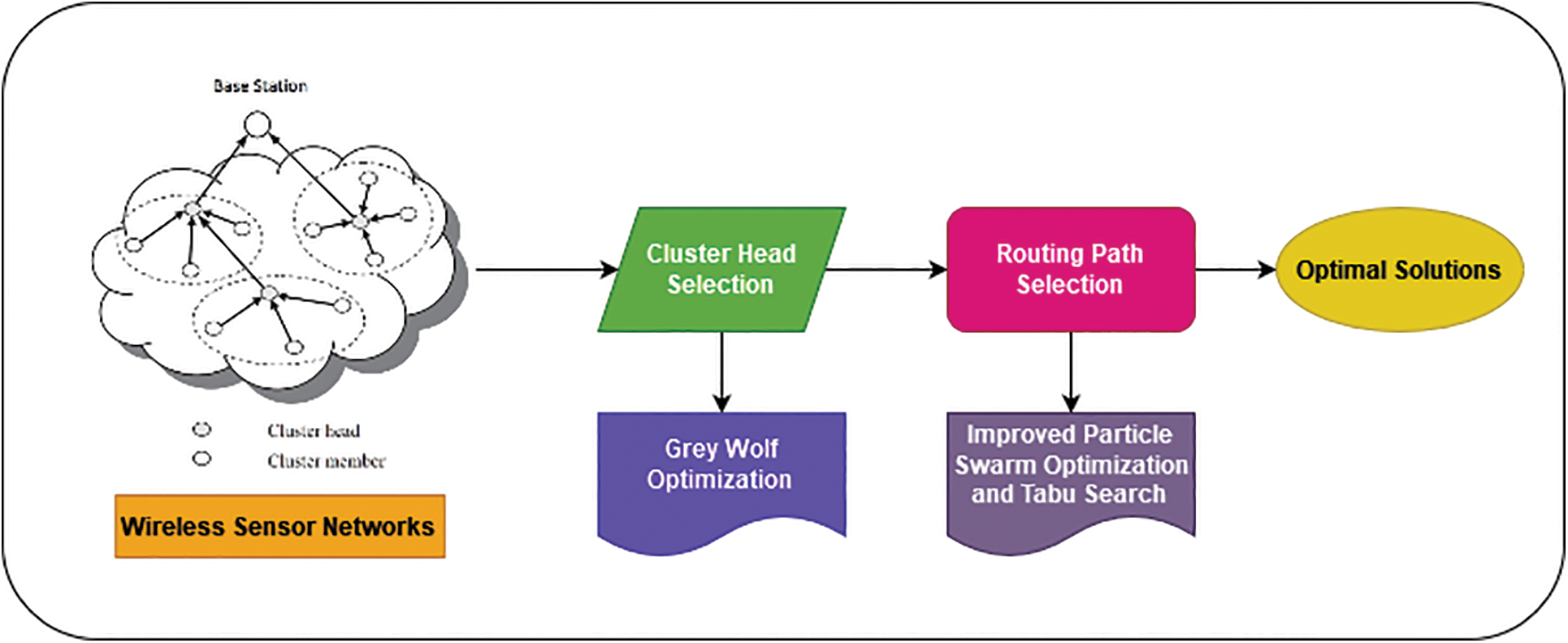
Figure 1: Architecture of proposed GW-IPSO-TS method
It consists of the network model, energy model, distance model, and signal channel model. The models are explained below.
This work presented a wireless sensor network concept. WSN is made up of various SNs, each of which is immobile and has the same abilities. Nodes can act as both a CH and a working sensor during the exchange of data. Overall, radio communication, sensor assignment, data sensing, topological aspects, and power usage are all connected to the WSN component. In the case of area efficiency, a sensor can be placed either randomly or practically. Clustering is a term used to describe the way-gathering SNs. It is an excellent approach for the future growth of WSN. Clusters are formed by collecting SNs during the clustering operation. The wireless sensor network is considered to have the following characteristics, with N sensor nodes randomly distributed in a two-dimensional rectangular area of X * Y.
• The networks should be stable with higher densities, which means that the sensor node deployment stays unchanged.
• Then the number of nodes can allow the network access and the comprehensive coverage of the monitored region.
• The base station is permanent and distinctive, with limitless power generation and controlled wireless transmission power.
• The initial energy is represented as EN0.
• Since each sensor node consumes different amounts of energy, the energy usage of the network is varied.
In WSN, the energy usage is a major concern. As WSN battery cannot be refilled, there is a risk of losing power when the battery is taken. Data must be transferred from SNs to BS, which requires more power. A first radio energy usage approach is used and the power ENTX required by the nodes to deliver l-bit information is taken into account.
Here ENelec denotes the 1-bit transmission of data; D represents the distances among the receiver and transmitter,
The energy ENRX required by nodes to collect L-bit information can be estimated in the following way.
Initially, all the CHs in the network nodes transfer an advertising packet to announce that they have taken the position of CH. Every SN in the system determines the CH distance in this situation. In this approach, a node is associated with a given cluster by ensuring that its communication range from the CH of the cluster is minimal, and therefore it delivers data to CH. If the communication range among the CH and the nodes is higher than the data transmission among BS and the nodes, the SNs pass the data directly to BS. The cluster-shaping configuration is based on the computation of near-data transmission. As a result, the chosen CH can re-bunch the nodes in the data work using a communication ring calculated using the formula below:
Here x and y are the coordinates of CH nodes.
There is a thick blockage in the transmission of wireless signaldue to the complicated surroundings, resulting in multi-path effects. This impact causes a high level of uncertainty in the intensity of the receiving signal and the quality of link. The signal reduction of the link (SL) between the nodes can be regarded to adhere to the below channel estimation given the small impact of multi-path propagation.
Here SL represents the signal attenuation of the link; n is the co-efficient of signal attenuation, D denotes the distances among the transceiver nodes. A and X are the fixed value and the random element.
The approximate link quality (LIq) of node i might thus be calculated as,
The network has implemented a retransmission system. Whenever the performance of the connection is low, a packet would be retransmitted. When the link quality deteriorates, the volume of the network data transmission as well as the network energy consumption get increased.
3.5 Tabu Search (TS) Algorithm
The metaheuristic TS guides a local heuristic searching that can uncover the solution space before the optimization problem. A TS method is used to extend the above search engine by effectively replacing one neighborhood N* with the another as the search progresses (x). The motion is the action that guides the localized or the neighborhood search to repeatedly obtain the optimal solution x′
Special memory architectures are employed, which would be the key aspect of the TS technique for determining N*(x), and they are structured in such a way that allows for exploring space. To prevent the cycles, TS uses a particular memory form called recently-based storage, which is handled through the Tabu list, to prevent some movements from becoming re-instantiated for a set duration. Recently-based storage is used to select the qualities that occur in Tabu-active classification by assigning Tabu-active classification. The duration of repetition throughout which an ascribed is kept as Tabu which is termed as tabu tenure.

Algorithm 1 shows the pseudocode of tabu search protocol.
3.6 Grey Wolf Optimization (GWO)
The top predator is the Grey Wolf (GW) that implies it is at the head of the ecological food supply chain. GWs frequently decide to live. A collection of 5–12 people is its average size. Alpha (α) wolves are male and female wolves lead their packs. Parameter ‘α’ wolf normally makes the decisions regarding where to sleep, when to wake up, when to hunt, and so on. The entire pack is notified by the choices considered. Nevertheless, there is evidence of democratic behavior. Wolf ‘α’ is in charge of a pack of wolves. The entire group recognizes the meeting by bringing their limbs together. The beta (
Encircling Prey is explained here. Hunting in the GWO method is based on the
Here I denotes the present repetition, C and G are the coefficients,
Here rand1 and rand2 are arbitrarily created vectors [0,1].
Hunting is determined by the capacity to recognize location of the prey that aids the GW in encircling the food. The effective quest is led through the α routine basis. In fact,
The
Next, GW starts the prey-attacking procedure once the prey settles down. The frequency of C is reduced to narrow the C from the greatest value in order to statistically depict the procedure of the imminent threat of the prey. Further, |C| < 1 encourages the GW to assault (exploit) the prey. This improves the performance of GWO while conducting the search strategy.
Finally, the prey searching in GWs usually look at the best option by looking at the positions of
3.7 Proposed Grey Wolf Improved Particle Swarm Optimization with Tabu Techniques
The proposed method selects the best Cluster Heads and provides optimal routing path. In the proposed study, the cluster head selection technique involves combining the best features of the GWO method with an indexed searching. Particularly, the Coefficient vectors control in terms of exploration and exploitation of GWO (C and G). Whenever the coefficient vectors are less than one, the wolves assault the prey (exploitation), and at the end, the GWO method gets improved. The GWO algorithm, on the other hand, works worse in exploration than in exploitation because the knowledge about possible solutions from the search area is distributed among the answers in the packs as limited data.
Multi-hop Path Optimization using Improved Particle Swarm Optimization
A fundamental combinational optimization technique in a WSN is multi-hop route choosing among the cluster heads. During multi-hop route selection among the cluster heads, this article provides an enhanced PSO method. The searching repetition effectiveness of the PSO method for the routing process can be enhanced by increasing the fitness function and startup procedure of the algorithm.
The fitness function is a crucial component of multi-hop path finding optimization using PSO method. The major purpose is to lengthen the life of the network. To symbolize a multi-hop route from the source nodes to the BS as PTi, the throughout transmissions path planning that corresponds to particles in the PSO method is done.
Here Enri is the residual energy for node i, Enraverage is the residual energy average node. Ec denotes the consumption of energy.
The location and the speed of the particles in the method are initialized once the cluster head node is chosen, and the fitness value is built using the nodes power usage, remaining energy, minimal hop count, distances from BS, and link quality. In order to establish the best route discovery [28–31] in the complex and dynamic surroundings of farming, the Particle Swarm Optimization technique is applied.
In Fig. 2, the working flow of the CH selection and searching a routing path between the CHs is provided.
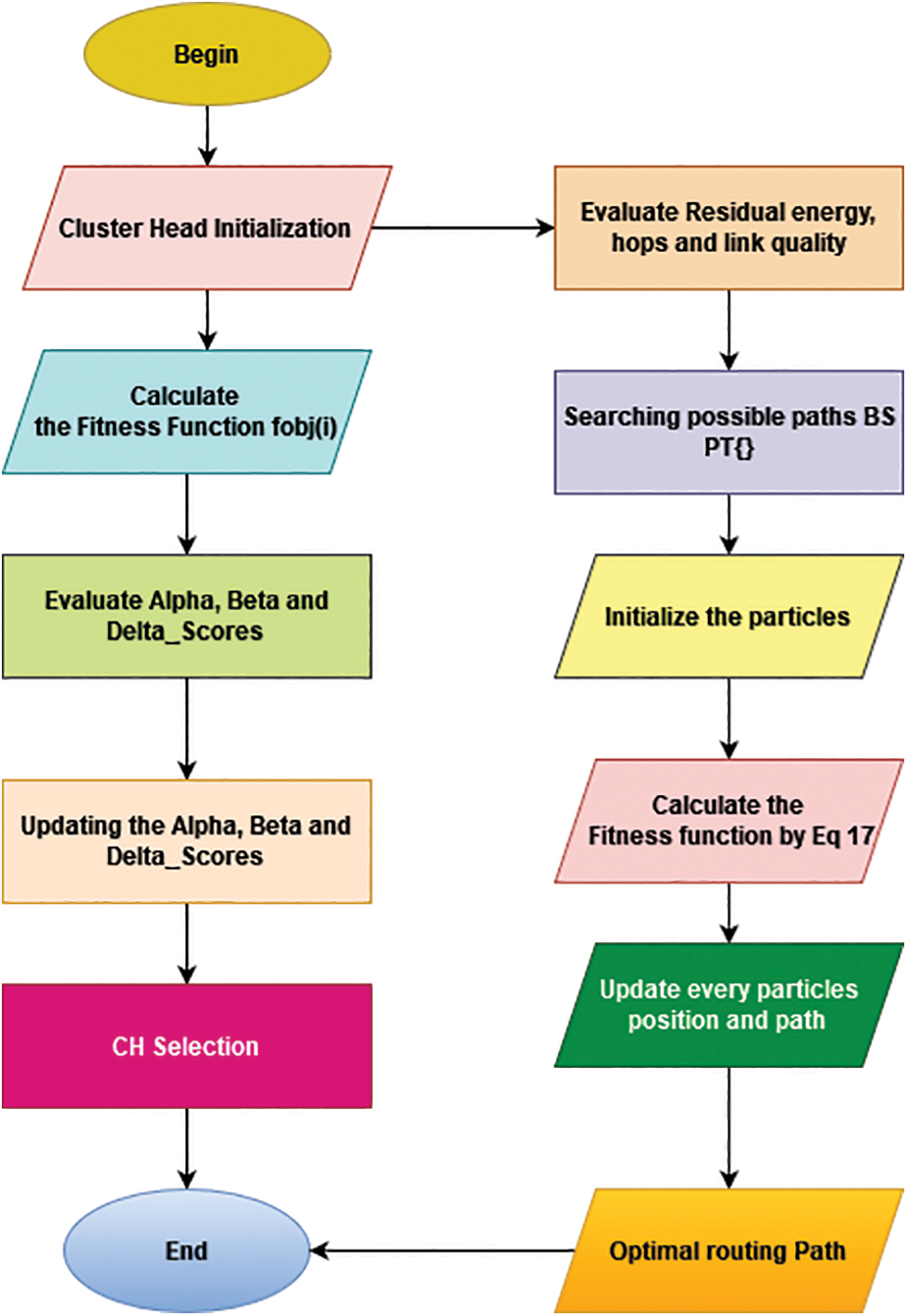
Figure 2: Flowchart of the proposed GW-IPSO-TS method

The algorithm 2 shows the selection of Cluster heads using GWO and provides a routing path between the CHs. Initially, the nodes are deployed, then the fitness values are calculated and then the alpha, beta and delta scores are updated. Then the optimal Cluster Heads are selected for data transmission. After the selection of CHs, the particles are initialized and then the fitness function is evaluated. Finally, the particle position and velocity are updated and the Tabu lists are used for finding the search space. Lastly, the optimum routing paths are determined.
The computations were carried out in an area of 400 × 400 m2. A total of 200 sensor network were planted at randomly and stayed stationary throughout the studies. MATLAB R2019 was used to run the simulations. Tab. 1 lists all the additional parameters utilized in the simulations.

The proposed method performed the following parameters such as average packet loss, end-to-end delay, number of alive nodes, average energy consumption, standard deviation and throughput. The experiment was evaluated by 1300 nodes and 800 rounds.
The proposed method has minimum average packet loss compared to LEACH [3], PSO [3], DUCF [28] and MSO-Tabu [2] as shown in Fig. 3. The proposed method GW-IPSO-TS has achieved 25.31% of average packet loss. Tab. 2 shows the average packet loss rate.
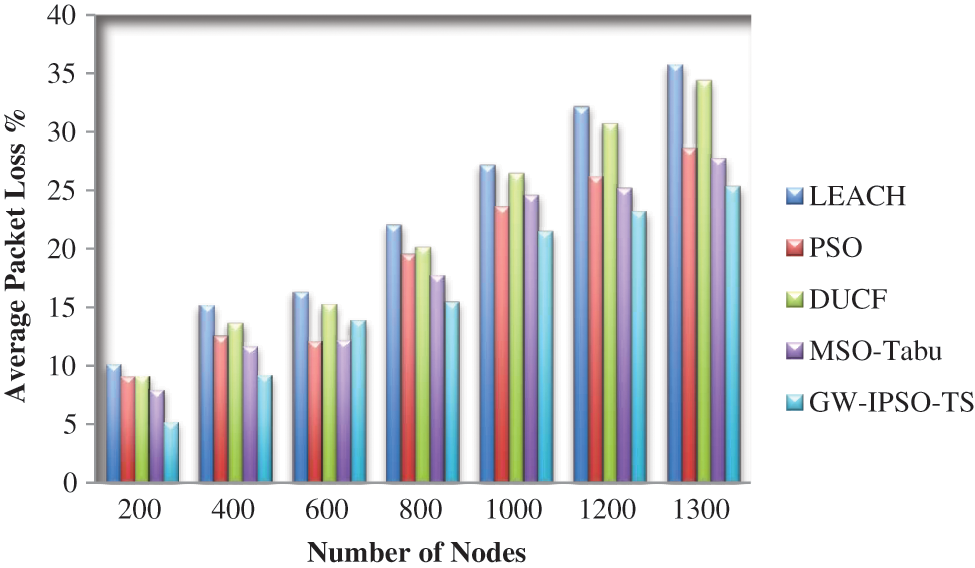
Figure 3: Average packet loss rate

The proposed method has minimum average end-to-end delay compared to LEACH, PSO, DUCF and MSO-Tabu. The proposed method GW-IPSO-TS has achieved 0.051001 s of end-to-end delay. Fig. 4 shows the average end-to-end delay.
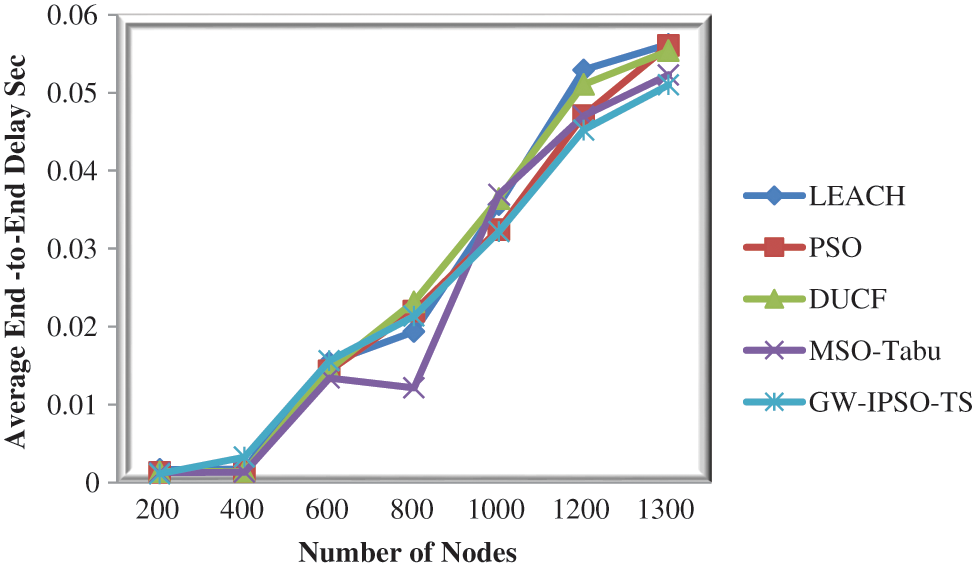
Figure 4: Average end-to-end delay
The proposed method has nearly 275 Alive nodes out of 300 nodes in 1300 rounds. Comparing with the other methods, LEACH has 120 alive nodes, PSO has 154 alive nodes, DUCF has 180 alive nodes and MSO-Tabu has 210 alive nodes. Fig. 5 shows the number of alive nodes present.
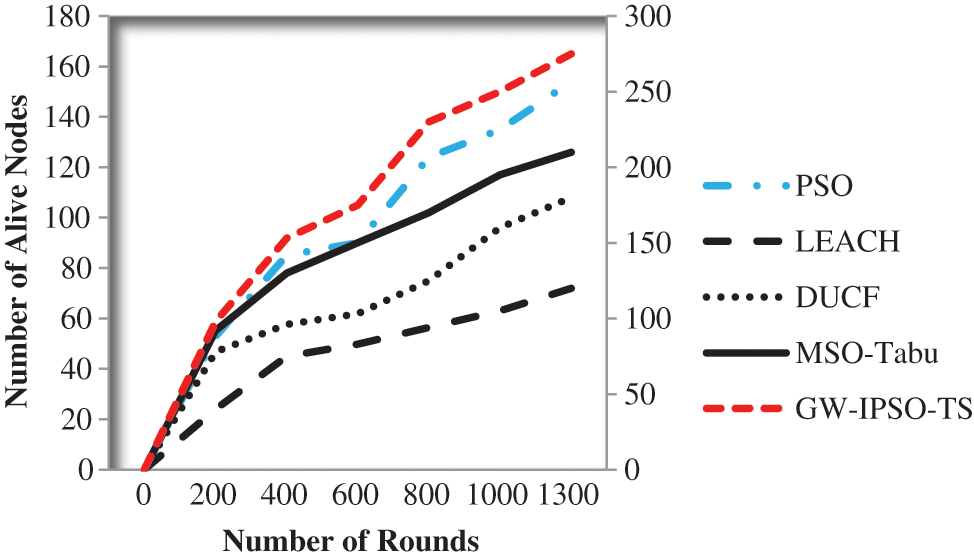
Figure 5: Number of alive nodes
The energy consumption effectiveness of network nodes, the average node energy usage per round Encr is divided by the present round of data transmission dttp that can be the thought of as the energy utilized when communicating 1 bit of information.
Fig. 6 shows the average energy usage of nodes in the network remains consistent, which would primarily be driven by the placement position of the network node.
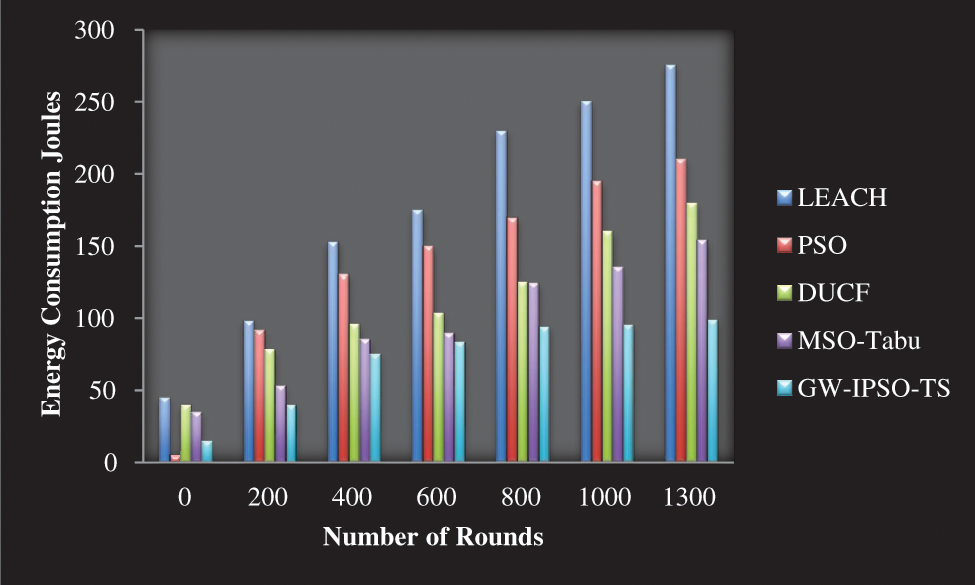
Figure 6: Energy consumption
The suggested model has a higher throughput than PSO, LEACH, DUCF and MSO-Tabu. Fig. 7 displays the suggested model throughput.
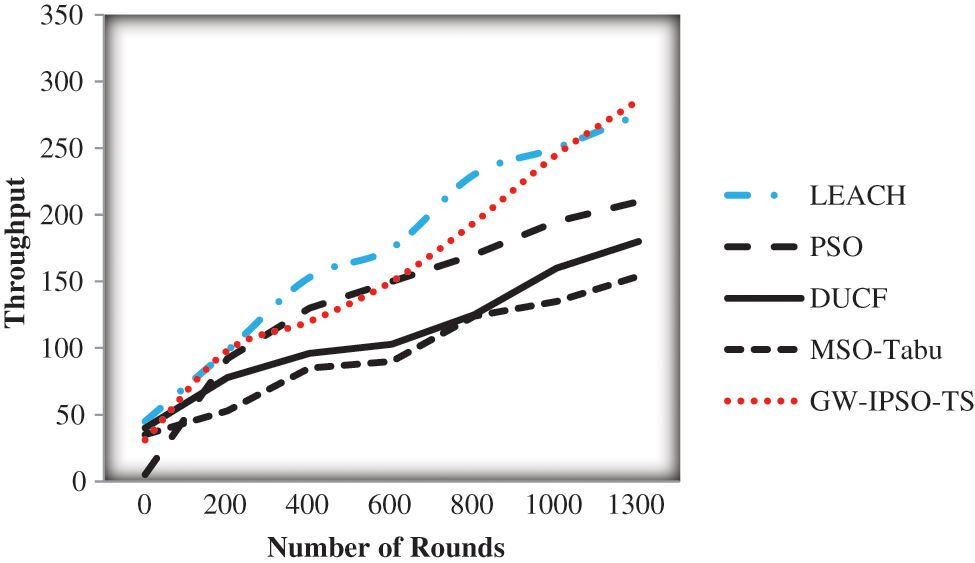
Figure 7: Throughput
The convergence curves of the proposed GW-IPSO-TS and known methods such as LEACH, PSO, DUCF, and MSO-Tabu are shown in Fig. 8. The curves depict the convergence of various optimum CHS methods as the number of observations increases. Again, for the suggested GW-IPSO-TS method, the convergence of the lowest best score to the smallest number of iterations can be noticed.
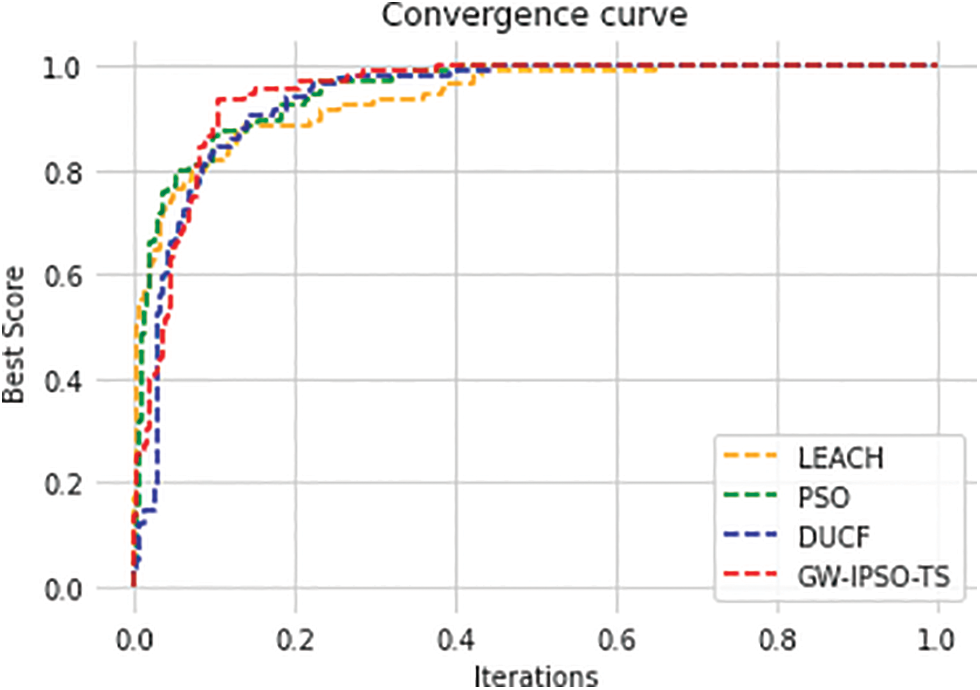
Figure 8: Convergence curve
One of the most important elements is conservation of energy for operating WSNs successfully and reliably. In the proposed method, a novel Grey Wolf Improved Particle Swarm Optimization with Tabu Search Techniques (GW-IPSO-TS) were used. The selection of Cluster Heads (CHs) and routing path of every CH from base station are enhanced by the proposed method. Following the formation of the clusters, the CH from every cluster is chosen based on the CH probabilistic reasoning of sensor nodes’. Moreover, four criteria (residual energy, length from the BS, distances from the center of the cluster, and intra-cluster distance) were used to determine the scoring of the sensor node. As a result, the power usage in the WSN is possible. The solution provided is for both saving the energy and networks’ adaptive. The proposed technique selected the effective CHs in respect to the system. Further, the suggested approach had optimized the routing and extended the lifetime of the network by selecting effective CHs. The proposed method optimized the best routing path, increasing the lifetime and energy efficiency of the network. Simultaneously, it had also improved the end-to-end delay and packet loss rate. The proposed GW-IPSO-TS method had enhanced the evaluation of alive nodes, dead nodes, network survival index, convergence rate and standard deviation of sensor nodes. In future, the performance could be improved by using the advanced optimization techniques.
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work through Larg Groups project Under Grant Number (71/43). Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R238), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia. The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: 22UQU4340237DSR20.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. X. Wang, H. Wu, Y. Miao and H. Zhu, “A hybrid routing protocol based on naïve Bayes and improved particle swarm optimization algorithms,” Electronics, vol. 11, no. 6, pp. 1–18, 2022. [Google Scholar]
2. S. Suganthi, S. Umapathi, N. Mahdal and M. Ramachandran, “Multi swarm optimization based clustering with tabu search in wireless sensor network,” Sensors, vol. 22, no. 5, 2022. [Google Scholar]
3. L. Nagarajan and S. Thangavelu, “Hybrid grey wolf sunflower optimization algorithm for energy-efficient cluster head selection in wireless sensor networks for lifetime enhancement,” IET Communications, vol. 15, no. 3, pp. 384–396, 2021. [Google Scholar]
4. S. Loganathan and J. Arumugam, “Energy efficient clustering algorithm based on particle swarm optimization technique for wireless sensor networks,” Wireless Personal Communication, vol. 119, pp. 815–843, 2021. [Google Scholar]
5. I. Das, R. N. Shaw and S. Das, “Location based and multipath routing performance analysis for energy consumption in wireless sensor networks,” Innovations in Electrical and Electronic Engineering, pp. 775–782, 2021. [Google Scholar]
6. Z. Wan, S. Liu, W. Ni and Z. Xu, “An energy efficient multilevel adaptive clustering routing algorithm for underwater wireless sensor networks,” Cluster Computing, vol. 22, pp. 14651–14660, 2019. [Google Scholar]
7. X. Fu, Y. Yang and O. Postolache, “Invulnerability of clustering wireless sensor networks against cascading failures,” IEEE System Journal, vol. 13, pp. 1431–1442, 2018. [Google Scholar]
8. D. Wohwe Sambo, D. Yenke, B. Förster and A. Dayang, “Optimized clustering algorithms for large wireless sensor networks: A review,” Sensors, vol. 19, 2019. [Google Scholar]
9. A. Shahraki, A. Taherkordi, O. Haugen and F. Eliassen, “Clustering objectives in wireless sensor networks: A survey and research direction analysis,” Computer Network, vol. 180, 2020. [Google Scholar]
10. M. Krishnan, S. Yun and Y. M. Jung, “Improved clustering with firefly optimization based mobile data collector for wireless sensor networks. AEU,” International Journal of Electron. Communicated, vol. 97, pp. 242–251, 2018. [Google Scholar]
11. M. Krishnan, Y. M. Jung and S. Yun, “An improved clustering with particle swarm optimization based mobile sink for wireless sensor networks,” in Proc. 2018 2nd Int. Conf. on Trends in Electronics and Informatics (ICOEI), Tirunelveli, India, pp. 11–12, 2018. [Google Scholar]
12. Y. Xu, O. Ding, R. Qu and K. Li, “Hybrid multi objective evolutionary algorithms based on decomposition for wireless sensor network coverage optimization,” Applied Soft Computing, vol. 68, pp. 268–282, 2018. [Google Scholar]
13. T. Kaur and D. Kumar, “Particle swarm optimization based unequal and fault tolerant clustering protocol for wireless sensor networks,” IEEE Sensor, vol. 18, pp. 4614–4622, 2018. [Google Scholar]
14. V. Varsha, J. Singh and M. Bala, “Tabu search based energy efficient clustering protocol for wireless sensor networks,” Global Journal of Computers & Technology, vol. 5, no. 2, pp. 302–309, 2017. [Google Scholar]
15. G. P. Gupta, “Improved cuckoo search based clustering protocol for wireless sensor networks,” Procedia Computer Science, vol. 125, pp. 234–240, 2018. [Google Scholar]
16. G. P. Gupta and S. Jha, “Integrated clustering and routing protocol for wireless sensor networks using cuckoo and harmony search based metaheuristic techniques,” Engineering Applications of Artificial Intelligence, vol. 68, pp. 101–109, 2018. [Google Scholar]
17. H. Wu, H. Zh and Y. Miao, “An energy efficient cluster-head rotation and relay node selection scheme for farmland heterogeneous wireless sensor networks,” Wireless Personal Communications, vol. 101, no. 3, pp. 1639–1655, 2018. [Google Scholar]
18. P. C. Rao, P. K. Ja and H. Ban, “A particle swarm optimization based energy efficient cluster head selection algorithm for wireless sensor networks,” Wireless Networks, vol. 23, no. 7, 2020. [Google Scholar]
19. S. Tabibi and A. Ghaffari, “Energy efficient routing mechanism for a mobile sink in wireless sensor networks using particle swarm optimization algorithm,” Wireless Personal Communications, vol. 104, no. 1, pp. 199–216, 2019. [Google Scholar]
20. T. Ahmad, M. Haque and A. M. Khan, “An energy efficient cluster head selection using artificial bees colony optimization for wireless sensor networks,” Advances in Nature Inspired Computing and Applications, pp. 189–203, 2019. [Google Scholar]
21. S. M. H. Daneshvar, P. A. Mohajer and S. M. Mazinani, “Energy efficient routing in WSN: A centralized cluster-based approach via grey wolf optimizer,” IEEE Access, vol. 7, pp. 170019–170031, 2019. [Google Scholar]
22. V. Varsha, J. Singh and M. Bala, “Tabu search based energy efficient clustering protocol for wireless sensor networks,” Global Journal of Computers & Technology, vol. 5, no. 2, pp. 302–309, 2017. [Google Scholar]
23. N. Mittal, U. Singh, R. Salgotra and M. Bansal, “An energy efficient stable clustering approach using fuzzy-enhanced flower pollination algorithm for WSNs,” Neural Computing and Applications, vol. 32, no. 11, pp. 7399–7419, 2020. [Google Scholar]
24. M. Jain, V. Singh and A. Rani, “A novel nature inspired algorithm for optimization: Squirrel search algorithm,” Swarm and Evolutionary Computation, vol. 44, pp. 148–175, 2019. [Google Scholar]
25. P. Wang, Y. Kong, X. He, M. Zhang and X. Tan, “An improved squirrel search algorithm for maximum likelihood DOA estimation and applicaion for MEMS vector hydrophone array,” IEEE Access, vol. 7, pp. 118343–118358, 2019. [Google Scholar]
26. B. Baranidharan and B. Santhi, “DUCF: Distributed load balancing unequal clustering in wireless sensor networks using fuzzy approach,” Applied Soft Computing, vol. 40, pp. 495–506, 2016. [Google Scholar]
27. J. Wang, X. J. Gu, W. Liu, A. K. Sangaiah and H. J. Kim, “An empower hamilton loop based data collection algorithm with mobile agent for WSNs,” Human-Centric Computing and Information Sciences, vol. 9, no. 1, pp. 1–14, 2019. [Google Scholar]
28. J. Wang, Y. Gao, C. Zhou, S. Sherrat and L. Wang, “Optimal coverage multi-path scheduling scheme with multiple mobile sinks for WSNs,” Computers, Materials & Continua, vol. 62, no. 2, pp. 695–711, 2020. [Google Scholar]
29. M. Kowsigan, J. Rajeshkumar, B. Baranidharan, N. Prasath and K. Venkatachalam, “A novel intrusion detection system to alleviate the black hole attacks to improve the security and performance of the MANET,” Wireless Personal Communications, pp. 1–21, 2021. [Google Scholar]
30. N. Bacanin, M. Zivkovic, T. Bezdan, K. Venkatachalam and M. Abouhawwash, “Modified firefly algorithm for workflow scheduling in cloud-edge environment,” Neural Computing and Applications, pp. 1–26, 2022. [Google Scholar]
31. K. Venkatachalam, P. Prabu, A. S. Alluhaidan, S. Hubálovský and P. Trojovský, “Deep belief neural network for 5G diabetes monitoring in big data on edge IoT,” Mobile Networks and Applications, pp. 1–10, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools