 Open Access
Open Access
ARTICLE
Optimized Resource Allocation for IoT-D2D Communication Using WSN
1 Department of Computer Science and Engineering, Holy Cross Engineering College, Vagaikulam, 628851, Tamil Nadu, India
2 Department of Computer Sceience, College of Computers and Information Technology, Taif University, P. O. Box 11099, Taif 21974, Saudi Arabia
3 Department of Industrial and Systems Engineering, College of Engineering, University of Jeddah, Jeddah, 21959, Saudi Arabia
* Corresponding Author: S. Arun Mozhi Selvi. Email:
Computer Systems Science and Engineering 2023, 45(2), 1789-1804. https://doi.org/10.32604/csse.2023.031341
Received 15 April 2022; Accepted 10 June 2022; Issue published 03 November 2022
Abstract
The need for a strong system to access radio resources demands a change in operating frequency in wireless networks as a part of Radio Resource Management (RRM). In the fifth-generation (5G) wireless networks, the capacity of the system is expected to be enhanced by Device-to-Device (D2D) communication. The cooperation and Resources Allocation (RA) in the development of Internet of Things (IoT) enabled 5G wireless networks are investigated in this paper. Developing radio RA methods for D2D communication while not affecting any Mobile Users’ (MU) communication is the main challenge of this research. Distinct performance goals such as practising equality in the rates of user data, increasing Network Throughput (NT), and reducing End-to-End Delay (EED) are achieved by RA. The study undertaken on optimising performance for various wireless networks is focused on in this research work. Proposing a polynomial-time Proportional Fair Resource Allocation Method (PFRAM), which considers the MU’s rate requirements, is the prime objective of this paper. Any Resource Allocation Method (RAM) can be used by the proposed method for MU, and the time and differing location channel conditions are the factors to be adapted with. Allotting more than one resource block is allowed by our PFRAM to a D2D pair. The automatic maintenance of battery-less IoT wireless devices’ energy level is done potentially using an Extensible Energy Management System (EEMS). Finally, the device’s Node Transmission Power (NTP) can be managed using an Energy-Saving Algorithm (ESA) designed in this work for Node Uplink Data Transmission (NUDT). The trade-off between the Packet Loss Rate (PLR) and NTP is balanced by the algorithm. The cost of NUDT’s average Energy Consumption (EC) is reduced by locating the optical NTP. In order to free much bandwidth for wireless information, NUDT conserves the harvested energy for minimising Radio Frequency (RF) Energy Transmission (ET). MATLAB simulations are used to assess the proposed EEMS. The IoT device’s NTP is managed using ESA designed for NUDT. The significant minimisation of channel hopping EED and the selection of the premium quality communication channel by the proposed framework are indications of the simulation results. 67.19% is the bandwidth to transmit DPs with the Bandwidth Allocation Algorithm (BAA), which is greater than the cases in its absence.Keywords
In the last few years, there has been a drastic increase in the requirement for high data rates with the development of new applications. The restricted resources of spectrum allotted in international agreements and the tremendous hike in the wireless mobility community’s size and need for high-speed multimedia communications are contrary to each other. Because of these growing needs, efficient spectrum/Radio Resource Management (RRM) is of utmost importance. This issue is expected to be addressed by 5G wireless networks. NT and spectral efficiency are expected to be enhanced by D2D communication in this scenario. The traffic at the Base Station (BS) is offloaded, and the local area services, context-based applications’ performance, and Quality of Service (QoS) are enhanced to enhance NT and spectral efficiency. Disruption in MU communication due to D2D communication is one of the significant drawbacks in the reuse of resources. One is required to address the functioning of RA for D2D communication if this need is fulfilled. Distinct performance goals are achieved using RA [1–5].
The internet connectivity that connects different physical and electronic devices and offers these devices a communication platform is defined as the IoT. In the context of enterprises such as hospitals, office buildings, and factories, the use of IoT is extensive. The IoT applications in enterprises are estimated to be around 2.1 billion devices by 2022. The Wireless Sensor Network (WSN), wireless technology, is used as a part of the IoT network in the enterprise context. Trust in data transmission, and the vast and economical generation of the network system are the merits of WSN. Due to the merits of WSN, hundreds and thousands of WSN devices can join the same network. Additionally, in a distinct network, the IoT platform enables the connection of WSN devices. Most of the WSN devices are wireless sensors and switches/digital controllers on the basis of the enterprise scenario [6–10].
From every layer of the International Organization of Standardization/Open Systems Interconnection model, various issues addressing strategies are integrated to study RA for WSN extensively. Since cross-layer control and RA in the WSN framework have the ability to help transfer information between different layers, they have attracted substantial attention [11].
Nevertheless, still, there is relevance to the fundamental problem of serving wireless IoT devices with multiple requirements by allotting them confined network resources. With the aim to introduce and validate support among interacting devices, RA and issues related to performance analysis for IoT systems are addressed in this paper, determined by the need for emerging challenges mentioned above. Improvement of IoT systems’ performance is the prime goal of this research paper. Wherever essential, the enhancement techniques and queueing theory analysis are used to address the issues. The forthcoming wireless network approach’s RRM is believed to give comprehensive knowledge of the results. Low NT provided by RRM through a substantial equality is obtained by its rates of user data. Contrarily, substantial equality is failed to be maintained among the rates of user data through high NT provided by RRM. Still, the balance between throughput and equality among users is maintained by the PFRAM. Thus, the PFRAM for D2D communication that can work with any RA technique deployed by the BS for MU is focused on in this dissertation [12–18].
WSN device’s EC is reduced while reducing the NTP of WSN device since radio function consumes most of WSN’s energy. Nonetheless, because of low NTP, there could be a loss of the transmitted packet. The Energy Integrated System (EIS)-NTP, where the average EC is minimized, is adjusted using an ESA that was designed on the basis of the model. The radio function for EC sends more energy than it receives according to the hardware characteristics. With the aim to introduce and validate support among interacting devices, RA and issues related to performance analysis for IoT systems are addressed in this paper, pushed by the need for emerging challenges mentioned above. The forthcoming wireless network approach’s RRM is believed to give comprehensive knowledge of the results [19–25].
An extensive study on RA for wireless networks has been carried out. There has been a presentation of cross-layer control and RA in WSN architectures from physical to transport layers like hybrid wireless-wireline networks, sensor networks, cellular, and ad-hoc. The development of networks containing billions of smart devices that require ultra-low latency, ultra-high reliability, and improved QoS will be necessitated by the proliferation of the IoT [26]. In IoT systems, one of the most significant components is WSNs. Indeed, for further processing, its fundamental aim is collecting data from the environment and pass it to central/distributed controllers. The IoT consists of sensors and is supposed to be more innovative, i.e., without any human interventions and optimal decisions when compared to traditional WSNs, depending on their limited resources and the crucial nature of the IoT environment Because RA in WSN is very active and requires connectivity to billions of devices, it has no direct application in IoT, but many researchers have experimented in this area. As a result, several new challenges and unique techniques emerge with which flexibility, efficiency, and development are essential for development [27].
There has been an extensive study of the max-min problem in the operations research domain. An ideal solution found in a non-simplex-based algorithm developed by the author solves a maximum and minimum (Max-Min) allocation issue with nonnegative integer variables. A study related to fairness has been carried out in both Medium Access Control (MAC) and the network layer [28]. A well-defined polynomial-time algorithm has been developed in recent times for the rate allocation calculation with a limited network lifetime related to two-tiered WSN. The problem associated with guaranteed Max-Min maximum NT bandwidth is solved using a Linear Programming (LP) formulation. Besides, a polynomial-time optimal algorithm solves the issue related to Lexicographical Max-Min Bandwidth Allocation (LMMBA). The author investigated RA for waning relay channels under each power limitation that belongs to Max-Min issues. But in the three-terminal network environment, it is being investigated [29].
For wireless networks, tremendous research work has been attempted on distributed optimization. By not focusing on cross-layer optimization, a few of these algorithms shed more light on issues related to channel assignment/power control [30]. In a disseminated manner, cross-layer optimization is addressed by research endeavours. Generally, power control, channel assignment, and scheduling are assumed to be an issue, thus proposing distributed optimization algorithms. Consequently, no interference exists as the authors believe that there is no overlapping in the time-sharing sub-intervals. Routing, scheduling, and power control are collectively considered during the investigation of a cross-layer optimization issue for cognitive radio networks. For multi-cell, multi-user, Orthogonal Frequency-Division Multiple Access (OFDMA) networks, the performance of adaptive modulation, power control, and channel assignment is proposed by a distributive non-cooperative game [31].
The resource-limited IoT devices that have confined computation, networking capabilities, and power spend most of their lives in sleep mode, and only when there is a necessity to swap data do they wake up. Hence, this kind of device requires significant energy-efficiency. Data requests from any other awaken node that is capable of storing a copy of the requested data are satisfied so that caching can enable to retrieve substance even though the network is constrained. So, in any IoT device, caching can be enabled or else it can be considered just on dynamic nodes. The tremendous benefits of caching, even in IoT devices with less capacity, are revealed in this research work [31–35].
3.1 Proportional Fair Resource Allocation Method for D2D Communication
We suggest a new PFRAM-RA to D2D communication in this chapter. We analyze a case where the BS has previously scheduled such resource blocks for MU. We suggest that such resources block can be reused by D2D operators without interfering with MU communications. We ensure that each MU receives the minimum needed rate in each sub-frame to preserve its QoS. If Signal To Interference Plus (SINR) obtained at BS exceeds the SINR limit needed to guarantee the minimum rate for MU, the SINR gap can be used to apportion power to D2D operators. We show that determining Maximum Weight Bipartite Matching (MWBP) in a whole bipartite graph in which the two vertex sets are now the set of resources and the set of D2D pairings can be transferred to the problem of RA for D2D operators. We use the MWBP to assign single and multiple resource blocks to D2D operators. For D2D operators, PFRAM-RA is dependent on not only the channel quality of the D2D link but also on interference caused by D2D communication to MU transmission. As a result, PFRAM rates for D2D pairs in close proximity to the base station may be very low [36–39].
Furthermore, resource distribution for these users may be on a periodical basis. Transmission Control Protocol (TCP)-based apps may suffer as a result of this, as they will timeout and then retransmit the same content. To solve this issue, we analyse the challenge of locating PFRAM-RA with each D2D pair receiving a maximum of a predetermined number of resource blocks. This minimises the service process’s burstiness. We can strike a compromise between enhancing system throughput while being fair for each sub-frame by altering the maximum resource value, the block which can be assigned to a D2D pair.
For enhancing network throughput and spectral efficiency, it is beneficial to reuse the radio resources in the uplink for D2D communication. Only the uplink resources will be concentrated for the remaining work. If the same resources are shared by the MU and the D2D pair, the D2D receivers are interrupted by MU, whereas interruption is caused to the BS by the D2D transmitter in the uplink spectrum sharing. Fig. 1 shows the network model to be applied in interference analysis.
Figure 1: Interference between CU vs. D2D
3.3 Dynamic Resource Allocation with IoT Device to Flexible Services
IoT devices can provide many heterogeneous network interfaces to share their resources. Predominantly, two objectives are fulfilled in this section: (1) for Mobile Nodes (MNs) in catastrophe areas, an inventive and real-time mobility model is proposed; (2) the Radio Networks (RN) are placed in less number so that the mobility model that precedes each MN can be linked with the backbone network. Later on, numerous mobile RN are required to be placed so that at least one RN fully covers each of the target squares under constrained transmission range, that is known as Square Disk Cover (SDC) problem. That is known as the Square Disk Cover (SDC) problem. In Fig. 2, this example has been described. In this part, we talk about the Binary Integer Programming Algorithm (BIPA), the Circle Covering Algorithm (CCA), and the Square Disk Cover (SDC).
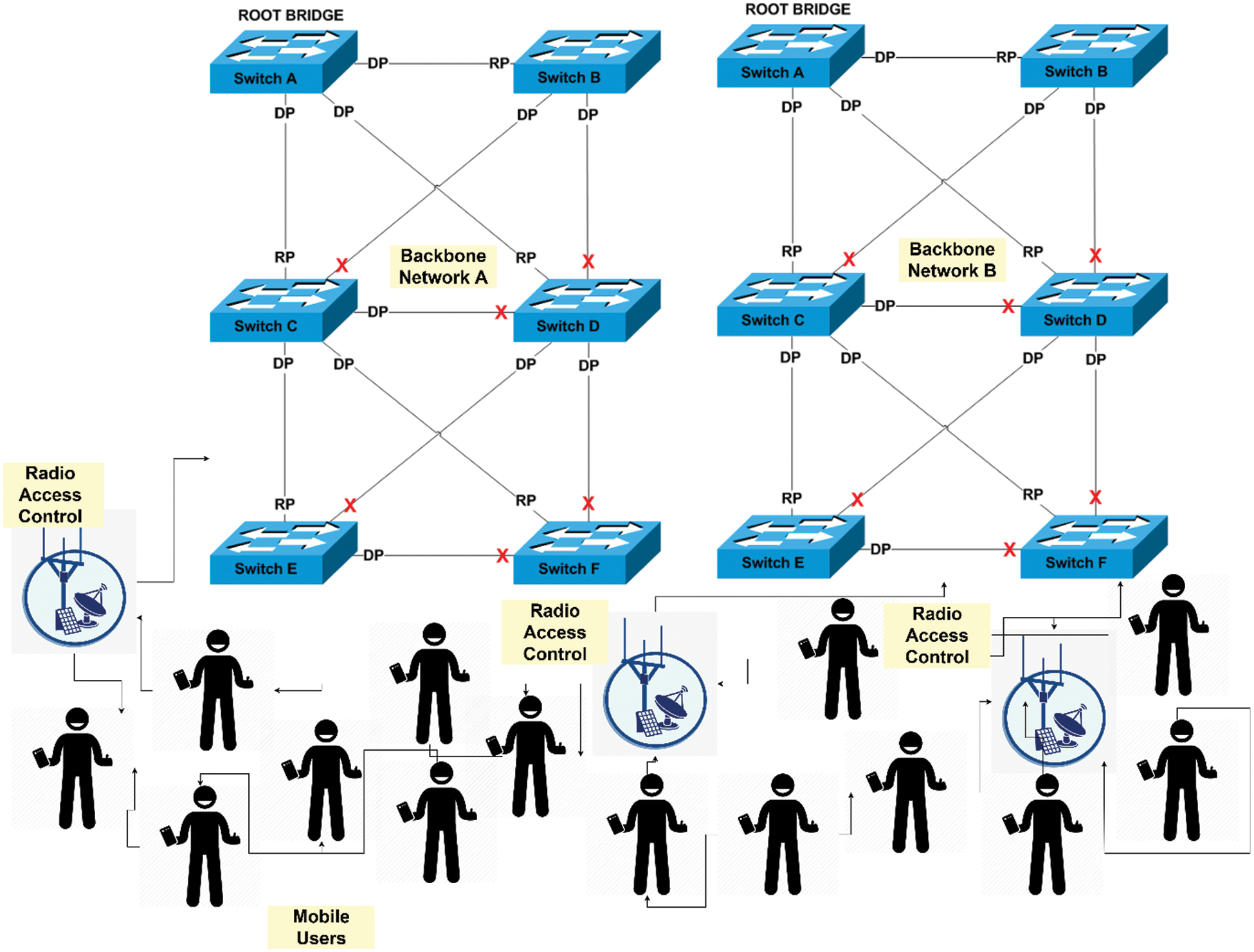
Figure 2: A real-life scenario of backbone network
Many services may use all or part of the interfaces’ resources. Each interface can provide access to various resources (e.g., data rate, computation, etc.). To meet their requests, we believe that such services are adaptable enough to distribute their allocations among several interfaces. We present a mathematical concept of distributing services for interfaces having heterogeneous resources inside one or more rounds using Mixed Integer Linear Programming (MILP). We demonstrate that such a problem is Nondeterministic Polynomial (NP)-complete and propose two techniques for approximating the optimum solutions for large instances. By calculating the average cost of interface resources, the first algorithm prioritises the most demanding service requirements. The second approach computes the resource share of the demands first and then assigns the much more demanding before picking at random among those equally demanding shares. The numerical findings show how the activation cost affects the service splits amongst interfaces. We also look at how the number of rounds affects total costs, using two approaches: (i) using the fewest rounds possible to achieve viability, as well as (ii) using several rounds as needed to gain the lowest overall cost at the disadvantage of utilising more rounds. Whenever the number of services is expanded, the cost difference between the two methods of the two boundaries (cost vs. task count) becomes more pronounced.
3.4 Algorithm for D2D Resource Block Allocation
Step 1. Set X: Sorted list of MU
Step 2. Set Y: D2D pairs in WSN
Step 3. CIxy: Channel input between MUx and MUy
Step 4. CIpq: Channel input between D2D pair
Step 5. CIBx: Channel gain between eNode_B and MUx
Step 6. CIrs: Channel input between eNode_B and D2D pair
Step 7. NTEx: Node Transmit Energy of MUx
Step 8. NTEy: Node Transmit Energy of D2D transmitter
Step 9. NTEp: Node Transmit Energy of eNode_B
Step 10. NNErb: No. Node RB fixed to MUx
Step 11. X = 1
Step 12. While x = X Do
Step 13. Select node RB with xth maximum threshold level;
Step 14. Choose D2D-‘A’ with low channel input to the MU with the xth value;
Step 15. Down Link ← N0 + N1;
Step 16. Down Link ← N0 + N1;
Step 17. f x ≥ γ Down Link, Target and d ≥ γ DL d, Target Then
Step 18. Common resource of MU with the xth maximum threshold with D2D pair x;
Step 19. D = D-{x};
Step 20. Else
Step 21. Not available node RB to D2D pair x;
Step 22. End If
Step 23. x = x + 1;
Step 24. End While
3.5 Algorithm for Mobility Model for MNs
Step 1. While N = 0
Step 2. For Each BSx,y
Step 3. If Ix,y,z > MNx,y,z
Step 4. Ix,y,t+1 = Ix,y,z-ξMNx,y,z
Step 5. Else
Step 6. Reorder (8, MNt, sx,y, Cxy)
Step 7. Ix,y,t+1 = 0;
Step 8. End If
Step 9. End For
Step 10. MNt+1 = MNt+2;
Step 11. t = t+1;
Step 12. End While
An Energy Integrated System (EIS) that is an example of an IoT system is proposed in this section. A Wireless Local Area Network (WLAN) based on Wireless Fidelity (Wi-Fi) as well as a WSN based on ZigBee have been included in EIS. The entire EIS, including the ZigBee dongle and smart gateway, obtained from the PCB, structures the EIS in hardware. Through executing hardware modification to the conventional ZigBee router device, the design of EIS is done. When the customized ZigBee packets, namely, the EP of the paper, are passed via the Radio Frequency Power Amplifier (RF PA), they are amplified by preparing a high-gain RF PA to the ZigBee router’s RF terminal. The RF energy that is the manageable RF energy resource for the EIS is treated so by the energy-enhanced carrier wave. The EIS is designed to fix an RF energy harvesting adaptor instead of conventional batteries on a ZigBee end-device. In the experiment platform, the ZigBee end-device functions like a wireless temperature sensor node. In accordance with the real-time application, the sensors or controllers can be of any type. The ZigBee end-device receives the supply energy of the RF energy harvesting adaptor. The harvested RF energy is converted by the adaptor into Direct Current (DC) energy and uses a power management circuit for storing the energy in a supercapacitor. The activation of a ZigBee end-device is done while charging the supercapacitor to a threshold voltage. Networking is the primary step of the ZigBee end-device. The networking process’s energy needs are fulfilled by the stored energy in the supercapacitor. Thus, the real-time ZigBee device’s characters are the basis of the supercapacitor selection.
The uniqueness from the perspective of software is that there is an adaptive energy management system that controls the ZigBee end-device’s energy level. The intensity of RF energy charging can be adjusted adaptively in accordance with the energy ZigBee end-device’s energy feedback. The maintenance of supercapacitor’s voltage level on the ZigBee end-device can be done in the range of 3 to 4 v with the aid of the mechanism. The ZigBee end-device can thus be kept running by the system. The designing of energy management protocols is enabled with the help of the system. In order to exchange energy-information between the DEIN system and the ZigBee end-device, it works. Moreover, on the basis of the energy-hungry degree’s periodic report obtained from the ZigBee end-device, the EIS is helped by this system for a dynamic adjustment of RF energy charging intensity.
The EIS proposed in this article is shown in Fig. 3, and it comprises the smart gateway setup as an Access Point (AP), Wi-Fi devices, a ZigBee dongle configured as a ZigBee coordinator, and the EIS. Including the ZigBee dongle, the smart gateway manages two wireless networks: Wi-Fi standard WLAN as well as ZigBee-based WSN. The EIS is connected to the rest of the world via an ethernet wire that connects the smart gateway to the network switch. By linking to the smart gateway, Wi-Fi devices like the iPad and laptops can access the internet. In terms of network performance, the EIS functions as both a ZigBee router and a ZigBee end-device. The ZigBee dongle is in charge of them all. The Linux computer running within the smart gateway facilitates data connection between them because the ZigBee dongle is inserted into a USB port on the smart gateway. As a result, the smart gateway can facilitate data flow among all of ESI’s devices. As a result, network users with the ESI in command can operate and monitor ZigBee-based gadgets in the ESI from a remote location. IEEE 802.11n, as well as IEEE 802.15.4, are the Wi-Fi and ZigBee standards, respectively.
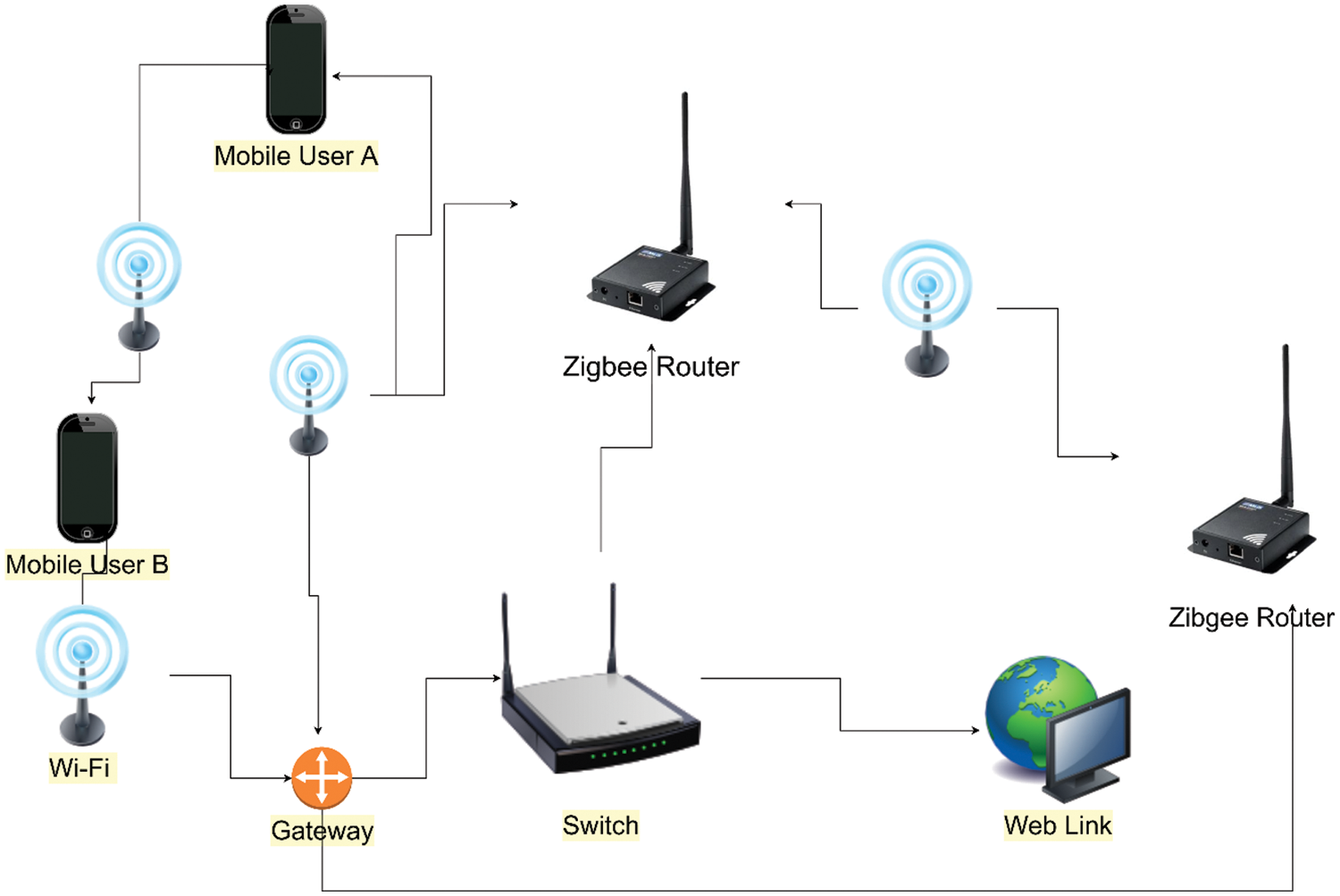
Figure 3: Network topology of EIS
3.7 An Extensible Energy Management System
The charging process between the voltage boosting stage and the voltage maintaining stage is described in Fig. 4, which shows a planned Extensible Energy Management System (EEMS) for maintaining the EIS’s energy level (VMS). The voltage feedback technique is used in the VMS to perform adaptive charging control and maintain the EIS constantly alive by managing the voltage level of a supercapacitor upon that battery-less EIS. The EIS is in power-off mode at the start of the voltage boosting stage, and the charging command from the ZigBee coordinator instructs the EIS to broadcast the EPs with highest charging intensity at regular intervals. The voltage regulator on the EIS gets enabled after the voltage of a supercapacitor on the EIS hits 3.9 v. That powers this ZigBee module as well as its peripherals, enabling the ZigBee function. After that, the voltage-maintenance stage begins.

Figure 4: Flow of EIS’s energy level
Every 5 Sec, the EIS’s ZigBee module detects the supercapacitor’s voltage but also grades its energy-hungry level in the VMS (EHL). As per the acquired voltage, the EHL is divided into three levels, with the matching grading standard shown in Fig. 4. The high EHL classification lowers the detected voltage. The present EHL is classed as Ll if the observed voltage is 4 v. If the voltage is decreased to 3.9 v after a while, the current EHL remains L1 until the voltage drops to 3.6 v. The EHL will be upgraded to L2. After the EHL has been validated, the value of a charging intensity degree would be retrieved from the most recently received EP and compared to the most recently detected EHL. If they’re the same, the voltage detection process repeats in 5 Sec. A charging command packet will be transmitted from EIS to a ZigBee coordinator as feedback if their values are not assigned to such a charging command packet. Following that, the feedback will be given to the smart gateway, and the coordinator will generate the charging command packet based on the smart gateway’s choice, which will subsequently be delivered to a EIS for updating the charging intensity.
We start by evaluating the performance of existing WSN scheduling techniques. We alter the range between 100 and 200 m in steps of 10 m to study the system level performance using varied range values. We measure the fairness of average user data rates using Jain’s fairness index metric to analyze the accuracy of our suggested scheduling algorithm. Let DRi denote the average data rate of user ‘i’ over N sub-frames. If the total number of users in U, then the Fairness Index (FI) is defined as,
If the FI is near 1, it indicates that the user data rates are fairly distributed. Figs. 5 and 6 show how NT changes when the distance between the D2D transmitter and receiver grows for both the single resource block as well as multiple resource block allocation schemes, respectively. Both graphs show that when the D2D range rises, the D2D User Throughput (UT) and NT drop, while the UT remains nearly constant. As a result, the fact that D2D communication is possible within a given range is quite important. D2D pairs should be close to each other in order to benefit from increased network performance increases.
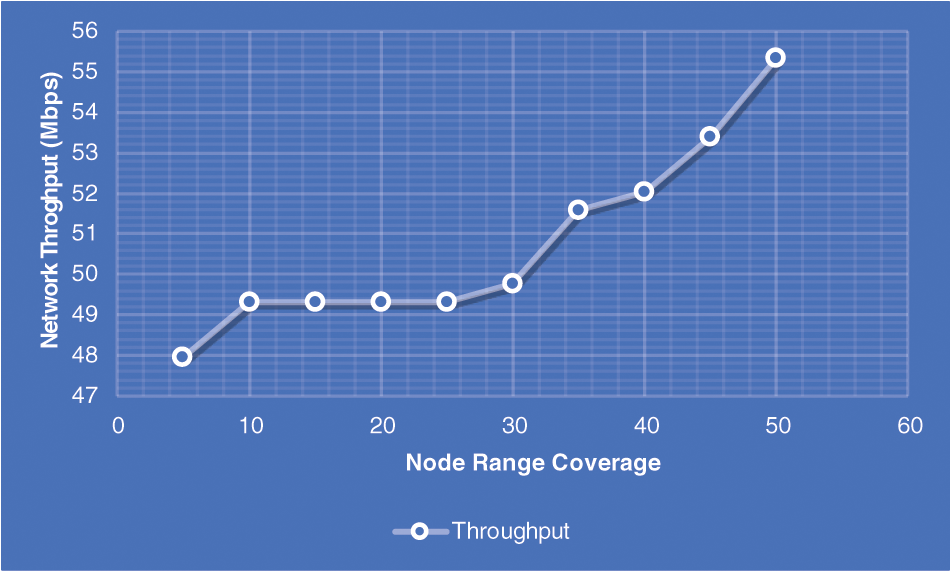
Figure 5: Performance of NT vs. D2D communication (Node 10–50)

Figure 6: Performance of NT vs. D2D communication (Node 10–100)
Figs. 7 and 8 show how the NT changes as the number of D2D pairs throughout the cell grows. We see an increase in the D2D-UT and overall NT. We also notice that the throughput of CUs has not degraded significantly. As a result, we may determine that such a network can support D2D pairings while still ensuring CU QoS. Additionally, increasing the maximum number of RB in a D2D pair can increase overall NT and D2D-UT.

Figure 7: Performance of NT vs. Single- Resource Allocation (Node10–50)

Figure 8: Performance of NT vs. multi- resource allocation (Node10–100)
4.1 Allocation of Heterogeneous Resources of an IoT Device to Flexible Services
Multiple heterogeneous network interfaces allow IoT devices to share their resources. Many services may use all or part of the interfaces’ resources. Every interface can provide various associated resources (e.g., energy computation, network data rate). We trust that those services are flexible enough to distribute their allocations among several interfaces to meet their requests. This paper presents a mathematical model for distributing services for interfaces having heterogeneous resources for one or more rounds using Mixed Integer Linear Programming (MILP). We establish that such a problem in NP provides two algorithms for approximating the optimal solution in big cases. By evaluating the average energy cost for interface resources, the algorithm prioritises the much more demanding service requests. The second method calculates the resource shares of the demands first and then distributes the most demanding by randomly selecting equally demanding shares. The numerical findings show how the activation cost affects the service split amongst interfaces. We also explore how the number of rounds affects total costs, using two approaches: (i) by using the fewest rounds to attain feasibility, or (ii) by using several rounds as necessary to achieve the lowest overall node energy cost at the disadvantage of utilising more rounds. Once the number of services is expanded, the cost difference between the two methods of the two boundaries (minimum rounds vs. node energy cost) becomes more pronounced.
4.2 Resource Allocation with Multiple Rounds
We used the following setup: we evaluated an IoT device with two interfaces, each with ten R1 and eight R2 units. For the first interface, the per-unit utilisation cost was X1 = (25, 35) for (R1, R2), respectively. The cost per unit for the second interface was fixed as X2 = (35, 45). The activation costs for the two interfaces are IF1 = 110 and IF2 = 120, respectively. We set up our simulator to randomly distribute 4, 7, or 10 services with varying resource demands of high variability.
For example, one service might have a dominating share of R1, another might have a dominant share of R2, and a third would want the same amount of both resources. To obtain insight into cost sensitivity, we altered the number of rounds R. It is clear that more than one round is required. For example, to fully serve 10 services, at least six rounds are required (Rmin = 6). The total cost decreases as the number of rounds increases, as expected. When Rmin is applied, the maximum overall cost for a specific configuration is incurred. As previously stated, this is expected because increasing R makes lower-cost resources available and hence utilised. As a result, as we add more rounds, the total cost decreases. Utilizing more than Rmax rounds is ineffective because we have already used the lowest-cost interface for every resource in each cycle.
On the other hand, if we want to lower overall the leftover capabilities, we may better utilise the interfaces’ available resources as well as serve the needs with fewer rounds; we should therefore employ the shortest number of rounds possible (Rmin). In this case, we increase the amount of resources used in each round while also raising the total cost.
4.3 Resource Allocation to Minimize the Energy Cost
Different simulation tests are carried out to evaluate the algorithm’s performance. The simulation tests use a range of RF-ET distances, ranging between 0.3 and 0.9 m with a 0.2 m step. Whenever the transmission antenna gets adjusted opposite to EIS (A)/EIS (B), the EIS will send 17000 EPs with about the same (127) bit-length for every time in each trial (B).
The NUDT of an EIS is based on the DC energy, which was captured through receiving 17000 EPs. When a varied RF-ET distance d is applied, Fig. 9 displays the maximum number (Duplink) of bits that can be communicated as uplink data that refers to the EIS’s transmission power. As the transmission power of the EIS grows, so does Duplink; hence more energy is gathered for NUDT. When a more extended RF-ET distance d is used, however, fewer NUDT can be communicated in association with relation to the same EIS because a more extended ‘d’ causes more energy loss within the air, as well as the available RF energy for the EIS’s receiving antenna. As a result, with less gathered energy, fewer NUDT can be communicated.

Figure 9: Node energy consumption vs. no. of rounds
When the RF-ET distance varies in sequence, Fig. 10 illustrates the total EC of the system during a successful NUDT procedure with regard to EIS transmission power. From the time the EIS starts transmitting EPs for charging an EIS to the time, the NUDT gets successfully transferred to the ZigBee coordinator, the NUDT procedure has been successful. The total EC is produced by sending 17000 EPs from DEINR to a ZigBee coordinator and passing the NUDT from DEINR to a ZigBee coordinator. When the EIS transmits EPs and forwards NUDT at a greater transmission power, it generates more EC. Moreover, as shown in Fig. 11, a greater EIS indicates that the EIS can transmit and transfer more NUDT. Increasing NUDT forwarding also increases EC. As a result, the system’s total EC rapidly rises as EIS rises. When EIS is fixed, however, less EC is produced during the NUDT process while ‘d’ is increased. Longer ‘d’ results in more energy loss, mainly in the air, lowering the amount of DC energy gathered. As a result, the EIS forwards less NUDT, weakening the total EC.
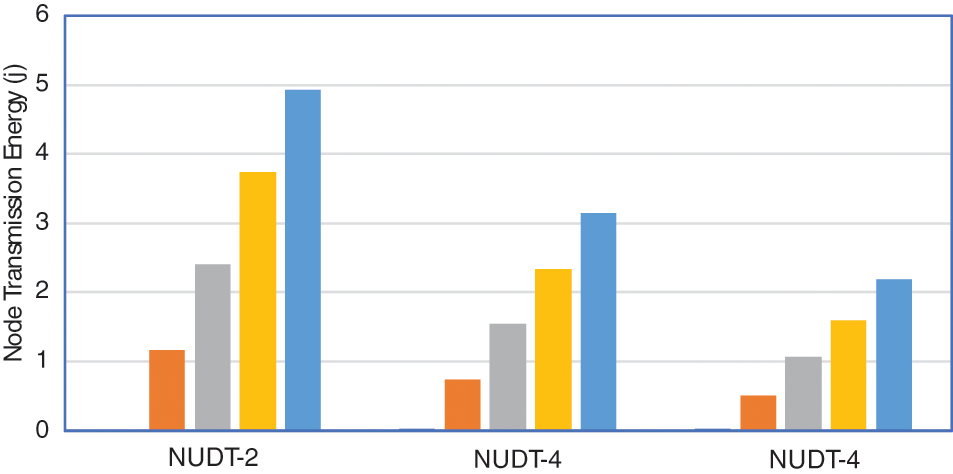
Figure 10: Node transmission energy with NUDT (Coverage range: 2–4)
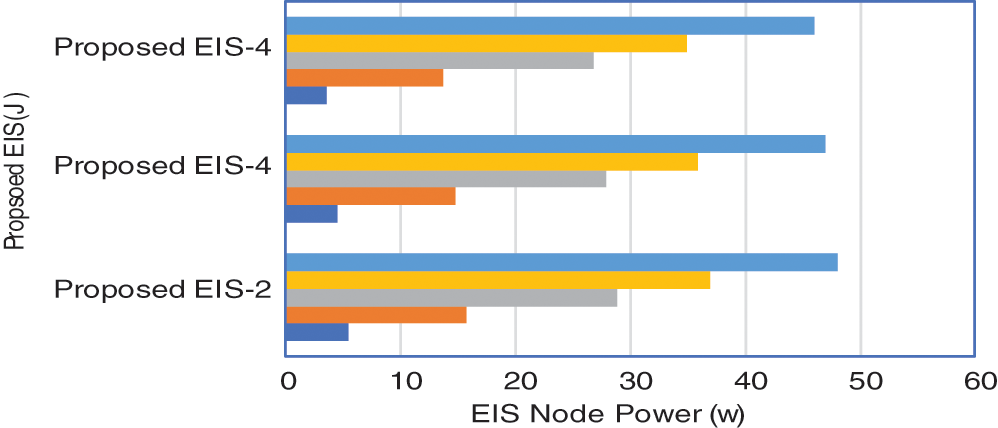
Figure 11: Node transmission energy with proposed EIS ( Coverage range: 2–4)
An EC per bit of a NUDT with regard to argument R is shown in Figs. 12 and 13 when a different RF-ET distance ‘d’ is used. The plots show that R is just a concave function with respect to R. As per the mathematical model, a small increase in R will raise the EIS’s transmission power, which will increase the EIS’s captured DC energy, that in turn increasing the number of NUDT. Even though EISs-EC increases, the NUDT grows at a faster data rate than the overall EC. As a result, the system’s spent energy per bit for uplink data drops first. With an increase in R, the EIS grows faster, and the EIS’s-EC grows faster than the NUDT. Because more NUDT means more EC, DEINT is forwarded in this, and this is the case. As a result, the system’s EC per bit for uplink data rises. The system’s EC per bit for NUDT is minimised for every distance ‘d’ when the method is used. The best performance can be achieved only by using the ideal R produced by the RA algorithm. Both transmission power and time allocated for NUDT are then calculated using the optimal R.
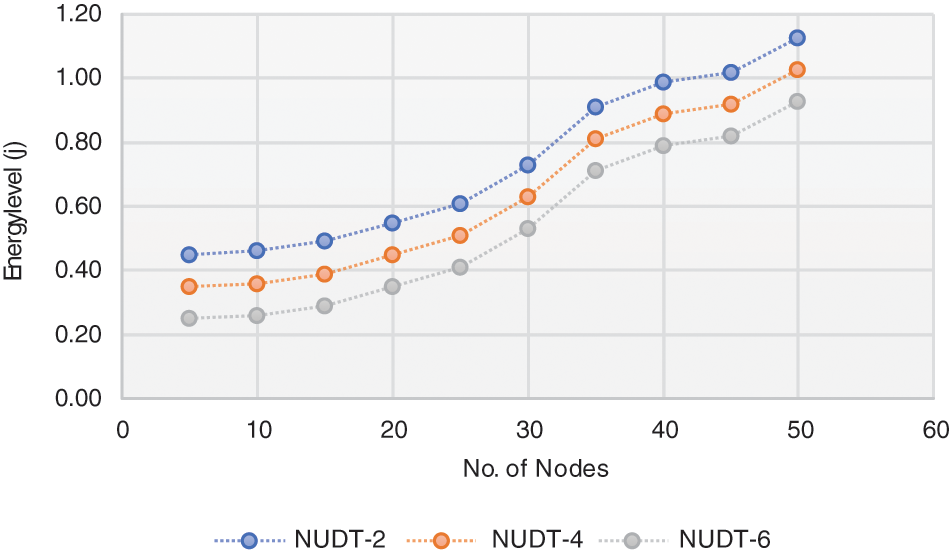
Figure 12: Node energy consumption vs. NUDT

Figure 13: Node energy consumption with proposed algorithm vs without algorithm
Although D2D communication backing WSN may improve the system capacity and spectrum efficiency, including D2D users can bring serious interference to the MU, causing MU communication to be hampered. As a result, effective D2D-RA solutions must be designed to improve spectral efficiency while also reducing interruption to the MU in terms of maintaining their QoS. We address this problem in this thesis and provide novel RA algorithms for the D2D underlying network. We’ve suggested a PFRAM that complies with MU’s rate criteria. The suggested PFRAM has the potential to work with any RA schemes in MU and can adapt to changing channel conditions across time and space. In a single-cell scenario, simulation findings prove capacity improvement over the current WSN as well as obtaining PFRAM among D2D users. This study looks at how to allocate IoT resources, analyse throughput and latency in IoT devices with relay nodes, schedule virtual machines, and use caches in IoT systems that handle dual kinds of network traffic. The mathematical formulation of the research cooperation and RA problems, the assessment of such systems metrics, algorithmic construction as well as computing complexity, and numerical results contribute to the scope of this research work. This research work used the RF-ET to relieve the pressure of quickly increasing energy management tasks due to the significant expansion of battery-powered IoT devices. As per the experiments, despite the RF-ET absorbing a portion of the bandwidth intended for data transmission, an average of 70.16% of the bandwidth is left for traditional wireless information transfer. According to the testing, the bandwidth of transmitting DPs well with BRA is 67.19%, which is more than in the circumstances without it. It also demonstrates that the NT of wireless data has improved dramatically.
Funding Statement: The authors are grateful to the Taif University Researchers Supporting Project number (TURSP-2020/36), Taif University, Taif, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Mukherjee, J. J. P. C. Rodrigues, P. Goswami, L. Manman, R. Hazra et al., “Green cooperative communication based cognitive radio sensor networks for IoT applications,” in IEEE Int. Conf. on Communications Workshops, Dublin, Ireland, pp. 1–6, 2020. [Google Scholar]
2. A. U. Priyadarshni and S. Sudhakar, “Cluster based certificate revocation by cluster head in mobile ad-hoc network,” International Journal of Applied Engineering Research, vol. 10, no. 20, pp. 16014–16018, 2015. [Google Scholar]
3. D. Costanzo, G. Masotti, G. Paolini and D. Schreurs, “Evolution of SWIPT for the IoT world: Near-and far-field solutions for simultaneous wireless information and power transfer,” IEEE Microwave Magazine, vol. 22, no. 12, pp. 48–59, 2021. [Google Scholar]
4. D. Feng, L. Lu, Y. W. Yi, G. Y. Li, G. Feng et al., “Device-to-device communications underlaying cellular networks,” IEEE Transactions on Communications, vol. 61, no. 8, pp. 3541–3551, 2013. [Google Scholar]
5. F. Akyildiz, W. Su, Y. Sankarasubramaniam and E. Cayirci, “A survey on sensor networks,” IEEE Communications Magazine, vol. 40, no. 8, pp. 102–114, 2002. [Google Scholar]
6. G. A. Akpakwu, B. J. Silva, G. P. Hancke and A. M. AbuMahfouz, “A survey on 5G networks for the internet of things: Communication technologies and challenges,” IEEE Access, vol. 6, pp. 3619–3647, 2018. [Google Scholar]
7. H. ElSawy, E. Hossain and M. S. Alouini, “Analytical modeling of mode selection and power control for underlay D2D communication in cellular networks,” IEEE Transactions on Communications, vol. 62, no. 11, pp. 4147–4161, 2014. [Google Scholar]
8. J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang et al., “A survey on internet of things: Architecture enabling technologies security and privacy and applications,” IEEE Internet of Things Journal, vol. 4, no. 5, pp. 1125–1142, 2017. [Google Scholar]
9. J. M. Williams, F. Gao, Y. Qian, C. Song, R. Khanna et al., “Solar and RF energy harvesting design model for sustainable wireless sensor tags,” IEEE Topical Conf. on Wireless Sensors and Sensor Networks, San Antonio, TX, USA , pp. 1–4, 2020. [Google Scholar]
10. L. Wang, H. Tang and M. Cierny, “Device-to-device link admission policy based on social interaction information,’’ IEEE Transactions on Vehicular Technology, vol. 64, no. 9, pp. 4180–4186, 2015. [Google Scholar]
11. N. Abedini, S. Tavildar, J. Li and T. Richardson, “Distributed synchronization for device-to-device communications in an LTE network,” IEEE Transactions on Wireless Communications, vol. 15, no. 2, pp. 1547–1561, 2016. [Google Scholar]
12. N. Abuzainab, W. Saad, C. S. Hong and H. V. Poor, “Cognitive hierarchy theory for distributed resource allocation in the internet of things,” IEEE Transactions on Wireless Communications, vol. 16, no. 12, pp. 7687–7702, 2017. [Google Scholar]
13. N. Satheesh, D. Sudha, D. Suganthi, S. Sudhakar, S. Dhanaraj et al., “Certain improvements to location aided packet marking and DDoS attacks in internet,” Journal of Engineering Science and Technology, vol. 15, no. 1, pp. 94–107, 2020. [Google Scholar]
14. O. Bujari, C. E. Gaggi, A. Palazzi and D. Ronzani, “Would current ad-hoc routing protocols be adequate for the internet of vehicles? a comparative study,” IEEE Internet of Things Journal, vol. 5, no. 5, pp. 3683–3691, 2018. [Google Scholar]
15. P. Mach, Z. Becvar and T. Vanek, “In-band device-to-device communication in OFDMA cellular networks: A survey and challenges,” IEEE Communications Surveys and Tutorials, vol. 17, no. 4, 1885–1922, 2015. [Google Scholar]
16. S. Bahtiyar and M. U. Caglayan, “Extracting trust information from security system of a service,” Journal of Network and Computer Applications, vol. 35, no. 1, pp. 480–490, 2012. [Google Scholar]
17. S. Chen, H. Xu, D. Liu, B. Hu and H. Wang, “A vision of IoT: Applications, challenges, and opportunities with China perspective,” IEEE Internet of Things Journal, vol. 1, no. 4, pp. 349–359, 2014. [Google Scholar]
18. S. Shahraki, A. Taherkordi, Ø. Haugen and F. Eliassen, “A survey and future directions on clustering: From WSNs to IoT and modern networking paradigms,” IEEE Transactions on Network and Service Management, vol. 18, no. 2, pp. 2242–2274, 2021. [Google Scholar]
19. S. Sudhakar and S. Chenthur Pandian, “Hybrid cluster-based geographical routing protocol to mitigate malicious nodes in mobile ad hoc network,” International Journal of Ad Hoc and Ubiquitous Computing, vol. 21, no. 4, pp. 224–236, 2016. [Google Scholar]
20. T. Qiu, N. Chen, K. Li, M. Atiquzzaman and W. Zhao, “How can heterogeneous internet of things build our future: A survey,” IEEE Communications Surveys & Tutorials, vol. 20, no. 3, pp. 2011–2027, 2018. [Google Scholar]
21. Y. Shi and M. A. Jensen, “Improved radiometric identification of wireless devices using MIMO transmission,” IEEE Transactions on Information Forensics and Security, vol. 6, no. 4, pp. 1346–1354, 2011. [Google Scholar]
22. Z. Zhang, X. Guo and Y. Lin, “Trust management method of D2D communication based on RF fingerprint identification,” IEEE Access, vol. 6, pp. 66082–66087, 2018. [Google Scholar]
23. G. Murugan, N. Keerthana, K. Sujatha, S. Sudhakar, K. Amarendra et al., “Towards taxonomy for cloud computing as business models and deployment: A technical review,” International Journal of Advanced Science and Technology, vol. 29, no. 3, pp. 9096–9106. 2020. [Google Scholar]
24. K. Muthumayil, R. Karuppathal, T. Jayasankar, B. Aruna Devi et al., “A big data analytical approach for prediction of cancer using modified k-nearest neighbour algorithm,” Journal of Medical Imaging and Health Informatics, vol. 11, no. 8, pp. 2120–2125, 2021. [Google Scholar]
25. K. Rajakumari, M. Vinoth Kumar, V. Garima, S. Balu, D. K. Sharma et al., “Fuzzy based ant colony optimization scheduling in cloud computing,” Computer Systems Science and Engineering, vol. 40, no. 2, pp. 581–592, 2022. [Google Scholar]
26. K. Sasi Kala Rani, D. Ramya, J. Manikandan and S. Sudhakar, “Monitoring emotions in the classroom using machine learning,” International Journal of Scientific & Technology Research, vol. 9, no. 1, pp. 3723–3726, 2020. [Google Scholar]
27. M. Avuthu Sai, S. Sudhakar, G. Arumugam, P. Srinivasan and K. B. Prakash, “Age and gender prediction using convolution, resnet50, and inception resnetv2,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1328–1334, 2020. [Google Scholar]
28. A. Deivendran, K. Anbazhagan, P. Sailaja, E. Sujatha, M. Rajesh Babu et al., “Scalability service in data center persistent storage allocation using virtual machines,” International Journal of Scientific & Technology Research, vol. 9, no. 2, pp. 2135–2139, 2020. [Google Scholar]
29. P. Kanmani, V. Priya, N. Yuvaraj, S. Sudhakar, V. P. Sriram, “Inaccuracy correction method for moving shapes and shadows in video coding object,” International Journal of Scientific & Technology Research, vol. 9, no. 3, pp. 4561–456, 2020. [Google Scholar]
30. P. S. Ngangbam, S. Shruti, R. P. Thandaiah, S. Tripti, R. Selvakumar et al., “Investigation on characteristics of monte carlo model of single-electron transistor using orthodox theory,” Sustainable Energy Technologies and Assessments, vol. 48, no. 101601, pp. 1–15, 2021. [Google Scholar]
31. P. Thirumoorthy, A. Daniyal, B. Surbhi, A. M. Areej, P. Dadheech et al., “Improved energy based multi-sensor object detection in wireless sensor networks,” Intelligent Automation & Soft Computing, vol. 33, no. 1, pp. 227–244, 2022. [Google Scholar]
32. R. Nithya, K. Amudha, A. Syed Musthafa, D. K. Sharma, E. H. R. Asis et al., “An optimized fuzzy-based ant colony algorithm for 5G-MANET,” Computers, Materials & Continua, vol. 70, no. 1, pp: pp. 1069–1087, 2022. [Google Scholar]
33. R. Vasanthi, O. I. Khalaf, C. A. T. Romero, S. Sudhakar and D. K. “Sharma “Interactive middleware services for heterogeneous systems,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1241–1253, 2022. [Google Scholar]
34. S. Mehbodniya, A. Bhatia, A. Mashat, E. Mohanraj and S. “Sudhakar “Proportional fairness based energy-efficient routing in wireless sensor network,” Computer Systems Science and Engineering, vol. 41, no. 3, pp. 1071–1082, 2022. [Google Scholar]
35. S. S. Y. Bharadwaj, P. Rajaram, V. P. Sriram, S. Sudhakar and K. B. Prakash, “Effective handwritten digit recognition using deep convolution neural network,” International Journal of Advanced Trends in Computer Science and Engineering, vol. 9, no. 2, pp. 1335–1339, 2020. [Google Scholar]
36. S. Stalin David, M. Anam, K. Chandraprabha, S. Arun Mozhi Selvi et al., “Cloud security service for identifying unauthorized user behaviour,” Computers, Materials & Continua, vol. 70, no. 2, pp. 2581–2600, 2022. [Google Scholar]
37. S. David, S. Arun Mozhi Selvi, S. Sivaprakash, P. Vishnu Raja, D. K. Sharma et al., “Enhanced detection of glaucoma on ensemble convolutional neural network for clinical informatics,” Computers, Materials & Continua, vol. 70, no. 2, pp. 2563–2579, 2022. [Google Scholar]
38. S. Sudhakar and S. Chenthur Pandian, “A trust and co-operative nodes with affects of malicious attacks and measure the performance degradation on geographic aided routing in mobile ad hoc network,” Life Science Journal, vol. 10, no. 4s, pp. 158–163, 2013. [Google Scholar]
39. S. Sudhakar and S. Chenthur Pandian, “An efficient agent-based intrusion detection system for detecting malicious nodes in MANET routing,” International Review on Computers and Software (I.RE.CO.S.), vol. 7, no. 6, pp. 3037–304, 2012. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools