 Open Access
Open Access
ARTICLE
Search and Rescue Optimization with Machine Learning Enabled Cybersecurity Model
1 Department of Information Systems, College of Computer and Information Sciences, Princess Nourah Bint Abdulrahman University, P. O. Box 84428, Riyadh, 11671, Saudi Arabia
2 Department of Industrial Engineering, College of Engineering at Alqunfudah, Umm Al-Qura University, Saudi Arabia
3 Department of Information Systems, College of Science & Art at Mahayil, King Khalid University, Saudi Arabia
4 Department of Computer Science, College of Science & Art at Mahayil, King Khalid University, Saudi Arabia
5 Research Centre, Future University in Egypt, New Cairo, 11745, Egypt
6 Department of Computer and Self Development, Preparatory Year Deanship, Prince Sattam bin Abdulaziz University, AlKharj, Saudi Arabia
7 Department of Mathematics, Faculty of Science, Cairo University, Giza, 12613, Egypt
* Corresponding Author: Manar Ahmed Hamza. Email:
Computer Systems Science and Engineering 2023, 45(2), 1393-1407. https://doi.org/10.32604/csse.2023.030328
Received 23 March 2022; Accepted 26 April 2022; Issue published 03 November 2022
Abstract
Presently, smart cities play a vital role to enhance the quality of living among human beings in several ways such as online shopping, e-learning, e-healthcare, etc. Despite the benefits of advanced technologies, issues are also existed from the transformation of the physical word into digital word, particularly in online social networks (OSN). Cyberbullying (CB) is a major problem in OSN which needs to be addressed by the use of automated natural language processing (NLP) and machine learning (ML) approaches. This article devises a novel search and rescue optimization with machine learning enabled cybersecurity model for online social networks, named SRO-MLCOSN model. The presented SRO-MLCOSN model focuses on the identification of CB that occurred in social networking sites. The SRO-MLCOSN model initially employs Glove technique for word embedding process. Besides, a multiclass-weighted kernel extreme learning machine (M-WKELM) model is utilized for effectual identification and categorization of CB. Finally, Search and Rescue Optimization (SRO) algorithm is exploited to fine tune the parameters involved in the M-WKELM model. The experimental validation of the SRO-MLCOSN model on the benchmark dataset reported significant outcomes over the other approaches with precision, recall, and F1-score of 96.24%, 98.71%, and 97.46% respectively.Keywords
The association between mental behavior and online social networks (OSNs) usage has been very much reported throughout the most recent ten years [1,2]. What has been most disturbing, nonetheless, is the unavoidable nature and effect of undesirable digital hostility throughout the long term. As OSN has adjusted and changed, there have been expanded dangers of self-destructive ideation, self-destruction, sexual abuse or sales, and a horde of other negative strategies for dealing with stress, for example, stopping school or losing discretion. Through a meta-investigation, an essential outcome of digital exploitation was viewed as expanded degrees of gloom, especially among females [3]. Due to this peculiarity, it is essential to address the effect cyberaggression has on different ages, basically juvenile ages yet in addition arising grown-ups have given some knowledge into how they adapt or oversee cyberbullying (CB). It can take different structures, for example, sending undesirable, disparaging, or compromising remarks, spreading bits of hearsay, sending pictures or recordings that are hostile or humiliating by message, email, talk, or posting on sites including OSN [4,5]. The different kinds of CB in OSN are shown in Fig. 1.
Figure 1: Different types of CB
One variable influencing predominance rates is the idea of the things used to evaluate CB. In certain occurrences, members are asked single-thing inquiries deciding if they have at any point been the person in question or the culprit of CB [6]. In different cases, members have posed a progression of inquiries deciding if they have been cyberbullied through various scenes (e.g., texting, text informing, email, online gaming). Normally, predominance gauges for CB are lower when single-thing measures are utilized instead of when more explicit things ask about CB that happens through specific scenes. Prior explores on CB are generally relying on the examination and measurements, that accentuation on the definitions, factual technique, and the effect of CB; this study worked on the reality of CB and made researchers center additional interest around CB from the view of earnestness [7]. In the element of calculation exploration, ML and DL strategies help researchers to more readily get human ways of behaving.
Applying these techniques to huge OSNs as far as scale and degree cause a few issues. From one viewpoint, the touchy development of OSNs upgrades and spreads forceful types of conduct by giving stages and networks to submit and engender such way of behaving [8]. Then again, OSNs offer significant information for investigating human way of behaving and association at a huge scope, and this information can be utilized by specialists to foster successful strategies for distinguishing and controlling trouble making and additionally forceful ways of behaving. OSNs give hoodlums instruments to perform forceful activities and networks to submit offenses [9]. Thusly, strategies that address the two perspectives (content and network) ought to be streamlined to recognize and control forceful ways of behaving in complex frameworks [10].
Fang et al. [11] focused on text-based CB recognition since it is the widely employed data transporter in social networks and is extensively commonly featured. Inspired by the recognized achievement of neural networks, we proposed a comprehensive model that combines the self-attention model and bi-directional gated recurrent unit (Bi-GRU). Exhaustively, introduced the model of GRU cell and Bi-GRU advantages to learning the fundamental relations among words from these two directions. Kumari et al. [12] presented a unified illustration of text and image to remove the requirement for dispersed learning models for text and image. A single-layer Convolution Neural Network system is utilized by a combined illustration. The most important results of this study are that the text characterized as image is an improved method for encoding the data. Also, we found that single-layer Convolution Neural Network is providing good outcomes with 2D representations.
Rosa et al. [13] a current method with demonstrated accomplishment in comparable task, Fuzzy Fingerprint, implements while identifying textual CB in social network. Notwithstanding, widely preserved as dual classifier tasks, we claim that recovery problems where the pertinent presentation is that of retrieving CB interaction. Experiment shows that the Fuzzy Fingerprint somewhat outperformed basic classifier while established in a closer to real time situation, whereby CB instance is fewer when compared to CB. Alotaibi et al. [14] proposed an automated CB technique for detecting destructive performance via a combined deep learning technique. This approach employs multi-channel DL based three methods, such a transformer block, the bidirectional gated recurrent unit (BiGRU), and convolution neural network (CNN), to categorize Tweet posts into two classes: not aggressive and aggressive. In [15], a hybrid method, Bi-GRU-Attention-CapsNet (Bi-GAC), benefitted by spatial location information and learning consecutive semantic representation through a Bi-GRU with self-attention afterward CapsNet for CB recognition in the text content of social network. The presented method is estimated to perform with ROC-AUC and curve F1-score as metrics.
This article devises a novel search and rescue optimization with machine learning enabled cybersecurity model for online social networks, named SRO-MLCOSN model. The presented SRO-MLCOSN model initially employs Glove’s technique for word embedding process. Besides, a multiclass-weighted kernel extreme learning machine (M-WKELM) model is utilized for effectual identification and categorization of CB. Finally, Search and Rescue Optimization (SRO) algorithm is exploited to fine tune the parameters involved in the M-WKELM model. The experimental validation of the SRO-MLCOSN model on the benchmark dataset.
In this study, a new SRO-MLCOSN model has been developed for the identification of CB that occurred in social networking sites. For achieving this, the SRO-MLCOSN model initially employs Glove’s technique for word embedding process. Followed by, M-WKELM model is utilized for effectual identification and categorization of CB. At last, SRO algorithm is exploited to fine tune the parameters involved in the M-WKELM model. The detailed working of these processes is given in Fig. 2.
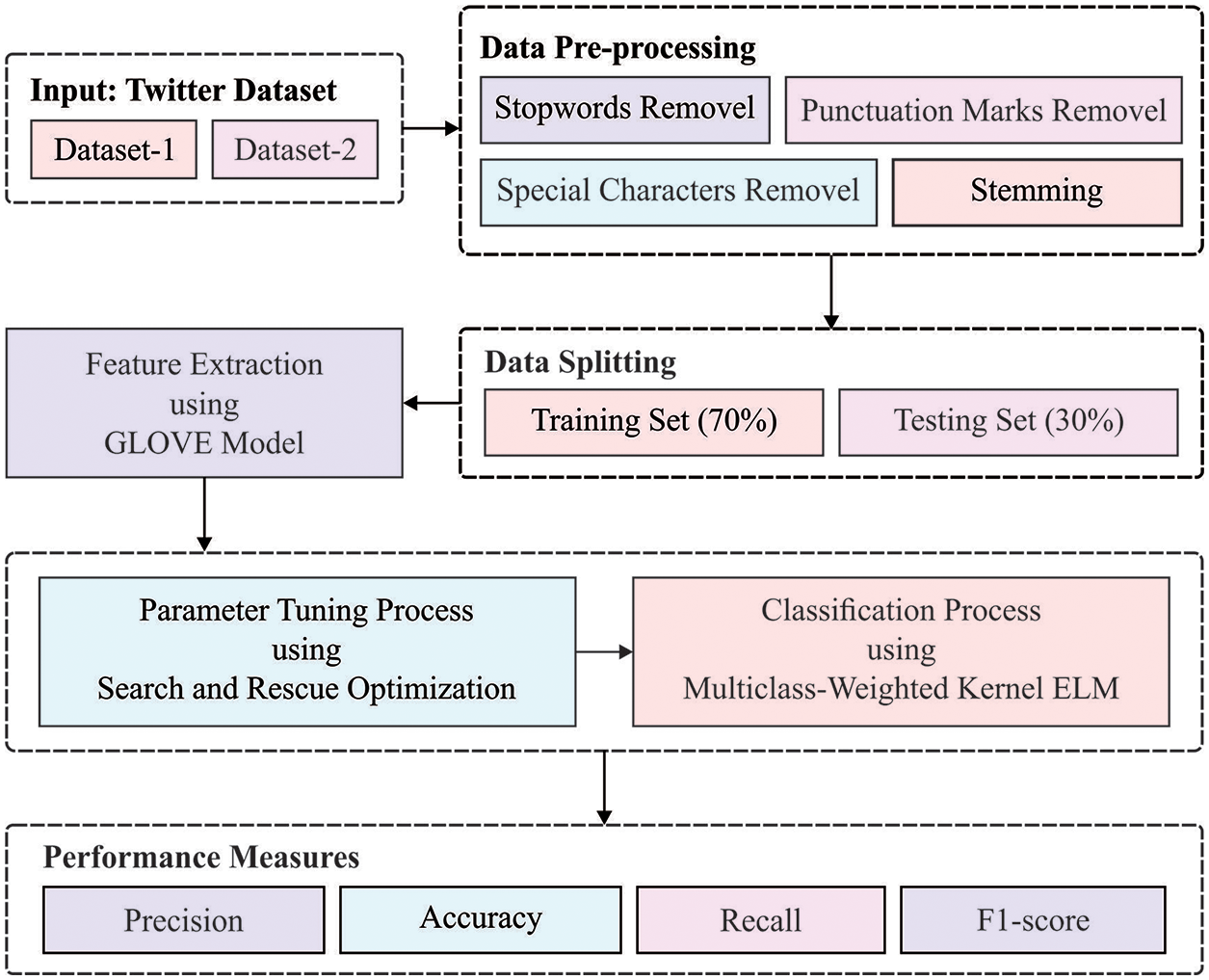
Figure 2: Workflow of SRO-MLCOSN model
At the preliminary phase, the proposed model employs preprocessing and Glove’s technique for word embedding process [16]. The GloVe word embedding approach has been employed in the projected approach to extract semantic features under the text on web page. The GloVe is short form of global vector, and GloVe embed was unsupervised learning approach for distributing word demonstration of the text distant under the web page. The GloVe approach was simpler to train on the information caused by its parallel performance. It gets the semantic connection of words from the vector space. The global co-occurrence matrix X has been produced employing the word initiate from the Wikipedia data set to train the GloVe word embed approach [16]. In the co-occurrence matrix, X: Xij defines the count of context words i which perform as word j. The GloVe approach minimizing the succeeding main function:
2.2 M-WKELM Based CB Classification
Once the features are derived, the M-WKELM model is utilized for effectual identification and categorization of CB [17]. ELM is widely applied for the process of classification. The ai and bi parameters are arbitrarily formed. It doesn’t adapt to the whole method. The hidden layer was described afterward the input parameter has been created. Based on their input parameter and hidden layer, it develops the result with the linear analytic solution. The ultimate objective of ELM attains the minimum trained error with low norm of resulting weight:
As per the abovementioned equation, it can be written by:
whereas h(x) = [G(a1, b1, x), …, G(aL, bL, x)], ξi indicates the trained error, and C denotes the regularized variable. According to the KarushKuhnTucker (KKT) optimized and Lagrange multiplier system conditions, training the ELM was equivalent to resolving the succeeding issues:
Now, αi,j denotes the Lagrange multiplier and βj shows the column vector of matrix β. In the KKT declaration, it might develop further:
As stated by Eqs. (5)–(7), the resulting weight, β, is specified by
afterward accomplishing the resulting weight β, the result of ELM is accomplished by:
The typical ELM does not consider the imbalance problem; however, the weighting ELM is intentional to address them. In such cased, 2 weighted techniques are given:
Now tk denotes the total sum of instances appropriate to kth class. Afterward executing weighted arrangement 1, attains a balanced ratio among the minority and majority
Now, tavg denotes the average number of instances. Once the quantity of tk is lesser the average, associated with ELM, the optimized technique of weighting ELM is given by:
To the multiple class-weighting kernel ELM, it is determined as a diagonal matrix, W i.e., connected to trained instance x. The resulting weight, β, has expressed by:
To offer a novel instance, x, the resulting function of weighting ELM classification is accomplished in f(x) = h(x)β:
Based on the SVM kernel technique, the kernel trick is employed in the above equation, in which the kernel function changes the internal products h(x) HT and HHT. The kernel trick kind of weighting ELM is the weighting kernel ELM. Thus, the N × N form of kernel ELM is written by:
Now
Therefore, the weighting kernel ELM presents a unified solution to network with different feature mappings and, instantaneously, strengthen the effect of minority class instance with weight matrix.
2.3 Parameter Optimization Using SRO Algorithm
At the final stage, the SRO algorithm is exploited to fine tune the parameters involved in the M-WKELM model [18]. SRO algorithm which is simulated as the research shown by humans at the searching and rescue methods. The searching and rescuing procedures include 2 phases, viz., individual and social phases. The clues left at the time of searching by the group member are stored from the memory matrix (O) whereas the human locate has been stored in the position matrix (W). The clue matrix B utilizing size
The 2 steps of human searching are modelled in the subsequent. i) social stage: The searching way is signified as SDi = (Wi − Bk) in which
At this point, f(Bi) & f(Wi) signifies the fitness function value for
Every solution can define from the solution space once the novel place is outer the solution space as:
In which
whereas MEn signifies the nth saved clues locate from the memory matrix and n signifies the arbitrary integer number ranges from 1 and N. In the clues searching function, if an optimal clue could not initiate neighboring the existing place then approximately count of searches, humans carry to a new place.
But the USN value has maximum if related to the higher ineffective searching number, the human became an arbitrary locate from the search space by Eq. (23), and the value of USNi is set to 0 for that human.
In this section, the performance validation of the SRO-MLCOSN model is carried out using two datasets namely dataset 1 [19] with 16090 instances and dataset 2 [20] with 24783 instances. These datasets include three class labels namely racism, sexism, and neither.
Fig. 3 demonstrates a pair of confusion matrices produced by the SRO-MLCOSN model on 70% of training set (TRS) and 30% of testing set (TSS) under dataset-1. On 70% of TRS, the SRO-MLCOSN model has identified 944 samples into racism, 1856 samples into sexism, and 7401 samples into neither class. Also, on 30% of TSS, the SRO-MLCOSN model has recognized 388 samples into racism, 775 samples into sexism, and 3239 samples into neither class.
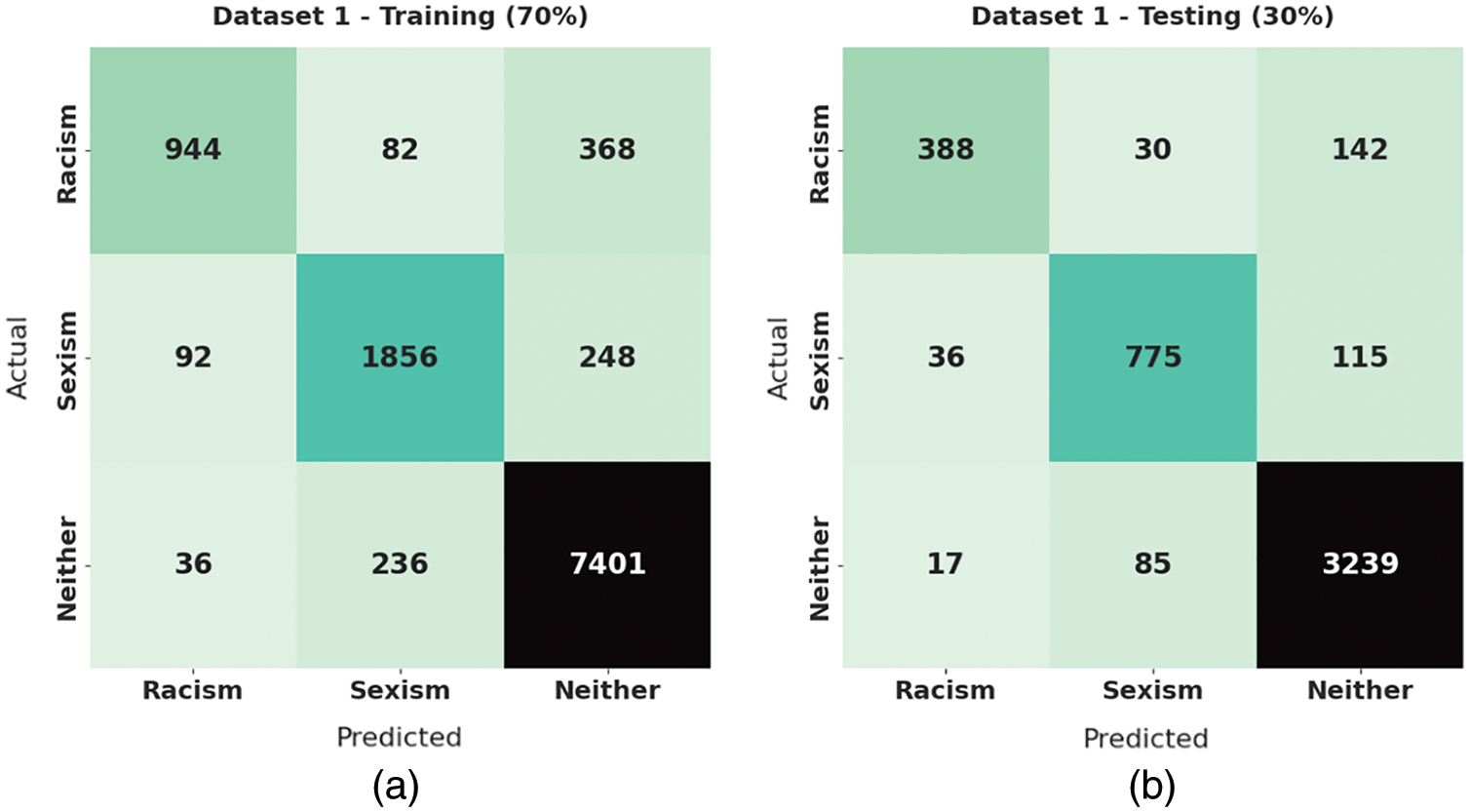
Figure 3: Confusion matrices of SRO-MLCOSN model on dataset-1: (a) 70% of TRS and (b) 30% of TSS
Tab. 1 provides a complete CB classification outcome of the SRO-MLCOSN model on 70% of TRS and 30% of TSS on dataset-1. Fig. 4 inspects the CB detection and classification results of the SRO-MLCOSN model on 70% of TRS on dataset 1. The figure specified that the SRO-MLCOSN model has identified racism class with accuy, precn, recal, and Fscore of 94.87%, 88.06%, 67.72%, and 76.56% respectively. Also, the SRO-MLCOSN model has identified sexism class with accuy, precn, recal, and Fscore of 94.16%, 85.37%, 84.52%, and 84.94% respectively. Above and beyond, the SRO-MLCOSN model has identified neither class with accuy, precn, recal, and Fscore of 92.12%, 92.32%, 96.46%, and 94.34% respectively.
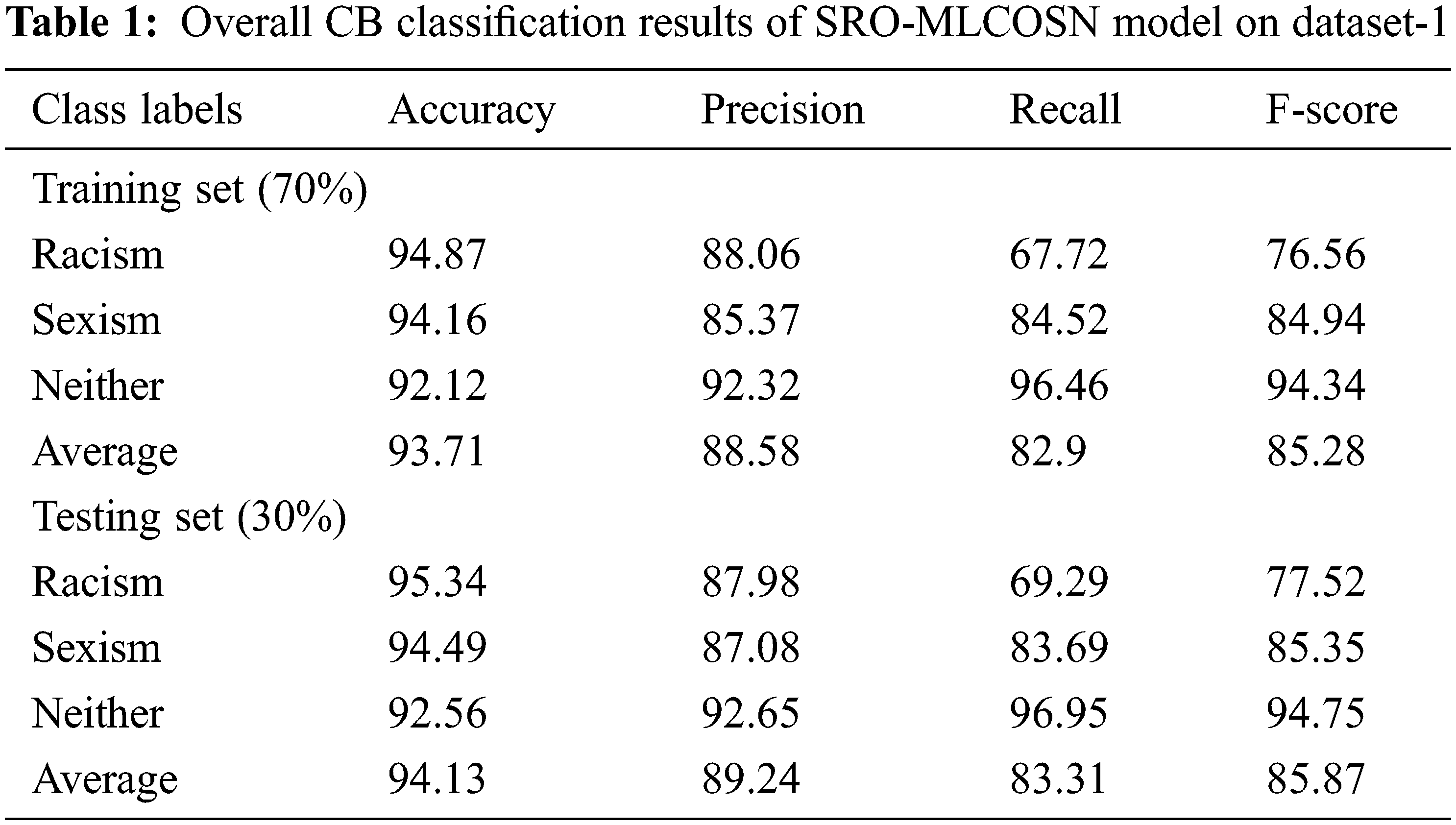
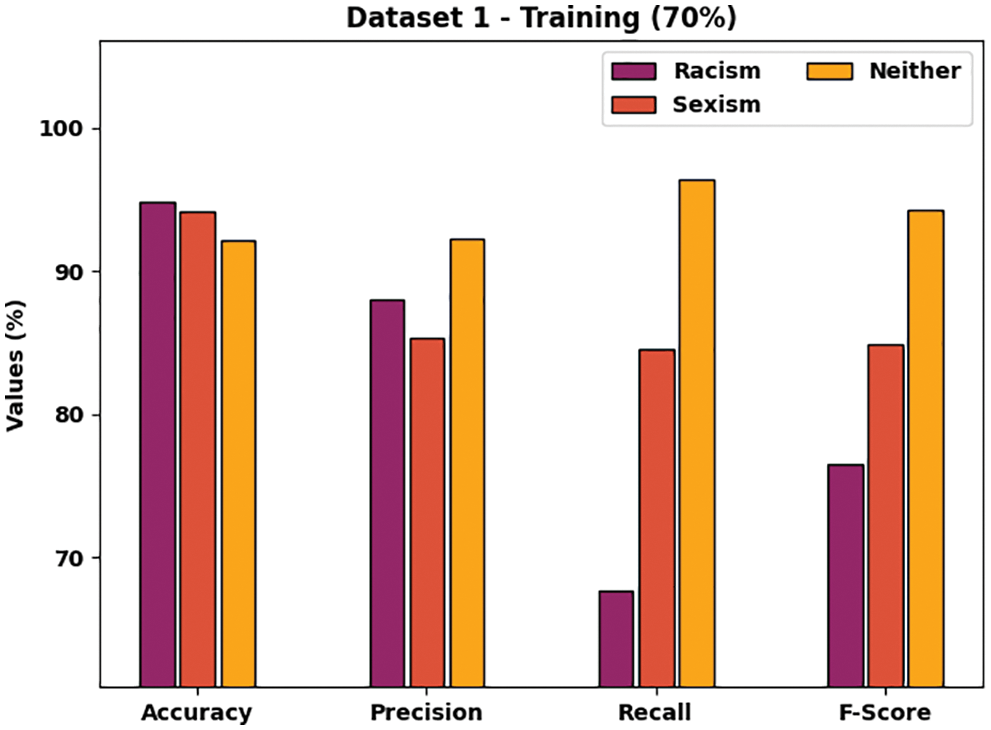
Figure 4: CB classification results of SRO-MLCOSN model on dataset-1 with 70% of TRS
Fig. 5 studies the CB detection and classification results of the SRO-MLCOSN model on 30% of TSS on dataset 1. The figure directed that the SRO-MLCOSN model has identified racism class with accuy, precn, recal, and Fscore of 95.34%, 87.98%, 69.29%, and 77.52% respectively. Additionally, the SRO-MLCOSN model has identified sexism class with accuy, precn, recal, and Fscore of 94.49%, 87.08%, 83.69%, and 85.35% respectively. Further, the SRO-MLCOSN model has identified neither class with accuy, precn, recal, and Fscore of 92.56%, 92.65%, 96.95%, and 94.75% respectively.
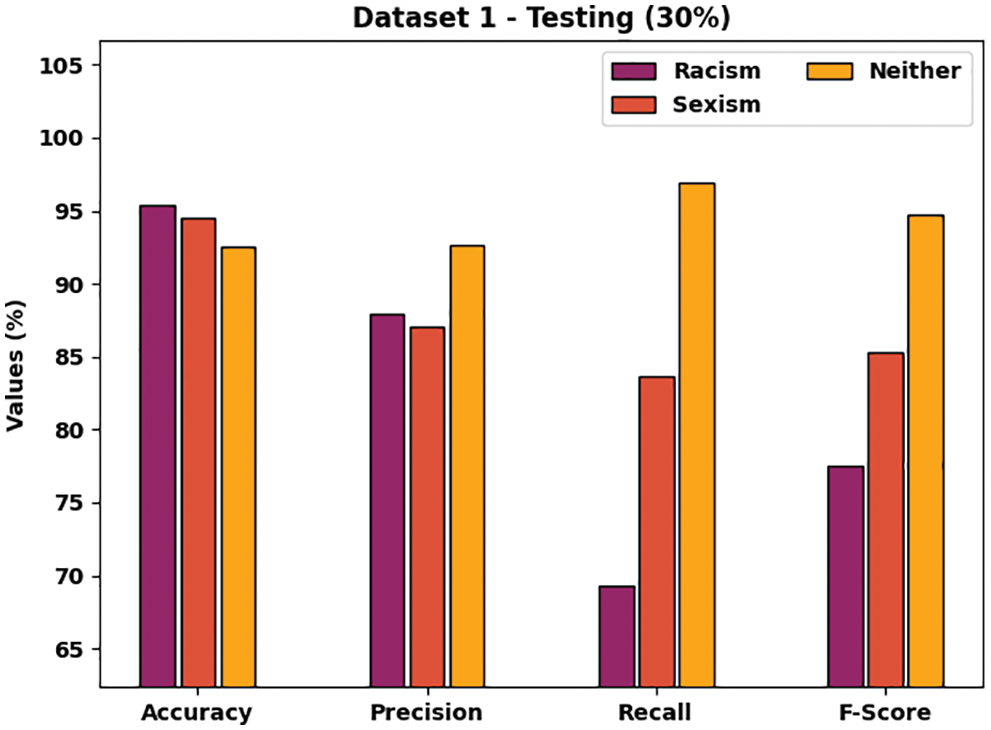
Figure 5: CB classification results of SRO-MLCOSN model on dataset-1 with 30% of TSS
Fig. 6 reveals a pair of confusion matrices produced by the SRO-MLCOSN model on 70% of TRS and 30% of TSS under dataset-2. On 70% of TRS, the SRO-MLCOSN model has identified 892 samples into hate, 13279 samples into offensive, and 2883 samples into neither class. Also, on 30% of TSS, the SRO-MLCOSN model has recognized 385 samples into hate, 5709 samples into offensive, and 1229 samples into neither class.
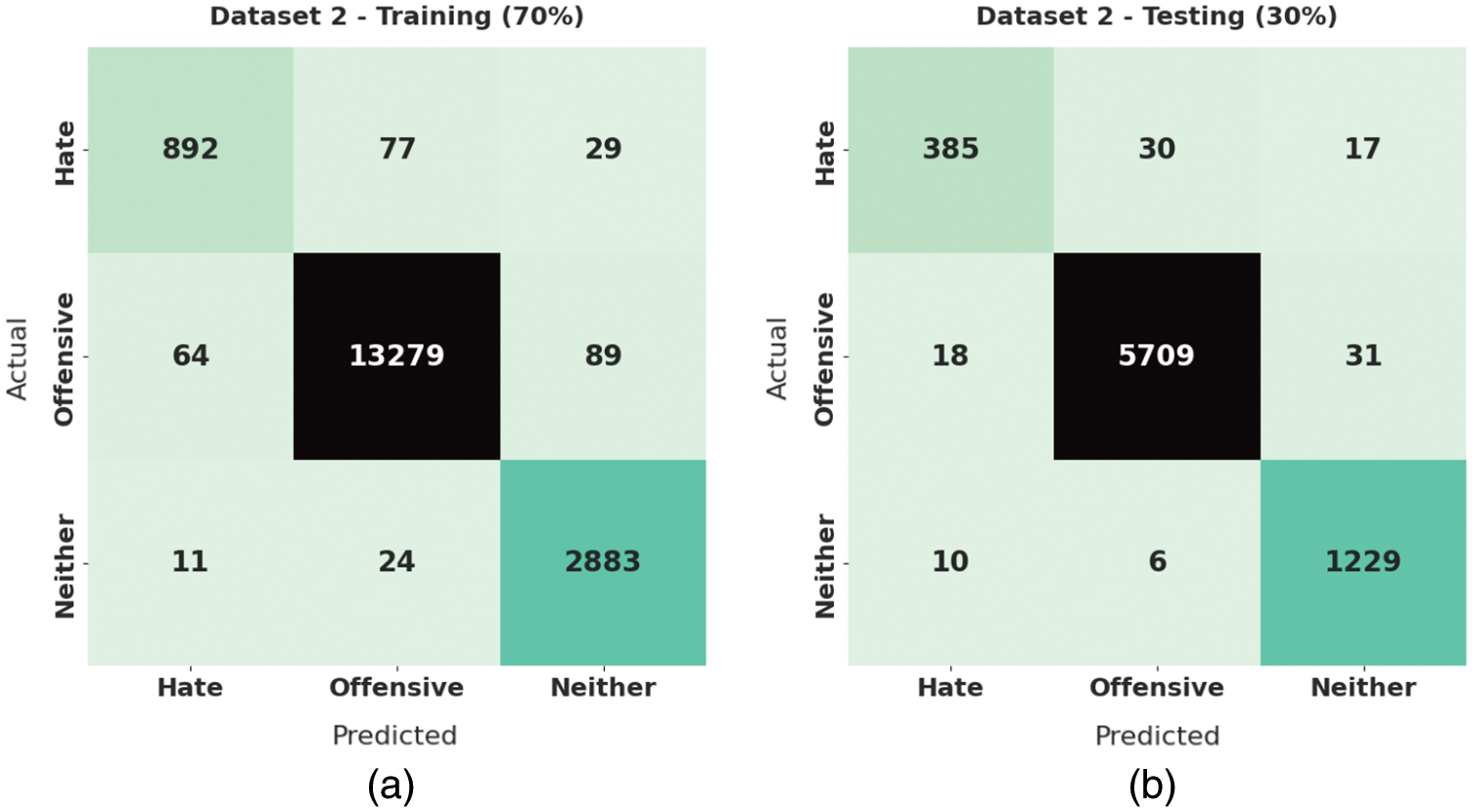
Figure 6: Confusion matrices of SRO-MLCOSN model on dataset-2: (a) 70% of TRS and (b) 30% of TSS
Tab. 2 reports the overall CB classification outcomes of the SRO-MLCOSN model on 70% of TRS and 30% of TSS on dataset-2. Fig. 7 examines the CB detection and classification results of the SRO-MLCOSN model on 70% of TRS on dataset 2. The figure indicated that the SRO-MLCOSN model has identified racism class with accuy, precn, recal, and Fscore of 98.96%, 92.24%, 89.38%, and 90.79% respectively. In addition, the SRO-MLCOSN model has identified sexism class with accuy, precn, recal, and Fscore of 98.54%, 99.25%, 98.86%, and 99.05% respectively. Besides, the SRO-MLCOSN model has identified neither class with accuy, precn, recal, and Fscore of 99.12%, 96.07%, 98.80%, and 97.42% respectively.
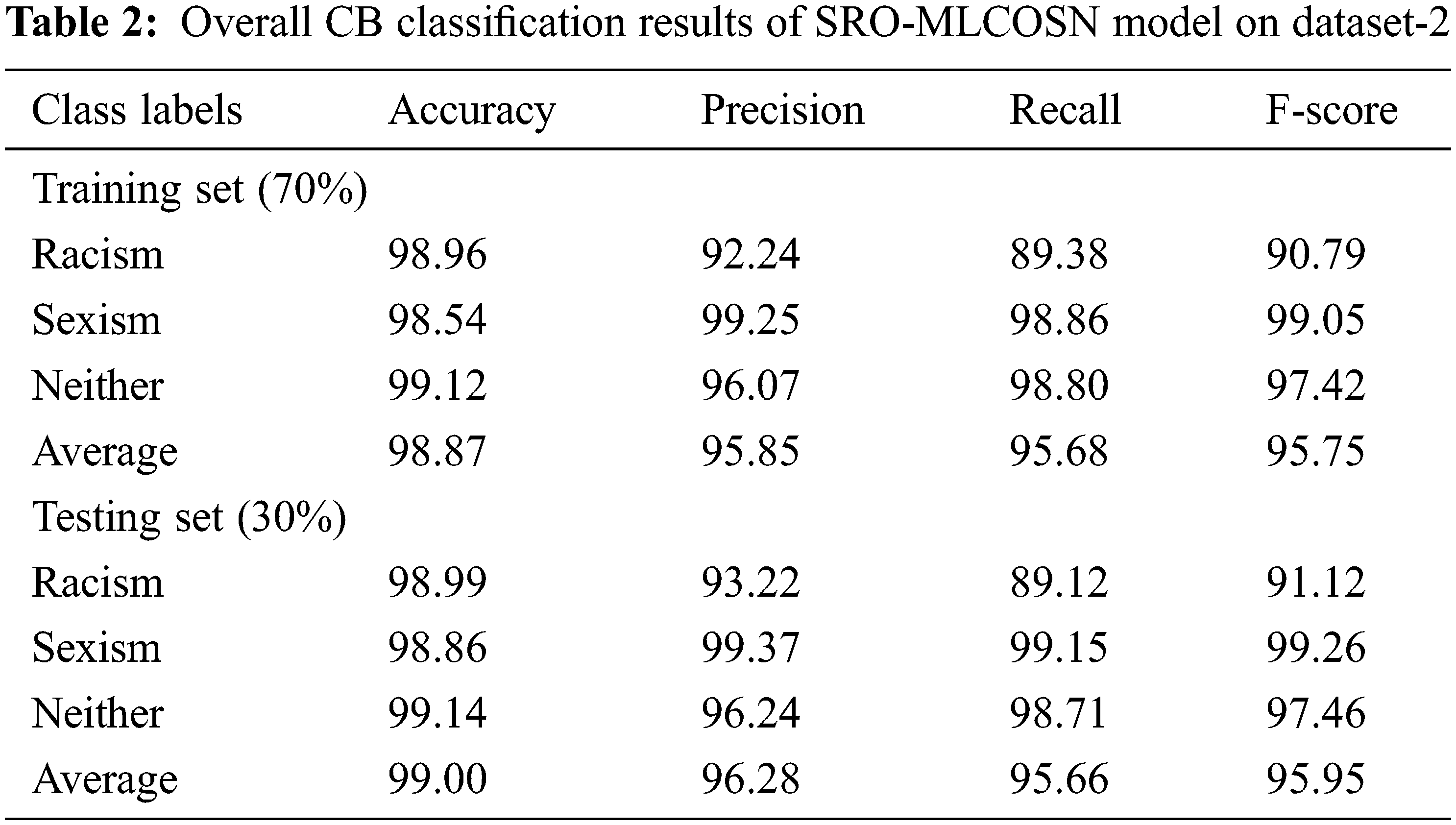
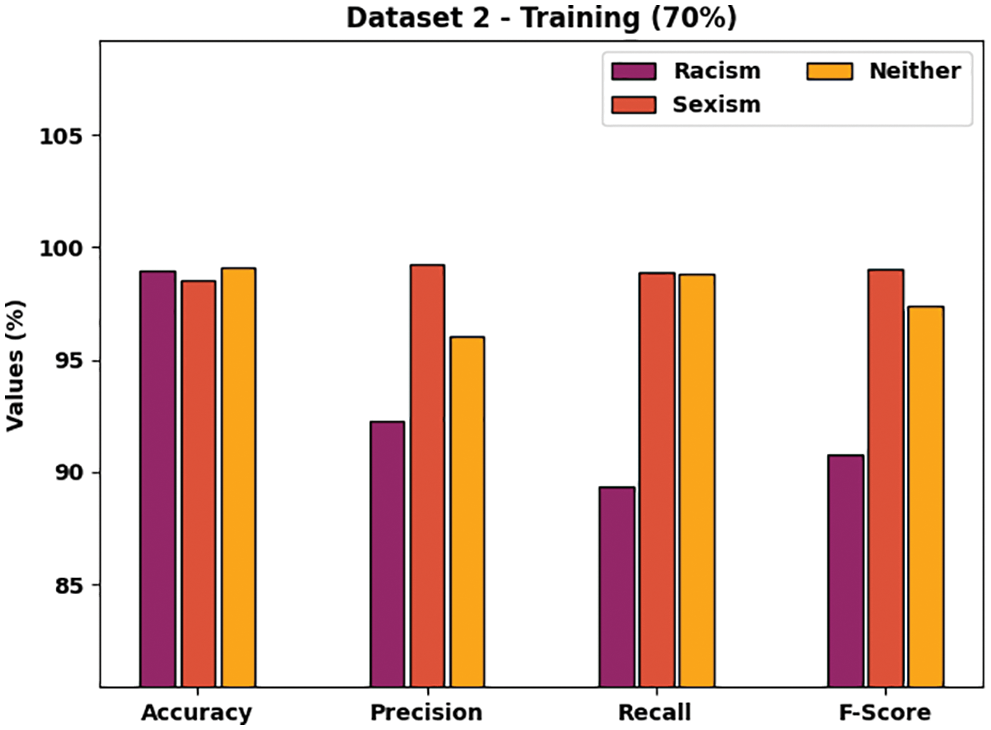
Figure 7: CB classification results of SRO-MLCOSN model on dataset-2 with 70% of TRS
Fig. 8 examines the CB detection and classification results of the SRO-MLCOSN model on 30% of TSS on dataset 2. The figure indicated that the SRO-MLCOSN model has identified racism class with accuy, precn, recal, and Fscore of 98.99%, 93.22%, 89.12%, and 91.12% respectively. In addition, the SRO-MLCOSN model has identified sexism class with accuy, precn, recal, and Fscore of 98.86%, 99.37%, 99.15%, and 99.26% respectively. Besides, the SRO-MLCOSN model has identified neither class with accuy, precn, recal, and Fscore of 99.14%, 96.24%, 98.71%, and 97.46% respectively.
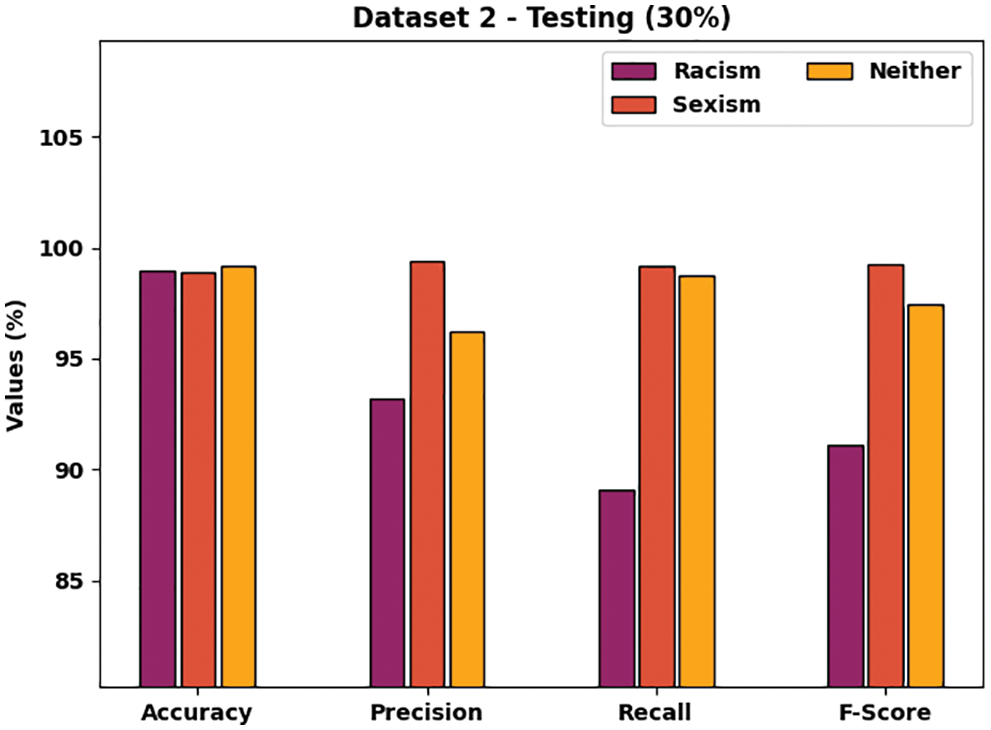
Figure 8: CB classification results of SRO-MLCOSN model on dataset-1 with 30% of TSS
Tab. 3 provides a complete comparative study of the SRO-MLCOSN model on the detection of CB and NCB on two datasets [21]. Fig. 9 examines the comaparative examination of the SRO-MLCOSN model with existing models on NCB classification of dataset-1. The figure indicated that the SRO-MLCOSN model has offered improved outcomes over the other methods. The results implied that the SRO-MLCOSN model has provided higher precn of 92.65% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have obtained lower precn of 85.14%, 85.29%, 84.92%, 88.67%, and 88.78% respectively. Besides, the outcome depicted that the SRO-MLCOSN model has gained increased recal of 96.95% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have exhibited decreased recal of 85.31%, 87.92%, 83.98%, 88.06%, and 90.15% respectively.

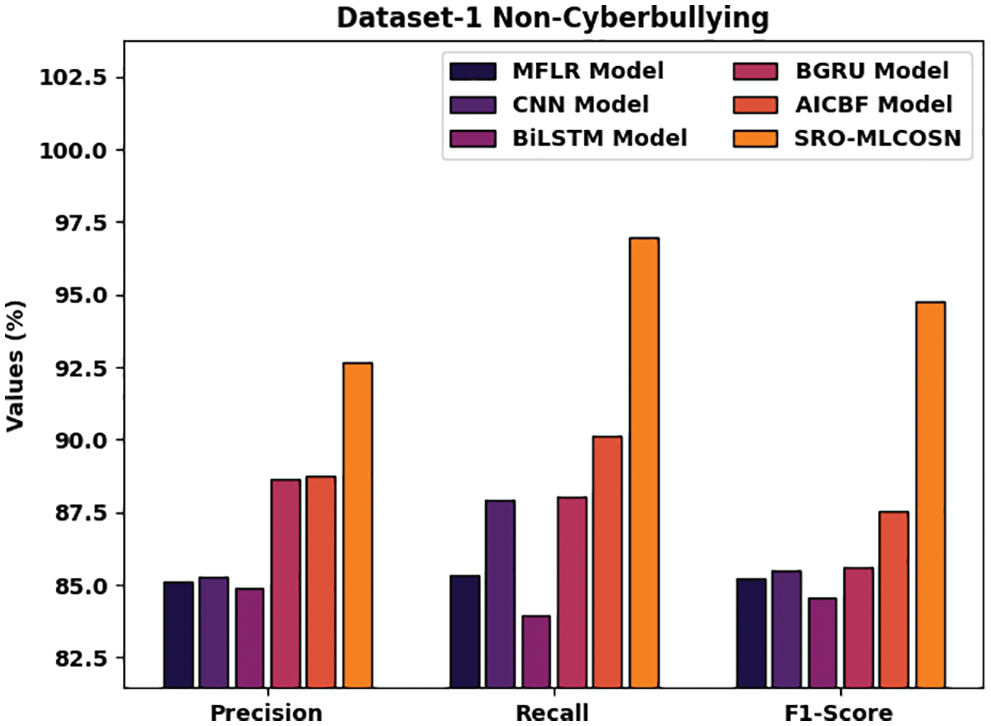
Figure 9: Comparative NCB classification results of SRO-MLCOSN model on dataset-1
Fig. 10 inspects the comparative investigation of the SRO-MLCOSN model with existing models on CB classification of dataset-1. The figure designated that the SRO-MLCOSN model has offered improved outcomes over the other methods. The results implied that the SRO-MLCOSN model has provided higher precn of 97.53% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have obtained lower precn of 65.45%, 70.11%, 70.32%, 72%, and 73.90% respectively. Moreover, the outcome depicted that the SRO-MLCOSN model has gained increased recal of 76.49% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have exhibited decreased recal of 70.04%, 63.40%, 66.49%, 74.63%, and 74.86% respectively.
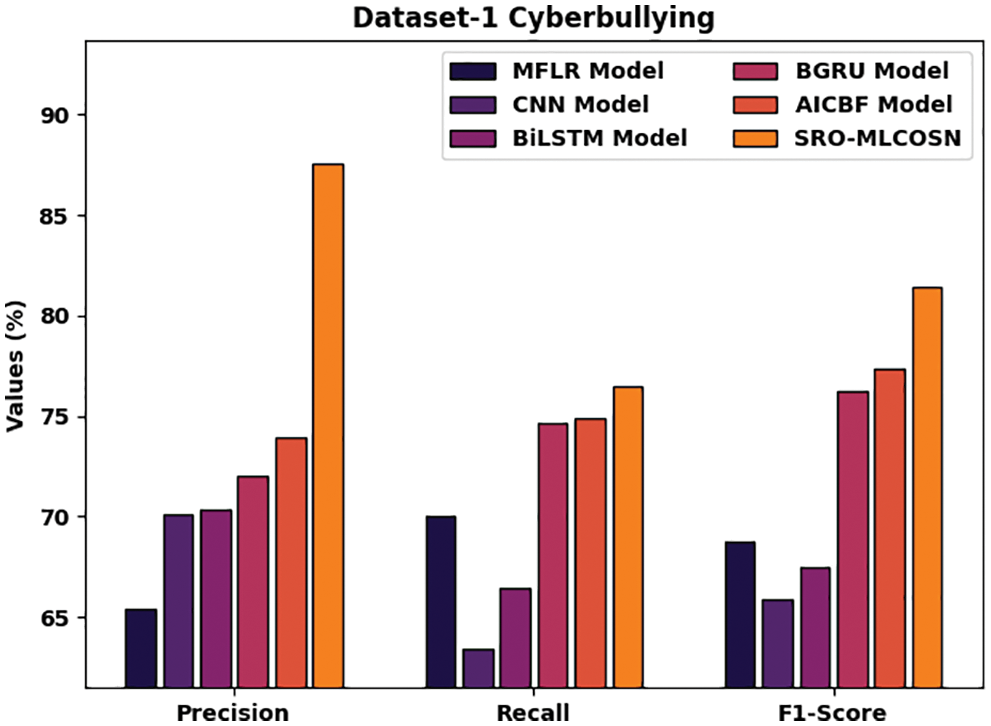
Figure 10: Comparative CB classification results of SRO-MLCOSN model on dataset-1
Fig. 11 observes the comparative inspection of the SRO-MLCOSN model with existing models on NCB classification of dataset-2. The figure specified that the SRO-MLCOSN model has offered improved outcomes over the other methods. The results implied that the SRO-MLCOSN model has provided higher precn of 96.24% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have obtained lower precn of 74.66%, 84.83%, 85.11%, 82.54%, and 83.94% respectively. Eventually, the outcome depicted that the SRO-MLCOSN model has gained increased recal of 98.71% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have exhibited decreased recal of 91.22%, 81.53%, 74.01%, 88.99%, and 91.18% respectively.
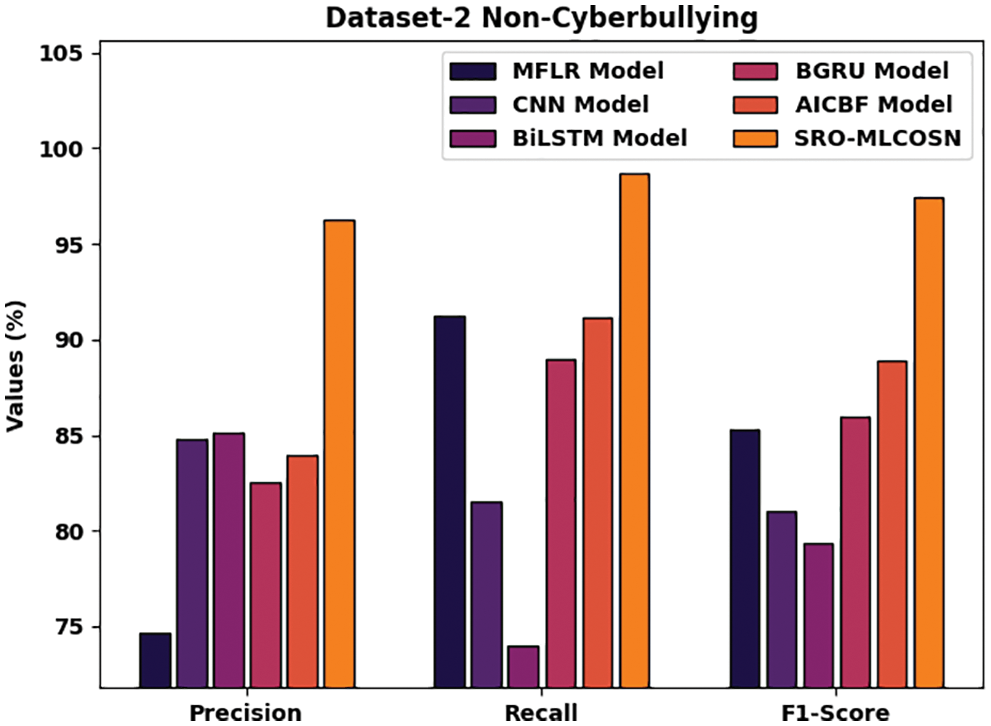
Figure 11: Comparative NCB classification results of SRO-MLCOSN model on dataset-2
Fig. 12 studies the comparative analysis of the SRO-MLCOSN model with existing models on CB classification of dataset-2. The figure showed that the SRO-MLCOSN model has offered improved outcomes over the other methods. The results implied that the SRO-MLCOSN model has provided higher precn of 96.30% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have obtained lower precn of 93.92%, 92.18%, 91.61%, 94.02%, and 95.68% respectively. Meanwhile, the outcome depicted that the SRO-MLCOSN model has gained increased recal of 94.14% whereas the MFLR, CNN, BiLSTM, BGRU, and AICBF models have exhibited decreased recal of 92.93%, 92.37%, 93.15%, 92.92%, and 93.75% respectively.
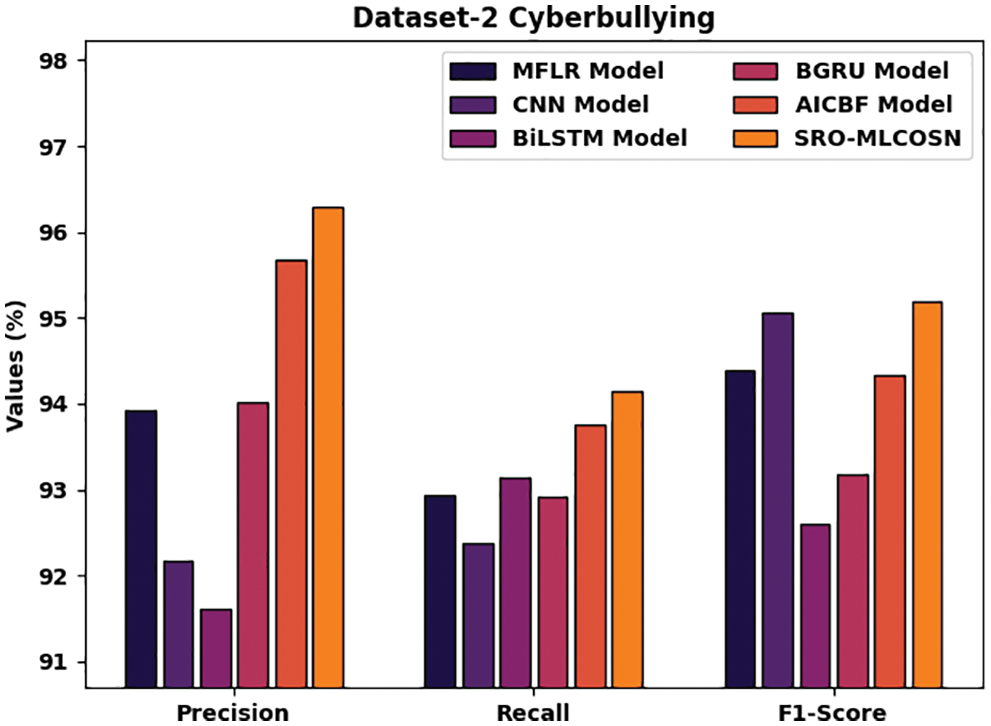
Figure 12: Comparative CB classification results of SRO-MLCOSN model on dataset-2
From the detailed results and discussion, it is observed that the SRO-MLCOSN model has exhibited superior performance over the existing models.
In this study, a new SRO-MLCOSN model has been developed for the identification of CB that occurred in social networking sites. For achieving this, the SRO-MLCOSN model initially employs Glove’s technique for word embedding process. Followed by, M-WKELM model is utilized for effectual identification and categorization of CB. At last, SRO algorithm is exploited to fine tune the parameters involved in the M-WKELM model. The experimental validation of the SRO-MLCOSN model on the benchmark dataset reported significant outcomes over the other approaches under several aspects. Thus, the presented SRO-MLCOSN model can appear as an automated tool for the identification of CB in OSN. In future, deep learning approaches can be included to improve the detection efficiency of the SRO-MLCOSN model.
Acknowledgement: The authors would like to thank the Deanship of Scientific Research at Umm Al-Qura University for supporting this work by Grant Code: (22UQU4340237DSR12).
Funding Statement: The authors extend their appreciation to the Deanship of Scientific Research at King Khalid University for funding this work under Grant Number (RGP 2/158/43). Princess Nourah bint Abdulrahman University Researchers Supporting Project Number (PNURSP2022R114), Princess Nourah bint Abdulrahman University, Riyadh, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. A. Bozyiğit, S. Utku and E. Nasibov, “Cyberbullying detection: Utilizing social media features,” Expert Systems with Applications, vol. 179, pp. 115001, 2021. [Google Scholar]
2. N. A. Azeez, S. O. Idiakose, C. J. Onyema and C. V. D. Vyver, “Cyberbullying detection in social networks: Artificial intelligence approach,” Journal of Cyber Security and Mobility, vol. 10, no. 4, pp. 745–774, 2021. [Google Scholar]
3. S. Kim, A. Razi, G. Stringhini, P. J. Wisniewski and M. De Choudhury, “A Human-centered systematic literature review of cyberbullying detection algorithms,” Proceedings of the ACM on Human-Computer Interaction, vol. 5, no. CSCW2, pp. 1–34, 2021. [Google Scholar]
4. M. Arif, “A systematic review of machine learning algorithms in cyberbullying detection: Future directions and challenges,” Journal of Information Security and Cybercrimes Research, vol. 4, no. 1, pp. 01–26, 2021. [Google Scholar]
5. D. L. Hall, Y. N. Silva, B. Wheeler, L. Cheng and K. Baumel, “Harnessing the power of interdisciplinary research with psychology-informed cyberbullying detection models,” International Journal of Bullying Prevention, vol. 4, no. 1, pp. 47–54, 2022. [Google Scholar]
6. J. Bhagya, and P. S. Deepthi, “Cyberbullying detection on social media using SVM,” in Inventive Systems and Control, Lecture Notes in Networks and Systems book series, Singapore: Springer, vol. 204, pp. 17–27, 2021. [Google Scholar]
7. A. Perera and P. Fernando, “Accurate cyberbullying detection and prevention on social media,” Procedia Computer Science, vol. 181, pp. 605–611, 2021. [Google Scholar]
8. F. Elsafoury, S. Katsigiannis, Z. Pervez and N. Ramzan, “When the timeline meets the pipeline: A survey on automated cyberbullying detection,” IEEE Access, vol. 9, pp. 103541–103563, 2021. [Google Scholar]
9. P. Khanna, A. Mathur, A. Chandra and A. Kumar, “Multimodal cyberbullying detection using ensemble learning,” in Int. Conf. on Artificial Intelligence and Sustainable Computing, Communications in Computer and Information Science book series, Cham, Springer, vol. 1434, pp. 221–229, 2021. [Google Scholar]
10. N. Yuvaraj, K. Srihari, G. Dhiman, K. Somasundaram, A. Sharma et al., “Nature-inspired-based approach for automated cyberbullying classification on multimedia social networking,” Mathematical Problems in Engineering, vol. 2021, pp. 1–12, 2021. [Google Scholar]
11. Y. Fang, S. Yang, B. Zhao and C. Huang, “Cyberbullying detection in social networks using bi-gru with self-attention mechanism,” Information, vol. 12, no. 4, pp. 171, 2021. [Google Scholar]
12. K. Kumari, J. P. Singh, Y. K. Dwivedi and N. P. Rana, “Towards cyberbullying-free social media in smart cities: A unified multi-modal approach,” Soft Computing, vol. 24, no. 15, pp. 11059–11070, 2020. [Google Scholar]
13. H. Rosa, J. P. Carvalho, P. Calado, B. Martins, R. Ribeiro et al., “Using fuzzy fingerprints for cyberbullying detection in social networks,” in 2018 IEEE Int. Conf. on Fuzzy Systems (FUZZ-IEEE), Rio de Janeiro, pp. 1–7, 2018. [Google Scholar]
14. M. Alotaibi, B. Alotaibi and A. Razaque, “A multichannel deep learning framework for cyberbullying detection on social media,” Electronics, vol. 10, no. 21, pp. 2664, 2021. [Google Scholar]
15. A. Kumar and N. Sachdeva, “A Bi-GRU with attention and CapsNet hybrid model for cyberbullying detection on social media,” World Wide Web, 2021. https://doi.org/10.1007/s11280-021-00920-4. [Google Scholar]
16. M. I. Short, R. Hudson, B. D. Besasie, K. R. Reveles, D. P. Shah et al., “Comparison of rectal swab, glove tip, and participant-collected stool techniques for gut microbiome sampling,” BMC Microbiology, vol. 21, no. 1, pp. 26, 2021. [Google Scholar]
17. C. Zhu, X. Liu, Q. Liu, Y. Ming and J. Yin, “Distance based multiple kernel elm: A fast multiple kernel learning approach,” Mathematical Problems in Engineering, vol. 2015, pp. 1–9, 2015. [Google Scholar]
18. S. Sreethar, N. Nandhagopal, S. A. Karuppusamy and M. Dharmalingam, “SARC: Search and rescue optimization-based coding scheme for channel fault tolerance in wireless networks,” Wireless Networks, vol. 27, no. 6, pp. 3915–3926, 2021. [Google Scholar]
19. Z. Waseem and D. Hovy, “Hateful symbols or hateful people? predictive features for hate speech detection on twitter,” in Proc. of the NAACL Student Research Workshop, San Diego, California, pp. 88–93, 2016. [Google Scholar]
20. T. Davidson, D. Warmsley, M. Macy and I. Weber, “Automated hate speech detection and the problem of offensive language,” in Eleventh Int. AAAI Conf. on Web and Social Media, Canada, vol. 11, no. 1, pp. 512–515, 2017. [Google Scholar]
21. A. A. Marghilani, “Artificial intelligence-enabled cyberbullying-free online social networks in smart cities,” International Journal of Computational Intelligence Systems, vol. 15, no. 1, pp. 9, 2022. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools