 Open Access
Open Access
ARTICLE
Resource Allocation Based on SFLA Algorithm for D2D Multicast Communications
1 University of Diyala, Department of Communications Engineering, Diyala, Baquba, 32001, Iraq
2 Erciyes University, Department of Electrical and Electronics Engineering, Kayseri, 38039, Turkey
* Corresponding Author: Wisam Hayder Mahdi. Email:
Computer Systems Science and Engineering 2023, 45(2), 1517-1530. https://doi.org/10.32604/csse.2023.030069
Received 17 March 2022; Accepted 23 May 2022; Issue published 03 November 2022
Abstract
Multicast device-to-device (D2D) communication technology is considered as one of the new technologies in the fifth generation (5G) networks that directly addresses the need for content sharing among internet users. In fact, when direct communication is available between devices, the spectral efficiency is improved by reusing the licensed cellular spectrum. The current studies show that D2D communication increases network capacity and reduces latency. In order to achieve the alternate capabilities, coordination is required to implement interference management. We considered subcarrier allocation for the uplink, in addition to the power control that takes place on the underlay network. The completed data rate in single multicast communication is significantly reduced and limited by nodes with lower channel quality. In this paper, we used Shuffled Frog Leaping Algorithm (SFLA) for resource allocation (RA) in D2D multicast communications. We compared the results of the SFLA algorithm with the Firefly Algorithm (FA), Ant Colony Optimization (ACO) and Particle Swarm Optimization (PSO); in terms of D2D user throughput, Cellular User (CU) throughput, network average throughput, network interference and signal interference noise ratio (SINR) target. The simulation results show that SFLA clearly outperforms other algorithms in terms of data rate under the high pressure of infeasibility.Keywords
The quick development that happened in cellular communication networks increases the complexity of the network structure and the number of users. As a result, D2D communication technology has been developed, and it now presents an important part in the modern 5G cellular network [1,2]. One of the basic 5G technologies is D2D communication network, which is described as a collection of devices that can communicate with each other wirelessly without the need for an infrastructure or a central authority [3]. The rapid increase in CUs, combined with the high demand for improving quality of service (QoS), has resulted in a decrease in spectral resources, which is one of several main factors restricting the development of modern communication networks [4,5] with the foreseeable explosion in the number of wireless devices, and the continuing development of multimedia services [6]. Multiplayer gaming and video streaming are considered as group communication applications, require firstly a high data rate and secondly low latency. Therefore, these applications require multicasting, which is an important feature of the cellular network [7]. Users who have the same request and are in close proximity to one other, may collaborate for improving data dissemination efficiency although the Device-to-Device users can send and receive the signals directly. However, sharing spectrum between the D2D users and the CUs produces untractable mutual interference. The most significant issues within the latter is the interference management [8]. Many studies focused on optimizing the resource allocation and reducing energy consumption, in addition to improving service performance [9]. Many studies have been conducted to investigate the resource allocation of D2D multicast communication with several objectives and constraints [10–13]. Other than the works that exist in [14–16], where these studies explain, analysis of a cooperative multicast strategy in D2D and examine the joint optimization technique in terms of subcarrier allocation. Optimizing of the data rate is the main objective that is achieved by the device user equipments (DUEs), taking into account the QoS guaranteed approach of the basic service to cellular user equipments (CUEs). The bio-inspired algorithms (BIAs) have emerged as feasible solutions to many of the wireless communication problems, such as controlling the transmission power of these dense networks in industrial environments [17], improving transmission power for wireless sensor systems [18], and optimizing coverage control for wireless sensor networks [19]. The swarm behavior of organisms is the basis of mimic that followed by swarm intelligence (SI) techniques, which lives and cooperates with each other in groups. Alhudhaif Adi et al used the PSO is also in deep learning for feature optimization and reduction using nature-based PSO [20]. As examples of the SI algorithms are PSO [21], ACO [22], Dragonfly Algorithm (DA) [23], Salp Swarm Algorithm (SSA) [24], Grey Wolf Optimizer (GWO) [25], FA [26], and SFLA [27]. In our model, DUE is permited to be allocated multiple subcarriers. The problem is described as mixed-integer nonlinear programming. This means that the cases of handling with linearity are combined with a harmonic burst of integer variables, which makes the design of the algorithm severe. In addition, the proposed resource allocation scheme is based on swarm intelligence metaphors.
According to studies in the literature review, D2D resources is very much organized in the unicast scenario [28–31]. Besides, the multicast scenario has special issues. Using a user equipment (UE) to replace the base station (BS) that performs the multicast function, which limits the network capabilities. Our review for the literature review devoted to resource assigned in the underlying device to device multicast communication, which focused essentially on the objective function that was taken into consideration, firstly for optimization, secondly for the system model that defines pattern of the interference. The study [32] proposes that the current works in Device-to-Device RA has focused on the multicast scenario largely. The authors extend their search in [11] as they study those scenarios in which DUEs can share the same subcarrier with CUs as long as there is no harm to cellular throughput from device to device transmissions. An area is defined around every D2D multicast set, not all CUEs in which area is allowed to use the same resources as the D2D transmitter. D2D throughput clusters and the probability of outage for cellular communication are discussed in [12]. In [13], The cognitive radio concept is used to discuss D2D multicast, according to a suggested two step algorithm, channel assign basics, and greedy seeking for power allocation. More specifically, it has been mentioned in a number of efforts in relation to the evolutionary computing of RA for device-to-machine communications [16]. Beside D2D communication, the technology Low Energy Wide Area Internet of Things (LPWAN) has many advantages such as: wide coverage, simple deployment, low cost and support for large communication [33], obtain high accuracy while running at interesting scope rates [34], therefore helps to have a high performance wireless connection between devices. In [35] a hybrid approach of improved binary SFLA and PSO are proposed to decrease sub-selected feature sets were optimized.
The paper consists of five sections and the remaining ones of these sections are as follows: the second section displays the model of the system and the problem. The algorithms that proposed is shown in the third section and in the fourth section the simulation results are presented. Finally, our study ends with a conclusion in the fifth section.
2 The Model of the System and the Problem
We can consider a D2D underlaying cellular network with pairs of N D2D and M CUs. The pairs D2D and CUs can locate at random when covering BS. The CU can send their packets to the BS. The D2D pairs can send their packets directly to the D2D pairs without going through the BS. Fig. 1, is an example of the studied scenarios [36].
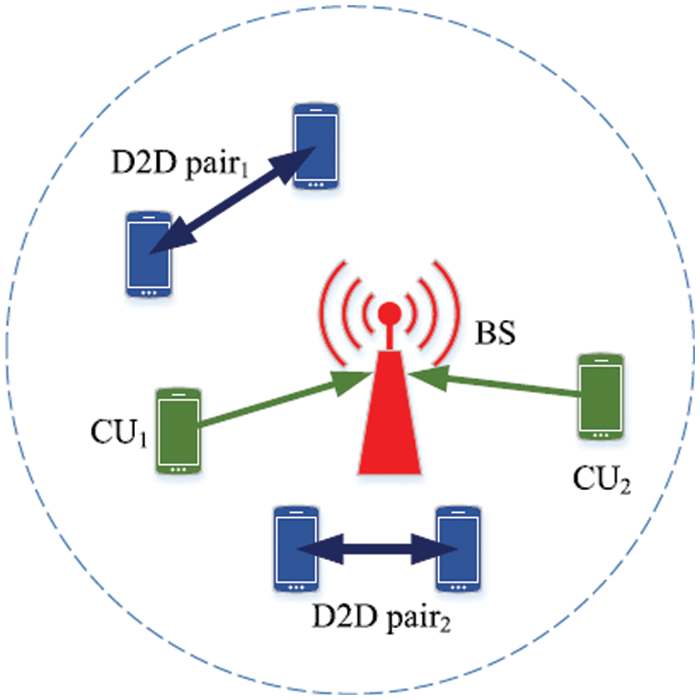
Figure 1: D2D communication underlaying cellular network [36]
The adopted architecture contains two tiers. The first level contains communication between the BS and the CUs. Communication D2D is the second level. A single-celled environment was explored, with BS at a circle center with a radius of R. M CUEs m = 1,…., M and N device-to-device pairs n = 1,…., N uniformly spread during the circle. The symbol r represents the maximum distance between the D2D transmitters and the corresponding D2D receivers. Set of D2D transmitters is C, while a set of receivers is K. The application of orthogonal allocation is done to the CUEs. Only a random number of D2D transmitters are allowed to use the same subcarrier with one CUE. Due to the obvious requirement to share download channels and strong coordination between the BS and users, sharing uplink resources is proven to be more efficient [37]. R assumes that there are a number of subcarriers. The BS suffers from D2D communication interference, and all remaining D2D receivers sharing the same subcarriers suffer from interference from D2D users and cellular users. SINR of CUE m is represented on subcarrier r by Eq. (1).
Maximizing the minimum throughput of device-to-device receivers is our objective to impose a minimum target quality of service for cellular users.
Eq. (5a) indicates for objective function on the basis of which it was formulated as the maximum–minimum problem. Eq. (5b) explains the QoS demands for the CUE as the τm threshold that is preseted. The constraints of the maximum power for device to device transmitters and CUEs are expressed by Eqs. (5c) and (5d), respectively. The maximum power for the transmitter i is represented by
3 Description of the used Optimization Algorithms
3.1 Firefly Algorithm (FA) Optimization
The algorithm idea is to find the value of the objective function at various points in the domain, initially chosen at random, while presuming that there was a firefly at each of these points and relating the functional value of these points to the light intensity generated by fireflies. Then interactions are made, following certain rules, with the objective of making the values converge to the point that generates the most brightness, that is, at the point where the function presents the optimal value. The steps for implementing the FA method can be explained as follows: One of the most important steps to do in this algorithm is to reach the convergence criterion through the objective function, set for parameters and work on generating the population through the fireflies, then calculate the light intensity I for xi in proportion to objective function for each firefly xi–. We calculated the attractiveness factor βo and then work to move the firefly x towards brightest fireflies. The steps of the algorithm can be defined as follows:


3.2 Particle Swarm Optimization (PSO)
PSO was introduced through Kennedy and Eberhart in 1995, is one of the methods inspired by nature and mimic the social interaction that occurs between a group of individuals cooperating for the purpose of obtaining food. Particle swarm method is an effective as well as an interesting approach to finding solutions to different optimization problems with enoughly perfect quality. The PSO method generally requires very moderate resource requirements except for objective function evaluation that may be somewhat costly based on the underlying problem. Velocity, current and the best position are only stored in the memory. The arithmetic procedures contained in the motion equations require main computations. Scatters the particles into a feasible region has conducted by classical algorithms, then moving them through the search space iteratively. Every particle i, at every time t, every particle include position


3.3 Ant Colony Optimization (ACO)
ACO is a probabilistic technique for finding optimal paths. The minimum flight path is represented by the maximum pheromone so that the ants follow this path [22]. Where weights are used to create solutions for random ants, the iteration has increased to 1, and new solutions are generated by finding the probability that the ants will take a different path and begin moving in that path, and a Gaussian kernel is selected by using the roulette wheel to generate new solutions. And until it reaches the end by defining a solution to the path of the ants with the least error, where the weights are updated based on the best solutions. The steps of the algorithm can be defined as follows:
3.4 Shuffled Frog Leaping Algorithm (SFLA)
SFLA is a combination of the features of a memory algorithm with PSO and was proposed in 2003. The SFLA is a random search method, which belonging to the swarm intelligence category [38]. SFLA is a meta heuristic algorithm that relied on the memetic development of a group of frogs in the event of a distinguished search for the location that contains the maximum amount of obtainable food. In SFLA, the population contains a set of frogs solutions that is divided into several subsets (memeplexes). In different memeplexes, it does a local search that considers different cultures of frogs. Examples of memes are ideas, catch phrases, clothes fashions, songs, and ways of building arches or of making pots. Frogs in every memeplex test a memetic development; which is, they contact solution local exploration space relying on particular strategies which permit the moving of meme among local individuals. After a series of memetic development steps, information is allowed to pass between memes in a shuffling process. The shuffling process and the local exploration are carried out alternatively till determined convergence criterion is accepted. So the main motive is to optimize the objective function i.e., throughput of the network. All are based on the same technique i.e finding the next best objective function and updating it. Algorithm SFLA depends on the local search technology and the global information exchange technology. The parameters that were achieved between the subsets of each other and based on certain steps of them are used to compare the two technologies. A population of frogs randomly generated. The frogs are represented as a vector of values (memo type) for the decision variables (d) contained within a d-dimensional search space, as in equation

Convergence speed and resilience for the purpose of trapping the local optima are the characteristics of the parameterization scheme. 30 times for each case was conducted during the running of the algorithm. As this value is considered within a wide range in the literature in the science of metaheuristics [30,32,37]. Here, to evaluate the performance of the four optimization algorithms, we perform a series of simulations. In Fig. 2, simulations are performed in the cell, so the distribution of Device-to-Device pairs and cellular users are randomly distributed with a 500 meter radius.
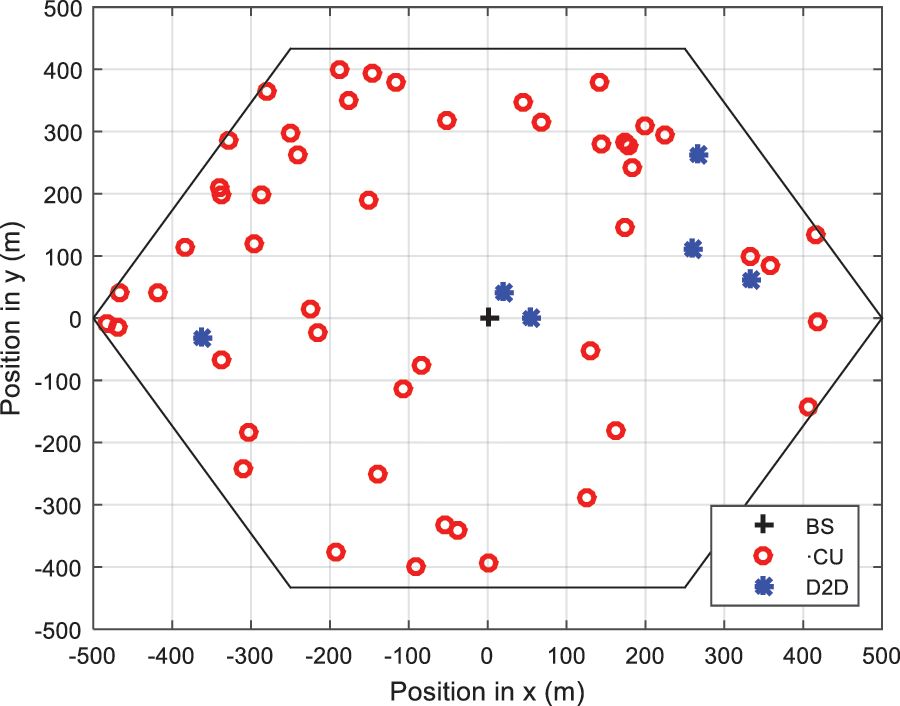
Figure 2: Network topology of D2D pairs for 50 cellular users
Tab. 3 lists the parameters for the main simulations.

Fig. 3, shows the throughput of D2D users vs. number of D2D pairs. We have considered the multi resource sharing scenario where D2D user sharing the resource block with CU user. As in starting D2D user uses the whole block that’s why the throughput is very high afterwards the throughput degraded as both D2D user and CU user sharing the same resource block. We are comparing by using four optimization techniques. As clear from the graph that SFLA optimization technique performs better than all the rest three optimization algorithms.
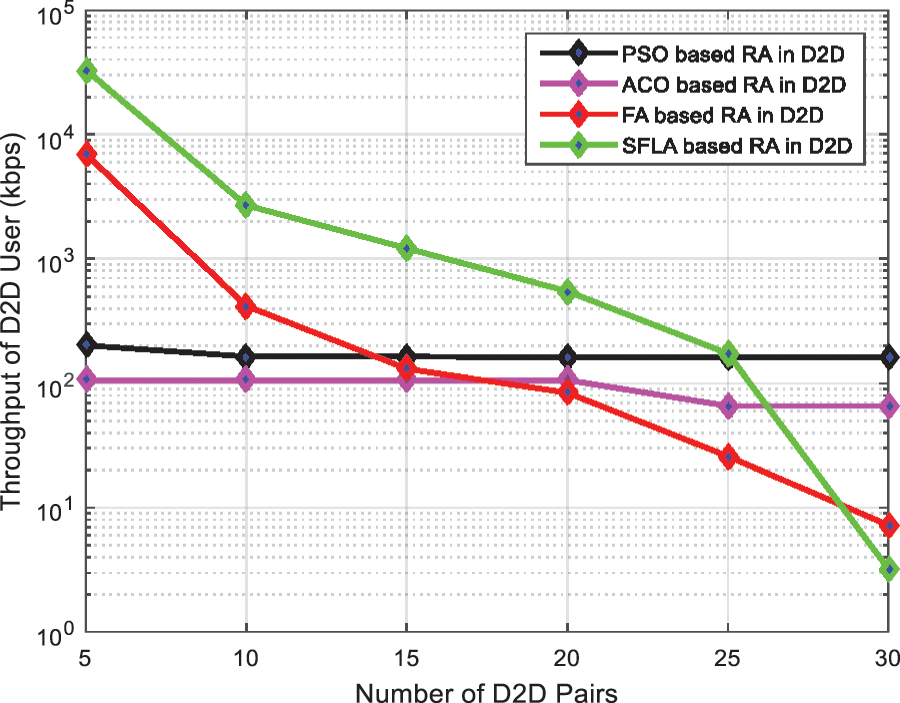
Figure 3: Throughput of D2D users vs. the number of D2D pairs
Fig. 4 shows network interference vs. the number of Device-to-Device users in the communication processes. As when starting resource block both D2D user and CU user share the same channel, so the interference is created for each other and the interference is very high, especially when two pairs of D2D with one CU user share the same channel, but after the 25th pair of D2D user, the interference slows down as we have fixed the CU users and rise the number of Device-to-Device pairs from 5 to 30.
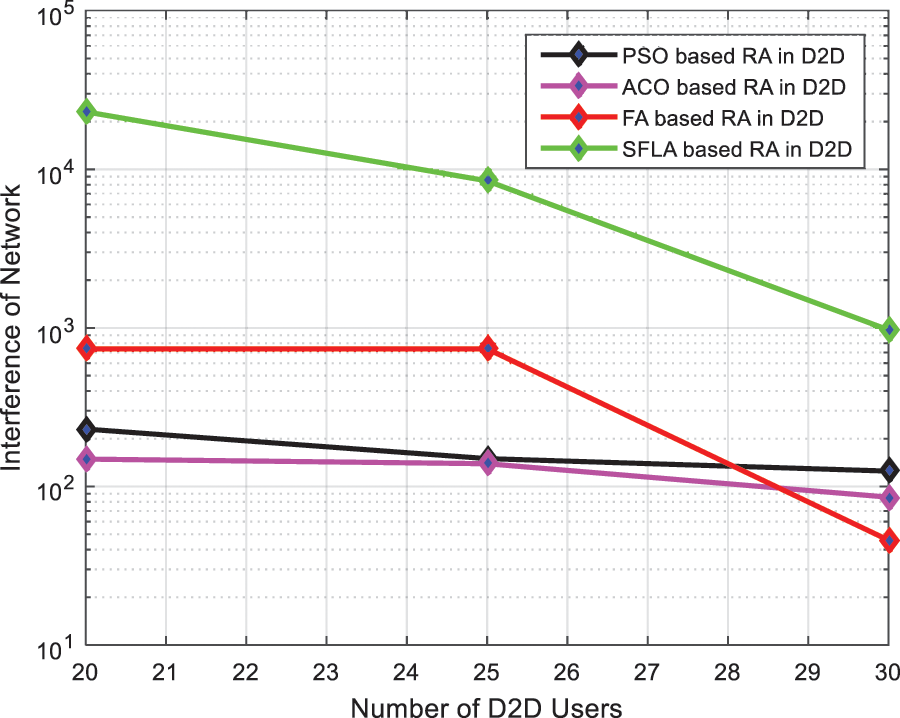
Figure 4: Network interference vs. D2D pairs
Fig. 5 shows the throughput of CU user vs. D2D pair in the network. We have fixed the CU users. At first, the BS allocates one channel to every CU user. When Device-to-Device pairs send the request for allocation then the BS allocate the same channel of CU user which create the interference thus the resulting throughput will be degraded.
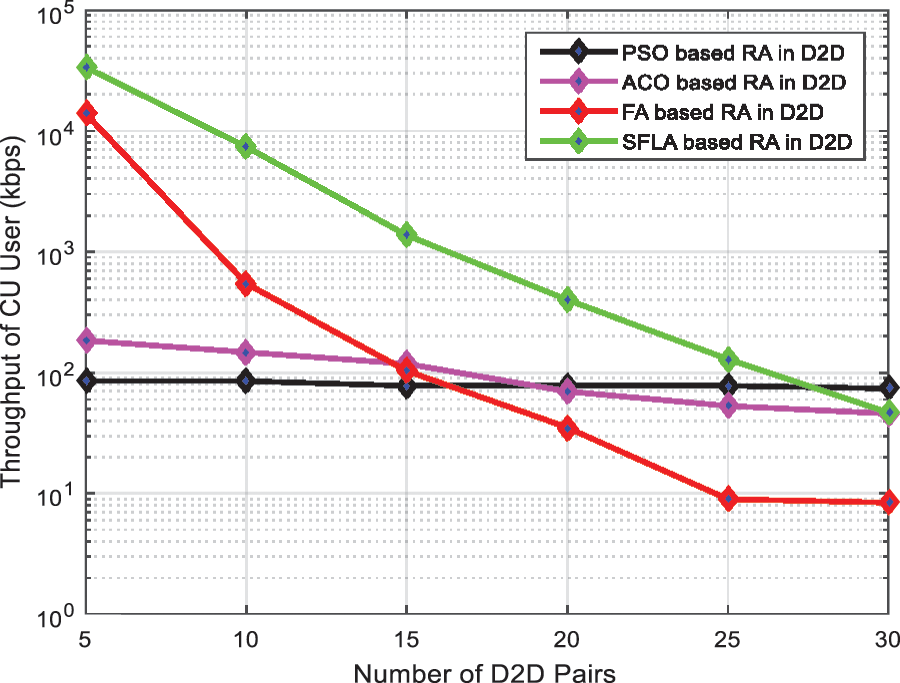
Figure 5: Throughput of CU user vs. D2D pairs
Fig. 6 shows the overall throughput of the network that is includes of D2D Users and CU Users. At first, there are 5 D2D Users and 15 CU Users. After that, we increases D2D number pairs to 30 before it was 5, we have noticed that the network total throughput is deteriorating continuously.
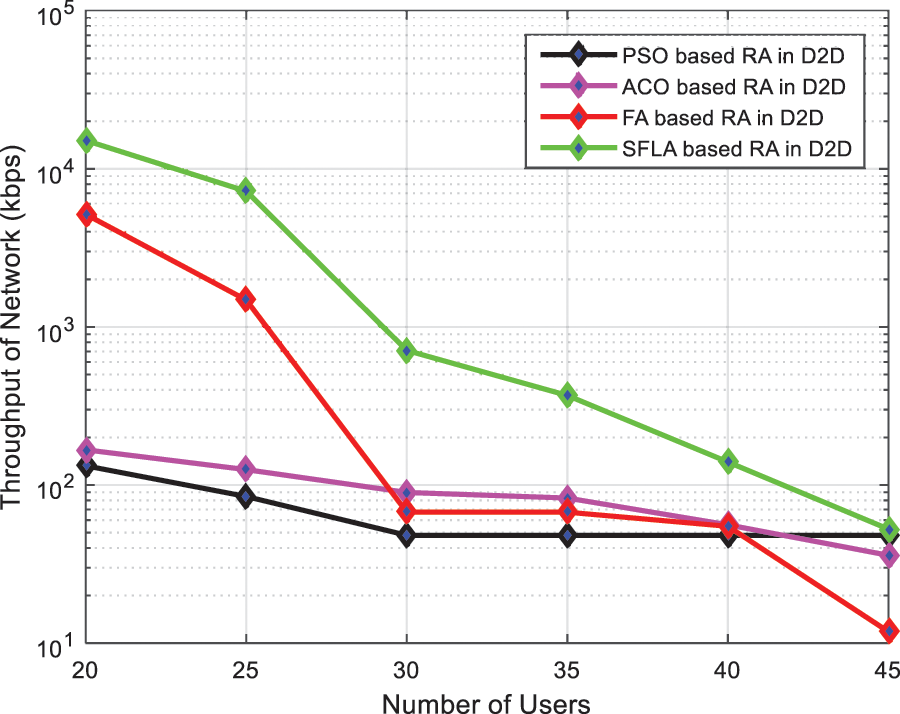
Figure 6: Total network throughput vs. (CU & D2D) users
Fig. 7 shows the throughput of D2D pair vs. the number of iteration. The precision of the algorithms increases as the number of iterations increases. Because this is a multicasts resource sharing scheme, the graph is initially low because the resource block is shared, Then the graph increases and rises clearly. SFLA and FA proved to be the best optimization technique.
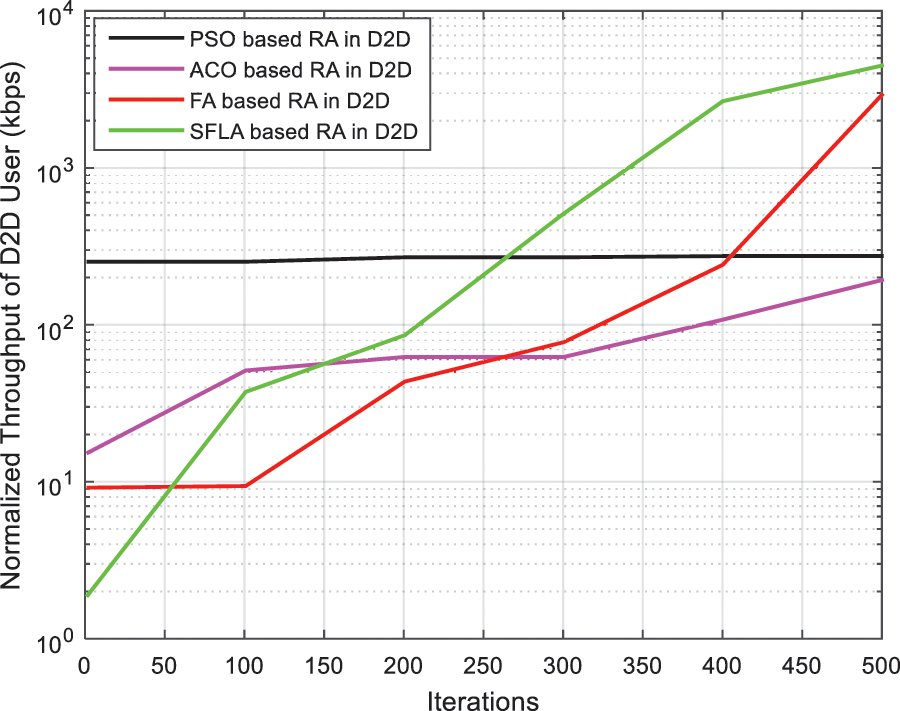
Figure 7: Throughput of D2D pair vs. the number of iterations
Fig. 8 shows the total throughput of the network vs. the number of iterations. So, increasing the number of iteration always give precise and clear results. Here as the number of iteration increases the throughput also increases. The throughput of CU and D2D users are optimized by four techniques in which PSO is consistent, while SFLA and FA are hybrid algorithms and give better results.

Figure 8: Total throughput of the network vs. number of iteration
Fig. 9 explains the effects of cellular SINR target on throughput. The behavior can be showed by the truth that the algorithm’s ability to enhance normalized D2D throughput is limited by considering the minimum target SINR that represented by each CU user. Targeting minimum range of SINR always helps in throughput performance.
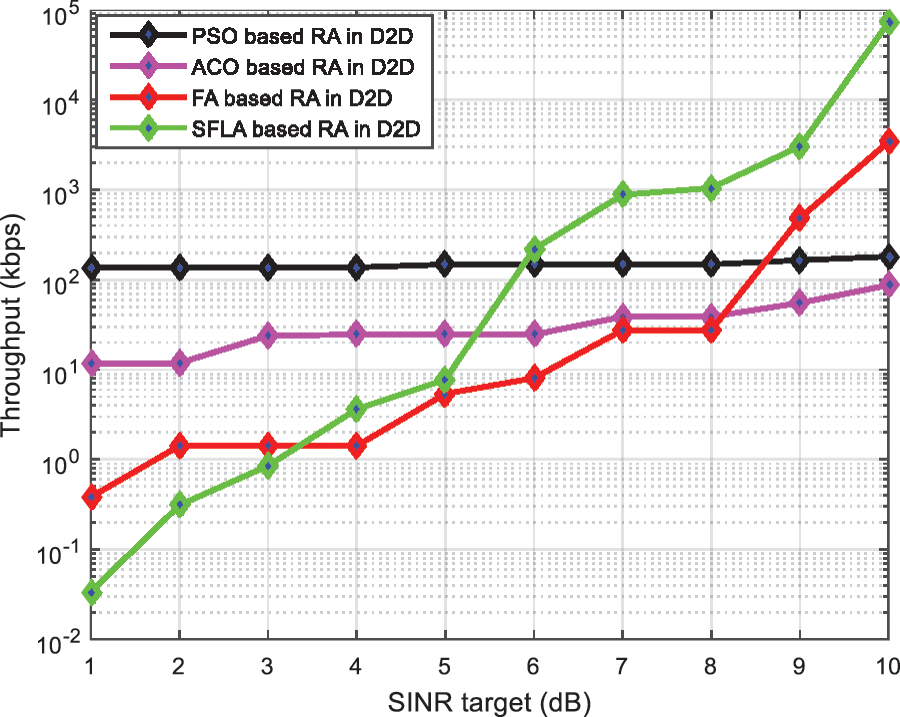
Figure 9: The effects of cellular SINR target on throughput
In this paper, we considered four algorithms: ACO, FA, PSO and SFLA to joint subcarrier allocation in D2D multicast underlay network. A monotonic ascending iteration process has been modeled and analyzed to be covered in a finite number of rounds. The optimization problem focused on increasing the minimum rate of D2D, which was dependent on the cellular spectral quality within the theory of constraints in the service sector, and the maximum constraints in the case of the transmission capacity. Our results, which included D2D user throughput, CU throughput, network average throughput, and SINR output, were obtained through optimization. The simulation results showed that despite the presence of some computational complexity relatively, the performance achieved high and distinctive results, and these results showed that the SFLA technique outperformed the other three techniques ACO, FA and PSO in different scenarios. For example, in Fig. 3, the throughput is high going towards105 for algorithm SFLA. In Fig. 7 for the throughput of D2D pair vs. the number of iteration, the throughput of SFLA algorithm, which starts from 100 by increasing the number of iterations, it is close to 105, which is a better case than the rest of the algorithms. As another superiority of algorithm SFLA over the rest of the algorithms, in Fig. 9 which showed the effects of cellular SINR target on throughput, it was noted that throughput of SFLA algorithm increases from 10-2 to 105, which is the best case in all algorithms.
Acknowledgement: This work was supported by the Erciyes University Scientific Research Projects Coordinating Unit [Project No: FDK-2021-10867].
Funding Statement: This research was funded by Erciyes University Scientific Research Projects Coordination Unit, Kayseri, Turkey, under grant No (FDK-2021-10867), Received by W.H.M and N.T. https://bap.erciyes.edu.tr.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. I. Loannou, V. Vassiliou, C. Christophorou and A. Pitsillides, “Distributed artificial intelligence solution for D2D communication in 5G networks,” IEEE Systems Journal, vol. 14, no. 3, pp. 4232–4241, 2020. [Google Scholar]
2. W. K. Lai, C. S. Shieh, F. S. Chou, C. Y. Hsu and M. H. Shen, “Handover management for D2D communication in 5G networks,” Applied Sciences, vol. 10, no. 12, pp. 4409, 2020. [Google Scholar]
3. V. Balaji and P. Selvaraj, “Gray-hole attack minimization in IoMT with 5G based D2D networks,” Computer Systems Science and Engineering, vol. 42, no. 3, pp. 1289–1303, 2022. [Google Scholar]
4. M. Hayati, H. Kalbkhani and M. G. Shayesteh, “Energy-efficient relay selection and power allocation for multi-source multicast network-coded D2D communications,” AEU- International Journal of Electronics and Communications, vol. 128, no. 3, pp. 153522, 2021. [Google Scholar]
5. Y. P. Llerena and P. R. L. Gondim, “Social-aware spectrum sharing for D2D communication by artificial bee colony optimization,” Computer Networks, vol. 183, no. 1, pp. 107581, 2020. [Google Scholar]
6. S. T. Shah, S. F. Hasan, B. C. Seet, P. H. J. Chong and M. Y. Chung, “Device-to-device communications: A contemporary survey,” Wireless Personal Communications, vol. 98, no. 1, pp. 1247–1284, 2018. [Google Scholar]
7. M. Hamdi, D. Yuan and M. Zaied, “GA-based scheme for fair joint channel allocation and power control for underlaying D2D multicast communications,” in 2017 13th Int. Wireless Communications and Mobile Computing Conf. (IWCMC), Valencia, Spain, pp. 446–451, 2017. [Google Scholar]
8. S. Toumi, M. Hamdi and M. Zaied, “An adaptive Q-learning approach to power control for D2D communications,” in 2018 Int. Conf. on Advanced Systems and Electric Technologies (IC-ASET), Hammamet, Tunisia, pp. 206–209, 2018. [Google Scholar]
9. M. Aldossary, “A review of dynamic resource management in cloud computing environments,” Computer Systems Science and Engineering, vol. 36, no. 3, pp. 461–476, 2021. [Google Scholar]
10. M. Hmila, M. F. Veiga, M. R. Perez and S. H. Alonso, “Distributed energy efficient channel allocation in underlay multicast D2D communications,” IEEE Transactions on Mobile Computing, vol. 21, no. 2, pp. 514–529, 2022. [Google Scholar]
11. H. Meshgi, D. Zhao and R. Zheng, “Optimal resource allocation in multicast device-to-device communications underlaying ITE networks,” IEEE Transactions on Vehicular Technology, vol. 66, no. 9, pp. 8357–8371, 2017. [Google Scholar]
12. J. Kim, J. Joung and J. W. Lee, “Resource allocation for multiple device-to-device cluster multicast communications underlay cellular networks,” IEEE Communications Letters, vol. 22, no. 2, pp. 412–415, 2018. [Google Scholar]
13. X. Wu, Y. Chen, X. Yuan and M. E. Mkiramweni, “Joint resource allocation and power control for cellular and device-to-device multicast based on cognitive radio,” IET Communications, vol. 16, no. 8, pp. 2805–2813, 2014. [Google Scholar]
14. S. Sun, K. Y. Kim, O. S. Shin and Y. Shin, “Device-to-device resource allocation in LTE-advanced networks by hybrid particle swarm optimization and genetic algorithm,” Peer-to-Peer Networking and Applications, vol. 9, no. 5, pp. 945–954, 2016. [Google Scholar]
15. Q. Li, X. Wang, D. Wang and L. Song, “Analysis of a cooperative caching-multicast strategy in D2D-aided networks,” IEEE Wireless Communications Letters, vol. 10, no. 12, pp. 2614–2618, 2021. [Google Scholar]
16. S. Sun and Y. Shin, “Resource allocation for D2D communication using particle swarm optimization in LTE networks,” in 2014 Int. Conf. on Information and Communication Technology Convergence (ICTC), Busan, South Korea, pp. 371–376, 2014. [Google Scholar]
17. X. Gong, D. Plets, E. Tanghe, T. D. Pessemier, L. Marterns et al., “An efficient genetic algorithm for large-scale transmit power control of dense and robust wireless networks in harsh industrial environments,” Applied Soft Computing, vol. 65, no. 4, pp. 243–259, 2018. [Google Scholar]
18. M. H. Fallah and R. Rafeh, “Proposing a centralized algorithm to minimize message broadcasting energy in wireless sensor networks using directional antennas,” Applied Soft Computing, vol. 64, no. April 4, pp. 272–281, 2018. [Google Scholar]
19. Y. Xu, O. Ding, R. Qu and K. Li, “Hybrid multi-objective evolutionary algorithms based on decomposition for wireless sensor network coverage optimization,” Applied Soft Computing, vol. 68, no. 2, pp. 268–282, 2018. [Google Scholar]
20. A. Alhudhaif, A. Saeed, T. Imran, M. Kamran, A. S. Alghamdi et al., “A particle swarm optimization based deep learning model for vehicle classification,” Computer Systems Science and Engineering, vol. 40, no. 1, pp. 223–235, 2022. [Google Scholar]
21. J. Kennedy, “Particle swarm optimization,” in Encyclopedia of Machine Learning. Boston, MA: Springer US, pp. 760–766, 2010. [Google Scholar]
22. M. Dorigo and G. D. Caro, “Ant colony optimization: A new meta-heuristic,” in Proceedings of the 1999 Congress on Evolutionary Computation (CEC99), vol. 2, pp. 1470–1477, 1999. [Google Scholar]
23. S. Mirjalili, “Dragonfly algorithm: A new meta-heuristic optimization technique for solving single-objective, discrete, and multi-objective problems,” Neural Computing and Applications, vol. 27, no. 4, pp. 1053–1073, 2016. [Google Scholar]
24. S. Mirjalili, A. H. Gandomi, S. Z. Mirjalili, S. Saremi, H. Faris et al., “Salp swarm algorithm: A bio-inspired optimizer for engineering design problems,” Advances in Engineering Software, vol. 114, pp. 163–191, 2017. [Google Scholar]
25. S. Mirjalili, S. M. Mirjalili and A. Lewis, “Grey wolf optimizer,” Advances in Engineering Software, vol. 69, pp. 46–61, 2014. [Google Scholar]
26. X. S. Yang, Nature-inspired metaheuristic algorithms, 2nd ed., United Kingdom: Luniver press, pp. 4–9, 2010. [Google Scholar]
27. M. M. Eusuff and K. E. Lansey, “Optimization of water distribution network design using the shuffled frog leaping algorithm,” Journal of Water Resources Planning and Management, vol. 129, no. 3, pp. 210–225, 2003. [Google Scholar]
28. M. Ahmed, H. Shi, X. Chen, Y. Li, M. Waqas et al., “Socially aware secrecy-ensured resource allocation in D2D underlay communication: An overlapping coalitional game scheme,” IEEE Transactions on Wireless Communications, vol. 17, no. 6, pp. 4118–4133, 2018. [Google Scholar]
29. F. Hussain, M. D. Y. Hassan, M. D. S. Hossen and S. Choudhury, “System capacity maximization with efficient resource allocation algorithms in D2D communication,” IEEE Access, vol. 6, pp. 32409–32424, 2018. [Google Scholar]
30. A. Celik, R. M. Radaydeh, F. S. Al-Qahtani and M. S. Alouini, “Joint interference management and resource allocation for device-to-device (D2D) communications underlying downlink/uplink decoupled (DUDe) heterogeneous networks,” in 2017 IEEE Int. Conf. on Communications (ICC 2017), Paris, France, pp. 1–6, 2017. [Google Scholar]
31. A. Algedir and H. H. Refai, “Adaptive D2D resources allocation underlaying (2-tier) heterogeneous cellular networks,” in 2017 IEEE 28th Annual Int. Sym. on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, Canada, pp. 1–6, 2017. [Google Scholar]
32. H. Monia and M. Zaied, “Resource allocation based on hybrid genetic algorithm and particle swarm optimization for D2D multicast communications,” Applied Soft Computing, vol. 83, no. 1, pp. 105605, 2019. [Google Scholar]
33. L. Ma, M. Zhao, D. Ma and Y. Fu, “A LoRaWAN access technology based on channel adaptive adjustment,” Journal of New Media, vol. 2, no. 1, pp. 11–20, 2020. [Google Scholar]
34. W. Sun, L. Dai, X. R. Zhang, P. S. Chang and X. Z. He, “RSOD: Real-time small object detection algorithm in UAV-based traffic monitoring,” Applied Intelligence, vol. 52, no. 8, pp. 8448–8463, 2022. [Google Scholar]
35. S. P. Rajamohana and K. Umamaheswari, “Hybrid approach of improved binary particle swarm optimization and shuffled frog leaping for feature selection,” Computers & Electrical Engineering, vol. 67, no. 4, pp. 497–508, 2018. [Google Scholar]
36. X. Jun and C. Guo, “Resource allocation for real-time D2D communications underlaying cellular networks,” IEEE Transactions on Mobile Computing, vol. 18, no. 4, pp. 960–973, 2018. [Google Scholar]
37. J. Zhang, G. Wu, W. Xiong, Z. Chen and S. Li, “Utility-maximization resource allocation for device-to-device communication underlaying cellular networks,” in 2013 IEEE Globecom Workshops, pp. 623–628, 2013. [Google Scholar]
38. M. Mafarjaa, I. Aljarahb, A. A. Heidaric, H. Farisb, P. F. Vigerd et al., “Binary dragonfly optimization for feature selection using time-varying transfer functions,” Knowledge-Based Systems, vol. 161, pp. 185–204, 2018. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools