 Open Access
Open Access
ARTICLE
Energy Proficient Reduced Coverage Set with Particle Swarm Optimization for Distributed Sensor Network
1 Department of Computer Science and Engineering, Arunachala College of Engineering for Women, Manavilai, Tamil Nadu, 629203, India
2 Department of Electronics and Communication Engineering, St. Xavier’s Catholic College of Engineering, Chunkankadai, Tamil Nadu, 629003, India
* Corresponding Author: T. V. Chithra. Email:
Computer Systems Science and Engineering 2023, 45(2), 1611-1623. https://doi.org/10.32604/csse.2023.026561
Received 30 December 2021; Accepted 22 February 2022; Issue published 03 November 2022
Abstract
Retransmission avoidance is an essential need for any type of wireless communication. As retransmissions induce the unnecessary presence of redundant data in every accessible node. As storage capacity is symmetrical to the size of the memory, less storage capacity is experienced due to the restricted size of the respective node. In this proposed work, we have discussed the integration of the Energy Proficient Reduced Coverage Set with Particle Swarm Optimization (PSO). PSO is a metaheuristic global search enhancement technique that promotes the searching of the best nodes in the search space. PSO is integrated with a Reduced Coverage Set, to obtain an optimal path with only high-power transmitting nodes. Energy Proficient Reduced Coverage Set with PSO constructs a set of only best nodes based on the fitness solution, to cover the whole network. The proposed algorithm has experimented with a different number of nodes. Comparison has been made between original and improved algorithm shows that improved algorithm performs better than the existing by reducing the redundant packet transmissions by 18% ~ 40%, thereby increasing the network lifetime.Keywords
An energy-efficient design of the Wireless Sensor Network (WSN) plays a vital role in the wireless network’s domain. To increase the lifetime of the sensor node, a novel algorithm that efficiently manages energy utilization is very much needed. WSNs are characterized as self-designed networks without infrastructure used to screen physical or natural conditions such as sound, temperature, weight, vibration, movement, or positions. WSN is also used to transmit multimedia content such as audio, video, images along with text and hence it is used in the personal area and trade computing [1]. Any sensor node can recover necessary data from the network by infusing queries to the sink node. In general, a WSN contains a huge number of inexpensive and lightweight microsensor nodes. The sensor nodes identify their neighbor nodes by broadcasting Radio Frequency signals after their deployment [2]. The Base Station may forward that meaningful information to the cloud via the Internet in a wired or wireless connectivity. A few advances exist to get energy from the earth, for example, sunlight-based, warm, active energy, and vibration energy. The benefits of energy collecting frameworks as the capacity to energize after exhaustion. Though many energies efficient techniques are existing, numerous significant issues are still to be addressed [3,4]. WSNs lack a standard technique for selecting and updating energy-intensive components. The current techniques concentrate on a single point of view and stack energy utilization in a variety of ways. Existing approaches do not take into account quantitative energy consumption proportions. They’re best used in explicit sensor systems with unusual properties.
A vast majority of sensors are powered by batteries, which are unstable in harsh settings, making the sensor a power hog. Because sensor nodes must preserve energy, it is challenging to build large-scale WSNs. A WSN model is shown in Fig. 1.
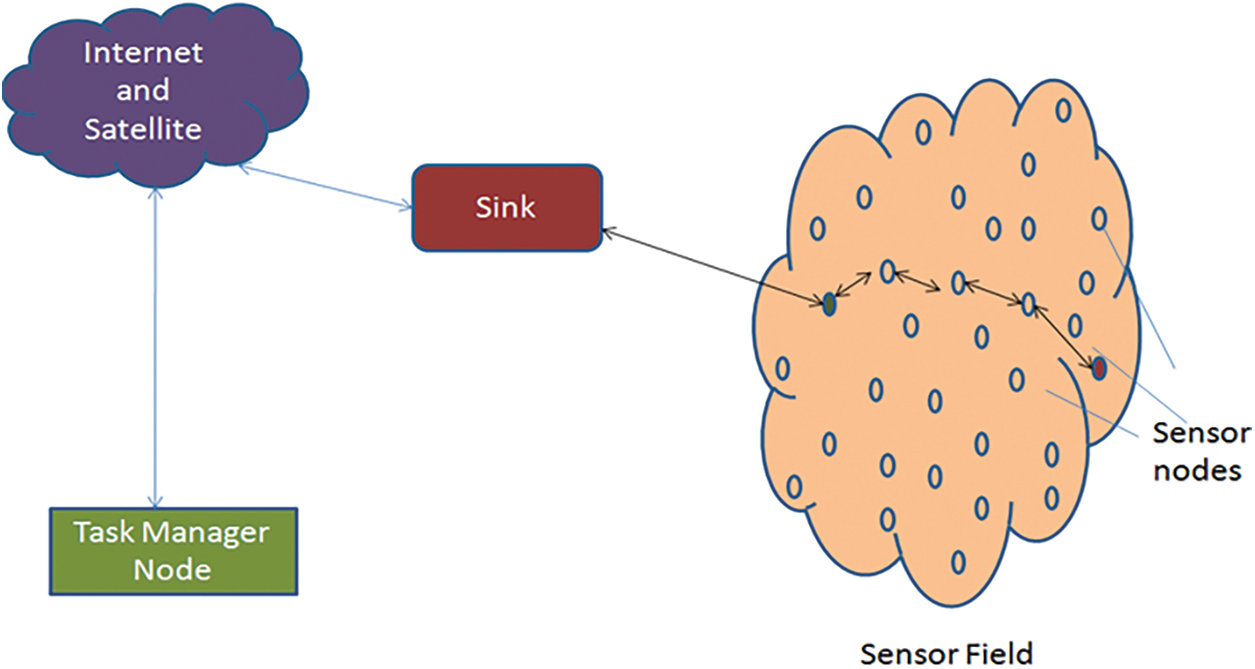
Figure 1: A Sample WSN
WSN challenges are often formulated as optimization problems such as node deployment, localization, memory consumption, energy-aware processing, and data transfer [5]. The traditional analytical optimization techniques suffer greatly from heavy computational efforts. An optimization method that consumes less memory and less computational resources also which can produce good results is much required, especially for individual sensor node implementation.
Sensor Protocol for Information via Negotiation is carried out and the primary goal of this protocol is to overcome the drawbacks of flooding and gossiping [6]. Sender informs the presence of new data using ADV which carries meta-data to every one of its neighbors. The sender in turn sends a DATA message which carries the real data. Low-Energy Adaptive Clustering Hierarchy (LEACH) belongs to node centric type of routing protocol [7]. In node-centric protocols, destinations are specified based on the numerical addresses of nodes. One node among the cluster is selected as cluster head. Thus, LEACH achieves an increase in system lifetime, limits energy utilization on every node, and diminishes the number of correspondence messages. This protocol uses probability-based calculation for cluster head selection periodically, so that the same node is not targeted as cluster head which can prevent energy depletion from a single node at all times. In Power Efficient Gathering in Sensor Information Systems (PEGASIS), the sender sensor node attempts to find its closest neighbor by measuring the 1-hop neighbors signal strength [8,9]. The sender sends the intended data to only the identified closest neighbor, who in turn forwards it to its closest neighbor and this procedure continues until data has reached the Base Station (BS). PEGASIS can perform better than LEACH protocol by avoiding cluster formation overhead and thereby increasing twice the network lifetime. The Directed Diffusion is one of the best examples of Data-Centric routing protocol [10]. Here the sink node or the base station prepares a query that contains the required data details and broadcast to its one-hop neighbors which in turn broadcast to its one-hop neighbors. The BS aggregates the related data that are received from the whole network and produces meaningful information. The primary task of Directed Diffusion is to eliminate redundancy and thereby increase the network lifetime [11,12]. The major objectives of the research are explained as, Study and analysis of different routing protocols and energy-efficient methods meant for reducing the energy utilization for improving the lifetime of the sensor Further to improve the lifetime of the sensor node, Energy Proficient Reduced Coverage Set Using PSO is proposed. To obtain a quantitative estimation and display of the general common energy utilization parameters. Analysis of the performance of (RCS), EPRCS-PSO, and Distance Mapping Algorithm (DMA) schemes in terms of different metrics such as flooding delay, delivery delay, and energy efficiency. PSO is a simple concept, easy implementation for WSN, robustness to control parameters, and computational efficiency compared to mathematical algorithm and other heuristic optimization techniques. Maximum number of iteration, the current number of iteration Iter.
The organization of the paper is represented as follows Chapter 1 presents the fundamental concepts of WSN, architecture, types, routing protocols, challenges, and its applications. Chapter 2 gives a detailed overview of various literature related to the research topic and the results arrived at after analyses. Chapter 3 presents the proposed energy proficient flooding scheme using the Reduced Coverage Set (RCS) algorithm for unreliable links. The mathematical expressions for energy consumption and background are discussed. Chapter 4 describes the performance of the Energy Proficient RCS Scheme with the PSO Technique. Chapter 5 concludes all the presented work in this thesis and discusses several ideas for future works.
Hu et al. [13] have proposed PSO-Traffic for determining large power transmitting nodes so that the largest possible connectivity is established or structured with the limited hardware setup for a real-world vigilance problem. Lots of nodes loaded with cameras, combined with greater transmission radii aided by costly heavy-power transmitters are used for research purposes. The research aims to determine high power transmitter nodes such that the prefect network is obtained. In addition to increased capital expenditure, the operating expenses are also higher, due to the necessary maintenance and repair.
Hong et al. [14] have proposed PSO Multi-Base which achieves the finest deployment of base stations in WSN. Application nodes can contact only with the sensor nodes they are assigned to according to PSO MultiBase. Application nodes contain high-range transmitters and giga speed processors. The PSO Multi-Base method minimizes the whole network lifetime and also demands less transmission power by minimizing the total application nodes distances to their nearest base station. It cannot work out the problems of scattering and also the computation time is high.
Borges et al. [15] exhibited a study on remote sensor applications. In this survey, the authors attempt to fill the gap in the WSN literature, via portraying the characterization parameters into six distinct classes such as service, service supplying components, transmission, the whole network, single node, and surroundings. Different application requirements demand a standard taxonomy for a clear understanding of which requirements are mostly required for a particular application area. The first generation refers to WSN that contains only isolated and self-contained systems. The third generation refers to Internet-Of-Things (IOT) where all the physical things in the world can be connected to the Internet.
Dezfouli et al. [16] proposed a Geowindow algorithm, for achieving better broadcasting performance in larger networks configured with dynamic topology. The authors attempt to increase the efficiency of Neighbour Collection Tree Construction (CTC) and Discovery and Link Estimation (NDLE) phases. NDLE phase is used for finding then estimating the reliability nature of neighbour links. A mathematical model is proposed to manage the length of the contention window, to overcome network conflicts and thereby increase the efficiency of NDLE and CTC to nearly 75%. Authors conclude that by combining linear and exponential backoff schemes, the accuracy of broadcasting improves greatly, without any extra overhead.
Wang et al. [17] proposed two efficient protocols, which guarantee better coverage and dynamic configuration setup for diverse application areas. Wide coverage is required to sustain node failures, overcome communication bottlenecks, and thereby achieve high throughput. The Coverage Configuration Protocol (CCP) guarantees various degrees of coverage as dictated by wide dynamic applications and to self-arrange a network, for a wide scope of uses and potentially powerful situations. Coordination of CCP criteria with SPAN criteria gives a new set of required criteria for any node to tune ON or OFF.
Medagliani et al. [18] discussed the crucial issue of energy proficient target recognition in unattended WSN. Authors propose an analytical model framework to optimize the system parameters such as notification, detection delay, and probability of failure in target finding. The proposed framework suits well in partially covered and randomly deployed WSN fields. To maximize the network lifetime, the duty-cycled style of operation operates at sensing and collaboration layers of WSN. Whenever a target is found, notification reaches the BS as fast as possible. An analytical framework accuracy increased as the number of deployed nodes increases.
Johnson et al. [19] presented a protocol that uses Dynamic Source Routing (DSR) for routing packets in a topology-changing network. In the source routing technique, before routing starts, the sender is fully aware of the list of nodes through which data may travel and reach the destination. DSR attempts to reduce traffic overhead by not forwarding advertisement messages periodically within a network. DSR performs route discovery by forwarding route requests within its radio limit and receiving route reply packets. However, this protocol does not deal with the security concerns that prevail in a dynamic network.
Shah et al. [20] proposed a new technique called energy-aware routing whose end goal is to attain energy gain by using sub-optimal paths at times of need. Authors have suggested avoiding the use of the lowest energy routes at all times, since it may affect the network lifetime and long-term connectivity. As nodes throughout the network may drain energy, leading to more degradation in service over time. The lowest energy path mostly consists of low-energy nodes that can drain faster. The reproduction outcomes display that energy-aware routing achieves up to a 40% increase in network lifetime over comparable methods like directed diffusion routing.
Wang et al. [21] defined Quality of Forwarding (QoF), as an important measurement for estimating the path quality obtained by aggregating the QoF measures of nodes and links present in the network. The authors also attempt to modify the Collection Tree Protocol (CTP). Simulation results show that in QoF based routing, there is a decrease in the transmission cost for each delivery by 28%–34%, also the throughput is found to be increased from 12%–15%. In existing CTP, the faulty nodes are unable to identify and hence more transmission failures occur. But in this modified-CTP, through QoF measure the quality of nodes and links are studied, and therefore traffic is made to flow along only through non-faulty nodes and non-faulty links resulting in improved performance.
Liono et al. [22] proposed Quality driven Data Summarizations (QDaS) for efficient data storage management in IoT devices. QDaS performs a data summarizations mechanism based on the Quality of Data (QoD) metric. An effective data quality estimation technique calculates QoD based on the data utility, accuracy, completeness, consistency, timeliness, availability, validity, integrity, and relevancy. The simulation result shows that the amount of data stored gets greatly reduced with the application of the QoD based data summarization mechanism.
Al-Ma’aitah et al. [23] proposed Transmission Adaptive Mode Selection (TAMS) for minimizing the energy expenditure of internet of things devices. In this paper, two more models are developed: (i) To lessen the collision, a controlled data dissemination model is performed i.e., TAMS dictates the receiving device to have energy above the minimum limit, also sending device, sends only a few data to the receiving device if and only if the sending device has enough energy for transmitting. (ii) To lessen the energy consumption, this energy-efficient model uses an entropy encoder to compress the block of data during transmission without affecting the quality. The simulation results show that the data loss due to less available energy and collision is greatly avoided.
The battery-operated sensors are frequently deployed in hostile environments and hence replacing dead batteries with new ones is a practically tedious task. The placement of sensor nodes is considered a crucial issue that can degrade the performance of network operations such as routing, security, and energy utilization. Sensor nodes placed near the base station will dissipate more energy than distantly placed nodes because they have to get and retransmit packets from and to other nodes. Thus, sensor node placement is the most fundamental problem in improving the lifetime of large-scale wireless sensor networks.
The lifetime of the network can be greatly improved by maximizing the coverage. To maximize the coverage, the sensor nodes are placed in a position to fully utilize their sensing capability. Also, if all the nodes involved in the transmission are within the communication limit, then the maximum coverage can be achieved. PSO algorithm helps to extend the network lifetime by providing the best coverage. PSO is used to determine the optimal node positions to attain maximum coverage.
PSO is well-known in the field of multidimensional improvement. Simple to use, high-quality arrangements, calculation productivity, and speed are all hallmarks of PSO. PSO is based on how birds or fish behave as a group. They usually travel in groups in search of food, water, and shelter to lessen their exertion when hunting for food, water, and shelter. This chapter provides an in-depth examination of PSO’s achievements in enhancing the energy efficiency of remote sensing systems.
There are two types of social interactions that occur among swarm members. Direct interactions fall into one of two categories: direct and indirect contacts. Direct engagement can take the form of visual or aural touch, as seen in honey bees dancing in the air. Individuals modify their habitats in response to environmental changes. This is referred to as the stigmergy technique, a type of indirect interaction, which communicates through the environment.
Dr. Kennedy and Dr. Eberhart presented PSO as a multi-dimensional global optimization approach in 1995. It’s an algorithm based on studies of flock movement behavior in birds and fish. The birds flock together or disperse in search of a food source. One of the birds in the group can detect the scent of food quite well, indicating that the bird is aware of the location of the food. Birds distribute the information about the food, to the other birds in a short interval of time, and hence the birds from other places will move to the area where food is present.
The proposed Energy Proficient Reduced Coverage Set with PSO (EPRCS-PSO) objective is to attain maximum coverage with the only minimum number of sensor nodes that are optimally placed through PSO [24]. EPRCS-PSO algorithm is proposed mainly to extend the lifetime of WSN. EPRCS-PSO improves the network lifetime by reducing the number of forwarding nodes using RCS and maximizing the coverage area using PSO. Wang et al. [25] mentioned that the PSO decides the search path as indicated by the speed and current position of the particle. PSO algorithm advantages include fast calculations, the requirement of less memory space, less parameter used, and are easier to realize [26]. Because of its enormous advantages, the algorithm can be utilized generally in the fields, for example, work optimization, the model order, machine study, neural system preparing, the sign procession, vague framework control, programmed adjustment control, and so forth. This social conduct is imitated by PSO utilizing a swarm of specialists named particles.
Particle neighborhood in PSO had been considered from two points of view; global neighborhood (
Every molecule I, in the swarm, hold the accompanying data:
The current position
The current speed
The current velocity
At the initial stages of PSO, every particle is allotted a random position and speed to move in the search space. At every iteration, every particle discovers its own best, i.e., individual best-called
The current position
Fitness function is calculated as per below Eq. (3)
The quality of the solution is determined by evaluating each particle’s fitness capability. PSO’s goal is to discover the best particle placements given a fitness function. The nature of the arrangement is assessed by a fitness function, which is an issue to be addressed. The present arrangement is compared with the fitness of

In this proposed work, an upgraded RCS calculation utilizing the PSO system (EPSO-RCS) calculation for coverage set choice is proposed for energy protection. The ideal determination of coverage set utilizing PSO minimizes the power consumption rate of every sensor node by sending information packets to its most extreme coverage neighbor node rather than straightforwardly sending them to the base station, which incredibly diminishes the energy consumption. PSO is engaged to calculate disjoint coverage sets and only the sensors in the set are used for transmitting and storing the information, and the rest of the sensors are expected as powerless dead sensors, which can be disposed of. The proposed calculation is intended for extending the lifetime of WSN shown in Fig. 2.
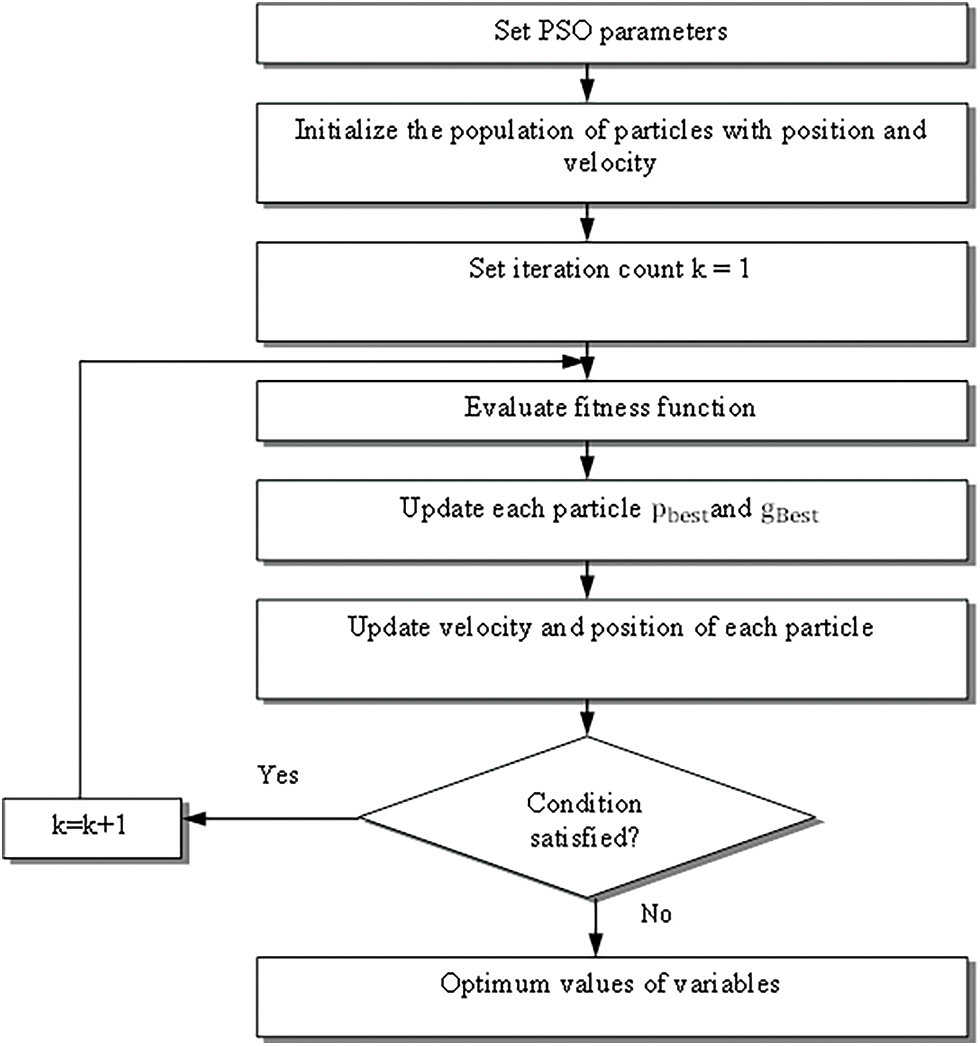
Figure 2: Flowchart of PSO
The following algorithm explains how the Reduced Coverage Set (RCS) is framed using PSO.

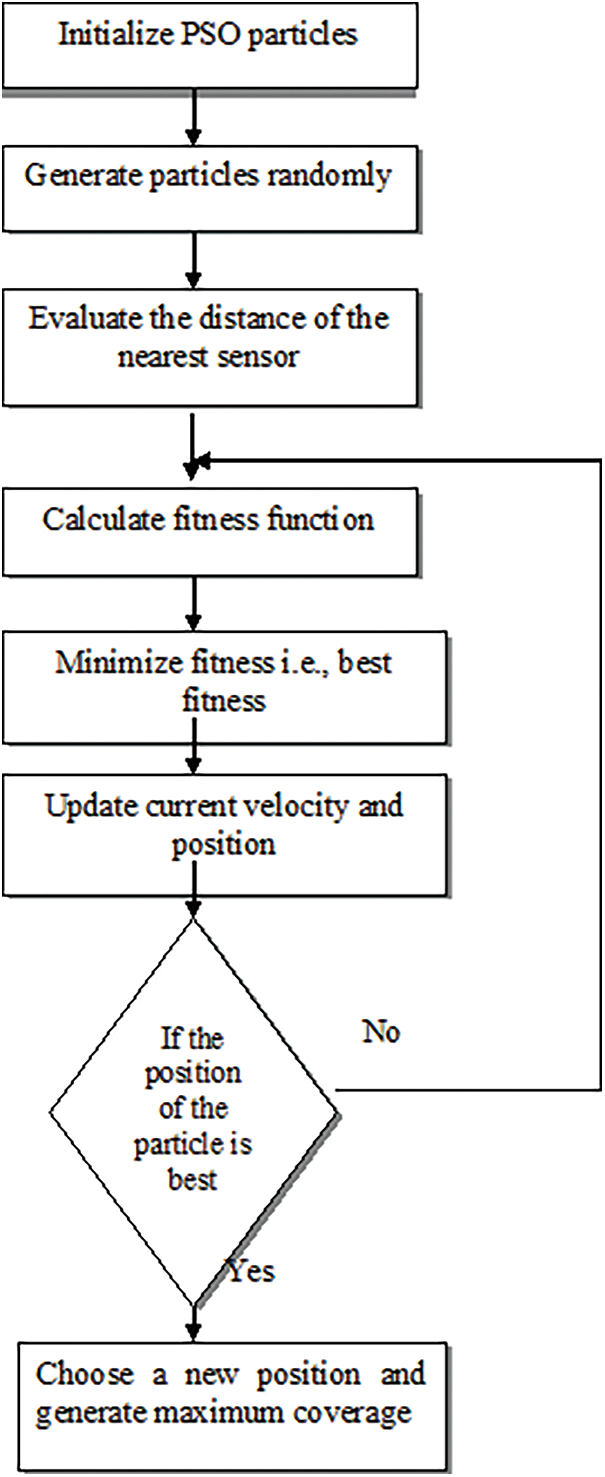
Figure 3: Flowchart of the proposed model
Network Model
The proposed work recreates the WSN with certain presumptions as follows:
i) All the chosen nodes are considered static after placement.
ii) Sensor node for observing the environmental conditions and the other node is a sink or base stations are the two kinds of nodes taken into account in a network.
iii) Sensor nodes are initially assigned with distinguishing proof and energy.
iv) Node is permitted to utilize transmission power of various levels.
v) The base station frequently sends solicitation messages for getting information from sensors.
vi) Links are considered symmetric.
WSN is modeled by randomly placing sensor nodes in the required region of interest. After the nodes are deployed randomly, they start acting as stationary nodes. The distance among the sensor nodes and that of the distance among each node to the base station are found. The fitness value for each of the chosen nodes is determined using the fitness function. Depending on the distance and position of a node, the best solution is found. Non-feasible solutions are rejected. To the base station, the entire sensing field is split into several regions. Sensor nodes perform indirect communication for the base station.
Considering the WSN model, each sensor node and each gateway are placed randomly. As nodes become stationary when they are deployed, they become mobile. We must then calculate the distance between each node and assign them to the Gateways. The next step is to determine the distance between each node and calculate the distance from each node to the sink node.
The basic steps in performing the above are:
Step 1: - There is the random deployment of nodes in the required region of interest. Based on these nodes a network is formed in form of mesh topology.
Step 2: - Implement PSO
Step 3: - Calculate the fitness value for each of the eligible nodes. The fitness value is calculated by using the fitness function. It gives the rate of change of distance and speed of a node.
Step 4: - Find the best solution. The best solution is based upon the distance and position of a node.
Step 5: - The selection process gives the optimal solution for the search space and also defines the feasible solution which consists of the most optimal solution with a smaller number of dead nodes.
Step 6: - Ignoring or eliminating all the non-feasible solutions.
Step 7: - Dividing the entire area into the different number of zones for the base station.
Step 8: - Finally there is indirect communication between nodes for the base station.
Step 9: - Define all the parameters.
The experimental results performance of the RCS, RCS with BLCS, and the proposed RCS with PSO is evaluated with the metrics (1) Flooding Delay (2) Average Delivery Delay, (3) Energy Efficiency and (4) Network Life Time
Flooding delay is the total time taken for a source node to flood data packets.
Average Delivery Delay is calculated by averaging the delivery delay per node per packet.
Energy Efficiency is the total number of data transmissions for flooding a certain number of data packets to the entire network.
Network lifetime is the time until the first sensor’s energy runs out is an important performance metric in WSNs [27]. In traditional WSNs, all the sensor nodes are configured to forward collected data to the sink through multihop communication.
The average delivery latency of present methods rises as the network size expands, as seen in Fig. 4 The suggested approach, on the other hand, reduces the average delivery latency, allowing for improved outcomes. Averaging the delivery delay per node per packet yields the average delivery delay. When a node is not forced to wait for a message for an extended time, its energy consumption is considerably decreased. Furthermore, the BLCS system is used for collision avoidance since it only outputs excellent connections for flooded packet forwarding. We may deduce the benefits of the planned work from these findings, such as a shorter delivery time.

Figure 4: Average delivery delay vs. network size
Average Delivery Delay is calculated by averaging the delivery delay per node per packet. The average flooding delay must decrease as the duty cycle increases. The existing algorithm’s average flooding delay also decreases as the duty cycle increases but not to the level of proposed algorithm performance. This is due to the fact, that our algorithm takes care of coverage set selection using the fitness function. The results are shown in Fig. 5.

Figure 5: Average flooding delay vs. duty cycle
Energy Efficiency is calculated as the total number of data transmissions for flooding a certain number of data packets to the entire network. The results are shown in Fig. 6 and it depicts that the proposed algorithm achieves a smaller number of transmissions compared to the existing algorithms. The proposed algorithm attempts to reduce the redundant transmissions among the neighbors, by selecting only a few neighbors who can cover maximum nodes.

Figure 6: Number of transmissions vs duty cycle
As the number of transmissions reduces, the network lifetime increases. The results are shown in Fig. 7. The proposed algorithm consumes fewer energy and has more network lifetime in compared with existing ones, it achieves better performance.

Figure 7: Network life time vs. nodes
PSO has been a prominent technique used to deal with optimization problems in WSNs due to its easiness, good kind of solutions, rapid convergence, and significant computational burden. A new technique is suggested in this research work which uses Reduced Coverage Set with PSO called Energy consumption of each node in WSN, thereby maximizing the whole network lifetime. The proposed algorithm has experimented with the different number of nodes. Comparison has been made between original and improved algorithm shows that improved algorithm performs better than the existing by reducing the redundant packet transmissions by 18% ~ 40%, thereby increasing the network lifetime. Research on Cross-layer optimization through PSO can be focused in the future.
Acknowledgement: Author with a deep sense of gratitude would thank the supervisor for his guidance and constant support rendered during this research.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. I. F. Akyildiz, W. Su, Y. Sankarasubramaniam and E. Cayirci, “Wireless sensor networks: A survey,” Computer Networks, vol. 38, no. 4, pp. 393–422, 2002. [Google Scholar]
2. D. S. Sundaram, P. Puri and V. Yang, “A general theory of ignition and combustion of nano-and micron-sized aluminum particles,” Combustion and Flame, vol. 169, no. 2, pp. 94–109, 2016. [Google Scholar]
3. J. Yick, B. Mukherjee and D. Ghosal, “Wireless sensor network survey,” Computer Networks, vol. 52, no. 12, pp. 2292–2330, 2008. [Google Scholar]
4. K. Romer and F. Mattern, “The design space of wireless sensor networks,” IEEE Wireless Communications, vol. 11, no. 6, pp. 54–61, 2004. [Google Scholar]
5. J. Kennedy and R. Eberhart, “Particle swarm optimization,” in Proc. ICNN’95-Int. Conf. on Neural Networks, Perth, WA, Australia, pp. 1942–1948, 1995. [Google Scholar]
6. K. Akkaya and M. Younis, “A survey on routing protocols for wireless sensor networks,” Ad Hoc Networks, vol. 3, no. 3, pp. 325–349, 2005. [Google Scholar]
7. Y. Del Valle, G. K. Venayagamoorthy, S. Mohagheghi, J. C. Hernandez and R. G. Harley, “Particle swarm optimization: Basic concepts, variants and applications in power systems,” IEEE Transactions on Evolutionary Computation, vol. 12, no. 2, pp. 171–195, 2008. [Google Scholar]
8. K. Price, R. M. Storn and J. A. Lampinen, “Differential evolution: a practical approach to global optimization,” in The Natural Computing Series, 1st ed., vol. 1. Berlin, Heidelberg: Springer, pp. XIX–539, 2006. [Google Scholar]
9. K. M. Passino, “Biomimicry of bacterial foraging for distributed optimization and control,” IEEE Control Systems Magazine, vol. 22, no. 3, pp. 52–67, 2002. [Google Scholar]
10. S. Lindsey and C. S. Raghavendra, “PEGASIS: Power-efficient gathering in sensor information systems,” in Proc. IEEE Aerospace Conf., Big Sky, MT, USA, pp. 3, 2002. [Google Scholar]
11. C. Intanagonwiwat, R. Govindan, D. Estrin, J. Heidemann and F. Silva, “Directed diffusion for wireless sensor networking,” IEEE/ACM Transactions on Networking, vol. 11, no. 1, pp. 2–16, 2003. [Google Scholar]
12. R. Hassan, B. Cohanim, O. De Weck and G. Venter, “A comparison of particle swarm optimization and the genetic algorithm,” in Proc. 46th AIAA/ASME/ASCE/AHS/ASC Structures, Structural Dynamics and Materials Conf., Austin, Texas, pp. 1897, 2005. [Google Scholar]
13. J. Hu, J. Luo, Y. Zheng and K. Li, “Graphene-grid deployment in energy harvesting cooperative wireless sensor networks for green IoT,” IEEE Transactions on Industrial Informatics, vol. 15, no. 3, pp. 1820–1829, 2018. [Google Scholar]
14. T. P. Hong and G. N. Shiu, “Allocating multiple base stations under general power consumption by the particle swarm optimization,” in Proc. 2007 IEEE Swarm Intelligence Symp., Honolulu, HI, USA, pp. 23–28, 2007. [Google Scholar]
15. L. M. Borges, F. J. Velez and A. S. Lebres, “Survey on the characterization and classification of wireless sensor network applications,” IEEE Communications Surveys & Tutorials, vol. 16, no. 4, pp. 1860–1890, 2014. [Google Scholar]
16. B. Dezfouli, M. Radi, S. Abd Razak, K. Whitehouse, K. A. Bakar et al., “Improving broadcast reliability for neighbor discovery, link estimation and collection tree construction in wireless sensor networks,” Computer Networks, vol. 62, pp. 101–121, 2014. [Google Scholar]
17. X. Wang, G. Xing, Y. Zhang, C. Lu, R. Plesset et al., “Integrated coverage and connectivity configuration in wireless sensor networks,” in Proc. the 1st Int. Conf. on Embedded Networked Sensor Systems, New York, NY, United States, pp. 28–39, 2003. [Google Scholar]
18. P. Medagliani, J. Leguay, G. Ferrari, V. Gay and M. Lopez-Ramos, “Energy-efficient mobile target detection in wireless sensor networks with random node deployment and partial coverage,” Pervasive and Mobile Computing, vol. 8, no. 3, pp. 429–447, 2012. [Google Scholar]
19. D. B. Johnson and D. A. Maltz, “Dynamic source routing in ad hoc wireless networks,” in Proc. Mobile Computing, Boston, MA, pp. 153–181, 1996. [Google Scholar]
20. R. C. Shah and J. M. Rabaey, “Energy-aware routing for low energy ad hoc sensor networks,” in 2002 IEEE Wireless Communications and Networking Conf. Record. WCNC 2002 (Cat. No. 02TH8609), vol. 1, pp. 350–355, 2002. [Google Scholar]
21. Y. Wang, P. M. Jodoin, F. Porikli, J. Konrad, Y. Benezeth et al., “CDnet 2014: An expanded change detection benchmark dataset,” in Proc. the IEEE Conf. on Computer Vision and Pattern Recognition Workshops, Sherbrooke, J1K 2R1, Canada Canberra ACT 2601, Australia 21078 Dijon, France Boston MA, 02215, USA, pp. 387–394, 2014. [Google Scholar]
22. J. Liono, Z. S. Abdallah, A. K. Qin and F. D. Salim, “Inferring transportation mode and human activity from mobile sensing in daily life,” in Proc. the 15th EAI Int. Conf. on Mobile and Ubiquitous Systems: Computing, Networking and Services, New York, NY, USA, pp. 342–351, 2020. [Google Scholar]
23. M. Al-Ma’aitah, A. Alwadain and A. Saad, “Transmission adaptive mode selection (TAMS) method for the internet of things device energy management,” Peer-to-Peer Networking and Applications, vol. 14, no. 4, pp. 2316–2326, 2021. [Google Scholar]
24. M. Alhussein and S. I. Haider, “Improved particle swarm optimization based on velocity clamping and particle penalization,” in Proc.2015 3rd Int. Conf. on Artificial Intelligence, Modelling and Simulation (AIMS), Kota Kinabalu, Malaysia, pp. 61–64, 2015. [Google Scholar]
25. J. Wang, M. Agrawala and M. F. Cohen, “Soft scissors: An interactive tool for real-time high-quality matting,” in Proc.ACM SIGGRAPH, 2007 Papers, New York, NY, United States, pp. 9-es, 2007. [Google Scholar]
26. T. V. Chithra and A. Milton, “Energy proficient flooding scheme using reduced coverage set algorithm for unreliable links,” Programming and Computer Software, vol. 44, no. 6, pp. 381–387, 2018. [Google Scholar]
27. A. Yadav, S. Kumar and S. Vijendra, “Network life time analysis of WSNs using particle swarm optimization,” Procedia Computer Science, vol. 132, no. 1, pp. 805–815, 2018. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools