 Open Access
Open Access
ARTICLE
Energy Efficient Unequal Fault Tolerance Clustering Approach
1 Department of Computer Science and Engineering, KG Reddy College of Engineering and Technology, Hyderabad, India
2 School of Computer Science and Engineering, Lovely Professional University, Phagwara, India
3 Department of Computer Science and Engineering, Chandigarh University, Mohali, India
4 Department of Computer Science and Engineering, Tailor’s University, Malaysia
5 Department of Computer Science, College of Computers and Information Technology, Taif University, Taif, 21944, Saudi Arabia
6 Department of Computer Engineering, College of Computer and Information Technology, Taif University, Taif, 21994, Saudi Arabia
* Corresponding Author: Kavita. Email:
Computer Systems Science and Engineering 2023, 45(2), 1971-1983. https://doi.org/10.32604/csse.2022.021924
Received 20 July 2021; Accepted 14 October 2021; Issue published 03 November 2022
Abstract
For achieving Energy-Efficiency in wireless sensor networks (WSNs), different schemes have been proposed which focuses only on reducing the energy consumption. A shortest path determines for the Base Station (BS), but fault tolerance and energy balancing gives equal importance for improving the network lifetime. For saving energy in WSNs, clustering is considered as one of the effective methods for Wireless Sensor Networks. Because of the excessive overload, more energy consumed by cluster heads (CHs) in a cluster based WSN to receive and aggregate the information from member sensor nodes and it leads to failure. For increasing the WSNs’ lifetime, the CHs selection has played a key role in energy consumption for sensor nodes. An Energy Efficient Unequal Fault Tolerant Clustering Approach (EEUFTC) is proposed for reducing the energy utilization through the intelligent methods like Particle Swarm Optimization (PSO). In this approach, an optimal Master Cluster Head (MCH)-Master data Aggregator (MDA), selection method is proposed which uses the fitness values and they evaluate based on the PSO for two optimal nodes in each cluster to act as Master Data Aggregator (MDA), and Master Cluster Head. The data from the cluster members collected by the chosen MCH exclusively and the MDA is used for collected data reception from MCH transmits to the BS. Thus, the MCH overhead reduces. During the heavy communication of data, overhead controls using the scheduling of Energy-Efficient Time Division Multiple Access(EE-TDMA). To describe the proposed method superiority based on various performance metrics, simulation and results are compared to the existing methods.Keywords
For collecting and processing of information from a target area and communication for a remote BS [1], the Wireless Sensor Networks (WSNs) contain the spatially distributed sensor nodes. The sensors available with lower costs and wireless sensor networks have included numerous applications in various fields like health, military, disaster management, and industry, etc. The limitation of power sources is the major restriction for WSNs [2]. In an unattended hostile environment, the battery-operated sensors have deployed, and the battery replacement is not possible that makes the constraint of energy for sensor nodes [3]. To improve a large scale WSNs, the major challenging issue is the energy consumption.
One of the efficient techniques is the clustering of sensor nodes that can incorporate energy consumption. The network categorizes into different groups in the clustering, known as clusters [4]. A leading node includes in each cluster known as cluster head, which gathers the local information from the sensor nodes in the clusters, aggregates it and sends it to a remote BS or other CHs. For notifying the public event, the public network like Internet relevant to the BS. Fig. 1, shows the cluster based WSN functionality. The benefits are provided with the clustering [5] such as improving network scalability, reduction of energy consumption by preventing the individual data transmission from each sensor node, and the communication bandwidth conserves due to communication with the CHs by nodes and the transmission of redundant messages can be restricted. For improving the network longevity, CHs have chosen in the clustering process because it affects the sensor node’s energy consumption. The main objective of a WSN has included the energy efficient data routing process [6]. But the CHs selection should be processed with proper care.
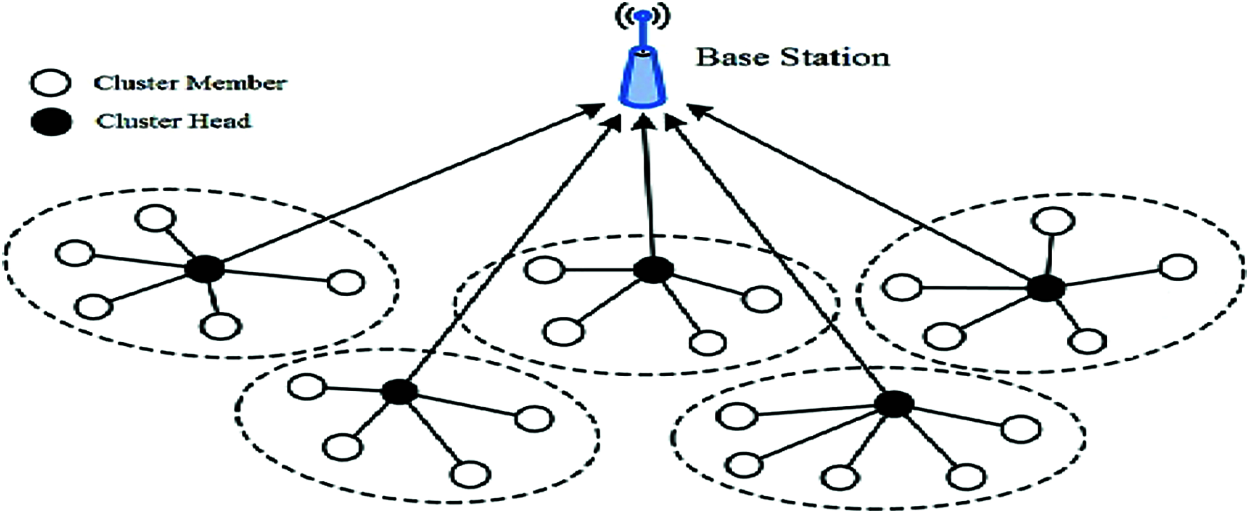
Figure 1: A cluster based WSN model
The selection of CH includes an NP-hard problem as optimization. With the increased size of a network, classical algorithms of optimization are not efficient. One of the efficient natural algorithms is the particle swarm optimization [7] which provides the resolutions for NP-hard problem as it has a high solution quality, easier implementation, quick convergence and ability to escape from the local optima.
We have focused on the issue of CH selection in the paper and a PSO based algorithm is presented. The MCHs choose efficiently among the sensor nodes using a proposed method. To choose the MCHs and Master Data Aggregators (MDAs), the algorithm of EEUFTC applies for the Particle Swarm Optimization algorithm is multi-objective fitness function for each cluster. The data accumulation from cluster members is performed using the chosen MCHs and the MDAs, transmit the aggregated data of MCHs. The node’s energy distribution has balanced and the earlier death of MCHs prevent using an energy threshold. If an MCH energy level is lower than the threshold, a new CH will be selected and frequent changes are reduced in the clusters. However, the energy is distributed over the network and the lifetime can be extended successively.
● The EEUFTC technique proposes for maximizing the lifetime of a network by creating the energy balanced optimal clusters.
● Based on the essential factors like average consumption of energy (ACE), neighbour density, distance between the sink and node, and the average energy of node (AE), the PSO-based multi-objective fitness function incorporates in EEUFTC to evaluate each sensor node’s fitness value.
● For reducing the MCH overhead, an MDA node is introduced for each cluster.
The important tasks of data collection from sensor nodes and data transmission to the BS is performed by the chosen MCHs and MDAs respectively.
The routing protocols of WSNs include different categories such as hierarchical, flat, and location-based routing protocols [8]. Based on the defined context, the proposed model [9] has dealt with the permission of dynamic enforcement for a specific application without intervention of a user. The profiles assigned to various applications using their functional groups in this model and a set of permissions contain in these profiles with some associated context.
The clustering protocol known as LEACH (Low-Energy Adaptive Clustering Hierarchy) proposes for improving the network lifetime [10]. CH with greater residual energy elects in EE-LEACH protocol and network lifetime enhances [11]. In [12], a lightweight and secure IoT-based framework is contributed as a technology for WSN. The proposed security method based on COOJA simulator is compared with the existing security solutions SIMON and SPECK.
One of the essential problems in designing is considered as the load balancing between minimization of energy consumption and maximizing the network lifetime as sensor nodes have restricted the consumption of energy. To overcome all these issues, various solutions are proposed in [13–16]. Based on max-hop count, a new mechanism of ad-hoc on-demand distance vector routing (AODV) is proposed by authors [17]. In the networks, the original AODV protocols is added the real-time and intelligent estimation function for getting the max hop data. The dynamic-adjusting AODV (DA-AODV) is used to estimate the max hop values and the parameters have adjusted dynamically and intelligently based on the max hop value for improving the performance of a network.
The Artificial Neural Network (ANN) is used for providing data security against dual attacks for BHA and GHA. By using the swarm-based Artificial Bee Colony (ABC) optimization method, it is implemented as a deep learning algorithm [18].
In [19], a technique is proposed for election-based mobile collection and results the optimization issue called as bounded relay hop mobile data gathering (BRH-MDG). The sensor node’s subgroup in a method will be labelled as polling points and transmit the collected data to the mobile collector.
In [20], the hybrid logical security framework- provides the data confidentiality and authentication in Internet of Things. A lightweight cryptographic mechanism is used by HLSF. The security level is enhanced and better network functionalities are provided based on the energy-efficient methods.
Liu [21] has proposed a novel clustering protocol known as IEE-LEACH for improving the network lifetime and reducing energy consumption of WSNs. Four different parameters are considered in the IEE-LEAH protocol such as average energy, total energy, residual energy and the initial energy of nodes. The number of CHs and distributions can optimize by the proposed technique that leads to the reduction of energy consumption. Instead of a single communication, the proposed technique incorporates the multi-hop, single-hop, and hybrid communications in data transmission. By analyzing the simulation results, the proposed protocol has showed better results in reliability and energy-efficiency than the existing methods.
Sood et al. [22] have proposed an energy-efficient routing protocol using fuzzy rules and fuzzy set to choose CHs and multi-hop routes are established for base station in wireless sensor networks. By comparing this with the earlier methods, such as FD-LEACH, OCM-FCM, and MH-EEBCDA, the proposed protocol has provided enhanced performance in network lifetime and throughput based on the simulation results.
To meet the stringent requirements, the underlying protocol is required for providing [23] interoperable and seamless communication in IoMT. It is a challenging problem that interoperability of multimedia sensors due to the heterogeneous nature. The existing protocol IoMT comprehensive review is provided and the feasibility is analyzed for multimedia streaming applications for understanding the challenges by interoperable and seamless communication in IoMT. The network energy conserved by hierarchical routing protocols [24].
The time and spatial-based traffic data details are exploited in the proposed scheme [25] and they are extracted based on LSTM and CNN networks for improving the accuracy of a model. The near term details are detected using the attention-based model and speed is very essential to predict the flow’s future value. The CHs are chosen by DB-LEACH which considers the distance from CHs to BS, based on two factors like node’s residual energy which is higher than the average residual energy and distance to BS, DB-LEACH improves with DBEA-LEACH [26].
In [27], a mixed or hybrid routing protocol is proposed for wireless sensor networks, which contains the mobile sinks. Multiple mobile sinks include for low-power networks, a combination of reactive and proactive routing protocols which are included in the routing protocol. In a certain zone that closer to the sink, the nodes maintain using DAG or directed acyclic graph. The on-demand sink can be used for discovering the sink at the nearest possible distance when the nodes do not utilize DAG outside the zone. It is useful for creating small zones in case of repeated modifications involved in the high sink mobility path to sink. For transmission of data to the sink node, the bigger zones can create if the mobility is slow.
In [28], a comprehensive review is presented on the machine learning methods for big data analysis in the healthcare. The existing methods benefits, and drawbacks are highlighted by different research challenges.
In [29], Position Responsive Routing Protocol performs well compared to LEACH protocol in the context of network lifetime, throughput and energy consumption of the network. In clustering techniques, [30] if it is focussed on reducing energy consumption and improving the load balancing then it leads to solve Intra and inter cluster challenges.
Particle swarm optimization is designed by inspiring from the flock of birds choreography including how they utilize the multi-dimensional search space for food and shelter and it is a natural swarm intelligence based algorithm.
A predefined number of particles Np contain in the PSO, termed as a swarm. An optimal solution provides by each particle Pi, 1≤ i ≤ Np that has position Xi,d and velocity Vi,d, 1≤ d ≤ D in the search space with dth dimension. All particles have same dimensions D. To validate the solution quality, each particle evaluates using a fitness function. The positions of particle determine using PSO that evaluates the given fitness function effectively. Each particle allocates randomly and velocity for moving the search space in the PSO initialization process. The best values are determined by each particle like the best global value called Gbest and personal best called Pbest while processing each iteration. To update the position Xi,d and velocity Vi,d, the technique utilizes the global and personal best values to obtain the global best solution based on below-mentioned Eqs. (1) and (2):
where, C1, C2, 0 ≤ C1, C2 ≤ 2 represent the acceleration coefficients, w, 0<w<1 indicates the inertia weight, and x1, x2, 0 < x1, x2< 1 indicate the generated random values. The process of updating repeats up to achieving Gbest acceptable value. The fitness function evaluates by the particle after reaching the new updated position. For the minimization problem, Pbesti and Gbest values update as follows:
EEUFTC technique aims to improve the network lifespan by creating the energy-balanced unequal fault tolerant clusters. Two different phases involve in the EEUFTC method such as TDMA based data aggregation and PSO based optimum node selection. To determine which node can act as a MCH optimally, the BS deploys the PSO in the phase of optimum node selection. For computing each node’s fitness value, the PSO algorithm utilizes the sensor node’s parameters like average consumption of energy (ACE), distance between the node to the sink, residual energy, average energy and neighbour density. A node with the higher fitness value adopts as a MCH. The next higher fitness value selects as a MDA that include in a node which is in the region of any MCH. After a CH is selected, EEUFTC uses the TDMA to schedule the data transmission by assigning time slots to the individual sensor nodes. Based on the assigned time slots, the cluster member nodes send the data to their respective MCHs. Further, the MDA aggregates the data from each MCHs and transmit the aggregated data to BS.
3.3 PSO Based Optimal Nodes Selection
The BS needs to understand the context of sensor nodes as they are located randomly in the network area. A request message transmits to all nodes. Accordingly, a reply message formulates by each sensor node that encompasses the information about ACE, residual energy, distance between node to the sink, AE, and neighbour density. For MDAs and MCHs, the node’s fitness value determines using this data and the PSO algorithm that applies to the BS. The below-mentioned crucial factors are used for computing each node’s fitness value and the fitness function is derived as follows:
The combination of different performance metrics is involved in the fitness function for expressing to be either minimized or maximized. Different fitness parameters are considered to evaluate the fitness function that decides the current individual’s fitness. The fitness functions reduce the consumption of energy that renders to the network longevity. While evaluating the fitness function, the following parameters are considered for the selection of MDAs and MCHs optimally in the network. In the fitness function, the fitness parameters incorporate and is described as follows:
Based on the average energy ratio and the dissimilarity among the CH energy expenditure, each node’s energy (e) can derive. The node that has maximum energy is to be chosen as MCH as the heterogeneous network is considered. The ratio of the residual energy to the total energy considered in the residual energy and it can compute using below Eq. (3).
ER(i) represents the sum of residual energy of ith node ratio, ET denotes the total energy for evaluating RE, and N indicates the total number of nodes.
To choose the MCH, another factor is considered i.e., a node’s average energy as the network featuring heterogeneous nature. The nodes with high initial energy prefer to select the MCH. Compared to the advanced nodes, super nodes endure for longer duration and advanced nodes prefer over the normal nodes. Using below Eq. (4), it can formulate:
where, N is the total number of nodes and Ei indicates the ith node’s energy.
Based on the distance, the energy consumption of a node if communication of nodes is done among themselves or with the sink. The node consumes low energy when distance is lower between sink and node. The below equation is minimized the average distance between nodes and sink using the CH selection or routing techniques.
where, (xbs, ybs) refers to the positions of BS and (xi, yi) represents the ith node’s positions x and y respectively.
The intra cluster communication has become a dominant one if the network size is large. The node can select as MCH which locates distance away with respect to other nodes, if it is not relied on the number of neighbouring nodes. To collect the data from other nodes in a cluster, higher energy is consumed by the MCH node. The number of neighbouring nodes consider to limit such selection. The parameter can be expressed using below Eq. (6):
where, CN represents the number of nodes in a cluster and Distance(i−j) indicates the distance between node i and j in the cluster.
3.4.5 Average Consumption of Energy (ACE)
The energy consumption rate of a node depends on a significant factor of ACE which considers to select the MCH. After initial round, the difference between the remaining energy and initial energy of node is computed. The node’s energy in the previous round has become the initial energy as the number of rounds proceeded. ACE evaluates and compares based on the average value of threshold. The node is to being MCH when the computed value is lower compared to the average value of threshold. Otherwise, it doesn’t qualify to be MCH for that round using the following Eq. (7):
where, Ep indicates the node’s energy value in the previous round, and EEC represents the consumed energy in the current round.
3.5 Final Fitness Function for the Network
Different fitness parameters integrate altogether to evaluate the fitness function that can formulate using below Eq. (8):
where, the weight coefficients are σ, α, γ, δ, and φ and σ + α + γ + δ + φ = 1.
3.6 EE-TDMA Based Data Aggregation Approach
The collisions prevent which are caused through the individual time slots for every node using the conventional TDMA-based MAC protocols. Since all nodes are in sleeping mode excluding the transmitting node, the energy consumption reduces using this scheme. The sensed information is sent to the cluster head by using the nodes in a cluster in the respective time slot. During the scheduled time, nodes with empty buffers turns the radio on and the MCH always on the radio for listening to the nodes in a cluster that leads to the energy wastage. Better performance is achieved with TDMA under high traffic load conditions. The transmission data have included in all nodes that refers to the high traffic load. The application that contains higher traffic load, conventional TDMA is the suitable one. Sensor networks involve fewer nodes in a cluster that do not have information for transmitting to the MCH in the assigned time slots. Some of the remaining energy consumed by the nodes that have empty buffers turn on the radio. For collection of data from the nodes, the MCH has required to be in the radio on state. As the energy wastes in the idle time, the CH is not able to utilize the energy with efficiency. Due to idle listening, the energy consumption reduces using the energy-efficient TDMA (EE-TDMA). If the data is not transmitted, sensor nodes can keep the radios in off state. During all timeslots, energy is consumed by MCH. The EE-TDMA protocol illustrates using the operation diagram as shown in Fig. 2.
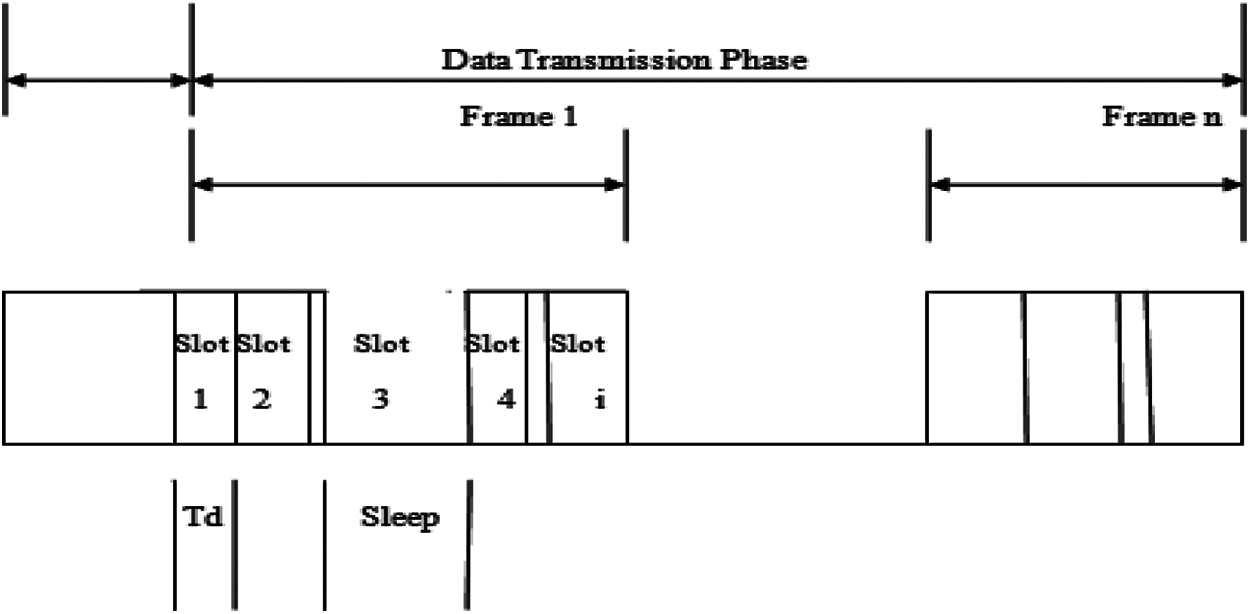
Figure 2: EE-TDMA operational diagram
A TDMA schedule established by the MCH and transmit the schedule to all nodes in the cluster in the setup phase. CH provides the information about all nodes including number of frames in a round, frame start or stop time and the start of current node. The phase of data transmission includes l frame and fixing the duration and size of each frame.
During the assigned time slots, nodes send the data to the MCH per frame. We make an assumption that n non-CH node and one MCH node exists in a cluster. The radio turns on by each node in the allocated time-slot during the data transmission and it sends to the MCH. The node turns off the radio immediately if data transmission is not there for energy saving after turning on the radio using any node to find an empty buffer. In the absence of information, sleep mode enabled by the nodes rather than the idle mode. The sensed data transmits to the buffer of MCH by non-CH nodes and aggregates the data after receiving it from the nodes. The information from MCHs would be collected by MDA and shared to BS in the assigned time slot The following Fig. 3 shows the brief explanation of proposed system.
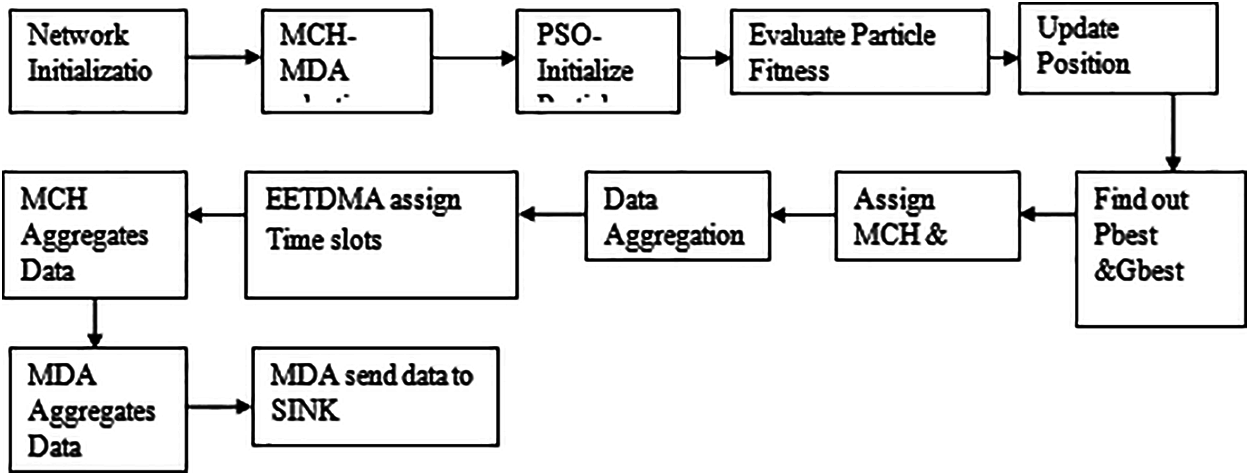
Figure 3: Block diagram of proposed system
3.7 Pseudo Code of Proposed System - PSO Based CH Selection
Set of sensor nodes S = {
fitness(p)=fitness of the Particle p;
Pbest(i)=particle best of i
Gbest = global best of all particles
NP = number of particles
##
Initialize particles Pi
For all i = 1 to Pi do
Calculate fitness(Pi)
Pbest(i) = Pi
End for
Gbest = { fitness(Pbestk) = best(Pbest(i)) }
While max iterations
For i = 0 to NP
Update velocity and position of Pi using (100) & (101)
Calculate fitness(Pi)
If (fitness(Pi) < fitness(Pbesti)
Pbest(i) = Pi
End if
If (fitness(Pi) < fitness(Gbest)
Gbest = Pi
End if
End for
End while
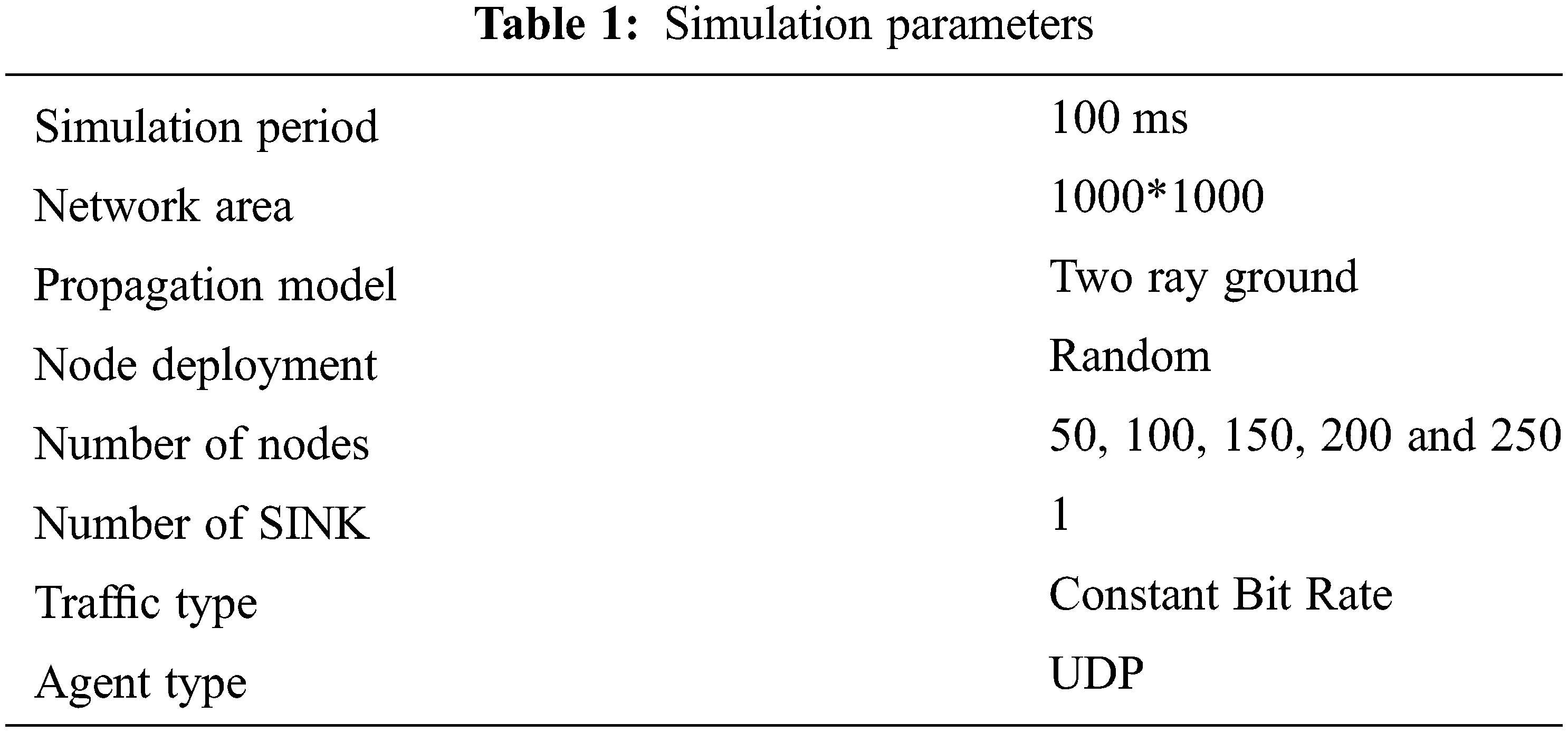
The proposed method has compared with two existing schemes such as EEFRP and IEE-LEACH. Based on static sensor nodes and plane co-ordinates, simulation tests are performed. Here, the initial energy of 100j configure for the nodes and CBR utilize as the traffic agent. At the central location of network area, the SINK locates. The simulation results are compared using different metrics like throughput, end-to-end delay, energy consumption, overhead, and packet delivery ratio. Tab. 1 shows the simulation parameters.
The end-to-end delay is calculated based on the time difference between the two consecutive packets to reach the destination. As the clustering is popular for efficient data aggregator and fault tolerance, we have implemented the technique and reduce the delay in the network. With the help of this approach, the network experiences the delay as low as 0.08 ms and the highest delay experiences in the proposed method was 0.2 ms, whereas the existing methods experience much higher delay than these. The lowest delay recorded in the EEFRP was 0.09 ms and in IEE-LEACH was 0.13 ms respectively. The evaluation values are shown in Tab. 2.
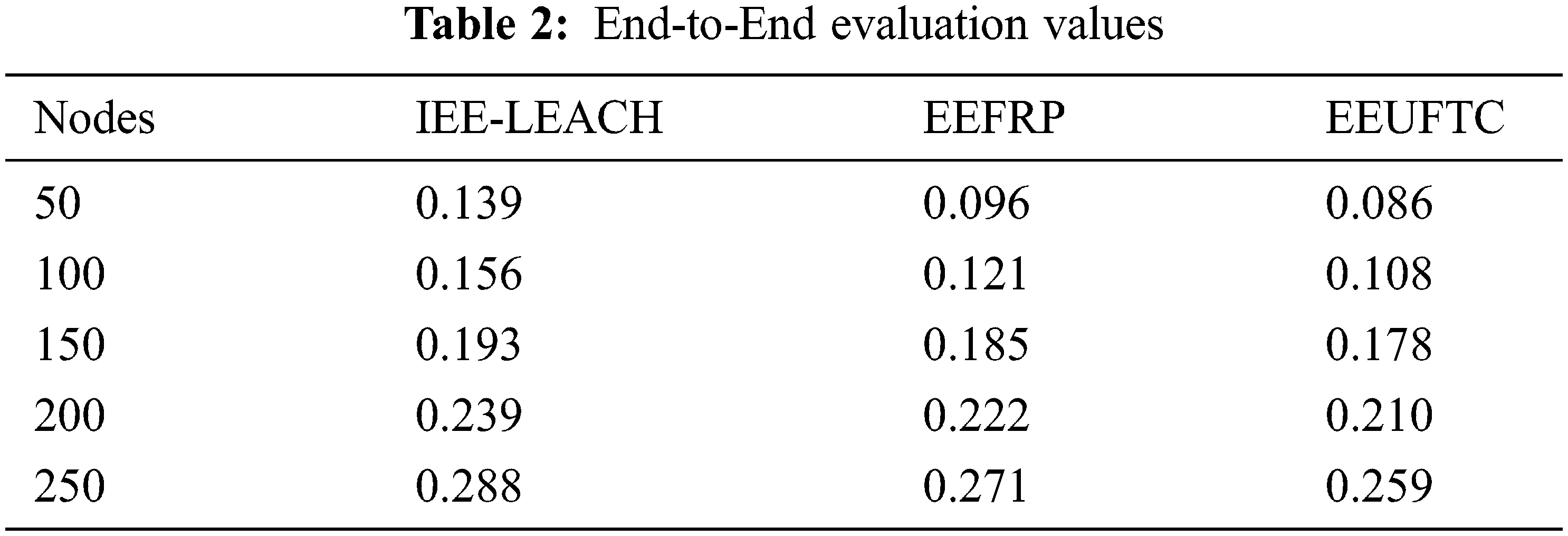
The wireless sensor network has considered the efficient energy consumption if the network is in proper condition. The existing methods recorded maximum energy consumption in the simulation evaluation. The main reason for decreased energy consumption under the proposed method is the consideration of node energy, distance, neighbour density & average consumption of energy. Also, the energy efficient TDMA scheduling helps a lot to decrease the consumption by optimally scheduling the data transmission on the different time slots. The evaluation results are listed in Tab. 3.

The routing overhead parameter is related to the amount of control packets required for networking tasks. The excess usage of the control packets increases the network overhead. Data loss, frequent path change, improper data collection affects the transmission and increase the overhead. In the evaluation, the proposed method recorded is only 0.5 as an average overhead whereas the existing methods were recorded almost 0.65 as routing overhead. The main reason for the minimum overhead is the proper data aggregation using data aggregators and CHs is also the effective usage of energy TDMA. The evaluation details are listed in Tab. 4.
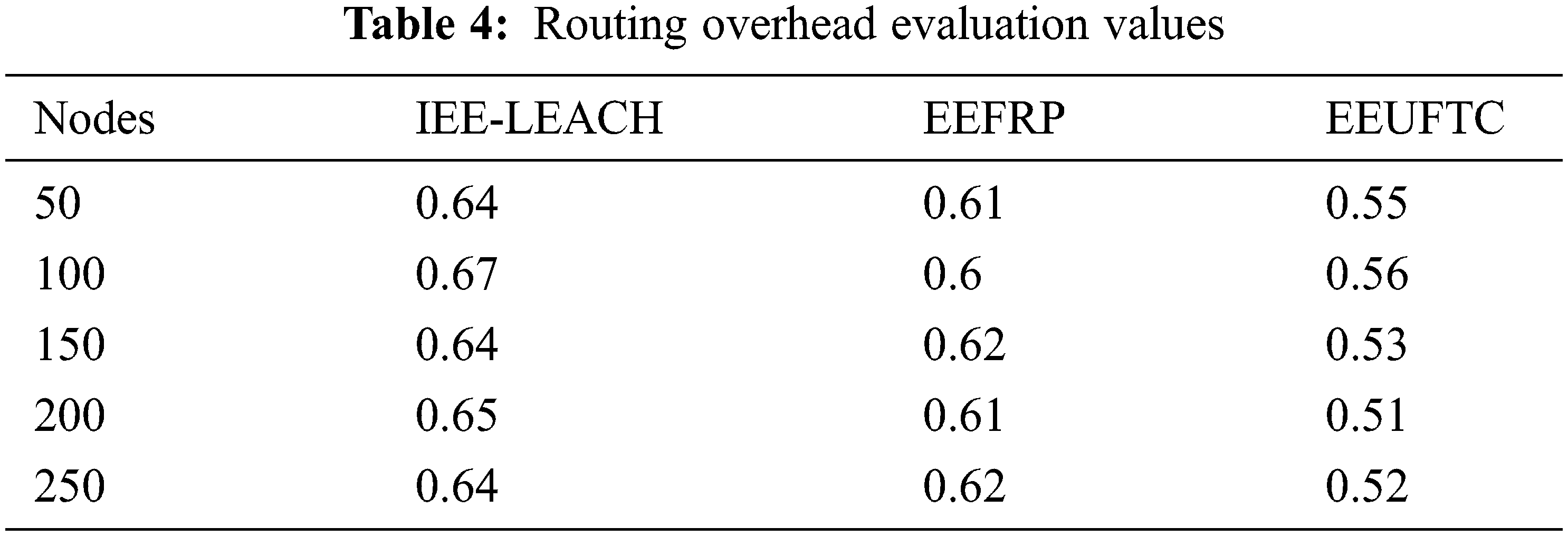
PDR can describe as the ratio between total number of received packets to the total number of transmitted packets. The main reason is the effective use of data aggregators and the energy efficient TDMA scheduling. The data scheduling takes place on the allotted time slots and the chances for data congestion is very less. Effective network clustering and CH selection also plays a major role to increase the delivery rate. In the evaluation, the proposed method recorded almost 0.94% delivery ratio. The evaluation results are listed in Tab. 5.

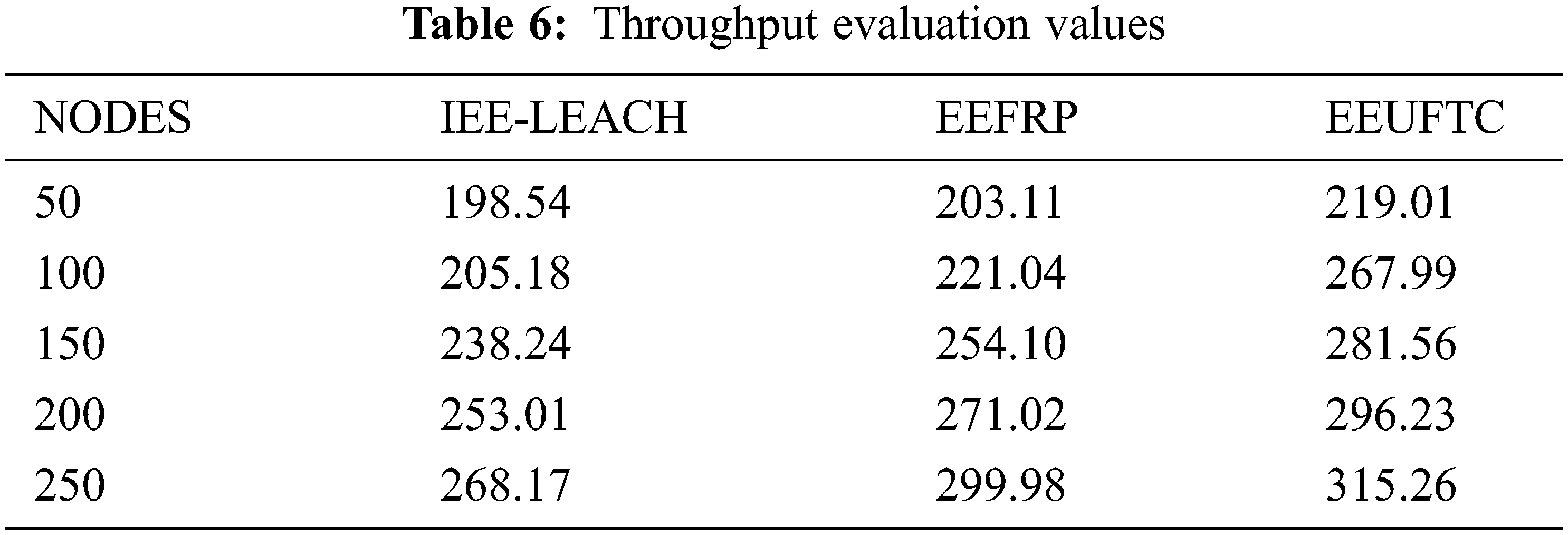
The parameter throughput can be defined as how much information can be transmitted from source to destination in a certain time-frame. It is measured as kilobits per second. In the evaluation, the proposed method has recorded almost 315 kilobits per second of throughput whereas the maximum throughput of existing IEE-LEACH & EEFRP recorded as 268 & 290 kbps respectively. The major reason behind the high throughput rate in the proposed method is the effective usage of the energy efficient TDMA and its effective data scheduling strategy. The proposed technique is outperformed than the previous methods based on these evaluation results. The throughput evaluation results are shown in Tab. 6.
Based on the Particle Swarm Optimization, using fitness function, efficient particle representation, an energy efficient clustering ,MCH and MDA selection algorithm i.e., EEUFTC is presented. To achieve energy efficiency, we consider the node residual energy, the Average energy of the node (AE), the distance between the node to the sink, neighbour density, and average consumption of energy (ACE). Energy efficient TDMA (EE-TDMA) is incorporated from inter & intra cluster data aggregation. The sensor nodes are assigned with time slots to communicate. If the sensor node has no data in its queue, then it can switch its transmitter off and being in idle state until it has data to send. The simulation results of proposed algorithm and the comparison of other existing algorithms called EEFRP and IEE-LEACH have been analysed. The better performance has resulted with the proposed technique in network lifetime. The number of received data packets by the BS and energy consumption than the previous methods. In further work, we can provide security on user data to transmit from nodes to base station.
Funding Statement: The authors would like to thank for the support from Taif University Researchers Supporting Project number (TURSP-2020/239), Taif University, Taif, Saudi Arabia.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. D. Bandur, B. Jakšić, M. Banđur and S. Jović, “An analysis of energy efficiency in wireless sensor networks applied in smart agriculture,” Computers and Electronics in Agriculture, vol. 156, pp. 500–507, 2019. [Google Scholar]
2. N. Muhammad, F. Subhan, W. Z. Khan, S. Hakak, S. Haider et al., “A systematic review on clone node detection in static wireless sensor networks,” IEEE Access, vol. 8, pp. 65450–65461, 2020. [Google Scholar]
3. T. N. Gia, V. K. Sarker, I. Tcarenko, A. M. Rahmani, T. Westerlund et al., “Energy efficient wearable sensor node for iot-based fall detection systems,” Microprocessors and Microsystems, vol. 56, pp. 34–46, 2018. [Google Scholar]
4. T. Khan, K. Singh, L. H. Son, M. Abdel-Basset, H. V. Long et al., “A novel and comprehensive trust estimation clustering based approach for large scale wireless sensor networks,” IEEE Access, vol. 7, pp. 58221–58240, 2019. [Google Scholar]
5. P. C. S. Rao, P. K. Jana and H. Banka, “A particle swarm optimization based energy efficient cluster head selection algorithm for wireless sensor networks,” Wireless Networks, vol. 23, no. 7, pp. 2005–2020, 2017. [Google Scholar]
6. A. Shankar and N. Jaisankar, “Base station positioning in wireless sensor network to aid cluster head selection process,” International Journal of Intelligent Engineering and Systems, vol. 10, no. 2, pp. 173–182, 2017. [Google Scholar]
7. B. Chopard and M. Tomassini, “Particle swarm optimization. in: An introduction to meta heuristics for optimization,” in Natural Computing Series, 1st ed., vol. 6, Springer Nature Switzerland, Cham, pp. 97–102, 2018. [Google Scholar]
8. H. Aetesam and I. Snigdh, “A comparative analysis of flat, hierarchical and location-based routing in wireless sensor networks,” Wireless Personal Communications, vol. 97, no. 4, pp. 5201–5211, 2017. [Google Scholar]
9. S. Kumar, R. Shankar and S. Verma, “A research paper on context aware dynamic permission model: A retrospect of privacy and security in android system,” in 2018 Int. Conf. on Intelligent Circuits and Systems, IEEE Xplore, Phagwara, India, pp. 324–329, 2018. [Google Scholar]
10. W. R. Heinzelman, A. Chandrakasan and H. Balakrishnan, “Energy-efficient communication protocol for wireless micro sensor networks,” in Proc. of the 33rd Annual Hawaii Int. Conf. on System Sciences, Maui, HI, USA, pp. 1–10, 2000. [Google Scholar]
11. G. S. Arumugam and T. Ponnuchamy, “EE-LEACH: Development of energy-efficient leach protocol for data gathering in wsn,” EURASIP Journal on Wireless Communications and Networking, vol. 7, no. 1, pp. 1–9, 2015. [Google Scholar]
12. L. Gaur, G. Singh, A. Solanki, N. Z. Jhanjhi, U. Bhatia et al.., “Disposition of youth in predicting sustainable development goals using the neuro-fuzzy and random forest algorithms,” Human-centric Computing and Information Sciences, vol. 11, 2021. [Google Scholar]
13. M. Yin, J. Chen, X. Duan, B. Jiao, Y. Lei et al., “Qebr: Q-learning based routing protocol for energy balance in wireless mesh networks,” in 2018 IEEE 4th Int. Conf. on Computer and Communications (ICCC), Dorsett Grand Chengdu, China, pp. 280–284, 2018. [Google Scholar]
14. P. L. Nguyen, Y. Ji, K. Le and T. H. Nguyen, “Load balanced and constant stretch routing in the vicinity of holes in WSNs,” in 2018 15th IEEE Annual Consumer Communications & Networking Conference (CCNC), Las Vegas, USA, pp. 1–6, 2018. [Google Scholar]
15. Z. Lv, L. Qiao, S. Verma, Kavita, “AI-Enabled IoT-edge data analytics for connected living,” ACM Trans. Internet Technol, vol. 21, pp. 1–20, 2021. [Google Scholar]
16. G. Sun, Y. Liu, S. Liang, Z. Chen, A. Wang et al., “A side lobe and energy optimization array node selection algorithm for collaborative beam forming in wireless sensor networks,” IEEE Access, vol. 6, pp. 2515–2530, 2017. [Google Scholar]
17. X. Zhang, Z. H. Qian, Y. Q. Guo and X. Wang, “An efficient hop count routing protocol for wireless adhoc networks,” International Journal of Automation and Computing, vol. 11, no. 1, pp. 93–99, 2014. [Google Scholar]
18. P. Rani, Kavita, S. Verma, and N. G. Nguyena, “Mitigation of black hole and gray hole attack using swarm inspired algorithm with artificial neural network,” IEEE Access, vol. 8, pp. 121755–121764, 2020. [Google Scholar]
19. M. S. Vidhya, V. Subhashini, N. V. Banu, A. Vaishnavi, M. Jayachithra et al., “Localisation algorithm based efficient controlled sink mobility for wireless sensor network,” International Journal of Electrical Engineering and Telecommunications, vol. 1, no. 1, pp. 82–89, 2015. [Google Scholar]
20. M. Kumar, P. Mukherjee, K. Verma, S. Verma, D. B. Rawat, “Improved deep convolutional neural network based malicious node detection and energy-efficient data transmission in wireless sensor networks,” IEEE Transactions on Network Science and Engineering. DOI: 10.1109/TNSE.2021.3098011. [Google Scholar] [CrossRef]
21. Y. Liu, Q. Wu, T. Zhao, Y. Tie, F. Bai et al., “An improved energy-efficient routing protocol for wireless sensor networks,” Sensors, vol. 19, no. 20, pp. 4579, 2019. [Google Scholar]
22. M. Sood, S. Verma, V. K. Panchal, Kavita, “Optimal path planning using swarm intelligence based hybrid techniques,” Journal of Computational and Theoretical Nanoscience, vol. 16, no. 9, pp. 3717–3727, 2019. [Google Scholar]
23. G. Yang, M. A. Jan, A. U. Rehman, M. Babar, M. M. Aimal et al., “Interoperability and data storage in internet of multimedia things: Investigating current trends, research challenges and future directions,” IEEE Access, vol. 8, pp. 124382–124401, 2020. [Google Scholar]
24. X. Xing Ding, M. Ling, Z. J. Wang and F. Lou Song, “DK-LEACH: An optimized cluster structure routing method based on leach in wireless sensor networks,” Wireless Personal Communications, vol. 96, no. 4, pp. 6369–6379, 2017. [Google Scholar]
25. B. Vijayalakshmi, K. Ramar, N. Z. Jhanjhi, S. Verma, M. Kaliappan et al., “An attention based deep learning model for traffic flow prediction using spatio temporal features towards sustainable smart city,” International Journal of Communication Systems, Wiley, vol. 34, pp. 1–14, 2020. [Google Scholar]
26. M. C. Mon Thein and T. Thein, “An energy efficient cluster-head selection for wireless sensor networks,” in 2010 Int. Conf. on Intelligent Systems, Modelling and Simulation, Liverpool, United Kingdom, pp. 287–291, 2010. [Google Scholar]
27. F. El-Moukaddem, E. Torng and G. Xing, “Mobile relay configuration in data-intensive wireless sensor networks,” IEEE Transactions on Mobile Computing, vol. 12, no. 2, pp. 261–273, 2013. [Google Scholar]
28. W. Li, Y. Chai, F. Khan, S. R. Ullah Jan, S. Verma et al., “A comprehensive survey on machine learning-based big data analytics for iot-enabled smart healthcare system,” Mobile Networks and Applications, Springer, vol. 26, pp. 234–252, 2021. [Google Scholar]
29. N. Zaman, L. T. Jung and M. M. Yasin, “Retracted: Enhancing energy efficiency of wireless sensor network through the design of energy efficient routing protocol,” Journal of Sensors, vol. 2019, Article ID 3486036, pp. 1, 2019. [Google Scholar]
30. A. Shahraki, A. Taherkordi, Ø. Haugen and F. Eliassen, “Clustering objectives in wireless sensor networks: A survey and research direction analysis,” Computer Networks, vol. 180, pp. 107376, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools