 Open Access
Open Access
ARTICLE
A Multi-Stage Secure IoT Authentication Protocol
1 College of Computing and Informatics, Saudi Electronic University, Riyadh, 11673, Saudi Arabia
2 King Abdullah II School for Information Technology, The University of Jordan, Amman, 11942, Jordan
* Corresponding Author: Marwah Almasri. Email:
Computer Systems Science and Engineering 2023, 45(1), 459-481. https://doi.org/10.32604/csse.2023.028536
Received 12 February 2022; Accepted 19 April 2022; Issue published 16 August 2022
Abstract
The Internet of Things (IoT) is a network of heterogeneous and smart devices that can make decisions without human intervention. It can connect millions of devices across the universe. Their ability to collect information, perform analysis, and even come to meaningful conclusions without human capital intervention matters. Such circumstances require stringent security measures and, in particular, the extent of authentication. Systems applied in the IoT paradigm point out high-interest levels since enormous damage will occur if a malicious, wrongly authenticated device finds its way into the IoT system. This research provides a clear and updated view of the trends in the IoT authentication area. Among the issues covered include a series of authentication protocols that have remained research gaps in various studies. This study applies a comparative evaluation of authentication protocols, including their strengths and weaknesses. Thus, it forms the foundation in the IoT authentication field of study. In that direction, a multi authentication architecture that involves secured means is proposed for protocol authentication. Informal analysis can affect the security of the protocols. Burrows-Abadi-Needham (BAN) logic provides proof of the attainment of mutual authentication. NS3 simulator tool is used to compare the performance of the proposed protocol to verify the formal security offered by the BAN logic.Keywords
Internet of Things (IoT) is one of the fast-growing technologies with intelligent features that use resources efficiently [1–4]. It combines physical objects with Internet connectivity for forming cyber-physical networks. Smart devices have a vital role in applications of IoT in the healthcare field as medical tools with IoT characteristics can perform several functionalities through their basic abilities, like sensing to collect information associated with health, process, and communication [5]. IoT permits sensing or controlling objects remotely through the present network infrastructure, generating opportunities to integrate the physical world into computerized systems directly, enhancing efficiency, improving accuracy, and achieving economic advantages with decreased human intervention [6–8].
The unique features of IoT depend on whether sensors are used or not. Sensors convert IoT from a standard network of passive devices into a more active network that can be integrated with the real world. An ecosystem consisting of constantly connected devices over the networks is created by IoT [9,10]. The system provides less control, regardless of any security measures; this leads to several attacker types being exposed to users. Due to the rapid introduction of IoT in the market and millions of IoT devices, security and other services are still challenges [11–14].
There are numerous threats to IoT security [15,16]. The main challenges include user privacy, confidentiality in business, and third-person trust. In addition to existing issues in other networks, IoT faces both passive and active attacks, which can easily interrupt its operation and decrease IoT's advantages and services. Attacks in passive mode can recover data from the network, and its behavior is unaffected. Attacks in active mode directly block the provided services [17,18]. Further, these threats can be broadly classified as either external threats originating from outside the network or internal threats generated from inside the network. Internal threats have access to confidential and valuable data accessible to services, making them more dangerous than external threats.
Various attacks in IoT are categorized based on attack vulnerabilities utilized in compromising the network [19–21]. Attacks can be classified based on the chances of being detected and how they influence the network. Attacks in the network can be classified as physical attacks, network attacks, software attacks, and encryption attacks.
A physical attack, which uses injected malicious nodes, was the most dangerous attack because it modifies the information and stops the services. In a network attack, a high-risk attack is the attack of a sinkhole [22]. This type of attack attracts the entire traffic to the base station and also initiates additional threats like chosen forwarding, modification, or packet dropping. A worm attack is a dangerous attack from the types of software attack since they can be the more destructive and unsafe format of the malware on the Internet [23]. A worm is a program that generates copies of itself to affect computers by utilizing security holes present in the software and hardware of networks. Also, system files can be erased, some data such as passwords can be robbed, passwords can be altered to become unknown to the user and further cause computer interruptions. Encryption attacks are the most difficult to handle. They occur through the usage of side-channel to make their detection difficult.
Other attacks include Man-in-the-middle attack, Denial of Service (DoS) attack, password guessing in the offline attack, impersonation of user attack, and the smart card is stolen attack [24]. A man-in-the-Middle attack interrupts communication among two nodes. They acquire sensitive information through eavesdropping. When a similar attack occurs on an encrypted line, the attacker interrupts the communication when keys are interchanged and acquires the key.
In a DoS attack, significant traffic floods the networks to stop its services from reaching the intended users [25]. When this attack takes place on the software side, the attacker restricts a user from an application layer by rejecting services. Since IoT networks have a similar architecture to a traditional network in the way devices are connected, imperfections of the traditional architecture of the network have been inherited in an IoT architecture.
Researchers proposed many solutions for handling the above attacks. Applying all available security measures and methods consumes computational power on devices, which is intolerable for IoT technology and their devices with limited resources. Security mechanisms are required for handling extreme security issues. At the same time, they must be lightweight and robust to fit IoT characteristics. Some IoT attacks can be eliminated by placing a few security precautions when the application is developed. Some attacks are challenging to detect or prevent. A secure and efficient solution is required [26].
IoT is applied in the healthcare field. A precise understanding of human anatomy permits healthcare experts to handle emergencies. Patient monitoring remotely by healthcare experts or doctors using Wireless Sensor Network (WSN) provides a solution for the shortage issues [5]. To monitor remotely with WSN, termed as Wireless Body Area Network (WBAN) or Wireless Medical Sensor Network (WMSN), uses several sensors that gather data from the human body that is later sent to a central device to process and store. WSN applications in healthcare can be divided into monitoring patients and monitoring by care centers for long-term databases [27].
Many limitations exist in WSN because sensor nodes are limited in power, storage, and process. That needs appropriate management of resources, especially in insecure communication in the wireless mode because of the lack of infrastructure [12,15]. Compromise of sensor nodes is carried out at ease due to: its heterogeneous nature and frequent change in topology because of failure in nodes, merging, and mobility.
The desired security characteristics include authentication, privacy, integrity, anti-playback, and non-repudiation. A large volume of data is transmitted over the network channels; this presents a high risk. Consequently, many cryptographic approaches, steganography methods, and additional techniques are widely used [17]. Security and authentication are the major issues facing IoT and wireless networks, and these requirements are the focus of this paper. A multi authentication architecture is proposed in this paper.
The proposed multi authentication architecture involves a secured means for protocol authentication. It can prevent IoT cyberattacks and data breaches by adding an extra layer of authentication.
The proposed Multi authentication architecture uses five steps: Initialization, user and sensor registration, login, authentication, and password renewal. The initialization phase describes the system setup. The registration phase involves sensor registration and user registration phases. The login phase explains how the authenticated user can access the sensor using the terminal's user ID, password, and biometric recognition. The authentication phase describes two authentication models; the first model will be selected if the Database has the sensor index number; if not, it will choose the second model. The password renewal phase describes how the user can renew the password. It is the only way, even if the user forgets the password and knows the rest of the authentication details, still, the user cannot access the secured gateway.
The rest of this paper is organized as follows: Section 2 reviews the relevant literature and methods related to the secure authentication protocols in IoT. Section 3 describes the proposed multi-authentication method architecture. The performance of the proposed method is analyzed in Section 4 by several metrics and compared with other existing methods using the NS3 simulation tool. Finally, Section 5 provides the conclusions and possible avenues for future work.
Body Sensor Networks (BSN) framework is applied through the IoT-based healthcare system to operate securely [28]. To ensure confidentiality in transmitting data and authentication of entities provided to smart objects, a backend BSN server, a local processing unit, and two communication processes are created by robust crypto primitives. The IoT-based healthcare system and its communication through the BSN servers help to achieve efficiency and robustness in transmission. A Raspberry PI platform was implemented on this proposed healthcare system and highlighted the feasibility and practicability. When crypto-hash modules replaced the traditional SHA-2 methods, acceptable computational cost and improved efficiency were achieved. From the results, the proposed method guaranteed practicability and robustness.
Yeh [29] developed an IoT healthcare system to focus on unbiased decision-making. Patient health parameters monitoring based on healthcare system using core IoT technologies such as BSN-based tiny and lightweight wireless sensor nodes. This proposed method is used in the healthcare system for strokes and coronary heart disease. This study is helpful to monitor the pulse rate, and its differentiation and panic situation has been alerted. This method is sensitive and could reduce the loss of lives.
In [30], the authors proposed a unique method for authenticating the exchange of information in WSN distinct from earlier existing authentication research for resisting attacks by capturing nodes in the network. The objective was to add an authentication scheme to exchange information in the earlier authentication method but does not offer a new approach. This method was developed with associated ideas of Home Gateway Node (HGWN) and other native sensor nodes. The home gateway network contacts every native sensor node and performs the authentication process to exchange information to resist security threats. The mechanism with dynamic contact was designed to prevent an attacker from predicting the period of communication between the sensor and the HGWN. Validation was done in three ways with detailed explanations of the offered scheme: security evaluation, BAN logic, and overall performance. These evaluations proved that the proposed authentication scheme for exchanging information could attain features of security and its goals. Though few benefits were offered, practical implementation was not performed to transfer data with novel security authentication to the sensor. Thus, this proposed scheme provided a new way to design a better scheme to enhance the original key agreement and authentication protocol.
Another study offered a novel and enhanced scheme for user authentication and the key agreement protocol for the heterogeneous WSN [31]. This scheme was designed for the IoT environment and was reliant on a proposed unique method of Turkanovic. Whereas the novelty of both the offered approach and Turkanovic were related to the primary authentication model of sensor node of four steps, all registered users in IoT contact directly with sensor node from WSN that does not get involved with the Gateway Node (GWN). By cryptanalysis of the existing method, certain shortcomings were identified based on security, which was vulnerable to many cryptographic attacks. The existing protection scheme of traceability and privacy of sensor nodes was not offered. Also, the method was exposed to attacks by breaching smart cards, impersonation attacks of sensor nodes, and man-in-the-middle attacks.
Further, the method tackled and eliminated all shortcomings of security and the susceptibilities of the existing method to preserve the novel framework and its functionalities. The method was analyzed using BAN logic and utilized a simulation tool, Automated Validation of Internet Security-sensitive Protocols and Applications (AVISPA), to automatically analyze the security of the cryptographic protocols; it assured the specified security of the proposed protocol. The performance results show that the proposed scheme consumed less storage and enabled unlimited and dynamic network growth without disturbing registration or the authentication functionality for sensor and user nodes.
The authors in [32] reviewed the existing method of 2-factor authentication. They later offered a 3-factor unspecified authentication method for wireless networks in an IoT environment. A fuzzy commitment method was implemented to handle the information from the user's biometrics. Analyzing the performance and thorough comparison of obtained results shows better computation efficiency with better security and functional characteristics. Additional processes related to simulation were not performed, and the offered scheme's efficiency still needs better evaluation. Various security approaches for applications of IoT were also studied. Such applications include smart environments like smart grid, healthcare with smart technology, and smart transportation system.
The authors in [33] developed an encoding technique based on XOR manipulation, rather than complicated encoding like hash function usage, to anti-counterfeit and protect privacy. In an IoT environment, the present security mechanisms of the Radio-frequency Identification (RFID) system can be improved using cryptography protocols. The drawbacks of RFID protocols can also be enhanced with lightweight cryptography protocols. Hardware implementation for lightweight cryptography protocol was also demonstrated. Additionally, the offered protocol may also be utilized for establishing a process of mutual authentication in the unique system of RFID for IoT implementations.
The authors in [34] proposed a highly secured healthcare system based on IoT with BSN termed BSN-care that accomplished the requirements efficiently. BSN authoritative technologies were utilized in the modern healthcare system. It needs less power and lightweight wireless sensors nodes, which were used to monitor the functions of the human body and the surrounding environment. BSN nodes were utilized for collecting complex data and operating in an unfriendly environment and need firm security methods that prevent interaction of malicious nodes with the system. Security and confidentiality were described based on the implementation of BSN in the healthcare field. Many researches were based on trending BSN attempted to solve the security problems but failed to offer more robust security services such as preserving the privacy of the patient's data. To solve such issues, the proposed framework of BSN-care resulted in better efficiency concerning the needs of the healthcare system.
The authors in [35] offered a novel authentication of crucial establishment based on a signature for the IoT environment. The proposed security solution was tested using BAN logic, analysis of the informal security, and formal verification of the security using the AVISPA tool. The proposed method was also applied with the NS2 simulation tool. The results of the simulation illustrate the real-time implementation of the scheme. Higher security, efficient computation, and reduced costs for communication proved that the proposed method outperforms existing approaches. The model for authenticating the upcoming applications with IoT was discussed, and later challenges and needs for better security were also illustrated.
The authors in [36] proposed a lightweight and mutually reliant authentication protocol with a unique public key encoding method for the applications in a smart city. The protocol is a hybrid solution that considers communication cost and efficiency without sacrificing security. The proposed protocol was comparatively better than other earlier protocols, such as Elliptic-Curve Cryptography (ECC) and RSA-based. The authors also analyzed the security of the offered encoding approach and the mutual authentication protocol. The protocol was evaluated using Powerful Wireless Microcontroller System-On-Chip for 2.4-GHz IEEE 802.15.4 (CC2538) and Contiki Operating System (OS) modules. The experiments’ results showed that the offered protocol on the level of 112 bits security was around 88 and seven times faster than ECC and RSA, respectively. The time for mutual authentication can also be decreased if offline or online methods are enabled. Evaluation of the protocol in a real-time hardware environment was not carried out, and instead, only software evaluation was done. The protocol can be further optimized when the size of the message is at maximum without altering the size of ciphertext.
Security and authentication are the major security issues facing IoT and wireless networks. These drawbacks and requirements are the primary focal points of the proposed method in this paper.
This section highlights the architecture of the proposed method. It also describes the multi-authentication process using five steps of Initialization, user and sensor registration, login, authentication, and password renewal implemented on the two Gateway nodes, HGWN and Foreign Gateway Node (FGWN).
In WSN, the gateway node GWN is authoritative and an essential part between the users and the sensors, and it is essential for information exchange. The data from sensors initially reach the GWN through the Internet and is sent to the user. Once they work, the sensors and GWN tend to be static. While communication occurs, the distance between the user and a particular sensor may change. GWN continuously shows the power and communication resource so that the user contact reduces the sensor energy cost, as shown in Fig. 1 [31]. Preference is given for transmitting messages from the user to the GWN to the sensor and vice versa. The multi-gateway authentication process implemented in this study meets the farther sensors' access requirement and solves only one GWN problem, which leads to packet collisions issues.
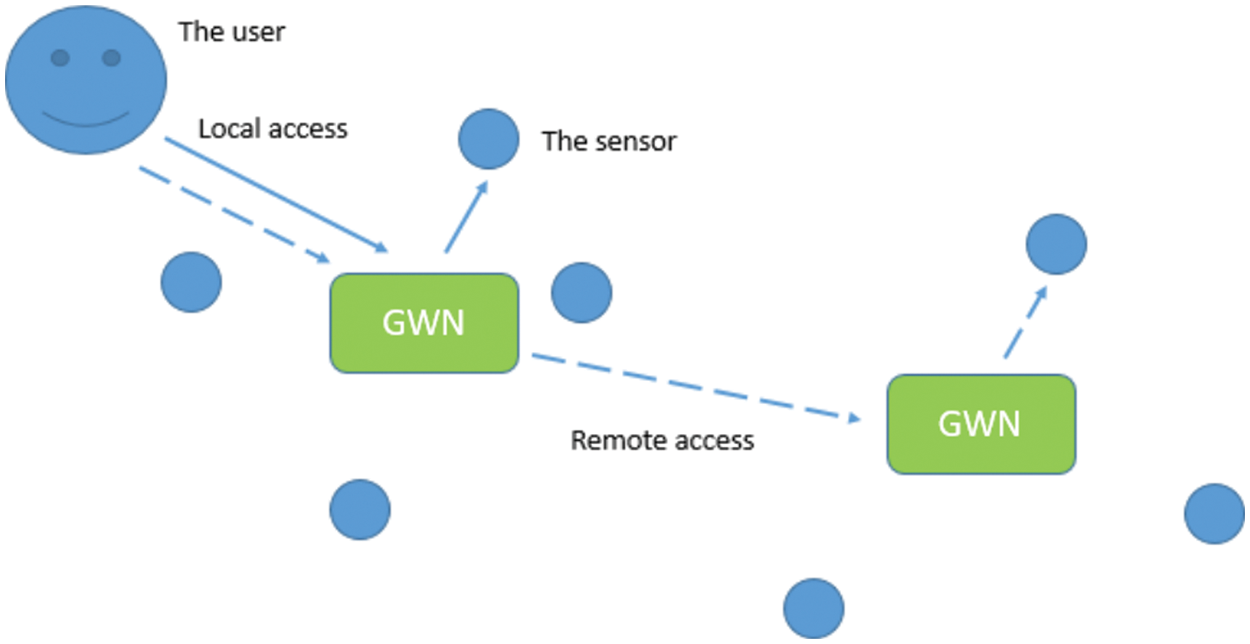
Figure 1: Multi-gateway sensor nodes access [31]
In the Multi-Gateway Sensor Nodes Access technique, the user is registered with a nearby GWN, and the data is obtained from the sensors. If the sensor is registered in the registered GWN's location, the user can access the sensor through GWN, and it is named a Home GWN or shortly an HGWN. Alternatively, if the sensor is near another GWN, it is called a Foreign GWN (FGWN), and the user can get the data through the FGWN.
The WSN communication environment is vulnerable [37,38], and security and privacy must be ensured. Mutual authentication and user tracking attacks are noted. Secret keys are generated using the BAN logic approach to share the information with the gateway nodes. The user and the sensors must register themselves. While entering into authentication, if it is not present in the HGWN database, it performs model 1 format, and if it is present, it performs model 2 based FGWN. Finally, the security system is verified using the multi-search tree algorithm.
3.2 Proposed Method Architecture
For a multi-gateway WSN architecture, a new authentication scheme named a three-factor authentication technique is used. The system needs to initialize the user identity, password, and biometrics [39]. The user and sensor nodes must be registered to share the information with the gateway nodes GWN. In this study, two Gateway nodes have been implemented, as shown in Fig. 2.
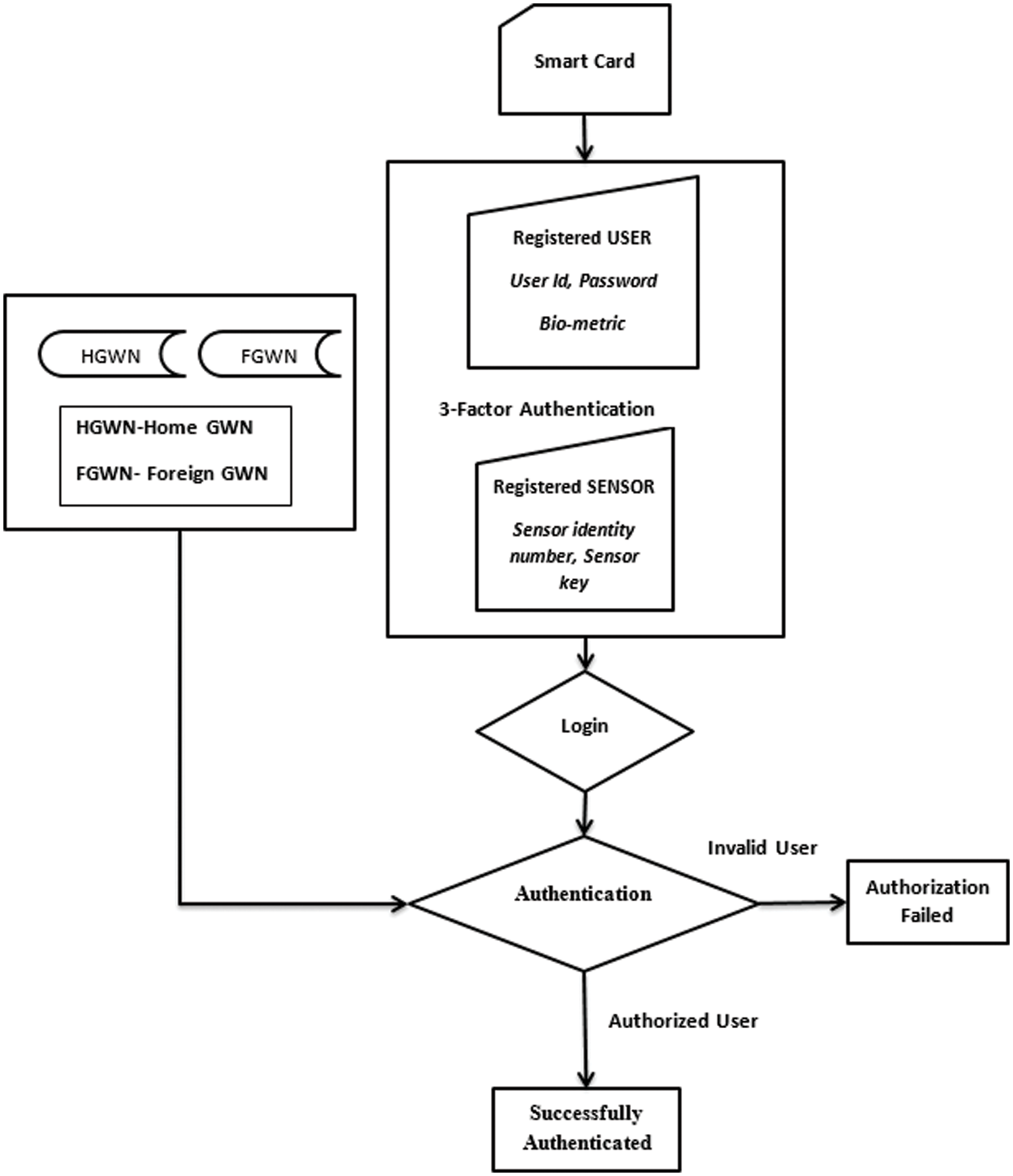
Figure 2: The multi-authentication process in GWN
To reach the gateway nodes, the sensors and users must register themselves using the BAN logic approach in an HGWN and using the BAN logic hashing inference rule in FGWN. Then the system has to log in to send the secret messages, and for that, the pseudo-identity number and other parameters are generated and sent to the HGWN. After that, the authentication phase exhibited nonce value. The user identity should be present in the Database for access, and if it is present in the HGWN database, it performs the model 1 procedure. If it is not present, then it performs model 2 procedure. For the verification, the multi-search-based encryption and decryption method is used. Both multi-search tree-based encryption and decryption were implemented to check the robustness of the model. Against simulation attacks, this scheme ensures security. This proposed study is based on security properties and performance as expected to be efficient compared to other techniques. Tab. 1 shows the notation used in the proposed protocol.
There are several assumptions for the multifactor authentication process against the adversary. The security property analysis rule has been demonstrated below:
1. Both Identity and Password identification are in relatively small sets. Searching for both is hard and takes time, and is considered a false premise. An assumption has been made that both can be guessed in polynomial time simultaneously. The adversary cannot identify or guess the hash values or nonce or secret key numbers because it has a greater secure length.
2. The three-factor authentications are considered robust because the last one is unidentified. Since an adversary can find out the user identity and password but still not the third authentication. Through side-channel attacks, the user identity can be identified. The false-positive issue even exists in biometric recognition.
3. Through the private and public channels, the messages have been transmitted. The adversary can damage the public channel until the three-factor authentication is cracked. However, the adversary could not damage the private channel. On the GWN side, the suspected system administrator's presence can crack the registered information sent to the GWN, but it is not happening in a private channel.
The methods followed in the multifactor authentication include the five phases developed in this study: system initialization, Registration, Login, Authentication, and Password renewal.
3.2.1 System Initialization Phase
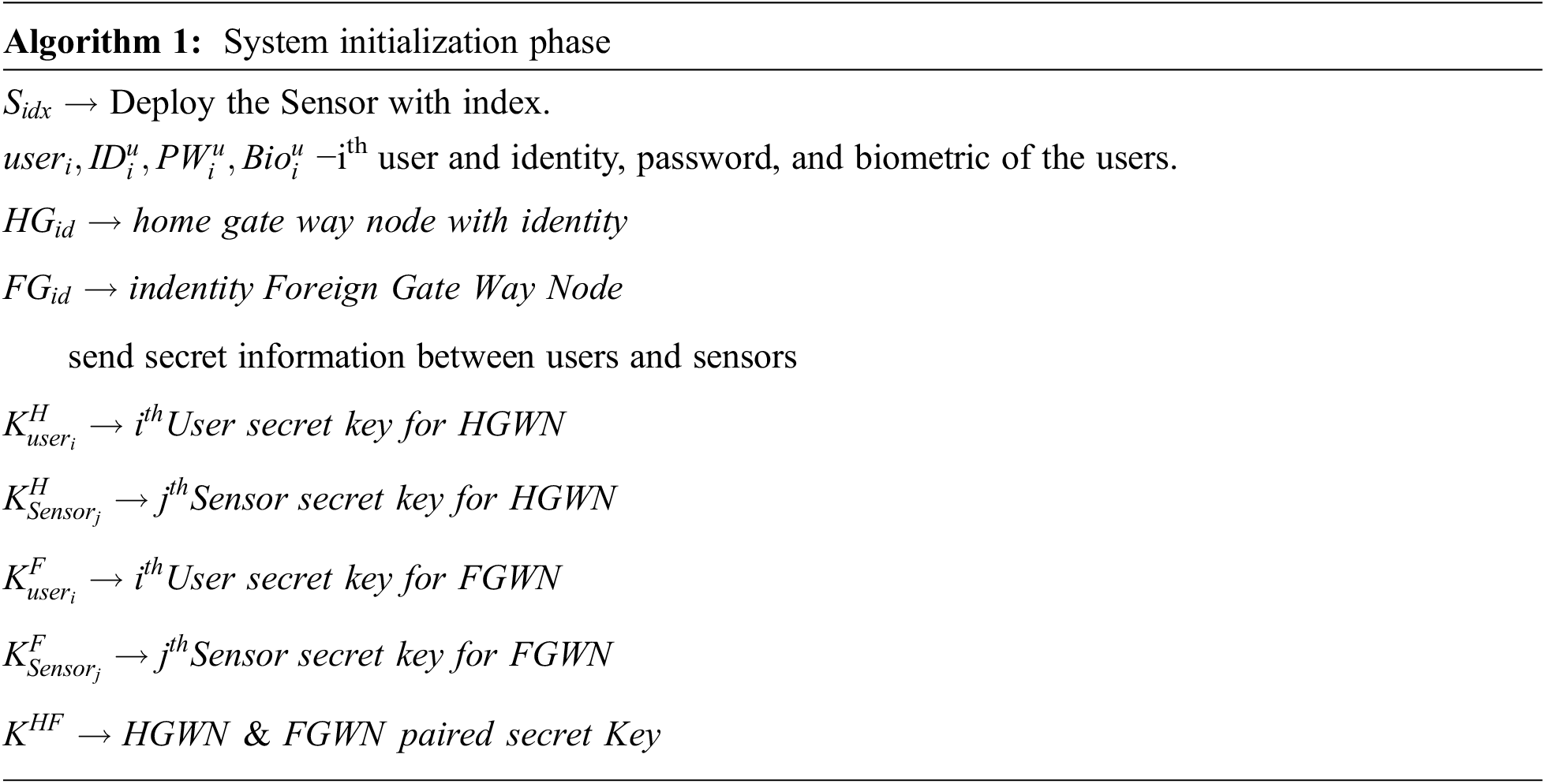
For WSN, efficient system initialization has to be designed [40]. Every GWN has its own identity, shown in the below initialization. For the HGWN, an identity HGid is established, and for the FGWN, an identity FGid is established. The sensor has its position recorded with a sensor index Sidx. Here three-way multi authentication processes are implemented. As explained below, identity, password, and biometrics have been established for every user. Between the users and sensors, secret information is sent through every identity.
1. If
2. If
3. Finally,
In this phase, after the sensor nodes are deployed in the target field, the information in the sensor nodes is sent to the legally registered user. Each sensor node has access using a secret key shared between the gateway nodes with authentication and key agreement. The registration phase involves sensor registration and user registration.
Sensor Registration
The sensor nodes are randomly deployed with general coordinates Sj. The sensor index Sidx generated a secret key
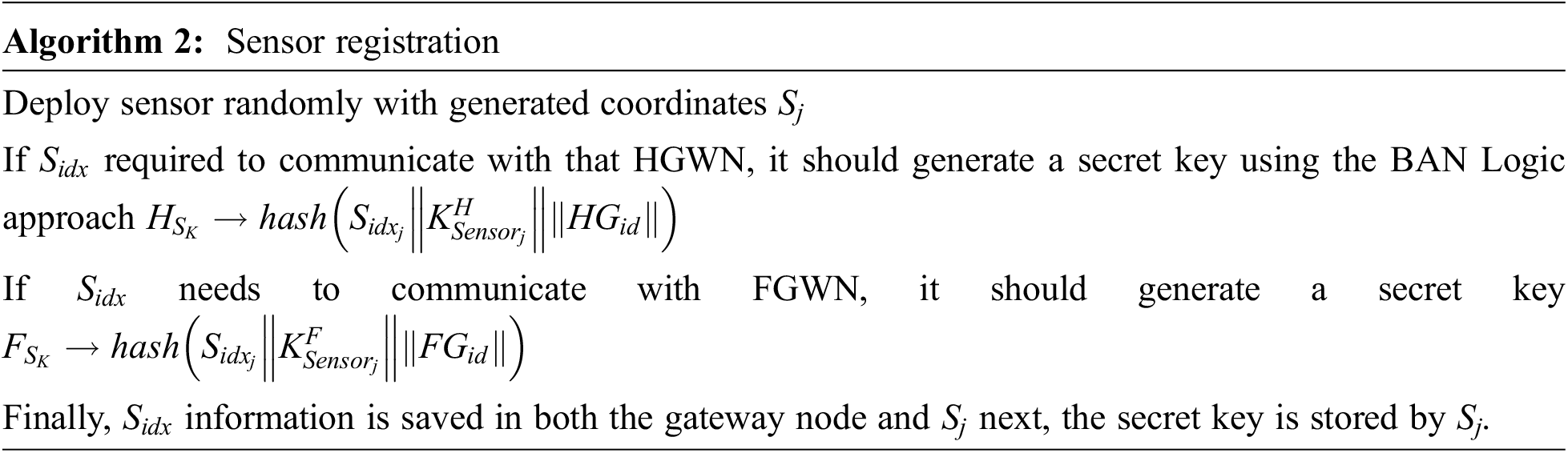
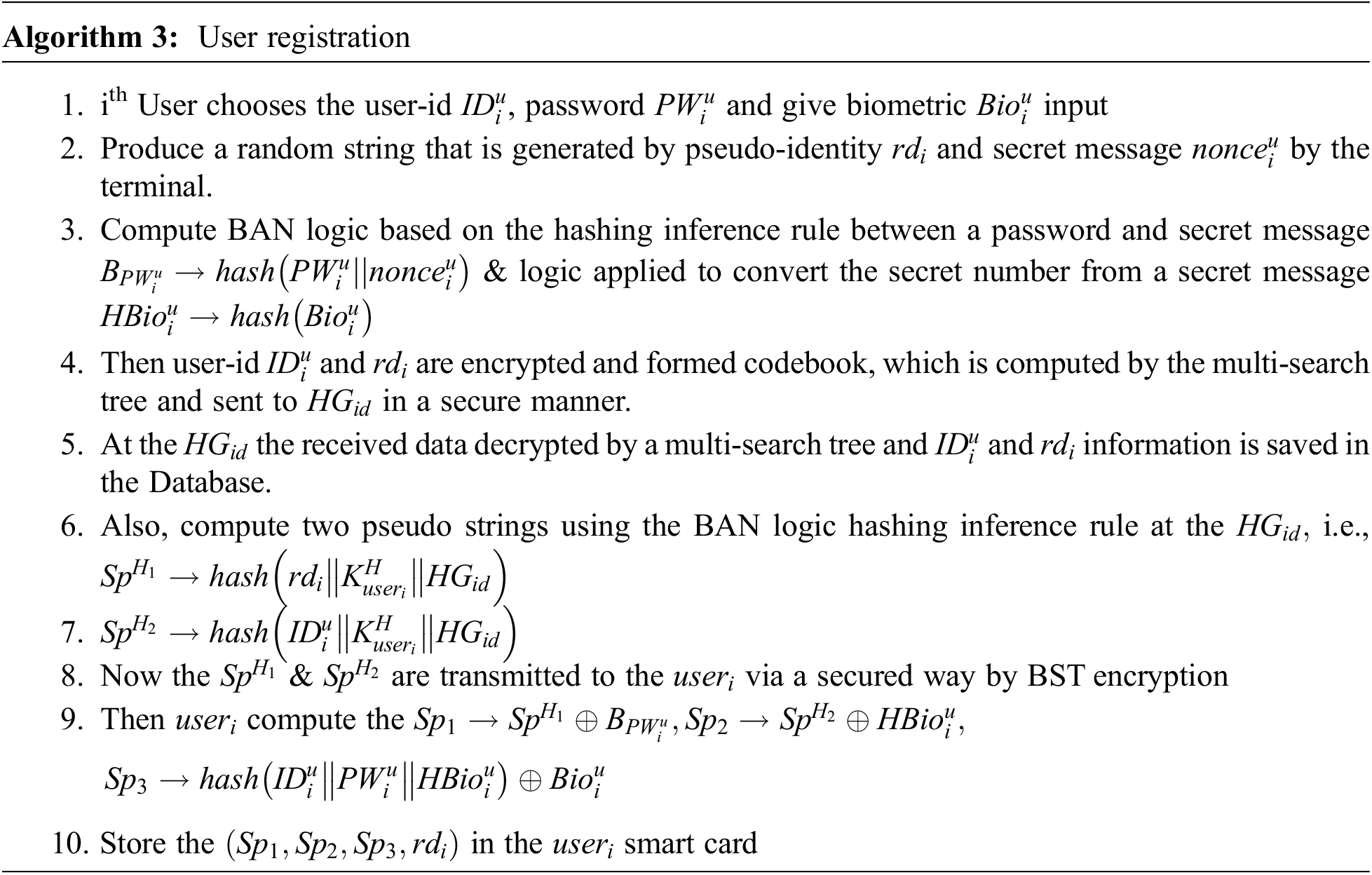
User Registration
The user registration undergoes three main steps to send the secret messages.
First: the ith user Useri selected the user-id
Second: the user identification number and pseudo-identity number retrieved data through decryption with the help of a multi-search tree and stored in the Database. The two pseudo strings
Third: then the value
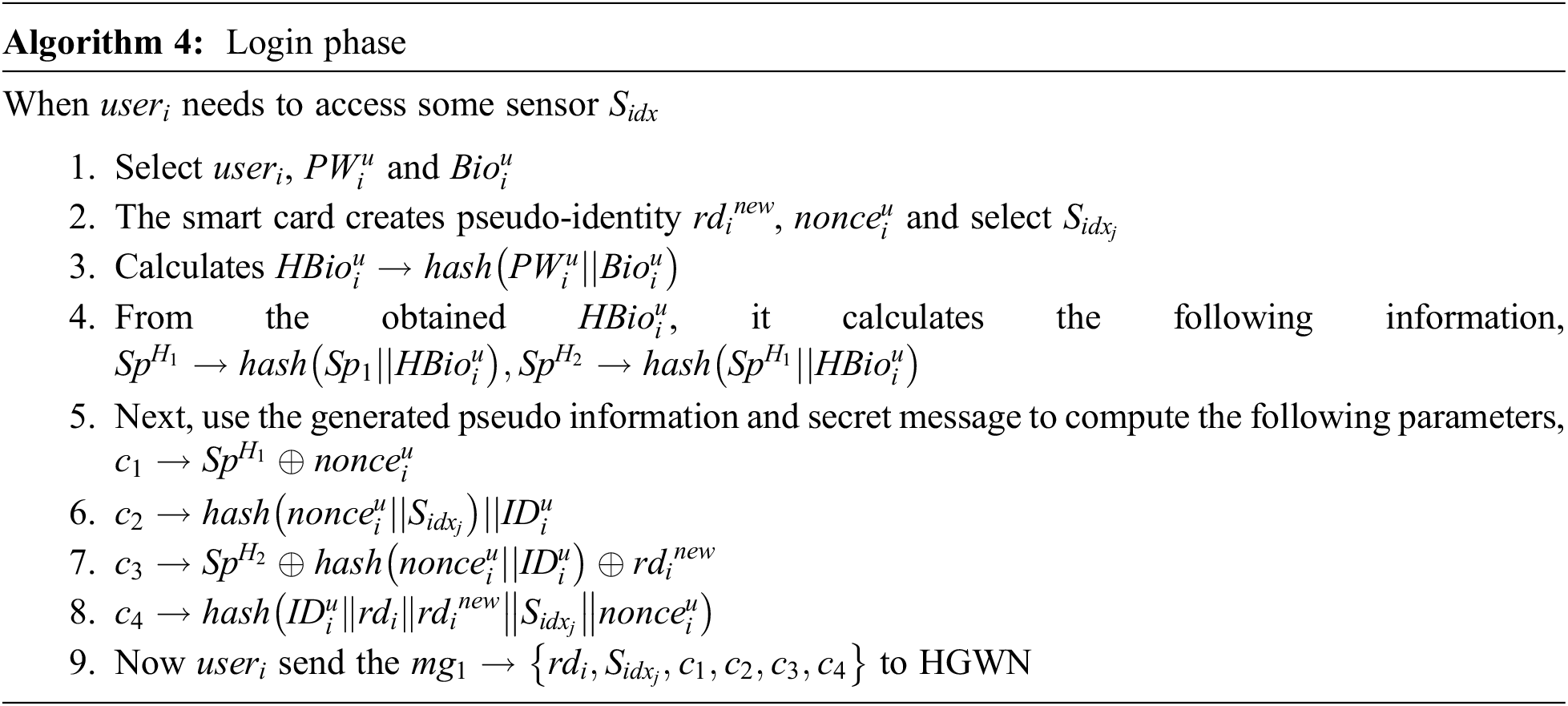
The login phase describes the authenticated user Useri access the sensor index number
In the authentication phase, the
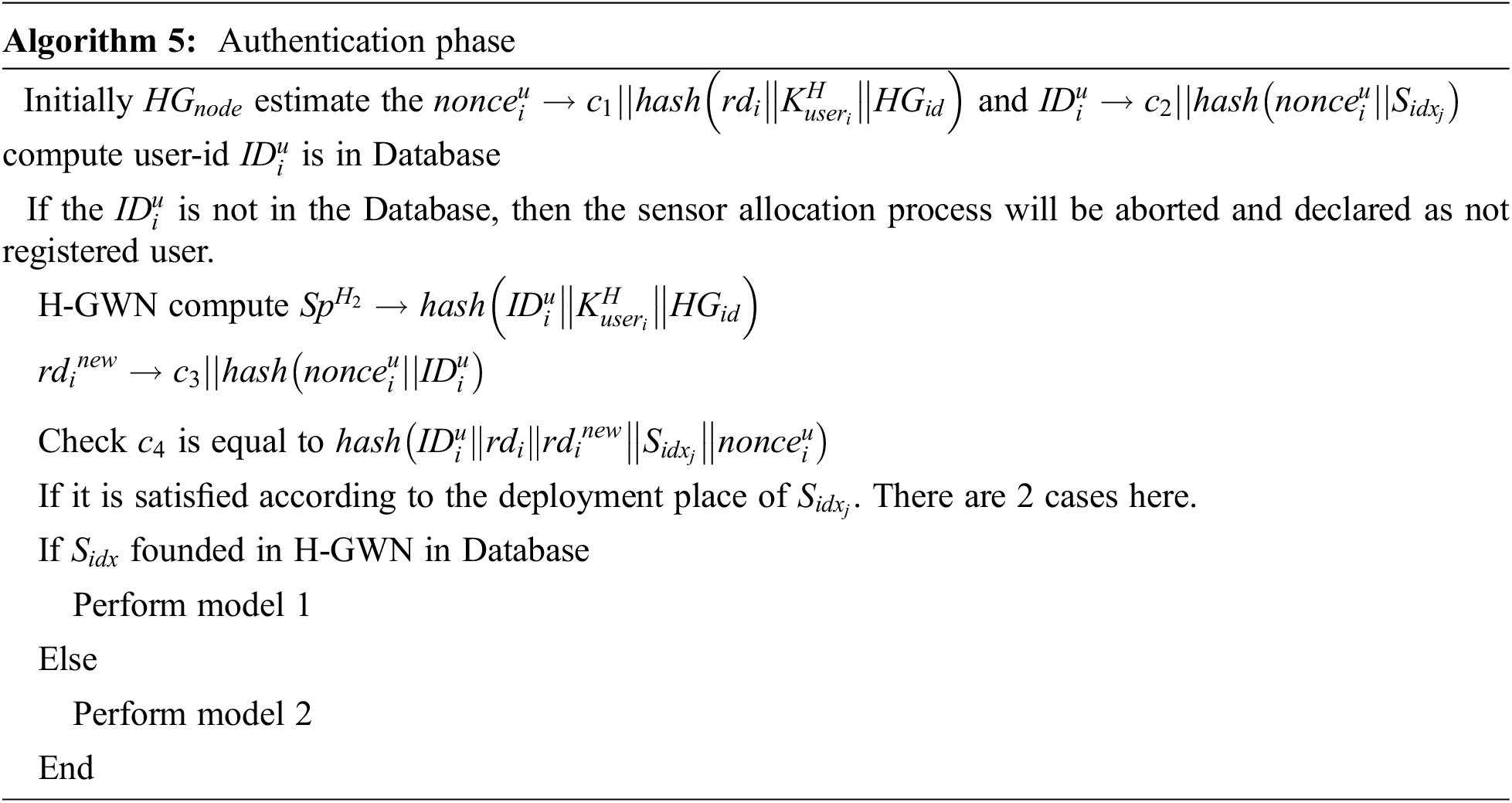
• Model 1:
If the HGWN database has the sensor index number
Step 1: In this step, the HGWN chooses the nonce secret message
Step 2: calculate the nonce value and nonce secret message computed by sensor Sj. Furthermore, check whether the c7 value equals the hash value. If it equals, then select the
Step 3: In this step the
Step 4: The smart card calculates the pseudo number and nonce values from the parameters and hash values after the mg4 is received. Then session value is computed, and if c12 equals the hash value of respected identity values and pseudo number values, then the new values of pseudo number and pseudo-identity are measured by the card. Finally, replace the
• Model 2:
If the HGWN database does not have the sensor index number
Step 1- The HGWN transmits the mg5 message containing the pseudo-identity number, sensor identity number
Step 2- The HGWN computed the new pseudo-identity number, c15, c16, and c17 values. Then the message mg7 is sent to Useri contains c15, c16, c17, and
Step 3- After receiving the mg7 value, the smart card measures the
Step 4- Now FGWN calculates the
Step 5- the sensor node Sj estimated the nonce value
Step 6-
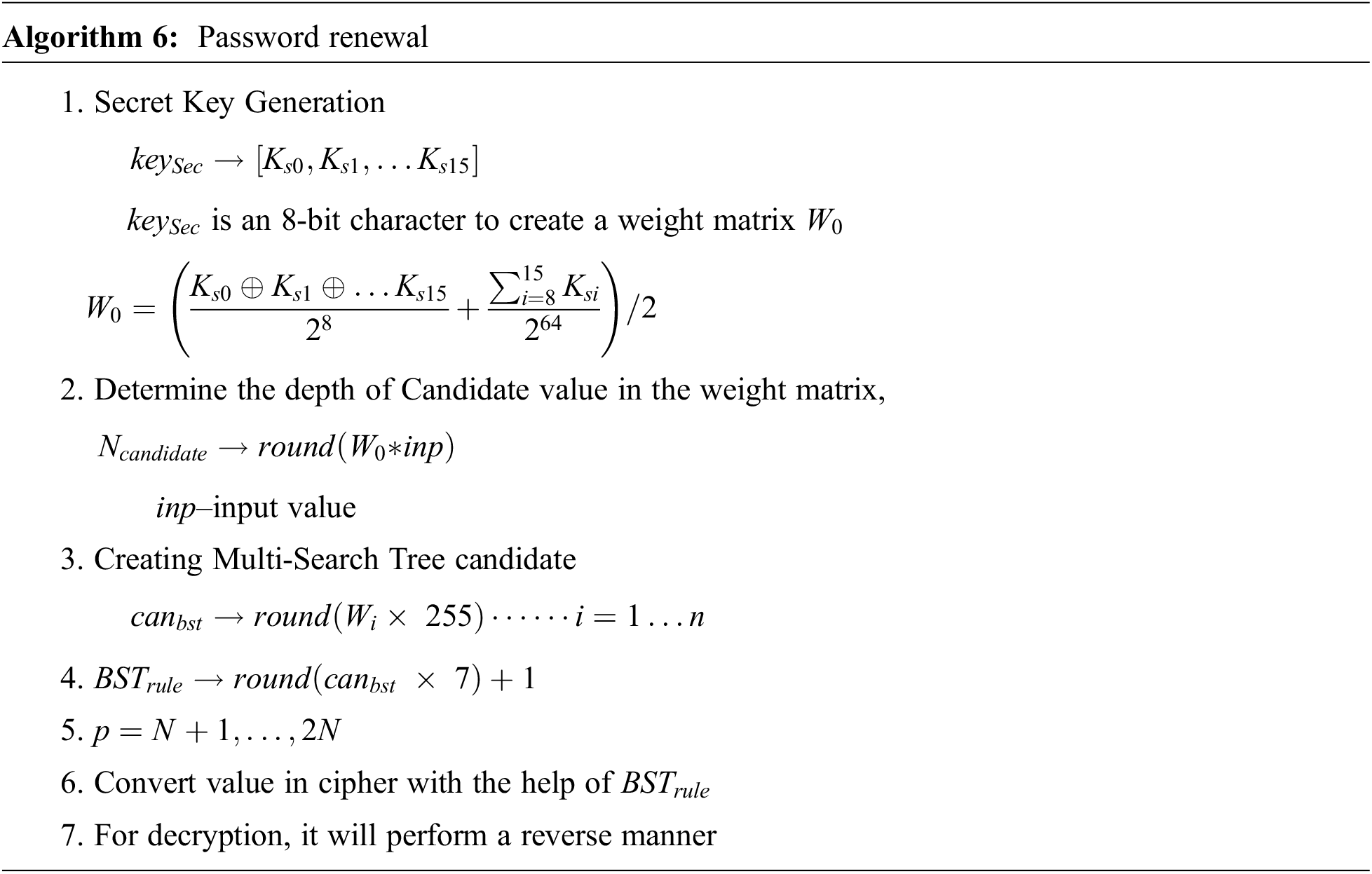
If the user forgets the password and knows the rest of the authentication details, still the user cannot access the secured gateway. The only option to change or renew the password is to follow the steps of password renewal by the user. The multi-search tree used the binary search concept for cipher values. It encrypts the message and decrypts the message at the receiver side to check the system's security. Algorithm 6 illustrates the password renewal steps.
4 Research Results and Discussion
The proposed method used multi-stages to authenticate users. Home and foreign gateways are used like HGWN and FGWN. The user registration and sensor registration are performed through the BAN logic approach. It has been evaluated through several experiments. The performance of the proposed IoT authentication method is evaluated in terms of metrics such as authorized and unauthorized sensors, energy utilization, network lifetime, misdetection probability, false-positive rate, and packet loss. These performance metrics results have been compared with other existing methods like Trust-Based Monitoring (TBM), Multi-Source Feedback Trust (MFTM), Software-defined networking-based (SDN-MG), and SMER. Trust-Based (TBM) follows the spoof detection, and trust construction and authenticates the message [39]. Multi-Source Feedback Trust (MFTM) depends on the lightweight trust mechanism reliable methodology. Software-defined networking-based (SDN-MG) security mechanism ensures data transfer security and continuous data flow. SMER is a secure method to exchange resources based on administering security in IoT environments resource exchange. The above traditional methods are used for analysis purposes since they are based on trust-based analysis and authentication.
NS-3 simulator tool was used to evaluate the proposed protocol. NS-3 provides an open, extensible network simulation platform. NS-3 simulates data packet networks, provides high performance, simulates the user’s engine, and provides a highly controlled system behavior and a reproducible learning network environment. It focuses on the protocols of the Internet and the working of the network. Moreover, the NS-3 tool can also be used for non-Internet-based systems.
The performance of this proposed method is analyzed by several metrics and compared with other existing methods using the NS3 tool as follows.
Sensors near the gateway node share the secret message after proper authentication in HGWN. If the sensor presents and shares the message to another gateway node but is still near, the sensor is FGWN. In Fig. 3, 100 sensors represented as green dots are around the HGWN, and sensors around FGWN are represented as blue dots.
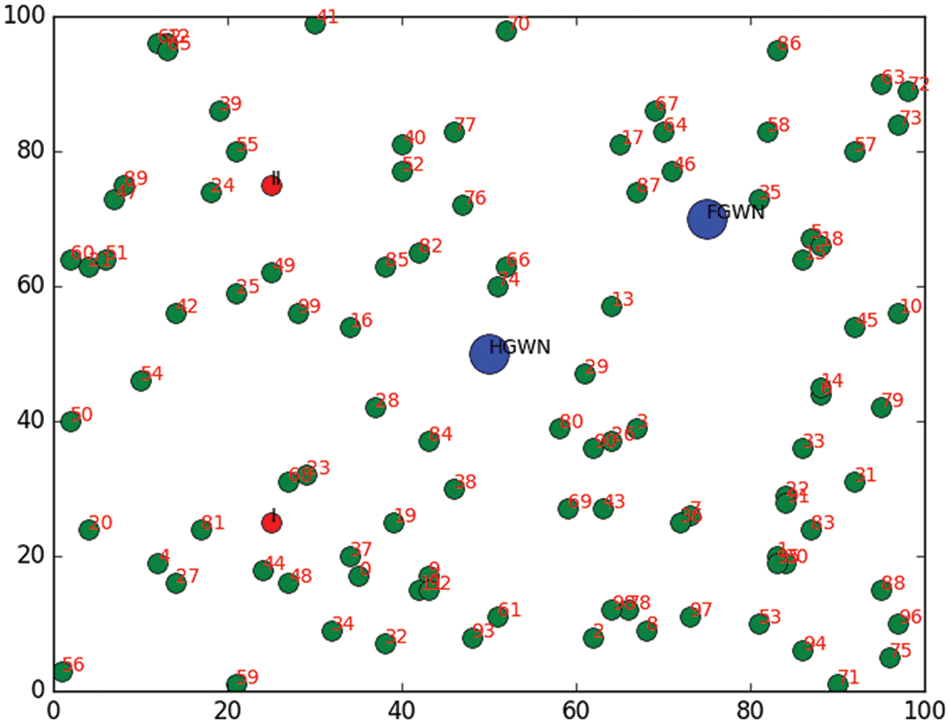
Figure 3: Authenticated sensors around the HGWN and FGWN
Fig. 4 shows the unauthenticated sensors as black dots. The sensor is considered unauthenticated if any authentications fail in the three-way authentication.
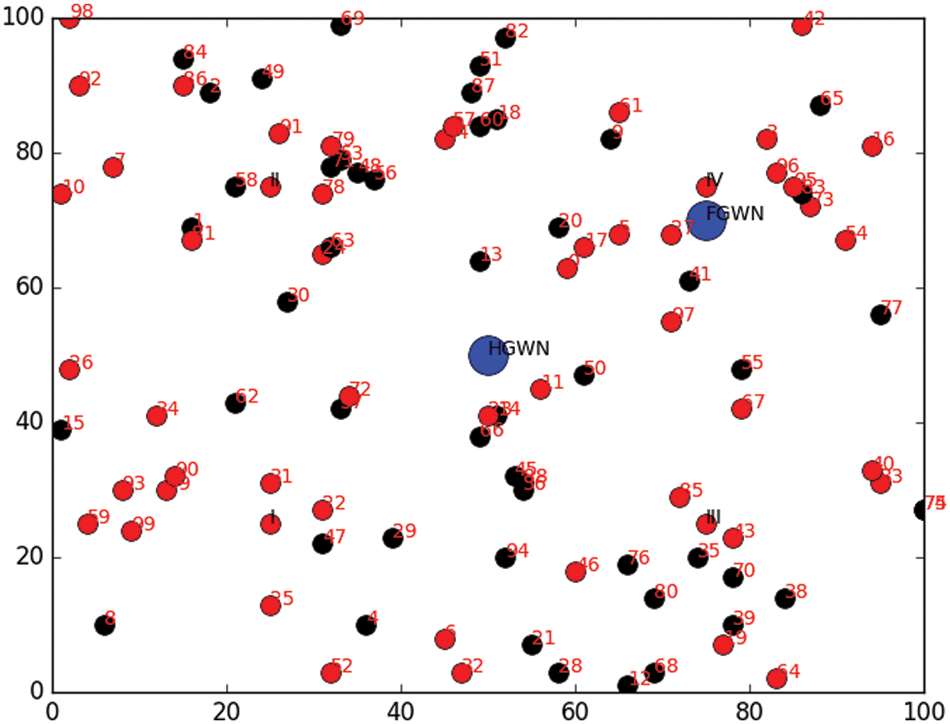
Figure 4: Unauthenticated sensors around HGWN and FGWN
4.2.2 Energy Utilization Comparison
The energy utilization of the proposed method is evaluated and compared with other existing methods, TBM [39], MFTM, SDN-MG, and SMER. If the message byte increases, the required energy to share the message increases. In Fig. 5, the proposed method increases energy utilization as the message bytes increase. Compared with other methods like SDN-MG, it shows a higher energy utilization than MFTM and SMER. In the case of TBM, energy utilization is sometimes better compared to others. The energy consumption has to be minimized concerning the message bytes.
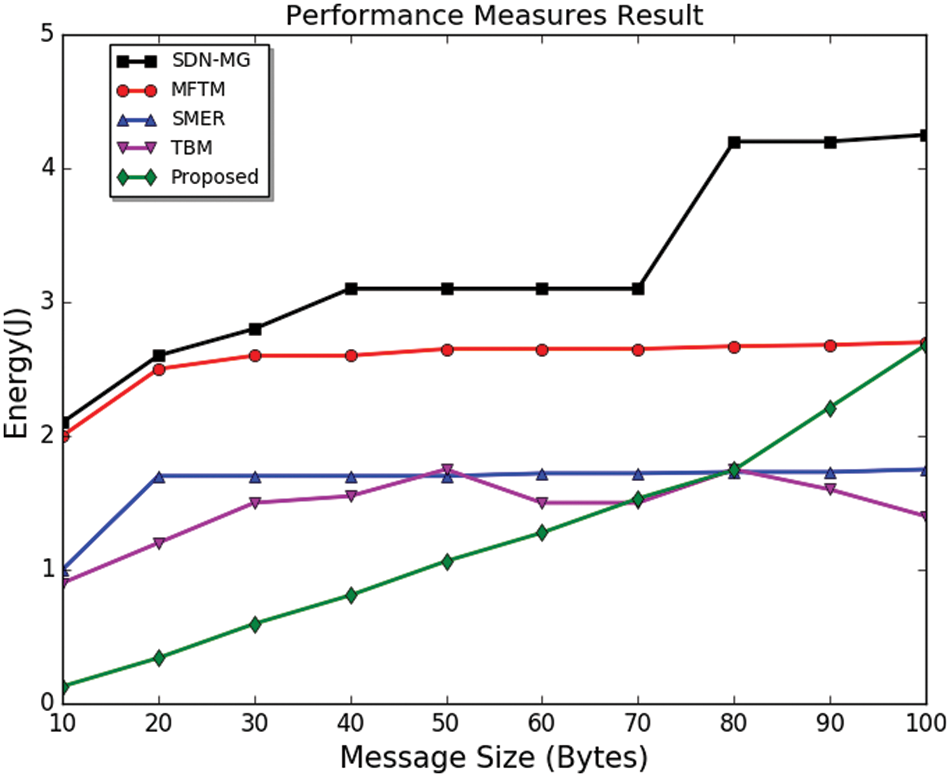
Figure 5: Comparison of energy utilization
4.2.3 Network Lifetime Comparison
The network lifetime depends on the energy consumption for sharing the message. If the network lifetime is high, then the processing and computational time are optimized, leading to efficiency in the whole process. Hence, more energy remaining leads to extra process time and a prolonged network lifetime. The comparison of a network lifetime with other existing methods is shown in Fig. 6. The proposed method shows a higher network lifetime under the same number of iterations. In case of energy loss, the data transmission decreases, and the remaining sensors used for the process are considered network failure. In the 4 cases of iterations, the network lifetime shows better results with the proposed protocol.
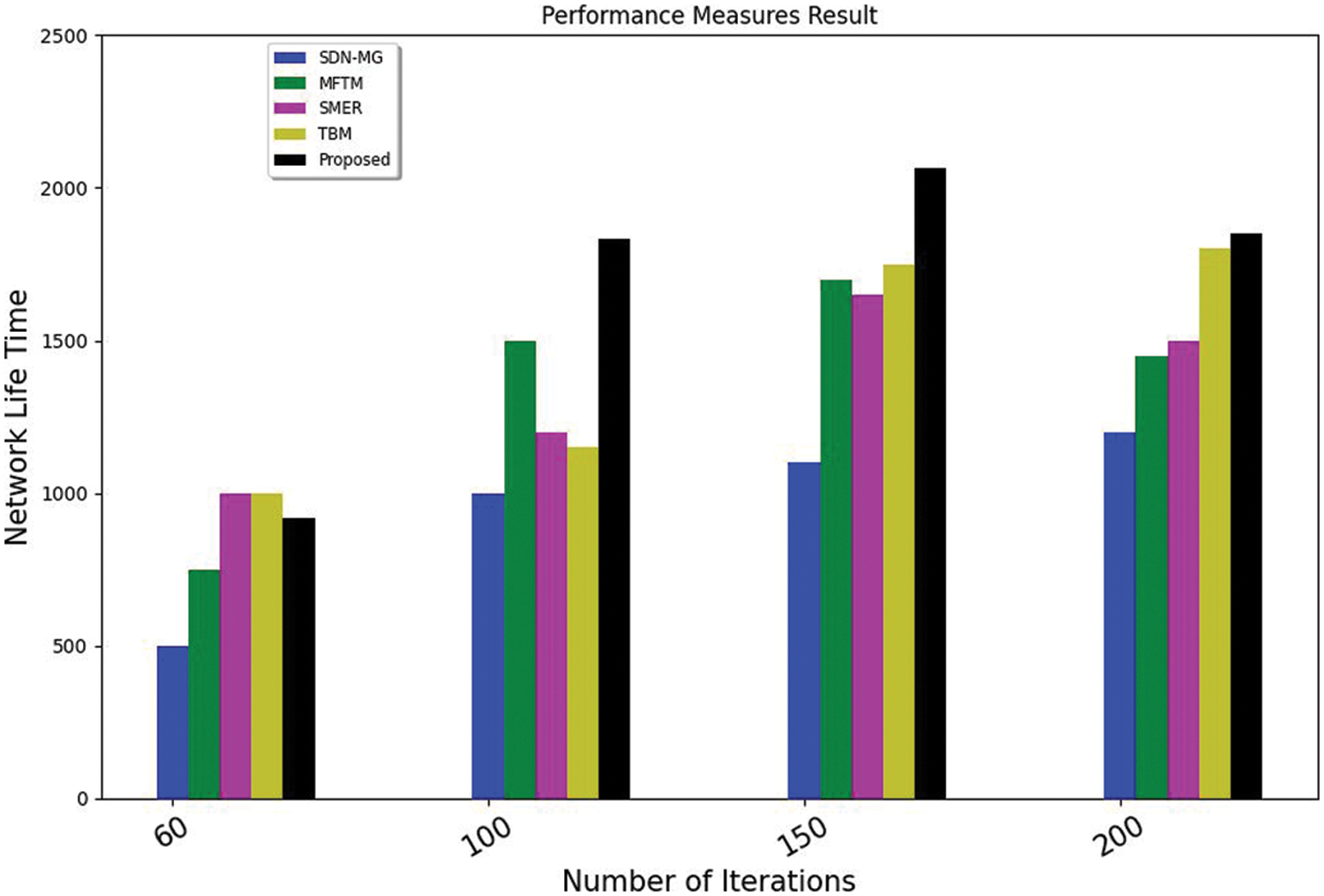
Figure 6: Comparison of network lifetime
4.2.4 Probability of Misdetection
The verification and trust monitoring levels are followed in the misdetection rate measurement. The misdetection may be present during the communication process. It is expected to be detected at an early stage, and even though it passed through initial analysis, it is detected at another stage by the evaluation factors. The misdetection probability rate is low when false alarm probability is low. The malicious sensor based on the BAN logic approach detection is called misdetection. In Fig. 7, the proposed method shows a decreased misdetection rate and a decreased false alarm rate. Compared to other existing approaches, the SDN-MG shows the highest malicious detection, followed by MFTM, SMER, and TBM, respectively [39].
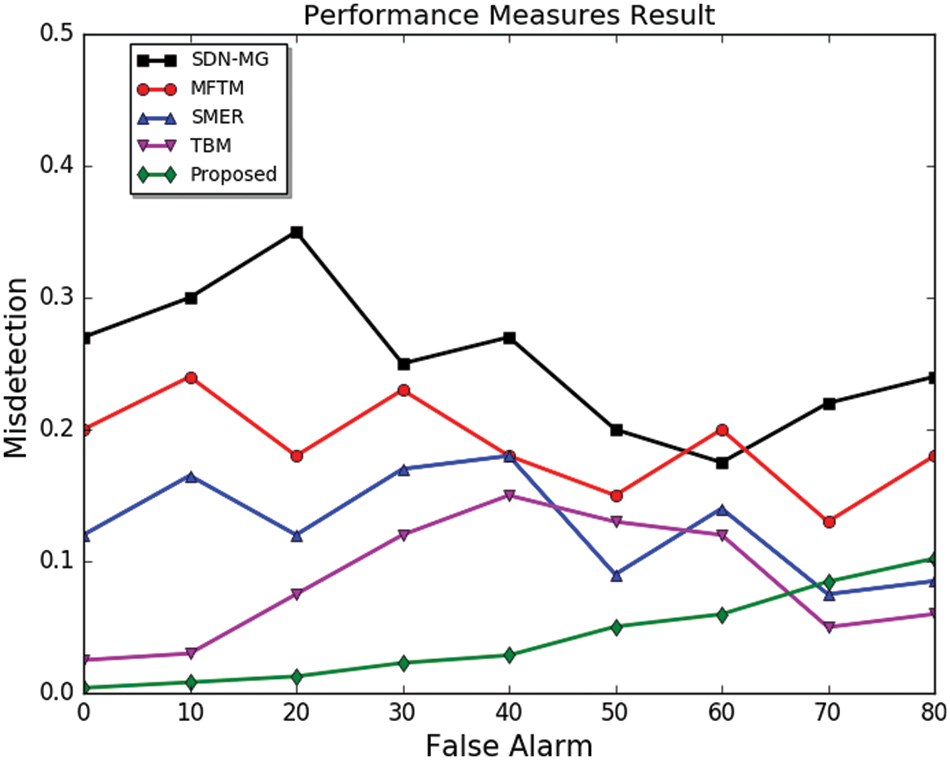
Figure 7: Probability of misdetection comparison
With the increase in distance, the false-positive rate varies. The device becomes illegal when the proximity between the devices increases. The false-positive rate is decreased by detecting the malicious threats accurately in the network. Fig. 8 compares the false-positive rate values with other approaches under different distances. Previous methods show a higher false-positive rate compared to the proposed method.
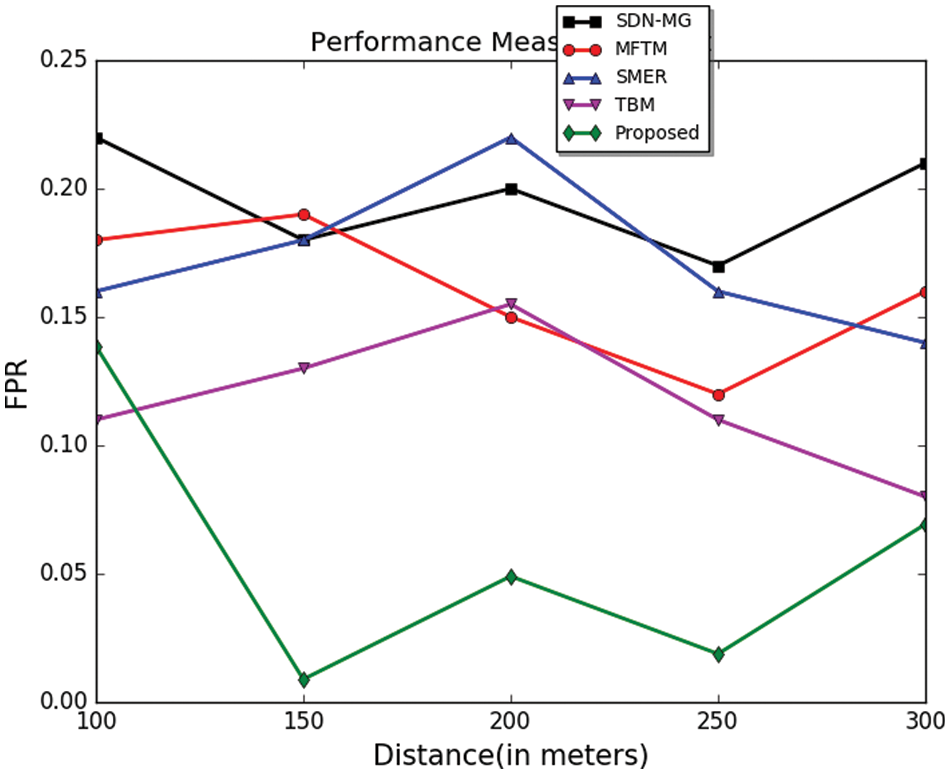
Figure 8: False positive rate comparisons
The authenticated packets should be delivered correctly to lead to a decrease in packet loss. If the sent packets are not delivered to the desired destination, packet loss is termed. It is considered a reduction in the accuracy of delivering the packets. Fig. 9 compares the packet loss of the proposed method with previous methods. SDN-MG has the highest packet loss rate, followed by MFTM, SMER, and TBM [39]. The packet loss rate slightly increased with the increase in the number of devices.
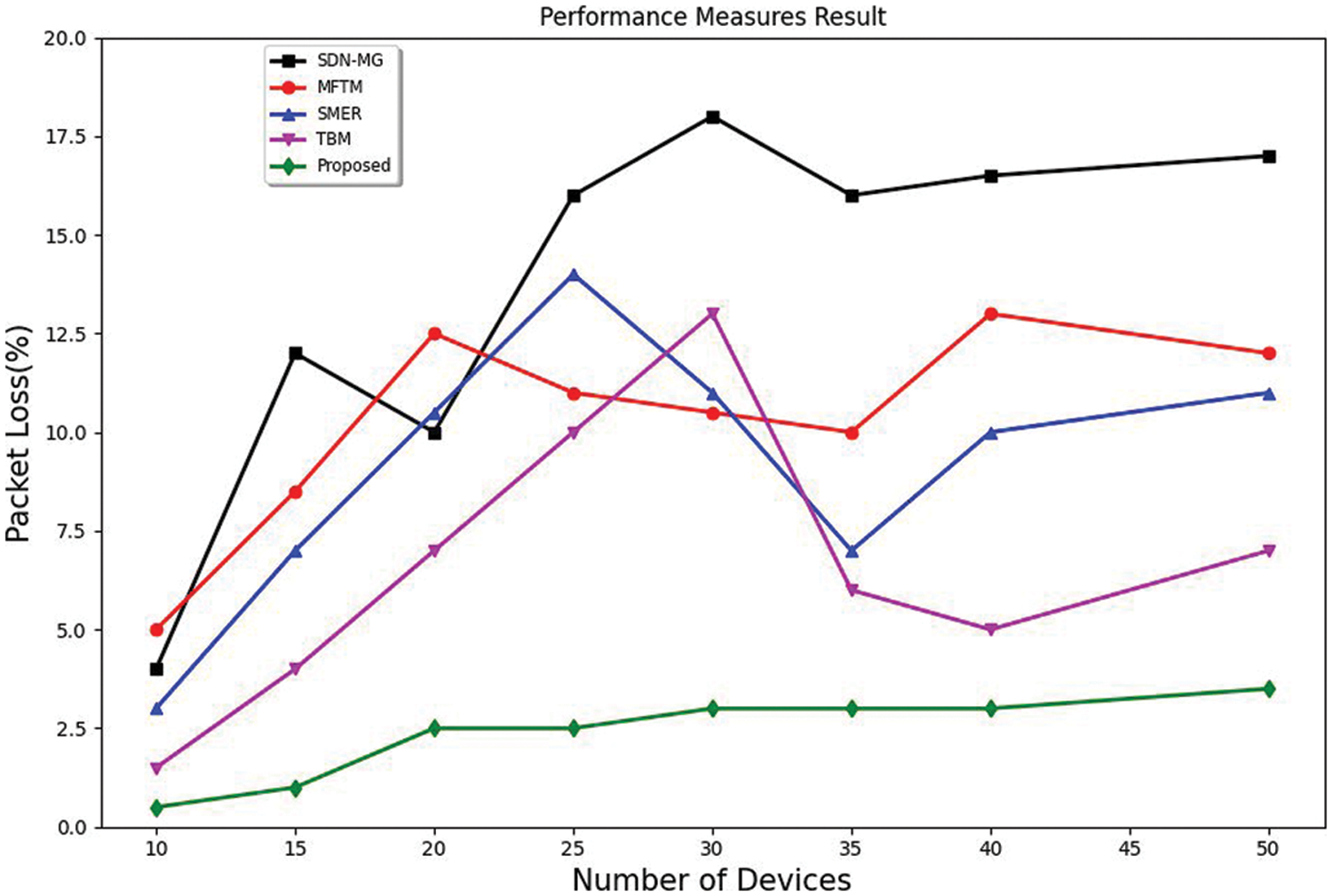
Figure 9: Packet loss comparisons
Fig. 10 compares the communication cost of the authentication process to other protocols with the increase in the message size. For acceptable packets, the authentication signature is placed in message authentication. The comparisons were also made to ensure that communication security improves reliability. The transmission process determines the communication message rate after the authentication process. It can be noticed that under the same message size, the proposed method's communication cost is less than the cost of the TBM method, which has a medium communication cost rate. The LSS method shows the highest communication cost value [39]. The communication rate increases for all three methods by increasing the message size rate.
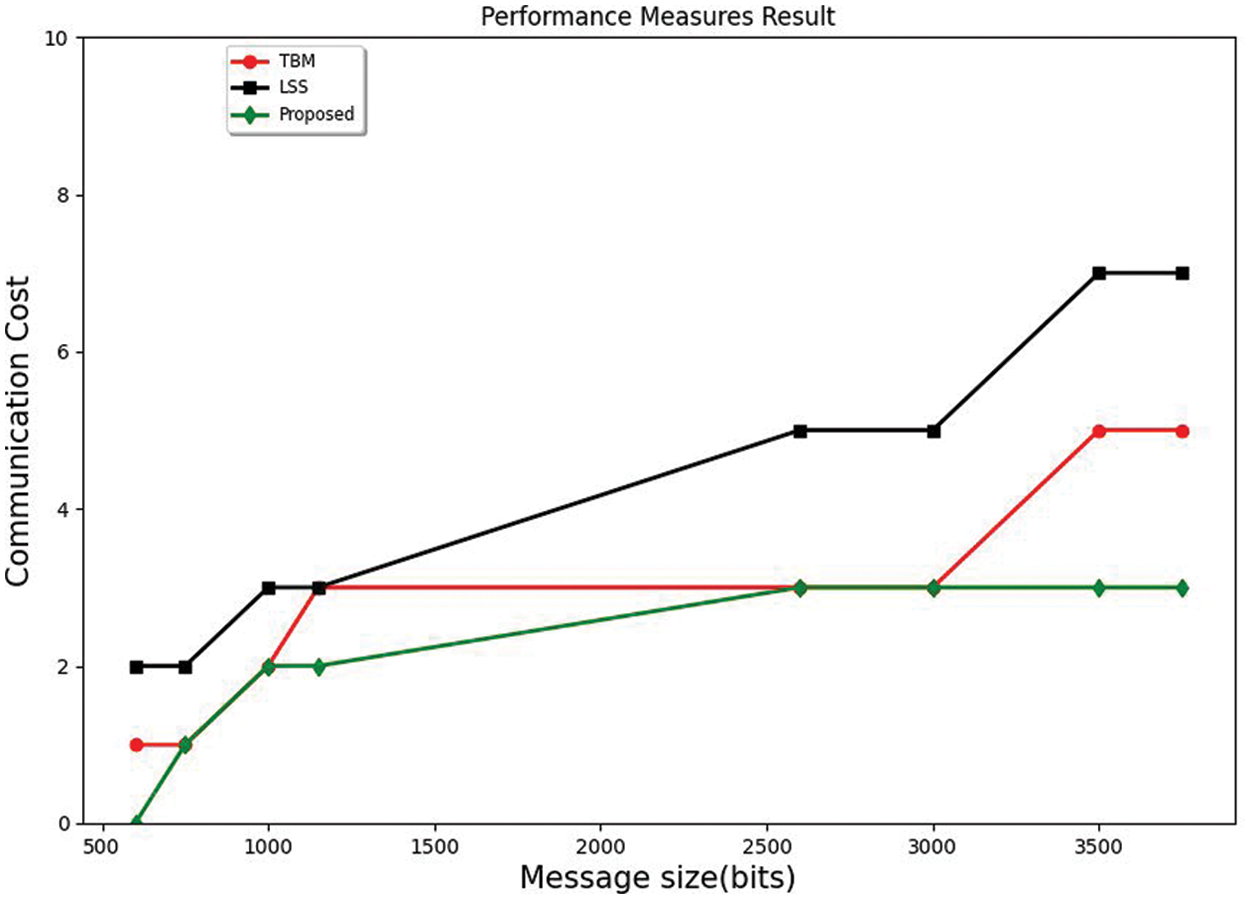
Figure 10: Communication cost comparison
4.2.8 Measurement of Time consumption, throughput, and End-to-End delay
Different schemes are compared in terms of time consumption, throughput, and End-to-End Delay. Based on the network transmission message rate, the time taken to share and receive the message has been measured in ms, as shown in Fig. 11. The throughput value is measured in bps and is shown in Fig. 12, and the End-to-End delay is measured in seconds and shown in Fig. 13.
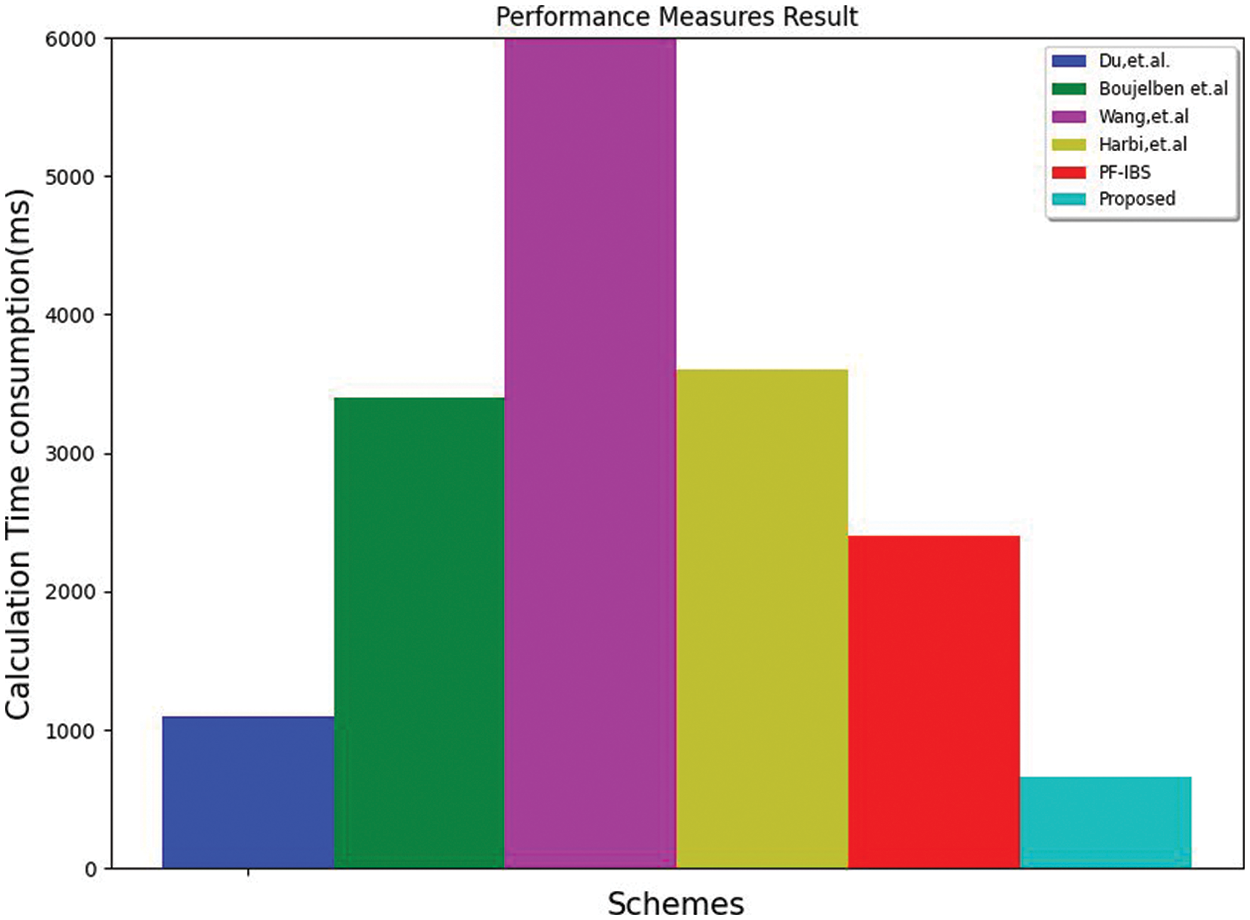
Figure 11: Time consumption calculation comparison
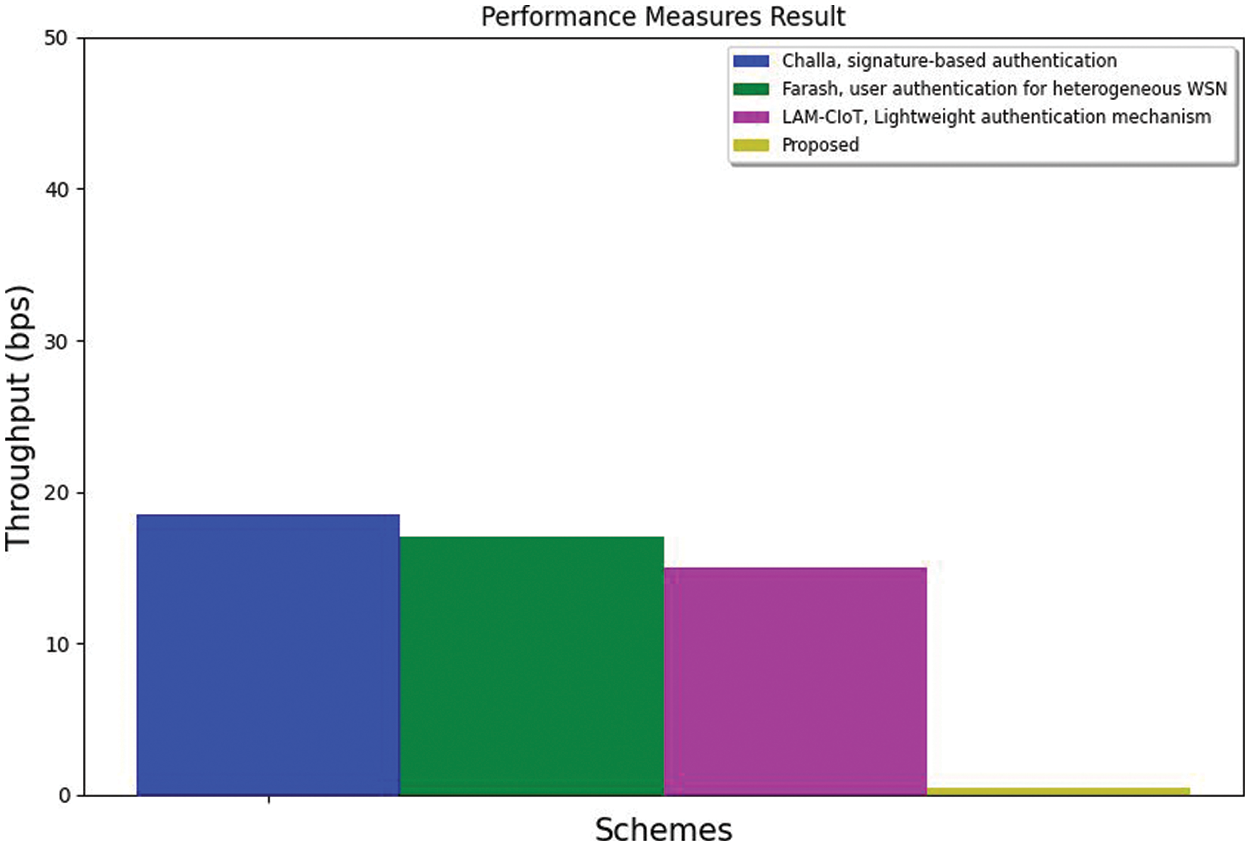
Figure 12: Throughput comparison
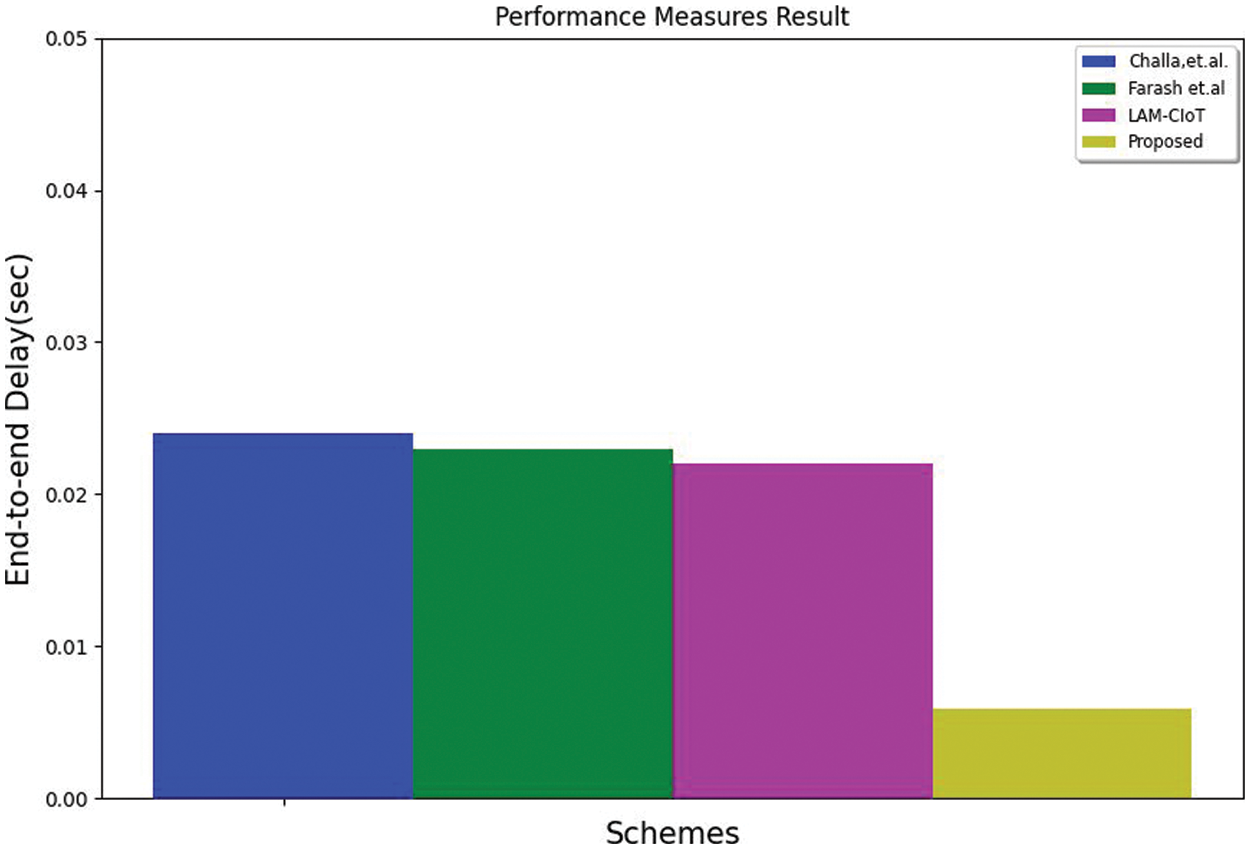
Figure 13: End-to-end delay comparison
From Fig. 11, the proposed method's time consumption decreases compared to other studies, indicating performance improvement. From Fig. 12, it can be noticed that the proposed method throughput value is less compared to other existing studies. From Fig. 13, it can be seen that the end-to-end delay value decreased compared to other methods, which improves the accuracy and reliability of the proposed method.
This study proposes a multi-authentication scheme using five steps: Initialization, user and sensor registration, login, authentication, and password renewal. The proposed scheme has been implemented on the Home Gateway Node (HGWN) and Foreign Gateway Node (FGWN). The 3-way authentication of user identity number, Password, and biometric recognition is followed. BAN logic approach of the hash inference rule is used to register the user and the sensor in a secure and trustworthy way. The proposed method ensures that secret message sharing and registration information sharing are done in an authenticated manner. If any one of the authentications fails, it is considered an unauthorized user. The proposed method has been evaluated in terms of performance metrics like False-Positive Rate (FPR), Network lifetime, packet loss, communication cost, and energy consumption and compared with other existing methods. The time consumption and End-to-End delay have been reduced, and the throughput value increased slightly. The loss of message packets, False positive rate value, and misdetection rate have been reduced. The energy consumption increased with the increase in the size of the messages. The network lifetime also increased in this proposed method. The communication cost is slightly high concerning the processing and message sharing rates. The main drawback is that BAN logic-based protocols sometimes have to be insecure and cannot be distinguished, and these variations tend to be critical. This protocol provides high security and robustness. Because of the inconsistency and insecurity in BAN logic, the log-regularly varying distribution protocol can be implemented and considered a possible avenue for future work.
Acknowledgement: Thanks to the Saudi Electronic University for sponsoring this work.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. P. Sarwesh, N. S. V. Shet and K. Chandrasekaran, “Energy efficient network design for IoT healthcare applications,” in Internet of Things and Big Data Technologies for Next Generation Healthcare, Cham, Switzerland, Springer, pp. 35–61, 2017. [Google Scholar]
2. A. Tiwary, M. Mahato, A. Chidar, M. K. Chandrol, M. Shrivastava et al., “Internet of Things (IoTResearch, architectures and applications,” International Journal on Future Revolution in Computer Science & Communication Engineering, vol. 4, no. 3, pp. 23–27, 2018. [Google Scholar]
3. P. Sanmartin, A. Rojas, L. Fernandez, K. Avila, D. Jabba et al., “Sigma routing metric for RPL protocol,” Sensors, vol. 18, no. 4, pp. 1–18, 2018. [Google Scholar]
4. M. Conti, P. Kaliyar, M. Rabbani and S. Ranise, “Attestation-enabled secure and scalable routing protocol for IoT networks,” Ad Hoc Networks, vol. 98, no. 3, pp. 102054, 2020. [Google Scholar]
5. K. Haseeb, A. Almogren, N. Islam, I. U. Din and Z. Jan, “An energy-efficient and secure routing protocol for intrusion avoidance in IoT-based WSN,” Energies, vol. 12, no. 21, pp. 354–369, 2019. [Google Scholar]
6. A. O. A. Salem and N. Shudifat, “Enhanced LEACH protocol for increasing a lifetime of WSNs,” Personal and Ubiquitous Computing, vol. 23, no. 5-6, pp. 901–907, 2019. [Google Scholar]
7. H. Kim, J. Ko, D. E. Culler and J. Paek, “Challenging the IPv6 routing protocol for low-power and lossy networks (RPLA survey,” IEEE Communications Surveys & Tutorials, vol. 9, no. 4, pp. 2502–2525, 2017. [Google Scholar]
8. F. A. Khan, M. Khan, M. Asif, A. Khalid and I. U. Haq, “Hybrid and multi-hop advanced zonal-stable election protocol for wireless sensor networks,” IEEE Access, vol. 7, pp. 25334–25346, 2019. [Google Scholar]
9. C. Nakas, D. Kandris and G. Visvardis, “Energy efficient routing in wireless sensor networks: A comprehensive survey,” Algorithms, vol. 13, no. 3, pp. 1–65, 2020. [Google Scholar]
10. E. Bertino, V. Casola, A. Castiglione and W. Susilo, “Security and privacy protection vs. sustainable development,” Computer Security, vol. 76, pp. 250–251, 2018. [Google Scholar]
11. D. N. Serpanos and A. G. Voyiatzis, “Security challenges in embedded systems,” ACM Transactions on Embedded Computing Systems, vol. 12, no. 1, pp. 1–10, 2013. [Google Scholar]
12. B. Aboushosha, R. A. Ramadan, A. D. Dwivedi, A. El-Sayed and M. Dessouky, “SLIM: A lightweight block cipher for internet of health things,” IEEE Access, vol. 8, pp. 203747–203757, 2020. [Google Scholar]
13. C. G. García, E. R. Núñez-Valdez, V. García-Díaz, C. P. García-Bustelo and M. Cueva Lovelle, “A review of artificial intelligence in the internet of things,” International Journal of Interactive Multimedia and Artificial Intelligence, vol. 5, no. 4, pp. 9–20, 2019. [Google Scholar]
14. D. Saeed, R. Iqbal, H. H. R. Sherazi and U. G. Khan, “Evaluating near-field communication tag security for identity theft prevention,” Internet Technology Letters, vol. 2, no. 5, pp. e123, 2019. [Google Scholar]
15. Z. Hong, W. Chen, H. Huang, S. Guo and Z. Zheng, “Multi-hop cooperative computation offloading for industrial IoT-edge-cloud computing environments,” IEEE Transactions on Parallel and Distributed Systems, vol. 30, no. 12, pp. 2759–2774, 2019. [Google Scholar]
16. A. Yousefpour, G. Ishigaki, R. Gour and J. P. Jue, “On reducing IoT service delay via fog offloading,” IEEE Internet of Things Journal, vol. 5, no. 2, pp. 998–1010, 2018. [Google Scholar]
17. M. S. Hossain, C. I. Nwakanma, J. M. Lee and D. S. Kim, “Edge computational task offloading scheme using reinforcement learning for IIoT scenario,” ICT Express, vol. 6, no. 4, pp. 291–299, 2020. [Google Scholar]
18. H. W. Kim, J. H. Park and Y. S. Jeong, “Adaptive job allocation scheduler based on usage pattern for computing offloading of IoT,” Future Generation Computer Systems, vol. 98, no. 2, pp. 18–24, 2019. [Google Scholar]
19. B. Jan, H. Farman, H. Javed, B. Montrucchio, M. Khan et al., “Energy efficient hierarchical clustering approaches in wireless sensor networks: A survey,” Wireless Communications and Mobile Computing, vol. 2017, pp. 1–14, 2017. [Google Scholar]
20. H. Wei, H. Luo, Y. Sun and M. S. Obaidat, “Cache-aware computation offloading in IoT systems,” IEEE Systems Journal, vol. 14, no. 1, pp. 61–72, 2020. [Google Scholar]
21. H. R. Ghorbani and M. H. Ahmadzadegan, “Security challenges in internet of things: Survey,” in 2017 IEEE Conf. on Wireless Sensors (ICWiSe), Miri, Malaysia, IEEE, pp. 1–6, 2017. [Google Scholar]
22. J. Deogirikar and A. Vidhate, “Security attacks in IoT: A survey,” in 2017 Int. Conf. on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)(I-SMAC2017, Palladam, India, IEEE, pp. 32–37, 2017. [Google Scholar]
23. D. S. David and A. Jeyachandran, “A comprehensive survey of security mechanisms in healthcare applications,” in 2016 Int. Conf. on Communication and Electronics Systems (ICCES), Coimbatore, India, IEEE, pp. 1–6, 2016. [Google Scholar]
24. N. A. El-mawla, M. Badawy and H. Arafat, “Security and key management challenges over WSN (A Survey),” International Journal of Computer Science & Engineering Survey (IJCSES), vol. 10, no. 1, pp. 15–34, 2019. [Google Scholar]
25. P. Nalajala and S. B. Lakshmi, “A secured IoT based advanced health care system for medical field using sensor network,” International Journal of Engineering & Technology, vol. 7, no. 2. 20, pp. 105–108, 2018. [Google Scholar]
26. R. S. Harry and R. Joseph, “Enhancements in anomaly detection in body sensor networks,” in 2019 IEEE Int. Conf. on Computational Science and Engineering (CSE) and IEEE Int. Conf. on Embedded and Ubiquitous Computing (EUC), New York, NY, USA, IEEE, pp. 384–389, 2019. [Google Scholar]
27. F. T. Zuhra, K. A. Bakar, A. Ahmed and M. A. Tunio, “Routing protocols in wireless body sensor networks: A comprehensive survey,” Journal of Network and Computer Applications, vol. 99, pp. 73–97, 2017. [Google Scholar]
28. R. Gravina, P. Alinia, H. Ghasemzadeh and G. Fortino, “Multi-sensor fusion in body sensor networks: State-of-the-art and research challenges,” Information Fusion, vol. 35, no. 3, pp. 68–80, 2017. [Google Scholar]
29. K. H. Yeh, “A secure IoT-based healthcare system with body sensor networks,” IEEE Access, vol. 4, pp. 10288–10299, 2016. [Google Scholar]
30. A. J. Abraham, A. Thomas and J. Pradeep, “IoT based real time cardiac activity monitoring system using body sensor network,” International Journal of Pure and Applied Mathematics, vol. 120, no. 6, pp. 1455–1464, 2018. [Google Scholar]
31. S. K. Yang, Y. M. Shiue, Z. Y. Su, I. H. Liu and C. G. Liu, “An authentication information exchange scheme in WSN for IoT applications,” IEEE Access, vol. 8, pp. 9728–9738, 2020. [Google Scholar]
32. M. S. Farash, M. Turkanović, S. Kumari and M. Hölbl, “An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the internet of things environment,” Ad Hoc Networks, vol. 36, no. 6, pp. 152–176, 2016. [Google Scholar]
33. X. Li, J. Niu, S. Kumari, F. Wu, A. K. Sangaiah et al., “A three-factor anonymous authentication scheme for wireless sensor networks in internet of things environments,” Journal of Network and Computer Applications, vol. 103, pp. 194–204, 2018. [Google Scholar]
34. J. Y. Lee, W. C. Lin and Y. H. Huang, “A lightweight authentication protocol for internet of things,” in 2014 Int. Symp. on Next-Generation Electronics (ISNE), Kwei-Shan Tao-Yuan, Taiwan, IEEE, pp. 1–2, 2014. [Google Scholar]
35. P. Gope and T. Hwang, “BSN-Care: A secure IoT-based modern healthcare system using body sensor network,” IEEE sensors journal, vol. 16, no. 5, pp. 1368–1376, 2015. [Google Scholar]
36. S. Challa, M. Wazid, A. K. Das, N. Kumar, A. G. Reddy et al., “Secure signature-based authenticated key establishment scheme for future IoT applications,” IEEE Access, vol. 5, pp. 3028–3043, 2017. [Google Scholar]
37. N. Li, D. Liu and S. Nepal, “Lightweight mutual authentication for IoT and its applications,” IEEE Transactions on Sustainable Computing, vol. 2, no. 4, pp. 359–370, 2017. [Google Scholar]
38. W. Teepe, “On BAN logic and hash functions or: How an unjustified inference rule causes problems,” Autonomous Agents and Multi-Agent Systems, vol. 19, no. 1, pp. 76–88, 2009. [Google Scholar]
39. F. Alqahtani, Z. Al-Makhadmeh, A. Tolba and O. Said, “TBM: A trust-based monitoring security scheme to improve the service authentication in the internet of things communications,” Computer Communications, vol. 150, no. 15, pp. 216–225, 2020. [Google Scholar]
40. L. Chan, K. Gomez-Chavez, H. Rudolph and A. Hourani, “Hierarchical routing protocols for wireless sensor network: A compressive survey,” Wireless Networks, vol. 26, no. 5, pp. 3291–3314, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools