 Open Access
Open Access
ARTICLE
Topology Driven Cooperative Self Scheduling for Improved Lifetime Maximization in WSN
1 Department of Electronics and Communication Engineering, Meenakshi College of Engineering, Chennai, 600078, India
2 Department of Electronics and Communication Engineering, St. Joseph’s College of Engineering, Chennai, 600119, India
* Corresponding Author: G. Brindha. Email:
Computer Systems Science and Engineering 2023, 45(1), 445-458. https://doi.org/10.32604/csse.2023.027329
Received 14 January 2022; Accepted 30 March 2022; Issue published 16 August 2022
Abstract
In Wireless Sensor Network (WSN), scheduling is one of the important issues that impacts the lifetime of entire WSN. Various scheduling schemes have been proposed earlier to increase the lifetime of the network. Still, the results from such methods are compromised in terms of achieving high lifetime. With this objective to increase the lifetime of network, an Efficient Topology driven Cooperative Self-Scheduling (TDCSS) model is recommended in this study. Instead of scheduling the network nodes in a centralized manner, a combined approach is proposed. Based on the situation, the proposed TDCSS approach performs scheduling in both the ways. By sharing the node statistics in a periodic manner, the overhead during the transmission of control packets gets reduced. This in turn impacts the lifetime of all the nodes. Further, this also reduces the number of idle conditions of each sensor node which is required for every cycle. The proposed method enables every sensor to schedule its own conditions according to duty cycle and topology constraints. Central scheduler monitors the network conditions whereas total transmissions occurs at every cycle. According to this, the source can infer the possible routes in a cycle and approximate the available routes. Further, based on the statistics of previous transmissions, the routes towards the sink are identified. Among the routes found, a single optimal route with energy efficiency is selected to perform data transmission. This cooperative approach improves the lifetime of entire network with high throughput performance.Keywords
The increasing penetration of information technology services provides easy access to different types of services through a variety of networks. Wireless Sensor Networks (WSN) hold an important place and are deployed in different conditions and locations for variety of purposes. WSN comprises of a lot of sensor nodes which are bound with limited energy due to its natural characteristics. This limited energy confines the total number of transmissions, a sensor can perform. Also, radio design restricts direct transmission with faraway nodes. These constraints encourage the cooperative transmission to be performed by any sensor node. Most of the sensor nodes spend their energy in listening packet reception and transmission. Even though the sensors do not contribute anything in data transmission, it listens to the signals through the duty cycle in which it is scheduled to wakeup stage.
Scheduling is the process of allocating the sensor nodes with specific conditions. The entire time is split into a number of duty cycles. In order to save the energy of sensor nodes, scheduling is enforced so as to allocate the conditions for sensor nodes. The nodes allocated towards wakeup stage alone listen to the entire duty cycle. However, energy loss occurs when listening the signals too. Numerous scheduling strategies have been proposed earlier to support the lifetime maximization of WSN. However, it makes use of the energy of nodes or the number of transmissions that the sensor is scheduled. These models mostly ended up in poor performance in scheduling the sensor nodes. Cluster-based approaches are used during different situations where limited number of cluster heads are selected. It needs to be transmitted to the cluster head after which no need to worry about it. In spite of all these developments, sensor nodes remain under-performing in terms of achieving the expected Quality of Service (QoS).
QoS of WSN completely relies upon various parameters namely throughput, energy utilization, latency and so on. Throughput performance is higher when the energy utilization is higher whereas it would be higher, when the route selection is efficient. Also, throughput performance and energy utilization create an impact on the lifetime of sensor nodes. By improving the energy utilization performance of sensor nodes, the lifetime of nodes can be improved which in turn would support achieving high throughput performance.
Consider that K number of sensor nodes exists in the topology while the scheduler has to send K number of packets towards various sensors. So, it replicates K × H number of transmissions to be performed among different intermediate nodes. In total, it claims (K × H) × μ amount of energy (in joules) to be spent upon controlling the scheduling signals. This claims the major part of energy from different sensor nodes which in turn reduces the lifetime of the network. So, the current study considers this issue and is motivated to design an efficient scheduling algorithm that can reduce the overhead caused by scheduling process.
The lifetime of sensor network can be improved by adapting efficient scheduling and route selection algorithms. However, when a minimal number of nodes are scheduled as working, it is easy to identify the number of routes to reach the sink point or service point. Among the routes available, there must be a method devised that can select the most efficient route to reach the service point. By selecting the efficient route, throughput performance as well as network lifetime can be improved. Different route selection algorithms are available in literature while mostly it uses traffic parameters to select the route so that the latency is reduced and throughput performance is increased. On the contrary, it reduces the lifetime as it consumes more energy. Similarly, hop count-based approach selects the shortest possible route but suffer from packet drop and result in retransmission issues. This phenomenon also claims high energy depletion. All these drawbacks are considered based on which the current study proposes the development of an efficient scheduling model.
According to the above discussed scheduling issues, the author is motivated at designing an efficient scheduling approach to achieve the following outcomes.
■ Scheduling approach should be performed in a cooperative manner, where the decision is locally enforced. The details of different sensors should be provided to all the nodes by the scheduler. Afterwards, the source can infer the condition of its neighbors according to the topology and can identify the possible wakeup nodes and their cycles.
■ Reduction of scheduling overhead that occurs during the transmission of control packets by sharing the details of the node and its neighbors through data packet. This is an excellent strategy to achieve topology statistics and support scheduling.
■ Scheduler floods with periodic details about the transmission details of various nodes which is shared among the nodes.
■ Scheduling is locally decided whereas the support is provided in a cooperative manner.
■ Route selection should be performed locally based on node statistics.
Numerous scheduling techniques have been presented earlier in sensor network while some of the techniques related to the problem undertaken are discussed in this section.
An adaptive scheduling towards Q-Learning was presented in [1] which considered the convergence nature of jobs in scheduling towards frames’ execution. A delay feature-based scheduling algorithm was presented in the literature [2], which maximizes the wakeup nodes. In this study, the shortest tree scheduling was used.
In the study conducted earlier [3], the author presented a Dynamic Hyper Round Policy (DHRP) scheme which considers the energy of sensor nodes to maximize the lifetime of the network. Similarly, in literature [4], the method uses connectivity between the nodes towards the measurement of dissimilarity between neighbors. The changing demand is monitored according to energy demands.
A multi objective optimization model was presented in [5] in which the scheduling is done in such a way that the blind area is covered. Similarly, in literature [6], an Energy-Efficient Broadcast Scheduling (EEBS) Algorithm was presented which integrates different time slots to cover the maximum network area.
A backtracking-based scheduling algorithm was discussed in [7] which works based on Langford subset generation. Similarly, in literature [8], energy availability-based scheduling algorithm was discussed which considers solar energy for increasing the lifetime of the nodes. In the study conducted earlier [9], the author used genetic algorithm towards the selection of power level, where efficient route is selected according to its power levels.
Multi-Constraint Adaptive Routing (MCAR) scheme was discussed in the study conducted earlier [10], which used a topology tree towards scheduling based on the energy of nodes. Similarly, in literature [11], energy-based partitioning scheme was presented for route selection.
An adaptive scheduling algorithm was presented in [12] which used location, activity and traffic conditions in scheduling the nodes with high lifetime. Similarly, in the study conducted earlier [13], the nodes were clustered according to their energy levels whereas the cluster head is selected based on its energy. In literature [14], scheduling was performed by adapting higher duty cycle and energy of nodes to reduce the retransmission.
In the study conducted earlier [15], the coverage problem was handled by adapting kalman filter which in turn improved the network lifetime as well. Similarly, a secure routing with game theoretic scheme was presented in [16]. This scheme is capable of reducing the power consumption, balance and traffic with the adaption of Elliptic Curve Cryptography (ECC).
Trust orient secure routing scheme was presented in literature [17] which inherits different features by including energy and trust to identify the least hop route. In this study, authentication was performed using key exchange process. Likewise, a trust-based model was presented earlier [18] which considers the persistence of correct behavior of nodes during route selection.
An optimal energy-based secure routing scheme was presented in [19] to reduce the consumption of energy by sensor nodes. In [20], a partitioning scheme was introduced towards lifetime maximization in WSN. The algorithm works based on energy consumption constrained routing method.
A lifetime maximization algorithm was presented in [21] which uses linear programming model to manage power level. An adaptive routing towards lifetime maximization in WSN was presented in [22] in which the method performed the routing based on tree and according to different parameters. The method considered the topology features of different neighbors, inter connection among various parts of the network and its power consumption.
Similarly, in literature [23], an efficient lifetime maximization algorithm was presented using solar energy towards agricultural sector. In the study conducted earlier [24], lifetime maximization in WSN was presented by adapting a hybrid routing approach. The method considered energy depletion and reduced the traffic during different sensors to maximize the lifetime. Data aggregation in WSN is approached via 3D Discrete Time Markov Chain (DTMC) model which monitors the conditions on different nodes and their queues about waiting data [25]. According to queue conditions in different active nodes, the method performs routing and data collection. Similarly, delay-based energy Efficient Flooding Algorithm (DEF) was presented in [26]. This method constructed a flood tree and diverted the traffic in different routes to maximize the energy efficiency. In the study conducted earlier [27], a slot assignment algorithm was proposed for Medium Access Control (MAC) layer which considers the traffic in different channels. According to the load, the method assigns the slots for different routes to perform data collection. Towards data aggregation, a reliable proliferation routing was presented in [28] with duty cycle. This method identifies the reliable route and randomly selects the routes to forward the data. Similarly, in [29], a two-step mobile data collection algorithm was presented earlier to select an adaptive route towards data collection. The method selects the route according to the traffic and the energy of routes. In literature [30], priority-based data collection algorithm was presented, where the method assigns priority according to the number of transmissions to classify the nodes and assign the priority of nodes.
The methods discussed above suffer from poor performance in scheduling and lifetime maximization.
3 Real Time Topology-Driven Cooperative Self Scheduling System Model
The proposed topology-driven model works in a cooperative and distributed model. Any source node, which has the data to be transmitted, searches for its duty cycle. At the cycle, the node identifies the list of sensors under working mode at the duty cycle, based on its previous records. With this information, a set of routes available is identified using the topology. The routes identified are then computed for route Life Support Measure (LSM). Finally, an optimal route is identified to transmit the data. The nodes present in the route are scheduled for working mode, whereas the remaining nodes are scheduled for sleep mode. The detailed approach is discussed in this section.
The working model of TDCSS scheme is displayed in Fig. 1 which contains various functional parts that are discussed in this section. The method monitors the arrival of new packet, based on which the routes are identified. Further, the method estimates the LSM measure for different routes. According to the value of measure, the method selects a single route following which the sensor nodes present in the route are scheduled to perform data transmission [31].
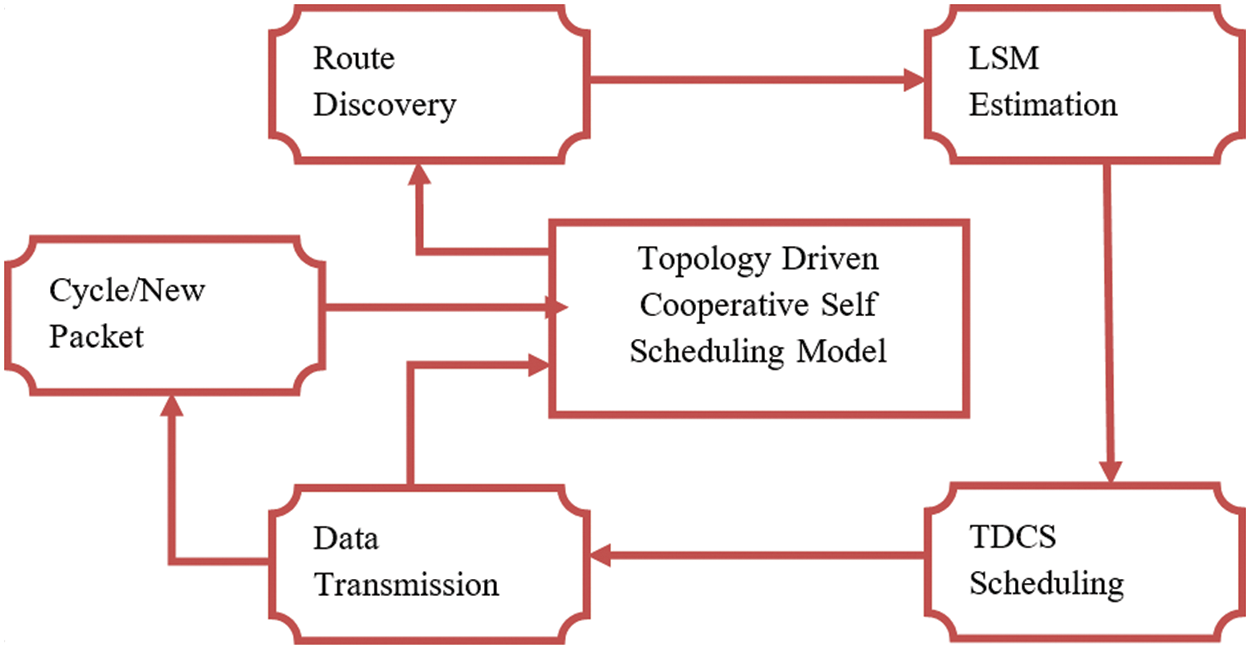
Figure 1: TDCSS system model
The central scheduler maintains the details of the topology and it shares the details to network sensors at the beginning. The initial data also contains information related to number of transmissions performed by any sensor and its respective state in previous duty cycle coupled with duration of duty cycle. Such information is flooded to the sensors of the network. Now, when a sensor receives a data to be transmitted, it computes the duty cycle time. Based on the computed value, it determines the time and cycle during when it should work. At that time, the topology constraints are used to identify the list of sensors that are awake for the cycle. Further, the constraints are also used to identify the routes available around sensors. After the routes have been identified, the value of LSM (Lifetime Support Measure) is computed. According to the estimated LSM values, a single route with maximum LSM is selected to perform data transmission.
Consider the initial packet P is received from the central scheduler. Then, the list of nodes present in the network are identified as follows.
Now, for any number of sensor nodes s, the node list contains sensor id, location and the number of transmission NT done and the current state is collected.
Based on Nlist details, at first, the list of routes that are awake are identified as given herewith.
The above equation identifies the list of wakeup nodes for current duty cycle, according to the previous state. If a sensor node slept in previous state, then it is considered during current duty cycle. From the list of wakeup nodes, the possible routes available to reach a sink are identified with a consideration that each sensor has the same transmission range.
Now, the list of routes through neighbors are identified using the equation given below.
The list of routes identified by the source is used to perform scheduling.
Now, for each route R, from RL, the method would compute the LSM value and a route with the maximum LSM value is selected. The selected route is then scheduled and the route list is given for scheduling the rest of the nodes.
The route given is measured for LSM, which shows the fitness of the route in achieving the maximum lifetime for WSN. LSM value is determined according to the number of transmissions by each sensor present in the route and their depletion of energy. Using these two values, the method computes the LSM for the route. The value of LSM is used to choose a single route to perform data transmission and scheduling.
Consider the route identified to be R, then the hop list of the route is identified as follows.
For each hop H, the list of transmission performed is measured as follows.
Similarly, the energy depletion of Hop H is measured as follows.
Using these two values of Tlist and Edr, the method computes the value of LSM.
The computed LSM value is used to perform route selection and scheduling.
Topology-driven cooperative self-scheduling algorithm is given a route which is identified by any source node at specific duty cycle. To complete the transmission of data, a source node identifies the list of sensor nodes according to their previous state. Based on the state and topology, a set of routes is identified. According to the LSM values, the source node selects an optimal route and give it to the scheduler. The scheduler, in turn, identifies the list of sensor nodes in the route and schedule them to whichever nodes that are in wakeup mode. Rest of the nodes around three hops are identified and scheduled under sleep mode. The concurrency control is performed according to the previous state and current state of the duty cycles. When a same node sa is scheduled to sleep by a source node s and another node s1 claims the node sa to wake up, then the scheduler adjusts the mode of the node. The update is given to the node, s. This makes the status of the nodes up to data and enables the scheduling to be performed efficiently.
TDCS Scheduling Algorithm
Given: Network Trace (NT), Route R, Route List Rl
Obtain: Null
Begin
Read the traces of network from NT.
For each node n from R
Set their status to wakeup.
n.status = wakeup.
End
Identify list of 3 hop neighbors of n as Nhl =
n.status = sleep and Send notifications.
End
Stop
The scheduler receives the list of routes and performs scheduling according to the previous state and the result of the source node.
The working process of the proposed Topology-Driven Cooperative Self Scheduling algorithm is shown in Fig. 2. This identifies the list of sensors nodes in the network to be awake, according to the condition of the previous duty cycle. Based on that, a topology is generated and identifies a set of routes. For each route identified, the method finds various features to measure the value of LSM. According to the LSM value, a single route is selected and scheduled to be in awake mode. However, rest of the nodes in the route, up to three hops, are notified to be present in sleep mode for current duty cycle. Based on the route identified, the method performs data transmission.
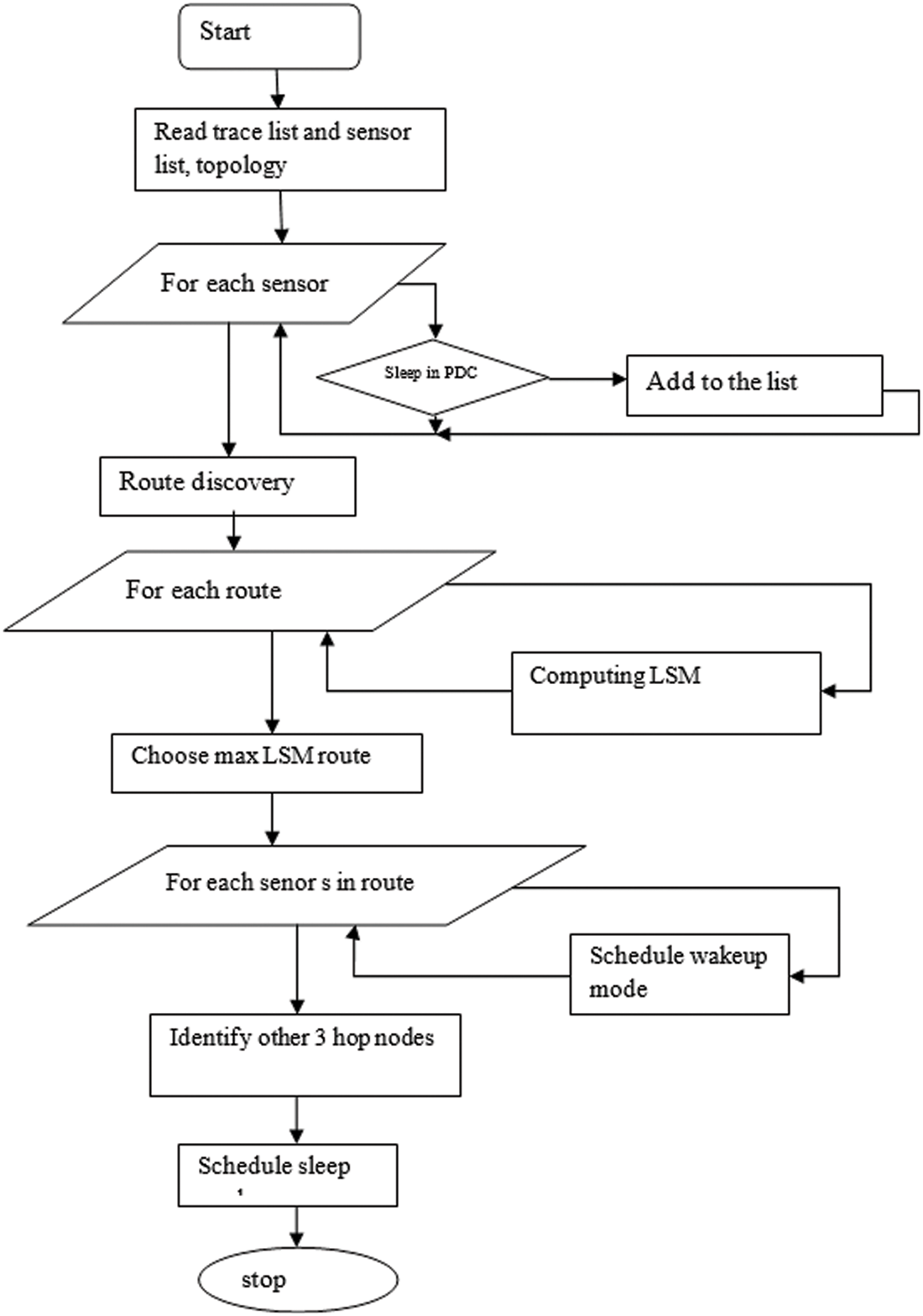
Figure 2: Flow chart of the proposed TDCSS model
Topology-driven cooperative self-scheduling schemes were simulated using NS2. The performance of the method was analyzed under different parameters and different simulation conditions and setup. The obtained results were then explored and compared against the results of other methods.
The simulation details, considered for the performance evaluation of the proposed scheme, is presented in Tab. 1.

The snapshot of initial topology and conditions, considered for the evaluation, is presented in Fig. 3. The node 0 was identified as a source whereas 8 was considered as destination node.
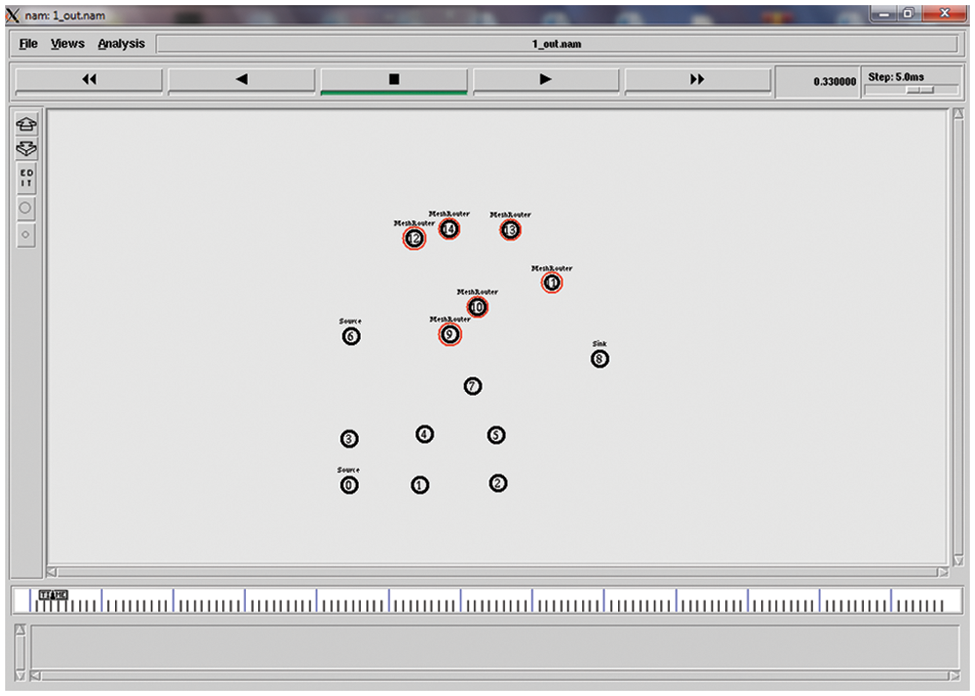
Figure 3: Snapshot of initial network condition and setup
The screen captured during data packet transmission between the nodes 0 and 8 is presented in Fig. 4. This schedules only the nodes that are required for data transmission whereas rest of the nodes were triggered to go under sleep mode.

Figure 4: Snapshot of the routing between the nodes, 0 and 8
The performance analysis of different algorithms was conducted for scheduling and the proposed TDCS approach achieved a high scheduling performance compared to other methods such as DHRP, EEBS, MCAR, and Energy Efficient Momento based Dynamic Scheduling Algorithm (EEMDS). Scheduling performance, achieved by different methods is measured in Tab. 2 and presented in Fig. 5. The TDCS scheme achieved an efficient scheduling compared to other techniques.
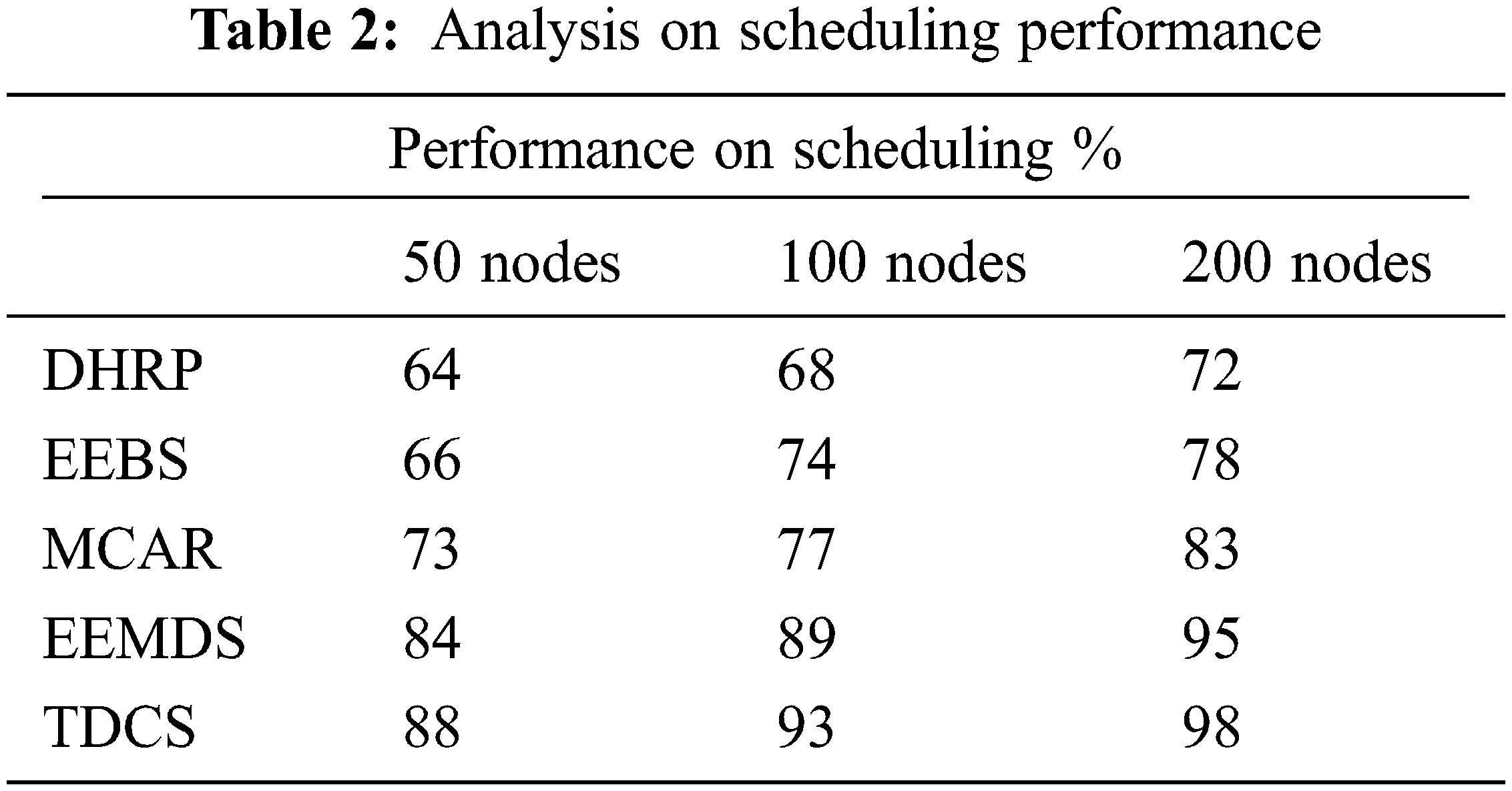

Figure 5: Analysis on scheduling performance
The achievement in throughput was measured for the number of methods and the results are presented in Tab. 3. Among the methods compared, the proposed TDCS scheme achieved the highest throughput under all the simulation conditions.

Throughput achievement was measured for all the methods considered and the results are presented in Fig. 6. TDCS scheme achieved the highest throughput under all simulation conditions.

Figure 6: Performance on throughput
Packet drop ratio, generated by different methods, was measured and compared and the results are shown in Tab. 4 and Fig. 7. TDCS scheme achieved less packet drop ratio in all the cases.


Figure 7: Analysis on drop ratio
The performance on lifetime maximization, introduced by different methods, was measured and the results are presented in Tab. 5 and Fig. 8. The proposed TDCS scheme produced excellent performance in terms of maximum lifetime support in all the cases than other methods.


Figure 8: Performance on lifetime maximization
Energy consumption and utilization, by different approaches, were measured and the results are presented in Tab. 6 and Fig. 9. The proposed TDCS algorithm consumed less energy compared to all other methods under all cases.
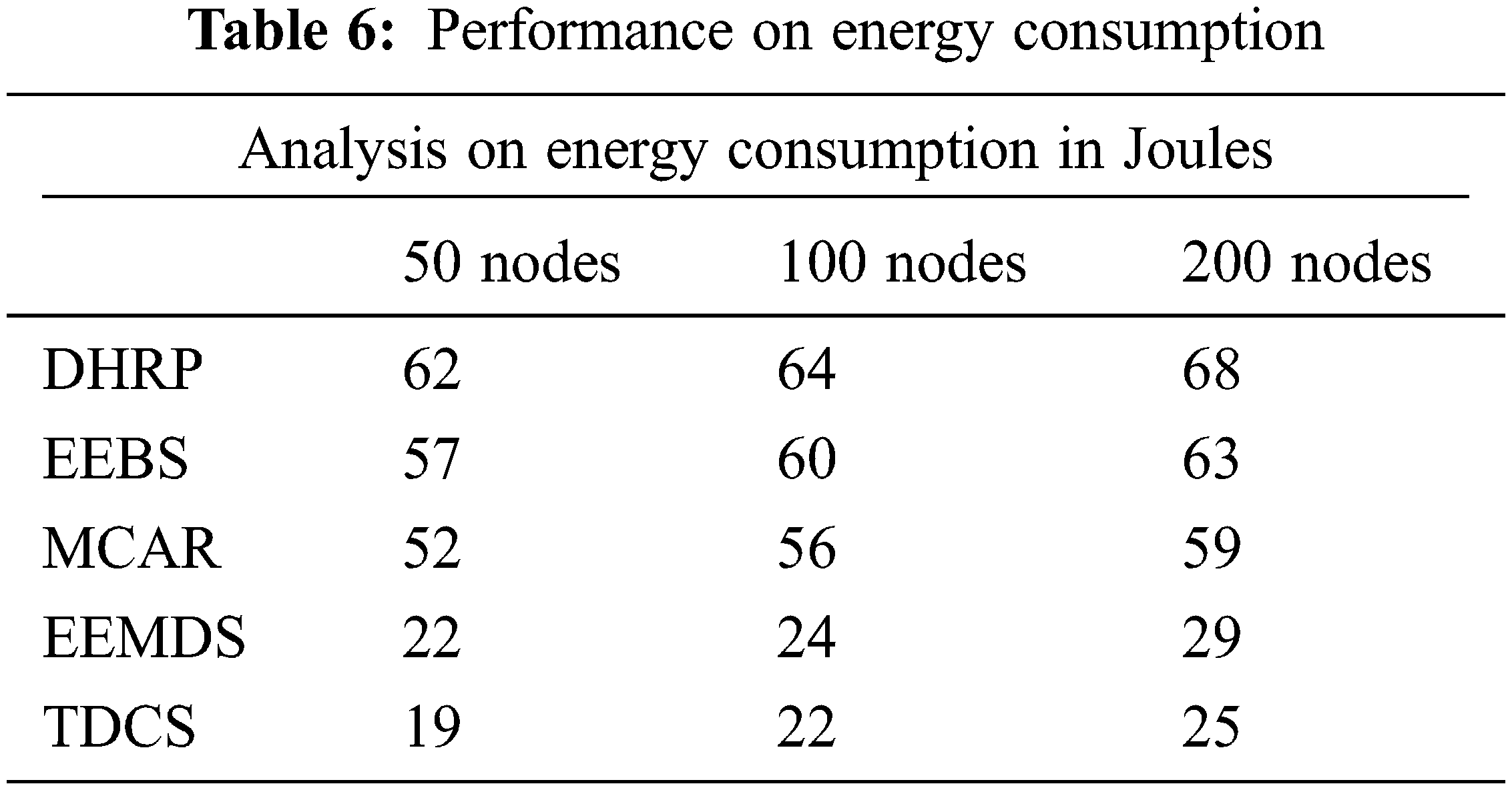

Figure 9: Performance on energy consumption
In current study, a dynamic topology-driven cooperative self-scheduling algorithm is presented. The source node has been provided with all topology constraints and transmission statistics at the beginning. With this information, the node can identify the idle sensors in previous duty cycle and the identified list of sensors are scheduled for current cycle. Based on this, a set of routes is identified. In every route, the method calculates the LSM value so that the best optimal route can be selected. After route selection, the sensors of the route are scheduled to be in wakeup mode. Further, the source provides the list of routes and the selected route to the scheduler. This scheduler schedules the remaining nodes that are not part of the selected route. The inclusion of the proposed model avoids unnecessary wakeup nodes for duty cycle, which improves the lifetime of the network. Further, it also can handle route scarcity problem by just sleeping with the rest of the nodes, only up to three hops. This helps in the scheduling of other nodes and support data transmission by other sources. Scheduling is performed in both the ways so that the overhead in scheduling is reduced along with route discovery. The proposed method improves the performance of QoS and increases the lifetime of entire network.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Y. Lu, T. Zhang, E. He and I. S. Comşa, “Self-learning-based data aggregation scheduling policy in wireless sensor networks,” Journal of Sensors, vol. 2018, pp. 1–12, 2018. [Google Scholar]
2. C. Feng, Z. Li, S. Jiang and W. Jing, “Delay-constrained data aggregation scheduling in wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 13, no. 6, pp. 155014771771659, 2017. [Google Scholar]
3. P. Neamatollahi, M. Naghibzadeh, S. Abrishami and M. Yaghmaee, “Distributed clustering-task scheduling for wireless sensor networks using dynamic hyper round policy,” IEEE Transactions on Mobile Computing, vol. 17, no. 2, pp. 334–347, 2018. [Google Scholar]
4. H. Liu, Q. Deng, S. Tian, X. Peng and T. Pei, “Recharging schedule for mitigating data loss in wireless rechargeable sensor network,” Sensors, vol. 18, no. 7, pp. 2223, 2018. [Google Scholar]
5. Z. Wang, Y. Chen, B. Liu, H. Yang, Z. Su et al., “A sensor node scheduling algorithm for heterogeneous wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 15, no. 1, pp. 155014771982631, 2019. [Google Scholar]
6. Q. Chen, T. Wang, L. Cheng, Y. Tao and H. Gao, “Energy-efficient broadcast scheduling algorithm in duty-cycled multihop wireless networks,” Wireless Communications and Mobile Computing, vol. 2019, pp. 1–14, 2019. [Google Scholar]
7. S. Kumar and H. Kim, “Energy efficient scheduling in wireless sensor networks for periodic data gathering,” IEEE Access, vol. 7, pp. 11410–11426, 2019. [Google Scholar]
8. S. Basagni, M. Y. Naderi, C. Petrioli, D. Spenza, “Wireless sensor networks with energy harvesting,” In Mobile ad hoc Networking: Cutting Edge Directions, Wiley-IEEE Press: Hoboken, NJ, USA, pp. 701–736, 2013. [Google Scholar]
9. F. Mansourkiaie, L. S. Ismail, T. M. Elfouly and M. H. Ahmed, “Maximizing lifetime in wireless sensor network for structural health monitoring with and without energy harvesting,” IEEE Access, vol. 5, pp. 2383–2395, 2017. [Google Scholar]
10. F. El Hajji, C. Leghris and K. Douzi, “Adaptive routing protocol for lifetime maximization in multi-constraint wireless sensor networks,” Journal of Communications and Information Networks, vol. 3, no. 1, pp. 67–83, 2018. [Google Scholar]
11. M. Z. Hasan, H. Al-Rizzo and M. Günay, “Lifetime maximization by partitioning approach in wireless sensor networks,” Journal of Communications and Information Networks, vol. 2017, no. 1, pp. 15, 2017. [Google Scholar]
12. D. S. Gangwar, S. Tyagi and S. K. Son, “Network lifetime maximization in wireless sensor network with multiple sink nodes,” Discovery, vol. 54, no. 271, pp. 284–290, 2018. [Google Scholar]
13. K. J. Elma and S. Meenakshi. “Energy efficient clustering for lifetime maximization and routing in WSN,” International Journal of Applied Engineering Research, vol. 13, no. 1, pp. 337–343, 2018. [Google Scholar]
14. J. Tan, A. Liu, M. Zhao, H. Shen and M. Ma, “Cross-layer design for reducing delay and maximizing lifetime in industrial wireless sensor networks,” EURASIP Journal on Wireless Communications and Networking, vol. 2018, no. 1, pp. 50, 2018. [Google Scholar]
15. N. A. A. Aziz, Z. Ibrahim, N. H. A. Aziz and K. A. Aziz, “Simulated kalman filter optimization algorithm for maximization of wireless sensor networks coverage,” in 2019 Int. Conf. on Computer and Information Sciences (ICCIS), Sakaka, Saudi Arabia, pp. 1–6, 2019. [Google Scholar]
16. H. Lazrag, R. Saadane and D. Aboutajdine. “A game theoretic approach for optimal and secure routing in WSN,” in Int. Afro-European Conf. for Industrial Advancement AECIA 2016: Proc. of the Third Int. Afro-European Conf. for Industrial Advancement—AECIA, Advances in Intelligent Systems and Computing, Cham, Springer, vol. 565, pp. 218–228, 2016. [Google Scholar]
17. K. Saini and P. Ahlawat, “A trust-based secure hybrid framework for routing in WSN,” Recent Findings in Intelligent Computing Techniques, Advances in Intelligent Systems and Computing Book Series (AISC), vol. 707, pp. 585–591, 2018. [Google Scholar]
18. G. M. N. Patil and P. I. Basarko, “Trust model for secure routing and localizing malicious attackers in WSN,” in Computing and Network Sustainability, Lecture Notes in Networks and Systems Book Series (LNNS), Singapore: Springer, vol. 12, pp. 1–9, 2017. [Google Scholar]
19. M. Kavitha and B. G. Geetha, “An efficient city energy management system with secure routing communication using WSN,” Cluster Computing, vol. 22, no. S6, pp. 13131–13142, 2019. [Google Scholar]
20. M. Noori, M. Ardakan, “Lifetime Analysis of Random Event-Driven Clustered Wireless Sensor Networks,” IEEE Trans. Mob. Comput., vol. 10, pp. 1448–1458, 2011. [Google Scholar]
21. H. Xu, X. Jin, F. Kong and Q. Deng, “Maximizing the lifetime of wireless sensor networks in trains for monitoring long-distance goods transportation,” International Journal of Distributed Sensor Networks, vol. 13, no. 5, pp. 155014771770789, 2017. [Google Scholar]
22. P. Zhong, F. Ruan, “An energy efficient multiple mobile sinks based routing algorithm for wireless sensor networks,” In IOP Conference Series: Materials Science and Engineering, IOP Publishing, vol. 323, no. 1, pp. 012029, 2018. [Google Scholar]
23. H. Sharma, A. Haque and Z. A. Jaffery, “Maximization of wireless sensor network lifetime using solar energy harvesting for smart agriculture monitoring,” Ad Hoc Networks, vol. 94, pp. 101966, 2019. [Google Scholar]
24. A. E. A. A. Abdulla, H. Nishiyama and N. Kato, “Extending the lifetime of wireless sensor networks: A hybrid routing algorithm,” Computer Communications, vol. 35, no. 9, pp. 1056–1063, 2012. [Google Scholar]
25. L. Guntupalli, J. M. Bauset, F. Y. Li and M. A. Weitnauer, “Aggregated packet transmission in duty-cycled wsns: Modeling and performance evaluation,” IEEE Transactions on Vehicular Technology, vol. 66, no. 1, pp. 563–579, 2017. [Google Scholar]
26. S. Wu, J. Niu, W. Chou and M. Guizani, “Delay-aware energy optimization for flooding in duty-cycled wireless sensor networks,” IEEE Transactions on Wireless Communications, vol. 15, no. 12, pp. 8449–8462, 2016. [Google Scholar]
27. S. Zhuo, Z. Wang, Y. Q. Song, Z. Wang and L. Almeida, “A traffic adaptive multi-channel mac protocol with dynamic slot allocation for WSNs,” IEEE Transactions on Mobile Computing, vol. 15, no. 7, pp. 1600–1613, 2016. [Google Scholar]
28. Venkatesha, T. N. Ashwini, A. L. Akshay, V. Tejaswi, K. R. Venugopal, S. S. Iyengar, L. M. Patnaik, “RPRDC: Reliable proliferation routing with low duty-cycle in wireless sensor networks,” Procedia Computer Science, vol. 54, pp. 37–46, 2015. [Google Scholar]
29. C. Wang, S. Guo and Y. Yang, “An optimization framework for mobile data collection in energy-harvesting wireless sensor networks,” IEEE Transactions on Mobile Computing, vol. 15, no. 12, pp. 2969–2986, 2016. [Google Scholar]
30. S. Say, H. Inata, J. Liu and S. Shimamoto, “Priority-based data gathering framework in UAV-assisted wireless sensor networks,” IEEE Sensors Journal, vol. 16, no. 14, pp. 5785–5794, 2016. [Google Scholar]
31. K. Dinakaran, D. Rajalakshmi and P. Valarmathie, “Efficient pattern matching for uncertain time series data with optimal sampling and dimensionality reduction,” Microprocessors and Microsystems, vol. 75, pp. 103057, 2020. [Google Scholar]
Cite This Article
 Copyright © 2023 The Author(s). Published by Tech Science Press.
Copyright © 2023 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools