DOI:10.32604/csse.2023.029356

| Computer Systems Science & Engineering DOI:10.32604/csse.2023.029356 |  |
| Article |
Secure e-Prescription Management System: Mitigating Blended Threat in IoBE
1ISAA Lab., Institute for Information and Communication, Ajou University, Suwon, 16499, Korea
2Korea Orphan & Essential Drug Center (KOEDC), Seoul, 04523, Korea
3Department of Cyber Security, Ajou University, Suwon, 16499, Korea
*Corresponding Author: Jin Kwak. Email: security@ajou.ac.kr
Received: 01 March 2022; Accepted: 06 April 2022
Abstract: New information and communication technologies (ICT) are being applied in various industries to upgrade the value of the major service items. Moreover, data collection, storage, processing, and security applications have led to the creation of an interrelated ICT environment in which one industry can directly influence the other. This is called the “internet of blended environments” (IoBE), as it is an interrelated data environment based on internet-of-things collection activities. In this environment, security incidents may increase as size and interconnectivity of attackable operations grow. Consequently, preemptive responses to combined security threats are needed to securely utilize IoBE across industries. For example, the medical industry has more stringent information protection measures than other industries. Consequently, it has become a major target of attackers, as more clinician–patient interactions occur over the internet owing to COVID-19. Therefore, this study aims to acquire security for IoBE while focusing on the medical industry. Among the various types of medical ICT services, this study analyzes data flow and potential security threats from the e-prescription lifecycle perspective, which is highly utilized, strongly data-centric, and has numerous security issues. Based on our analysis, we propose a secure authentication and data-sharing scheme.
Keywords: Authentication scheme; blended threat; e-prescription; internet of blended environments
With the continuous development of information and communication technologies (ICTs), new internet of things (IoT) devices, cloud-based storage and operations, big data and business intelligence services, mobile applications, and artificial intelligence (AI) models are continuously emerging. Notably, these technologies are being utilized in a more interrelated, blended manner than ever and have enabled data convergence among the formerly segregated industrial fields [1,2]. This new environment is called the “internet of blended environment” (IoBE), and it adds layers of complexity to security risks as the interconnectivity of attackable data-dependent operations grow [3]. Thus, new types of security threats are being identified. Therefore, studies to create a secure IoBE must be urgently conducted.
From the several complex security risks that spread across the IoBE, the current study focuses on the medical industry, which regularly creates, manipulates, and stores sensitive patient data. Hence, the medical industry has the largest damage potential and has become a major target of the attackers, as an increasing number of clinician–patient interactions are taking place over the internet owing to COVID-19 restrictions [4].
Among the plethora of data-heavy medical services, the current study focuses on the e-prescription system, which is heavily targeted by cybercriminals [5,6], and incident rates are continuously increasing. For example, in one incident, approximately 700 million patient and prescription records were compromised, and at least 400 million were confirmed as sold. In another incident, approximately 78 million prescription records were illegally harvested and sold to pharmacies as contact information.
Therefore, this study analyzes various security threats affecting the generation, collection, and processing of e-prescription data to provide a sharing and authentication scheme to improve IoBE security.
The rest of this paper is organized as follows. Section 2 provides an overview of the e-prescription system and analyzes the security risks that may occur in the analyzed environment. Section 3 proposes a secure sharing and authentication scheme for the e-prescription system. Section 4 verifies the proposed authentication and data-sharing technology, and Section 5 presents our conclusions.
The e-prescription system allows clinicians and patients to avoid handling paper prescriptions and dealing with clinician-to-pharmacy coordination and printing. In the legacy prescription process, patients receive a paper prescription after diagnosis and obtain medications and equipment at a separate dispensary. However, paper prescriptions face counterfeiting, forgery, and loss/theft risks. To overcome these problems, e-prescription methods that electronically manage prescriptions have recently received great attention. With the ubiquity and lowering costs of ICT and the rapid utilization of smart devices, the construction of e-prescription systems is accelerating. However, with fast growth comes great risk, as the medical information handled on such networks is among the most sensitive in all e-commerce. See the examples in Tab. 1. When medical information is leaked, patient privacy is violated, and they encounter added personal risks. Hence, focusing on the e-prescription aspect, potent and quickly available security measures are needed.

2.2 Security Threats in the E-Prescription System
In this section, e-prescription system security risks are presented and analyzed [7]. Agents that participate in e-prescription processes consist of patients, clinicians, pharmacists, and e-prescription management center (ePMC) agents who manage cloud-based services. The security threats and mitigation requirements of e-prescription activities per agent are summarized in Tab. 2. Furthermore, the roles of each are explained as follows:
• Patients: Patients engage clinicians to receive diagnoses and treatment options via an e-prescription, and they receive medications and equipment from pharmacists accordingly. A patient may request changes to their prescription options using the e-prescription system after full authentication.
• Clinicians: Clinicians fully authenticate their identity on the e-prescription system to provide patients with medical services and prescriptions.
• Pharmacists: Pharmacists fully authenticate their identity on the e-prescription system to dispense drugs according to the corresponding prescription.
• ePMC agents: ePMC agents fully authenticate their identity on the e-prescription system so that patients, doctors, and pharmacists can perform their roles. ePMC agents also manage the storage, modification, deletion, and recovery of e-prescriptions, and they generate unique codes and verify validity periods, availability, and other authentication activities.

2.2.1 Analysis of the E-Prescription Issuance Process
The e-prescription issuance process is detailed next so that the phases of security threats in Tab. 2 can be further analyzed [8,9].
❑ Entire process for issuing e-prescription
Step 1: Patient authenticates and receives treatment from clinician.
Step 2: Clinician sends e-prescription to ePMC agent.
Step 3: ePMC agent generates an e-prescription code.
Step 4: ePMC agent stores/manages e-prescription and code.
Step 5: ePMC agent sends e-prescription code to patient.
Step 6: Patient presents the e-prescription code to pharmacist.
Step 7: Pharmacist sends e-Prescription code to ePMC agent for verification.
Step 8: ePMC agent verifies the e-prescription code.
Step 9: ePMC agent sends e-prescription authorization to pharmacist.
Step 10: Pharmacist dispenses prescribed medications or equipment.
Step 11: Pharmacist sends e-prescription processing results to ePMC agent.
Step 12: ePMC agent updates the e-prescription processing result.
❑ Patient-to-hospital process for issuing e-prescription
Step 1: Patient requests treatment from a clinician.
Step 2: Clinician requests patient authentication.
Step 3: Patient authenticates to prove their identity.
Step 4: Clinician treats patient.
Step 5: Clinician requests ePMC agent issuance of e-prescription.
Step 6: ePMC agent requests clinician authentication.
Step 7: Clinician authenticates to prove their identity.
Step 8: ePMC agent issues e-prescription.
Steps 9~11: ePMC agent manages e-prescription code/stores and manages e-prescription and code/sends e-prescription code. See entire process for issuing e-prescription.
❑ Patient-to-pharmacy process for issuing e-prescription
Step 1~2: Patient presents e-prescription code/requests inquiry of e-prescription code. This is identical to the corresponding process for issuing e-prescription.
Step 3: ePMC agent requests authentication of pharmacist.
Step 4: Pharmacist authenticates to prove their identity.
Steps 5~9: Pharmacist sends e-prescription code/sends e-prescription/provides prepared medicines or equipment/sends e-prescription processing result; ePMC agent updates e-prescription processing result. This is identical to the corresponding process for issuing e-prescription.
❑ Patient-to-ePMC process for issuing e-prescription
Step 1: Patient requests e-prescription inquiry of ePMC agent.
Step 2: ePMC agent requests authentication of patient.
Step 3: Patient authenticates to prove identity.
Step 4: ePMC agent examines patient’s e-prescription.
Step 5: ePMC agent provides the content the of e-prescription to the patient.
Step 6: ePMC agent takes necessary action (modification, deletion, or recovery).
Step 7: ePMC agent updates the e-prescription processing result.
2.2.2 Detailed Analysis of Security Threats for E-Prescription Issuance Process
In the e-prescription issuance process analyzed in Section 2.2.1, security threats exist in the process of sending and receiving information (e.g., issuances, transfers, and inquiries). The risk areas are expanded in Tabs. 3–6.




The e-prescription system security threats (Fig. 1) are shown in Tab. 3.

Figure 1: Entire process for issuing e-prescription
In Step 1, the exchange of patient authentication information is threatened by sniffing, falsification, spoofing, reuse, and repudiation attacks, and invasion of privacy is possible due to the leakage of sensitive information.
In Step 2, the exchange of clinician authentication information and the issuance of e-prescriptions are threatened by sniffing, falsification, spoofing, reuse, and repudiation attacks, and invasion of privacy is possible.
In Step 5, the issuance of a unique e-prescription code issued by the ePMC agent is threatened by sniffing, falsification, reuse, and repudiation. In this case, spoofing and invasion of privacy are not considered, as the ePMC agent is a trusted agent, and the unique e-prescription code does not contain sensitive information.
In Step 7, the exchange of pharmacist authentication information and e-prescription code requests is threatened by sniffing, falsification, spoofing, reuse, and repudiation attacks.
In Step 9, the exchange of e-prescription information is threatened by sniffing, falsification, reuse, and repudiation attacks, and invasion of privacy is possible. Spoofing is not considered in this case, as the ePMC agent is a trusted agent.
In Step 11, the exchange of e-prescription processing results is threatened by sniffing, falsification, and spoofing attacks.
The security threats of the patient-to-clinician e-prescription issuance exchange in Fig. 2 are detailed in Tab. 4. The authsentication threats of Steps 3 and 7 are identical to those of Steps 1 and 2 in Tab. 3. The e-prescription issuance security threats in Step 8 are identical to those of Step 2 in Tab. 3. The e-prescription code transmission threats of Step 11 are identical to those of Step 5 in Tab. 3.

Figure 2: Patient-to-hospital process for issuing e-prescription
The security threats of the patient-to-pharmacist e-prescription issuance process in Fig. 3 are detailed in Tab. 5. The e-prescription code threats in Steps 2 and 4 are identical to those of Step 7 in Tab. 3. However, Step 2 is not considered as it does not have a privacy invasion risk. The e-prescription transmission threats in Step 6 are identical to those of Step 9 in Tab. 3. The e-prescription processing result exchange threats in Step 8 are identical to those of Step 11 in Tab. 3.

Figure 3: Patient-to-pharmacy process for issuing e-prescription
The security threats of the patient-to-ePMC agent e-prescription issuance process in Fig. 4 are detailed in Tab. 6. The patient authentication threats in Step 3 are identical to those of Step 1 in Tab. 3. The e-prescription issuance process of Step 5 is identical to those of Step 9 in Tab. 3, which can occur when the e-prescription is transmitted. In Step 6, threats of sniffing, falsification, spoofing, reuse, and repudiation attacks for patient requests to the ePMC agent also exist.
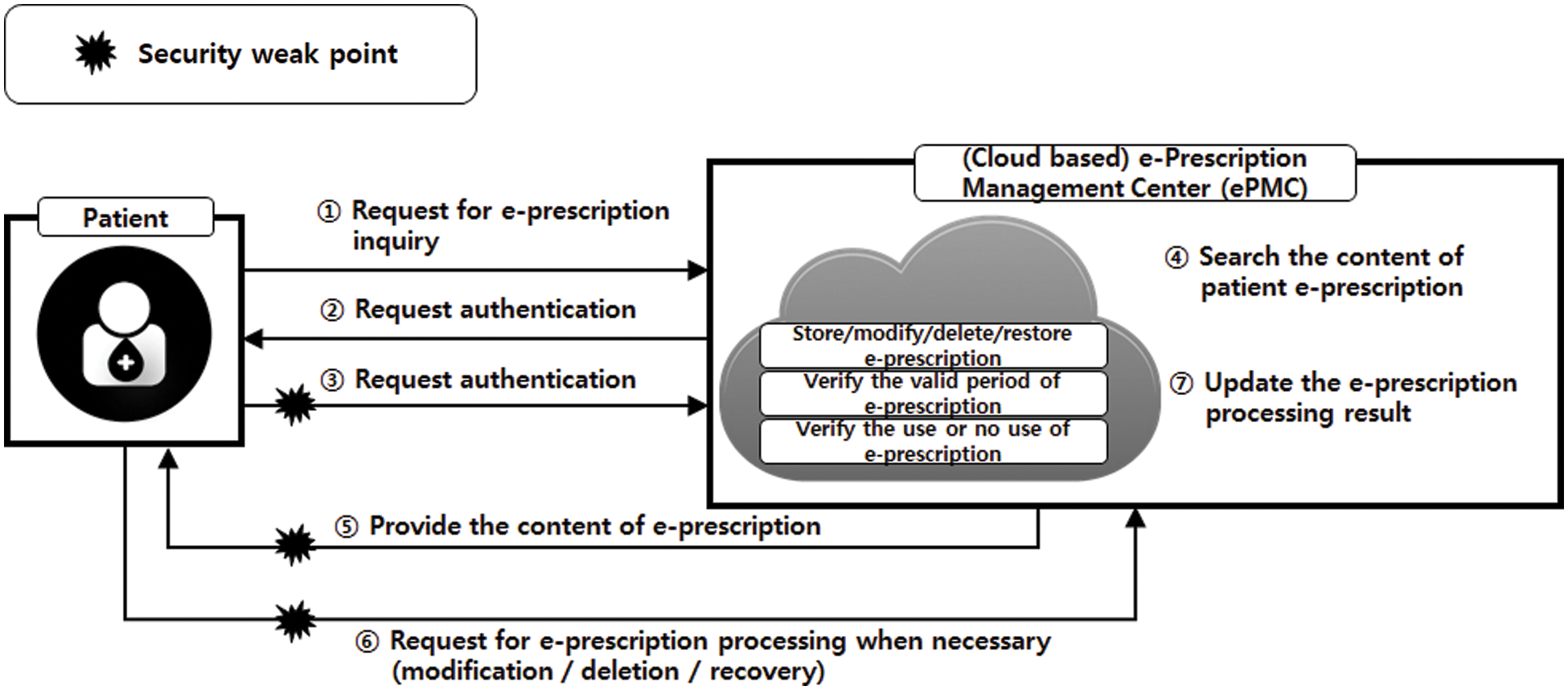
Figure 4: Patient-to-ePMC process for issuing e-prescription
From this mapping, the proposed protection scheme can now be illustrated.
In this section, a more secure e-prescription management scheme is proposed according to the issuance requirements of each entity (agent). The entities participating in the e-prescription system consist of patients, clinicians, pharmacists, and ePMC agents. They are set as entities, depending on the similarity of the authentication and e-prescription-related processing behaviors of the analyzed processes. The scheme is executed by the ePMC agent, who manages the overall e-prescription process. There are three subprocesses: registration phase, authentication phase, and data transfer phase. Tab. 7 shows the notations used.

Fig. 5 shows the registration phase proposed to perform authentication between entities comprising the e-prescription issuance and processing, and the process is described below.
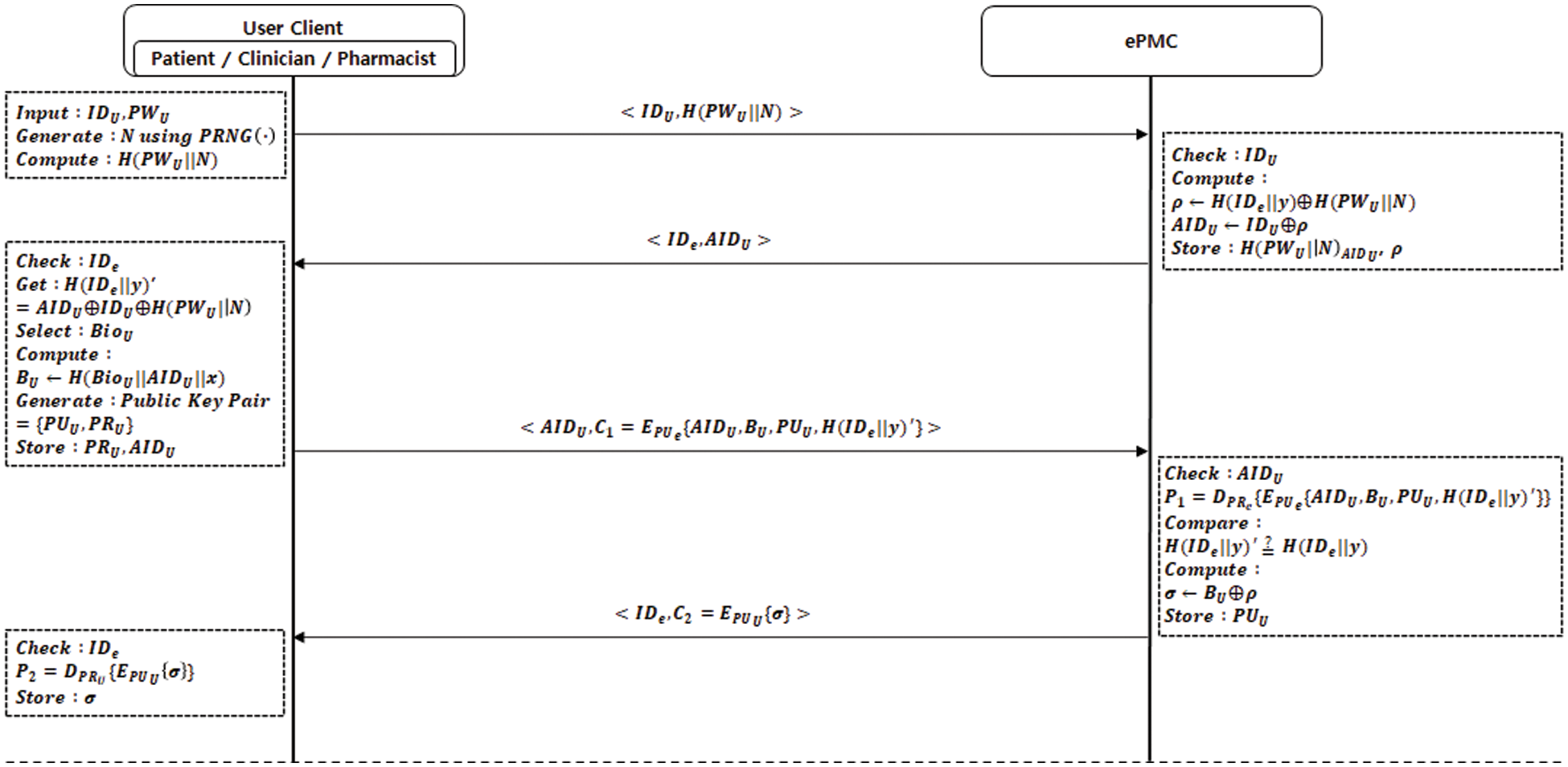
Figure 5: Registration phase in our scheme
Step 1. [User client sends <
The user client inputs
Step 2. [ePMC checks
The ePMC checks the identifier
Then, the
Afterward, the ePMC stores the
Step 3. [User client checks
The user client checks the ePMC’s identifier,
Then, the user client selects their biometric information,
Then, the user client generates their public key pair
Step 4. [ePMC checks
The ePMC checks the anonymous identifier,
Afterward, the ePMC stores the public key,
Step 5. [User client checks
The user client checks the ePMC’s identifier,
Fig. 6 shows the authentication phase proposed to perform authentication between entities comprising the issuance and processing of e-prescriptions, and the process is described below.
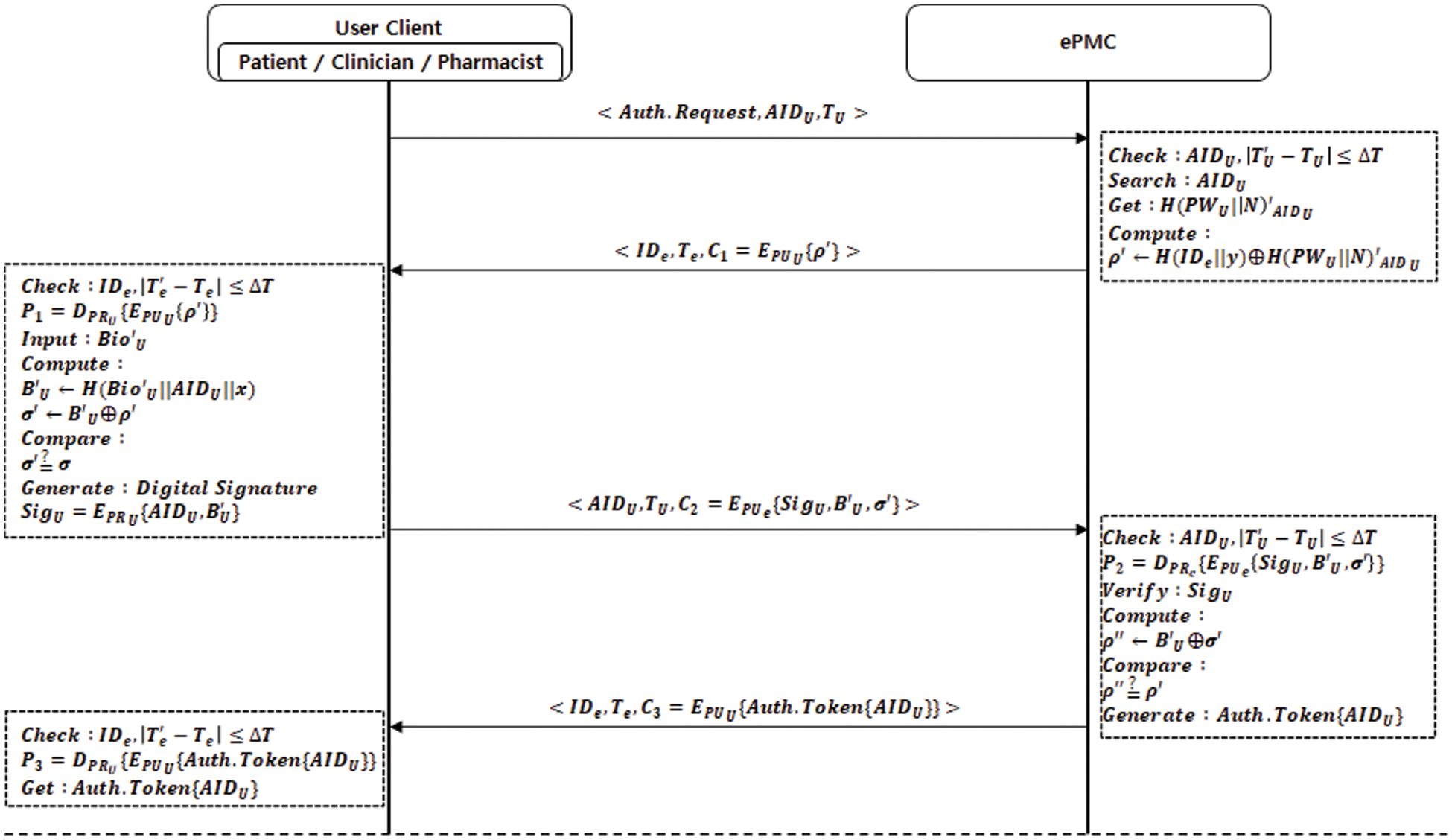
Figure 6: Authentication phase in our scheme
Step 1. [User client sends <
To request authentication, the user client sends their anonymous identifier,
Step 2. [ePMC checks
The ePMC checks the validity of the user client’s anonymous identifier,
Afterward, the ePMC sends
Step 3. [User client checks
The user client checks the validity of the ePMC’s identifier,
Furthermore, the user client computes another authentication challenge value,
After comparing and verifying the computed
Step 4. [ePMC checks
The ePMC checks the validity of the user client’s anonymous identifier,
The ePMC then compares and verifies the computed
Step 5. [User client checks
The user client checks the validity of the ePMC’s identifier,
Fig. 7 shows the data transfer phase proposed to perform data storage and request among entities comprising the issuance and processing of e-prescriptions, and the process is described below.
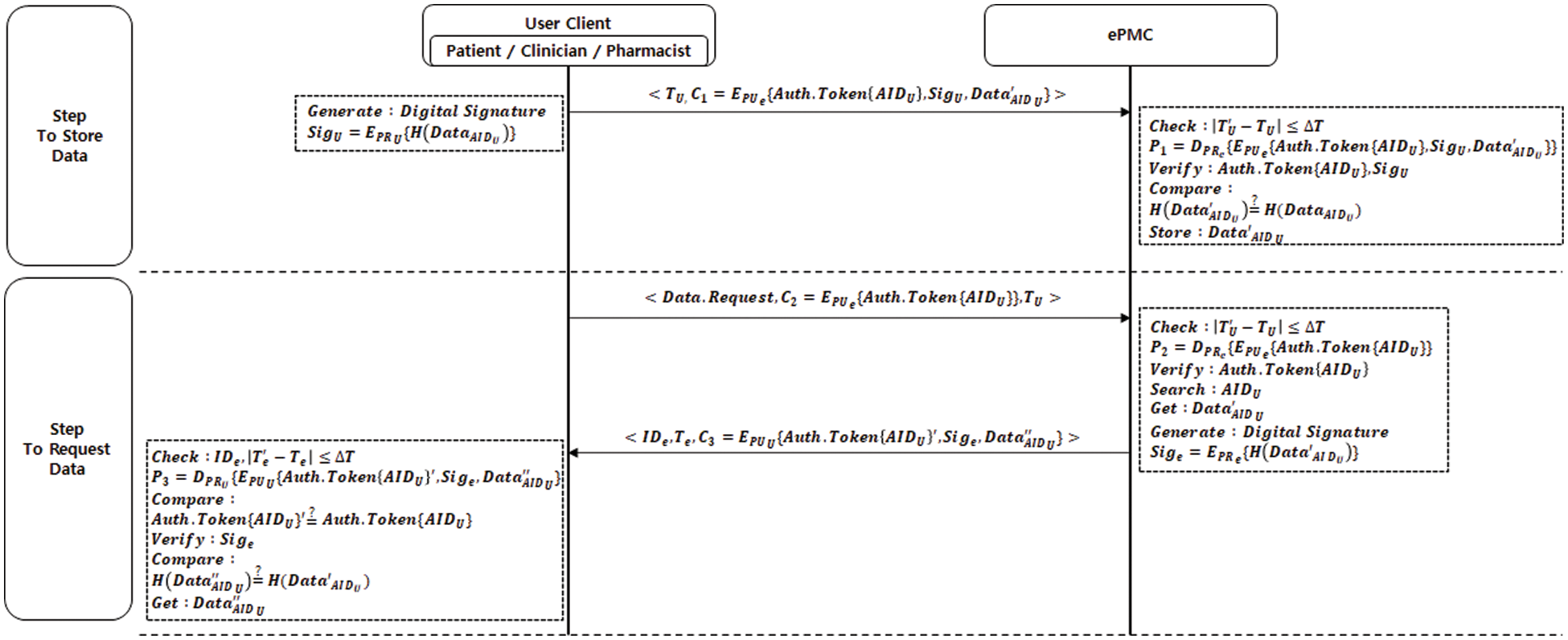
Figure 7: Data transfer phase in our scheme
3.3.1 Data Transfer Process to Store Data (Step to Store Data)
Step 1. [User client sends <
To store data at the ePMC, the user client generates the electronic signature value,
Step 2. [ePMC checks
The ePMC checks the validity of the user client’s time stamp value,
3.3.2 Data Transfer Process to Request Data (Step to Request Data)
Step 1. [User client sends <
To request data, the user client sends
Step 2. [ePMC checks
The ePMC checks the validity of the user client’s time-stamp value,
Afterward, the ePMC generates the electronic signature value,
Step 3. [User client checks
The user client checks the validity of the ePMC identifier,
4 Security Analysis of the Proposed Scheme
In this section, a security analysis is performed to respond to the analyzed security threats of the e-prescription system.
4.1 Information Sniffing Prevention
Exchanged information can be leaked through data-packet sniffing during the authentication and data-transfer phases. To prevent this, the proposed scheme applies public key encryption using
4.2 Information Falsification Prevention
Data can be falsified by attackers during authentication and data-transfer phases or as a result of errors during data communication. This presents reliability problems for the generated data collected and processed by the e-prescription system. During authentication, attackers can obtain the client’s anonymous identifier,
4.3 Entity Spoofing Prevention
When data are generated, collected, and processed from unauthorized entities, the reliability problem of the e-prescription system is exacerbated, and violations occur. To prevent this, the proposed scheme performs mutual authentication during registration and authentication phases. In particular, Fast IDentity Online (FIDO) authentication is applied to prevent threats in network and physical environments, such as when agents steal a clinician’s computer to issue illegal e-prescriptions.
Consequently, the biometric authentication element,
A user client who uses the e-prescription system may repudiate e-prescription data reception. Consequently, authentication and data-transfer phases are carried out using the digital signature value,
4.5 Prevention of Information Reuse
Attackers can cause availability violations in authentication and data processing using retransmission attacks on data exchanged between entities during authentication or data-transfer phases. Attackers can sniff information containing an
4.6 Privacy Invasion Prevention
The ripple effect is high when data are leaked from the e-prescription system because it uses sensitive data. Furthermore, when FIDO is used, the biometric information is replicated in the user client’s smart devices. Hence, privacy invation can occur if the user client’s biometric information leaks during authentication. Therefore, the user client’s anonymous identifier,
This study proposed an authentication and data-sharing scheme for agents using a centralized data management center for an e-prescription system and verified its potential security capability. The innovative capability provided by this study improves the security of the growing e-prescription system in the medical industry. The security of medical services has been long-researched [10], but most studies viewed data flow in scope that was too large. Hence, detailed response measures to potential security threats were insufficient. Moreover, with the application of many new technologies, the surface area of attack has become larger, and the attack paths have become more diversified. Thus, a more advanced response to security threats is needed. Moreover, in countries with advanced medical welfare programs, such as Australia and Sweden, related information used in medical information management systems is transmitted and managed through centralized data management centers operated by the state. The innovations provided by this tudy will improve the security and efficiency of these systems over legacy medical service institutions. The security of medical services can be secured by preventing illegal access and leakage of medical information via proper authentication and data-sharing capabilities. Furthermore, the safety and security provided by e-prescription system services can be enhanced by constructing a centralized data management-centric environment and acquiring security techniques based on the proposals of this study. This study is expected to contribute to the security of IoBE worldwide by considering multi-industry linkages.
Funding Statement: This work was supported by the National Research Foundation of Korea (NRF) grant funded by the Korea government (MSIT; No. 2021R1A2C2011391).
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. V. S. Naresh, S. S. Pericherla, P. S. R. Murt and S. Reddi, “Internet of Things in healthcare: Architecture, applications, challenges, and solutions,” Computer Systems Science and Engineering, vol. 35, no. 6, pp. 411–421, 2020. [Google Scholar]
2. H. Su, X. Yuan, Y. Tang, R. Tian, E. Sun et al., “A learning-based power control scheme for edge-based eHealth IoT systems,” KSII Transactions on Internet and Information Systems, vol. 15, no. 12, pp. 4385–4399, 2021. [Google Scholar]
3. M. Lee, J. Jang-Jaccard and J. Kwak, “Novel architecture of security orchestration, automation and response in internet of blended environment,” Computers, Materials & Continua, 2022. http://dx.doi.org/10.32604/cmc.2022.028495. [Google Scholar]
4. Q. A. Bui, W. B. Lee, J. S. Lee, H. L. Wu and J. Y. Liu, “Biometric-based key management for satisfying patient’s control over health information in the HIPAA regulations,” KSII Transactions on Internet and Information Systems, vol. 14, no. 1, pp. 437–454, 2020. [Google Scholar]
5. M. Samadbeik, M. Ahmadi, F. Sadoughi and A. Garavand, “A comparative review of electronic prescription systems: Lessons learned from developed countries,” Journal of Research in Pharmacy Practice, vol. 6, no. 1, pp. 3–11, 2017. [Google Scholar]
6. N. Noorbakhsh-Sabet, R. Zand, Y. Zhang and V. Abedi, “Artificial intelligence transforms the future of health care,” The American Journal of Medicine, vol. 132, no. 7, pp. 795–801, 2019. [Google Scholar]
7. D. Kim and J. Kwak, “A Framework for preventing illegitimate e-prescribing practices,” in Advances in Computer Science and Ubiquitous Computing:CSA-CUTE 17, Singapore: Springer, pp. 648–653, 2018. [Google Scholar]
8. D. Kim and J. Kwak, “The framework of 3P-based secure ehealth-information system,” in Proc. IEEE Int. Conf. on Platform Technology and Service (PlatCon), Jeju, Republic of Korea, pp. 1–6, 2018. [Google Scholar]
9. D. Kim and J. Kwak, “A study on secure information flow control in centralized ehealth-information system,” in Proc. 12th Asia Pacific Int. Conf. on Information Science and Technology (APIC-IST), Chiang Mai, Thailand, pp. 120–122, 2017. [Google Scholar]
10. X. Liu, Y. Li., J. Qu and Y. Ding, “A lightweight pseudonym authentication and key agreement protocol for multi-medical server architecture in TMIS,” KSII Transaction on Internet and Information Systems, vol. 11, no. 2, pp. 924–944, 2017. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |