DOI:10.32604/csse.2023.028269

| Computer Systems Science & Engineering DOI:10.32604/csse.2023.028269 |  |
| Article |
Hierarchical Data Aggregation with Data Offloading Scheme for Fog Enabled IoT Environment
1Department of Computer Science and Engineering, Kings College of Engineering, Punalkulam, 613303, Tamilnadu, India
2Department of Computer Science and Engineering, University College of Engineering, Ariyalur, 621704, Tamilnadu, India
*Corresponding Author: P. Nalayini. Email: nalav79@gmail.com
Received: 06 February 2022; Accepted: 10 March 2022
Abstract: Fog computing is a promising technology that has been emerged to handle the growth of smart devices as well as the popularity of latency-sensitive and location-awareness Internet of Things (IoT) services. After the emergence of IoT-based services, the industry of internet-based devices has grown. The number of these devices has raised from millions to billions, and it is expected to increase further in the near future. Thus, additional challenges will be added to the traditional centralized cloud-based architecture as it will not be able to handle that growth and to support all connected devices in real-time without affecting the user experience. Conventional data aggregation models for Fog enabled IoT environments possess high computational complexity and communication cost. Therefore, in order to resolve the issues and improve the lifetime of the network, this study develops an effective hierarchical data aggregation with chaotic barnacles mating optimizer (HDAG-CBMO) technique. The HDAG-CBMO technique derives a fitness function from many relational matrices, like residual energy, average distance to neighbors, and centroid degree of target area. Besides, a chaotic theory based population initialization technique is derived for the optimal initial position of barnacles. Moreover, a learning based data offloading method has been developed for reducing the response time to IoT user requests. A wide range of simulation analyses demonstrated that the HDAG-CBMO technique has resulted in balanced energy utilization and prolonged lifetime of the Fog assisted IoT networks.
Keywords: Internet of things; fog computing; barnacles mating optimizer; data offloading; data aggregation
IoT is an emerging technology in Information and Technology (IT) [1]. It is a group of internet-connected embedding devices which can able to sense and transmit information from one place to other without human intervention [2]. IoT refers to things that are interconnected to the internet through transmission technology including near field communication, wireless sensor network, Bluetooth, and radio frequency identification. IoT gives a number of advantages in each aspect of human life. IoT application includes industrial Internet, smart homes, smart cities, smart supply chains, smart grids, connected health, wearables, connected cars, smart retail, smart farming, and so on [3]. With the increasing demand for user applications, transmission technology plays a significant role in computing services. Fog computing is a transmission-support model that expands cloud service and application to the network edge. The user under the network edge utilizes the application, platform, and service of cloud service in an interoperable way [4]. A fog layer is widely deployed among the user plane and the cloud to ease access, service sharing, and computing prospects. Fog is a decentralized computing model developed for avoiding latency problems in cloud resource sharing and allocation. Like cloud layer, the fog layer comprises devoted gateways and servers for accepting user requests and processing them. The device includes switches, routers, access points, and servers with smart computing capability are the element of fog layer [5]. The incorporation of multilevel service and computing paradigms enhances the reliability of the transmission method. Nonetheless, data processing and resolving difficult problems remains a challenge in accomplishing appropriate optimization. Decision-making and Processing techniques and algorithms are required to enhance the optimization rate. Fig. 1 illustrates the process of fog enabled IoT environment.
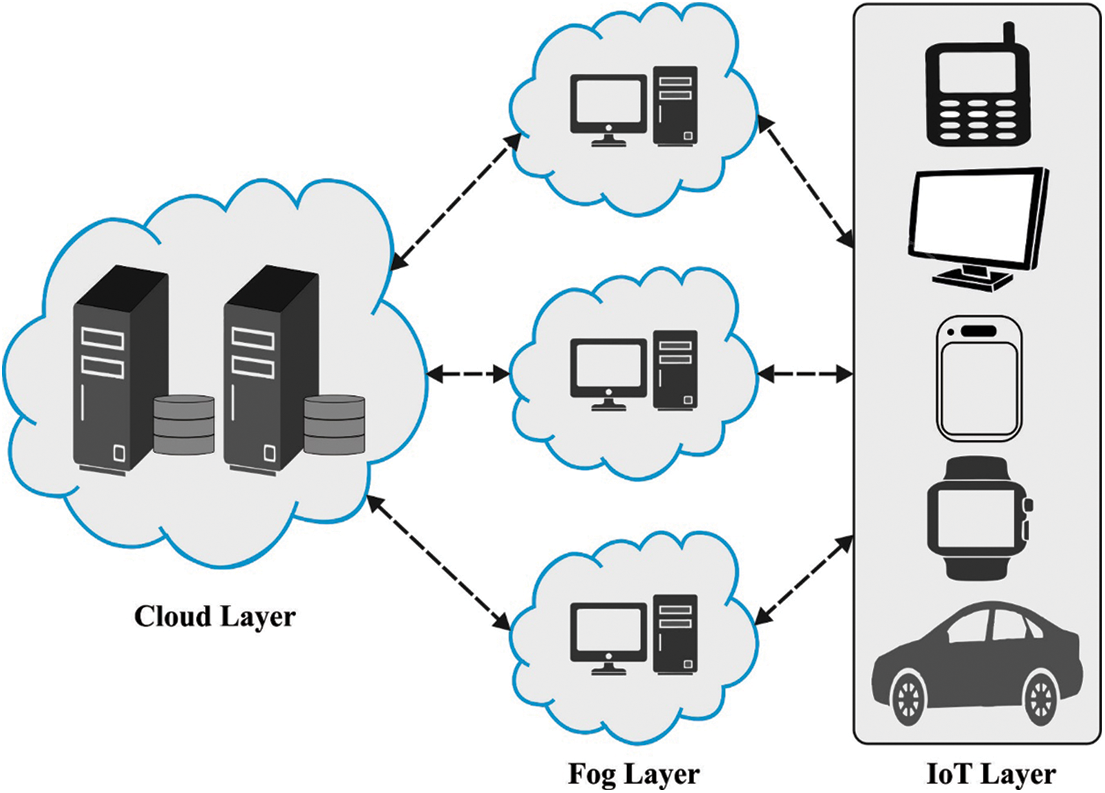
Figure 1: Fog enabled IoT environment
Energy is a limited resource in IoT. Thus, energy preservation is a major problem in IoT [6]. Various methods are presented for redoing energy utilization in IoT. Sleeping mechanisms, Energy-aware routing, data aggregation, and congestion-aware routing have been presented approaches in IoT. In energy-aware routing, the present protocol contains node reliance techniques, energy-aware solar routing, data-driven approaches, multihop hierarchical clustering, duty cycling for extending lifetime of the network [7]. It can be fundamental process for saving energy and eliminating redundant data [8]. As well, it expanded lifetime of the network [9]. This technique is appropriate for some applications including gas leakage monitoring and temperature monitoring. The current data aggregation technique is region-based routing and clustering for reducing duplicate data communication over the network [10]. This study presents a new hierarchical data aggregation with chaotic barnacles mating optimizer (HDAG-CBMO) technique for fog assisted WSN. The HDAG-CBMO technique computes a fitness function using several relational matrices such as residual energy, average distance to neighbors, and centroid degree of target area. Moreover, a chaotic theory based population initialization technique is computed to optimally select the barnacle's initial positions. Furthermore, a learning based data offloading method is designed for reducing the response time to IoT user requests. In order to ensure the enhanced outcomes of the fog assisted WSN, a comprehensive simulation analysis was performed and the results are inspected under several aspects.
Alli et al. [11] presented a secure computation off-loading method from Fog-Cloud-IoT environment (SecOFF-FCIoT). Utilizing ML approaches, it can be accomplishing effectual, secured offloading from Fog-IoT setting. In specific, it can be utilized Neuro-Fuzzy Method for securing information at the smart gateway, afterward, the IoT devices choose a better Fog node for that it is offloading their workload utilizing PSO utilized smart gateway. Daraghmi et al. [12] presented the Client-Fog-Cloud (CFC) multilayer data process and aggregation infrastructure which is planned for promoting latency-sensitive applications from the IoT contexts. The infrastructure has been planned for addressing the present IoT based challenge: an extensive distribution, huge uploaded, minimal latency, and real time interface. The presented infrastructure has of device gateway, fog servers, and clouds. Wang et al. [13] progressed the task-driven data offloading (TDO) technique from urban IoT service. Especially, a 3-layer urban IoT service infrastructure has been presented, and the TDO procedure has been expressed as combination optimized issue taking task deadlines and capabilities of fog device as to consideration. Afterward, it is demonstrated the TDO issue has NP-hard, and G-TDO technique has been developed for solving it with carefully planned utility function. In [14], the role of context or condition for performing the offloading has been considered and drawn to end which for meeting the efficacy requirement of IoT enabled service, context-based offloading is role an important play. In several existing structures EMCO, MobiCOP-IoT, Autonomic Management structure, CSOS, Fog Computing structure dependent upon its novelty and optimal efficiency are taken to execution analysis. Hossen et al. [15] utilized a Spark based big data processing scheme (BDPS) for accelerating the distributed database (RDD) delay effectual approach from the fog to a decentralized heterogeneous network structure for reinforcing appropriate data allocation utilizing IoTs. It can be present BDPS dependent upon Spark-RDD from the fog-IoT overlay structure for addressing the efficacy issue across the network orchestration. Chen et al. [16] examined the privacy and energy co-aware data aggregation compute offloading to fog assists IoT network. In detail, a fog supported 3-layer security compute structure was established for counteracting security threats and allowing the aggregation function is executed from ciphertext. In the meantime, a drive gradient descent based energy effective offloading decision technique has been established for minimizing the entire energy utilization of computation tasks that attains an optimum value with fast convergence rate.
In this study, an effective HDAG-CBMO algorithm has been developed for data aggregation and data offloading processes in the fog assisted WSN. The HDAG-CBMO technique computes a fitness function using several relational matrices such as residual energy, average distance to neighbors, and centroid degree of target area. At last, a learning based data offloading method is designed for reducing the response time to IoT user requests.
Barnacles are microbes which get involved in the objects that exist from the water. They have the major characteristics of lengthy penis. The mating process includes all neighbors and competitors who exist in the reaching area of the penis. The BMO approach was stimulated by the mating nature of the barnacles [17]. It involves three stages of operations such as initialization, selection, and reproduction. At the initial stage, the barnacles are considered as candidate solutions where the population matrix is defined by Eq. (1). Followed by, the mating of the chosen parents takes place using Eqs. (2) and (3).
where N denotes barnacle count, n indicates control variable count, barnacle−d and barnacle−m represent the parent's undergone mating process. As there exist no particular formulations in deriving the productivity of barnacles. It is noted that the penis length (pl) acts as an essential part in computing the exploitation and exploration process. When the choice of barnacles mating exists in the range of pl of Dad barnacle, the exploitation procedure is carried out. The process involved in the generation of new parameters of offspring from barnacle parents is defined as follows.
where p denotes uniform distribution number,
where rand () implies arbitrary number in the range of [0, 1]. It is noted that newly created offspring is represented as Mum barnacle as it attains that the sperms are released to the water by other barnacles. At this point, the barnacle's location can be upgraded using Eqs. (4) or (5). Fig. 2 depicts the flowchart of BMO.
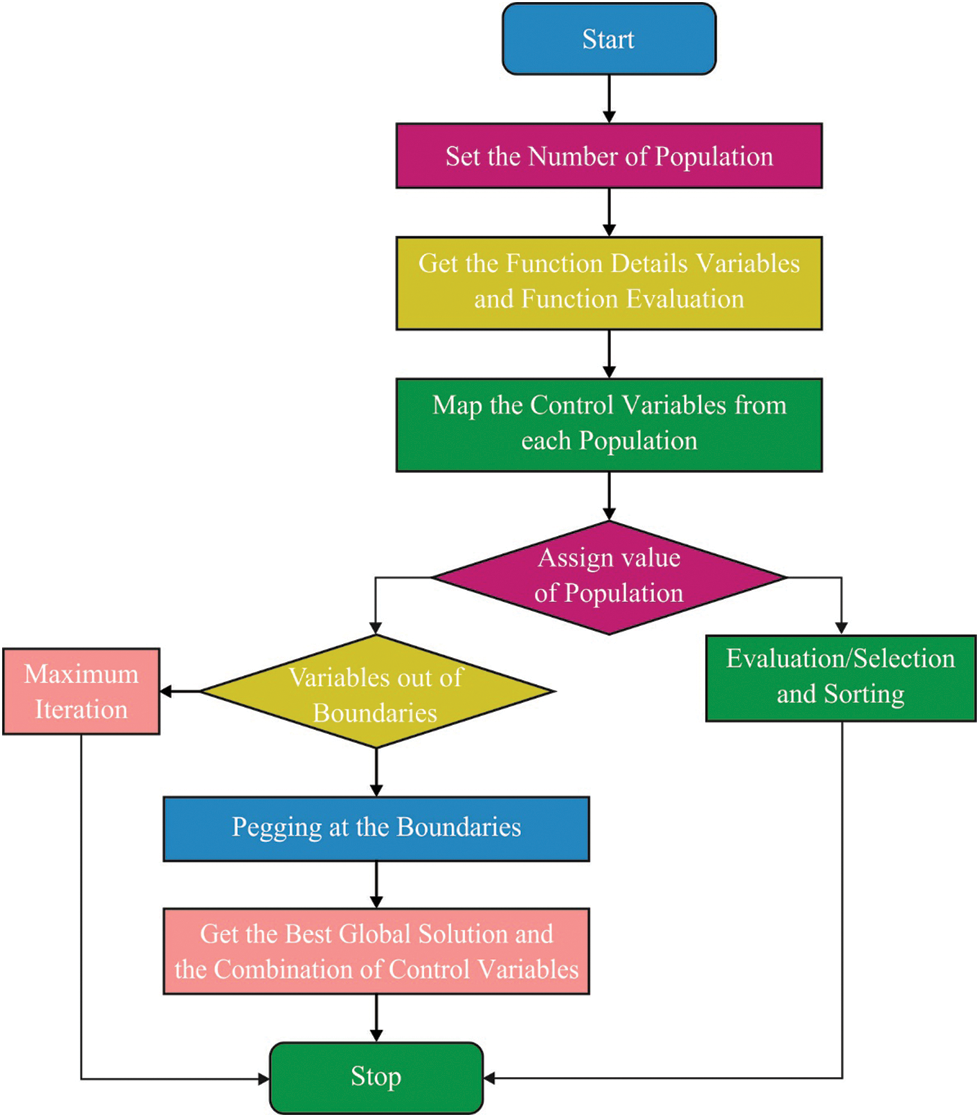
Figure 2: Flowchart of BMO
Besides, a chaotic theory based population initialization [18] technique is computed to optimally select the barnacle's initial positions. During random optimization algorithm, chaotic variable is used in place of random variable and is named as chaotic optimization algorithm (COA). Due to the fact that the chaos holds the characteristics of non-repetition and ergodicity, it carries out entire searching process at maximum speed compared to stochastic searching process which is based on probability. To accomplish this, 1-D non-invertible maps is applied for producing chaotic set. In [19], the model investigation of energy utilization is conducted and an optimal amount of CHs are attained as:
where N refers the entire amount of sensor nodes from the area and M represents the border length of square monitored region. In order to resolve an optimum issue, the explanation of FFs is role an important play in the feature of algorithm efficacy. In order for CHs, an essential task is for collecting information in their member node. So, it should not only have superior RE, for keeping the lesser the average distance to every node from its clusters. In addition, for preventing the place of CHs at the edge of clusters, it is ensured as nearer feasible to the center of region that is shorten the distance in member nodes fundamentally. According to above study, many estimation issues are evaluated and the Equivalent equation is provided as:
where the sensor node nj goes to cluster Ck, and |Ck| implies the amount of nodes from the cluster Ck. d(nj, CHk) stands for the distance amongst the member nodes ni and their CH. In addition,
During the offloading method, significant data has been provided to requested user. Also, the procedures exceeding the capacity of devices were shared through the neighbors to parallel computation. It can be minimized overloading of devices with decreasing data and task congestion rate with lesser delay. The benefit of ML was more extended to connections amongst the fog layer and end user from the user layer. To the observed sa accumulated data, appropriate offloading has vital for preventing data unallocation and minimizing retrieval times. The fog element assigned the sensed data to the request in the user layers. The sensed data has been made in the cloud by fog components for minimizing the request waiting time [20]. Assume Pij be present the probability to end user devices request being mapped to jth fog component
Since the request space of fog component has been restricted, the optimality of making sure Pij = 1 has shown with request arrival rate (rar). The request arrival rate has been calculated utilizing in Eq. (9),
where rn refers the amount of requests transferred at time tr. Assume cj implies the capacity of jth fog component; otherwise, if rar > cj, the fog component offloads request to their neighbor. The offloading of user requests improves the waiting time before dropping. The aggregation rate has irrespective of the amount of end users and requests. For improving the consistency of responses and the service utility rate, downloaded or data access success was evaluated. Assume dp represent the download probability of end users that is evaluated utilizing in Eq. (10):
The ratio of downloading drat is then calculated utilizing
where da stands for the data accumulated at ta intervals and rn signifies the amount of requests in the user layer. At this point, the ML procedure started from the previous interface has been modeled for working from the recursive approach. The drat attained from the preceding iterate was make sure at all iterates with minimal route cost. The procedure of recursive learning interms of the consideration of drat. The learning procedure was planned for achieving a superior drat for da and ta with gathering information in sa out of si sensors. In particular, for sa sensor, the route cost has
This procedure of learning are distinct in convention neural learning [21,22] since it can be structured for deriving the particular
where tw implies the wait time of requests, and
The experimental validation of the HDAG-CBMO technique takes place in this section. The results are inspected under varying numbers of requests and rounds. Tab. 1 and Fig. 3 inspect the processing time (PT) examination of the HDAG-CBMO model under distinct number of requests. The results indicated that the HDAG-CBMO model has accomplished effectual outcomes with minimal PT.
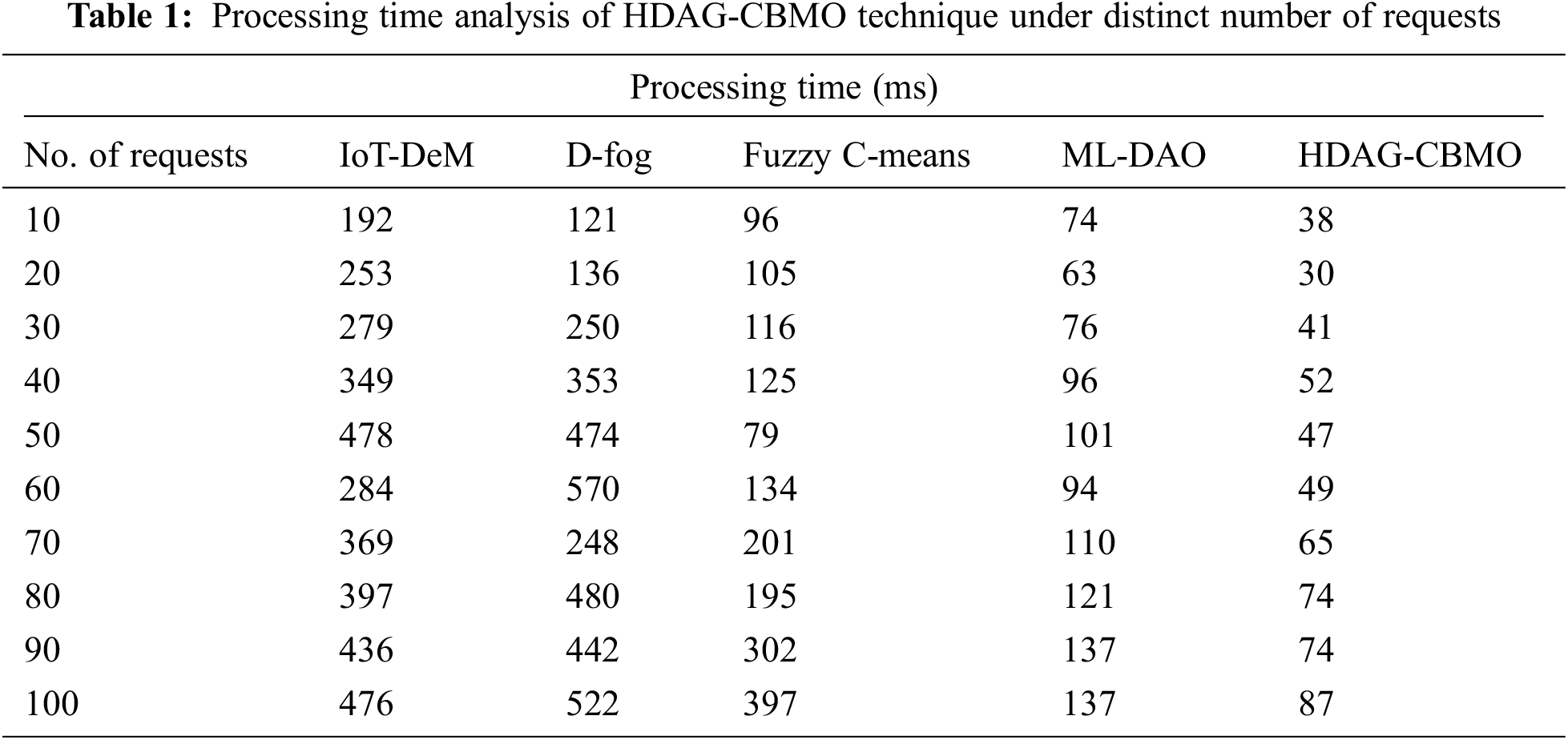
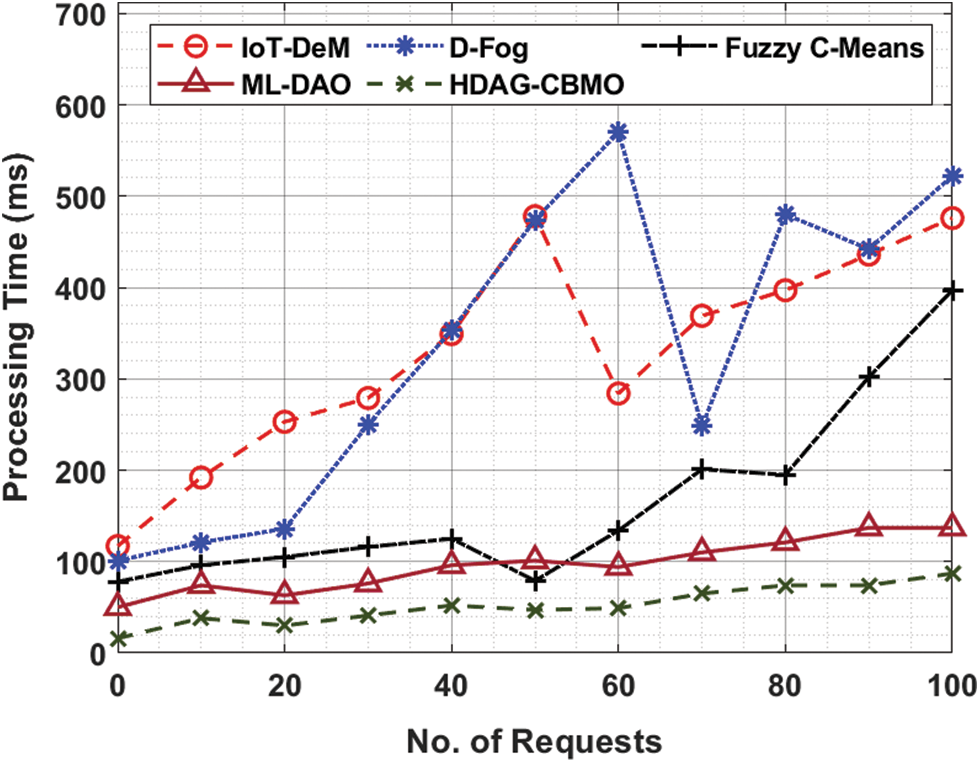
Figure 3: PT analysis of HDAG-CBMO technique with recent approaches
For instance, with 10 requests, the HDAG-CBMO model has gained lower PT of 38 ms whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have obtained higher PT of 192 ms, 121 ms, 96 ms, and 74 ms respectively. Eventually, with 50 requests, the HDAG-CBMO model has provided reduced PT of 47 ms whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have attained increased PT of 478 ms, 474 ms, 79 ms, and 101 ms respectively. Meanwhile, with 100 requests, the HDAG-CBMO model has accomplished minimal PT of 87 ms whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have reached maximum PT of 476 ms, 522 ms, 397 ms, and 137 ms respectively. Tab. 2 and Fig. 4 depict the response time (RT) examination of the HDAG-CBMO technique under distinct count of requests. The results outperformed that the HDAG-CBMO approach has accomplished effectual outcomes with minimal RT.
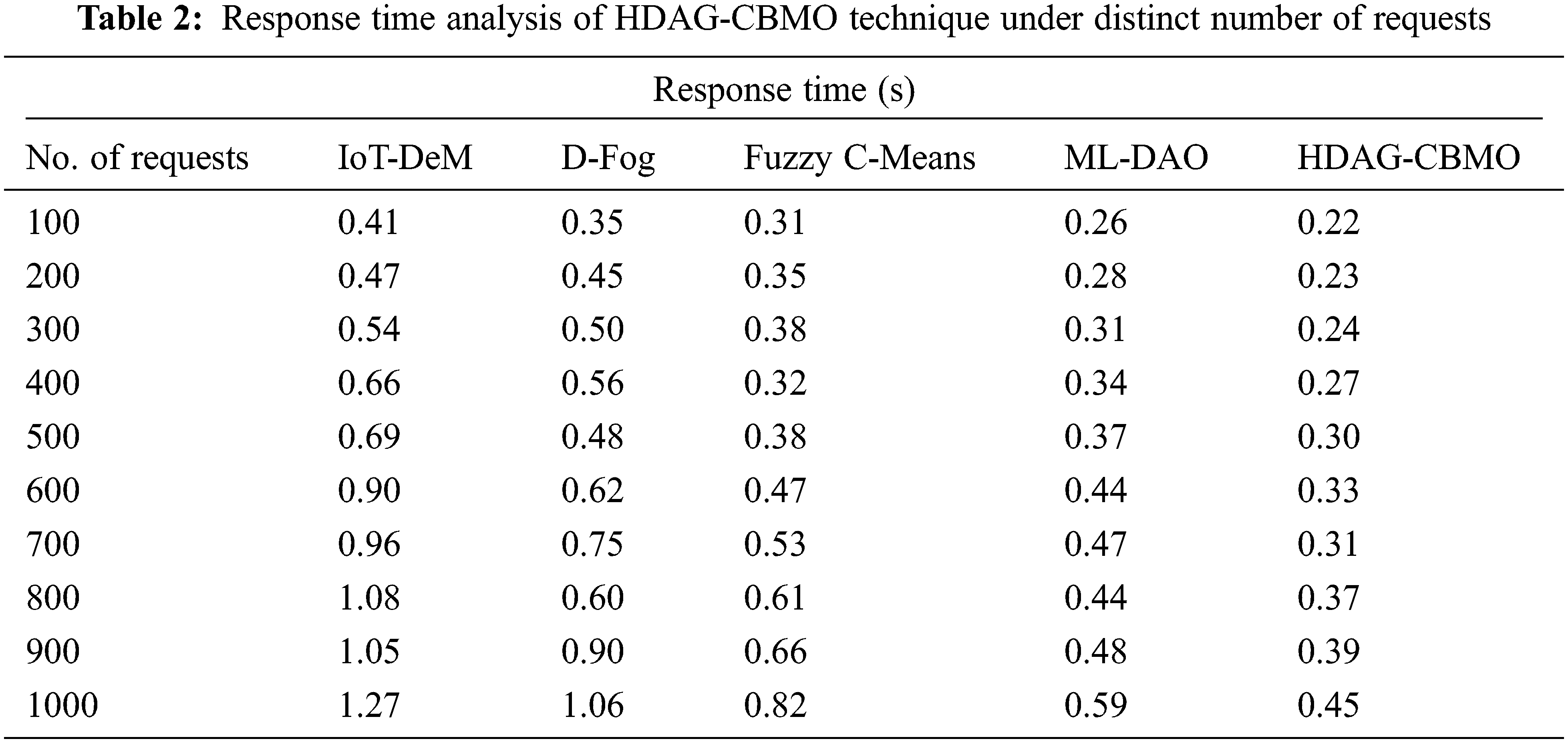
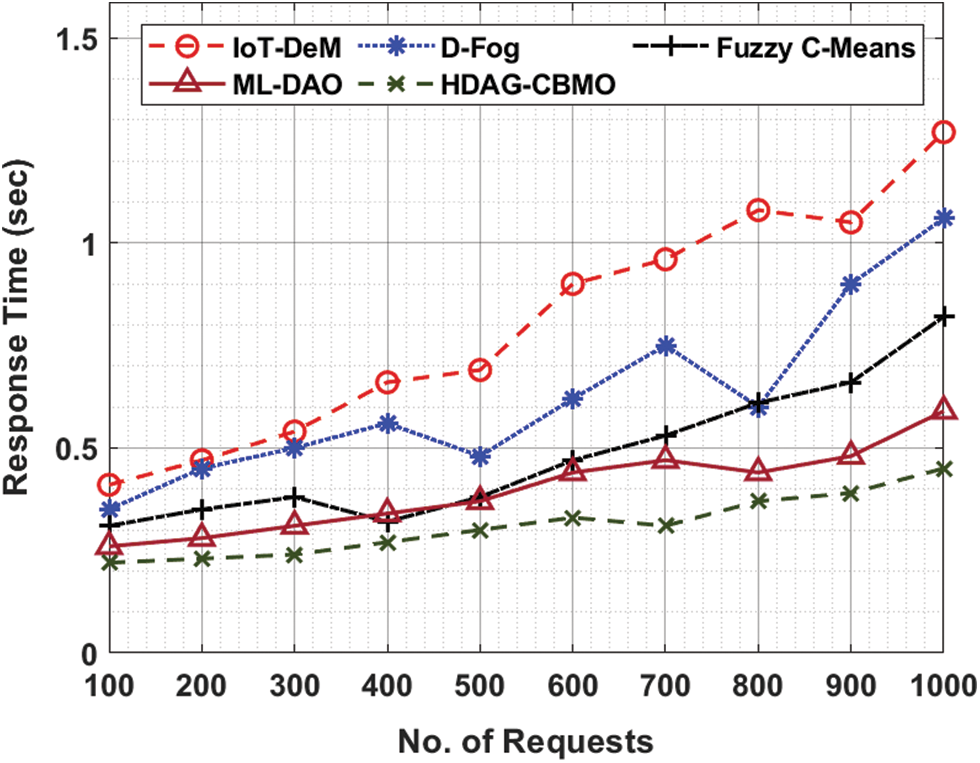
Figure 4: RT analysis of HDAG-CBMO technique with recent approaches
For instance, with 100 requests, the HDAG-CBMO algorithm has reached minimal RT of 0.22 s whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have obtained maximal RT of 0.41 s, 0.35 s, 0.31 s, and 0.26 s correspondingly. Followed by, with 500 requests, the HDAG-CBMO algorithm has offered reduced RT of 0.30 s whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have attained maximal RT of 0.69 s, 0.48 s, 0.38 s, and 0.37 correspondingly. Lastly, with 1000 requests, the HDAG-CBMO system has accomplished minimal RT of 0.45 s whereas the IoT-DeM, D-Fog, FCM, and ML-DAO approaches have reached higher RT of 1.27 s, 1.06 s, 0.82 s, and 0.59 s correspondingly. Tab. 3 and Fig. 5 demonstrate the failure probability (FP) examination of the HDAG-CBMO model under distinct number of requests. The results indicated that the HDAG-CBMO approach has accomplished effectual outcomes with minimal FP. For instance, with 100 requests, the HDAG-CBMO methodology has reached decreased FP of 0.17 whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have obtained higher FP of 0.50, 0.45, 0.26, and 0.21 correspondingly. Likewise, with 500 requests, the HDAG-CBMO model has offered reduced FP of 0.17 whereas the IoT-DeM, D-Fog, FCM, and ML-DAO systems have attained increased FP of 0.47, 0.34, 0.20, and 0.23 correspondingly. At last, with 1000 requests, the HDAG-CBMO technique has accomplished lesser FP of 0.25 whereas the IoT-DeM, D-Fog, FCM, and ML-DAO systems have attained superior FP of 0.85, 0.42, 0.37, and 0.32 correspondingly.
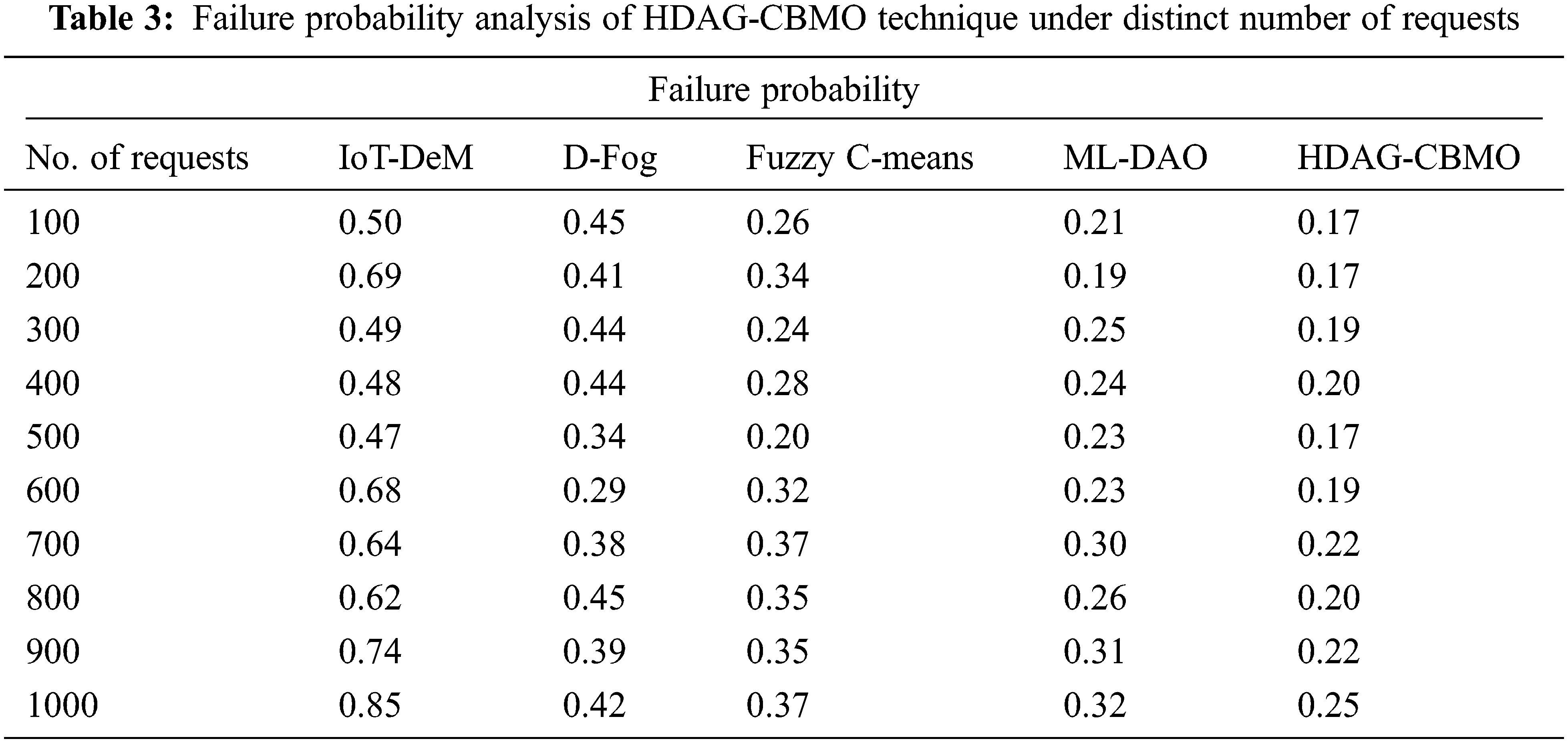
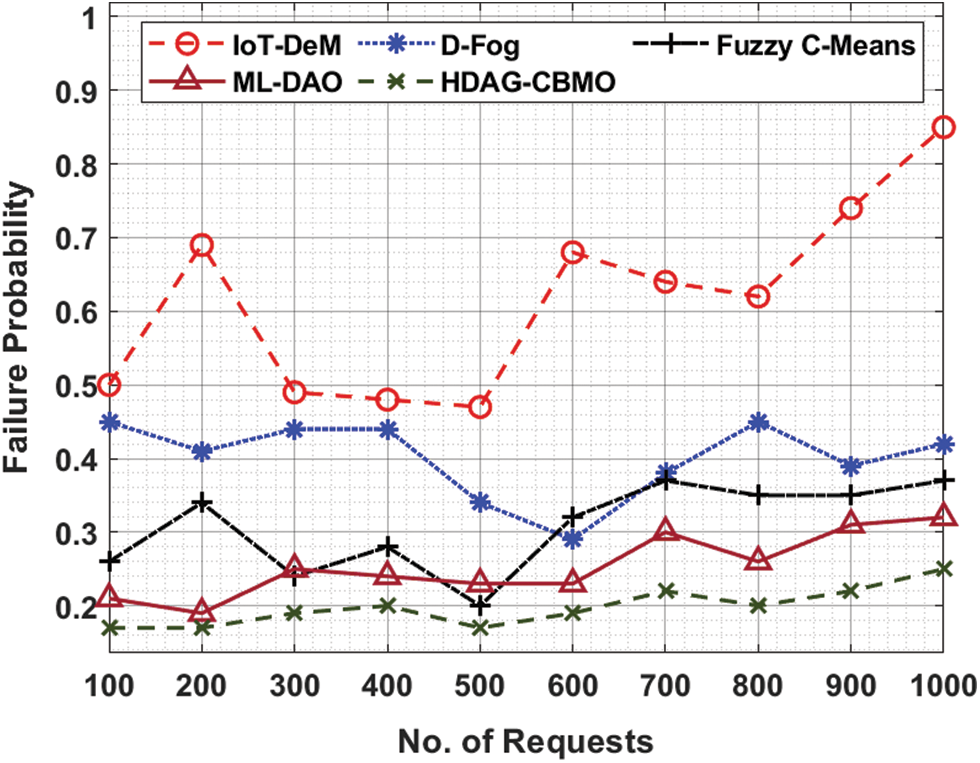
Figure 5: FP analysis of HDAG-CBMO technique with recent approaches
Tab. 4 and Fig. 6 determine the aggregation time (AT) examination of the HDAG-CBMO model under distinct count of requests. The results revealed that the HDAG-CBMO technique has accomplished effectual outcomes with minimal AT. For instance, with 1000 requests, the HDAG-CBMO model has gained lower AT of 279 ms whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have obtained higher AT of 1059 ms, 831 ms, 592 ms, and 345 ms respectively.
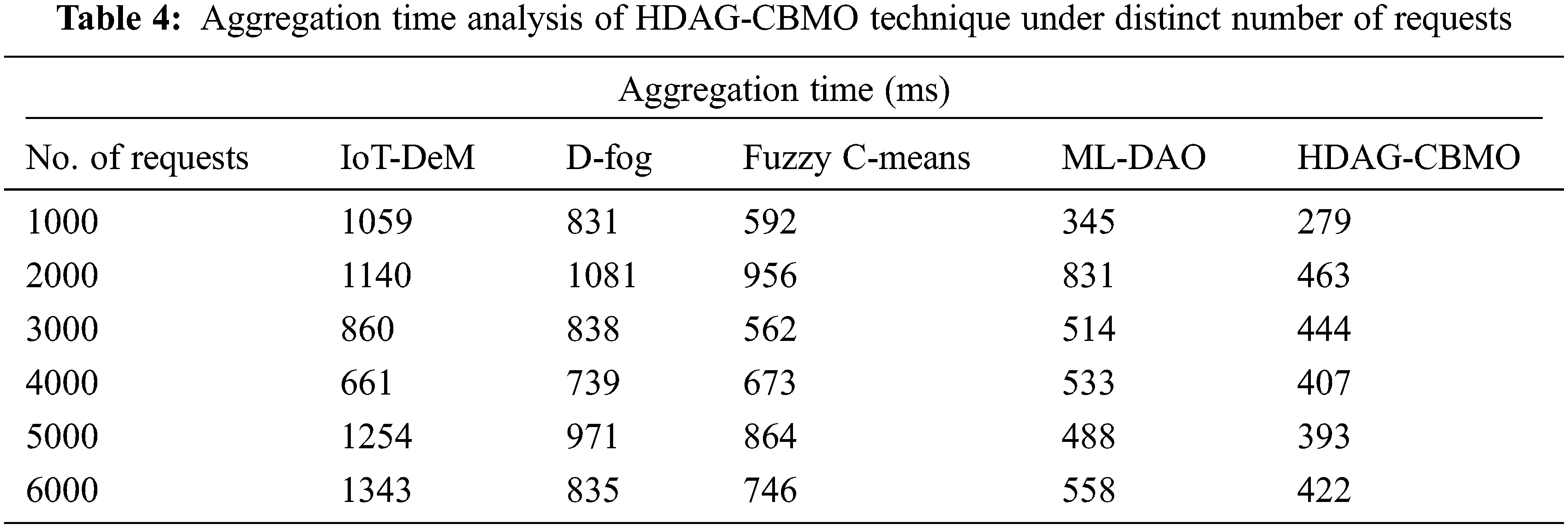
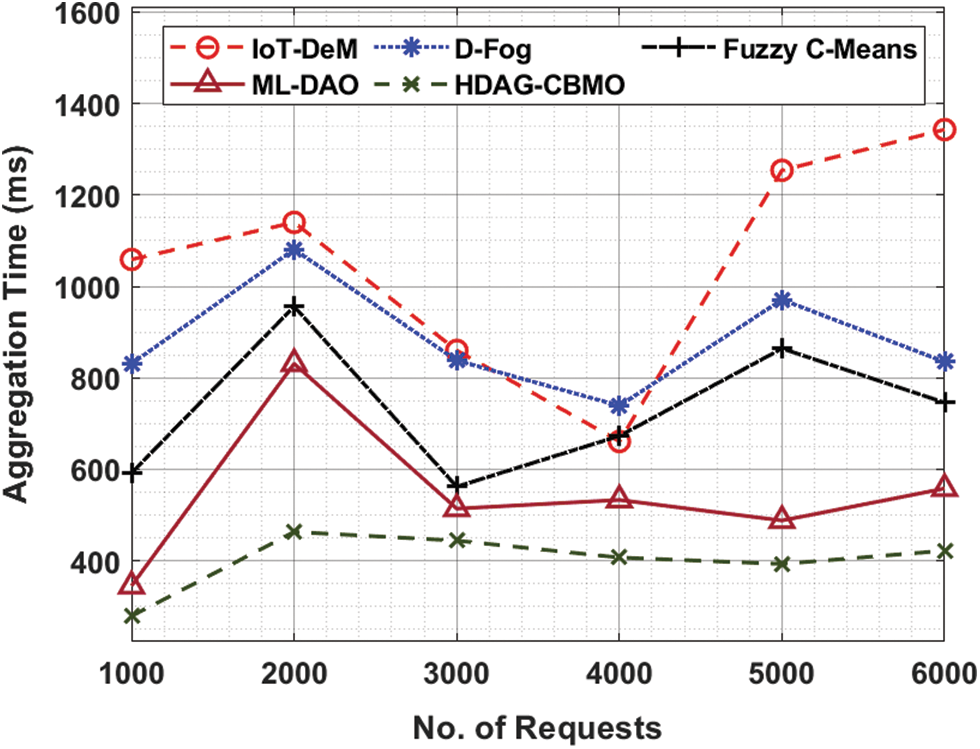
Figure 6: AT analysis of HDAG-CBMO technique with recent approaches
Eventually, with 3000 requests, the HDAG-CBMO model has provided reduced AT of 444 ms whereas the IoT-DeM, D-Fog, FCM, and ML-DAO approaches have obtained increased AT of 860 ms, 838 ms, 562 ms, and 514 ms correspondingly. Finally, with 6000 requests, the HDAG-CBMO model has accomplished decreased AT of 422 ms whereas the IoT-DeM, D-Fog, FCM, and ML-DAO methods have reached higher AT of 1343 ms, 835 ms, 746 ms, and 558 ms respectively. Tab. 5 and Fig. 7 examine the unallocated data chunks (UDC) examination of the HDAG-CBMO method under distinct number of requests. The results indicated that the HDAG-CBMO approach has accomplished effectual outcomes with minimal UDC. For instance, with 50 requests, the HDAG-CBMO approach has gained lower UDC of 160 whereas the IoT-DeM, D-Fog, FCM, and ML-DAO systems have obtained higher UDC of 407, 308, 328, and 249 respectively.
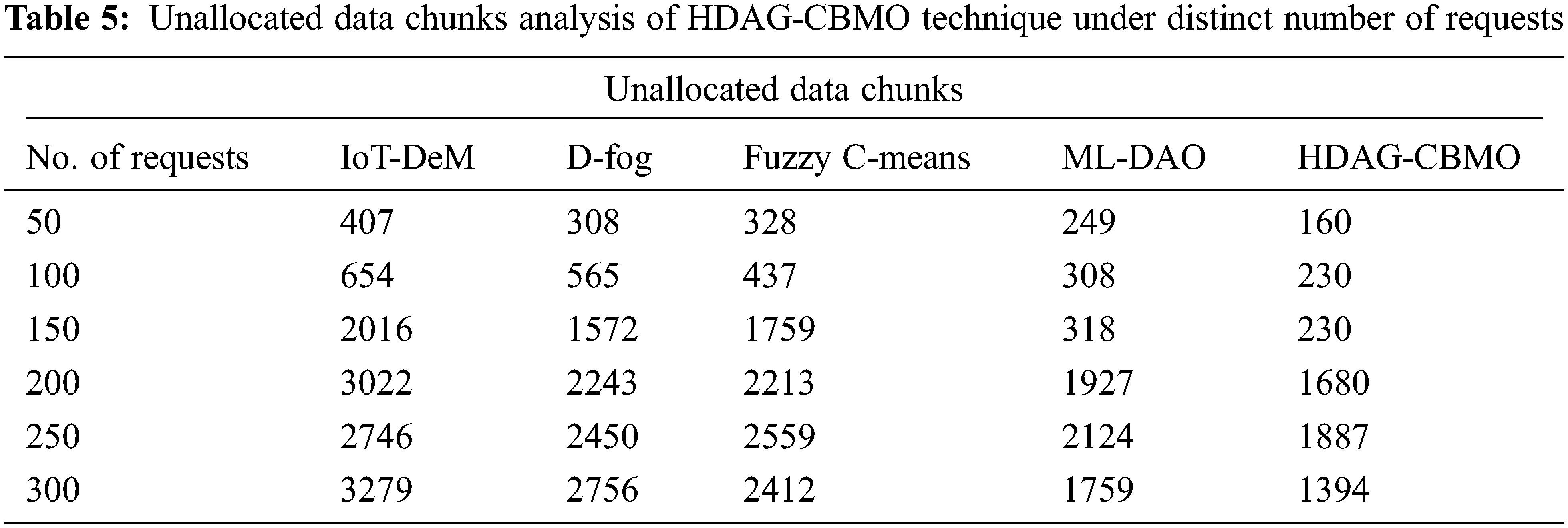
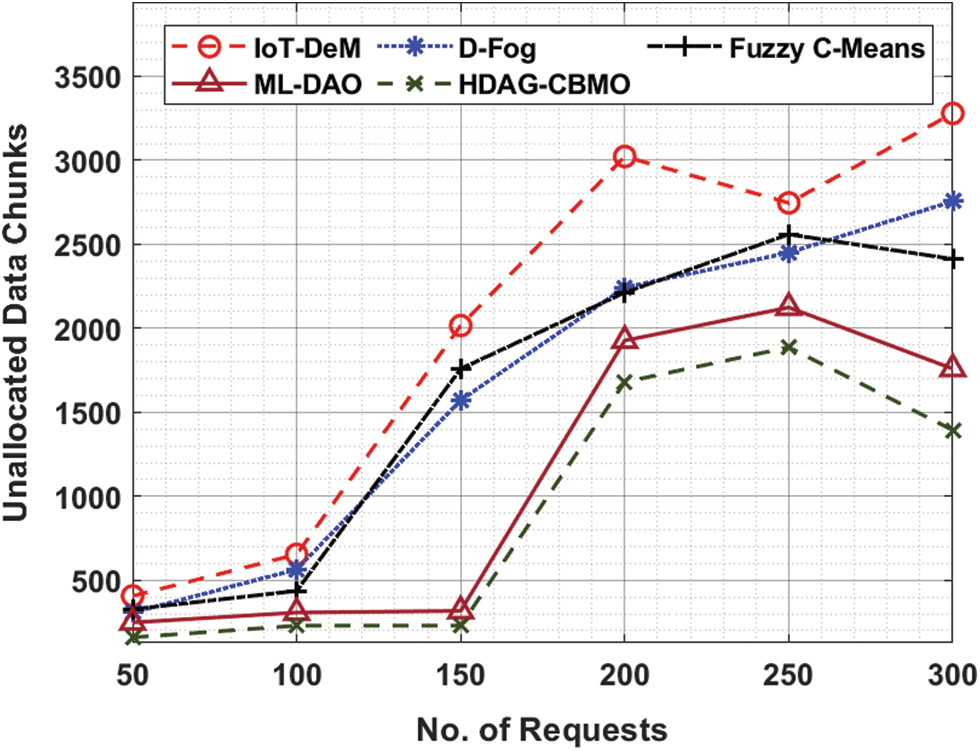
Figure 7: UDC analysis of HDAG-CBMO technique with recent approaches
Meanwhile, with 150 requests, the HDAG-CBMO system has provided lesser UDC of 230 whereas the IoT-DeM, D-Fog, FCM, and ML-DAO models have attained enhanced UDC of 2016, 1572, 1759, and 318 correspondingly. In the meantime, with 300 requests, the HDAG-CBMO model has accomplished minimal UDC of 1394 whereas the IoT-DeM, D-Fog, FCM, and ML-DAO algorithms have gained increased UDC of 3279, 2756, 2412, and 1759 respectively.
A comparative total residual energy (TRE) investigation of the HDAG-CBMO model with recent methods is offered in Tab. 6 and Fig. 8. The experimental results indicated that the HDAG-CBMO model has resulted in higher values of TRE compared to existing techniques.
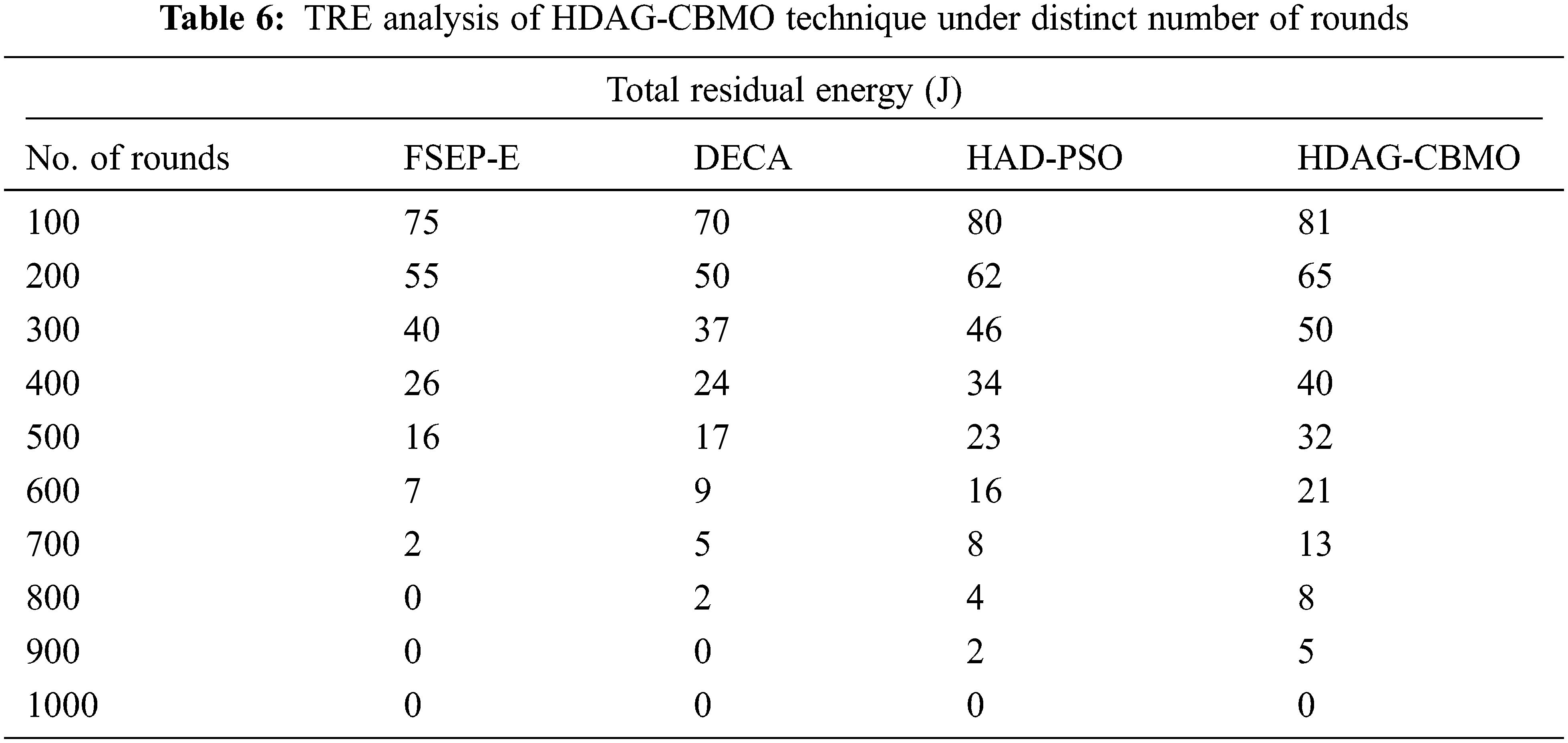

Figure 8: TRE analysis of HDAG-CBMO technique with recent approaches
For example, with 100 rounds, the HDAG-CBMO model has provided higher TRE of 81 J whereas the FSEP-E, DECA, and HAD-PSO models have attained lower TRE of 75 J, 70 J, and 80 J respectively. In addition, with 500 rounds, the HDAG-CBMO model has accomplished increased TRE of 32 J whereas the FSEP-E, DECA, and HAD-PSO models have resulted in reduced TRE of 16 J, 17 J, and 23 J respectively.
A comparative throughput (THRPT) examination of the HDAG-CBMO model with recent techniques is offered in Tab. 7 and Fig. 9. The experimental outcomes exposed that the HDAG-CBMO model has resulted in higher values of THRPT compared to existing techniques. For example, with 120 rounds, the HDAG-CBMO system has provided superior THRPT of 162.94Mbps whereas the FSEP-E, DECA, and HAD-PSO methods have attained lower THRPT of 128.54Mbps, 140.01Mbps, and 148.61Mbps correspondingly. Besides, with 1000 rounds, the HDAG-CBMO algorithm has accomplished improved THRPT of 1057.05Mbps whereas the FSEP-E, DECA, and HAD-PSO methodologies have resulted to reduce THRPT of 595.66Mbps, 756.14Mbps, and 968.21Mbps correspondingly.
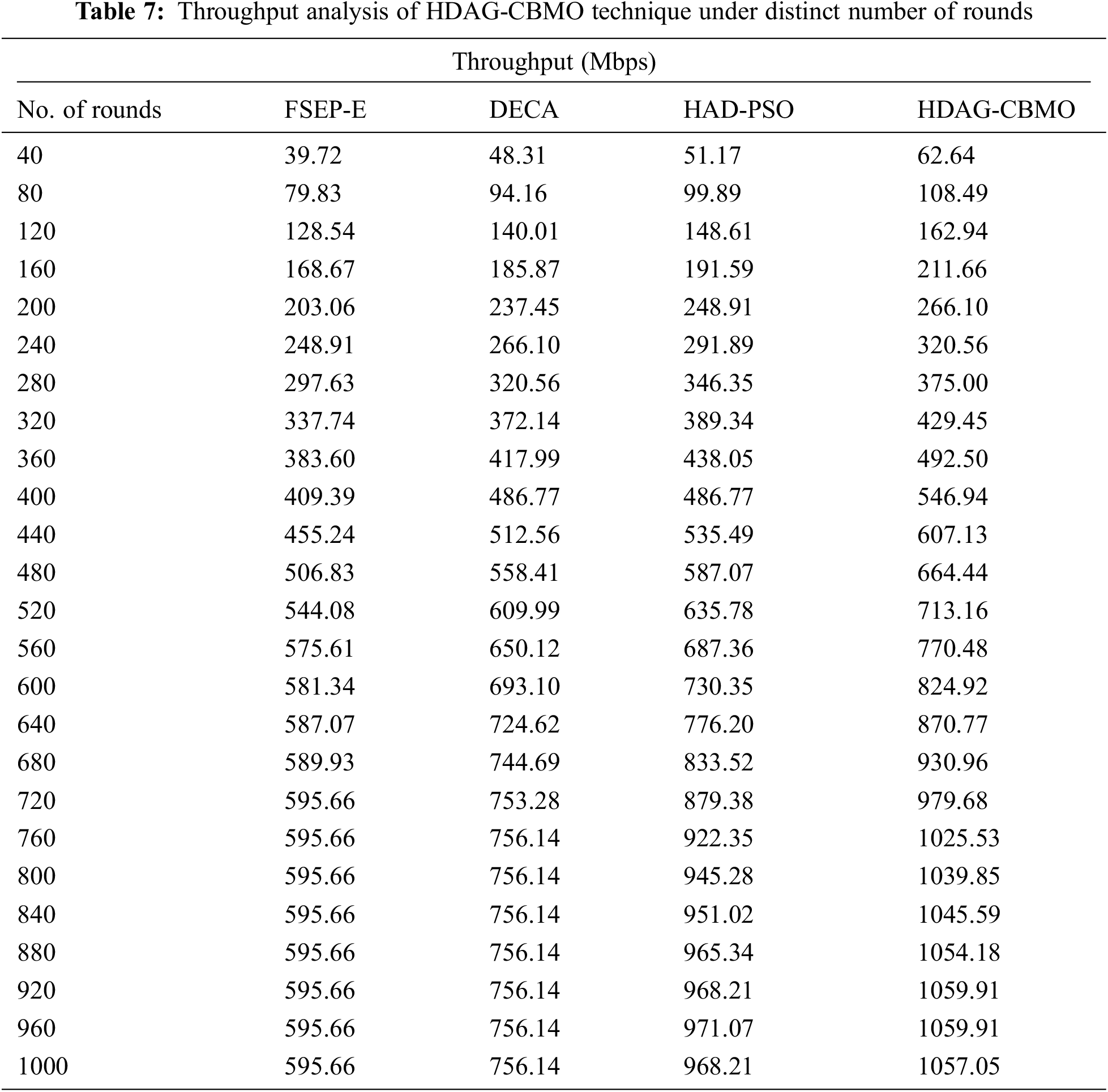
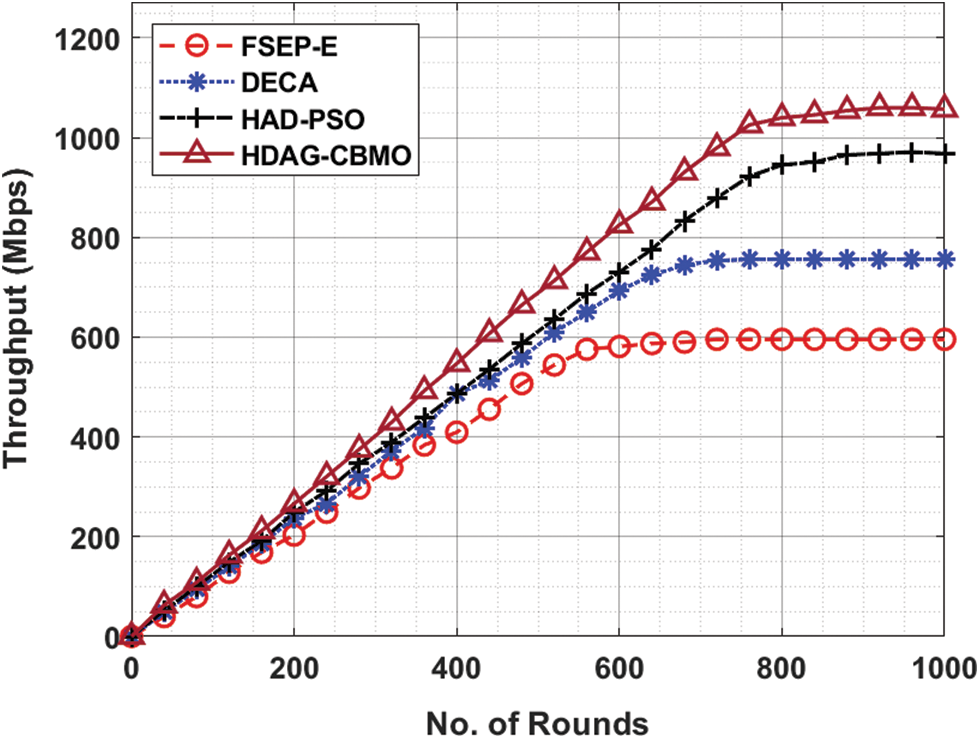
Figure 9: Throughput analysis of HDAG-CBMO technique with recent approaches
After examining the above mentioned results and discussion, it is evident that the HDAG-CBMO model has accomplished superior performance over the other methods.
In this study, an effective HDAG-CBMO algorithm has been developed for data aggregation and data offloading processes in the fog assisted WSN. The HDAG-CBMO technique computes a fitness function using several relational matrices such as residual energy, average distance to neighbors, and centroid degree of target area. Besides, a chaotic theory based population initialization technique is computed to optimally select the barnacle's initial positions. At last, a learning based data offloading method is designed for reducing the response time to IoT user requests. In order to ensure the enhanced outcomes of the fog assisted WSN, a comprehensive simulation analysis was performed and the results are inspected under several aspects. The experimental results pointed out the better outcomes of the HDAG-CBMO technique over the other recent techniques. In future, hybrid metaheuristics based routing techniques can be developed for fog assisted IoT networks.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Sennan, S. Balasubramaniyam, S. Luhach, A. K. Ramasubbareddy, S., Chilamkurti et al., “Energy and delay aware data aggregation in routing protocol for internet of things.” Sensors, vol. 19, no. 24, pp. 5486–5498, 2019. [Google Scholar]
2. R. Lu, K. Heung, A. H. Lashkari and A. A. Ghorbani, “A lightweight privacy-preserving data aggregation scheme for fog computing-enhanced IoT,” IEEE Access, vol. 5, no. 8, pp. 3302–3312, 2017. [Google Scholar]
3. F. Yildirim Okay, F. Ozdemir and Y. Xiao, “Fog computing-based privacy preserving data aggregation protocols,” Transactions on Emerging Telecommunications Technologies, vol. 31, no. 4, pp. 3900–3915, 2020. [Google Scholar]
4. X. Shen, L. Zhu, K. Xu, C. Sharif and R. Lu, “A Privacy-preserving data aggregation scheme for dynamic groups in fog computing,” Information Sciences, vol. 7, no. 514, pp. 118–130, 2020. [Google Scholar]
5. F. Yildirim, F. Okay, S. S. Ozdemir and Y. Xiao, “Fog computing-based privacy preserving data aggregation protocols,” Transactions on Emerging Telecommunications Technologies, vol. 31, no. 4, pp. 3900–3917, 2020. [Google Scholar]
6. Y. Huo, C. Yong and Y. Lu, “Re-ADP: Real-time data aggregation with adaptive-event differential privacy for fog computing,” Wireless Communications and Mobile Computing, vol. 12, no. 2, pp. 312–325, 2018. [Google Scholar]
7. A. Amuthan and R. Sendhil, “Hybrid GSW and DM based fully homomorphic encryption scheme for handling false data injection attacks under privacy preserving data aggregation in fog computing,” Journal of Ambient Intelligence and Humanized Computing, vol. 11, no. 11, pp. 5217–5231, 2020. [Google Scholar]
8. M. Yang, T. Zhu, B. Liu, Y. Xiang and W. Zhou, “Machine learning differential privacy with multifunctional aggregation in a fog computing architecture.” IEEE Access, vol. 6, no. 1, pp. 17119–17129, 2020. [Google Scholar]
9. K. Gu, N. Wu, B. Yin and W. Jia, “Secure data query framework for cloud and fog computing,” IEEE Transactions on Network and Service Management, vol. 17, no. 1, pp. 332–345, 2019. [Google Scholar]
10. K. Sarwar, S. Yongchareon, J. Yu and S. ur Rehman, “Lightweight, divide-and-conquer privacy-preserving data aggregation in fog computing,” Future Generation Computer Systems, vol. 12, no. 119, pp. 188–199, 2020. [Google Scholar]
11. A. Alli and M. Alam, “SecOFF-FCIoT: Machine learning based secure offloading in Fog-cloud of things for smart city applications,” Internet of Things, vol. 1, no. 7, pp. 100070–100085, 2019. [Google Scholar]
12. E. Y. Daraghmi, M. C. Wu and S. M. Yuan, “A multilayer data processing and aggregating fog-based framework for latency-sensitive iot services,” Applied Sciences, vol. 11, no. 4, pp. 1374–1385, 2021. [Google Scholar]
13. P. Wang, R. Yu, N. Gao, C. Lin and Y. Liu, “Task-driven data offloading for fog-enabled urban iot services,” IEEE Internet of Things Journal, vol. 8, no. 9, pp. 7562–7574, 2020. [Google Scholar]
14. K. Bajaj, B. Sharma and R. Singh,“Implementation analysis of IoT-based offloading frameworks on cloud/edge computing for sensor generated big data,” Complex & Intelligent Systems, vol. 19, no. 1, pp. 1–18, 2021. [Google Scholar]
15. R. Hossen, M. Whaiduzzaman, M. Uddin, M. N. Islam, N. Faruqui et al., “BDPS: An efficient spark-based big data processing scheme for cloud fog-IoT orchestration,” Information, vol. 12, no. 12, p.5 17–523, 2021. [Google Scholar]
16. S. Chen, Z. You and X. Ruan, “Privacy and energy co-aware data aggregation computation offloading for fog-assisted IoT networks,” IEEE Access, vol. 8, no. 4, pp. 72424–72434, 2020. [Google Scholar]
17. M. H. Sulaiman, Z. Mustaffa, M. M. Saari and H. Daniyal, “Barnacles mating optimizer: A new bio-inspired algorithm for solving engineering optimization problems,” Engineering Applications of Artificial Intelligence, vol. 8, no. 7, pp.103330–103345, 2020. [Google Scholar]
18. M. Wang and H. Chen, “Chaotic multi-swarm whale optimizer boosted support vector machine for medical diagnosis,” Applied Soft Computing, vol. 8, no. 5, pp. 105946–105958, 2020. [Google Scholar]
19. X. Yin, X. Li and S. Lin, “A novel hierarchical data aggregation with particle swarm optimization for internet of things,” Mobile Networks and Applications, vol. 24, no. 6, pp. 1994–2001, 2019. [Google Scholar]
20. O. Alfarraj, “A machine learning-assisted data aggregation and offloading system for cloud–IoT communication,” Peer-to-Peer Networking and Applications, vol. 14, no. 4, pp. 2554–2564, 2021. [Google Scholar]
21. X. R. Zhang, W. F. Zhang, W. Sun, X. M. Sun and S. K. Jha, “A robust 3-D medical watermarking based on wavelet transform for data protection,” Computer Systems Science & Engineering, vol. 41, no. 3, pp. 1043–1056, 2022. [Google Scholar]
22. X. R. Zhang, X. Sun, X. M. Sun, W. Sun and S. K. Jha, “Robust reversible audio watermarking scheme for telemedicine and privacy protection,” Computers, Materials & Continua, vol. 71, no. 2, pp. 3035–3050, 2022. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |