DOI:10.32604/csse.2023.026603

| Computer Systems Science & Engineering DOI:10.32604/csse.2023.026603 |  |
| Article |
Chaotic Sandpiper Optimization Based Virtual Machine Scheduling for Cyber-Physical Systems
1Department of Electronics and Communication Engineering, University College of Engineering, BIT Campus, Anna University, Tiruchirapalli, 620025, India
2Department of Electronics and Communication Engineering, Kongu Engineering College, Perundurai, 638060, India
3Department of Electronics and Communication Engineering, M. Kumarasamy College of Engineering, Karur, 639113, India
*Corresponding Author: P. Ramadevi. Email: ramadevi.mohan@gmail.com
Received: 30 December 2021; Accepted: 22 February 2022
Abstract: Recently, with the growth of cyber physical systems (CPS), several applications have begun to deploy in the CPS for connecting the cyber space with the physical scale effectively. Besides, the cloud computing (CC) enabled CPS offers huge processing and storage resources for CPS that finds helpful for a range of application areas. At the same time, with the massive development of applications that exist in the CPS environment, the energy utilization of the cloud enabled CPS has gained significant interest. For improving the energy effectiveness of the CC platform, virtualization technologies have been employed for resource management and the applications are executed via virtual machines (VMs). Since effective scheduling of resources acts as an important role in the design of cloud enabled CPS, this paper focuses on the design of chaotic sandpiper optimization based VM scheduling (CSPO-VMS) technique for energy efficient CPS. The CSPO-VMS technique is utilized for searching for the optimum VM migration solution and it helps to choose an effective scheduling strategy. The CSPO algorithm integrates the concepts of traditional SPO algorithm with the chaos theory, which substitutes the main parameter and combines it with the chaos. In order to improve the process of determining the global optimum solutions and convergence rate of the SPO algorithm, the chaotic concept is included in the SPO algorithm. The CSPO-VMS technique also derives a fitness function to choose optimal scheduling strategy in the CPS environment. In order to demonstrate the enhanced performance of the CSPO-VMS technique, a wide range of simulations were carried out and the results are examined under varying aspects. The simulation results ensured the improved performance of the CSPO-VMS technique over the recent methods interms of different measures.
Keywords: Resource scheduling; cyber physical systems; cloud computing; VM migration; energy efficiency
Recently, cyber-physical system (CPS) has emerged as a new computing paradigm that has received wide attention in the fields of healthcare, manufacturing, and traffic control [1]. Many corporations use CPS for implementing distributed computing resources. In CPS, physical system works as sensor nodes to gather data in realtime and transmit the sensory data to computing platform for detailed analysis. Computing platform process and analyses the data and later send a command or feedback to physical system [2]. The real-time data transported by CPS is important to take effective decisions. With the developments of mobile devices, the incorporation of mobile devices and CPS provide further opportunities to obtain further details. But the complex application in CPSs (that is monitor and industrial applications) frequently requires computing resources and massive storage for meeting the user requirement [3]. Because of the computing capacity and storage limits of mobile devices, the efficiency of CPS applications is incapable of filling the bill. In order to fulfil the storage and resource needs of applications in CPSs, cloud computing (CC) is emerged as a new computational system to provide rich computational resources [4,5]. Fig. 1 illustrates the structure of CPS.
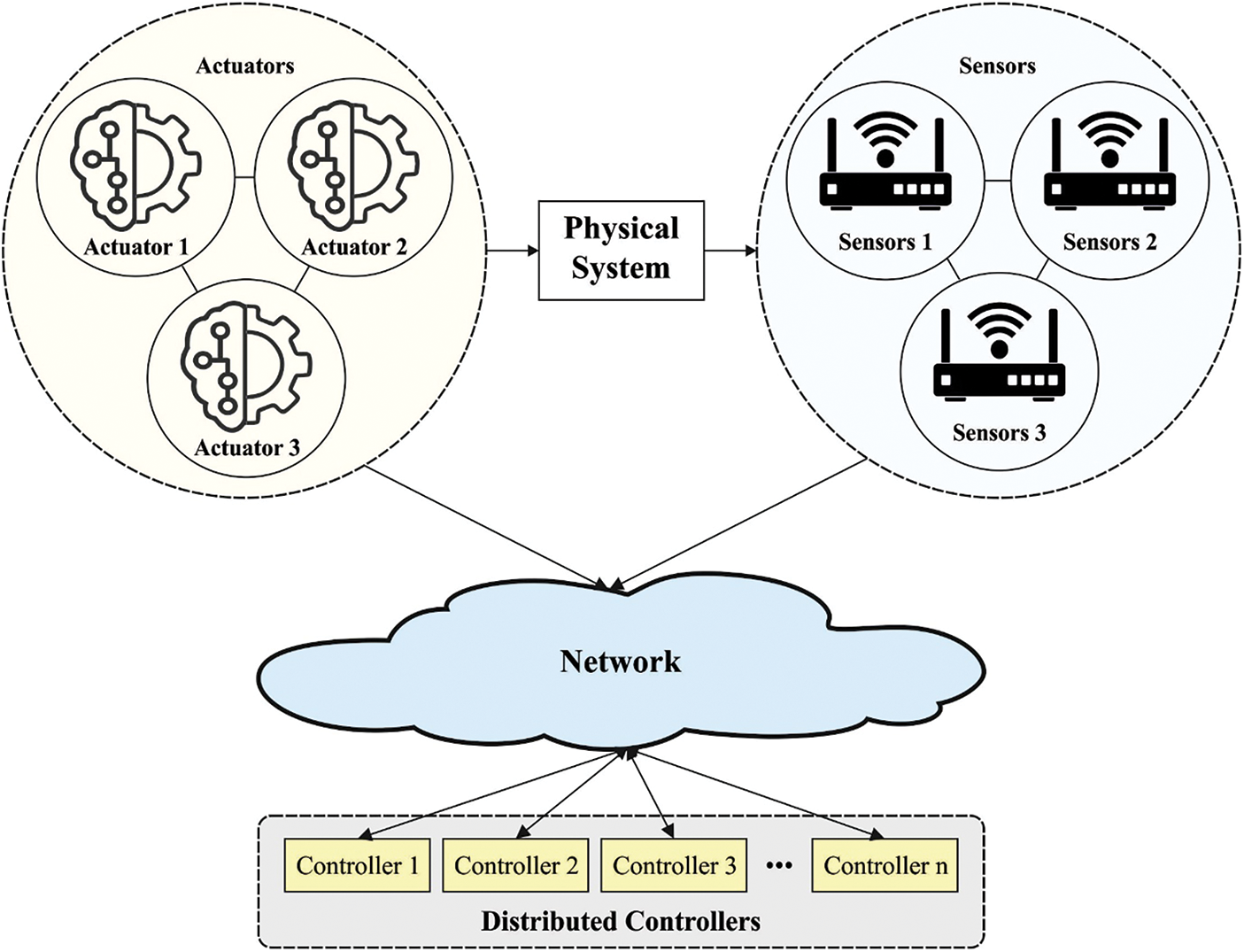
Figure 1: Architecture of CPS
To provide the physical resource dynamically, virtualized technique is widely employed for managing resources from the cloud platform [6] that offers an efficient method to enhance the resource efficacy of the cloud-related CPS. Running application on the virtual machine (VM) provides an opportunity for low energy consumption and higher resource utilization. By incorporating cloud with CPS, several systems such as cloud-integrated vehicles that is unattainable because of the resource limits capable of being deployed effectively [7]. In order to provide better user experience of cloud-based CPS, moderate scheduling strategy is needed for migrating applications to cloud most effectively. In spite of the benefits of VM migration, it generates communication delay and the communication of VM image results in further energy utilization of the switches in the datacentre [8]. Hence, it is important to take into account the positive and negative features of the VM migration and define the moderate scheduling strategies because of the various requirements of the user.
At present, the energy utilization of cloud-based CPS has gained much recognition because it increases the operational costs of the cloud provider, and also drastically reduces lifetime of the battery [9]. Therefore, decreasing energy utilization of the cloud datacentre becomes a major constraint for effective service-experience of extensive resource application in cloud-related CPSs [10]. Mo et al. [11] presented an architecture for optimum defence resource allocation (RA) to minimize unsupplied demands of CPS under uncertain cyberattacks. The vulnerability method of cyber component is defined by an attacker-defender two-phase min-max game. The inaccessibility of cyber module creates the performance loss of the monitored physical component.
Gai et al. [12] concentrated on the problem of RA in CPS and consider the satisfaction of quality of experience (QoE) in content-centric computing systems. A new method is presented for using reinforcement learning method to attain higher accuracy QoE in RA. The assessment of the presented method has been processed by experimental evaluations and theoretical proofs. Vilgelm et al. [13] adapt a cross-layer model to scheduling in wireless networks. The study formulates RA in order to maximalize the efficiency interms of network-induced error. Then, the study develops a Maximum Predicted Error First (MPEF) scheduler that provides an optimum efficiency when only depending on offline data regarding the control loops.
Lu et al. [14] presented an intelligent and secure framework to optimize secrecy of the information. Next, the study presented a new privacy-preserving Fuzzy logic (FL) methodology and developed a two-stage mitigating system comprising collaborative data leakage detection and intelligent data transformation. Li et al. [15] presented a transmission system based 5G to assist the deployment of CPIoTS with a central controller. Depending on the proposed system, different actuators and sensors found transmission links with the centralized controller in full-duplex mode. Gai et al. [16] addressed the issue of task allocation in heterogeneous cloud is shown as an NP-hard problem. The presented method is named Smart Cloud-based Optimizing Workload (SCOW) method which utilizes prediction cloud capacity and considers sustainable factors to allocate tasks to heterogeneous cloud.
This paper presents an effective chaotic sandpiper optimization based VM scheduling (CSPO-VMS) technique for searching the optimum VM migration solution and it helps to choose the effective scheduling strategy. The CSPO algorithm integrates the concepts of traditional SPO algorithm with the chaos theory, which substitutes the main parameter and combines it with the chaos. In order to improve the process of determining the global optimum solutions and convergence rate of the SPO algorithm, the chaotic concept is included in the SPO algorithm. The CSPO-VMS technique also derives a fitness function to choose optimal scheduling strategy in the CPS environment. For ensuring the betterment of the CSPO-VMS technique, a comprehensive experimental analysis is performed and the results are examined under varying aspects.
In this study, a novel CSPO-VMS technique has been presented for searching the optimum VM migration solution and it helps to choose an effective scheduling strategy. The CSPO algorithm integrates the concepts of traditional SPO algorithm with the chaos theory, which substitutes the main parameter and combines it with the chaos. Fig. 2 demonstrates the system framework of VM Scheduling Process.
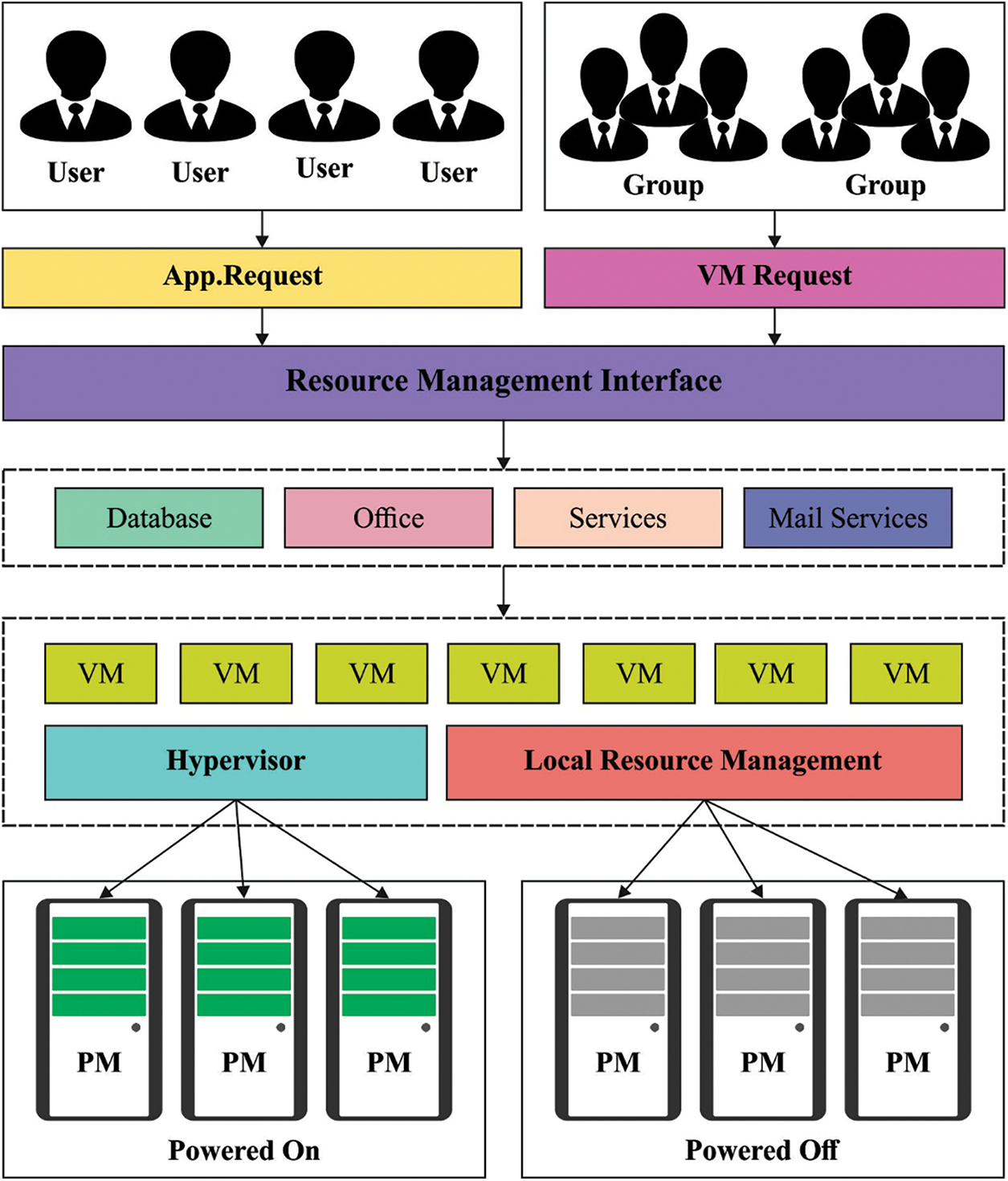
Figure 2: System architecture of VM scheduling process
The SPO algorithm is simulated from the migration and attacking behaviors of sandpipers [17]. Primarily, the SPO technique generates a primary uniformly distributing population of Sandpiper for optimizing an optimum parameter value of DL based FDCN. An optimum solution was upgrading with SPO technique. Initialization of the population of sandpipers that utilized to decrease collision q = 0, 1, 2, …iterMax. Afterward, the procedure of initialized, an input parameter to DL based FDCN is arbitrarily generated by support of SPO technique. During this phase, the sandpiper's maximum fitness value was selected dependent upon sandpiper fitness migration and attacking performance. The FF of the solution was
This technique describes the life of sandpiper bird that transfers from one place to another. At this point, collisions take place, it drives maximum computational complexity and cost function and decreases the accuracy. During the Collision avoidance stage,
where KB stands for collision avoidance,
where
where
where Wradius implies the radius of all spins, χ refers the variable lie from the range of
where
During the end phase, the SPO technique for optimizing main function as computational complexity and cost functions were minimized, and maximizing the accuracy for detecting intrusion in KELM is continually redoing step 3 still the end condition is met. Eventually, the outcomes of SPO technique are reached with one of the experienced places of an optimum main function value to KELM technique.
A new Chaotic with SPO technique is named CSPO that changes the important parameter and embeds chaos as to recent SPO [19]. But, the SPO retains optimum convergence rate, it still could not implement appropriately in determining the global optimum that successively affects the convergence rate of technique. For reducing this outcome and for improving their performance, the method of chaos was established as to SPO technique. The chaotic map is imbedding as SPO for improving the techniques solution quality. The most important parameter of SPO is maximum step size (α) that remains a constant parameter. At this point, this value (α) was changed by 10 varying chaotic maps in trying to enhance the efficiency of SPO. For implementing the maps, every map is normalized amongst zero and one. Also, the parameter of α was changed by 10 distinct chaotic maps with the subsequent formula in Eq. (11).
where ct+1 signifies the distinct chaotic variables are present iteration
During the secondary phase, the fitness function (FF) values of every sandpiper are established from the search space and estimated utilizing the different typical benchmark functions. The lesser fitness value was considered that elite (an optimum FF value). The chaotic number of chaotic maps was established for adjusting the parameter of SPO. During the tertiary phase, the CSPO technique runs successively, whereas every sandpiper is upgrading its places, the resultant in the primary place as optimum solutions. The value of parameter is also upgraded together with the course of all iterations, where
2.2 Resource Utilization Analysis
During the cloud data center, several VM samples are generated for allocating resources. The resource requirement is quantified by the amount of VM samples. Assume that cn be the capacity of
Assume Kn be the flag for judging if the pn has running that is measured as:
where Lm implies the binary variable for determining where vm hosts a load, and their computation is written as:
Therefore, the entire amount of running PMs are computed as:
The resource consumption rate was computed as:
2.3 Application of CSPO Algorithm for Resource Scheduling
Assume that N PMs from the cloud environments utilized under the application implementation represented as P = {p1, p2,… = pN}. Also, there are M CPS application running on PM from P, implied as V = {v1, v2, …, vM}. It can be typical application as different VMs that has several VM samples [20]. In addition, it can be model the QoS indicator of VM scheduling as energy utilization, downtime, resource consumption rate to quantify the QoS requirement. Assume X = {x, x, …, xM} be VM scheduling policies to VM from V, where xm ∈ P(m = {1, 2, …, M}) refers the PM that VM vm has transferred to. Assume that Y = {y1, y2, …, yM} be the VM new utilization to the VM from V, where ym ∈ P(m = {1, 2, …, M}) is the PM that the VM vm has initially used on.
During this case, the proposed model concentrate on the QoS-aware VM scheduling technique for reducing the energy utilization, downtime, and resource consumption, and the VM scheduling problem was determined as:
This section inspects the performance validation of the CSPO-VMS technique under different numbers of applications such as 50, 100, 150, and 200. The results are compared with the benchmark, ESM, and QVMS techniques.
Tab. 1 and Fig. 3 investigate the resource utilization (RU) analysis of the CSPO-VMS technique with recent methods under distinct applications. The experimental results show that the CSPO-VMS technique has attained improved performance over the other techniques. For instance, with 50 applications, the CSPO-VMS technique has attained higher RU of 0.9254 whereas the benchmark, ESM, and QVMS techniques have obtained lower RU of 0.4347, 0.8248, and 0.8903 respectively. Moreover, with 100 applications, the CSPO-VMS technique has offered increased RU of 0.8865 whereas the benchmark, ESM, and QVMS techniques have resulted in reduced RU of 0.0.4112, 0.7725, and 0.8432 respectively. Furthermore, with 200 applications, the CSPO-VMS technique has accomplished maximum RU of 0.9023 whereas the benchmark, ESM, and QVMS techniques have reached maximum RU of 0.4400, 0.8196, and 0.8851 respectively.

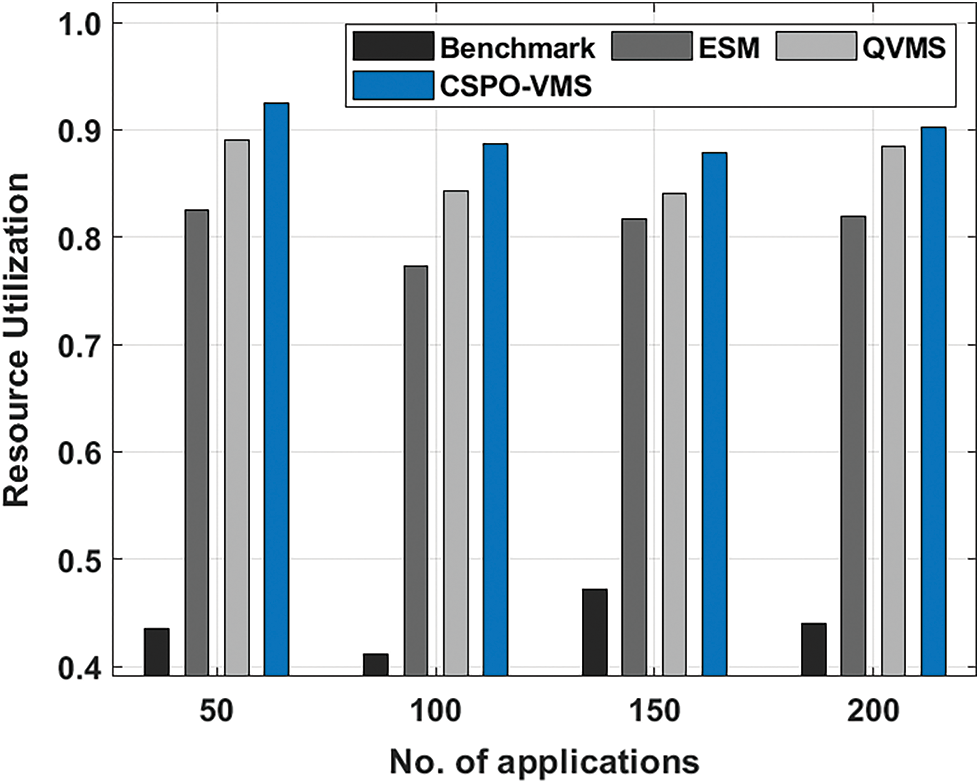
Figure 3: Resource utilization analysis of CSPO-VMS technique
The downtime analysis of the CSPO-VMS technique with other techniques under various applications is shown in Tab. 2 and Fig. 4. The experimental results stated the improvements of the CSPO-VMS technique by attaining least downtime compared to other methods. For instance, with 50 applications, the CSPO-VMS technique has offered lower downtime of 27.14 s whereas the benchmark, ESM, and QVMS techniques have reached higher downtime of 44.42, 43.38, and 34.16 s respectively. Along with that, with 200 applications, the CSPO-VMS technique has accomplished minimal downtime of 32.53 s whereas the benchmark, ESM, and QVMS techniques have depicted maximum downtime of 43.51, 37.54, and 35.46 s respectively.
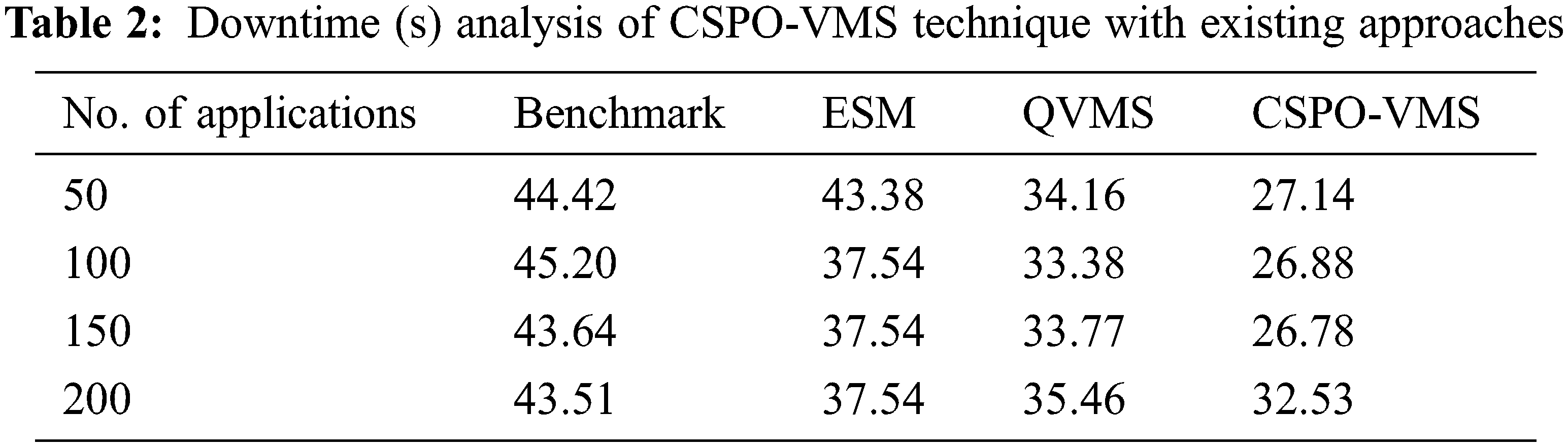
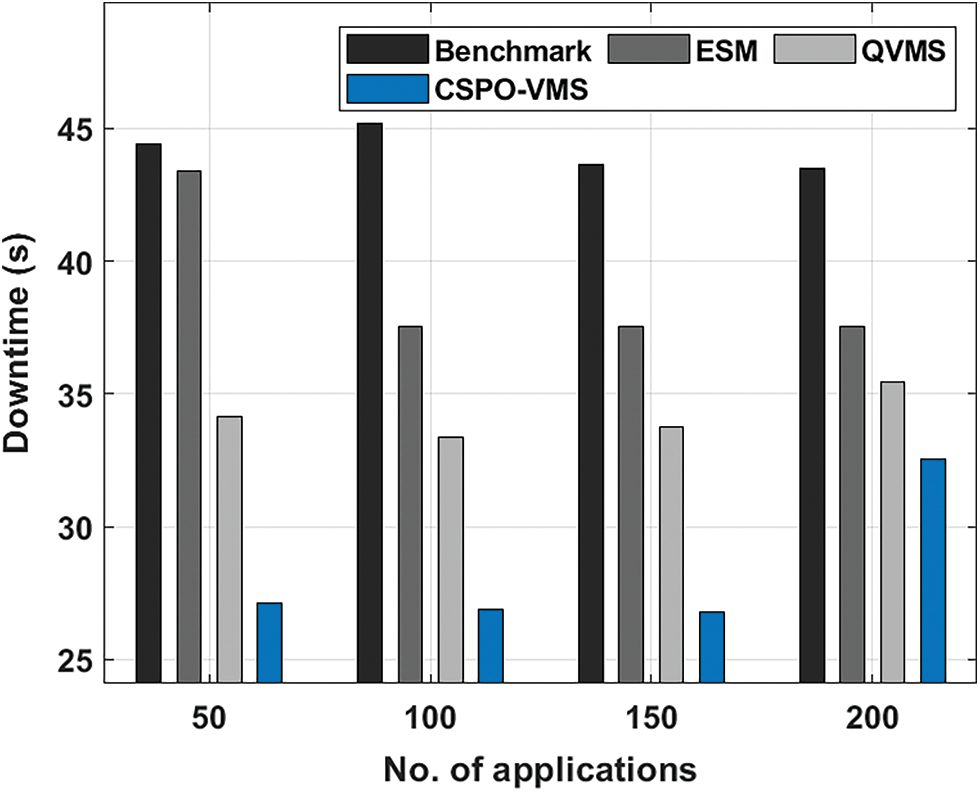
Figure 4: Downtime analysis of CSPO-VMS technique
The energy consumption based on VMs (ECVM) of the CSPO-VMS approach with other techniques under various applications is shown in Tab. 3 and Fig. 5. The experimental outcomes depicted the enhancements of the CSPO-VMS technique by attaining worse ECVM compared to other approaches. For instance, with 50 applications, the CSPO-VMS methodology has obtainable lower ECVM of 74.56 kW.h whereas the benchmark, ESM, and QVMS techniques have achieved to increased ECVM of 84.99, 80.79, and 78.69 kW.h respectively. Finally, with 200 applications, the CSPO-VMS technique has accomplished reduced ECVM of 312.67 kW.h whereas the benchmark, ESM, and QVMS systems have outperformed superior ECVM of 343.25, 336.95, and 335.90 kW.h respectively.
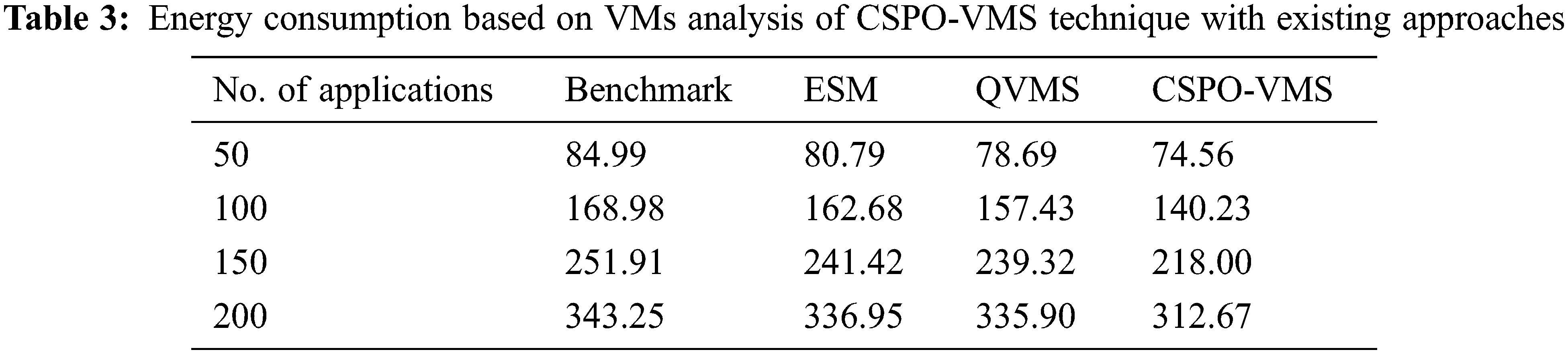
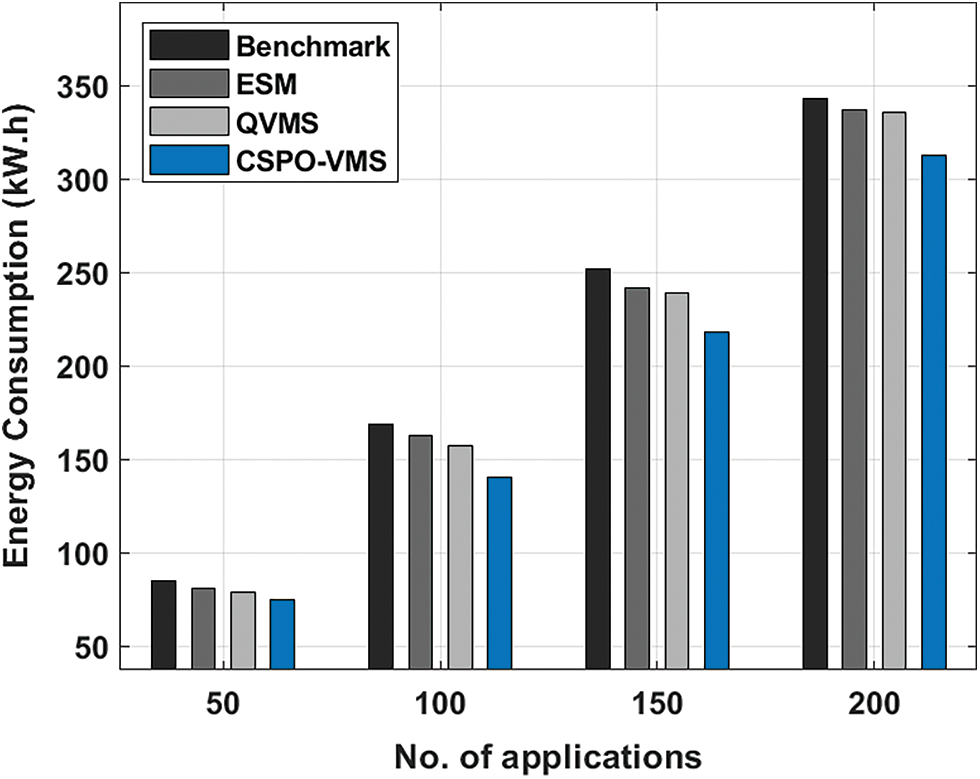
Figure 5: Energy consumption of running VMs on existing with proposed model
The energy consumption based on switches (ECS) of the CSPO-VMS system with other techniques under varying applications is illustrated in Tab. 4 and Fig. 6. The experimental results demonstrated the developments of the CSPO-VMS approach by obtaining lesser ECS compared to other techniques. For instance, with 50 applications, the CSPO-VMS technique has offered lower ECS of 64.14 kW.h whereas the benchmark, ESM, and QVMS techniques have reached to higher ECS of 88.60, 77.51, and 70.12 kW.h correspondingly. In addition, with 200 applications, the CSPO-VMS algorithm has accomplished minimal ECS of 198.65 kW.h whereas the benchmark, ESM, and QVMS methodologies have depicted enhanced ECS of 626.19, 326.91, and 253.01 kW.h correspondingly.
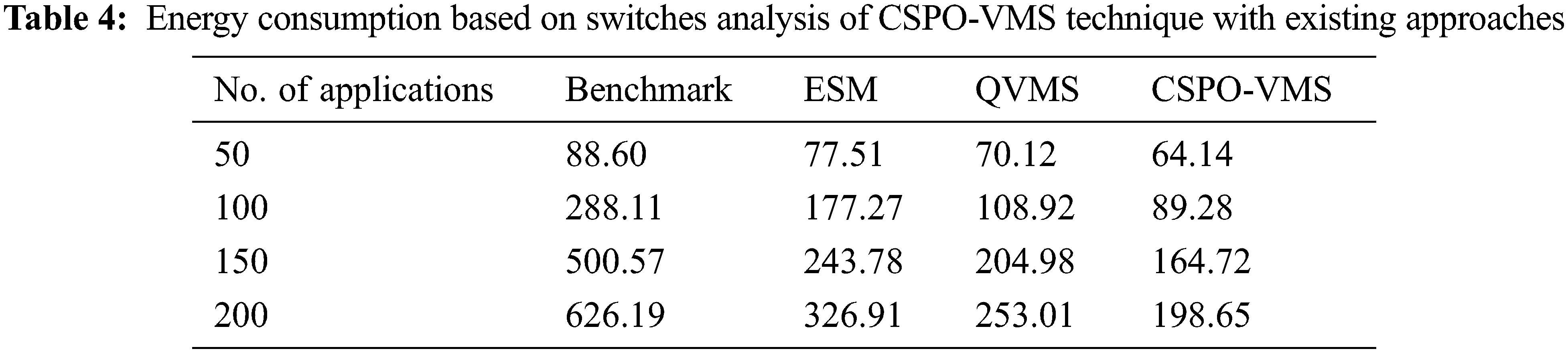
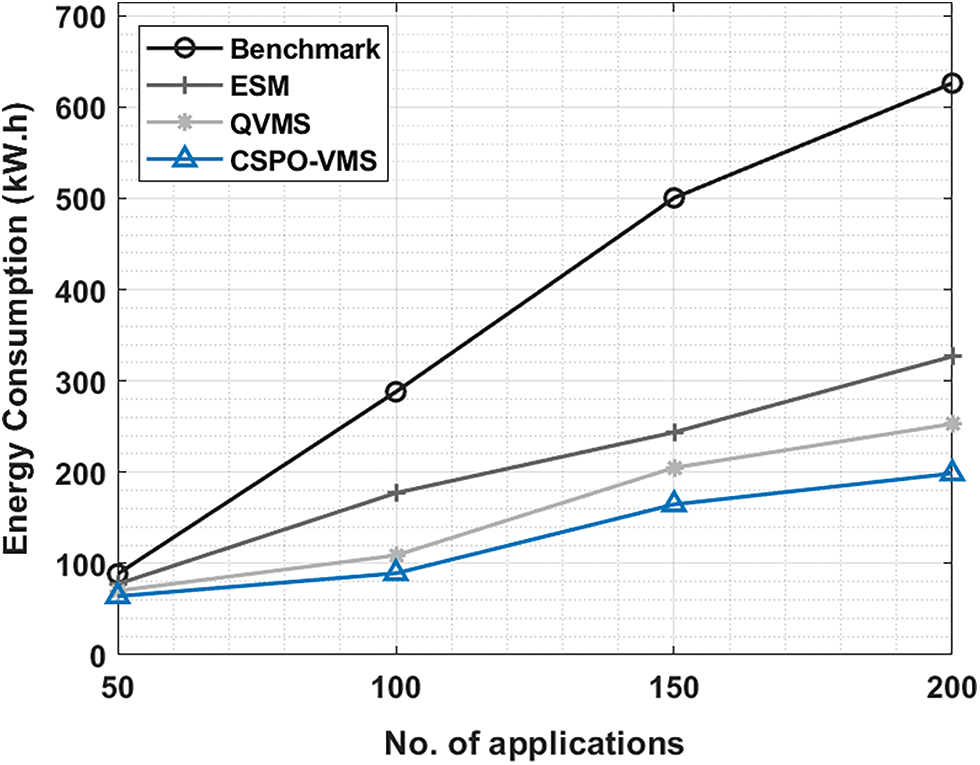
Figure 6: Energy consumption of switches on existing with proposed model
The number of running PMs (NRPM) of the CSPO-VMS approach with other methods under distinct applications are shown in Tab. 5 and Fig. 7. The experimental outcomes revealed the improvements of the CSPO-VMS approach by obtaining minimum NRPM compared to other algorithms. For instance, with 50 applications, the CSPO-VMS system has obtainable lower NRPM of 114.56 whereas the benchmark, ESM, and QVMS techniques have attained superior NRPM of 191.37, 160.27, and 143.52 correspondingly. Besides, with 200 applications, the CSPO-VMS algorithm has accomplished minimal NRPM of 617.95 whereas the benchmark, ESM, and QVMS methodologies have demonstrated higher NRPM of 830.27, 681.91, and 672.34 correspondingly.
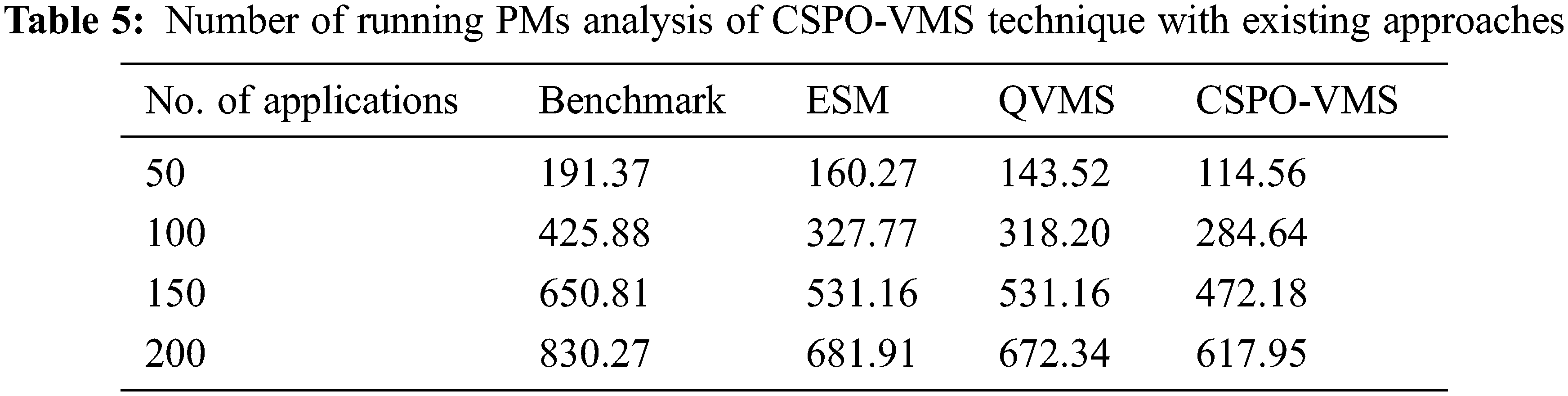
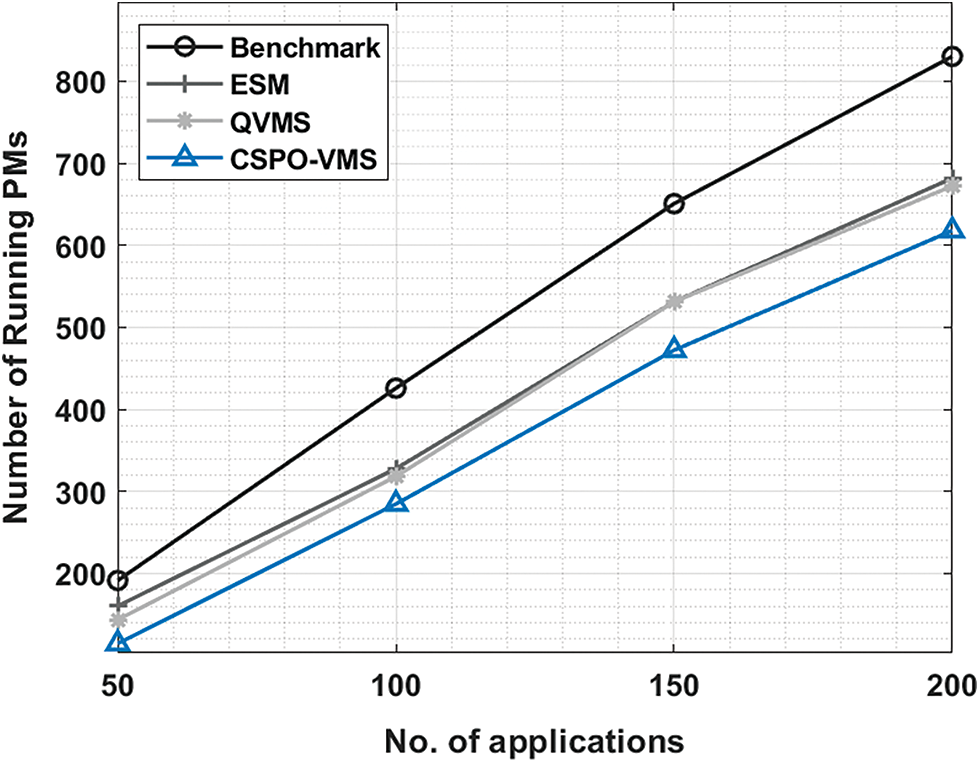
Figure 7: Number of running PMs on existing with proposed model
After examining the above results and discussion, it is ensured that the CSPO-VMS technique has the ability to accomplish superior performance over the other methods.
In this study, a novel CSPO-VMS technique has been presented for searching the optimum VM migration solution and it helps to choose an effective scheduling strategy. The CSPO algorithm integrates the concepts of traditional SPO algorithm with the chaos theory, which substitutes the main parameter and combines it with the chaos. For improving the process of determining the global optimum solutions and convergence rate of the SPO algorithm, the chaotic concept is included in the SPO algorithm. The CSPO-VMS technique has derived a fitness function to choose optimal scheduling strategy in the CPS environment. In order to demonstrate the enhanced performance of the CSPO-VMS technique, a wide range of simulations were carried out and the results are examined under varying aspects. The simulation results ensured the improved performance of the CSPO-VMS technique over the recent methods interms of different measures. In future, data aggregation schemes can be combined into the CPS to reduce energy dissipation.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. B. Jha, R. F. Babiceanu and R. Seker, “Formal modeling of cyber-physical resource scheduling in IIoT cloud environments,” Journal of Intelligent Manufacturing, vol. 31, no. 5, pp. 1149–1164, 2020. [Google Scholar]
2. D. Mourtzis and E. Vlachou, “A Cloud-based cyber-physical system for adaptive shop-floor scheduling and condition-based maintenance,” Journal of Manufacturing Systems, vol. 47, pp. 179–198, 2018. [Google Scholar]
3. J. R. Jiang, “An improved cyber-physical systems architecture for industry 4.0 smart factories,” in 2017 Int. Conf. on Applied System Innovation (ICASI), Sapporo, Japan, pp. 918–920, 2017. [Google Scholar]
4. M. G. Arani, A. Souri, F. Safara and M. Norouzi, “An efficient task scheduling approach using moth-flame optimization algorithm for cyber-physical system applications in fog computing,” Transactions on Emerging Telecommunications Technologies, vol. 31, no. 2, pp. 1–14, 2020. [Google Scholar]
5. K. M. Alam and A. El Saddik, “C2PS: A digital twin architecture reference model for the cloud-based cyber-physical systems,” IEEE Access, vol. 5, pp. 2050–2062, 2017. [Google Scholar]
6. W. Hao, P. Yao, T. Yang and Q. Yang, “Industrial cyber-physical system defense resource allocation using distributed anomaly detection,” IEEE Internet of Things Journal, pp. 1, 2021, https://doi.org/10.1109/jiot.2021.3088337. [Google Scholar]
7. C. Canali, L. Chiaraviglio, R. Lancellotti and M. Shojafar, “Joint minimization of the energy costs from computing, data transmission, and migrations in cloud data centers,” IEEE Transactions on Green Communications and Networking, vol. 2, no. 2, pp. 580–595, 2018. [Google Scholar]
8. W. Dou, X. Xu, S. Meng, X. Zhang, C. Hu et al., “An energy-aware virtual machine scheduling method for service QoS enhancement in clouds over big data,” Concurrency and Computation: Practice and Experience, vol. 29, no. 14, pp. e3909, 2017. [Google Scholar]
9. R. Gravina, C. Ma, P. Pace, G. Aloi, W. Russo et al., “Cloud-based activity-aaservice cyber–physical framework for human activity monitoring in mobility,” Future Generation Computer Systems, vol. 75, pp. 158–171, 2017. [Google Scholar]
10. M. S. Hasan, Y. Kouki, T. Ledoux and J. L. Pazat, “Exploiting renewable sources: When green sla becomes a possible reality in cloud computing,” IEEE Transactions on Cloud Computing, vol. 5, no. 2, pp. 249–262, 2017. [Google Scholar]
11. H. Mo and G. Sansavini, “Dynamic defense resource allocation for minimizing unsupplied demand in cyber-physical systems against uncertain attacks,” IEEE Transactions on Reliability, vol. 66, no. 4, pp. 1253–1265, 2017. [Google Scholar]
12. K. Gai and M. Qiu, “Optimal resource allocation using reinforcement learning for IoT content-centric services,” Applied Soft Computing, vol. 70, pp. 12–21, 2018. [Google Scholar]
13. M. Vilgelm, O. Ayan, S. Zoppi and W. Kellerer, “Control-aware uplink resource allocation for cyber-physical systems in wireless networks,” in European Wireless 2017; 23th European Wireless Conf., Dresden, Germany, pp. 1–7, 2017. [Google Scholar]
14. Y. Lu, X. Huang, Y. Dai, S. Maharjan and Y. Zhang, “Federated learning for data privacy preservation in vehicular cyber-physical systems,” IEEE Network, vol. 34, no. 3, pp. 50–56, 2020. [Google Scholar]
15. S. Li, Q. Ni, Y. Sun, G. Min and S. Al-Rubaye, “Energy-efficient resource allocation for industrial cyber-physical iot systems in 5 g era,” IEEE Transactions on Industrial Informatics, vol. 14, no. 6, pp. 2618–2628, 2018. [Google Scholar]
16. K. Gai, M. Qiu, H. Zhao and X. Sun, “Resource management in sustainable cyber-physical systems using heterogeneous cloud computing,” IEEE Transactions on Sustainable Computing, vol. 3, no. 2, pp. 60–72, 2018. [Google Scholar]
17. A. Kaur, S. Jain and S. Goel, “Sandpiper optimization algorithm: A novel approach for solving real-life engineering problems,” Applied Intelligence, vol. 50, no. 2, pp. 582–619, 2020. [Google Scholar]
18. J. Metan, A. Y. Prasad, K. S. A. Kumar, M. Mathapati and K. K. Patil, “Cardiovascular MRI image analysis by using the bio inspired (sand piper optimized) fully deep convolutional network (Bio-FDCN) architecture for an automated detection of cardiac disorders,” Biomedical Signal Processing and Control, vol. 70, pp. 103002, 2021. [Google Scholar]
19. M. Rajalakshmi and K. A. Panaiyappan, “A multimodal architecture using adapt-HKFCT segmentation and feature-based chaos integrated deep neural networks (Chaos-DNN-SPOA) for contactless biometricpalm vein recognition system,” International Journal of Intelligent Systems, vol. 37, no. 3, p. int.22758, 2021. https://doi.org/10.1002/int.22758. [Google Scholar]
20. L. Qi, Y. Chen, Y. Yuan, S. Fu, X. Zhang et al., “A QoS-aware virtual machine scheduling method for energy conservation in cloud-based cyber-physical systems,” World Wide Web, vol. 23, no. 2, pp. 1275–1297, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |