DOI:10.32604/csse.2023.026294

| Computer Systems Science & Engineering DOI:10.32604/csse.2023.026294 |  |
| Article |
Improved Dual-image Quality with Reversible Data Hiding Using Translocation and Switching Strategy
Department of Information Management, Chaoyang University of Technology, Taichung, 41349, Taiwan
*Corresponding Author: Kuo-Chung Chan. Email: s10914902@gm.cyut.edu.tw
Received: 21 December 2021; Accepted: 18 February 2022
Abstract: Dual-image reversible data hiding (RDH) is a technique for hiding important messages. This technology can be used to safely deliver secret messages to the recipient through dual images in an open network without being easily noticed. The recipient of the image must receive the two stego-images before the secret message can be completely retrieved. Imperceptibility is one of the main advantages of data hiding technology; to increase the imperceptibility, the quality requirements of the stego-images are relatively important. A dual steganographic image RDH method, called a DS-CF scheme that can achieve a better steganographic image quality using the center folding (CF) strategy. In this paper, we developed a translocation and switching strategy (TaS) to shorten the distances between the stego-pixel coordinates and the cover pixel coordinates after information being hidden. Compared with the DS-CF scheme, our proposed DS-TaS scheme can effectively improve the quality of the steganographic images at the same level of embedding capability. The experimental results show that the PSNR of our DS-TaS scheme at
Keywords: Information hiding; reversible data hiding (RDH); dual-image RDH; center folding (CF) strategy
With the advances in information technology, the Internet has become an indispensable tool in human life; in particular, the Internet of Things along with 5G networks will produce a higher speed and greater data transmission on the network. Many transactions in a virtual environment can be easily, quickly, effectively, and conveniently conducted. However, data in these transactions may be illegally stolen, monitored, tampered, copied, and/or damaged during the transfer process. Therefore, security is a prerequisite in the virtual environment, and convenient functions in a secure environment have been in high demand.
To protect digital data and privacy from being infringed, encryption technology has been more commonly used. The sending parties use a key to generate the cipher text of the digital data and transmit the cipher text to the receiving parties. The data party uses the same key to restore the digital data; therefore, even if it is stolen during the transmission process, the original data cannot be known without the key. However, because the data during the transmission process are unintelligible cipher text, although it is impossible to know the original data, it is easy for the person of interest to know whether the data are cipher text, and if so, tamper with or destroy them. Even if the receiving party has the key, the data of the original sender cannot be smoothly obtained. Therefore, if privacy and important data are hidden in the transmitted media, such as pictures, images, sounds, texts, and other digital data, and not easily detected, they can be safely transmitted to the recipient without being detected or tampered with. To achieve the goal of information security, hiding plays an extremely important role in data transmission in a virtual environment.
Information hiding technology can be divided into non-reversible [1–4] and reversible [5–8] data hiding technology, depending on whether the cover image can be restored. Information hiding technology means that when the cover image is embedded with confidential information, it cannot be restored without distortion after the confidential information is retrieved. Extraction is a reversible information-hiding technology. A reversible dual image method can restore the original image that was first generated after removing the secret messages, and thus it can be used in military information transmission and medical applications that do not allow an image distortion.
The dual-image reversible data hiding (RDH) method uses the original image to generate two identical images, and then uses these two generated images to hide the secret message. This method is similar to the secret sharing method in cryptography, which involves splitting the secret in an appropriate manner. Each share after splitting is managed by a different participant, and secret information cannot be recovered by a single participant. Secret information can only be obtained through cooperation among these players.
This study proposes a translocation and switching (TaS) strategy that uses translocation and switching operations to effectively shorten the distance between the cover pixel coordinates and the stego-pixel coordinates. We use the TaS strategy to hide information on dual images, which is called the DS-TaS scheme. The DS-TaS scheme improves the image quality of the DS-CF scheme under the same payload, and can achieve almost the same quality of the dual images.
The contributions of this research are as follows:
1. We developed a translocation and switching strategy, referred to as the TaS strategy, to shorten the distances between the stego-pixel coordinates and the cover pixel coordinates after information hiding.
2. To effectively improve the image quality, we proposed a dual steganographic image reversible data hiding method called the DS-TaS scheme based on the TaS strategy.
3. The DS-TaS scheme carries out (2, 2) secret sharing through a simple information hiding process, preventing over-concentration of secrets and providing efficient dispersal of information for security and load balancing.
In 2007, Chang et al. proposed an exploiting modification direction (EMD) method based on dual-image reversible information hiding [9], hereinafter referred to as a DS-EMD scheme. For 8-bit gray images, pixel values are integers that range from 0 (black) to 255 (white). Therefore, the DS-EMD scheme creates a 256 × 256 reference matrix (
In 2009, Lee et al. proposed a two-image reversible information hiding method based on the position and direction [10]. This technology uses two stego-pixels to match the four directions of the cross pattern to generate stego-pixels into a double image; thus, we abbreviate this method as the DS-Cross scheme. The DS-EMD scheme defines two sets of 2-bit data in four combinations in the upper, lower, left, and right directions of the center of the cross coordinates. Therefore, when embedding confidential information, two stego-pixel pairs can be generated based on a combination of the information in the cross coordinates. In 2013, Lee and Huang proposed a dual-image reversible information hiding method based on the orientation [11], which is referred to as the DS-OD scheme. The DS-OD scheme defines 25 rules for embedding information and controls the camouflage and original pixel pairs. The range of variation of the pixel pair improves the information load of both the DS-EMD and DS-Cross schemes. In 2014, Chang et al. proposed a two-image reversible information hiding method based on a tortoise shell [12], hereinafter referred to as the DS-TS scheme. The embedding method of the DS-TS scheme is similar to that of the DS-EMD scheme, and the main key technology is to develop a reference matrix with hexagonal turtle shells that are continuously and closely adjacent to each other. Each tortoise shell contains eight different numbers, ranging from 0 to 7.
In 2015, Lu et al. proposed a two-image reversible information hiding method with a central fold strategy [13], referred to as the DS-CF scheme. The center-folding strategy converts all
The DS-CF scheme uses the concept of the averaging method to hide
where
The DS-CF scheme of the central fold strategy recodes the secret values to reduce the difference between the stego-pixel and the original pixel, thereby improving the stego-image quality. The hiding process is as shown in Fig. 1.

Figure 1: Schematic diagram of the hiding process of the central folding strategy

Figure 2: Schematic diagram of
In 2017, Yao et al. proposed using the selection strategy of shiftable pixels [14] (DS-SP scheme) to improve the collection of DS-CF schemes. The DS-SP scheme of Yao et al. finds more space to hide information through the central folding strategy. As key technology, if
In this section, Section 3.1 elaborates on the viewpoints of this research method and describes how to use the translocation and switching strategy (TaS strategy) to optimize the quality of the stego-image. Section 3.2 proposes a reversible dual image information hiding method based on the TaS strategy.
The DS-CF scheme method takes one cover pixel
It is worth noting that the position of the red frame in Fig. 3 is the coordinates of the stego-pixel pair
This research proposes a translocation and switching (TaS) strategy, which uses translocation and switching operations to effectively shorten the distance between the cover pixel coordinates and stego-pixel coordinates. The TaS strategy can make full use of

Figure 3: The relative positions of the stego-pixels (
The proposed TaS strategy defines two manipulation functions: translocation () and switching ().
The translocation function is
Through the
Taking
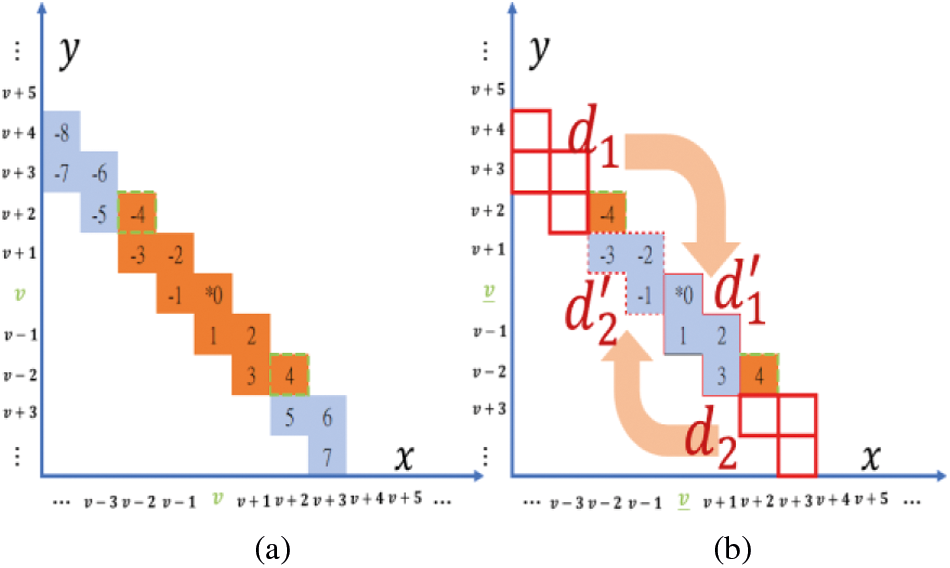
Figure 4: TaS strategy (translocation manipulation)
Again, taking
For the switching manipulation, when
Assuming
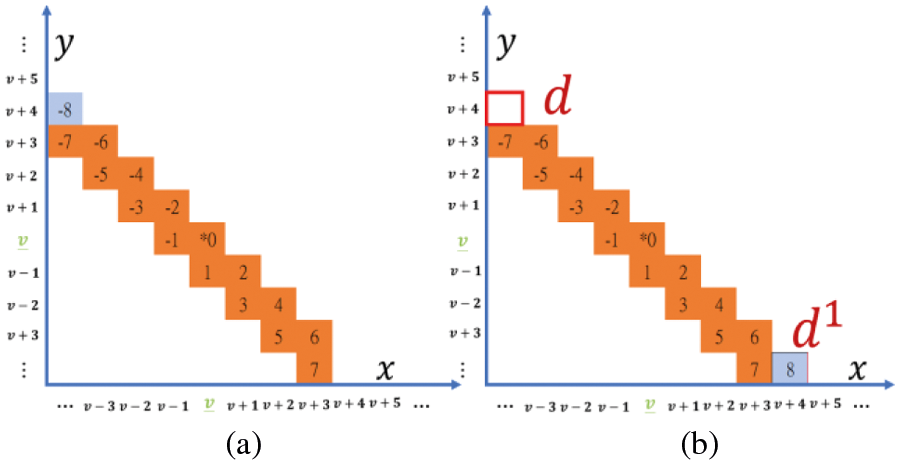
Figure 5: TaS strategy (switching function)
3.2 Proposed Dual Stegano Image Method
Using the TaS strategy, we propose a dual stegano image RDH method, referred to as the DS-TaS scheme. In contrast to the DS-CF scheme, our DS-TaS scheme takes out two secret messages
Input: An original image
Output: Two stego-images
Step 1: For
Step 2: Extract two sets of secret bytes each time, namely, (
Step 3: Use the center-folding strategy to convert
Step 4: If the condition
Step 5: If the conditions of Step 4 are true, use the TaS strategy to calculate the two pairs of stego-pixels (
Case 1:
Case 2: i
Case 3:
Step 6: Let
The following sections describe the process of using the TaS strategy to embed information. Let
Case 1: When
For the black part shown in Figs. 6a1 and 6a2,
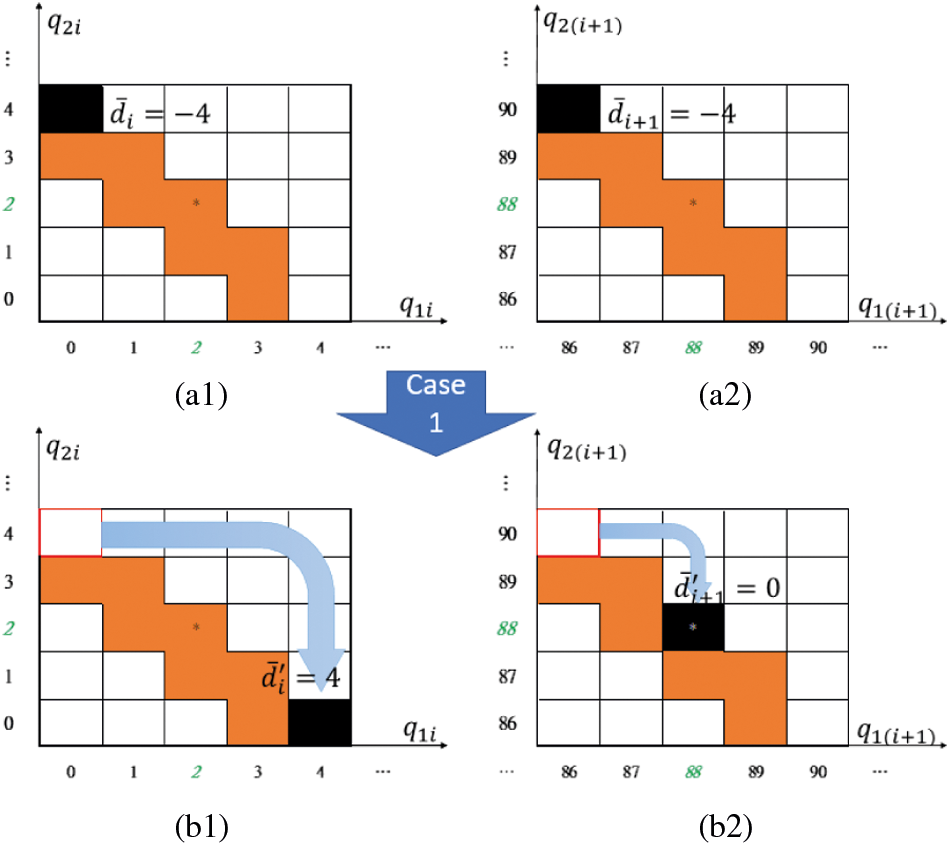
Figure 6: Case1: switching (
The probability of occurrence of the condition is observed as follows, where the image size is H × W. For a grayscale image with a size of 512 × 512, where the 3-bit data are to be hidden into a pair of cover pixels, the image will be modified into 2048 pixels.
Case 2: When
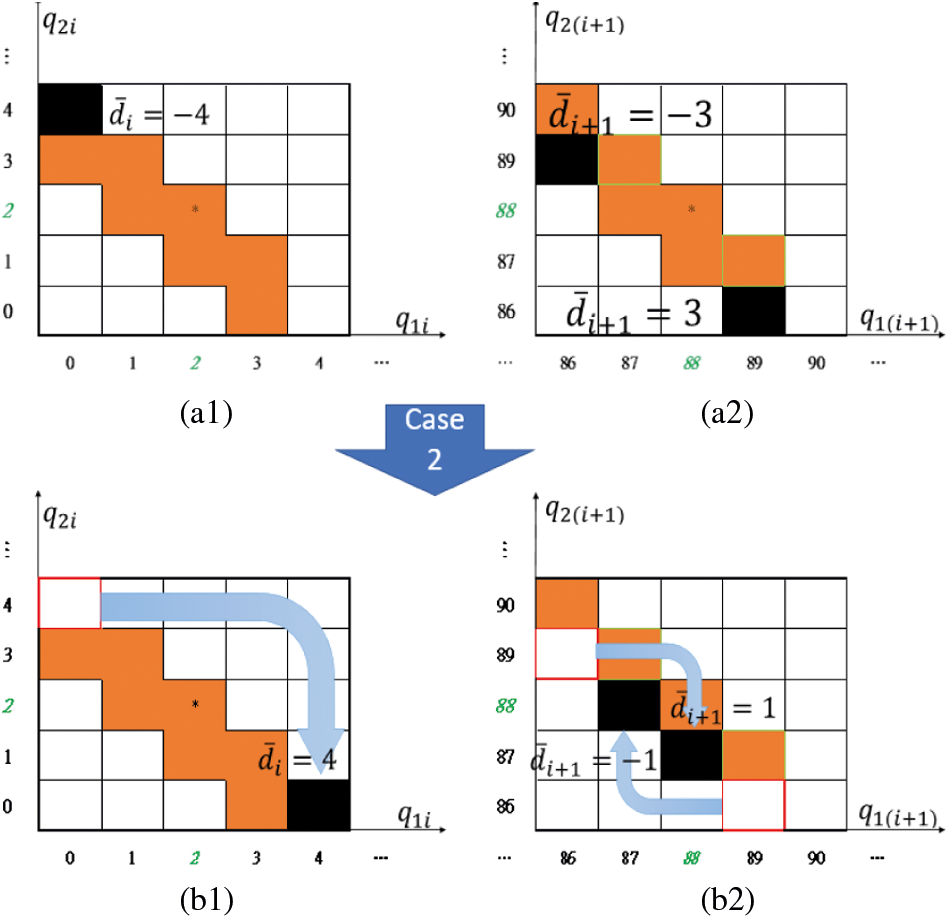
Figure 7: Case2: switching (
The number of pixels that the image will be modified into is shown below.
Case 3: When
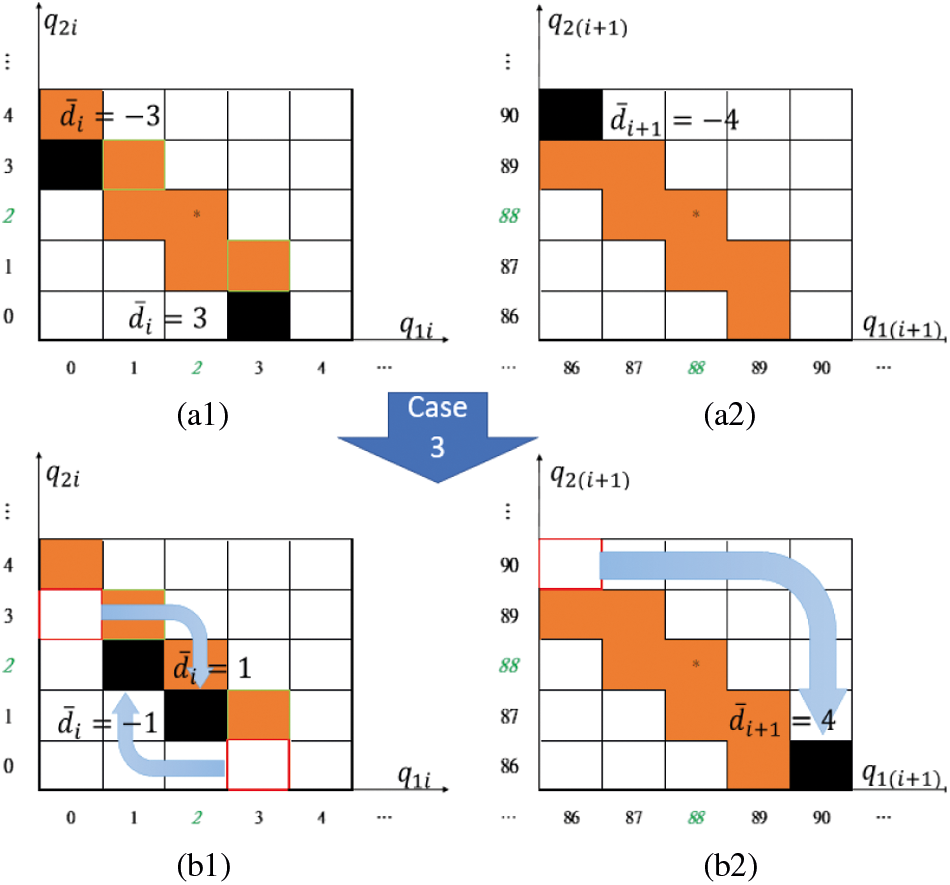
Figure 8: Case3: switching (
The two pairs of stego-pixels hidden are as follows:
The number of pixels that the image will be modified into is the same as in Case 2.
3.3 Data Extraction and Image Recovery Procedure
Input data: Stego-image
Output data: Cover image
Step 1: First, take out two pairs of pixels {
Step 2: Restore the pixel pair {
Step 3: Calculate
Case 1: if
Case 2: if
Case 3: if
Step 4: By Eq. (4),
Step 5: Convert
Section 4.1 describes the experiment environment and metrics evaluation. Section 4.2 presents the reduction in the number of shifted pixels through the proposed DS-Tas scheme. Finally, Section 4.3 shows the results and benefits of the DS-TaS scheme compared with other methods.
4.1 Experiment Environment and Metrics Evaluation
The experiment uses MATLAB R2017ab software to implement the proposed method and compare the results with those of other methods. We used six commonly applied standard grayscale images (size 512 × 512) as test images, i.e., Lena, Goldhill, Peppers, Baboon, Barbara, and Boat, as shown in Fig. 9.
Figure 9: Six standard grayscale images
The distortion in a stego-image can be measured based on the peak signal-to-noise ratio (PSNR), which can be computed using Eq. (3), where
The bits per pixel (bpp) provide the average embedding capacity for each pixel. The higher the bpp value is, the greater the embedding capacity. The total embedding capacity must be divided by 2 to apply dual images to hide the secret information. Eq. (4) shows the calculation method used to express the capacity of each image to carry information.
We calculated the length of the secret information that can be carried by each pixel
Observing the various evaluation indicators in the Lena image, when
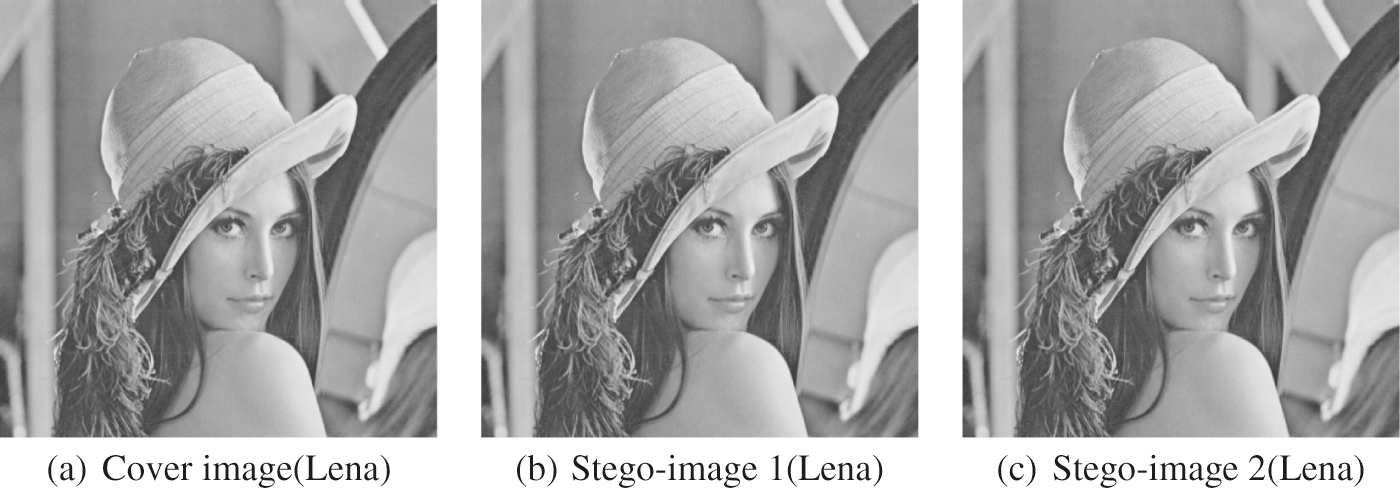
Figure 10: Visual quality results of proposed scheme when
4.2 Using DS-Tas Scheme to Reduce Shifted Pixels
The DS-TaS scheme is used to optimize the DS-CF scheme [13]; therefore, when observing all pixels of the two stego-images hidden using the DS-CF scheme, it is important that the sum of the pixels and the MSE be optimized by the DS-TaS scheme. The MSE is the square of the difference between the mask and stego-pixels. The larger the value is, the worse the displayed image quality, as shown in Eq. (3).
As shown in Tab. 1. this method is used to adjust the conditions of Case 1, Case 2, and Case 3 in a stego-image under
In Tab. 1, “the number of adjusted pixels” shows that our method reduces the number of pixel modifications compared to the DS-CF method under the same embedding capacity. In addition, “MSE reduction” represents the difference between the MSEs of the two methods. In the process of hiding the message, when

4.3 Comparison of DS-TaS Scheme with Other Methods
Tab. 2 shows the DS-TaS scheme and other methods proposed in this paper, i.e., Lee et al. [10], Lee et al. [11], Lu et al. [15], Jafar et al. [16], and Lu et al. [13] for
In the proposed DS-TaS scheme, when

In Tab. 3, the DS-TaS method (when

In this study, a translocation and switching strategy (TaS strategy) is proposed that uses switching and transposition functions to calculate a “re-encoding substitute” of a confidential message such that the changes from the original pixels are significantly reduced, thus effectively improving the image quality. The results show that when the hiding capacity is the same, the quality of the stego-image of the proposed DS-TaS scheme is better than that of the other methods. Compared with the DS-CF scheme proposed, the proposed DS-TaS scheme can effectively improve the quality of stenographic images. Not only does our method achieve a better performance in terms of the image quality, it also has more options than the DS-CF method in terms of the embedding capacity for each stego-pixel. It can hide 0.5 bits for each stego-pixel and can be applied to produce higher-quality stego-images.
Our proposed DS-TaS RDH scheme produces high image quality, and the quality of the 2 images is similar, so an attacker cannot suspect that the image carries a secret message. In addition, because of the spirit of (2, 2) secret sharing, a legal person with two secret images can fully extract the secret information. Therefore, this dual-image-based technology can avoid excessive concentration of information, thereby achieving risk dispersion and load balancing.
In the future, the method will be strengthened by combining it with other reversible dual-image approaches to improve the quality of information hiding images and increase imperceptibility requirements.
Acknowledgement: We are grateful to all authors who participated in this research.
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. C. K. Chan and L. Cheng, “Hiding data in images by simple LSB substitution,” Pattern Recognition, vol. 37, no. 3, pp. 469–474, 2004. [Google Scholar]
2. J. Mielikainen, “LSB matching revisited,” IEEE Signal Processing Letters, vol. 13, no. 5, pp. 285–287, 2006. [Google Scholar]
3. R. Z. Wang, C. F. Lin and J. C. Lin, “Image hiding by optimal LSB substitution and genetic algorithm,” Pattern Recognition, vol. 34, no. 3, pp. 671–683, 2001. [Google Scholar]
4. X. Zhang and S. Wang, “Efficient steganographic embedding by exploiting modification direction,” IEEE Communications Letters, vol. 10, no. 11, pp. 781–783, 2006. [Google Scholar]
5. Z. Ni, Y. Shi, N. Ansari and W. Su, “Reversible data hiding,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 16, no. 3, pp. 354–362, 2006. [Google Scholar]
6. J. Tian, “Reversible data embedding using a difference expansion,” IEEE Transactions on Circuits and Systems for Video Technology, vol. 13, no. 8, pp. 890–896, 2003. [Google Scholar]
7. C. C. Chang, K. T. Duc and Y. C. Chou, “Reversible data hiding scheme using two steganographic images,” in Proc. of TENCON 2007, Taipei, Taiwan, pp. 1–4, 2007. [Google Scholar]
8. C. F. Lee, K. H. Wang, C. C. Chang and Y. L. Huang, “A reversible data hiding scheme based on dual steganographic images,” in Proc. of the Third Int. Conf. on Ubiquitous Information, New York, NY, USA, pp. 228–237, 2009. [Google Scholar]
9. C. C. Chang, T. D. Kieu and Y. C. Chou, “Reversible data hiding scheme using two stenographic images,” in Proc. of IEEE Region Tenth Int. Conf. (TENCON), Taipei, Taiwan, pp. 1–4, 2007. [Google Scholar]
10. C. F. Lee, K. H. Wang, C. C. Chang and Y. L. Huang, “A reversible data hiding scheme based on dual steganographic images,” in Proc. of the Third Int. Conf. on Ubiquitous Information Management and Communication, New York, NY, USA, pp. 228–237, 2009. [Google Scholar]
11. C. F. Lee and Y. L. Huang, “Reversible data hiding scheme based on dual stegano images using orientation combinations,” Telecommunication Systems, vol. 52, no. 4, pp. 2237–2247, 2011. [Google Scholar]
12. C. C. Chang, Y. J. Liu and T. S. Nguyen, “A novel turtle shell based scheme for data hiding,” in Proc. of the Tenth Int. Conf. on Intelligent Information Hiding and Multimedia Signal Processing Conf. IIH-MSP, Kitakyushu, Japan, pp. 89–93, 2014. [Google Scholar]
13. T. C. Lu, J. H. Wu and C. C. Huang, “Dual-image based reversible data hiding method using center folding strategy,” Signal Processing, vol. 115, no. 4, pp. 195–213, 2015. [Google Scholar]
14. H. Yao, C. Qin, Z. J. Tang and Y. Tian, “Improved dual-image reversible data hiding method using the selection strategy of shiftable pixels’ coordinates with minimum distortion,” Signal Processing, vol. 135, no. 8, pp. 26–35, 2017. [Google Scholar]
15. T. C. Lu, C. Y. Tseng and J. Wu, “Dual imaging-based reversible hiding technique using LSB matching,” Signal Processing, vol. 108, no. 4, pp. 77–89, 2015. [Google Scholar]
16. I. F. Jafar, K. A. Darabkh, R. T. Al-Zubi and R. R. Saifan, “An efficient reversible data hiding algorithm using two steganographic images,” Signal Processing, vol. 128, no. 2, pp. 98–109, 2016. [Google Scholar]
17. T. C. Lu, N. Yang and T. C. Chang, “Reversible hiding method base on double image using center fording strategy and interval scale,” Communications of the CCISA, vol. 24, pp. 1–17, 2018. [Google Scholar]
18. X. Chen and W. Guo, “Reversible data hiding scheme based on fully exploiting the orientation combinations of dual stego-images,” International Journal of Network Security, vol. 22, pp. 126–135, 2020. [Google Scholar]
19. T. C. Lu, N. Yang and T. N. Vo, “Dual stego-images based lossless steganographic scheme with interval scale table,” Journal of Computers, vol. 32, pp. 1–7, 2021. [Google Scholar]
20. W. He and Z. Cai, “Reversible data hiding based on dual pairwise prediction-error expansion,” IEEE Transactions on Image Processing, vol. 30, pp. 5045–5055, 2021. [Google Scholar]
21. Z. Wang, A. C. Bovik and H. R. Sheikh, “Image quality assessment: From error visibility to structural similarity,” IEEE Transactions on Image Processing, vol. 13, no. 4, pp. 600–612, 2004. [Google Scholar]
22. H. R. Sheikh and A. C. Bovik, “Image information and visual quality,” IEEE Transactions on Image Processing, vol. 15, no. 2, pp. 430–444, 2006. [Google Scholar]
23. W. Xue and L. Zhang, “Gradient magnitude similarity deviation: An highly efficient perceptual image quality index,” IEEE Transactions on Image Processing, vol. 23, no. 2, pp. 684–695, 2014. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |