DOI:10.32604/csse.2022.021694

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.021694 |  |
| Article |
QoS Constrained Network Coding Technique to Data Transmission Using IoT
1Department of ECE, The Kavery Engineering College, Mecheri, 636453, Tamilnadu, India
2Department of EEE, Karpagam College of Engineering, Coimbatore, 641032, India
3Department of EEE, M. Kumarasamy College of Engineering, Karur, 639113, India
4Department of Computer Science and Engineering, CMR Technical Campus, Hyderabad, 501401, India
5Department of CST, Manav Rachna University, Faridabad, 121004, India
6Department of EEE, Kongu Engineering College, Perundurai, 638060, India
7Department of EEE, Nandha Engineering College, Perundurai, Tamilnadu, 638052, India
*Corresponding Author: A. Sathishkumar. Email: aasathishkumar2021@gmail.com
Received: 11 July 2021; Accepted: 27 August 2021
Abstract: The research work presents, constrained network coding technique to ensure the successful data transmission based composite channel cmos technology using dielectric properties. The charge fragmentation and charge splitting are two components of the filtered switch domino (FSD) technique. Further behavior of selected switching is achieved using generator called conditional pulse generator which is employed in Multi Dynamic Node Domino (MDND) technique. Both FSD and MDND technique need wide area compared to existing single node-keeper domino technique. The aim of this research is to minimize dissipation of power and to achieve less consumption of power. The proposed research, works by introducing the method namely Interference and throughput aware Optimized Multicast Routing Protocol (IT-OMRP). The main goal of this proposed research method is to introduce the system which can forward the data packets towards the destination securely and successfully. To achieve the bandwidth and throughput in optimized data transmission, proposed multicast tree is selected by Particle Swarm Optimization which will select the most optimal host node as the branches of multi cast tree. Here node selection is done by considering the objectives residual energy, residual bandwidth and throughput. After node selection multi cast routing is done with the concern of interference to ensure the reliable and successful data transmission. In case of transmission range size is higher than the coverage sense range, successful routing is ensured by selecting secondary host forwarders as a backup which will act as intermediate relay forwarders. The NS2 simulator is used to evaluate research outcome from which it is proved that the proposed technique tends to have increased packet delivery ratio than the existing work.
Keywords: Multicast routing; optimal node selection; secondary relay nodes; probability of interference; residual energy; bandwidth; throughput
Environmental monitoring system in home based applications, wearable devices like sensors are integrated with applications which interact and accessed remotely to the people [1]. A recent developmental application like smart city, smart medical system, smart transports etc uses IoT for its deployment [2]. IoT is used in high end sensing applications like information sensing, data transmission, cloud distributed system for storage and process [3]. Other applications are E-healthcare, Internet of medical things, digital security, smart watch so on. These major applications are interconnected using 4G and 5G architectures [4].
IoT data are generated based on core network of IoT. Various data is sensed by smart device and transmitted to the network via IoT devices [5]. The loss of data packets and fake data interferences in IoT are due wireless communication of IoT [6]. Finally invention of software defined networks becomes very useful to improve IoT communication system [7].
The QoS improving techniques in ad hoc networks are well studied, where the main goal is to develop the parameters used in QoS [8]. However, security system needs are not paid attention and main problem id enhancing QoS in ad hoc networks [9]. A application widely depend on QoS for security provision, such as network security from Denial of Service attacks and fabrication based attacks [10]. The patient health monitoring system requires data integrity and timely computation of data in network. So QoS is considered as significant task for reducing delay and high throughput problems. QoS provides fined tuned channels for data communication [11].
The dynamic IoT networks can be easily run and execute in a wireless system [12]. The intruders can be captured easily and it manipulate illegally of any information transfer via wireless communication. Therefore, in same time multiple identities used to transmit same data by an adversary, which is called as Sybil attack. A Sybil attack leads to impersonation , Denial of Service, and other similar attacks [13]. Thus finally degrading happens in the QoS provisioning, apart from issues like Link and MAC layer in ad hoc networks.
The main aim of this research work is to introduce the techniques that can perform optimal and reliable data communication in the IoT network that consists of millions of small devices. This is done by adapting the network coding and the multicast routing to ensure the optimal and reliable data transmission. To achieve this various optimization algorithms and the network coding techniques have been adapted.
The overall structure of the research work is given as follows: In this section detailed introduction about the IoT devices and the need of data communication has been given. In Section 2, discussion about the various related research technologies has been given. In Section 3, detailed overview of the proposed research techniques in terms of their working procedure along with suitable examples and explanation is given. In Section 4, discussion of the simulation outcome of the proposed techniques and their comparison evaluation with the existing techniques are given. Finally in Section 5, overall conclusion of the research work based on simulation outcome is given.
Zhao et al. [14] proposed model for flow of data. It tends to capture the every data transmission among IoT device. The process works from starting stage (creating redundancy using original data) to the various stage of repair with fewer devices.
Zhao et al. [15], the offloading technique is proposed smartly via deep reinforcement learning technique. In this procedure, automatic learning is done using deep Q network. The decision of offloading helps to optimize the performance of system and trained neural network helps to predict action in offloading. The environmental system helps to generate the trained data.
Pustišek et al. [16] discusses about Distributed Low-Bandwidth Applications architecture—an gateway with application awareness among Internet of things (IoT) communication devices. A backend of cloud servers connected to modular technologies and messaging formats are managed. The native API application logic meets the communication conditions of limited resources of end devices.
Ma et al. [17] implemented two techniques for bandwidth optimization and flows allocation: the method network utility maximization (NUM) and asymptotic examination method. The NUM technique gives general optimization solution for the problem, but certain computational complexity is required. The analysis using asymptotic techniques examines inherent network property and solution are explicitly expressed in terms parameters in protocol and traffic requirements.
Gravalos et al. [18] implemented Integer Linear Programming (ILP) to decrease networks total cost with respect to the deployed devices. Here it focus to achieve QoS requirements. The solution for random topology reveals effectiveness in less networking cost and high efficiency.
Peng et al. [19] proposed healthcare design to monitor the reliable data communication mechanism with requirements of using many-to-one streaming technique. This Fault-tolerant in coding Mechanism of network proposes a greedy algorithm based on grouping. It divides network topology into small logical units; it generates coding for linear network using spanning tree randomly. Further it also helps to generate independent linear coding in linear combination.
Gravalos et al. [20] brings great planning for the problem known as integer linear program (ILP). This formula reduces the device cost which is deployed in the network and also achieves QoS needs. Authors suggest heuristic techniques with less complexity which was experimental to present solutions near optimal outcome. The result evaluation exhibits the performance and effectiveness of the proposed techniques in parameters using cost of network and network efficiency.
Hasan et al. [21] proposed formulation using analytics for the error rate and a decisive path-loss structure is defined using specified level. There is also trust among nodes that are most frequently used. Additionally, irregular in the degree is addressed using parameters. The geographical transmission across distributed networks switches based on two schemes: 1. hop-by-hop retransmission scheme and 2. end-to-end retransmission scheme.
Cao et al. [22] implements technique for saving energy across mobile network. IoT devices are battery powered applications which tends to perform real-time approximate computation under the quality-of-service (QoS) constraint. Li et al. [23] promotes hybrid technique for automation using average CSI being available at the transmitter. It improves system performance at high level.
3 Interference and Throughput Aware Multicast Routing
The main aim of this proposed research method is to introduce the system which can forward the data packets towards the destination securely and successfully. The proposed research method introduces the following research methods to achieve the bandwidth and throughput optimized data transmission. Multicast tree is selected by introducing the optimization approach namely Particle Swarm Optimization which will select the most optimal host node as the branches of multi cast tree. Here node selection is done by considering the objectives residual energy, residual bandwidth and throughput. After node selection multi cast routing is done with the concern of interference to ensure the reliable and successful data transmission. In case of transmission range size is higher than the coverage sense range, successful routing is ensured by selecting secondary host forwarders as a backup which will act as intermediate relay forwarders. The processing flow of the proposed research method is shown in the following Fig. 1.
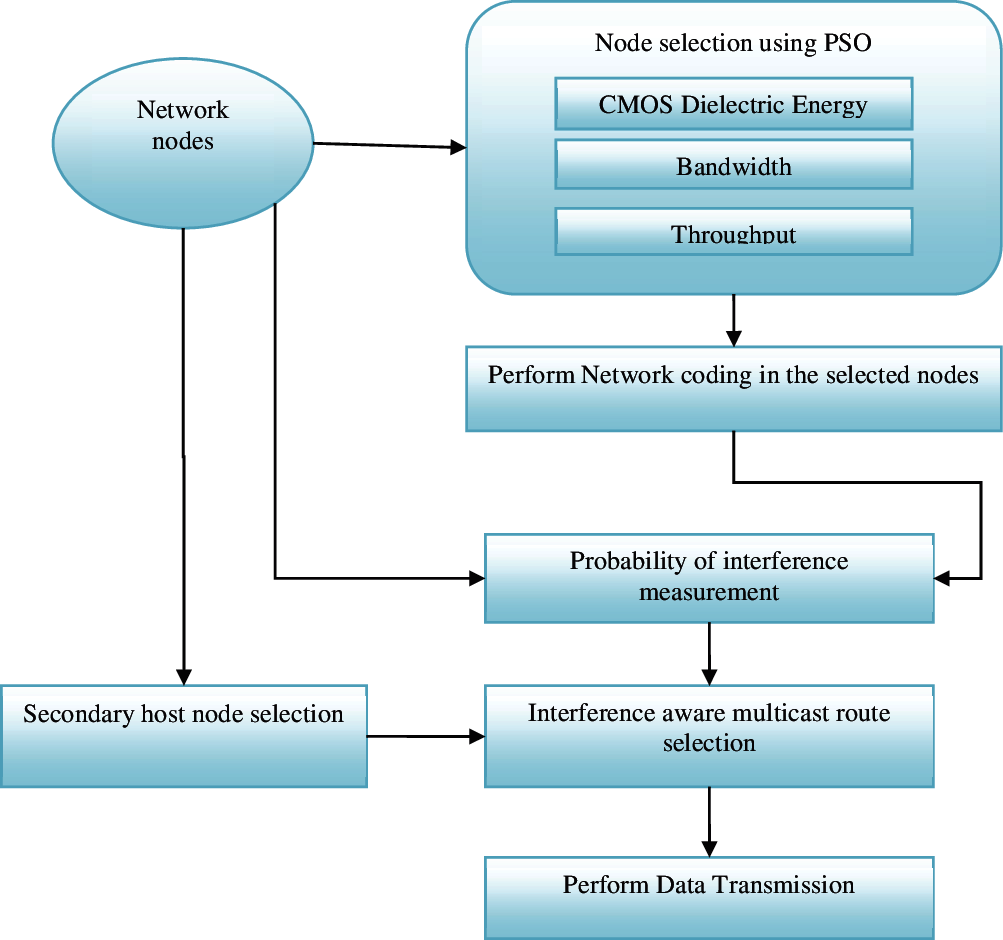
Figure 1: Processing flow of the proposed research work
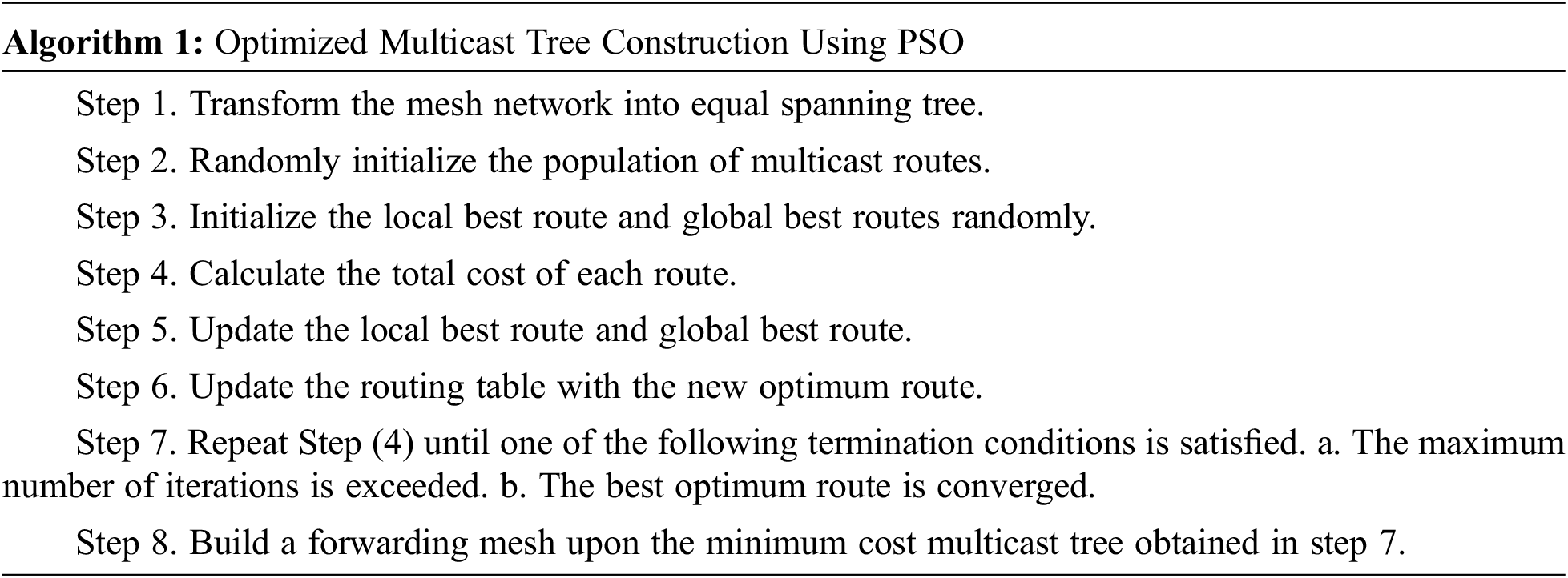
3.1 Optimized Multicast Tree Construtction Using PSO
The PSO is a stochastic population-based evolutionary computational algorithm for problem solving. A multicast routing problem is given and a fitness function is used to evaluate a proposed optimal route. The communication structure, which assigns a neighbour for each individual to interact with it, is also defined. The fitness evaluation function iteratively evaluates the fitness of the population of multicast routes and remembers the location where they had their best success. The best optimal route of an individual is called the local best. Each set of nodes that forms a route makes this information available to its neighbour nodes. Here node selection is done by considering the objectives residual energy, residual bandwidth and throughput. The On-Demand Multicast Routing Protocol (ODMRP) is a mesh based multicast routing protocol, which uses a mesh over which packets are forwarded through the use of scoped flooding. It is proved that, reducing the forwarding nodes is equivalent to finding the solution at less cost multicast tree. Finally less cost tree is acquired with multicasting mesh. The proposed approach considers to minimize the data overhead and supervised to bring greater performance than traditional ODMRP at a less cost, in terms of forwarding efficiency. The algorithm 1 is computed using the following steps:
3.2 Perform Network Coding in Nodes
The data transmitted across IoT network may be huge size compared to single packet. For example, in air smart devices are updated using new firm ware. So first the data is divided into small fragments, and then transmits one data fragment in one packet at time among multiple packets. The packets must be transmitted linearly to get the original data. A data present in the source code is fragmented in to equal length. Finally coding group is formed using ‘n’ data packets to compute in network as liner coding randomly. In coding section ‘hi’ in each packet, encodes using vector Δi = [δi,1, δi,2, …., δi,n] (δi,j ∈ GF(2m), 1 ≤ i, j ≤ n). This vector is appended to identify the packet used in encoding of hi. GF(2m) specify the finite elements of 2m where m ∈ {8, 16, 32, 64,..}, which determines the size of symbol. For uncoded packet hi, the all vector elements will become zero except δi,j = 1. The source node request Algorithm 2 to transfer the encoded packet
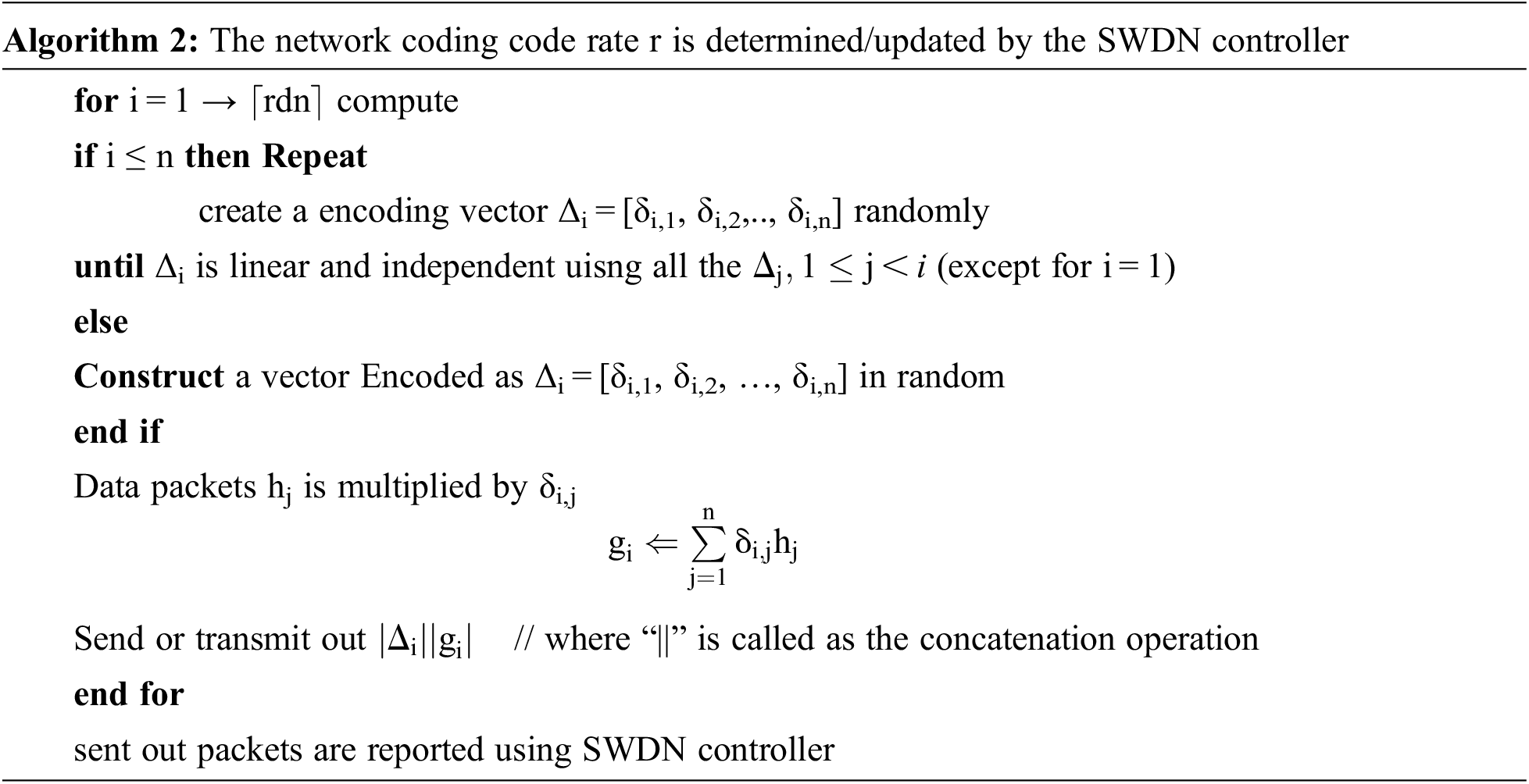
In Algorithm 2, generates a source program
For every coding group, the receiving memory opens at intermediate node for storing the fresh incoming packets from designated nodes of SDWN controller for data encoding. Further encoded vectors are recorded for incoming packets at intermediate nodes. Fresh packet is created by encoding vector which is linearly independent by already received packets. The trade off between the diversity of packet and delay in communication is received by encoding new packets by intermediate node. The new packets are getting during preset τ interval. This interval is measured using timer then removes the buffer received at the time and it waits for new incoming fresh packets to restart all timer and buffering. For better understanding, packets are split as each of the nτ fresh packets at receiving side buffer into the vector encoding Δi and data gi (1 ≤ i ≤ nτ ). nτ Represents total number of fresh packets available in receiving side of buffer. Algorithm 3 is used by intermediate node to send out
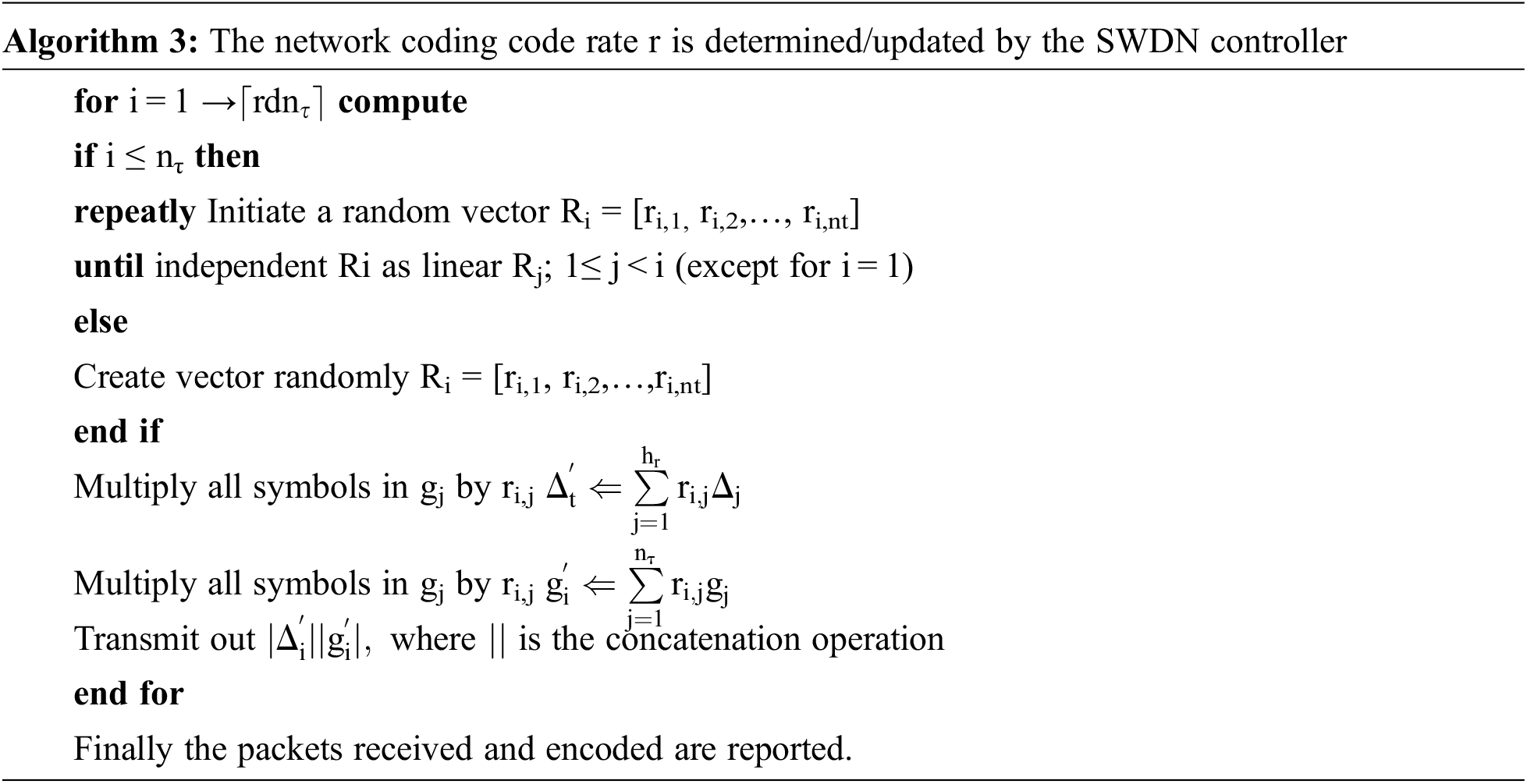
The dimension of vector Ri is generated as
Once the linearly n independent packets received at sink nodes, the Eq. (1) can be solved and original data packets can be decoded as h1, h2,…,hn.
Then concatenation of h1, h2,…,hn can be restored for original data. The sink node reports periodically for receiving packets status in SWDN controller.
Since the SWDN controller gets the status of packets sending/receiving from each node in the IoT core network periodically. The network coding rate can be adjusted based on the nodes. Let packets transmitted by node i is
where max() represents selection operation of maximum element. The SDWN controller contains information regarding topology for all nodes i. The succeeding relay nodes is specified to receive packets from node i.

3.3 Probability of Interference Measurement
Specifically, all neighbor nodes of nodes within range of interference are potential sources. We define consequently the node interference to be set of nodes cardinality covered using disks which are induced by range of interference. The neighbor nodes at interference range are also defined as interference node. However, there will be various interference levels at neighbor nodes to have the different nodes accordingly to Euclidean distances from node: if the distance is far between neighbor nodes, the interference will be small; if distance is small, their interferences is large. This condition helps to represent weights for various interference levels. Simply, 3 interference parts are divided (Fig. 2), and different weights are assigned to each and every part. In this article, the interference range is assumed as
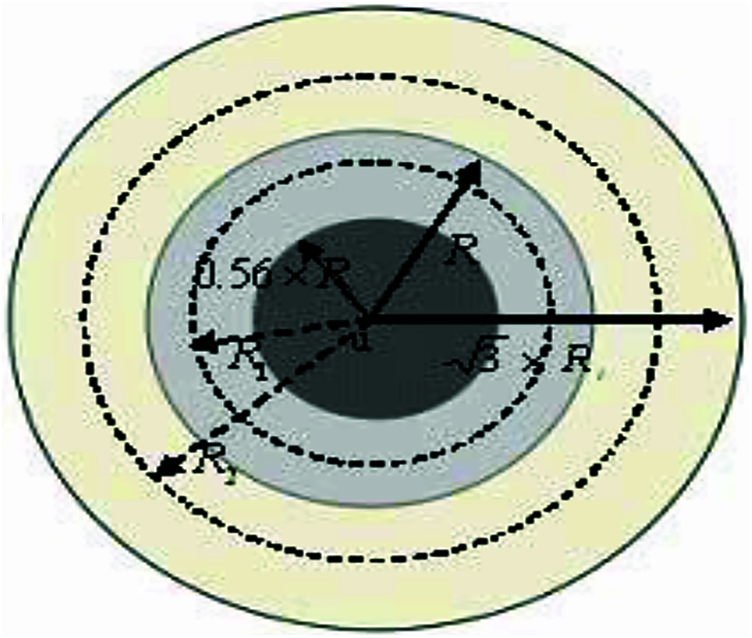
Figure 2: Interference in computation is illustrated
In Fig. 2 the circle is full of interference area with radius of
In Eq. (3), dark area is represented as N1, shaded area is represented as N2, and yellow area nodes represented as N3. N2 weight is α and N3 weight is β (less than 1) respectively, β is minimum than α. Equation [4] defines path loss TWO RAY GROUND model, the Pr is receiving power signal from a sender which is d meters far away as Eq. (4).
In Eq. (4), Gt and Gr are considers as gains of antenna transmitter and receiver, respectively. Pt is the sender node power transmission. ht and hr are antenna height respectively. Here, we assume that the homogeneous MANET, the each node is identical for radio parameters. In dark shaded section, the strong interference is generated by node and the interference difference at source node among nodes is imperceptible. We minimum power (d = 0.56Rt) is received to represent this area. However, other two areas and interference difference at source node and among nodes cannot be ignored. To be simple, mean range is chosen to represent the area, such as
We have kas 2. The final node-interference is
Based on interference node, interference link is estimated-as below:
Here, link e = (u, v), I (u) and I (v) are the interference of node u and v respectively. For a path P(u0, un) : u0e1u1e2u2……un−1enun the interference is computed as Eq. (9).
Single problem is interference path is directly related to path length. A low interference link with long path where all places than new path with large interference link. Therefore all path divides using Eq. (12)
Here, n is the path link, represents path length. Since considering average estimation length, link-interference paths (Metric) might balance Traffic to reduce path interference.
3.4 Interference Aware Multicast Routing
We execute ODMRP protocol called interference routing. These routing techniques are used by two protocols, which seen as two parts: discovery and maintenance of routing. The value of interference at each node is recorded using CLALIE protocol for every node presents in the network. It computes interference value using related links. Finally packets at route request is attains destination node. The whole path has interference which is figured easily and average value is computed finally for all paths. All Reply packet are induced by request packets of route. The possible path for routing is represented using request route packets. From destination node reply packets are transmitted to source nodes. The information regarding average interference is recorded by source node with path details using routing table.
The routing table is constructed locally with nodes and link which consists of candidate routing paths. Then the source node transmits data packet in path with less average link-interference among all paths which is possible between the source and destination.
The CLALIE protocol implemented by adding new sector in common pocket header such as metric in article [8]. All the node must know nodes number within 0.56 times range of transmission and range of interference respectively (1 N, 2 N and 3 N) before implementing the value of interference for itself.

In the route, intermediate nodes are updated as their routing tables based on the information given by the Replay packet of Route. Once the Route-Reply packet send to source node, then it records path information and corresponding Metric value to its local table of routing for future use. The minimum metric path is selected by source node to transmit data to destination. Due to topological variation drastically, path data at tables will be invalid. For every 10s once our protocol reads routing table and updates about new information regarding routing. This protocol works similarly as DSR routing mechanism.
In this section, the performance measurement of entire research work is done in the NS2 simulation environment along with the performance metrics for the proposed Interference and Throughput aware Optimized Multicast Routing Protocol (IT-OMRP). The comparison evaluation is done with the existing method namely secure multicast routing protocol (SMRP). The experimental setup is designed in Cadence–Virtuoso analog tools in 180 nm CMOS technology. This is resolved by proposed techniques and results are evaluated as follows.
Nowadays, Routing protocols are used to delivery packets. The rate of packet delivery is measured as number of packets received to sender and is calculated as follows:
The PDR of the methodology namely SMRP and IT-OMRP are compared together. Based on this the result IT-OMRP shows the improved performance than the existing methodology according to the Fig. 3. IT-OMRP shows 17% increased PDR than SMRP.
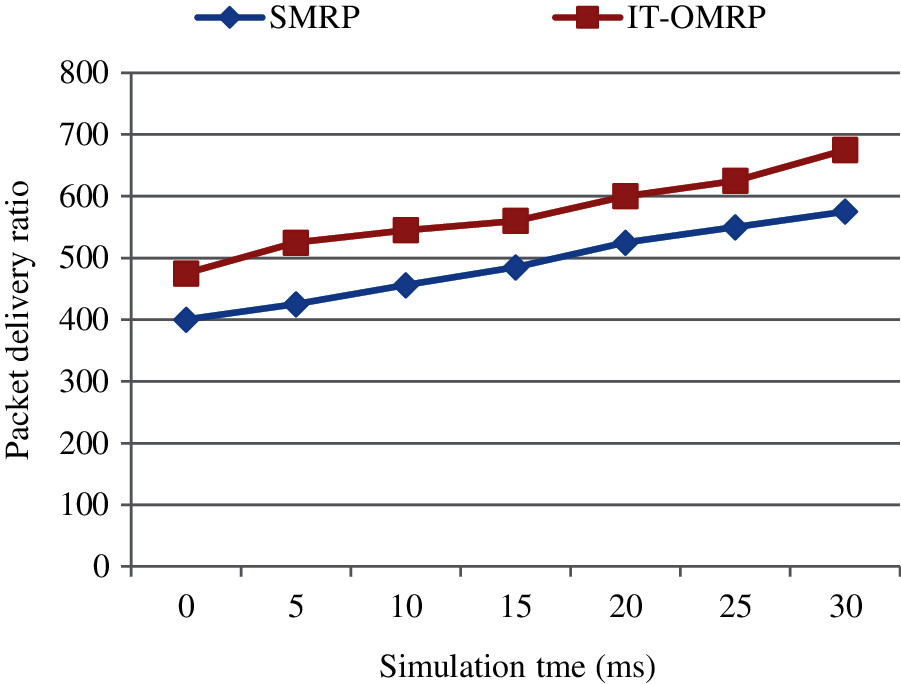
Figure 3: Packet delivery rate
The Packet Loss Rate (PLR) is a metric calculated in a protocol. PLR is estimated as follows,
The PLR of the methodology namely SMRP and IT-OMRP are compared together. Based on this the result IT-OMRP shows the 11.14% improved performance than the other existing methodology according to the Fig. 4.
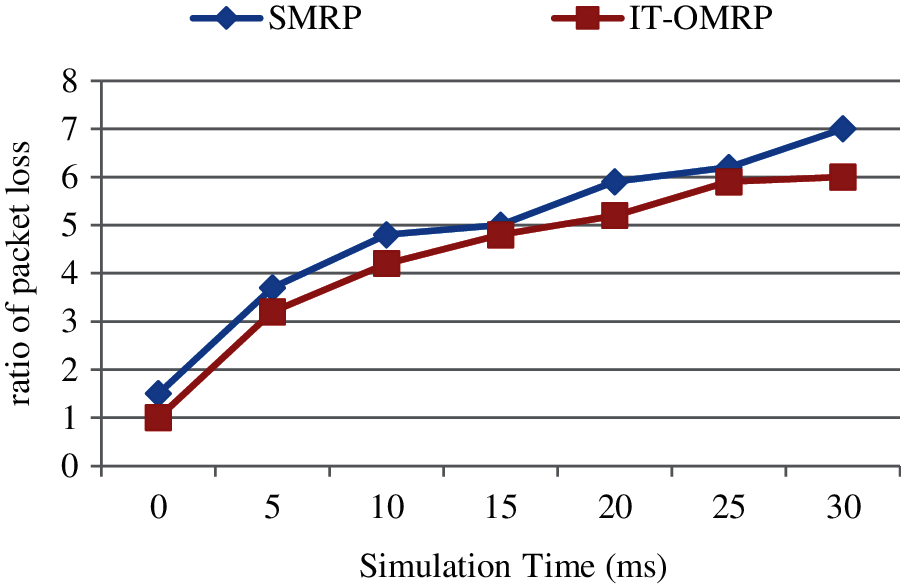
Figure 4: Packet loss rate
The difference in time between the current incoming packet and the last packet received bound is called as the average delay at node. It is measured using following equation.
The average delay of the methodology namely SMRP and IT-OMRP are compared together. Based on this the result IT-OMRP shows the 18.67% improved performance than the existing methodology according to the Fig. 5.
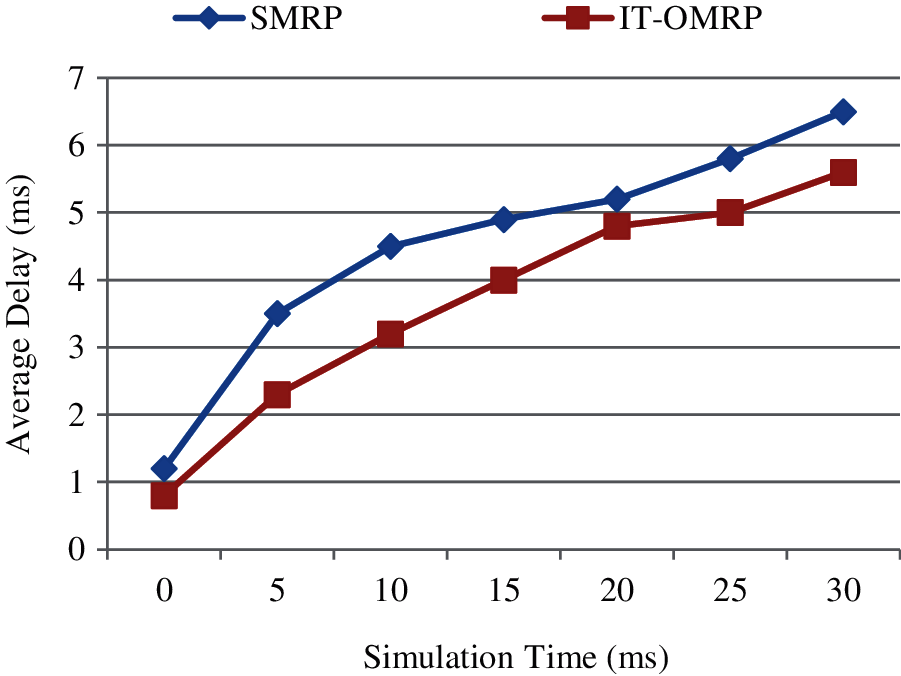
Figure 5: Average delay
The stability of the network in selecting the destination at beginning of simulation i.e., calculation of correct delivering of packets to destination. This is shown in Fig. 6.
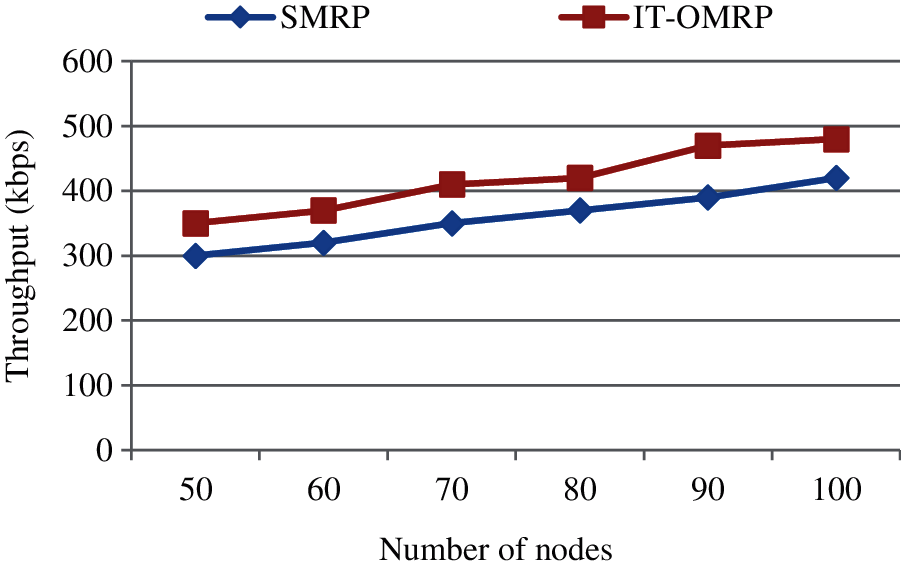
Figure 6: Throughput
The throughput of various methodologies in simulation environment from the source to each destination node is shown in Fig. 6. As a result it concludes that the IT-OMRP will produce the 16.27% better results compared to the existing SMRP.
The end-to-end delay is time interval between generation time of data packet and last bit arrival time at the destination.
The end to end delay of various methodologies in simulation environment from the source to each destination node is shown in Fig. 7. As a result it concludes that the IT-OMRP will produce the 9.06% better results compared to the existing SMRP.
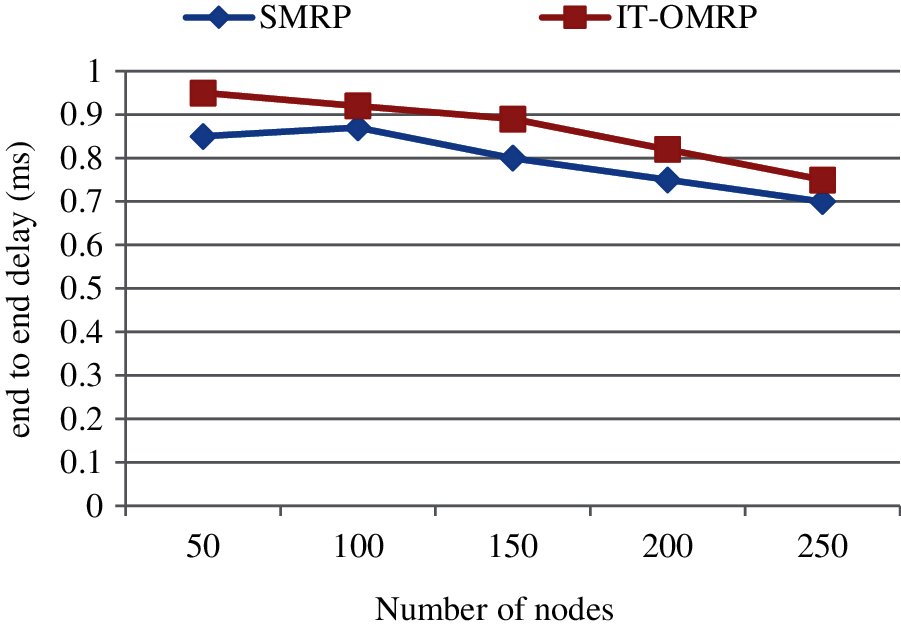
Figure 7: End to end delay
In this research work, multicast tree is selected by introducing the optimization approach namely Particle Swarm Optimization which will select the most optimal host node as the branches of multi cast tree. Here node selection is done by considering the objectives residual energy, residual bandwidth and throughput. After node selection multi cast routing is done with the concern of interference to ensure the reliable and successful data transmission. In case of transmission range size is higher than the coverage sense range, successful routing is ensured by selecting secondary host forwarders as a backup which will act as intermediate relay forwarders. The overall analysis of the research work is done in the NS2 simulation environment from which it is proved that the proposed technique tends to have increased packet delivery ratio than the existing work. In future swarm intelligence based various optimization algorithm can be used to check the performance of the route optimization.
Funding Statement: The authors have received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Li, D. Xu and L. Zhao, “5G internet of things: A survey,” Journal of Industrial Information Integration, vol. 10, pp. 1–9, 2018. [Google Scholar]
2. Y. Mehmood, F. Ahmad, I. Yaqoob, A. Adnane, M. Imran et al., “Internet of things-based smart cities: Recent advances and challenges,” IEEE Communications Magazine, vol. 55, no. 9, pp. 16–24, 2017. [Google Scholar]
3. D. Hanes, G. Salgueiro, P. Grossetete, R. Barton and J. Henry, “IoT fundamentals: Networking technologies, protocols, and use cases for the internet of things,” Cisco Press, [Online]. Available: https://ptgmedia.pearsoncmg.com/images/9781587144561/samplepages/9781587144561_CH08.pdf, 2017. [Google Scholar]
4. E. Ezhilarasan and M. Dinakaran, “A review on mobile technologies: 3G, 4G and 5G,” in Proc. ICRTCCM, Tindivanam, India, pp. 369–373, 2017. [Google Scholar]
5. X. Liu, B. Cui, J. Fu and J. Ma, “HFuzz: Towards automatic fuzzing testing of NB-IoT core network protocols implementations,” Future Generation Computer Systems, vol. 108, pp. 390–400, 2020. [Google Scholar]
6. Q. Li, G. Wu, A. Papathanassiou and U. Mukherjee, “An end-to-end network slicing framework for 5G wireless communication systems,” ArXiv Preprint ArXiv, 1608.00572, pp. 1–13, 2016. [Google Scholar]
7. D. B. Rawat and S. Reddy, “Recent advances on software defined wireless networking,” in Proc. Southeast Conf, Virginia, USA, pp. 1–8, 2016. [Google Scholar]
8. F. Khan, A. Rehman, A. Yahya, M. A. Chuma, J. Hussain et al., “A QoS-aware secured communication scheme for IoT-based networks,” Sensors, vol. 19, pp. 1–18, 2019. [Google Scholar]
9. T. Phakathi, F. Lugayizi and M. Esiefarienrhe, “Quality of service-aware security framework for mobile ad hoc networks using optimized link state routing protocol,” ArXiv Preprint ArXiv, pp. 1–18, 2020. [Google Scholar]
10. D. Roy, G. Das, P. De and D. Buyya, “QoS-aware secure transaction framework for internet of things using blockchain mechanism,” Journal of Network and Computer Applications, vol. 144, pp. 59–78, 2019. [Google Scholar]
11. M. M. Badawy, Z. H. Ali and H. A. Ali, “QoS provisioning framework for service-oriented internet of things,” Cluster Computing, vol. 23, pp. 1–17, 2019. [Google Scholar]
12. N. Ouerhani, N. Pazos, M. Aeberli and M. Muller, “IoT-based dynamic street light control for smart cities use cases,” in Proc. ISNCC, Yasmine Hammamet, Tunisia, pp. 1–5, 2016. [Google Scholar]
13. M. Faisal, S. Abbas and H. U. Rahman, “Identity attack detection system for 802.11-based ad hoc networks,” EURASIP Journal on Wireless Communications and Networking, vol. 1, 2018. [Google Scholar]
14. X. Zhao, D. E. Lucani, X. Shen and H. Wang, “Reliable IoT storage: Minimizing bandwidth use in storage without newcomer nodes,” IEEE Communications Letters, vol. 22, no. 7, pp. 1462–1465, 2018. [Google Scholar]
15. R. Zhao, X. Wang, J. Xia and L. Fan, “Deep reinforcement learning based mobile edge computing for intelligent internet of things,” Physical Communication, vol. 43, pp. 1–18, 2020. [Google Scholar]
16. M. Pustišek, D. Dolenc and A. Kos, “LDAF: Low bandwidth distributed applications framework in a use case of blockchain enabled IoT devices,” Sensors, vol. 19, no. 10, 2019. [Google Scholar]
17. Z. Ma, Q. Zhao and J. Huang, “Optimizing bandwidth allocation for heterogeneous traffic in IoT,” Peer-to-Peer Networking and Applications, vol. 10, no. 3, pp. 610–621, 2017. [Google Scholar]
18. I. Gravalos, P. Makris, K. Christodoulopoulos and E. A. Varvarigos, “Efficient gateways placement for internet of things with QoS constraints,” in Proc. GLOBECOM, Washington, USA, pp. 1–6, 2016. [Google Scholar]
19. Y. Peng, X. Wang, L. Guo, Y. Wang and Q. Deng, “An efficient network coding-based fault-tolerant mechanism in WBAN for smart healthcare monitoring systems,” Applied Sciences, vol. 7, no. 8, pp. 1–18, 2017. [Google Scholar]
20. I. Gravalos, P. Makris, K. Christodoulopoulos and E. A. Varvarigos, “Efficient network planning for internet of things with QoS constraints,” IEEE Internet of Things Journal, vol. 5, no. 5, pp. 3823–3836, 2018. [Google Scholar]
21. M. Z. Hasan, F. Al-Turjman and H. Al-Rizzo, “Analysis of cross-layer design of quality-of-service forward geographic wireless sensor network routing strategies in green internet of things,” IEEE Access, vol. 6, pp. 20371–20389, 2018. [Google Scholar]
22. K. Cao, G. Xu, J. Zhou, T. Wei, M. Chen et al., “QoS-adaptive approximate real-time computation for mobility-aware IoT lifetime optimization,” IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, vol. 38, no. 10, pp. 1799–1810, 2018. [Google Scholar]
23. H. Y. Li, Y. Gursoy, M. C. Velipasalar and S. Schmeink, “Throughput analysis of low latency IoT systems with QoS constraints and finite blocklength codes,” IEEE Transactions on Vehicular Technology, vol. 69, no. 3, pp. 3093–3104, 2020. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |