DOI:10.32604/csse.2022.023269

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.023269 |  |
| Article |
Fuzzy-Based Secure Clustering with Routing Technique for VANETs
1Saveetha School of Engineering, Saveetha Institute of Medical and Technical Sciences, Saveetha University, Chennai, 602105, India
2Department of Electronics and Communication Engineering, College of Engineering & Technology, SRM Institute of Science and Technology, Vadapalani Campus, Chennai, 600026, India
3Institute of Biomedical Engineering, Saveetha School of Engineering, Saveetha Institute of Medical and Technical Sciences, Saveetha University, Chennai, 602105, India
4Department of Electronics and Communication Engineering, SRM Institute of Science and Technology, 600026, Chennai, India
5Department of Civil Engineering, Saveetha School of Engineering, Saveetha Institute of Medical and Technical Sciences, Saveetha University, Chennai, 602105, India
*Corresponding Author: S. Srinivasan. Email: srinivasan.me.03@gmail.com
Received: 01 September 2021; Accepted: 29 October 2021
Abstract: Due to the advanced developments in communication technologies, Internet of vehicles and vehicular adhoc networks (VANET) offers numerous opportunities for effectively managing transportation problems. On the other, the cloud environment needs to disseminate the emergency message to the vehicles which are consistently distributed on the roadway so that every vehicle gets the messages from closer vehicles in a straightforward way. To resolve this issue, clustering and routing techniques can be designed using computational intelligence approaches. With this motivation, this paper presents a new type-2 fuzzy sets based clustering with metaheuristic optimization based routing (T2FSC-MOR) technique for secure communication in VANET. The T2FSC-MOR technique aims to elect CHs and optimal routes for secure intercluster data transmission in VANET. The proposed model involves T2FSC technique for the selection of CHs and construction of clusters. The T2FSC technique uses different parameters namely traveling speed (TS), link quality (LQ), trust factor (TF), inter-vehicle distance (IVD), and neighboring node count (NCC). The inclusion of trust factor helps to select the proper cluster heads (CHs) for secure data dissemination process. Moreover, trust aware seagull optimization based routing (TASGOR) approach was derived for the optimal selection of routes in VANET. In order to validate the enhanced performance of proposed technique, the set of simulations take place and the outcomes are examined interms of different measures. The experimental outcomes highlighted the improved performance of the proposed model over the other state of art techniques with a higher throughput of 98%.
Keywords: VANET; security; clustering; routing; fuzzy logic systems; metaheuristic algorithms
As a major components of Intelligent Transportation Systems (ITS), vehicular ad hoc network (VANET) have fascinated many scientists from distinct areas and huge research have attempts been performed. In VANETs, there are 2 kinds of communication [1]. VANET enables vehicle-to-infrastructure (V2I) transmission and vehicle-to-vehicle (V2V) transmission. In VANET, infrastructures and the vehicles, like Roadside Units (RSU) and application server, interchange data for entertainment, safe driving, navigation, etc. roadside units (RSUs) On- and board units (OBUs) in a VANET deploys correlation with dedicated short range communication (DSRC). The load balancing of a VANET should be preserved while the network is enhanced [2]. Now, smart clustering methods are highly significant and are utilized to develop a vehicular network using a remarkably adaptable, efficient, equalized, and reliable load distribution. Clustering in a scheme implies that nodes are gathered based on their demerits and merits for attaining optimal network efficiency. In a cluster/group, a single cluster member (CM) was selected as the cluster head (CH). In a VANET, vehicles were utilized as network nodes and are gathered to cluster [3]. It is categorized as an NP-hard problem. CH selection is essential to the clustering approach. The CH performs different processes, such as termination of a cluster, cluster placement, assume the network topology for provisioning and maintenance of resources. Also, the CH should handle transmission between internal and external, clusters, with another available cluster in the scheme.
In VANETs, topology based routing protocol uses connection data which present in the network for performing packet transmitting. It preserves the routes i.e., now being used. Hence, it decreases the overload in the network. It comprises a route finding stage where the query packet is flooded to the network for searching the path, and this stage finishes once the route is established [4]. The general kinds of reactive routing protocol in V2V transmission consist of dedicated short-range (DSR), Temporally Ordered Routing Algorithm (TORA), and Ad hoc On-demand Distance Vector Routing (AODV). In cluster based routing protocol, virtual network framework should be made by the clustering of nodes for providing scalability. The general kinds of cluster based routing protocol consist of Location Routing Algorithm with Cluster-Based Flooding (LORA-CBF), Clustering for Open IVC (Inter-vehicle communication) Network (COIN), and cluster based routing protocol (CBRP). But, taking into account the environmental factors, irregular roads, and higher mobility of vehicles, the conventional VANET, and MANET routing protocols mayn’t fulfill network transmission and data interchange in this environment. Thus, clustering routing protocol becomes most significant choice.
A VANET offers distinct resources and functionalities, particularly infotainment, driver security, and directional guidance. The VANET prioritizes safety over non-safety data. Safety data warns the driver if any threat occurs, and provides a solution. But, VANET also has few challenges, mainly with privacy and security when transferring data [5]. When the vehicle exit or enters highways, they should follow security, defined by the factors such as road conditions, roadwork, traffic congestion, etc. Such factors must be taken into account while making decision to attain the end with no interruptions. This detail should be updated frequently for avoiding delays. Particularly, the malicious nodes might neglect or purposely alter the vital safety details beforehand transmitting the data to the user that might lead to dramatic effects. Furthermore, the feature of VANETs, such as volatility and mobility, are variables, and wireless transmission networks have susceptible to VANETs in huge external and internal attacks [6]. Due to the dynamic topology and the decentralized structure of VANETs, the security of users, vehicles, and data is significant, and malicious nodes must be recognized. In a VANET, vehicles interchange private data, and traffic is changed consequently. The lack of authorized data leads to malicious attacks which cause severe issues for the drivers. The messages could be authorized by tracing the vehicles via a network and find the essential details; but, this compromises the safety of user. Hence, a balance must be established among privacy and authentication of the user. Privacy of vehicles and Trust management is complication problems for VANET.
Chandren Muniyandi et al. [7] aim is to suggest an enhanced EHSO method which considers the configurations of OLSR parameter by combining 2 phases, a process for optimization is performed by the EHSO method on the basis of implanting 2 common election approaches in its memory, i.e., tournament and roulette wheel selections. Tariq et al. [8], proposed an IMOC for a drone-assisted vehicular networks. This system is utilized for providing maximal coverage for the vehicular nodes with minimal CH needed for routing. Providing optimum route by Delivering end to end connection with minimal overheads is the essential problem tackled in this study. Transmission range, Node density, and grid sizes are the efficacy parameter utilized for comparison studies. These parameters are different at the time simulation for all algorithms, and the outcomes are noted.
Alsuhli et al. [9] proposed the clustering optimization problem as many objective optimization problems. Subsequently, they proposed a method for optimizing clustering configuration parameters. NSGA-III several objective Meta heuristic is utilized as the optimization tool in this method. The presented technique is experimentally calculated by optimize the DHC approach and relating their performances with and without the optimization technique. Husnain and Anwar [10] discuss a new optimization algorithm that considers node density, transmission range, grid size, speed, and direction at the time of clustering. The WOACNET has been presented for selecting an optimal CH and was evaluated and calculated on the basis of capability and intelligence.
Ahsan et al. [11] presented the GOA based node clustering approach for VANET to select optimum CH. The presented approach decreased network overheads in unpredictable node density scenarios. Therefore, various studies have been carried out for comparative analyses of GOA using another advanced method. Kolandaisamy et al. [12] introduced an SPPA method. This method monitors the location at all field stations in transmitting the data to execute DDoS attacks. The technique calculates several aspects such as Attack signature sample rate, Conflict field, and data. With this factor, the approach recognizes the reliability of the packets and involves it in decision-making.
In order to enhance the efficacy of V2V, Effective Clustering V2V Routing Based on PSO in VANET (CRBP) is presented [13]. Firstly, vehicle nodes with similar moving directions are determined and the CH is chosen. Next, for the essential routing optimization, the velocity coding rules, and its iteration rules, fitness function, and route particle are developed. Then, the method could enhance the routing efficacy in the cluster and amongst clusters are presented. Fatemidokht and Rafsanjani [14], proposed a clustering routing protocol, called QMM-VANET, consider QoS requirements, the distrust value parameter, and mobility constraints. This protocol is made up of 3 portions: (i) compute the QoS of vehicle and select a trustier vehicle as a CH, (ii) select a group of suitable neighboring nodes as gateways to retransmit the packet, and (iii) utilize gateway recovery approach for selecting other gateways if connection fails.
Hadded et al. [15] proposed an AWCP algorithm, particularly developed for vehicular network, that take direction of vehicles, position, speed, highway ID and the amount of neighbouring vehicles for enhancing network topology stability. But, the multiple control parameter of AWCPs, makes parameter tuning a non-trivial challenge. For optimizing the protocol, they determine multiobjective problems whose inputs are the AWCP parameter and objective consists of: maximize data delivery rate, reduce the cluster overhead, and provide stable cluster structure. Raja [16] proposed a perception on road safety adapted routing protocol for hybrid VANET WSN transmission (PRAVN) on the basis of three-fold contribution. The initial contribution of PRAVN protocol is to execute clustering with the help of IWWO method. The next contribution to calculate the CH nodes of SN amongst many nodes depends on multi constraint features i.e., collected from the SN. The 3rd contribution is to present the RO method for neighbourhood election that offers the lossless connection and network lifetime. Lastly, the PRAVN protocol is utilized for forwarding the accurate data from source to destination which improves the road security.
Hosmani and Mathapati [17] presented a lightweight CH election and cluster formation by taking into account mobility and various neighbours depend on geographical distances of the vehicle key parameters at each clustering interval for achieving network stability. The superiority of this technique is that it is simple and inclusive of the portion of standard routing operation. For all vehicles the weight is calculated for the CH using mobility and neighbours parameter, therefore this technique is known as WCV for VANET routing protocol. Zhang et al. [18] presented a novel routing method FLHQRP by taking into account the features of realtime transmission in VANET. The virtual grids are presented for dividing the vehicle network to cluster. The node’s mobility and centrality, and bandwidth efficacy are treated with the help of FL method for selecting the appropriate CH using the stable transmission link in the cluster. Also, novel heuristic functions are presented in FLHQRP approach.
This paper presents a new type-2 fuzzy sets based clustering with metaheuristic optimization based routing (T2FSC-MOR) technique for secure communication in VANET. The proposed model involves T2FSC technique for the selection of CHs and construction of clusters. The T2FSC technique uses different parameters namely travelling speed (TS), link quality (LQ), trust factor (TF), inter-vehicle distance (IVD), and neighboring node count (NCC). The inclusion of trust factor helps to select the proper CHs for secure data dissemination process. Moreover, trust aware seagull optimization based routing (TASGOR) approach is derived for the optimal selection of routes in VANET. For validating the enhanced performance of the proposed technique, the set of simulations take place and the outcomes are examined interms of different measures.
The rest of the study is organized as follows. Section 2 introduces the presented model and Section 3 offers the performance validation. Lastly, Section 4 concludes the study.
The T2FSC-MOR technique aims to elect CHs and optimal routes for secure intercluster data transmission in VANET. The proposed technique encompasses two major phases namely T2FSC based clustering and TASGOR based route selection techniques. The detailed working of these processes is offered in the succeeding sections.
VANET has the features of higher mobility and non-uniform spatial distribution of vehicles that leads to sufficient topology changes and network links disconnectivity. In order to solve these problems, a clustered VANET network is developed for offering reliable transmission and energy efficient. Fig. 1 displays the basic structure of VANET. In generic vehicular service situation, a set of vehicles is integrated to create moving clusters. The cluster holds a leader named Cluster Head (CH) i.e., capable of managing the data based on data transmission and CMs. In this study, the subsequent assumptions are developed. All vehicles have an OBU and identifier. GPS services are provided to gather fundamental informations such as moving direction, current location of velocity, and vehicle. The vehicle communicates the data amongst itself through beacon signals. The beacon messages get promoted and collected at all beacon intervals which consist of position, vehicle id, moving direction, velocity, and so on.
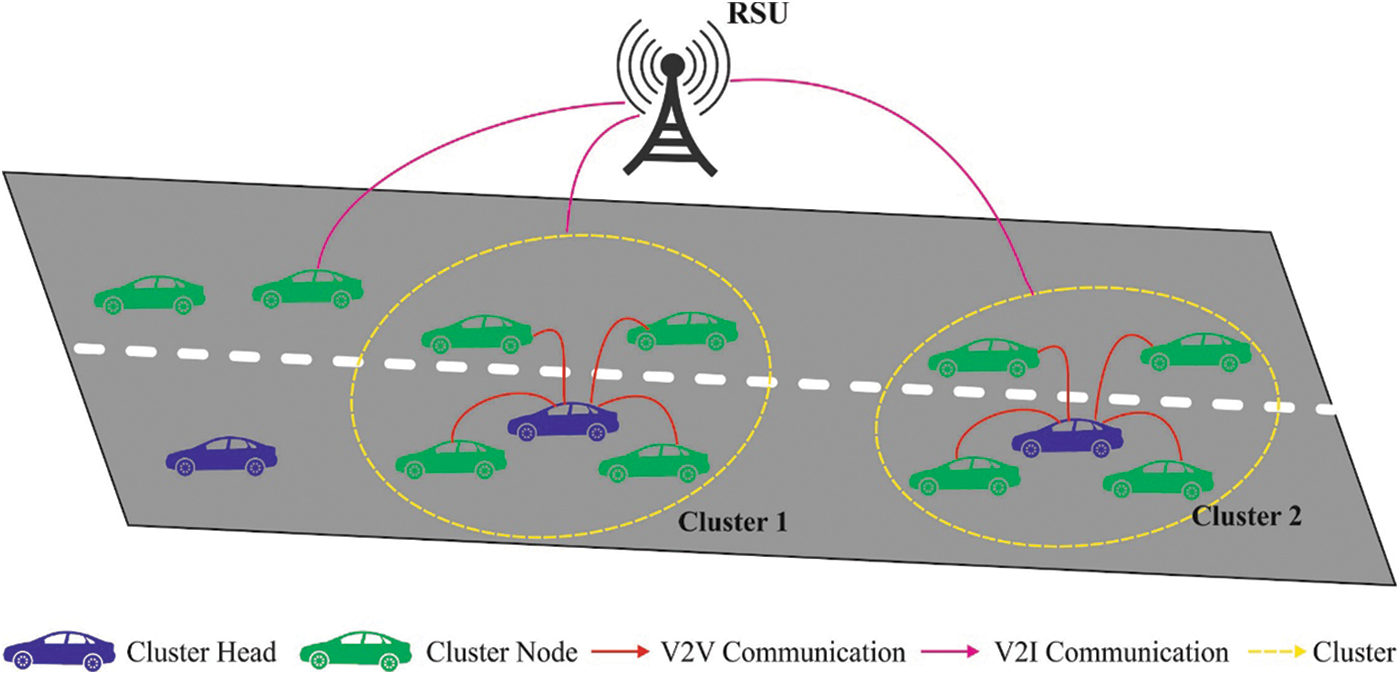
Figure 1: Structure of VANET
2.2 Design of T2FSC Technique for Clustering Process
In VANET, a CH is considered as constant utilization in roadside based on broadcast radius. All vehicles address the exiting place to CH. At this point, the CH election was stimulated by the fundamental of auto configuration as it can be preserved as location servers and record the place briefly of all vehicles. Assuming the detailed, the route was created to data transferred. Once the CH was chosen, the vehicle is registered in CH together with secured and exclusive ID and password. Primarily, the vehicle makes a random confidential value which uses for computing ID as well as passwords. Afterward, it forwards the registration request to High Way Authority (HWA) with protective station. Then receiving the request, a random value was created for estimating the ID of chosen vehicle. If the vehicle was connected to cellular network, pre-registration is performed and arbitrary bit identity was created to data transmission resolve.
To select the CH, a novel technique was utilized named Fuzzy Logic (FL). This FL has 5 input variables namely TS, LQ, TF, IVD, as well as NCC were utilized. Then, the output features are composed with probability of becoming CH (PCH). Primarily, the TS represents the mobile speed of vehicles, the LQ has superiority of vehicle linked, TF depicts the intensity of stability, the IVD defines the distance from vehicle, and NCC indicates the amount of vehicles located neighboring place. In T2FL has of 4 levels are provided:
Fuzzifier
It can be utilized for converting the actual inputs as fuzzified values. Some input features with respect to linguistic attributes were utilized to select the CH and cluster size [19–22]. At this point, there are any linguistic parameters to RE has low, medium, and high. Likewise, the linguistic feature of DBS has near, far, and farthest but ND has minimum, moderate, and maximum correspondingly.
Fuzzy rules/Inference engine
The framework of T1FL and T2FL are similar. At this point, the group of 27 rules was implemented. Then, the group of fuzzy rules to CH and decided cluster size. Therefore, the rule was given in Eq. (1).
where
When the PCH was received, it transmits the message to target vehicle. This message was enclosed with vehicle ID and PCH measure. The vehicle is superior probability was chosen as CH and transmit CH_WIN to equivalent vehicle only few vehicles received several CH_WIN from nearby vehicles. At this point, it sends a CH_LINK message and related to nearby CH. at the moment of retrieved CH_LINK message, adjacent CH verifies the provided cluster size before taken novel member. Thus the complete CM doesn’t go above the defined cluster size, it approves a novel CM by forwards CM_RECEIVE message, and then, it transmits CH_DISCARD message.
If the vehicle receives a CM_DISCARD message when it re-transmit a CM_LINK message to future CH with no statement of eliminated CH that was repeated till a novel CH is searched. Besides, the vehicle cannot be related to other CH to be inside coverage regions ‘R’, after it elects as CH. Thus, all vehicles go to clusters where divided vehicles in VANET. With the modelling of different rounds, for eliminating the premature death of CH, rotation function was performed by CH. If the remaining Energy (RE) of CH was superior if related to threshold value, afterward CH rotation exists. But, the RE of CH exceeded threshold values, a novel CH was elected utilizing PCH. As function remove the first death of CH and improve the lifespan of network.
Type reducer/Defuzzifier
This technique processes a T1FL outcome that is recreated for mathematical expression then the execution of defuzzifier is ended.
2.3 Design of TASGOR Technique
SGO is mostly inspired by the migration and attack performances of seagulls in nature. The seagulls are type of seabird everywhere in the world, with distinct species that mostly feed on insects, fish, reptiles, amphibians, and earthworms. In seagulls were extremely clever birds which utilize their wisdom for finding food as well as attack prey. For sample, it can be utilized breadcrumb for attracting fish as well as its feet for imitating the sound of rain for luring earthworm hidden underground. The migration and attacks are some of the essential performances of seagulls. An attack performance is determined as attack performances from seagulls beside the migrated bird at sea. Currently, the seagulls are meet the subsequent condition. For avoiding collisions amongst seagulls as well as neighboring seagulls, variable A was added for calculating a novel search agent place.
where
where:
where
where
where
where
where
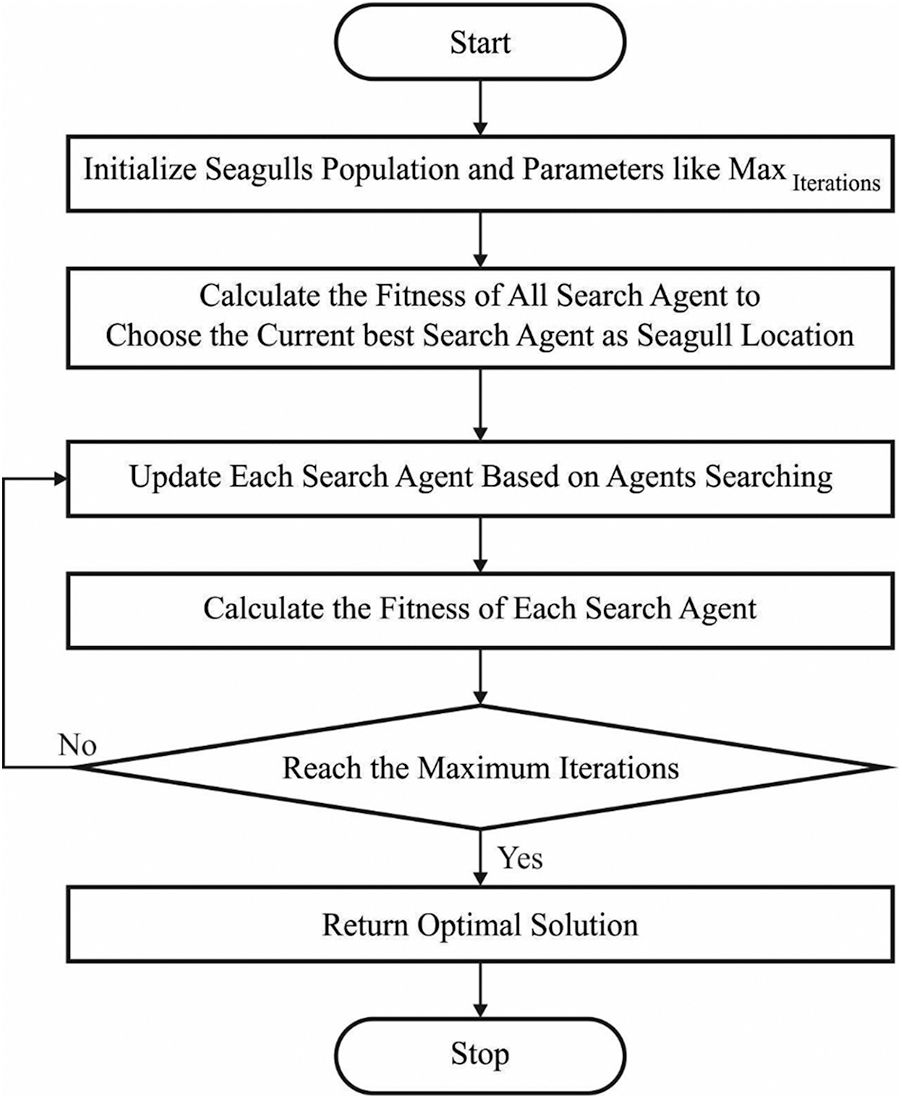
Figure 2: Flowchart of SOA
TASGOR derived an FF for achieving data transmission set election. The goal of FF is for normalizing the incorporated effects on distance to bandwidth, target, and node mobility for selecting relay vehicles for data transmission. Also, FF includes an overall of 4 components with separate conditions as shown in Eq. (13).
In which
Next,
whereas
For improving QoS, bandwidth is a significant variable i.e., processed as third term
Let
whereas,
3 Experimental Results Analysis
This section validates the simulation results of the proposed T2FSC-MOR technique. The T2FSC-MOR technique is simulated using MATLAB tool. Firstly, the results analysis of the T2FSC-MOR technique takes place interms of number of clusters generated under varying node count and transmission range in Fig. 3.
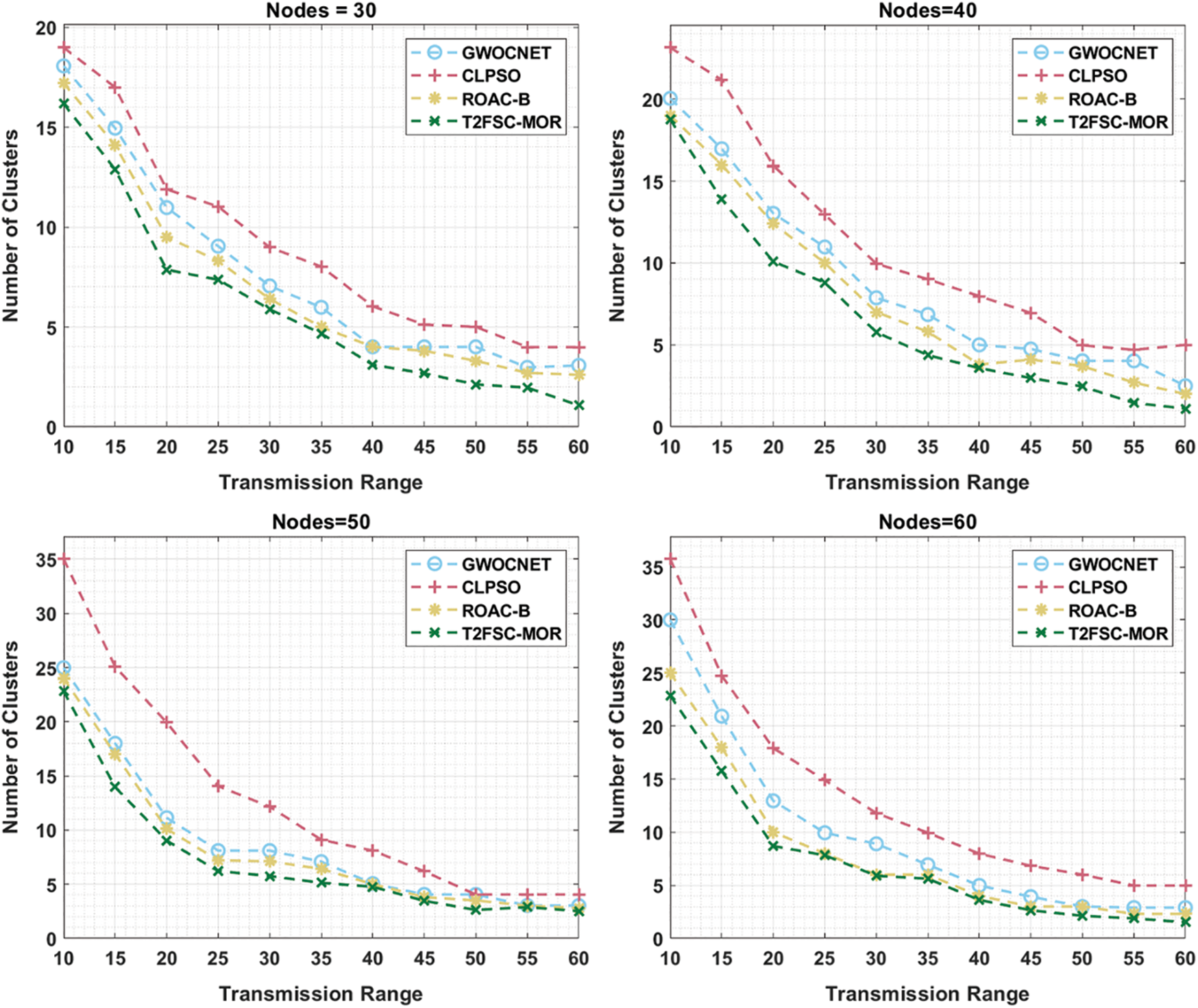
Figure 3: Result analysis of T2FSC-MOR model under distinct nodes
On examining the results under 30 nodes, the T2FSC-MOR technique has gained effectual outcome with the least number of clusters whereas the GWOCNET, CLPSO, and ROAC-B techniques have showcased slightly degraded outcomes with the increased number of clusters.
Simultaneously, on investigative the outcomes under 40 nodes, the T2FSC-MOR approach has obtained effective results with minimum number of clusters whereas the GWOCNET, CLPSO, and ROAC-B methods have demonstrated somewhat degraded outcomes with the improved number of clusters. Concurrently, on observing the results under 50 nodes, the T2FSC-MOR manner has attained effectual results with the worse number of clusters whereas the GWOCNET, CLPSO, and ROAC-B methodologies have outperformed slightly degraded outcomes with the superior number of clusters. Meanwhile, on exploratory results under 60 nodes, the T2FSC-MOR technique has achieved efficient outcomes with the lesser number of clusters whereas the GWOCNET, CLPSO, and ROAC-B algorithms have demonstrated somewhat degraded outcomes with the enhanced number of clusters.
An ETE delay analysis of the T2FSC-MOR technique with other techniques takes place in Tab. 1 and Fig. 4. The results demonstrated that the T2FSC-MOR technique has resulted in an improved outcome with minimal ETE delay. For instance, with 20 node count, the T2FSC-MOR technique has offered a lower ETE delay of 0.0810s whereas the HEEPA, LAKAP, ASC, and ROAC-B techniques have obtained a higher ETE delay of 0.2800s, 0.1191s, 0.1300s, and 0.1000s respectively. In addition, with 40 node count, the T2FSC-MOR approach has accessible a lesser ETE delay of 0.1600s whereas the HEEPA, LAKAP, ASC, and ROAC-B algorithms have gained an increased ETE delay of 0.2905s, 0.1715s, 0.2095s, and 0.1800s correspondingly. Moreover, with 60 node count, the T2FSC-MOR method has offered a minimum ETE delay of 0.1770s whereas the HEEPA, LAKAP, ASC, and ROAC-B algorithms have reached a superior ETE delay of 0.3300s, 0.2715s, 0.2405s, and 0.1900s correspondingly. Eventually, with 80 node count, the T2FSC-MOR method has existed a minimum ETE delay of 0.2730s whereas the HEEPA, LAKAP, ASC, and ROAC-B algorithms have gained an increased ETE delay of 0.4300s, 0.3715s, 0.3215s, and 0.2900s correspondingly. Furthermore, with 100 node count, the T2FSC-MOR approach has obtainable a lower ETE delay of 0.2570s whereas the HEEPA, LAKAP, ASC, and ROAC-B methodologies have gained a maximum ETE delay of 0.4715s, 0.5215s, 0.3525s, and 0.3000s correspondingly.
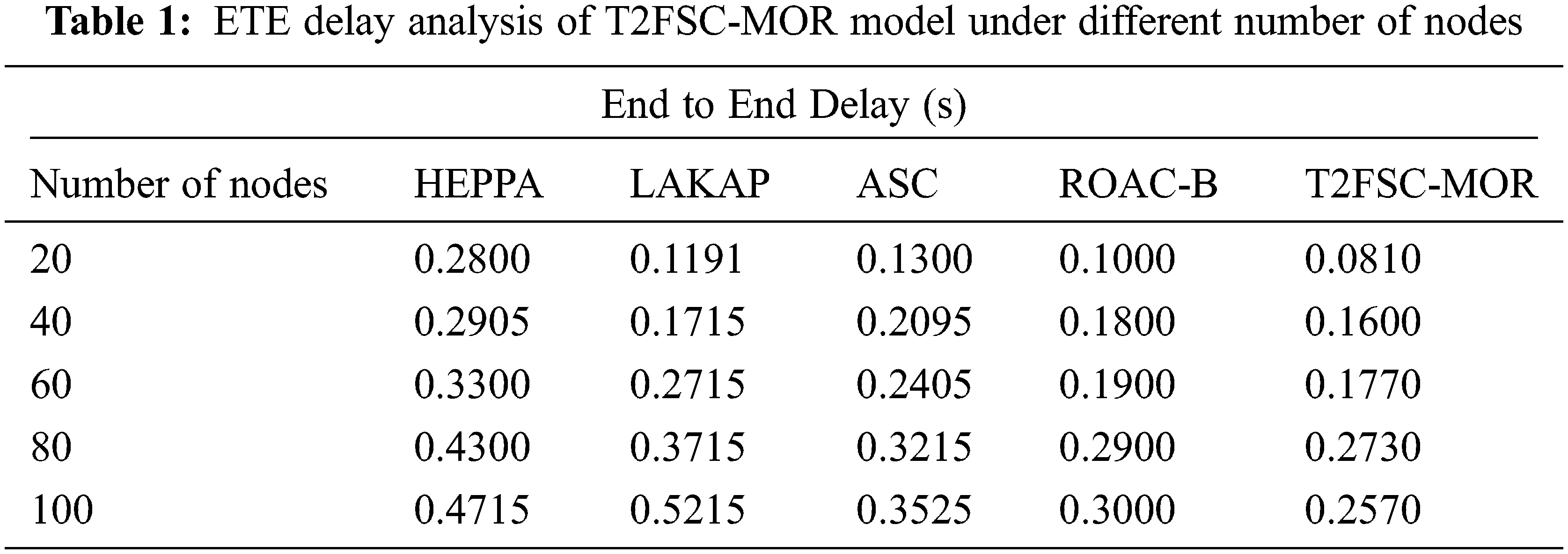
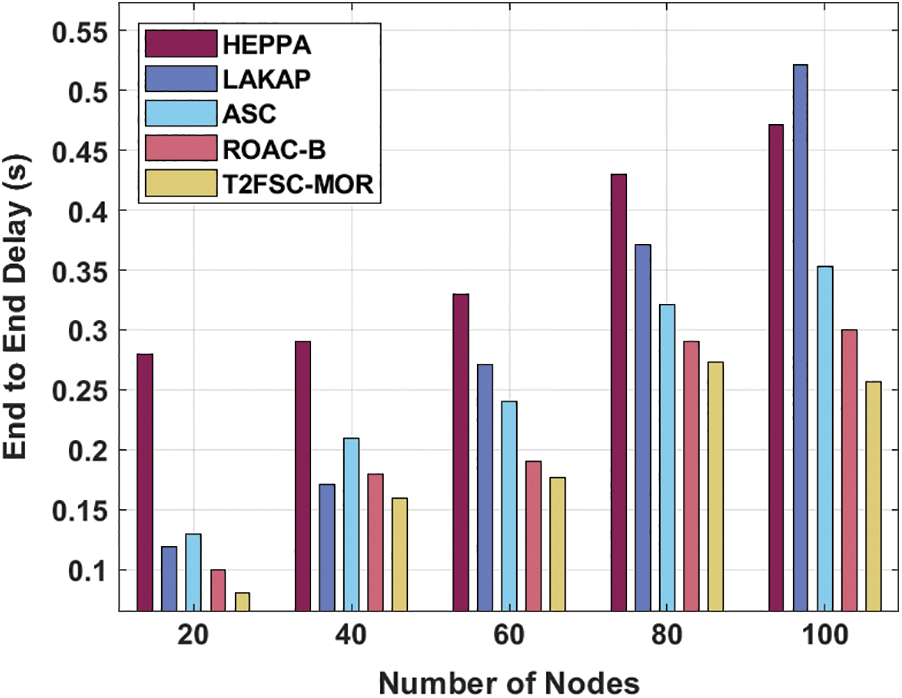
Figure 4: ETE delay analysis of T2FSC-MOR model with existing methods
A PDR analysis of the T2FSC-MOR technique with other approaches under varying node count is performed in Tab. 2 and Fig. 5. The experimental outcomes demonstrated the better performance of the T2FSC-MOR technique with the maximum PDR values. For instance, with 20 node count, the T2FSC-MOR technique has accomplished an increased PDR of 0.93 whereas the HEPPA, LAKAP, ASC, and ROAC-B techniques have attained a reduced PDR of 0.84075, 0.70, 0.75925, and 0.90 respectively. In line with, with 40 node count, the T2FSC-MOR approach has accomplished an enhanced PDR of 0.82 whereas the HEPPA, LAKAP, ASC, and ROAC-B methods have obtained a minimum PDR of 0.73, 0.67950, 0.63, and 0.76 correspondingly. At the same time, with 60 node count, the T2FSC-MOR approach has accomplished an improved PDR of 0.80 whereas the HEPPA, LAKAP, ASC, and ROAC-B techniques have gained a minimal PDR of 0.70, 0.64075, 0.57950, and 0.75 respectively.
Along with that, with 80 node count, the T2FSC-MOR technique has accomplished a maximum PDR of 0.74 whereas the HEPPA, LAKAP, ASC, and ROAC-B methodologies have attained a reduced PDR of 0.67125, 0.64225, 0.56955, and 0.70 respectively. At last, with 100 node count, the T2FSC-MOR algorithm has accomplished a superior PDR of 0.72 whereas the HEPPA, LAKAP, ASC, and ROAC-B techniques have reached lesser PDR of 0.57125, 0.57125, 0.53, and 0.63 correspondingly.

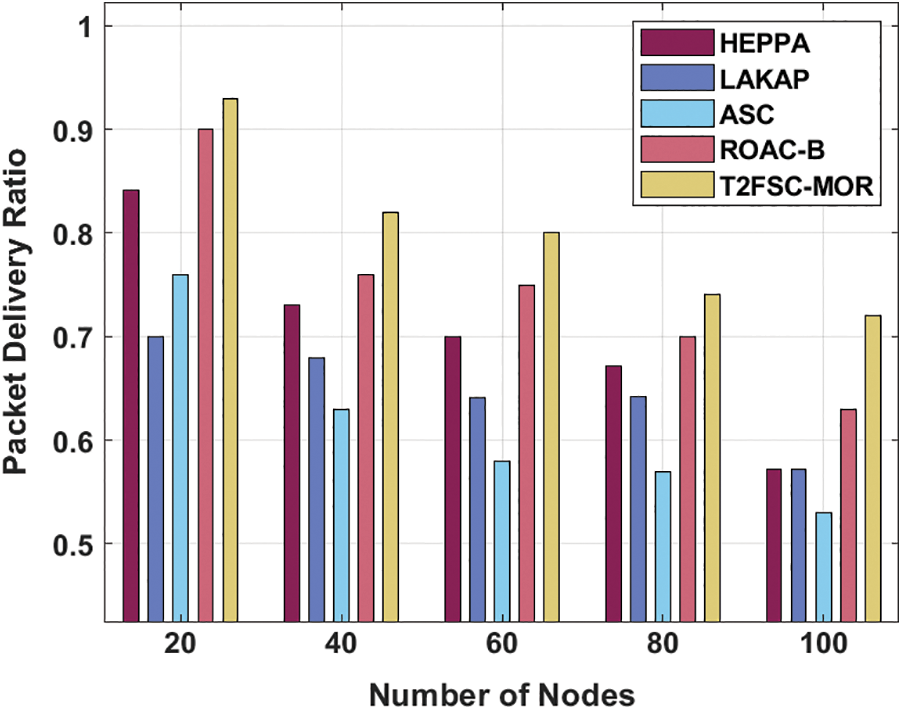
Figure 5: PDR analysis of T2FSC-MOR model with existing methods
A throughput analysis of the T2FSC-MOR algorithm with other techniques under different simulation times is implemented in Tab. 3 and Fig. 6. The experimental results outperformed optimum efficiency of the T2FSC-MOR manner with the maximal throughput values. For sample, with 20s simulation time, the T2FSC-MOR method has accomplished an improved throughput of 21% whereas the HEPPA, LAKAP, ASC, and ROAC-B methods have reached a minimal throughput of 8.25%, 6.75%, 11.29%, and 15% correspondingly. Followed by, with 40s simulation time, the T2FSC-MOR approach has accomplished a superior throughput of 58% whereas the HEPPA, LAKAP, ASC, and ROAC-B techniques have reached a reduced throughput of 27.05%, 29.30%, 50%, and 53% correspondingly. Simultaneously, with 60s simulation time, the T2FSC-MOR approach has accomplished a maximal throughput of 68% whereas the HEPPA, LAKAP, ASC, and ROAC-B techniques have achieved a lower throughput of 42.10%, 47%, 60.15%, and 63% respectively. Also, with 80s simulation time, the T2FSC-MOR methodology has accomplished an enhanced throughput of 85% whereas the HEPPA, LAKAP, ASC, and ROAC-B techniques have gained a decreased throughput of 65.80%, 70%, 75.20%, and 79% correspondingly. Eventually, with 100s simulation time, the T2FSC-MOR method has accomplished a higher throughput of 98% whereas the HEPPA, LAKAP, ASC, and ROAC-B algorithms have obtained a minimal throughput of 80.09%, 83.09%, 90%, and 94% respectively. The experimental outcomes highlighted the improved performance of the proposed model over the other state of art techniques due to secure intercluster data transmission and clustering process.

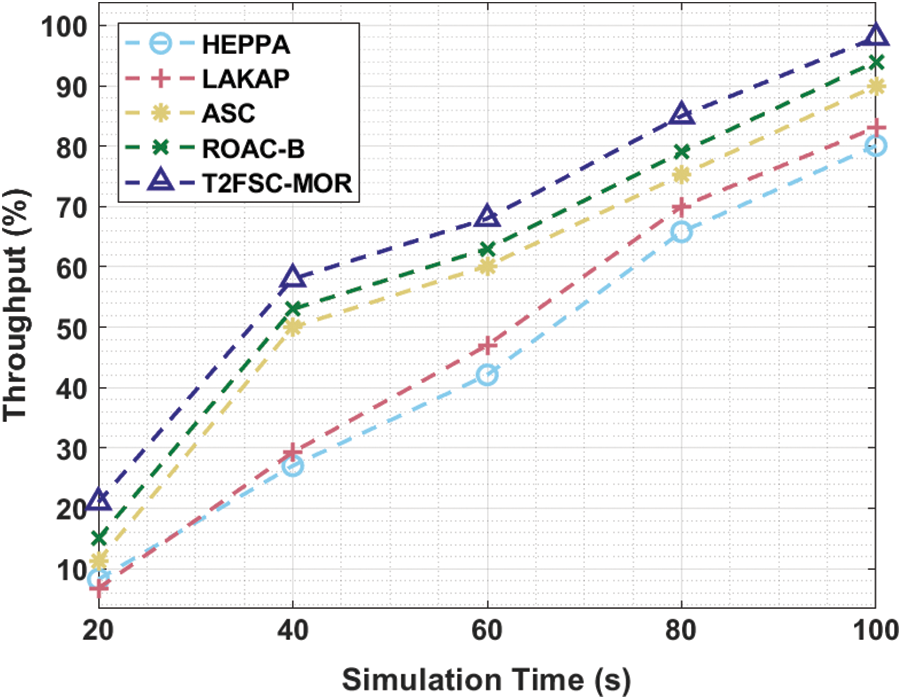
Figure 6: Throughput analysis of T2FSC-MOR model with existing methods
This study has developed a new T2FSC-MOR technique for secure communication in VANET. The T2FSC-MOR technique aims to elect CHs and optimal routes for secure intercluster data transmission in VANET. The proposed technique encompasses two major phases namely T2FSC based clustering and TASGOR based route selection techniques. The T2FSC technique uses different parameters namely TS, LQ, TF, IVD, and NCC. The inclusion of trust factor helps to select the proper CHs for secure data dissemination process. Moreover, TASGOR technique is derived for the optimal selection of routes in VANET. For validating the enhanced performance of proposed technique, the set of simulations take place and the outcomes are examined interms of different measures. The experimental outcomes highlighted the improved performance of the proposed model over the other state of art techniques. In future, the presented model can be improved by the use of multi-objective optimization based clustering with routing techniques for Internet of Vehicles (IoV).
Funding Statement: The authors received no specific funding for this study.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. M. S. Maharajan, T. Abirami, I. V. Pustokhina, D. A. Pustokhin and K. Shankar, “Hybrid swarm intelligence based QoS aware clustering with routing protocol for WSN,” Computers, Materials & Continua, vol. 68, no. 3, pp. 2995–3013, 2021. [Google Scholar]
2. M. Elhoseny, R. S. Rajan, M. Hammoudeh, K. Shankar and O. Aldabbas, “Swarm intelligence-based energy efficient clustering with multihop routing protocol for sustainable wireless sensor networks,” International Journal of Distributed Sensor Networks, vol. 16, no. 9, pp. 155014772094913, 2020. [Google Scholar]
3. G. P. Joshi, E. Perumal, K. Shankar, U. Tariq, T. Ahmad et al., “Toward blockchain-enabled privacy-preserving data transmission in cluster-based vehicular networks,” Electronics, vol. 9, no. 9, pp. 1358, 2020. [Google Scholar]
4. A. K. Dutta, M. Elhoseny, V. Dahiya and K. Shankar, “An efficient hierarchical clustering protocol for multihop Internet of vehicles communication,” Transactions on Emerging Telecommunications Technologies, vol. 31, no. 5, pp. 1–11,2020. [Google Scholar]
5. R. Punithavathi, C. Kurangi, S. P. Balamurugan, I. V. Pustokhina, D. A. Pustokhin et al., “Hybrid BWO-IACO algorithm for cluster based routing in wireless sensor networks,” Computers, Materials & Continua, vol. 69, no. 1, pp. 433–449, 2021. [Google Scholar]
6. T. Vaiyapuri, V. S. Parvathy, V. Manikandan, N. Krishnaraj, D. Gupta et al., “A novel hybrid optimization for cluster-based routing protocol in information-centric wireless sensor networks for iot based mobile edge computing,” Wireless Personal Communications, vol. 49, pp. 145, 2021. [Google Scholar]
7. R. C. Muniyandi, M. K. Hasan, M. R. Hammoodi and A. Maroosi, “An improved harmony search algorithm for proactive routing protocol in vanet,” Journal of Advanced Transportation, vol. 2021, pp. 1–17, 2021. [Google Scholar]
8. R. Tariq, Z. Iqbal and F. Aadil, “IMOC: Optimization technique for drone-assisted VANET (DAV) based on moth flame optimization,” Wireless Communications and Mobile Computing, vol. 2020, pp. 1–29, 2020. [Google Scholar]
9. G. H. Alsuhli, A. Khattab and Y. A. Fahmy, “An evolutionary approach for optimized vanet clustering,” in 2019 31st International Conference on Microelectronics (ICM), Cairo, Egypt, pp. 70–73, 2019. [Google Scholar]
10. G. Husnain and S. Anwar, “An intelligent cluster optimization algorithm based on Whale Optimization Algorithm for VANETs (WOACNET),” PLoS ONE, vol. 16, no. 4, pp. e0250271, 2021. [Google Scholar]
11. W. Ahsan, M. F. Khan, F. Aadil, M. Maqsood, S. Ashraf et al., “Optimized node clustering in VANETs by using meta-heuristic algorithms,” Electronics, vol. 9, no. 3, pp. 394, 2020. [Google Scholar]
12. R. Kolandaisamy, R. M. Noor, I. Kolandaisamy, I. Ahmedy, L. M. Kiah et al., “A stream position performance analysis model based on DDoS attack detection for cluster-based routing in VANET,” Journal of Ambient Intelligence and Humanized Computing, vol. 12, no. 6, pp. 6599–6612, 2021. [Google Scholar]
13. X. Bao, H. Li, G. Zhao, L. Chang, J. Zhou et al., “Efficient clustering V2V routing based on PSO in VANETs,” Measurement, vol. 152, no. 4, pp. 107306, 2020. [Google Scholar]
14. H. Fatemidokht and M. K. Rafsanjani, “QMM-VANET: An efficient clustering algorithm based on QoS and monitoring of malicious vehicles in vehicular ad hoc networks,” Journal of Systems and Software, vol. 165, pp. 110561, 2020. [Google Scholar]
15. M. Hadded, R. Zagrouba, A. Laouiti, P. Muhlethaler and L. A. Saidane, “A multi-objective genetic algorithm-based adaptive weighted clustering protocol in VANET,” in 2015 IEEE Congress on Evolutionary Computation (CEC), Sendai, Japan, pp. 994–1002, 2015. [Google Scholar]
16. M. Raja, “PRAVN: Perspective on road safety adopted routing protocol for hybrid VANET-WSN communication using balanced clustering and optimal neighborhood selection,” Soft Computing, vol. 25, no. 5, pp. 4053–4072, 2021. [Google Scholar]
17. S. Hosmani and B. Mathapati, “Efficient vehicular ad hoc network routing protocol using weighted clustering technique,” International Journal of Information Technology, vol. 13, no. 2, pp. 469–473, 2021. [Google Scholar]
18. W. Zhang, X. Yang, Q. Song and L. Zhao, “V2V routing in vanet based on fuzzy logic and reinforcement learning,” International Journal of Computers Communications & Control, vol. 16, no. 1, pp. 1–19, 2021. [Google Scholar]
19. J. C. C. Martinez, A. J. Y. Delgado and A. T. Cabrera, “Cluster head enhanced election type-2 fuzzy algorithm for wireless sensor networks,” IEEE Communications Letters, vol. 21, no. 9, pp. 2069–2072, 2017. [Google Scholar]
20. D. Molodtsov, “Soft set theory—First results,” Computers & Mathematics with Applications, vol. 37, no. 4–5, pp. 19–31, 1999. [Google Scholar]
21. M. Mizumoto and K. Tanaka, “Fuzzy sets and their operations,” Information and Control, vol. 48, no. 1, pp. 30–48, 1981. [Google Scholar]
22. T. Mahmood, “A novel approach towards bipolar soft sets and their applications,” Journal of Mathematics, vol. 2020, pp. 1–11, 2020. [Google Scholar]
23. Y. Che and D. He, “A hybrid whale optimization with seagull algorithm for global optimization problems,” Mathematical Problems in Engineering, vol. 2021, pp. 1–31, 2021. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |