DOI:10.32604/csse.2022.021767

| Computer Systems Science & Engineering DOI:10.32604/csse.2022.021767 |  |
| Article |
Analysis of Critical Factors in Manufacturing by Adopting a Cloud Computing Service
1Department of Marketing and Distribution Management, National Kaohsiung University of Science and Technology, Kaohsiung (824), Taiwan
2Department of Information Management, Da-Yeh University, Changhua (515), Taiwan
3Graduate Institute of Management, National Kaohsiung University of Science and Technology, Kaohsiung (824), Taiwan
*Corresponding Author: Hsin-Pin Fu. Email: hpfu@nkust.edu.tw
Received: 14 July 2021; Accepted: 23 August 2021
Abstract: The advantages of a cloud computing service are cost advantages, availability, scalability, flexibility, reduced time to market, and dynamic access to computing resources. Enterprises can improve the successful adoption rate of cloud computing services if they understand the critical factors. To find critical factors, this study first reviewed the literature and established a three-layer hierarchical factor table for adopting a cloud computing service based on the Technology-Organization-Environment framework. Then, a hybrid method that combines two multi-criteria decision-making tools—called the Fuzzy Analytic Network Process method and the concept of VlseKriterijumska Optimizacija I Kompromisno Resenje acceptable advantage—was used to objectively identify critical factors for the adoption of a cloud computing service, replacing the subjective decision of the authors. The results of this study determined five critical factors, namely data access security, information transmission security, senior management support, fallback cloud management, and employee acceptance. Finally, the paper presents the findings and implications of the study.
Keywords: Cloud computing service; multi-criteria decision-making; critical factors; fuzzy analytic network process; vlseKriterijumska optimizacija i kompromisno resenje; technology-organization-environment
Enterprises can adopt cloud computing to create innovative solutions, migrate critical applications, and improve financial performance by eliminating expensive older technologies. In addition, it can help enterprises transform their businesses, gain flexibility, and improve operational resilience. Al-Hujran et al. [1] also pointed out that the advantages of a cloud computing service are cost advantages, availability, scalability, flexibility, reduced time to market, and dynamic access to computation resources. Recently, the cloud computing architecture has added increasingly diversified and extensible applications. While organizations in developed countries are increasingly adopting cloud computing, the technology’s adoption rate in developing countries has stagnated, although it has the potential to accelerate the pace of digital transformation [2]. The adoption of a cloud computing service is a form of digital transformation. Understanding its critical factors (CFs) will help enterprises improve the successful adoption rate of cloud computing services.
Boynton et al. [3] defined CFs as a small number of events that can guarantee the success of a business or an organizational manager. If companies focus on certain critical areas—referred to as the CFs—they will have performed successfully in the context of competition. Therefore, it is highly important to determine CFs objectively. However, most of the literature that identified CFs in the past used regression analysis or structural equation modeling (SEM) to find the influencing factors, where subjective decisions were subsequently made by the authors [4,5]. Furthermore, as finding CFs is a problem of multi-criteria decision-making (MCDM), this study uses a hybrid tool that integrates two MCDM tools to identify CFs objectively.
In the past, numerous studies have discussed the factors affecting the introduction of cloud computing. Kim et al. [6] argued that the external environment is a significant factor, especially for cloud computing service providers and government support. Senyo et al. [7] conducted a meta-analysis of cloud computing research in information systems from 2009 to 2015 and found that majority of the literature focused on the technological dimension. Such research is detrimental to the business, conceptualization, and application domains. In the field of education, Sabi et al. [8] developed an adoption model based on contextual factors and constructs from two theories of technology adoption to discover the factors that influence the diffusion, adoption, and use of cloud computing in sub-Saharan African universities. They discovered that socio-cultural factors, demonstrability of results, usefulness, and data security significantly affect their adoption. In addition to achieving knowledge management, Arpaci [9] surveyed the antecedents and consequences of adopting cloud computing in education and found that perceived usefulness is an important factor in adopting cloud services. Hassan et al. [10] investigated the factors influencing small and medium-sized enterprises (SMEs) adopting cloud computing services in Malaysia and found that IT resources and external pressures significantly affected the adoption of cloud computing. Adjei et al. [2] used partial least squares structural equation modeling (PLS-SEM) to study the adoption of cloud computing in Ghana, taking into account institutional factors, and found that institutional factors can influence organizations’ adoption of cloud computing in Ghana. Further, they found that the perceived nature of the prohibited data transmission is essential in shaping the adoption of cloud computing. Ali et al. [11] combined the literature on cloud computing adoption and information systems complexity framework to propose a complexity assessment model for cloud computing adoption. In particular, they found that organizational structural complexity, technological structural complexity, organizational dynamic complexity, and technological dynamic complexity are the critical complexity aspects to be considered in the cloud computing adoption process. Priyadarshinee et al. [5] used a two-stage method to identify the influencing factors using SEM based on 660 professional experts. The results were then used as input data for an artificial neural network model to understand and predict the factors for cloud computing adoption. The results showed that “trust”, “perceived IT security risk”, and “management style” were the most important predictors. Dincă et al. [12] used a logistic regression analysis to identify the determinants of cloud computing adoption among Romanian SMEs and found that managers’ know-how of cloud computing and the perceived costs of implementing the technology represent the main elements influencing the spreading of cloud computing among Romanian SMEs. Furthermore, Raut et al. [13] and Sharma et al. [14] also used MCDM to find factors of cloud computing adoption, indicating that finding CFs is also an MCDM issue.
In the past, studies on CFs have been quantified or are qualitative in nature. Langvinienė et al. [15] used literature analysis to identify CFs that influence the model of entry into foreign business markets in the hotel industry. In addition, Martens et al. [16] utilized a systematic literature review that combines bibliometrics and content analysis to understand the key topics of sustainability in project management and conducted a survey of project managers to determine sustainable CFs in project management. Assaf et al. [17] used regression analysis to find out the CFs entering the foreign market of international hotels. Moreover, Raut et al. [4] used Interpretive Structural Modeling (ISM) to identify CFs for the adoption of cloud computing in micro, small, and medium-sized enterprises (MSMEs), and the results indicated that ‘previous technological experience’ was the most significant factor.
In summary, regression analysis and SEM have been frequently used by authors in previous studies to identify CFs subjectively from influential or important factors of adopting cloud computing. Although the β4value of regression analysis can be expressed as factor importance, it is an estimate that may be subject to error or collinearity, whose resulting value may even be negative [18]. A better way to identify CFs is to use MCDM tools to obtain factor weights and objectively identify CFs.
In terms of the theoretical framework, Tornatzky et al. [19] proposed the technology-organization-environment (TOE) model. TOE provides a clear analytical framework, which can be used as an influencing factor to verify the factors influencing the use of innovative/information technologies in organizations, such as the adoption factors of cloud computing [1,5] and the determinants of cloud computing adoption in higher education [20]. Therefore, this study uses TOE as a theoretical basis to develop a three-layer hierarchical factor table (a dimensional layer, a criterion layer, and a factor layer) that influences manufacturing by introducing cloud computing services based on the literature review.
The choice of CFs is an MCDM issue [13,14], and MCDM techniques can be used to select the best combination and synergy method for a problem. Thus, this study utilizes a hybrid approach that integrates two MCDM tools, namely the Fuzzy Analytic Network Process (FANP) method and the concept of VlseKriterijumska Optimizacija I Kompromisno Resenje (VIKOR) acceptable advantage method [21] based on the TOE framework to find appropriate CFs objectively.
This study considers the research problem as an MCDM issue. The Analytic Hierarchy Process (AHP) proposed by Saaty [22] is the most popular MCDM method for obtaining the weight of factors. However, the AHP method, using a hierarchical structure, is too subjective in assessing values and analyzing various factors, thus failing to explain properly the correlations and interdependence among factors [23]. Saaty [23] subsequently developed the analytic network process (ANP) to improve the deficiencies of the AHP, allowing for a more accurate investigation of specific attributes. Although AHP [22] or ANP [23] is widely applied to solve MCDM problems, it cannot take into account the fuzziness of human thought patterns or the uncertainty of real environments. Therefore, van Laarhoven et al. [24] proposed to integrate the fuzzy concept to the AHP method (called fuzzy AHP), which considers issues of uncertainty, multiple criteria, and opinions of experts and decision-makers, thereby avoiding overly subjective pairwise comparisons. Therefore, this paper integrates the fuzzy concept into the ANP method called fuzzy ANP (FANP). Further, several researchers have used FANP to resolve information and management issues [25,26].
The VIKOR method consists mainly of sorting simultaneously and selecting a set of alternatives to provide a compromise solution to a multi-criteria conflict problem [25]. This so-called “compromise resolution” is close to the ideal solution. Providing this compromise solution, the VIKOR method uses the concepts of “acceptable advantage” and “acceptance stability” to determine the maximum “most-favoured-group utility” and the minimum of the “personal regret of the opponent”. As a result, this negotiated compromise solution emerges as a more acceptable solution for decision-makers. Hence, after applying FANP to find the weights of the factors and sorting them, the concept of VIKOR acceptable advantage is used to objectively identify the CFs. Authors can refer to Opricovic et al. [21] for detailed calculation steps for VIKOR. Integrating the FANP and the concept of VIKOR acceptance advantage, the following steps are taken:
Step 1: Create a hierarchy table
A hierarchical factor table using the TOE framework was established based on a previous literature review of the factors that affect the adoption of cloud computing services.
Step 2: Collect information
Based on the hierarchical factor table, a pairwise questionnaire—called the expert questionnaire—was designed to compare the factors of the same layer. Particularly, respondents answered questions on the comparison of importance between factors.
Step 3: Create a fuzzy number
Generally, there are two main methods for calculating fuzzy numbers: triangular fuzzy numbers and trapezoidal fuzzy numbers. The trapezoidal fuzzy number is more extensive—it reflects the subjectivity of the decision-maker more effectively and contains more uncertainty than the triangular fuzzy number [27]. Thus, trapezoidal fuzzy numbers (Fig. 1) were used in this study to create fuzzy numbers. Buckley [28] extracted four numbers from the collected data for calculation.
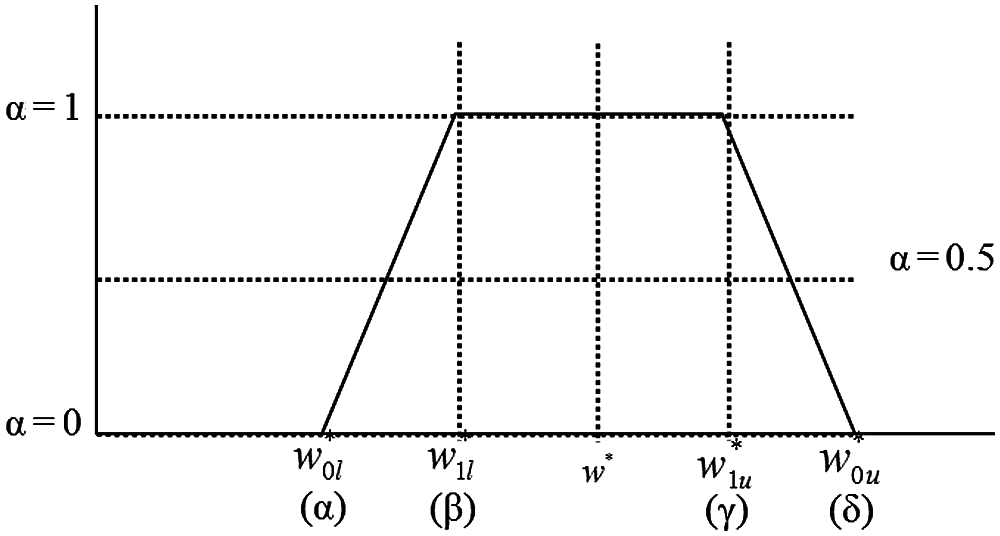
Figure 1: Trapezoidal fuzzy number
These four numbers (α, β, γ, and δ) can form a trapezoidal fuzzy number, and the fuzzy numbers α and δ represent the minimum and maximum values of all membership functions. The fuzzy numbers represented by β and γ are the smallest average and largest average value of the interval, respectively. W*0l, W*1l, W*1u, and W*0u are the fuzzy weight interval values.
Step 4: Establish a fuzzy positive reciprocal matrix
Based on the trapezoidal fuzzy numbers, an n × n fuzzy positive reciprocal matrix (A) was constructed, which can be defined as follows:
Let
Then,
Step 5: Check for consistency
Before calculating the factor weights, the consistency check was first performed on the positive reciprocal matrix, as presented in the expert questionnaire. The consistency indicator is mainly the reasonable degree of the judgments made by the experts during the evaluation process. According to Csutora et al. [29], let
It consists of using the fuzzy pairwise comparison values of all respondents. n is the number of elements of this matrix, and RIn is a random index [30] (Tab. 1) with Saaty [22], suggesting that CR ≤ 0.1 and its consistency are acceptable.
Step 6: Obtain the fuzzy weights, and de-fuzzify and normalize the fuzzy numbers

The matrix established in the previous step was used to perform operations on the starting matrix, and the eigenvalues of the eigenvectors of the starting matrix are calculated and normalized to obtain standardized eigenvalues. This study used the α-cut method and the geometric mean to obtain the fuzzy weights. First, Csutora et al. [29] proposed the α-cut method to determine the fuzzy weight interval values (W*01, W*1l, W*1u, W*0u) for each factor. This method has three advantages: (1) it can handle any pairwise comparison of fuzzy number types, (2) it is computationally simple and does not require calculus, requiring only vector values and eigenvector values of the positive matrix, and (3) it reduces ambiguity compared to other methods [27]. The procedures for calculating the α-cut method are as follows:
Let α = 1 and the α-cut method be used to obtain the fuzzy positive reciprocal matrices A1l and A1u, where A1l = β and A1u = γ. The minimum possible K1l is the maximum possible K1u, and the equation to obtain the fuzzy weight interval values is as follows:
Thus, the fuzzy number interval values can be obtained from K1l and K1u as follows:
Let α = 0.5 and the α-cut method be used to obtain the fuzzy positive reciprocal matrices A0.5l and A0.5u. The minimum and maximum possible numbers are K0.5l and K0.5u, respectively. Then, the fuzzy weight values are obtained. Finally, W*0.5l and W*0.5u can be obtained.
Let α = 0 and the α-cut method be used to obtain the fuzzy positive reciprocal matrices A0l and A0u. The minimum and maximum possible numbers are K0l and K0u, respectively. Then, the fuzzy weight values were obtained. Finally, W*0l and W*0u can be obtained. According to this formula, the fuzzy weight interval values (W*0l, W*1l, W*1u, and W*0u) of each factor can be obtained. Then, the fuzzy weight interval of each factor was de-fuzzified using the geometric mean to obtain the explicit weight value (W*). Finally, the weight values of the factors were normalized to obtain the local weights, and then the local weights of the various hierarchies were connected in series to obtain the global weights. Refer to Csutora et al. [29] for the calculation steps of the α-cut method.
Step 7. Calculate the weighting of the factors
The expert questionnaire was divided into an independent factor questionnaire and a dependent factor questionnaire. The collected expert questionnaires were applied to the above method to calculate the weight values. The weights of FANP were obtained by multiplying the dependent factor weight matrix and the independent factor weight matrix obtained separately. Finally, the weight values were normalized to obtain the local weights, and then the local weights of different layers were connected in series to obtain the global weights.
Step 8: Find CFs using the concept of VIKOR acceptable advantage
Let Q(i) be the ith evaluated alternative (i = 1, 2…j), where j is the number of alternatives, Q(1) is the most suitable solution among all alternatives, and Q(2) represents the second suitable solution among the alternatives.
If TD ≥ DQ, then the better solution Q(i) is the compromise solution, where TD = Q(i + 1) − Q(i) and DQ = 1/(j − 1).
4 Establishing a Hierarchy and Collecting Data
This section analyzes the collection of factors that affect the use of cloud computing and establishes a three-layer hierarchical framework during the literature review. The factor layer table is established based on the recommendations of Saaty [22] (i.e., the factors in the same layer must not exceed 7). Each layer in this study consists of three factors, which is a commonly used method to prevent respondents from becoming impatient due to the complexity of the questionnaire, thus avoiding situations of excessive invalid questionnaires. According to Saaty [22], using a 3-layer, hierarchical model with criteria, sub-criteria, and factor layers in a hierarchical factor design is preferable. In summary, there are 27 factors in the 3 × 3 hierarchical factor table (Tab. 2) from the literature review. The hierarchy table is similar to that studied by Fu et al. [31], except that there are some differences, such as the inclusion of organizational strategies. They verified that the independence of each factor in the same layer is acceptable. Besides, while previous studies verified the importance of most collected factors, this particular study did not need to re-verify its significance.

Following the recommendations of Saaty et al. [35], after establishing the hierarchical factor table, the questionnaire in this study was designed. The factors in each layer were measured using a ratio scale and a pairwise comparison method. Their relative importance was compared, and their importance was then ranked in ascending order, expressed by 1, 2, 3… 9. Tabs. 3–6 show the questionnaires for the criteria layer, while questionnaires for the other layers were similarly designed with the criteria layer.




As soon as the questionnaires were designed, they were sent to the Project Office of Cloud Computing Promotion located at the Industrial Development Bureau (IDB) of the Ministry of Economic Affairs (MOEA), Republic of China. The IDB of MOEA then helped the authors distribute the questionnaires to the senior management of the information technology (IT) departments of 887 large manufacturing enterprises. They further sent each company a copy of the questionnaires, eventually collecting 225 questionnaires in one month. After reviewing, 194 questionnaires were excluded for failing to pass the consistency test (CR ≦ 0.1). This high rejection rate could be due to the complicated questionnaires used in the FANP. Finally, 31 valid questionnaires were used. Following the recommendations of Saaty et al. [35], the decision-making opinions indicated in the collected valid questionnaires were integrated using an arithmetic mean to obtain a pairwise comparison matrix for each criterion. Since the FANP is not based on a statistical method, its greatest advantage is that it does not require large statistical samples [36] and therefore focuses on whether the samples correctly represent the overall image rather than whether there are a sufficient number of samples [36]. Since FAHP uses expert questionnaires, the more senior experts fill out the questionnaire, the better the results will become. Thus, the sampling method is purposive sampling. Regarding the sample size of the expert questionnaires, Delbecq et al. [37] claim that 15 to 30 is a reasonable sample if the group of experts is highly homogeneous. Therefore, the preliminary image can be adequately plotted using the opinions of the 31 experts since the respondents of the questionnaires are senior managers in the IT departments of manufacturing companies. The surveyed group meets the expert feedback requirements with high homogeneity. Besides, purposive sampling is a non-probability sampling method that occurs when the elements selected for the sample are chosen through the researcher’s judgment. Researchers generally believe that they can obtain a representative sample through sound judgment, thereby saving time and cost [38]. Therefore, the sample is suitable for this study.
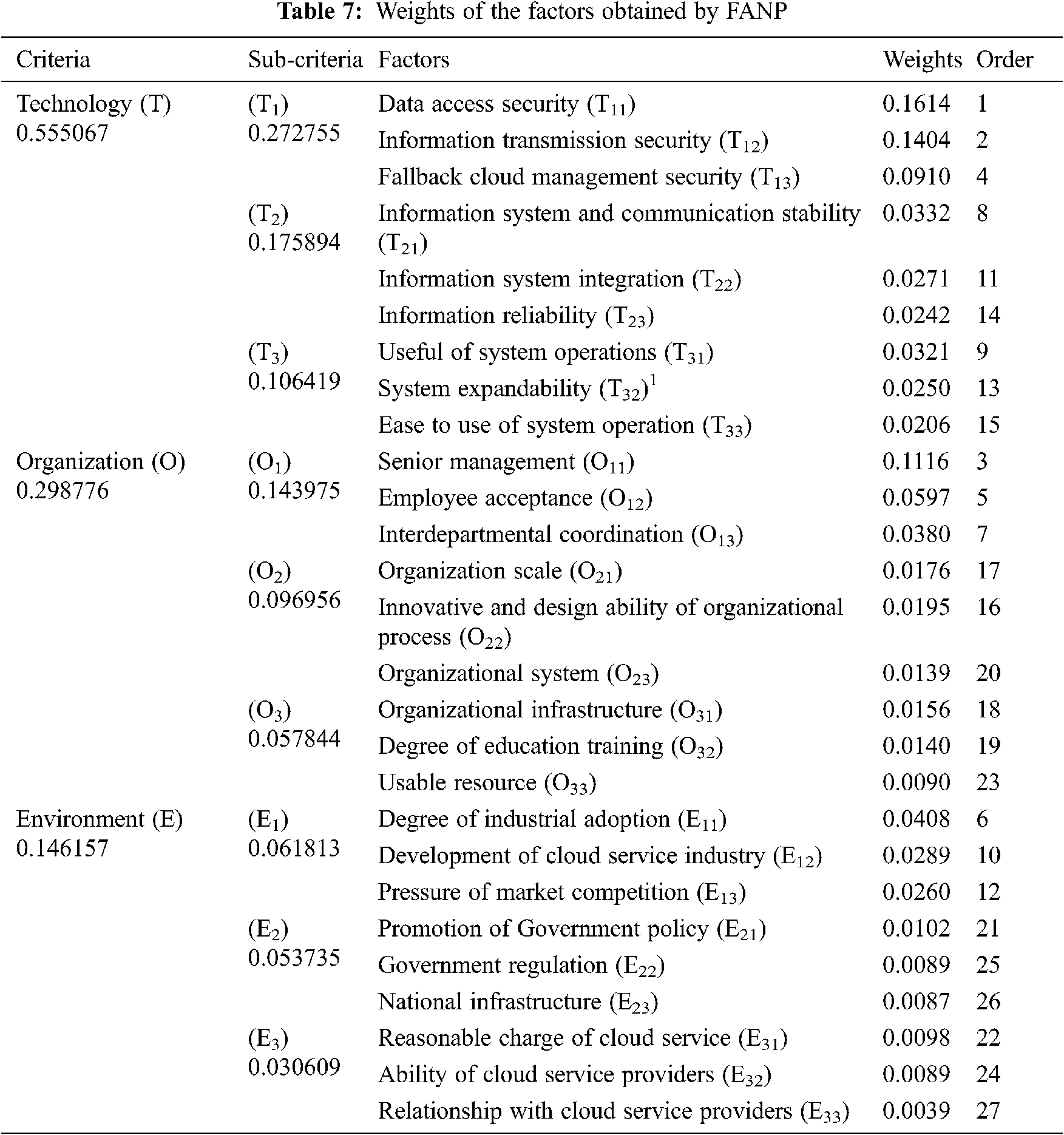
The next step was to calculate the weights of the factors. Based on the 31 valid questionnaires completed by the experts, the weights of the three factors were obtained using the issue of independent factors (Tab. 3) according to steps 3 to 6 indicated in the methodology section of this study. In addition, the weights of the dependent factors can be obtained using the same method (Tabs. 4–6). As such, step 7 is performed. After a set of independent factor weights can form a 3 × 1 matrix and three sets of interdependent factor weights can form a 3 × 3 matrix, the weights of the three factors are obtained by multiplying the separately obtained dependent factor weight matrix and the independent factor weight matrix. The weights of other factors in the same layer can be obtained using the same method, and the obtained weights are normalized to obtain the local weights. Thereafter, the local weights of different layers are connected in series to obtain the global weights of each factor, as shown in Tab. 7.
In step 8, the concept of VIKOR acceptance advantage involves finding a set of feasible solutions gradually. To avoid finding too many solutions for the first time and going beyond the limit, the first 13 factors (81.53%) with an accumulated 80% weight (80/20 rule) are used in finding the CFs. First, the break values of the 13 alternatives should be as follows:
Break value (i) = (Q1−Qi)/(Q1−Q13)
Break value (1) = (0.1614–0.1614)/(0.1614–0.0250) = 0
Break value (2) = (0.1614–0.1404)/(0.1614–0.0250) = 0.1509
The above method calculates the 13th break value as follows:
Break value (13) = (0.1614–0.0250)/(0.1614–0.0250) = 1
TD (1) = Break value (2)-Break value (1) = 0.1539
TD (12) = Break value (13)-Break value (12) = 0.0072
Based on the above procedure, all break and TD values can be calculated (Tab. 8).

In most industries, three to six CFs can be found [3]. However, most studies show the existence of at least 4 CFs [39,40,41]. In this study, the principle of the concept of VIKOR acceptance advantage for extracting CFs involved stopping the extraction immediately if there were more than four CFs with a cumulative weight of more than 50% [42]. If the principle is not simultaneously satisfied, then the CFs extraction work will continue. Based on the above extraction principle, the first extraction in this study obtained five CFs (data access security, information transmission security, senior management support, fallback cloud management, and employee acceptance) with a cumulative weight of 56.42%, exceeding 50% and in line with the principle of stopping extraction. Thus, a total of 5 CFs were obtained (Tab. 8).
This study used the method that combines two MCDM tools to find five CFs for the adoption of a cloud service. Finally, this paper describes the findings and implications of the study as follows.
1)The first CF is data access security (0.1614) under system security, indicating that enterprises should pay the greatest attention to the privacy and confidentiality of cloud computing. This factor is a top priority. Therefore, an enterprise is more likely to adopt a cloud provider’s system if it provides highly secure access to cloud data. Access security must include not only an account and password but also data access, access numbers, and a system to control who can access such data.
2)The second CF is information transmission security (0.1404). Some enterprises prefer that the data be transmitted to cloud computing over the Internet because they have to choose public cloud computing due to cost considerations. However, the Internet poses many security problems—For example, hackers may capture confidential data during transmission. Thus, the protection mechanism provided by a cloud computing provider is essential.
3)The third CF is the support and participation of senior management (0.1116). The introduction of new technologies is an important strategy that requires coordination between an enterprise’s strategy and its resources, as well as the support and participation of senior management. More so, it can be hindered if senior management is unwilling to provide adequate support. Therefore, senior management support is an important influencing factor.
4)The fourth CF is fallback cloud management security (0.0910). It can be seen that the senior management is concerned about the inability of the cloud computing system to provide services after a disaster, possibly causing an enterprise to suffer huge losses. Thus, the cloud computing system must be shockproof, fireproof, and have an uninterruptible power supply, as well as other fallback mechanisms. Therefore, it must provide a high level of Service Level Agreements (SLAs).
5)The fifth CF is employee acceptance (0.0597). If employees accept the new technology, then the likelihood of them using cloud computing will increase. When an enterprise decides to use cloud computing, there must be discussion and communication within them in order to reach a consensus. Importantly, relevant personnel must be trained.
1) The method presented in this paper can objectively identify CFs, which differs from previous studies mainly due to the authors’ subjective decisions.
This paper describes a study that is an extension of the TOE framework in cloud computing research. The TOE framework has been found to analyze an enterprise’s internal and external situations clearly and effectively when adopting information systems. In addition, this paper integrates MCDM tools to identify CFs objectively based on the TOE framework, which applies to the factors affecting the adoption of cloud computing services. This feature differentiates this study from previous studies on the method of identifying CFs.
2) The most important factor affecting the use of cloud computing in the industry is information security.
Cloud computing relies heavily on data transmission and access via the Internet. If users can connect to a network, then they can perform multiple operations. Since serious data leakage is extremely difficult to prevent when using the Internet, enterprises must prioritize information security and do everything possible to perfect the mechanism before using cloud computing. Furthermore, preventing the cloud system from being hacked is crucial for cloud computing service providers when building the cloud system.
3) Enterprises should pay attention to organizational issues when implementing cloud computing.
The literature related to cloud computing discusses adoption factors based on an organizational or strategic perspective. The results of the study indicate that the support and participation of senior management are the third CF. In addition, employee acceptance is a CF. The implementation of cloud computing is a major project for enterprises and involves many dimensions. The active participation of senior management in providing support and resources relevant to the project is vital, thus minimizing employees’ skepticism and their resistance to the system. This will significantly increase the likelihood of a successful introduction of cloud computing.
4) Enterprises should allocate suitable resources for the adoption of a cloud computing service.
The study identified five CFs for enterprises to adopt a cloud computing service so that they can strategically plan and allocate adequate resources, thereby avoiding adoption failures due to faulty decision-making. Therefore, enterprises with limited resources should preferably allocate their resources to the five CFs. If there are surplus resources, these can be allocated to other important factors. In this way, enterprises can better allocate their resources for adopting cloud computing services at a lower cost and with greater efficiency.
5) The study provides information that will be beneficial to cloud computing service providers.
This study collected the adoptive factors of cloud computing services from a literature review based on the TOE framework and used the proposed hybrid approach to identify CFs objectively. Cloud computing service providers can use these results to develop products for cloud computing service solutions that meet customer requirements, especially in terms of Internet safety, security, and privacy protection. Furthermore, cloud computing service providers can develop more effective marketing strategies by understanding the different layers of factors important to their clients.
This study used the TOE framework from a literature review to establish a hierarchical table of factors affecting an enterprise’s adoption of cloud computing services. Further, it used two combined MCDM tools to identify CFs objectively, replacing the authors of previous studies who decided CFs subjectively. After analyzing the factor weights, five CFs (data access security, information transmission security, senior management support, fallback cloud management, and employee acceptance) were found among enterprises’ adoption of cloud computing services, and the findings and implications were discussed. The study results can enable enterprises to identify CFs objectively in adopting a cloud computing service and allocate their resources based on the weights of the CFs to adopt new systems that are less costly and more efficient, thus enhancing the success rate of adopting cloud computing services. In addition, some previous literature has discussed the adoptive factors of cloud computing services from the viewpoint of cloud service providers. The current study reveals that enterprises should pay more attention to the “degree of industrial adoption” in the external environment, despite some previous studies suggesting that the stability and professionalism of cloud service providers should remain an important factor in the external environment. Finally, companies will be more willing to use a cloud computing service only when their technology platforms are rich and mature.
To determine the factors affecting the use of cloud computing in enterprises, this study established a hierarchical factor table for analysis with reference to the TOE framework, as used by scholars in previous literature. The dimensions affecting the use of cloud computing are extensive, bearing the possibility that not all factors were found. Moreover, if too many factors are listed, respondents may have difficulty completing the questionnaire. Besides, we examined a different approach, and the questionnaire developed for the survey adopted the FANP, which can resolve the dependencies between evaluation factors. However, due to the complexity and the extensive content of the questionnaire, respondents may not fully understand the answering method and may lose patience, resulting in many invalid questionnaires.
Although cloud computing research covers several fields, this study only focuses on the demands of large-scale manufacturing enterprises in Taiwan. In the future, the authors can further explore whether the factors affecting the use of cloud computing differ at different developmental phases of adoption and in different countries, such as different sizes of enterprises and different specific industries. Moreover, the authors can investigate issues from time to time and conduct comparative analyses across different industries or across different business scales or different areas to see differences.
Funding Statement: This research was supported by the Ministry of Science and Technology (MOST), Taiwan, R.O.C. (104-2410-H-327-024-).
Conflicts of Interest: All the authors declare that they have no conflicts of interest to report regarding the present study.
1. O. Al-Hujran, E. M. Al-Lozi, M. M. Al-Debei and M. Maqableh, “Challenges of cloud computing adoption from the toe framework perspective,” International Journal of E-Business Research, vol. 14, no. 3, pp. 18, 2018. [Google Scholar]
2. J. K. Adjei, S. Adams and L. Mamattah, “Cloud computing adoption in Ghana; accounting for institutional factors,” Technology in Society, vol. 65, pp. 101583, 2021. [Google Scholar]
3. A. C. Boynton and R. W. Zmud, “An assessment of critical success factors,” Sloan Management Review, vol. 25, no. 4, pp. 17–27, 1984. [Google Scholar]
4. R. D. Raut, B. B. Gardas, M. K. Jha and P. Priyadarshinee, “Examining the critical success factors of cloud computing adoption in the MSMEs by using ISM model,” Journal of High Technology Management Research, vol. 28, no. 2, pp. 125–141, 2017. [Google Scholar]
5. P. Priyadarshinee, R. D. Raut, M. K. Jha and B. B. Gardas, “Understanding and predicting the determinants of cloud computing adoption: A two staged hybrid SEM–neural networks approach,” Computers in Human Behavior, vol. 76, pp. 341–362, 2017. [Google Scholar]
6. S. H. Kim, S. Y. Jang and K. H. Yang, “Analysis of the determinants of software-as-a-service adoption in small businesses: Risks, benefits, and organizational and environmental factors,” Journal of Small Business Management, vol. 55, no. 2, pp. 303–325, 2017. [Google Scholar]
7. P. K. Senyo, E. Addae and R. Boateng, “Cloud computing research: A review of research themes, frameworks, methods and future research directions,” International Journal of Information Management, vol. 38, no. 1, pp. 128–139, 2018. [Google Scholar]
8. H. M. Sabi, F. M. E. Uzoka, K. Langmia, F. N. Njeh and C. K. Tsuma, “A cross-country model of contextual factors impacting cloud computing adoption at universities in sub-saharan Africa,” Information Systems Frontiers, vol. 20, no. 6, pp. 1381–1404, 2018. [Google Scholar]
9. I. Arpaci, “Antecedents and consequences of cloud computing adoption in education to achieve knowledge management,” Computers in Human Behavior, vol. 70, pp. 382–390, 2017. [Google Scholar]
10. H. Hassan, M. H. M. Nasir, N. Khairudin and I. Adon, “Factors influencing cloud computing adoption in small and medium enterprises,” Journal of Information and Communication Technology, vol. 16, no. 1, pp. 21–41, 2017. [Google Scholar]
11. O. Ali, A. Shrestha, M. Ghasemaghaei and G. Beydoun, “Assessment of complexity in cloud computing adoption: A case study of local governments in Australia,” Information Systems Frontiers, 2021. (online publication). https://doi.org/10.1007/s10796-021-10108-w. [Google Scholar]
12. V. M. Dincă, A. M. Dima and Z. Rozsa, “Determinants of cloud computing adoption by Romanian SMEs in the digital economy,” Journal of Business Economics and Management, vol. 20, no. 4, pp. 798–820, 2019. [Google Scholar]
13. R. D. Raut, B. B. Gardas, B. E. Narkhede and V. S. Narwane, “To investigate the determinants of cloud computing adoption in the manufacturing micro, small and medium enterprises: A DEMATEL-based approach,” Benchmarking: an International Journal, vol. 26, no. 3, pp. 990–1019, 2019. [Google Scholar]
14. M. Sharma, R. Gupta and P. Acharya, “Prioritizing the critical factors of cloud computing adoption using multi-criteria decision-making techniques,” Global Business Review, vol. 21, no. 1, pp. 142–161, 2020. [Google Scholar]
15. N. Langvinienė and I. Daunoravičiūtė, “Factors influencing the success of business model in the hospitality service industry,” Procedia - Social and Behavioral Sciences, vol. 213, pp. 902–910, 2015. [Google Scholar]
16. M. L. Martens and M. M. Carvalho, “Key factors of sustainability in project management context: A survey exploring the project managers’ perspective,” International Journal of Project Management, vol. 35, no. 6, pp. 1084–1102, 2017. [Google Scholar]
17. A. G. Assaf, A. Josiassen and F. W. Agbola, “Attracting international hotels: Locational factors that matter most,” Tourism Management, vol. 47, pp. 329–340, 2015. [Google Scholar]
18. J. F. Hair, W. C. Black and B. J. Babin, Multivariate Data Analysis: Global Edition, London: Pearson education, 2010. [Google Scholar]
19. L. Tornatzky and M. Fleischer, The Process of Technology Innovation, Lexington, MA: Lexington Books, 1990. [Google Scholar]
20. M. B. Ali, “Multiple perspective of cloud computing adoption determinants in higher education,” International Journal of Cloud Applications and Computing, vol. 9, no. 3, pp. 21, 2019. [Google Scholar]
21. S. Opricovic and G. H., Tzeng, “Compromise solution by MCDM methods: A comparative analysis of VIKOR and TOPSIS,” European Journal of Operational Research, vol. 156, no. 2, pp. 445–455, 2004. [Google Scholar]
22. T. L. Saaty, The Analytic Hierarchy Process, New York: McGraw-Hill, 1980. [Google Scholar]
23. T. L. Saaty, The Analytic Network Process, Pittsburgh: RWS Publications. Expert Choice, Inc., 1996. [Google Scholar]
24. P. J. M. van Laarhoven and W. Pedrycz, “A fuzzy extension of saaty’s priority theory,” Fuzzy Sets and Systems, vol. 11, pp. 229–241, 1983. [Google Scholar]
25. T. A. Cagri, F. Tuysuz and C. Kahraman. “A fuzzy multi-criteria decision analysis approach for retail location selection,” International Journal of Information Technology & Decision Making, vol. 12, no. 4, pp. 729–755, 2013. [Google Scholar]
26. S. Ahmed and A. Alhumam, “Unified computational modelling for healthcare device security assessment,” Computer Systems Science and Engineering, vol. 37, no. 1, pp. 1–18, 2021. [Google Scholar]
27. R. J. Girubha and S. Vinodh, “Application of fuzzy VIKOR and environmental impact analysis for material selection of an automotive component,” Materials & Design, vol. 37, pp. 478–486, 2012. [Google Scholar]
28. J. J. Buckley, “Fuzzy hierarchical analysis,” Fuzzy Sets and Systems, vol. 17, no. 3, pp. 233–247, 1985. [Google Scholar]
29. R. Csutora and J. J. Buckley, “Fuzzy hierarchical analysis: The lambda-max method,” Fuzzy Sets and Systems, vol. 120, no. 2, pp. 181–195, 2001. [Google Scholar]
30. J. Aguaron and J. M. Moreno-Jiménez, “The geometric consistency index: Approximated thresholds,” European Journal of Operational Research, vol. 147, no. 1, pp. 137–145, 2003. [Google Scholar]
31. H. P. Fu and T. S. Chang, “An analysis of the factors affecting the adoption of cloud consumer relationship management in the machinery industry in Taiwan,” Information Development, vol. 32, pp. 1741–1756, 2016. [Google Scholar]
32. M. Alenezi, “Safeguarding cloud computing infrastructure: A security analysis,” Computer Systems Science and Engineering, vol. 37, no. 2, pp. 159–167, 2021. [Google Scholar]
33. L. E. Bautista-Villalpando and A. Abran, “A data security framework for cloud computing services,” Computer Systems Science and Engineering, vol. 37, no. 2, pp. 203–218, 2021. [Google Scholar]
34. V. I. C. Chang, “A proposed framework for cloud computing adoption,” International Journal of Organizational and Collective Intelligence, vol. 6, no. 3, pp. 75–98, 2016. [Google Scholar]
35. T. L. Saaty and L. G. Vargas, Models, Methods, Concepts and Applications of the Analytic Hierarchy Process, Germany: Kluwer Academic Publishers, 2001. [Google Scholar]
36. J. M. Duke and R. Aull-Hyde, “Identifying public preferences for land preservation using the analytic hierarchy process,” Ecological Economics, vol. 42, no. 1–2, pp. 131–145, 2002. [Google Scholar]
37. A. L. Delbecq, A. H. Van de Ven, D. H. Gustafson, A. L. Delbecq, V. de Ven, H. Andrew and D. H. Gustafson, Group Techniques for Program Planning: a Guide to Nominal Group and Delphi Processes, Illinois: Scott, Foresman and Company, 1975. [Google Scholar]
38. K. Black, Business Statistics: For Contemporary Decision Making, 9th editionHoboken, NJ: Wiley, 2016. [Google Scholar]
39. A. Zarei and S. Iran, “Identification of key success factors - in developing a character merchandising in the Iranian marketplace using grounded theory method,” Journal of Business Management, vol. 10, no. 3, pp. 567–582, 2018. [Google Scholar]
40. V. Janjić, M. Todorović and D. Jovanović, “Key success factors and benefits of kaizen implementation,” Engineering Management Journal, vol. 32, no. 2, pp. 98–106, 2020. [Google Scholar]
41. S. Moya and M. Camacho, “Identifying the key success factors for the adoption of mobile learning,” Education and Information Technologies, vol. 26, pp. 3917–3945, 2021. [Google Scholar]
42. A. Lin, T. H. Chang, H. P. Fu, H. P. Yeh, K. Y. Hsu and H. Y. Tsai, “Analysis of the CSFs affecting project execution: A case application,” Total Quality Management & Business Excellence, vol. 29, no. 7-8, pp. 848–865, 2018. [Google Scholar]
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |