DOI:10.32604/csse.2021.015284

| Computer Systems Science & Engineering DOI:10.32604/csse.2021.015284 |  |
| Article |
Impact of Tools and Techniques for Securing Consultancy Services
1Department of Information Technology, College of Computers and Information Technology, Taif University, P.O. Box 11099, Taif 21944, Saudi Arabia
2Department of Computer Science, College of Computers and Information Technology, Taif University, P.O. Box 11099, Taif 21944, Saudi Arabia
3Department of Information Technology, Babasaheb Bhimrao Ambedkar University, Lucknow, 226025, India
4Department of Computer Application, Shri Ramswaroop Memorial University, Barabanki, 225003, India
*Corresponding Author: Rajeev Kumar. Email: rs0414@gmail.com
Received: 13 November 2020; Accepted: 11 January 2021
Abstract: In a digital world moving at a breakneck speed, consultancy services have emerged as one of the prominent resources for seeking effective, sustainable and economically viable solutions to a given crisis. The present day consultancy services are aided by the use of multiple tools and techniques. However, ensuring the security of these tools and techniques is an important concern for the consultants because even a slight malfunction of any tool could alter the results drastically. Consultants usually tackle these functions after establishing the clients’ needs and developing the appropriate strategy. Nevertheless, most of the consultants tend to focus more on the intended outcomes only and often ignore the security-specific issues. Our research study is an initiative to recommend the use of a hybrid computational technique based on fuzzy Analytical Hierarchy Process (AHP) and fuzzy Technique for Order Preference by Similarity to Ideal Solutions (TOPSIS) for prioritizing the tools and techniques that are used in consultancy services on the basis of their security features and efficacy. The empirical analysis conducted in this context shows that after implementing the assessment process, the rank of the tools and techniques obtained is: A7 > A1 > A4 > A2 > A3 > A5 > A6 > A7, and General Electric McKinsey (GE-McKinsey) Nine-box Matrix (A7) obtained the highest rank. Thus, the outcomes show that this order of selection of the tools and techniques will give the most effective and secure services. The awareness about using the best tools and techniques in consultancy services is as important as selecting the most secure tool for solving a given problem. In this league, the results obtained in this study would be a conclusive and a reliable reference for the consultants.
Keywords: Consultancy services; fuzzy AHP; fuzzy TOPSIS; consultancy tools and techniques; security evaluation
There has been an exponential growth in the field of consultancy services. This is evident from the survey that cites that more than 4.3 million people were involved in this sector in 2018–2019 and the revenue generated in this field was 634 billion USD [1,2]. Many experts in different professions are focusing more on providing consultancy services nowadays because of the flexibility of work hours, freedom to choose one’s project, challenge to innovate and lucrative returns that a consultancy assignments offer. A study undertaken in this context states that 36% of the consultancy services are established in the USA alone and 20% of these professionals are working as full-time consultants [2].
Consultant, as a term, usually refers to an expert who renders the much needed advise, solution or recommendations to a particular group of people or an organisation. Consultant’s expertise is sought for changing, improvising and enhancing the existing mechanisms for best results. However, the most elemental constraint in the consultancy services is to deliver highly productive, cost-effective as well as sustainable solutions for a particular problem. There are several tools and techniques for delivering highly productive, cost-effective as well as sustainable solutions and the consultants need to choose the most secure tools and techniques for solving the client’s problem. Moreover, making a judicious and informed choice of the right tool and technique becomes even more critical when the problem needs to be addressed within a stipulated timeline [3].
Thus, to save on the resources and time while ensuring the best dividends for the clients’ trust, it becomes imperative for the consultants to be aware about the effectiveness of the tools and techniques that are to be used for rendering the services. Selection of tools and techniques is a critical task. Moreover, there can be several options and preferences depending on the consultants’ experiences. Hence, in this scenario of multiple options, the best solution can be reached by employing the fuzzy based MCDM technique to select the most conversant options. The present study is an attempt to evaluate the impact of tools and techniques that are used by the consultants. To achieve the stated objective, our study has used the hybrid computational method based on fuzzy AHP and fuzzy TOPSIS. The ranking order would enable the consultant to opt for the most secure tool at a given time for working on the best solution to a problem.
Depending on their contributions, nature and domain of work, consultancy services can be categorised into three different types: management consultancy services, corporate consultancy services, and the independent consultancy services [3]. Brief explanations on the three have been enlisted below:
2.1 Management Consultancy Services
Management consultancy services are dominated by large organizations that want to improve their business and hire the consultants to help them shape their visions. In the professional world, management consultants are known to be the recipients of the highest salary package.
2.2 Corporate Consultancy Services
Corporate consultancy services are more pertinent to the corporate world. House consultancy services, business to business consultancy services, implementation team are some of the examples of corporate consultancy services. In this field, the consultant should have a minimum of 10 years of experience in corporate working. In- house consultants are usually a part of software or the IT firms, etc.
2.3 Independent Consultancy Services
Independent consultancy services are more like self-employment ventures in offering consultancy facilities. Millions of independent consultants are creating attractive business for themselves.
3 Phases of Consultancy Services
Five phases of consultancy services that have been coined by Block [3] are shown in Fig. 1 below.

Figure 1: Phases of consultancy services
This phase deals with the first interface between the client and the consultant. The meeting between the two stakeholders includes the following concerns:
Understanding the client’s need and the intended objective.
This interview also helps the clients to determine if the consultants have the requisite skills.
Listing the clients’ goals.
Specifying what expectations the client & the consultant have.
Drafting the blueprint for the project.
3.2 Data Collection and Diagnosis
In this phase, the consultants dissect, analyse and comprehend the problem. The key factors that the consultant focuses on might include: who defined the problem, what tools and techniques need to be used, what kind of data must be collected and how long will it take to resolve the issue.
Feedback is an essential phase in which the consultants give a detailed report to the clients about the possible strategies and solutions needed to meet the intended target. Usually, the consultant decides upon how the client should be involved in the extraction of data. A consultant should be ready to face resistance from the organization when giving feedback.
This phase includes the process of implementing the solutions as strategized by the consultant after a detailed discussion with the client. If any changes are made in the implementation, then a series of meetings and training sessions are organised.
In this phase, the consultant takes a decision about whether the process needs to be extended or not. If the implementation is successful, the process extends further; otherwise the process is terminated [4].
There are four types of consultative approaches are:
This approach is very popular in organizations for fixing a problems.
This approach is used for problems in their worst condition and experts are contacted for accurate diagnosis of the problem.
This approach of consultancy services involves a series of steps formulated by the consultant to assimilate, understand the clients’ needs and work on the most viable solution.
The emergent approach is used to address contexts that might arise in future. This approach is added as a feature in the present approach and is intended to further improve the project in future.
5 Tools and Techniques for Consultancy Services
Various tools and techniques are used by the consultants for providing effective and satisfactory services. A consultant can use the best tool and technique for securing the collected data or information. Some pertinent tools and techniques are discussed below in Fig. 2 [5].

Figure 2: Pertinent tools and techniques
SWOT analysis is a technique for the strategic planning of the information. This technique is used by the consultant to identify the strengths, weaknesses, opportunities, and possible threats associated with a plan. This tool is used in the primary stage of the decision making process and aids in calculation of the strategy for the organization. This tool does not prioritize the issues and does not provide the solutions.
This tool helps the consultant to compare the business and performance metrics of one organisation with the other organization. Benchmarking helps in improving the performance of the organization. Performance metrics compared by benchmarking includes production costs, employee turnover, and process time. Benchmark does not provide the solutions to the problem. The technique helps in identifying the areas that require improvement.
It is a graphical tool of consultancy services that lists the causes of a problem along with the possible effects. It shows all the causes simultaneously. It is also known as the Ishikawadiagram. It provides the relevant causes of a problem [6].
The balanced scorecard helps to track the purpose, vision, values, strategic and operational activities of the organization. This tool is used in different matrices like revenue, earning, and market share, etc. [7,8].
Porter’s five forces is a framework for evaluating a business and for identifying a qualitative strategy for potential profitability in any industry. Porter’s principle is based on five parameters. These parameters help the consultants to design a strategic plan for their client. These parameters are as follows:
Competitor Rivalry
Supplier Power
Buyer Power
The Threat of New Entrants
The Threat of Substitute Offerings
5.6 The BCG Growth-Share Matrix
This tool was developed by Boston Consulting Group (BCG). It is used to assess the strength of product lines within the portfolios of the industry. Product lines are assigned to one of the following four quadrants:
Cash Cows
Stars
Question Marks
Dogs
5.7 The GE-Mckinsey Nine-Box Matrix
This tool is used for assessing the business matrix of various opportunities and prioritizes its investments among its business units. GE McKinsey Matrix gives appropriate solutions for issues like low-profit margins, shortage of skilled and experienced workforce in an organisation. Nine-Box matrix helps the organization in planning more effective business strategies for higher profitability.
6 Securing Consultancy Services
Security issues pertaining to the tools and techniques that are used in consultancy services have been discussed below in Fig. 3. All these factors affect the security of consultancy services through tools and techniques. Security is the main concern in the consultancy services and security depends on effectiveness of tools and techniques during consultancy services. Besides ensuring the security of consultancy services through tools and techniques, the steps that involve the processing and the elicitation of information also require security at every level [9].

Figure 3: Consultancy tools, techniques and criteria
Confidentiality of the data is required at the processing and elicitation time. Consultancy services need all the information related to their clients and the clients provide the highly classified information with the belief that their data will remain confidential. Hence, the feature of confidentiality assumes a major role in this context.
Information of the clients should not change or be changed under any circumstances. Even a slightest change in the information can alter the end results which may not meet the clients’ expectations.
Authentication of the tools and techniques at the consultants’ end should be done before processing the data.
Authorization of the consultants should be done before processing the information. Authorization checks the legal use of the tools and techniques.
Tools and technique should be available whenever the needs arise.
Fuzzy AHP was first proposed by Thomas L. Saaty [10]. The practitioners mostly used the AHP technique for any multiple criteria decision problem [10–15]. This technique collates the opinions of the experts on a given context as the input. The multifaceted opinions are then converted into quantitative values for a detailed analysis. However the AHP method has some limitations, more so in the case of reaching a balanced judgement and in doing pair-wise comparison of the factors [11]. Fuzzy AHP is more effective for solving these issues in the hierarchy process. By the fuzzy AHP, the decision makers can give the best approximate, if not the exact, solution to the problem. Fuzzy AHP adopted TFN to simplify the calculations. Fuzzy number is defined in TFN as a (k, l, m) [12]. In the triangle, k denotes a small promising value, l as the most promising value and m as a large promising value.
Definition 1: In this equation,  ,
,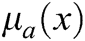 denotes membership function, a is a real number among the
denotes membership function, a is a real number among the 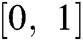 .
.
Definition 2: Operations on the TFN 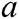 are defined as a (k, l, m) as shown in Fig. 4, and the membership function
are defined as a (k, l, m) as shown in Fig. 4, and the membership function 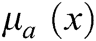 is explained by Eq. (1).
is explained by Eq. (1).
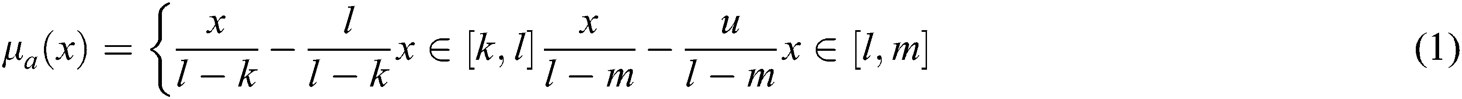
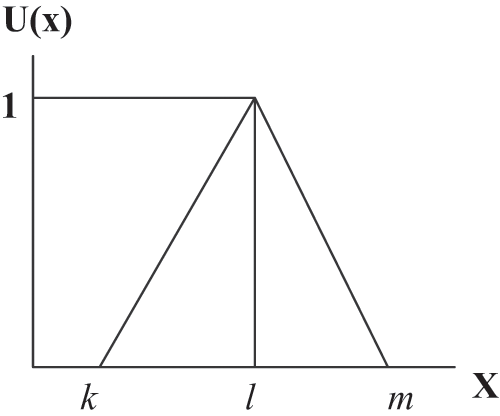
Figure 4: Triangular fuzzy number
Experts assigned the score of their opinions quantitatively. This is presented through Saaty’s scale as shown in Tab. 1.
Table 1: The Saaty scale of TFN

Assume M1 and M2 to be two TFN parameters of the triangle M1 = (k, l, m) and M2 = (k, l, m). The laws of operational on these two TFN are performed by Eqs. (2)–(4).
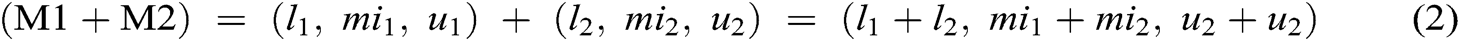
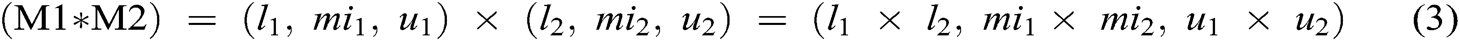
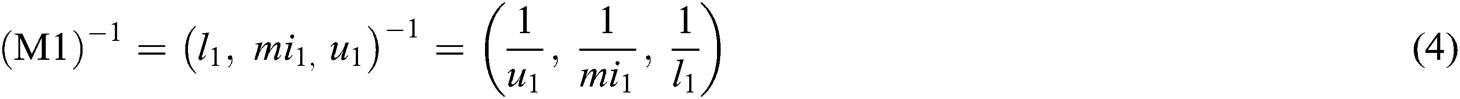
After calculating the TFN values of the M1 and M2, n x n matrix fuzzy pair-wise comparison matrix is constructed with the help of Eq. (5) and pair-wise matrix is converted into TFN numbers.

Eq. (6) is used to calculate the average of the preferences of decision makers. In Eq. (6)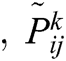 presents the dth decision makers’ preference of the ith criteria over the jth criteria. If two and more decision makers are available in the decision making group, then the preferences are calculated by the Eq. (6).
presents the dth decision makers’ preference of the ith criteria over the jth criteria. If two and more decision makers are available in the decision making group, then the preferences are calculated by the Eq. (6).

After calculating the preferences of the decision makers, the fuzzy geometrical mean of each factor is calculated by Eq. (7).

The final tabulation is achieved after calculating the geometric mean of the factors. Thereafter the average of the fuzzy weights is determined. The weights and normalized fuzzy weight criteria are obtained by Eq. (8). The weights are assigned to all the factors and alternatives. The factors and the alternatives are ranked according to their respective weights.

Definition 3: For the final analysis, the value is defuzzified by the COA technique which is used to calculate the BNP (Best Non-fuzzy Performance) value of the fuzzy weights of each measurement with the help of Eqs. (9)–(11).


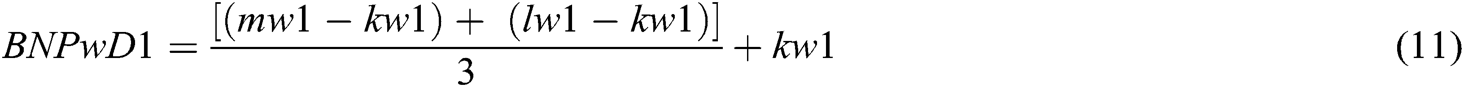
Fuzzy TOPSIS is used for assigning the ranks to the chosen alternatives and calculating the alternative that is closest to the ideal solution [13–15]. Alternatives’ closeness is calculated in both the positive and the negative way. The Fuzzy Ideal Positive Solution (FPIS) and Fuzzy Ideal Negative Solution (FNIS) are calculated by using this method as in [16–18]. Steps involved in the Fuzzy TOPSIS are discussed below:
Step 1—In this step, the linguistic variable of the criteria is determined. Membership function is assigned to each linguistic variable.
Step 2—Fuzzy Decision Matrix
Fuzzy decision matrix is constructed by the n criteria and m alternatives (nxm), and the matrix is directly related to the criteria and alternatives (Eqs. (12)–(14)).


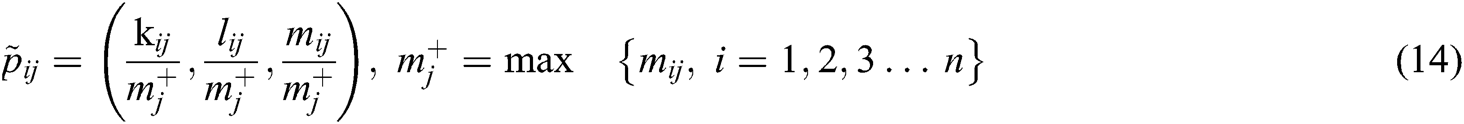
A1, A2….A7 are the alternatives of the tools and techniques which are ranked by the selected criteria, 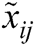 represents the ranking of the alternatives, Normalized decision matrix is shown by
represents the ranking of the alternatives, Normalized decision matrix is shown by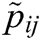 , authors have set the max values of
, authors have set the max values of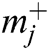 as equal to 1, otherwise it is 0.
as equal to 1, otherwise it is 0.
Step 3—Weight Fuzzy Decision Matrix
The weighted normalized fuzzy decision matrix is calculated by multiplying the weights of the alternatives and the normalized fuzzy decision matrix. By using the Eqs. (15) and (16), we calculated the weighted normalized decision matrix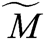 .
.
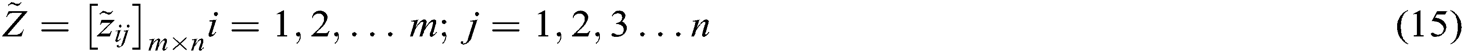
where

Step 4—Evaluate the FPIS and FNIS
Normalized fuzzy decision matrix is used to evaluate the FPIS & FNIS distance from the ideal solution. The values of the ideal solution lie between [0,1]. FPIS & FNIS are evaluated by the Eqs. (17) and (18).


Here 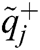 = (1, 1, 1) and
= (1, 1, 1) and 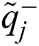 = (0, 0, 0), j = 1, 2, 3… n.
= (0, 0, 0), j = 1, 2, 3… n.
Step 5—Distance of the Alternatives
Distance of the alternatives from the FPIS & FNIS is represented by 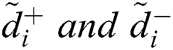 of each alternative
of each alternative 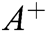 and
and 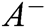 evaluated by Eqs. (19) and (20).
evaluated by Eqs. (19) and (20).
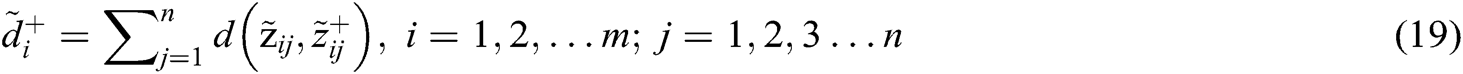
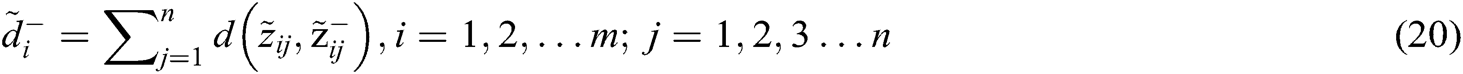
Step 6—Closeness Coefficient
Closeness coefficient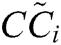 determines the ranks of the alternatives.
determines the ranks of the alternatives. 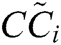 represent the closeness from FPIS to the alternative and the farthest distance from FNIS of the alternatives. Closeness coefficient
represent the closeness from FPIS to the alternative and the farthest distance from FNIS of the alternatives. Closeness coefficient 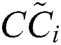 of the alternatives is evaluated by Eq. (21).
of the alternatives is evaluated by Eq. (21).

Step 7—Ranking of the Alternatives
Ranks are assigned to each alternative by evaluating the closeness coefficient. The highest coefficient represents the highest rank and the best alternative.
The researchers used the Fuzzy AHP for ranking 7 specific tools and techniques that are frequently used by the consultants. In the fuzzy AHP, a group of experts gave their decisions on this method. For this, the initial step was to profile a questionnaire prepared by a consultant. The questionnaires drew responses from the clients. These responses were collated to provide the ranking to the linguistic variables for calculating the weights. The weights were assigned to each tool and technique according to their levels of security. The weights determined the ranks of the tools and techniques. The ranking was solely based on the clients’ satisfaction with the use of a particular consultancy services. Pair-wise aggregated matrix was constructed by using the linguistic terms, as shown in Tab. 1 and Eqs. (1)–(8) [17–19]. The results are mapped in Tab. 2.
Weights of the factors or criteria are calculated through Eqs. (9)–(11) and assigned to the rank according to the obtained weight; results are shown in Tab. 3. According to weights of factors and ranking, it is evident that the scope of the project plays an important role in meeting the clients’ needs. The client’s problem has obtained the lowest rank. Through Eqs. (12)–(16), we have calculated the subjective cognition results that are shown in Tab. 4, normalized fuzzy-decision matrix has been shown in Tab. 5, and normalized weighted fuzzy-decision matrix is depicted in Tab. 6. After calculating the fuzzy decision matrix, through Eqs. (17)–(21), we calculated the defuzzified value and the satisfaction degree of each alternative, as shown in Tab. 7 and Fig. 5.
Linguistic terms are transformed into TFN to form a subjective cognition matrix. Fuzzy decision matrix is normalized by Eqs. (12)–(14) and shown in Tab. 5. The weighted normalized fuzzy-decision matrix is constructed by using Eqs. (15) and (16), as shown in Tab. 6. By using Eqs. (17) and (18), we evaluated the FPIS & FNIS of the alternatives. Distance between the alternatives from FPIS & FNIS was calculated by Eqs. (19) and (20), as shown in Tab. 7. The closeness coefficient of each alternative and the rank of each alternative were evaluated by the Eq. (21), shown in Tab. 7 and Fig. 5. According to the results of closeness coefficients, as shown in Tab. 7, the ranking order of each secure alternatives is: A7 > A1 > A4 > A2 > A3 > A5 > A6. Thus, A7 alternative is closest to the FPIS & farthest from the FNIS.
Table 2: Fuzzy aggregated pair wise matrix
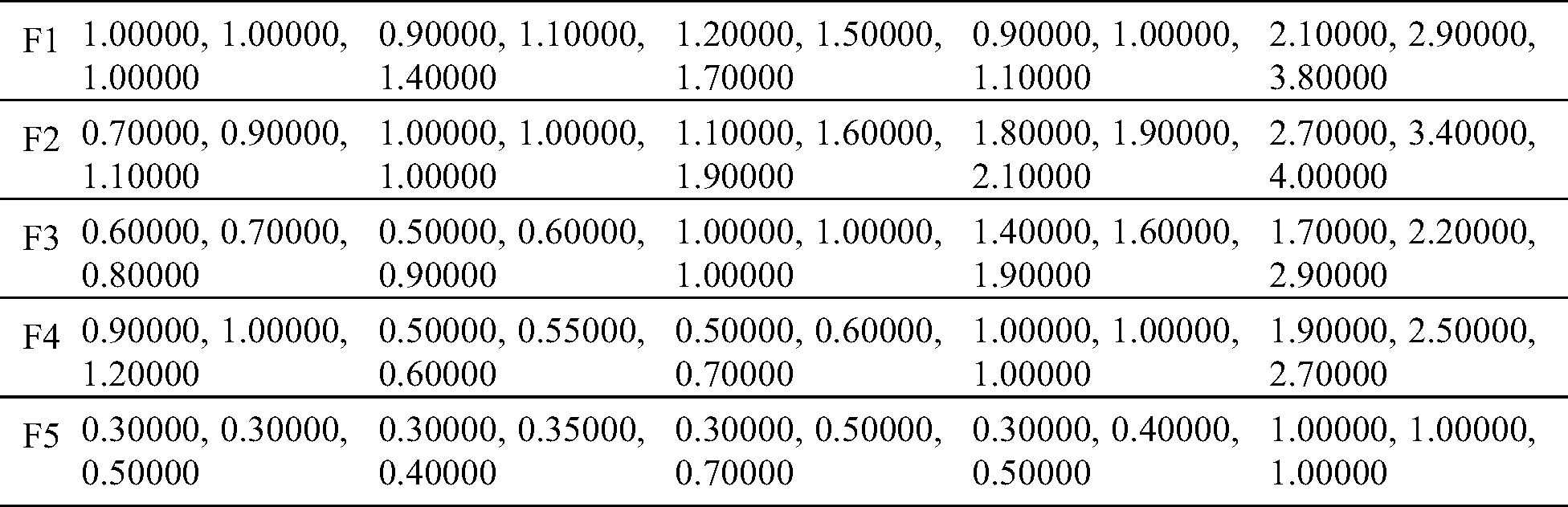
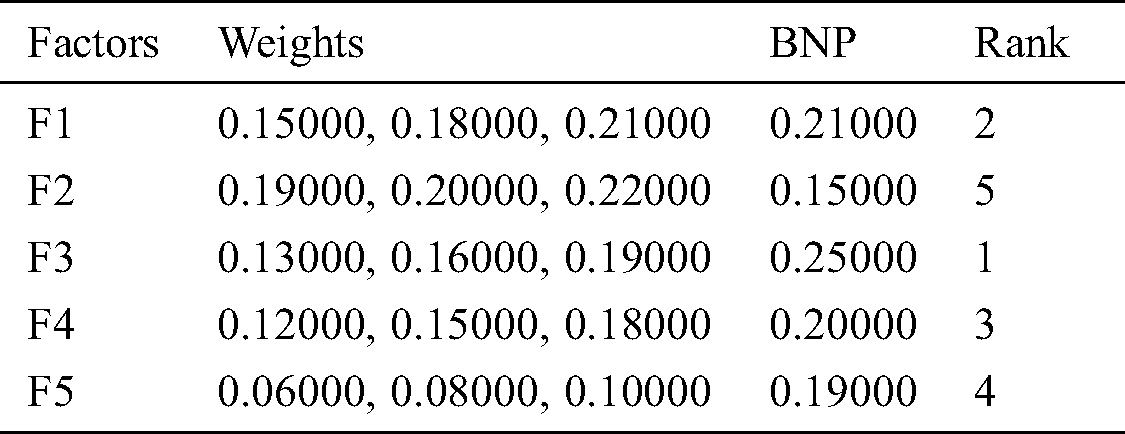
Table 4: Subjective cognition results of the evaluators in linguistic terms

Table 5: The normalized fuzzy-decision matrix

Table 6: The weighted normalized fuzzy-decision matrix

Table 7: Closeness coefficients to the aspired level among the different alternatives
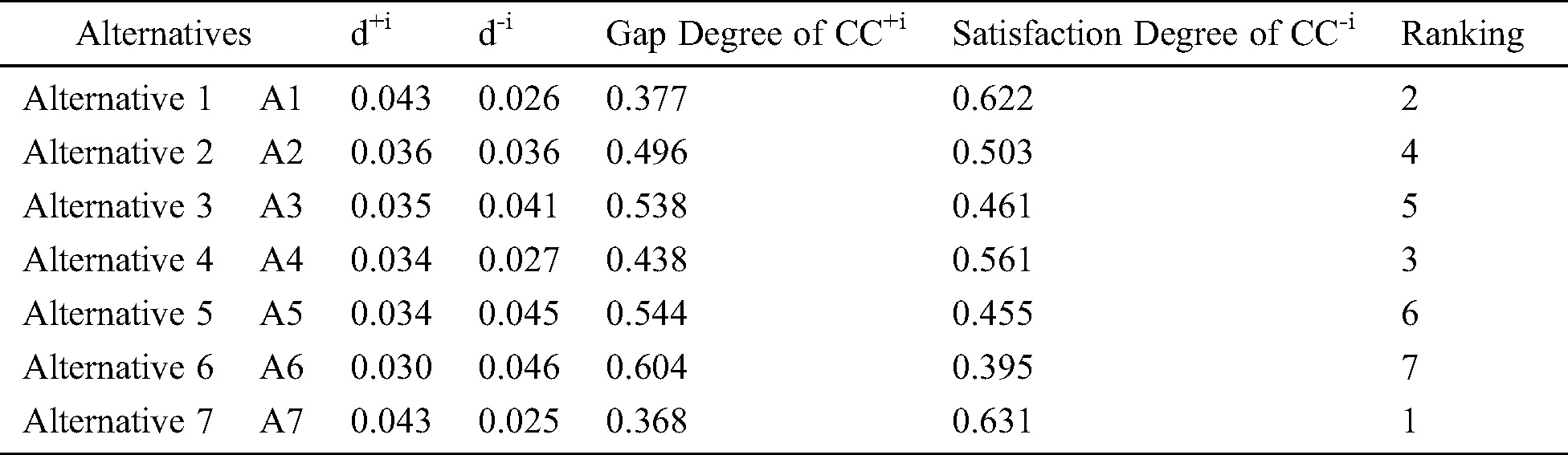
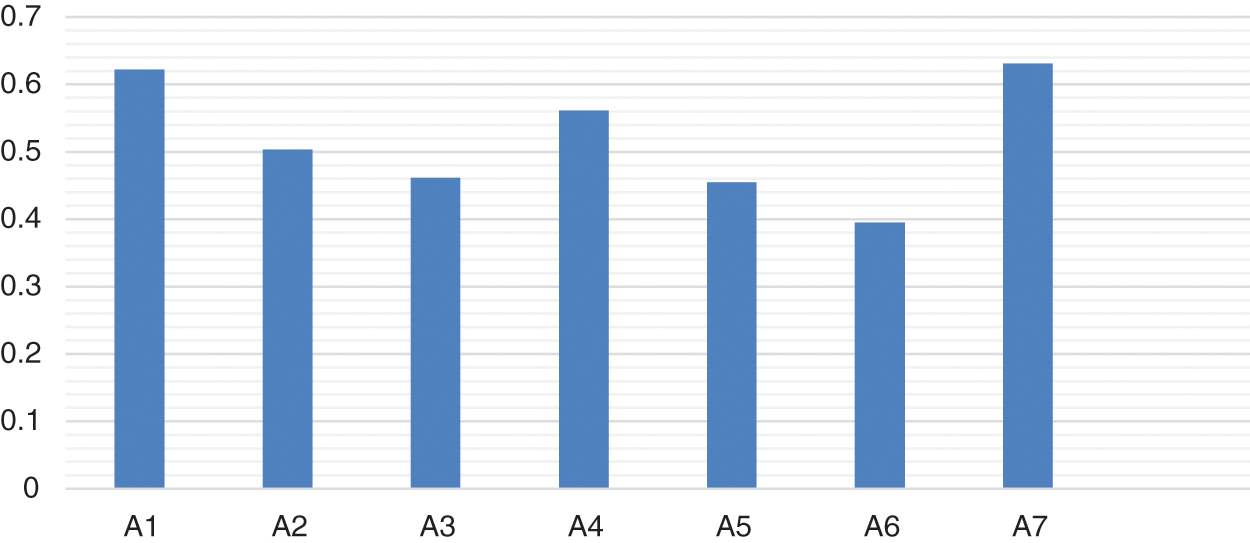
Figure 5: Graphical representation of closeness coefficients
Security is an essential facet for all services. Security is also essential in the consultancy services for better results. It is imperative for the consultants to ensure that the tools and techniques chosen by them are effective for delivering solutions without compromising the security of the tool used and protecting the integrity of the clients’ data as well. Consultants gather information from the client and extract useful information. After the consultants apply the tools and techniques on the filtered information, the consultants must check the impact of tools and techniques for better results. However, selecting the tools and techniques that would also meet the requisites for the various processes in the consultancy services is a crucial task. If a wrong and unsecured tool and technique is applied on the data, then the outcomes will also be flawed. Various tools and techniques are available for best results. In this study, we have prioritized the techniques according to their security levels. In our study, we found that A7 is the more secure alternative for solving of the client’s problem. Consultants can use our framework for the selecting the most efficacious tool.
Achieving customer satisfaction and protecting the security of the client’s information is the first priority for any consultant. For eliciting the best solutions for a given problem, the consultants apply the tools and techniques on the data. In this context, selection of the most conversant tool that is need-specific as well as secure becomes a necessity. To resolve this issue, we have used fuzzy AHP-TOPSIS in this study for the selection of secure tools and techniques. The findings of our study prove that fuzzy AHP-TOPSIS is the most accurate methodology for ranking the tools and techniques in the order of their satisfaction degrees and weights. According to the results of the closeness coefficients, the ranking order of the security of each alternative is: A7 > A1 > A4 > A2 > A3 > A5 > A6. The study concludes that the most secure alternative is A7. Moreover, the quantitative and systematic analysis done in this study is thorough, accurate and conclusive. Hence, the proposed framework is a corroborative reference that will aid in all types of consultancy services in choosing the most secure tool and technique for achieving the desired results.
Acknowledgement: This research was supported by Taif University Researchers Supporting Project number (TURSP-2020/254), Taif University, Taif, Saudi Arabia.
Funding Statement: Funding for this study was received from the Taif University Researchers Supporting Projects at Taif University, Kingdom of Saudi Arabia under Grant No. TURSP-2020/254.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
1. S. Mosonyi, E. L. Empson and J. P. Gond. (2020). “Management consulting: Towards an integrative framework of knowledge, identity, and power,” International Journal of Management Reviews, vol. 22, no. 5, pp. 120–149. [Google Scholar]
2. L. Zeenny, What is consultancy. Consultancy.uk, United Kingdom, 2020. [Online]. Available: https://www.consulting.com/what-is-consulting-definition [Google Scholar]
3. Paulus P. B. and Brown V. R. (2007). “Toward more creative and innovative group idea generation: A cognitive-social-motivational perspective of brainstorming,” Social and Personality Psychology Compass, vol. 1, no. 5, pp. 248–265. [Google Scholar]
4. X. Zhang. (2017). “Knowledge management system use and job performance: A multilevel contingency model,” MIS Quarterly, vol. 41, no. 6, pp. 811–840. [Google Scholar]
5. N. Andler. (2016). Tools for project management, workshops, and consulting: A must have compendium of essential tools and techniques. Public is Erlangen, Paris, France: John Wiley & Sons, . [Online]. Available: https://books.google.co.in/books/about/Tools_for_Project_Management_Workshops_a.html?id=30X7GWXVYF8C&redir_esc=y [Google Scholar]
6. A. Attar. (2020). “Tools and techniques for effective consulting,” Chartered Management Institute, vol. 1, no. 5, pp. 1–11. [Google Scholar]
7. A. Deshmukh. (2020). Must know tools & Techniques in a business consulting world. India: Insights Success, . [Online]. Available: https://www.insightssuccess.in/must-know-tools-techniques-in-a-business-consulting-world/ [Google Scholar]
8. Harvard Professional Development Team. (2020). 6 tools every business consultant should know. Massachusetts: Harvard Division of Continuing Education, . [Online]. Available: https://blog.dce.harvard.edu/professional-development/6-tools-every-business-consultant-should-know [Google Scholar]
9. J. Y. Chen and Y. T. E. Yu. (2019). “Workshop: Team-based learning (TBLA structured approach to help medical students to learn problem-solving in family medicine,” in Proc. WONCA Asia Pacific Regional Conference, Kyoto, Japan, pp. 54–61, . [Online]. Available: http://hub.hku.hk/handle/10722/277391 [Google Scholar]
10. T. L. Saaty, Decision making with dependence and feedback: The analytic network process. New York, USA: New York Public Library, RWS Publications, 1996. [Online]. Available: https://books.google.co.in/books/about/Decision_Making_with_Dependence_and_Feed.html?id=MGpaAAAAYAAJ [Google Scholar]
11. O. S. Vaidya and S. Kumar. (2006). “Analytic hierarchy process: An overview of applications,” European Journal of Operational Research, vol. 169, no. 5, pp. 1–29. [Google Scholar]
12. P. J. M. Vanlaarhoven and W. A. Pedrcyz. (1983). “Fuzzy extension of Saaty’s priority theory,” Fuzzy Sets Systems, vol. 11, no. 11, pp. 229–241. [Google Scholar]
13. M. Moayeri, A. Shahvarani, M. Behzadi and F. H. Lotfi. (2015). “Comparison of fuzzy AHP and fuzzy TOPSIS methods for math teacher’s selection,” Indian Journal of Science and Technology, vol. 8, no. 10, pp. 174–185. [Google Scholar]
14. K. Sahu and R. K. Srivastava. (2018). “Soft computing approach for prediction of software reliability,” ICIC Express Letters, vol. 12, no. 12, pp. 1213–1222. [Google Scholar]
15. K. Sahu and R. K. Srivastava. (2020). “Needs and importance of reliability prediction: An industrial perspective,” Information Sciences Letters, vol. 9, no. 1, pp. 33–37. [Google Scholar]
16. K. Sahu and R. K. Srivastava. (2019). “Revisiting software reliability,” Advances in Intelligent Systems and Computing, vol. 802, pp. 221–235. [Google Scholar]
17. A. Abdullah, A. Attaallah, M. Ahmad, A. Agrawal, R.Kumar et al. (2020). , “A fuzzy multi-objective covering-based security quantification model for mitigating risk of web based medical image processing system,” International Journal of Advanced Computer Science and Applications, vol. 11, no. 1, pp. 481–489. [Google Scholar]
18. A. K. Pandey, A. I. Khan, Y. B. Abushark, M. M. Alam, A. Agrawal et al. (2020). , “Key issues in healthcare data integrity: Analysis and recommendations,” IEEE Access, vol. 8, no. 5, pp. 40612–40628. [Google Scholar]
19. A. Abdullah, A. Attaallah, M. Ahmad, A. Agrawal, R. Kumar et al. (2020). , “A hybrid fuzzy rule-based multi-criteria framework for security assessment of medical device software,” International Journal of Intelligent Engineering and Systems, vol. 31, no. 5, pp. 51–62. [Google Scholar]
Appendix
| Symbol | Description |
|---|---|
| TFN | Triangular Fuzzy Number |
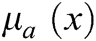 | Membership Function |
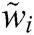 | Fuzzy Weight |
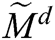 | Fuzzy Pair-Wise Comparison Matrix |
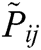 | Average Preference of Decision Makers |
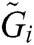 | Fuzzy Geometrical Mean of Factors |
| COA | Center of Area |
| BNP | Best Non-Fuzzy Performance |
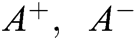 | Fuzzy Positive and Negative Ideal Solution (FPIS, FNIS) |
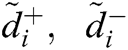 | Distance of Alternatives from FPIS and FNIS |
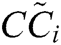 | Closeness Coefficient |
 | This work is licensed under a Creative Commons Attribution 4.0 International License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. |