 Open Access
Open Access
ARTICLE
Anomaly Detection of Controllable Electric Vehicles through Node Equation against Aggregation Attack
State Grid Jiangsu Electric Power Co., Ltd. Research Institute, State Grid Corporation of China, Nanjing, 211100, China
* Corresponding Author: Jing Guo. Email:
(This article belongs to the Special Issue: Best Practices for Smart Grid SCADA Security Systems Using Artificial Intelligence (AI) Models)
Computers, Materials & Continua 2025, 82(1), 427-442. https://doi.org/10.32604/cmc.2024.057045
Received 06 August 2024; Accepted 11 October 2024; Issue published 03 January 2025
Abstract
The rapid proliferation of electric vehicle (EV) charging infrastructure introduces critical cybersecurity vulnerabilities to power grids system. This study presents an innovative anomaly detection framework for EV charging stations, addressing the unique challenges posed by third-party aggregation platforms. Our approach integrates node equations-based on the parameter identification with a novel deep learning model, xDeepCIN, to detect abnormal data reporting indicative of aggregation attacks. We employ a graph-theoretic approach to model EV charging networks and utilize Markov Chain Monte Carlo techniques for accurate parameter estimation. The xDeepCIN model, incorporating a Compressed Interaction Network, has the ability to capture complex feature interactions in sparse, high-dimensional charging data. Experimental results on both proprietary and public datasets demonstrate significant improvements in anomaly detection performance, with F1-scores increasing by up to 32.3% for specific anomaly types compared to traditional methods, such as wide & deep and DeepFM (Factorization-Machine). Our framework exhibits robust scalability, effectively handling networks ranging from 8 to 85 charging points. Furthermore, we achieve real-time monitoring capabilities, with parameter identification completing within seconds for networks up to 1000 nodes. This research contributes to enhancing the security and reliability of renewable energy systems against evolving cyber threats, offering a comprehensive solution for safeguarding the rapidly expanding EV charging infrastructure.Keywords
Glossary/Nomenclature/Abbreviations
| EV | Electric Vehicle |
| Agg-plat | Aggregation platform |
| MCMC | Markov Chain Monte Carlo |
| CIN | Compressed Interaction Network |
The global energy sector is experiencing a significant shift, propelled by the increasing adoption of renewable energy sources in industrial development [1]. Electric vehicles (EVs) play a pivotal role in this transformation, with their sales growth paralleling the expansion of the lithium battery market [2,3]. The rapid increase in EV adoption has spurred substantial growth in the charging service market. In China, for instance, public charging consumption is expected to surpass 338 billion kilowatt-hours by 2030 [4,5]. The charging infrastructure has expanded rapidly, with the recent addition of millions of new charging units [6,7]. Government policies have supported this growth, leading to the proliferation of third-party Agg-plat serving over 87% of EV users [8,9]. The rapid proliferation of EV charging infrastructure poses significant challenges to power grid operations. The intermittent and high-power nature of EV charging can lead to voltage fluctuations, harmonic distortions, and potential overloading of distribution transformers. Studies have shown that uncoordinated EV charging can increase peak load by up to 30%, potentially compromising grid stability and power quality. Moreover, the geographic concentration of charging stations in urban areas may exacerbate local grid congestion, necessitating costly infrastructure upgrades.
Although these platforms improve user experience through wireless technologies, they simultaneously introduce critical vulnerabilities to the power grid [10,11]. The rapid market expansion, coupled with inadequate security measures, has left these platforms susceptible to aggregation attacks [12], such as: 1) unusual power consumption patterns; 2) inconsistencies between reported and actual charging states; 3) Unexpected changes in charging duration or frequency. These malicious activities can exploit vulnerabilities in terminal devices, potentially leading to power anomalies, voltage fluctuations, and grid stability threats [13]. Consequently, the development of robust anomaly detection mechanisms for third-party Agg-plat is critical [14]. Beyond cybersecurity concerns, these Agg-plat also impact grid stability and power quality. Their ability to control large numbers of charging stations simultaneously can lead to sudden load changes, potentially triggering frequency deviations and voltage sags. Furthermore, the complex interactions between multiple aggregators and the grid can introduce unforeseen dynamics, complicating traditional power system control and optimization strategies. The primary purposes of anomaly detection for EV charging stations are multifaceted:
1. Cybersecurity: To protect against malicious attacks that could compromise the integrity of the charging infrastructure or the power grid [15].
2. Operational Efficiency: To identify malfunctioning equipment or inefficient charging patterns that could lead to increased operational costs [16].
3. Grid Stability: To detect unusual charging behaviors that might destabilize the local power distribution network [17].
These motivations are increasingly critical as the EV charging infrastructure expands and becomes more integrated with smart grid technologies.
Recent studies have investigated diverse methods to tackle this challenge, encompassing both unsupervised and supervised learning approaches. Mestav et al. introduced a GAN-based framework for detecting anomalies in power system measurements [18]. Miraftabzadeh et al. developed an advanced density-based spatial clustering algorithm for power grid anomaly detection [19]. Supervised anomaly detection techniques have gained traction due to their ability to leverage labeled datasets [20]. Haldorai et al. proposed an ensemble framework combining multiple machine learning algorithms for detecting anomalies in EV charging data [21]. Tang et al. introduced a deep neural network architecture incorporating attention mechanisms [22]. Deep cross-network models have shown promise in capturing complex feature interactions in sparse, high-dimensional data. Badr et al. adapted the Wide & Deep architecture for anomaly detection in smart meter data [23], while Wu et al. utilized a modified DeepFM architecture to detect fraudulent charging behaviors. Considering these challenges, there is a pressing need for advanced monitoring and control systems that can ensure grid stability and power quality while accommodating the growing EV charging load. Our proposed anomaly detection framework not only addresses cybersecurity threats but also contributes to improved grid management. By accurately identifying abnormal charging behaviors, this approach enables system operators to swiftly respond to potential disturbances, optimize power flow, and maintain grid stability under varying EV charging scenarios.
This study introduces an innovative anomaly detection framework for EV charging stations, addressing the critical security challenges faced by third-party Agg-plat. Our approach integrates node equation-based parameter identification with a novel deep learning model, xDeepCIN, to detect abnormal data reporting indicative of aggregation attacks. The xDeepCIN model, a deep cross-network architecture incorporating a Compressed Interaction Network, is designed to capture complex feature interactions in sparse, high-dimensional data typical of charging infrastructure. Our research contributes to ensuring the security and reliability of renewable energy systems against evolving cyber threats. By addressing the unique challenges of third-party charging platforms, this framework represents a substantial advancement in cybersecurity for smart vehicle ecosystems, offering enhanced protection for the rapidly expanding EV charging infrastructure. By integrating node equation-based parameter identification with deep learning techniques, our framework provides a comprehensive solution for enhancing both the security and operational efficiency of EV charging infrastructure. This approach not only detects potential cyber threats but also offers valuable insights for grid operators, enabling more effective load balancing, improved power quality management, and optimized utilization of existing grid infrastructure in the face of increasing EV adoption. In conclusion, our study makes several key contributions to the field:
1. A graph-theoretic approach to rigorously model EV charging networks;
2. A MCMC method to accurately estimate charging terminal parameters from aggregation platform data;
3. A novel deep cross-network architecture, xDeepCIN, incorporating a Compressed Interaction Network, designed to capture complex feature interactions in sparse, high-dimensional charging data.
4. Demonstrating the effectiveness of our framework through extensive experiments on both proprietary and public datasets, showing significant improvements in anomaly detection performance compared to existing methods.
To rigorously model the EV charging network within the power distribution system, we employ a graph-theoretic approach. Let G = (V, E) represent the distribution network, where V is the set of nodes (buses) and E is the set of edges (lines). Each EV charging station is modeled as a node vi ∈ V with time-varying power injection Pi(t) + jQi(t). The power flow equations for the network can be expressed as:
where
For the EV charging stations, we model the power injection as a function of the charging rate
where f(·) is a nonlinear function capturing the characteristics of the charging process.
2.2 Node Equation in Distributed Charging Terminal
Fig. 1a illustrates the architecture of a typical charging distributed terminal, comprising both the power system and the third-party Agg-plat. Solid black lines show device data flow within the power system, while dashed green lines represent data flow in third-party platforms like Tesla Superchargers. Data transmission occurs wirelessly via 4G/5G networks, which, despite their efficiency, introduce vulnerabilities to aggregation attacks (illustrated by red dotted lines). To improve anomaly detection in Agg-plat, we employed node voltage equations to inversely solve terminal device parameters. Based on the node equation theory, all topology’s structures in the power distribution network (PDN) can be simplified as three typical forms, Γ-type, T-type, and

Figure 1: The diagram of the Agg-plat with charging terminal. (a) The frame diagram of charging distributed terminal; (b) The frame diagram of charging distributed terminal
Fig. 1b depicts real-time measurements of active power Pd, reactive power Qd, and voltage Ud at the transformer’s high-voltage side. Other critical parameters, including transformer and line characteristics, are harder to detect but essential for PDN analysis. We adopted a Γ-type equivalent circuit model to balance computational efficiency with accuracy. This simplification assumes negligible shunt capacitance, which is generally valid for short distribution lines. However, this assumption may introduce errors for longer lines or in networks with significant capacitive effects. The balanced three-phase system assumption satisfies the most of the application occasions and simplifies calculations and is often reasonable for well-designed distribution networks. However, this may not hold in some special scenarios, particularly in networks with significant single-phase loads or unbalanced conditions. These parameters follow a specific mathematical relationship, crucial for understanding network behavior as Eq. (3).
where
At bus c, the voltage Uc, longitudinal value
Based on the Eqs. (1) to (5), the voltage at bus c can be regarded as the objective minimal function,
2.3 Parameter Identification of Charging Devices
We utilize Markov Chain Monte Carlo (MCMC) techniques to determine charging terminal line and equipment parameters from aggregation platform data [24,25]. MCMC updates the Bayesian posterior probability distribution using Markov process transition probabilities. It then generates random values for power distribution network parameters, stabilizing the Markov process. This process postulates that an object’s state is solely dependent on its immediately preceding state, as illustrated in Eq. (5). This approach enables efficient parameter space exploration and robust identification within the search space.
In this model,
where the
where initial distributions include short-circuit loss (pk), voltage percentage (uk%), and no-load current percentage (ik%). These distributions account for the nonlinear nature of the probability space. Monte Carlo simulations generate parameter values aligned with these initial distributions, which are then combined with actual feeder line data for power flow calculations. The resulting loss function informs a Markov chain process that updates the parameter distributions. This iterative process continues, with Monte Carlo methods generating new parameter values based on updated distributions, followed by power flow calculations to determine low-voltage side voltages and new loss functions.
The convergence of our MCMC-based parameter estimation method can be analyzed using the theory of Markov chain convergence to stationary distributions. Let π be the target posterior distribution of the parameters θ. We prove that our Markov chain
where
2.4 Deep Cross-Network Equipped with a CIN
We developed an advanced CIN architecture to improve the detection of complex feature interactions while preserving vector-level processing efficiency. This method structures input features and hidden layers as matrices, X0 and Xk, where

Figure 2: The basic structure of CIN
For the kth layer, the work flow is expressed as:
where

Figure 3: The work-flow of CIN. (a) An example of a tensor; (b) The calculation process of a tensor
Our model effectively processes high-dimensional, sparse data typical of EV charging systems, enhancing anomaly detection accuracy. The CIN offers key advantages: increasing depth of feature interactions with network layers, capturing multi-order interaction patterns through pooling connections, and maintaining layer-specific parameters with fixed input X0. By integrating CIN with linear regression (LR) and fully connected neural networks, we developed xDeepCIN, a comprehensive model leveraging both explicit and implicit high-order feature interactions. In Fig. 4, this hybrid approach combines memorization and generalization strengths, enabling more nuanced anomaly detection in complex EV charging data.

Figure 4: The structure of xDeepCIN
The xDeepCIN model demonstrates superior performance compared to traditional methods for several reasons: 1) Feature Interaction Modeling: xDeepCIN’s CIN component effectively captures complex, high-order feature interactions. This is particularly beneficial for EV charging data, where relationships between features are often non-linear and interdependent; 2) Hybrid Architecture: By combining linear and deep components, xDeepCIN leverages both memorization and generalization capabilities. This allows it to capture both low-order and high-order feature interactions effectively; 3) Adaptive Feature Learning: The model’s deep neural network components enable adaptive feature learning, allowing it to automatically extract relevant features from high-dimensional, sparse data. The xDeepCIN enhances capturing intricate relationships in sparse, high-dimensional EV charging datasets. This improved feature interaction modeling enables more accurate identification of subtle anomalies, potentially indicating security threats or system malfunctions.
3.1 Results and Discussions of MCMC for Charging Node Equation
To reduce result variability, we emphasize parameter standard precision in our analysis. We deem randomness insignificant when parameter updates in subsequent iterations fall below the standard precision threshold. Table 1 displays the static parameters of the standard 10 kV feeder network used in this study.

To validate the generalizability of our approach, we examined charging pile data collected on 01 January 2024, using a supervisory control system with 15-min sampling intervals. Fig. 5 illustrates: (a) high-voltage side three-phase first section voltage, (b) low-voltage side three-phase voltage, (c) low-voltage side three-phase active power, and (d) low-voltage side three-phase reactive power. This comprehensive dataset al.lows for a thorough evaluation of our method’s performance across various electrical parameters.

Figure 5: The three-phase first section. (a) High voltage side; (b) Low voltage side; (c) Active power; (d) Re-active power
To demonstrate our approach’s generalizability, we analyzed charging pile data from 01 January 2024, collected using a supervisory control system with 15-min sampling intervals. Fig. 5 illustrates three-phase first section: (a) high voltage, (b) low voltage, (c) low-voltage side’s active power, and (d) low-voltage side’s reactive power. This comprehensive dataset al.lows for a thorough evaluation of our method’s performance across various electrical parameters.
Fig. 5a demonstrates that the high-voltage side (UC in Fig. 1b) complies with the three-phase balance principle, satisfying the prerequisites for node equation solving and parameter identification. Fig. 5b–d reveals consistent trends in active power, reactive power, and low-voltage side parameters (Pd, Qd, and Ud in Fig. 1b), validating data stability for identification purposes. Fig. 6 presents the MCMC method’s parameter identification results. It demonstrates remarkable consistency between high-voltage values derived from our MCMC-based real-time identification method (Umcmc) and actual measured high-voltage values (Ustd) across 1000 consecutive 15-min sampling periods.
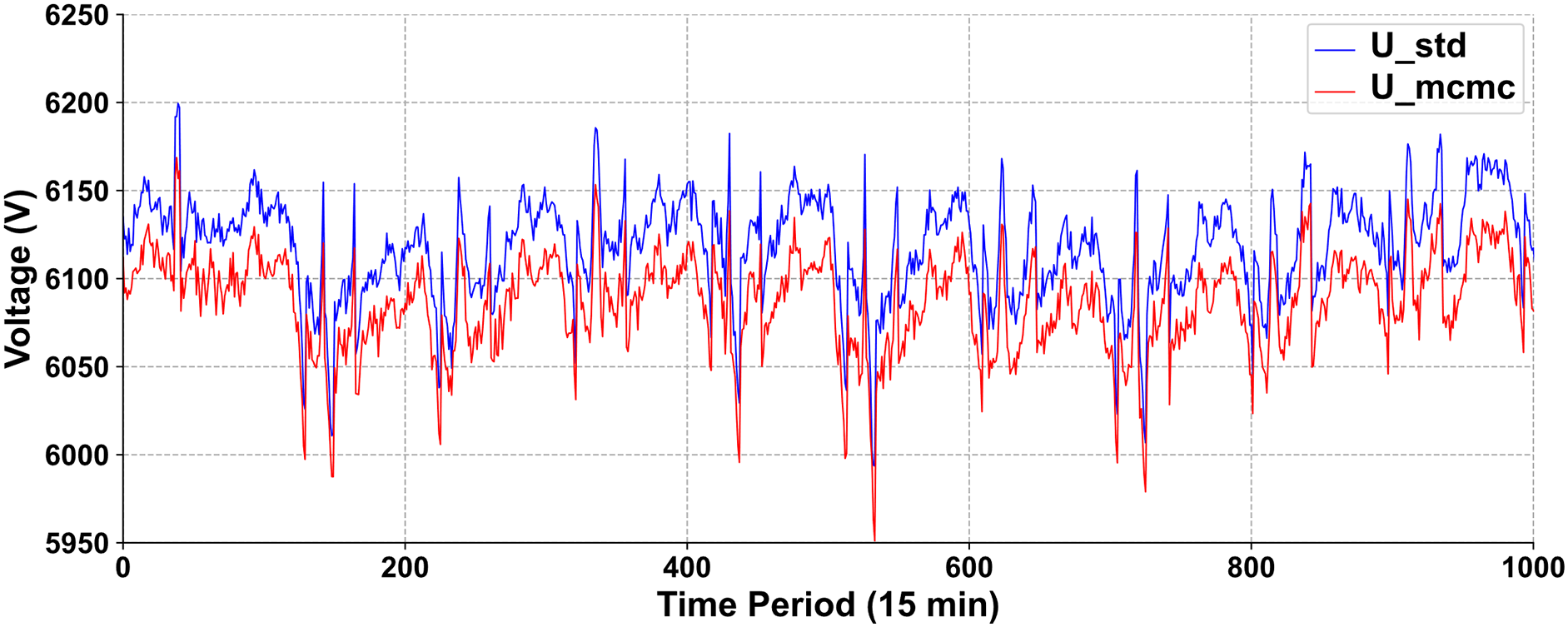
Figure 6: MCMC method’s parameter identification results
The xDeepCIN exhibits high sensitivity to high-voltage fluctuations, confirming its ability to accurately estimate terminal device parameters from aggregation platform data. This responsiveness to real-time variations is crucial, enhancing the model’s capacity for continuous monitoring and rapid detection of potential aggregation attacks. It provides a robust framework for detecting anomalies indicative of malicious activities or system irregularities in EV charging infrastructure by delivering real-time parameter estimations that accurately reflect actual system behavior. The demonstrated accuracy and responsiveness of our MCMC-based parameter identification method underscore its potential as an effective tool for maintaining the security and reliability of charging networks, particularly against evolving threats. Our results demonstrate the effectiveness of the proposed framework under the stated assumptions. Future studies could focus on adapting the model to handle unbalanced systems, incorporating distributed generation effects, and exploring its applicability to different voltage levels and network topologies.
3.2 Results and Discussions of xDeepCIN
The MCMC-based method accurately estimates distributed terminal device parameters through the aggregation platform, improving real-time monitoring and detection of potential aggregation attacks in power generation systems. To evaluate xDeepCIN anomaly detection model, we conducted comprehensive testing using diverse datasets, including our proprietary data and public Adaptive Charging Network (ACN) datasets.
Table 2 provides an overview of the key characteristics of these datasets. Our proprietary dataset represents a large-scale industrial charging environment, featuring high-power DC fast charging stations and vehicle-to-grid (V2G) capabilities. This dataset provides insights into advanced charging scenarios not captured in the public datasets. The ACN datasets, in contrast, represent a range of charging environments, from small office settings to larger mixed-use facilities. Table 3 summarizes the performance metrics.


These results validate the scalability and robustness of our framework in several ways:
1. Scale Adaptability: The model performs well on both small (ACN Office, 8 charging points) and large (Proprietary, 85 charging points) datasets, indicating good scalability.
2. Environment Flexibility: Consistent performance across different charging environments (public, workplace, industrial) suggests the model’s adaptability to various use cases.
3. Feature Handling: The model effectively manages the unique features of each dataset, such as the V2G capabilities in the proprietary data, demonstrating its ability to handle complex, real-world scenarios.
We evaluated xDeepCIN’s performance using representative anomalous data samples, comparing it to two established cross-network models: the first-order Wide and Deep model [26] (WAD) and the second-order DeepFM model [27] (DFM). Table 4 summarizes extensive testing and comparative analysis, providing a quantitative evaluation of xDeepCIN, WAD, and DFM models in detecting anomalies across various charging scenarios. These results offer valuable insights into the models’ relative strengths and performances, highlighting xDeepCIN’s advancements in anomaly detection for EV charging infrastructure.

We deconstructed the xDeepCIN model to evaluate various combinations of the Compressed Interaction Network (CIN) with other modules. Table 5 demonstrates CIN’s significant impact on performance.

The ablation study reveals that the Compressed Interaction Network (CIN) component contributes most significantly to the enhancement of anomaly detection performance. When integrated with Linear Regression (LR), CIN shows an average improvement of 12.7% in AUC and 11.6% in F1-score across all datasets. This substantial improvement can be attributed to CIN’s ability to capture complex, high-order feature interactions efficiently. To further illustrate the impact of CIN, we analyzed its contribution to detecting different types of anomalies in Table 6, the metric is F1-score.

Table 6 presents a more focused view of CIN’s contribution to anomaly detection across different types of anomalies, using F1-score as the primary metric. F1-score is particularly suitable for evaluating anomaly detection performance in imbalanced datasets, as it provides a balanced measure of precision and recall. The consistent and substantial improvement in F1-scores across all anomaly types underscores CIN’s versatility and effectiveness. By significantly boosting F1-scores, CIN demonstrates its value in creating a more robust and reliable anomaly detection system, capable of handling the diverse challenges presented by modern EV charging infrastructure. The balanced nature of the F1-score ensures that these improvements reflect both a reduction in false positives (improved precision) and false negatives (improved recall), which is crucial for practical application in real-world EV charging systems where both missed anomalies and false alarms can have significant operational and security implications. It should be noted that the data types and distribution characteristics of charging piles in different places are different. If the topology or data type can be approximateely simplied as a two-dimensional matrix, the convolutional neural network and transformer also can be added to the CIN structure [28].
The xDeepCIN model, incorporating all components, achieved the highest performance, validating our approach’s efficacy in anomaly detection for EV charging systems. While implementing the competing models, we encountered several challenges:
1. WAD Model: This model’s performance was limited by its inability to capture complex, high-order feature interactions effectively. Its linear component primarily captures low-order interactions, which may not fully represent the complexity of EV charging anomalies;
2. DFM Model: While DeepFM improves upon WAD by introducing factorization machines for second-order feature interactions, it still struggles with higher-order interactions. This limitation becomes apparent in complex anomaly detection scenarios.
3.3 Computational Performance and Scalability
The real-time applicability of our framework, particularly the MCMC-based parameter identification process, is a crucial aspect of its practical implementation. To evaluate its computational performance and scalability, we conducted a series of experiments on networks of varying sizes and complexities ((Intel Core i7-10700K, 32 GB RAM, NVIDIA 4080 Super). Table 7 summarizes the average processing times for different network sizes.

The MCMC parameter identification process, while more computationally intensive, still operates within acceptable timeframes for real-time monitoring. For networks up to 1000 nodes, the process completes within seconds, allowing for frequent updates of network parameters. This result reveals that the MCMC parameter identification time scales approximately linearly with the number of nodes, while the xDeepCIN anomaly detection time exhibits sub-linear scaling.
This research introduces an innovative anomaly detection method for EV charging stations by integrating node equation-based parameter identification with the xDeepCIN deep learning model. By leveraging MCMC for parameter space identification, our approach demonstrates superior performance in detecting subtle anomalies compared to traditional methods. Experimental results validate the framework’s effectiveness, with xDeepCIN showing significant improvements in AUC and F1-score across our collected dataset and three public adaptive charging network datasets. Our results underscore the potential of integrating node equation-based parameter estimation with advanced deep learning architectures to bolster the security and reliability of EV charging infrastructure. Although our findings are promising, additional research is necessary to investigate the scalability and generalizability of our approach across diverse charging environments and various cyber-attack scenarios. Future work should focus on integrating our framework with real-time monitoring systems and developing proactive defense mechanisms.
This study contributes to advancing cybersecurity in smart vehicle ecosystems by addressing unique challenges faced by third-party charging aggregation platforms. Ongoing research and cross-disciplinary collaboration are essential to safeguard the security and reliability of the rapidly expanding EV charging infrastructure against emerging cyber threats.
Acknowledgement: The authors would like to express our sincere gratitude to Chuanjun Wang for his invaluable assistance with statistical analysis.
Funding Statement: This work was supported by Jiangsu Provincial Science and Technology Project, grant number J2023124. Jing Guo received this grant, the URLs of sponsors’ website is https://kxjst.jiangsu.gov.cn/ (accessed on 06 June 2024).
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Jing Guo, Ziying Wang; data collection: Jing Guo, Yajuan Guo; analysis and interpretation of results: Jing Guo, Ziying Wang, Yajuan Guo; draft manuscript preparation: Jing Guo, Haitao Jiang. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data that support the findings of this study are available from the corresponding author Jing Guo upon reasonable request.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. L. Zhang and T. Ponomarenko, “Directions for sustainable development of china’s coal industry in the post-epidemic era,” Sustainability, vol. 15, no. 8, 2023, Art. no. 6518. doi: 10.3390/su15086518. [Google Scholar] [CrossRef]
2. Y. Y. Zhao et al., “A review on battery market trends, second-life reuse, and recycling,” Sustain. Chem., vol. 2, no. 1, pp. 167–205, 2021. doi: 10.3390/suschem2010011. [Google Scholar] [CrossRef]
3. S. M. Parsa et al., “Lithium-ion battery thermal management via advanced cooling parameters: State-of-the-art review on application of machine learning with exergy, economic and environmental analysis,” J. Taiwan Inst. Chem. Eng., vol. 148, 2023, Art. no. 104854. doi: 10.1016/j.jtice.2023.104854. [Google Scholar] [CrossRef]
4. F. T. Hesary, K. Dong, C. Zhao, and H. Phoumin, “Can financial and economic means accelerate renewable energy growth in the climate change era? The case of China,” Econ. Anal. Policy, vol. 78, no. 10, pp. 730–743, 2023. doi: 10.1016/j.eap.2023.04.013. [Google Scholar] [CrossRef]
5. C. Zhao, K. Dong, Z. Liu, and X. Ma, “Is digital economy an answer to energy trilemma eradication? The case of China,” J. Environ. Manag., vol. 349, no. 2, 2024, Art. no. 119369. doi: 10.1016/j.jenvman.2023.119369. [Google Scholar] [PubMed] [CrossRef]
6. I. Mahmud, M. B. Medha, and M. Hasanuzzaman, “Global challenges of electric vehicle charging systems and its future prospects: A review,” Res. Transport. Business Manag., vol. 49, no. 1, 2023, Art. no. 101011. doi: 10.1016/j.rtbm.2023.101011. [Google Scholar] [CrossRef]
7. P. Alaee, J. Bems, and A. Anvari-Moghaddam, “A review of the latest trends in technical and economic aspects of EV charging management,” Energies, vol. 16, no. 9, 2023, Art. no. 3669. doi: 10.3390/en16093669. [Google Scholar] [CrossRef]
8. A. Unterweger, F. Knirsch, D. Engel, D. Musikhina, A. Alyousef and H. de Meer, “An analysis of privacy preservation in electric vehicle charging,” Energy Inform., vol. 5, no. 3, 2022, Art. no. 2615. doi: 10.1186/s42162-022-00190-y. [Google Scholar] [CrossRef]
9. J. M. Clairand, J. R. García, and C. Alvarez-Bel, “Smart charging for electric vehicle aggregators considering users’ preferences,” IEEE Access, vol. 6, pp. 54624–54635, 2018. doi: 10.1109/ACCESS.2018.2872725. [Google Scholar] [CrossRef]
10. Y. He, C. Zhang, B. Wu, Z. Geng, K. Xiao and H. Li, “A trusted architecture for EV shared charging based on blockchain technology,” High-Confid. Comput., vol. 1, no. 2, 2021, Art. no. 100001. doi: 10.1016/j.hcc.2021.100001. [Google Scholar] [CrossRef]
11. D. Kern and C. Krauß, “Detection of e-mobility-based attacks on the power grid,” presented at the 2023 53rd Annual IEEE/IFIP Int. Conf. Depend. Syst. Netw., Porto, Portugal, Jun. 27–30. doi: 10.1109/DSN58367.2023.00042. [Google Scholar] [CrossRef]
12. A. P. Diaz, E. H. Gerding, and F. McGroarty, “Catching cheats: Detecting strategic manipulation in distributed optimisation of electric vehicle aggregators,” J. Artif. Intell. Res., vol. 67, pp. 437–470, 2020. doi: 10.1613/jair.1.11573. [Google Scholar] [CrossRef]
13. M. Ghafouri et al., “Detection and mitigation of cyber attacks on voltage stability monitoring of smart grids,” IEEE Trans. Smart Grid, vol. 11, no. 6, pp. 5227–5238, 2020. doi: 10.1109/TSG.2020.3004303. [Google Scholar] [CrossRef]
14. M. Keshk, E. Sitnikova, N. Moustafa, J. Hu, and I. Khalil, “An integrated framework for privacy-preserving based anomaly detection for cyber-physical systems,” IEEE Trans. Sustain. Comput., vol. 6, no. 1, pp. 66–79, 2021. doi: 10.1109/TSUSC.2019.2906657. [Google Scholar] [CrossRef]
15. P. R. Badu, B. Palaniswamy, A. G. Reddy, V. Odelu, and H. S. Kim, “A survey on security challenges and protocols of electric vehicle dynamic charging system,” Secur. Privacy, vol. 5, no. 3, 2022, Art. no. e210. doi: 10.1002/spy2.21. [Google Scholar] [CrossRef]
16. Y. Chen, Y. Zhang, S. Maharjan, M. Alam, and T. Wu, “Deep learning for secure mobile edge computing in cyber-physical transportation systems,” IEEE Network, vol. 33, no. 4, pp. 36–41, 2019. doi: 10.1109/MNET.2019.1800458. [Google Scholar] [CrossRef]
17. A. R. Kizhakkan, A. K. Rathore, and A. Awasthi, “Review of electric vehicle charging station location planning,” in 2019 IEEE Transport. Electrif. Conf., Bengaluru, India, Dec. 17–19, 2019, pp. 1–5. doi: 10.1109/ITEC-India48457.2019.ITECINDIA2019-226. [Google Scholar] [CrossRef]
18. K. R. Mestav, X. Wang, and L. Tong, “A deep learning approach to anomaly sequence detection for high-resolution monitoring of power systems,” IEEE Trans. Power Syst., vol. 38, no. 1, pp. 4–13, 2022. doi: 10.1109/TPWRS.2022.3168529. [Google Scholar] [CrossRef]
19. S. M. Miraftabzadeh, C. G. Colombo, M. Longo, and F. Foiadelli, “K-means and alternative clustering methods in modern power systems,” IEEE Access, vol. 11, pp. 119596–119633, 2023. doi: 10.1109/ACCESS.2023.3327640. [Google Scholar] [CrossRef]
20. Q. Feng, H. Li, Y. Zhou, D. Feng, Y. Wang and Y. Su, “Review of electric vehicles’ charging data anomaly detection based on deep learning,” in 2022 Power System and Green Energy Conf., Shanghai, China, Aug. 25–27, 2022, pp. 337–341. doi: 10.1109/PSGEC54663.2022.9881073. [Google Scholar] [CrossRef]
21. A. Haldorai, R. B.Lincy, S. Murugan, and M. Balakrishnan, “A review on smart charging approaches for electric vehicle,” Artif. Intell. Sustain. Develop., vol. 9, pp. 177–196, 2024. doi: 10.1007/978-3-031-53972-5_9. [Google Scholar] [CrossRef]
22. A. Tang, Y. Jiang, Q. Yu, and Z. Zhang, “A hybrid neural network model with attention mechanism for state of health estimation of lithium-ion batteries,” J. Energ. Storage, vol. 68, no. 4, 2023, Art. no. 107734. doi: 10.1016/j.est.2023.107734. [Google Scholar] [CrossRef]
23. M. M. Badr, M. I. Ibrahem, H. A. Kholidy, M. M. Fouda, and M. Ismail, “Review of the data-driven methods for electricity fraud detection in smart metering systems,” Energies, vol. 16, no. 6, 2023, Art. no. 2852. doi: 10.1016/j.est.2023.107734. [Google Scholar] [CrossRef]
24. A. Bott, T. Janke, and F. Steinke, “Deep learning-enabled MCMC for probabilistic state estimation in district heating grids,” Appl. Energy, vol. 336, no. 9, 2023, Art. no. 120837. doi: 10.1016/j.apenergy.2023.120837. [Google Scholar] [CrossRef]
25. B. Li et al., “A method for parameter identification of distribution network equipment based on sequential model-based optimization,” Int. Trans. Electr. Energy Syst., vol. 2022, no. 1, 2022, Art. no. 9880284. doi: 10.1155/2022/5358965. [Google Scholar] [CrossRef]
26. Z. He et al., “A spatiotemporal deep learning approach for unsupervised anomaly detection in cloud systems,” IEEE Trans. Neural Netw. Learn. Syst., vol. 34, no. 4, pp. 1705–1719, 2020. doi: 10.1109/TNNLS.2020.3027736. [Google Scholar] [PubMed] [CrossRef]
27. Y. Ji and X. Li, “An efficient intrusion detection model based on deepFM,” in 2020 IEEE 4th Inform. Technol. Netw. Electron. Autom. Control Conf. (ITNEC), Chongqing, China, Jun. 12–14, 2020, pp. 778–783. doi: 10.1109/ITNEC48623.2020.9084722. [Google Scholar] [CrossRef]
28. K. Hu, D. Sun, and Y. Zhao, “Enhanced single-frame interferometry via hybrid conv-transformer architecture for ultra-precise phase retrieval,” Opt. Express., vol. 32, no. 17, pp. 30226–30241, 2024. doi: 10.1364/OE.530142. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools