 Open Access
Open Access
ARTICLE
A Verifiable Trust-Based CP-ABE Access Control Scheme for Cloud-Assisted Renewable Energy Systems
1 Department of Control and Computer Engineering, North China Electric Power University, Beijing, 102206, China
2 State Grid Information & Communication Company of Hunan Electric Power Corporation, Changsha, 410118, China
3 State Grid Hunan Electric Power Corporation Chenzhou Power Supply Branch, Chenzhou, 423000, China
* Corresponding Author: Jiyu Zhang. Email:
Computers, Materials & Continua 2025, 82(1), 1211-1232. https://doi.org/10.32604/cmc.2024.055243
Received 21 June 2024; Accepted 28 October 2024; Issue published 03 January 2025
Abstract
Renewable Energy Systems (RES) provide a sustainable solution to climate warming and environmental pollution by enhancing stability and reliability through status acquisition and analysis on cloud platforms and intelligent processing on edge servers (ES). However, securely distributing encrypted data stored in the cloud to terminals that meet decryption requirements has become a prominent research topic. Additionally, managing attributes, including addition, deletion, and modification, is a crucial issue in the access control scheme for RES. To address these security concerns, a trust-based ciphertext-policy attribute-based encryption (CP-ABE) device access control scheme is proposed for RES (TB-CP-ABE). This scheme effectively manages the distribution and control of encrypted data on the cloud through robust attribute key management. By introducing trust management mechanisms and outsourced decryption technology, the ES system can effectively assess and manage the trustworthiness of terminal devices, ensuring that only trusted devices can participate in data exchange and access sensitive information. Besides, the ES system dynamically evaluates trust scores to set decryption trust thresholds, thereby regulating device data access permissions and enhancing the system’s security. To validate the security of the proposed TB-CP-ABE against chosen plaintext attacks, a comprehensive formal security analysis is conducted using the widely accepted random oracle model under the decisional q-Bilinear Diffie-Hellman Exponent (q-BDHE) assumption. Finally, comparative analysis with other schemes demonstrates that the TB-CP-ABE scheme cuts energy/communication costs by 43%, and scales well with rising terminals, maintaining average latency below 50 ms, ensuring real-time service feasibility. The proposed scheme not only provides new insights for the secure management of RES but also lays a foundation for future secure energy solutions.Keywords
Under the pressure of global warming and fossil fuel depletion, the exploration and utilization of renewable energy systems (RES) [1] have emerged as a prominent global hot topic. With the empowerment of Internet of Things (IoT) technology, RES has effectively monitored various power equipment statuses and precise fault localization. Simultaneously, supported by cloud computing technology, they have efficiently handled the storage, in-depth analysis, and management of vast datasets. Post-analysis by the cloud platform, the acquired data serves internal enterprise users or devices, and serves external government and relevant departments, facilitating further processing, analysis, and application.
However, the deficiencies in permission management and configuration of cloud platforms for RES render them susceptible to unauthorized access, thereby heightening the risk of data leakage. Therefore, ensuring data integrity and privacy in the cloud environments, while restricting access solely to authorized users, has emerged as a pressing research focus. Traditional Role-Based Access Control (RBAC) [2] schemes struggle to adapt to dynamic user roles, trust management, and implementing fine-grained data control within cloud environments. In contrast, Attribute-Based Access Control (ABAC) [3], leveraging the capability to determine access permissions based on various attributes such as users, resources, and environmental factors, coupled with the flexibility and adaptability of access policies achieved through logical attribute combinations, have emerged as a pivotal research avenue for addressing data access control challenges in cloud environments. This solution not only enhances the precision and diversity of control but also protects the data privacy of the cloud environment for RES.
In cloud environments, flexible access and diverse control strategies necessitate attribute-based encryption (ABE) for effective rights management in data access control. Sahai and Waters [4] initially introduced ABE, which can be classified into two types based on whether the access structure is related to the key or the ciphertext: key-policy ABE (KP-ABE) [5] and ciphertext-policy ABE (CP-ABE) [6]. KP-ABE is ideal for scenarios with limited users requiring high flexibility. At the same time, CP-ABE is more appropriate for scenarios involving a large user base that necessitates high scalability. Given the diverse terminals connected to cloud platforms, especially in resource-constrained environments, researchers have focused on offloading computational burdens to edge servers (ES) and cloud service providers (CSP). Schemes that enable efficient outsourcing of decryption tasks have been proposed to reduce computational overhead and enhance system scalability.
Moreover, attribute revocation capabilities have been studied to adapt access rights based on terminal properties and dynamic policies. Recent advancements have also emphasized fine-grained access control through attribute weighting and multi-authority attribute policies, facilitating more decentralized and secure access control solutions. However, challenges persist in managing complex access structures, multi-dimensional permissions, user revocation, and trust management for further exploration and innovation. Table 1 lists the limitations of the existing schemes. A more detailed analysis will be undertaken in the Related Work section.
Considering the limitations of current research and the unique security characteristics of RES, the designed CP-ABE scheme must continue the existing solution and be able to outsource the decryption of ES. Furthermore, as the attributes assigned to RES devices fluctuate with factors such as working hours, geographical location, and operational requirements, the scheme must support attribute revocation to delete the expired or inapplicable attribute key and other information from the attribute authority. Finally, RES devices lack comprehensive trust management during data interaction with the cloud platform, and their trustworthiness cannot be adequately assessed solely through static attributes. As ES enacts access control strategies for RES devices, the proposed scheme must empower ES with trust management capabilities, which have not been proposed in current schemes, which would enable ES to assess device trustworthiness based on device properties, and successful decryption numbers, and subsequently regulate data access accordingly.
Given the three aforementioned security properties, the contributions of this paper are fourfold:
1) The proposed trust-based ciphertext-policy attribute-based encryption scheme for RES (TB-CP-ABE) achieves the secure communication of RES devices to the encrypted data on the cloud. The use of one-way cryptographic hash functions and bilinear pairing renders TB-CP-ABE a secure access control scheme.
2) The proposed TB-CP-ABE scheme incorporates an attribute revocation algorithm to revoke expired device attributes. The updated attribute keys are issued from AA to the CSP, ES, and data owner (DO). Furthermore, a trust management mechanism allows the DO to specify the minimum trust level required for accessing data. The ES regulates device data access by decrypting the trust threshold, which enhances the scheme’s security.
3) The widely accepted formal security analysis based on the q-Bilinear Diffie-Hellman Exponent assumption (q-BDHE) validates the proposed scheme’s performance against chosen plaintext attack (CPA) security.
4) Finally, a comprehensive comparative study was conducted to evaluate the proposed TB-CP-ABE, focusing on communication and computation costs. The analysis results reveal that the proposed scheme achieves a superior tradeoff between communication and computation costs compared to other related schemes.
The rest of this paper is organized as follows. Section 2 briefly outlines the related work. The network model, threat model and preliminaries of the proposed TB-CP-ABE are presented in Section 3. Section 4 provides an in-depth and algorithm-wise discussion on the proposed TB-CP-ABE. A formal security analysis is conducted in Section 5. Section 6 undertakes a comparative performance analysis with other related schemes. Conclusions are presented in Section 7.
Given the diverse number and types of terminals connected to the cloud platform for RES, a flexible control strategy is essential. To address this need, this paper will propose a scheme based on CP-ABE to meet the high scalability scenarios of multiple users in cloud environments. This scheme aims to ensure the stability and security of the cloud while accommodating the access requirements of various terminals.
Due to resource constraints arising from application demands and hardware limitations, terminals connected to RES often struggle to perform the basic operation of the ABE scheme, namely the bilinear pairing operation. Meanwhile, the cloud platform of the RES is supported by edge devices with robust data computing and processing capabilities. Consequently, terminals can offload some decryption tasks to edge devices to alleviate their computational burden. Xue et al. [7] introduced an efficient ABAC scheme, which effectively offloads high computational loads to CSP. However, connecting large-scale terminals to CSP in RES and increasing its burden is not a good solution. Zhang et al. [8] proposed a decentralized scheme that uses a version control subprogram to manage the version of each attribute. However, in a distributed environment, the scheme does not use blockchain for trust or reputation management. Building on Zhang’s work, Zhao et al. [9] introduced a data outsourcing access control scheme that offloads operation loads to fog nodes, reducing computational costs. This scheme is suitable for resource-constrained environments but lacks consideration for attribute revocation and device security.
To further improve secure data sharing, Xu et al. [10] developed a data distribution system with cloud-fog-device architecture by delegating the task of identifying data sources to fog nodes. However, it does not propose an algorithm for attribute revocation. In a similar vein, Ge et al. [11] proposed a lightweight CP-ABE scheme based on a trusted billing mechanism. By integrating anonymous authentication and ABAC, this scheme empowers the DO to autonomously determine fine-grained access policies and set the maximum number of accesses for authorized users. Although both schemes effectively outsource high computational loads to CSP, they do not address attribute weighting, resulting in ciphertext being associated solely with attribute-based access policies. Li et al. [12] introduced a weighted access control scheme, wherein the DO assigns weights to attributes to establish a fine-grained access structure. Heavy computational tasks are deferred to the offline stage, resulting in improved weighted access control and increased risk of impersonated terminals.
In contrast, Zhang et al. [13] proposed a secure and lightweight scheme for sharing smart health devices by outsourced verifiable decryption and supporting online/offline encryption and decryption testing. However, the usage of AND gate has brought about complex access structure management. Further exploring this domain, Tao et al. [14] proposed an outsourced attribute encryption scheme called ORR-CP-ABE that allows for reusable decryption results. This system enables outsourcing devices to reuse pre-computed decryption results for subsequent outsourcing requests by transforming keys, thereby reducing the computational burden on the system. Unfortunately, this system does not address trust management and user revocation issues.
Since the properties of terminals in RES may vary due to deployment location, operational duration, and work requirements, the proposed scheme must incorporate property revocation functionality to adapt the access rights of terminals. Xu et al. [15] introduced an efficient and secure ABAC framework, which supports attribute revocation to prevent the extraction of private information through the control matrix. However, due to the lack of outsourced decryption, the terminal computational pressure is heavy. Xiong et al. [16] proposed a signature scheme based on identity. Utilizing a binary tree structure, this scheme ensures secure data communication between data collectors and data analysis systems by achieving attribute revocation. Meanwhile, due to the limited expressive power of binary trees, attribute management and scalability will become very poor. Ma et al. [17] introduced a lightweight, and scalable CP-ABE mechanism, which includes user key revocation, key leakage prevention, and verifiable outsource decryption. However, it relies on a centralized authorization strategy and has complex access structure management.
With the development of blockchain technology and the increasing emphasis on device security, access control schemes based on blockchain have gradually become a research focus. Liu et al. [18] proposed a trading schema using the directed acyclic graph blockchain system based on renewable energy certificates. However, the management authority of the certificate does not belong to the user and IoT devices, so it is not applicable to the context of this article. Feng et al. [19] proposed a policy hiding method integrating CP-ABE and blockchain. The scheme considers trust management of terminals while neglecting attribute revocation, making it inflexible in the IoT environment. Alqbaishi et al. [20] introduced a comprehensive approach that evaluates the requester’s reputation with respect to regulating access requests for IoT resources. However, excessive trust management can affect the real-time performance of services. Wei et al. [21] proposed a trustworthy access control method for 6G-multiaccess edge computing networks. But the solution addresses the issues of data sharing between edge devices, not the data access between users and IoT devices discussed in this article.
Despite extensive researches on access control in RES within edge computing environments, the existing schemes fail to fully balance the trust management of devices with the excessive computing pressure. Moreover, in multi-user collaborative computing environments, the dynamism and randomness of terminal behavior make resource access control complex. Trust management theory and blockchain provide effective solutions to these challenges. However, current blockchain solutions either have high trust management costs or only address the issue of data sharing between devices. Therefore, in order to realize the secure sharing of cloud-based data in edge-computing RES, this paper proposes a flexible access control scheme based on trust management, which comprehensively considers attribute revocation and lightweight computing.
Let
1) Bilinearity: for
2) Non-degeneracy:
3) Computability: for
A secret sharing scheme across a set of parties
1) Each party is represented as a vector over
2) There exists a matrix
Based on the aforementioned description, the linear reconstruction secret sharing scheme can be defined as follows:
Let the access structure
3.3 Decisional q-BDHE Assumption
Based on the system security parameter, the challenger selects two groups
Distinguishing
Definition 1: It’s inferred that the (decisional) q-parallel BDHE assumption holds if no polytime algorithm has a nonnegligible advantage in solving the decisional q-parallel BDHE problem.
The TB-CP-ABE scheme for RES involves five entities: CSP, AA, ES, DO, and DU, each serving specific roles and interactions as described below:
CSP is responsible for storing ciphertexts generated by DO. When ES submits a data access request, CSP validates the access permissions and subsequently delivers the relevant ciphertext to ES.
AA generates the system’s public parameters, initializes attributes, and produces a master secret key and public key. DO utilizes the public key for encryption. Upon receiving a request for key generation, AA provides ES with an outsourcing decryption key.
ES utilizes a trust management model to conduct an in-depth analysis of user behavior data, environmental conditions, and other relevant factors, thereby comprehensively assessing the trustworthiness of the data user (DU). To ensure the security of trust scores and device data during transmission and storage, ES employs advanced encryption technologies, safeguarding trust scores and related data from tampering or leakage during transmission. Additionally, ES uploads ciphertexts to CSP and forwards access requests from DU to AA to obtain secret keys. Upon receiving the secret key, ES decrypts the trust threshold, evaluates DU’s trust value against the specified threshold, partially decrypts CSP-received ciphertext for DU.
DO defines access structures and encrypts plaintext data using these structures and the public key. ES subsequently sends the ciphertext to CSP for storage and processing.
DU represents RES devices with constrained resources. DU forwards access requests to ES to obtain partially decrypted results, which DU further decrypts to access plaintext data.
The established security model, detailed in Reference [22], will be used to prove the security of the scheme, where a malicious adversary, denoted as
1) Initialization:
2) Setup:
3) Phase 1:
4) Challenge:
5) Phase 2: Phase 1 is repeated under the condition that none of the attribute sets adhere to the access structure
6) Guess:
The advantage
Definition 2: A CP-ABE scheme is deemed CPA-secure if no adversary can gain a significant advantage in winning the CPA-CP-ABE game within polynomial time.
Assuming the KGC is a fully trusted entity, it generates the system parameters and securely distributes encryption and decryption keys to other entities through secure channels. The CSP is considered semi-trusted, faithfully executing system operations but potentially capable of launching passive attacks. DUs are untrustworthy and may initiate any type of attack. As receivers, DUs may attempt to decrypt unauthorized ciphertexts. As senders, they might impersonate unauthorized senders by generating messages to others. For simplicity, unauthorized parties refer to colluding entities among CSP, ESs, and DUs who lack valid decryption and encryption keys. Below is a summary of potential attacks in RES system:
Insider Attack: Insider attacks arise when authorized users exploit their legitimate access to circumvent access policies. They may manipulate their attributes, steal decryption keys, or exploit system vulnerabilities to decrypt or modify sensitive data. This unauthorized access undermines system security, necessitating rigorous monitoring, audits, and user training to mitigate risks.
Impersonation Attack: In an impersonation attack, any party can mimic an encryption key with unauthorized attributes or craft ciphertexts by attaching unauthorized sender’s attributes, misleading receivers. Furthermore, having obtained a valid ciphertext, unauthorized parties might attempt to replace or modify the underlying message to impersonate the corresponding sender.
Collusion Attack: Unauthorized parties can collaborate to launch the aforementioned attacks. For instance, they may combine multiple decryption keys to decrypt unauthorized ciphertexts or exchange encryption keys to generate ciphertexts without authorizing the sender’s attributes.
Distributed Denies of Service (DDoS) Attack: DDoS attacks can overwhelm the system by flooding it with requests from multiple sources, exploiting authorized users’ devices or hijacked resources. This overwhelms the servers, degrades performance, and potentially denies legitimate users access to encrypted data and services, disrupting the secure data sharing ecosystem.
The TB-CP-ABE scheme for the edge-computing-assisted REIoT is presented in this section. The TB-CP-ABE scheme includes seven algorithms: Setup, AASetup, Encrypt, KeyGen, ESDec, DUDec, and AttrRevo. At the beginning, KGC runs Setup to select total system parameters, and AA runs AASetup to pick public key and private key. DO is required to run the Encrypt algorithm to prescribe the generation of Linear Secret Sharing Scheme (LSSS) matrix and decryption material, encrypt and upload data to the cloud. When DU intends to download data encrypted by DO, DU can submit a request to AA. Subsequently, AA performs the KeyGen to produce the attribute key tailored to DU’s specific attributes. Then, ES is tasked with running ESDec to decrypt the trust threshold necessary for the plaintext and evaluate whether the DU’s trust level exceeds this threshold. If so, ES proceeds with decrypting part of the encrypted data and transmitting the data to DU. After DU executes DUDec to complete the final decryption, DU obtains the plaintext data. As DU’s attributes may vary based on geographical location, working hours, and security level, this TB-CP-ABE also incorporates AttrRevo algorithm to revoke the expired attributes associated with DU. The notations used in TB-CP-ABE is listed in Table 2 and the overall negotiation process is shown in Fig. 1 and the trust evaluation process is shown in Fig. 2 below.
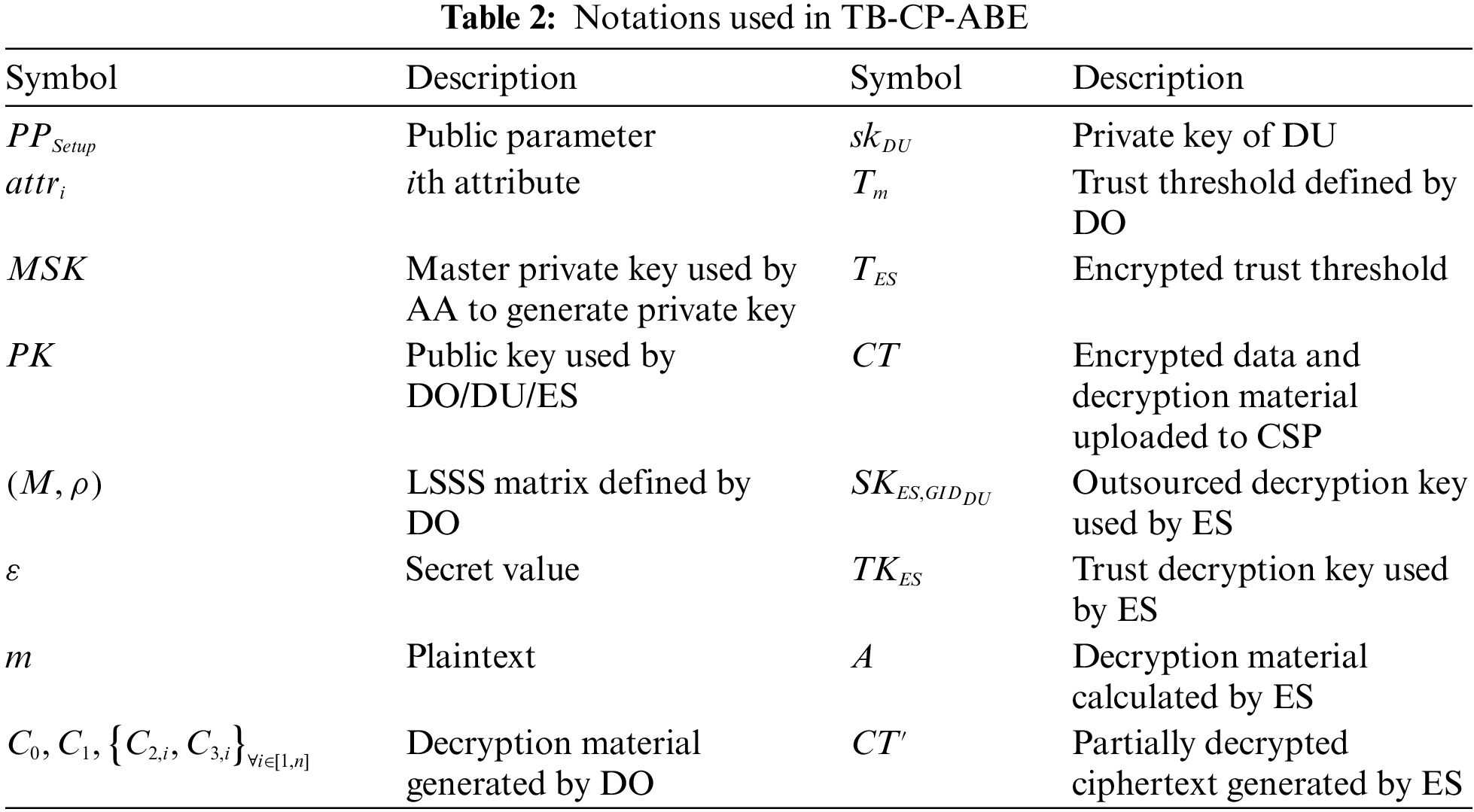
Figure 1: Access control phase in the proposed TB-CP-ABE
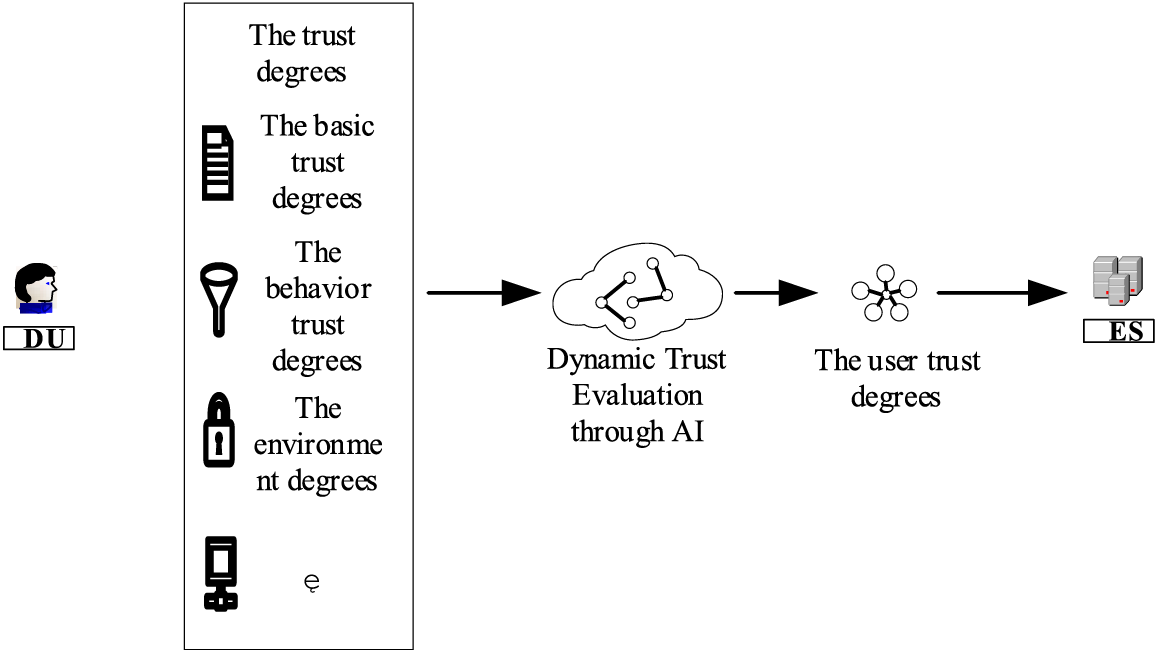
Figure 2: The trust evaluation process in the proposed TB-CP-ABE
In the Setup phase, the system initializes the essential parameters required for encryption and decryption. Security parameter
In the AASetup phase, the attribute field
In the Encrypt phase, DO runs the algorithm to encrypt the plaintext
In the KeyGen phase, the attributes list from
In the ESDec phase, the public parameters
As ES gathers data including DU’s application resource success rates, attribute details, and attribute update frequency to gauge DU’s trustworthiness, it can compare DU’s trust level with the trust threshold necessary for accessing the data. If DU’s trust level fails to meet the specified threshold, ES will decline the delivery of encrypted packets to DU. Otherwise, ES will assist DU by decrypting a portion of the ciphertext to alleviate the decryption burden on DU and send
DU only requires basic operations to decrypt the plaintext
Due to the variability of DU’s attributes, influenced by factors such as geographical location and security level, the scheme needs to support for specific attribute revocation. The output of this algorithm is
Then, AA regenerates outsourced decryption key
Finally, AA updates decryption material
After updating the three parameters above, the specific attribute is revoked.
Theorem 1: Assuming the decisional q-BDHE assumption is valid, it follows that no adversary can undermine the proposed scheme within probabilistic polynomial-time when confronted with the challenge involving a specified access structure
Proof: Assume the existence of an adversary
1) Initialization: The challenger
2) Setup: The challenger
For
1) If
2) If
For
3) If
4) If
For
3) Phase 1:
The adversary
For
For
(1) If
(2) If
(3) If
The challenger
4) Challenge:
5) Phase 2: This phase resembles Phase 1.
6) Guess: For
Consequently, the challenger
Upon the above proof, it becomes evident that if
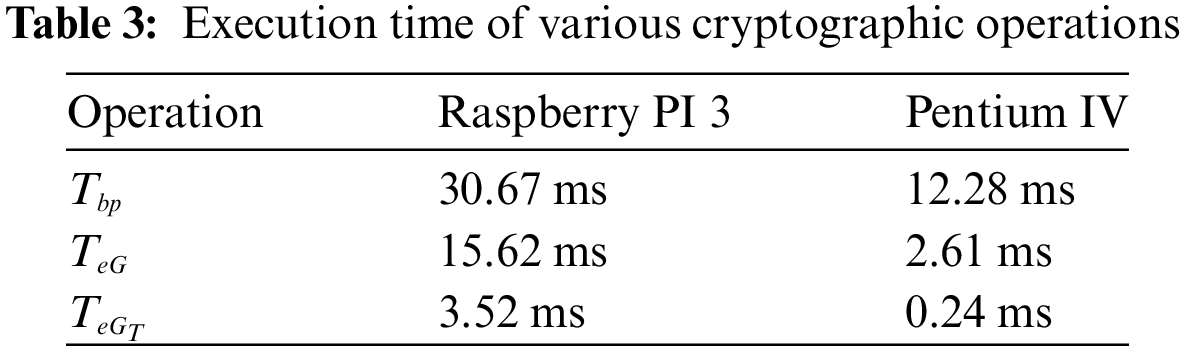
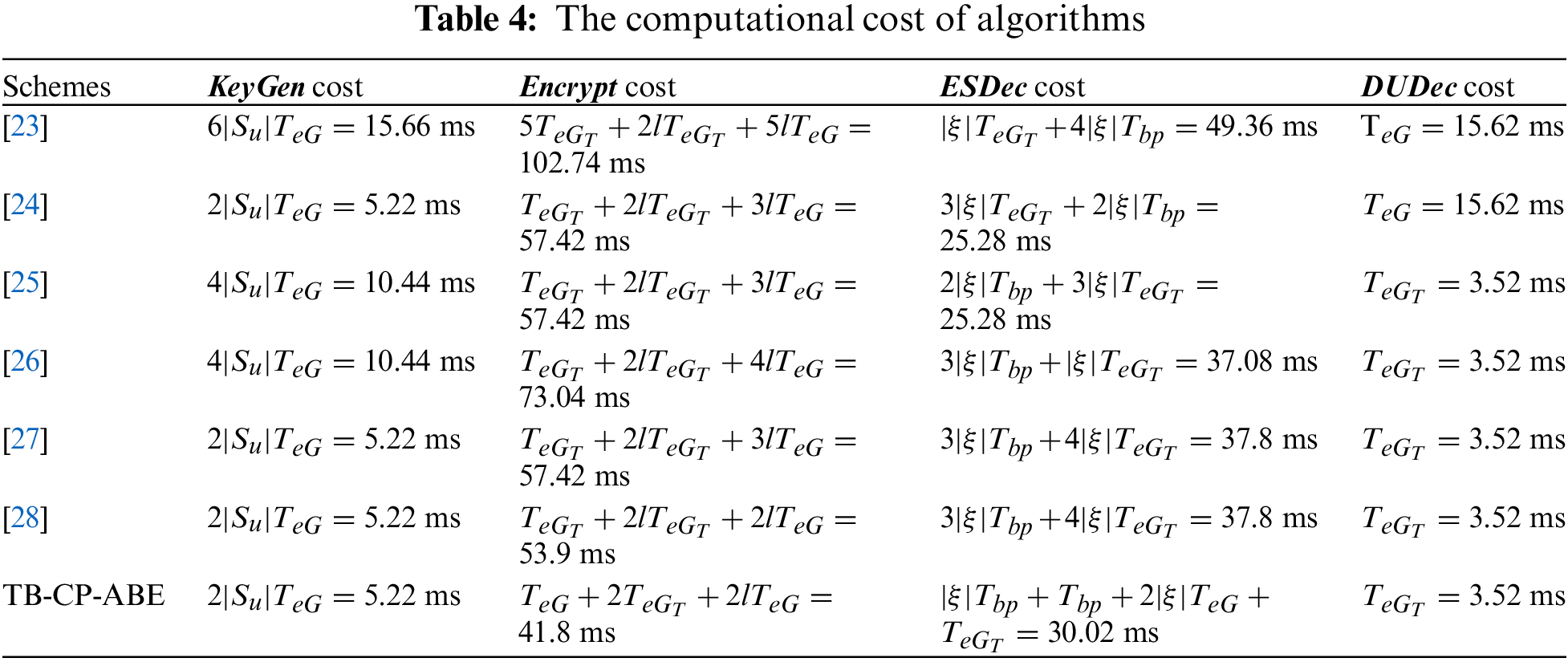
6.1 Computational Costs Comparison
For calculating the computational costs during access control phase, it’s assumed that the notations
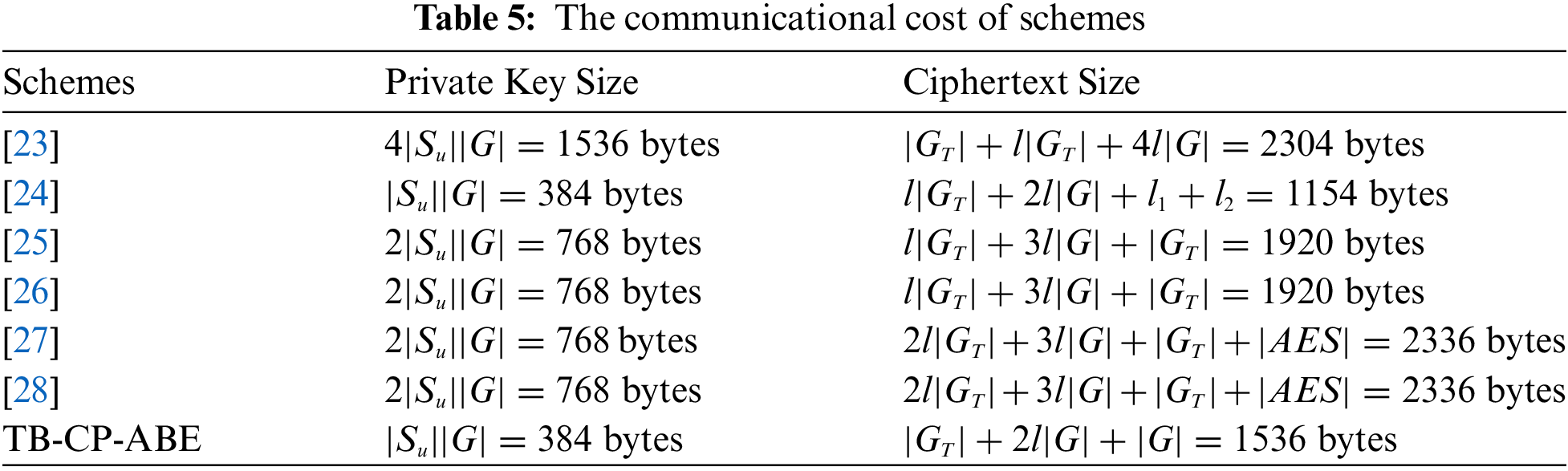
6.2 Communicational Costs Comparison
For calculating the communication costs during access control phase, it’s assumed that a random number, an elliptic curve point, an AES ciphertext are 32, 384 and 32 bytes, respectively. The proposed scheme includes private key size and ciphertext size with the communication costs of 384 bytes and 1536 bytes, respectively, totaling 1920 bits. The communication costs of Sethi et al. [23], Zhang et al. [24], Huang et al. [25], Tu et al. [26], Fugkeaw et al. [27], Fugkeaw et al. [28] are 3840, 1538, 2688, 2688, 3104, 3104 bytes respectively as provided in Table 5. It is clear that TB-CP-ABE scheme achieves a substantial reduction in communication overhead compared to the majority of existing schemes.
6.3 Performance Comparison of Algorithms
(1) Computational Performance: To assess the practical feasibility and computational performance of the TB-CP-ABE scheme, experiments are conducted to focus on three key algorithms: KeyGen, Encrypt, and ESDec. The increasing prevalence of ABE in various applications necessitates an understanding of its performance characteristics under varying attribute set sizes. Hence, this empirical investigation aims to elucidate how the execution times of these algorithms are affected by the growth in attribute complexity. The results are depicted in Figs. 3–5, where the x-axis represents the number of the user attributes ranging from 0 to 30, and the y-axis represents the time (in milliseconds) required for encryption operations. As the size of the user attribute set increases, all five schemes show an overall upward trend, indicating an increase in encryption complexity and therefore requiring longer computation time. However, it can be clearly seen that as the attribute set increases, the proposed scheme does not significantly increase the operation time of KeyGen, Encrypt, and ESDec algorithms, which proves that TB-CP-ABE outperforms the other four schemes in terms of encryption performance.
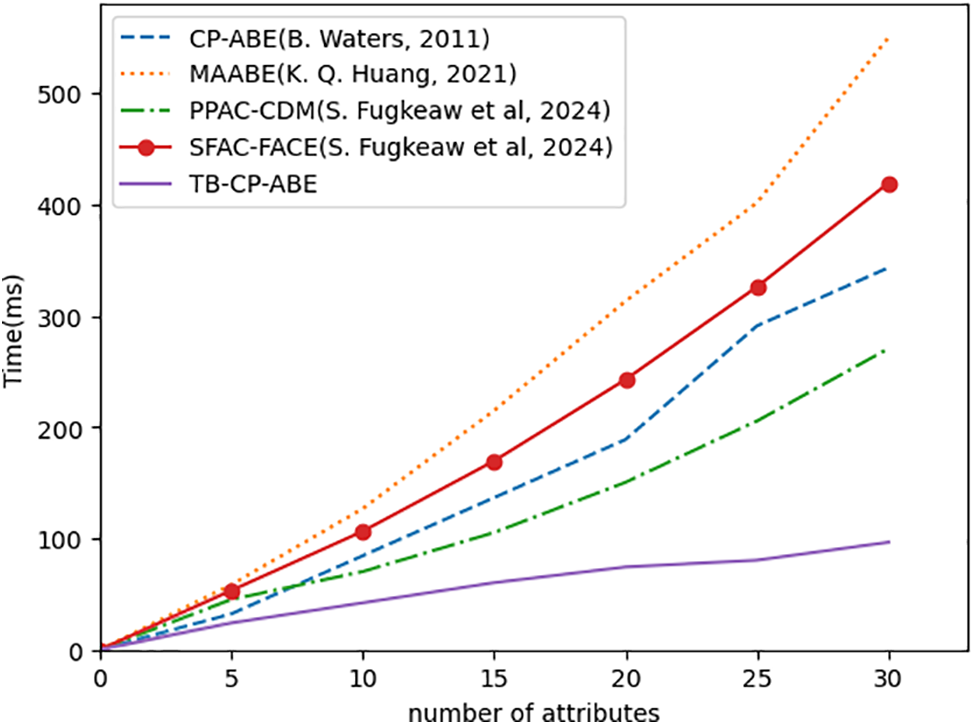
Figure 3: Performance of KeyGen [22,25,27,28]
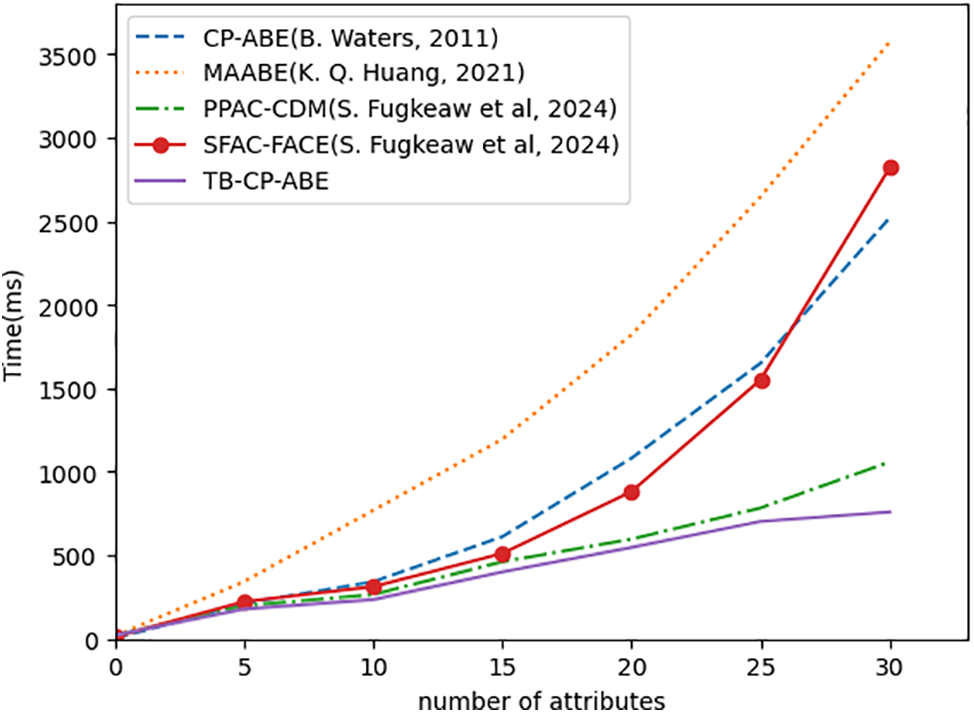
Figure 4: Performance of Encrypt [22,25,27,28]
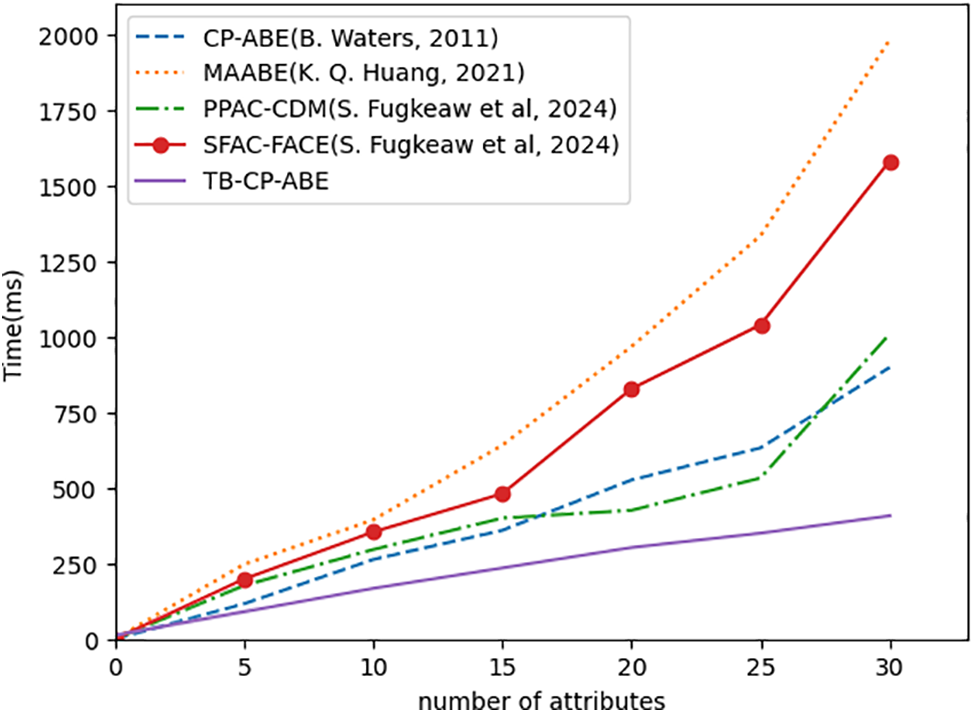
Figure 5: Performance of ESDec [22,25,27,28]
(2) Energy Consumption: In order to understand the energy consumption of different algorithms in different devices, 14 nodes were selected for testing, including 4 high-performance nodes to simulate ESs and 10 low performance nodes to simulate DUs. The 14 nodes on the x-axis in the Fig. 6 are arranged in order of computing power, and the y-axis represents energy consumption (in kWh). From the graph, it can be seen that the TB-CP-ABE scheme has the lowest computational cost in both high-performance and low performance nodes. This is consistent with the analysis of computational and communication costs, and the proposed solution has good performance, reducing the burden on devices.
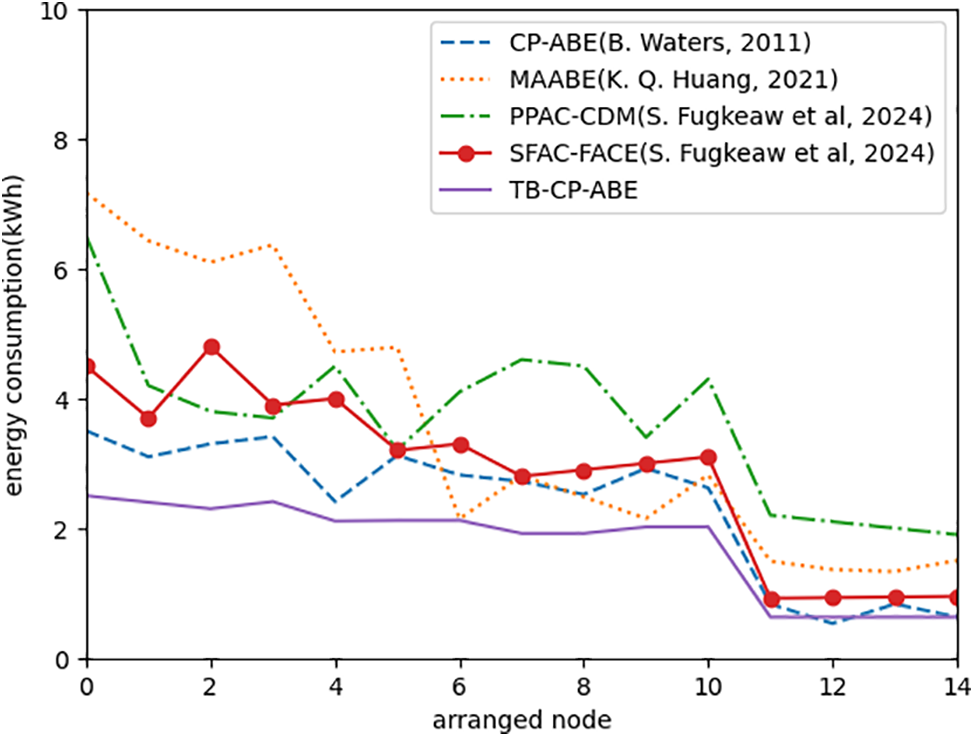
Figure 6: Energy demand comparison [22,25,27,28]
(3) Scalability: Scalability refers to how efficiently the dynamic access control mechanism handles the growth in network overhead or the time required to complete all necessary calculations as the number of DU nodes increases. Starting with an initial count of 10 nodes, the system’s scalability is evaluated by incrementally adding five nodes at a time until 800 nodes, where each new set of nodes brings a proportional increase in computing power. In essence, scalability measures the ability of the access control system to adapt and maintain performance as the network expands.
Fig. 7 illustrates the variation in network computation time as the number of nodes expands. The proposed TB-CP-ABE exhibits a linear growth in computation time as the number of nodes increases, indicating a steady but predictable rise in processing requirements. In contrast, due to the poorly expressive access structure, References [27,28] have longer overall computation times as the number of devices increases, indicating that it may not be able to scale effectively. On the other hand, References [22,25] start with lower computation times. However, as the number of nodes increases, the complex scheme process introduces huge overhead, resulting in a rapid increase in computation time, highlighting the potential scalability challenges of this method under network growth conditions.
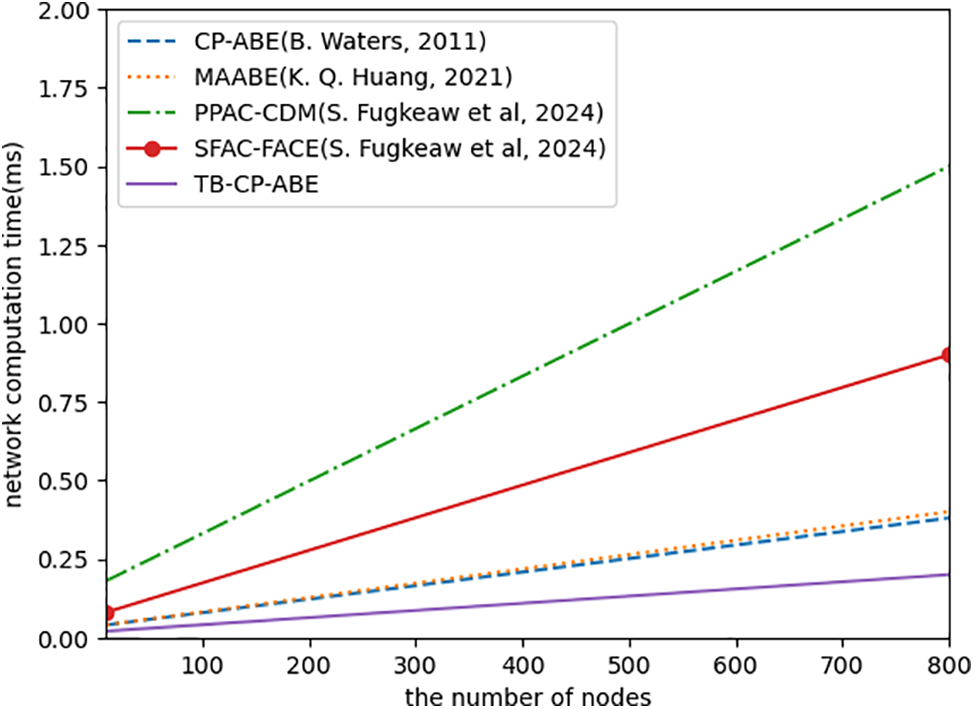
Figure 7: Scalability comparison [22,25,27,28]
(4) Latency Test: The purpose of latency testing is to examine the device’s ability to process messages. The experiment will calculate the time taken by DU from initiating the request to receiving the ciphertext and decrypting it. The latency requirement for general real-time services is 50 ms. From Fig. 8, it can be seen that due to excessive bilinear operations and frequent message passing, the delays of [25,27,28] are relatively large (mostly above 50 ms), making them unsuitable for real-time network environments. The delay of the method is close to that of the proposed algorithm, but due to the early proposal of the scheme, the security cannot meet the current requirements.
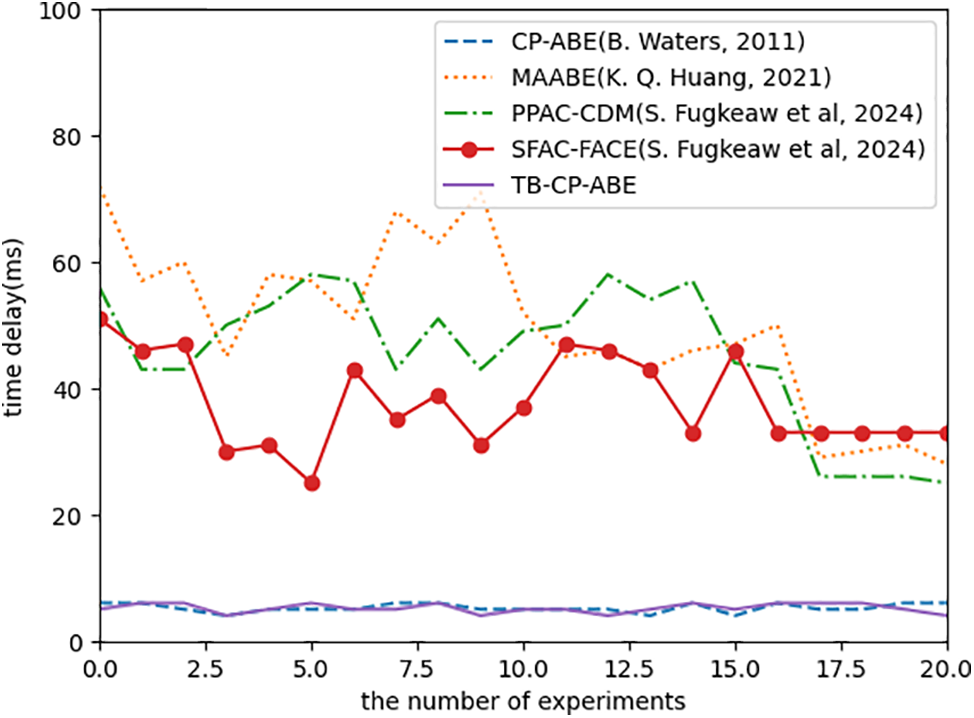
Figure 8: Time delay comparison [22,25,27,28]
In this article, a trust-based device access control CP-ABE scheme has been proposed for RES, which efficiently manages the distribution and control of encrypted data on the cloud through attribute key management. Due to the structural requirements of RES and the constraints of resource-limited terminals, the proposed scheme utilizes outsourced decryption to significantly mitigate the computational burden introduced by bilinear pairing operations. Moreover, the integration of attribute revocation and trust management enhances the flexibility and adaptability of the scheme in attribute and terminal management. A formal security analysis demonstrates that TB-CP-ABE scheme provides security against CPA. Analysis of performance demonstrates that TB-CP-ABE scheme optimizes the trade-off between computational and communication costs. This is particularly evident when comparing operational efficiency, message lengths, and security characteristics with other existing schemes, highlighting a notable reduction in the burden on resource-constrained terminals. In conclusion, the proposed TB-CP-ABE scheme offers a robust and efficient solution for securing RES, thereby advancing secure access control in cloud-assisted RES.
It is worth noting that while blockchain has shown great potential in ensuring data transaction security due to its decentralized, tamper-proof, and highly transparent characteristics, this paper has not yet considered this emerging technology when exploring device security transaction technologies. To further enhance data security and sharing efficiency, future research will focus on exploring the integration of blockchain with Ciphertext-Policy Attribute-Based Encryption (CP-ABE). This approach aims to create a decentralized data security sharing environment, providing more reliable security guarantees and flexible access control mechanisms for data transactions. In addition, we plan to apply machine learning for dynamic trust evaluation and test this scheme in various cloud-based Renewable Energy Systems (RES) environments. Through these efforts, we aim to achieve smarter and more efficient data security management, further improving the adaptability and security of the system.
Acknowledgement: The authors express their sincere gratitude to all individuals who have contributed to this paper. Their dedication and insights have been invaluable in shaping the outcome of this work.
Funding Statement: This work was supported by the Science and Technology Project of the State Grid Corporation of China, Grant number 5700-202223189A-1-1-ZN.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Kehe Wu, Zheng Tian; data collection: Yizhen Sun, Yuxi Wu, Yaogong Guo; analysis and interpretation of results: Jiyu Zhang, Ruomeng Yan; draft manuscript preparation: Jiyu Zhang, Ruomeng Yan. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data that support the findings of this study are available from the corresponding author, Jiyu Zhang, upon reasonable request.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare no conflicts of interest to report regarding the present study.
References
1. M. M. Alam, A. Haque, M. A. Khan, N. M. Sobahi, I. M. Mehedi and A. I. Khan, “Condition monitoring and maintenance management with grid-connected renewable energy systems,” Comput. Mater. Contin., vol. 72, no. 2, pp. 3999–4017, 2022. doi: 10.32604/cmc.2022.026353. [Google Scholar] [CrossRef]
2. N. R. R. Paul and D. P. Raj, “Enhanced trust based access control for multi-cloud environment,” Comput. Mater. Contin., vol. 69, no. 3, pp. 3079–3093, 2021. doi: 10.32604/cmc.2021.018993. [Google Scholar] [CrossRef]
3. H. A. Hussain, Z. Mansor, Z. Shukur, and U. Jafar, “Ether-IoT: A realtime lightweight and scalable blockchain-enabled cache algorithm for iot access control,” Comput. Mater. Contin., vol. 75, no. 2, pp. 3797–3815, 2023. doi: 10.32604/cmc.2023.034671. [Google Scholar] [CrossRef]
4. A. Sahai and B. R. Waters, “Fuzzy identity based encryption,” in Proc. Eur. Cryptol. Conf., Aarhus, Denmark, 2005, pp. 457–473. [Google Scholar]
5. L. H. Guo, J. Yang, and H. T. Wu, “A lightweight abe security protection scheme in cloud environment based on attribute weight,” Comput. Mater. Contin., vol. 76, no. 2, pp. 1929–1946, 2023. doi: 10.32604/cmc.2023.039170. [Google Scholar] [CrossRef]
6. L. Nkenyereye, S. M. R. Islam, M. Hossain, M. Abdullah-Al-Wadud, and A. Alamri, “Fog-based secure framework for personal health records systems,” Comput. Mater. Contin., vol. 66, no. 2, pp. 1937–1948, 2021. doi: 10.32604/cmc.2020.013025. [Google Scholar] [CrossRef]
7. K. P. Xue, N. Gai, J. N. Hong, D. S. L. Wei, P. L. Hong and N. H. Yu, “Efficient and secure attribute-based access control with identical sub-policies frequently used in cloud storage,” IEEE Trans. Dependable Secure Comput., vol. 19, no. 1, pp. 635–646, 2022. doi: 10.1109/TDSC.2020.2987903. [Google Scholar] [CrossRef]
8. Z. S. Zhang, W. Huang, S. J. Zhou, and Y. J. Liao, “A revocable multi-authority fine-grained access control architecture against ciphertext rollback attack for mobile edge computing,” J. Syst. Archit., vol. 129, no. 102589, p. 20, 2022. doi: 10.1016/j.sysarc.2022.102589. [Google Scholar] [CrossRef]
9. J. Zhao, P. Zeng, and K. K. R. Choo, “An efficient access control scheme with outsourcing and attribute revocation for fog-enabled e-health,” IEEE Access, vol. 9, pp. 13789–13799, 2021. doi: 10.1109/ACCESS.2021.3052247. [Google Scholar] [CrossRef]
10. S. M. Xu et al., “Match in my way: Fine-grained bilateral access control for secure cloud-fog computing,” IEEE Trans. Dependable Secure Comput., vol. 19, no. 2, pp. 1064–1077, 2022. [Google Scholar]
11. C. Ge, Z. Liu, W. Susilo, L. Fang, and H. Wang, “Attribute-based encryption with reliable outsourced decryption in cloud computing using smart contract,” IEEE Trans. Depend. Secure Comput., vol. 21, no. 2, pp. 937–948, 2023. doi: 10.1109/TDSC.2023.3265932. [Google Scholar] [CrossRef]
12. Q. Li, Q. Zhang, H. Huang, W. Zhang, W. Chen and H. Wang, “Secure, efficient, and weighted access control for cloud-assisted industrial IoT,” IEEE Internet Things J., vol. 9, no. 18, pp. 16917–16927, 2022. doi: 10.1109/JIOT.2022.3146197. [Google Scholar] [CrossRef]
13. L. Y. Zhang, W. T. You, and Y. Mu, “Secure outsourced attribute-based sharing framework for lightweight devices in smart health systems,” IEEE Trans. Serv. Comput., vol. 15, no. 5, pp. 3019–3030, 2022. doi: 10.1109/TSC.2021.3073740. [Google Scholar] [CrossRef]
14. Y. Tao et al., “ORR-CP-ABE: A secure and efficient outsourced attribute-based encryption scheme with decryption results reuse,” Future Gener. Comput. Syst., vol. 161, pp. 559–571, 2024. doi: 10.1016/j.future.2024.07.040. [Google Scholar] [CrossRef]
15. R. H. Xu, J. Joshi, and P. Krishnamurthy, “An integrated privacy preserving attribute-based access control framework supporting secure deduplication,” IEEE Trans. Depend. Secure Comput., vol. 18, no. 2, pp. 706–721, 2021. doi: 10.1109/TDSC.2019.2946073. [Google Scholar] [CrossRef]
16. H. Xiong, K. K. R. Choo, and A. V. Vasilakos, “Revocable identity-based access control for big data with verifiable outsourced computing,” IEEE Trans. Big Data, vol. 8, no. 1, pp. 1–13, 2022. doi: 10.1109/TBDATA.2017.2697448. [Google Scholar] [CrossRef]
17. H. Ma, R. Zhang, S. Z. Sun, Z. S. Song, and G. S. Tan, “Server-aided fine-grained access control mechanism with robust revocation in cloud computing,” IEEE Trans. Serv. Comput., vol. 15, no. 1, pp. 164–173, 2022. doi: 10.1109/TSC.2019.2925028. [Google Scholar] [CrossRef]
18. W. J. Liu, W. Y. Chiu, and W. Hua, “Blockchain-enabled renewable energy certificate trading: A secure and privacy-preserving approach,” Energy, vol. 290, 2024. doi: 10.1016/j.energy.2023.130110. [Google Scholar] [CrossRef]
19. L. Feng et al., “SDAC-BBPP: A secure dynamic access control scheme with blockchain-based privacy protection for IIoT,” IEEE Trans. Netw. Serv. Manag., vol. 21, no. 3, pp. 3179–3193, 2024. doi: 10.1109/TNSM.2024.3371521. [Google Scholar] [CrossRef]
20. A. A. Alqbaishi and A. E. S. Ahmed, “Reputation evaluation using fuzzy logic for blockchain-based access control in an IoT environment,” IEEE Access, vol. 12, pp. 97386–97404, 2024. doi: 10.1109/ACCESS.2024.3426993. [Google Scholar] [CrossRef]
21. Y. Wei, K. Gai, J. Yu, L. Zhu, and K. K. R. Choo, “Trustworthy access control for multiaccess edge computing in blockchain-assisted 6G systems,” IEEE Trans. Ind. Inform., vol. 20, no. 5, pp. 7732–7743, 2024. doi: 10.1109/TII.2024.3360467. [Google Scholar] [CrossRef]
22. B. Waters, “Ciphertext-policy attribute-based encryption: An expressive, efficient, and provably secure realization,” in Proc. 14th Int. Conf. Pract. Theor. Public Key Cryptogr., Taormina, Italy, 2011, pp. 53–70. doi: 10.1007/978-3-642-19379-8_4. [Google Scholar] [CrossRef]
23. K. Sethi, A. Pradhan, and P. Bera, “Practical traceable multi-authority CP-ABE with outsourcing decryption and access policy updation,” J. Inf. Secur. Appl., vol. 51, 2020, Art. no. 102435. doi: 10.1016/j.jisa.2019.102435. [Google Scholar] [CrossRef]
24. Z. S. Zhang and S. J. Zhou, “A decentralized strongly secure attribute-based encryption and authentication scheme for distributed internet of mobile things,” Comput. Netw., vol. 201, 2021, Art. no. 108553. doi: 10.1016/j.comnet.2021.108553. [Google Scholar] [CrossRef]
25. K. Q. Huang, “Secure efficient revocable large universe multi-authority attribute-based encryption for cloud-aided IoT,” IEEE Access, vol. 9, pp. 53576–53588, 2021. doi: 10.1109/ACCESS.2021.3070907. [Google Scholar] [CrossRef]
26. S. S. Tu, M. Waqas, F. M. Huang, G. Abbas, and Z. H. Abbas, “A revocable and outsourced multi-authority attribute-based encryption scheme in fog computing,” Comput. Netw., vol. 195, 2021, Art. no. 108196. doi: 10.1016/j.comnet.2021.108196. [Google Scholar] [CrossRef]
27. S. Fugkeaw and L. Hak, “PPAC-CDW: A privacy-preserving access control scheme with fast OLAP query and efficient revocation for cloud data warehouse,” IEEE Access, vol. 12, pp. 78743–78758, 2024. doi: 10.1109/ACCESS.2024.3408221. [Google Scholar] [CrossRef]
28. S. Fugkeaw, R. Prasad Gupta, and K. Worapaluk, “Secure and fine-grained access control with optimized revocation for outsourced IoT EHRs with adaptive load-sharing in fog-assisted cloud environment,” IEEE Access, vol. 12, pp. 82753–82768, 2024. doi: 10.1109/ACCESS.2024.3412754. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2025 The Author(s). Published by Tech Science Press.
Copyright © 2025 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools