 Open Access
Open Access
ARTICLE
Classification of Cybersecurity Threats, Vulnerabilities and Countermeasures in Database Systems
1 King Abdullah the II IT School, University of Jordan, Amman, 11942, Jordan
2 The National Research Center for Giftedness and Creativity, King Faisal University, Al-Ahsa, 31982, Saudi Arabia
3 Department of Networks and Cybersecurity, Al-Ahliyya Amman University, Amman, 19328, Jordan
* Corresponding Authors: Mohammed Amin Almaiah. Email: ; Romel Al-Ali. Email:
Computers, Materials & Continua 2024, 81(2), 3189-3220. https://doi.org/10.32604/cmc.2024.057673
Received 24 August 2024; Accepted 25 October 2024; Issue published 18 November 2024
Abstract
Database systems have consistently been prime targets for cyber-attacks and threats due to the critical nature of the data they store. Despite the increasing reliance on database management systems, this field continues to face numerous cyber-attacks. Database management systems serve as the foundation of any information system or application. Any cyber-attack can result in significant damage to the database system and loss of sensitive data. Consequently, cyber risk classifications and assessments play a crucial role in risk management and establish an essential framework for identifying and responding to cyber threats. Risk assessment aids in understanding the impact of cyber threats and developing appropriate security controls to mitigate risks. The primary objective of this study is to conduct a comprehensive analysis of cyber risks in database management systems, including classifying threats, vulnerabilities, impacts, and countermeasures. This classification helps to identify suitable security controls to mitigate cyber risks for each type of threat. Additionally, this research aims to explore technical countermeasures to protect database systems from cyber threats. This study employs the content analysis method to collect, analyze, and classify data in terms of types of threats, vulnerabilities, and countermeasures. The results indicate that SQL injection attacks and Denial of Service (DoS) attacks were the most prevalent technical threats in database systems, each accounting for 9% of incidents. Vulnerable audit trails, intrusion attempts, and ransomware attacks were classified as the second level of technical threats in database systems, comprising 7% and 5% of incidents, respectively. Furthermore, the findings reveal that insider threats were the most common non-technical threats in database systems, accounting for 5% of incidents. Moreover, the results indicate that weak authentication, unpatched databases, weak audit trails, and multiple usage of an account were the most common technical vulnerabilities in database systems, each accounting for 9% of vulnerabilities. Additionally, software bugs, insecure coding practices, weak security controls, insecure networks, password misuse, weak encryption practices, and weak data masking were classified as the second level of security vulnerabilities in database systems, each accounting for 4% of vulnerabilities. The findings from this work can assist organizations in understanding the types of cyber threats and developing robust strategies against cyber-attacks.Keywords
Database management systems (DBMS) constitute a critical component of Information Technology (IT) infrastructure in any information system, primarily due to their role in storing sensitive data [1]. These systems are essential for maintaining customer data and transaction records. Consequently, organizations have become increasingly reliant on DBMS due to their substantial benefits. However, this dependence has introduced new challenges related to cybersecurity risks and attacks. Currently, cyber threats represent the most significant challenges facing database management systems, with the number of cyber-attacks on these systems increasing and becoming more sophisticated [2]. Cyber risks in DBMS can have severe consequences, including data loss, reputational damage, and system failure. Therefore, it is crucial to understand the behavior of cyber threats on database systems and identify appropriate countermeasures to mitigate their impacts [3]. In the contemporary digital landscape, database systems serve as the backbone of modern IT society, supporting various applications such as business operations, scientific research, and technological innovation. DBMS offers numerous advantages, including ease of data storage, retrieval, modification, and deletion, as well as various data processing operations. As database management systems continue to evolve and expand, they face significant challenges due to emerging attacks that threaten their security [4].
While database systems offer numerous advantages, including enhanced information quality, consistency, accessibility, and efficiency, they are also more susceptible to cybersecurity attacks. The widespread adoption of database systems in organizations has given rise to new cybersecurity vulnerabilities that can be exploited. In the database field, cybersecurity attacks such as SQL injection, distributed denial-of-service (DDoS), and ransomware have become increasingly prevalent, posing significant risks [5,6]. The continuous development of new attack techniques by cybercriminals presents substantial challenges that require addressing [7,8]. Consequently, database security analysts must continuously assess security threats to detect emerging risks and protect database systems and their data from unauthorized modifications. Organizations must remain vigilant about potential threats to their databases, comprehend their impacts, implement preventive measures, and mitigate their negative consequences. Furthermore, they should identify and address vulnerabilities in their systems and devices promptly upon discovery, striving to maintain data confidentiality, integrity, and availability. The most common threats to database systems include insider threats, SQL injections, phishing, and DDoS attacks [7,8].
Previous studies have highlighted several security issues in database systems, including inadequate encryption, insufficient access controls, and outdated software [9,10]. These vulnerabilities may lead to data corruption, unauthorized access, and service interruptions. Database security threats are defined as exploitable weaknesses that compromise the confidentiality, integrity, and availability of stored data. In recent years, numerous cybersecurity attacks have been witnessed on database systems. For instance, Verizon’s 2020 Data Breach Investigations Report revealed that 45% of breaches involved hacking, while 22% were attributed to social attacks such as phishing or pretexting. Additionally, an IBM (International Business Machines Corporation) study reported that the average cost of a data breach in 2020 was $3.86 million. Risk assessment can safeguard companies against such financial losses. Therefore, understanding potential threats is crucial in risk assessment and should be considered when developing a robust security strategy to prevent data breaches. Security risk assessment plays a vital role in identifying potential threats, implementing proactive security measures, and mitigating the likelihood of successful attacks. Cybersecurity risk assessment for database systems is an ongoing process rather than a one-time task. By identifying and classifying risks, implementing appropriate security controls, and evaluating their effectiveness, organizations can significantly reduce potential threats and risks in database systems. Consequently, this research aims to achieve the following objectives:
(1) To identify and categorize the primary cybersecurity threats in database systems.
(2) To identify and classify the principal cybersecurity vulnerabilities in database systems.
(3) To identify and systematize the key cybersecurity countermeasures in database systems.
Several studies have explored and classified cybersecurity risks and threats in database systems. Omotunde et al. [3] conducted a comprehensive review to identify the main security controls in database systems. They categorized these controls into five groups: privacy-enhancing techniques, Intrusion Detection Systems (IDS), auditing, encryption, and access control and authentication. Touil et al. [6] analyzed critical cyber-attacks in database systems based on blockchain technology. Their findings revealed that the primary cyber-attacks in database systems include DoS, unauthorized access, internal threats, black hat activities, social engineering, SQL injection, and abuse of excessive privilege. Similarly, Pan et al. [5] investigated the main cyber threats in database systems and identified SQL injection, cross-site scripting, data leakage, and malware as the primary threats that attackers can exploit to compromise database systems. Teimoor [4] conducted a study to identify cyber threats, risks, and countermeasures in databases. The research classified cyber-attacks into two main types: passive attacks and active attacks. Passive attacks encompass static leakage, outflow of information, and dynamic leakage, while active attacks include spoofing, splicing, and replay. The study also identified five key countermeasures to protect databases: access control, inference strategy, user authentication, accountability and auditing, and encryption techniques.
3 Research Design and Framework
This section outlines the research design for proposing a risk assessment framework for database systems. The framework comprises four primary stages: (1) identifying key components, (2) threat identification, (3) vulnerability identification, and (4) countermeasure identification. Each stage is informed by the findings from the literature review. The primary objective of this risk assessment framework is to provide a robust and comprehensive approach for addressing all types of threats, vulnerabilities, and countermeasures in database systems. Fig. 1 illustrates the main stages of the risk assessment framework.
Figure 1: The main stages of risk assessment framework
3.1 Stage One: Identifying Key Components
The initial phase of the risk assessment framework involves compiling data from literature review findings to establish the dataset for this study. This process entails a comprehensive examination of existing studies, models, frameworks, and literature in the field of security database systems. The collected data encompasses threat types, vulnerability categories, and countermeasure methodologies. The information gathered during this stage will undergo analysis in subsequent phases.
3.2 Stage Two: Threats Identification
Following data collection in the first stage, the subsequent phase involves analyzing the gathered information to identify and categorize existing cybersecurity threats in database systems. This stage encompasses a comprehensive and systematic process that identifies various types of threats with the potential to exploit vulnerabilities in database systems, potentially resulting in compromised systems.
3.3 Stage Three: Vulnerabilities Identification
In the third stage, following data collection, an analysis is conducted to identify existing technical security vulnerabilities that could potentially compromise database systems. This stage of the risk assessment framework incorporates a comprehensive systematic review to determine critical vulnerability types that may be exploited to breach database systems.
3.4 Stage Four: Countermeasures Identification
The final phase of the risk assessment framework involves identifying and categorizing effective countermeasures to address potential cybersecurity threats and vulnerabilities in database systems. The identification of these countermeasures is directly linked to all types of threats and vulnerabilities identified in the previous stages’ findings. Consequently, this stage provides solutions to mitigate potential threats that could compromise the integrity of database systems.
4 Cyber Threats, Vulnerabilities, and Countermeasures Framework
Fig. 2 illustrates the primary components of the research framework. The framework comprises three main parts: (1) threat identification, (2) vulnerability identification, and (3) countermeasure identification. The following subsections will provide detailed explanations of each step within the framework.
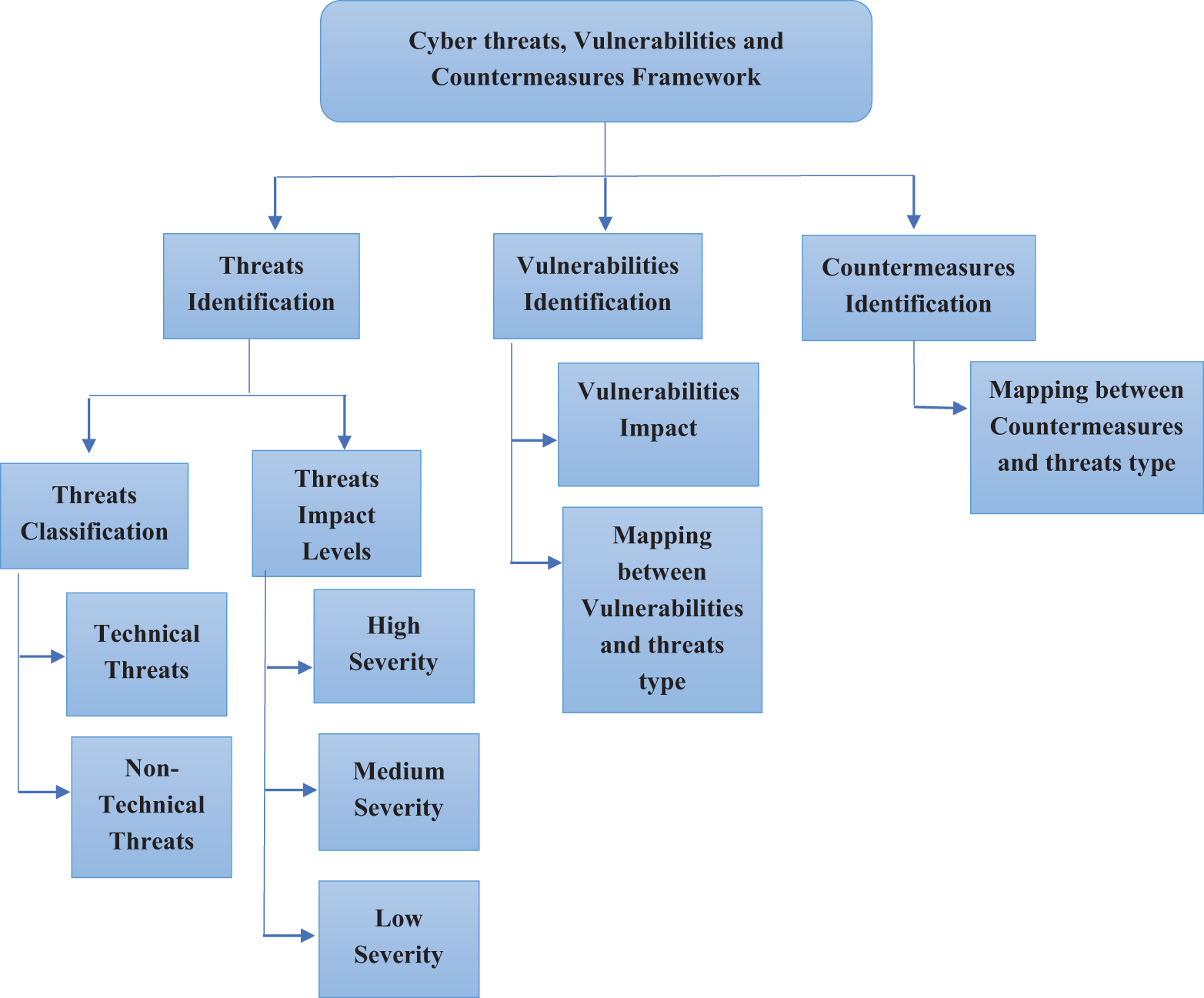
Figure 2: Cyber threats, vulnerabilities and countermeasures framework
The initial phase of the framework involves identifying and classifying existing cybersecurity threats in database systems. This step encompasses a comprehensive, systematic classification of all potential threats that could exploit vulnerabilities in database systems, potentially leading to compromised systems. The threat classification is categorized into two main groups: (1) technical threats and (2) non-technical threats. Technical threats encompass malware types that exploit security weaknesses in the IT infrastructure of database systems, such as SQL injection attacks, DDoS attacks, TCP (Transmission Control Protocol) spoofing attacks, and malicious traffic attacks. Conversely, non-technical threats include insider threats, bypass/physical attacks, human errors, and illegal user behavior. The classification analysis is based on multiple dimensions, including threat characteristics, behaviors, and their impacts. Each threat type is described with an explanation of its potential impact on database systems. The subsequent subsections provide a detailed threat classification of both technical and non-technical threats.
4.1.1 Classification of Technical Threats
As discussed in the preceding section, we categorize cyber threats in database systems into technical threats, as illustrated in Table 1. Technical threats encompass various malware types that exploit security vulnerabilities in the IT infrastructure of database systems, including SQL injection attacks, DDoS attacks, TCP spoofing attacks, and malicious traffic attacks. According to Table 1, ransomware is a specific type of malware that restricts access to the victim’s data through encryption and demands a ransom payment for restoring access. There are two primary types of ransomware attacks on databases: (1) Encryption ransomware, which utilizes built-in database functions and methods such as transparent data encryption or traditional encryption standards like Advanced Encryption Standard (AES), Rivest–Shamir–Adleman (RSA), and Data Encryption Standard (DES) to encrypt data before writing it to a disk, and (2) Exfiltration ransomware, whose primary objective is data theft. Attackers may employ database dumping tools, evasion techniques such as Domain Name System (DNS) exfiltration to evade detection and circumvent security controls, and utilize SELECT queries.
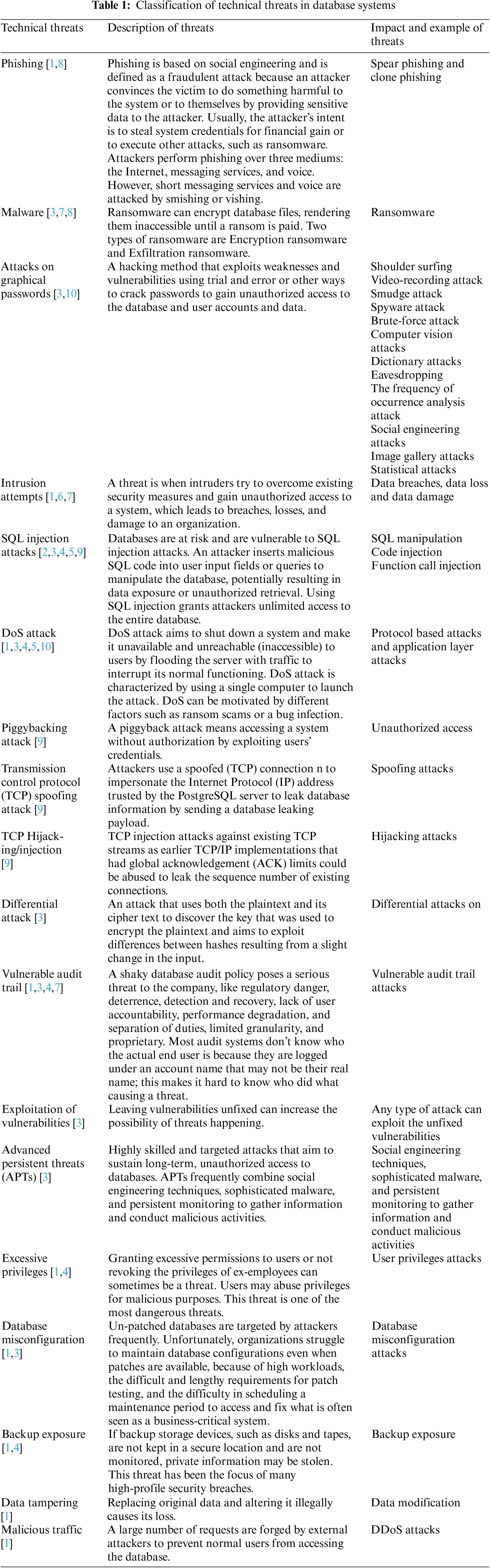
SQL Injection represents another type of threat, involving the insertion of malicious code into original SQL database queries with the intent to subvert the application’s purpose [11]. Poorly written web application code or configuration errors can lead to compromises in integrity, availability, and confidentiality through SQL Injection [12]. Two primary forms of input injection exist: (1) SQL Injection, which targets traditional databases by inserting unauthorized SQL statements into input fields, and (2) NoSQL Injection, which focuses on big data platforms and involves inserting malicious statements into big data components. A successful attack may grant the attacker unrestricted access to the entire database. Furthermore, SQL injection attacks can be conducted through three methods: (1) SQL Manipulation, which alters SQL commands within the application, (2) Code Injection, which exploits computer bugs caused by invalid data processing to add additional SQL statements or commands to existing SQL statements, and (3) Function Call Injection, which inserts database or operating system function calls into vulnerable SQL statements to manipulate data or execute privileged system calls [13,14]. Another technical threat involves graphical passwords, which are user-friendly authentication mechanisms. However, their increasing popularity correlates with a rise in their vulnerability to security attacks. As outlined in Table 1, security attacks on passwords can be categorized into twelve distinct types:
1. Shoulder surfing:
This form of attack frequently occurs in crowded environments. It involves a malicious actor observing an individual as they input a password on a computer, with the intent of gaining unauthorized access to private or sensitive information.
2. Video-recording attack:
Utilizing a device equipped with a camera, a malicious actor can record the login process and subsequently replay the video to extract the password [15].
3. Smudge attack:
When users input their passwords by tapping on touchscreen devices or drawing patterns, residual oils and dirt from their fingers leave smudges on the screen. These smudges can potentially be analyzed by attackers to deduce the password [16].
4. Spyware attacks:
Malicious software installed by an attacker on a victim’s device can record information and actions. One example is a screen scraper, which captures user activity displayed on the screen [17].
5. Brute-force attack:
A brute-force attack involves an attacker attempting to guess a password by systematically trying every possible combination until the correct one is identified. This method typically targets passwords with a limited character space. The attack may utilize a collection of forge-fingerprint details or Optical Character Recognition (OCR) techniques in the case of CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart).
6. Computer vision attack:
This method employs artificial intelligence to ascertain an individual’s password by analyzing a live or pre-recorded video of the user’s finger interactions with a touch screen. The video footage is input into a system that tracks finger movements from the camera’s perspective. Utilizing sophisticated algorithms, the system generates multiple patterns, which are subsequently transformed from the camera’s viewpoint to the user’s perspective. These patterns are then ranked according to predefined criteria. Ultimately, the system presents the attacker with potential graphical password(s), potentially facilitating unauthorized access.
7. Dictionary attack:
A dictionary attack is a password-cracking technique that employs a systematic key approach. In this method, the attacker systematically attempts all possible passwords from a precompiled list, which is typically based on common user behaviors and patterns.
8. Eavesdropping:
A man-in-the-middle attack occurs when an attacker intercepts communication between the user and the server. The attacker either decrypts information sent by the user to the server or intercepts the user’s request and replays it to the server. Data eavesdropping, also known as sniffing or snooping, involves the interception of data when an attacker exploits insecure or vulnerable networks to read or steal information as it travels between two devices during the transmission process.
9. The frequency of occurrence analysis (FOA) attack:
This method analyzes the frequency of recurring patterns during the login process. It identifies and restricts the keys utilized for authentication, and depending on the scheme’s design, it examines either image or keypress location frequency.
Image frequency analysis refers to a method employed by malicious actors to deduce passwords by identifying and exploiting patterns in the most frequently occurring images.
Keypress location frequency analysis: determining the most frequently selected final image location for authentication by generating a heat map based on occurrence data.
10. Social engineering attacks:
Persuading users to unknowingly divulge their information. Phishing represents a prominent social engineering tactic.
11. Image gallery attacks:
Physical access attacks occur when an unauthorized individual gains direct access to a physical server or database. This type of breach potentially enables the attacker to log in as any user, circumvent authentication protocols, and alter images utilized during the authentication process.
12. Sonar attack:
In a sonar attack, an adversary detects the user’s device-unlocking gesture and infers the pattern utilized by analyzing recorded sound waves. The attack exploits the device’s microphone to capture a frequency emitted by the application, which is often imperceptible to human hearing.
4.1.2 Classification of Non-Technical Threats
Non-technical threats refer to dangers arising from human activities that may lead to unauthorized access to sensitive data. In this study, these threats are classified based on their nature and sources, as illustrated in Table 2. Non-technical threats encompass human vulnerabilities that can be exploited to breach database systems. These can be categorized into insider threats, human errors, physical thefts, third-party risks, social engineering, data exposure, data tampering, illegal user behavior, and unauthorized access.

Fig. 3 illustrates the analysis results of technical and non-technical cyber threats classifications. The findings reveal that SQL injection attacks and DoS attacks were the most prevalent technical threats in database systems, each accounting for 9% of incidents. Vulnerable audit trails, intrusion attempts, and ransomware attacks were identified as the second tier of technical threats, representing 7%, 7%, and 5% of incidents, respectively. The third tier of technical threats comprised phishing, database misconfiguration, attacks on graphical passwords, and backup exposure, each constituting 4% of incidents. Other technical threats, including TCP spoofing attacks, TCP hijacking/injection, piggybacking attacks, and malicious traffic, were observed less frequently, each accounting for 2% of incidents. Regarding non-technical threats, insider threats emerged as the most common, representing 5% of incidents. Other non-technical threats, such as bypass/physical attacks, illegal user behaviors, physical theft of assets, and third-party privilege elevation, were categorized in the second tier, each accounting for 2% of incidents.
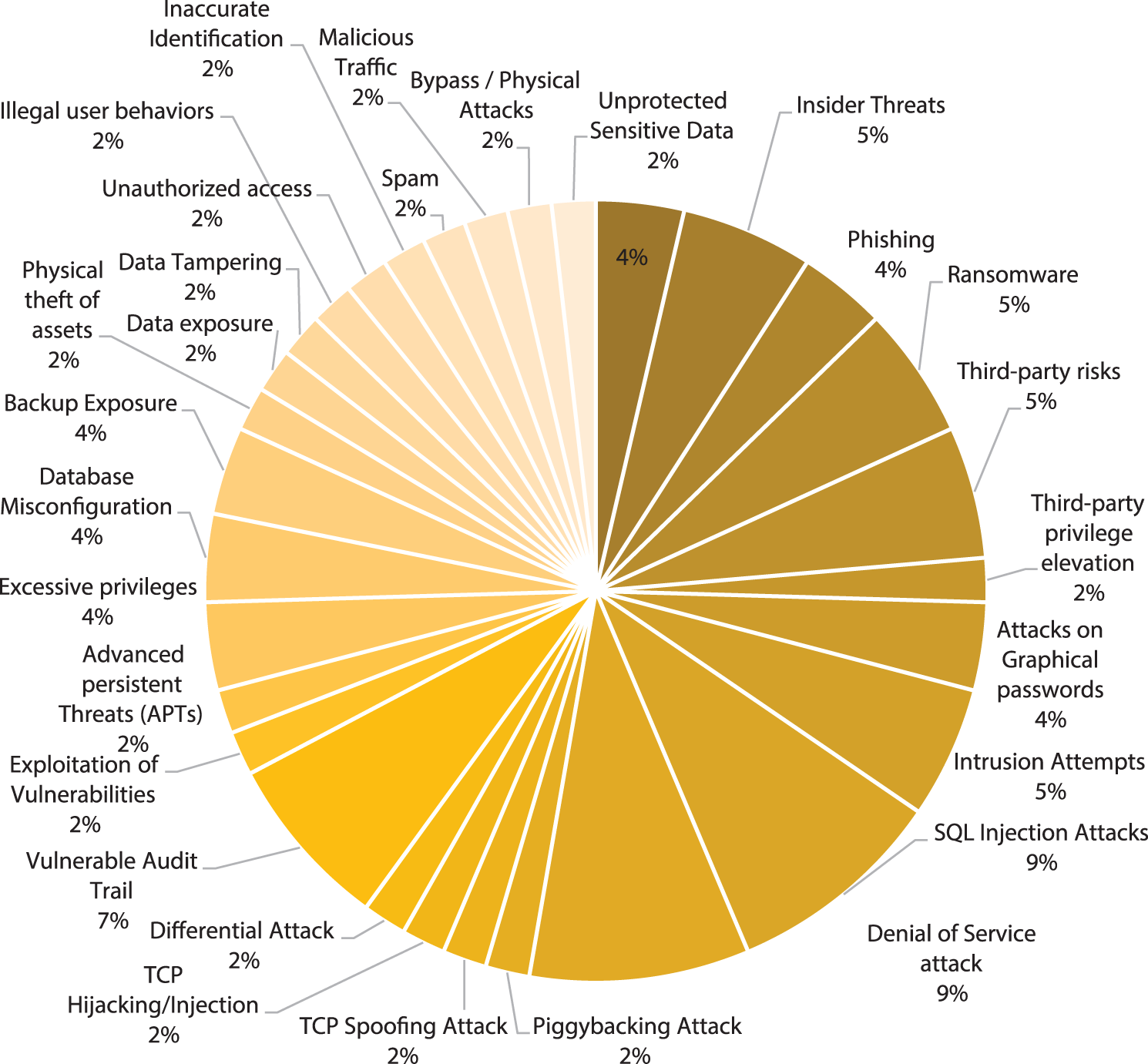
Figure 3: Analysis of classifications of technical and non-technical cyber threats
4.2 Vulnerabilities Identification
The second step of the framework aims to identify the technical security vulnerabilities that could be exploited to compromise the database systems’ assets. These vulnerabilities may be associated with either single or multiple operational or cyber security threats. Vulnerability scans and assessments are crucial steps in the risk assessment process to identify critical technical vulnerabilities. In this study, the classification of vulnerabilities is divided into twenty main categories: weak authentication, untrusted third-party, unnecessary third-party granted access, software bugs, unpatched database, insecure coding practices, weak security controls, weak audit trail, limited security expertise and education, unmanaged sensitive data, insecure network, password misuse, platform vulnerabilities, integration challenges, management complexity, weak encryption practices, weak data masking, multiple usage of an account, weak security awareness, and ineffective key management, as shown in Fig. 4. Table 3 summarizes the main technical vulnerabilities in database systems, describing these vulnerabilities and their impacts.
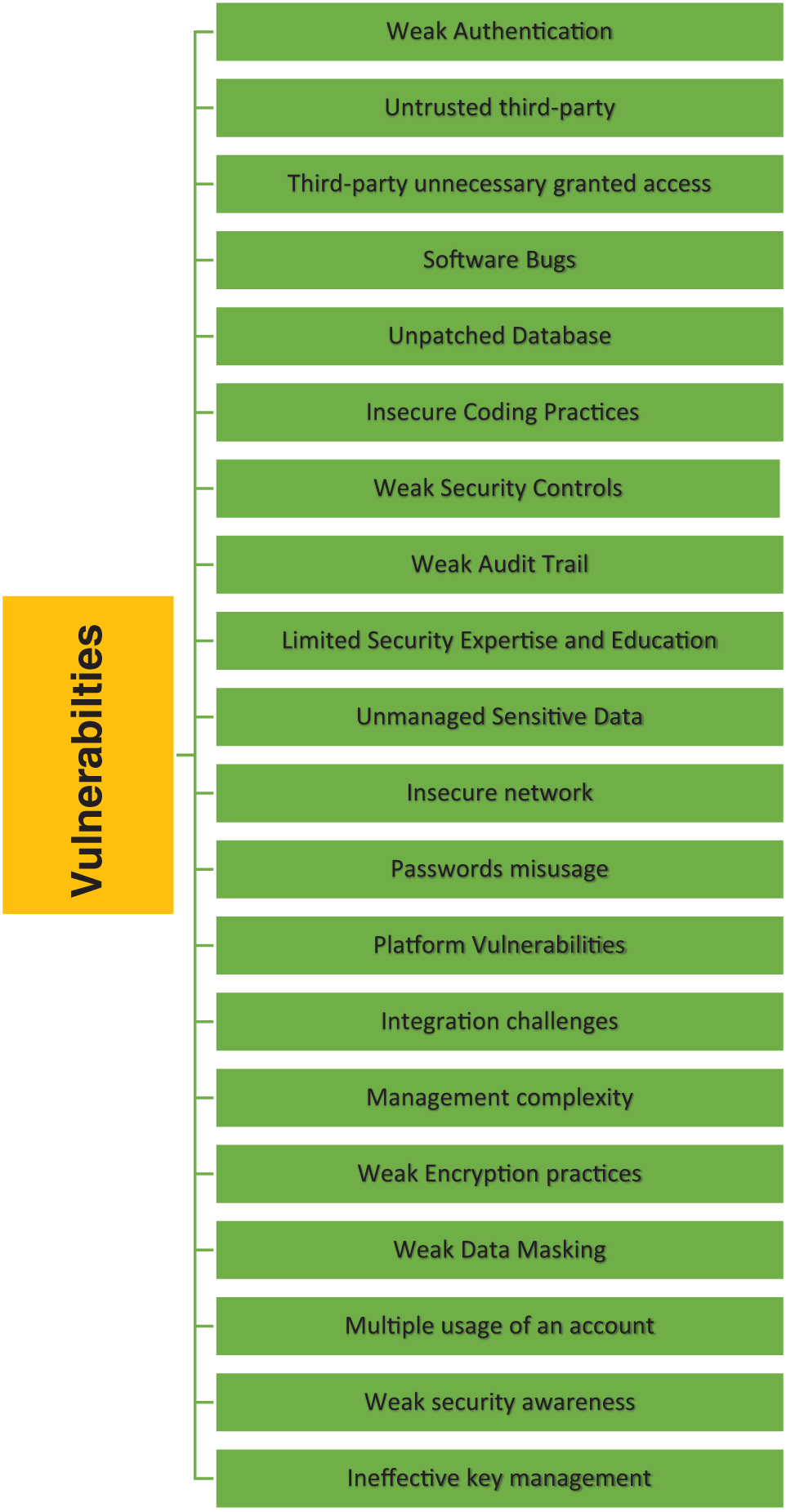
Figure 4: The most common technical security vulnerabilities in database systems

Fig. 5 illustrates the analysis results of technical security vulnerability classifications. The findings indicate that weak authentication, unpatched databases, weak audit trails, and multiple usage of a single account were the most prevalent technical vulnerabilities in database systems, each accounting for 9% of the identified issues. Furthermore, software bugs, insecure coding practices, weak security controls, insecure networks, password misuse, weak encryption practices, and inadequate data masking were classified as secondary-level security vulnerabilities in database systems, each representing 4% of the identified vulnerabilities. Additionally, the study revealed that weak security awareness, limited security expertise and education, untrusted third parties, unnecessary third-party access, and management complexity were the most common non-technical vulnerabilities in database systems, each comprising 4% of the identified issues.
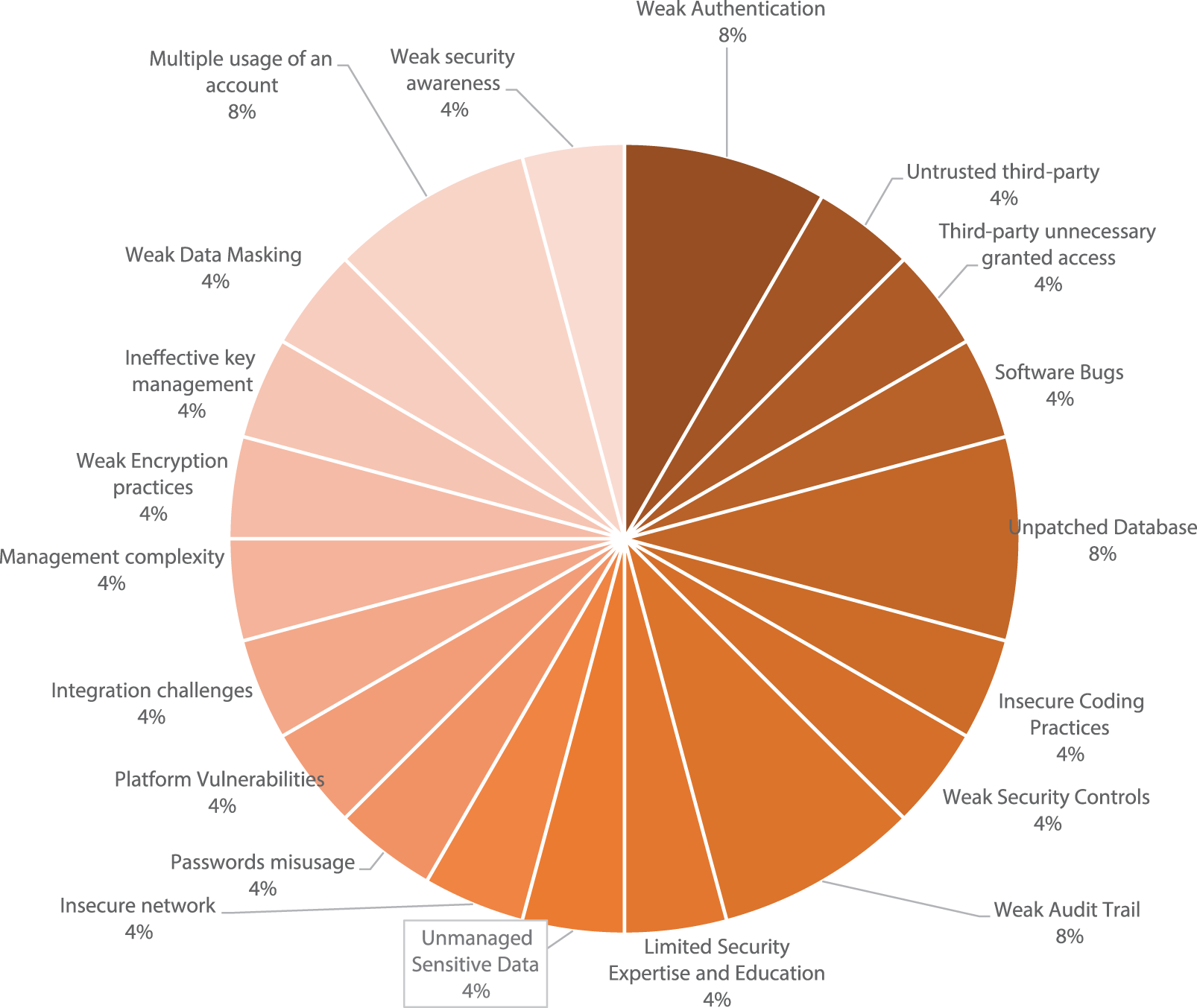
Figure 5: Analysis of classifications of technical security vulnerabilities
4.3 Countermeasures Identification
In this phase, we conduct a comprehensive analysis of essential countermeasures aimed at reducing and mitigating the impact of vulnerabilities associated with cyber threats. Our study identified a range of security controls designed to enhance database system security against cyber-attacks. These measures include data encryption, access control, authentication, firewalls, data backup, behavior detection, spam detection, security audits, anomaly detection methods, and others, as illustrated in Table 4.
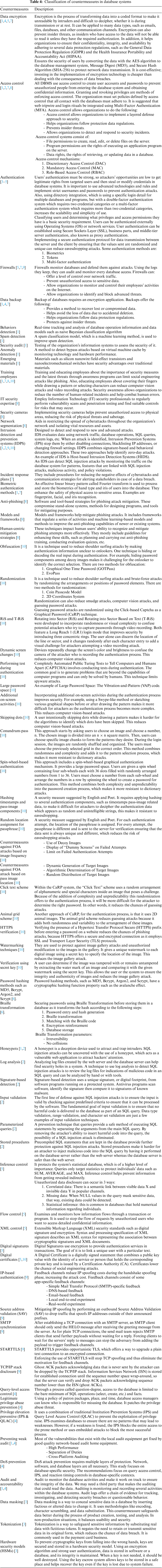
Security controls and countermeasures are mechanisms and tools developed to protect database systems from cyber threats and attacks. These countermeasures are crucial for maintaining data integrity and safeguarding database systems from unauthorized access. They can be categorized into several types based on their functions, usage, effectiveness, and importance. As shown in Fig. 6a,b, encryption methods are considered one of the most powerful technical security controls for database systems, protecting sensitive data and preventing unauthorized access. Multi-factor authentication is also a robust technique for preventing unauthorized access to sensitive data and database systems. Firewalls offer monitoring capabilities for databases and defend them against attacks. Using the logs they maintain, they can audit and monitor all database access. Firewalls provide a level of control over network traffic and prevent unauthorized access to sensitive data. Network segmentation helps restrict the spread of cyberattacks throughout the network and isolate vital resources and assets. IDPS is designed to detect and respond to new and advanced attacks. IDS evaluates data using network traffic, database operations, SQL queries, system logs, and other sources. When an attack is identified, IPS stop them by disabling connections, blacklisting IP addresses, or modifying firewall settings. IDPS combines signature-based and behavioral detection approaches, which help identify zero-day attacks. Fig. 7 represents the most common countermeasures in database systems.
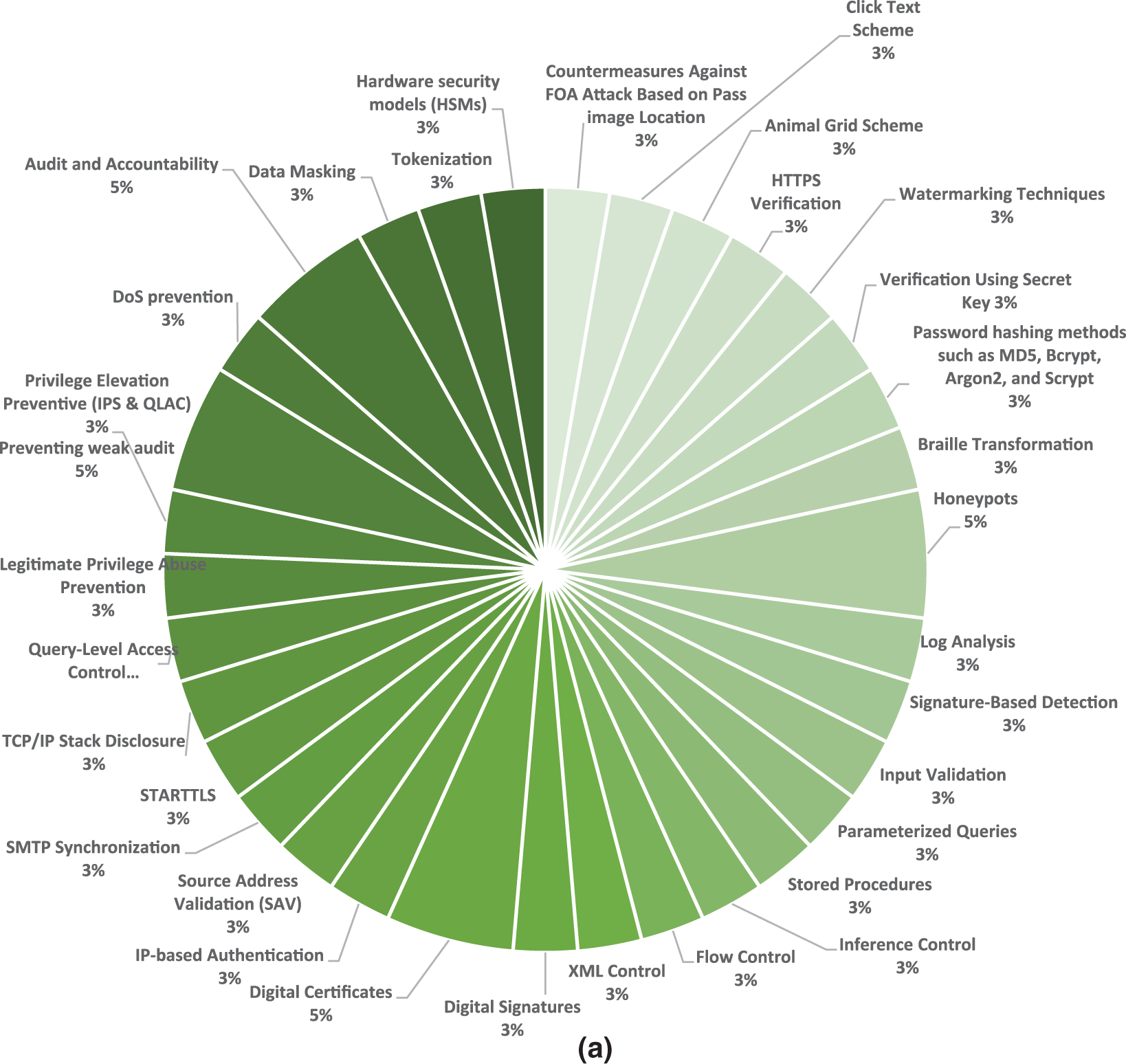
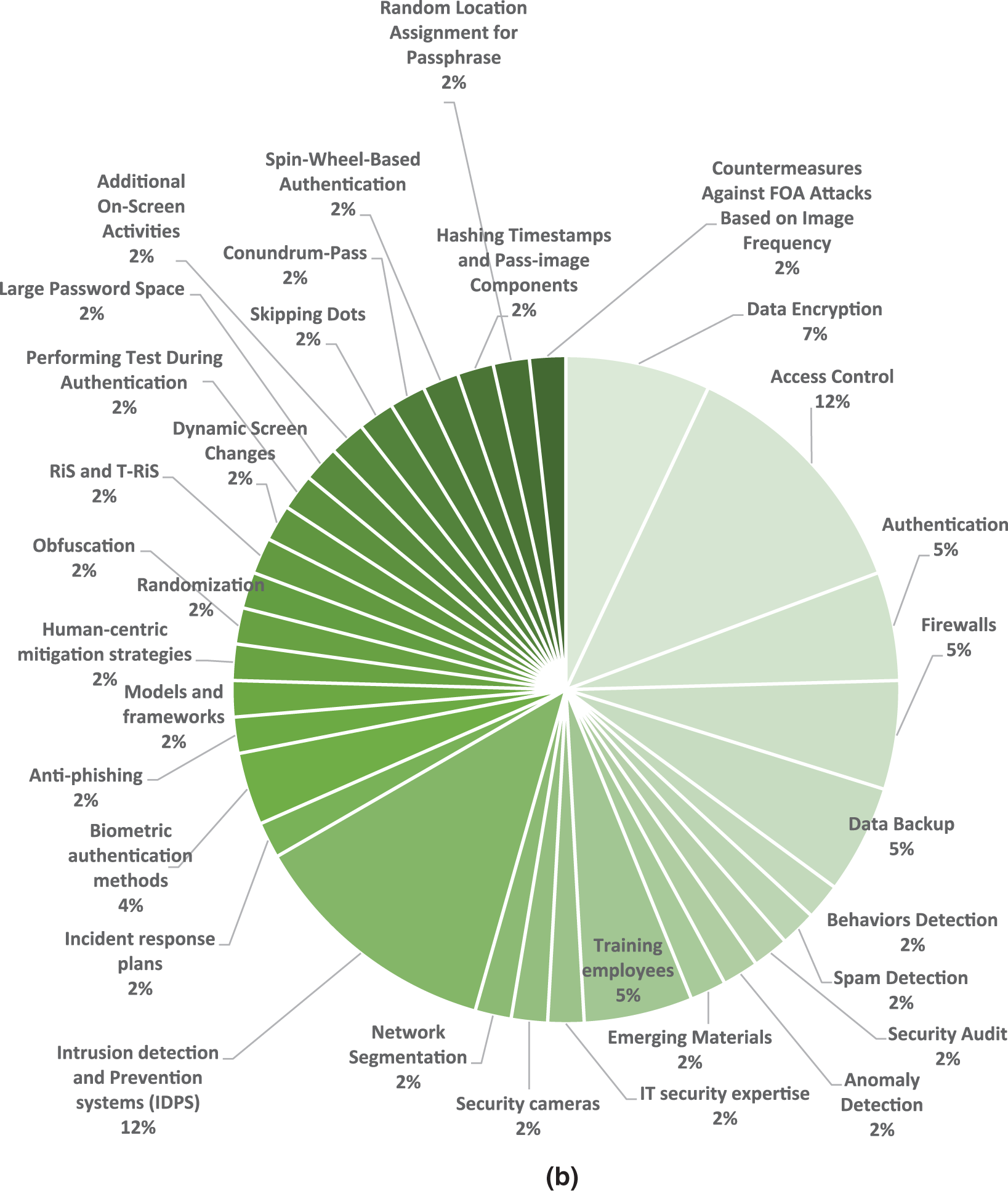
Figure 6: Analysis of classifications of technical security countermeasures

Figure 7: The most common countermeasures in the database systems
While this research offers a comprehensive analysis of cyber risks in database systems, including the classification of threats, vulnerabilities, impacts, and countermeasures, certain limitations warrant consideration. Firstly, cybersecurity threats and vulnerabilities are in constant evolution, with new threats emerging continuously. Consequently, the identification and classification of these threats may become outdated. Organizations, scholars, and researchers must therefore remain vigilant in updating their threat investigations to stay ahead of malicious actors. Secondly, cyber threats are often interconnected and may occur simultaneously or in rapid succession. For example, a cybercriminal might initiate a phishing attack to breach database systems, subsequently deploying ransomware once access is gained. In such scenarios, traditional methods of addressing threats in isolation may prove insufficient. Thus, a more holistic approach to threat management is necessary. Lastly, cyber threat classifications typically consider various factors, including attack vectors, attacker motivations, and organizational impact. However, these factors are often complex, as cyber-attacks can have multiple, overlapping motivations and consequences. An attack on a database system, for instance, might be driven by financial gain, political objectives, or personal vendetta. This complexity challenges accurate identification and classification of attacker intentions, necessitating organizational vigilance and adaptability in response. While cyber risk classifications are crucial for effective defense in database systems, organizations, scholars, and researchers must also recognize the associated limitations and challenges.
In the current digital landscape, cyber threats pose the most critical challenges to database management systems, with an increasing number of sophisticated cyber-attacks targeting these systems. The impact of cyber risks on database management systems can be severe, potentially resulting in data loss, reputational damage, and system failure. Consequently, it is crucial to comprehend the behavior of cyber threats on database systems and identify appropriate countermeasures to mitigate their effects. Cyber risk classification and assessment play a vital role in risk management, establishing a significant framework for identifying and responding to cyber threats. Risk assessment facilitates understanding the impact of cyber threats and developing suitable security controls for risk mitigation. This study presents a comprehensive analysis of cyber risks in database management systems, including the classification of threats, vulnerabilities, impacts, and countermeasures. This classification aids in understanding the appropriate security controls required to mitigate cyber risks for each type of threat.
The study’s findings revealed that SQL injection attacks and DoS attacks were the most prevalent technical threats to database systems, each accounting for 9% of observed threats. Vulnerable audit trails, intrusion attempts, and ransomware attacks were identified as the second tier of technical threats, representing 7%, 7%, and 5% of threats, respectively. Additionally, insider threats emerged as the most common non-technical threat to database systems, constituting 5% of observed threats. Furthermore, the results indicated that weak authentication, unpatched databases, weak audit trails, and multiple usage of a single account were the most frequent technical vulnerabilities in database systems, each accounting for 9% of observed vulnerabilities. The second tier of security vulnerabilities included software bugs, insecure coding practices, weak security controls, insecure networks, password misuse, weak encryption practices, and inadequate data masking, each representing 4% of observed vulnerabilities.
The classification framework presented in this study serves as a vital tool for practitioners, policymakers, and researchers to identify, classify, and mitigate cyber threats within database systems. This research provides a comprehensive analysis of the classification of cyber threats, vulnerabilities, impacts, and countermeasures in database systems. The findings from this work can assist organizations in understanding the types of cyber threats and developing robust strategies against cyber-attacks.
Acknowledgement: Not applicable.
Funding Statement: This work was supported by the Deanship of Scientific Research, Vice Presidency for Graduate Studies and Scientific Research, King Faisal University, Saudi Arabia (Grant No. KFU242068).
Author Contributions: Study conception and design: Mohammed Amin Almaiah, Leen Mohammad Saqr, Leen Ahmad Al-Rawwash, Layan Ahmed Altellawi, Romel Al-Ali, Omar Almomani; data collection: Mohammed Amin Almaiah, Leen Mohammad Saqr, Leen Ahmad Al-Rawwash, Layan Ahmed Altellawi, Romel Al-Ali, Omar Almomani; analysis and interpretation of results: Mohammed Amin Almaiah, Leen Mohammad Saqr, Leen Ahmad Al-Rawwash, Layan Ahmed Altellawi, Romel Al-Ali, Omar Almomani; draft manuscript preparation: Mohammed Amin Almaiah, Leen Mohammad Saqr, Leen Ahmad Al-Rawwash, Layan Ahmed Altellawi, Romel Al-Ali, Omar Almomani. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Y. Wang, J. Xi, and T. Cheng, “The overview of database security threats’ solutions: Traditional and machine learning,” J. Inf. Secur., vol. 12, no. 1, pp. 34–45, 2021. doi: 10.4236/jis.2021.121002. [Google Scholar] [CrossRef]
2. V. Abdullayev and A. S. Chauhan, “SQL injection attack: Quick view,” Mesopotamian J. Cyber Security, vol. 2023, pp. 30–34, 2023. doi: 10.58496/MJCS/2023/006. [Google Scholar] [CrossRef]
3. H. Omotunde and M. Ahmed, “A comprehensive review of security measures in database systems: Assessing authentication, access control, and beyond,” Mesopotamian J. Cyber Security, vol. 2023, pp. 115–133, 2023. doi: 10.58496/MJCSC/2023/016. [Google Scholar] [CrossRef]
4. R. A. Teimoor, “A review of database security concepts, risks, and problems,” UHD J. Sci. Technol., vol. 5, no. 2, pp. 38–46, 2021. doi: 10.21928/uhdjst.v5n2y2021.pp38-46. [Google Scholar] [CrossRef]
5. X. Pan, A. Obahiaghon, B. Makar, S. Wilson, and C. Beard, “Analysis of database security,” Open Access Library J., vol. 11, no. 4, pp. 1–9, 2024. doi: 10.4236/oalib.1111366. [Google Scholar] [CrossRef]
6. H. Touil, N. El Akkad, K. Satori, N. F. Soliman, and W. El-Shafai, “Efficient braille transformation for secure password hashing,” IEEE Access, vol. 12, pp. 5212–5221, 2024. doi: 10.1109/ACCESS.2024.3349487. [Google Scholar] [CrossRef]
7. V. Bandari, “Enterprise data security measures: A comparative review of effectiveness and risks across different industries and organization types,” Int. J. Bus. Intell. Big Data Anal., vol. 6, no. 1, pp. 1–11, 2023. [Google Scholar]
8. B. Naqvi, K. Perova, A. Farooq, I. Makhdoom, S. Oyedeji and J. Porras, “Mitigation strategies against the phishing attacks: A systematic literature review,” Comput. Secur., vol. 132, 2023, Art. no. 103387. doi: 10.1016/j.cose.2023.103387. [Google Scholar] [CrossRef]
9. Y. Pan and C. Rossow, “TCP spoofing: Reliable payload transmission past the spoofed TCP handshake,” in 2024 IEEE Symp. Security and Privacy (SP), San Francisco, CA, USA, 2024, pp. 4497–4515. [Google Scholar]
10. L. Y. Por, I. O. Ng, Y. L. Chen, J. Yang, and C. S. Ku, “A systematic literature review on the security attacks and countermeasures used in graphical passwords,” IEEE Access, vol. 12, pp. 53408–53423, 2024. doi: 10.1109/ACCESS.2024.3373662. [Google Scholar] [CrossRef]
11. H. Ahmad, I. Dharmadasa, F. Ullah, and M. A. Babar, “A review on C3I systems’ security: Vulnerabilities, attacks, and countermeasures,” ACM Comput. Surv., vol. 55, no. 9, pp. 1–38, 2023. doi: 10.1145/3558001. [Google Scholar] [CrossRef]
12. S. M. Toapanta, O. A. Quimis, L. E. Gallegos, and M. R. Arellano, “Analysis for the evaluation and security management of a database in a public organization to mitigate cyber-attacks,” IEEE Access, vol. 8, pp. 169367–169384, 2020. doi: 10.1109/ACCESS.2020.3022746. [Google Scholar] [CrossRef]
13. E. Altulaihan, M. A. Almaiah, and A. Aljughaiman, “Cybersecurity threats, countermeasures and mitigation techniques on the IoT: Future research directions,” Electronics, vol. 11, no. 20, 2022, Art. no. 3330. doi: 10.3390/electronics11203330. [Google Scholar] [CrossRef]
14. Ö. Aslan, S. S. Aktuğ, M. Ozkan-Okay, A. A. Yilmaz, and E. Akin, “A comprehensive review of cyber security vulnerabilities, threats, attacks, and solutions,” Electronics, vol. 12, no. 6, 2023, Art. no. 1333. doi: 10.3390/electronics12061333. [Google Scholar] [CrossRef]
15. M. A. Almaiah, “A new scheme for detecting malicious attacks in wireless sensor networks based on blockchain technology,” in Artificial Intelligence and Blockchain for Future Cybersecurity Applications, Cham, Switzerland: Springer, 2021, pp. 217–234. [Google Scholar]
16. R. Kumar and R. Goyal, “On cloud security requirements, threats, vulnerabilities and countermeasures: A survey,” Comput. Sci. Rev., vol. 33, pp. 1–48, 2019. doi: 10.1016/j.cosrev.2019.05.002. [Google Scholar] [CrossRef]
17. A. Naguib and K. M. Fouad, “Database security: Current challenges and effective protection strategies,” in 2024 6th Int. Conf. Comput. Informat. (ICCI), Cairo, Egypt, 2024, pp. 120–130. [Google Scholar]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools