 Open Access
Open Access
ARTICLE
Trust Score-Based Malicious Vehicle Detection Scheme in Vehicular Network Environments
1 School of Computer and Information, Anqing Normal University, Anqing, 246133, China
2 State Key Laboratory for Novel Software Technology, Nanjing University, Nanjing, 210023, China
3 Yunnan Key Laboratory of Service Computing, Yunnan University of Finance and Economics, Kunming, 650221, China
* Corresponding Author: Wenming Wang. Email:
Computers, Materials & Continua 2024, 81(2), 2517-2545. https://doi.org/10.32604/cmc.2024.055184
Received 19 June 2024; Accepted 13 September 2024; Issue published 18 November 2024
Abstract
Advancements in the vehicular network technology enable real-time interconnection, data sharing, and intelligent cooperative driving among vehicles. However, malicious vehicles providing illegal and incorrect information can compromise the interests of vehicle users. Trust mechanisms serve as an effective solution to this issue. In recent years, many researchers have incorporated blockchain technology to manage and incentivize vehicle nodes, incurring significant overhead and storage requirements due to the frequent ingress and egress of vehicles within the area. In this paper, we propose a distributed vehicular network scheme based on trust scores. Specifically, the designed architecture partitions multiple vehicle regions into clusters. Then, cloud supervision systems (CSSs) verify the accuracy of the information transmitted by vehicles. Additionally, the trust scores for vehicles are calculated to reward or penalize them based on the trust evaluation model. Our proposed scheme demonstrates good scalability and effectively addresses the main cause of malicious information distribution among vehicles. Both theoretical and experimental analysis show that our scheme outperforms the compared schemes.Keywords
Vehicular network represents a fusion of real-time sensing, communication, and computation that transcends their role as mere transportation. From a consumer’s perspective, they resemble scintillating electronic to in the field of consumer electronics. As a novel paradigm of network application, it has emerged as a focal point of widespread attention and research. Particularly, the advent of 5G technology has ushered in significant transformations and developmental opportunities in this area [1]. By leveraging advanced on-board units equipped with superior sensing, communication, and networking capabilities, vehicles can establish communication links with neighboring vehicles or infrastructures. This enables the widespread dissemination of traffic information [2]. Not only does this convergence of in-vehicle networks improve driving safety and efficiency, but it also revolutionizes urban transportation systems through intelligent traffic management.
Despite offering significant convenience, vehicular networking presents numerous challenges, particularly in security and privacy protection. First, vehicles face difficulties in quickly verifying the accuracy of the shared information. In the event that malicious vehicles deliberately transmit misinformation, the implications may be severe, even endangering drivers’ life. Consequently, it is critical for vehicles to develop a mechanism to monitor and control malicious activities of vehicles [3]. Simultaneously, trust issues arise in communication and collaboration between vehicles. Thus, it is imperative to establish a reliable trust system among devices to prevent malicious device attacks [4]. Additionally, vehicular networks must meet requirements for real-time response, reliability, and scalability to navigate the complex and dynamic traffic conditions [5].
In order to actualize the detection of malicious vehicles, researchers have proposed solutions involving algorithmic models, cryptographic techniques, and identity verification. For example, by dynamically collaborating with the vehicle and the surrounding roadside units, and employing sequential detection algorithms, the accuracy of malicious vehicle identification is enhanced [6]. Building on this, some scholars introduced the Evolutionary Public Goods Game (EPGG) model to detect malicious information. Additionally, a countermeasure against such malicious information is implemented through broadcasting anti-malicious rumor information [7]. To address the potential cross-domain issues in the transmission and sharing of vehicular network data across different regions, a federated detection hierarchical mechanism is proposed. This mechanism facilitates a unified evaluation among devices, expedites identity authentication, and increases the detection accuracy of malicious devices [8]. However, the blockchain in this scheme, aimed at constructing a trust platform, suffers from low detection efficiency and limited scalability. Consequently, it is unsuitable for vehicular network scenarios that require high real-time performance.
In response to the aforementioned issues, this paper proposes an effective trust evaluation mechanism for distributed vehicular networks. This mechanism is intended to counteract the malicious behavior of vehicles spreading misleading messages. Our main contributions are summarized as follows:
(1) We employ a trust aggregation approach, coupled with a trust evaluation model, to calculate initial trust scores for vehicles. Subsequently, we thoroughly analyze vehicle data to refine the trust scores of each vehicle, thereby assessing their credibility. Finally, we introduce cloud supervision systems (CSSs) to verify the authenticity of the information transmitted by vehicles. Malicious vehicles spreading misleading information will be punished, whereas honest vehicles will gain bonus points, thus enhancing the system’s environmental credibility.
(2) To enhance the robustness of the trust mechanism in vehicular networks, we propose a distributed architecture comprising the trusted authority institution (TAI) and CSSs. Among them, TAI is the core node which manages and coordinates the trust evaluation process, CSSs manages system-wide trust evaluation, process addressing various scenarios and requirements. This setup promotes labor division, cooperation, and performance optimization.
(3) To efficiently utilize the resource characteristics of CSSs, we introduce a heartbeat mechanism for their scheduling and load balancing. Through this mechanism, CSSs are allowed to periodically transmit their availability information to TAI, which can then make scheduling decisions for each CSS’s resources. This achieves optimal load balancing and enhances system performance.
The rest of this paper is organized as follows. Section 2 introduces the related work. The system and attack model are presented in Section 3. Section 4 details the specific scheme. A safety proof and analysis are performed in Section 5. An overview of performance evaluation is provided in Section 6. Section 7 discusses the feasibility and limitations of the proposed scheme. Finally, Section 8 concludes the paper.
A. Applications of Trust Management Mechanism
Faced with a growing number of vehicles and diverse service demands, both academia and business are striving to promulgate novel paradigms to enhance road safety by transmitting traffic information via vehicles. Concurrently, a trust management mechanism has emerged as a key solution to prevent malevolent vehicles from spreading false information and harming the system. This mechanism could include three trust models: a Context and Entity-oriented Trust Model [9,10], a Data-oriented Trust Model [11], and a Combined Trust Model [12]. Furthermore, deploying a reputation management mechanism can help establish trust relationships amongst vehicles [13]. Based on this concept, Tian et al. [14] devised a reputation-based architecture, wherein vehicles are necessitated to invest money in reporting accurate traffic events to gain reputation scores. However, this scheme has been identified to have two deficiencies. First, the centralization poses a significant challenge [15]. Without trustworthy Roadside Units (RSUs), the reliance solely on a single central server for traffic information verification risks system paralysis from potential attacks. Trust aggregation through different network paths can help to consolidate a single trust value, enhancing reliability [16]. Therefore, designing a more secure and reliable communication mechanism is crucial to ensure the system’s overall reliability and security. Simultaneously, it is necessary to ascertain how to establish a trustworthy interaction mechanism among vehicles to mitigate malicious behavior more effectively. In summary, trust management mechanisms are pivotal for maintaining the integrity and reliability of vehicular networks.
B. Applications of Blockchain Technology
Considering the centralization dilemmas mentioned above, many academics have explored the blockchain technology as a prospective solution [15,17–19]. In addition, researchers have effectively deployed consortium blockchain to enhance security and privacy in vehicular network information dissemination. For instance, Kang et al. [19] introduced a secure sharing framework based on the consortium blockchain and smart contract technologies. This approach employs a tri-weight subjective logic model to elect data sources, enhancing the credibility of the disseminated data. Chen et al. [20] introduced a trust computation methodology based on collaborative filtering. Using this technique, they considered inter-vehicular interactions and historical data to accurately infer and evaluate trust values, thus enhancing the credibility of the information dissemination. Javaid et al. [21] have employed physical unclonable functions (PUF) and certificates in blockchain protocols, facilitating faster trust management among vehicles. Zhang et al. [22] then established a blockchain-based trust management mechanism to preserve vehicular reputation values. This research enhanced inter-vehicular trust management, bolstering secure information dissemination in vehicular networks. Furthermore, provided by these studies is a solid theoretical foundation and practical guidance for security and trust management in Telematics, which not only demonstrate the potential of blockchain technology in addressing the problems traditional to the field but also experimentally prove its effectiveness in enhancing the security and trustworthiness of data. Yang et al. [23] suggested a decentralized trust management system using Bayesian inference models to validate information, further supporting secure communication. El-Sayed et al. [24] estimated trustworthiness among vehicular entities using a hybrid trust model, ensuring secure and reliable information exchange. Collectively, these studies underscore the potential of blockchain technology in fortifying the security and trustworthiness of vehicular networks.
C. Challenges to Blockchain Technology
Due to its enhanced efficiency and reduced costs, consortium blockchain emerges as a superior choice for scenarios requiring secure vehicular data sharing. Cui et al. [18] introduced a consortium blockchain-based scheme for secure vehicular data sharing, which facilitates efficient traceability and reliable information sharing. They also conceptualized a consensus algorithm based on a trust score model, aimed at improving the quality and reliability of the shared data. Despite the blockchain’s significant advantages, such as secure vehicular data sharing and effective mitigation of information tampering [18–20,22], its immutable mechanism poses challenges. Once data has been appended to a block, altering or removing it becomes difficult. This issue could potentially arise in situations such as erroneous data entry or unintended disclosure of confidential information. Furthermore, blockchain nodes are required to store substantial data, leading to high storage demands and latency issues [25]. This is particularly essential in vehicular networks, where vehicles constantly generate and exchange data. Utilizing blockchain technology for data processing could potentially affect the network’s stability and latency [26]. Qiao et al. [27] emphasized the importance of evaluating both direct and indirect trust, proposing a combined trust evaluation model involving edge servers and data users to improve trust assessment accuracy. Therefore, while blockchain offers promising solutions, its implementation in vehicular networks requires careful consideration of these challenges.
To address the issues outlined above, this paper proposes a trust aggregation authentication scheme, through a trust scoring system model for vehicles. The scheme tackles malicious vehicles dissemination, the single point of failure in centralized trust models, and the high communication and storage overhead in blockchain-based vehicular networks.
3 System Model and Attack Model
The proposed model for preserving vehicular privacy through a trust-score system is depicted in Fig. 1. It is composed of CSSs arrays, TAI, RSUs, and Vehicles (V). The roles of each component are explained below:
CSSs:
They are primarily responsible for monitoring traffic conditions in real-time and collating relevant information. In practice, this responsibility is delegated to the camera-based traffic monitoring system. Leveraging advanced sensors and communication devices, CSSs can capture complex vehicular motion parameters such as location, velocity, and acceleration. CSSs are fully trusted entities capable of withstanding various attacks. They possess ample storage resources and computational power, enabling them to monitor vehicular information promptly and accurately. This capability ensures that traffic conditions are continuously monitored, and relevant data is reliably collected and processed in real-time.
TAI:
This component consists of official entities such as government transportation departments. Its duties include generating public-private key pairs, issuing public keys, and registering vehicular identity information. When a vehicle detects malicious behavior from another, it can report this to the TAI. Subsequently, TAI conducts an initial screening and verification of the reported information before collaborating with CSS to verify the accuracy and timeliness of the information.
V:
They are equipped with communication devices, including Dedicated Short Range Communication (DSRC) and Wireless Access for Vehicular Environment (WAVE), which facilitate communication with their surroundings [28]. These devices can receive and transmit data such as the vehicle’s location, velocity, direction, road conditions, and traffic signals. These data provide essential information about the vehicle’s status and the environmental conditions. Simultaneously, each vehicle incorporates an On-Board Unit (OBU) that serves as the central controller, interfacing with the Electronic Control Unit (ECU) to manage and control the vehicle’s operations.
RSUs:
They are wireless communication devices engineered to enhance intelligent transportation systems. They enable bidirectional data exchange with Cluster Head Vehicles (CHVs), solely relaying CHVs’ information to the TAI. In our scheme, different regions are divided by various RSUs, with interactions between regions conducted through CHVs. The formation of these regions generally utilizes scalable clustering algorithms [29]. It is noteworthy that the selection of clustering algorithms is not the focus of this paper. If you are interested in this topic, you can refer to References [30–33]. Vehicles entering a new region cannot access information from their previous region or the historical data of the new region, ensuring data security. This facilitates the identity verification of vehicles and data encryption without storing any personal information of the users or participate in the authentication operation. Moreover, it functions solely as a relay node. This fundamentally eliminates the risk of crucial data breaches, thus safeguarding the privacy and security of vehicle users.
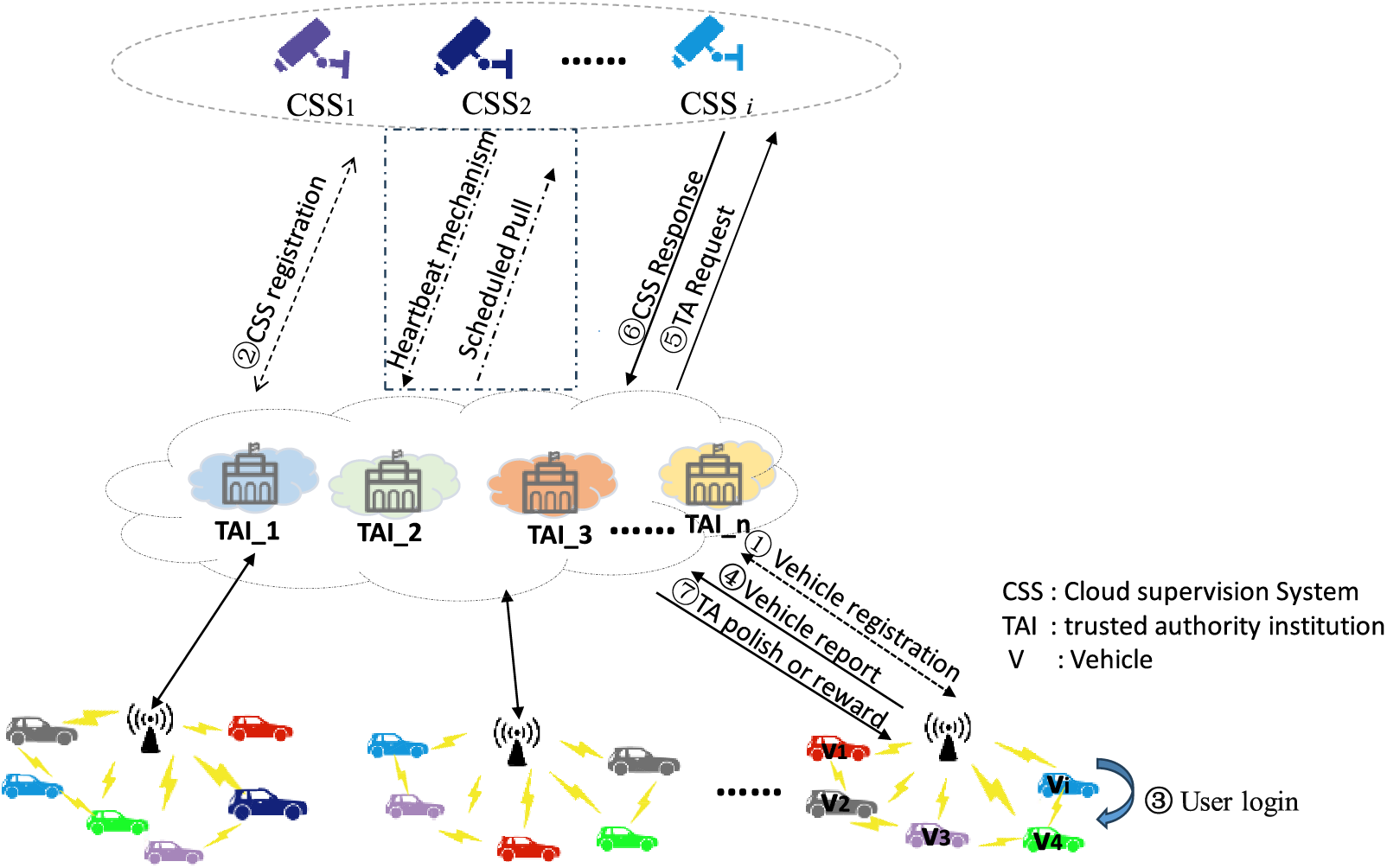
Figure 1: System model
The wireless interaction between V and CSS poses the risk of interception by malicious entities. These attackers may exploit vulnerabilities to steal, manipulate, or engage in impersonation and replay attacks. To address this risk, we employ the established Canetti and Krawczyk’s adversary model (CK-adversary model) [34] as our threat framework. Specifically, in this study, RSU serve solely as intermediaries for message forwarding, without engaging in message storage; the TAI acts as the authenticating body for messages between V and CSS. We make the assumption that both RSUs and TAI are reliable.
The distributed vehicle system model based on trust scoring proposed in this paper must be resistant to various malicious attacks while maintaining reliable performance. The specific requirements are as follows:
(1) Anonymity: It is required to prevent other entities from recognizing the true identity of the vehicle user. Thus, it is necessary to effectively encrypt the identity of the vehicle user during the interaction process to ensure that his or her identity is not compromised.
(2) Traceability: In vehicular communication systems, vehicles exchange information to enable functions such as real-time traffic information sharing and real-time road condition monitoring. To ensure the source and authenticity of the messages, it is crucial that messages sent by vehicles are traceable. Failure to trace messages can pose a potential threat to traffic safety.
(3) Mutual Authentication: It refers to the bidirectional identity verification between vehicles, which aims to confirm the identity and legitimacy of the communicating vehicles. This helps prevent the intrusion and attacks from malicious entities, and ensures communication only with authorized vehicles.
(4) Resistance to Data Replay Attack: It occurs when an attacker intercepts and replays legitimate vehicle control commands, leading to misleading and potentially dangerous vehicle operations. Furthermore, the attacker can manipulate location information and road condition data, disrupting the cooperative work and decision-making processes of the vehicle network, and potentially resulting in a chaotic vehicle network system. To mitigate this attack, the inter-entity interaction verification is employed in this paper.
(5) Timed Heartbeat Mechanism and Pull Services: To maximize utility, CSS entities are scheduled to send availability messages to TAI before a vehicle sends a request. Additionally, TAI is scheduled to pull the list of CSS services to verify their availability.
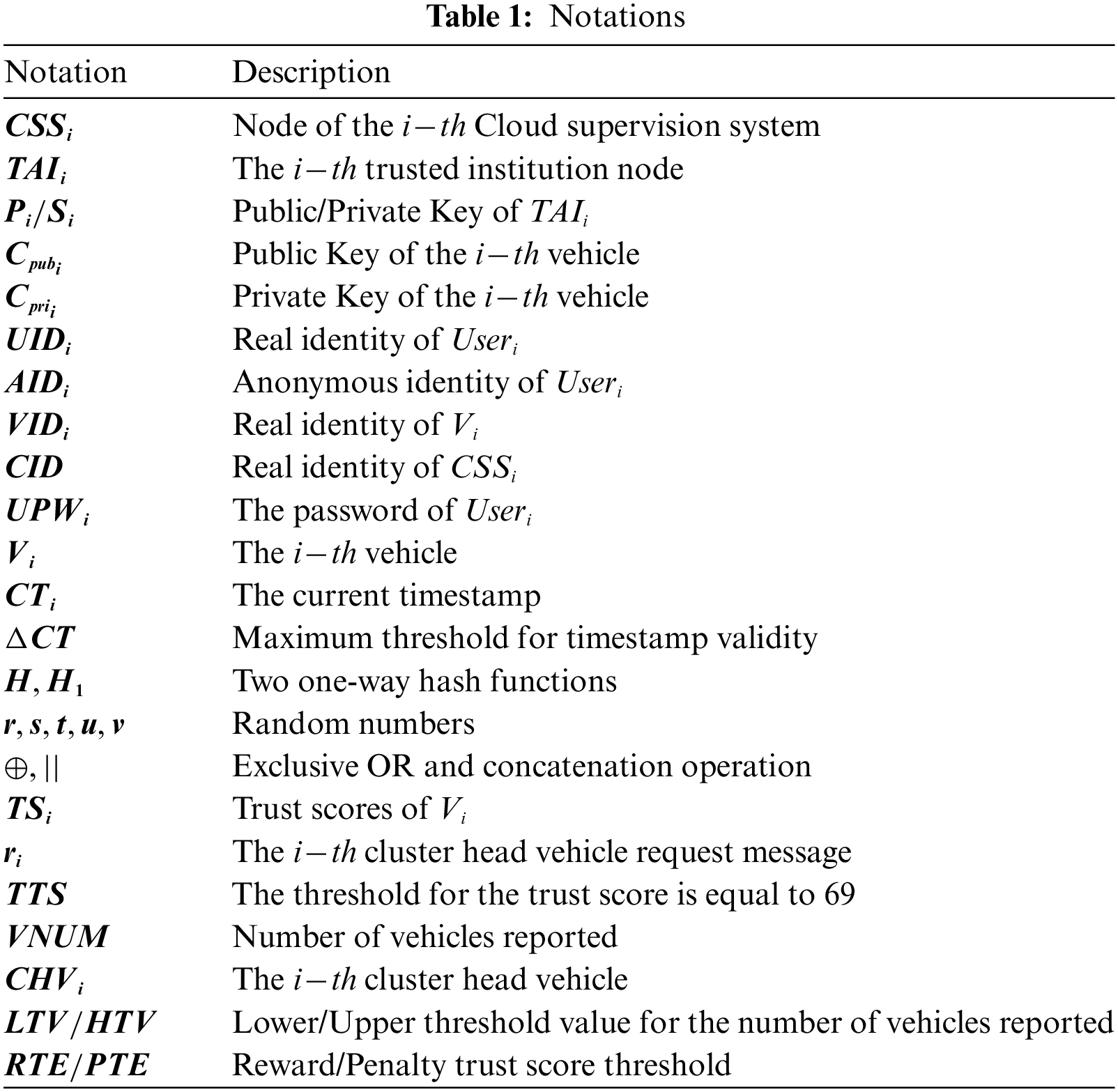
In this section, we will introduce the proposed scheme from four phases: 1) System initialization phase; 2) Registration phase; 3) User login phase; and 4) Trust score update phase. Table 1 shows the notations of the proposed scheme.
4.2 System Initialization Phase
In this phase, the
To participate in the trusted traffic system,
Registration of the vehicle is essential for accessing various services and ensuring personal safety. Fig. 2 schematically represents the vehicle registration process.
(1) Initially, the user
(2) Upon receiving the parameters,
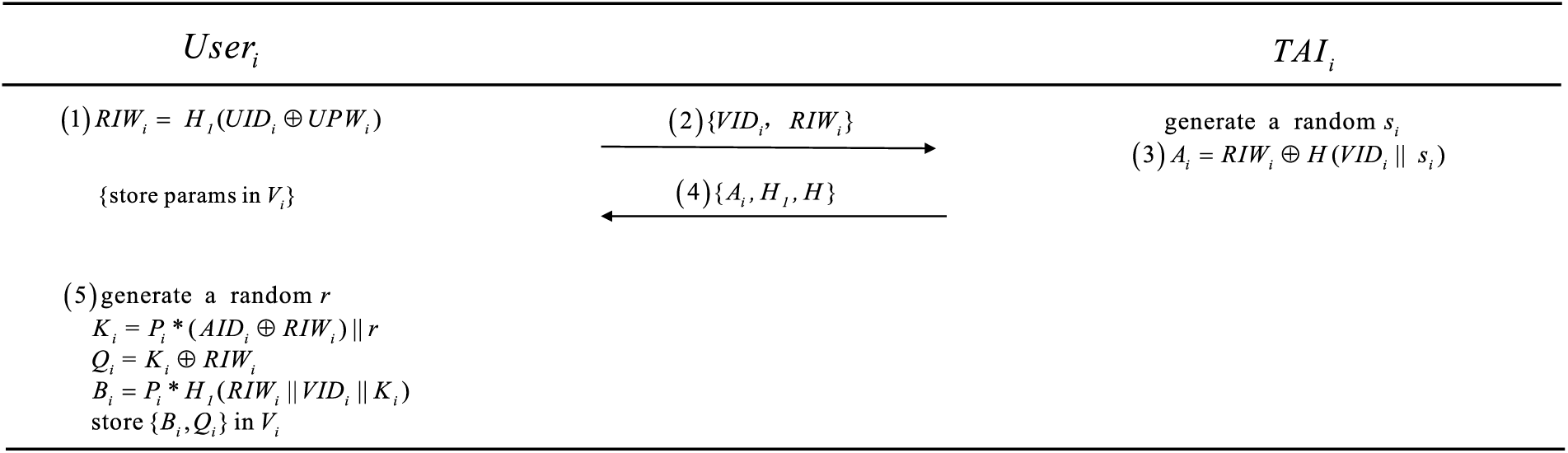
Figure 2: Vehicle registration phase
4.3.2 Cloud Supervision System Registration
Fig. 3 depicts the interaction process between the CSS and TAI. Each service provider in CSS, identified as
(1)
(2) After receiving the parameters from
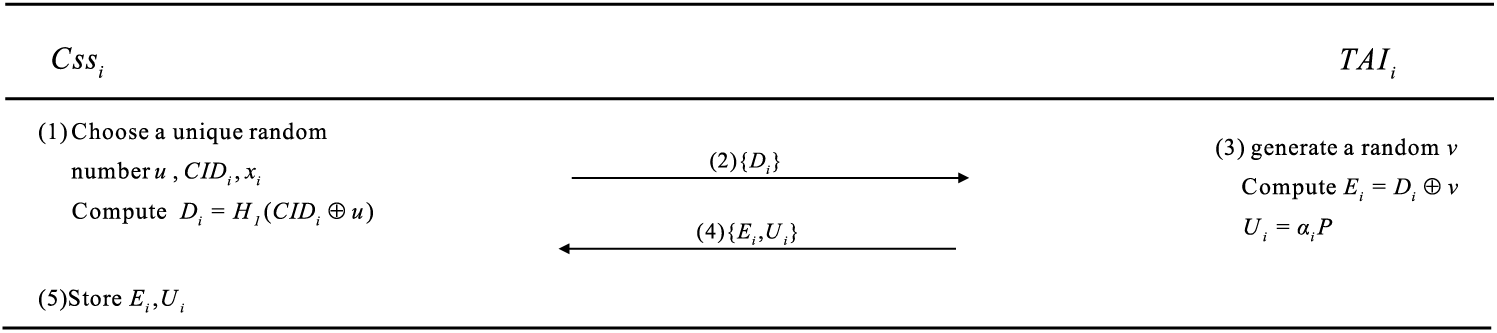
Figure 3: Cloud supervision system registration phase
Fig. 4 illustrates the steps for a user to log into the vehicle system. This process ensures the legitimacy of the user’s identity and the system’s security.
(1)
(2) After receiving the message from
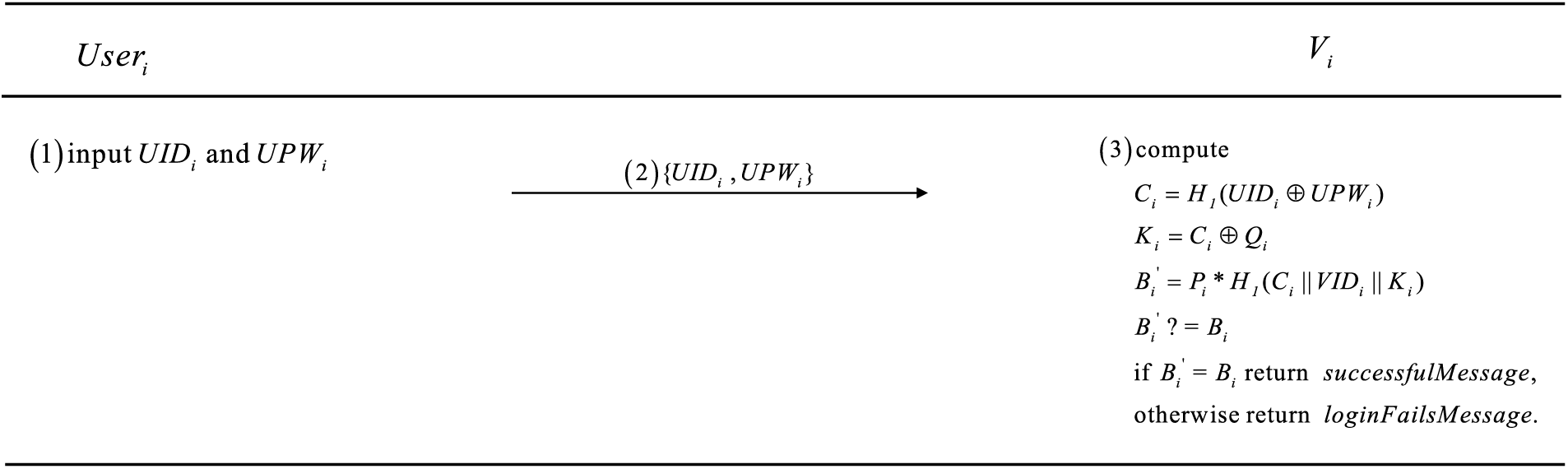
Figure 4: User login phase
Legitimate vehicles send report information to
4.5.1 Inter Vehicle Authentication and Key Agreement
(1) First, the vehicles are required to establish initial trust by exchanging messages (
(2) To be specific,
(3) The delivery rate (DR) [36], effective propagation rate (EPR), and safety-distance information rate (SDIR) [37] are the three key metrics used to calculate a vehicle’s trust score. The higher these three metrics are, the more reliable the vehicle is and the higher the score. Conversely, vehicles with low metrics are indicative of serious transmission failures during data transmission. Therefore, the trust level of the affected vehicle should be adjusted downwards to reflect its decreased reliability.
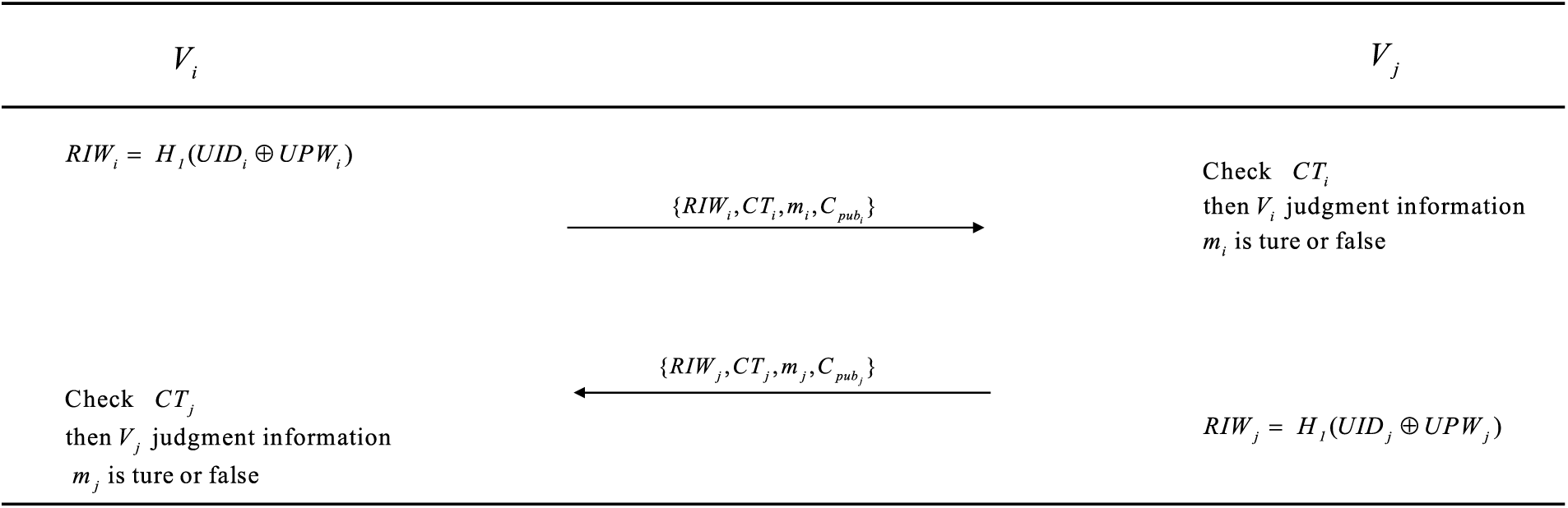
Figure 5: Inter vehicle authentication and key agreement
In the initialization phase, vehicles obtain initial trust through mutual interactions and historical behavior information. To accurately evaluate the trustworthiness of vehicles, our model employs three methods: DR, EPR, and SDIR. When a vehicle’s malicious behavior is reported by another vehicle, the report is first preliminarily screened by the TAI and subsequently verified by the CSS. In this interaction, the CSS is responsible for validating the integrity of the report by comparing it with locally stored data and logs, and then sending its verification results back to TAI for final judgment. If the report is found to be accurate, the TAI rewards the reporting vehicle and penalizes the malicious vehicle by deducting trust points. Conversely, if the report is false and the reported vehicle was wrongly accused, the CSS verifies this, and the vehicle that was falsely accused is rewarded with trust points, while the malicious reporting vehicle is penalized.
(1) The vehicle trust may increase or decrease, depending on the vehicle’s behavior of the vehicle. As illustrated in Fig. 6, vehicle
(2) Upon receiving the requested data from the vehicle,
(3) In Spring Cloud Netflix [38], the registry Eureka [39] is designed to ensure high service availability. In this paper, we adopt a similar approach, using
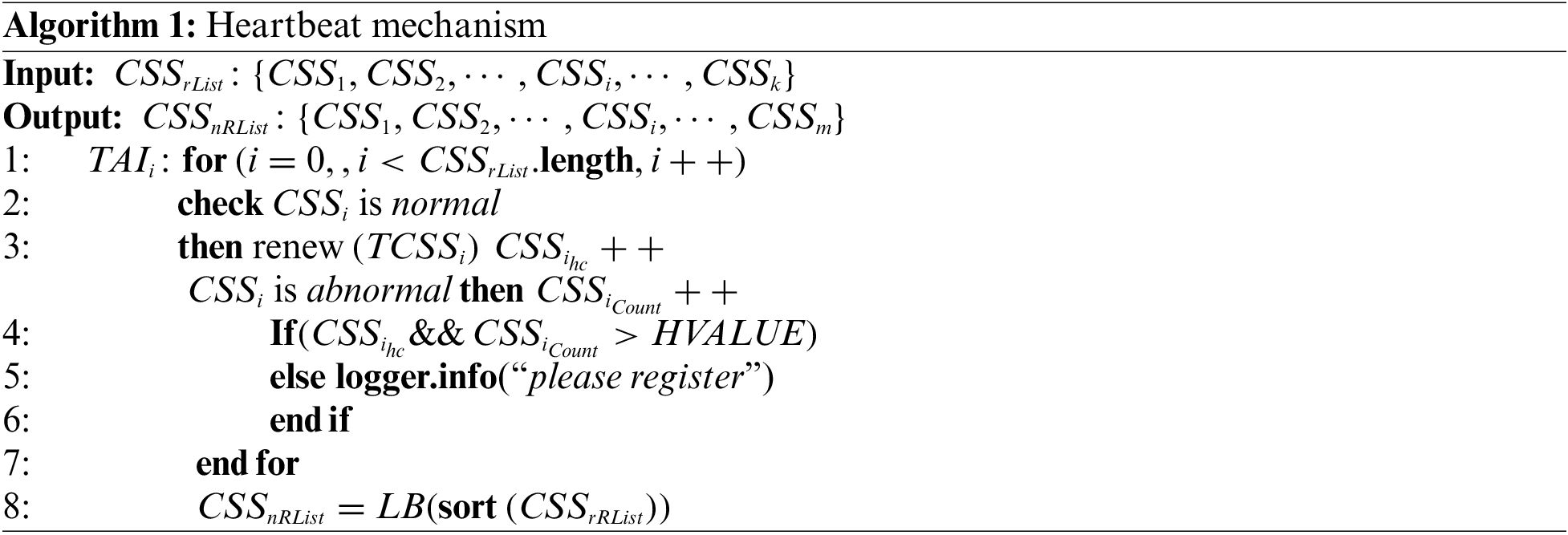
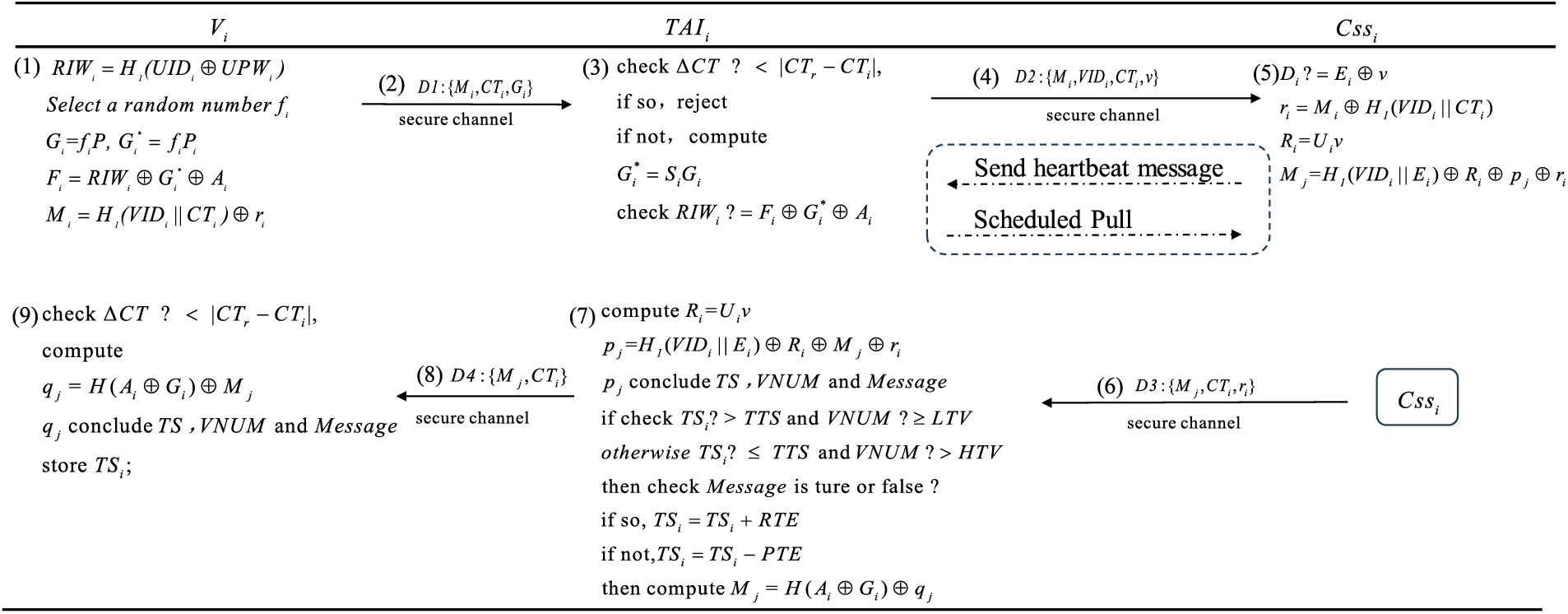
Figure 6: Phase of updating trust scores
To ensure the high availability of
TAI determines the available services list
(4)
(5)
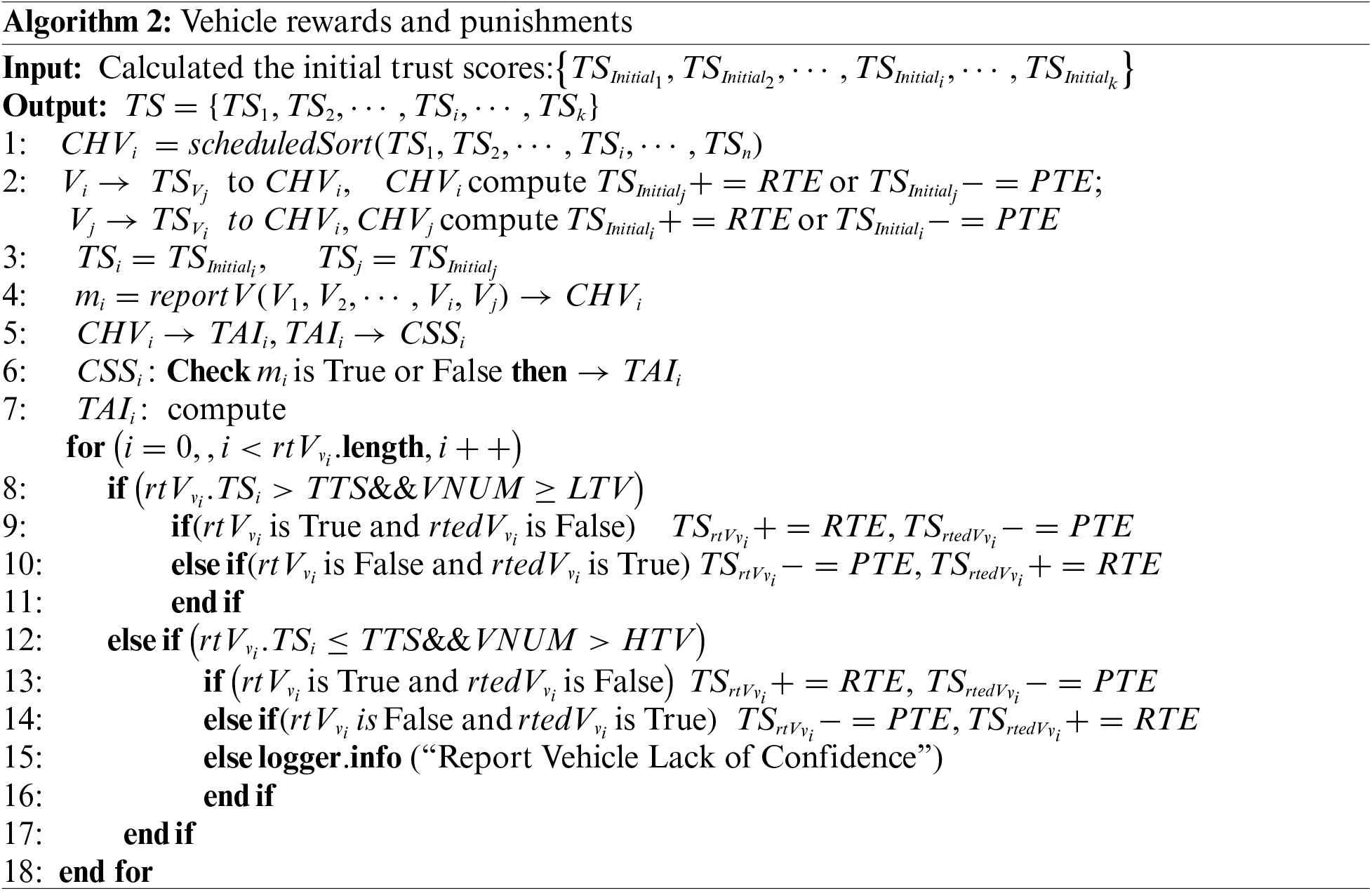
Primarily, the initial trust scores (
Ultimately,
In Algorithm 2, the
(6)
This section mainly analyzes and proves the security of the proposed authentication scheme.
To ensure secure interactions between V and CSS, we have developed a robust security model. Our goal is to ensure the system’s reliability and confidentiality. The model involves three entities: V, CSS, and TAI. We denote their arbitrary instances as
(1) AKA Request: In this scenario, adversary (A) intercepts the information exchanged during the authentication and key negotiation phase among entities
(2) Indirect Request: During this communication, A attempts to intercept and manipulate the message between the parties. In response to this tampering threat, C promptly addresses the situation by replying within the same context.
(3) Private Key Request: In the context of a communication session, A initiates a request to query the session key shared among participating entities. Upon the session’s completion, C securely transmits the session key to A by encrypting the message, and then intercepting a portion of the encrypted transmission.
(4) Test Request: A initiates a query to retrieve interaction information. In response, C assesses the information’s freshness based on the timestamp and validates it through entity encryption. Finally, C returns the appropriately formatted information.
Definition1: Considering the assumption that the successful outcome of A in the game is a polynomial-time problem (PPT), we can conclude that our proposed scheme is deemed to possess absolute security.
Definition2:If the interaction among
The scheme proposed in this paper relies on Diffie-Hellman Challenge (DCH) and Diffie-Hellman Problem (DHP), as below:
Theorem: In response to A’s parameterized request attack, our scheme utilizes the approach of creating pseudo-data resembling the original and validating freshness, thereby guaranteeing the scheme’s efficacy.
Proof: To assess the security of our proposed scheme, we introduce a game between challengers C and opponents A. It is crucial to evaluate any potential vulnerabilities If A can compromise our scheme. During the game, A may initiate the following requests:
Initialization: C Setup List:
(1) AKA Request: When A seeks to inquire about the messages (
(2) Indirect Request: In the given context, A sends a request for
(3) Private Key Request: When A makes a query with
(4) Test Request: Upon receiving a request with
(1) Anonymity: In the vehicular network discussed in this paper, protecting the identity and password of vehicle users from potential theft is considered crucial. To achieve this objective, a hash function derived as
(2) Traceability: The report message sent by each vehicle is attached with its unique identification
(3) Mutual authentication: Messages from vehicle
(4) Resistance to data replay attack: Timestamps are employed in interactions between entities. For instance, upon receiving a message,
(5) Timed heartbeat mechanism and pull services:
6.1 Comparison of Computation Overhead
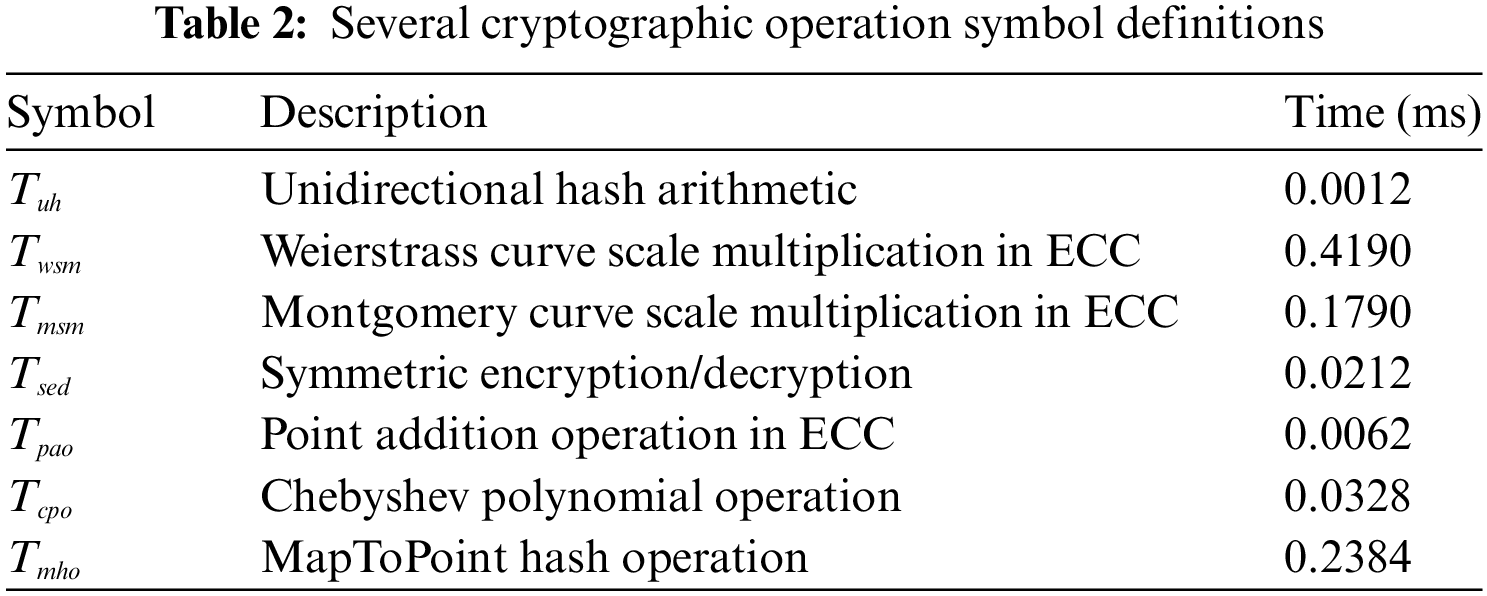
In this subsection, we compare our proposed scheme with three alternative schemes to show its superior performance. Due to resource constraints, we conduct our tests using a personal computer (Lenovo, with an Intel(R) Core(TM) i9-12900H@ 2.50 GHz processor, 16 GB main memory, and the windows11 operation system) to serve as the platforms for the testing of three entities: Vehicle, TAI and CSS. Utilizing the renowned MIRACL library, we execute 5000 iterations of the operations and to obtain the average time required for each. Results are presented in Table 2. The Montgomery curve scalar multiplication
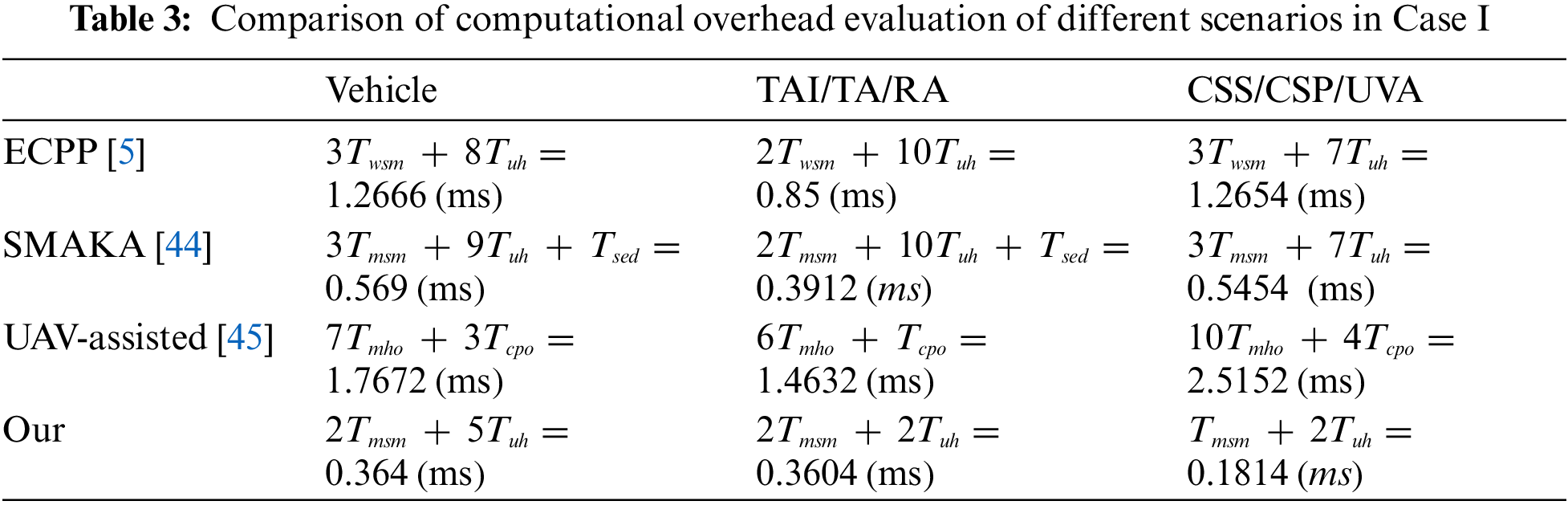
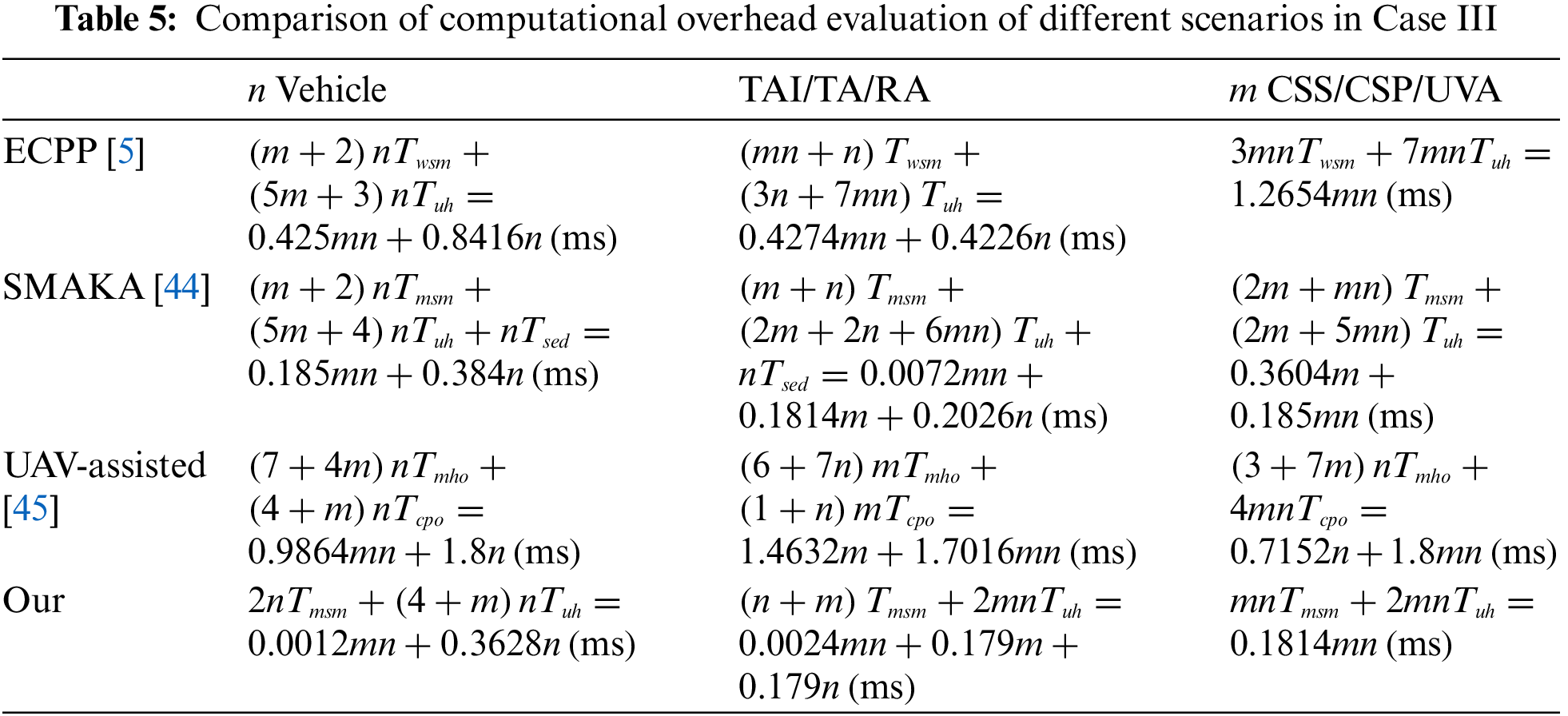
(1) Case I: In this case, a single vehicle interacts solely with a CSS node system. Table 3 illustrates a comparison of the computational overhead between our scheme and three other schemes [5,44,45] across the login, authentication, and key negotiation phases. These compared schemes also adopt a three-layer architecture similar to our scheme. During the login phase in our scheme, the vehicle needs to compute two one-way hash function operations. The authentication and key negotiation phases do not necessitate additional operations. Thus, the computational overhead for the vehicle is
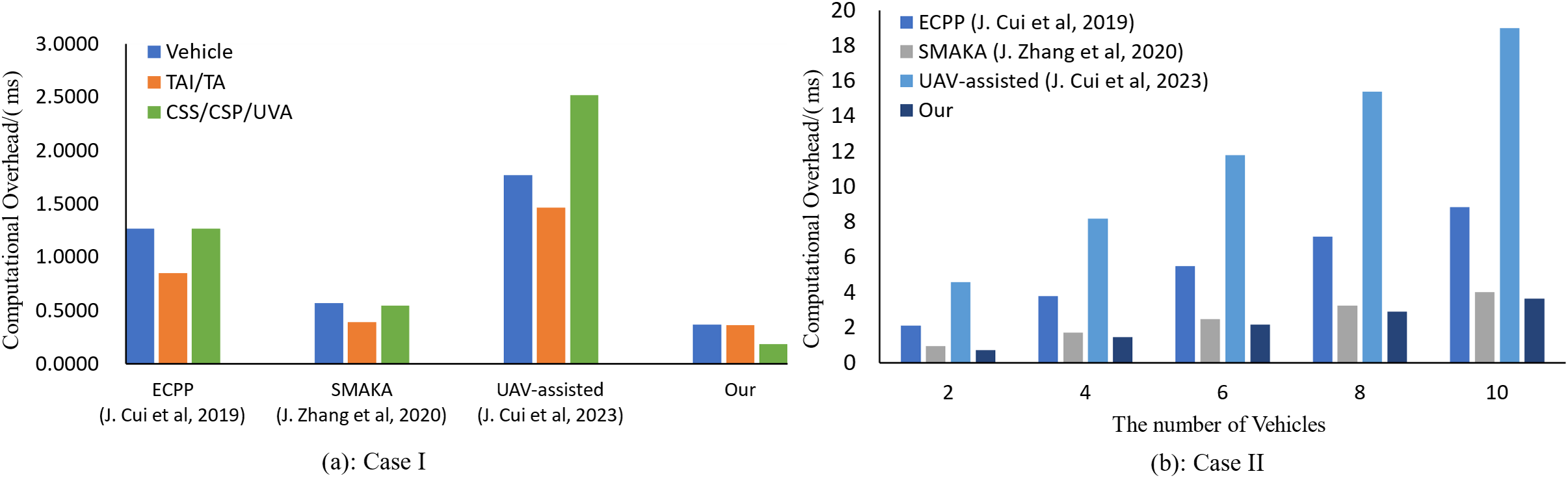
Figure 7: Computational overhead (a Vehicle to a CSS; n Vehicle to a CSS, n from 2 to 10) [5,44,45]
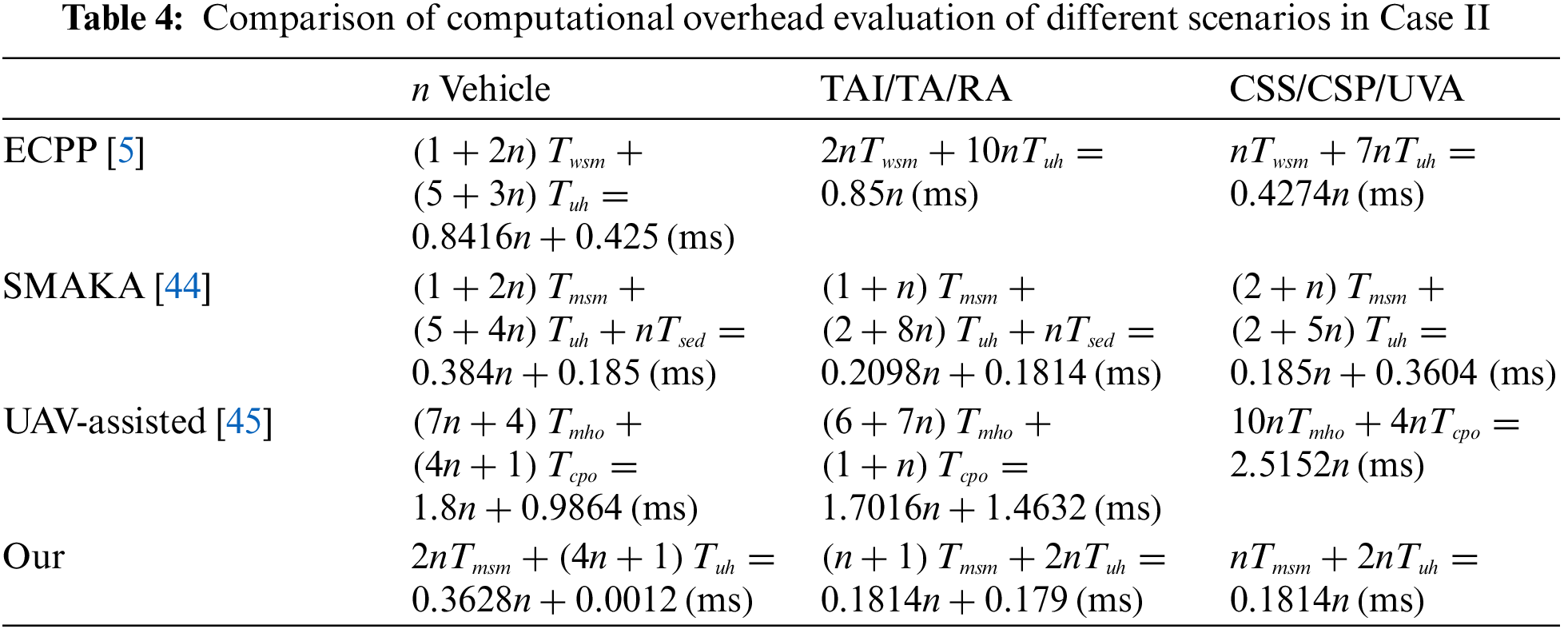
(2) Case Ⅱ: In this case, a single CSS system is interacted with by
(3) Case Ⅲ: In this case,
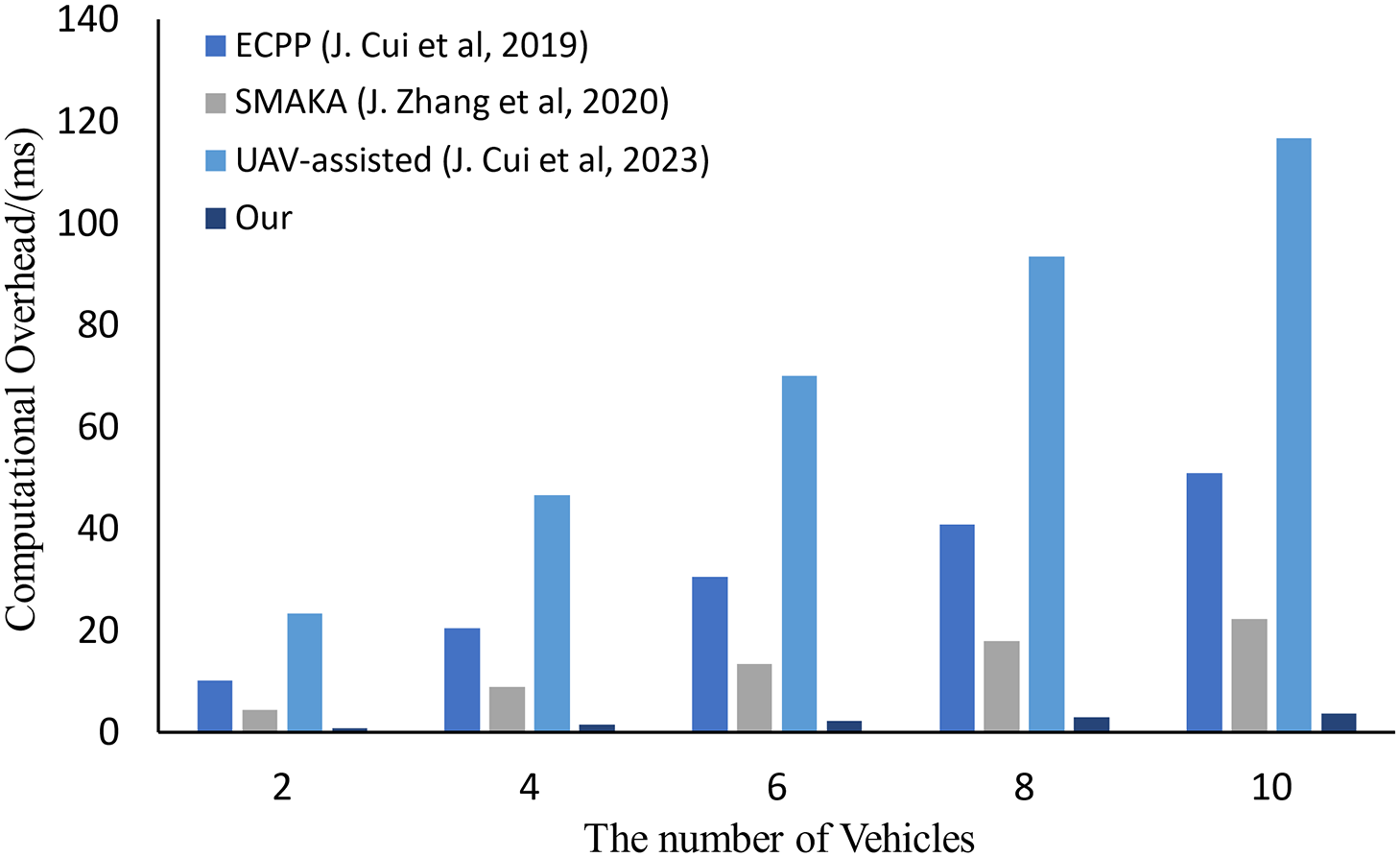
Figure 8: Computational overhead (n Vehicle to m CSS, n from 2 to 10, m = 10) [5,44,45]
The analysis above demonstrates that, our proposed scheme has a lower total computational overhead than the schemes [5,44,45], exhibiting a significant advantage. This reduction in computational overhead enhances the efficiency of the trust evaluation mechanism, making it more suitable for real-time applications in vehicular networks where vehicles have limited computational resources.
6.2 Comparison of Communication Overhead
Initially, we establish an identical security condition, where
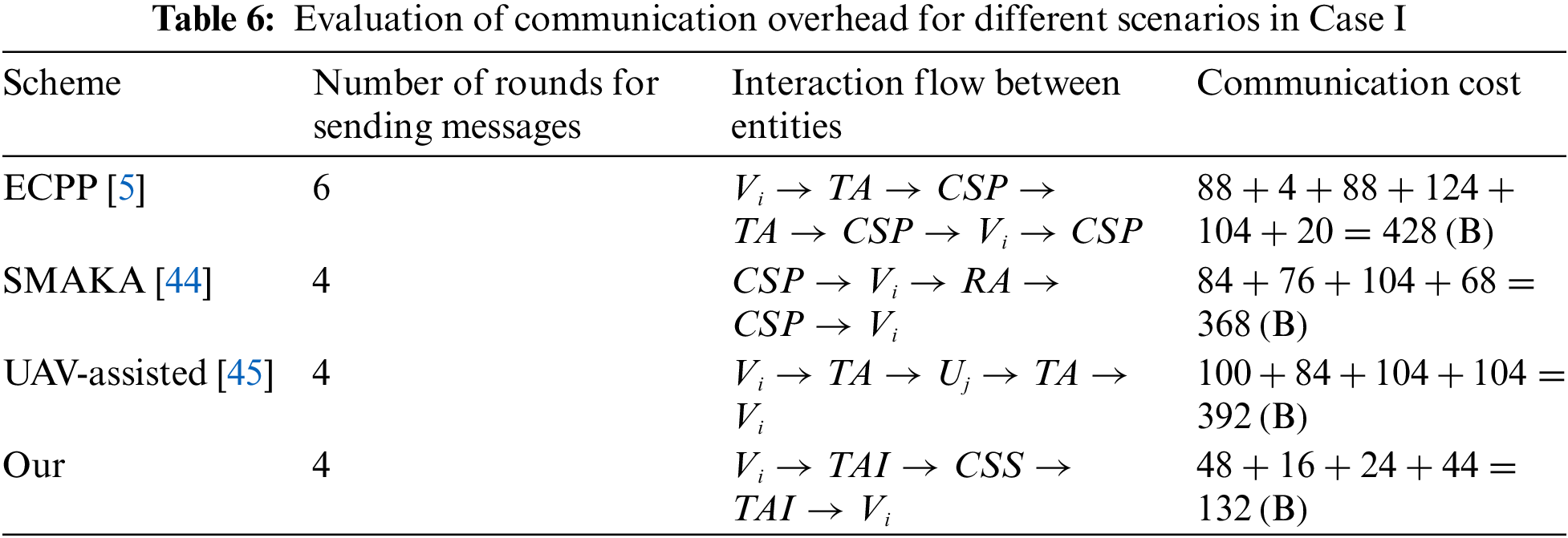
(1) Case I: Table 6 lists the rounds required for a vehicle to send information to the CSS node and the interaction among various entities, and calculates the communication overhead for each process. During the vehicle login, authentication, and key negotiation stages, the proposed scheme requires four rounds of information transmission. These four pieces of information are
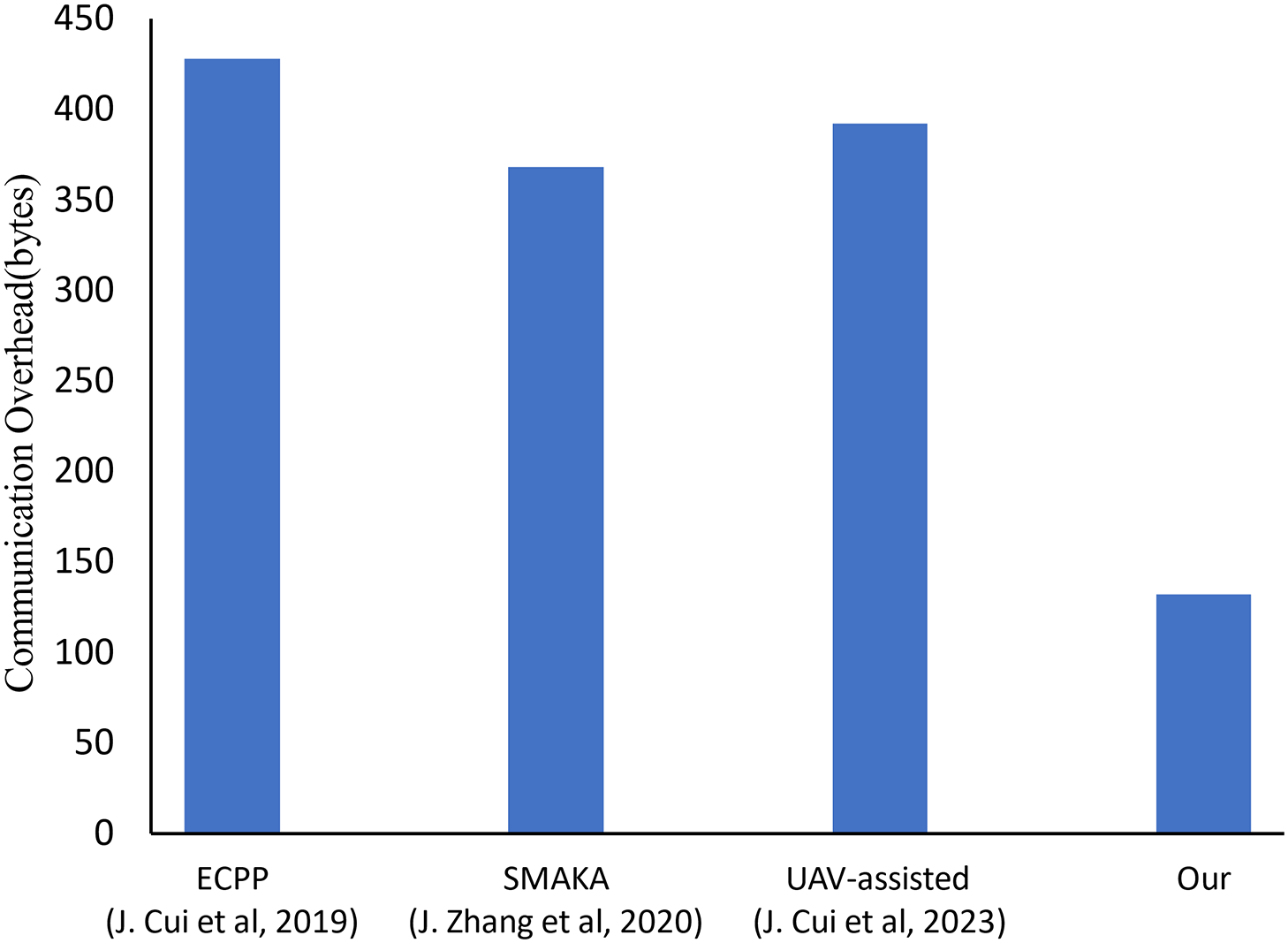
Figure 9: Evaluation of communication overhead for different scenarios (a Vehicle to a CSS) [5,44,45]
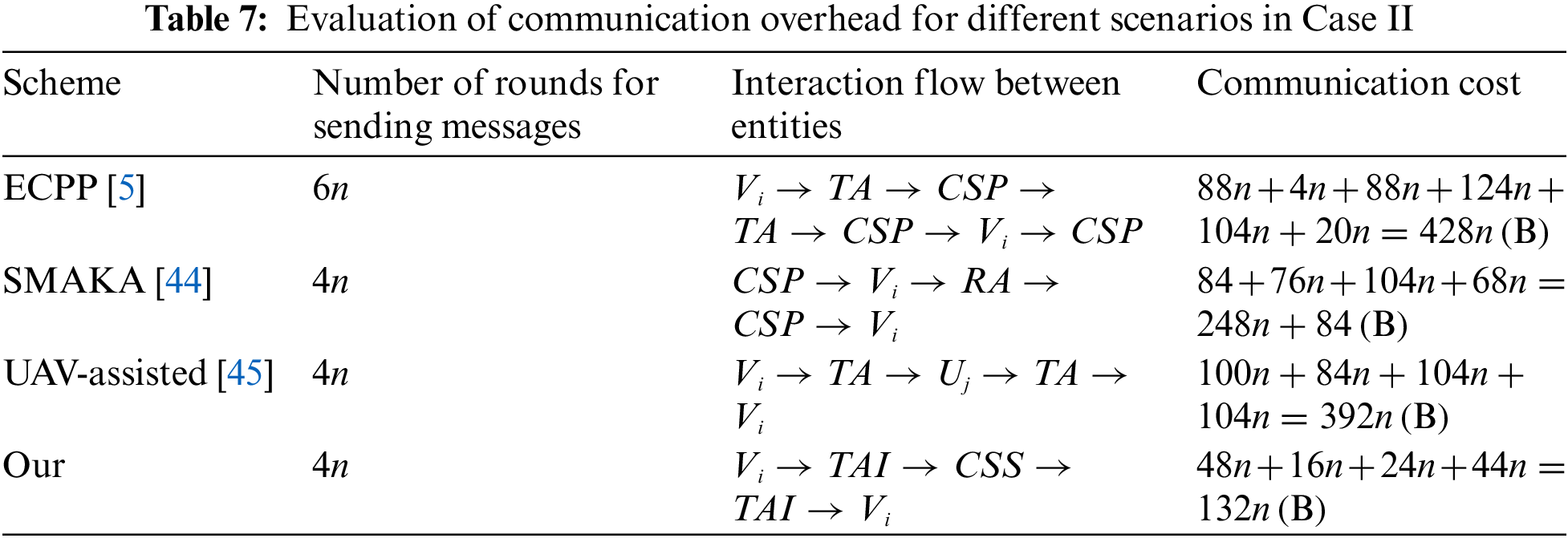
(2) Case Ⅱ: As illustrated in Table 7, the proposed scheme necessitates
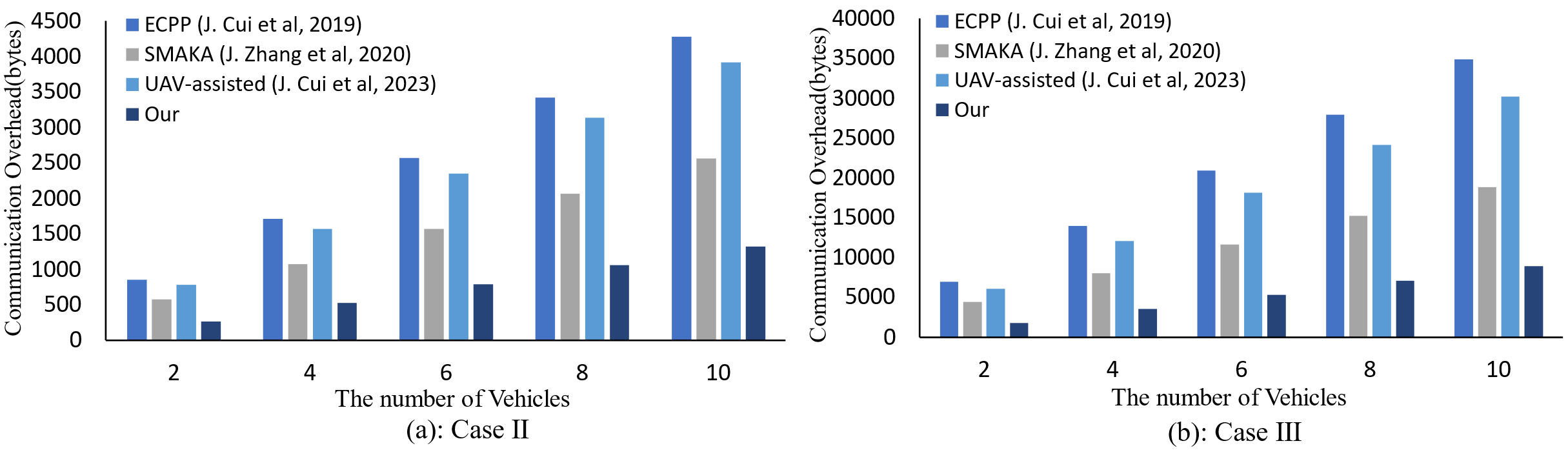
Figure 10: Communication overhead (n Vehicle to a CSS, n from 2 to 10; n Vehicle to m CSS, n from 2 to 10, m = 10) [5,44,45]
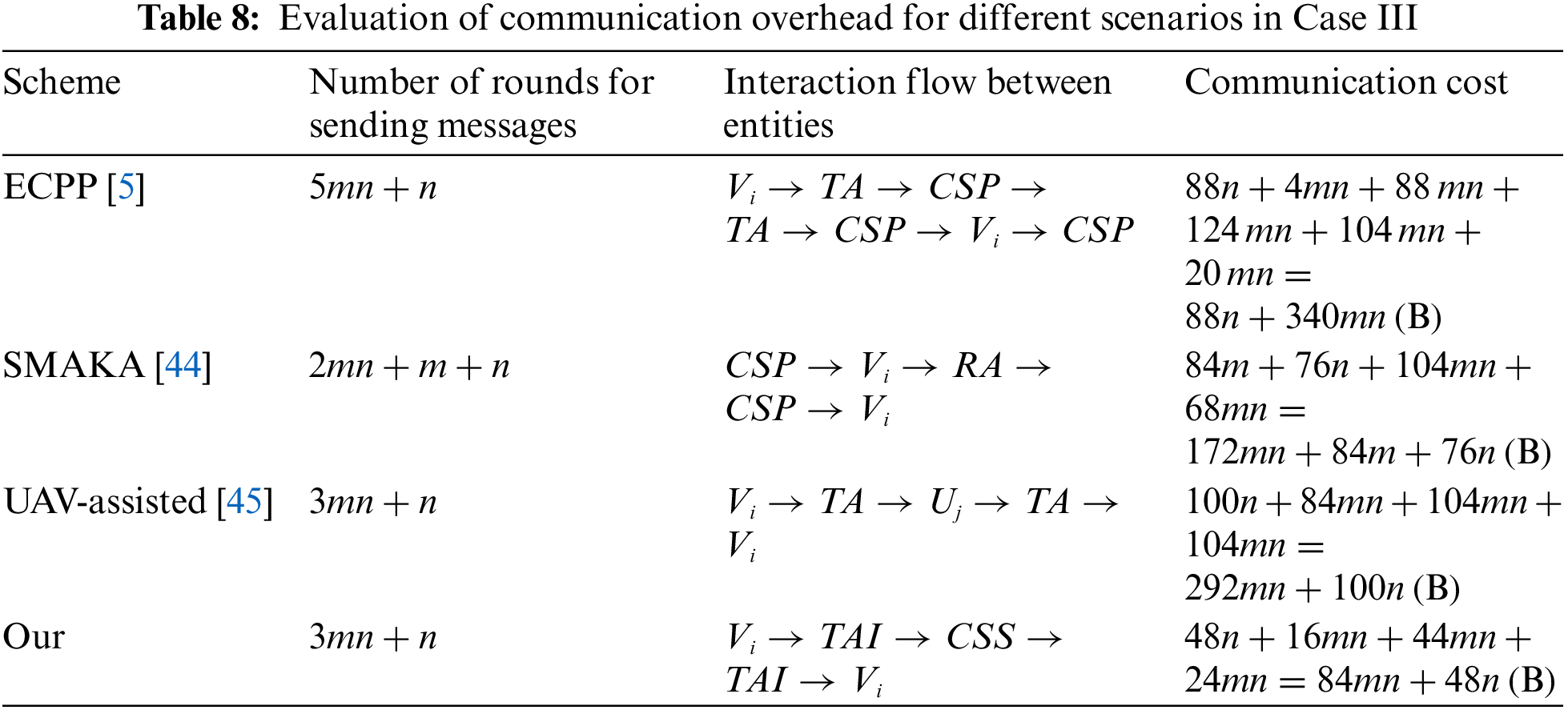
(3) Case Ⅲ: As shown in Table 8, the proposed scheme requires
The above analysis, evidently show that the communication cost of our proposed scheme is lower than that of the related schemes [5,44,45]. This reduction in communication overhead enables the trust evaluation mechanism to handle more nodes and interactions with reduced delay, improving scalability.
6.3 Comparison of Storage Overhead
In system evaluation, storage overhead plays a crucial role. Given that the size of
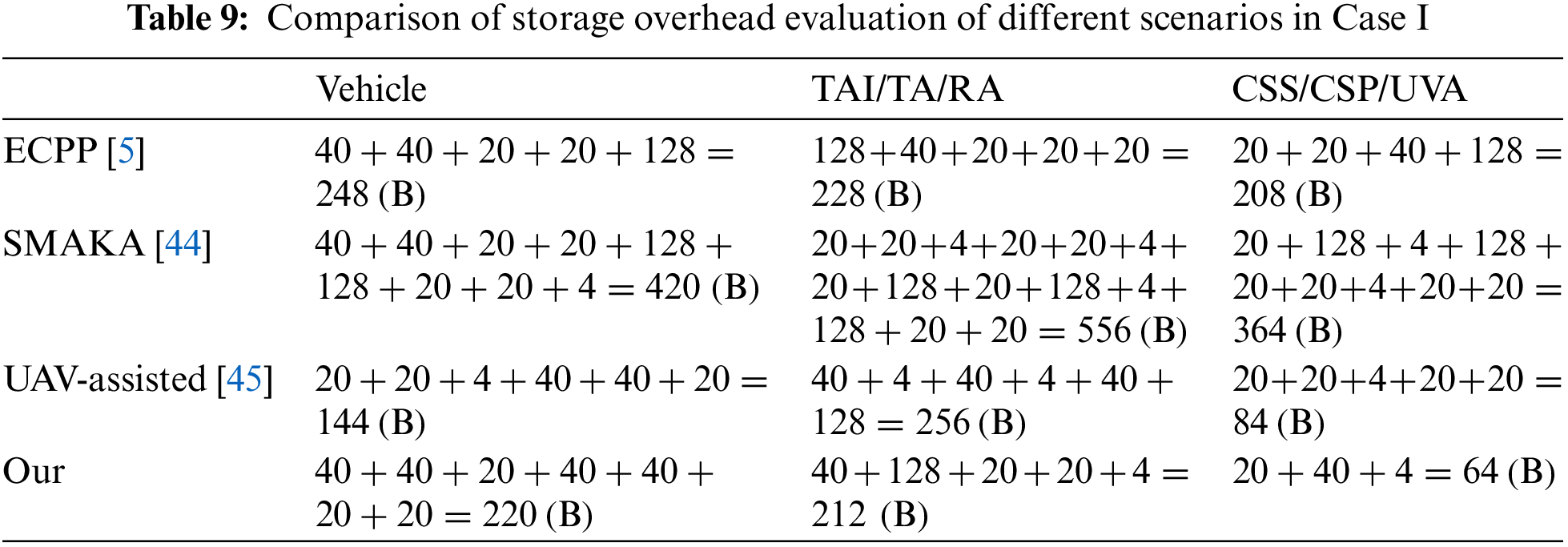
(1) Case I: In this case, a single vehicle interacts with a single CSS node. As shown in Table 9, we compare the storage overhead of our scheme with other schemes during the registration, login, authentication, and key agreement phases. When a vehicle registers with the TAI, it needs to store two parameters encrypted with the TAI’s public key. The parameters required for the login phase are already stored during registration, eliminating the need for additional storage at that stage. For key agreement between vehicles, each vehicle stores the unique identifier and the hashed value of the password for both itself and the interacting vehicle. Additionally, vehicles interacting with the TAI need to store two hash functions,
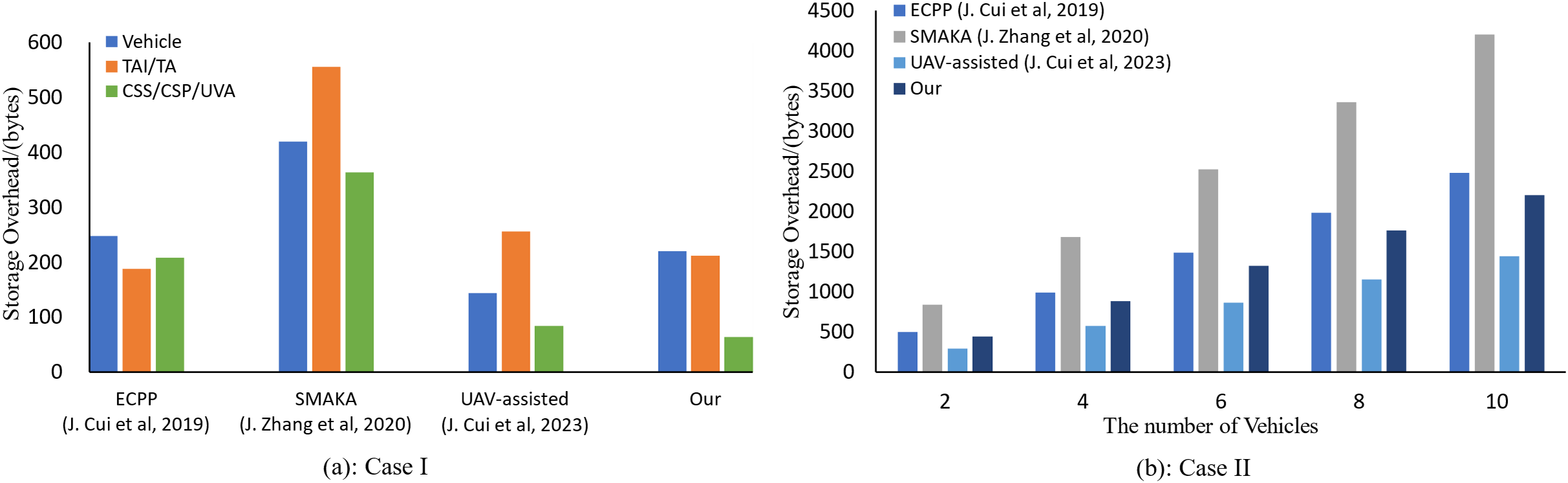
Figure 11: Storage overhead (a Vehicle to a CSS; n Vehicle to a CSS, n from 2 to 10) [5,44,45]
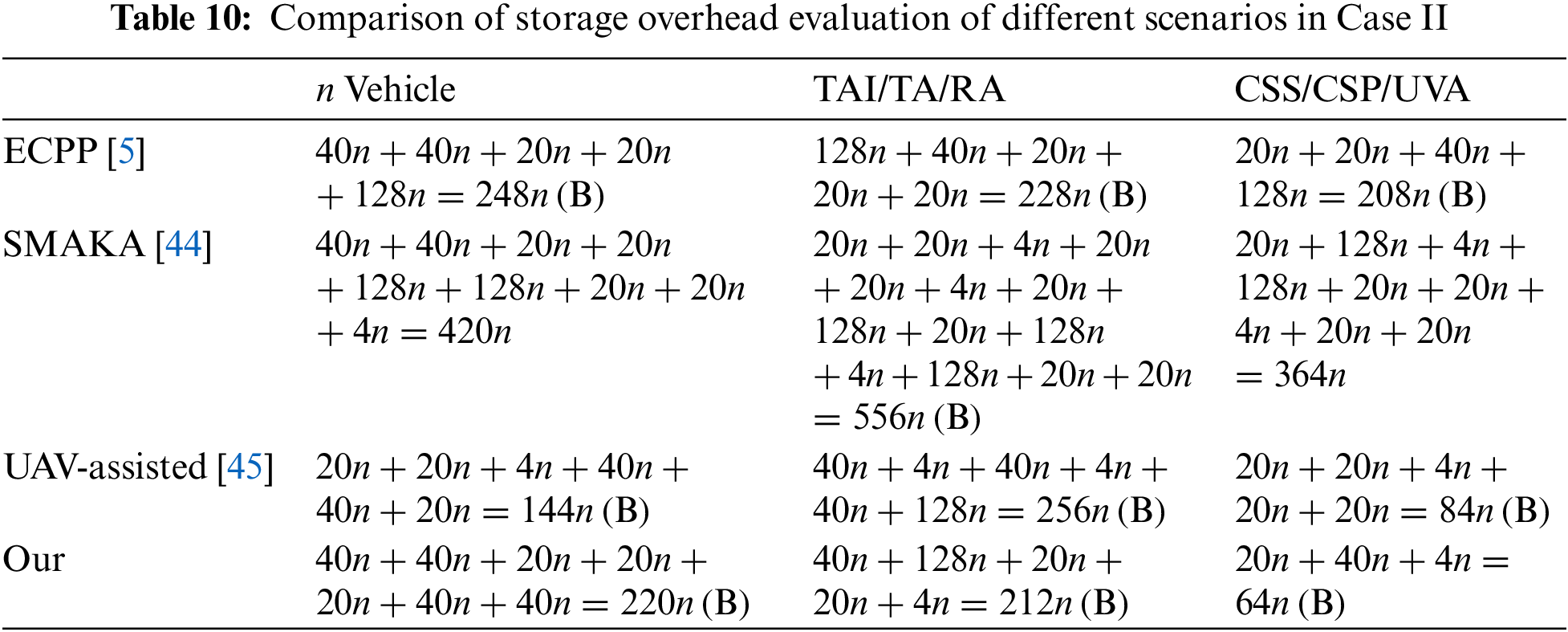
(2) Case Ⅱ: In this case,
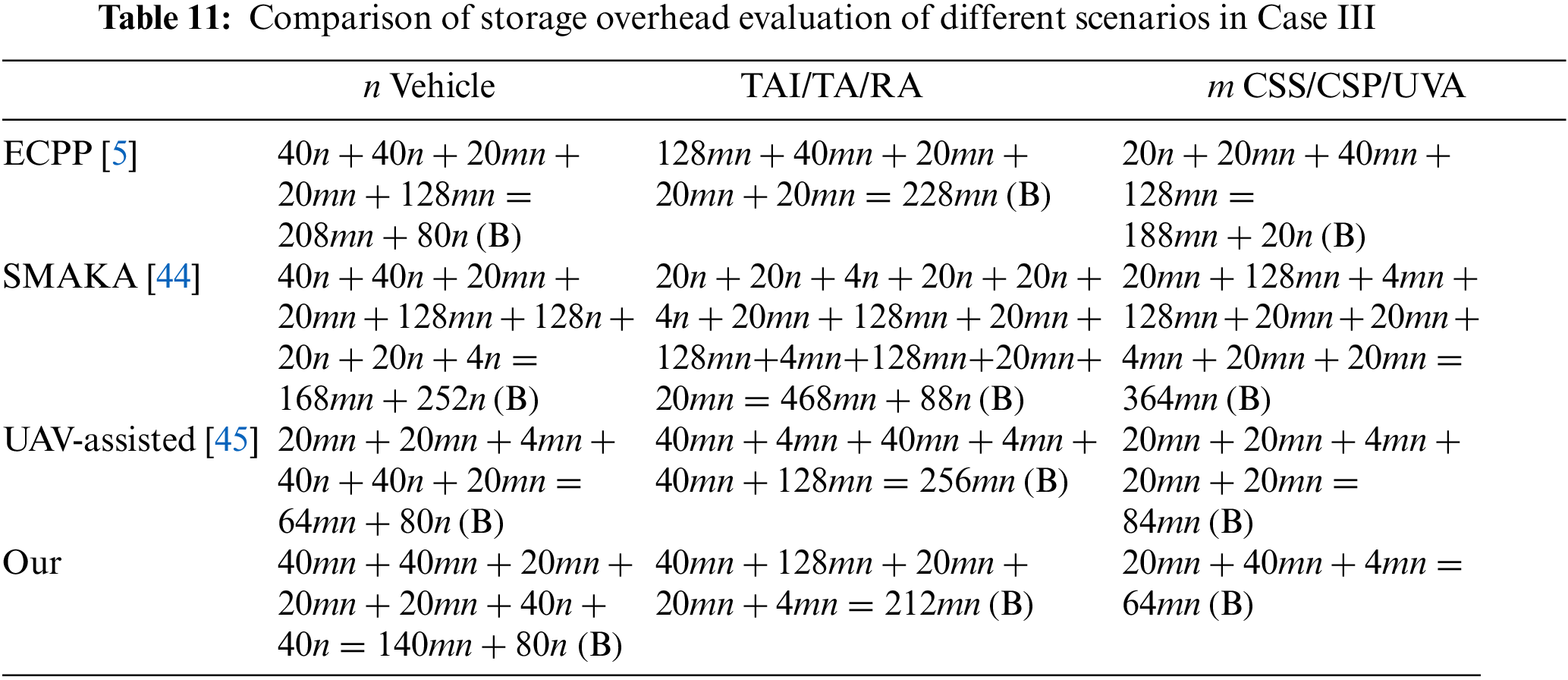
(3) Case Ⅲ: In this case, n vehicles transmit authentication messages to m CSSs. We compare the storage overhead of our proposed scheme with other schemes [5,44,45], focusing on different stages such as registration, login, key agreement, and inter-entity interaction, as shown in Table 11. Given the focus on resource-constrained vehicles in practical environments, we specifically discuss the computational and storage overhead for the vehicle entities. In our scheme, each vehicle is required to store
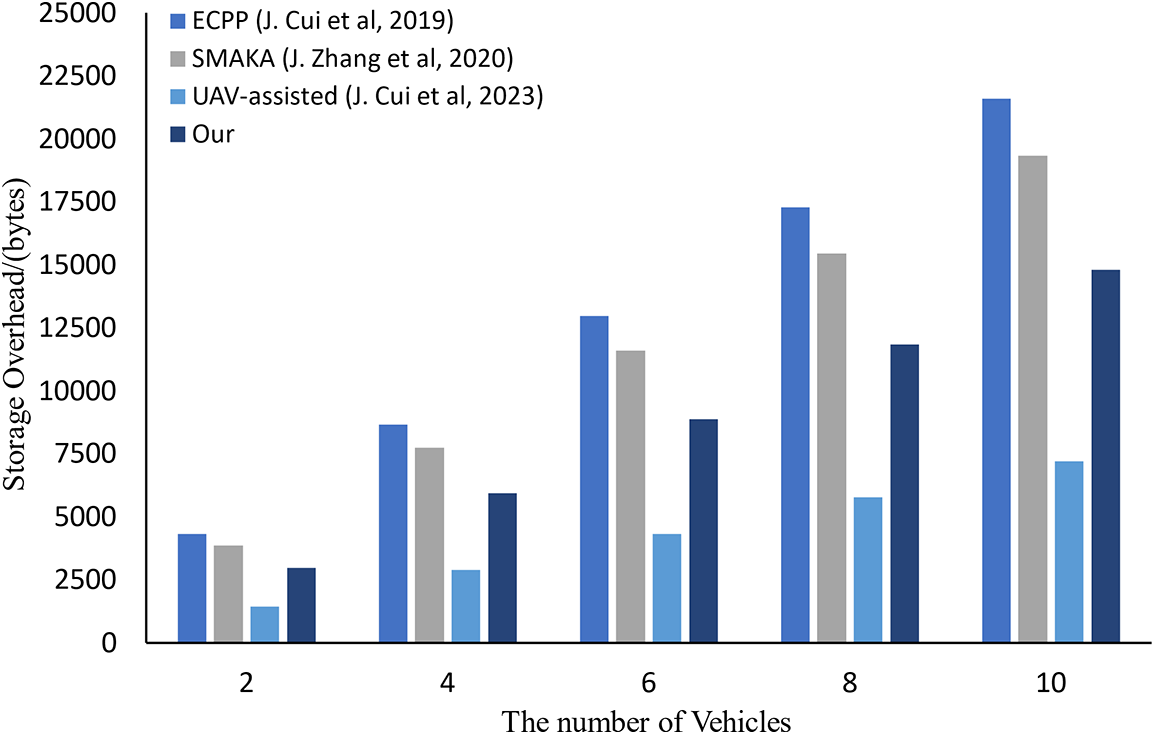
Figure 12: Storage overhead (n Vehicle to m CSS, n from 2 to 10, m = 10) [5,44,45]
The above analysis demonstrates that our proposed scheme offers a significant advantage in terms of total storage overhead. Although the storage overhead on the vehicle side is higher compared to scheme [45], our scheme provides clear benefits over scheme [5] and scheme [44]. Additionally, in terms of storage overhead at the TAI and CSS sides, our scheme performs more efficiently than schemes [5,44,45]. By employing a trust evaluation mechanism, our scheme optimizes storage distribution by focusing on real-time monitoring and dynamic trust updates, reducing the need for excessive data retention. This enhances both the performance and adaptability of the scheme in vehicular networks, particularly in environments where efficient storage use is critical for ensuring security and maintaining trust during real-time communication.
The proposed scheme employs a trust evaluation mechanism, where CSS plays a crucial role in real-time monitoring of road conditions and vehicle interactions. This real-time supervision is vital, as failure to detect malicious behavior can lead to serious security issues. In our scheme, we assume that the CSS is fully trusted. If malicious vehicles attempt to send deceptive information during vehicle-to-vehicle interactions, the reporting vehicle can file a complaint to the CSS via the TAI. Given that the CSS continuously monitors road conditions, both the behavior of the reporting and the reported vehicles will be accurately assessed, minimizing the risks of false positives or negatives. The CSS then applies trust evaluation to reward or penalize the involved vehicles accordingly. This mechanism is essential, as real-time monitoring and punishing malicious vehicles in practical vehicular networks would otherwise entail significant computational, communication, and storage overhead. By utilizing this trust-based approach, our scheme effectively mitigates these challenges, thus fostering a more secure vehicular network environment.
However, in practical scenarios, the assumption of a fully trusted CSS may be limiting, as achieving complete trustworthiness in real-world deployments is challenging. Additionally, vehicular networks are inherently dynamic systems. In our scheme, different regions are managed by distinct RSUs, and interactions between vehicles in different regions are facilitated through cluster head vehicles. Vehicles entering a new region do not have access to the previous interaction data of that region, while vehicles exiting the region no longer have access to subsequent interactions occurring within it. Failure to maintain this boundary could introduce security vulnerabilities. This dynamic nature poses a challenge to the scalability of the scheme, as vehicles frequently enter and exit different regions.
To address these challenges, integrating federated learning with blockchain technology offers a promising solution. Federated learning allows vehicles to collaboratively learn trust models without sharing sensitive data, preserving privacy while improving the accuracy of trust evaluations. Meanwhile, blockchain ensures the integrity and immutability of trust records across different regions, allowing vehicles entering new areas to verify past interactions without accessing the full historical data. This combination enhances the scalability of the scheme by securely managing dynamic vehicle interactions and mitigating trust issues without overloading the network with communication and computational overhead. By leveraging these technologies, our scheme could more effectively handle the inherent dynamism of vehicular networks while maintaining security and efficiency.
This paper proposed a distributed network architecture based on trust scores. It aimed to improve the vehicular network environment by enabling numerous vehicles to report malicious ones disseminating erroneous information to the TAIs. Specifically, vehicles sent reporting information to the TAIs, which then relayed this information to the CSSs for detection. Based on the CSSs’ s detection results, the TAI increased or decreased the trust scores of the reporting and the reported vehicles, thus enhancing the security across the vehicular network. Regarding security, we demonstrated the proposed scheme achieved the security objectives. Compared to other schemes, our scheme had lower computation and communication overhead and exhibited superior scalability. In the future, we will further improve this scheme by using a federated learning-based trust score evaluation mechanism to accommodate more complex scenarios.
Acknowledgement: The authors would like to express our sincere gratitude and appreciation to each other for our combined efforts and contributions throughout the course of this research paper. Thanks to the reviewers and experts of your magazine for their valuable opinions on the article revision.
Funding Statement: This work is supported the by Anhui Provincial Natural Science Foundation under Grant 2308085MF223; in part by the Open Fund of State Key Laboratory for Novel Software Technology under Grant KFKT2022B33; in part by the by the Foundation of Yunnan Key Laboratory of Service Computing under Grant YNSC23106; and in part by the Key Project on Anhui Provincial Natural Science Study by Colleges and Universities under Grant 2023AH050495, 2024AH051078 and Grant KJ2020A0513.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Wenming Wang, Zhiquan Liu, Guijiang Liu; data collection: Zhiquan Liu, Shumin Zhang; analysis and interpretation of results: Wenming Wang, Zhiquan Liu, Guijiang Liu; draft manuscript preparation: Zhiquan Liu, Shumin Zhang. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: Not applicable.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. X. Ge, Z. Li, and S. Li, “5G software defined vehicular networks,” IEEE Commun. Mag., vol. 55, no. 7, pp. 87–93, Jul. 2017. doi: 10.1109/MCOM.2017.1601144; [Google Scholar] [CrossRef]
2. S. Bojjagani, Y. P. Reddy, T. Anuradha, P. V. Rao, B. R. Reddy and M. K. Khan, “Secure authentication and key management protocol for deployment of internet of vehicles (IoV) concerning intelligent transport systems,” IEEE Trans. Intell. Transp. Syst., vol. 23, no. 12, pp. 24698–24713, Sep. 2022. doi: 10.1109/TITS.2022.3207593; [Google Scholar] [CrossRef]
3. L. Song, G. Sun, H. Yu, X. Du, and M. Guizani, “FBIA: A fog-based identity authentication scheme for privacy preservation in internet of vehicles,” IEEE Trans. Veh. Technol., vol. 69, no. 5, pp. 5403–5415, Mar. 2020. doi: 10.1109/TVT.2020.2977829. [Google Scholar] [CrossRef]
4. L. Yang, K. Yu, S. X. Yang, C. Chakraborty, Y. Lu and T. Guo, “An intelligent trust cloud management method for secure clustering in 5G enabled internet of medical things,” IEEE Trans. Ind. Inf., vol. 18, no. 12, pp. 8864–8875, Nov. 2021. doi: 10.1109/TII.2021.3128954. [Google Scholar] [CrossRef]
5. J. Cui, X. Zhang, H. Zhong, J. Zhang, and L. Liu, “Extensible conditional privacy protection authentication scheme for secure vehicular networks in a multi-cloud environment,” IEEE Trans. Inf. Forensics Secur., vol. 15, pp. 1654–1667, Oct. 2019. doi: 10.1109/TIFS.2019.2946933. [Google Scholar] [CrossRef]
6. W. Pi, P. Yang, D. Duan, C. Chen, and H. Li, “Malicious user detection for cooperative mobility tracking in autonomous driving,” IEEE Internet Things J., vol. 7, no. 6, pp. 4922–4936, Feb. 2020. doi: 10.1109/JIOT.2020.2973661. [Google Scholar] [CrossRef]
7. Q. Ding, J. Wang, X. Zhang, and D. K. Sung, “Modeling and characterization of the detection and suppression of bogus messages in vehicular ad hoc networks,” IEEE Trans. Mob. Comput., vol. 22, no. 10, pp. 6027– 6040, Jun. 2022. doi: 10.1109/TMC.2022.3182005. [Google Scholar] [CrossRef]
8. C. Li et al., “Federated hierarchical trust-based interaction scheme for cross-domain industrial IoT,” IEEE Internet Things J., vol. 10, no. 1, pp. 447–457, Aug. 2022. doi: 10.1109/JIOT.2022.3200854. [Google Scholar] [CrossRef]
9. M. Gerlach, “Trust for vehicular applications,” in Proc. 8th Int. Symp. Auton. Decentralized Syst., Sedona, AZ, USA, Jun. 2007, pp. 295–304. [Google Scholar]
10. U. F. Minhas, J. Zhang, T. Tran, and R. Cohen, “Towards expanded trust management for agents in vehicular ad-hoc networks,” Int. J. Comput. Intell. Theory Pract., vol. 5, no. 1, pp. 3–15, Jun. 2010. [Google Scholar]
11. M. Raya, P. Papadimitratos, V. D. Gligor, and J. -P. Hubaux, “On data-centric trust establishment in ephemeral ad hoc networks,” in Proc. IEEE INFOCOM 27th Conf. Comput. Commun., Apr. 2008, pp. 1238–1246. [Google Scholar]
12. F. Dötzer, L. Fischer, and P. Magiera, “VARS: A vehicle ad-hoc network reputation system,” in Proc. 6th IEEE Int. Symp. World Wireless Mobile Multimedia Netw., Jun. 2005, pp. 454–456. [Google Scholar]
13. B. Mokhtar and M. Azab, “Survey on security issues in vehicular ad hoc networks,” Alexandria Eng. J., vol. 54, no. 4, pp. 1115–1126, Dec. 2015. doi: 10.1016/j.aej.2015.07.011. [Google Scholar] [CrossRef]
14. Z. Tian, X. Gao, S. Su, and J. Qiu, “Vcash: A novel reputation framework for identifying denial of traffic service in internet of connected vehicles,” IEEE Internet Things J., vol. 7, no. 5, pp. 3901–3909, May 2019. doi: 10.1109/JIOT.2019.2951620. [Google Scholar] [CrossRef]
15. L. Sun, Q. Yang, X. Chen, and Z. Chen, “RC-chain: Reputation-based crowdsourcing blockchain for vehicular networks,” J. Network Comput. Appl., vol. 176, Feb. 2021, Art. no. 102956. doi: 10.1016/j.jnca.2020.102956. [Google Scholar] [CrossRef]
16. A. Hbaieb, S. Ayed, and L. Chaari, “A survey of trust management in the Internet of Vehicles,” Comput. Networks, vol. 203, Feb. 2022, Art. no. 108558. doi: 10.1016/j.comnet.2021.108558. [Google Scholar] [CrossRef]
17. X. Huang, D. Ye, R. Yu, and L. Shu, “Securing parked vehicle assisted fog computing with blockchain and optimal smart contract design,” IEEE/CAA J. Autom. Sin., vol. 7, no. 2, pp. 426–441, Mar. 2020. doi: 10.1109/JAS.2020.1003039. [Google Scholar] [CrossRef]
18. J. Cui, F. Ouyang, Z. Ying, L. Wei, and H. Zhong, “Secure and efficient data sharing among vehicles based on consortium blockchain,” IEEE Trans. Intell. Transp. Syst., vol. 23, no. 7, pp. 8857–8867, Jun. 2021. doi: 10.1109/TITS.2021.3086976. [Google Scholar] [CrossRef]
19. J. Kang et al., “Blockchain for secure and efficient data sharing in vehicular edge computing and networks,” IEEE Internet Things J., vol. 6, no. 3, pp. 4660–4670, Oct. 2018. doi: 10.1109/JIOT.2018.2875542. [Google Scholar] [CrossRef]
20. J. -M. Chen, T. -T. Li, and J. Panneerselvam, “TMEC: A trust management based on evidence combination on attack-resistant and collaborative internet of vehicles,” IEEE Access, vol. 7, pp. 148913–148922, Nov. 2018. doi: 10.1109/ACCESS.2018.2876153. [Google Scholar] [CrossRef]
21. U. Javaid, M. N. Aman, and B. Sikdar, “A scalable protocol for driving trust management in internet of vehicles with blockchain,” IEEE Internet Things J., vol. 7, no. 12, pp. 11815–11829, Jun. 2020. doi: 10.1109/JIOT.2020.3002711. [Google Scholar] [CrossRef]
22. H. Zhang, J. Liu, H. Zhao, P. Wang, and N. Kato, “Blockchain-based trust management for internet of vehicles,” IEEE Trans. Emerging Top. Comput., vol. 9, no. 3, pp. 1397–1409, Nov. 2020. doi: 10.1109/TETC.2020.3033532. [Google Scholar] [CrossRef]
23. Z. Yang, K. Yang, L. Lei, K. Zheng, and V. C. Leung, “Blockchain-based decentralized trust management in vehicular networks,” IEEE Internet Things J., vol. 6, no. 2, pp. 1495–1505, May 2018. doi: 10.1109/JIOT.2018.2836144. [Google Scholar] [CrossRef]
24. H. El-Sayed, H. Alexander, P. Kulkarni, M. A. Khan, R. M. Noor and Z. Trabelsi, “A novel multifaceted trust management framework for vehicular networks,” IEEE Trans. Intell. Transp. Syst., vol. 23, no. 11, pp. 20084–20097, Nov. 2022. doi: 10.1109/TITS.2022.3187788. [Google Scholar] [CrossRef]
25. J. Tang, X. Lu, Y. Xiang, C. Shi, and J. Gu, “Blockchain search engine: Its current research status and future prospect in Internet of Things network,” Future Gen. Comput. Syst., vol. 138, no. 11, pp. 120–141, Jan. 2023. doi: 10.1016/j.future.2022.08.008. [Google Scholar] [CrossRef]
26. M. Wazid, A. K. Das, and S. Shetty, “TACAS-IoT: Trust aggregation certificate-based authentication scheme for edge-enabled IoT systems,” IEEE Internet Things J., vol. 9, no. 22, pp. 22643–22656, Jun. 2022. doi: 10.1109/JIOT.2022.3181610. [Google Scholar] [CrossRef]
27. F. Qiao, J. Wu, J. Li, A. K. Bashir, S. Mumtaz and U. Tariq, “Trustworthy edge storage orchestration in intelligent transportation systems using reinforcement learning,” IEEE Trans. Intell. Transp. Syst., vol. 22, no. 7, pp. 4443–4456, Jun. 2020. doi: 10.1109/TITS.2020.3003211. [Google Scholar] [CrossRef]
28. S. Abdelhamid, H. S. Hassanein, and G. Takahara, “Vehicle as a resource (VaaR),” IEEE Netw., vol. 29, no. 1, pp. 12–17, Jan. 2015. doi: 10.1109/MNET.2015.7018198. [Google Scholar] [CrossRef]
29. M. Ren, J. Zhang, L. Khoukhi, H. Labiod, and V. Vèque, “A unified framework of clustering approach in vehicular ad hoc networks,” IEEE Trans. Intell. Transp. Syst., vol. 19, no. 5, pp. 1401–1414, Aug. 2017. doi: 10.1109/TITS.2017.2727226. [Google Scholar] [CrossRef]
30. K. Zhang, J. Wang, C. Jiang, T. Q. Quek, and Y. Ren, “Content aided clustering and cluster head selection algorithms in vehicular networks,” in Proc. IEEE Wireless Commun. Netw. Conf. (WCNC), San Francisco, CA, USA, Mar. 2017, pp. 1–6. [Google Scholar]
31. D. Zhang, H. Ge, T. Zhang, Y. -Y. Cui, X. Liu and G. Mao, “New multi-hop clustering algorithm for vehicular ad hoc networks,” IEEE Trans. Intell. Transp. Syst., vol. 20, no. 4, pp. 1517–1530, Aug. 2018. doi: 10.1109/TITS.2018.2853165. [Google Scholar] [CrossRef]
32. M. Z. Alam, F. S. Abkenar, I. Adhicandra, S. Murali, and A. Jamalipour, “Low-delay path selection for cluster-based buffer-aided vehicular communications,” IEEE Trans. Veh. Technol., vol. 69, no. 9, pp. 9356–9363, Mar. 2020. doi: 10.1109/TVT.2020.2976926. [Google Scholar] [CrossRef]
33. W. Wang et al., “Vehicle trajectory clustering based on dynamic representation learning of internet of vehicles,” IEEE Trans. Intell. Transp. Syst., vol. 22, no. 6, pp. 3567–3576, Jun. 2021. doi: 10.1109/TITS.2020.2995856. [Google Scholar] [CrossRef]
34. H. Zhong, L. Wang, J. Cui, J. Zhang, and I. Bolodurina, “Secure edge computing-assisted video reporting service in 5G-enabled vehicular networks,” IEEE Trans. Inform. Forensic Secur., vol. 18, pp. 3774–3786, Jun. 2023. doi: 10.1109/TIFS.2023.3287731. [Google Scholar] [CrossRef]
35. U. V. Vazirani and V. V. Vazirani, “Efficient and secure pseudo-random number generation,” in Found. Comput. Sci., Singer Island, FL, USA, Oct. 1984, pp. 193–202. [Google Scholar]
36. R. Hou et al., “Data forwarding scheme for vehicle tracking in named data networking,” IEEE Trans. Veh. Technol., vol. 70, no. 7, pp. 6684–6695, May 2021. doi: 10.1109/TVT.2021.3081448. [Google Scholar] [CrossRef]
37. Y. -C. Chu and N. -F. Huang, “An efficient traffic information forwarding solution for vehicle safety communications on highways,” IEEE Trans. Intell. Transp. Syst., vol. 13, no. 2, pp. 631–643, Dec. 2011. doi: 10.1109/TITS.2011.2177456. [Google Scholar] [CrossRef]
38. Spring, “Spring cloud,” 2003. Accessed: Feb. 12, 2022. [Online]. Available: https://spring.io/projects/spring-cloud [Google Scholar]
39. E. Chen, S. Wang, Y. Fan, Y. Zhu, and S. S. Yau, “SaaSC: Toward pay-as-you-go mode for software service transactions based on blockchain’s smart legal contracts,” IEEE Trans. Serv. Comput., vol. 16, no. 5, pp. 3665–3681, Apr. 2023. doi: 10.1109/TSC.2023.3267489. [Google Scholar] [CrossRef]
40. M. Randles, D. Lamb, and A. Taleb-Bendiab, “A comparative study into distributed load balancing algorithms for cloud computing,” in IEEE Int. Conf. Adv. Inf. Netw. Appl. Workshops, Perth, WA, Australia, Apr. 2010, pp. 551–556. [Google Scholar]
41. T. Li, D. Baumberger, and S. Hahn, “Efficient and scalable multiprocessor fair scheduling using distributed weighted round-robin,” ACM Sigplan Not., vol. 44, no. 4, pp. 65–74, Feb. 2009. doi: 10.1145/1594835.1504188. [Google Scholar] [CrossRef]
42. A. Singh, P. Goyal, and S. Batra, “An optimized round robin scheduling algorithm for CPU scheduling,” Int. J. Comput. Sci. Eng., vol. 2, no. 7, pp. 2383–2385, Feb. 2010. doi: 10.48550/arXiv.1605.00362. [Google Scholar] [CrossRef]
43. L. Zhu, J. Cui, and G. Xiong, “Improved dynamic load balancing algorithm based on Least-Connection Scheduling,” in IEEE Inf. Technol. and Mechatronics Eng. Conf., Chongqing, China, Dec. 2018, pp. 1858–1862. [Google Scholar]
44. J. Zhang, H. Zhong, J. Cui, Y. Xu, and L. Liu, “SMAKA: Secure many-to-many authentication and key agreement scheme for vehicular networks,” IEEE Trans. Inf. Forensics Secur., vol. 16, pp. 1810–1824, Dec. 2020. doi: 10.1109/TIFS.2020.3044855. [Google Scholar] [CrossRef]
45. J. Cui et al., “A practical and provably secure authentication and key agreement scheme for UAV-assisted VANETs for emergency rescue,” IEEE Trans. Network Sci. Eng., vol. 11, no. 2, pp. 1454–1468, Oct. 2023. doi: 10.1109/TNSE.2023.3323972. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools