 Open Access
Open Access
ARTICLE
Message Verification Protocol Based on Bilinear Pairings and Elliptic Curves for Enhanced Security in Vehicular Ad Hoc Networks
1 Department of Computer Science and Software Engineering, Jaramogi Oginga Odinga University of Science and Technology, Bondo, 40601, Kenya
2 Department of Applied Electronics, Saveetha School of Engineering, SIMATS, Chennai, Tamilnadu, 602105, India
3 Information Technology Department, Management Technical College, Southern Technical University, Basrah, 61004, Iraq
4 Department of Computer Science, College of Education for Pure Sciences, University of Basrah, Basrah, 61004, Iraq
5 College of Big Data and Internet, Shenzhen Technology University, Shenzhen, 518118, China
6 Huazhong University of Science and Technology, Shenzhen Institute, Shenzhen, 518000, China
7 National Engineering Laboratory for Big Data System Computing Technology, Shenzhen University, Shenzhen, 518060, China
8 Computer Technology Engineering Department, Iraq University College, Basrah, 61004, Iraq
9 Department of Mathematics, College of Education for Pure Sciences, University of Basrah, Basrah, 61004, Iraq
10 Institute of Mathematics, University of Debrecen, Debrecen, H-4002, Hungary
11 Department of Electrical Engineering and Mechatronics, Faculty of Engineering, University of Debrecen, Debrecen, 4028, Hungary
* Corresponding Authors: Zaid Ameen Abduljabbar. Email: ; Junchao Ma. Email:
Computers, Materials & Continua 2024, 81(1), 1029-1057. https://doi.org/10.32604/cmc.2024.053854
Received 11 May 2024; Accepted 01 September 2024; Issue published 15 October 2024
Abstract
Vehicular ad hoc networks (VANETs) provide intelligent navigation and efficient route management, resulting in time savings and cost reductions in the transportation sector. However, the exchange of beacons and messages over public channels among vehicles and roadside units renders these networks vulnerable to numerous attacks and privacy violations. To address these challenges, several privacy and security preservation protocols based on blockchain and public key cryptography have been proposed recently. However, most of these schemes are limited by a long execution time and massive communication costs, which make them inefficient for on-board units (OBUs). Additionally, some of them are still susceptible to many attacks. As such, this study presents a novel protocol based on the fusion of elliptic curve cryptography (ECC) and bilinear pairing (BP) operations. The formal security analysis is accomplished using the Burrows–Abadi–Needham (BAN) logic, demonstrating that our scheme is verifiably secure. The proposed scheme’s informal security assessment also shows that it provides salient security features, such as non-repudiation, anonymity, and unlinkability. Moreover, the scheme is shown to be resilient against attacks, such as packet replays, forgeries, message falsifications, and impersonations. From the performance perspective, this protocol yields a 37.88% reduction in communication overheads and a 44.44% improvement in the supported security features. Therefore, the proposed scheme can be deployed in VANETs to provide robust security at low overheads.Keywords
The continuously increasing volume of vehicles on roads has led to difficulties in urban traffic management. Additionally, frequent accidents and heavy traffic jams pose numerous challenges to traffic management systems. This situation has led to the development of vehicular ad hoc networks (VANETs) to offer efficient and intelligent transport management [1–3]. VANETs are a special case of self-organizing mobile networks, in which vehicles share information through vehicle-to-vehicle (V2V) or vehicle-to-roadside unit (V2R) transmission modes. As explained in Reference [4], rapid advancements in microelectronic and wireless technologies have contributed to the speedy developments in VANETs. A typical VANET environment comprises vehicles, trusted authorities (TAs), and roadside units (RSUs). According to Reference [5], the on-board unit (OBU) installed in each vehicle detects safety messages from its environment (e.g., customers, pedestrians, other vehicles, Internet, traffic lights, cloud, parking areas, and sensors). TAs register all RSUs and vehicles within the VANET, whilst RSUs act as relays during data exchanges amongst vehicles [6]. For message exchanges, vehicle-to-infrastructure (V2I) and V2V are two major modes deployed in VANETs [7].
OBUs use dedicated short-range communication (DSRC) to transmit safety messages to surrounding vehicles or infrastructure at a distance of up to 300 m every 100–300 milliseconds. The broadcast messages may include vehicle location, speed, traffic status, and route. These messages serve to boost safety and reduce accidents on roads. They also help VANETs in offering efficient, secure traffic and route management on roads [8]. Accidents can also be significantly reduced through emergency and rule violation warnings [9]. Additionally, infotainment applications, e.g., intelligent navigation, file sharing, parking, multimedia services, and toll collection, can boost comfort. Ultimately, this configuration results in time savings, cost reductions, and efficiency enhancements on roads. As explained in Reference [10], the resulting intelligent transportation system (ITS) consisting of the internet of vehicles (IoV) facilitates traffic route management. This system can also enhance driving safety and minimize traffic congestion [11].
Despite the many benefits of VANET deployments, the open nature of the wireless channels deployed during communication exposes these networks to numerous security and privacy violations [12]. Some serious issues in VANETs include data leakages, eavesdropping, and session hijacking attacks. Additionally, replays, man-in-the-middle (MitM) attacks, impersonations, and message fabrications can be present in these networks [7]. Attackers can also implant malicious vehicles in these networks to execute malevolent activities, such as the misuse of the offered route management [13]. Although beacons and messages are signed, the lack of encryption before broadcast has been noted to be a serious issue in VANETs [8,14]. Therefore, attackers can intercept these messages and, hence, violate privacy [15–17]. Additionally, adversaries can exploit these messages for malicious activities. Another serious challenge in VANETs is heterogeneity occasioned by the deployment of hardware from different manufacturers. Such heterogeneity results in different protocols for message transmission and authentication, thereby potentially causing inconsistencies in security and privacy implementations [8].
Numerous schemes have been developed recently to address the security and privacy issues above. The majority of these solutions are based on public key infrastructure (PKI) [18], blockchain, certificates, and physically unclonable functions (PUFs). Unfortunately, most of these schemes still face serious privacy, performance, and security setbacks. Additionally, the majority of the current traffic route management schemes incur high computation and communication overheads [10]. Limited bandwidths, heavy data volumes, scalability, short communication periods, and strict real-time operations call for efficient communication protocols. High mobility in VANETs likewise implies a short authentication and communication time amongst different entities. Therefore, the efficiency of the current authentication protocols must be improved. The major contributions of this study are as follows:
• We develop an authentication method based on elliptic curve cryptography (ECC) and bilinear pairings (BPs) to offer efficient and secure source and message verification.
• Stochastic one-time secret keys are incorporated in the proposed scheme during mutual validations to boost vehicle and RSU privacy. Additionally, these dynamic stochastic one-time secret keys help thwart adversarial linkability and traceability.
• Conditional privacy is preserved in the proposed protocol so that malicious network entities can be identified and revoked by a fully trusted network entity. This aspect is crucial in preventing malicious parties from overwhelming VANETs with fake messages that can cause denial of service (DoS), traffic jams, and accidents.
• A formal security analysis is conducted to demonstrate that the proposed scheme is provably secure. Additionally, an informal security analysis demonstrates that our scheme can withstand numerous attacks, such as message falsifications, forgeries, packet replays, impersonations, and MitM attacks. The protocol can also offer mutual authentication, perfect key secrecy, anonymity, unlinkability, non-repudiation, and source and message integrity.
• We perform extensive comparative performance evaluations, demonstrating that the proposed scheme incurs relatively low computation costs and the least communication overheads. Therefore, it is concluded that the scheme offers robust security at low overheads.
1.1 This Sub-Section Aims to Present Some Mathematical Formulations upon Which the Proposed Protocol Is Based. The Two Building Blocks for the Proposed Protocol Are BP and Elliptic Curve (EC) Operations.
Let λ1, λ2, and λ3 represent a cyclic group consisting of prime numbers, the order of which is p. Additionally, let gi be the generator of cyclic group λi. We also denote the one-to-one mapping from λ2 to λ1 as I(g2). The computable bilinear map is represented as I(g2) = g2. BM: λ1 × λ2 → λ3. In this scenario, BP has the following properties:
Computability: For any cyclic group generators
Bilinearity: For all cyclic group generators gi
Non-degeneracy: If
Let p and q be large prime numbers, whilst Fp is a finite field, the order of which is p. Additionally, let E represent an EC denoted by y2 = x3 + ax + b mod p, where
Point addition: Suppose that P and Q are two points of group G. We denote an intersection of the straight line connecting P and Q and the EC E as R. Thereafter, R = P + Q, provided that the two points are different. On condition that P = Q, intersection R is denoted as R = P + Q. However, when P = −Q, P + Q = 0.
Point multiplication: Suppose that
The strength of the resulting ECC-based security protocol is based on the difficulties of solving the elliptic curve discrete logarithm problem (ECDLP) and the elliptic curve computational Diffie-Hellman problem (ECCDHP). The two problems can be mathematically formulated as follows:
ECDLP: Suppose that points P and Q are random points on E, such that
ECCDHP: Let x and y be some two unknown integers and Q and R be two random points on E. Additionally, let {x.P, y.P, P} be some values such that
1.2 Security and Privacy Requirements
Without strong privacy and security protections, VANET message exchanges are exposed to numerous malicious entities and activities. As such, the proposed protocol must fulfill the following requirements to uphold strong privacy and security in this environment:
Anonymity: The actual identities of vehicles and RSUs should be hidden from adversaries. This strategy ensures that eavesdroppers cannot determine these unique identities for malicious activities.
Conditional privacy: TAs could determine the real identity and trace and eliminate any malicious RSU from the network. This situation prevents these malicious entities from transmitting high volumes of falsified messages that can lead to accidents or DoS.
Mutual authentication: All parties in the VANET must validate one another before exchanging any messages.
Source and message integrity: It should be impossible for attackers to change the messages exchanged in the VANET environment.
Backward key secrecy: Attackers should be unable to use the present session keys to derive any keys utilized in previous data exchange sessions.
Forward key secrecy: Adversaries with access to the present session keys should be unable to use these keys to compute the keys to be deployed in subsequent communication processes.
Unlinkability: Eavesdroppers in the network should be unable to associate any transmitted messages to a particular vehicle or RSU.
Nonrepudiation: Communicating entities should not be in a position to deny having participated in message exchange.
This section models adversarial capabilities that could compromise the proposed protocol. In our protocol, adversary Å is thought to have the capabilities advocated in the Canetti-Krawczyk (C-K) model. In this model, Å is capable of the following attacks:
• Intercepting, eavesdropping, impersonating, modifying, and deleting the exchanged packets;
• Physically capturing OBUs and retrieving all security tokens stored in their memories;
• Capturing the session states and keys negotiated amongst the vehicles and RSUs.
The proposed protocol is required to avert all these adversarial attack vectors and guarantee strong privacy and security protection.
Message transmission in VANETs is executed over open public channels prone to attacks. In this environment, attackers can intercept, delete, replay, and modify messages. Adversaries could also impersonate legitimate and authorized entities and broadcast fake information. Additionally, the inability of the VANET entities to establish message and source authenticity may result in accidents and traffic jams. Therefore, all VANET entities must validate message source authenticity, determine message integrity, and preserve confidentiality. Equally important is to maintain the anonymity and privacy of vehicles and RSUs, without which these entities are exposed to numerous attacks. For example, attackers may obtain the vehicle’s real identity, travel routes, and current location, which enables the adversaries to perform tracking [19–21] of network entities. Performance is another important metric that must be enhanced in VANETs so that multiple messages are processed immediately. This particular case involves vehicles moving at high speeds, in which receivers should be capable of processing multiple messages within 100–300 ms [22]. Given that OBUs installed in vehicles are not as endowed in computation and storage as TAs and RSUs, they can be easily overwhelmed with high computational overheads when numerous high-mobility vehicles broadcast multiple messages. This is particularly the case in dense traffic regions. Hence, there is a need to reduce this complexity.
Numerous security and privacy preservation solutions have been developed to secure the communication process in VANETs. For example, the identity-based scheme (IBS) is presented in Reference [23]. However, key escrow problems continue to be a serious issue in IBS-based approaches [24]. A signature-based scheme utilizing public key infrastructure and identity is developed in Reference [25], whilst a conditional privacy preservation scheme is introduced in Reference [26]. Unfortunately, message verification and identity detection tend to have long execution durations, which degrades the performance of the two approaches above [27]. In addition, the scheme in Reference [26] incurs huge storage overheads for large pools of identities and secret keys. Privacy-preserving authentication protocols using group signatures are developed in Reference [28,29]. However, identifying malicious vehicles within a network may be cumbersome [30]. Reference [31] presents a signature-based batch verification scheme in VANETs, though failing to offer key secrecy, conditional privacy, and unlinkability. Meanwhile, the algorithm in Reference [32] is only evaluated against collusion attacks, and the protocol in Reference [33] does not consider non-repudiation and unlinkability. A lightweight authentication solution is introduced in Reference [34] based on the difficulty of ECCDHP. During registration, each vehicle is issued a smart card, which is used in conjunction with passwords for login. Similarly, an authentication approach utilizing passwords is presented in Reference [35]. Unfortunately, the technique in Reference [34] cannot withstand smart card loss and password-guessing attacks [7], and the approach in Reference [35] is not robust against attacks such as password guessing, sensor capturing, traceability, and impersonations [36].
To address the issues in Reference [34], message authenticated codes (MACs) are deployed in Reference [37] instead of passwords. Although MAC offers protection against attacks such as impersonations, privileged insiders, DoS, and packet replays, it has not been evaluated against MiTM attacks, forgeries, and message falsifications. The issues in Reference [35] are handled by the two-factor authentication technique in Reference [36], which deploys biometric templates instead of passwords. Although this scheme is robust against smart cards, stolen sink nodes, and replay attacks, it incurs high storage complexity in the sink node’s memory. Additionally, the revocation of malicious entities is not considered and has high communication and computation overheads [7]. A privacy-preserving scheme using a law executor is introduced in Reference [38], and a two-factor security protocol is meanwhile developed in Reference [39], both incurring low computation costs. However, session keys derived in References [38,39] are not secured against the C-K adversary attack [7]. For secure VANETs, techniques deploying PUFs are developed in References [40–42]. Although these techniques minimize redundant authentications [7], PUFs have instability issues [43]. Reference [44] introduces a privacy-preserving hybrid signcryption security solution. Other signcryption-based protocols are presented in References [8,33].
However, the use of several time-consuming operations in these schemes reduces their efficiency [44]. For example, the generation, distribution, processing, validation, and revocation of certificates result in long delays. Additionally, PKI-based signcryption protocols render it cumbersome for vehicles to manage large pools of certificates and key pairs. The scheme in Reference [8] also fails to offer key secrecy.
To enable vehicles to execute batch validation of other nearby vehicles, a privacy-preserving scheme is presented in Reference [45]. A similar batch authentication approach is developed in Reference [8]. Meanwhile, a mutual authentication technique for an IoV environment is introduced in Reference [14]. Although these schemes are provably secure and efficient, they fail to provide message confidentiality [44]. A security protocol using BP operations is introduced in Reference [46]. Meanwhile, a pairing-free security solution is presented in Reference [47]. Unfortunately, the technique in Reference [46] involves three pairing operations, which increases its computation complexity. Although the approach in Reference [47] is efficient owing to the deployment of ECC, it fails to offer anonymity and traceability. Besides, it cannot resist message replays [44]. A security technique based on pairing operations is introduced in Reference [7], but it fails to consider message integrity, non-repudiation, and conditional privacy. To curb some of the preceding challenges, schemes based on blockchain technology have been developed and shown to offer anonymity, immutability, and decentralization. For example, a blockchain certificate-based technique is developed in Reference [48].
However, it requires frequent interactions between certificate authorities and vehicles [49], thereby increasing its communication overheads. Similarly, blockchain-based protocols are developed in References [50–53]. However, blockchain technology incurs huge storage overheads [54] and, hence, is not energy-efficient [55,56]. Additionally, the protocol in Reference [53] does not consider message falsifications, non-repudiations, and impersonations. Nevertheless, a combination of pseudonyms and blockchains is deployed in Reference [57] to establish distributed trust in VANETs.
Similarly, a blockchain-based technique was introduced in Reference [58] to facilitate vehicle revocability without the need for TA’s assistance. However, the scheme in Reference [50] results in significant communication costs and delays due to the frequent involvement of the certificate authority (CA) in public key updates. Meanwhile, a fault tolerance technique was introduced in Reference [59], while an anti-jamming technique was developed in Reference [60]. Despite these advancements, it is crucial to conduct extensive formal and informal security analyses in these schemes. Table 1 offers a detailed summary of these related studies.
The preceding review shows that most current VANET security solutions are PKI-, identity-, ECC-, blockchain-, certificateless-, or PUF-based. These schemes still face serious privacy, performance, and security setbacks. For example, most identity-based approaches have key escrow and revocation challenges. Conversely, security solutions based on PKI incur huge storage costs. Although certificateless solutions solve the key escrow issues in identity-based protocols, the key revocation challenge is still challenging in these approaches. Owing to frequent mobility in VANETs, authentication and message exchange durations are extremely short. As such, a need arises to enhance the efficiency of authentication and communication procedures. The proposed protocol is robust and efficient, helping address many of these challenges.
Fig. 1 depicts the main entities in the proposed scheme: vehicles, RSUs, and TA. Before data exchange amongst vehicles and RSUs, they must register at the TA and be issued security tokens to deploy during the authentication and data exchange phases.
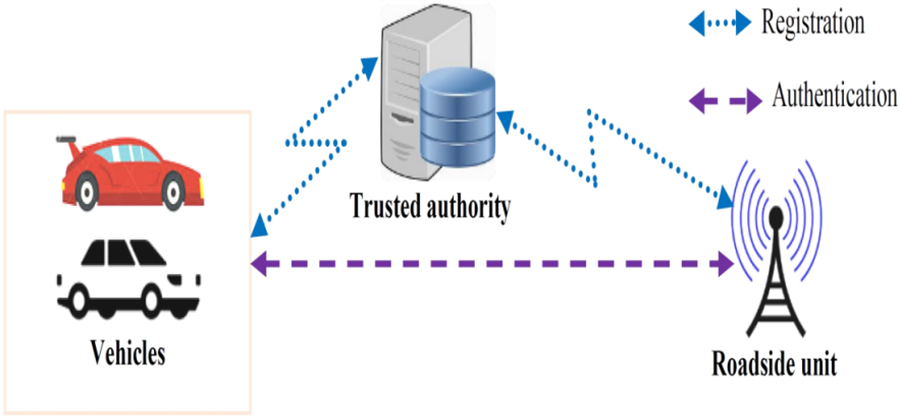
Figure 1: Network model
Registration between the RSU and the TA, as well as vehicles and TA, is executed over secured communication channels. However, authentication and data exchange procedures are carried over wireless communication channels. Table 2 details the notations used in this paper.

The proposed scheme is executed in three major phases: system setup, registration, and mutual authentication.
First, TA randomly selects p and q, where
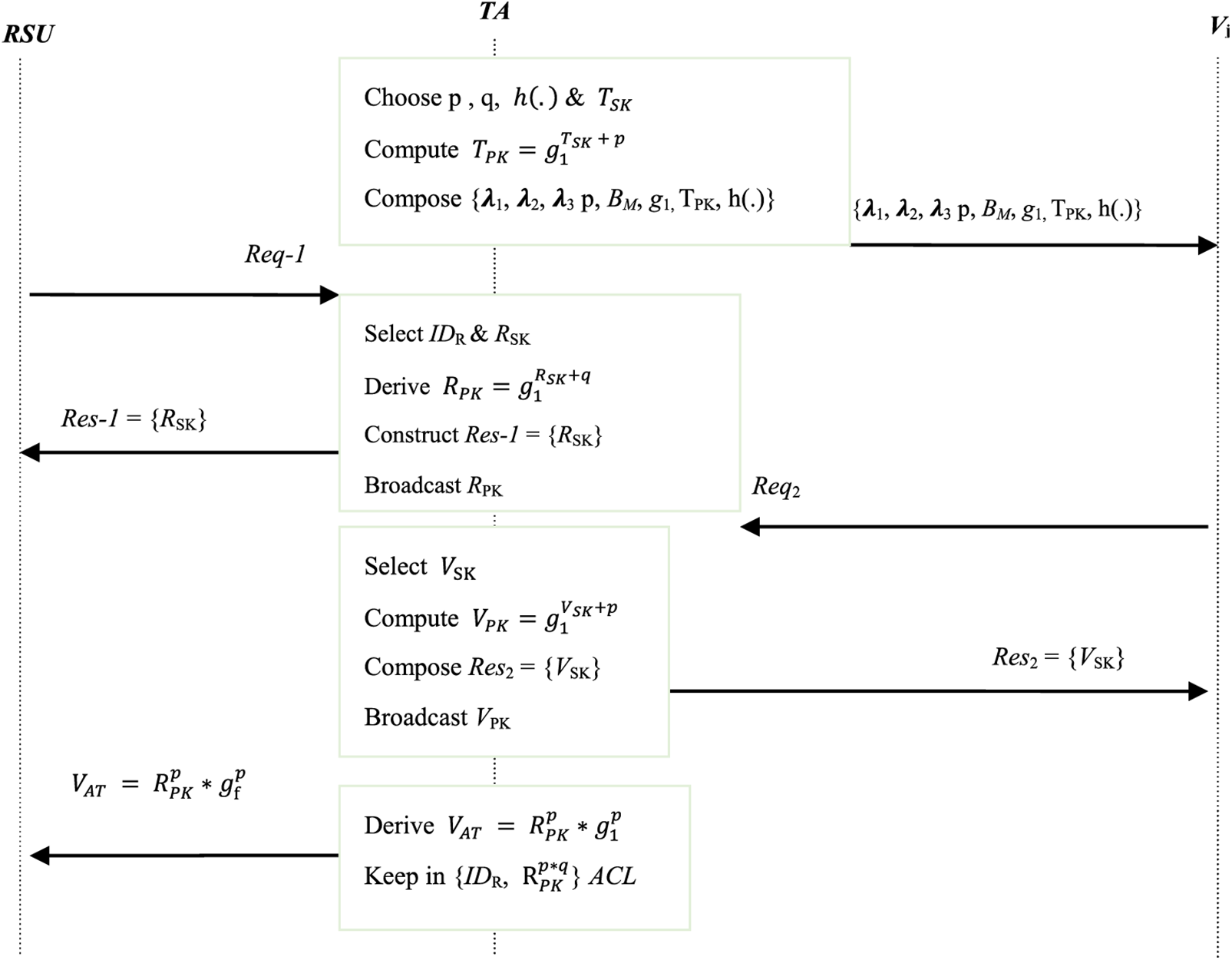
Figure 2: System setup and registration phases
Each vehicle and RSU must register at the TA before proceeding to other phases, such as authentication and data exchanges. The execution of the following four steps facilitates this process:
Step 1: Roadside unit RSUi sends request Req-1 to TA through secured communication channels. Upon receiving this request, TA selected IDR as RSUi’s unique identity. Thereafter, it chooses some secret key RSK for RSUi, where
Step 2: TA computes public key RPK for RSUi, where
Step 3: First, vehicle Vj sends registration request Req2 to TA, which chooses random nonce
Step 4: TA generates and offers the vehicle access token
In the authentication phase, the communicating parties derive signatures and certificates used to ensure the integrity of the transmitted payload PLV and PLR. The first part of this phase is vehicle-to-RSUi authentication, while the second part is RSU- to-vehicle authentication. The goal of Vj → RSUi authentication is to transfer data from vehicles to RSUs securely. As detailed in Step 1→ Step 6, this process upholds the privacy of vehicle Vj communication from the rest of the vehicles. However, the second phase of the authentication process aims to transfer sensitive data from RSUs to vehicles securely. The specific details of the authentication procedures are described as follows:
Step 1: Vehicle Vj chooses some random number Rj from the set of random numbers ℝ to act as its one-time secret key, where R1, R2,…Rℝ
Step 2: Vj stochastically chooses a random nonce
Step 3: Vehicle Vj derives signature
Step 4: After obtaining Msg-1, RSUi confirms the freshness of timestamp Ts. In particular,, authentication is aborted if the timestamp freshness check flops. Otherwise, payload and source integrity are checked next.
Step 5: RSUi derives
Step 6: RSUi verifies the integrity of the transmitted payload using the signature derived previously. To accomplish this step, it checks whether or not
Step 7: RSUi chooses some random number Ři from ℝ to act as its one-time secret key, where Ř1, Ř2,…Řℝ
Step 8: RSUi derives certificate ℂ2 by randomly choosing parameters
Step 9: To preserve the integrity of the payload PLR generated at RSUi, it computes signature
Step 10: After receiving message Msg2, Vj validates the freshness of timestamp T2, such that the session is aborted upon verification failure. This step is followed by the validity check of the source (RSUi) and the integrity checks of message Msg2. These checks are accomplished by computing parameters B3** = B3* × B4* and B4** = B4* × PPK. Thereafter, it computes value A4..∼ = h (PPK||B3**||B4**||TPK) and checks whether or not A4∼
Step 11: Upon successful verification of certificate ℂ2, Vj proceeds to validate the integrity of payload PLR. To accomplish this step, it checks whether or not
Therefore,
Step 12: In this phase, the payload
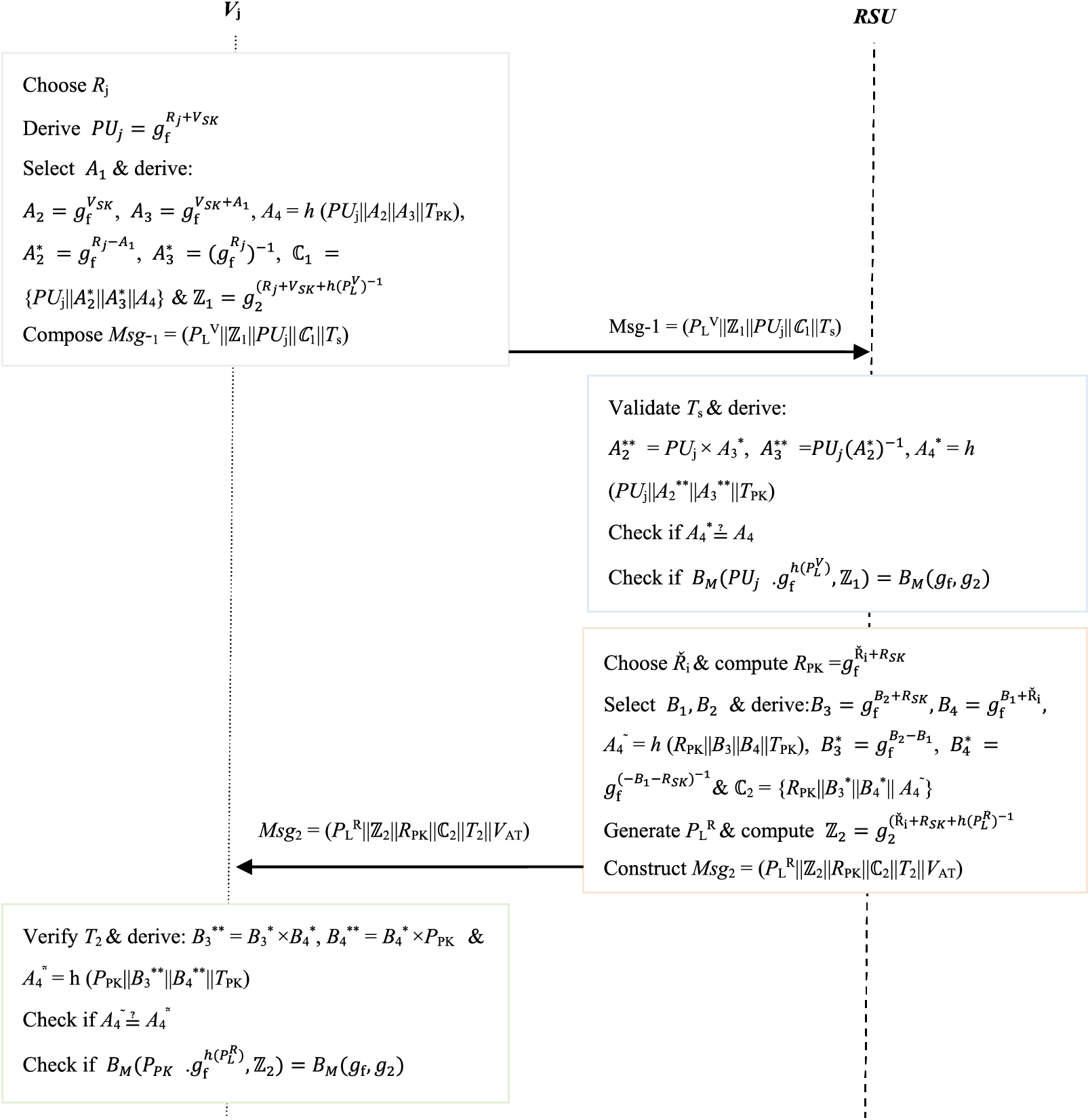
Figure 3: Authentication phase
Therefore, the proposed protocol could attain conditional privacy for all communicating entities. This aspect is essential in identifying and revoking malicious entities from the network.
This section ultimately aims to offer some formal security analysis of the proposed scheme, followed by its informal security analysis. Formal security analysis demonstrates the semantic security of the authentication procedures. Conversely, informal security analysis shows our scheme’s resilience against typical VANET attacks. The detailed illustration of the analyses is presented in the following sub-sections.
This sub-section deploys the BAN logic to analyze the proposed protocol. Accordingly, various postulates and notations of the BAN logic are used, including the nonce verification rule (NVR), message–meaning rule (MMR), jurisdiction rule (JR), and decomposition rule (DR). Table 3 presents some of the BAN logic notations.
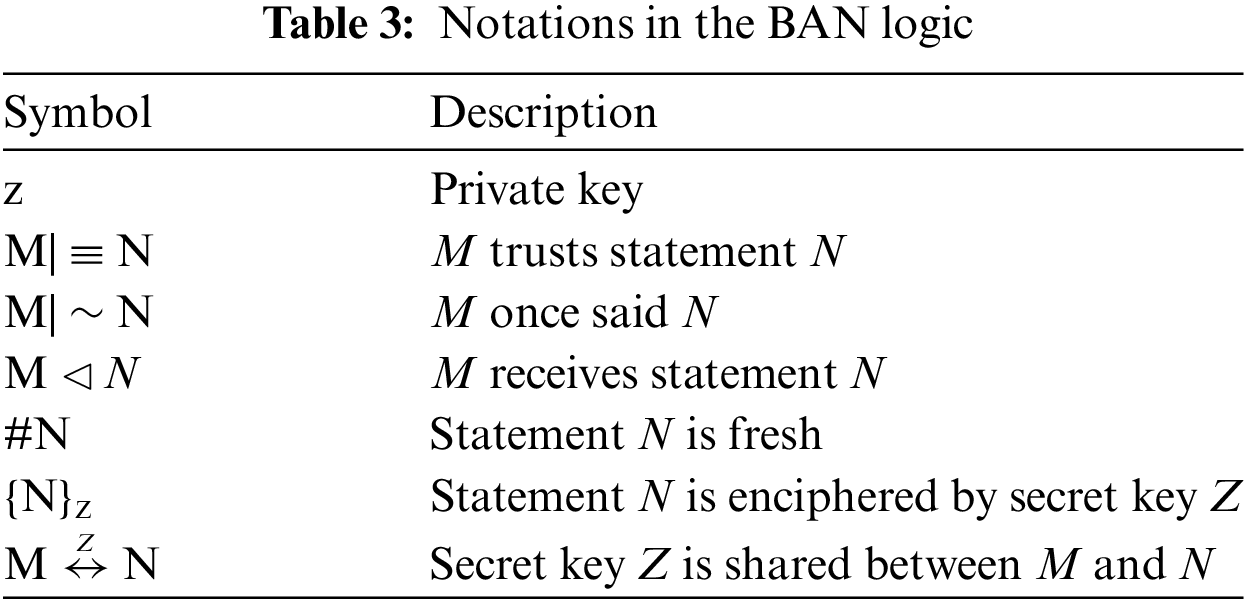
The BAN logic mathematical formulations of the various rules are described using the notations in Table 3.
MMR:
This rule means that M believes N said A, provided that M believes that key Z is the shared key with N. Moreover, M sees A, which is enciphered using key Z.
JR:
This rule implies that M trusts A if M believes N has jurisdiction over A and M trusts that N believes A.
NVR:
This rule means that M believes N trusts A provided that M believes A has been transmitted recently, and N has said A.
DR:
i)
ii)
iii)
The three postulates under DR are essential in decomposing the transmitted messages and validating their freshness. DR (i) implies that M can discern A provided that it observes all messages. Meanwhile, DR (ii) means that the combination of A and B is fresh provided that one of these components is fresh. However, the consequences of DR (iii) are that amalgamating an assortment of message components means that entities trust them independently.
The formal analysis of this scheme, a rigorous process that follows a systematic approach, proceeds as follows using the BAN logic notations and the preceding rules.
We obtain P1 in accordance with the provisions of MMR.
P1:
Using the NVR, P2 is obtained as:
P2:
Similarly, applying JR yields P3, as shown below:
P3:
However, in accordance with DR, P4 is obtained.
P4:
This being the case, MMR is applied to yield P5.
P5:
Thereafter, the application of NVR yields P6, as shown below:
P6:
However, the usage of JR yields P7.
P7:
Thereafter, DR is applied to obtain P8 and P9.
P8:
Also,
P9:
Since
P10:
Consequently, we get P11 as:
P11:
This is because
Based on MMR, the following is obtained:
P12:
Similarly, NVR is deployed to yield P13.
P13:
Then, it follows that:
P14:
Using the same logic, we obtain P14 as:
P14:
The BAN logic proves that the messages exchanged in this protocol are fresh. Hence, replay attacks are easily detected. Additionally, the BAN logic proves that this protocol offers a secure mechanism for validating the exchanged messages through the certificates encapsulated in the messages.
4.2 Informal Security Analysis
This sub-section explains and verifies some theorems to prove that our technique provides the desired security and privacy characteristics. The theorems formulated are also deployed to prove that this approach is robust against some common VANET attack vectors.
Theorem 1: This protocol can withstand packet replays.
Proof: Timestamps are incorporated in all messages exchanged between Vj and RSUi to curb packet replay attacks. For instance, message Msg-1 = (PLV||ℤ1||PUj||ℂ1||Ts) sent from Vj to RSUi contains timestamp Ts. The freshness of this timestamp is verified at RSUi. Particularly, the session is aborted when the freshness check flops. Similarly, message Msg2 = (PLR||ℤ2||RPK||ℂ2||T2||VAT) forwarded from RSUi towards Vj incorporates timestamp T2 that is also validated by Vj. The authentication session is aborted when T2 fails the freshness check.
Theorem 2: Robust authentication is executed.
Proof: To keep intruders at bay, this protocol utilizes certificates attached to all exchanged messages. For example, vehicle Vj derives certificate
Theorem 3: MitM and message falsification attacks are prevented.
Proof: To prevent these attacks, Vj and RSUi validate all received messages. This objective is achieved using the signatures and certificates derived by these entities. For example, to validate the correctness of message Msg-1 = (PLV||ℤ1||PUj||ℂ1||Ts) sent from Vj, RSUi computes
Theorem 4: Source and message integrity are preserved in this scheme.
Proof: In this protocol, signatures are used to ensure that messages are not changed over the communication channels as they are transmitted among the communicating parties. For example, Vj computes signature
Theorem 5: Anonymity of the network entities is preserved.
Proof: Suppose that adversary Å is interested in establishing the actual identity of roadside unit RSUi (i.e., IDR). To achieve this objective, Å intercepts messages Msg-1 = (PLV||ℤ1||PUj||ℂ1||Ts) and Msg2 = (PLR||ℤ2||RPK||ℂ2||T2||VAT), where PLV and PLR are the vehicle and RSU payloads, respectively. Meanwhile,
Theorem 6: The proposed scheme prevents forgery attacks.
Proof: Suppose adversary Å is interested in forging the derived signatures and certificates. In the proposed scheme, the derived signatures incorporate one-time secret keys and private keys of the communicating entities. For example, the signature
Theorem 7: Key secrecy is preserved.
Proof: Let’s consider a scenario where the attacker has intercepted the one-time private key for for Vj (i.e., Rj) and the one-time secret key Ři for RSUi for the current session. The attacker’s objective is to use these keys to compute subsequent communication session certificates
Theorem 8: Impersonation attacks are prevented.
Proof: Suppose that adversary Å is interested in masquerading as vehicle Vj or roadside unit RSUi. To achieve this scenario, an attempt is made to compute signatures
Theorem 9:Communication session unlinkability is preserved.
Proof: To achieve communication session unlinkability, the proposed protocol deploys stochastic one-time secret keys Ři and Rj to derive the distinct signatures ℤ1, ℤ2 and certificates ℂ1 and ℂ2 for each session. Particularly,
Theorem 10: The proposed protocol provides conditional privacy for the communicating entities.
Proof: In this scheme, RSUs and vehicles deploy signatures and certificates instead of their actual identities. This method effectively hides their actual identities from other communicating parties. Based on Theorem 9, adversarial tracking of RSUi and Vj is not feasible. However, TA can trace the exact identity of any RSUi. This goal is accomplished by deploying its certificate ℂ2 = {RPK||B3*||B4*|| A4∼}. Suppose a malicious RSUj has sent that payload
Theorem 11: The proposed protocol assures nonrepudiation of exchanged messages.
Proof: In this scheme, receivers can always validate the authenticity of the sender using certificates
Theorem 12: Our scheme supports scalability and adaptability.
Proof: During the registration phase, all the vehicles and RSUs must register at the TA and be issued with security tokens deployable in the subsequent phases. After the successful registration phase, the TA stores the parameter set {IDR,
This sub-section aims to conduct a comparative analysis of our scheme. This goal is achieved using metrics commonly deployed in the evaluation of authentication schemes, including the computation overheads, the communication overheads, and the offered security features. The specific details of this comparative analysis are described below.
The proposed protocol incorporates certificates and signatures in all exchanged messages. As such, the time taken to verify these certificates and signatures is considered. Let TH, TBP, TPM, TSE, TBSM, TBPA, TBMH, TPA, and TE denote the time taken for one-way hashing, BP, EC point multiplication, symmetric encryption, BP scalar multiplication, BP point addition, BP map to point hash, EC point addition, and exponential operations, respectively. Additionally, let
Using the execution durations in Table 4, the computation costs for the diverse cryptographic operations are given in Table 5.
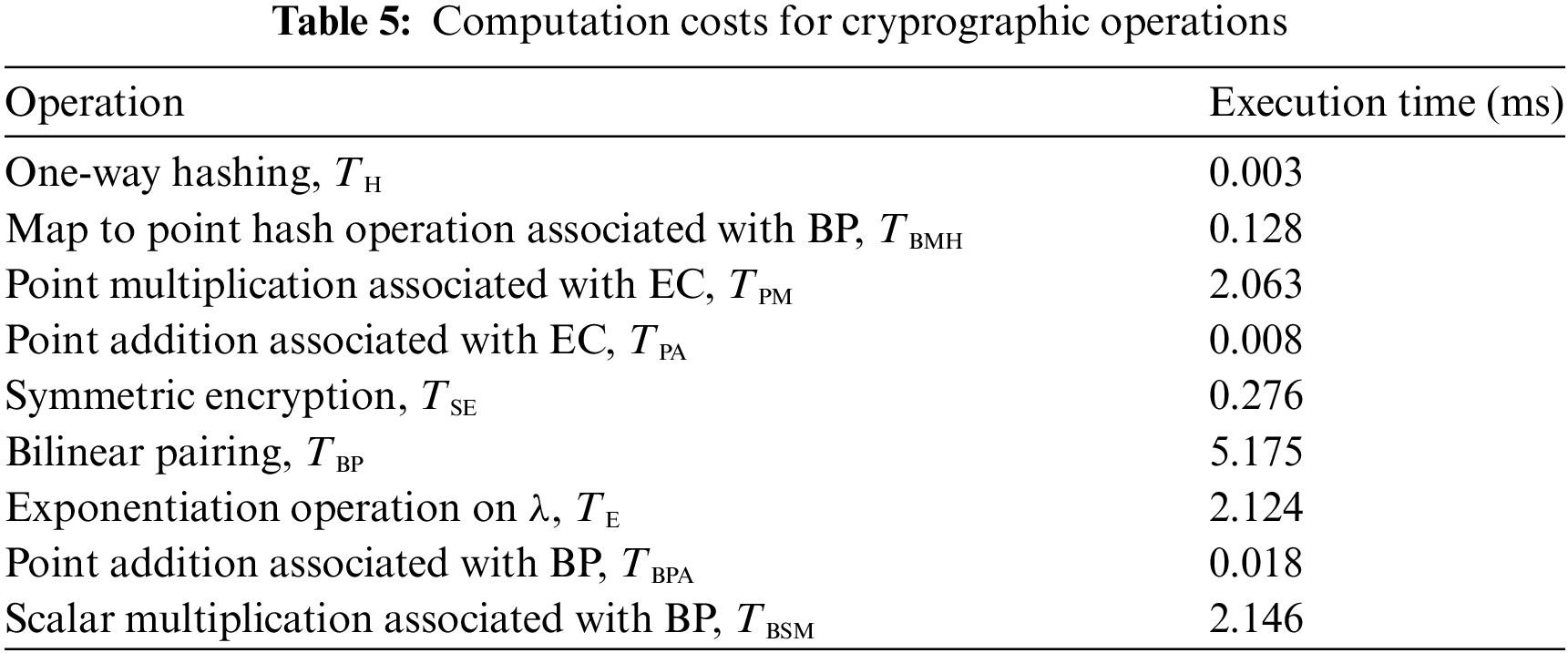
Based on the values in Table 5,
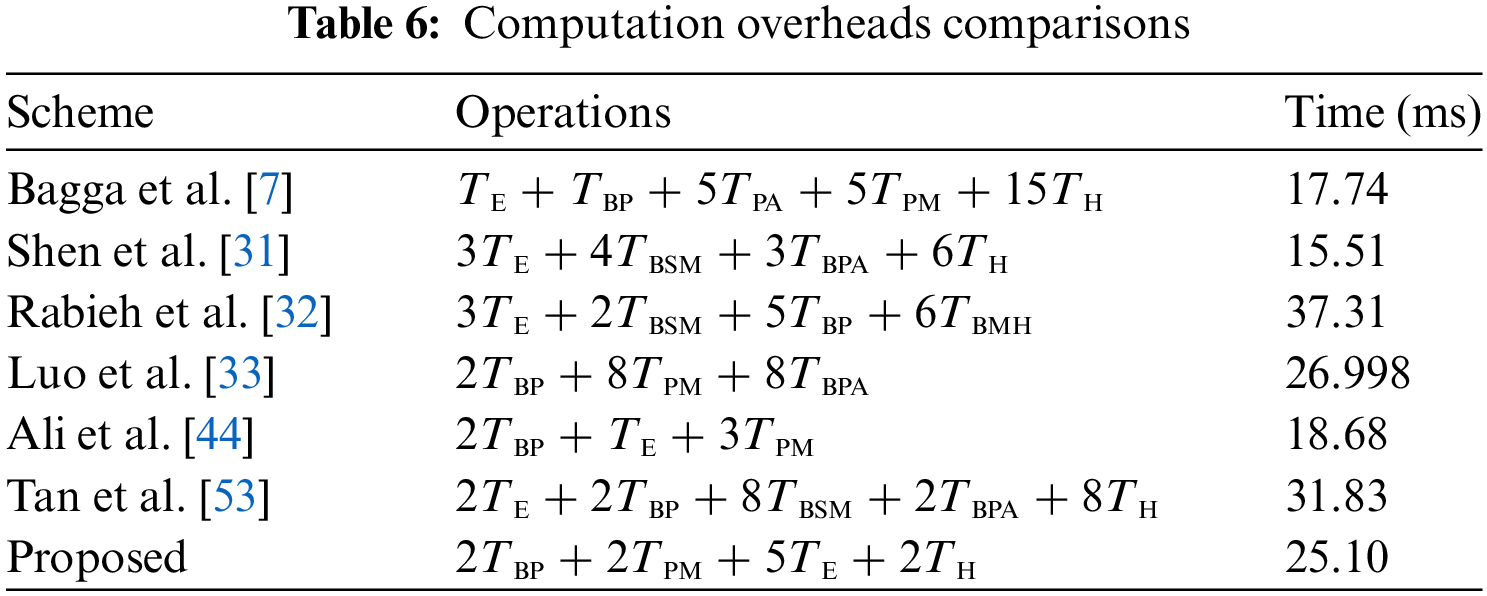
As shown in Table 6, the protocol in Reference [33] requires 26.998 ms to fully execute the authentication process, whilst the scheme in Reference [44] needs 18.68 ms. The protocols in References [53,8,32,31], take 31.83, 17.74, 37.31, and 15.51 ms, respectively. As illustrated in Fig. 4, the scheme in Reference [32] exhibits the longest execution time of 37.31 ms, which is attributed to the numerous pairing activities required during its authentication.
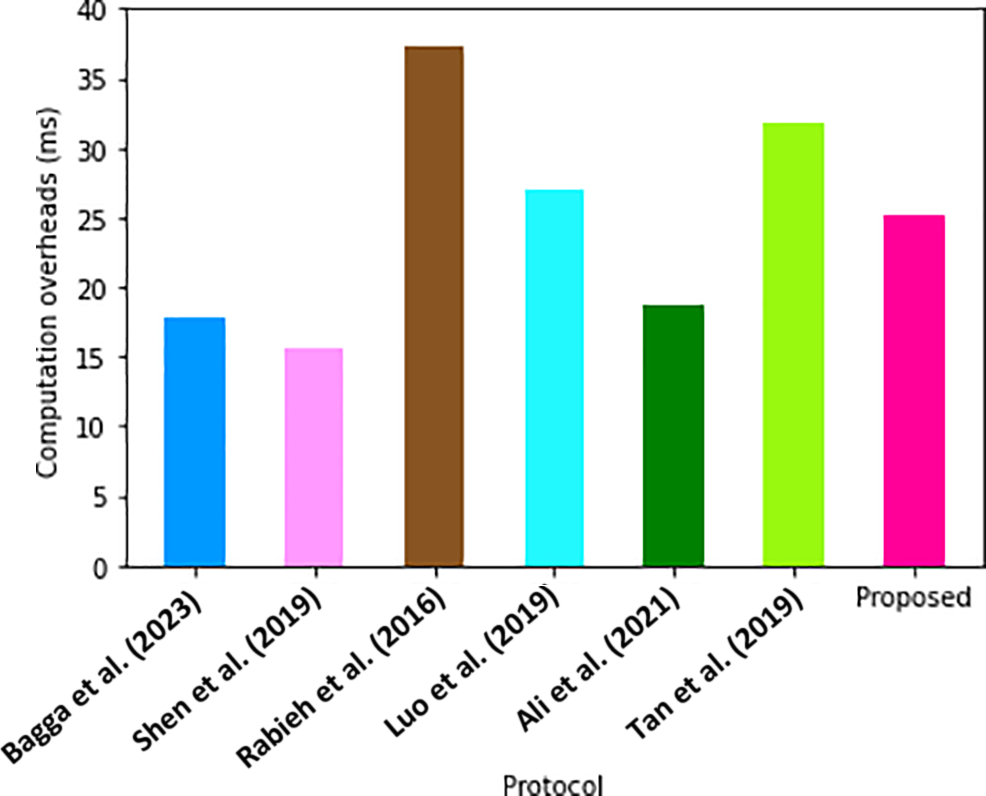
Figure 4: Computation overheads comparisons [7,31–33,44,53]
However, the protocol in Reference [31] takes the shortest time to fully execute. The reason is that it generally executes one-way hashing, scalar multiplication, point addition, and exponentiation operations on λ, all of which are lightweight compared with the BP operations in Reference [32]. The proposed protocol also executes two BP operations, rendering it relatively computationally extensive. However, it supports the highest number of security features, as shown in Table 9 of Section 5.3. Although the scheme in Reference [31] exhibits the shortest execution time, it does not offer backward key secrecy, conditional privacy, backward key secrecy, and unlinkability.
Similarly, the protocol in Reference [7] does not provide conditional privacy, nonrepudiation, and source and message integrity. Moreover, it has not been evaluated against forgeries and message falsifications. The scheme in Reference [44] fails to offer key secrecy and has not been evaluated against attacks such as MitM and impersonations.
The system setup and registration phases are carried out once, hence they are excluded in the derivation of the communication overheads of the authentication protocols. Accordingly, only the two messages exchanged during authentication are deployed to derive the communication costs of our protocol. The two messages are Msg-1 = (PLV||ℤ1||PUj||ℂ1||Ts), which is constructed at Vj and forwarded to RSUi; and Msg2 = (PLR||ℤ2||RPK||ℂ2||T2||VAT), which is composed of RSUi and transmitted to Vj. In this implementation, the output of TH is 20 bytes [49], IDR = Ts =T2 = VAT = 4 bytes [49],
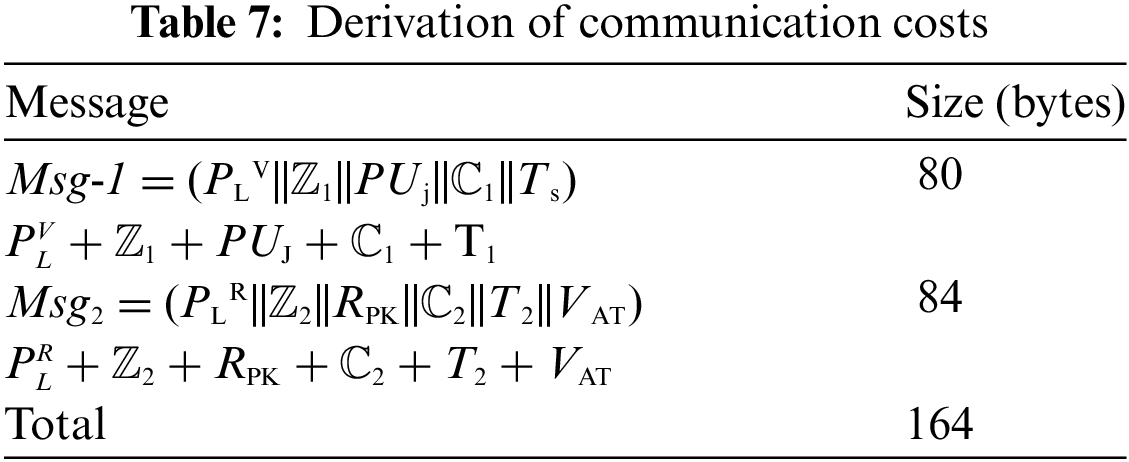
As shown in Table 7, the two messages exchanged in the proposed protocol have a size of 164 bytes. Table 8 compares the communication costs of the various approaches. In Reference [53], the system parameter set {TSN, IDRSU, R, Q, Cert} is broadcast. Thereafter, the authentication requests
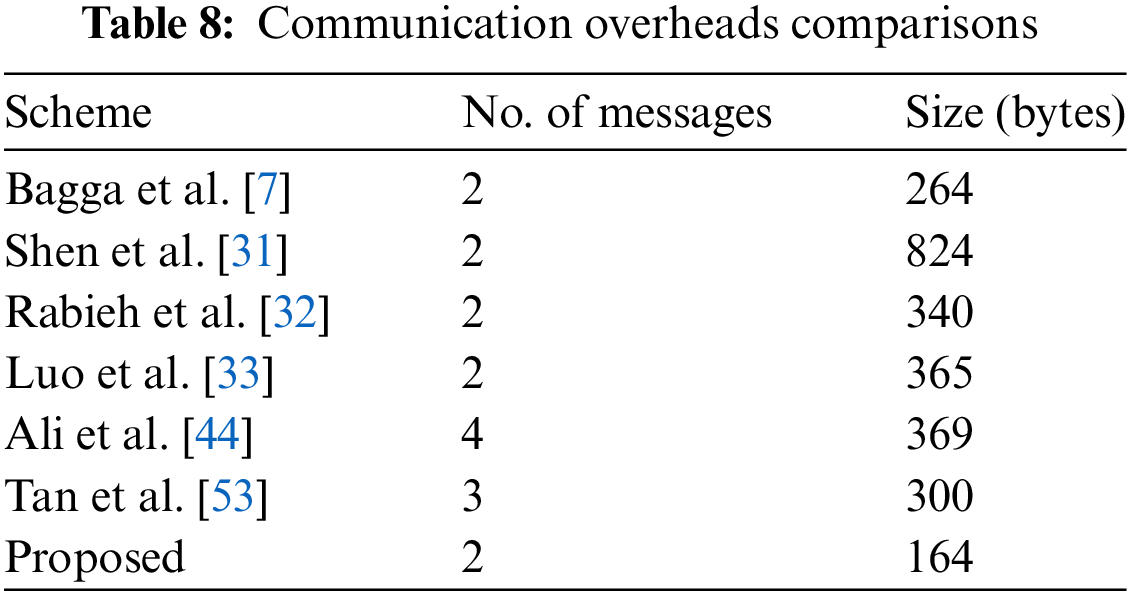
Similarly, the protocol in Reference [7] requires two messages to fully execute authentication and key agreement. The first message is the authentication message {TIDi, VFi, VGi, VLi, r1, TSVi}, which is sent from Vi to TA, the size of which is 116 bytes. The second message is the authentication replay {Qi, V2, V3, V4,
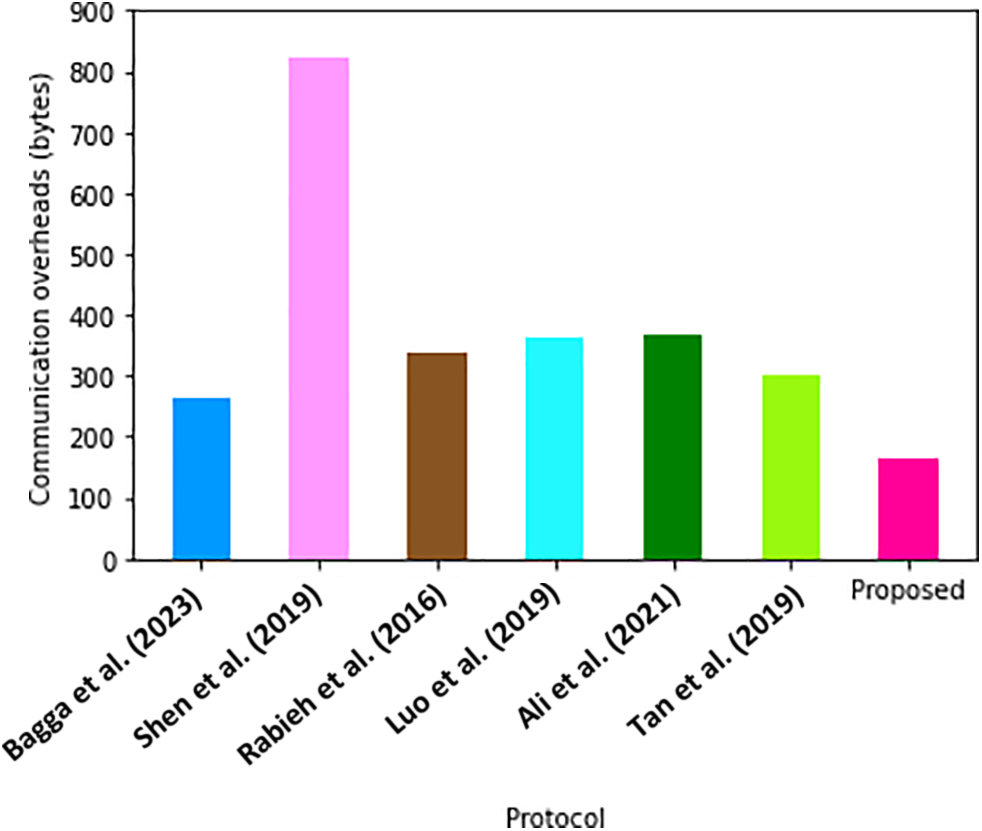
Figure 5: Comparative evaluation of communication overheads [7,31–33,44,53]
Considering the communication limitations in most VANET devices, such as OBUs, the proposed technique is the most applicable in this environment.
5.3 Supported Security Features
This sub-section evaluates our protocol and other related schemes against typical VANET attacks, including packet replays, message falsification, forgery, impersonation, and MitM. Additionally, these security techniques are analyzed based on whether or not they offer non-repudiation, authentication, conditional privacy, unlinkability, key secrecy, anonymity, and source and message integrity. Table 9 presents the results of this analysis.
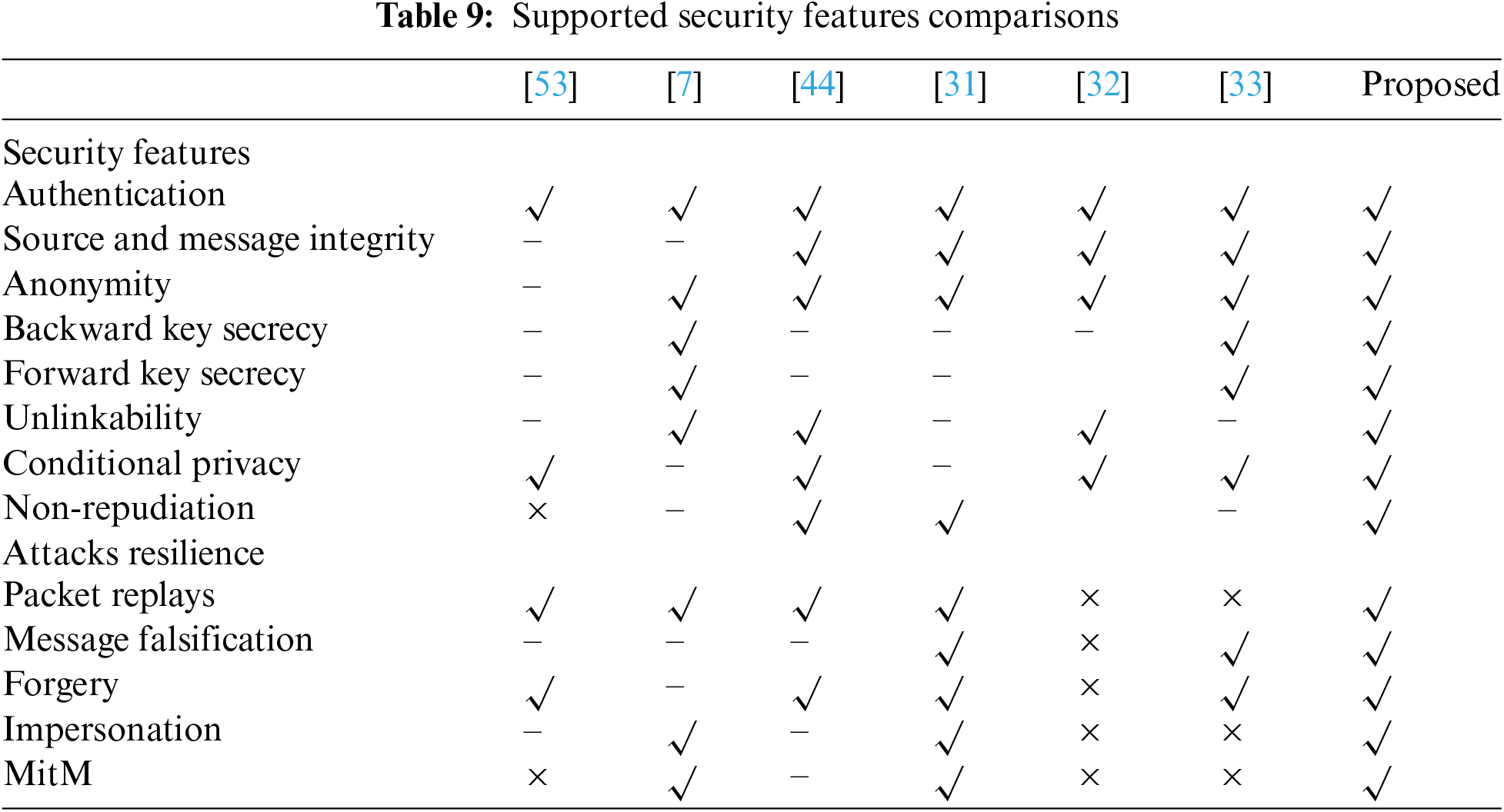
As shown in Table 9, the protocol in Reference [53] supports only four security features. Therefore, it is the most vulnerable. Those follow this protocol in Reference [32], which supports only five security features. The schemes in References [7,33,44] support eight security features each. However, the scheme in [31] supports nine security features. Meanwhile, the proposed protocol supports all 13 features. Therefore, it is the most secure. Using the nine security features in Reference [31] as bases, our approach evidently offers a 44.44% enhancement in the supported privacy and security features. Note that our protocol improves communication overhead by 37.88%. The proposed scheme provides enhanced security at minor communication costs and moderately short execution time.
This sub-section tests the performance of the proposed scheme under network simulators. Specifically, the proposed protocol is simulated in Network Simulator version 3 (NS3) in a 2000 m × 2000 m simulation area over a duration of 300 s. The MAC layer deployed is 802.11 p, while the transmission power is 50 mW. The data transmission rate is 6 Mbps, and broadcasting rate is 100 ms. In this environment, we test the efficiency of our protocol in terms of throughput, packet delivery ratio (PDR), and end-to-end (E2E) latency. In all simulation scenarios, the number of vehicles is increased from the initial value of 10 to a maximum of 100. As shown in Fig. 6, network throughput rises steadily as the number of vehicles is incremented.
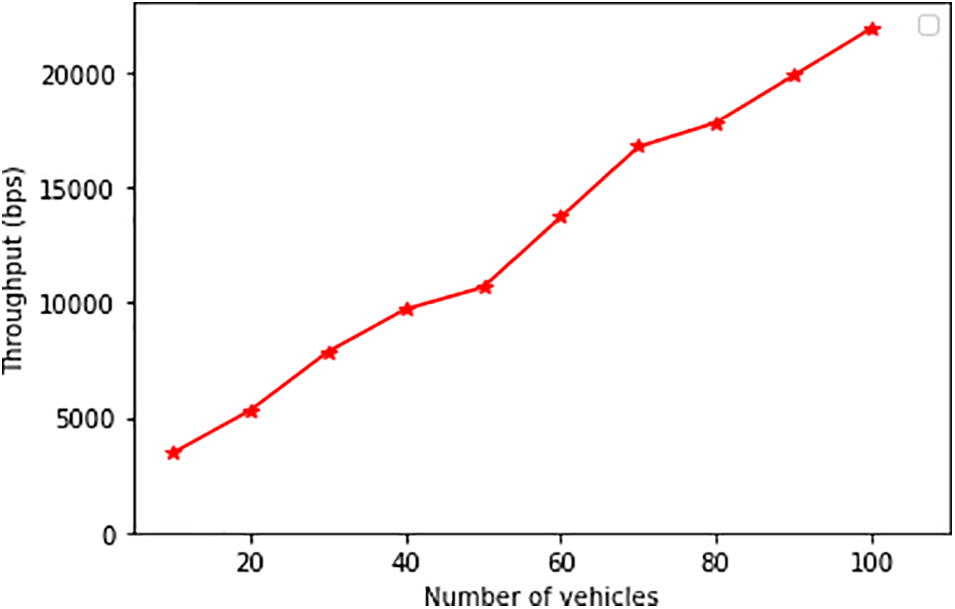
Figure 6: Network throughput
This finding is attributed to the high number of packets sent across the network when the number of vehicles surges. Fig. 7 shows the variations of packet delivery rate at different vehicle volumes.
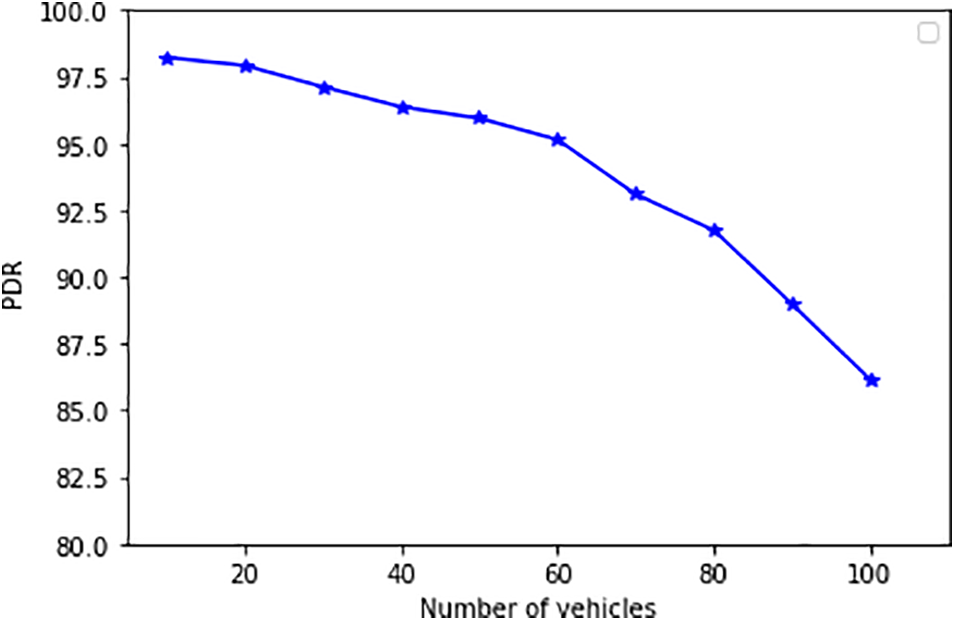
Figure 7: Network PDR
As Fig. 7 demonstrates, PDR decreases as the number of vehicles increases. This decline is a direct result of network congestions, which are triggered by the surge in packet volume during high traffic. These congestions lead to packet drops, thereby reducing the number of successfully delivered packets. Fig. 8 further illustrates the impact of increasing vehicular traffic on E2E latencies.
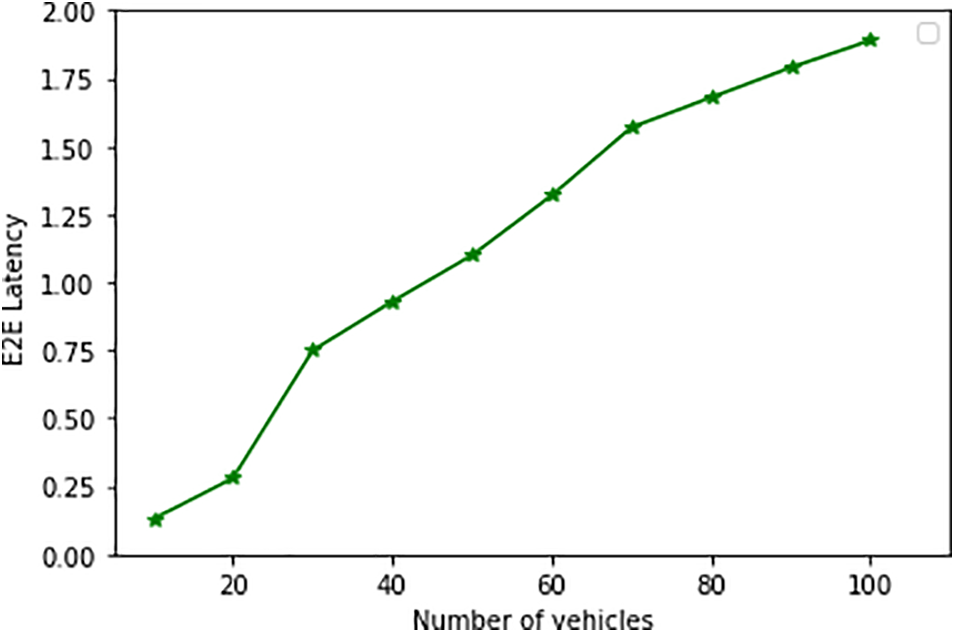
Figure 8: E2E latency
Fig. 8 shows an increase in E2E latencies as vehicles surge. At high traffic levels, end devices are overwhelmed with many data packets and requests that must be processed. Therefore, E2E generally increases as the number of vehicles in the network increases.
VANETs have been shown to face serious challenges in spite of their outstanding services, such as route management, intelligent navigation and file sharing. For example, malicious modification of driving route information can result in traffic jams, whilst illegitimate alteration of speed information can cause traffic accidents. Given that these issues directly affect human life and property safety, the development of strong message authentication schemes is extremely urgent. This aspect is particularly important because it will reduce the number of privacy and security violations that will eventually lead to the success of VANET applications. Hence, several security solutions have been presented in the recent past. Nevertheless, many of these schemes are either inefficient or are vulnerable to attacks. Accordingly, the proposed scheme has been demonstrated to be provably secure under the BAN logic model. It has also been shown to be robust against typical VANET attacks exampled by MitM, impersonations, forgery, replays and message falsification. The computation cost in our scheme is relatively lower compared with other BP-based techniques. Moreover, it results in a 44.44% improvement in the supported privacy and security features, as well as a 37.88% reduction in communication overheads.
Acknowledgement: Not applicable.
Funding Statement: This research is supported by Teaching Reform Project of Shenzhen University of Technology under Grant No. 20231016.
Author Contributions: The authors confirm contribution to the paper as follows: study conception and design: Vincent Omollo Nyangaresi, Arkan A. Ghaib, Hend Muslim Jasim, Zaid Ameen Abduljabbar, Junchao Ma; data collection: Mustafa A. Al Sibahee, Abdulla J. Y. Aldarwish, Ali Hasan Ali, Husam A. Neamah; analysis and interpretation of results: Vincent Omollo Nyangaresi, Arkan A. Ghaib, Hend Muslim Jasim, Zaid Ameen Abduljabbar, Junchao Ma; writing—original draft preparation: Mustafa A. Al Sibahee, Abdulla J. Y. Aldarwish, Ali Hasan Ali, Husam A. Neamah; writing—review and editing: Vincent Omollo Nyangaresi, Arkan A. Ghaib, Hend Muslim Jasim, Zaid Ameen Abduljabbar, Junchao Ma; supervision: Zaid Ameen Abduljabbar, Junchao Ma. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data that support the findings of this study are available from the corresponding author, upon reasonable request.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. X. Dai, Z. Xiao, H. Jiang, and J. C. S. Lui, “UAV-assisted task offloading in vehicular edge computing networks,” IEEE Trans. Mob. Comput., vol. 23, no. 4, pp. 2520–2534, 2023. doi: 10.1109/TMC.2023.3259394. [Google Scholar] [CrossRef]
2. G. Sun, Y. Zhang, H. Yu, X. Du, and M. Guizani, “Intersection fog-based distributed routing for V2V communication in urban vehicular ad hoc networks,” IEEE Trans. Intell. Transp. Syst., vol. 21, no. 6, pp. 2409–2426, 2019. doi: 10.1109/TITS.2019.2918255. [Google Scholar] [CrossRef]
3. Y. Ren, Z. Lan, L. Liu, and H. Yu, “EMSIN: Enhanced multi-stream interaction network for vehicle trajectory prediction,” IEEE Trans. Fuzzy Syst., pp. 1–15, 2024. doi: 10.1109/TFUZZ.2024.3360946. [Google Scholar] [CrossRef]
4. J. Zhang and Q. Zhang, “On the security of a lightweight conditional privacy-preserving authentication in VANETs,” IEEE Trans. Inform. Forensic. Sec., vol. 18, pp. 1037–1038, 2021. doi: 10.1109/TIFS.2021.3066277. [Google Scholar] [CrossRef]
5. Z. Xiao, J. Shu, H. Jiang, G. Min, H. Chen and Z. Han, “Perception task offloading with collaborative computation for autonomous driving,” IEEE J. Sel. Areas Commun., vol. 41, no. 2, pp. 457–473, 2022. doi: 10.1109/JSAC.2022.3227027. [Google Scholar] [CrossRef]
6. G. Sun, L. Song, H. Yu, V. Chang, X. Du and M. Guizani, “V2V routing in a VANET based on the autoregressive integrated moving average model,” IEEE Trans. Veh. Technol., vol. 68, no. 1, pp. 908–922, 2018. doi: 10.1109/TVT.2018.2884525. [Google Scholar] [CrossRef]
7. P. Bagga, A. K. Das, and J. J. Rodrigues, “Bilinear pairing-based access control and key agreement scheme for smart transportation,” Cyber Secur. Appl., vol. 1, 2023, Art. no. 100001. doi: 10.1016/j.csa.2022.100001. [Google Scholar] [CrossRef]
8. I. Ali, Y. Chen, N. Ullah, R. Kumar, and W. He, “An efficient and provably secure ECC-based conditional privacy-preserving authentication for vehicle-to-vehicle communication in VANETs,” IEEE Trans. Veh. Technol., vol. 70, no. 2, pp. 1278–1291, 2021. doi: 10.1109/TVT.2021.3050399. [Google Scholar] [CrossRef]
9. G. Sun, Y. Zhang, D. Liao, H. Yu, X. Du and M. Guizani, “Bus-trajectory-based street-centric routing for message delivery in Urban vehicular ad hoc networks,” IEEE Trans. Veh. Technol., vol. 67, no. 8, pp. 7550–7563, 2018. doi: 10.1109/TVT.2018.2828651. [Google Scholar] [CrossRef]
10. J. Zhang, H. Fang, H. Zhong, J. Cui, and D. He, “Blockchain-assisted privacy-preserving traffic route management scheme for fog-based vehicular ad-hoc networks,” IEEE Trans. Netw. Serv. Manage., vol. 20, pp. 2854–2868, 2023. doi: 10.1109/TNSM.2023.3238307. [Google Scholar] [CrossRef]
11. Z. Qu, X. Liu, and M. Zheng, “Temporal-spatial quantum graph convolutional neural network based on schrödinger approach for traffic congestion prediction,” IEEE Trans. Intell. Transp. Syst., vol. 24, pp. 8677–8686, 2022. doi: 10.1109/TITS.2022.3203791. [Google Scholar] [CrossRef]
12. K. A. -A. Mutlaq, V. O. Nyangaresi, M. A. Omar, and Z. A. Abduljabbar, “Symmetric key based scheme for verification token generation in internet of things communication environment,” in EAI Int. Conf. Appl. Cryptogr. Comput. Commun., Springer, 2022, pp. 46–64. doi: 10.1007/978-3-031-17081-2_4. [Google Scholar] [CrossRef]
13. G. Luo et al., “EdgeCooper: Network-aware cooperative LiDAR perception for enhanced vehicular awareness,” IEEE J. Sel. Areas Commun., vol. 42, pp. 207–222, 2023. doi: 10.1109/JSAC.2023.3322764. [Google Scholar] [CrossRef]
14. P. Bagga, A. K. Das, M. Wazid, J. J. P. C. Rodrigues, K. -K. R. Choo and Y. Park, “On the design of mutual authentication and key agreement protocol in internet of vehicles-enabled intelligent transportation system,” IEEE Trans. Veh. Technol., vol. 70, no. 2, pp. 1736–1751, 2021. doi: 10.1109/TVT.2021.3050614. [Google Scholar] [CrossRef]
15. H. Jiang, M. Wang, P. Zhao, Z. Xiao, and S. Dustdar, “A utility-aware general framework with quantifiable privacy preservation for destination prediction in LBSs,” IEEE/ACM Trans. Netw., vol. 29, no. 5, pp. 2228–2241, 2021. doi: 10.1109/TNET.2021.3084251. [Google Scholar] [CrossRef]
16. Z. Xiao et al., “Understanding private car aggregation effect via spatio-temporal analysis of trajectory data,” IEEE Trans. Cybern., vol. 53, no. 4, pp. 2346–2357, 2021. doi: 10.1109/TCYB.2021.3117705. [Google Scholar] [PubMed] [CrossRef]
17. J. Ma and J. Hu, “Safe consensus control of cooperative-competitive multi-agent systems via differential privacy,” Kybernetika, vol. 58, no. 3, pp. 426–439, 2022. doi: 10.14736/kyb-2022-3-0426. [Google Scholar] [CrossRef]
18. W. Li, W. Susilo, C. Xia, L. Huang, F. Guo and T. Wang, “Secure data integrity check based on verified public key encryption with equality test for multi-cloud storage,” IEEE Trans. Dependable Secur. Comput., pp. 1–15, 2024. doi: 10.1109/TDSC.2024.3375369. [Google Scholar] [CrossRef]
19. B. Chen, J. Hu, and B. K. Ghosh, “Finite-time tracking control of heterogeneous multi-AUV systems with partial measurements and intermittent communication,” Sci. China Inf. Sci., vol. 67, no. 5, 2024, Art. no. 152202. doi: 10.1007/s11432-023-3903-6. [Google Scholar] [CrossRef]
20. L. Zhao, H. Xu, S. Qu, Z. Wei, and Y. Liu, “Joint trajectory and communication design for UAV-assisted symbiotic radio networks,” IEEE Trans. Veh. Technol., vol. 73, pp. 8367–8378, 2024. doi: 10.1109/TVT.2024.3356587. [Google Scholar] [CrossRef]
21. X. Liu, Y. Wang, Z. Zhou, K. Nam, C. Wei and C. Yin, “Trajectory prediction of preceding target vehicles based on lane crossing and final points generation model considering driving styles,” IEEE Trans. Veh. Technol., vol. 70, no. 9, pp. 8720–8730, 2021. doi: 10.1109/TVT.2021.3098429. [Google Scholar] [CrossRef]
22. J. Thota, N. F. Abdullah, A. Doufexi, and S. Armour, “V2V for vehicular safety applications,” IEEE Trans. Intell. Transp. Syst., vol. 21, no. 6, pp. 2571–2585, 2019. doi: 10.1109/TITS.2019.2920738. [Google Scholar] [CrossRef]
23. Y. Li, Y. Qi, and L. Lu, Secure and Efficient V2V Communications for Heterogeneous Vehicle Ad Hoc Networks. Los Alamitos, CA, USA: IEEE, 2017, pp. 93–99. doi: 10.1109/NaNA.2017.54. [Google Scholar] [CrossRef]
24. V. O. Nyangaresi, Z. A. Abduljabbar, I. Y. Maolood, M. A. A. Sibahee, J. Ma and A. J. Y. Aldarwish, Transient Session Key Derivation Protocol for Key Escrow Prevention in Public Key Infrastructure. Switzerland: Springer, 2022, pp. 103–116. doi: 10.1007/978-3-031-25222-8_9. [Google Scholar] [CrossRef]
25. Y. Wang, H. Zhong, Y. Xu, J. Cui, and F. Guo, “Efficient extensible conditional privacy-preserving authentication scheme supporting batch verification for VANETs,” Secur. Commun. Netw., vol. 9, no. 18, pp. 5460–5471, 2016. doi: 10.1002/sec.1710. [Google Scholar] [CrossRef]
26. M. A. Al-Shareeda, M. Anbar, I. H. Hasbullah, S. Manickam, and S. M. Hanshi, “Efficient conditional privacy preservation with mutual authentication in vehicular ad hoc networks,” IEEE Access, vol. 8, pp. 144957–144968, 2020. doi: 10.1109/ACCESS.2020.3014678. [Google Scholar] [CrossRef]
27. J. Zhang, Q. Zhang, X. Lu, and Y. Gan, “A novel privacy-preserving authentication protocol using bilinear pairings for the VANET environment,” Wirel. Commun. Mob. Comput., vol. 2021, no. 1, 2021, Art. no. 6692568. doi: 10.1155/2021/6692568. [Google Scholar] [CrossRef]
28. S. Wang and N. Yao, “LIAP: A local identity-based anonymous message authentication protocol in VANETs,” Comput. Commun., vol. 112, pp. 154–164, 2017. doi: 10.1016/j.comcom.2017.09.005. [Google Scholar] [CrossRef]
29. S. H. Islam, M. S. Obaidat, P. Vijayakumar, E. Abdulhay, F. Li and M. K. C. Reddy, “A robust and efficient password-based conditional privacy preserving authentication and group-key agreement protocol for VANETs,” Future Gener. Comput. Syst., vol. 84, pp. 216–227, 2018. doi: 10.1016/j.future.2017.07.002. [Google Scholar] [CrossRef]
30. Z. A. Abduljabbar et al., “Session-dependent token-based payload enciphering scheme for integrity enhancements in wireless networks,” J. Sens. Actuator Netw., vol. 11, no. 3, 2022, Art. no. 55. doi: 10.3390/jsan11030055. [Google Scholar] [CrossRef]
31. J. Shen, D. Liu, X. Chen, J. Li, N. Kumar and P. Vijayakumar, “Secure real-time traffic data aggregation with batch verification for vehicular cloud in VANETs,” IEEE Trans. Veh. Technol., vol. 69, no. 1, pp. 807–817, 2019. doi: 10.1109/TVT.2019.2946935. [Google Scholar] [CrossRef]
32. K. Rabieh, M. M. Mahmoud, and M. Younis, “Privacy-preserving route reporting schemes for traffic management systems,” IEEE Trans. Veh. Technol., vol. 66, no. 3, pp. 2703–2713, 2016. doi: 10.1109/TVT.2016.2583466. [Google Scholar] [CrossRef]
33. M. Luo, Y. Wen, and X. Hu, “Practical data transmission scheme for wireless sensor networks in heterogeneous IoT environment,” Wirel. Pers. Commun., vol. 109, no. 1, pp. 505–519, 2019. doi: 10.1007/s11277-019-06576-8. [Google Scholar] [CrossRef]
34. B. Ying and A. Nayak, “Anonymous and lightweight authentication for secure vehicular networks,” IEEE Trans. Veh. Technol., vol. 66, no. 12, pp. 10626–10636, 2017. doi: 10.1109/TVT.2017.2744182. [Google Scholar] [CrossRef]
35. S. Yu, J. Lee, K. Lee, K. Park, and Y. Park, “Secure authentication protocol for wireless sensor networks in vehicular communications,” Sensors, vol. 18, no. 10, 2018, Art. no. 3191. doi: 10.3390/s18103191. [Google Scholar] [PubMed] [CrossRef]
36. M. J. Sadri and M. R. Asaar, “A lightweight anonymous two-factor authentication protocol for wireless sensor networks in Internet of Vehicles,” Int. J. Commun. Syst., vol. 33, no. 14, 2020, Art. no. e4511. doi: 10.1002/dac.4511. [Google Scholar] [CrossRef]
37. C. -M. Chen, B. Xiang, Y. Liu, and K. -H. Wang, “A secure authentication protocol for internet of vehicles,” IEEE Access, vol. 7, pp. 12047–12057, 2019. doi: 10.1109/ACCESS.2019.2891105. [Google Scholar] [CrossRef]
38. L. Wu et al., “An efficient privacy-preserving mutual authentication scheme for secure V2V communication in vehicular ad hoc network,” IEEE Access, vol. 7, pp. 55050–55063, 2019. doi: 10.1109/ACCESS.2019.2911924. [Google Scholar] [CrossRef]
39. H. Vasudev, V. Deshpande, D. Das, and S. K. Das, “A lightweight mutual authentication protocol for V2V communication in internet of vehicles,” IEEE Trans. Veh. Technol., vol. 69, no. 6, pp. 6709–6717, 2020. doi: 10.1109/TVT.2020.2986585. [Google Scholar] [CrossRef]
40. S. A. Alfadhli, S. Lu, K. Chen, and M. Sebai, “MFSPV: A multi-factor secured and lightweight privacy-preserving authentication scheme for VANETs,” IEEE Access, vol. 8, pp. 142858–142874, 2020. doi: 10.1109/ACCESS.2020.3014038. [Google Scholar] [CrossRef]
41. M. N. Aman, U. Javaid, and B. Sikdar, “A privacy-preserving and scalable authentication protocol for the internet of vehicles,” IEEE Internet Things J., vol. 8, no. 2, pp. 1123–1139, 2020. doi: 10.1109/JIOT.2020.3010893. [Google Scholar] [CrossRef]
42. T. Alladi, S. Chakravarty, V. Chamola, and M. Guizani, “A lightweight authentication and attestation scheme for in-transit vehicles in IoV scenario,” IEEE Trans. Veh. Technol., vol. 69, no. 12, pp. 14188–14197, 2020. doi: 10.1109/TVT.2020.3038834. [Google Scholar] [CrossRef]
43. V. O. Nyangaresi and N. Petrovic, “Efficient PUF based authentication protocol for internet of drones,” in 2021 Int. Telecommun. Conf. (ITC-Egypt), Alexandria, Egypt, 2021, pp. 1–4. doi: 10.1109/ITC-Egypt52936.2021.9513902. [Google Scholar] [CrossRef]
44. F. Ali, Y. Chen, N. Ullah, M. Afzal, and H. E. Wen, “Bilinear pairing-based hybrid signcryption for secure heterogeneous vehicular communications,” IEEE Trans. Veh. Technol., vol. 70, no. 6, pp. 5974–5989, 2021. doi: 10.1109/TVT.2021.3078806. [Google Scholar] [CrossRef]
45. A. K. Sutrala, P. Bagga, A. K. Das, N. Kumar, J. J. P. C. Rodrigues and P. Lorenz, “On the design of conditional privacy preserving batch verification-based authentication scheme for internet of vehicles deployment,” IEEE Trans. Veh. Technol., vol. 69, no. 5, pp. 5535–5548, 2020. doi: 10.1109/TVT.2020.2981934. [Google Scholar] [CrossRef]
46. J. Liu, A. Ren, L. Zhang, R. Sun, X. Du and M. Guizani, “A novel secure authentication scheme for heterogeneous internet of things,” in ICC, 2019-2019 IEEE Int. Conf. Commun. (ICC), Shanghai, China, 2019, pp. 1–6. doi: 10.1109/ICC.2019.8761951. [Google Scholar] [CrossRef]
47. M. Cui, D. Han, and J. Wang, “An efficient and safe road condition monitoring authentication scheme based on fog computing,” IEEE Internet Things J., vol. 6, no. 5, pp. 9076–9084, 2019. doi: 10.1109/JIOT.2019.2927497. [Google Scholar] [CrossRef]
48. Z. Lu, Q. Wang, G. Qu, H. Zhang, and Z. Liu, “A blockchain-based privacy-preserving authentication scheme for VANETs,” IEEE Trans. Very Large-Scale Integr. (VLSI) Syst., vol. 27, no. 12, pp. 2792–2801, 2019. doi: 10.1109/TVLSI.2019.2929420. [Google Scholar] [CrossRef]
49. H. Zhang and F. Zhao, “Cross-domain identity authentication scheme based on blockchain and PKI system,” High-Confid. Comput., vol. 3, no. 1, 2023, Art. no. 100096. doi: 10.1016/j.hcc.2022.100096. [Google Scholar] [CrossRef]
50. C. Lin, D. He, X. Huang, N. Kumar, and K. -K. R. Choo, “BCPPA: A blockchain-based conditional privacy-preserving authentication protocol for vehicular ad hoc networks,” IEEE Trans. Intell. Trans. Syst., vol. 22, no. 12, pp. 7408–7420, 2020. doi: 10.1109/TITS.2020.3002096. [Google Scholar] [CrossRef]
51. M. A. Shawky et al., “Blockchain-based secret key extraction for efficient and secure authentication in VANETs,” J. Inf. Secur. Appl., vol. 74, 2023, Art. no. 103476. doi: 10.1016/j.jisa.2023.103476. [Google Scholar] [CrossRef]
52. M. A. Shawky, M. Bottarelli, G. Epiphaniou, and P. Karadimas, “An efficient cross-layer authentication scheme for secure communication in vehicular ad-hoc networks,” IEEE Trans. Veh. Technol., vol. 72, no. 7, pp. 8738–8754, 2023. doi: 10.1109/TVT.2023.3244077. [Google Scholar] [CrossRef]
53. H. Tan and I. Chung, “Secure authentication and key management with blockchain in VANETs,” IEEE Access, vol. 8, pp. 2482–2498, 2019. doi: 10.1109/ACCESS.2019.2962387. [Google Scholar] [CrossRef]
54. Z. A. Abduljabbar, V. O. Nyangaresi, J. Ma, M. A. Al Sibahee, M. S. Khalefa and D. G. Honi, “MAC-based symmetric key protocol for secure traffic forwarding in drones,” in Future Access Enablers for Ubiquitous and Intelligent Infrastructures, Springer, 2022, pp. 16–36. doi: 10.1007/978-3-031-15101-9_2. [Google Scholar] [CrossRef]
55. J. Mou, K. Gao, P. Duan, J. Li, A. Garg and R. Sharma, “A machine learning approach for energy-efficient intelligent transportation scheduling problem in a real-world dynamic circumstance,” IEEE Trans. Intell. Trans. Syst., vol. 24, no. 12, pp. 15527–15539, 2022. doi: 10.1109/TITS.2022.3183215. [Google Scholar] [CrossRef]
56. Y. Yin, Y. Guo, Q. Su, and Z. Wang, “Task allocation of multiple unmanned aerial vehicles based on deep transfer reinforcement learning,” Drones, vol. 6, no. 8, 2022, Art. no. 215. doi: 10.3390/drones6080215. [Google Scholar] [CrossRef]
57. Y. Yang, L. Wei, J. Wu, C. Long, and B. Li, “A blockchain-based multidomain authentication scheme for conditional privacy preserving in vehicular ad-hoc network,” IEEE Internet of Things J., vol. 9, no. 11, pp. 8078–8090, 2021. doi: 10.1109/JIOT.2021.3107443. [Google Scholar] [CrossRef]
58. S. Son, J. Lee, Y. Park, K. Park, and A. K. Das, “Design of blockchain-based lightweight V2I handover authentication protocol for VANET,” IEEE Trans. Netw. Sci. Eng., vol. 9, no. 3, pp. 1346–1358, 2022. doi: 10.1109/TNSE.2022.3142287. [Google Scholar] [CrossRef]
59. S. A. Syed et al., “QoS aware and fault tolerance based software-defined vehicular networks using cloud-fog computing,” Sensors, vol. 22, no. 1, 2022, Art. no. 401. doi: 10.3390/s22010401. [Google Scholar] [PubMed] [CrossRef]
60. Y. Yao, B. Zhao, J. Zhao, F. Shu, Y. Wu and X. Cheng, “Anti-jamming technique for IRS aided JRC system in mobile vehicular networks,” IEEE Trans. Intell. Transp. Syst., vol. 25, pp. 12550–12560, 2024. doi: 10.1109/TITS.2024.3384038. [Google Scholar] [CrossRef]
61. X. Zeng, G. Xu, X. Zheng, Y. Xiang, and W. Zhou, “E-AUA: An efficient anonymous user authentication protocol for mobile IoT,” IEEE Internet of Things J., vol. 6, no. 2, pp. 1506–1519, 2018. doi: 10.1109/JIOT.2018.2847447. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF
 Downloads
Downloads
 Citation Tools
Citation Tools