 Open Access
Open Access
ARTICLE
Adaptive Update Distribution Estimation under Probability Byzantine Attack
Faculty of Computing, Harbin Institute of Technology, Harbin, 150000, China
* Corresponding Author: Zhaoxin Zhang. Email:
Computers, Materials & Continua 2024, 81(1), 1667-1685. https://doi.org/10.32604/cmc.2024.052082
Received 22 March 2024; Accepted 28 June 2024; Issue published 15 October 2024
Abstract
The secure and normal operation of distributed networks is crucial for accurate parameter estimation. However, distributed networks are frequently susceptible to Byzantine attacks. Considering real-life scenarios, this paper investigates a probability Byzantine (PB) attack, utilizing a Bernoulli distribution to simulate the attack probability. Historically, additional detection mechanisms are used to mitigate such attacks, leading to increased energy consumption and burdens on distributed nodes, consequently diminishing operational efficiency. Differing from these approaches, an adaptive updating distributed estimation algorithm is proposed to mitigate the impact of PB attacks. In the proposed algorithm, a penalty strategy is initially incorporated during data updates to weaken the influence of the attack. Subsequently, an adaptive fusion weight is employed during data fusion to merge the estimations. Additionally, the reason why this penalty term weakens the attack has been analyzed, and the performance of the proposed algorithm is validated through simulation experiments.Keywords
With rapid technological advancements, the emergence of sensor networks [1], the Internet of Things [2], and distributed systems [3,4] has presented unprecedented opportunities for data acquisition and information interaction. This influx of information offers immense potential for understanding and optimizing complex systems [5]. However, it also brings forth new challenges. In this age of information explosion, the efficient estimation of system parameters [6,7] has become a focal point of attention.
Distributed parameter estimation, a prominent research area in the fields of information science and engineering, strives to develop methods capable of extracting information about the state or characteristics of a system from distributed data sources [8,9]. Differing from traditional centralized estimation methods, distributed parameter estimation achieves inference of system parameters by leveraging observational data from multiple nodes scattered throughout the network [10–12]. The uniqueness of distributed networks lies in their adaptability to large-scale, dynamically changing environments, coupled with robustness and real-time capabilities. Consequently, the application of distributed networks is becoming increasingly widespread.
In distributed networks, the most representative algorithm is undoubtedly the diffusion least mean square (DLMS) algorithm because of its excellent adaptive capability and stable performance. Due to these advantages, the distributed DLMS algorithm has gained widespread adoption. For instance, in [13], a detailed derivation of the DLMS algorithm under Gaussian noise is presented, along with the algorithm’s convergence conditions. Based on this, Reference [14] considers pulse noise and proposes a distributed algorithm with the maximum correntropy criterion. These algorithms consider data fusion without delay. However, in some instances, communication delays may exist in the network. Therefore, Reference [15] investigates this scenario and provides insights into its data fusion methodology and performance analysis. These applications primarily focus on single-task parameter estimation. As applications become more complex, the occurrence of multi-task parameter estimation becomes more frequent. In [16], the authors investigate a multi-task distributed network that considers multiple parameter estimations and propose an adaptive multi-task parameter estimation algorithm. Besides, Reference [17] further studies the asynchronous sampling of multi-task estimation problem and then proposes a distributed estimation algorithm with asynchronous data fusion under a secure estimation environment. Despite the considerable expansion of these studies into various scenarios, it is noteworthy that they all assume the distributed network is normal. When a distributed network is invaded by attackers [7,18,19], it leads to the contamination of certain data, rendering it malicious. If there is no secure action to address these malicious data in the network, it cannot work properly. In other words, the network will estimate incorrect parameters [14,16,17]. In recent years, an increasing number of strategies have been designed to counteract intrusion attacks. In [19], the research focuses on attacks targeting sensing and communication processes and proposes a secure distributed estimation algorithm. In [20], the impact of a false data injection attack is investigated, and a data cross-validation strategy is designed. Apart from these attacks, there is another common type in real-life scenarios: Byzantine attacks. This attack is more prevalent and easier for attackers in daily life. The characteristics of such attacks have been studied in [21,22]. To mitigate the impact of Byzantine attack, a distributed estimation algorithm with a sign adaptation function gradient in DLMS (SA-DLMS) algorithm is proposed in [23], aiming to balance the abnormal gradient errors caused by Byzantine attacks and the errors from various abnormal data.
However, despite the numerous proposed counter-strategies against the Byzantine attack, most researchers still focus on this scenario where the Byzantine attack occurs throughout the entire process. In other words, the Byzantine attack is present throughout the entire algorithm execution. This attack model does not align with the intention of attackers in real-world situations. The occurrence probability of an attack should be random and determined by the attackers. Differing from these studies, this paper primarily investigates a type of probability Byzantine (PB) attack based on real-life scenarios. Furthermore, their existing secure algorithms typically rely on additional detection mechanisms to identify Byzantine attack, thereby increasing the operational burden and energy consumption of distributed nodes. Moreover, their algorithms may not necessarily optimize the performance of the detection algorithm. To address these issues, this paper designs an adaptive penalty strategy to mitigate the impact of PB attack. Subsequently, an adaptive distributed estimation algorithm with adaptive fusion weights is designed based on this strategy. Through mathematical analysis and simulations, it is evident that regardless of whether the network is under PB attack or what the probability of attack is, the proposed algorithm can consistently achieve optimal estimation.
The main contributions of this paper are concluded as:
1) A probability Byzantine attack whose probabilistic attack model adheres to a Bernoulli distribution, more aligned with the real-life scenario, is studied.
2) An adaptive update distributed estimation algorithm is proposed, which incorporates an adaptive penalty strategy and adaptive fusion weight, to mitigate the impact of PB attack.
3) Mathematical analyses of the proposed algorithm are conducted to ascertain why it can effectively mitigate PB attacks, and its effectiveness is further validated through experiments.
The remaining part of the paper is organized as follows. In Section 2, the distributed network model is presented, and the PB attack model is proposed. In Section 3, the adaptive update algorithm with penalty mechanism and adaption fusion weight is designed. The convergence analysis of mathematical behavior is achieved in Section 4, and the simulation experiments are done in Section 5. In the last, Section 6 concludes the conclusion of this paper.
2 Network Model and Probability Byzantine Attack Model
Consider a distributed network composed of
where
In traditional Byzantine attack [18,26], the form of attack involves arbitrarily changing sensed data from normal data to malicious data that is unknown and different. This can be expressed by
where
In our real life, since the attacker can intrude into the nodes and tamper with the data, it must be a smarter kind of decision maker. In order to maximize data contamination, the attacker must be capable of inducing prolonged adverse effects with a certain amount of stored energy. That is, the attacker employs a more energy-efficient method to induce data contamination while maintaining the capability to sustain the attack for a longer duration. Consequently, in this paper, we study a stochastic Byzantine attack with a probabilistic form, which is more intelligent. Differing from (2), PB attack can be expressed as
where
Noting the attack form (3), if the attacker selects a suitable attack probability
3 Proposed Adaptive Update Algorithm
In this section, the distributed estimation algorithm is first introduced. Based upon this distributed algorithm, the adaptive update with penalty term strategy is designed. Furthermore, an adaptive weight fusion mechanism is proposed to enhance the algorithm’s estimation capabilities.
3.1 Distributed Estimation Algorithm
In the distributed network described in this paper, each node exchanges information exclusively with neighbor nodes within the set
where
Based on the cost function
where
and
In other References [13,20], the information fusion weight
and
where
3.2 Secure Distributed Estimation with Adaptive Update
Based on the above Section 2, it can be observed that in the presence of a PB attack, there is a significant data deviation between the perceived data and normal data. In contrast, normal data typically incurs relatively small errors, which is primarily influenced by noise
In the presence of PB attack, such penalty terms manifest minimal data updates, or even remain devoid of updates, whereas in the context of tolerable data differentials that may be caused by noise, they exhibit conventional data updates. Within the domain of difference-based penalty functions, prevalent exemplars include the Geman-McClure function, the Cauchy function, and the Huber function. The responsiveness of these functions to differentials is delineated in Fig. 1. The corresponding parameters of Cauchy function and Huber function are set as 0.9.
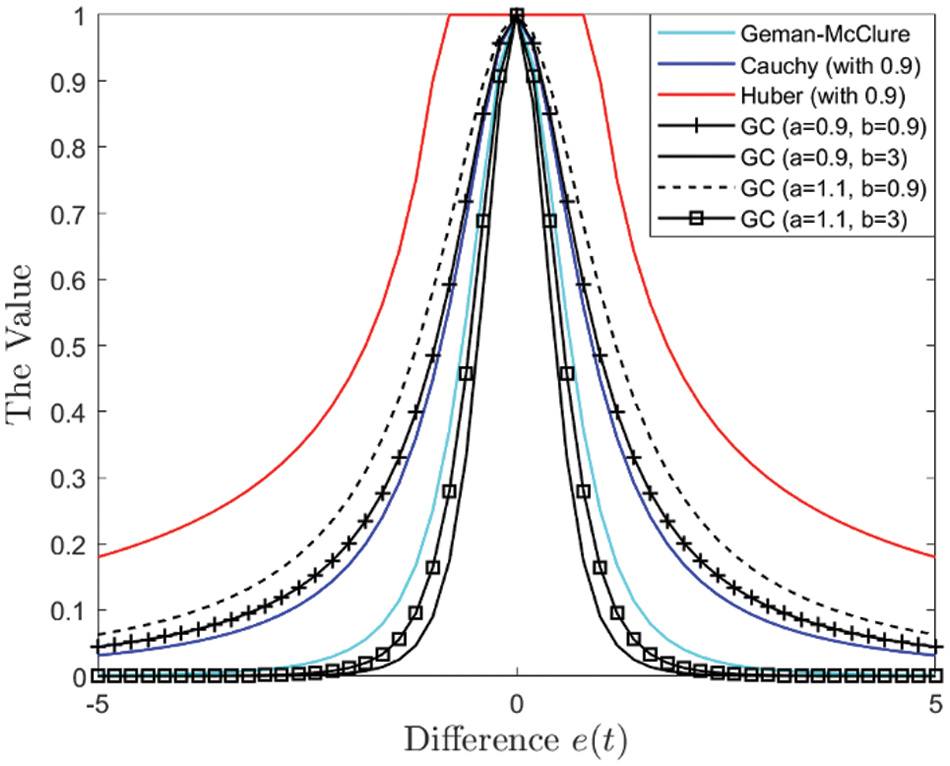
Figure 1: The reactions of difference under different functions
Based on the Geman-McClure function and the Cauchy function, an adaptive penalty term function can be devised and named as GC. Its mathematical formulation is expressed by the following equation:
where
Combining with the penalty term (10), the adaptive negative gradient update with penalty term can be designed as follows:
In other References [7,18,19,31], because the data may be tampered with by PB attack, the adaptation step could not fuse the neighbor information
where
and
Combining with the intermediate estimation
where
The adaptive weight
Since one has owned the neighboring information
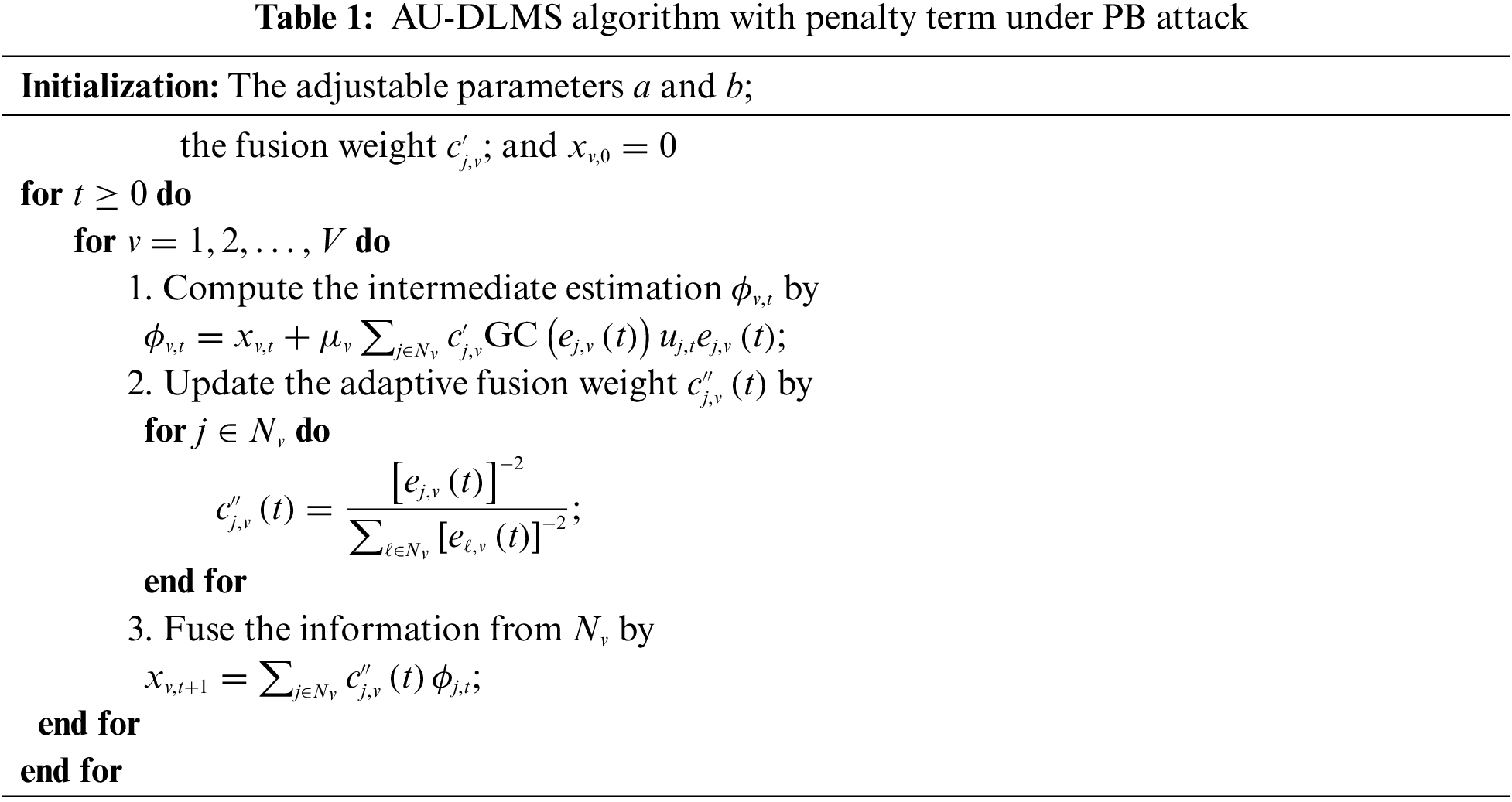
Therefore, we can derive the distributed adaptive update DLMS (AU-DLMS) algorithm with penalty term as follows:
and the proposed algorithm has been also summarized in Table 1.
4 Convergence Analysis of Mathematical Behavior
Convergence analysis is a crucial aspect for estimation algorithms to reach their optimal solutions. In this section, we will derive the convergence analyses of the proposed AU-DLMS algorithm from both mean and mean square behaviors. To better analyze this mathematical process, we first examine the convergence status of the normal nodes. Subsequently, based on the convergence status of these normal nodes, we analyze the situation of the malicious nodes invaded by PB attack.
According to the PB attack model (3), when node
To facilitate expression, we introduce the following formulas [32]:
and
Therefore, Formula (17) can be written as
Because of
Under the expectation
where
where
Based on the operational property of the spectral radius and the characteristic of fusion weight (7) from Formula (23), we can have
If Formula (24) can hold, the following condition need to be satisfied:
Based on Formula (25), we can get the following convergence condition:
From Fig. 1, it is found that
Therefore, when step-size
When node
where
Under Formula (28), the relation (21) becomes
Similarly, one has the following expectation operation:
Comparing Formulas (21) and (30), it can be observed that their difference lies in the following term:
Therefore, as long as the behavior of
Based on the characteristic of fusion weight (7), the convergence behavior of variable
Combining with (10), one has
When the node
Let
Therefore, (34) can be denoted as
In order to make analysis convenient, the function
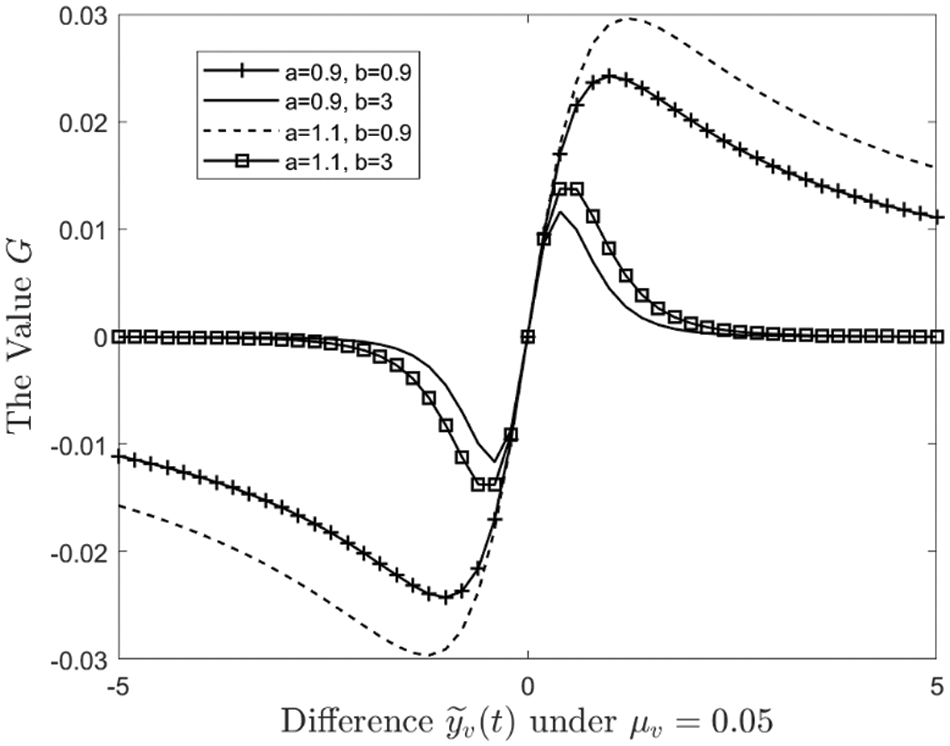
Figure 2: The function
Based on all above analysis, when node
In this section, to assess the efficacy of the proposed AU-DLMS algorithm in mitigating the impact of malicious attack nodes invaded by PB attack on the network, MSD and excess mean square error (EMSE) [13,18,31] are employed as the metric to gauge algorithm performance. At time
and the EMSE for the entire network is viewed as
In simulations, the distributed network is composed of
Figure 3: The distributed network
Figure 4: The distributed network under PB attack
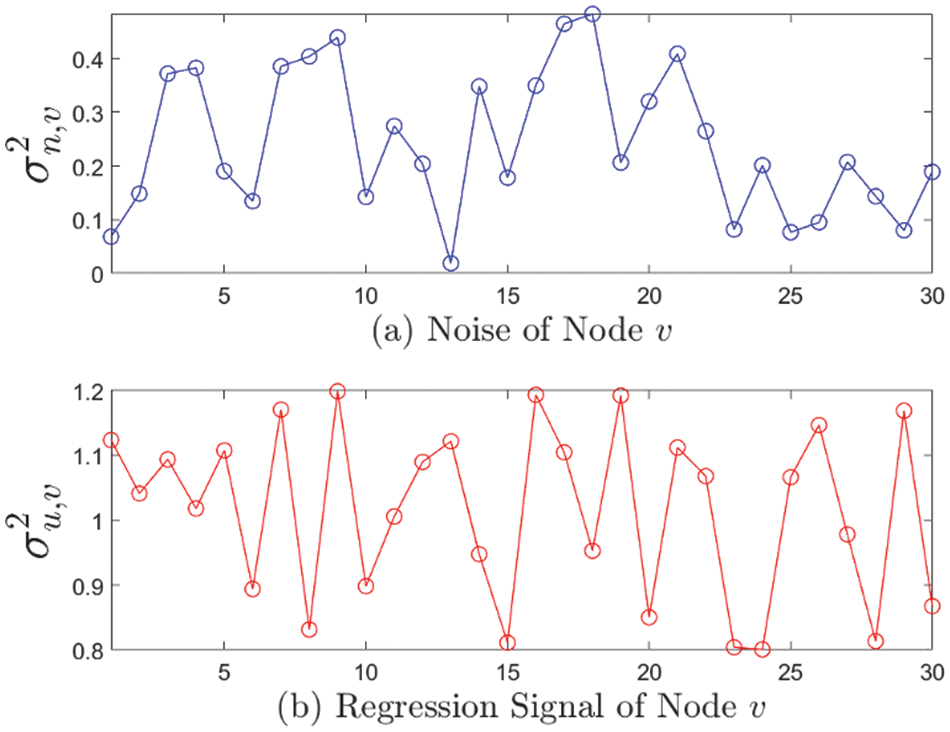
Figure 5: The variance of noise and regression signal
In the experimental simulations, to thoroughly demonstrate the performance of the proposed AU-DLMS algorithm, two sets of probabilistic experiments are conducted in the following parts. In the first set of experiments, these nodes invaded by PB attack are consistently subjected to attacks, implying that the PB attack probability is a complete probability. Subsequently, in the following set of experiments, these nodes invaded by PB attack are modeled according to a Binomial distribution.
In the first experiment, the attack probability of all malicious nodes is set to 1. That is, Byzantine attackers continuously expends energy to carry out consecutive attacks. Fig. 6 depicts transient MSD of different algorithms, and Fig. 7 shows the steady MSD of different nodes of different algorithms. Observing Figs. 6 and 7, it is evident from the NC-LMS algorithm curve that the performance of the five malicious nodes is markedly poor, while the other nodes maintain normal performance. Furthermore, it is observed that the DLMS algorithm exhibits significantly degraded performance when facing attacks without the implementation of security strategies. From these two curves, it is discernible that although the nodes intruded by attackers are minimal, such malicious behavior can exert a network-wide performance impact through cooperation among nodes. The SA-DLMS [23] algorithm demonstrates a certain level of adversarial resilience against PB attacks, but there still exist discernible performance fluctuations. Across both figures, it is apparent that the proposed AU-DLMS algorithm exhibits commendable stability in the face of attacks. Moreover, it is noticeable that the design of penalty mechanism can effectively enhance and improve estimation performance regardless of the presence of PB attack.
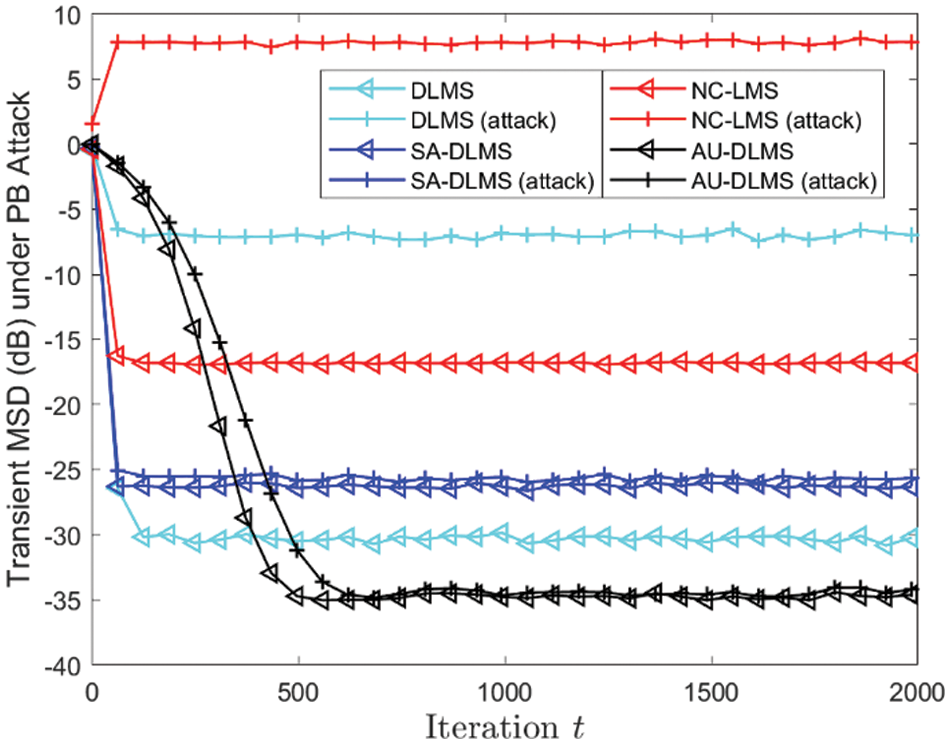
Figure 6: Transient MSD of different algorithms under PB attack with
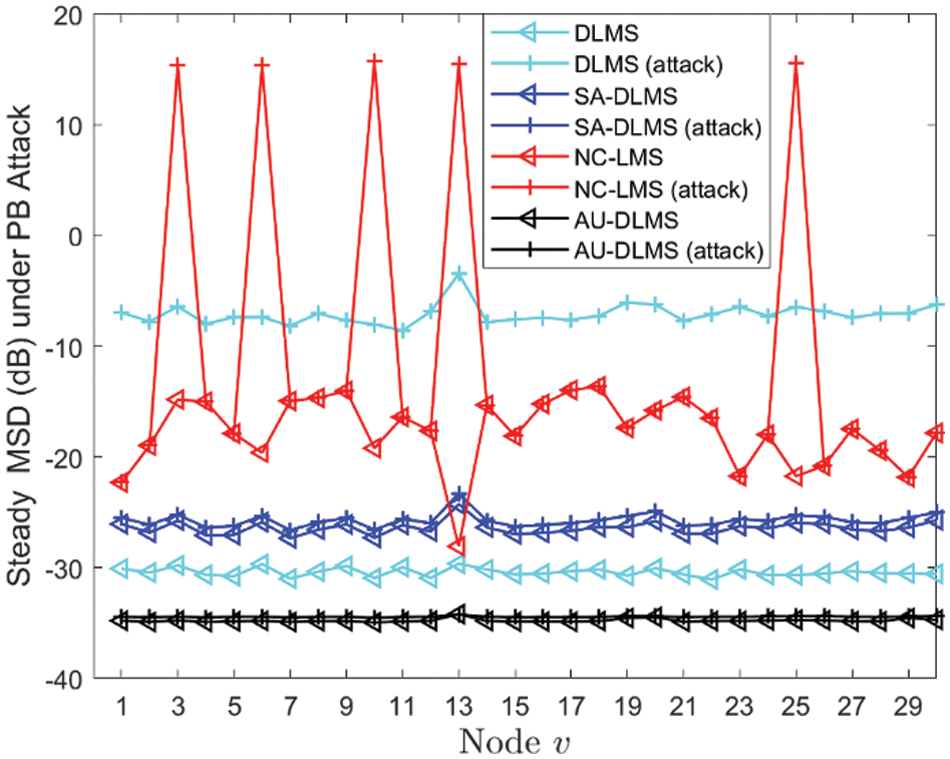
Figure 7: Steady MSD of different nodes of different algorithms under PB attack with
Fig. 8 depicts transient EMSE of different algorithms, and Fig. 9 shows the steady EMSE of different nodes of different algorithms. From these two figures, it can be observed that the EMSE performance of all curves aligns consistently with the MSD performance. It is also evident that the proposed AU-DLMS algorithm stands out as the optimal algorithm among all, irrespective of the presence of attacks.
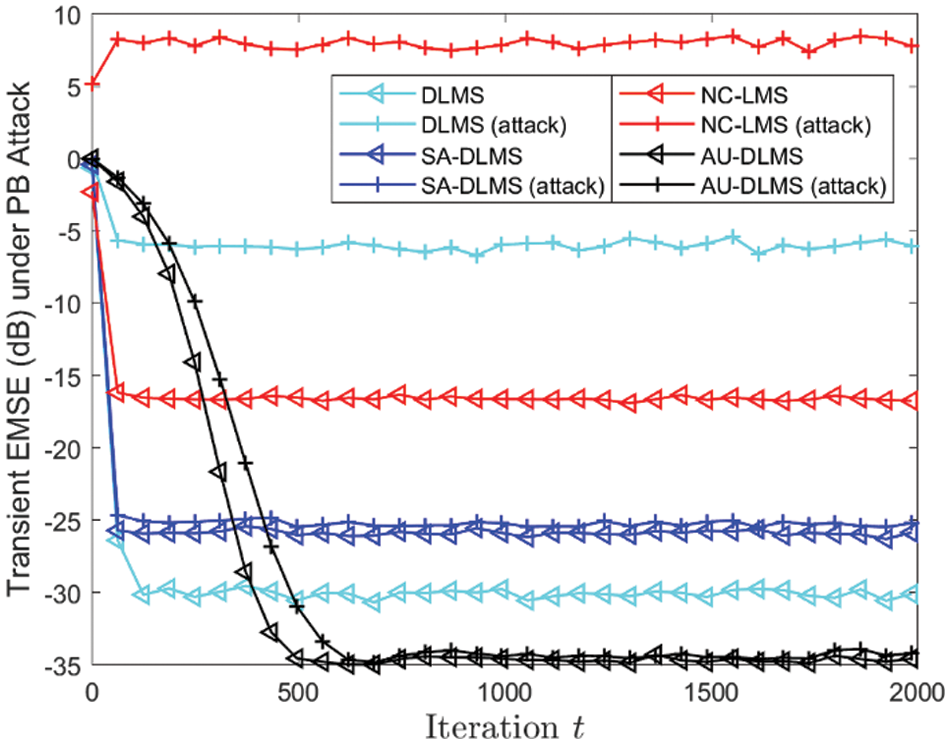
Figure 8: Transient EMSE of different algorithms under PB attack with
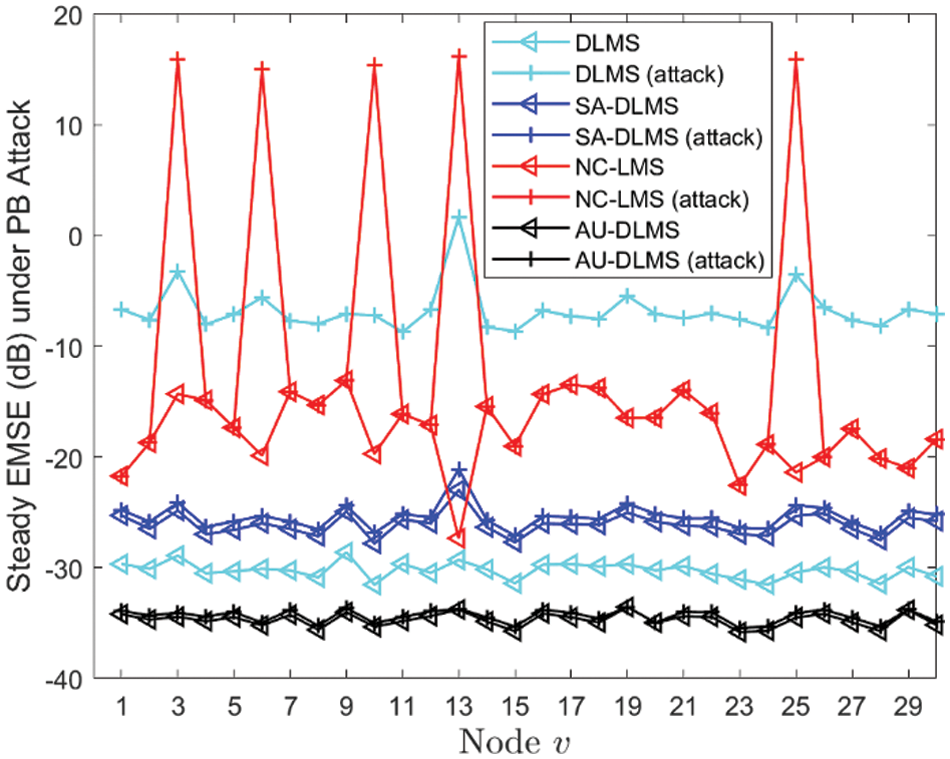
Figure 9: Steady EMSE of different nodes of different algorithms under PB attack with
In the second experiment, the attack probabilities for all malicious nodes are set to follow a Binomial distribution. The probabilities of nodes being attacked are set as 0.5, 0.6, 0.7, 0.8, and 0.9, respectively. Fig. 10 depicts transient MSD of different algorithms with different
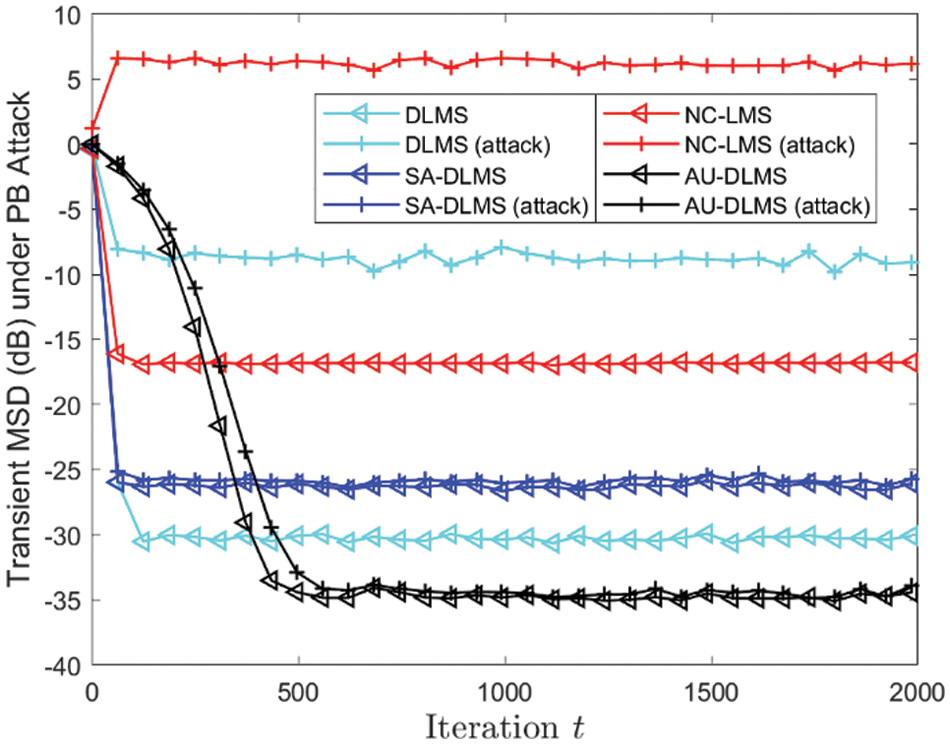
Figure 10: Transient MSD of different algorithms under PB attack with different
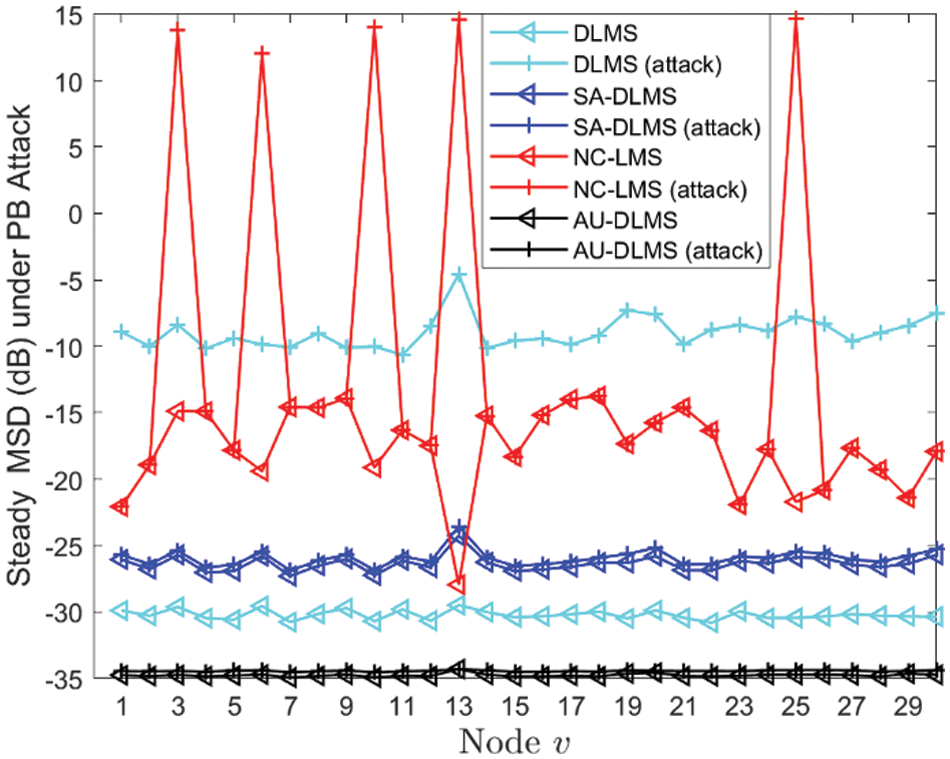
Figure 11: Steady MSD of different nodes of different algorithms under PB attack with different
Fig. 12 depicts transient EMSE of different algorithms with different
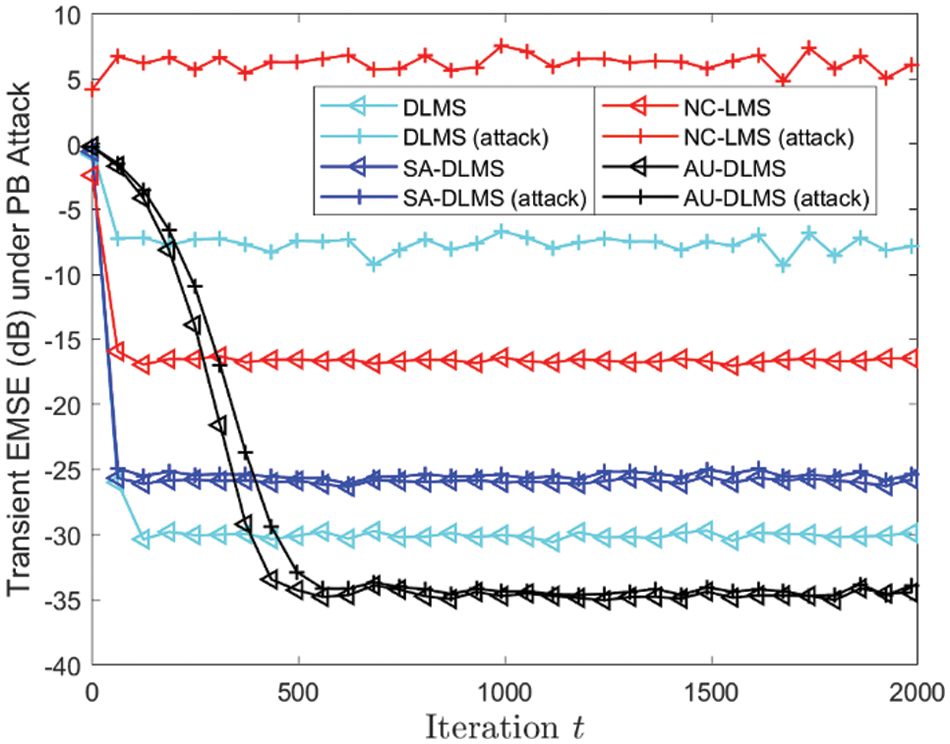
Figure 12: Transient EMSE of different algorithms under PB attack with different
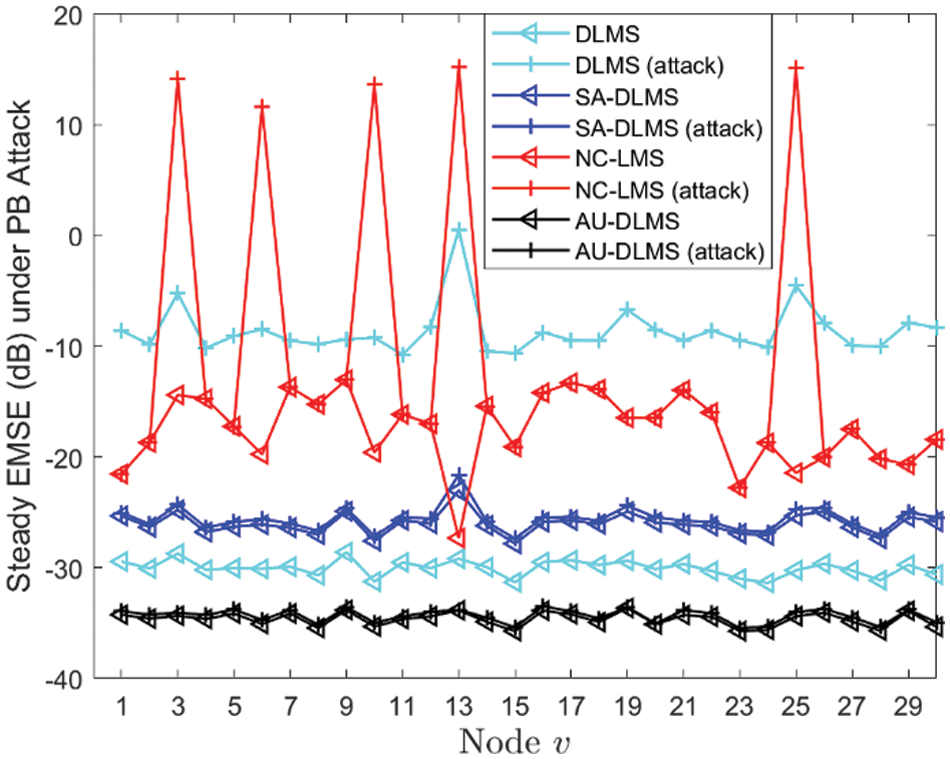
Figure 13: Steady EMSE of different nodes of different algorithms under PB attack with different
From all the simulation experiments, it is evident that even when attackers employ Byzantine attacks with certain probabilities, it can still have a detrimental impact on their estimation algorithms. This implies that attackers can utilize such probabilistic attack to inflict more enduring malicious effects. Therefore, employing the penalty strategy designed in this paper not only effectively mitigates these impacts but also improves the original estimation performance, which proves the effectiveness of the designed strategy. Hence, it can be considered that the proposed AU-DLMS algorithm exhibits superior advantages in distributed parameter estimation.
In this paper, a probability Byzantine attack is investigated, simulated by a Bernoulli distribution, which closely resembles real-life scenarios. To reduce energy consumption and alleviate the burden on distributed nodes, a penalty strategy is devised in the adaptation step. Subsequently, an adaptive fusion weight method is proposed to combine all intermediate estimations in the combination step. Through convergence analysis, a stability condition can be derived, ensuring the convergence of the distributed AU-DLMS algorithm if the step size satisfies this condition. Furthermore, the rationale behind the efficacy of this penalty item in weakening the attack has been analyzed. Simulation experiments have also been presented to validate the performance of the proposed algorithm. Through these simulations, it becomes evident that the AU-DLMS algorithm enhances estimation performance under normal network conditions and effectively mitigates the impact of PB attacks.
Future directions will include: (1) considering the design of the secure method for false data injection attacks and bad communication attacks; (2) considering the presence of the impulse noise; (3) considering the energy efficiency of the node.
Acknowledgement: We thank all the members who have contributed to this work with us.
Funding Statement: This work was not supported in part by any funding.
Author Contributions: The authors confirm contribution to the paper as follows. Gang Long: Study conception, design, and draft manuscript preparation; Zhaoxin Zhang: Simulation, analysis, interpretation of results and draft manuscript preparation. All authors reviewed the results and approved the final version of the manuscript.
Availability of Data and Materials: The data that support the findings of this study are available from the corresponding author.
Ethics Approval: Not applicable.
Conflicts of Interest: The authors declare that they have no conflicts of interest to report regarding the present study.
References
1. Y. Xia et al., “A trust-based reliable confident information coverage model of wireless sensor networks for intelligent transportation,” IEEE Trans. Vehicular Technol., vol. 72, no. 7, pp. 9542–9554, 2023. doi: 10.1109/TVT.2023.3253131. [Google Scholar] [CrossRef]
2. L. Hu, Z. Chen, Y. Jia, M. Wang, and T. Q. Quek, “Asymptotically optimal arrival rate for IoT networks with AoI and peak AoI constraints,” IEEE Commun. Lett., vol. 25, no. 12, pp. 3853–3857, 2021. doi: 10.1109/LCOMM.2021.3119350. [Google Scholar] [CrossRef]
3. F. Ullah, G. Srivastava, S. Ullah, and L. Mostarda, “Privacy-Preserving federated learning approach for distributed malware attacks with intermittent clients and image representation,” IEEE Trans. Consumer Electron., vol. 70, no. 1, pp. 4585–4596, Jan. 2023. doi: 10.1109/tce.2023.3342644. [Google Scholar] [CrossRef]
4. Y. Hua, F. Chen, S. Duan, and J. Wu, “Distributed data-selective DLMS estimation under channel attacks,” IEEE Access, vol. 7, pp. 83863–83872, 2019. doi: 10.1109/ACCESS.2019.2925009. [Google Scholar] [CrossRef]
5. F. Ullah, G. Srivastava, S. Ullah, K. Yoshigoe, Y. Zhao, “NIDS-VSB: Network intrusion detection system for VANET using spark-based big data optimization and transfer learning,” IEEE Trans. Consum. Electron., vol. 70, no. 1, pp. 1798–1809, Feb. 2024. doi: 10.1109/TCE.2023.3328320. [Google Scholar] [CrossRef]
6. H. Zayyani, “Robust minimum disturbance diffusion LMS for distributed estimation,” IEEE Trans. Circuits Syst. II: Express Briefs, vol. 68, no. 1, pp. 521–525, 2020. [Google Scholar]
7. F. Wan, T. Ma, Y. Hua, B. Liao, and X. Qing, “Secure distributed estimation under Byzantine attack and manipulation attack,” Eng. Appl. Artif. Intell., vol. 116, no. 1, 2022, Art. no. 105384. doi: 10.1016/j.engappai.2022.105384. [Google Scholar] [CrossRef]
8. Y. Hua, F. Wan, H. Gan, and B. Liao, “One-step asynchronous data fusion dlms algorithm,” IEEE Commun. Lett., vol. 25, no. 5, pp. 1660–1664, 2021. doi: 10.1109/LCOMM.2021.3049965. [Google Scholar] [CrossRef]
9. F. Ullah, S. Ullah, G. Srivastava, and J. C. Lin, “IDS-INT: Intrusion detection system using transformer-based transfer learning for imbalanced network traffic,” Digit. Commun. Netw., vol. 10, no. 1, pp. 190–204, Mar. 2023. doi: 10.1016/j.dcan.2023.03.008. [Google Scholar] [CrossRef]
10. F. Chen, S. Deng, Y. Hua, S. Duan, L. Wang and J. Wu, “Communication-reducing algorithm of distributed least mean square algorithm with neighbor-partial diffusion,” Circuits, Syst., Signal Process., vol. 39, no. 9, pp. 4416–4435, 2020. doi: 10.1007/s00034-020-01374-1. [Google Scholar] [CrossRef]
11. Z. Xu, Y. Liu, and C. Li, “Distributed semi-supervised learning with missing data,” IEEE Trans. Cybern., vol. 51, no. 12, pp. 6165–6178, 2020. doi: 10.1109/TCYB.2020.2967072. [Google Scholar] [PubMed] [CrossRef]
12. Y. Hua, F. Wan, B. Liao, Y. Zong, S. Zhu and X. Qing, “Adaptive multitask clustering algorithm based on distributed diffusion least-mean-square estimation,” Inf. Sci., vol. 606, no. 4, pp. 628–648, 2022. doi: 10.1016/j.ins.2022.05.074. [Google Scholar] [CrossRef]
13. F. S. Cattivelli and A. H. Sayed, “Diffusion LMS strategies for distributed estimation,” IEEE Trans. Signal Process., vol. 58, no. 3, pp. 1035–1048, 2009. doi: 10.1109/TSP.2009.2033729. [Google Scholar] [CrossRef]
14. F. Chen, X. Li, S. Duan, L. Wang, and J. Wu, “Diffusion generalized maximum correntropy criterion algorithm for distributed estimation over multitask network,” Digit. Signal Process., vol. 81, no. 4–5, pp. 16–25, 2018. doi: 10.1016/j.dsp.2018.02.008. [Google Scholar] [CrossRef]
15. F. Hua, R. Nassif, C. Richard, H. Wang, and A. H. Sayed, “Diffusion LMS with communication delays: Stability and performance analysis,” IEEE Signal Process. Lett., vol. 27, pp. 730–734, 2020. doi: 10.1109/LSP.2020.2990086. [Google Scholar] [CrossRef]
16. J. Chen, C. Richard, and A. H. Sayed, “Multitask diffusion adaptation over networks,” IEEE Trans. Signal Process., vol. 62, no. 16, pp. 4129–4144, 2014. doi: 10.1109/TSP.2014.2333560. [Google Scholar] [CrossRef]
17. Y. Hua, H. Gan, F. Wan, X. Qing, and F. Liu, “Distributed estimation with adaptive cluster learning over asynchronous data fusion,” IEEE Trans. Aerosp. Electron. Syst., vol. 59, no. 5, pp. 5262–5274, Oct. 2023. [Google Scholar]
18. J. Li, W. Abbas and X. Koutsoukos, “Resilient distributed diffusion in networks with adversaries,” IEEE Trans. Signal Inf. Process. Over Netw., vol. 6, pp. 1–17, 2019. [Google Scholar]
19. Y. Liu and C. Li, “Secure distributed estimation over wireless sensor networks under attacks,” IEEE Trans. Aerosp. Electron. Syst., vol. 54, no. 4, pp. 1815–1831, 2018. doi: 10.1109/TAES.2018.2803578. [Google Scholar] [CrossRef]
20. Y. Hua, F. Wan, H. Gan, Y. Zhang, and X. Qing, “Distributed estimation with cross-verification under false data-injection attacks,” IEEE Trans. Cybern., vol. 53, no. 9, pp. 5840–5853, 2023. doi: 10.1109/TCYB.2022.3197591. [Google Scholar] [PubMed] [CrossRef]
21. B. Kailkhura, Y. S. Han, S. Brahma, and P. K. Varshney, “Distributed Bayesian detection in the presence of Byzantine data,” IEEE Trans. Signal Process., vol. 63, no. 19, pp. 5250–5263, 2015. doi: 10.1109/TSP.2015.2450191. [Google Scholar] [CrossRef]
22. J. Wu et al., “Analysis of Byzantine attack strategy for cooperative spectrum sensing,” IEEE Commun. Lett., vol. 24, no. 8, pp. 1631–1635, 2020. doi: 10.1109/LCOMM.2020.2990869. [Google Scholar] [CrossRef]
23. J. Ni, J. Chen, and X. Chen, “Diffusion sign-error LMS algorithm: Formulation and stochastic behavior analysis,” Signal Process., vol. 128, no. 8, pp. 142–149, 2016. doi: 10.1016/j.sigpro.2016.03.022. [Google Scholar] [CrossRef]
24. B. Chen, L. Xing, J. Liang, N. Zheng, and J. C. Principe, “Steady-state mean-square error analysis for adaptive filtering under the maximum correntropy criterion,” IEEE Signal Process. Lett., vol. 21, no. 7, pp. 880–884, 2014. doi: 10.1109/LSP.2014.2319308. [Google Scholar] [CrossRef]
25. F. Wan, Y. Hua, B. Liao, T. Ma, and X. Qing, “Distributed estimation with novel adaptive data selection based on a cross-matching mechanism,” Circuits Syst., Signal Process., vol. 42, no. 10, pp. 6324–6346, 2023. doi: 10.1007/s00034-023-02410-6. [Google Scholar] [CrossRef]
26. D. Yin, Y. Chen, R. Kannan, and P. Bartlett, “Byzantine-robust distributed learning: Towards optimal statistical rates,” in Int. Conf. Mach. Learn, PMLR, Stockholm, Sweden, 2018, pp. 5650–5659. [Google Scholar]
27. H. Zayyani, F. Oruji, and I. Fijalkow, “An adversary-resilient doubly compressed diffusion LMS algorithm for distributed estimation,” Circuits Syst., Signal Process., vol. 41, no. 11, pp. 6182–6205, 2022. doi: 10.1007/s00034-022-02072-w. [Google Scholar] [CrossRef]
28. V. Shumovskaia, M. Kayaalp, and A. H. Sayed, “Distributed decision-making for community structured networks,” in Proc. IEEE Int. Conf. Acoust., Speech Signal Process (ICASSP), Seoul, Republic of Korea, 2024, pp. 9316–9320. [Google Scholar]
29. B. Chen, L. Xing, H. Zhao, N. Zheng, and J. C. Principe, “Generalized correntropy for robust adaptive filtering,” IEEE Trans. Signal Process., vol. 64, no. 13, pp. 3376–3387, 2016. doi: 10.1109/TSP.2016.2539127. [Google Scholar] [CrossRef]
30. Y. Hua, L. Hu, and F. Chen, “An adaptive malicious punishment over secure distributed estimation under attacks,” in 2018 IEEE 4th Int. Conf. Comput. Commun. (ICCC), Chengdu, China, 2018, IEEE, 2018, pp. 2195–2199. [Google Scholar]
31. Y. Hua, F. Chen, S. Deng, S. Duan, and L. Wang, “Secure distributed estimation against false data injection attack,” Inf. Sci., vol. 515, no. 8, pp. 248–262, 2020. doi: 10.1016/j.ins.2019.12.016. [Google Scholar] [CrossRef]
32. F. Chen, T. Shi, S. Duan, L. Wang, and J. Wu, “Diffusion least logarithmic absolute difference algorithm for distributed estimation,” Signal Process., vol. 142, no. 5, pp. 423–430, 2018. doi: 10.1016/j.sigpro.2017.07.014. [Google Scholar] [CrossRef]
Cite This Article
 Copyright © 2024 The Author(s). Published by Tech Science Press.
Copyright © 2024 The Author(s). Published by Tech Science Press.This work is licensed under a Creative Commons Attribution 4.0 International License , which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited.


 Submit a Paper
Submit a Paper Propose a Special lssue
Propose a Special lssue View Full Text
View Full Text Download PDF
Download PDF Downloads
Downloads
 Citation Tools
Citation Tools